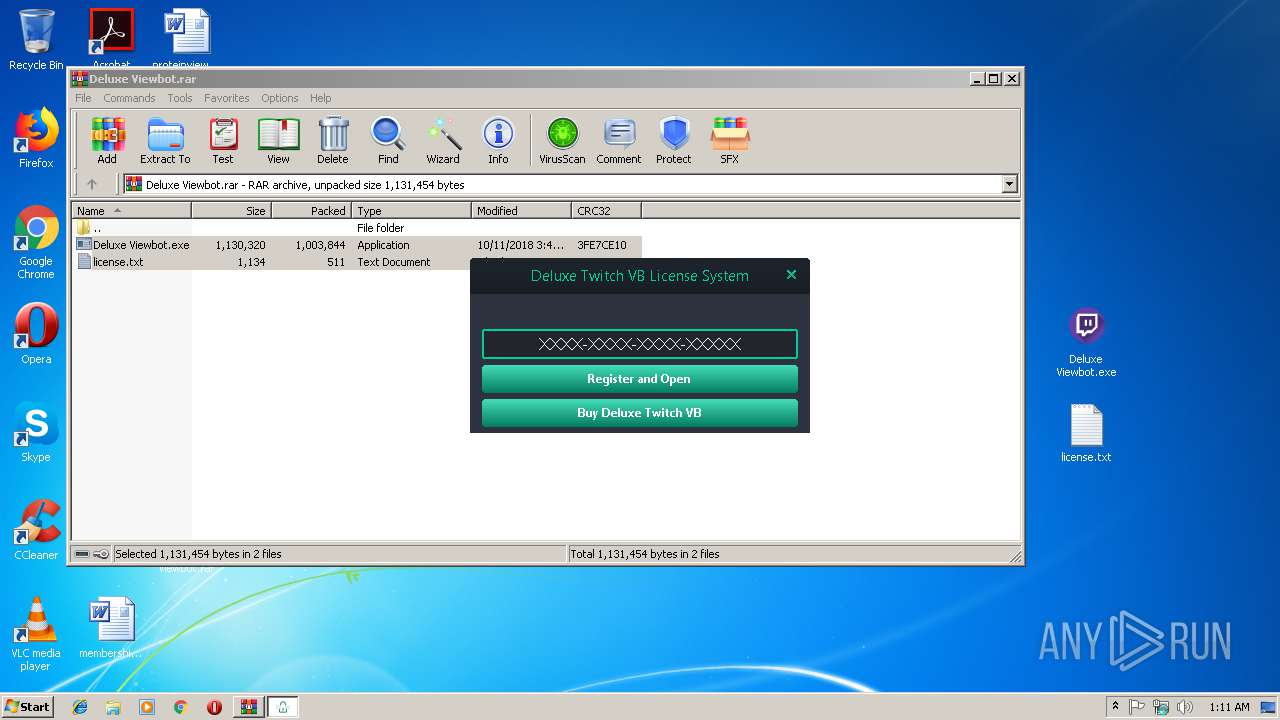
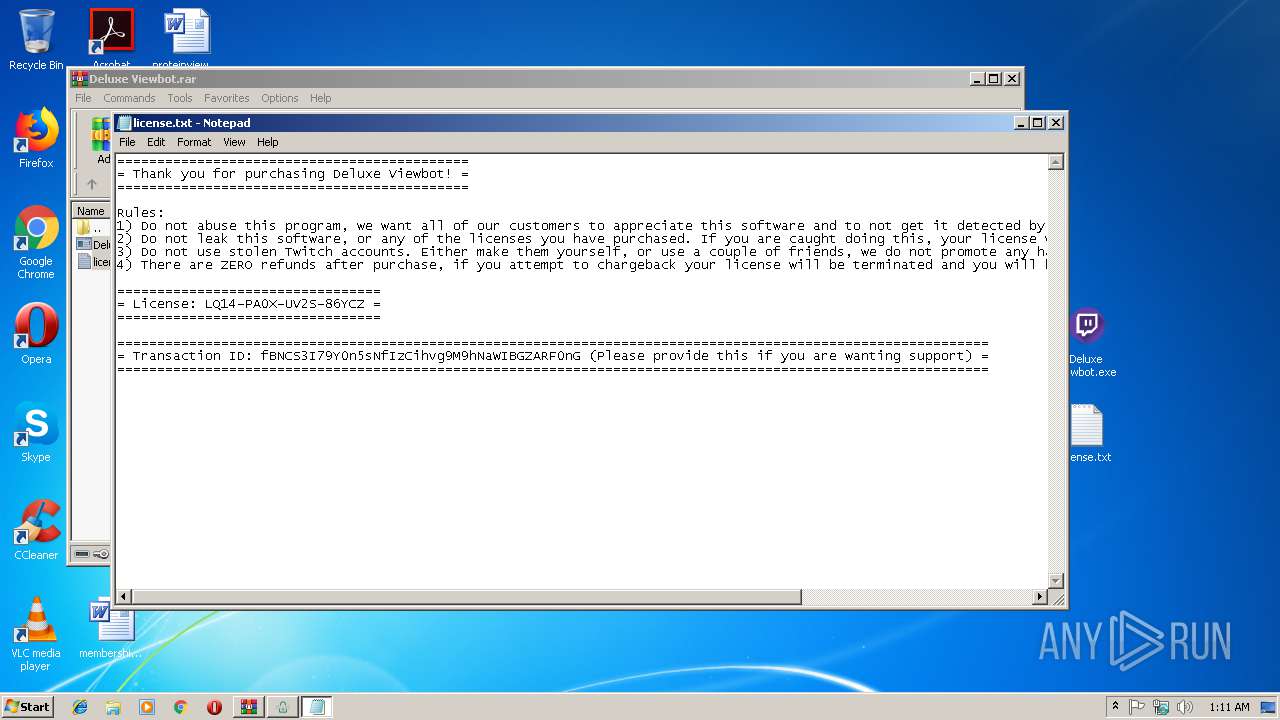
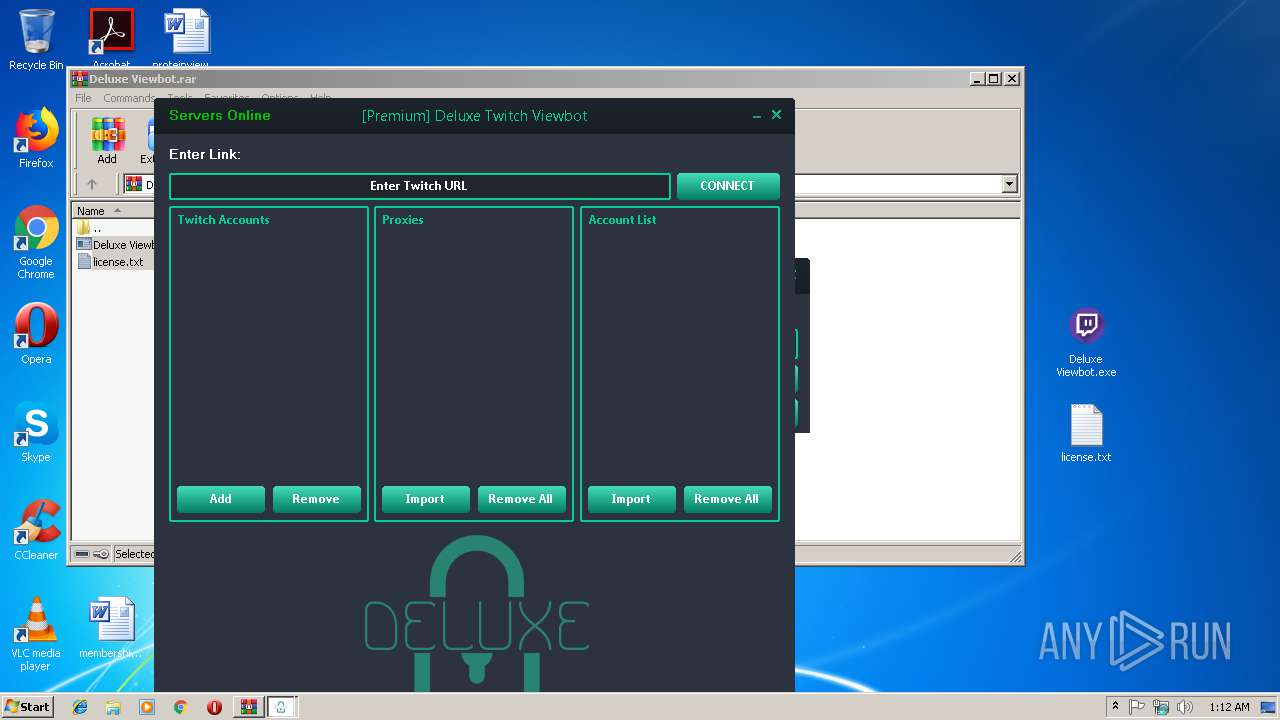
| File name: | Deluxe Viewbot.rar |
| Full analysis: | https://app.any.run/tasks/6f92ec43-089d-449a-afa2-b9dca6610e60 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | January 23, 2019, 01:11:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 37699B905519F2EDCC1D62A9025DD39F |
| SHA1: | DDA44FC5F8B428D012AC73F50DDFC8DF99F69485 |
| SHA256: | 323681FFD410D21D66D7E192CFB0D02348F9DE23F4D223237DACABCA742FF283 |
| SSDEEP: | 24576:c1GZoqKnrFXSZ6S3dx67PmHo3i4aZ+56op:2+cnBiwS3dxIaZ+56K |
MALICIOUS
Application was dropped or rewritten from another process
- Deluxe Viewbot.exe (PID: 2856)
- File.exe (PID: 2552)
- svhost.exe (PID: 2464)
Runs app for hidden code execution
- Deluxe Viewbot.exe (PID: 2856)
Changes the autorun value in the registry
- reg.exe (PID: 3968)
Orcus was detected
- svhost.exe (PID: 2464)
SUSPICIOUS
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3284)
Executable content was dropped or overwritten
- Deluxe Viewbot.exe (PID: 2856)
- cmd.exe (PID: 3284)
Starts CMD.EXE for commands execution
- Deluxe Viewbot.exe (PID: 2856)
Connects to unusual port
- svhost.exe (PID: 2464)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
42
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2132 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\license.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2464 | "C:\Users\admin\AppData\Local\Temp\svhost.exe" | C:\Users\admin\AppData\Local\Temp\svhost.exe | Deluxe Viewbot.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 3.5.30729.4926 built by: NetFXw7 Modules
| |||||||||||||||
| 2552 | "C:\Users\admin\AppData\Local\Temp\File.exe" | C:\Users\admin\AppData\Local\Temp\File.exe | — | Deluxe Viewbot.exe | |||||||||||
User: admin Company: Deluxe VB Integrity Level: MEDIUM Description: Deluxe Viewbot Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2808 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES4C0D.tmp" "c:\Users\admin\AppData\Local\Temp\CSC4BFC.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 8.00.50727.4940 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 2856 | "C:\Users\admin\Desktop\Deluxe Viewbot.exe" | C:\Users\admin\Desktop\Deluxe Viewbot.exe | explorer.exe | ||||||||||||
User: admin Company: Deluxe VB Integrity Level: MEDIUM Description: Deluxe Viewbot Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Deluxe Viewbot.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3284 | "cmd.exe" | C:\Windows\system32\cmd.exe | Deluxe Viewbot.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3528 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\xwdt_sru.cmdline" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\csc.exe | — | svhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 8.0.50727.4927 (NetFXspW7.050727-4900) Modules
| |||||||||||||||
| 3968 | reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\Windows API\hostapi.exe.lnk" /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
737
Read events
719
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Deluxe Viewbot.rar | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3072) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2856) Deluxe Viewbot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2856) Deluxe Viewbot.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3072.40311\Deluxe Viewbot.exe | — | |
MD5:— | SHA256:— | |||
| 3072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3072.40311\license.txt | — | |
MD5:— | SHA256:— | |||
| 3528 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC4BFC.tmp | — | |
MD5:— | SHA256:— | |||
| 2808 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES4C0D.tmp | — | |
MD5:— | SHA256:— | |||
| 3528 | csc.exe | C:\Users\admin\AppData\Local\Temp\xwdt_sru.dll | — | |
MD5:— | SHA256:— | |||
| 3528 | csc.exe | C:\Users\admin\AppData\Local\Temp\xwdt_sru.out | — | |
MD5:— | SHA256:— | |||
| 2856 | Deluxe Viewbot.exe | C:\Users\admin\AppData\Local\Temp\File.exe | executable | |
MD5:— | SHA256:— | |||
| 2856 | Deluxe Viewbot.exe | C:\Users\admin\AppData\Local\Temp\Windows API\hostapi.exe.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2464 | svhost.exe | C:\Users\admin\AppData\Local\Temp\xwdt_sru.0.cs | text | |
MD5:— | SHA256:— | |||
| 2856 | Deluxe Viewbot.exe | C:\Users\admin\AppData\Local\Temp\Windows API\hostapi.exe.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2464 | svhost.exe | 152.44.44.237:10115 | distantcheats.pw | Gardner-Webb University | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
distantcheats.pw |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |