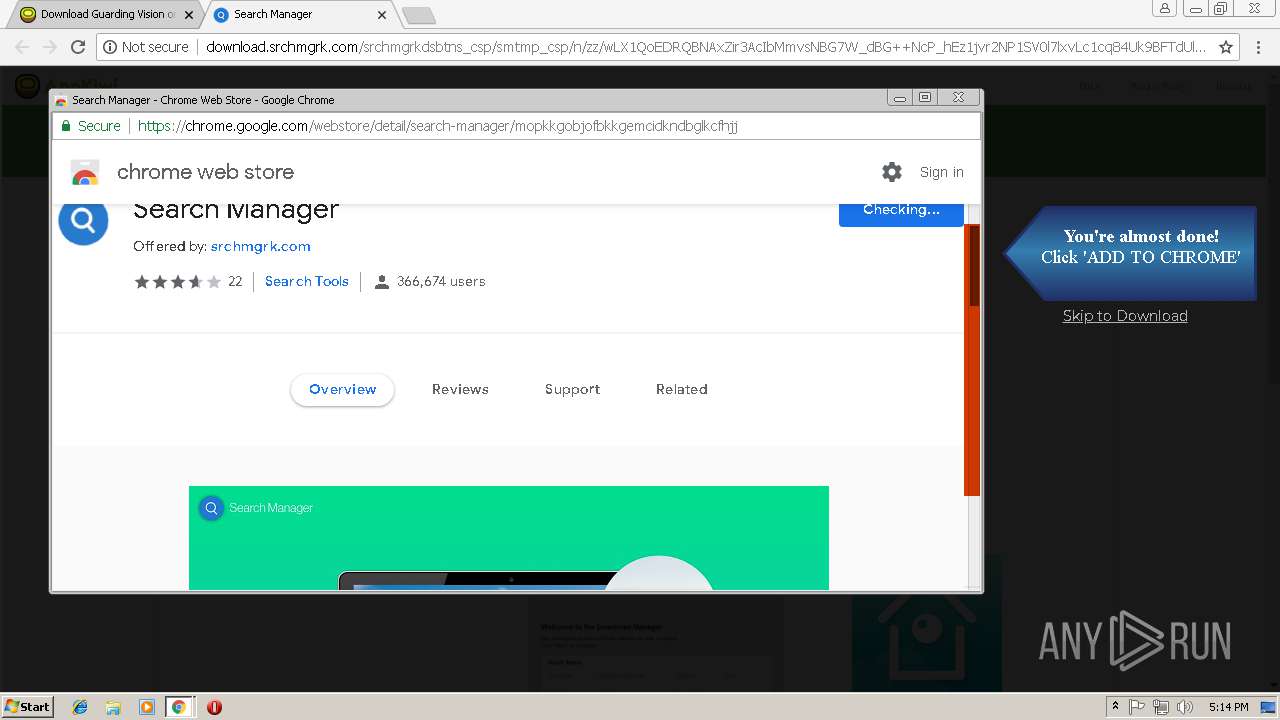
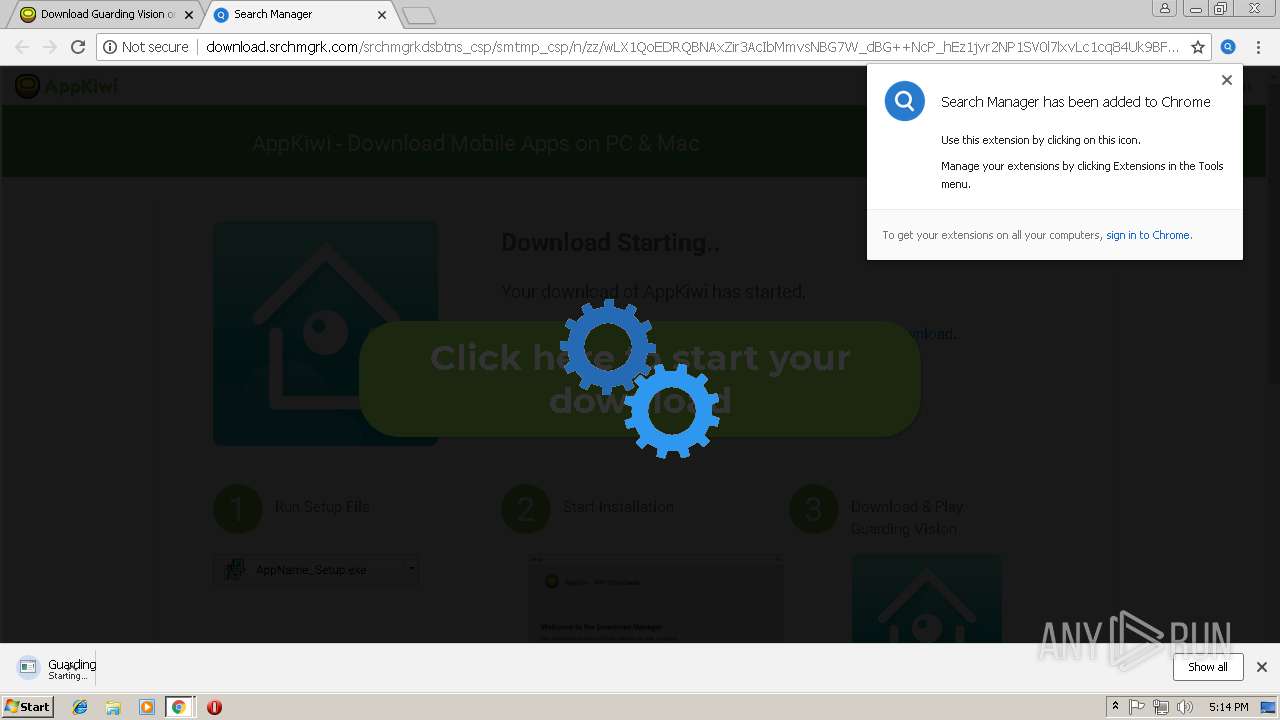
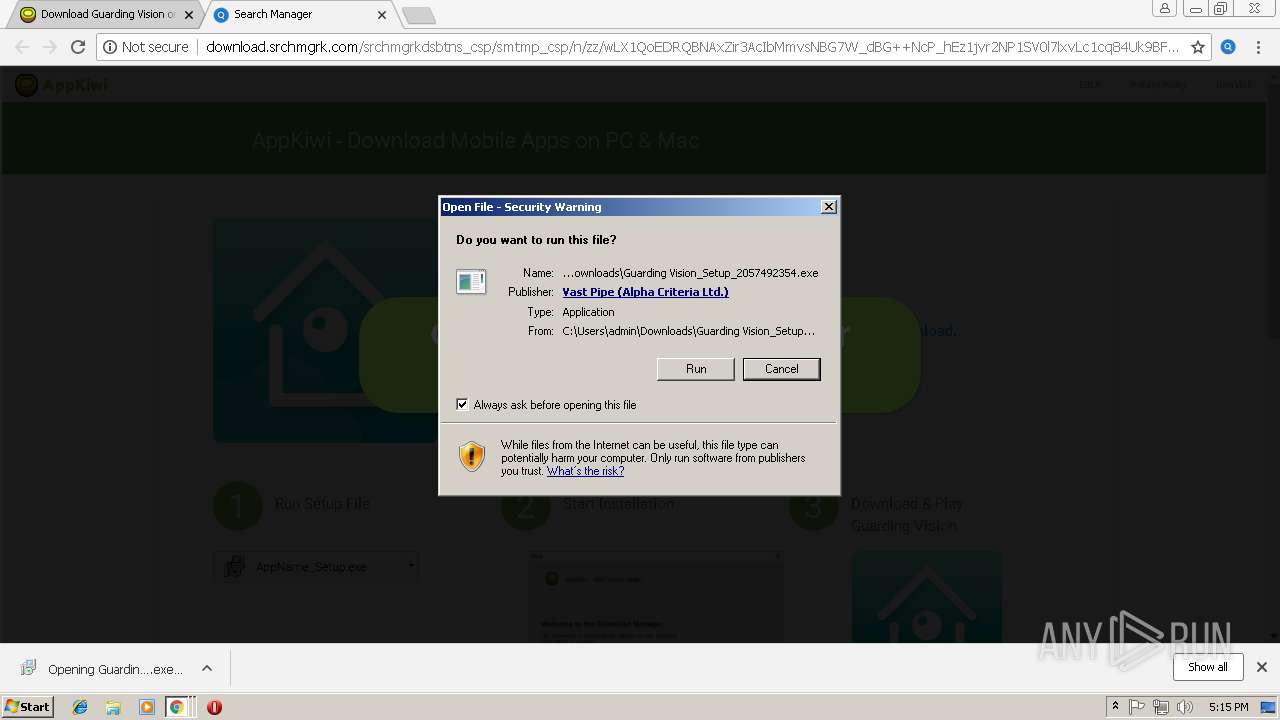
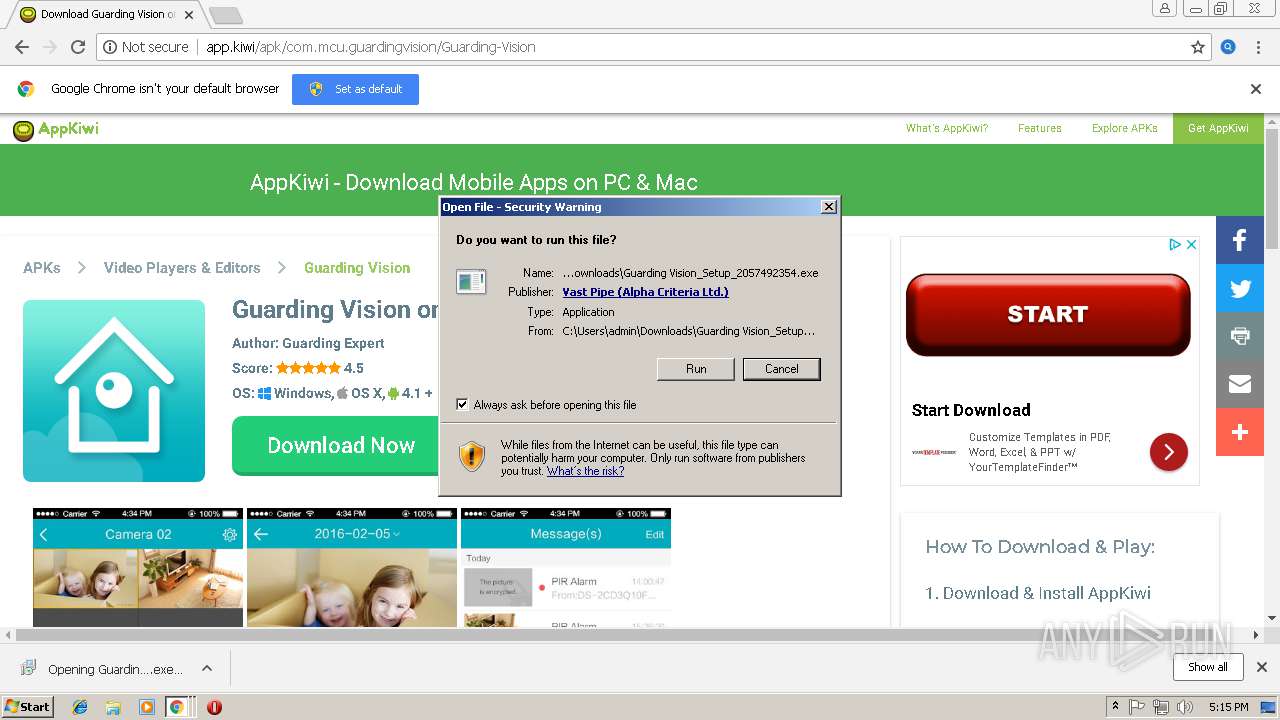
| URL: | http://app.kiwi/apk/com.mcu.guardingvision/Guarding-Vision |
| Full analysis: | https://app.any.run/tasks/f88d8619-ce2c-4b84-83c0-28e6ec357c7d |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | October 31, 2018, 17:13:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 25BFB7F7536C5E5C3DC786229422670F |
| SHA1: | 52FE41C218DA87A5DC0B5AB0AF8B804F55A78812 |
| SHA256: | 319B09EFCE9CF597D8DCFC9AB6B4CA17C6BD1AEE880613A381ED3592A91C1DEB |
| SSDEEP: | 3:N1Kf/SMfkBGLCz5HZj+L:CX/sBGu0 |
MALICIOUS
Application was dropped or rewritten from another process
- Guarding Vision_Setup_2057492354.exe (PID: 2220)
- Guarding Vision_Setup_2057492354.exe (PID: 892)
- OperaSetup.exe (PID: 912)
- OperaSetup.exe (PID: 2480)
- avgSetup.exe (PID: 2916)
- OperaSetup.exe (PID: 2300)
- OperaSetup.exe (PID: 2308)
- OperaSetup.exe (PID: 3836)
- OperaSetup.exe (PID: 3936)
- avg_antivirus_free_setup.exe (PID: 3996)
- instup.exe (PID: 1688)
- instup.exe (PID: 3836)
- sbr.exe (PID: 1972)
- installer.exe (PID: 3156)
- OperaSetup.exe (PID: 1688)
- launcher.exe (PID: 2320)
- installer.exe (PID: 572)
- opera.exe (PID: 3296)
- opera.exe (PID: 960)
- opera.exe (PID: 2504)
- opera.exe (PID: 3752)
- opera.exe (PID: 2860)
- opera.exe (PID: 1960)
- opera.exe (PID: 2652)
- opera.exe (PID: 2900)
- opera.exe (PID: 1016)
- opera.exe (PID: 2796)
- opera.exe (PID: 2372)
- opera_autoupdate.exe (PID: 504)
- opera.exe (PID: 2288)
- opera_crashreporter.exe (PID: 624)
- opera.exe (PID: 2824)
- opera_crashreporter.exe (PID: 1256)
- opera_crashreporter.exe (PID: 2008)
- opera_crashreporter.exe (PID: 2820)
- launcher.exe (PID: 3500)
- installer.exe (PID: 3144)
- opera.exe (PID: 3964)
- installer.exe (PID: 1764)
- opera_autoupdate.exe (PID: 5128)
- SetupInf.exe (PID: 1860)
- SetupInf.exe (PID: 2996)
- SetupInf.exe (PID: 5728)
- SetupInf.exe (PID: 4936)
- RegSvr.exe (PID: 3400)
- RegSvr.exe (PID: 5892)
- RegSvr.exe (PID: 1860)
- aswRunDll.exe (PID: 5796)
- wsc_proxy.exe (PID: 3604)
- instup.exe (PID: 5644)
- instup.exe (PID: 4684)
- AVGSvc.exe (PID: 6100)
- instup.exe (PID: 2424)
- AvEmUpdate.exe (PID: 1684)
- AvEmUpdate.exe (PID: 5324)
- AvEmUpdate.exe (PID: 6136)
- AvEmUpdate.exe (PID: 4288)
- AvEmUpdate.exe (PID: 4792)
- AVGUI.exe (PID: 5352)
Connects to CnC server
- Guarding Vision_Setup_2057492354.exe (PID: 892)
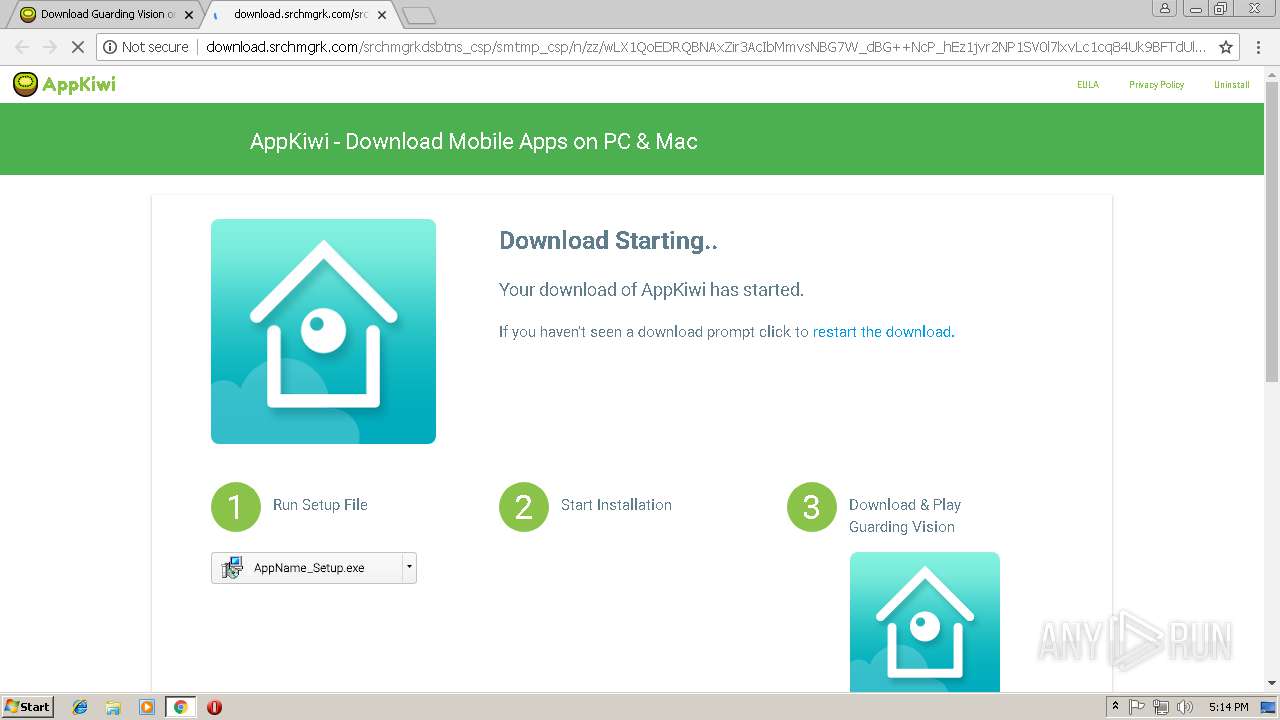
Downloads executable files from the Internet
- chrome.exe (PID: 2248)
- Guarding Vision_Setup_2057492354.exe (PID: 892)
- avgSetup.exe (PID: 2916)
- AvEmUpdate.exe (PID: 4288)
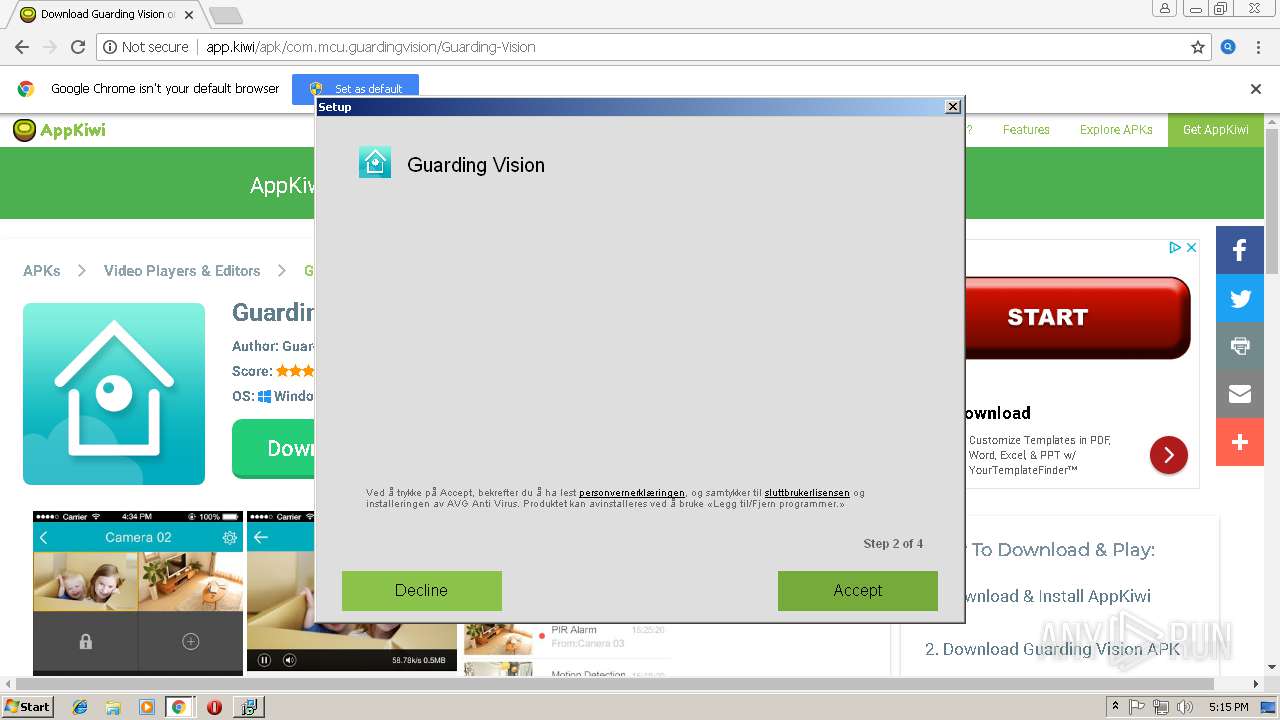
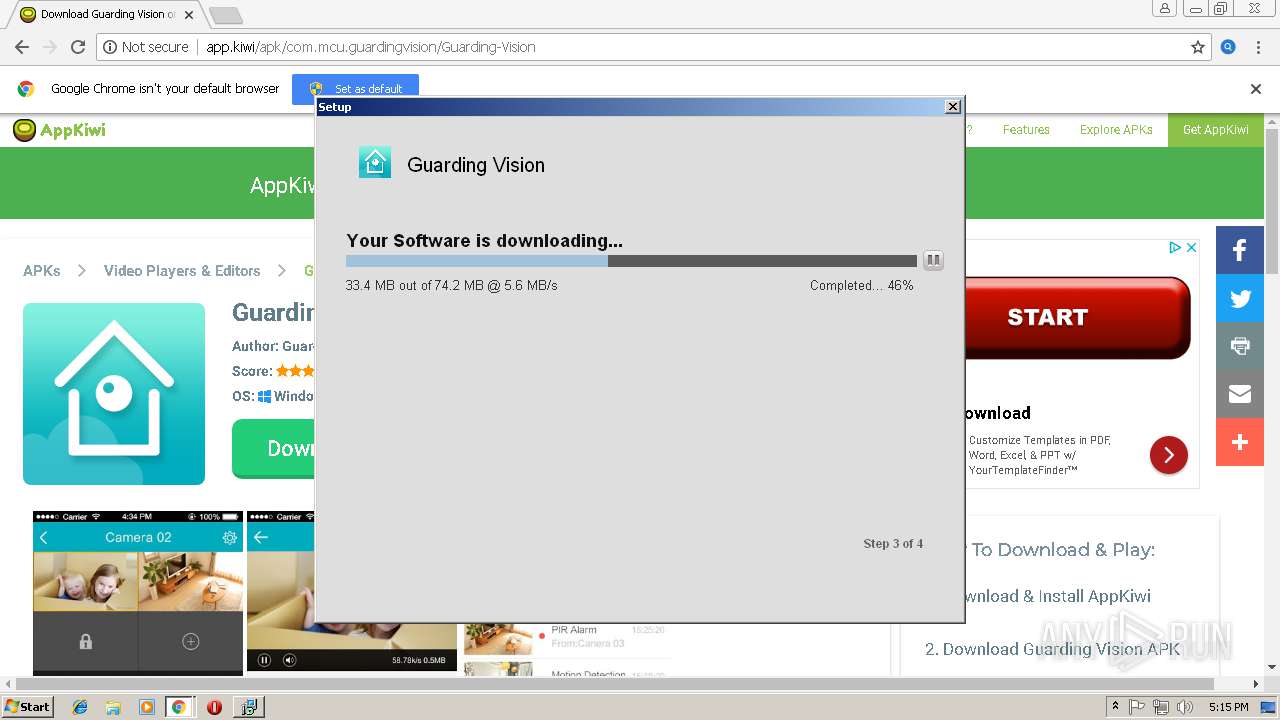
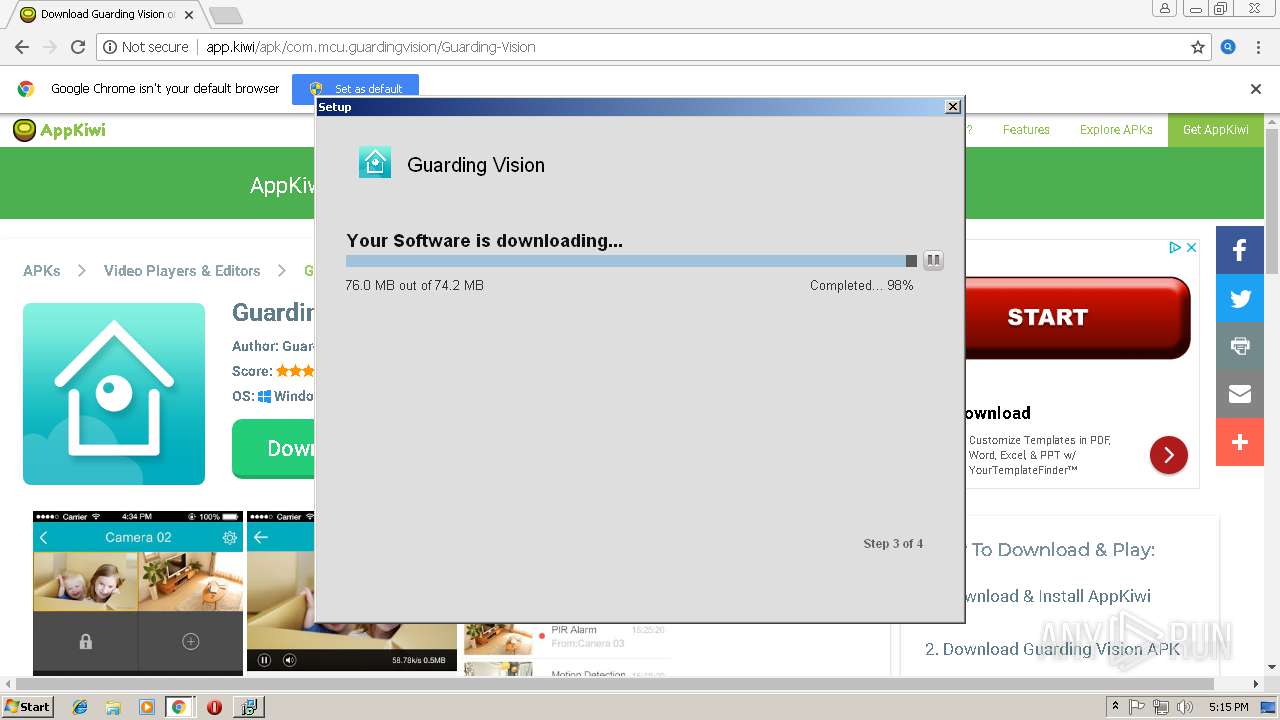
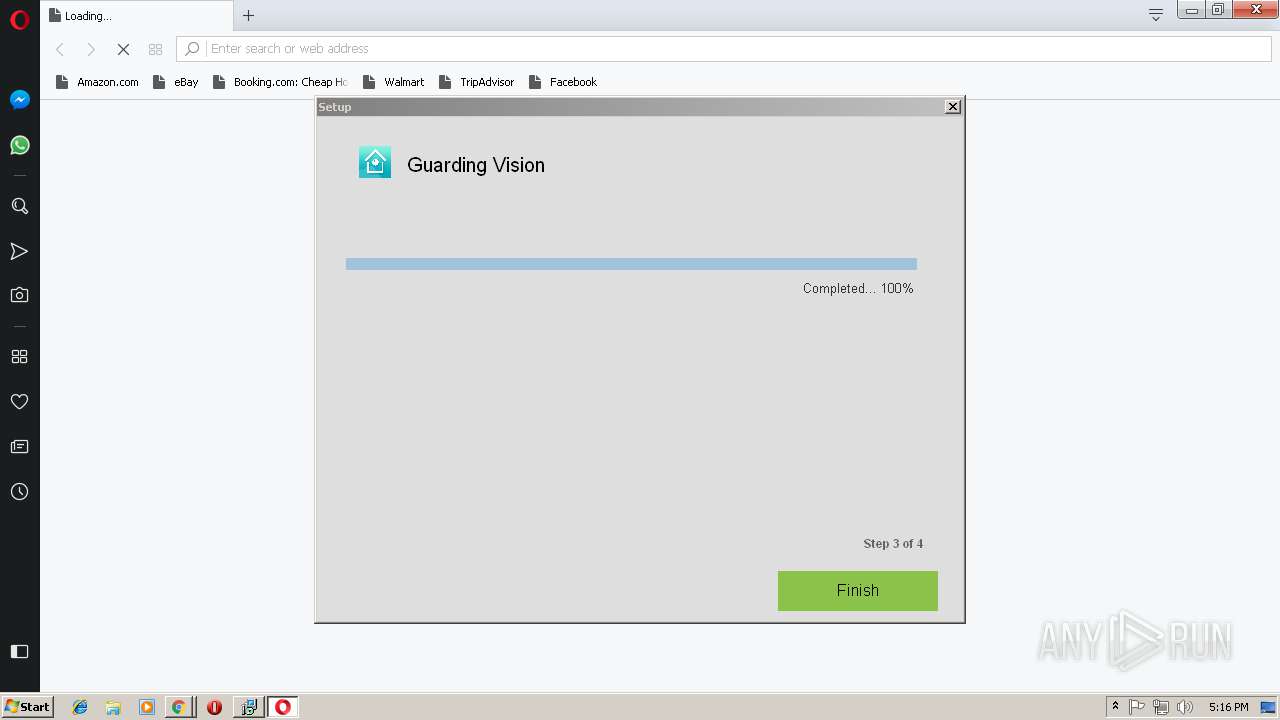
INSTALLCORE was detected
- Guarding Vision_Setup_2057492354.exe (PID: 892)
Loads dropped or rewritten executable
- OperaSetup.exe (PID: 2300)
- OperaSetup.exe (PID: 2480)
- OperaSetup.exe (PID: 3836)
- OperaSetup.exe (PID: 912)
- OperaSetup.exe (PID: 2308)
- OperaSetup.exe (PID: 3936)
- OperaSetup.exe (PID: 1688)
- installer.exe (PID: 572)
- instup.exe (PID: 3836)
- instup.exe (PID: 1688)
- installer.exe (PID: 3156)
- installer.exe (PID: 3144)
- opera.exe (PID: 960)
- opera.exe (PID: 2860)
- opera.exe (PID: 3964)
- installer.exe (PID: 1764)
- AvEmUpdate.exe (PID: 6136)
- AvEmUpdate.exe (PID: 4288)
- AvEmUpdate.exe (PID: 1684)
- AvEmUpdate.exe (PID: 5324)
- RegSvr.exe (PID: 3400)
- RegSvr.exe (PID: 5892)
- aswRunDll.exe (PID: 5796)
- AVGSvc.exe (PID: 6100)
- instup.exe (PID: 5644)
- chrome.exe (PID: 3724)
- AvEmUpdate.exe (PID: 4792)
- AVGUI.exe (PID: 5352)
Changes settings of System certificates
- OperaSetup.exe (PID: 912)
- AVGSvc.exe (PID: 6100)
Changes the autorun value in the registry
- instup.exe (PID: 1688)
- instup.exe (PID: 5644)
Loads the Task Scheduler COM API
- installer.exe (PID: 572)
- opera.exe (PID: 2504)
- AvEmUpdate.exe (PID: 6136)
- AvEmUpdate.exe (PID: 4288)
- overseer.exe (PID: 4560)
- AvEmUpdate.exe (PID: 4792)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2248)
- Guarding Vision_Setup_2057492354.exe (PID: 892)
- cmd.exe (PID: 3972)
- OperaSetup.exe (PID: 912)
- OperaSetup.exe (PID: 2480)
- OperaSetup.exe (PID: 2300)
- OperaSetup.exe (PID: 2308)
- OperaSetup.exe (PID: 1688)
- OperaSetup.exe (PID: 3936)
- avg_antivirus_free_setup.exe (PID: 3996)
- avgSetup.exe (PID: 2916)
- instup.exe (PID: 3836)
- installer.exe (PID: 3144)
- installer.exe (PID: 572)
- installer.exe (PID: 1764)
- launcher.exe (PID: 3500)
- AppKiwi_setup.exe (PID: 3392)
- instup.exe (PID: 1688)
- AvEmUpdate.exe (PID: 4288)
- AppKiwi_setup.tmp (PID: 4628)
- AVGSvc.exe (PID: 6100)
- instup.exe (PID: 5644)
Application launched itself
- Guarding Vision_Setup_2057492354.exe (PID: 2220)
- cmd.exe (PID: 1428)
- OperaSetup.exe (PID: 912)
- OperaSetup.exe (PID: 2308)
- installer.exe (PID: 572)
- opera.exe (PID: 3296)
- opera.exe (PID: 2504)
- AvEmUpdate.exe (PID: 4288)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2248)
Cleans NTFS data-stream (Zone Identifier)
- Guarding Vision_Setup_2057492354.exe (PID: 2220)
Reads CPU info
- Guarding Vision_Setup_2057492354.exe (PID: 892)
Reads the date of Windows installation
- Guarding Vision_Setup_2057492354.exe (PID: 892)
Reads internet explorer settings
- Guarding Vision_Setup_2057492354.exe (PID: 892)
Starts CMD.EXE for commands execution
- Guarding Vision_Setup_2057492354.exe (PID: 892)
- cmd.exe (PID: 1428)
Creates files in the Windows directory
- avgSetup.exe (PID: 2916)
- instup.exe (PID: 1688)
- AVGSvc.exe (PID: 6100)
- keytool.exe (PID: 3532)
- keytool.exe (PID: 5008)
Low-level read access rights to disk partition
- avgSetup.exe (PID: 2916)
- avg_antivirus_free_setup.exe (PID: 3996)
- instup.exe (PID: 3836)
- instup.exe (PID: 1688)
- AvEmUpdate.exe (PID: 4288)
- AvEmUpdate.exe (PID: 1684)
- AvEmUpdate.exe (PID: 5324)
- overseer.exe (PID: 4560)
- AVGSvc.exe (PID: 6100)
- wsc_proxy.exe (PID: 3604)
- instup.exe (PID: 5644)
- instup.exe (PID: 4684)
- instup.exe (PID: 2424)
- AvEmUpdate.exe (PID: 4792)
- AVGUI.exe (PID: 5352)
Starts itself from another location
- OperaSetup.exe (PID: 912)
- instup.exe (PID: 3836)
Creates files in the user directory
- OperaSetup.exe (PID: 2300)
- installer.exe (PID: 572)
- opera.exe (PID: 2504)
- opera.exe (PID: 3296)
- opera_autoupdate.exe (PID: 504)
Adds / modifies Windows certificates
- OperaSetup.exe (PID: 912)
Creates files in the program directory
- avg_antivirus_free_setup.exe (PID: 3996)
- instup.exe (PID: 3836)
- installer.exe (PID: 572)
- OperaSetup.exe (PID: 2308)
- opera_autoupdate.exe (PID: 5128)
- instup.exe (PID: 1688)
- AvEmUpdate.exe (PID: 4288)
- wsc_proxy.exe (PID: 3604)
- instup.exe (PID: 4684)
- AVGSvc.exe (PID: 6100)
- instup.exe (PID: 5644)
- AVGUI.exe (PID: 5352)
Modifies the open verb of a shell class
- installer.exe (PID: 572)
- instup.exe (PID: 1688)
Creates a software uninstall entry
- installer.exe (PID: 572)
- instup.exe (PID: 1688)
Reads the machine GUID from the registry
- opera.exe (PID: 3296)
- opera.exe (PID: 2504)
Connects to unusual port
- opera.exe (PID: 2504)
Creates or modifies windows services
- instup.exe (PID: 1688)
- AvEmUpdate.exe (PID: 4288)
- AVGSvc.exe (PID: 6100)
- instup.exe (PID: 5644)
Creates COM task schedule object
- instup.exe (PID: 1688)
- RegSvr.exe (PID: 1860)
- RegSvr.exe (PID: 3400)
- RegSvr.exe (PID: 5892)
Creates files in the driver directory
- instup.exe (PID: 1688)
Reads Internet Cache Settings
- instup.exe (PID: 1688)
Searches for installed software
- AVGSvc.exe (PID: 6100)
Removes files from Windows directory
- AVGSvc.exe (PID: 6100)
INFO
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3624)
- iexplore.exe (PID: 3212)
Application launched itself
- chrome.exe (PID: 2248)
Reads Internet Cache Settings
- chrome.exe (PID: 2248)
- iexplore.exe (PID: 3212)
Changes internet zones settings
- iexplore.exe (PID: 684)
Reads internet explorer settings
- iexplore.exe (PID: 3212)
Dropped object may contain Bitcoin addresses
- OperaSetup.exe (PID: 2308)
- instup.exe (PID: 1688)
- AppKiwi_setup.tmp (PID: 4628)
- instup.exe (PID: 5644)
Reads settings of System Certificates
- opera.exe (PID: 2504)
- AVGSvc.exe (PID: 6100)
Application was dropped or rewritten from another process
- AppKiwi_setup.tmp (PID: 4628)
Creates files in the program directory
- AppKiwi_setup.tmp (PID: 4628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
141
Monitored processes
97
Malicious processes
27
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=932,987160047099419416,13862072720296554965,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=44BC0AF802CB36B8382984AB6AB5CE1B --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=44BC0AF802CB36B8382984AB6AB5CE1B --renderer-client-id=17 --mojo-platform-channel-handle=4748 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 504 | "C:\Program Files\Opera\56.0.3051.52\opera_autoupdate.exe" --host=https://autoupdate.geo.opera.com/ --pipeid --version=56.0.3051.52 --edition --lang=en-US --producttype --requesttype=start --operadir="C:\Program Files\Opera\56.0.3051.52" --installdir="C:\Program Files\Opera" --profile="C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable" --installationdatadir="C:\Program Files\Opera" --firstrunver=56.0.3051.52 --consent-info=eyJzdGFydHBhZ2VfbmV3c19jb25zZW50X2dpdmVuIjpmYWxzZSwic3RhdGlzdGljc19jb2xsZWN0aW9uX2VuYWJsZWQiOnRydWUsInVzZXJfZXhwZXJpZW5jZV9tZXRyaWNzX3JlcG9ydGluZ19lbmFibGVkIjp0cnVlfQ== --firstrunts=1541006175 | C:\Program Files\Opera\56.0.3051.52\opera_autoupdate.exe | opera.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera auto-updater Exit code: 0 Version: 56.0.3051.52 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Opera\56.0.3051.52\installer.exe" --backend --initial-pid=912 --install --import-browser-data=1 --enable-stats=1 --enable-installer-stats=1 --launchopera=1 --installfolder="C:\Program Files\Opera" --profile-folder --language=en --singleprofile=0 --copyonly=0 --allusers=0 --setdefaultbrowser=1 --startmenushortcut=1 --desktopshortcut=1 --quicklaunchshortcut=1 --pintotaskbar=1 --server-tracking-data=server_tracking_data --install-subfolder=56.0.3051.52 --package-dir="C:\Users\admin\AppData\Local\Temp\Opera Installer\opera_package_201810311715251" --session-guid=2aec5eba-1db5-4b14-a57a-51499907359a --server-tracking-blob=ZTNkMWU5OGE3Y2FmMDE3NWRmY2EwMjIyZThmOTYwMTI5ZjJhZDBiNzhiZGI4MWE5NWVjZTI2NzBkNzBkMjBlZjp7ImNvdW50cnkiOiJOTyIsImluc3RhbGxlcl9uYW1lIjoiT3BlcmFTZXR1cC5leGUiLCJwcm9kdWN0Ijoib3BlcmEiLCJxdWVyeSI6Ii9vcGVyYS9zdGFibGU/dXRtX21lZGl1bT1wYmMmdXRtX3NvdXJjZT1haXMmdXRtX2NhbXBhaWduPV9iMl9uYyZ1dG1faWQ9VDF1cmZnOEElMkJuY0tBdnNDZTNiJTJCY2drRSUyQjNRY1FhczNCd0QlMkZjZ0lEJTJGM0FMQSUyRmh5RHdMNGNnOEY2U3hjVktveEIzMiUyRkpraFRqVEZWUmJ3bVNCU3NNVmtCJTJGWDRJQiUyRnB5REFMNWRRdiUyQlRRQUFBRG95ejBNJTNEIiwidGltZXN0YW1wIjoiMTU0MTAwNjEyMi4yMjg3IiwidXNlcmFnZW50IjoiTW96aWxsYS80LjAgKGNvbXBhdGlibGU7IE1TSUUgOC4wOyBXaW5kb3dzIE5UIDYuMTsgVHJpZGVudC80LjA7IFNMQ0MyOyAuTkVUIENMUiAyLjAuNTA3Mjc7IC5ORVQgQ0xSIDMuNS4zMDcyOTsgLk5FVCBDTFIgMy4wLjMwNzI5OyBNZWRpYSBDZW50ZXIgUEMgNi4wOyAuTkVUNC4wQzsgLk5FVDQuMEUpIiwidXRtIjp7ImNhbXBhaWduIjoiX2IyX25jIiwiaWQiOiJUMXVyZmc4QStuY0tBdnNDZTNiK2Nna0UrM1FjUWFzM0J3RC9jZ0lELzNBTEEvaHlEd0w0Y2c4RjZTeGNWS294QjMyL0praFRqVEZWUmJ3bVNCU3NNVmtCL1g0SUIvcHlEQUw1ZFF2K1RRQUFBRG95ejBNPSIsIm1lZGl1bSI6InBiYyIsInNvdXJjZSI6ImFpcyJ9LCJ1dWlkIjoiOGVmMzkxNGQtMjdmNC00MDgxLTljZGEtNTQ0NmIxNTczNjdhIn0= --silent | C:\Program Files\Opera\56.0.3051.52\installer.exe | OperaSetup.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 56.0.3051.52 Modules
| |||||||||||||||
| 600 | TIMEOUT 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 624 | "C:\Program Files\Opera\56.0.3051.52\opera_crashreporter.exe" --start-maximized --ran-launcher --crash-reporter-parent-id=3296 | C:\Program Files\Opera\56.0.3051.52\opera_crashreporter.exe | — | opera.exe | |||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera crash-reporter Exit code: 3 Version: 56.0.3051.52 Modules
| |||||||||||||||
| 628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=932,987160047099419416,13862072720296554965,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=31F7CAF061FE71A3D49F22B80B32A5F2 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=31F7CAF061FE71A3D49F22B80B32A5F2 --renderer-client-id=20 --mojo-platform-channel-handle=2120 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x701900b0,0x701900c0,0x701900cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 892 | "C:\Users\admin\Downloads\Guarding Vision_Setup_2057492354.exe" /RSF /ppn:YHhybg0dXAt1eGqREw /ads:1 /mnl | C:\Users\admin\Downloads\Guarding Vision_Setup_2057492354.exe | Guarding Vision_Setup_2057492354.exe | ||||||||||||
User: admin Company: Kil Integrity Level: HIGH Description: Palosofate Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 912 | "C:\Users\admin\AppData\Local\Temp\in3B17FABD\OperaSetup.exe" --silent --allusers=0 | C:\Users\admin\AppData\Local\Temp\in3B17FABD\OperaSetup.exe | Guarding Vision_Setup_2057492354.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: HIGH Description: Opera Installer Exit code: 0 Version: 56.0.3051.52 Modules
| |||||||||||||||
Total events
10 068
Read events
4 528
Write events
5 524
Delete events
16
Modification events
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {578DD807-DD30-11E8-BFAB-5254004AAD11} |
Value: 0 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070A0003001F0011000D003600F401 | |||
Executable files
306
Suspicious files
555
Text files
2 299
Unknown types
161
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 684 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 684 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\Guarding-Vision[1].txt | — | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\Guarding-Vision[1].htm | html | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\icon[1].txt | text | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\addthis_widget[1].js | text | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\css[1].txt | text | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\style[1].css | text | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\f[1].txt | text | |
MD5:— | SHA256:— | |||
| 3212 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
274
TCP/UDP connections
319
DNS requests
261
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3212 | iexplore.exe | GET | 200 | 172.217.23.98:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 27.3 Kb | whitelisted |
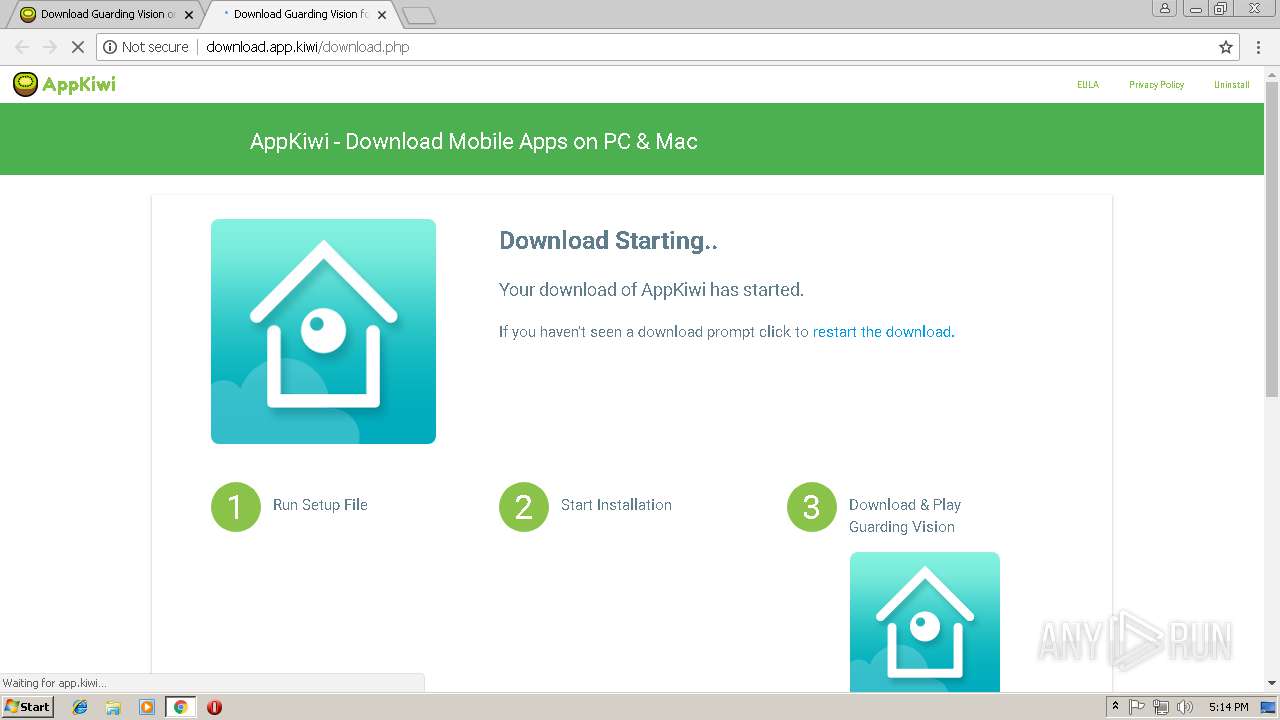
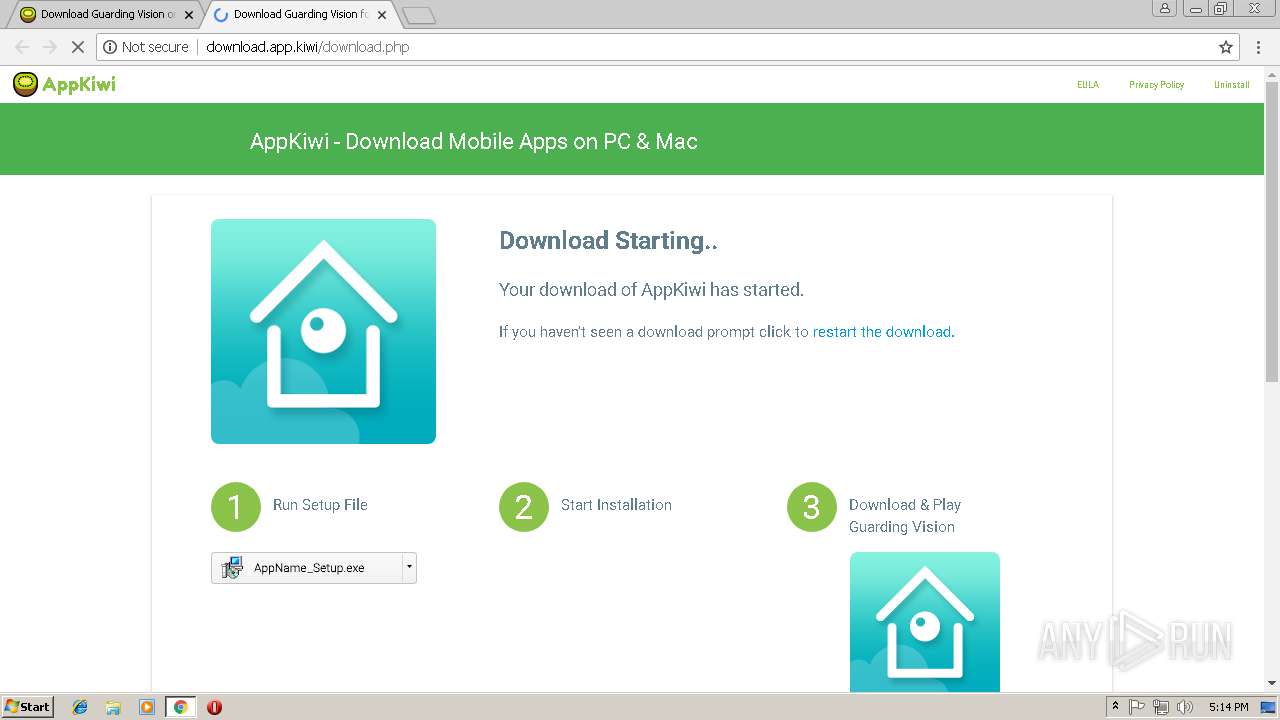
3212 | iexplore.exe | GET | 200 | 13.56.84.11:80 | http://app.kiwi/apk/com.mcu.guardingvision/Guarding-Vision | US | html | 4.65 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 23.210.248.44:80 | http://s7.addthis.com/js/300/addthis_widget.js | NL | text | 111 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 216.58.205.99:80 | http://fonts.gstatic.com/s/bitter/v13/rax8HiqOu8IVPmn7f4xt.eot | US | eot | 28.2 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 172.217.23.98:80 | http://pagead2.googlesyndication.com/pagead/js/r20181024/r20180604/show_ads_impl.js | US | text | 74.4 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 216.58.205.106:80 | http://fonts.googleapis.com/css?family=Montserrat|Bitter|Fredoka+One|Roboto | US | text | 285 b | whitelisted |
3212 | iexplore.exe | GET | 200 | 54.192.94.94:80 | http://img.app.kiwi/ss/OqIq_I7Z52E9t8Dt43dlfVQFyhB41-ceDWvW-gX_QUIitPKu3SEfiZI2UCDEXKuDsIxe | US | image | 32.3 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 13.56.84.11:80 | http://app.kiwi/img/logo.png | US | image | 4.35 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 54.192.94.94:80 | http://img.app.kiwi/ss/4EPNc4kjsHX33sF1f5x-5shkxHi18qjkXFloHx-BlPGILfmtoOGok8xYzWHU9te5psc | US | image | 35.9 Kb | whitelisted |
3212 | iexplore.exe | GET | 200 | 54.192.94.94:80 | http://img.app.kiwi/icon/nm9vVDMU5zrT3Ty6V_pFYAs2ksYrxpvUBAcxFm1iBLMh5JJiJEbi2fgJJdUocdYM2w | US | image | 42.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
684 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3212 | iexplore.exe | 13.56.84.11:80 | app.kiwi | Amazon.com, Inc. | US | unknown |
3212 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
3212 | iexplore.exe | 104.19.196.151:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
3212 | iexplore.exe | 172.217.23.98:80 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3212 | iexplore.exe | 23.210.248.44:80 | s7.addthis.com | Akamai International B.V. | NL | whitelisted |
3212 | iexplore.exe | 216.58.205.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3212 | iexplore.exe | 216.58.205.106:80 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3212 | iexplore.exe | 216.58.205.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3212 | iexplore.exe | 172.217.23.66:443 | googleads.g.doubleclick.net | Google Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
app.kiwi |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
img.app.kiwi |
| whitelisted |
adservice.google.no |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2248 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2248 | chrome.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
892 | Guarding Vision_Setup_2057492354.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M2 |
892 | Guarding Vision_Setup_2057492354.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M1 |
892 | Guarding Vision_Setup_2057492354.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M4 |
892 | Guarding Vision_Setup_2057492354.exe | Misc activity | ADWARE [PTsecurity] PUP.Optional.InstallCore Artifact M3 |
892 | Guarding Vision_Setup_2057492354.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Possible threat - .exe downloading with HEAD option |
892 | Guarding Vision_Setup_2057492354.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
892 | Guarding Vision_Setup_2057492354.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
892 | Guarding Vision_Setup_2057492354.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
instup.exe | [2018-10-31 17:15:34.877] [error ] [Ares ] [ 3836: 2416] Unable to resolve hosts after 1740 ms (258, The wait operation timed out.)
|
AVGSvc.exe | [2018-10-31 17:17:37.688] [error ] [aavm_lic ] [ 6100: 3508] Account holder is null pointer.
|
AVGSvc.exe | [2018-10-31 17:17:37.688] [error ] [aavm_lic ] [ 6100: 3508] Account holder is null pointer.
|
AVGSvc.exe | [2018-10-31 17:17:37.688] [error ] [aavm_lic ] [ 6100: 3508] FrameworkLicenseRefresh - no licenses provided.
|
AVGSvc.exe | [2018-10-31 17:17:40.111] [error ] [fmwbase ] [ 6100: 4112] Get fmw dll path fail 2
|
AVGSvc.exe | [2018-10-31 17:17:40.111] [error ] [fmwbase ] [ 6100: 4112] Failed to Load fmw base (0xe0010013)
|
AVGSvc.exe | [2018-10-31 17:17:41.335] [error ] [aavm ] [ 6100: 4976] OnPushNotification failed. Native Messaging host process ID is 0.
Exception: Native Messaging host process ID is 0.
|
AVGSvc.exe | [2018-10-31 17:17:41.351] [error ] [aavm ] [ 6100: 4976] OnPushNotification failed. Native Messaging host process ID is 0.
Exception: Native Messaging host process ID is 0.
|
AVGSvc.exe | [2018-10-31 17:17:41.764] [error ] [av_pp_prov ] [ 6100: 4112] Exception: Unable to open the license file 'C:\ProgramData\AVG\Subscriptions\license.avglic'!
Code: 0x00000002 (2)
|
AVGSvc.exe | [2018-10-31 17:17:42.109] [error ] [av_pp_prov ] [ 6100: 4112] app.alpha.GetAvailableTrials failed: Request 'app.alpha.GetAvailableTrials' was not processed. Routing parameters:
|