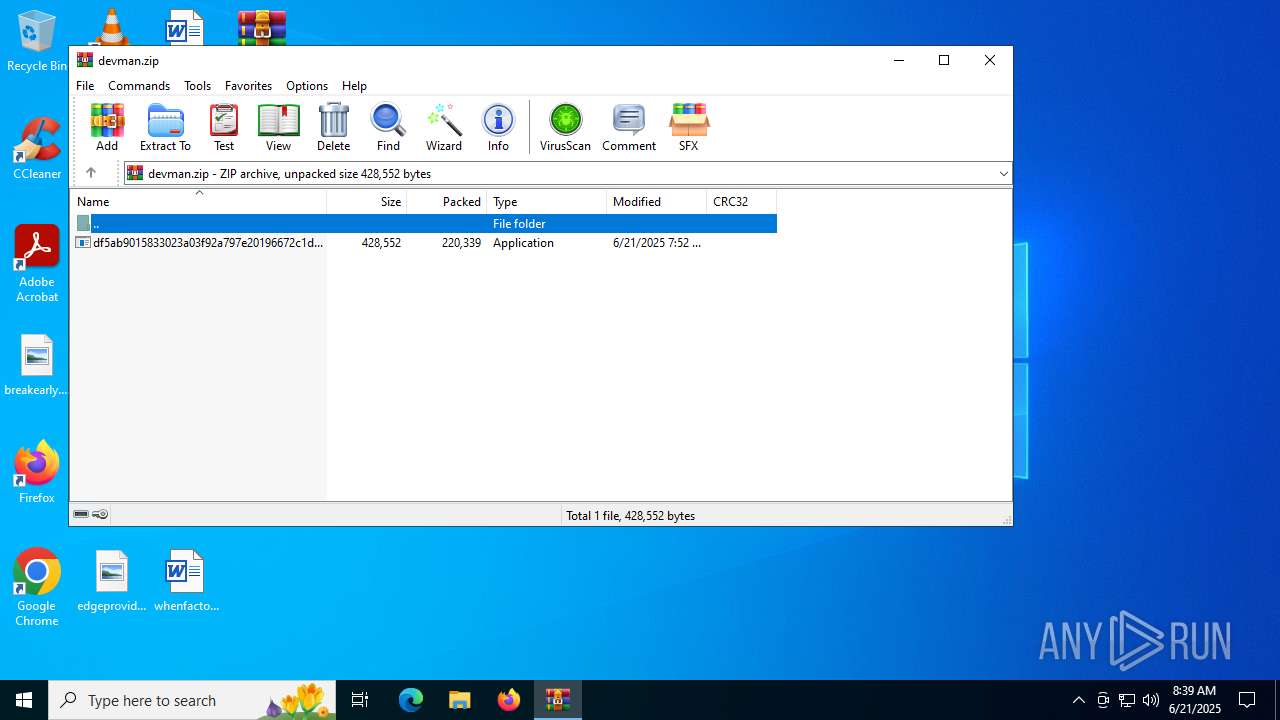
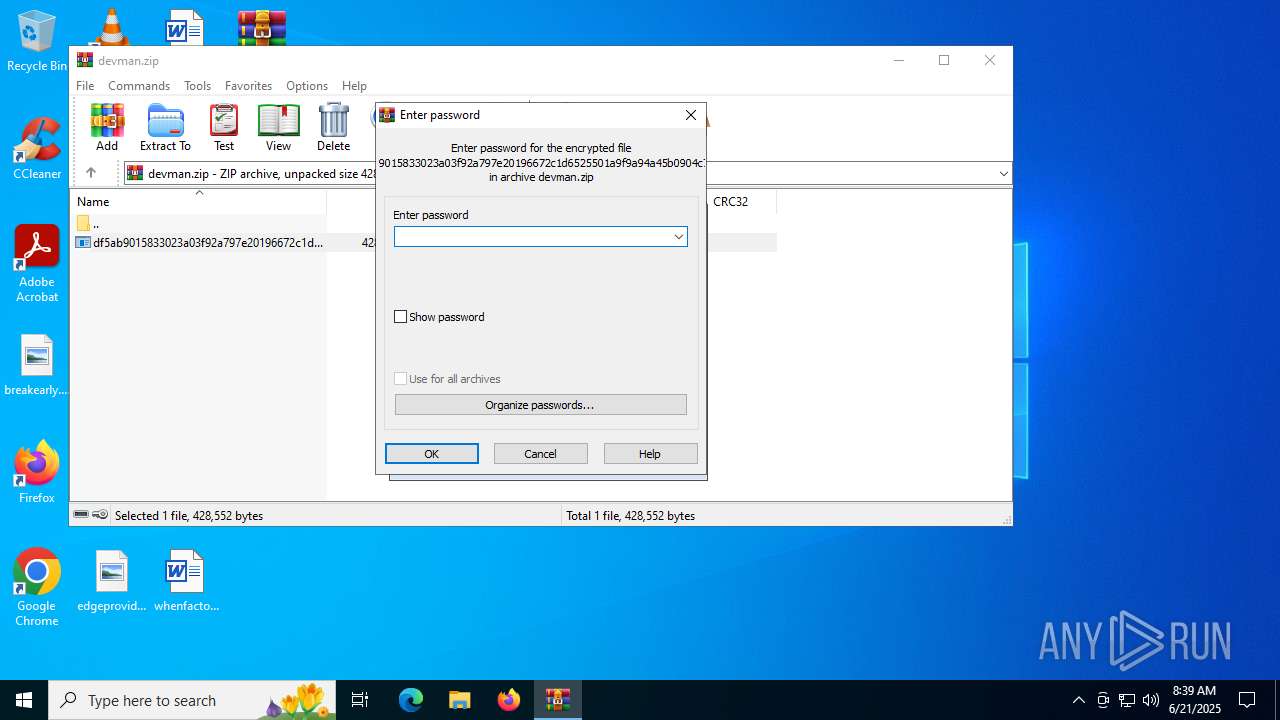
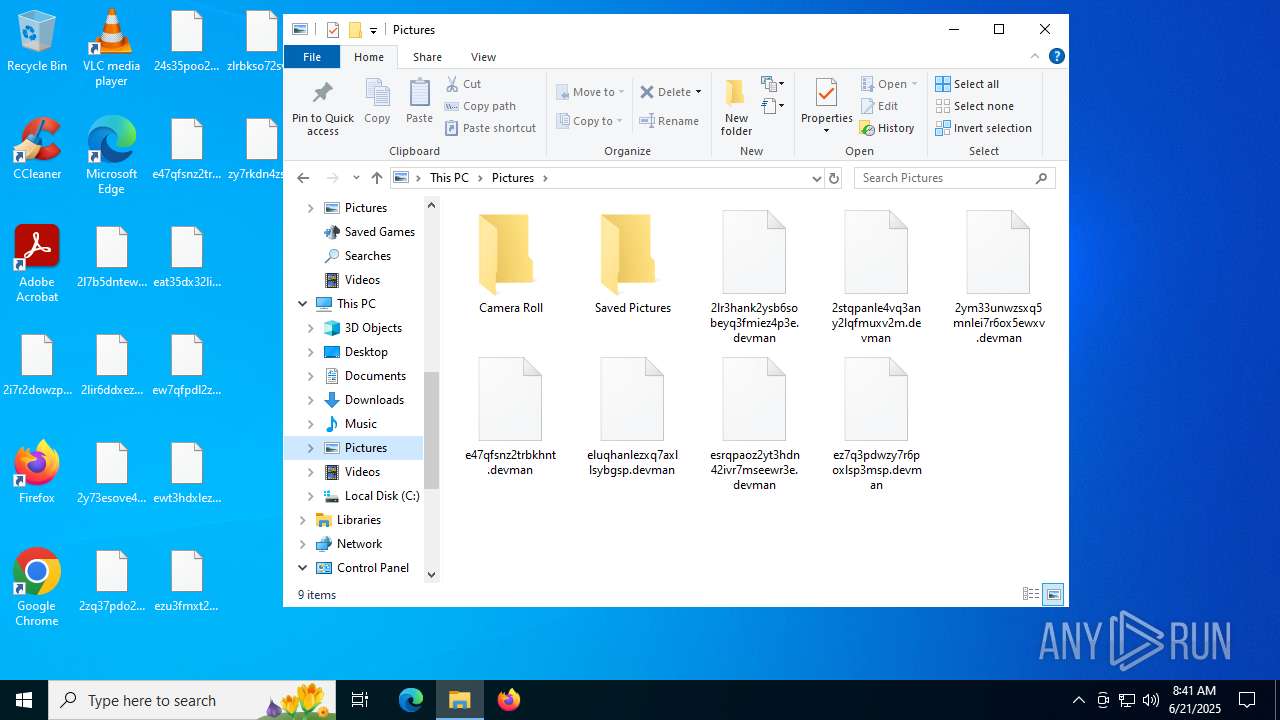
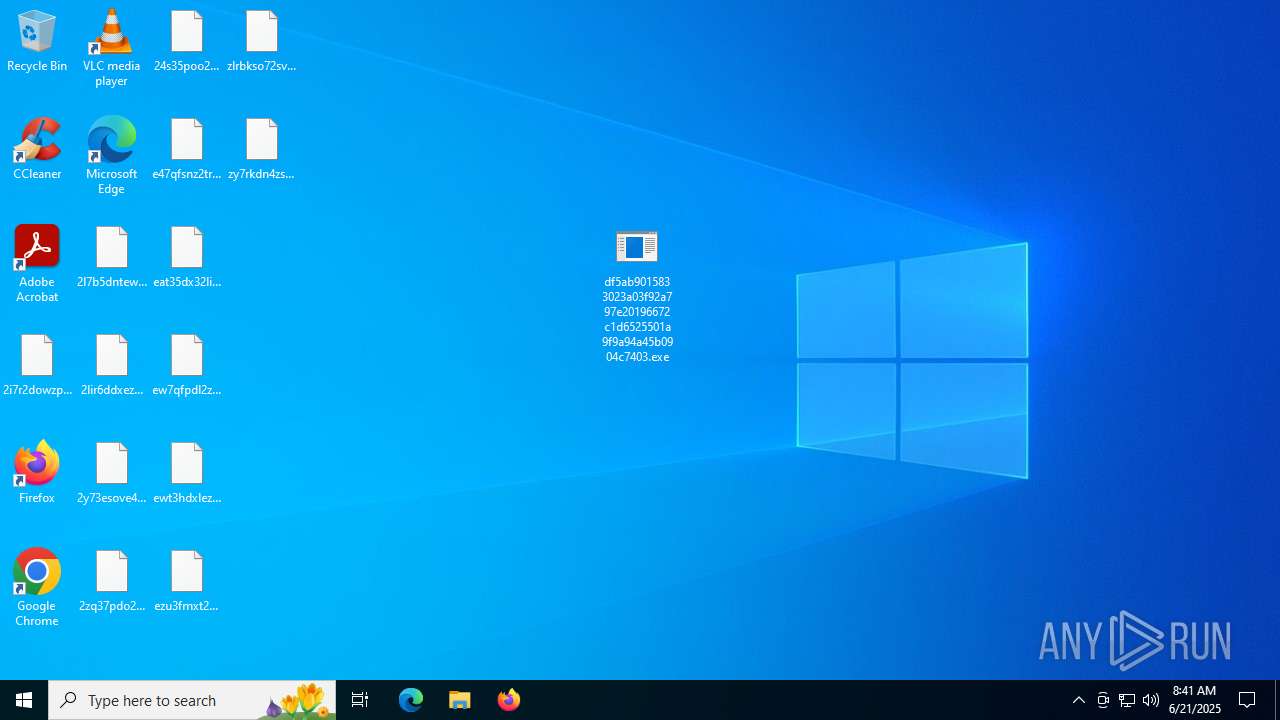
| File name: | devman.zip |
| Full analysis: | https://app.any.run/tasks/8c2685e4-8f31-4e60-8a33-b58d77cc7225 |
| Verdict: | Malicious activity |
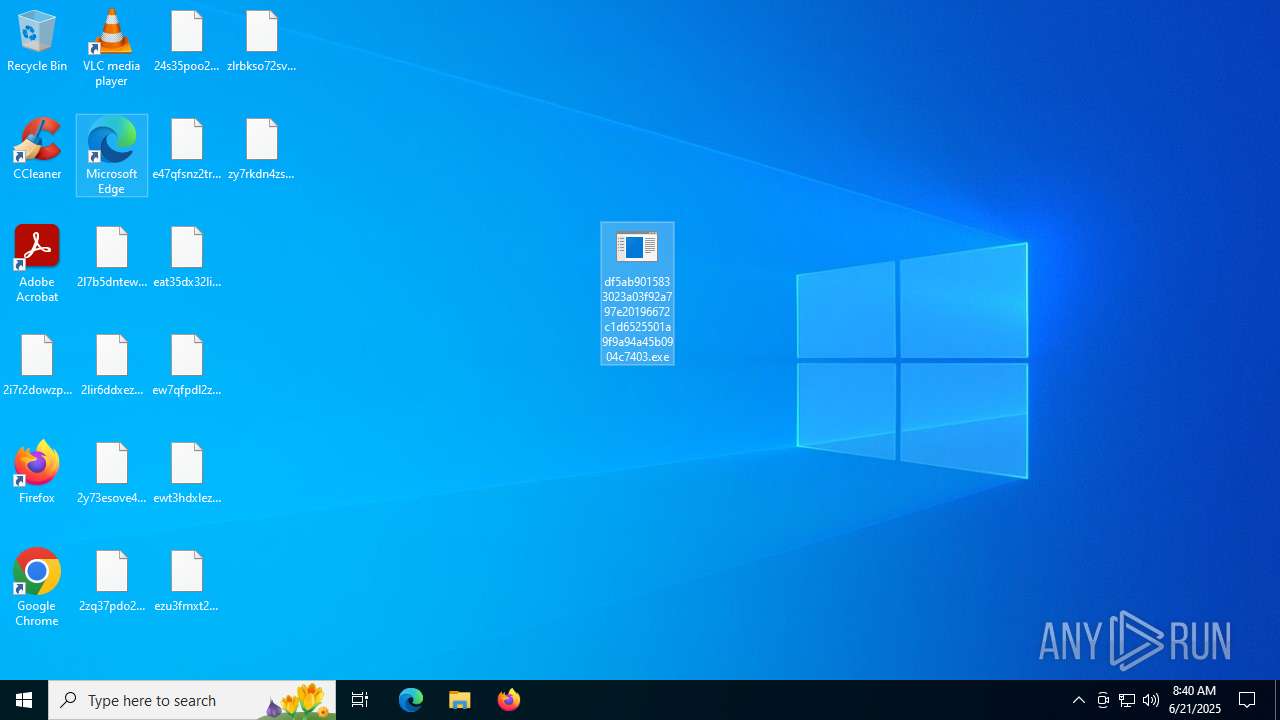
| Threats: | DragonForce is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model. First reported in December 2023, it encrypts files with ChaCha8, renames them with random strings, and appends “.dragonforce_encrypted.” By disabling backups, wiping recovery, and spreading across SMB shares, DragonForce maximizes damage and pressures victims into multimillion-dollar ransom negotiations. It has targeted manufacturing, construction, IT, healthcare, and retail sectors worldwide, making it a severe threat to modern enterprises. |
| Analysis date: | June 21, 2025, 08:39:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 24B2494440EE17B893DDA61C3FC706C7 |
| SHA1: | C7DED76DEF3DEA524B4E27811B3942C3ABAF0CD7 |
| SHA256: | 3185682C173BE4F993C68A43149E69A0C491497901B27595E84D006C2DF5CA22 |
| SSDEEP: | 6144:2YS+bjd8h6mqygFwkGzyr3p8n2ItB3VYJRvO+tXa/0n:9ah/bgezu3pontBlMO+9vn |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5644)
DRAGONFORCE has been found (auto)
- WinRAR.exe (PID: 5644)
RANSOMWARE has been detected
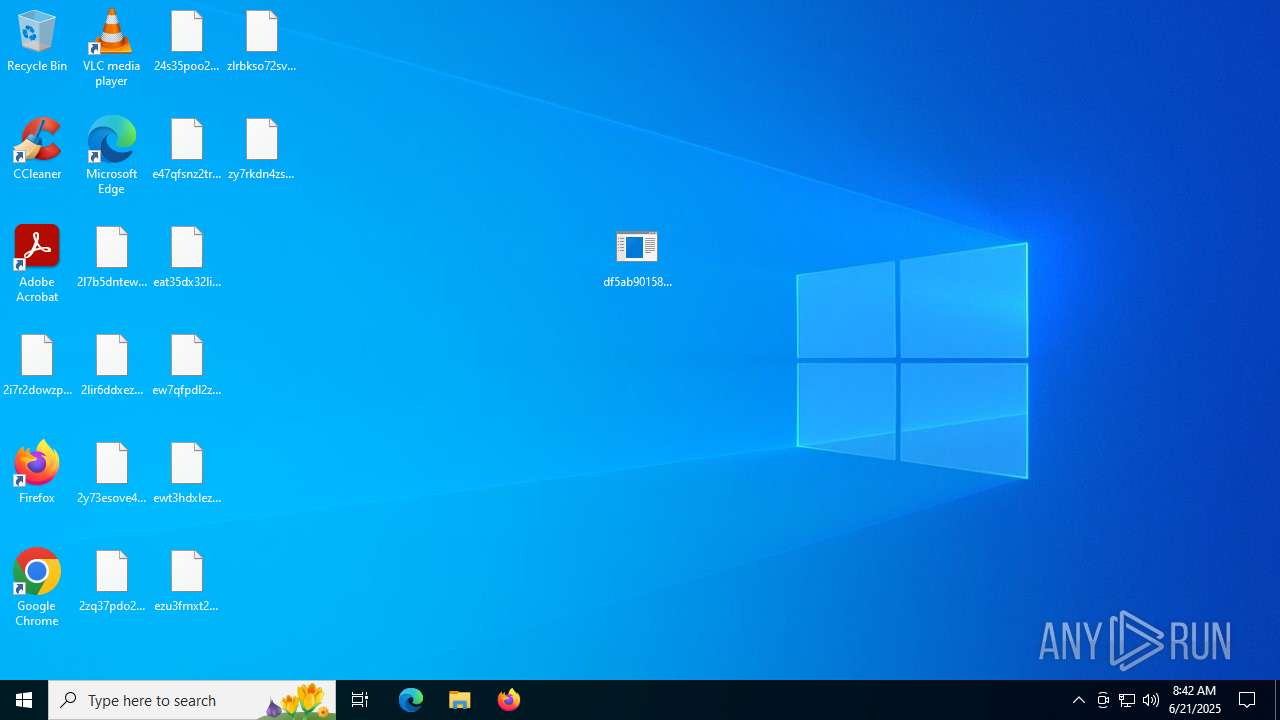
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
SUSPICIOUS
Creates file in the systems drive root
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
Write to the desktop.ini file (may be used to cloak folders)
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5644)
Manual execution by a user
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
- Taskmgr.exe (PID: 4804)
- Taskmgr.exe (PID: 6404)
Checks supported languages
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
Reads the computer name
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
Reads the machine GUID from the registry
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
Creates files in the program directory
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
Creates files or folders in the user directory
- df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe (PID: 3624)
- Taskmgr.exe (PID: 6404)
Reads the software policy settings
- slui.exe (PID: 2368)
Checks proxy server information
- slui.exe (PID: 2368)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:06:21 07:52:26 |
| ZipCRC: | 0x2df6952c |
| ZipCompressedSize: | 220339 |
| ZipUncompressedSize: | 428552 |
| ZipFileName: | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe |
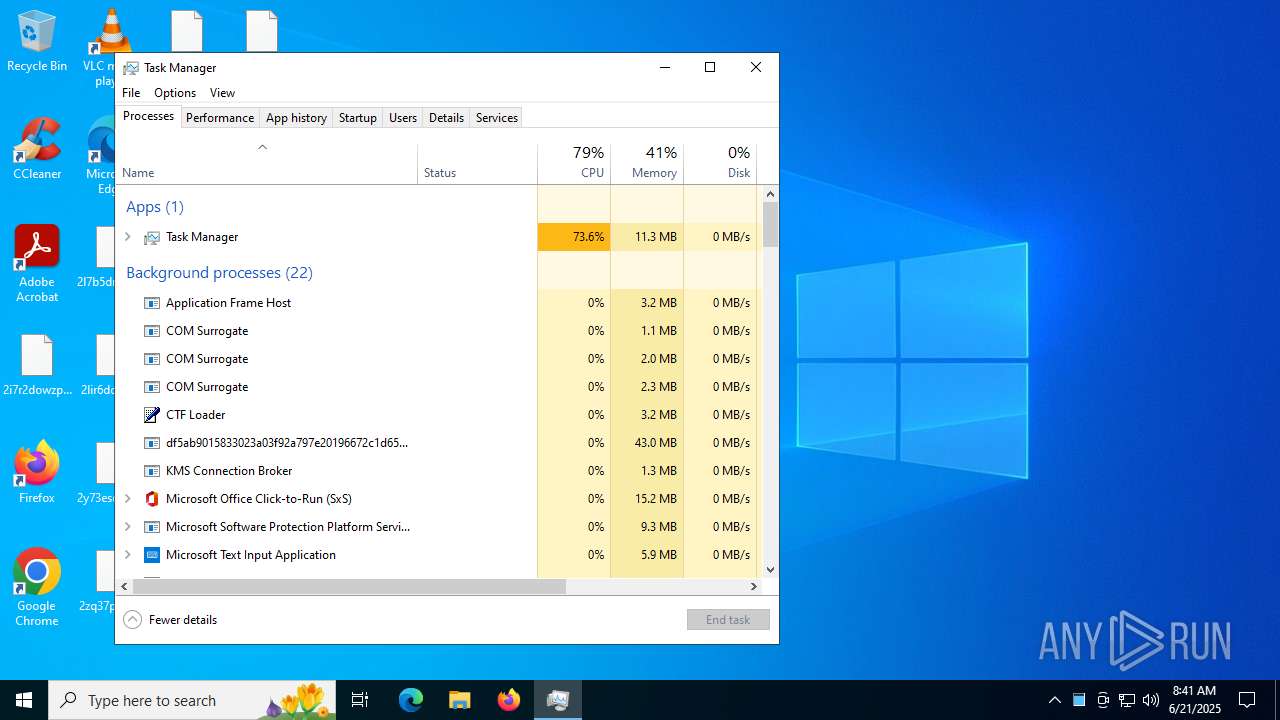
Total processes
143
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2368 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\Desktop\df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe" | C:\Users\admin\Desktop\df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4804 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5644 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\devman.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6404 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 014
Read events
3 992
Write events
21
Delete events
1
Modification events
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\devman.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
8
Suspicious files
1 391
Text files
541
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\readme.txt | text | |
MD5:D403F38DFAD3D7D6BD62591838F2BA79 | SHA256:F26BB5D17EFF4A6566E09783D21FF40DB7D5C7EC8F2E76681AB72E9F992DD7AD | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Adobe\readme.txt | text | |
MD5:D403F38DFAD3D7D6BD62591838F2BA79 | SHA256:F26BB5D17EFF4A6566E09783D21FF40DB7D5C7EC8F2E76681AB72E9F992DD7AD | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\bootTel.dat | binary | |
MD5:F06DB11C04653D7030755899B88732E4 | SHA256:AE7FA7ACA7B93C53EBFDFF14714469BD90E2ABC8C7F5BDD2A293BBF56DFB6742 | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Comms\readme.txt | text | |
MD5:D403F38DFAD3D7D6BD62591838F2BA79 | SHA256:F26BB5D17EFF4A6566E09783D21FF40DB7D5C7EC8F2E76681AB72E9F992DD7AD | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\profile_count_308046B0AF4A39CB.json | binary | |
MD5:1200778498F97374760D27905BC15EE4 | SHA256:C9E58443BB83D8AF5ABC69CD7A620A02D34DC05BC2C0450D245D75B20C39B61F | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\readme.txt | text | |
MD5:D403F38DFAD3D7D6BD62591838F2BA79 | SHA256:F26BB5D17EFF4A6566E09783D21FF40DB7D5C7EC8F2E76681AB72E9F992DD7AD | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Microsoft OneDrive\readme.txt | text | |
MD5:D403F38DFAD3D7D6BD62591838F2BA79 | SHA256:F26BB5D17EFF4A6566E09783D21FF40DB7D5C7EC8F2E76681AB72E9F992DD7AD | |||
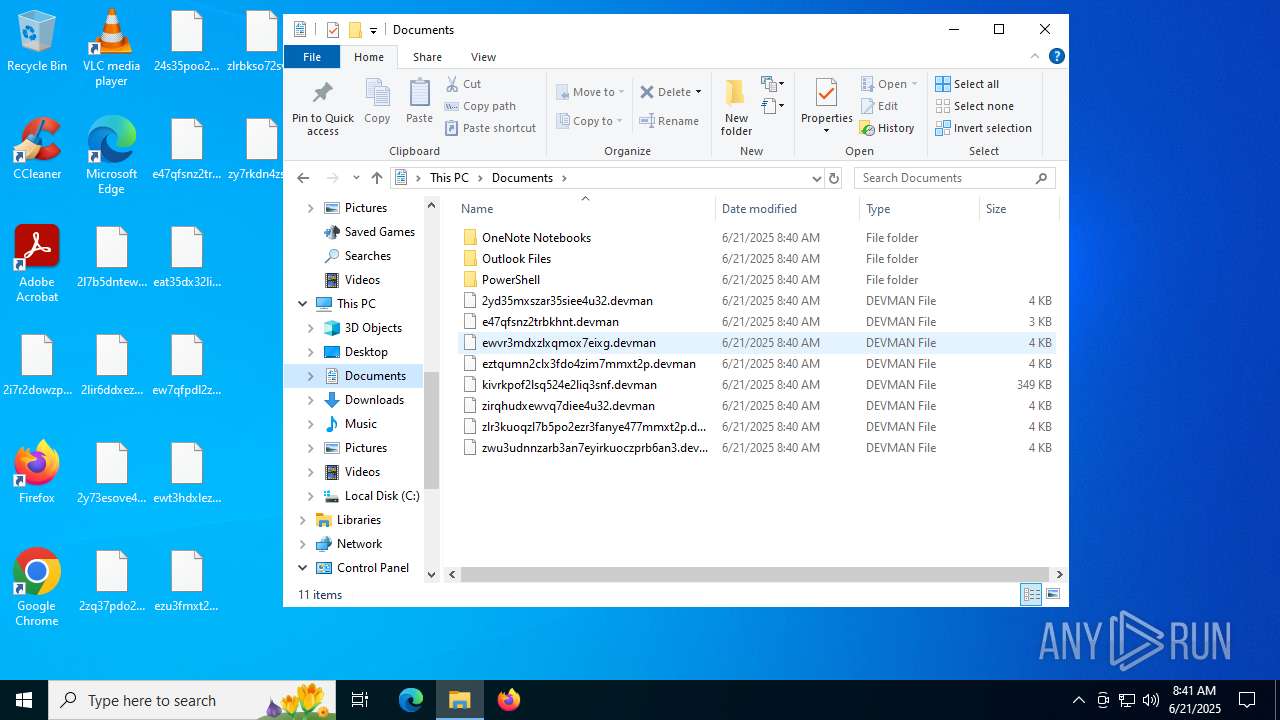
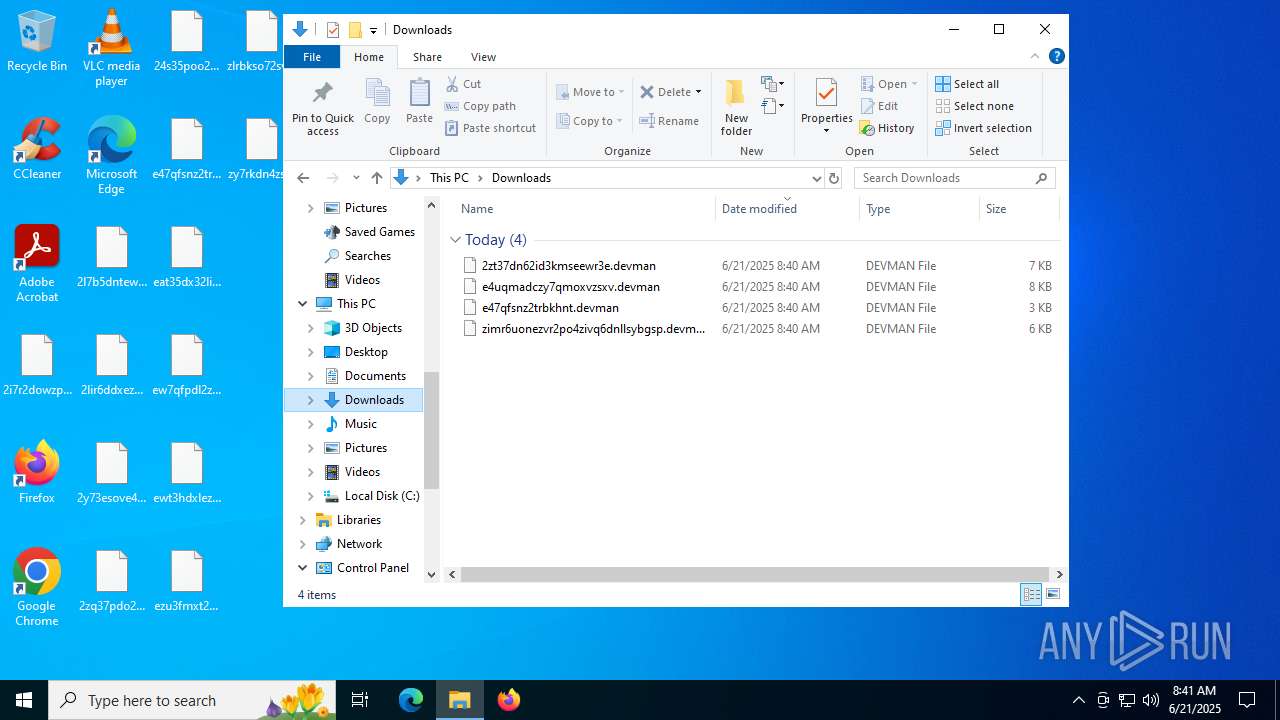
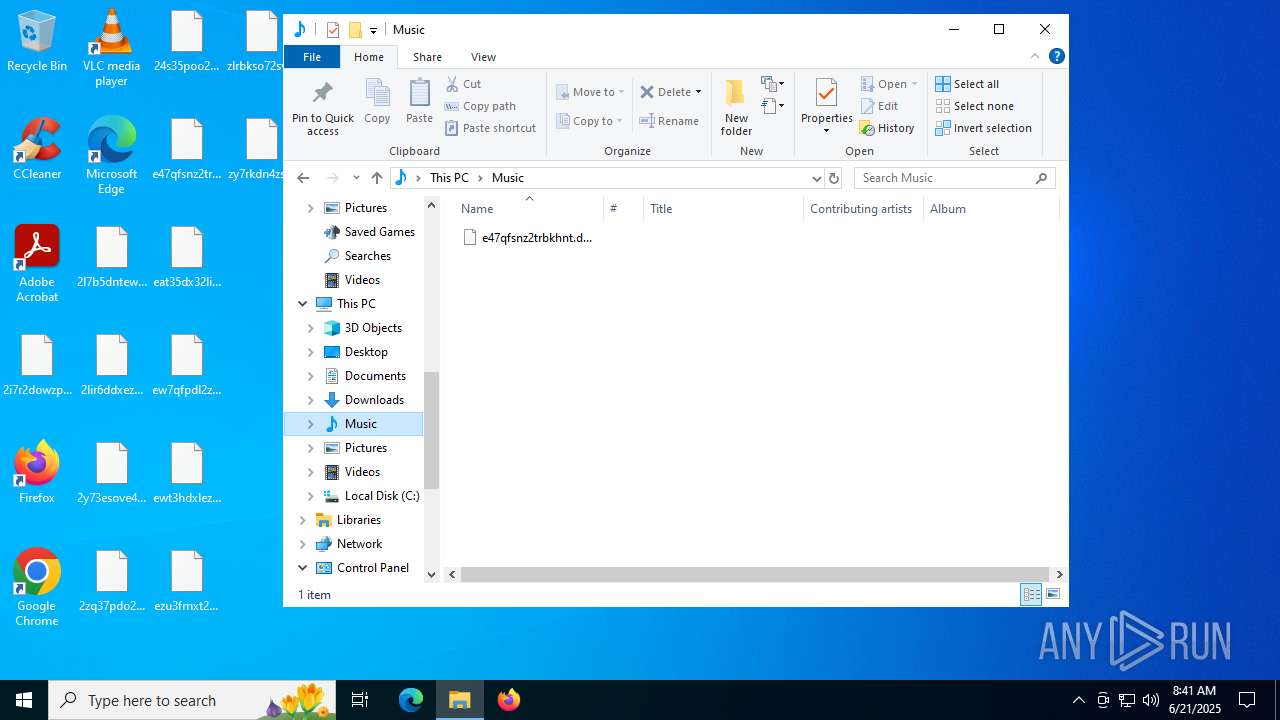
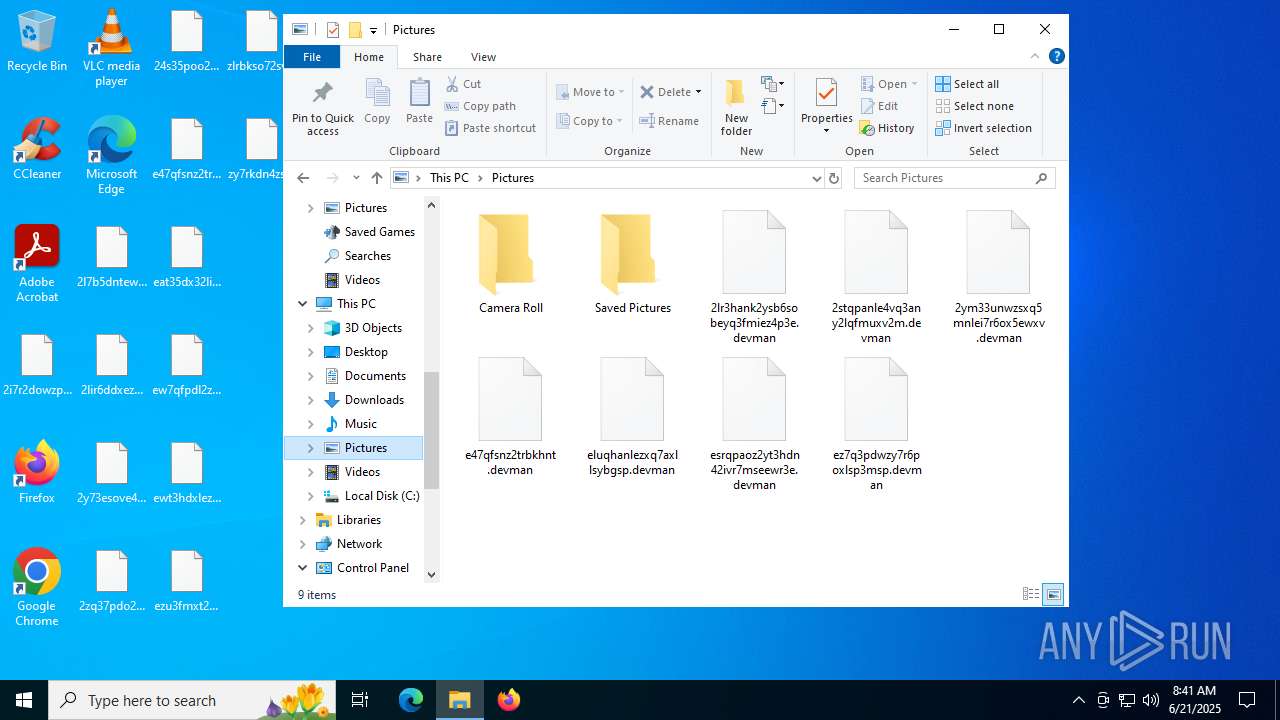
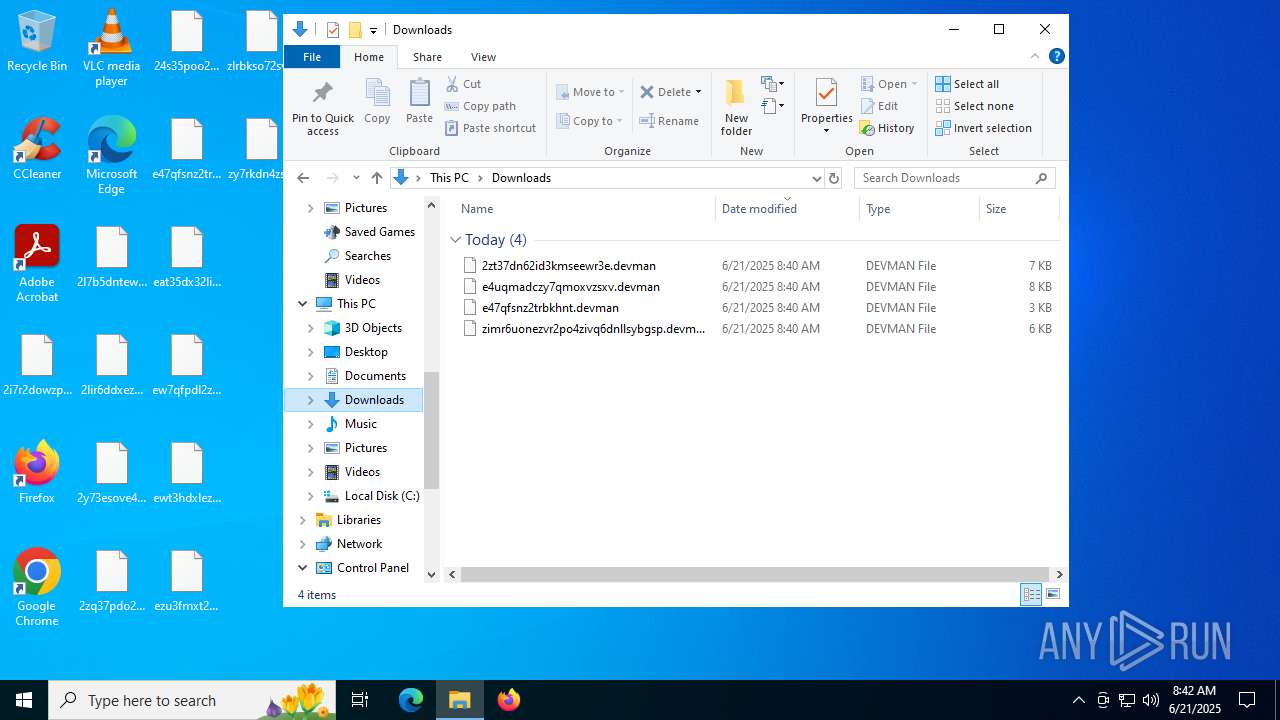
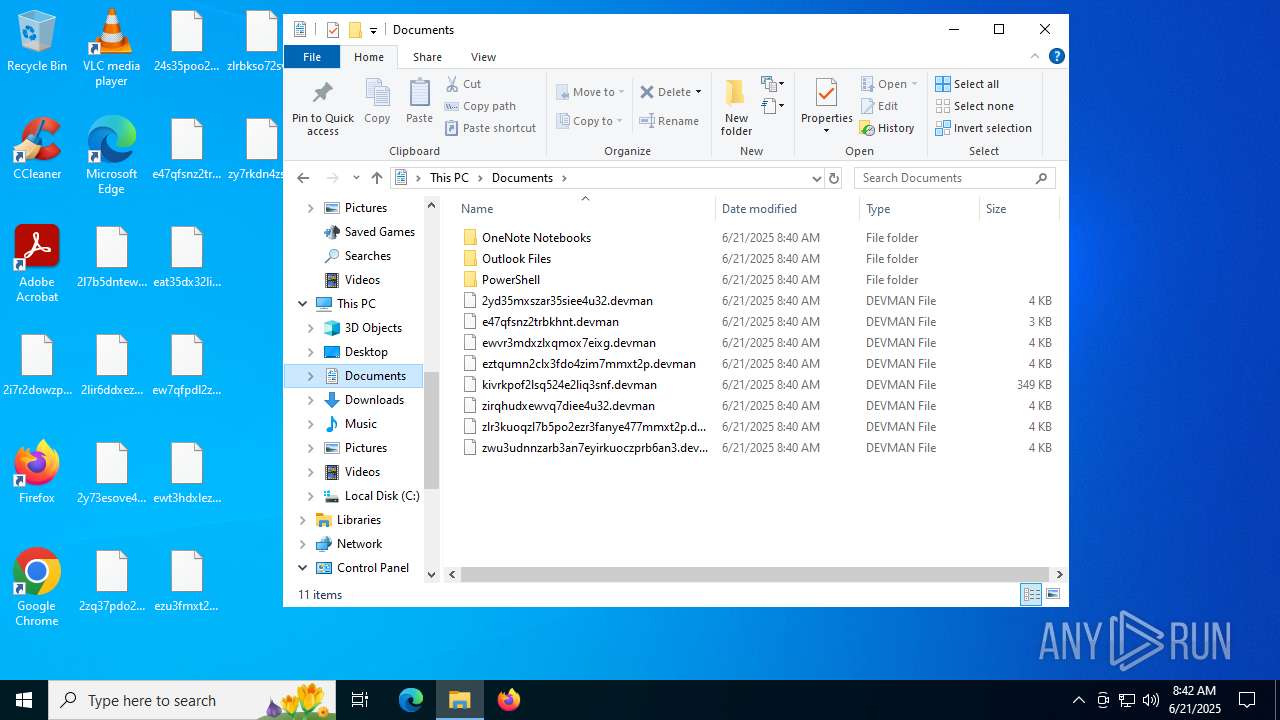
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Microsoft OneDrive\e47qfsnz2trbkhnt.devman | binary | |
MD5:12B67A0E4FE3B8F52ABFBD1BE6F577C0 | SHA256:917690D93B7E9A1245E8DA29B9FF8F89D3395BC1B829DCEC88C00C1432F46C4A | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\e47qfsnz2trbkhnt.devman | binary | |
MD5:279F97CA94EA5CA18809D538E67E501C | SHA256:1548F1F9A12BB6BEA0FAF9F3986E83FE7F39DD57A4362664BAC58B434A77DA4F | |||
| 3624 | df5ab9015833023a03f92a797e20196672c1d6525501a9f9a94a45b0904c7403.exe | C:\ProgramData\Mozilla-1de4eec8-1241-4177-a864-e594e8d1fb38\ews3hsx4zi7yhpdceyrbkrsx3gmngzwqkkp6fiitk6sx7vuflsyb3dde.devman | binary | |
MD5:1200778498F97374760D27905BC15EE4 | SHA256:C9E58443BB83D8AF5ABC69CD7A620A02D34DC05BC2C0450D245D75B20C39B61F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
34
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3100 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2792 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3100 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3100 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |