| File name: | 91.z |
| Full analysis: | https://app.any.run/tasks/690ce16a-2ece-4ef7-9b81-1771dafe4ccf |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | August 13, 2019, 12:58:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
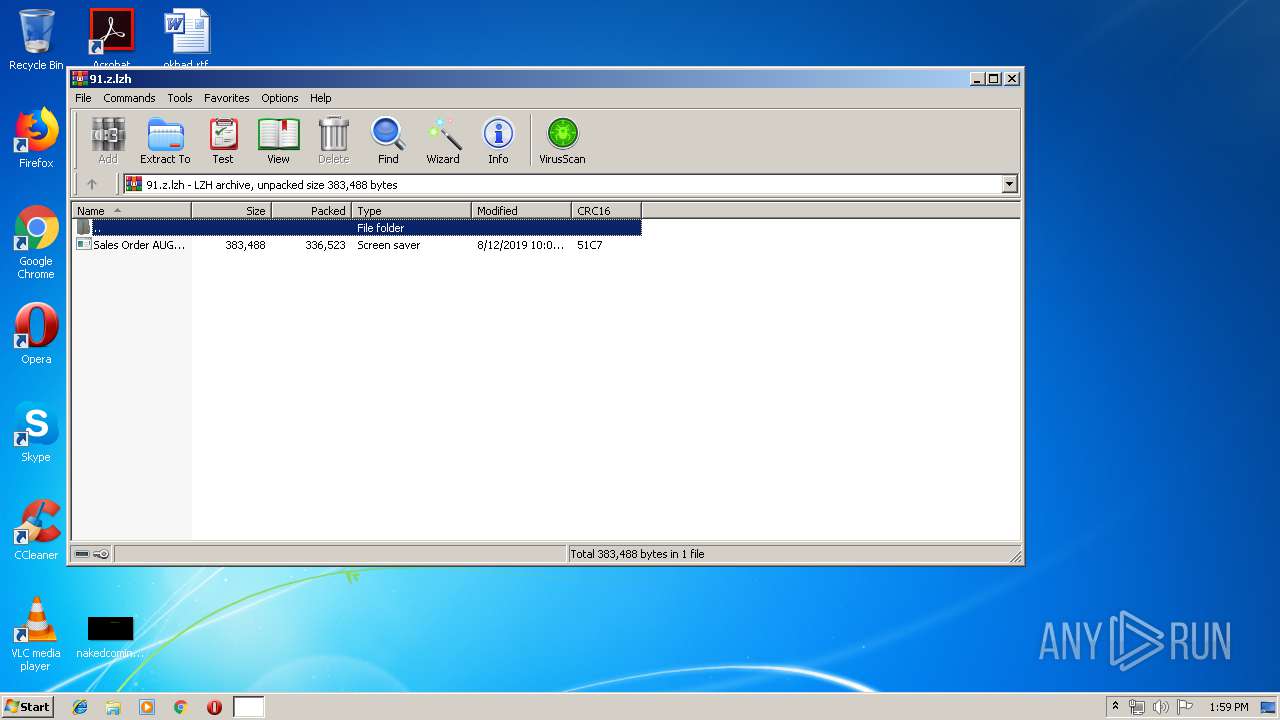
| MIME: | application/x-lzh-compressed |
| File info: | LHa (2.x) archive data [lh5], with "Sales Order AUGT (GD-2907019)_Docx.scr" |
| MD5: | 8199EA976F8076C8AC2A451B02EAB24C |
| SHA1: | 795E0385174DD04D75CE9BF4FF24015BA00F43DD |
| SHA256: | 310002C1244DECD0B8C231667E747AD3607A469F5E3B334758F40202DDCDA85B |
| SSDEEP: | 6144:C3fRD70tEs7jBP5SAB9b0WJY3FM5FxDsREFFdhVAvs:CZDw1jBPAAT0WJY3FMpD |
MALICIOUS
Application was dropped or rewritten from another process
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2812)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3584)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2832)
Uses Task Scheduler to run other applications
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2812)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2328)
- schtasks.exe (PID: 3368)
AVEMARIA was detected
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3584)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2832)
Connects to CnC server
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3584)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2832)
SUSPICIOUS
Reads the BIOS version
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2812)
Starts application with an unusual extension
- WinRAR.exe (PID: 2556)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2812)
Creates files in the user directory
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2556)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
Application launched itself
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3624)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2812)
Reads the machine GUID from the registry
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3584)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2832)
INFO
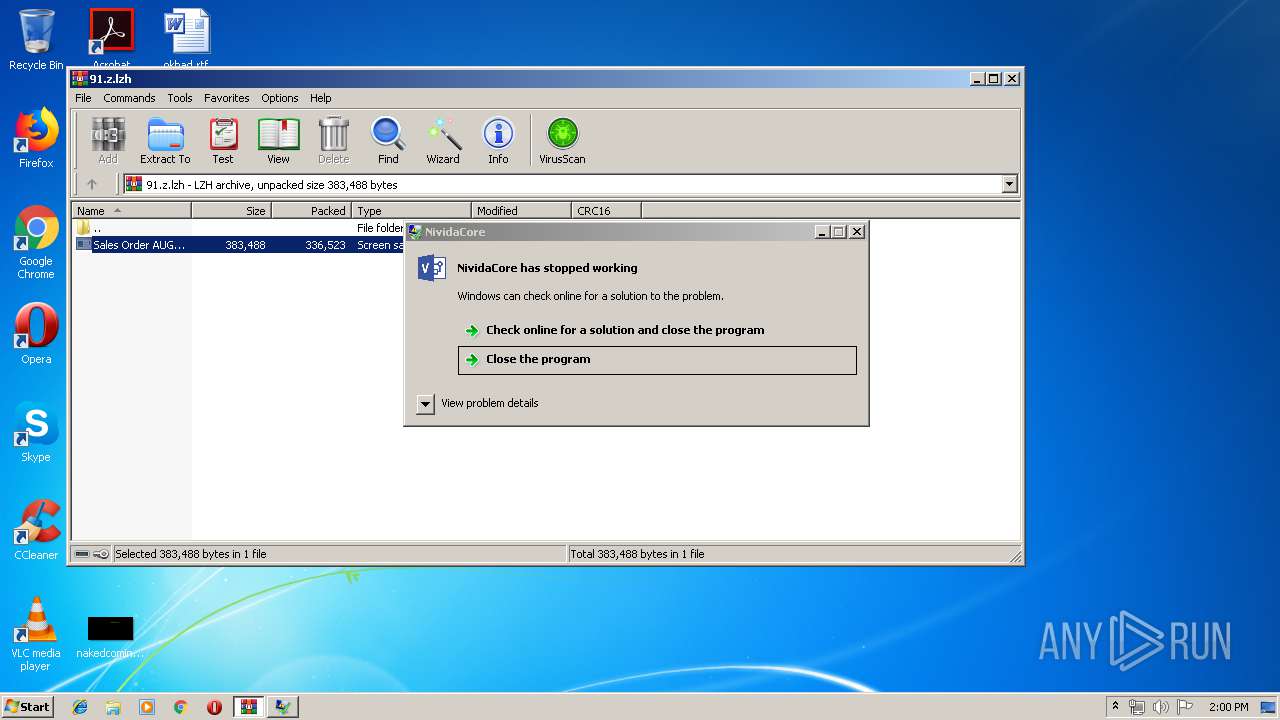
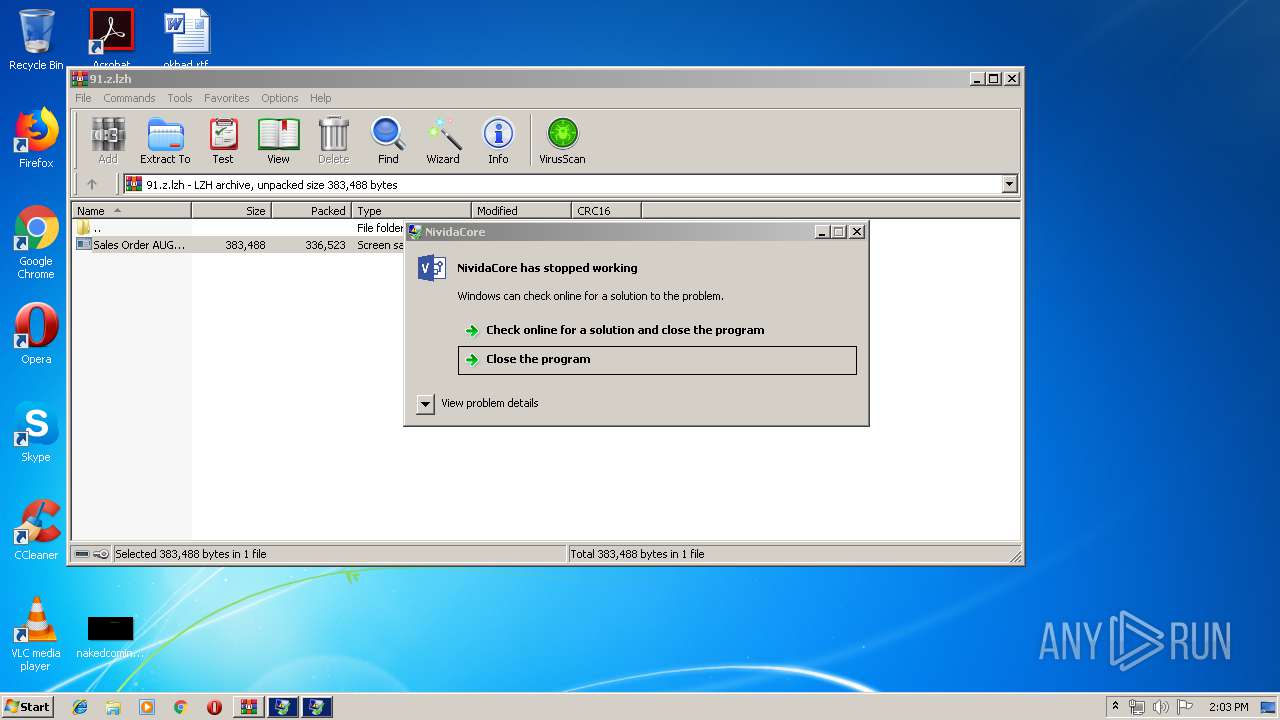
Application was crashed
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 3584)
- Sales Order AUGT (GD-2907019)_Docx.scr (PID: 2832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lzh/lha | | | LHARC/LZARK compressed archive (generic) (100) |
|---|
Total processes
46
Monitored processes
7
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2328 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\dHoxLCwd" /XML "C:\Users\admin\AppData\Local\Temp\tmpC4AC.tmp" | C:\Windows\System32\schtasks.exe | — | Sales Order AUGT (GD-2907019)_Docx.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\91.z.lzh" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2812 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.16854\Sales Order AUGT (GD-2907019)_Docx.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.16854\Sales Order AUGT (GD-2907019)_Docx.scr | — | WinRAR.exe | |||||||||||
User: admin Company: Nividia Host Corporations Integrity Level: MEDIUM Description: NividaCore Exit code: 0 Version: 9.9.4.6 Modules
| |||||||||||||||
| 2832 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.16854\Sales Order AUGT (GD-2907019)_Docx.scr" | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.16854\Sales Order AUGT (GD-2907019)_Docx.scr | Sales Order AUGT (GD-2907019)_Docx.scr | ||||||||||||
User: admin Company: Nividia Host Corporations Integrity Level: MEDIUM Description: NividaCore Exit code: 3221225477 Version: 9.9.4.6 Modules
| |||||||||||||||
| 3368 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\dHoxLCwd" /XML "C:\Users\admin\AppData\Local\Temp\tmp2C5F.tmp" | C:\Windows\System32\schtasks.exe | — | Sales Order AUGT (GD-2907019)_Docx.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3584 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.14643\Sales Order AUGT (GD-2907019)_Docx.scr" | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.14643\Sales Order AUGT (GD-2907019)_Docx.scr | Sales Order AUGT (GD-2907019)_Docx.scr | ||||||||||||
User: admin Company: Nividia Host Corporations Integrity Level: MEDIUM Description: NividaCore Exit code: 0 Version: 9.9.4.6 Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.14643\Sales Order AUGT (GD-2907019)_Docx.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.14643\Sales Order AUGT (GD-2907019)_Docx.scr | WinRAR.exe | ||||||||||||
User: admin Company: Nividia Host Corporations Integrity Level: MEDIUM Description: NividaCore Exit code: 0 Version: 9.9.4.6 Modules
| |||||||||||||||
Total events
615
Read events
589
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\91.z.lzh | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @shell32,-10162 |
Value: Screen saver | |||
| (PID) Process: | (2556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3624 | Sales Order AUGT (GD-2907019)_Docx.scr | C:\Users\admin\AppData\Local\Temp\tmpC4AC.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | Sales Order AUGT (GD-2907019)_Docx.scr | C:\Users\admin\AppData\Local\Temp\tmp2C5F.tmp | — | |
MD5:— | SHA256:— | |||
| 2556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.14643\Sales Order AUGT (GD-2907019)_Docx.scr | executable | |
MD5:— | SHA256:— | |||
| 2556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2556.16854\Sales Order AUGT (GD-2907019)_Docx.scr | executable | |
MD5:— | SHA256:— | |||
| 3624 | Sales Order AUGT (GD-2907019)_Docx.scr | C:\Users\admin\AppData\Roaming\dHoxLCwd.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3584 | Sales Order AUGT (GD-2907019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
2832 | Sales Order AUGT (GD-2907019)_Docx.scr | 79.134.225.39:2134 | ndubaba45.warzonedns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ndubaba45.warzonedns.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3584 | Sales Order AUGT (GD-2907019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
2832 | Sales Order AUGT (GD-2907019)_Docx.scr | A Network Trojan was detected | MALWARE [PTsecurity] AveMaria.RAT Encrypted Checkin |
2 ETPRO signatures available at the full report