| File name: | è°·æå®è£ å _19.25.13.exe |
| Full analysis: | https://app.any.run/tasks/d482301d-bc6d-4381-966a-a6273bb7bfab |
| Verdict: | Malicious activity |
| Threats: | FatalRAT is a malware that gives hackers remote access and control of the system and lets them steal sensitive information like login credentials and financial data. FatalRAT has been associated with cyber espionage campaigns, particularly targeting organizations in the Asia-Pacific (APAC) region. |
| Analysis date: | April 29, 2025, 14:12:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 312774722B2A953142E3D39C464FA9DF |
| SHA1: | 8F97BD42B627D1AAE74C775E78E05D85BD31B4AE |
| SHA256: | 30F1434C85FCBFB70B8C294460EE2F7368F4FF1AEBFB85E06AAC5ED3D5046C47 |
| SSDEEP: | 786432:VCkdXcQjbQerCh1ies8DJsQ+4rjpGuZFOazORU:VCicQjbQACh1ie7DJsr4rjMuZFDzO+ |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 684)
FATALRAT has been detected (SURICATA)
- svchost.exe (PID: 684)
SUSPICIOUS
Reads the Windows owner or organization settings
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
ADVANCEDINSTALLER mutex has been found
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
Process drops legitimate windows executable
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
Executable content was dropped or overwritten
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
- 135.0.7049.115_chrome_installer.exe (PID: 2288)
- setup.exe (PID: 2084)
Executes as Windows Service
- VSSVC.exe (PID: 5380)
- TjNKNP.exe (PID: 5452)
Detects AdvancedInstaller (YARA)
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- msiexec.exe (PID: 6040)
There is functionality for taking screenshot (YARA)
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
Application launched itself
- TjNKNP.exe (PID: 5680)
- TjNKNP.exe (PID: 6560)
- setup.exe (PID: 2084)
- setup.exe (PID: 1852)
- GoogleUpdate.exe (PID: 3300)
Process requests binary or script from the Internet
- svchost.exe (PID: 5048)
Potential Corporate Privacy Violation
- svchost.exe (PID: 5048)
Connects to unusual port
- svchost.exe (PID: 684)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 684)
INFO
Checks supported languages
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- msiexec.exe (PID: 6800)
- msiexec.exe (PID: 6040)
Reads Environment values
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
Reads the computer name
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- msiexec.exe (PID: 6040)
- msiexec.exe (PID: 6800)
Create files in a temporary directory
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
The sample compiled with chinese language support
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- msiexec.exe (PID: 6040)
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with english language support
- è°·æå®è£ å _19.25.13.exe (PID: 4724)
- msiexec.exe (PID: 6040)
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
- 135.0.7049.115_chrome_installer.exe (PID: 2288)
- setup.exe (PID: 2084)
Manages system restore points
- SrTasks.exe (PID: 3304)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6040)
The sample compiled with french language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with german language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
Manual execution by a user
- TjNKNP.exe (PID: 6560)
- TjNKNP.exe (PID: 5680)
- setup.exe (PID: 4152)
The sample compiled with arabic language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with bulgarian language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with czech language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with spanish language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with Indonesian language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with japanese language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with Italian language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
Starts application with an unusual extension
- msiexec.exe (PID: 6040)
The sample compiled with korean language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with polish language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with swedish language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with russian language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with turkish language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with portuguese language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
The sample compiled with slovak language support
- setup.exe (PID: 4152)
- GoogleUpdateSetup.exe (PID: 6816)
Executes as Windows Service
- elevation_service.exe (PID: 2040)
Application launched itself
- chrome.exe (PID: 6708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:05:31 13:15:01+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 2484736 |
| InitializedDataSize: | 945664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d6f94 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| CompanyName: | TargetCommandSwiftUI |
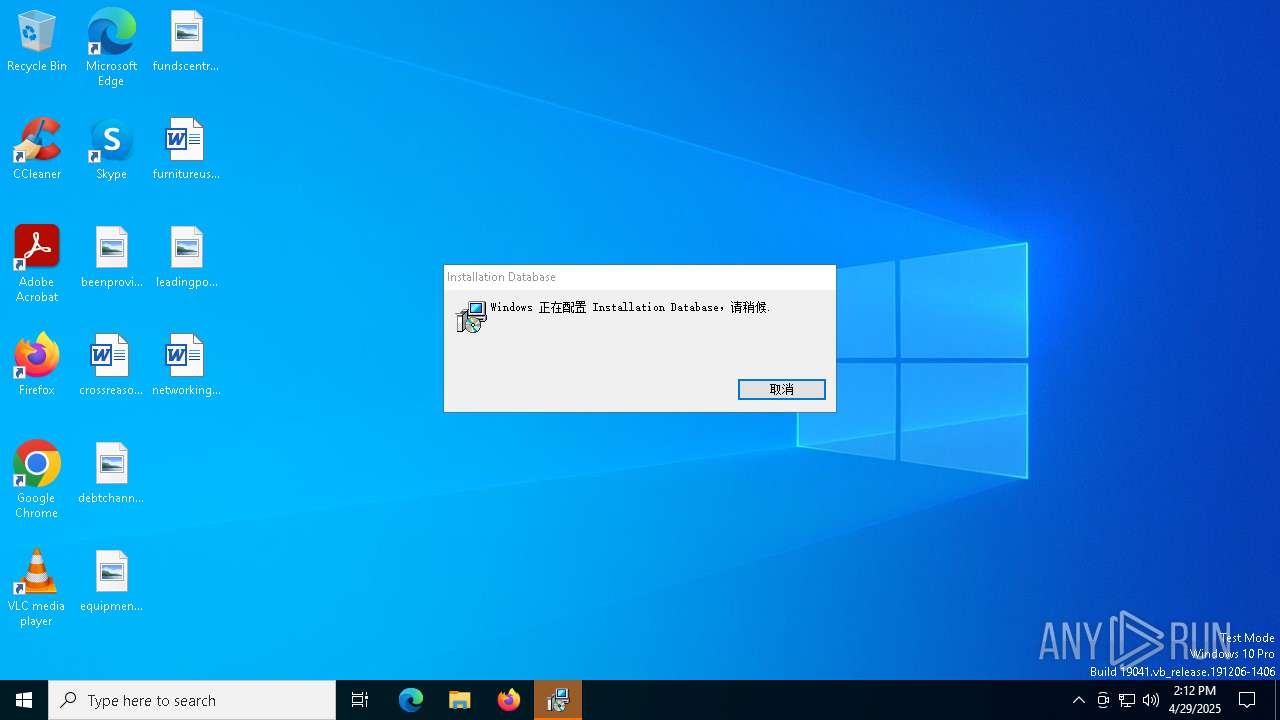
| FileDescription: | Installation Database Installer |
| FileVersion: | 1.0.0 |
| InternalName: | 转接口 |
| LegalCopyright: | Copyright (C) 2025 TargetCommandSwiftUI |
| OriginalFileName: | 转接口.exe |
| ProductName: | Installation Database |
| ProductVersion: | 1.0.0 |
Total processes
206
Monitored processes
77
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files (x86)\Google\Update\Install\{52590461-AC34-473F-88B6-86CA11481751}\CR_BC89C.tmp\setup.exe" --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=135.0.7049.115 --initial-client-data=0x290,0x294,0x298,0x26c,0x29c,0x7ff65bbb95f8,0x7ff65bbb9604,0x7ff65bbb9610 | C:\Program Files (x86)\Google\Update\Install\{52590461-AC34-473F-88B6-86CA11481751}\CR_BC89C.tmp\setup.exe | — | setup.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 135.0.7049.115 Modules
| |||||||||||||||
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --field-trial-handle=1996,i,3888499534003619586,4328887081420140704,262144 --variations-seed-version --mojo-platform-channel-handle=5188 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 135.0.7049.115 Modules
| |||||||||||||||
| 684 | "C:\ProgramData\NVIDIARV\svchost.exe" | C:\ProgramData\NVIDIARV\svchost.exe | setup.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Modules
| |||||||||||||||
| 856 | C:\Windows\syswow64\MsiExec.exe -Embedding DCB98D3C3D6C90C0852E4D9F5653CB25 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | TjNKNP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --field-trial-handle=1996,i,3888499534003619586,4328887081420140704,262144 --variations-seed-version --mojo-platform-channel-handle=4148 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 135.0.7049.115 Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | TjNKNP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=1996,i,3888499534003619586,4328887081420140704,262144 --variations-seed-version --mojo-platform-channel-handle=3440 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 135.0.7049.115 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=1996,i,3888499534003619586,4328887081420140704,262144 --variations-seed-version --mojo-platform-channel-handle=3940 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 135.0.7049.115 Modules
| |||||||||||||||
| 1240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 757
Read events
23 008
Write events
1 709
Delete events
40
Modification events
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000008F4BD9C310B9DB0198170000180C0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000F7AEDBC310B9DB0198170000180C0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000050D752C410B9DB0198170000180C0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000050D752C410B9DB0198170000180C0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000DB0C5AC410B9DB0198170000180C0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000008A745CC410B9DB0198170000180C0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6040) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (5380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000FB74EBC410B9DB0104150000001A0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5380) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | write | Name: | Element |
Value: 0000000000000000000000000000000006000000000000004800000000000000715E5C2FA985EB1190A89A9B763584210000000000000000745E5C2FA985EB1190A89A9B7635842100000000000000000000000000000000 | |||
Executable files
162
Suspicious files
153
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | è°·æå®è£ å _19.25.13.exe | C:\Users\admin\AppData\Roaming\TargetCommandSwiftUI\Installation Database 1.0.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 4724 | è°·æå®è£ å _19.25.13.exe | C:\Users\admin\AppData\Roaming\TargetCommandSwiftUI\Installation Database 1.0.0\install\5DE3BAC\转接口.msi | — | |
MD5:— | SHA256:— | |||
| 6040 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6040 | msiexec.exe | C:\Windows\Installer\113fd5.msi | — | |
MD5:— | SHA256:— | |||
| 4724 | è°·æå®è£ å _19.25.13.exe | C:\Users\admin\AppData\Roaming\TargetCommandSwiftUI\Installation Database 1.0.0\install\5DE3BAC\CommonAppDataFolder\backup\LineInst.exe | — | |
MD5:— | SHA256:— | |||
| 4724 | è°·æå®è£ å _19.25.13.exe | C:\Users\admin\AppData\Local\Temp\MSIF263.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 4724 | è°·æå®è£ å _19.25.13.exe | C:\Users\admin\AppData\Local\Temp\shiF09B.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 6040 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{abdff9b6-bb9b-42e1-93db-84e79728de91}_OnDiskSnapshotProp | binary | |
MD5:44F0C931BDF71718EECE248C69E38039 | SHA256:0FDFDE2F4D5E7AF1C27D5281CB6E1DF27A324FEFEBBBDC5E701AEB491264E46F | |||
| 6040 | msiexec.exe | C:\Windows\Installer\MSI4362.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
| 6040 | msiexec.exe | C:\Windows\Installer\MSI42F4.tmp | executable | |
MD5:C7FBD5EE98E32A77EDF1156DB3FCA622 | SHA256:E140990B509DD6884A5742BDE64F2CDAA10012D472B0B32DE43EBECBC83242B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
62
DNS requests
67
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2552 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2552 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5048 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome/ackxpvrm3yhql4zsr7kcxuakkwkq_135.0.7049.115/135.0.7049.115_chrome_installer.exe | unknown | — | — | whitelisted |
3300 | GoogleUpdate.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
3300 | GoogleUpdate.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
3620 | chrome.exe | GET | 200 | 216.58.206.46:80 | http://clients2.google.com/time/1/current?cup2key=8:lBZ5M3HM9OTKOPtVFNaOeVhc6sqdbyxkMHk5bN8-6Zk&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3300 | GoogleUpdate.exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDQZgpWpezrXAmFnbj86J49 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.40:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2552 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2552 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
5048 | svchost.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5048 | svchost.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
5048 | svchost.exe | Misc activity | ET INFO Packed Executable Download |
684 | svchost.exe | Malware Command and Control Activity Detected | ET MALWARE FatalRAT CnC Activity |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |