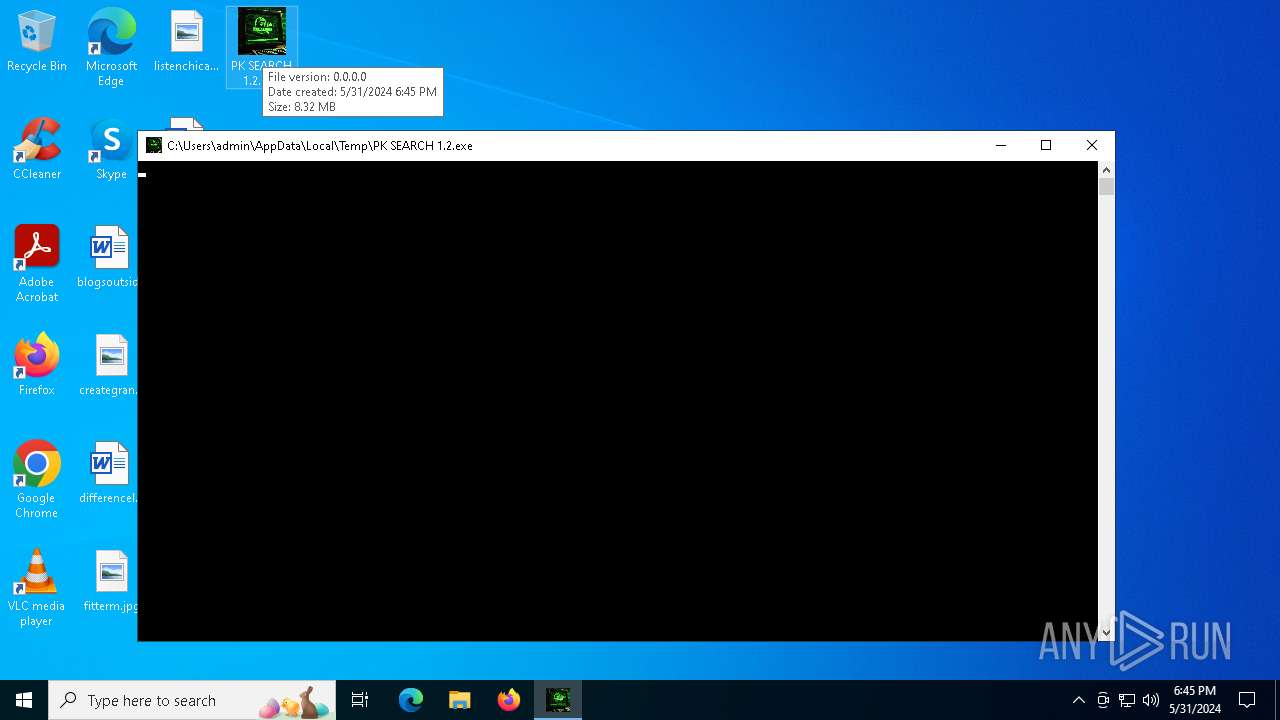
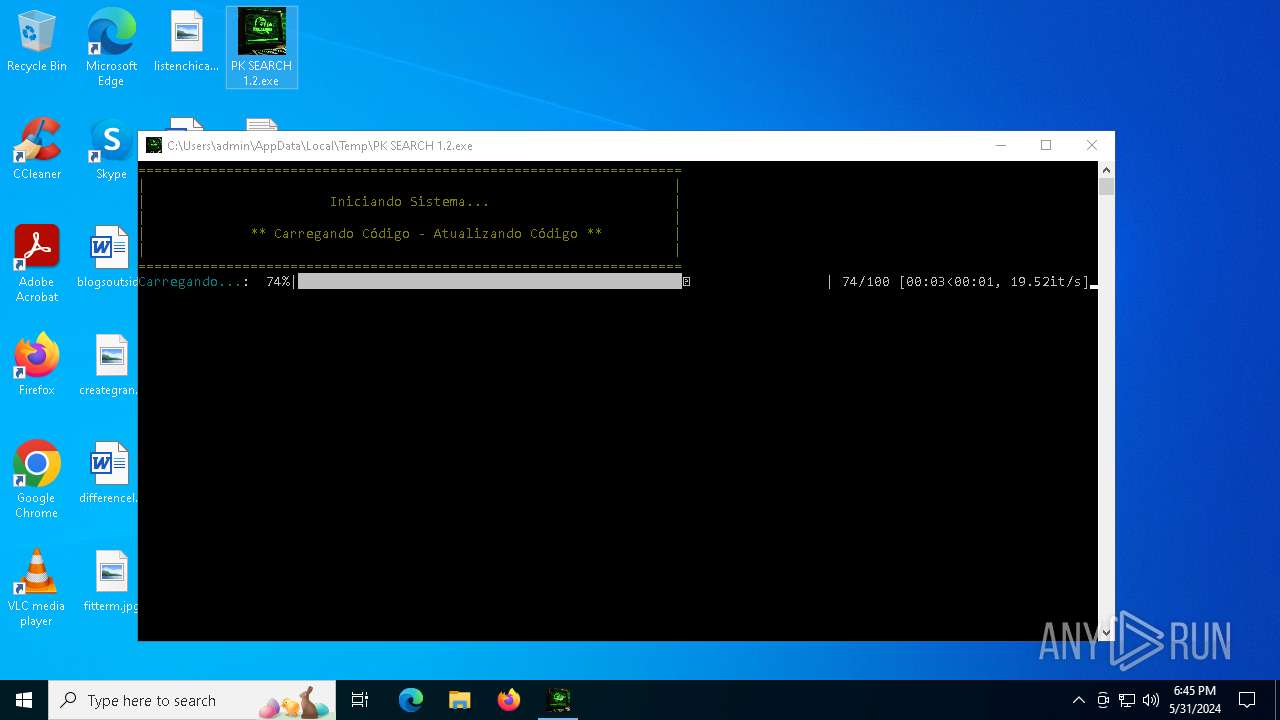
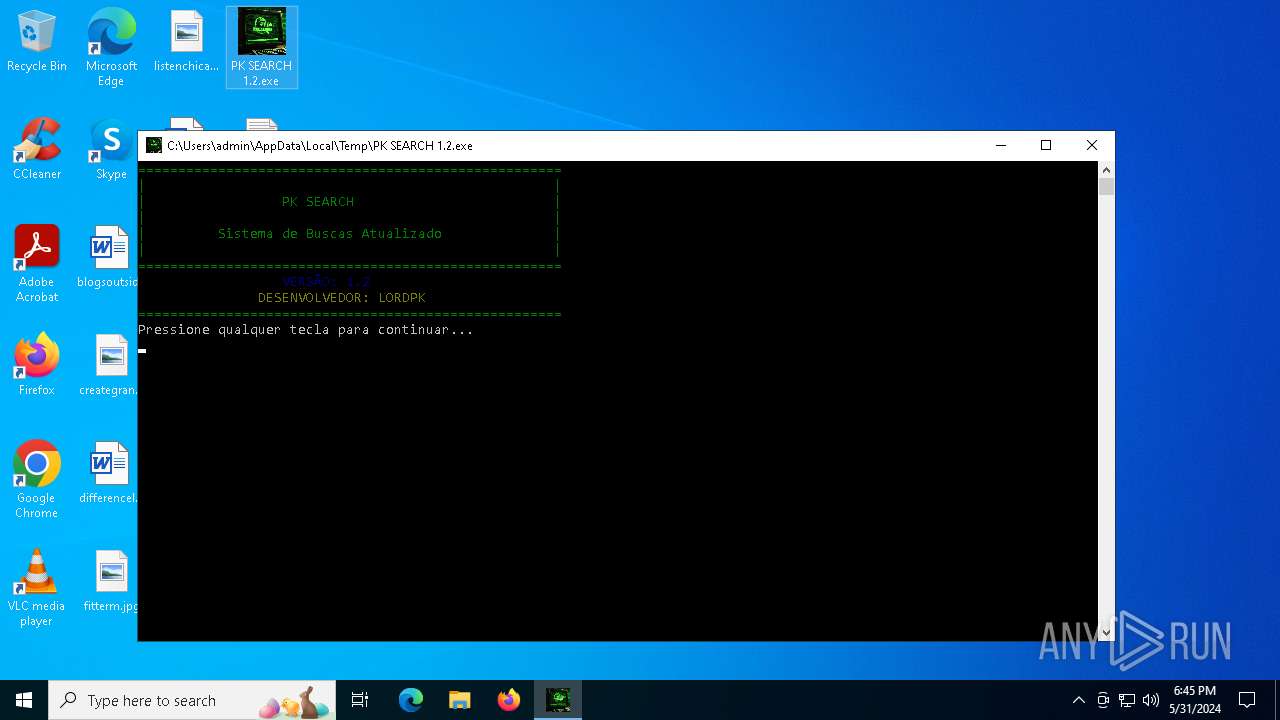
| File name: | PK SEARCH 1.2.exe |
| Full analysis: | https://app.any.run/tasks/b2f845d9-35ee-46a1-b2f1-0dcd3ef4e357 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 31, 2024, 18:45:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | AF1683832F44BB89893C189F94786304 |
| SHA1: | EA14D8CE6ACDBC76A3612E4576831C483FFDA674 |
| SHA256: | 30EC0A2D9D0564BB7596326733902C73B69C5AB3572A84E1C077C680372F2CC3 |
| SSDEEP: | 98304:VcJ4kobsrn7IRoRjfjBdJEhm8LZ50LLfw9T0/4DO7NQ+dukjplD9mG9S2piBs+Z9:g56StCnSZ5kVUmxT |
MALICIOUS
Drops the executable file immediately after the start
- PK SEARCH 1.2.exe (PID: 6268)
- PK SEARCH 1.2.exe (PID: 6364)
ASYNCRAT has been detected (YARA)
- PK SEARCH.exe (PID: 6332)
SUSPICIOUS
The process drops C-runtime libraries
- PK SEARCH 1.2.exe (PID: 6364)
Process drops legitimate windows executable
- PK SEARCH 1.2.exe (PID: 6364)
Executable content was dropped or overwritten
- PK SEARCH 1.2.exe (PID: 6268)
- PK SEARCH 1.2.exe (PID: 6364)
Process drops python dynamic module
- PK SEARCH 1.2.exe (PID: 6364)
Application launched itself
- PK SEARCH 1.2.exe (PID: 6364)
Starts CMD.EXE for commands execution
- PK SEARCH 1.2.exe (PID: 6444)
Connects to unusual port
- PK SEARCH.exe (PID: 6332)
Loads Python modules
- PK SEARCH 1.2.exe (PID: 6444)
Reads the date of Windows installation
- PK SEARCH 1.2.exe (PID: 6268)
Reads security settings of Internet Explorer
- PK SEARCH 1.2.exe (PID: 6268)
INFO
Reads the computer name
- PK SEARCH 1.2.exe (PID: 6268)
- PK SEARCH.exe (PID: 6332)
- PK SEARCH 1.2.exe (PID: 6364)
Checks supported languages
- PK SEARCH 1.2.exe (PID: 6364)
- PK SEARCH 1.2.exe (PID: 6268)
- PK SEARCH 1.2.exe (PID: 6444)
- PK SEARCH.exe (PID: 6332)
Creates files or folders in the user directory
- PK SEARCH.exe (PID: 6332)
Reads the machine GUID from the registry
- PK SEARCH.exe (PID: 6332)
- PK SEARCH 1.2.exe (PID: 6268)
Create files in a temporary directory
- PK SEARCH 1.2.exe (PID: 6364)
- PK SEARCH 1.2.exe (PID: 6268)
Reads Environment values
- PK SEARCH.exe (PID: 6332)
Process checks computer location settings
- PK SEARCH 1.2.exe (PID: 6268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(6332) PK SEARCH.exe
C2 (1)186.26.107.205
Ports (1)4400
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexzifbymzliwgywfwv
InstallFolder%Temp%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_Signaturefp8wQrPO0A3qalnFveEA9dY+WRbUu9cwrHbH8ASj4ZfptFKb1hhpjozLPwQHV90Q2Ehwj17WM8t9dJ036oOQZ7sq4YCx97w6iLqQi6txmXY7C7E39tNcvT0EZx0Hu6jZ7CxhxFOoIRwUHp/P/guu6lReeMDTyHZDktP2CHH9LP0=
Keys
AES9f80269e8e0fcdbe799ec5c5392ea8eebf99473d4522f56be5ae67f875812d86
SaltVenomRATByVenom
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:30 22:15:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 11 |
| CodeSize: | 8457216 |
| InitializedDataSize: | 271872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | XBinderOutput.exe |
| LegalCopyright: | |
| OriginalFileName: | XBinderOutput.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
120
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6268 | "C:\Users\admin\Desktop\PK SEARCH 1.2.exe" | C:\Users\admin\Desktop\PK SEARCH 1.2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 6332 | "C:\Users\admin\AppData\Local\Temp\PK SEARCH.exe" | C:\Users\admin\AppData\Local\Temp\PK SEARCH.exe | PK SEARCH 1.2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 6.0.1 Modules
AsyncRat(PID) Process(6332) PK SEARCH.exe C2 (1)186.26.107.205 Ports (1)4400 VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3 Options AutoRuntrue Mutexzifbymzliwgywfwv InstallFolder%Temp% Certificates Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN... Server_Signaturefp8wQrPO0A3qalnFveEA9dY+WRbUu9cwrHbH8ASj4ZfptFKb1hhpjozLPwQHV90Q2Ehwj17WM8t9dJ036oOQZ7sq4YCx97w6iLqQi6txmXY7C7E39tNcvT0EZx0Hu6jZ7CxhxFOoIRwUHp/P/guu6lReeMDTyHZDktP2CHH9LP0= Keys AES9f80269e8e0fcdbe799ec5c5392ea8eebf99473d4522f56be5ae67f875812d86 SaltVenomRATByVenom | |||||||||||||||
| 6364 | "C:\Users\admin\AppData\Local\Temp\PK SEARCH 1.2.exe" | C:\Users\admin\AppData\Local\Temp\PK SEARCH 1.2.exe | PK SEARCH 1.2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PK SEARCH 1.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | "C:\Users\admin\AppData\Local\Temp\PK SEARCH 1.2.exe" | C:\Users\admin\AppData\Local\Temp\PK SEARCH 1.2.exe | — | PK SEARCH 1.2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | PK SEARCH 1.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 538
Read events
4 530
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6268) PK SEARCH 1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6268) PK SEARCH 1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6268) PK SEARCH 1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6268) PK SEARCH 1.2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
19
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6268 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\PK SEARCH.exe | executable | |
MD5:01E77A0B330B7432C5AB92A199C9255A | SHA256:C4ED073EF70F66AD998F88BBB06F376BD5A99EC850C9F6550F258FE295DE1730 | |||
| 6268 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\PK SEARCH 1.2.exe | executable | |
MD5:02386348258A629E287754B1960C0491 | SHA256:5220E076C62D44A682B829675E235C87B5B3CB7D0A920E2DC8C02516E3F0E2DD | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\_ctypes.pyd | executable | |
MD5:452305C8C5FDA12F082834C3120DB10A | SHA256:543CE9D6DC3693362271A2C6E7D7FC07AD75327E0B0322301DD29886467B0B0E | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\_bz2.pyd | executable | |
MD5:90F58F625A6655F80C35532A087A0319 | SHA256:BD8621FCC901FA1DE3961D93184F61EA71068C436794AF2A4449738CCF949946 | |||
| 6332 | PK SEARCH.exe | C:\Users\admin\AppData\Roaming\MyData\DataLogs.conf | text | |
MD5:CF759E4C5F14FE3EEC41B87ED756CEA8 | SHA256:C9F9F193409217F73CC976AD078C6F8BF65D3AABCF5FAD3E5A47536D47AA6761 | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\libcrypto-3.dll | executable | |
MD5:51E8A5281C2092E45D8C97FBDBF39560 | SHA256:2A234B5AA20C3FAECF725BBB54FB33F3D94543F78FA7045408E905593E49960A | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\python312.dll | executable | |
MD5:48EBFEFA21B480A9B0DBFC3364E1D066 | SHA256:0CC4E557972488EB99EA4AEB3D29F3ADE974EF3BCD47C211911489A189A0B6F2 | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\_queue.pyd | executable | |
MD5:5AA4B057BA2331EED6B4B30F4B3E0D52 | SHA256:D43DCA0E00C3C11329B68177E967CF5240495C4786F5AFA76AC4F267C3A5CDB9 | |||
| 6364 | PK SEARCH 1.2.exe | C:\Users\admin\AppData\Local\Temp\_MEI63642\libffi-8.dll | executable | |
MD5:0F8E4992CA92BAAF54CC0B43AACCCE21 | SHA256:EFF52743773EB550FCC6CE3EFC37C85724502233B6B002A35496D828BD7B280A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
23
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 13.69.239.79:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5612 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4856 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
6332 | PK SEARCH.exe | 186.26.107.205:4400 | — | 2MM2 SERVICOS DE TELECOMUNICACOES | BR | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5456 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2908 | OfficeClickToRun.exe | 20.189.173.18:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |