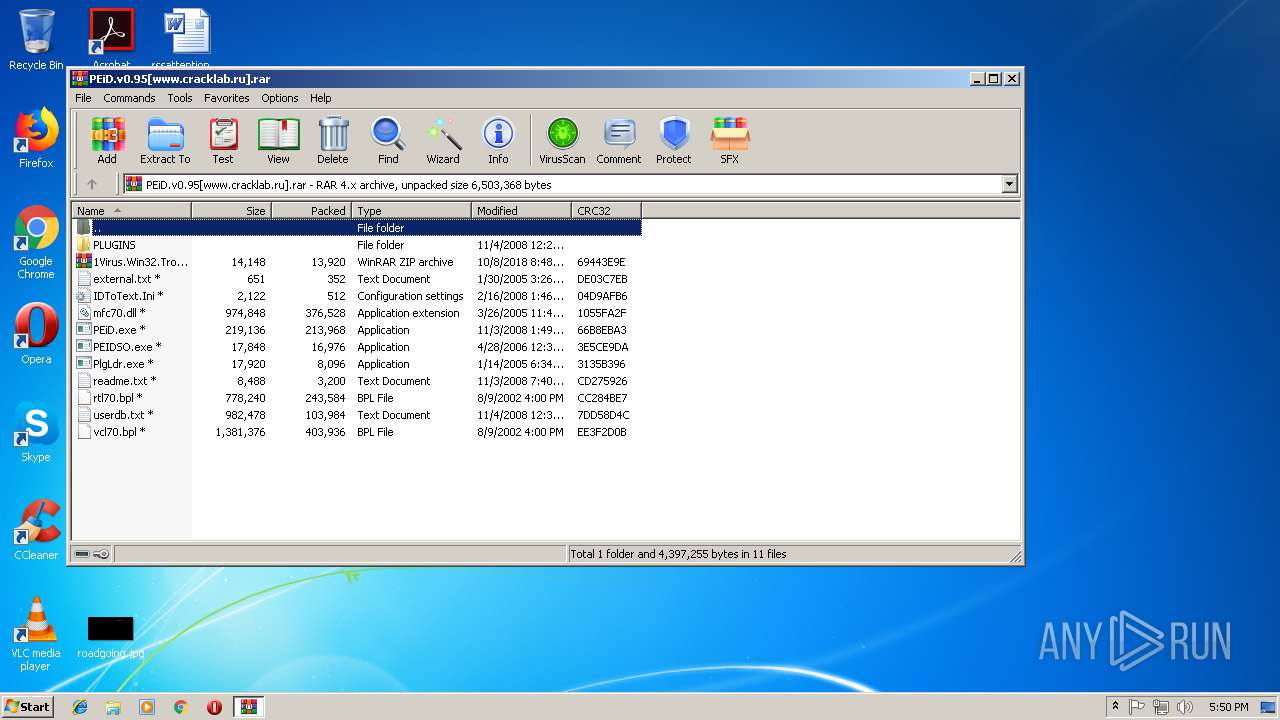
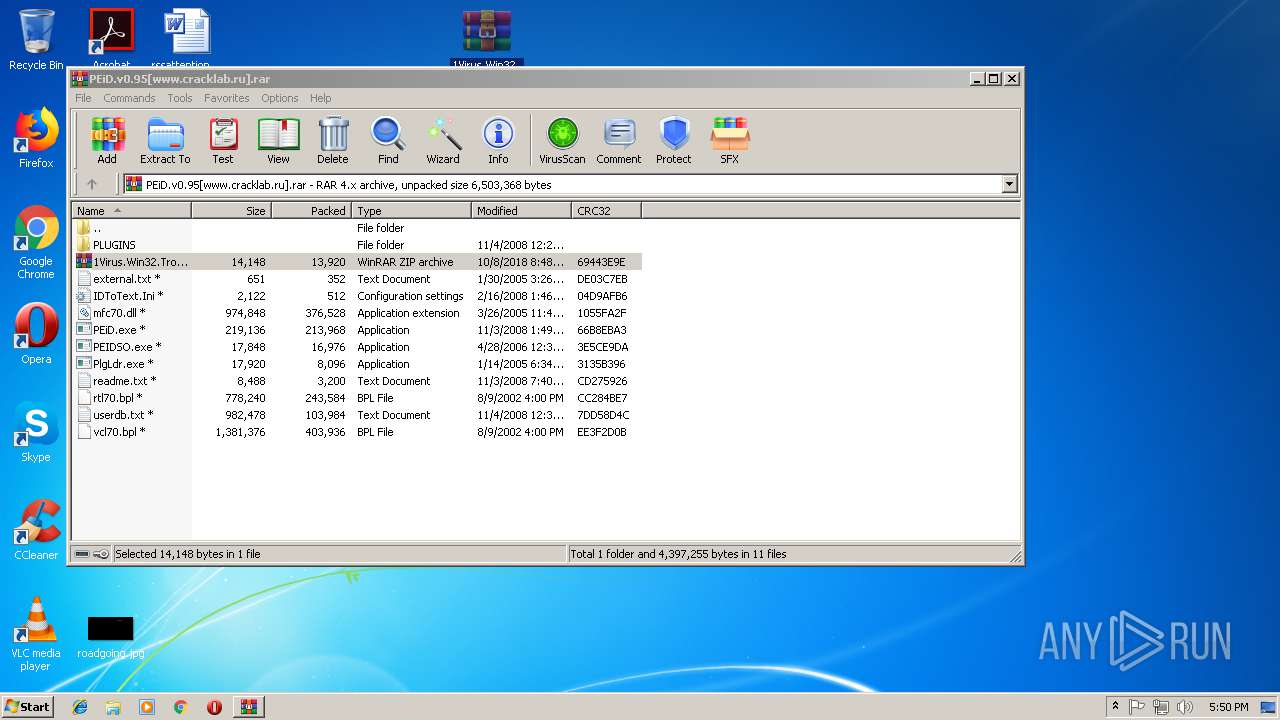
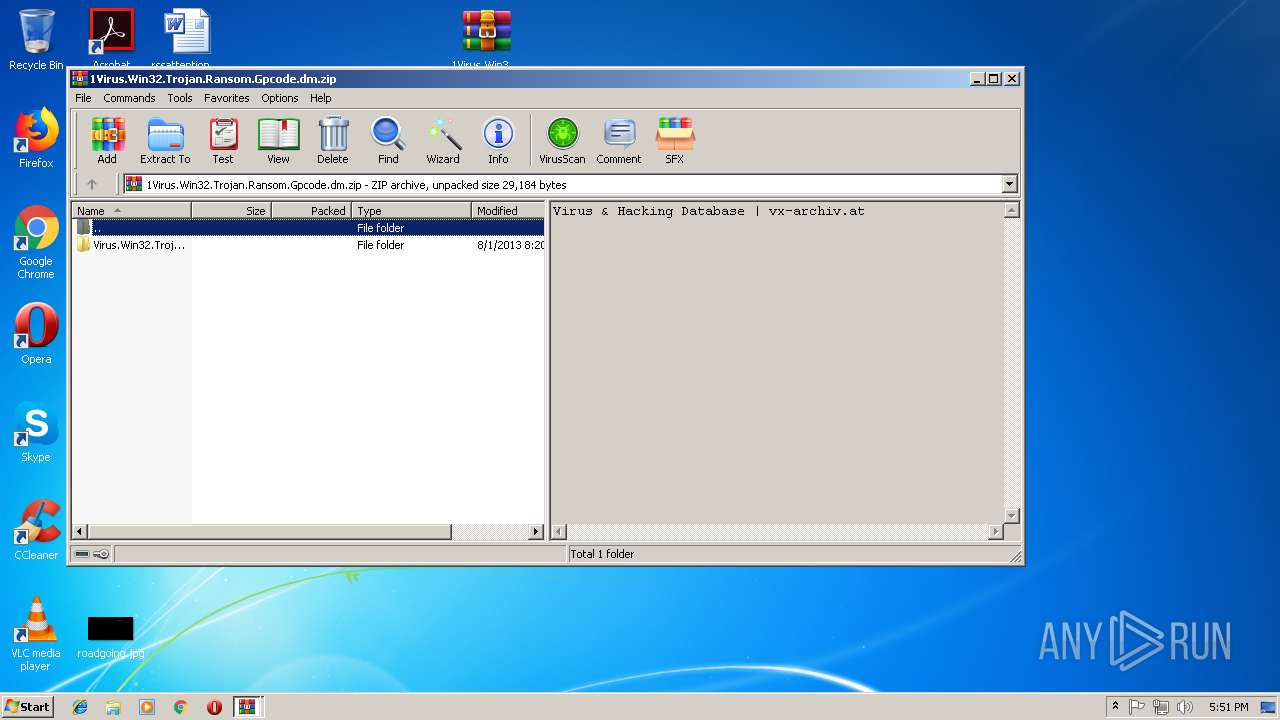
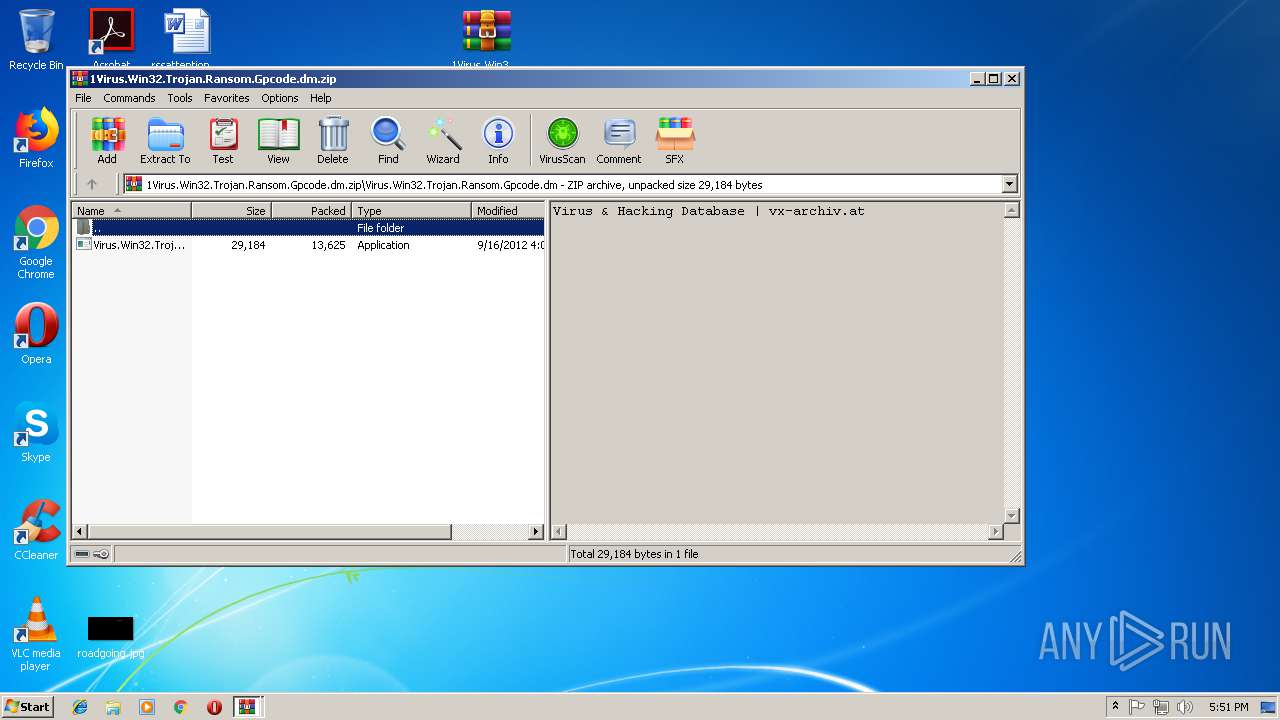
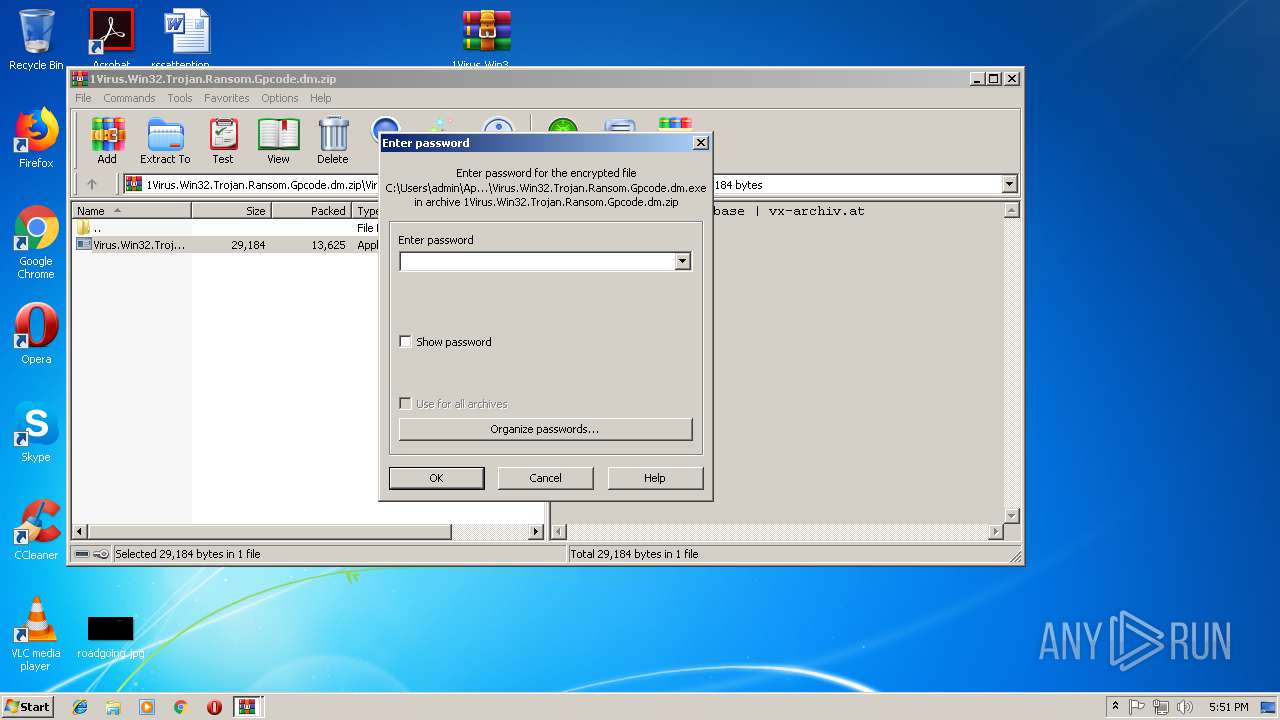
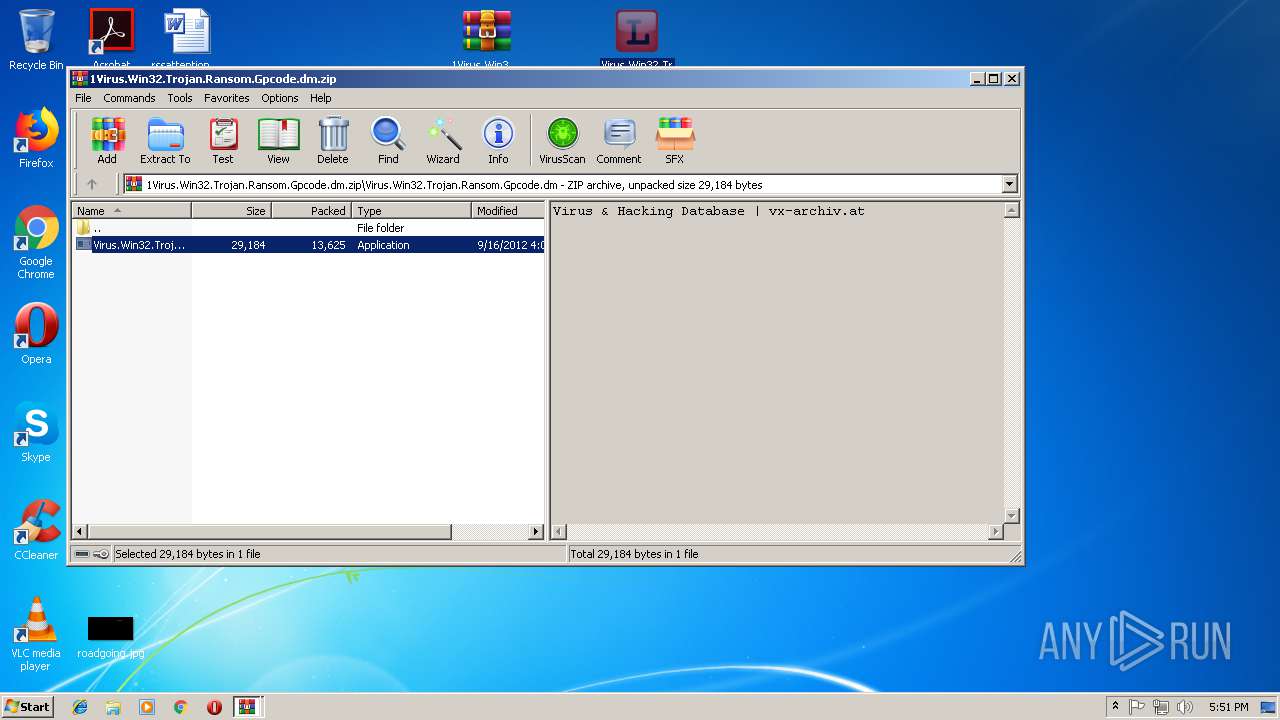
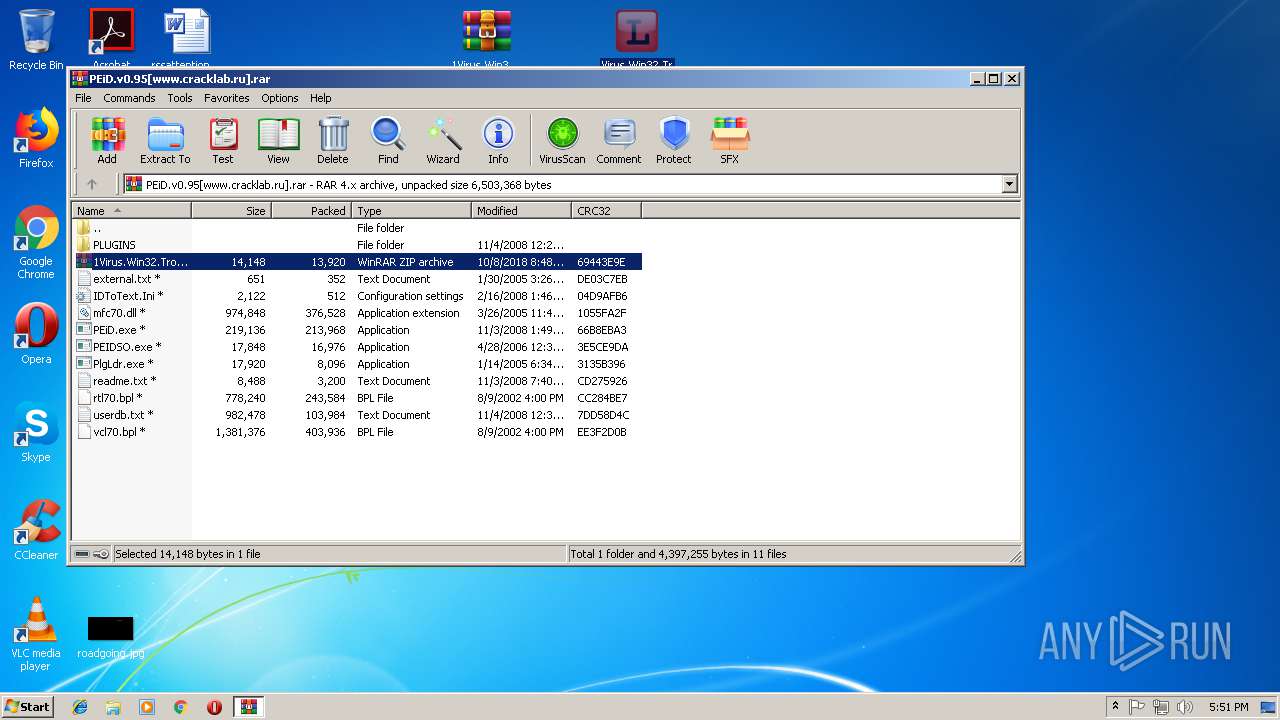
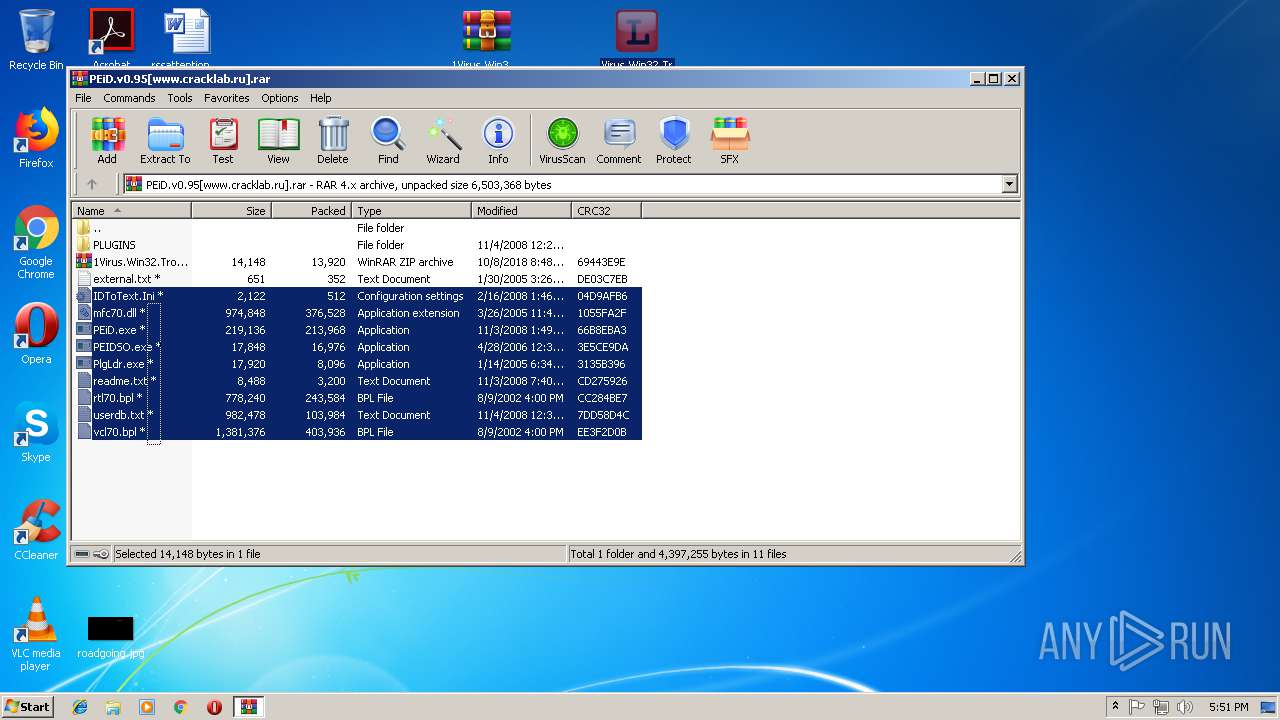
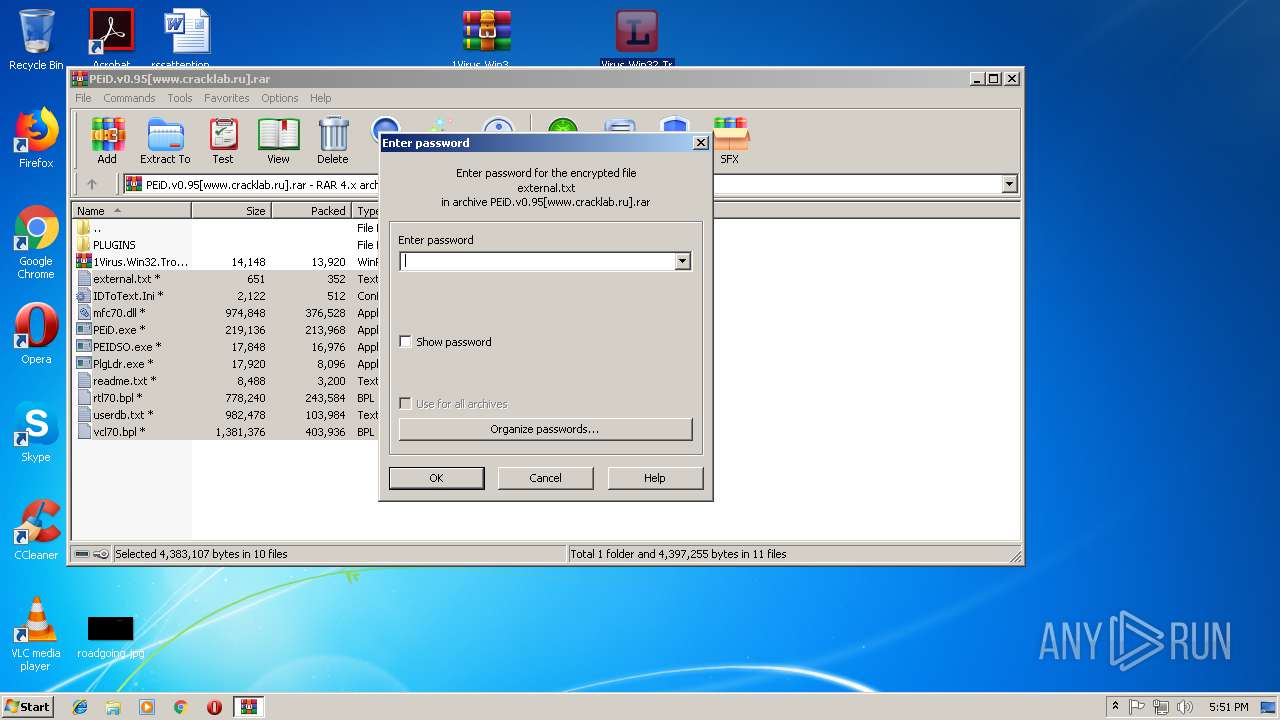
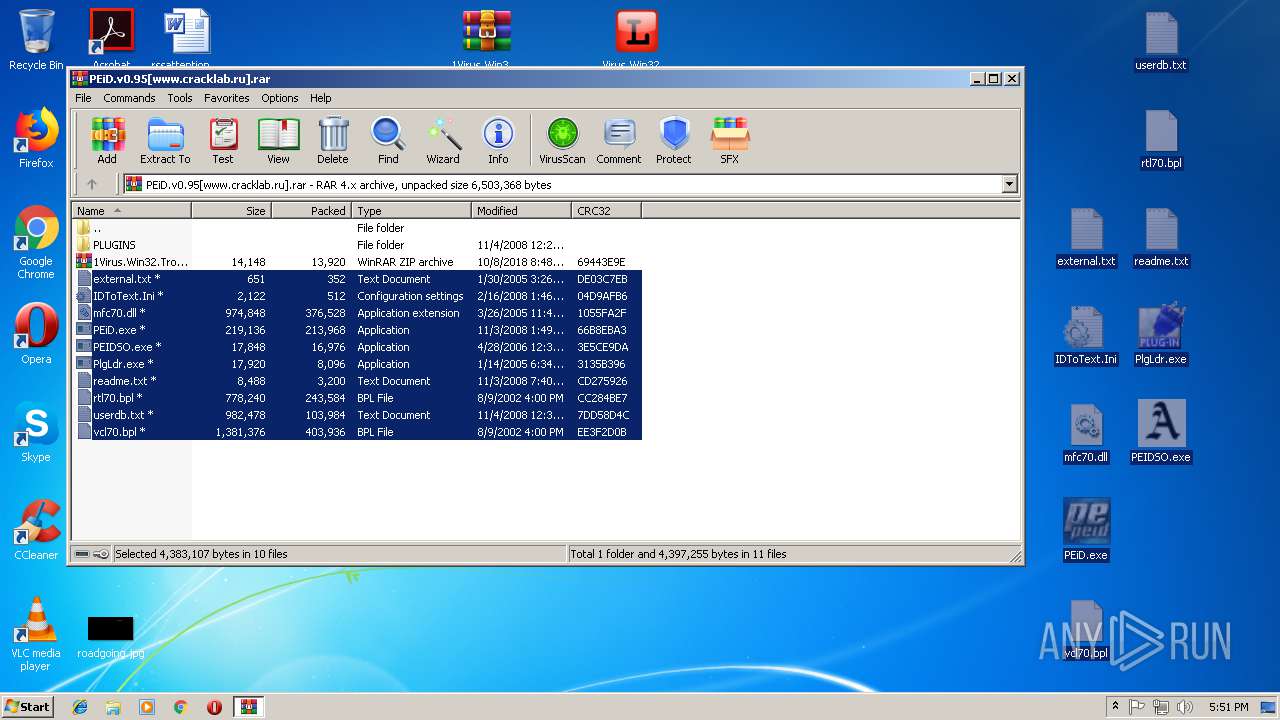
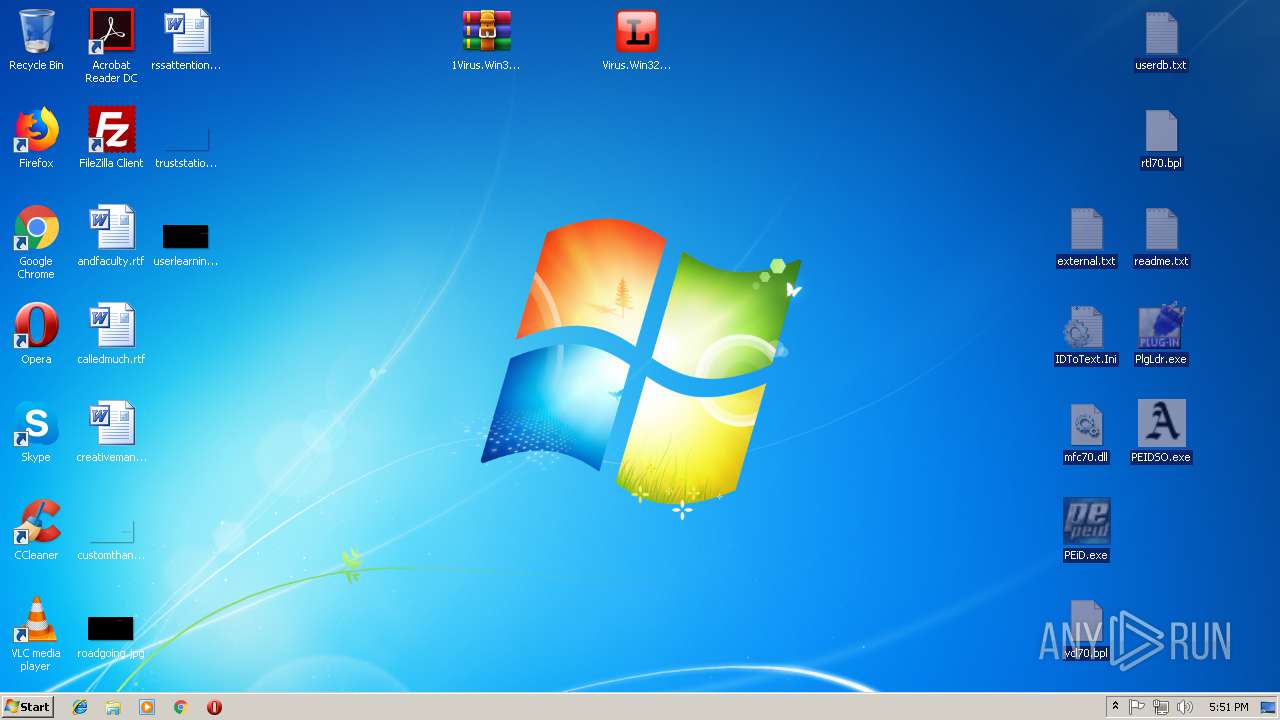
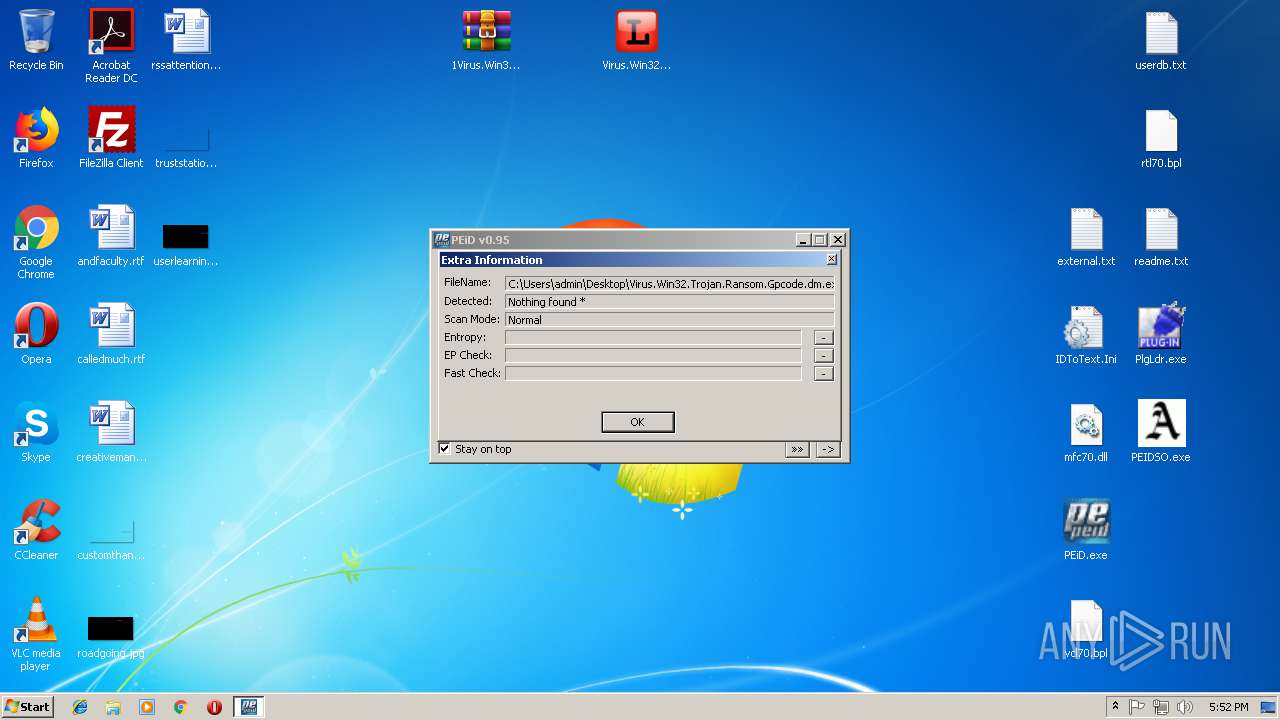
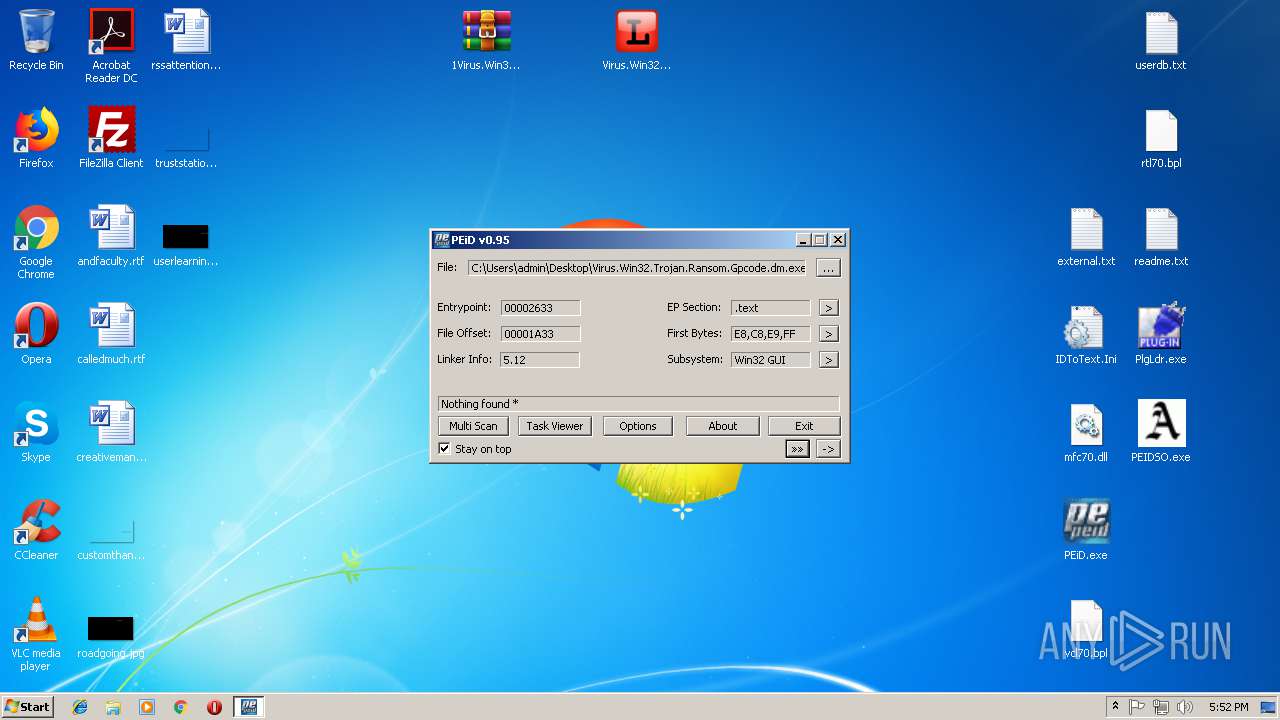
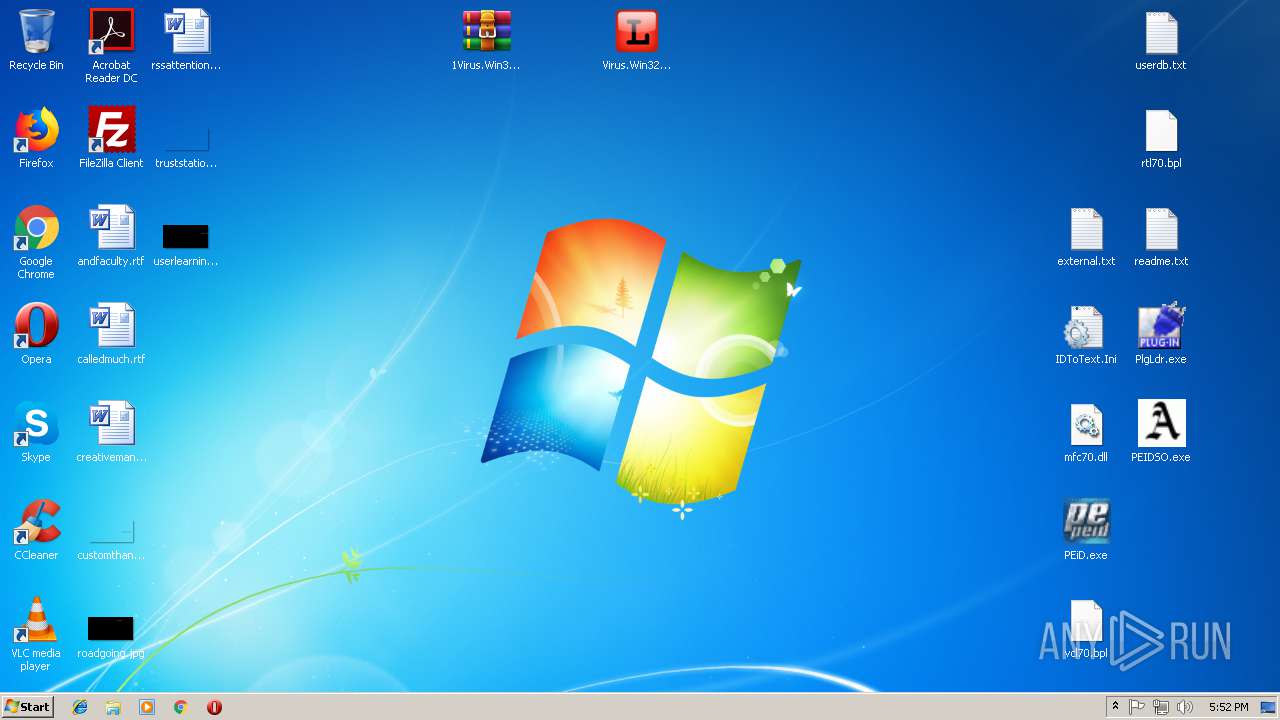
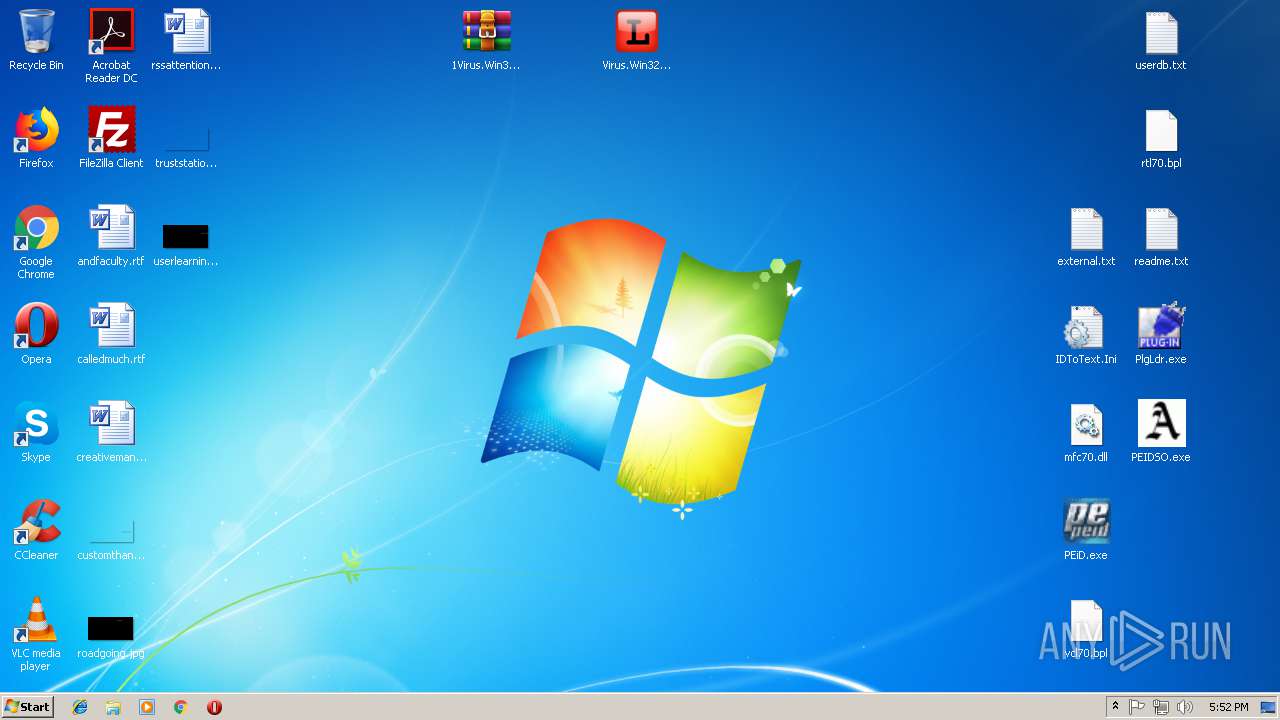
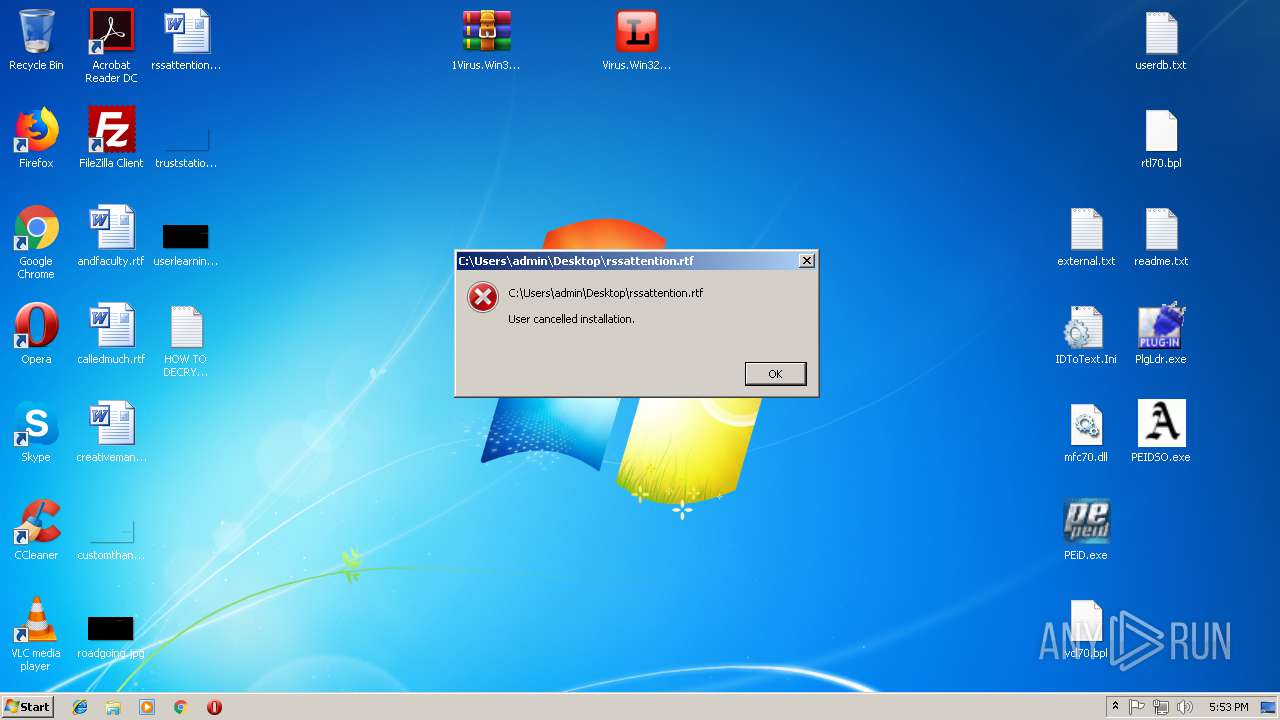
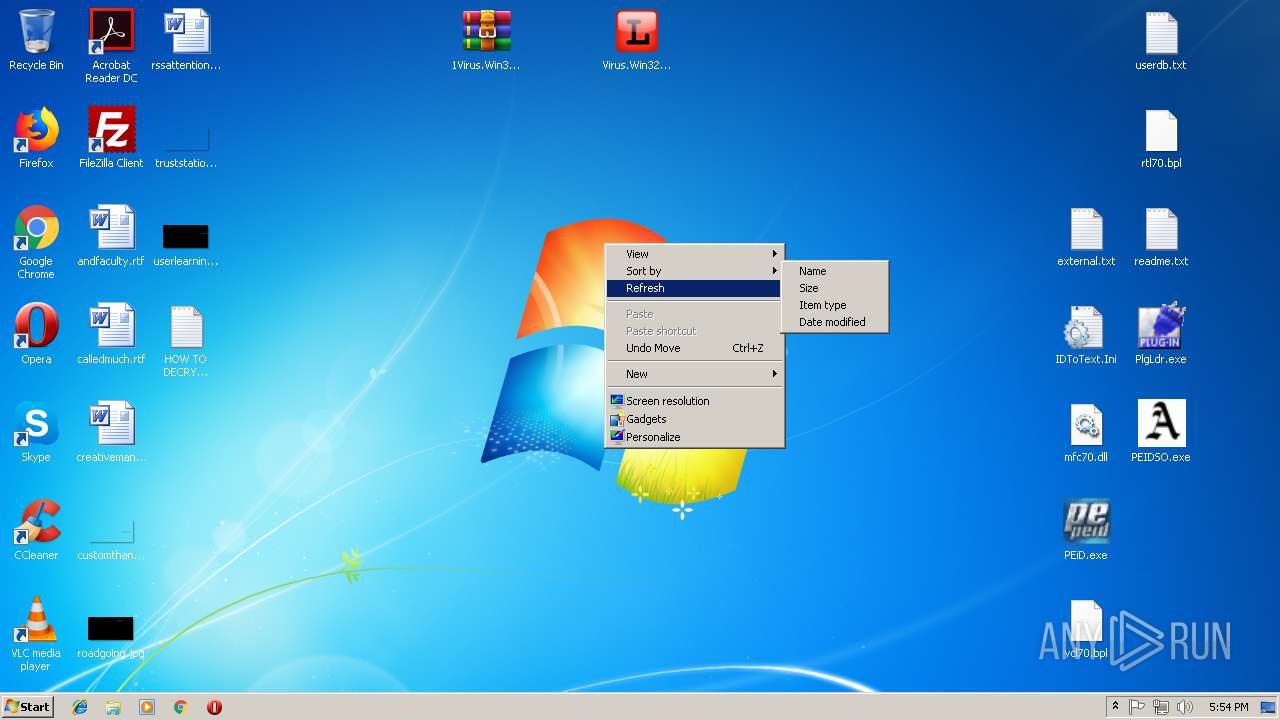
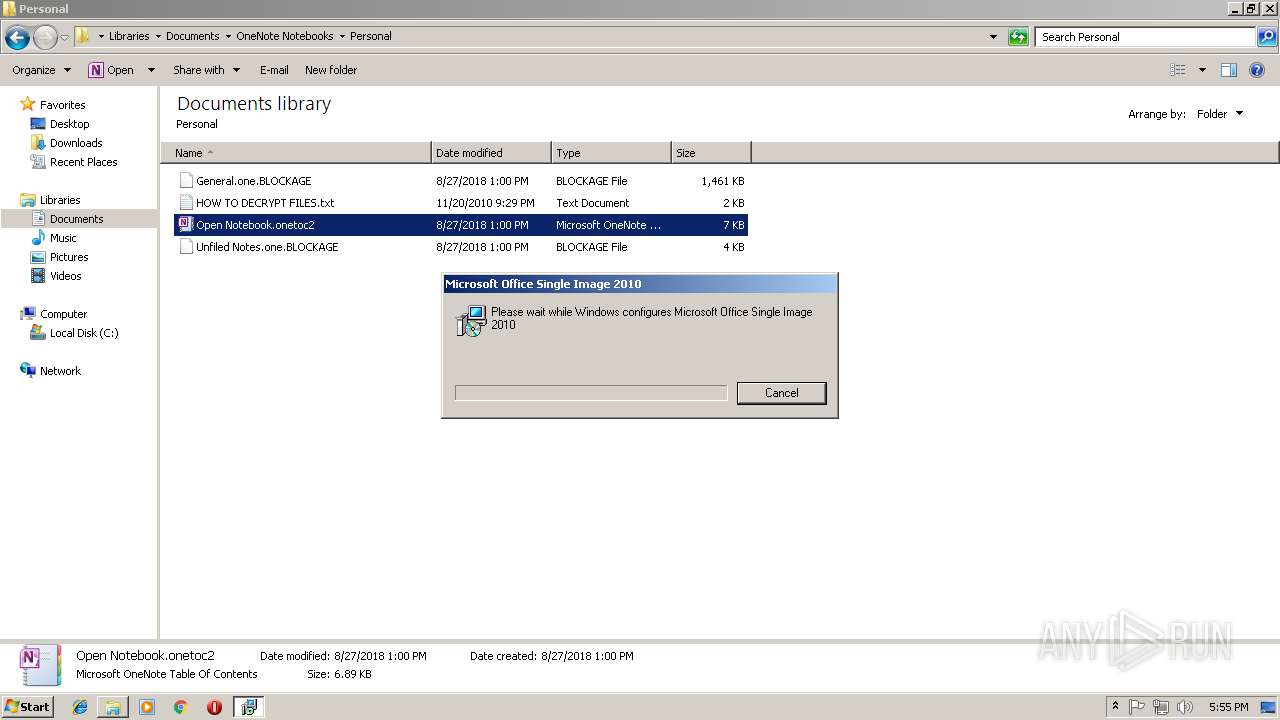
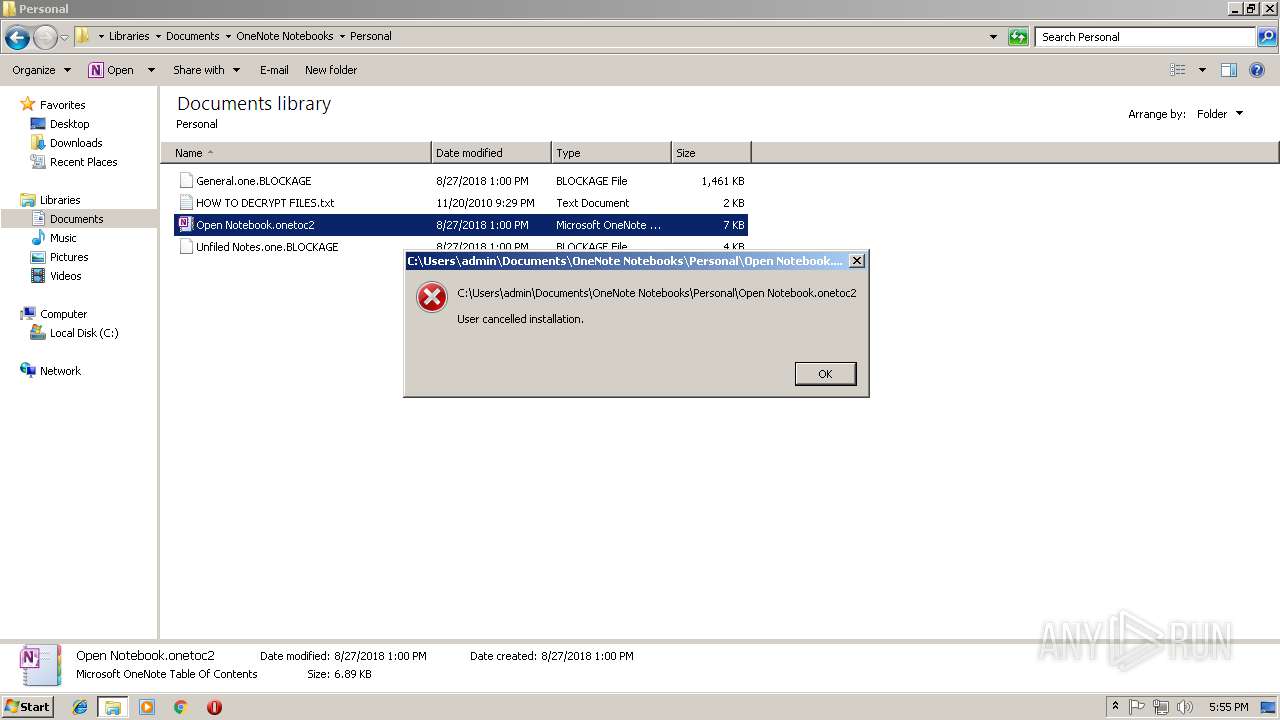
| File name: | PEiD.v0.95[www.cracklab.ru].rar |
| Full analysis: | https://app.any.run/tasks/be3d2d45-3f2d-4c10-9bd3-a0e62c7fee89 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | October 08, 2018, 16:50:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 628032C7BC8AD9E369D6D5A2870256E8 |
| SHA1: | 2682A9461CC0DDFCE6AB5616B61B7C7D807F914A |
| SHA256: | 307B3E6E1225B7EBB3B26462C49D449124F23D462AA92C0C826C571AC9B639FA |
| SSDEEP: | 49152:AAnjm0wVHwA1zKXr/TGS82RjqHszN+DvS7Cqelhk4n9vD9zY+VLG/KRxmTZ1Wg/:vavr0XrrVNeS7Chlh77Y+xTqTZ1Ww |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3740)
- SearchProtocolHost.exe (PID: 1992)
Application was dropped or rewritten from another process
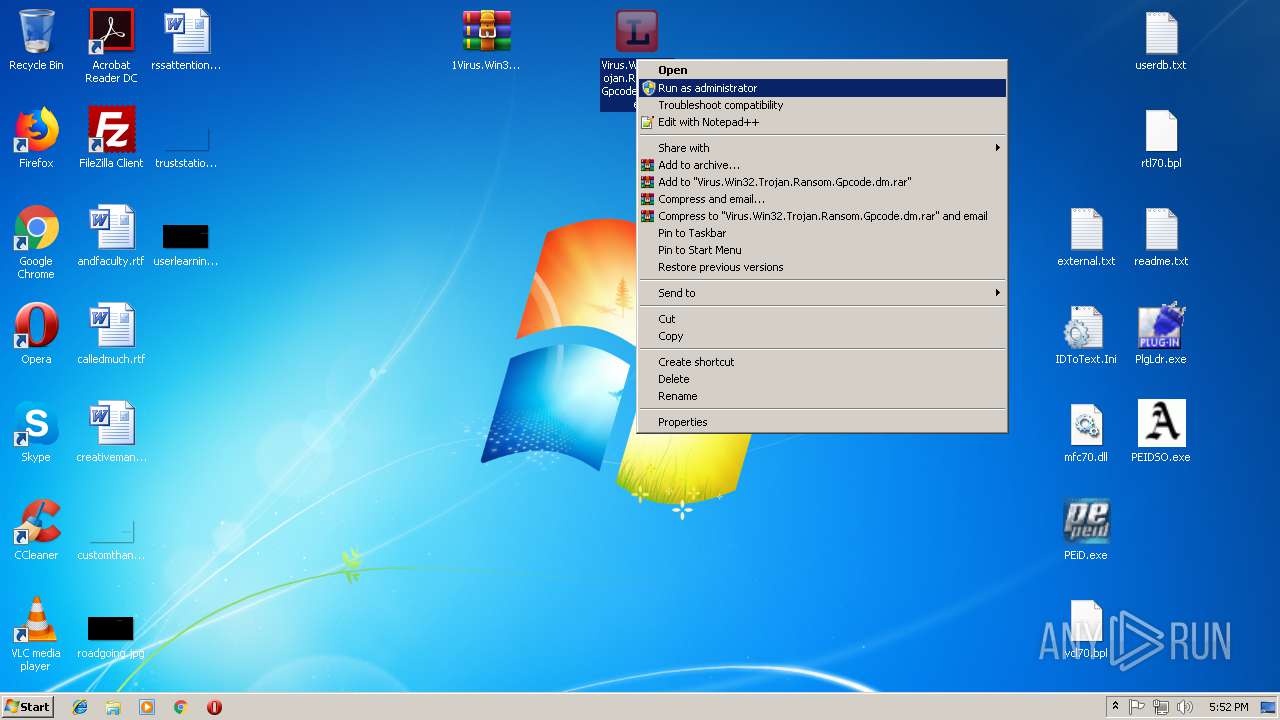
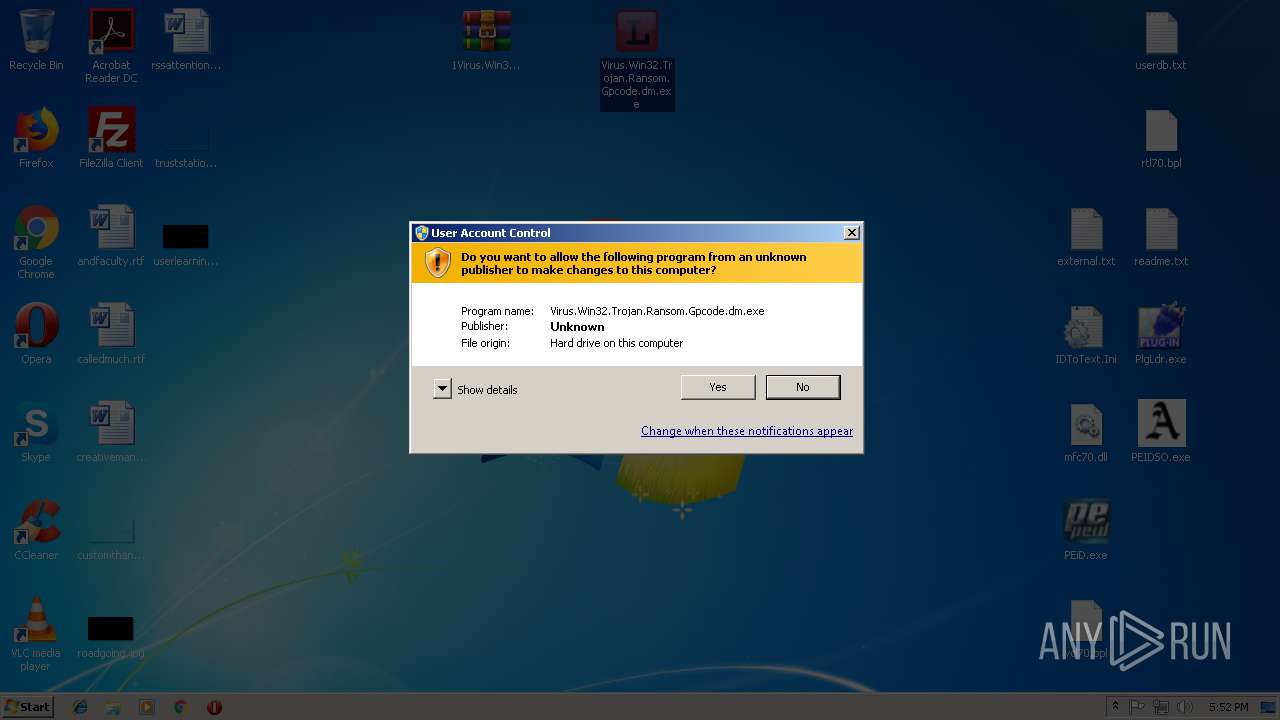
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
- PEiD.exe (PID: 1088)
Writes to a start menu file
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
Actions looks like stealing of personal data
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
Stealing of credential data
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
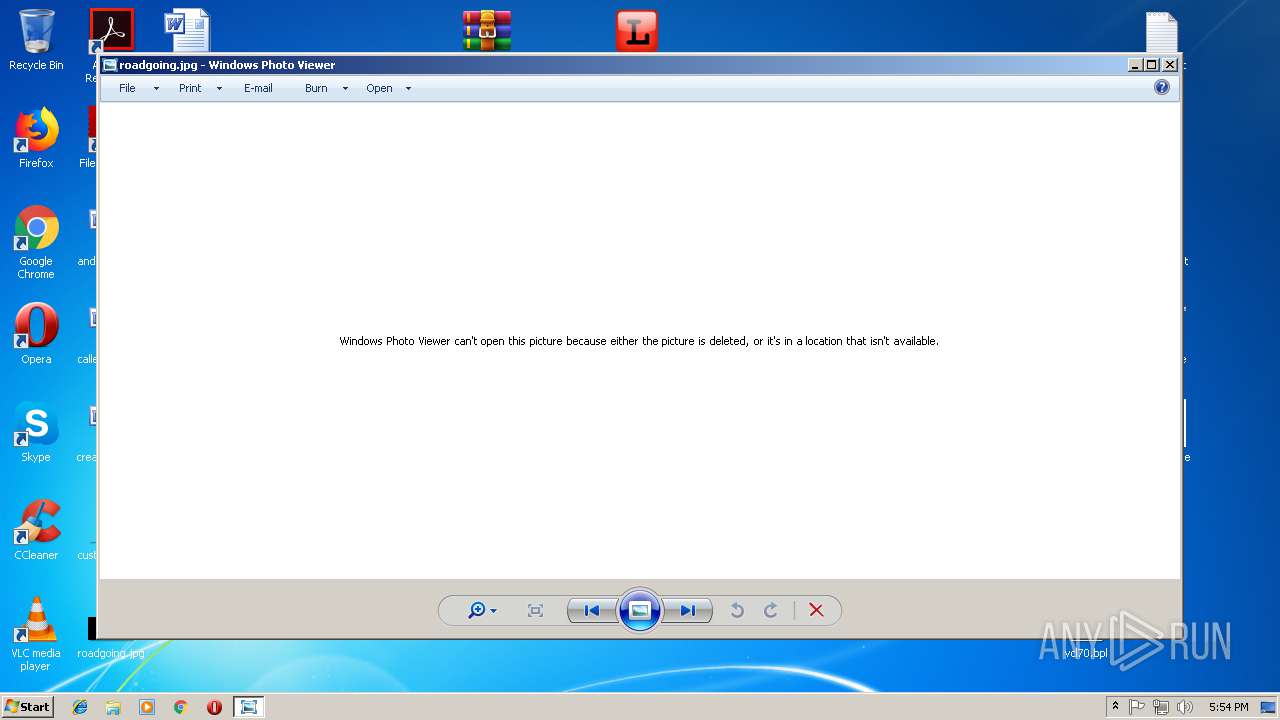
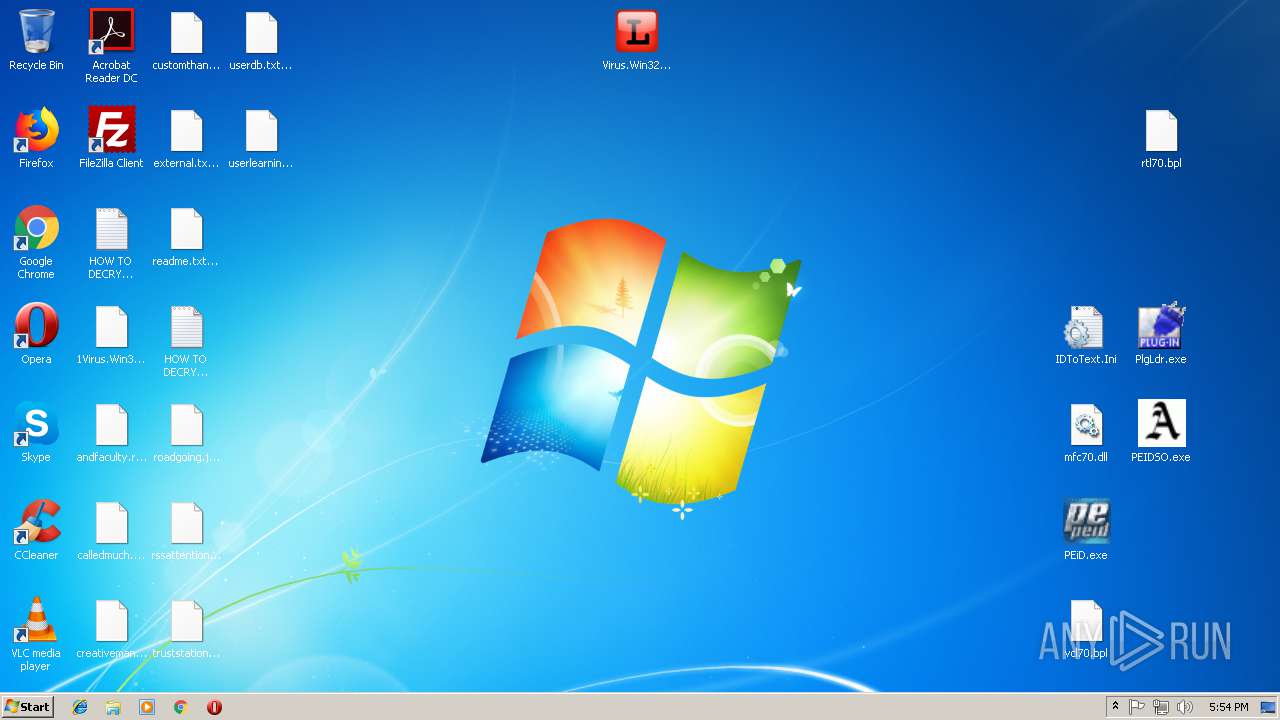
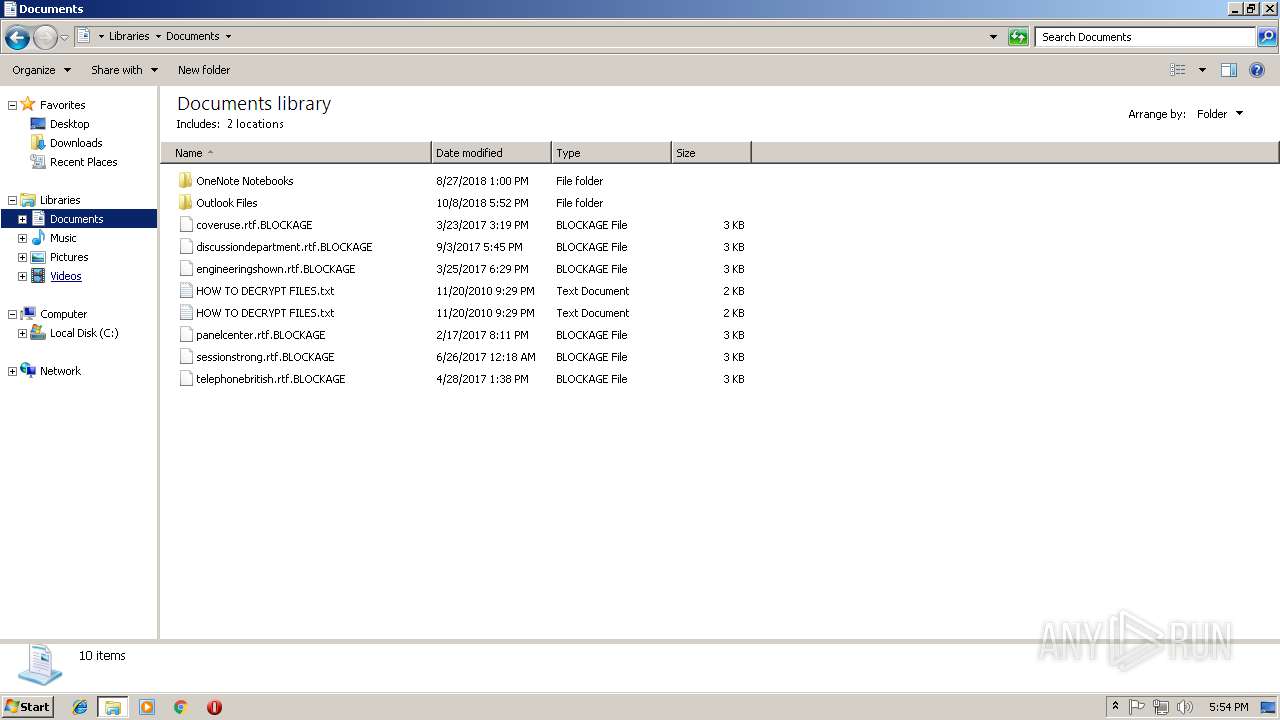
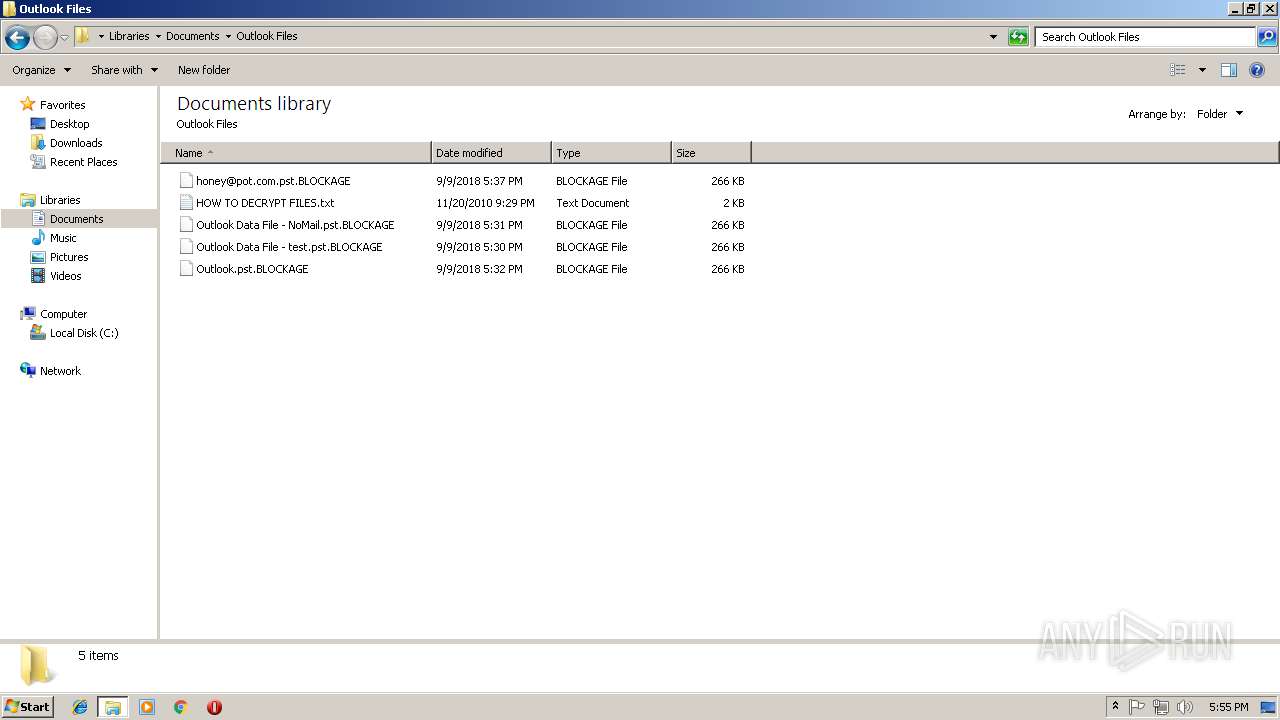
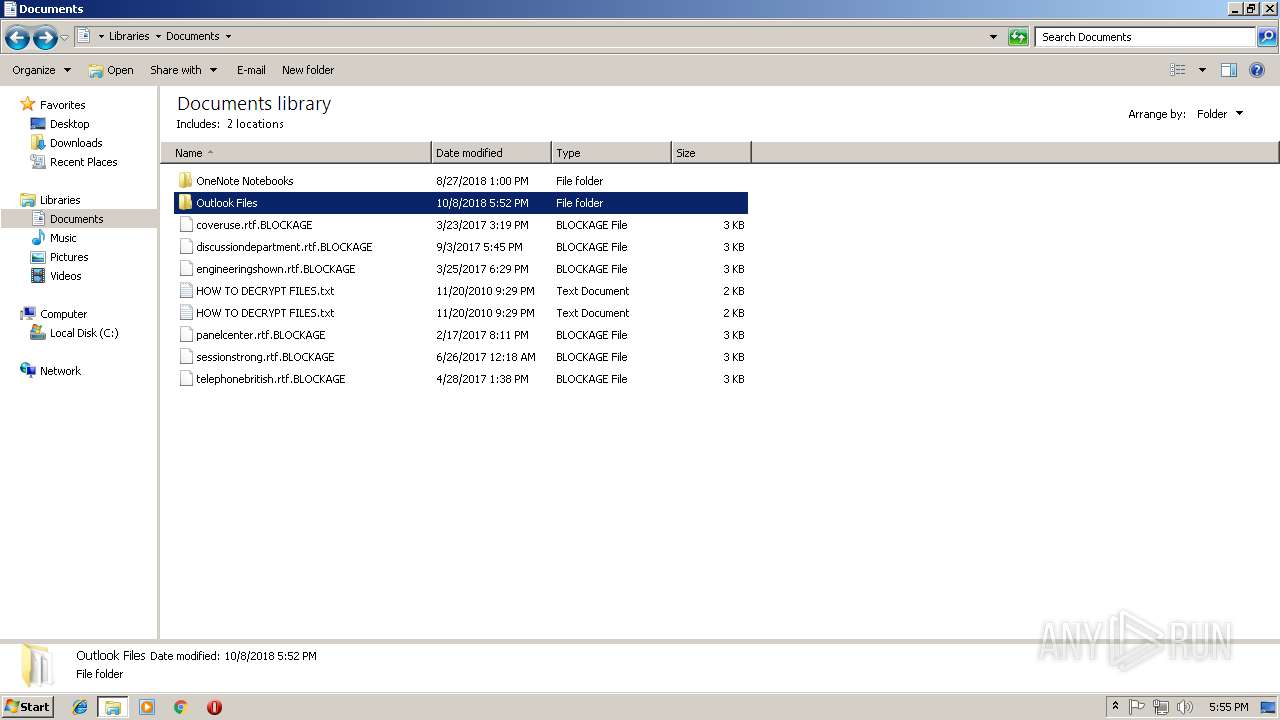
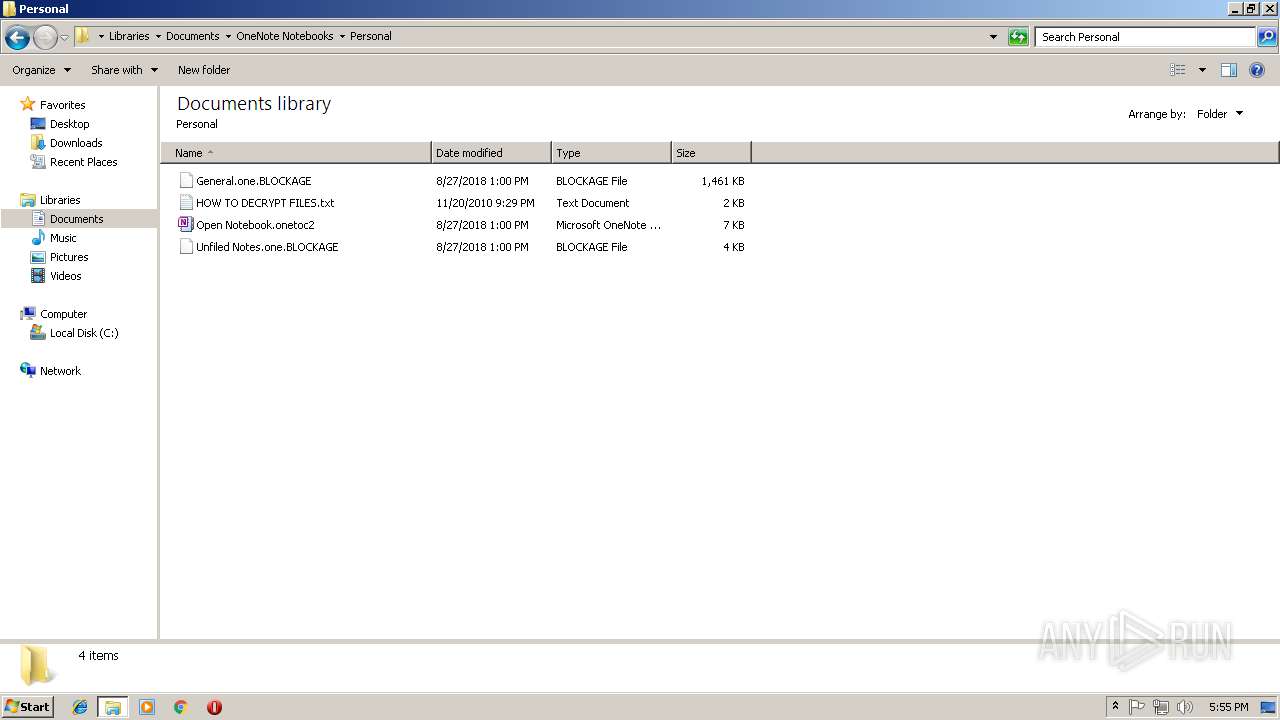
Renames files like Ransomware
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
Modifies files in Chrome extension folder
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1508)
- msiexec.exe (PID: 4092)
- MsiExec.exe (PID: 3920)
- MsiExec.exe (PID: 3252)
Reads Internet Cache Settings
- SearchProtocolHost.exe (PID: 1072)
Creates files in the program directory
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
- SearchIndexer.exe (PID: 3988)
- SearchIndexer.exe (PID: 3972)
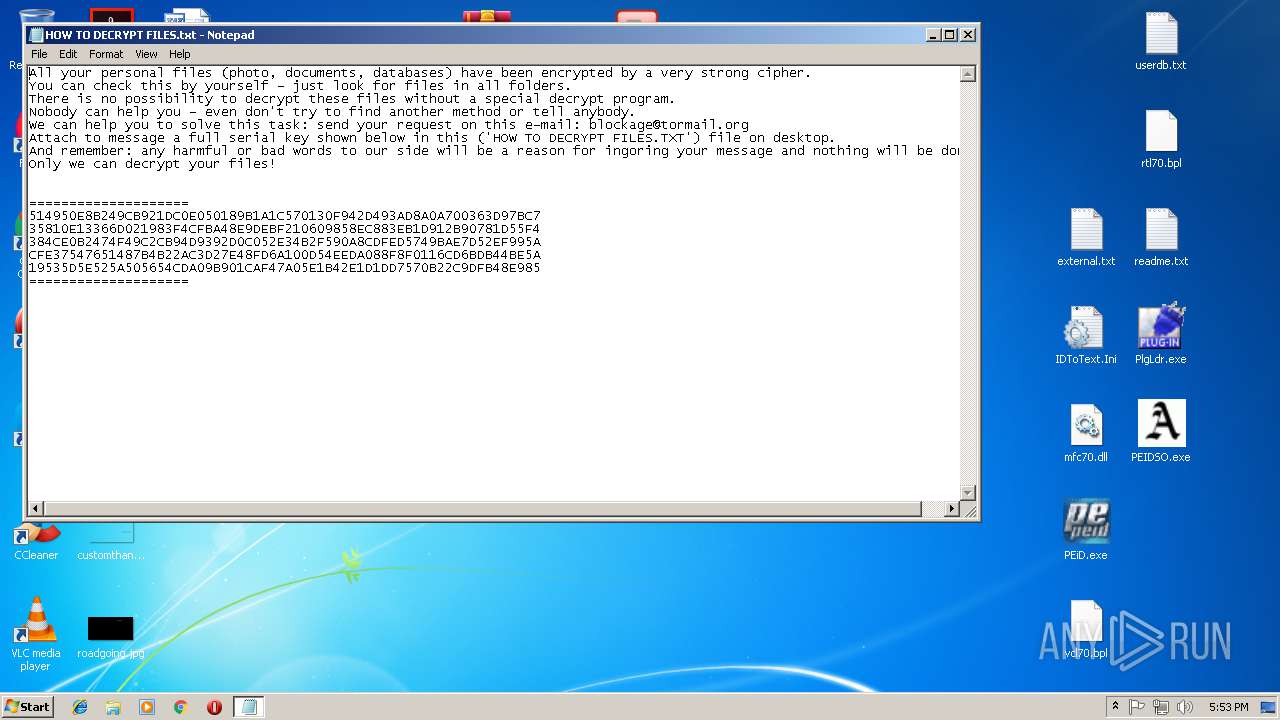
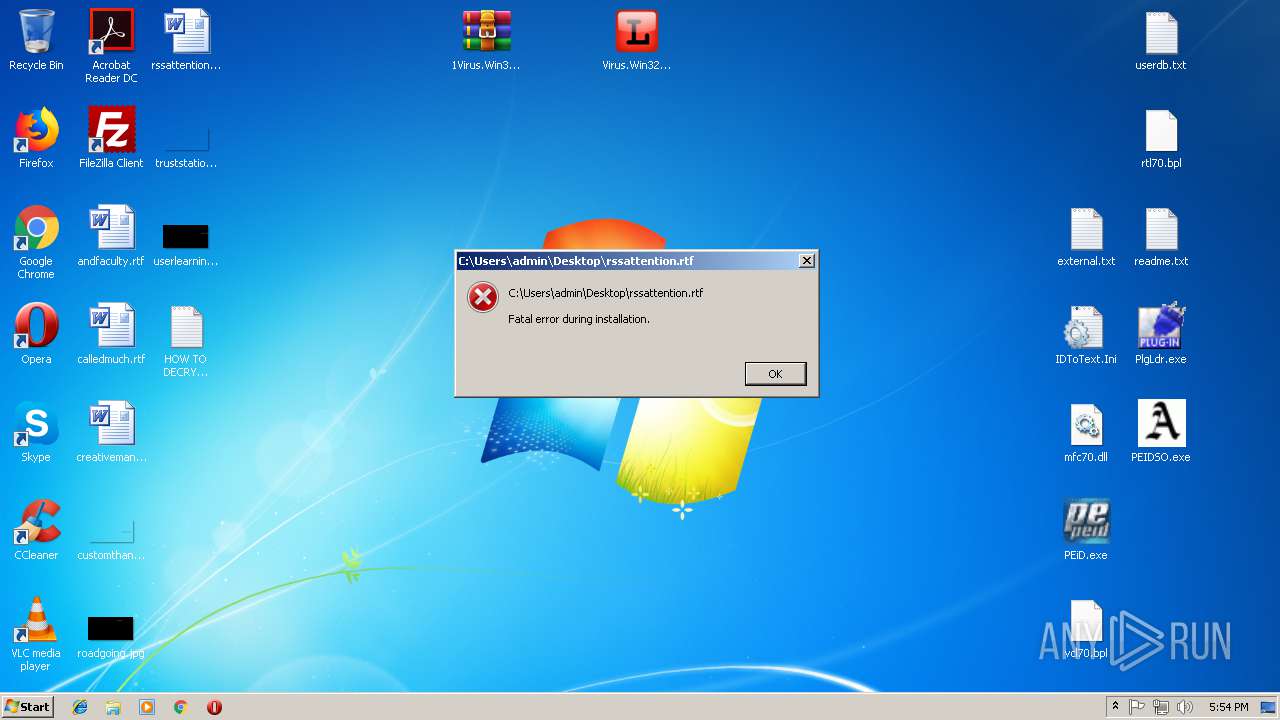
Creates files like Ransomware instruction
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
Creates files in the user directory
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
INFO
Dropped object may contain Bitcoin addresses
- Virus.Win32.Trojan.Ransom.Gpcode.dm.exe (PID: 3272)
Reads Microsoft Office registry keys
- MsiExec.exe (PID: 3920)
- SearchProtocolHost.exe (PID: 1072)
- MsiExec.exe (PID: 3252)
Application launched itself
- msiexec.exe (PID: 4092)
Creates files in the program directory
- MsiExec.exe (PID: 1320)
- MsiExec.exe (PID: 3732)
- msiexec.exe (PID: 4092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 393 |
|---|---|
| UncompressedSize: | 651 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2005:01:30 15:26:17 |
| PackingMethod: | Best Compression |
| ArchivedFileName: | external.txt |
Total processes
63
Monitored processes
19
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-10002 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\HOW TO DECRYPT FILES.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
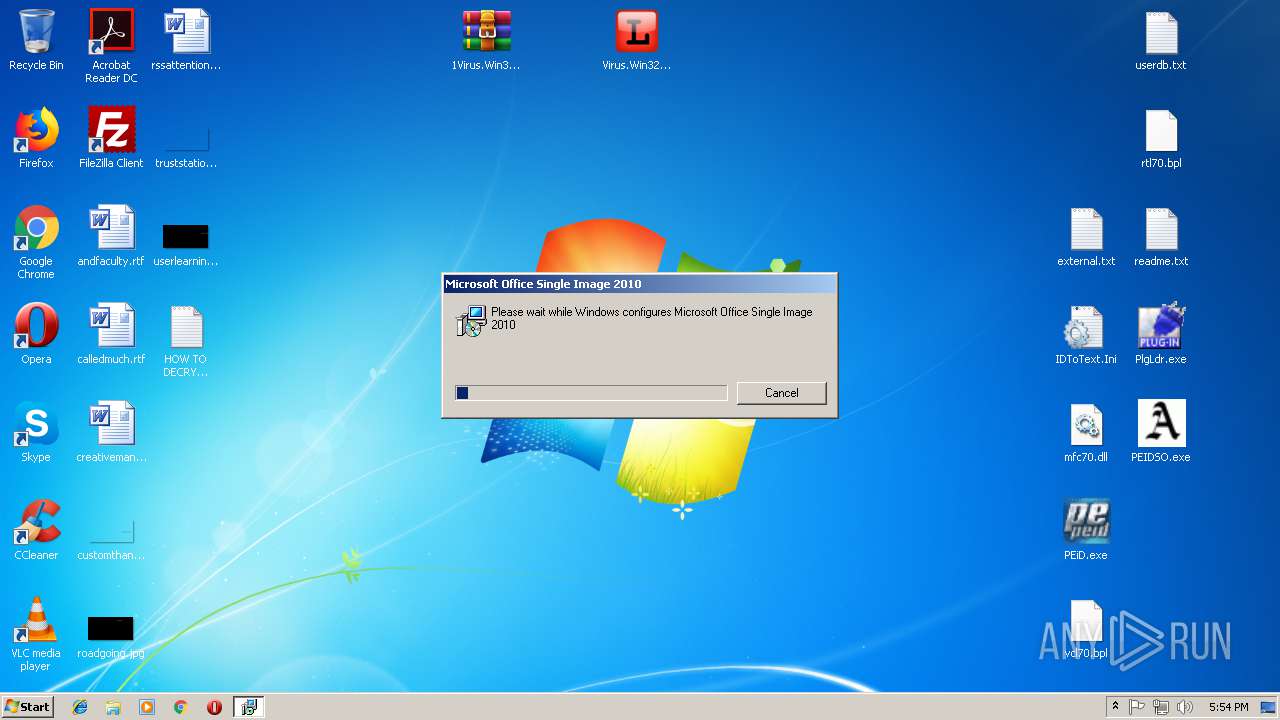
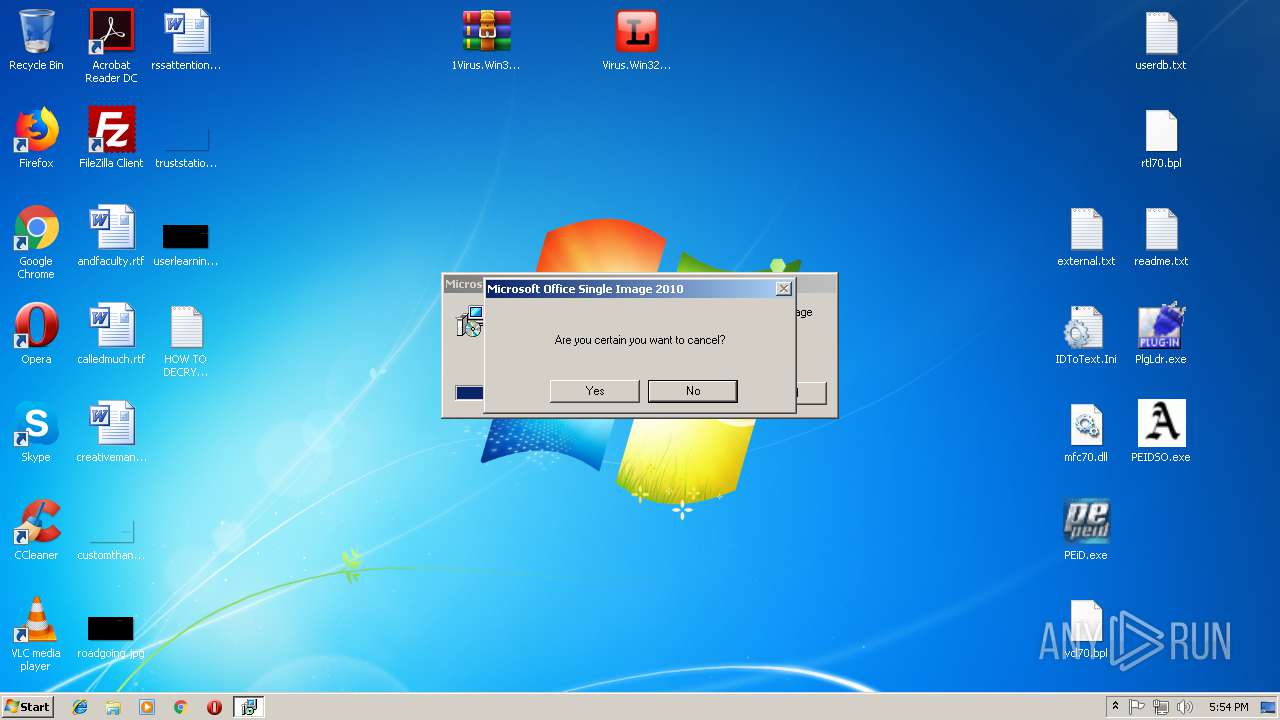
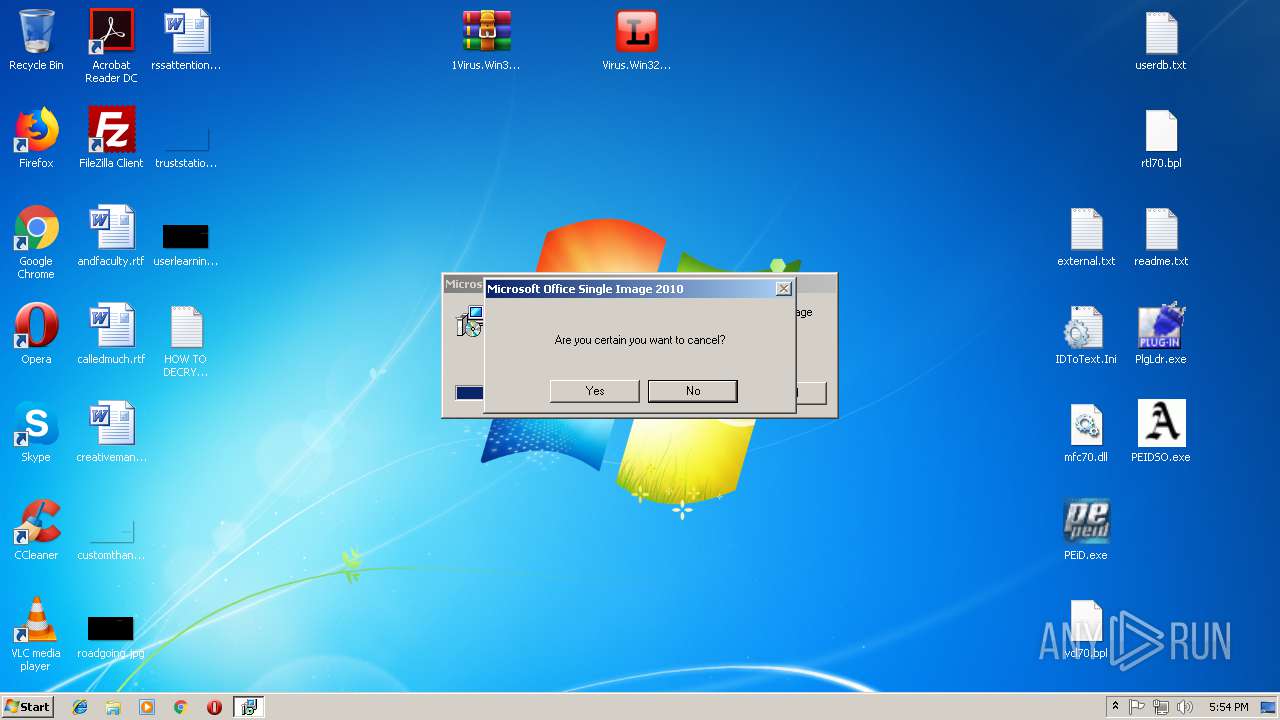
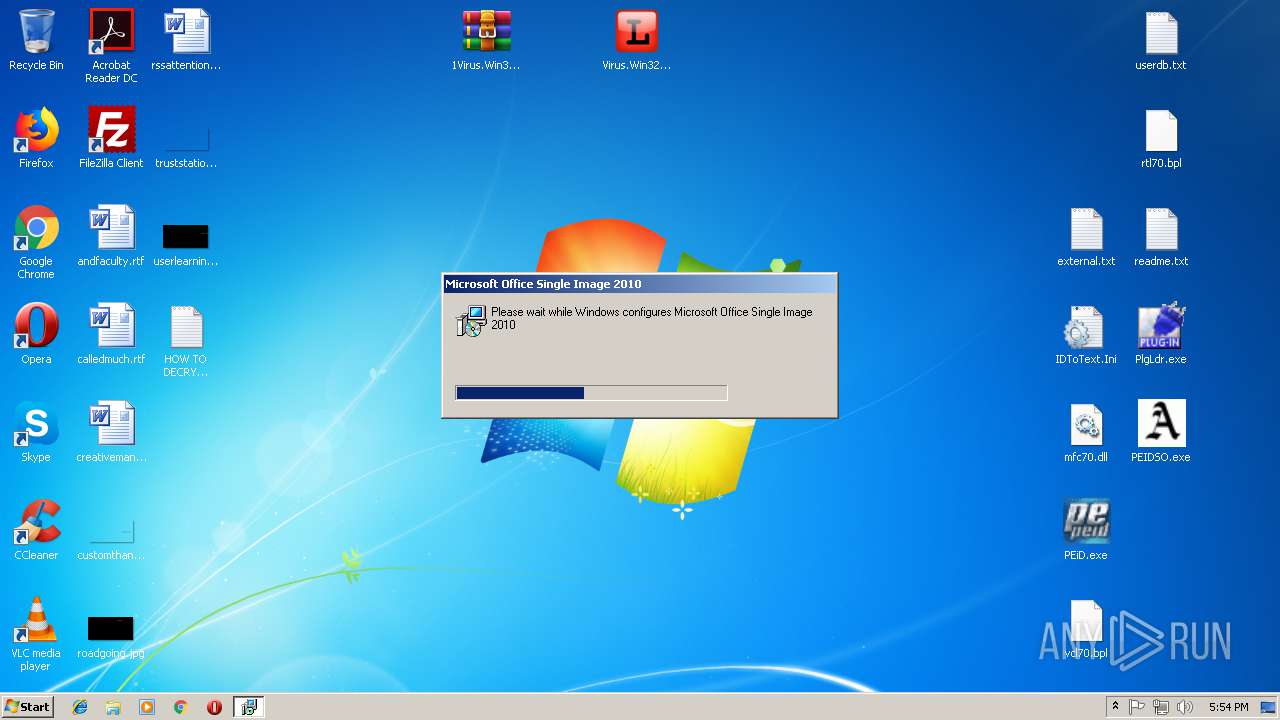
| 1088 | "C:\Users\admin\Desktop\PEiD.exe" | C:\Users\admin\Desktop\PEiD.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1320 | C:\Windows\system32\MsiExec.exe -Embedding 5E6343712976271BE1E9B832C0DE4696 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1508 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PEiD.v0.95[www.cracklab.ru].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1992 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe1_ Global\UsGthrCtrlFltPipeMssGthrPipe1 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2480 | C:\Windows\system32\MsiExec.exe -Embedding 267037F1A0855C85A512D0F8A5F1153A | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Windows\system32\SearchFilterHost.exe" 0 516 520 528 65536 524 | C:\Windows\system32\SearchFilterHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Filter Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 312
Read events
5 657
Write events
2 382
Delete events
273
Modification events
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PEiD.v0.95[www.cracklab.ru].rar | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1508) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
12
Suspicious files
3 802
Text files
2 990
Unknown types
58
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1508.12921\1Virus.Win32.Trojan.Ransom.Gpcode.dm.zip | — | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3296.16755\Virus.Win32.Trojan.Ransom.Gpcode.dm\Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | — | |
MD5:— | SHA256:— | |||
| 1508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1508.18390\userdb.txt | — | |
MD5:— | SHA256:— | |||
| 1508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1508.18390\vcl70.bpl | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0016-0409-0000-0000000FF1CE}-C\ExcelMUI.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0016-0409-0000-0000000FF1CE}-C\Setup.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0018-0409-0000-0000000FF1CE}-C\PowerPointMUI.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0018-0409-0000-0000000FF1CE}-C\Setup.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0019-0409-0000-0000000FF1CE}-C\PublisherMUI.xml | — | |
MD5:— | SHA256:— | |||
| 3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | C:\MSOCache\All Users\{90140000-0019-0409-0000-0000000FF1CE}-C\Setup.xml | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | POST | 200 | 199.59.242.151:80 | http://stard.0fees.net/gate.php | US | html | 3.84 Kb | malicious |
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | POST | 200 | 199.59.242.151:80 | http://stard.0fees.net/gate.php | US | html | 3.84 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | 199.59.242.151:80 | stard.0fees.net | Bodis, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stard.0fees.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | A Network Trojan was detected | ET TROJAN Trojan Generic - POST To gate.php with no referer |
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | A Network Trojan was detected | ET TROJAN Trojan Generic - POST To gate.php with no accept headers |
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | A Network Trojan was detected | ET TROJAN Trojan Generic - POST To gate.php with no referer |
3272 | Virus.Win32.Trojan.Ransom.Gpcode.dm.exe | A Network Trojan was detected | ET TROJAN Trojan Generic - POST To gate.php with no accept headers |