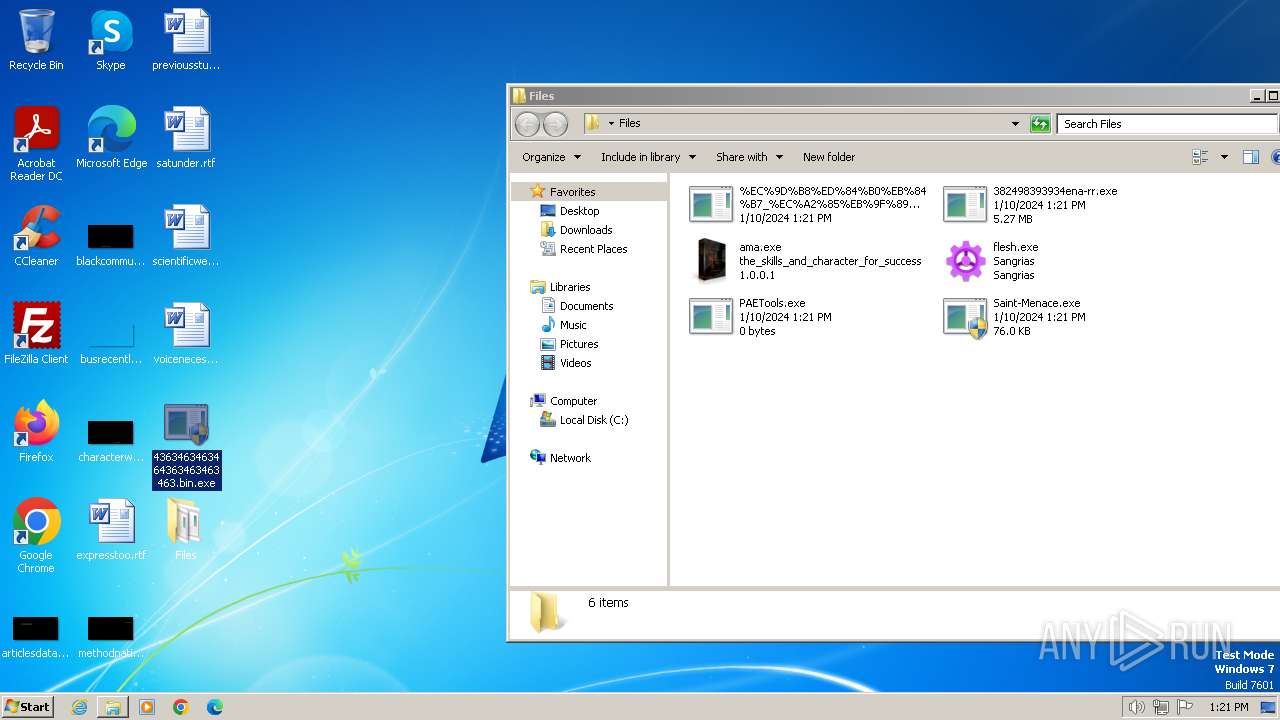
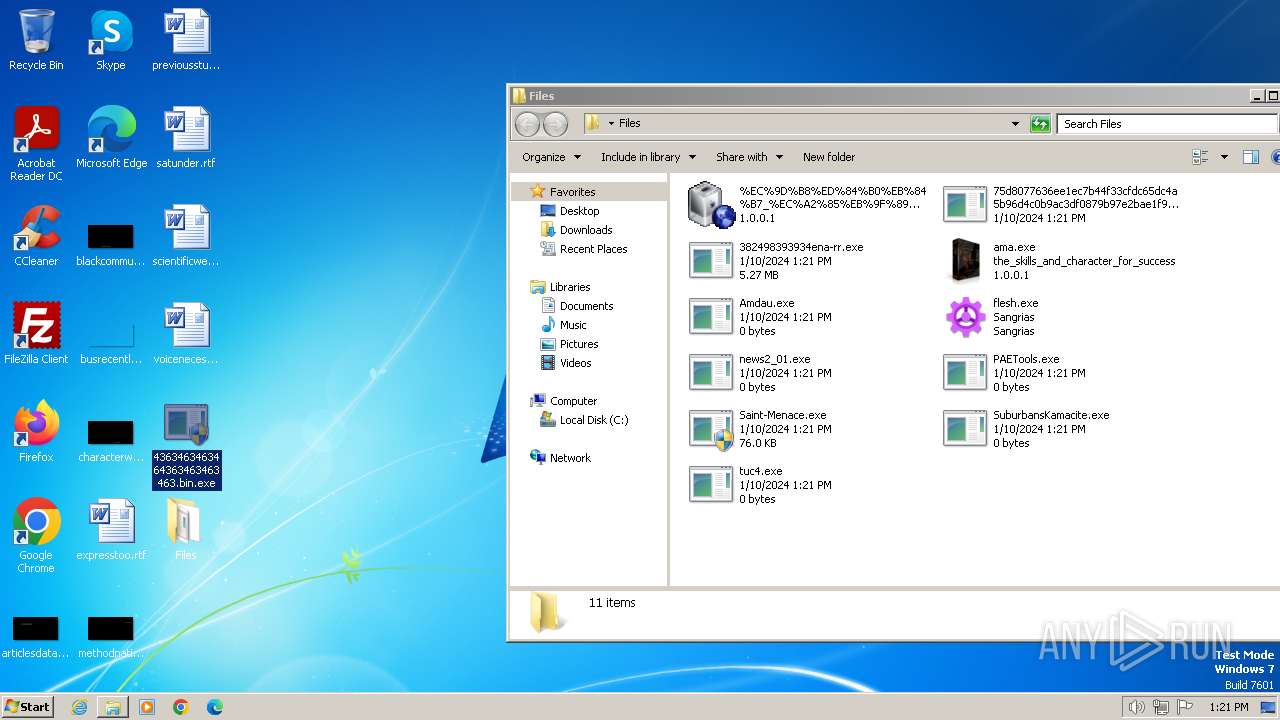
| File name: | 4363463463464363463463463.bin |
| Full analysis: | https://app.any.run/tasks/fc80e283-67a8-4c85-8382-d3687258194f |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | January 10, 2024, 13:20:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Steals credentials from Web Browsers
- flesh.exe (PID: 584)
Create files in the Startup directory
- flesh.exe (PID: 584)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.bin.exe (PID: 2064)
- 4363463463464363463463463.bin.exe (PID: 1748)
Actions looks like stealing of personal data
- flesh.exe (PID: 584)
- pinf.exe (PID: 2036)
Adds process to the Windows Defender exclusion list
- Gang.exe (PID: 2300)
Starts CMD.EXE for self-deleting
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2964)
UAC/LUA settings modification
- Gang.exe (PID: 2300)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 4648)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.bin.exe (PID: 2064)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 1592)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 2168)
- 4363463463464363463463463.bin.exe (PID: 4284)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5668)
- 4363463463464363463463463.bin.exe (PID: 5780)
- 4363463463464363463463463.bin.exe (PID: 6060)
- 4363463463464363463463463.bin.exe (PID: 5900)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 5264)
Adds/modifies Windows certificates
- 4363463463464363463463463.bin.exe (PID: 2064)
- 4363463463464363463463463.bin.exe (PID: 1748)
Reads the Internet Settings
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 1592)
- 4363463463464363463463463.bin.exe (PID: 2560)
- timeSync.exe (PID: 1740)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 2812)
- Gang.exe (PID: 2300)
- 4363463463464363463463463.bin.exe (PID: 3144)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2964)
- 4363463463464363463463463.bin.exe (PID: 2168)
- powershell.exe (PID: 1832)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4284)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5212)
- fortnite3.exe (PID: 5396)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5780)
- 4363463463464363463463463.bin.exe (PID: 5668)
- 4363463463464363463463463.bin.exe (PID: 5900)
- 4363463463464363463463463.bin.exe (PID: 6060)
- InstallUtil.exe (PID: 6116)
- ghjkl.exe (PID: 5996)
- 4363463463464363463463463.bin.exe (PID: 4116)
- peinf.exe (PID: 5876)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 5264)
- 4363463463464363463463463.bin.exe (PID: 5552)
Searches for installed software
- flesh.exe (PID: 584)
Reads browser cookies
- flesh.exe (PID: 584)
Script adds exclusion path to Windows Defender
- Gang.exe (PID: 2300)
Starts POWERSHELL.EXE for commands execution
- Gang.exe (PID: 2300)
- powershell.exe (PID: 4212)
- wlanext.exe (PID: 5492)
- BelgiumchainAGRO.exe (PID: 2932)
Script adds exclusion process to Windows Defender
- Gang.exe (PID: 2300)
Starts CMD.EXE for commands execution
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2964)
- wscript.exe (PID: 6440)
- Wattyl.exe (PID: 7524)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4336)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1832)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 4984)
Base64-obfuscated command line is found
- powershell.exe (PID: 4212)
Executing commands from a ".bat" file
- wscript.exe (PID: 6440)
The process executes VB scripts
- new.exe (PID: 6364)
INFO
Checks supported languages
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- qemu-ga.exe (PID: 1804)
- ama.exe (PID: 1824)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3068)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 3028)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 75d8077636ee1ec7b44f33cfdc65dc4a5b96d4c0b9ac3df0879b97e2bae1f9dd.exe (PID: 3356)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 4020)
- pinf.exe (PID: 2036)
- SuburbansKamacite.exe (PID: 3860)
- 4363463463464363463463463.bin.exe (PID: 3904)
- ww.exe (PID: 1308)
- 4363463463464363463463463.bin.exe (PID: 1592)
- 32.exe (PID: 2204)
- Gang.exe (PID: 2300)
- timeSync.exe (PID: 1740)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- PAETools.exe (PID: 2344)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- jet.exe (PID: 1656)
- 4363463463464363463463463.bin.exe (PID: 2244)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2964)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 2168)
- easy.exe (PID: 4292)
- 4363463463464363463463463.bin.exe (PID: 4284)
- toolspub2.exe (PID: 4600)
- 4363463463464363463463463.bin.exe (PID: 4564)
- news2_01.exe (PID: 4764)
- 4363463463464363463463463.bin.exe (PID: 4872)
- toolspub2.exe (PID: 4860)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5100)
- fortnite3.exe (PID: 5396)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5668)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5780)
- peinf.exe (PID: 5876)
- 4363463463464363463463463.bin.exe (PID: 5900)
- ghjkl.exe (PID: 5996)
- 4363463463464363463463463.bin.exe (PID: 6060)
- InstallUtil.exe (PID: 6116)
- 987123.exe (PID: 4260)
- BLduscfibj.exe (PID: 4276)
- ghjkl.exe (PID: 560)
- BLduscfibj.exe (PID: 4492)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 5264)
- wlanext.exe (PID: 5492)
- 4363463463464363463463463.bin.exe (PID: 5552)
Reads the computer name
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- qemu-ga.exe (PID: 1804)
- ama.exe (PID: 1824)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 1592)
- SuburbansKamacite.exe (PID: 3860)
- Gang.exe (PID: 2300)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- timeSync.exe (PID: 1740)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 4284)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2964)
- 4363463463464363463463463.bin.exe (PID: 2168)
- easy.exe (PID: 4292)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5668)
- fortnite3.exe (PID: 5396)
- 4363463463464363463463463.bin.exe (PID: 5780)
- ghjkl.exe (PID: 5996)
- 4363463463464363463463463.bin.exe (PID: 6060)
- 4363463463464363463463463.bin.exe (PID: 5900)
- BLduscfibj.exe (PID: 4276)
- InstallUtil.exe (PID: 6116)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 4692)
- BLduscfibj.exe (PID: 4492)
- peinf.exe (PID: 5876)
- 4363463463464363463463463.bin.exe (PID: 3120)
- wlanext.exe (PID: 5492)
- 4363463463464363463463463.bin.exe (PID: 5552)
- 4363463463464363463463463.bin.exe (PID: 5264)
Reads product name
- flesh.exe (PID: 584)
Reads Environment values
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 1592)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 2168)
- 4363463463464363463463463.bin.exe (PID: 4284)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5780)
- 4363463463464363463463463.bin.exe (PID: 5900)
- 4363463463464363463463463.bin.exe (PID: 5668)
- 4363463463464363463463463.bin.exe (PID: 6060)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 5552)
- 4363463463464363463463463.bin.exe (PID: 5264)
Reads the machine GUID from the registry
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 1592)
- SuburbansKamacite.exe (PID: 3860)
- timeSync.exe (PID: 1740)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 2168)
- 4363463463464363463463463.bin.exe (PID: 4284)
- easy.exe (PID: 4292)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5360)
- fortnite3.exe (PID: 5396)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5780)
- 4363463463464363463463463.bin.exe (PID: 5668)
- ama.exe (PID: 1824)
- ghjkl.exe (PID: 5996)
- 4363463463464363463463463.bin.exe (PID: 6060)
- 4363463463464363463463463.bin.exe (PID: 5900)
- InstallUtil.exe (PID: 6116)
- BLduscfibj.exe (PID: 4276)
- peinf.exe (PID: 5876)
- BLduscfibj.exe (PID: 4492)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 4692)
- Gang.exe (PID: 2300)
- 4363463463464363463463463.bin.exe (PID: 5552)
- 4363463463464363463463463.bin.exe (PID: 5264)
Drops the executable file immediately after the start
- 4363463463464363463463463.bin.exe (PID: 2064)
- flesh.exe (PID: 584)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3792)
- jet.exe (PID: 1656)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5212)
- ama.exe (PID: 1824)
- 4363463463464363463463463.bin.exe (PID: 3388)
- ghjkl.exe (PID: 5996)
- 4363463463464363463463463.bin.exe (PID: 5360)
- BLduscfibj.exe (PID: 4492)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5264)
- fund.exe (PID: 6360)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 6452)
- 4363463463464363463463463.bin.exe (PID: 5552)
- 4363463463464363463463463.bin.exe (PID: 6040)
- twztl.exe (PID: 6016)
- comSvc.exe (PID: 6168)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 7784)
- BelgiumchainAGRO.exe (PID: 2932)
- Wattyl.exe (PID: 7524)
REDLINE has been detected (SURICATA)
- flesh.exe (PID: 584)
Creates files or folders in the user directory
- flesh.exe (PID: 584)
- pinf.exe (PID: 2036)
- wlanext.exe (PID: 5492)
Connects to the server without a host name
- 4363463463464363463463463.bin.exe (PID: 2064)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3200)
Connects to unusual port
- flesh.exe (PID: 584)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 4020)
- easy.exe (PID: 4292)
Process requests binary or script from the Internet
- 4363463463464363463463463.bin.exe (PID: 2064)
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 3068)
Manual execution by a user
- 4363463463464363463463463.bin.exe (PID: 1748)
- 4363463463464363463463463.bin.exe (PID: 1740)
- 4363463463464363463463463.bin.exe (PID: 2660)
- 4363463463464363463463463.bin.exe (PID: 2804)
- 4363463463464363463463463.bin.exe (PID: 2892)
- 4363463463464363463463463.bin.exe (PID: 664)
- 4363463463464363463463463.bin.exe (PID: 2532)
- 4363463463464363463463463.bin.exe (PID: 2844)
- 4363463463464363463463463.bin.exe (PID: 3068)
- 4363463463464363463463463.bin.exe (PID: 1196)
- 4363463463464363463463463.bin.exe (PID: 3136)
- 4363463463464363463463463.bin.exe (PID: 2956)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 1408)
- 4363463463464363463463463.bin.exe (PID: 3148)
- 4363463463464363463463463.bin.exe (PID: 3200)
- 4363463463464363463463463.bin.exe (PID: 3388)
- 4363463463464363463463463.bin.exe (PID: 2772)
- 4363463463464363463463463.bin.exe (PID: 3676)
- 4363463463464363463463463.bin.exe (PID: 3792)
- 4363463463464363463463463.bin.exe (PID: 3832)
- 4363463463464363463463463.bin.exe (PID: 3904)
- 4363463463464363463463463.bin.exe (PID: 4020)
- 4363463463464363463463463.bin.exe (PID: 2148)
- 4363463463464363463463463.bin.exe (PID: 1736)
- 4363463463464363463463463.bin.exe (PID: 956)
- 4363463463464363463463463.bin.exe (PID: 1592)
- 4363463463464363463463463.bin.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 3044)
- 4363463463464363463463463.bin.exe (PID: 2844)
- 4363463463464363463463463.bin.exe (PID: 3284)
- 4363463463464363463463463.bin.exe (PID: 604)
- 4363463463464363463463463.bin.exe (PID: 3844)
- 4363463463464363463463463.bin.exe (PID: 3736)
- 4363463463464363463463463.bin.exe (PID: 2244)
- 4363463463464363463463463.bin.exe (PID: 3024)
- 4363463463464363463463463.bin.exe (PID: 3144)
- 4363463463464363463463463.bin.exe (PID: 1772)
- 4363463463464363463463463.bin.exe (PID: 2168)
- 4363463463464363463463463.bin.exe (PID: 3652)
- 4363463463464363463463463.bin.exe (PID: 1728)
- 4363463463464363463463463.bin.exe (PID: 2812)
- 4363463463464363463463463.bin.exe (PID: 4284)
- 4363463463464363463463463.bin.exe (PID: 4232)
- 4363463463464363463463463.bin.exe (PID: 4492)
- 4363463463464363463463463.bin.exe (PID: 4664)
- 4363463463464363463463463.bin.exe (PID: 4564)
- 4363463463464363463463463.bin.exe (PID: 4872)
- 4363463463464363463463463.bin.exe (PID: 4820)
- 4363463463464363463463463.bin.exe (PID: 4956)
- 4363463463464363463463463.bin.exe (PID: 4708)
- 4363463463464363463463463.bin.exe (PID: 4992)
- 4363463463464363463463463.bin.exe (PID: 5064)
- 4363463463464363463463463.bin.exe (PID: 5100)
- 4363463463464363463463463.bin.exe (PID: 5212)
- 4363463463464363463463463.bin.exe (PID: 5176)
- 4363463463464363463463463.bin.exe (PID: 5360)
- 4363463463464363463463463.bin.exe (PID: 5324)
- 4363463463464363463463463.bin.exe (PID: 5556)
- 4363463463464363463463463.bin.exe (PID: 5520)
- 4363463463464363463463463.bin.exe (PID: 5668)
- 4363463463464363463463463.bin.exe (PID: 5632)
- 4363463463464363463463463.bin.exe (PID: 5744)
- 4363463463464363463463463.bin.exe (PID: 5856)
- 4363463463464363463463463.bin.exe (PID: 5900)
- 4363463463464363463463463.bin.exe (PID: 5780)
- 4363463463464363463463463.bin.exe (PID: 6024)
- 4363463463464363463463463.bin.exe (PID: 6060)
- 4363463463464363463463463.bin.exe (PID: 4328)
- 4363463463464363463463463.bin.exe (PID: 4116)
- 4363463463464363463463463.bin.exe (PID: 4380)
- 4363463463464363463463463.bin.exe (PID: 4692)
- 4363463463464363463463463.bin.exe (PID: 4840)
- 4363463463464363463463463.bin.exe (PID: 3120)
- 4363463463464363463463463.bin.exe (PID: 5224)
- 4363463463464363463463463.bin.exe (PID: 5264)
- 4363463463464363463463463.bin.exe (PID: 5408)
- 4363463463464363463463463.bin.exe (PID: 5552)
- 4363463463464363463463463.bin.exe (PID: 4988)
- 4363463463464363463463463.bin.exe (PID: 5792)
- 4363463463464363463463463.bin.exe (PID: 4524)
- 4363463463464363463463463.bin.exe (PID: 6044)
- 4363463463464363463463463.bin.exe (PID: 5792)
- 4363463463464363463463463.bin.exe (PID: 6040)
- 4363463463464363463463463.bin.exe (PID: 4276)
- 4363463463464363463463463.bin.exe (PID: 5864)
- 4363463463464363463463463.bin.exe (PID: 6164)
- 4363463463464363463463463.bin.exe (PID: 6452)
- 4363463463464363463463463.bin.exe (PID: 7252)
- 4363463463464363463463463.bin.exe (PID: 7424)
- 4363463463464363463463463.bin.exe (PID: 7316)
- 4363463463464363463463463.bin.exe (PID: 7460)
- 4363463463464363463463463.bin.exe (PID: 7128)
- 4363463463464363463463463.bin.exe (PID: 7176)
- 4363463463464363463463463.bin.exe (PID: 7784)
- 4363463463464363463463463.bin.exe (PID: 7868)
- 4363463463464363463463463.bin.exe (PID: 7528)
- 4363463463464363463463463.bin.exe (PID: 7592)
- 4363463463464363463463463.bin.exe (PID: 7720)
- 4363463463464363463463463.bin.exe (PID: 7916)
Create files in a temporary directory
- 4363463463464363463463463.bin.exe (PID: 1748)
- jet.exe (PID: 1656)
- ama.exe (PID: 1824)
- ghjkl.exe (PID: 5996)
- wlanext.exe (PID: 5492)
Checks proxy server information
- timeSync.exe (PID: 1740)
- fortnite3.exe (PID: 5396)
- InstallUtil.exe (PID: 6116)
- peinf.exe (PID: 5876)
Process checks whether UAC notifications are on
- Gang.exe (PID: 2300)
Application launched itself
- toolspub2.exe (PID: 4600)
- ghjkl.exe (PID: 5996)
- BLduscfibj.exe (PID: 4276)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 4412)
- powershell.exe (PID: 4212)
- s5.exe (PID: 3424)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 6500)
Connects to the CnC server
- timeSync.exe (PID: 1740)
STEALC has been detected (SURICATA)
- timeSync.exe (PID: 1740)
Changes the registry key values via Powershell
- powershell.exe (PID: 4212)
KELIHOS has been detected (SURICATA)
- 4363463463464363463463463.bin.exe (PID: 1408)
The process executes via Task Scheduler
- powershell.exe (PID: 6688)
Bypass execution policy to execute commands
- powershell.exe (PID: 6688)
Writes files like Keylogger logs
- 6.exe (PID: 6260)
Run PowerShell with an invisible window
- powershell.exe (PID: 6688)
Starts itself from another location
- twztl.exe (PID: 6016)
Executed via WMI
- schtasks.exe (PID: 6700)
- schtasks.exe (PID: 6908)
- schtasks.exe (PID: 6924)
- schtasks.exe (PID: 6976)
- schtasks.exe (PID: 6880)
- schtasks.exe (PID: 6696)
- schtasks.exe (PID: 7048)
- schtasks.exe (PID: 4536)
- schtasks.exe (PID: 7128)
- schtasks.exe (PID: 7016)
- schtasks.exe (PID: 7020)
- schtasks.exe (PID: 7032)
- schtasks.exe (PID: 7056)
- schtasks.exe (PID: 1192)
- schtasks.exe (PID: 6716)
- schtasks.exe (PID: 6800)
- schtasks.exe (PID: 6828)
- schtasks.exe (PID: 6852)
- schtasks.exe (PID: 6744)
- schtasks.exe (PID: 7064)
- schtasks.exe (PID: 7472)
- schtasks.exe (PID: 6756)
- schtasks.exe (PID: 7588)
- schtasks.exe (PID: 7720)
- schtasks.exe (PID: 7796)
- schtasks.exe (PID: 6780)
- schtasks.exe (PID: 6820)
- schtasks.exe (PID: 6772)
- schtasks.exe (PID: 7152)
- schtasks.exe (PID: 7256)
- schtasks.exe (PID: 7300)
- schtasks.exe (PID: 7264)
- schtasks.exe (PID: 7432)
- schtasks.exe (PID: 7444)
- schtasks.exe (PID: 7088)
- schtasks.exe (PID: 7896)
- schtasks.exe (PID: 8000)
- schtasks.exe (PID: 6476)
- schtasks.exe (PID: 6448)
- schtasks.exe (PID: 5404)
- schtasks.exe (PID: 8132)
- schtasks.exe (PID: 6896)
- schtasks.exe (PID: 1832)
- schtasks.exe (PID: 6812)
- schtasks.exe (PID: 6864)
- schtasks.exe (PID: 6732)
- schtasks.exe (PID: 7996)
- schtasks.exe (PID: 6160)
- schtasks.exe (PID: 6224)
- schtasks.exe (PID: 7672)
- schtasks.exe (PID: 8160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
417
Monitored processes
233
Malicious processes
43
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | C:\Users\admin\Desktop\Files\ghjkl.exe | C:\Users\admin\Desktop\Files\ghjkl.exe | ghjkl.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 584 | "C:\Users\admin\Desktop\Files\flesh.exe" | C:\Users\admin\Desktop\Files\flesh.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Company: Sangrias Integrity Level: HIGH Description: Sangrias Exit code: 0 Version: 39.86.93 Modules
| |||||||||||||||
| 604 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 956 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1192 | schtasks.exe /create /tn "conhost" /sc ONLOGON /tr "'C:\Program Files\MSBuild\conhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 1196 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1308 | "C:\Users\admin\Desktop\Files\ww.exe" | C:\Users\admin\Desktop\Files\ww.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
129 117
Read events
128 353
Write events
764
Delete events
0
Modification events
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (584) flesh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (584) flesh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (584) flesh.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
83
Suspicious files
34
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1748 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1748 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:BA00CDA824AED3562B003AFD345C4D28 | SHA256:2C0F8DE2E1A59F937CF65747E351AA8624B2E0D0FBBDB9B8DD544EEA373EA6D4 | |||
| 1656 | jet.exe | C:\Users\admin\AppData\Local\Temp\GS6492.tmp | executable | |
MD5:7D46EA623EBA5073B7E3A2834FE58CC9 | SHA256:4EBF13835A117A2551D80352CA532F6596E6F2729E41B3DE7015DB558429DEA5 | |||
| 1748 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\Local\Temp\Tar26FD.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3144 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\office.exe | binary | |
MD5:BAA0120690A3C960C3E4F59117CCC1B5 | SHA256:FA99D651752D3F61A4545C993322C3C396B47DE110BFDE205F91410D8015E95A | |||
| 4716 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs72DB.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2244 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\toolspub2.exe | executable | |
MD5:CE67C364513FC67E13215D7B25E0A039 | SHA256:185D500E68DB0931B23E580C949FCDE4B1CDDF87F13D5A9D95AC9D0BA7014714 | |||
| 5100 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\peinf.exe | executable | |
MD5:DFFA738E21DAF5B195CDA9A173D885FC | SHA256:FC7F4A32AD5D939024F941C04F123EDC4E4E51D4974313E001130A2E466119A2 | |||
| 1832 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rn02p4wg.4fo.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1832 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
191
DNS requests
67
Threats
340
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2064 | 4363463463464363463463463.bin.exe | GET | 200 | 77.91.68.21:80 | http://77.91.68.21/lend/flesh.exe | unknown | executable | 342 Kb | unknown |
2064 | 4363463463464363463463463.bin.exe | GET | 200 | 185.172.128.121:80 | http://185.172.128.121/ama.exe | unknown | executable | 5.94 Mb | unknown |
2064 | 4363463463464363463463463.bin.exe | GET | 200 | 88.151.192.77:80 | http://88.151.192.77/382498393934ena-rr.exe | unknown | executable | 5.28 Mb | unknown |
1748 | 4363463463464363463463463.bin.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0c6364f78002bafb | unknown | compressed | 65.2 Kb | unknown |
2064 | 4363463463464363463463463.bin.exe | GET | 200 | 121.53.202.238:80 | http://cfs7.blog.daum.net/upload_control/download.blog?fhandle=MEtnWE5AZnM3LmJsb2cuZGF1bS5uZXQ6L0lNQUdFLzAvMC5leGU=&filename=%EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe/%EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe | unknown | executable | 268 Kb | unknown |
2660 | 4363463463464363463463463.bin.exe | GET | 200 | 42.177.83.63:80 | http://download.doumaibiji.cn/doumai/news2/v1.0.7.01/news2_01.exe | unknown | executable | 1.66 Mb | unknown |
1748 | 4363463463464363463463463.bin.exe | GET | 200 | 39.106.158.243:80 | http://soft.110route.com/PAETools.exe | unknown | executable | 183 Kb | unknown |
3068 | 4363463463464363463463463.bin.exe | GET | 200 | 176.126.201.5:80 | http://artmediastudio.ro/Amdau.exe | unknown | executable | 3.20 Mb | unknown |
1408 | 4363463463464363463463463.bin.exe | GET | 200 | 85.209.11.204:80 | http://85.209.11.204/api/files/software/ww.exe | unknown | executable | 494 Kb | unknown |
2532 | 4363463463464363463463463.bin.exe | GET | 200 | 41.185.8.154:80 | http://hopvibestravel.co.za/BelgiumchainAGRO.exe | unknown | executable | 1.57 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2064 | 4363463463464363463463463.bin.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2064 | 4363463463464363463463463.bin.exe | 77.91.68.21:80 | — | Foton Telecom CJSC | RU | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2064 | 4363463463464363463463463.bin.exe | 185.172.128.121:80 | — | OOO Nadym Svyaz Service | RU | unknown |
584 | flesh.exe | 5.42.65.31:48396 | — | CJSC Kolomna-Sviaz TV | RU | malicious |
2064 | 4363463463464363463463463.bin.exe | 88.151.192.77:80 | — | Dyjix Association | DE | unknown |
2064 | 4363463463464363463463463.bin.exe | 121.53.202.238:80 | cfs7.blog.daum.net | Kakao Corp | KR | unknown |
1748 | 4363463463464363463463463.bin.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
cfs7.blog.daum.net |
| unknown |
paingta.xyz |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
soft.110route.com |
| malicious |
download.doumaibiji.cn |
| malicious |
needs.hitsturbo.com |
| malicious |
github.com |
| shared |
bitbucket.org |
| shared |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2064 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2064 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2064 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2064 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2064 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
11 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.bin.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.bin.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.bin.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.bin.exe | The request was aborted: Could not create SSL/TLS secure channel.
|