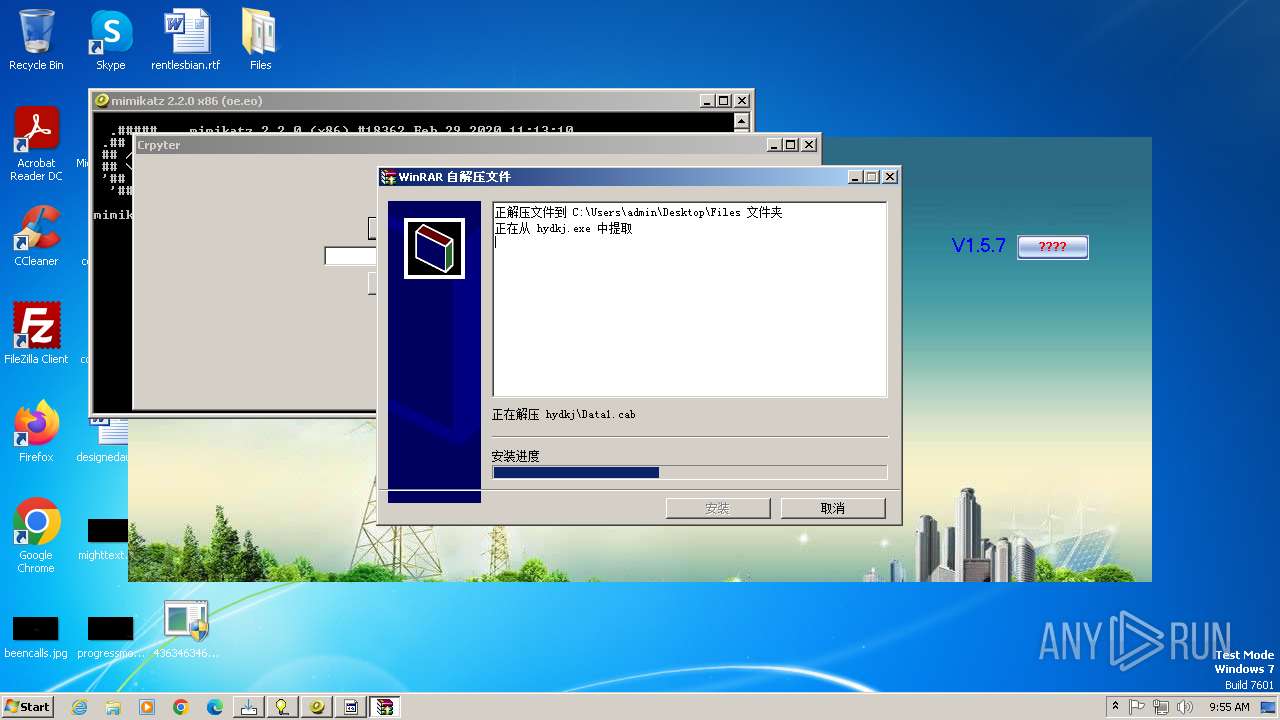
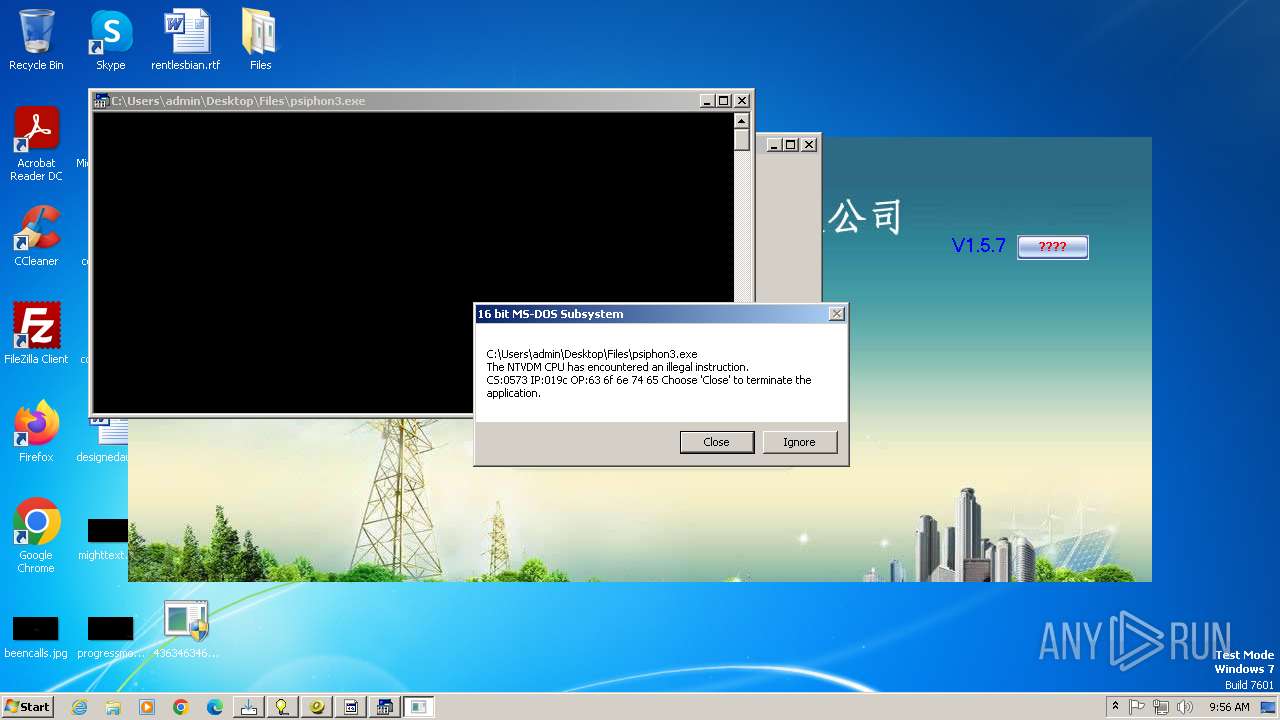
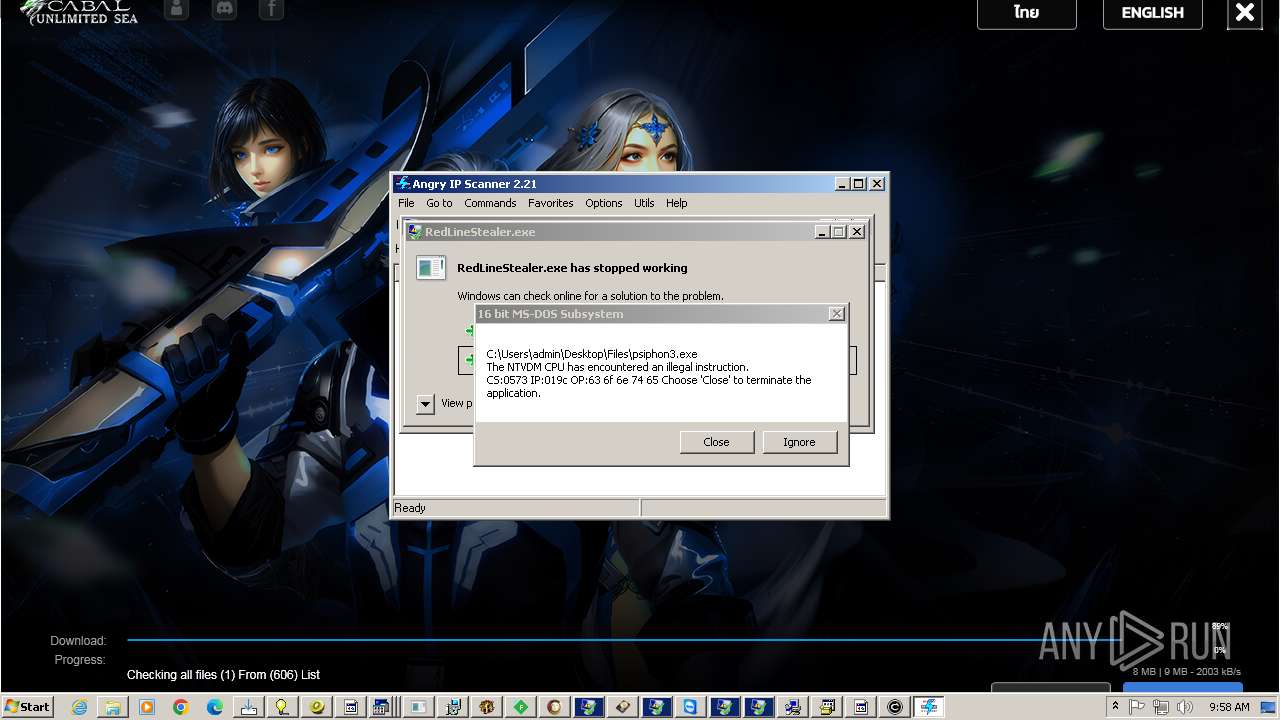
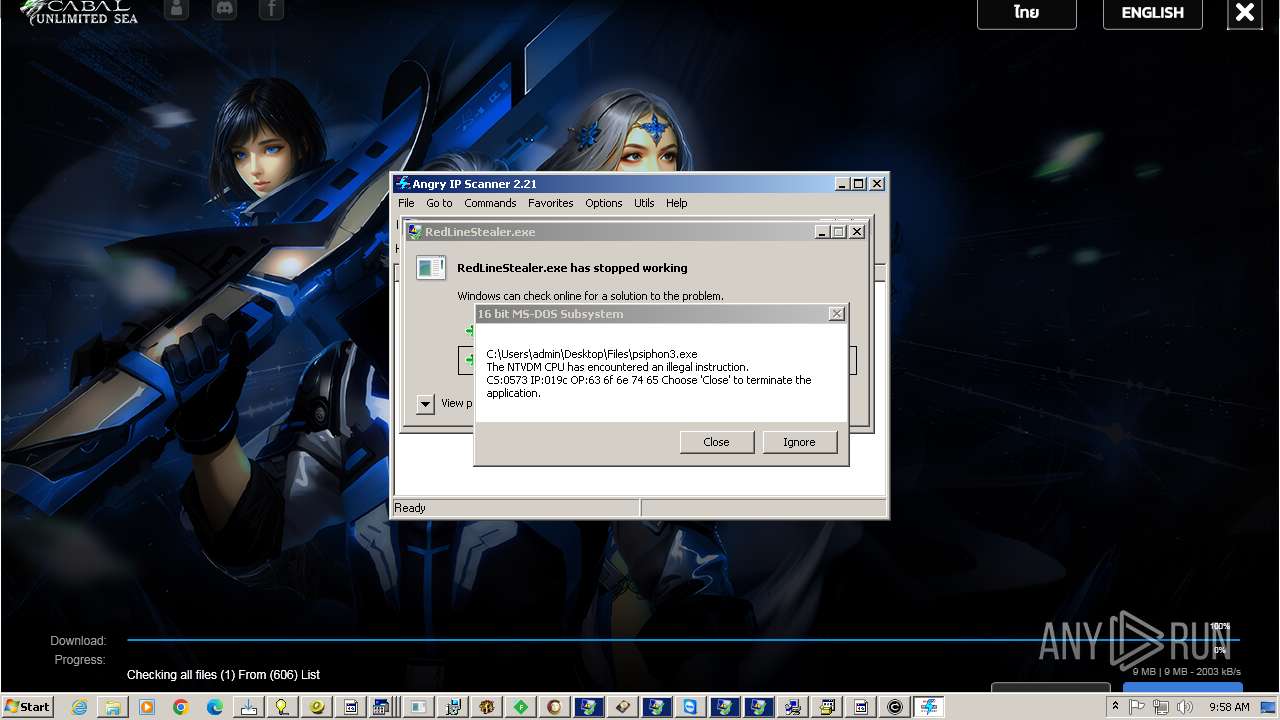
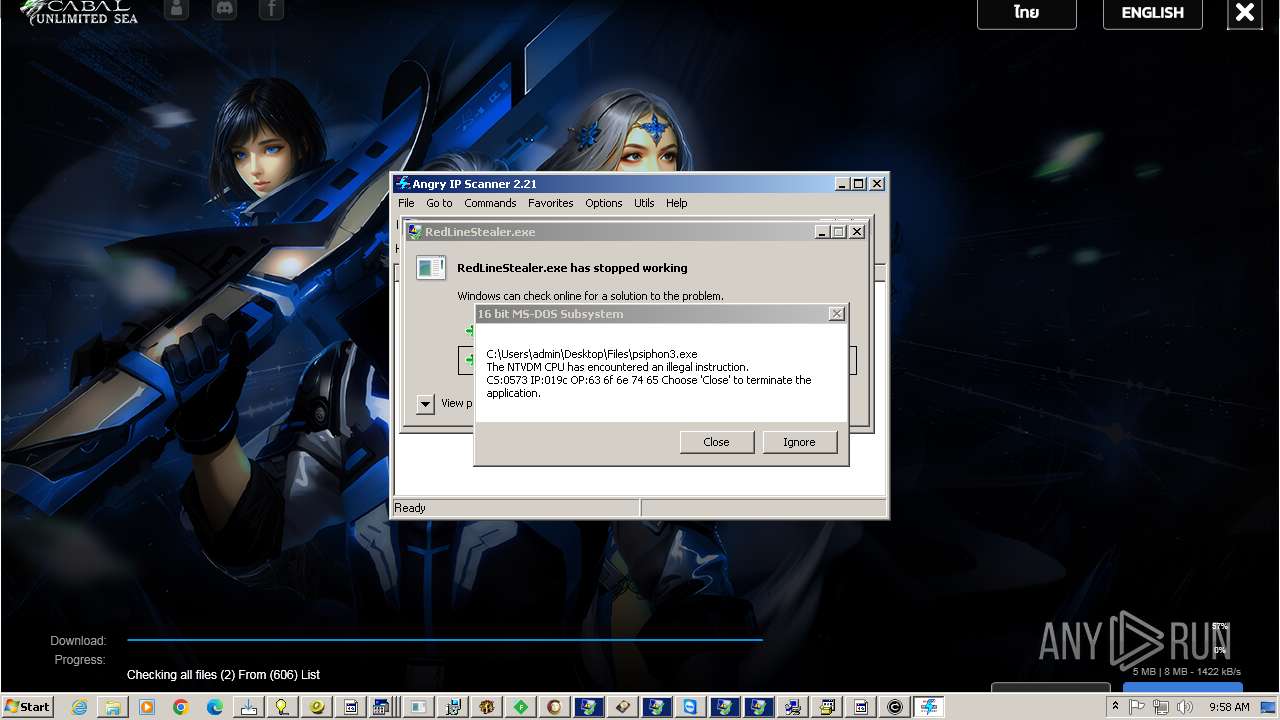
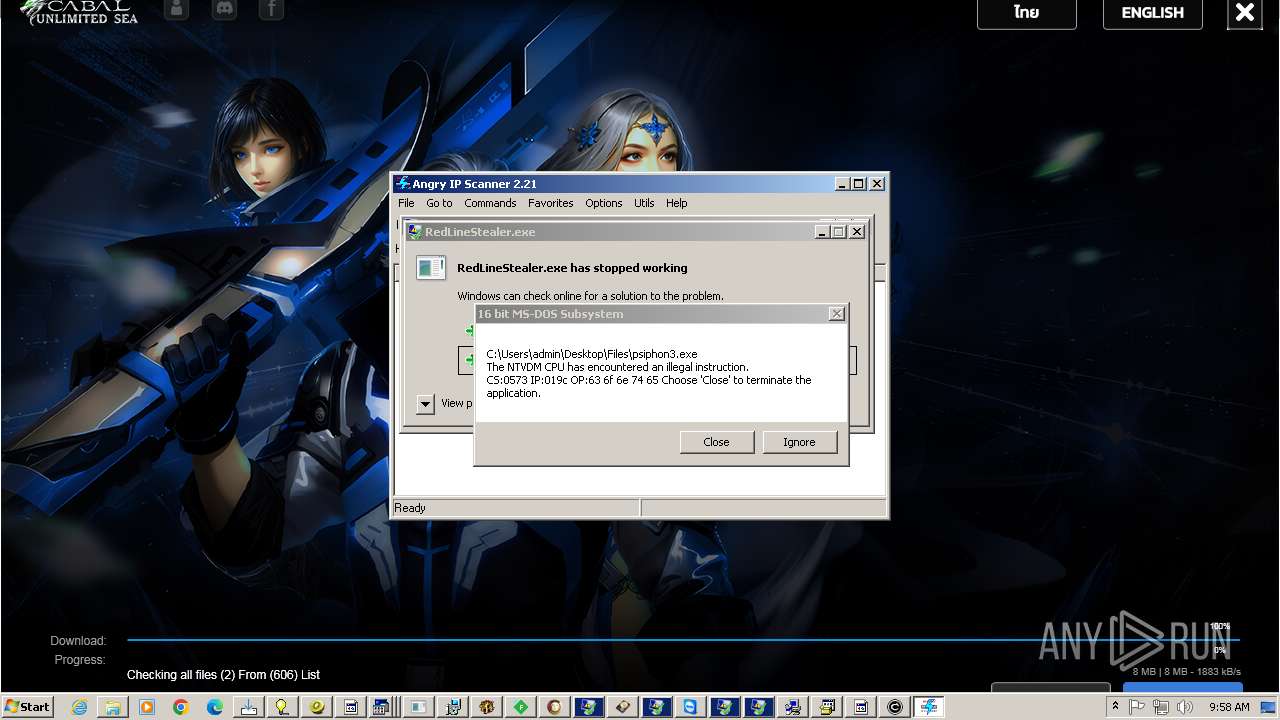
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/fac90953-da61-410d-8101-ec35330b24d7 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | May 16, 2025, 08:54:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 2336)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
- image%20logger.exe (PID: 3116)
Create files in the Startup directory
- svchost.exe (PID: 2612)
- XClient.exe (PID: 3108)
- IDriverT.exe (PID: 3400)
XWORM has been detected
- svchost.exe (PID: 2612)
BOTNET has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
Changes the autorun value in the registry
- svchost.exe (PID: 2612)
- XClient.exe (PID: 3108)
- MSystem32.exe (PID: 3712)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 3108)
Bypass execution policy to execute commands
- powershell.exe (PID: 676)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3756)
ASYNCRAT has been detected (MUTEX)
- image%20logger.exe (PID: 3116)
- syteam.exe (PID: 3352)
- Solara_Protect.exe (PID: 448)
Changes Windows Defender settings
- XClient.exe (PID: 3108)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2952)
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- windows 3543.exe (PID: 2776)
- Client.exe (PID: 2940)
- JUSCHED.EXE (PID: 1408)
- jusched.exe (PID: 2476)
- windows 3543.exe (PID: 3648)
- Client.exe (PID: 2600)
- Client-built4.exe (PID: 3664)
- defender64.exe (PID: 892)
- defenderx64.exe (PID: 3188)
- svhost.exe (PID: 2744)
- svhost.exe (PID: 2072)
- Client-built.exe (PID: 2316)
- PerfWatson1.exe (PID: 3860)
- WenzCord.exe (PID: 5060)
- WenzCord.exe (PID: 4980)
- cmd.exe (PID: 5180)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 3108)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 3108)
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
- CleanerV2.exe (PID: 3292)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2072)
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2316)
- WenzCord.exe (PID: 4980)
- RuntimeBroker.exe (PID: 5352)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2336)
VIDAR has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 3108)
- MSystem32.exe (PID: 3712)
XWORM has been detected (YARA)
- XClient.exe (PID: 3108)
QUASAR has been detected (YARA)
- windows 3543.exe (PID: 2776)
- asdasdasdasdasd.exe (PID: 2564)
- Client.exe (PID: 2940)
- windows 3543.exe (PID: 3648)
- Client.exe (PID: 2600)
- Neverlose%20Loader.exe (PID: 856)
- jusched.exe (PID: 2476)
- svhost.exe (PID: 2744)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 2336)
Connects to the CnC server
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 1080)
ASYNCRAT has been detected (YARA)
- syteam.exe (PID: 3352)
Executing a file with an untrusted certificate
- 3911_wz.exe (PID: 3692)
NJRAT has been found (auto)
- Client.exe (PID: 3700)
NANOCORE has been detected (YARA)
- MSystem32.exe (PID: 3712)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
- ApiUpdater.exe (PID: 2584)
- 4363463463464363463463463.exe (PID: 2336)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 3656)
- $77-Bitdefender.exe (PID: 3748)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 2084)
TEAMVIEWER has been detected (SURICATA)
- TeamViewer.exe (PID: 576)
- svchost.exe (PID: 1080)
NJRAT has been detected (YARA)
- testme.exe (PID: 932)
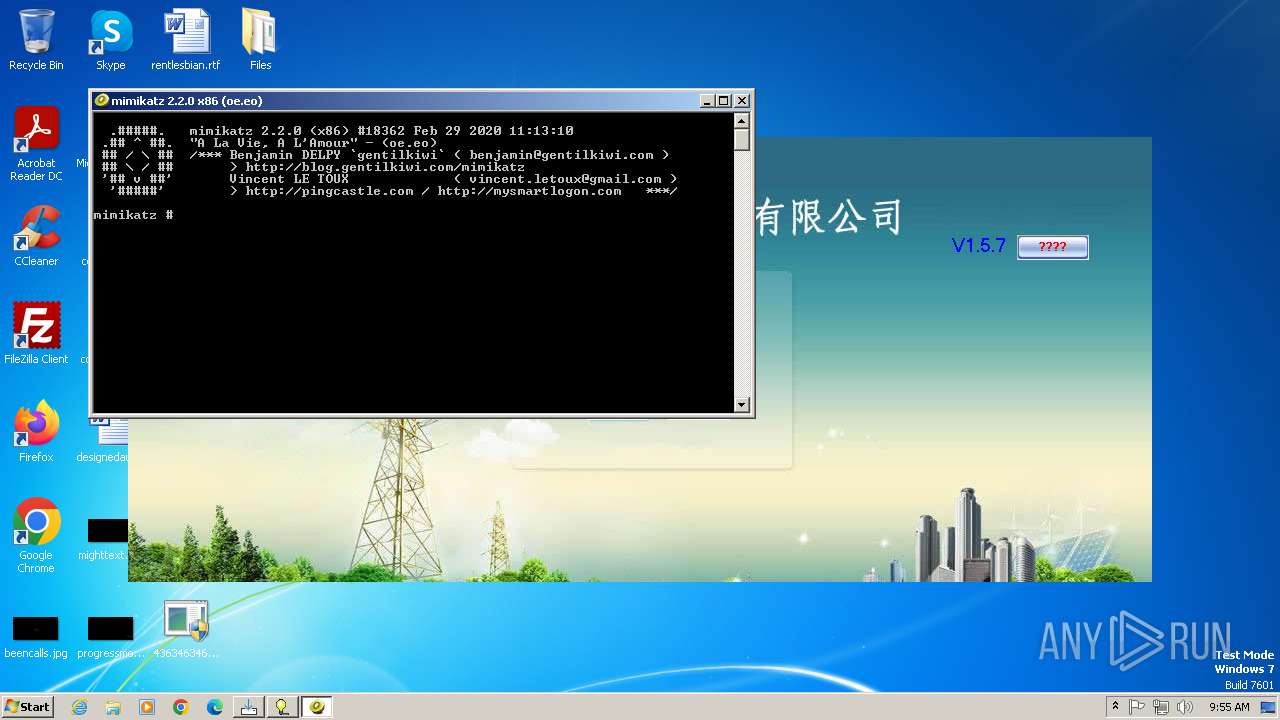
MIMIKATZ has been detected (YARA)
- Mizedo.exe (PID: 1404)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 2336)
Stealers network behavior
- svchost.exe (PID: 1080)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1080)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2336)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2336)
- XClient.exe (PID: 3108)
- svchost.exe (PID: 2612)
- image%20logger.exe (PID: 3116)
- powershell.exe (PID: 676)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3756)
- XW_XXGL.exe (PID: 1808)
- CritScript.exe (PID: 1496)
- windows 3543.exe (PID: 2776)
- hydkj.exe (PID: 3420)
- rardkj.exe (PID: 3228)
- 3911_wz.exe (PID: 3692)
- Client.exe (PID: 3700)
- defenderx64.exe (PID: 3188)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2336)
- msiexec.exe (PID: 3424)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- svhost.exe (PID: 2072)
- Client.exe (PID: 3700)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2336)
- image%20logger.exe (PID: 3116)
- XClient.exe (PID: 3108)
- XW_XXGL.exe (PID: 1808)
- CritScript.exe (PID: 1496)
- windows 3543.exe (PID: 2776)
- hydkj.exe (PID: 3420)
- rardkj.exe (PID: 3228)
- 3911_wz.exe (PID: 3692)
- Client.exe (PID: 3700)
- defenderx64.exe (PID: 3188)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2336)
- random.exe (PID: 2304)
- svchost.exe (PID: 2612)
- image%20logger.exe (PID: 3116)
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- XClient.exe (PID: 3108)
- JUSCHED.EXE (PID: 1408)
- CritScript.exe (PID: 1496)
- hydkj.exe (PID: 3420)
- Client-built4.exe (PID: 3664)
- MSystem32.exe (PID: 3712)
- FiddlerSetup.exe (PID: 3616)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2072)
- Client.exe (PID: 3700)
- ApiUpdater.exe (PID: 2584)
- Client-built.exe (PID: 2316)
- viewpoint_support.exe (PID: 2436)
- dxwsetup.exe (PID: 4712)
- dxwebsetup.exe (PID: 4672)
- cabal.exe (PID: 4812)
- WenzCord.exe (PID: 4980)
- services.exe (PID: 5556)
- Cloudy.exe (PID: 5884)
- RuntimeBroker.exe (PID: 5352)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 2096)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 896)
- UpAgent.exe (PID: 3924)
- update.exe (PID: 5376)
- explorer.exe (PID: 2052)
- ZubovLekciya.exe (PID: 3020)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2336)
- 3911_wz.exe (PID: 3692)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2336)
- VXCX.exe (PID: 5784)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 1080)
- TeamViewer.exe (PID: 576)
Connects to unusual port
- asdasdasdasdasd.exe (PID: 2564)
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- windows 3543.exe (PID: 2776)
- XW_XXGL.exe (PID: 1808)
- jusched.exe (PID: 2476)
- windows 3543.exe (PID: 3648)
- Client.exe (PID: 2600)
- MSystem32.exe (PID: 3712)
- svhost.exe (PID: 2744)
- benpolatalemdar.exe (PID: 3272)
- TeamViewer.exe (PID: 576)
- systempreter.exe (PID: 5096)
- Cloudy.exe (PID: 5884)
- services.exe (PID: 5556)
- powershell.exe (PID: 4920)
Checks for external IP
- svchost.exe (PID: 1080)
- svchost.exe (PID: 2612)
- XClient.exe (PID: 3108)
- Cloudy.exe (PID: 5884)
- svchost.exe (PID: 5316)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 3108)
- cmd.exe (PID: 1800)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 3108)
Executing commands from a ".bat" file
- image%20logger.exe (PID: 3116)
- windows 3543.exe (PID: 2776)
- defenderx64.exe (PID: 3188)
- windows 3543.exe (PID: 3648)
- PerfWatson1.exe (PID: 3860)
- WenzCord.exe (PID: 5060)
- RuntimeBroker.exe (PID: 5496)
- pornhub_downloader.exe (PID: 4032)
- pornhub_downloader.exe (PID: 2980)
- Terminal_9235.exe (PID: 4596)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2544)
- cmd.exe (PID: 5280)
Starts CMD.EXE for commands execution
- image%20logger.exe (PID: 3116)
- windows 3543.exe (PID: 2776)
- defenderx64.exe (PID: 3188)
- windows 3543.exe (PID: 3648)
- ApiUpdater.exe (PID: 2584)
- wscript.exe (PID: 3928)
- $77-Bitdefender.exe (PID: 3748)
- PerfWatson1.exe (PID: 3860)
- WenzCord.exe (PID: 5060)
- RuntimeBroker.exe (PID: 5496)
- pornhub_downloader.exe (PID: 2980)
- cmd.exe (PID: 1800)
- Terminal_9235.exe (PID: 4596)
- pornhub_downloader.exe (PID: 4032)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 3108)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3712)
- powershell.exe (PID: 676)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3756)
Probably fake Windows Update
- schtasks.exe (PID: 3196)
- windows 3543.exe (PID: 2776)
- schtasks.exe (PID: 4020)
- windows 3543.exe (PID: 3648)
- schtasks.exe (PID: 3656)
Probably fake Windows Update file has been dropped
- JJSPLOIT.V2.exe (PID: 3636)
The executable file from the user directory is run by the CMD process
- syteam.exe (PID: 3352)
- windows 3543.exe (PID: 3648)
Starts itself from another location
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- JUSCHED.EXE (PID: 1408)
- Client-built4.exe (PID: 3664)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2072)
- Client.exe (PID: 3700)
- Client-built.exe (PID: 2316)
- WenzCord.exe (PID: 4980)
- RuntimeBroker.exe (PID: 5352)
- UpAgent.exe (PID: 3924)
Creates file in the systems drive root
- ntvdm.exe (PID: 348)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 2336)
- hydkj.exe (PID: 3420)
- dxwebsetup.exe (PID: 4672)
- dxwsetup.exe (PID: 4712)
- RuntimeBroker.exe (PID: 5352)
- services.exe (PID: 5556)
- update.exe (PID: 5376)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 896)
The process executes via Task Scheduler
- XClient.exe (PID: 756)
- XClient.exe (PID: 3092)
- XClient.exe (PID: 2388)
- XClient.exe (PID: 4568)
- XClient.exe (PID: 1400)
There is functionality for taking screenshot (YARA)
- windows 3543.exe (PID: 2776)
- asdasdasdasdasd.exe (PID: 2564)
- Client.exe (PID: 2940)
- windows 3543.exe (PID: 3648)
- Neverlose%20Loader.exe (PID: 856)
- Client.exe (PID: 2600)
- svhost.exe (PID: 2744)
- jusched.exe (PID: 2476)
- IDriver.exe (PID: 904)
- TeamViewer.exe (PID: 576)
Access to an unwanted program domain was detected
- XW_XXGL.exe (PID: 1808)
Contacting a server suspected of hosting an CnC
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 1080)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3244)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 5664)
Starts application with an unusual extension
- cmd.exe (PID: 3244)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 5664)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3424)
- IDriver.exe (PID: 904)
Application launched itself
- msiexec.exe (PID: 3424)
- lkkkkk.exe (PID: 5264)
- alex1213321.exe (PID: 3548)
- cmd.exe (PID: 1800)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 3424)
Executes as Windows Service
- IDriverT.exe (PID: 3400)
Write to the desktop.ini file (may be used to cloak folders)
- IDriverT.exe (PID: 3400)
Searches for installed software
- IDriver.exe (PID: 904)
Reads Internet Explorer settings
- 3911_wz.exe (PID: 3692)
Reads Microsoft Outlook installation path
- 3911_wz.exe (PID: 3692)
Uses NETSH.EXE to add a firewall rule or allowed programs
- testme.exe (PID: 932)
- WindowsServices.exe (PID: 3904)
- mos%20ssssttttt.exe (PID: 3696)
Malware-specific behavior (creating "System.dll" in Temp)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- viewpoint_support.exe (PID: 2436)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1196)
- cmd.exe (PID: 1864)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 1800)
Found strings related to reading or modifying Windows Defender settings
- wscript.exe (PID: 3928)
The process executes VB scripts
- ApiUpdater.exe (PID: 2584)
- taskmoder.exe (PID: 2112)
Drops 7-zip archiver for unpacking
- viewpoint_support.exe (PID: 2436)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 4004)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- mos%20ssssttttt.exe (PID: 3696)
Starts a Microsoft application from unusual location
- dxwebsetup.exe (PID: 4672)
- dxwsetup.exe (PID: 4712)
- cleanup_tool.exe (PID: 4784)
- RuntimeBroker.exe (PID: 5352)
- RuntimeBroker.exe (PID: 5496)
- services.exe (PID: 5556)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1800)
Downloads file from URI via Powershell
- powershell.exe (PID: 4920)
Found IP address in command line
- powershell.exe (PID: 4920)
INFO
Disables trace logs
- 4363463463464363463463463.exe (PID: 2336)
- XClient.exe (PID: 3108)
- svchost.exe (PID: 2612)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- random.exe (PID: 2304)
- random.tmp (PID: 3168)
- asdasdasdasdasd.exe (PID: 2564)
- XClient.exe (PID: 3108)
- image%20logger.exe (PID: 3116)
- JJSPLOIT.V2.exe (PID: 3636)
- windows 3543.exe (PID: 2776)
- CleanerV2.exe (PID: 3292)
- syteam.exe (PID: 3352)
- Client.exe (PID: 2940)
- XClient.exe (PID: 756)
- Solara_Protect.exe (PID: 448)
- XW_XXGL.exe (PID: 1808)
- CritScript.exe (PID: 1496)
- JUSCHED.EXE (PID: 1408)
- Neverlose%20Loader.exe (PID: 856)
- jusched.exe (PID: 2476)
- ProctorU.1.30.win.07.exe (PID: 1760)
- Mizedo.exe (PID: 1404)
- chcp.com (PID: 2764)
- VB.NET%20CRYPTER%20V2.exe (PID: 1380)
- windows 3543.exe (PID: 3648)
- hydkj.exe (PID: 3420)
- Client-built4.exe (PID: 3664)
- rardkj.exe (PID: 3228)
- setup.exe (PID: 3636)
- Client.exe (PID: 2600)
- XClient.exe (PID: 3092)
- 5c8b08b37a426.exe (PID: 3644)
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3152)
- IDriverT.exe (PID: 3400)
- IDriver.exe (PID: 904)
- MSystem32.exe (PID: 3712)
- 3911_wz.exe (PID: 3692)
- FiddlerSetup.exe (PID: 3616)
- testme.exe (PID: 932)
- FiddlerSetup.exe (PID: 1948)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- Client.exe (PID: 3700)
- defender64.exe (PID: 892)
- defenderx64.exe (PID: 3188)
- svhost.exe (PID: 2072)
- svhost.exe (PID: 2744)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 3820)
- chcp.com (PID: 4068)
- WindowsServices.exe (PID: 3904)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- random.exe (PID: 2304)
- random.tmp (PID: 3168)
- asdasdasdasdasd.exe (PID: 2564)
- image%20logger.exe (PID: 3116)
- XClient.exe (PID: 3108)
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- windows 3543.exe (PID: 2776)
- syteam.exe (PID: 3352)
- Client.exe (PID: 2940)
- XClient.exe (PID: 756)
- XW_XXGL.exe (PID: 1808)
- Solara_Protect.exe (PID: 448)
- CritScript.exe (PID: 1496)
- Neverlose%20Loader.exe (PID: 856)
- JUSCHED.EXE (PID: 1408)
- jusched.exe (PID: 2476)
- ProctorU.1.30.win.07.exe (PID: 1760)
- Mizedo.exe (PID: 1404)
- VB.NET%20CRYPTER%20V2.exe (PID: 1380)
- windows 3543.exe (PID: 3648)
- hydkj.exe (PID: 3420)
- Client-built4.exe (PID: 3664)
- rardkj.exe (PID: 3228)
- Client.exe (PID: 2600)
- 5c8b08b37a426.exe (PID: 3644)
- XClient.exe (PID: 3092)
- setup.exe (PID: 3636)
- msiexec.exe (PID: 3424)
- IDriverT.exe (PID: 3400)
- IDriver.exe (PID: 904)
- msiexec.exe (PID: 3152)
- 3911_wz.exe (PID: 3692)
- MSystem32.exe (PID: 3712)
- FiddlerSetup.exe (PID: 3616)
- FiddlerSetup.exe (PID: 1948)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- testme.exe (PID: 932)
- svhost.exe (PID: 2072)
- defenderx64.exe (PID: 3188)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2744)
- Client.exe (PID: 3700)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2336)
- asdasdasdasdasd.exe (PID: 2564)
- XClient.exe (PID: 3108)
- svchost.exe (PID: 2612)
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- windows 3543.exe (PID: 2776)
- Client.exe (PID: 2940)
- Neverlose%20Loader.exe (PID: 856)
- JUSCHED.EXE (PID: 1408)
- jusched.exe (PID: 2476)
- windows 3543.exe (PID: 3648)
- Client-built4.exe (PID: 3664)
- Client.exe (PID: 2600)
- MSystem32.exe (PID: 3712)
- testme.exe (PID: 932)
- svhost.exe (PID: 2072)
- defenderx64.exe (PID: 3188)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2744)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2336)
- msiexec.exe (PID: 3424)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 2612)
- XClient.exe (PID: 3108)
- image%20logger.exe (PID: 3116)
- asdasdasdasdasd.exe (PID: 2564)
- JJSPLOIT.V2.exe (PID: 3636)
- windows 3543.exe (PID: 2776)
- CleanerV2.exe (PID: 3292)
- Client.exe (PID: 2940)
- syteam.exe (PID: 3352)
- XW_XXGL.exe (PID: 1808)
- XClient.exe (PID: 756)
- Neverlose%20Loader.exe (PID: 856)
- JUSCHED.EXE (PID: 1408)
- jusched.exe (PID: 2476)
- Solara_Protect.exe (PID: 448)
- ProctorU.1.30.win.07.exe (PID: 1760)
- VB.NET%20CRYPTER%20V2.exe (PID: 1380)
- windows 3543.exe (PID: 3648)
- Client-built4.exe (PID: 3664)
- rardkj.exe (PID: 3228)
- Client.exe (PID: 2600)
- XClient.exe (PID: 3092)
- msiexec.exe (PID: 3424)
- setup.exe (PID: 3636)
- msiexec.exe (PID: 3152)
- IDriverT.exe (PID: 3400)
- IDriver.exe (PID: 904)
- MSystem32.exe (PID: 3712)
- 3911_wz.exe (PID: 3692)
- testme.exe (PID: 932)
- defender64.exe (PID: 892)
- defenderx64.exe (PID: 3188)
- svhost.exe (PID: 2744)
- svhost.exe (PID: 2072)
- Client.exe (PID: 3700)
Create files in a temporary directory
- random.exe (PID: 2304)
- image%20logger.exe (PID: 3116)
- CritScript.exe (PID: 1496)
- windows 3543.exe (PID: 2776)
- rardkj.exe (PID: 3228)
- setup.exe (PID: 3636)
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3152)
- FiddlerSetup.exe (PID: 3616)
- MSystem32.exe (PID: 3712)
- testme.exe (PID: 932)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 2712)
- FiddlerSetup.exe (PID: 1948)
- defenderx64.exe (PID: 3188)
- Client.exe (PID: 3700)
Creates files or folders in the user directory
- svchost.exe (PID: 2612)
- JJSPLOIT.V2.exe (PID: 3636)
- CleanerV2.exe (PID: 3292)
- XClient.exe (PID: 3108)
- JUSCHED.EXE (PID: 1408)
- MSystem32.exe (PID: 3712)
- 3911_wz.exe (PID: 3692)
- testme.exe (PID: 932)
- defender64.exe (PID: 892)
- svhost.exe (PID: 2072)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 676)
- powershell.exe (PID: 3712)
- powershell.exe (PID: 3260)
- powershell.exe (PID: 3756)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 2336)
- hydkj.exe (PID: 3420)
- msiexec.exe (PID: 4036)
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3152)
- FiddlerSetup.exe (PID: 3616)
- viewpoint_support.exe (PID: 2436)
- dxwebsetup.exe (PID: 4672)
- dxwsetup.exe (PID: 4712)
- RuntimeBroker.exe (PID: 5352)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 896)
- UpAgent.exe (PID: 3924)
- update.exe (PID: 5376)
- msiexec.exe (PID: 3008)
Detects InnoSetup installer (YARA)
- random.exe (PID: 2304)
- random.tmp (PID: 3168)
Compiled with Borland Delphi (YARA)
- random.exe (PID: 2304)
- random.tmp (PID: 3168)
- windows 3543.exe (PID: 3648)
- Neverlose%20Loader.exe (PID: 856)
- Client.exe (PID: 2600)
- MSystem32.exe (PID: 3712)
- msiexec.exe (PID: 4036)
- svhost.exe (PID: 2744)
- testme.exe (PID: 932)
- VB.NET%20CRYPTER%20V2.exe (PID: 1380)
- IDriver.exe (PID: 904)
- ntvdm.exe (PID: 3372)
- TeamViewer.exe (PID: 576)
- ntvdm.exe (PID: 3236)
- Mizedo.exe (PID: 1404)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 1196)
- jusched.exe (PID: 2476)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 3820)
Checks proxy server information
- XW_XXGL.exe (PID: 1808)
- 3911_wz.exe (PID: 3692)
Changes the display of characters in the console
- cmd.exe (PID: 3244)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 5664)
The sample compiled with chinese language support
- hydkj.exe (PID: 3420)
- 4363463463464363463463463.exe (PID: 2336)
- msiexec.exe (PID: 3152)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 2096)
Creates files in the program directory
- Client-built4.exe (PID: 3664)
- MSystem32.exe (PID: 3712)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3424)
- msiexec.exe (PID: 3152)
- msiexec.exe (PID: 4036)
- msiexec.exe (PID: 3008)
Process checks whether UAC notifications are on
- MSystem32.exe (PID: 3712)
The sample compiled with korean language support
- 4363463463464363463463463.exe (PID: 2336)
Connects to unusual port
- iexplore.exe (PID: 2084)
Application launched itself
- msedge.exe (PID: 3428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(3108) XClient.exe
C2127.0.0.1:1504
Keys
AES123456789
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
Mutexp6Jc9GPiVmwSu2YD
Quasar
(PID) Process(2776) windows 3543.exe
Version1.4.1
C2 (6)192.168.50.1:4782
10.0.0.113:4782
LETSQOOO-62766.portmap.host:62766
89.10.178.51:4782
LETSQOOO-62766.portmap.host:62766
Sub_Dirwindows updater
Install_Namewindows 3543.exe
Mutex90faf922-159d-4166-b661-4ba16af8650e
Startupwindows background updater
TagROBLOX EXECUTOR
LogDirroblox executor
SignatureDowhTcCNRmPne/jP3WQ8VLNtjW2b7COPJ9f99kZ79UFTzRFEvY6/5+otwvW1Bwmg9g0QfHHt35ZhSkuKX/JTqAAzWBJF4jgN5VBXj8eypchVIP3+JtYmO932+ak0qLmQH0HXpIdH0VUJZJaxFcaI3G20cO9f5EBgxHsey09u6g7O39z3AMmFvru9wuI2/bQkFreKMve5G63LPGchmgImAWCO+i3qtDNkH/D47EjSUKhBQjEwRNXoIahVTqBJr+eIfI/o/mQV8pWk2FKc5M20xfErtWCuSzMJ0rIULHdKHXDZ...
CertificateMIIE9DCCAtygAwIBAgIQAKXago0cfl52srIGgNzsZzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDgyNTE2NDk0M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhErQjQ8fpDYpYN1iZUcL3evTfxYkIWCVDolaEBfQA2elEwvnikLo+0s8mPHF86S0Qr9u+daX...
(PID) Process(2564) asdasdasdasdasd.exe
Version1.4.1
C2 (2)go-dramatically.gl.at.ply.gg:2676
Sub_DirSubDir
Install_NameClient.exe
Mutexfb394b82-3336-4303-8c07-5f17c76f1d95
StartupQuasar Client Startup
TagOffice04
LogDirLogs
SignatureR5FhpSlt0QWyazUiXi7985SLTfqrsVFrbAIn7D6jQVOPmxzl10942/77cs+ZGbCCWfpqitV1LI5c5R+HnSPGVI222KxAq6QPpfL7M+9p7mZxW0CGW1FckAdMBRhF1VC/j95/uYgwOJ65MlZnJMQ2WbyowEQJdH39nR+gJeEUrz9kuesDEKDfsICI7ZBzUuS3/pVGVFOpf10UudDUeA3501/QuQZjB4PcsxBLAOGIlMioCU4H+QdtOGtjqiuqaIGeKqTIS+N3E4xUtHf8Y+jFW1PMR02Oqvq1BRCeoIwFf6uU...
CertificateMIIE9DCCAtygAwIBAgIQAMeXUwnb9yEMycM8rl/0CTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDQwNTE1MjUwNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAu+8QadKEP51WpY7grxWqbSjXMuLHHF4unqYzNQF1Fn9xrl5NKFiy0Ss5fLfyK/NH8fZtcub/...
(PID) Process(2940) Client.exe
Version1.4.1
C2 (2)192.168.4.185:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex1607a026-352e-4041-bc1f-757dd6cd2e95
StartupCleanerV2
TagCleanerV2
LogDirClean
SignatureaRogJrq9hUhroi2yRCxFCfE+mXc/GvQG7eVh7ArjCeuURH+zboKSDt31Wff+SIInkno4hIQs7tRc6uLFL+H8LqKGy5JPvKlBVH/vsLgQMz2Hri+jlAj+4J5ZX0Qs23sz7UqIoRbwMHdNzuyTEDKHt/bsObNt8K+mybe50A+4iIlVs0lofsrxI8a8dSh5IxFx4M80uR9L+SGmloN53TuHqrpUrdi65VcSjCa61BUkfKqpOiJaQqZ9zqC/rXbMAu0KTssZ9Nlucysj04DgLCV83TfJfpVpZerpVLZvUsSr/BiW...
CertificateMIIE9DCCAtygAwIBAgIQAOw5PfKqmSNRWe7n9URebzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDYzMDExMjUxNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAq68uWSLSM7tj6l08I9iy5ilFsS9PluFC5ENWxT8Kmp0gDJD1br0B0Nr+ZIofw9ykVSR9kDvk...
(PID) Process(3648) windows 3543.exe
Version1.4.1
C2 (6)192.168.50.1:4782
10.0.0.113:4782
LETSQOOO-62766.portmap.host:62766
89.10.178.51:4782
LETSQOOO-62766.portmap.host:62766
Sub_Dirwindows updater
Install_Namewindows 3543.exe
Mutex90faf922-159d-4166-b661-4ba16af8650e
Startupwindows background updater
TagROBLOX EXECUTOR
LogDirroblox executor
SignatureDowhTcCNRmPne/jP3WQ8VLNtjW2b7COPJ9f99kZ79UFTzRFEvY6/5+otwvW1Bwmg9g0QfHHt35ZhSkuKX/JTqAAzWBJF4jgN5VBXj8eypchVIP3+JtYmO932+ak0qLmQH0HXpIdH0VUJZJaxFcaI3G20cO9f5EBgxHsey09u6g7O39z3AMmFvru9wuI2/bQkFreKMve5G63LPGchmgImAWCO+i3qtDNkH/D47EjSUKhBQjEwRNXoIahVTqBJr+eIfI/o/mQV8pWk2FKc5M20xfErtWCuSzMJ0rIULHdKHXDZ...
CertificateMIIE9DCCAtygAwIBAgIQAKXago0cfl52srIGgNzsZzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDgyNTE2NDk0M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhErQjQ8fpDYpYN1iZUcL3evTfxYkIWCVDolaEBfQA2elEwvnikLo+0s8mPHF86S0Qr9u+daX...
(PID) Process(856) Neverlose%20Loader.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameNeverlose Loader.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
(PID) Process(2600) Client.exe
Version1.4.1
C2 (2)0.tcp.ap.ngrok.io:11526
Sub_Dirkazeku
Install_NameClient.exe
Mutex7fb11f4b-e530-407c-a46c-8834ab5c4f45
Startupkazeku
Tagkazeku
LogDirLogs
SignatureaMYVFTI8bGBPC7PouD2vwX/brxoHYpnB+5N+J03N7p5Xs/o16IuqXSbe/TmoNMA8820i4g/yWsrVtI5tWW8PCM62pkqq2SoxkmSYh/KzjwHMMJQpiqq8e/2jFZHKsYIQfcz1hpcFmisvPeTRsEdNI3xoPyCm0182mcvoVl7KPt2/v1jKNvTCo3hibOR2NqLcXicDFcY9EfbVQ19hHHfja0j8o2IQ//59NTxPhouZF3eO1H/PaAOIgSLUYY1Jh3NvT9AS5DKwRSJw1OhWyMjIjwZFG6Mkdd2tkECKzjR4cR7h...
CertificateMIIE9DCCAtygAwIBAgIQANc8h9qchCFSUU+cYA3KWTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDIyNTA3MzgyN1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAqiYNu1Fz6WGc2+cUwJi9+hM8emrgoGRKv0eQjwodUqSQAGkyo052y+7ws3stDxX2/J8XJW0O...
(PID) Process(2744) svhost.exe
Version1.4.0
C2 (2)151.177.61.79:4782
Sub_Dirsvhost
Install_Namesvhost.exe
Mutexa148a6d8-1253-4e62-bc5f-c0242dd62e69
Startupsvhost
Tagsvhost
LogDirLogs
SignatureFiHplcBrV3S97M+7U8Wkv2OAUt8PgnZIpuptBCDmcV3pFCoNQMGru4y6fV4vlwM/qWOV6CUP402T365DHIPm+6uj+1+vgzHGFfiR7S/L+/lpirBGRMTeHcZhxJzbykEf03VPu+8sHMP4tw2JwiJxdryS9YfIuKQufusBaH0ML1oD+gCJoYiH2J1gluHBKSiZAKHI9pdYN7CJN5LNrm41d9IDcibaRPDEiB1m+MVRrQfkHuJZQmYDBxKx3tJF1EBhs5FoUNcpEcF0CWvkWO/psUToSydby8u8lhLv2k962B8w...
CertificateMIIE9DCCAtygAwIBAgIQAMlib63Pu5Cv0/jbVZpvUzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIwMTAwNTAyMTAzM1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlo+RQClgYhgaYwiwVrdvbvyE47OD8EJLOY/MXs9Z6hD3wx89223nnET+I8zcZNGYn80cgt+q...
(PID) Process(2476) jusched.exe
Version1.4.1
C2 (2)193.161.193.99:32471
Sub_DirJava
Install_Namejusched.exe
Mutex807f3187-d087-4fff-beff-e73293a32af8
StartupJava Update Scheduler
TagDDNS
LogDirCachedLogs
SignaturesBocLBRxMUw3To7ZzewZ3YsrO0Z+fc3KsRzMzv9mfbF5sJ1MJ+tSUeK3n4v0qA9CdzuiNoXDrsMLx0lNGdFJEPGAtWXTb1QPmup0gzzxZYzgUjbW3K6OUlQnrnCRJ5B/gVJhvjpeytHJcJXoVVThOCBhfRHkUdKjWvea5McjXDhUWz1Xu7FF9MqOxPols3wY2Arj/mHwFcuAzhnR5Fg27eVVh2bANkzob/YNZrH+PoUvxMthySf1+JI28o0Nzl9a/PDUUuq4nPq78M0M4glGmHqp4kgCf57NRQhEjF8nTyIm...
CertificateMIIE9DCCAtygAwIBAgIQAKdj9OEEtK/PmVn/2IlEdTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTExMjA2MTQxN1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAt79yvi82zMkZkRdUuCBbnaQ9a7fqidLALKNd/BEjRKS1OWiYAzTf9ZzAK1K+kOAeePTlezhU...
AsyncRat
(PID) Process(3352) syteam.exe
C2 (1)18.141.204.5
Ports (1)80
Version0.5.7B
BotnetDefault
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%Temp%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAIQIWleL0frBIeSQnuAJuTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwMzIyMDMyODIxWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKX5mwRbyfv2cMBQSb31Ov/ZLK9YMWp68guIQ9AGKqyfGCo0xK9xsD4RQYo8ukDIvCwxawZHu/j4...
Server_SignatureSlw1S0CB1MQ0Vr7eeR5UA3J0XHOjJfspjFdk9C6rTOXRPzGxJH9uSNOY0Ql6J2roa9jMR/bJB/E/i8GIoDD7e//tlmVxAGgqJ8fn3DRgSNMnXjztqGPEKSPRVKbTzOIbMV0KnS5/cT9+Qf69BLeEpIEuljR+S5KIvCYMorbzyFu+5p3mwc9iZ+1WmC5qCncICclFsrnOVGu1Aqc2FuRKtRIWBfJtszgh5m5zKgCJzFL6jpOifEdmqY/uzB1/lkug0Iwc9e/YN3Q0xCmXM+mO5FeoC9MJGXNYzRFbagGG/bNA...
Keys
AESf2b2168fe19a40d2a006ef4a806ae1da93537f874c52238edc371debd2b651da
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Nanocore
(PID) Process(3712) MSystem32.exe
KeyboardLoggingTrue
BuildTime2023-08-28 20:06:58.286896
Version1.2.2.0
Mutex27f61c82-a893-4fbd-9acd-5df9ed98d52d
DefaultGroupCustomRPC
PrimaryConnectionHostsulfux.ddns.net
BackupConnectionHost90.113.178.145
ConnectionPort9033
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
NjRat
(PID) Process(932) testme.exe
C2127.0.0.1
Ports8080
BotnetHacked!
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\94fd569ecca6fc088d293c04362d882f
Splitter|'|'|
Version0.7d
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
315
Monitored processes
200
Malicious processes
43
Suspicious processes
16
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\Files\CrazyCoach.exe" | C:\Users\admin\Desktop\Files\CrazyCoach.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 184 | C:\Windows\system32\MsiExec.exe -Embedding D9D03342560EB2C07D3202207DC7DC7D C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | "C:\Users\admin\Desktop\Files\Solara_Protect.exe" | C:\Users\admin\Desktop\Files\Solara_Protect.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 576 | "schtasks" /create /tn "Java Update Scheduler" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\Java\jusched.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | jusched.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | "C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe" | C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe | viewpoint_support.exe | ||||||||||||
User: admin Company: TeamViewer Germany GmbH Integrity Level: HIGH Description: TeamViewer 11 Version: 11.3.62585.0 Modules
| |||||||||||||||
| 676 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\Files\XClient.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | XClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 756 | C:\Users\admin\AppData\Roaming\XClient.exe | C:\Users\admin\AppData\Roaming\XClient.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 848 | "schtasks" /create /tn "svhost" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\svhost\svhost.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | svhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\Desktop\Files\Neverlose%20Loader.exe" | C:\Users\admin\Desktop\Files\Neverlose%20Loader.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Version: 1.4.0 Modules
Quasar(PID) Process(856) Neverlose%20Loader.exe Version1.4.0 C2 (5)192.168.31.99:4782 2001:4bc9:1f98:a4e::676:4782 255.255.255.0:4782 fe80::cabf:4cff:fe84:9572%17:4782 Sub_DirSubDir Install_NameNeverlose Loader.exe Mutex1f65a787-81b8-4955-95e4-b7751e10cd50 StartupJava Updater TagOffice04 LogDirLogs SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs... CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa... | |||||||||||||||
Total events
89 258
Read events
87 515
Write events
1 662
Delete events
81
Modification events
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
197
Suspicious files
60
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svchost.exe | executable | |
MD5:1ECE670AAA09AC9E02AE27B7678B167C | SHA256:B88C6884675CDB358F46C1FBFEDDF24AF749372A6C14C1C4A2757D7BDE3FBC39 | |||
| 2304 | random.exe | C:\Users\admin\AppData\Local\Temp\is-19HSF.tmp\random.tmp | executable | |
MD5:E4C43138CCB8240276872FD1AEC369BE | SHA256:46BE5E3F28A5E4ED63D66B901D927C25944B4DA36EFFEA9C97FB05994360EDF5 | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\random.exe | executable | |
MD5:DCBFAB753554CD4CD7372AFB49FB0EE1 | SHA256:A6E46CC6EA6BB54C37B6846E77047932BC3C871D7363A9114A916EB44702A039 | |||
| 3712 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5nfdtbah.poh.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 348 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs462C.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 3116 | image%20logger.exe | C:\Users\admin\AppData\Local\Temp\tmp362E.tmp.bat | text | |
MD5:33B569987551CB94F129BB8F91DB9C8D | SHA256:7F170F721DE40C2EB7B75FB2E44977098B404477E398C61A09BF422F35C7548E | |||
| 2612 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.lnk | binary | |
MD5:43427FFEC2BBB4EB29304E03651B37B7 | SHA256:3E0F5DBE8115AB5410304F6578B0B34204B114F4688C7DCCC07750824799BE2D | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\xmrig.exe | executable | |
MD5:CB166D49CE846727ED70134B589B0142 | SHA256:49DA580656E51214D59702A1D983EFF143AF3560A344F524FE86326C53FB5DDB | |||
| 676 | powershell.exe | C:\Users\admin\AppData\Local\Temp\w1gopi0c.wvn.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3636 | JJSPLOIT.V2.exe | C:\Users\admin\AppData\Roaming\windows updater\windows 3543.exe | executable | |
MD5:D4A776EA55E24D3124A6E0759FB0AC44 | SHA256:7EF4D0236C81894178A6CFC6C27920217BEA42A3602AD7A6002834718BA7B93C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
69
TCP/UDP connections
561
DNS requests
87
Threats
175
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2612 | svchost.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/unique1/random.exe | unknown | — | — | unknown |
2336 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/skibidisigmer/FNcleanerV2/raw/refs/heads/main/CleanerV2.exe | unknown | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | GET | 200 | 121.40.112.176:8087 | http://121.40.112.176:8087/02.08.2022.exe | unknown | — | — | unknown |
1808 | XW_XXGL.exe | GET | 200 | 112.5.156.15:20006 | http://data.yhydl.com:20006/file/XWGL/aa.inf | unknown | — | — | malicious |
2336 | 4363463463464363463463463.exe | GET | — | 47.98.177.117:8888 | http://47.98.177.117:8888/supershell/compile/download/1.exe | unknown | — | — | malicious |
2336 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/sfyklight/VB-KasperSky-Undetectedtable-Crypter/raw/refs/heads/main/VB.NET%20CRYPTER%20V2.exe | unknown | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | GET | — | 103.216.119.164:80 | http://quanlyphongnet.com/net/Coc%20Coc.exe | unknown | — | — | unknown |
2336 | 4363463463464363463463463.exe | GET | 200 | 202.97.231.78:80 | http://src1.minibai.com/uploads/thirdupload/5c8b08b37a426.exe | unknown | — | — | malicious |
2336 | 4363463463464363463463463.exe | GET | 200 | 120.26.3.86:80 | http://wz.3911.com/3911_wz.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | 185.156.72.2:80 | — | Tov Vaiz Partner | RU | unknown |
2336 | 4363463463464363463463463.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2612 | svchost.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
2564 | asdasdasdasdasd.exe | 147.185.221.27:2676 | go-dramatically.gl.at.ply.gg | PLAYIT-GG | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
github.com |
| whitelisted |
ip-api.com |
| whitelisted |
go-dramatically.gl.at.ply.gg |
| malicious |
objects.githubusercontent.com |
| whitelisted |
data.yhydl.com |
| malicious |
LETSQOOO-62766.portmap.host |
| malicious |
ftp.ywxww.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2336 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2336 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 34 |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2336 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2336 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2336 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1080 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2612 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2612 | svchost.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
Process | Message |
|---|---|
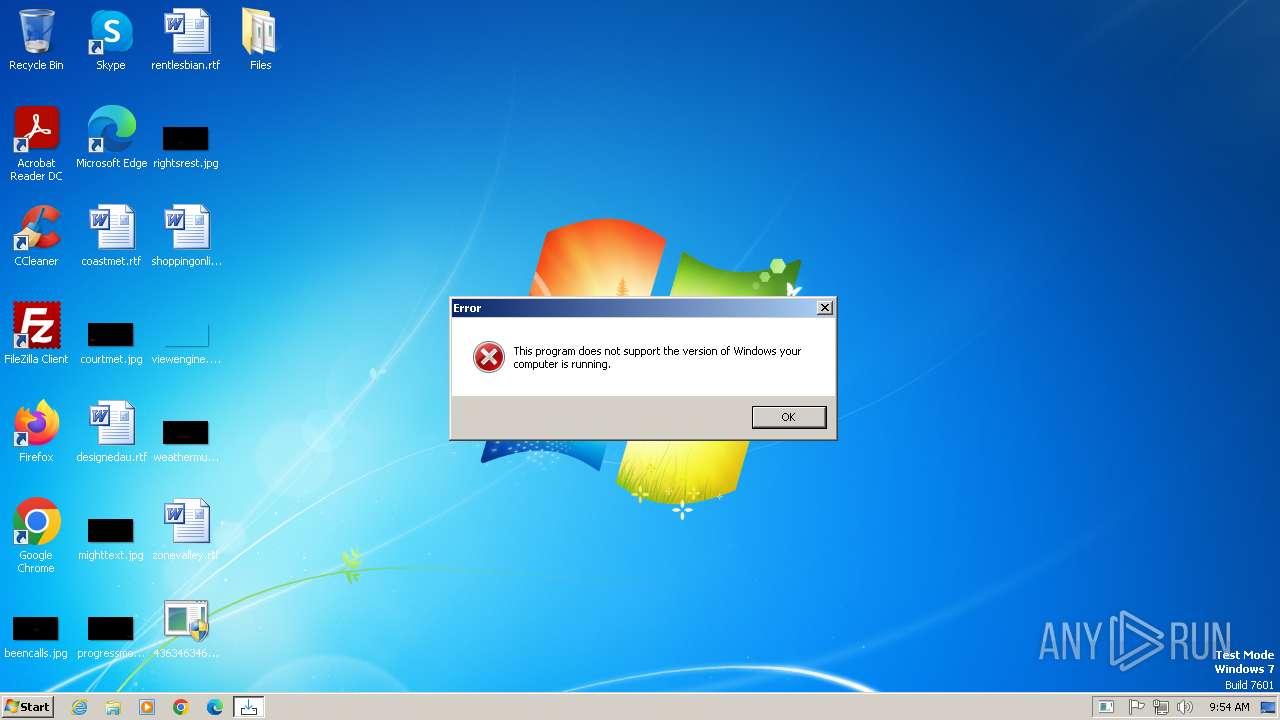
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
CritScript.exe | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE |
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
CritScript.exe | C:\Users\admin\AppData\Local\Temp\ZOMBIES.AHK |
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|