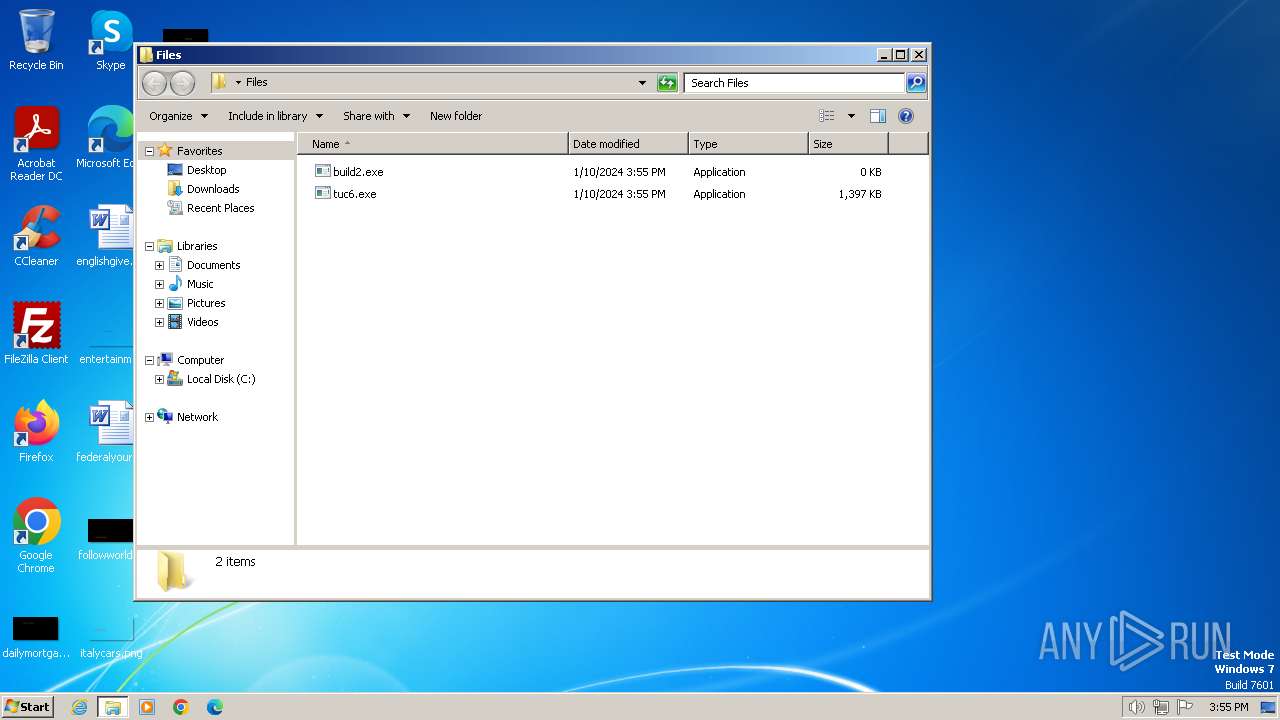
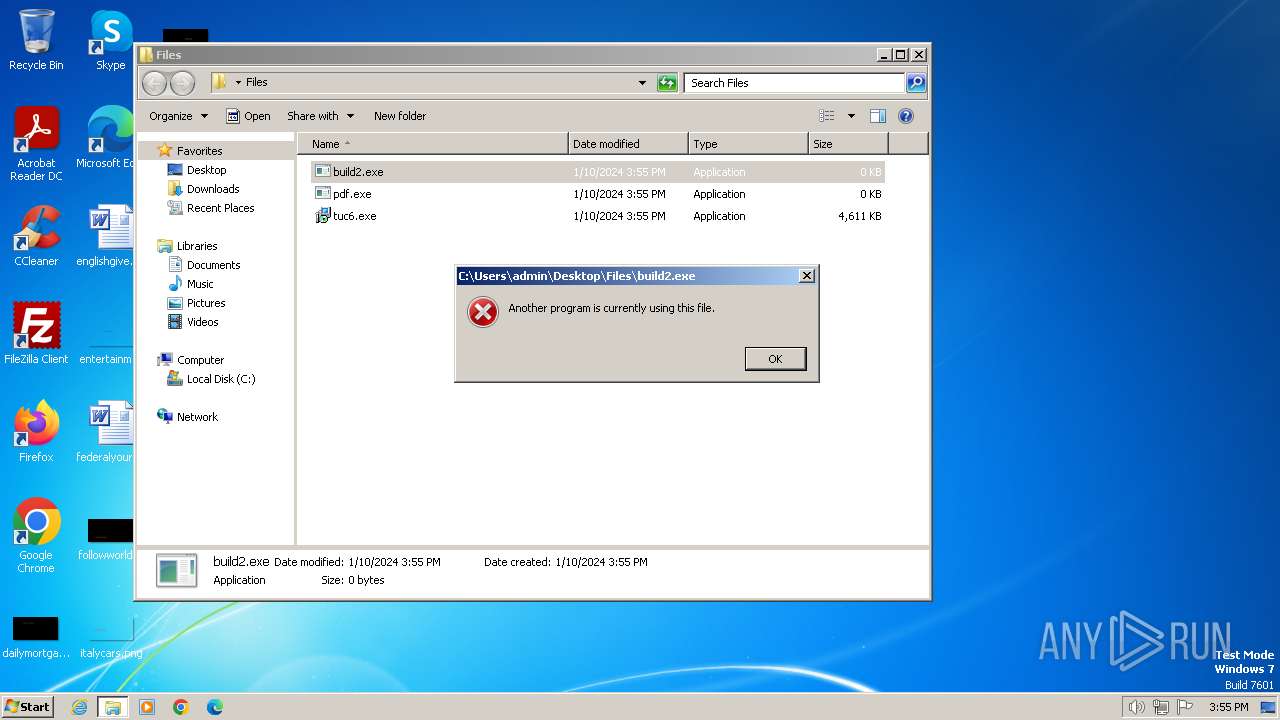
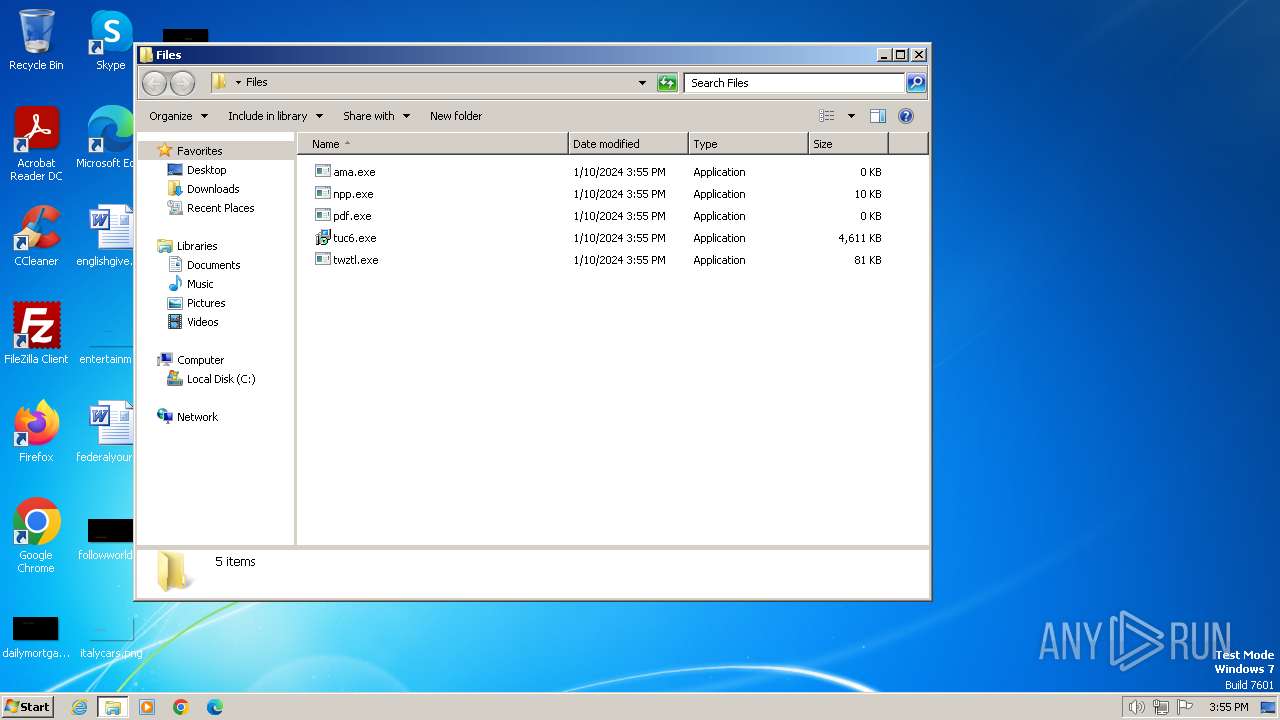
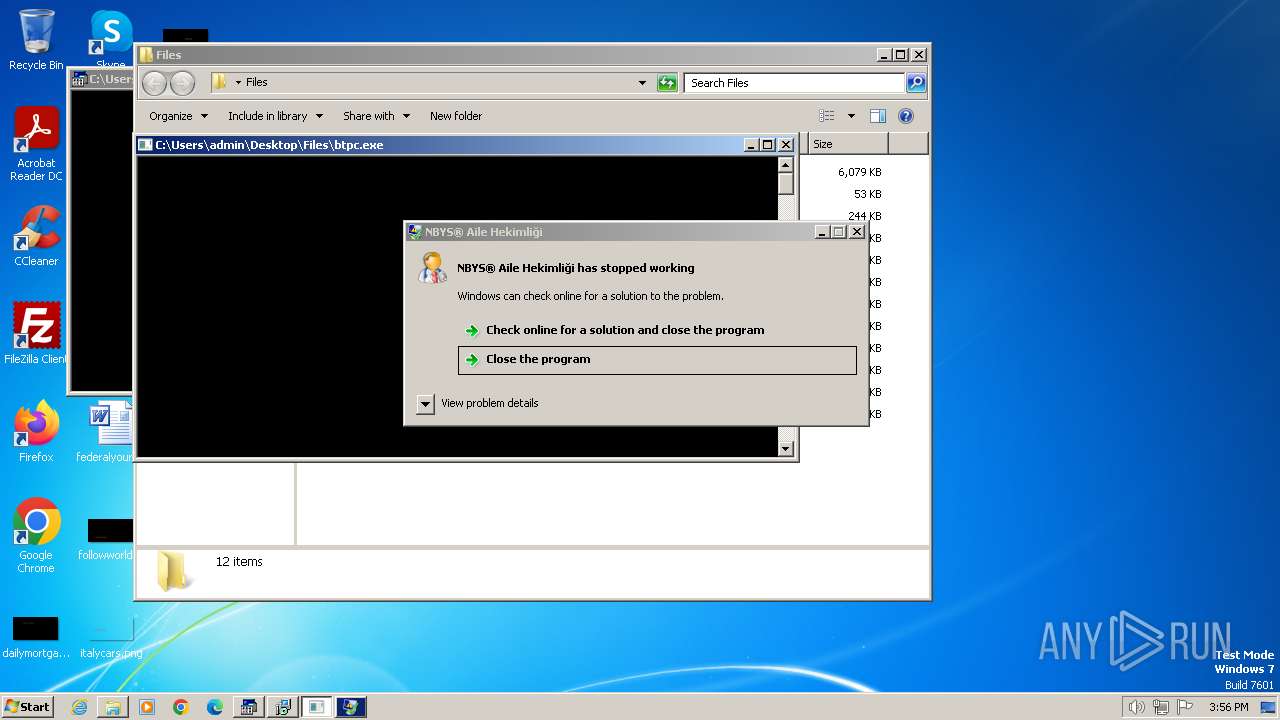
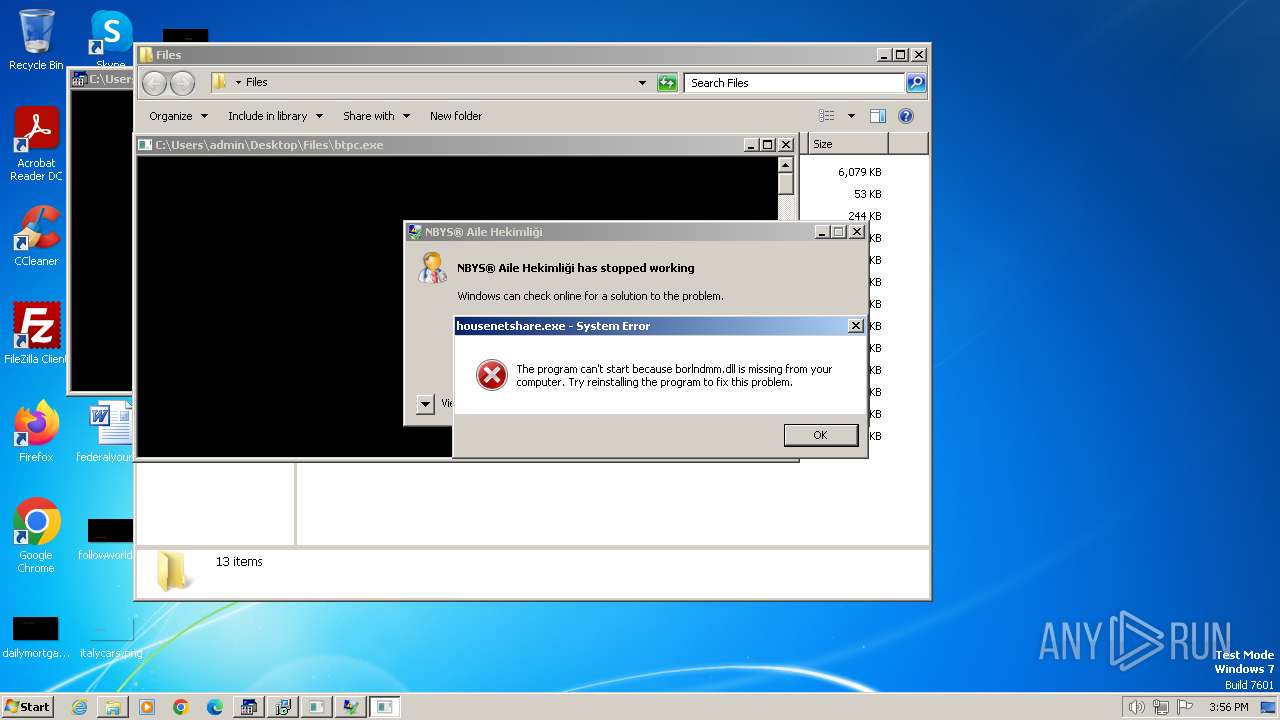
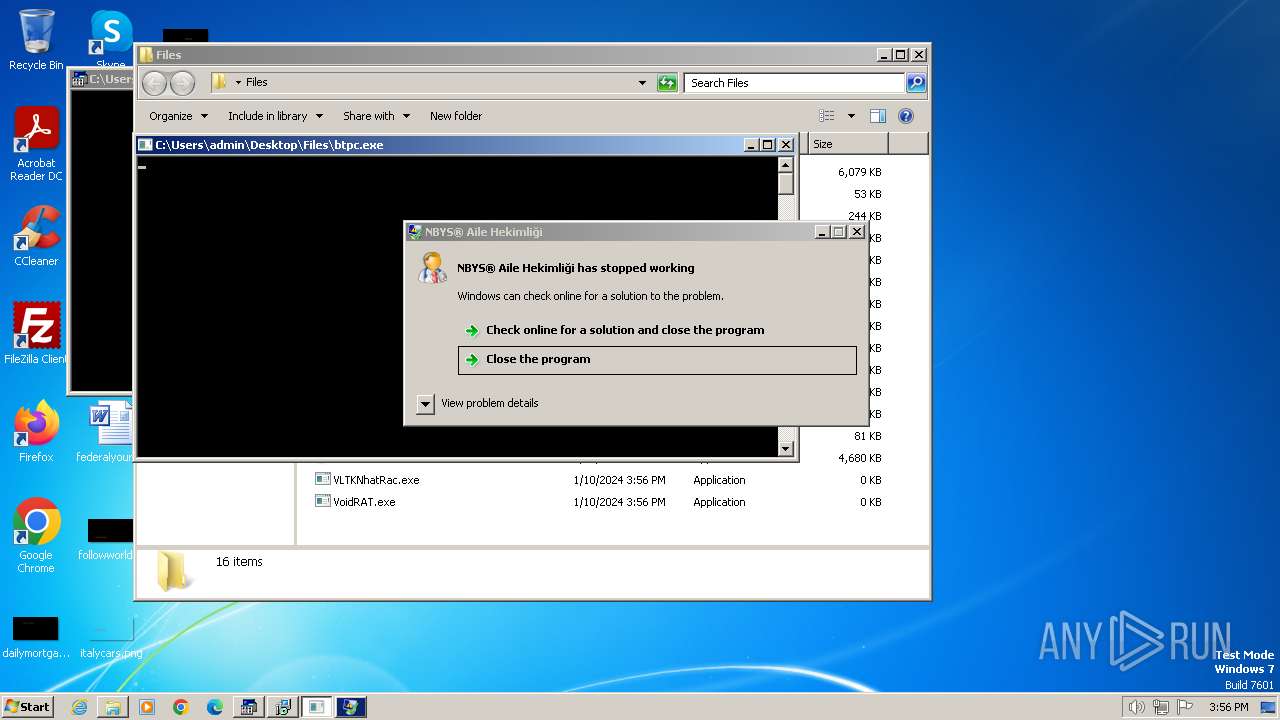
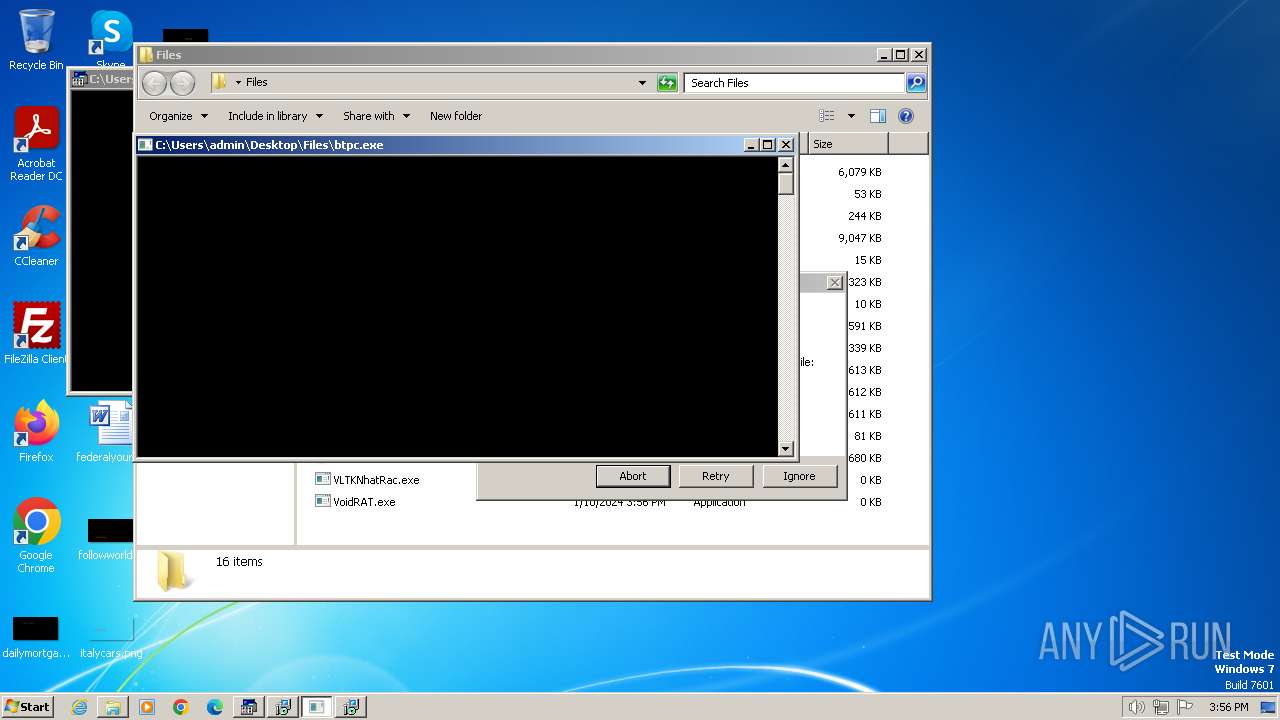
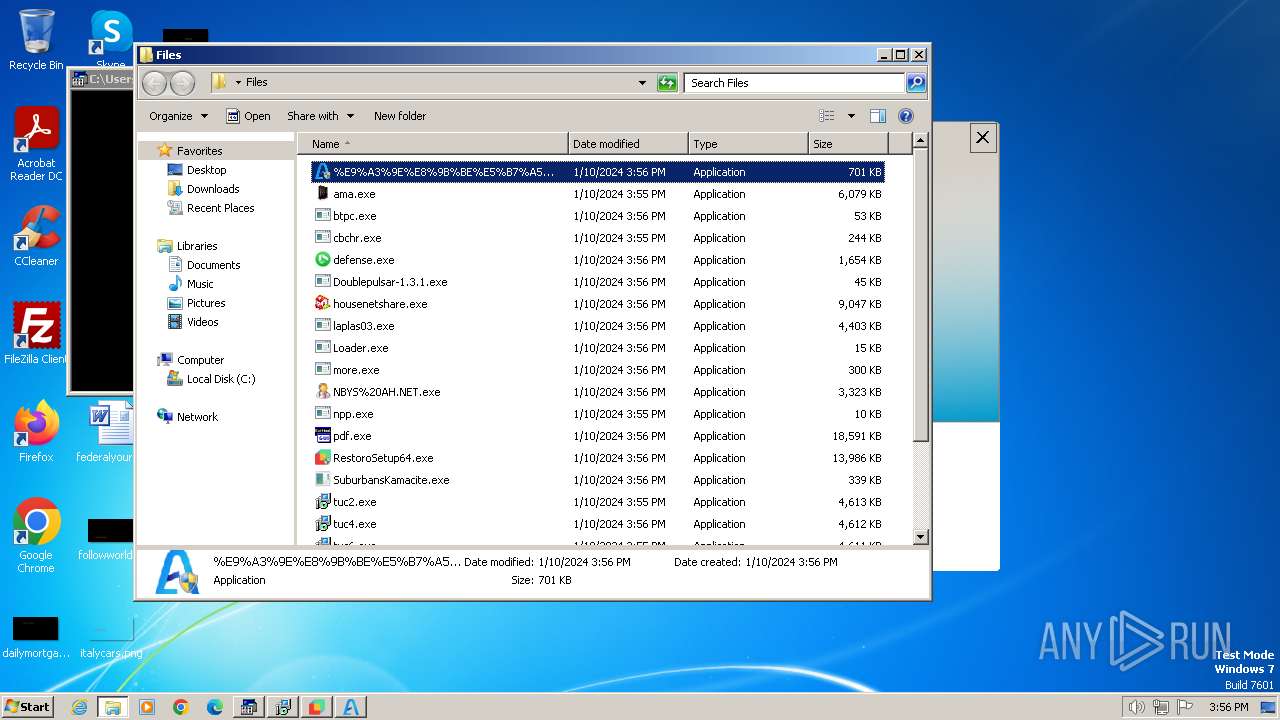
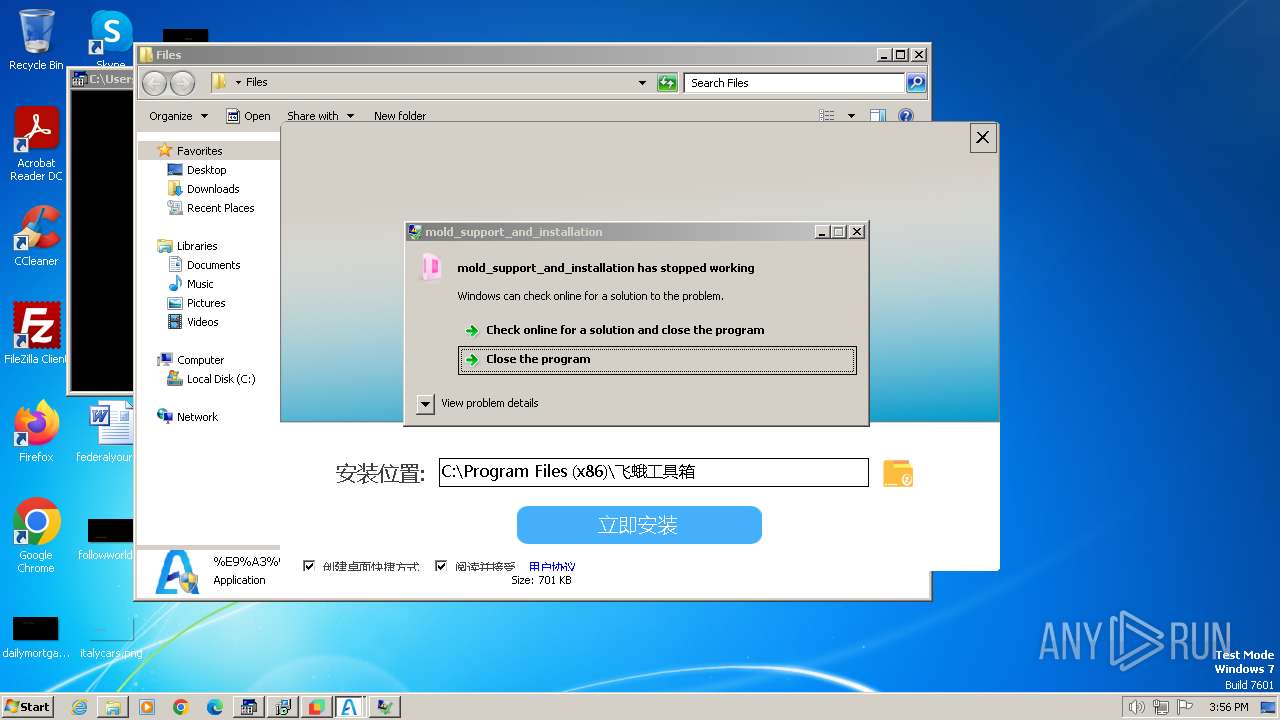
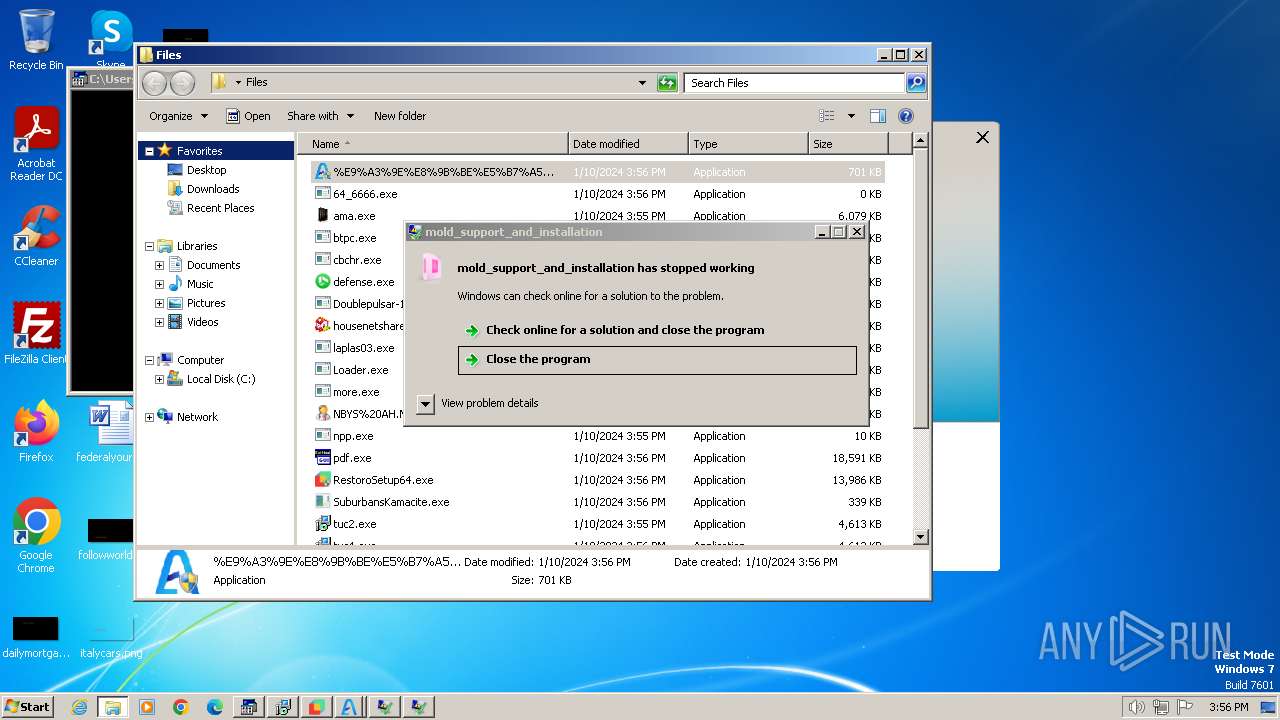
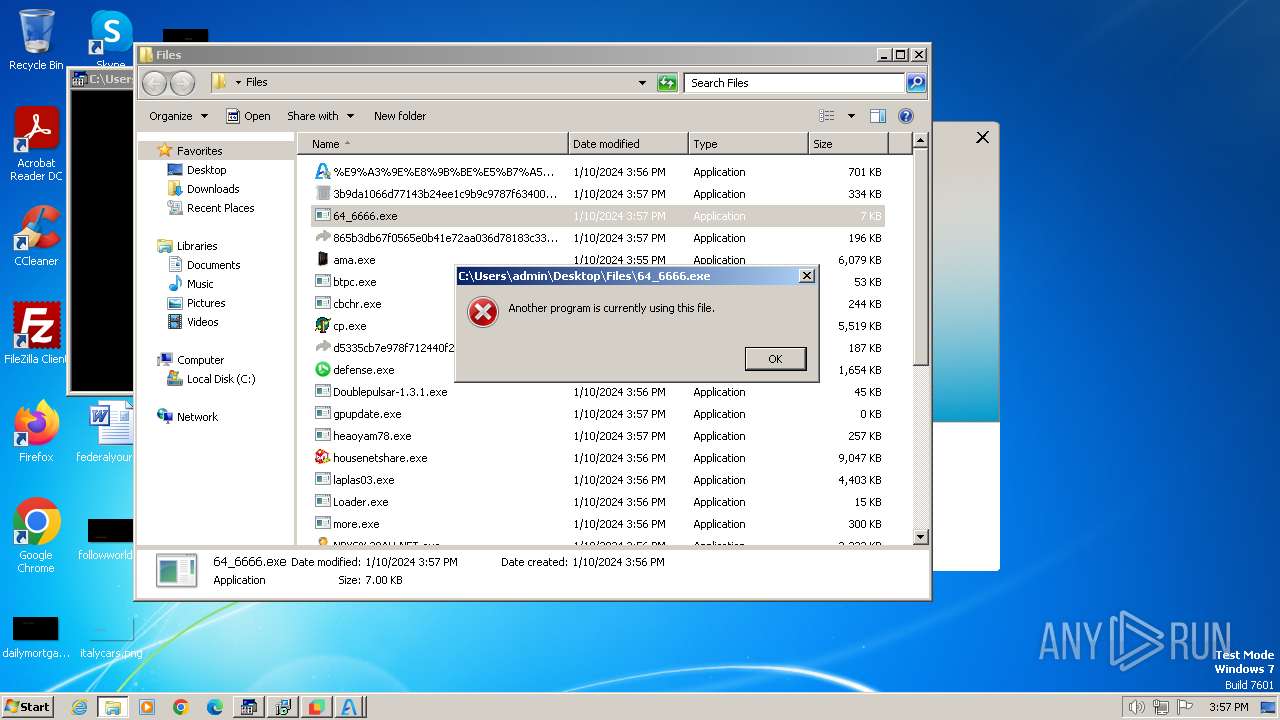
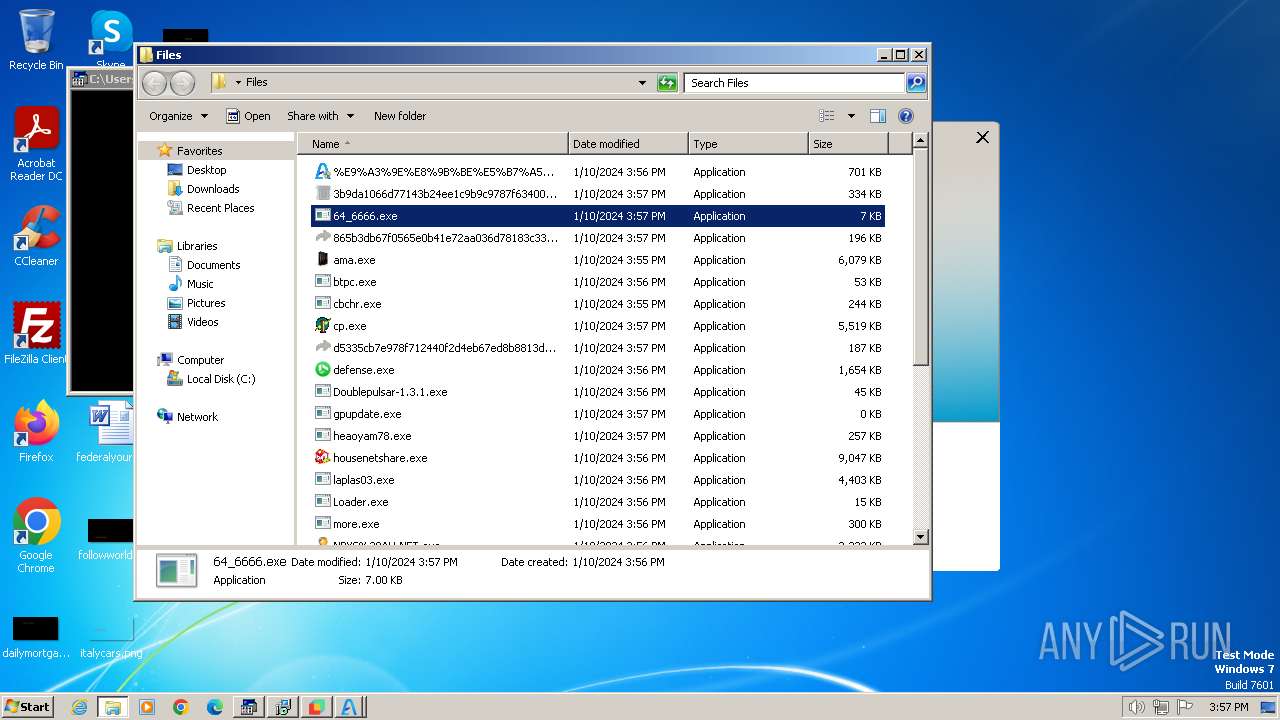
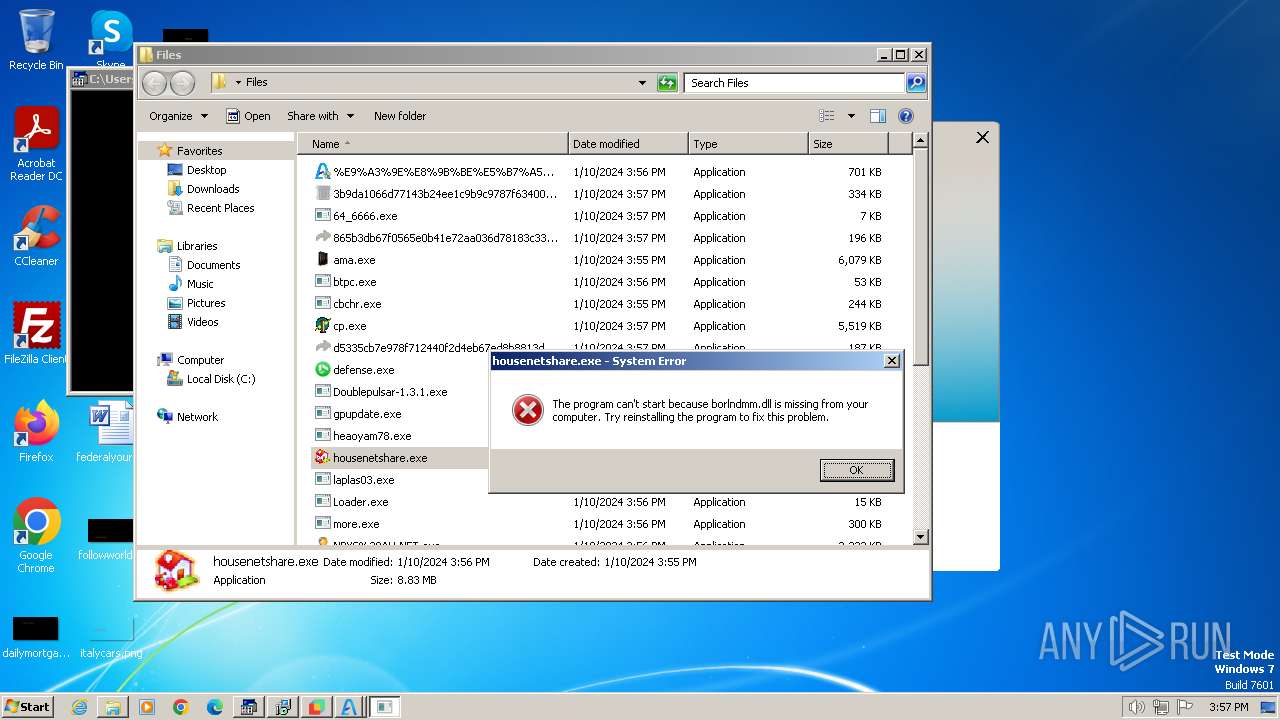
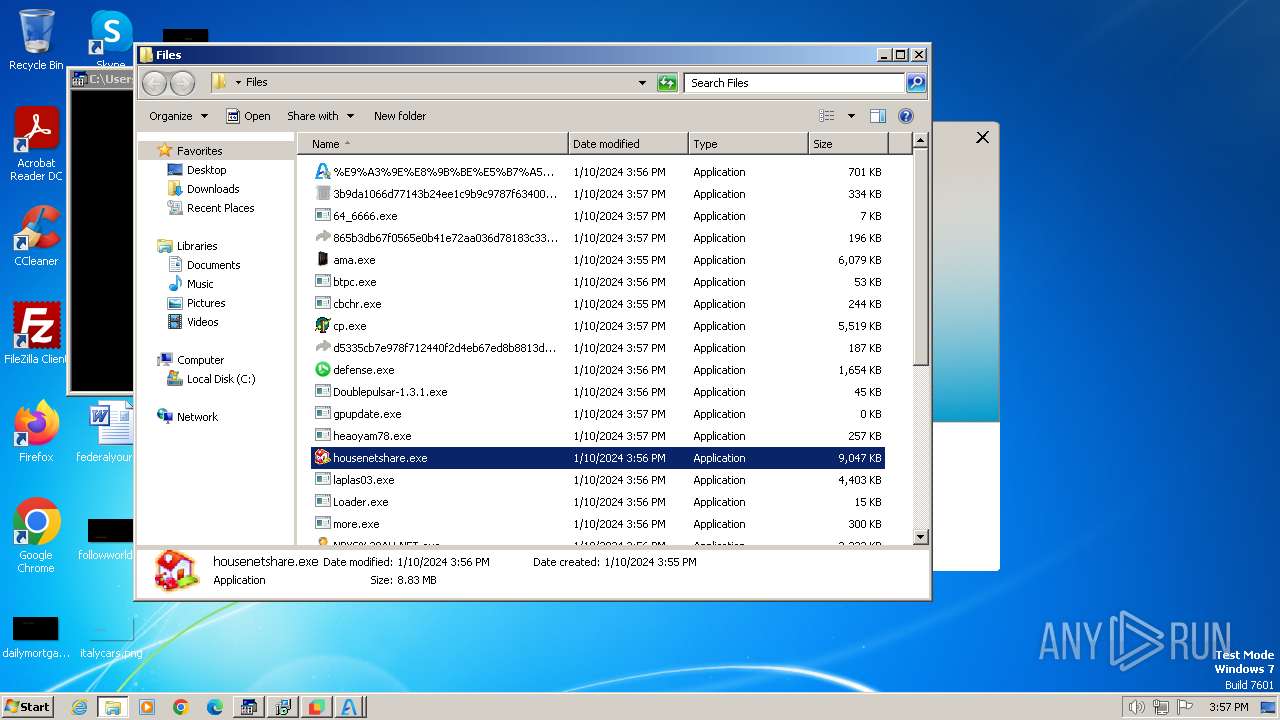
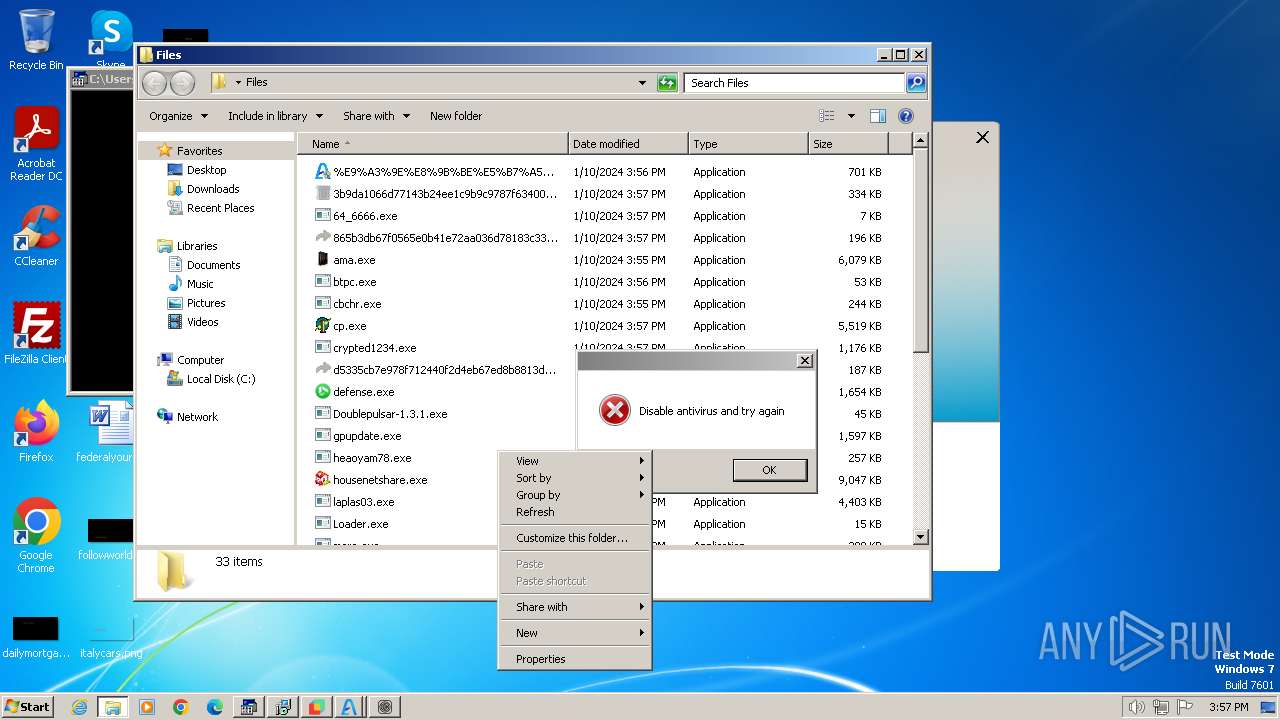
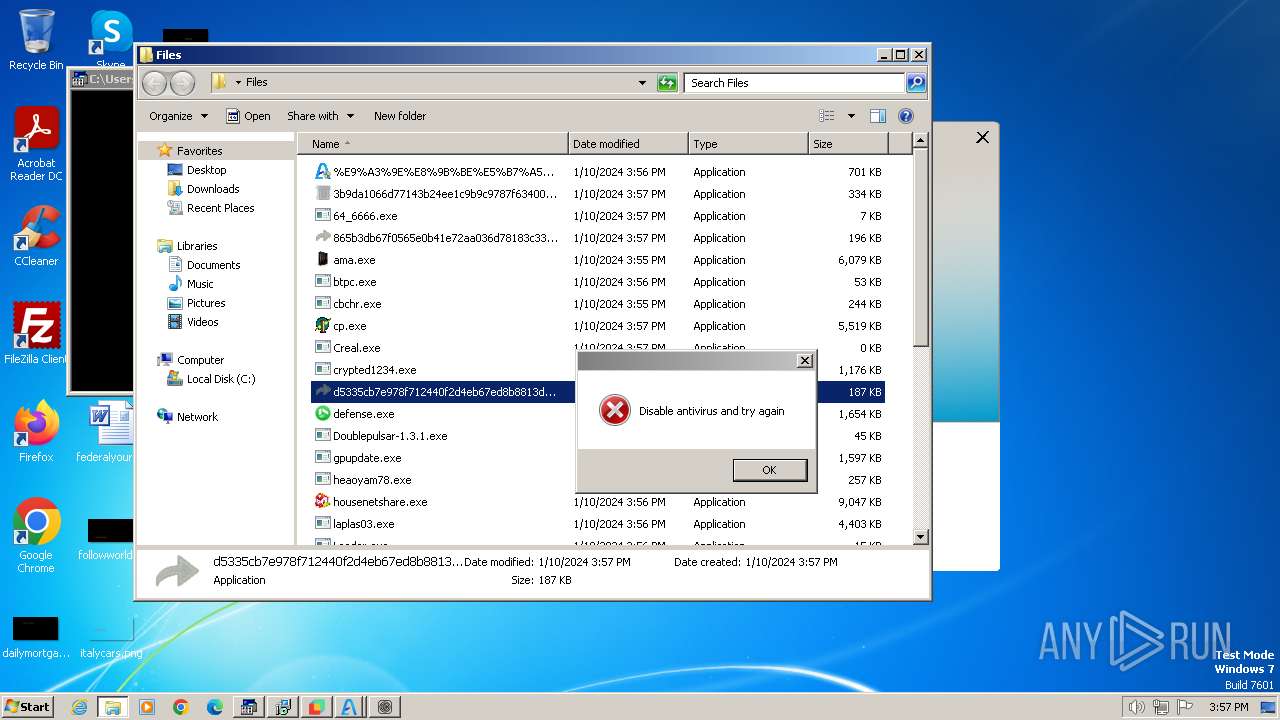
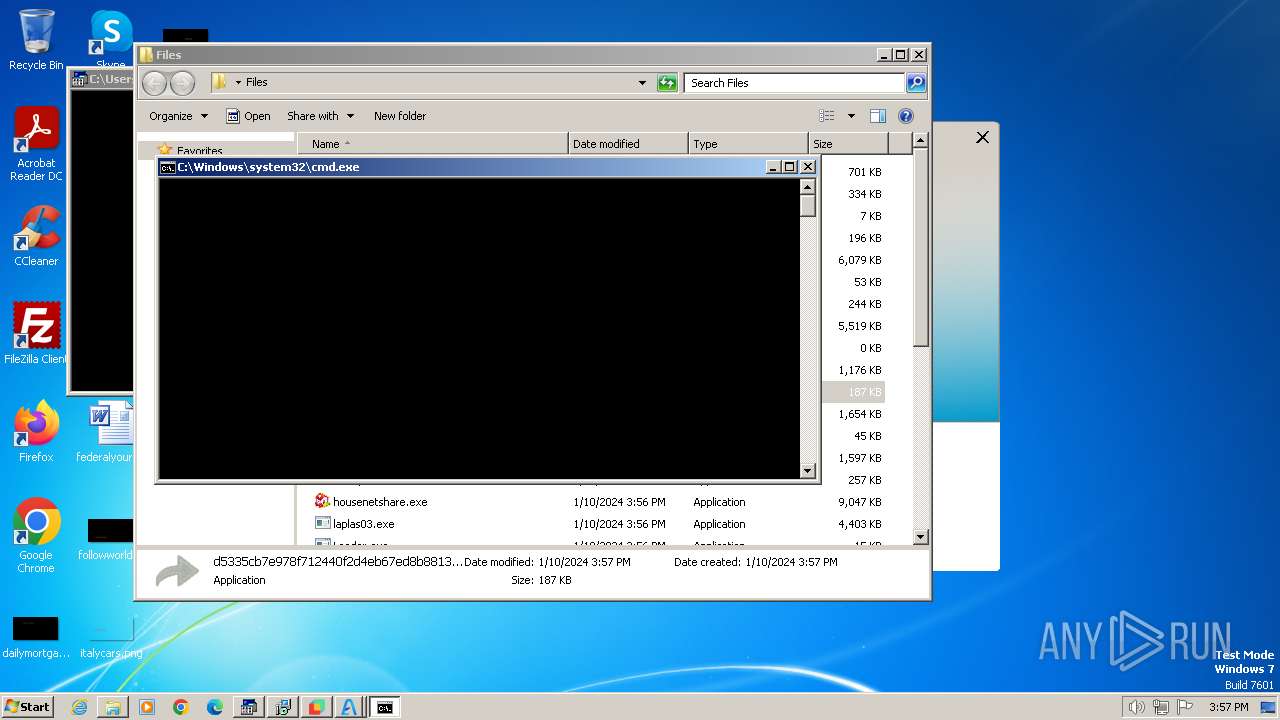
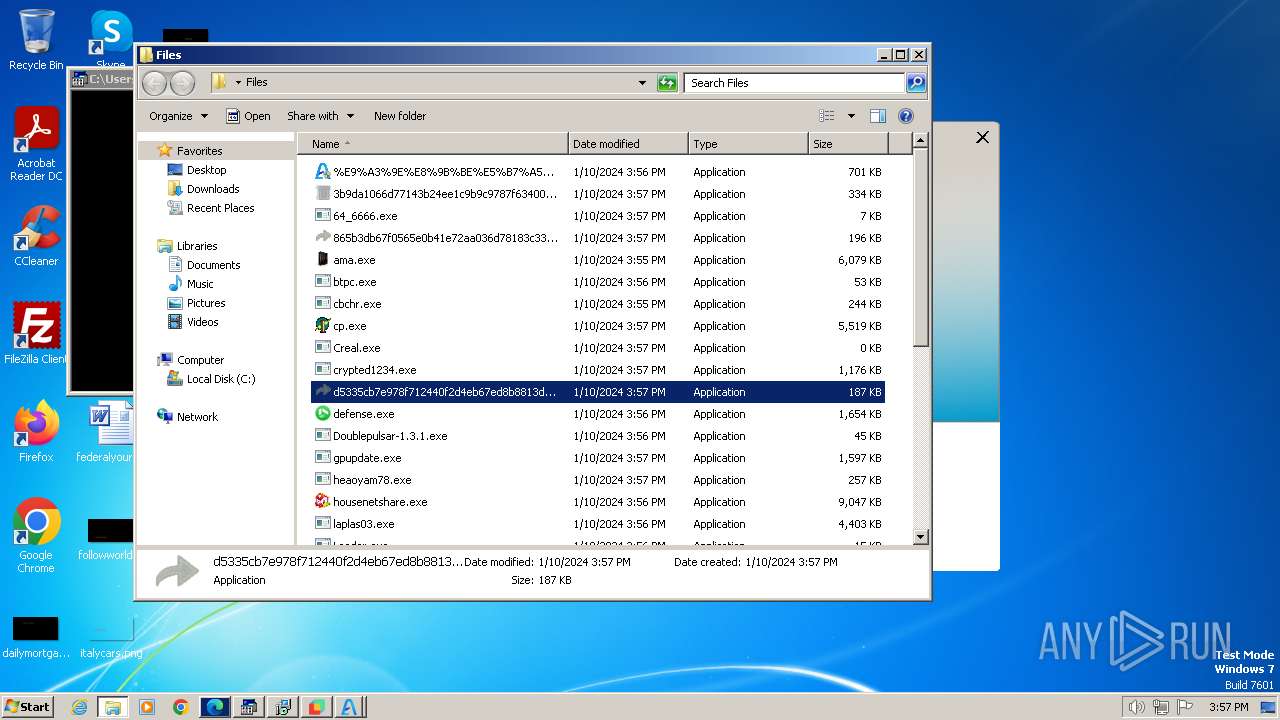
| File name: | 4363463463464363463463463.bin |
| Full analysis: | https://app.any.run/tasks/ef225dcb-732c-4b3d-9c68-6127fc7b89ad |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | January 10, 2024, 15:55:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
HAUSBOMBER has been detected (YARA)
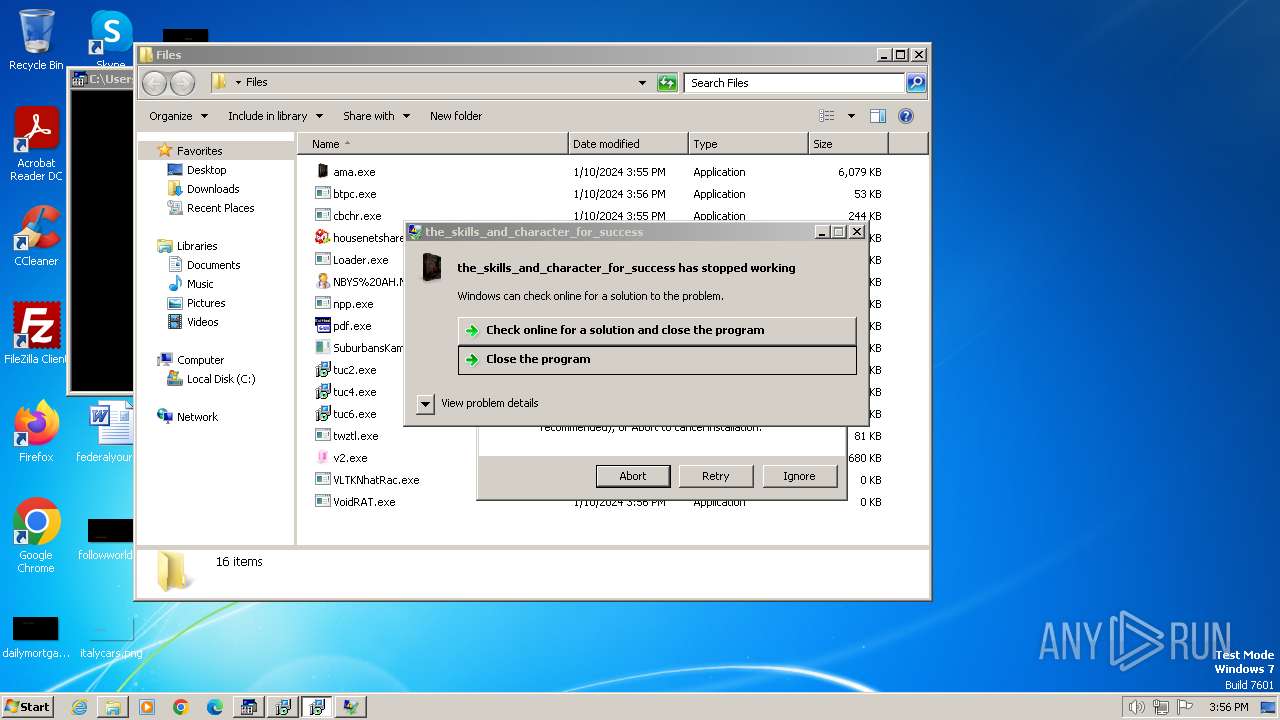
- 4363463463464363463463463.bin.exe (PID: 2268)
- 4363463463464363463463463.bin.exe (PID: 1732)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3372)
- cmd.exe (PID: 3012)
Changes the autorun value in the registry
- 158351868.exe (PID: 3068)
Changes Security Center notification settings
- sylsplvc.exe (PID: 3116)
ASYNCRAT has been detected (YARA)
- calc.exe (PID: 3104)
Create files in the Startup directory
- dllhost.exe (PID: 3624)
- 5up4SW7.exe (PID: 2020)
REDLINE has been detected (YARA)
- v2.exe (PID: 2536)
- heaoyam78.exe (PID: 3868)
- RegSvcs.exe (PID: 2560)
- RegSvcs.exe (PID: 3120)
- ms_tool.exe (PID: 3632)
Uses Task Scheduler to run other applications
- more.exe (PID: 2572)
- AdobeUpdateres.exe (PID: 3640)
- cmd.exe (PID: 2780)
- more.exe (PID: 3404)
Adds path to the Windows Defender exclusion list
- more.exe (PID: 2572)
Disables Windows Defender
- 5up4SW7.exe (PID: 2020)
Risepro uses scheduled tasks to run itself
- cmd.exe (PID: 2780)
- cmd.exe (PID: 3012)
Steals credentials from Web Browsers
- 5up4SW7.exe (PID: 2020)
Actions looks like stealing of personal data
- 5up4SW7.exe (PID: 2020)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.bin.exe (PID: 2268)
- 4363463463464363463463463.bin.exe (PID: 1732)
- npp.exe (PID: 2620)
- syspolrvcs.exe (PID: 2580)
- npp.exe (PID: 1196)
- cbchr.exe (PID: 2372)
- sylsplvc.exe (PID: 3116)
- InstallUtil.exe (PID: 3832)
- more.exe (PID: 2572)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- more.exe (PID: 3404)
- syncUpd.exe (PID: 4072)
- cp.exe (PID: 3764)
- powershell.exe (PID: 2496)
- AdobeUpdateres.exe (PID: 3640)
- more.exe (PID: 2592)
- RegAsm.exe (PID: 3084)
- 3Eb73mM.exe (PID: 1880)
- images.exe (PID: 3524)
- powershell.exe (PID: 3384)
- 5up4SW7.exe (PID: 2020)
- bitrixreportlib.exe (PID: 1924)
Reads settings of System Certificates
- 4363463463464363463463463.bin.exe (PID: 1732)
- 4363463463464363463463463.bin.exe (PID: 2268)
- 5up4SW7.exe (PID: 2020)
Reads the Windows owner or organization settings
- tuc6.tmp (PID: 632)
- tuc2.tmp (PID: 3148)
- tuc4.tmp (PID: 3984)
Executing commands from a ".bat" file
- cbchr.exe (PID: 2372)
- cp.exe (PID: 3764)
- more.exe (PID: 2592)
Starts CMD.EXE for commands execution
- cbchr.exe (PID: 2372)
- cp.exe (PID: 3764)
- more.exe (PID: 2592)
- 5up4SW7.exe (PID: 2020)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3040)
- cmd.exe (PID: 1264)
- cmd.exe (PID: 2824)
Searches for installed software
- tuc2.tmp (PID: 3148)
- tuc4.tmp (PID: 3984)
- 5up4SW7.exe (PID: 2020)
Adds/modifies Windows certificates
- 4363463463464363463463463.bin.exe (PID: 2268)
- 4363463463464363463463463.bin.exe (PID: 1732)
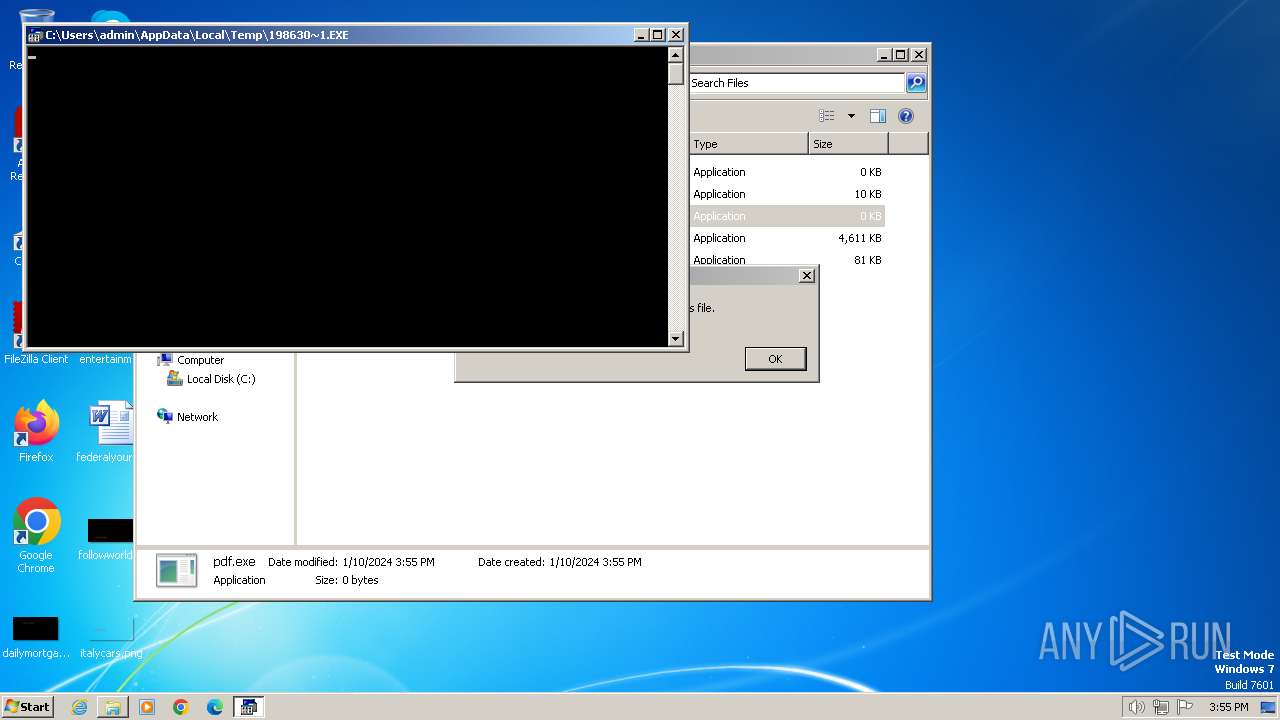
The process executes VB scripts
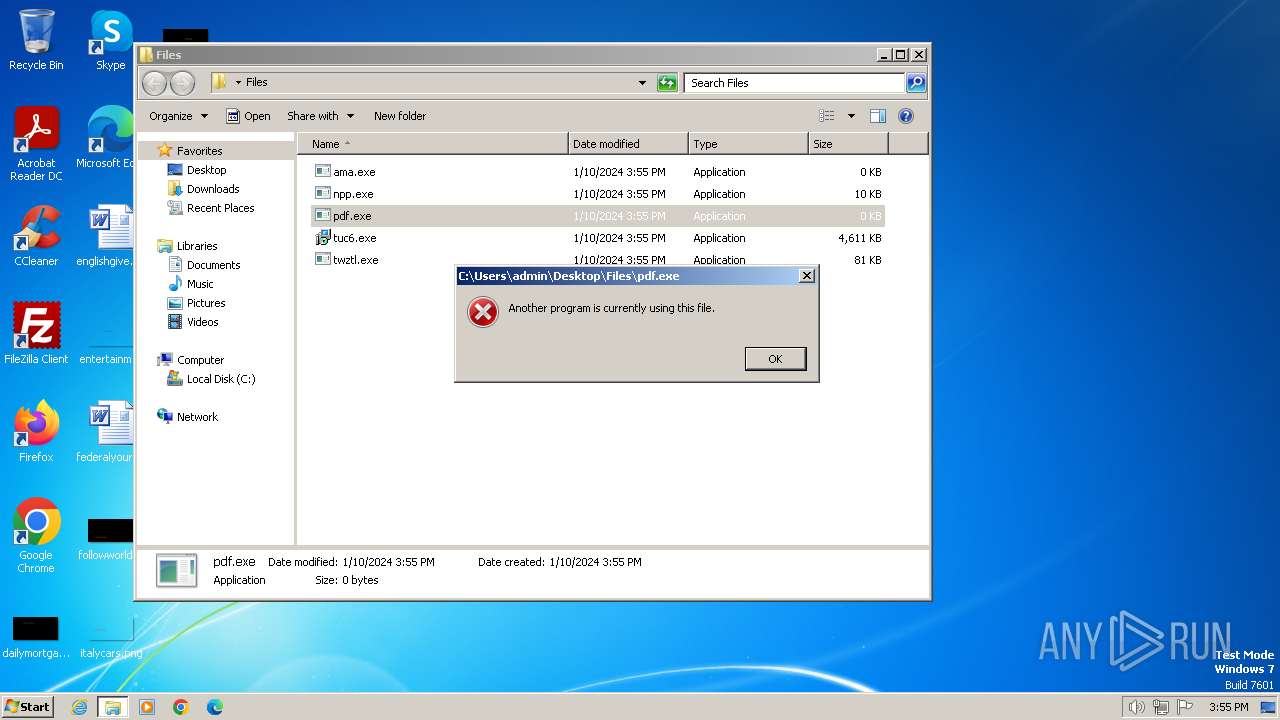
- pdf.exe (PID: 3424)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
The process creates files with name similar to system file names
- RestoroSetup64.exe (PID: 2388)
Reads the BIOS version
- cp.exe (PID: 3764)
- AdobeUpdateres.exe (PID: 3640)
- cp.exe (PID: 4984)
- cp.exe (PID: 5028)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2496)
- powershell.exe (PID: 3384)
Starts POWERSHELL.EXE for commands execution
- more.exe (PID: 2572)
- 5up4SW7.exe (PID: 2020)
Script adds exclusion path to Windows Defender
- more.exe (PID: 2572)
Query Microsoft Defender preferences
- 5up4SW7.exe (PID: 2020)
Reads browser cookies
- 5up4SW7.exe (PID: 2020)
Accesses Microsoft Outlook profiles
- 5up4SW7.exe (PID: 2020)
INFO
Checks supported languages
- 4363463463464363463463463.bin.exe (PID: 2268)
- 4363463463464363463463463.bin.exe (PID: 1732)
- tuc6.exe (PID: 1844)
- twztl.exe (PID: 2632)
- bitrixreportlib.exe (PID: 2440)
- npp.exe (PID: 2620)
- tuc6.tmp (PID: 632)
- bitrixreportlib.exe (PID: 1924)
- syspolrvcs.exe (PID: 2580)
- twztl.exe (PID: 2800)
- npp.exe (PID: 1196)
- ama.exe (PID: 2516)
- cbchr.exe (PID: 2372)
- 158351868.exe (PID: 3068)
- sylsplvc.exe (PID: 3116)
- tuc2.exe (PID: 3108)
- tuc2.tmp (PID: 3148)
- calc.exe (PID: 3104)
- 3188220585.exe (PID: 2784)
- pdf.exe (PID: 3424)
- NBYS%20AH.NET.exe (PID: 3608)
- vbc.exe (PID: 3536)
- InstallUtil.exe (PID: 3832)
- tuc4.exe (PID: 1876)
- tuc4.tmp (PID: 3984)
- SuburbansKamacite.exe (PID: 4088)
- v2.exe (PID: 4032)
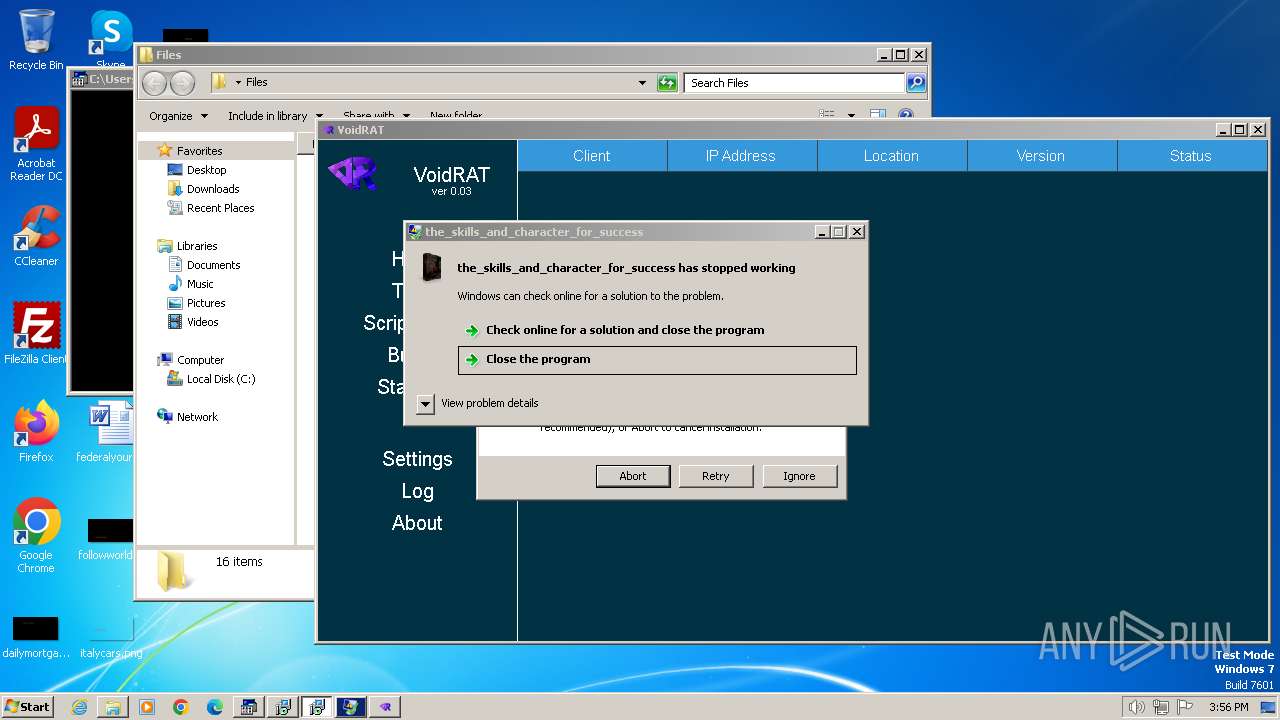
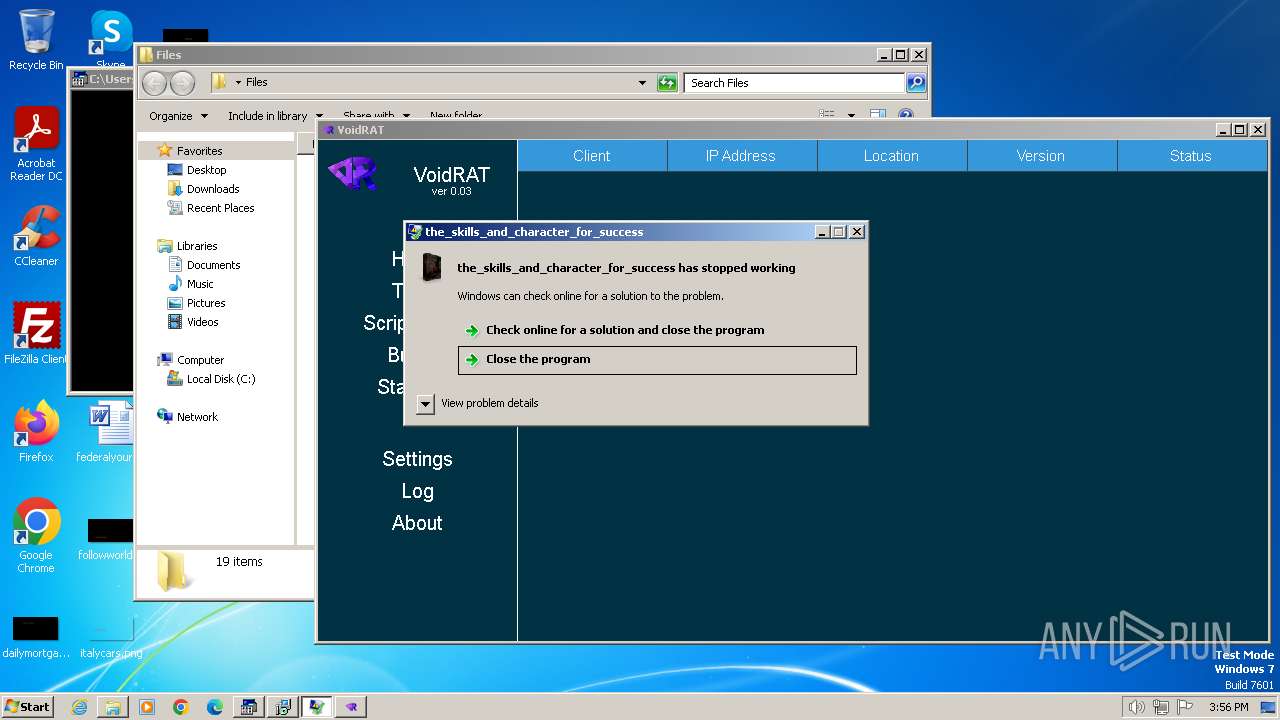
- VoidRAT.exe (PID: 296)
- RegSvcs.exe (PID: 2560)
- RestoroSetup64.exe (PID: 2388)
- defense.exe (PID: 2084)
- bitrixreportlib.exe (PID: 1588)
- bitrixreportlib.exe (PID: 2440)
- more.exe (PID: 2572)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- v2.exe (PID: 2536)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- v2.exe (PID: 2476)
- RegSvcs.exe (PID: 3120)
- heaoyam78.exe (PID: 3868)
- RegSvcs.exe (PID: 3196)
- more.exe (PID: 3404)
- syncUpd.exe (PID: 4072)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 3744)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 3452)
- cp.exe (PID: 3764)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 896)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 2128)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 1768)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 1216)
- more.exe (PID: 2592)
- crypted1234.exe (PID: 4060)
- ms_updater.exe (PID: 3936)
- valid.exe (PID: 4052)
- RegAsm.exe (PID: 3084)
- ms_tool.exe (PID: 3632)
- 3Eb73mM.exe (PID: 1880)
- 5up4SW7.exe (PID: 2020)
- images.exe (PID: 3524)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 4304)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 4448)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4952)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4660)
- crypted1234.exe (PID: 4884)
- RegAsm.exe (PID: 4908)
- cp.exe (PID: 4984)
- AdobeUpdateres.exe (PID: 3640)
- cp.exe (PID: 5028)
- more.exe (PID: 5084)
Drops the executable file immediately after the start
- 4363463463464363463463463.bin.exe (PID: 2268)
- tuc6.exe (PID: 1844)
- tuc6.tmp (PID: 632)
- twztl.exe (PID: 2632)
- bitrixreportlib.exe (PID: 2440)
- tuc2.exe (PID: 3108)
- cbchr.exe (PID: 2372)
- 158351868.exe (PID: 3068)
- tuc2.tmp (PID: 3148)
- 4363463463464363463463463.bin.exe (PID: 1732)
- ama.exe (PID: 2516)
- tuc4.exe (PID: 1876)
- dllhost.exe (PID: 3624)
- tuc4.tmp (PID: 3984)
- RestoroSetup64.exe (PID: 2388)
- cp.exe (PID: 3764)
- more.exe (PID: 2572)
- more.exe (PID: 2592)
- RegAsm.exe (PID: 3084)
- valid.exe (PID: 4052)
- 5up4SW7.exe (PID: 2020)
- msedge.exe (PID: 3496)
Reads the machine GUID from the registry
- 4363463463464363463463463.bin.exe (PID: 1732)
- 4363463463464363463463463.bin.exe (PID: 2268)
- npp.exe (PID: 2620)
- npp.exe (PID: 1196)
- syspolrvcs.exe (PID: 2580)
- cbchr.exe (PID: 2372)
- calc.exe (PID: 3104)
- sylsplvc.exe (PID: 3116)
- pdf.exe (PID: 3424)
- vbc.exe (PID: 3536)
- InstallUtil.exe (PID: 3832)
- NBYS%20AH.NET.exe (PID: 3608)
- SuburbansKamacite.exe (PID: 4088)
- ama.exe (PID: 2516)
- v2.exe (PID: 4032)
- RegSvcs.exe (PID: 2560)
- defense.exe (PID: 2084)
- more.exe (PID: 2572)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- RestoroSetup64.exe (PID: 2388)
- v2.exe (PID: 2476)
- v2.exe (PID: 2536)
- RegSvcs.exe (PID: 3120)
- more.exe (PID: 3404)
- heaoyam78.exe (PID: 3868)
- RegSvcs.exe (PID: 3196)
- syncUpd.exe (PID: 4072)
- more.exe (PID: 2592)
- AdobeUpdateres.exe (PID: 3640)
- ms_tool.exe (PID: 3632)
- images.exe (PID: 3524)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- 5up4SW7.exe (PID: 2020)
- bitrixreportlib.exe (PID: 1924)
- more.exe (PID: 5084)
Create files in a temporary directory
- tuc6.exe (PID: 1844)
- tuc6.tmp (PID: 632)
- npp.exe (PID: 2620)
- syspolrvcs.exe (PID: 2580)
- npp.exe (PID: 1196)
- cbchr.exe (PID: 2372)
- tuc2.exe (PID: 3108)
- tuc2.tmp (PID: 3148)
- sylsplvc.exe (PID: 3116)
- ama.exe (PID: 2516)
- tuc4.exe (PID: 1876)
- tuc4.tmp (PID: 3984)
- RestoroSetup64.exe (PID: 2388)
- cp.exe (PID: 3764)
- more.exe (PID: 2572)
- more.exe (PID: 2592)
- valid.exe (PID: 4052)
- 5up4SW7.exe (PID: 2020)
- 4363463463464363463463463.bin.exe (PID: 1732)
- more.exe (PID: 3404)
Process requests binary or script from the Internet
- 4363463463464363463463463.bin.exe (PID: 2268)
- 4363463463464363463463463.bin.exe (PID: 1732)
- npp.exe (PID: 2620)
- npp.exe (PID: 1196)
Reads the computer name
- 4363463463464363463463463.bin.exe (PID: 2268)
- tuc6.tmp (PID: 632)
- bitrixreportlib.exe (PID: 2440)
- npp.exe (PID: 2620)
- syspolrvcs.exe (PID: 2580)
- npp.exe (PID: 1196)
- ama.exe (PID: 2516)
- cbchr.exe (PID: 2372)
- tuc2.tmp (PID: 3148)
- calc.exe (PID: 3104)
- 4363463463464363463463463.bin.exe (PID: 1732)
- sylsplvc.exe (PID: 3116)
- NBYS%20AH.NET.exe (PID: 3608)
- pdf.exe (PID: 3424)
- vbc.exe (PID: 3536)
- InstallUtil.exe (PID: 3832)
- SuburbansKamacite.exe (PID: 4088)
- v2.exe (PID: 4032)
- tuc4.tmp (PID: 3984)
- bitrixreportlib.exe (PID: 1588)
- RegSvcs.exe (PID: 2560)
- defense.exe (PID: 2084)
- more.exe (PID: 2572)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- RestoroSetup64.exe (PID: 2388)
- v2.exe (PID: 2536)
- v2.exe (PID: 2476)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- more.exe (PID: 3404)
- heaoyam78.exe (PID: 3868)
- RegSvcs.exe (PID: 3196)
- RegSvcs.exe (PID: 3120)
- syncUpd.exe (PID: 4072)
- cp.exe (PID: 3764)
- more.exe (PID: 2592)
- AdobeUpdateres.exe (PID: 3640)
- ms_tool.exe (PID: 3632)
- crypted1234.exe (PID: 4060)
- RegAsm.exe (PID: 3084)
- 3Eb73mM.exe (PID: 1880)
- images.exe (PID: 3524)
- 5up4SW7.exe (PID: 2020)
- bitrixreportlib.exe (PID: 1924)
- crypted1234.exe (PID: 4884)
- more.exe (PID: 5084)
Reads Environment values
- 4363463463464363463463463.bin.exe (PID: 2268)
- cbchr.exe (PID: 2372)
- calc.exe (PID: 3104)
- 4363463463464363463463463.bin.exe (PID: 1732)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 2912)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- defense.exe (PID: 2084)
- 5up4SW7.exe (PID: 2020)
Manual execution by a user
- 4363463463464363463463463.bin.exe (PID: 1316)
- twztl.exe (PID: 2800)
- npp.exe (PID: 1196)
- 4363463463464363463463463.bin.exe (PID: 1732)
- v2.exe (PID: 2476)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3044)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3216)
- v2.exe (PID: 2536)
- more.exe (PID: 3404)
- housenetshare.exe (PID: 2460)
- msedge.exe (PID: 3496)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 4304)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4660)
- crypted1234.exe (PID: 4884)
- cp.exe (PID: 4984)
- cp.exe (PID: 5028)
Connects to the server without a host name
- 4363463463464363463463463.bin.exe (PID: 1732)
- 4363463463464363463463463.bin.exe (PID: 2268)
- syspolrvcs.exe (PID: 2580)
- sylsplvc.exe (PID: 3116)
- InstallUtil.exe (PID: 3832)
- syncUpd.exe (PID: 4072)
- AdobeUpdateres.exe (PID: 3640)
Process drops legitimate windows executable
- tuc6.tmp (PID: 632)
- tuc2.tmp (PID: 3148)
- tuc4.tmp (PID: 3984)
- 4363463463464363463463463.bin.exe (PID: 1732)
Creates files or folders in the user directory
- tuc6.tmp (PID: 632)
- npp.exe (PID: 2620)
- syspolrvcs.exe (PID: 2580)
- cbchr.exe (PID: 2372)
- tuc2.tmp (PID: 3148)
- tuc4.tmp (PID: 3984)
- dllhost.exe (PID: 3624)
- more.exe (PID: 2572)
- more.exe (PID: 2592)
- AdobeUpdateres.exe (PID: 3640)
- RegAsm.exe (PID: 3084)
- 5up4SW7.exe (PID: 2020)
Drops 7-zip archiver for unpacking
- tuc6.tmp (PID: 632)
- tuc2.tmp (PID: 3148)
- tuc4.tmp (PID: 3984)
Creates files in the program directory
- bitrixreportlib.exe (PID: 2440)
- bitrixreportlib.exe (PID: 1924)
- cp.exe (PID: 3764)
- AdobeUpdateres.exe (PID: 3640)
- 5up4SW7.exe (PID: 2020)
Checks proxy server information
- npp.exe (PID: 2620)
- syspolrvcs.exe (PID: 2580)
- npp.exe (PID: 1196)
- sylsplvc.exe (PID: 3116)
- InstallUtil.exe (PID: 3832)
- syncUpd.exe (PID: 4072)
- AdobeUpdateres.exe (PID: 3640)
- bitrixreportlib.exe (PID: 1924)
Starts itself from another location
- twztl.exe (PID: 2632)
- 158351868.exe (PID: 3068)
- sylsplvc.exe (PID: 3116)
Connects to the CnC server
- syspolrvcs.exe (PID: 2580)
- sylsplvc.exe (PID: 3116)
- InstallUtil.exe (PID: 3832)
- 5up4SW7.exe (PID: 2020)
- bitrixreportlib.exe (PID: 1924)
- syncUpd.exe (PID: 4072)
PHORPIEX has been detected (SURICATA)
- syspolrvcs.exe (PID: 2580)
- 4363463463464363463463463.bin.exe (PID: 2268)
- sylsplvc.exe (PID: 3116)
The executable file from the user directory is run by the CMD process
- calc.exe (PID: 3104)
- images.exe (PID: 3524)
Connects to unusual port
- syspolrvcs.exe (PID: 2580)
- calc.exe (PID: 3104)
- sylsplvc.exe (PID: 3116)
- vbc.exe (PID: 3536)
- RegSvcs.exe (PID: 2560)
- 4363463463464363463463463.bin.exe (PID: 1732)
- RegSvcs.exe (PID: 3120)
- RegSvcs.exe (PID: 3196)
- heaoyam78.exe (PID: 3868)
- ms_tool.exe (PID: 3632)
- 5up4SW7.exe (PID: 2020)
- bitrixreportlib.exe (PID: 1924)
- more.exe (PID: 5084)
Unusual connection from system programs
- vbc.exe (PID: 3536)
AMADEY has been detected (SURICATA)
- InstallUtil.exe (PID: 3832)
Malware-specific behavior (creating "System.dll" in Temp)
- RestoroSetup64.exe (PID: 2388)
Process checks whether UAC notifications are on
- cp.exe (PID: 3764)
- AdobeUpdateres.exe (PID: 3640)
PARALLAX has been detected (SURICATA)
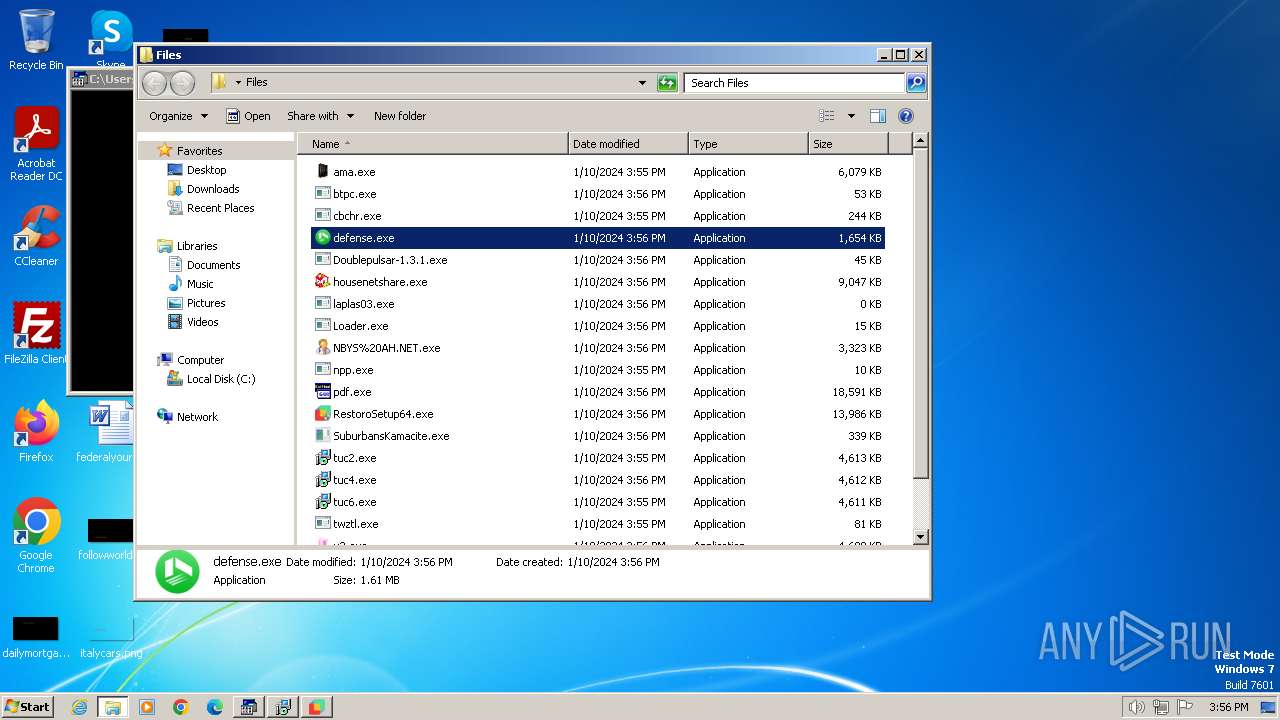
- defense.exe (PID: 2084)
Reads product name
- defense.exe (PID: 2084)
Application launched itself
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 3744)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 3452)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 896)
- more.exe (PID: 2572)
- msedge.exe (PID: 1072)
- msedge.exe (PID: 3348)
- msedge.exe (PID: 896)
- msedge.exe (PID: 3496)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 4304)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4660)
- more.exe (PID: 3404)
STEALC has been detected (SURICATA)
- syncUpd.exe (PID: 4072)
Reads mouse settings
- 3Eb73mM.exe (PID: 1880)
Checks for external IP
- 5up4SW7.exe (PID: 2020)
RISEPRO has been detected (SURICATA)
- 5up4SW7.exe (PID: 2020)
Steals credentials
- 5up4SW7.exe (PID: 2020)
SOCKS5SYSTEMZ has been detected (SURICATA)
- bitrixreportlib.exe (PID: 1924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3104) calc.exe
C2 (1)89.23.100.93
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexoonrejgwedvxwse
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureQjWeZe4F4TuWy0hUx2CJx3viPXMuRkFhkXGrVGT29pa7LM+06mEXhUkglBWpLmYPaFBKG5FEqOime2j0+7Cf0hyosj2teh9TnTiRihwU6ooSTFBg9MLZW6DOqN3NYbQAxzaJZu29Z/KHkeaWOVYrTDURnnk62Z+gzdMHhMH1F5k=
Keys
AES30514d0354cda998b840312f75ae05f11383b533e04a6b2d1084a39d2adc412e
SaltVenomRATByVenom
RedLine
(PID) Process(2536) v2.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
(PID) Process(2560) RegSvcs.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
(PID) Process(3632) ms_tool.exe
C2 (1)20.79.30.95:13856
BotnetLiveTraffic
Version1
(PID) Process(3120) RegSvcs.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
222
Monitored processes
132
Malicious processes
20
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\4363463463464363463463463.bin.exe" | C:\Users\admin\Desktop\4363463463464363463463463.bin.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 296 | "C:\Users\admin\Desktop\Files\VoidRAT.exe" | C:\Users\admin\Desktop\Files\VoidRAT.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 9.3.2.4 Modules
| |||||||||||||||
| 532 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0x178,0x17c,0x180,0x14c,0x194,0x6596f598,0x6596f5a8,0x6596f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 632 | "C:\Users\admin\AppData\Local\Temp\is-DFPM0.tmp\tuc6.tmp" /SL5="$2012E,4469780,54272,C:\Users\admin\Desktop\Files\tuc6.exe" | C:\Users\admin\AppData\Local\Temp\is-DFPM0.tmp\tuc6.tmp | — | tuc6.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 840 | "C:\Users\admin\Desktop\Files\housenetshare.exe" | C:\Users\admin\Desktop\Files\housenetshare.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 896 | "C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe" | C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 896 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.youtube.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | 3Eb73mM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://accounts.google.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | 3Eb73mM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1196 | "C:\Users\admin\Desktop\Files\npp.exe" | C:\Users\admin\Desktop\Files\npp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe" | C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe | — | 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
40 144
Read events
39 709
Write events
432
Delete events
3
Modification events
| (PID) Process: | (2268) 4363463463464363463463463.bin.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2268) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2268) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (1732) 4363463463464363463463463.bin.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1732) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1732) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1732) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1732) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2268) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2268) 4363463463464363463463463.bin.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
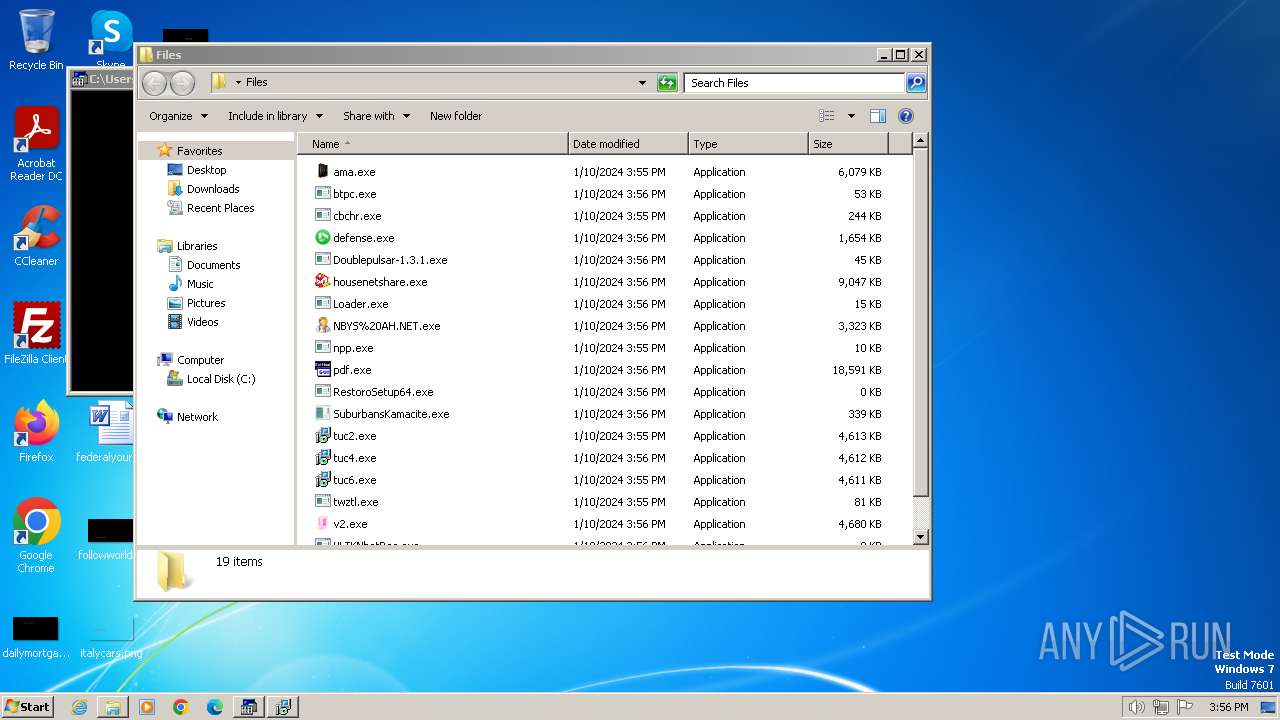
Executable files
282
Suspicious files
156
Text files
95
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Temp\is-B0DTD.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\basscd.dll | executable | |
MD5:F0F973781B6A66ADF354B04A36C5E944 | SHA256:04AB613C895B35044AF8A9A98A372A5769C80245CC9D6BF710A94C5BC42FA1B3 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\is-QNGNJ.tmp | executable | |
MD5:4E35BA785CD3B37A3702E577510F39E3 | SHA256:0AFE688B6FCA94C69780F454BE65E12D616C6E6376E80C5B3835E3FA6DE3EB8A | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\is-OEOSU.tmp | executable | |
MD5:8EE91149989D50DFCF9DAD00DF87C9B0 | SHA256:3030E22F4A854E11A8AA2128991E4867CA1DF33BC7B9AFF76A5E6DEEF56927F6 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\is-D8O6L.tmp | executable | |
MD5:F0F973781B6A66ADF354B04A36C5E944 | SHA256:04AB613C895B35044AF8A9A98A372A5769C80245CC9D6BF710A94C5BC42FA1B3 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\bassmix.dll | executable | |
MD5:8EE91149989D50DFCF9DAD00DF87C9B0 | SHA256:3030E22F4A854E11A8AA2128991E4867CA1DF33BC7B9AFF76A5E6DEEF56927F6 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\bin\x86\is-H76IL.tmp | executable | |
MD5:9FF783BB73F8868FA6599CDE65ED21D7 | SHA256:E0234AF5F71592C472439536E710BA8105D62DFA68722965DF87FED50BAB1816 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Temp\is-B0DTD.tmp\_isetup\_isdecmp.dll | executable | |
MD5:A813D18268AFFD4763DDE940246DC7E5 | SHA256:E19781AABE466DD8779CB9C8FA41BBB73375447066BB34E876CF388A6ED63C64 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Temp\is-B0DTD.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 632 | tuc6.tmp | C:\Users\admin\AppData\Local\Bitrix Report LIB\is-OBHIT.tmp | executable | |
MD5:1172A227DB98406391B2E76AED087E82 | SHA256:F6F6A91592E0137AEF38A7731D1849E5DCA11E4B53AA3CAEE4E4F8DC4E8B7752 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
409
DNS requests
57
Threats
160
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2268 | 4363463463464363463463463.bin.exe | GET | — | 211.181.24.132:80 | http://brusuax.com/dl/build2.exe | unknown | — | — | unknown |
1732 | 4363463463464363463463463.bin.exe | GET | 200 | 89.23.98.92:80 | http://89.23.98.92/file4/pdf.exe | unknown | executable | 18.1 Mb | unknown |
2268 | 4363463463464363463463463.bin.exe | GET | 200 | 185.215.113.84:80 | http://185.215.113.84/twztl.exe | unknown | executable | 80.5 Kb | unknown |
2268 | 4363463463464363463463463.bin.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/npp.exe | unknown | executable | 9.50 Kb | unknown |
2268 | 4363463463464363463463463.bin.exe | GET | 200 | 185.172.128.32:80 | http://185.172.128.32/ama.exe | unknown | executable | 5.94 Mb | unknown |
2580 | syspolrvcs.exe | GET | — | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
2620 | npp.exe | GET | 404 | 185.215.113.84:80 | http://twizt.net/newtpp.exe | unknown | html | 564 b | unknown |
2620 | npp.exe | GET | 200 | 185.215.113.84:80 | http://twizt.net/peinstall.php | unknown | html | 564 b | unknown |
1196 | npp.exe | GET | 404 | 185.215.113.84:80 | http://twizt.net/newtpp.exe | unknown | html | 564 b | unknown |
2580 | syspolrvcs.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | binary | 79.7 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2268 | 4363463463464363463463463.bin.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2268 | 4363463463464363463463463.bin.exe | 211.181.24.132:80 | brusuax.com | LG DACOM Corporation | KR | unknown |
1732 | 4363463463464363463463463.bin.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1732 | 4363463463464363463463463.bin.exe | 104.21.46.59:443 | cream.hitsturbo.com | CLOUDFLARENET | — | unknown |
1732 | 4363463463464363463463463.bin.exe | 89.23.98.92:80 | — | LLC Smart Ape | RU | unknown |
2268 | 4363463463464363463463463.bin.exe | 185.215.113.84:80 | twizt.net | 1337team Limited | SC | unknown |
2268 | 4363463463464363463463463.bin.exe | 185.215.113.66:80 | — | 1337team Limited | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
brusuax.com |
| unknown |
cream.hitsturbo.com |
| malicious |
twizt.net |
| unknown |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
lang.topteamlife.com |
| malicious |
www.update.microsoft.com |
| whitelisted |
stdown.dinju.com |
| malicious |
frezzyhook.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2268 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2268 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2268 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1732 | 4363463463464363463463463.bin.exe | A Network Trojan was detected | ET HUNTING Suspicious Request for Pdf.exe Observed in Zeus/Luminosity Link |
1732 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1732 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1732 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
1732 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1732 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1732 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
12 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.bin.exe | An exception occurred during a WebClient request.
|
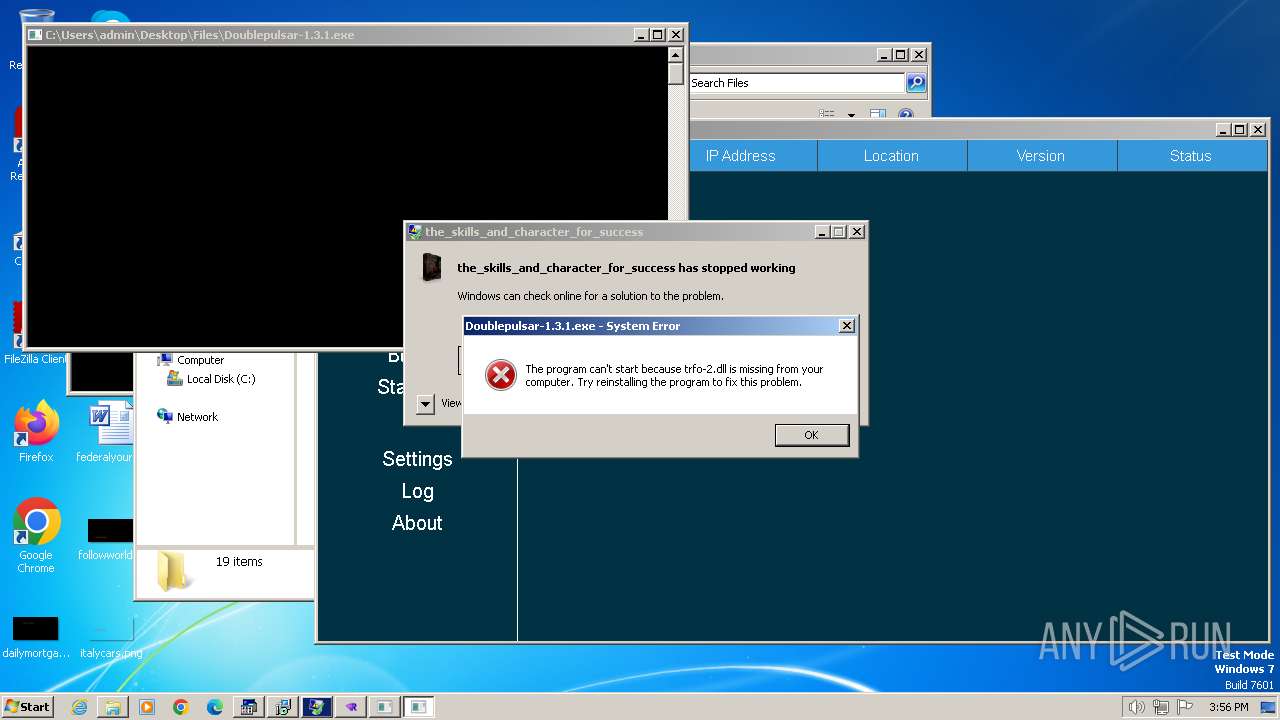
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | The request was aborted: Could not create SSL/TLS secure channel.
|