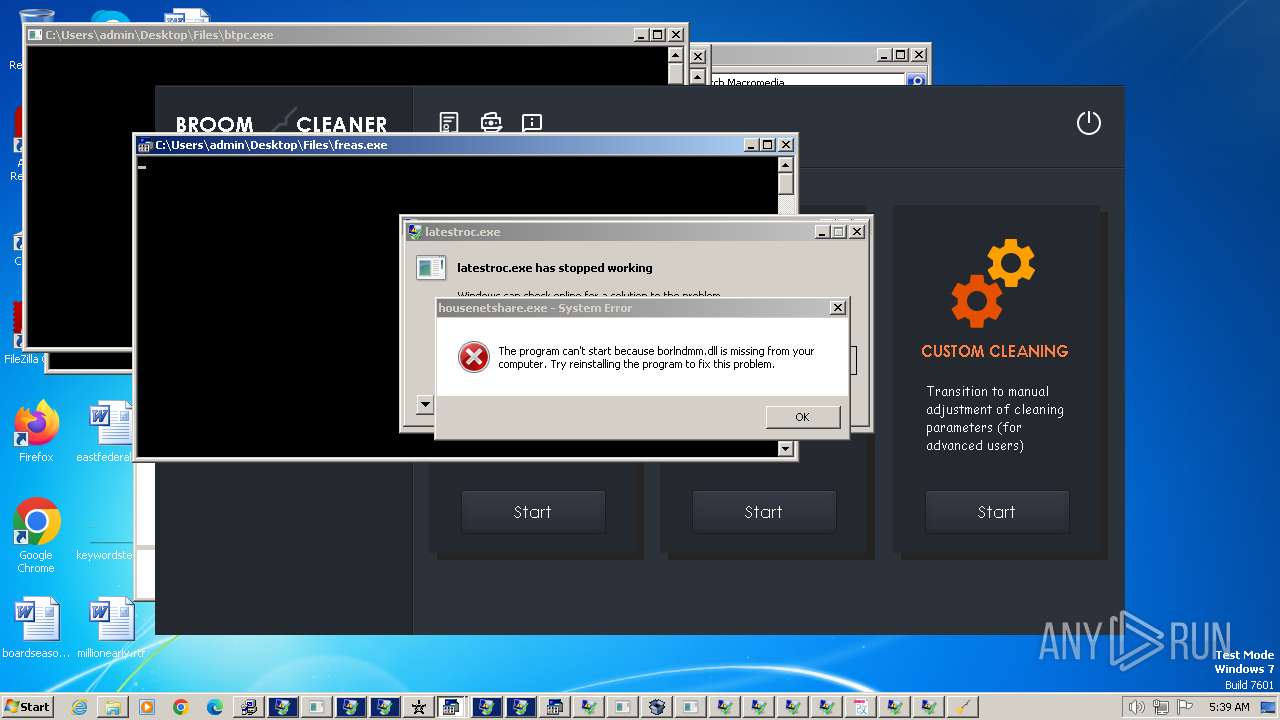
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/e06222b2-c568-47e1-9f7d-811e4a86de21 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 15, 2024, 05:36:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- payload.exe (PID: 3500)
- peterzx.exe (PID: 1824)
- net.exe (PID: 1860)
- 4363463463464363463463463.exe (PID: 2848)
- BBLb.exe (PID: 2248)
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- costa.exe (PID: 2584)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- cp.exe (PID: 3104)
- fund.exe (PID: 3452)
- STAR.exe (PID: 2916)
- comSvc.exe (PID: 2948)
- conhost.exe (PID: 1768)
- IMEDICTUPDATE.exe (PID: 4848)
- peinf.exe (PID: 4772)
- 2464713057.exe (PID: 5516)
- Client.exe (PID: 5532)
- april.exe (PID: 5716)
- april.tmp (PID: 5724)
- screenrecorderext.exe (PID: 5824)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
- univ.exe (PID: 6124)
- more.exe (PID: 5480)
- amert.exe (PID: 4656)
- bin.exe (PID: 864)
- more.exe (PID: 2512)
- M5traider.exe (PID: 4800)
- Archevod_XWorm.exe (PID: 4152)
- InstallSetup8.exe (PID: 5800)
- latestroc.exe (PID: 6100)
- GorgeousMovement.exe (PID: 2044)
- cmd.exe (PID: 3868)
- loader.exe (PID: 4136)
- rhsgn_protected.exe (PID: 5288)
- ARA.exe (PID: 5032)
- Msblockreview.exe (PID: 6140)
- amd.exe (PID: 6548)
- svshost.exe (PID: 11444)
- WinlockerBuilderv5.exe (PID: 11060)
- upx_compresser.exe (PID: 12204)
- jusched.exe (PID: 11560)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2848)
Changes the autorun value in the registry
- peterzx.exe (PID: 1824)
- images.exe (PID: 3032)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
- Archevod_XWorm.exe (PID: 4152)
- 2464713057.exe (PID: 5516)
- WinlockerBuilderv5.exe (PID: 11060)
Actions looks like stealing of personal data
- peterzx.exe (PID: 1824)
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- STAR.exe (PID: 2916)
- bott.exe (PID: 764)
- RegSvcs.exe (PID: 3924)
- dialer.exe (PID: 4932)
- Accommodations.pif (PID: 2988)
- jsc.exe (PID: 5180)
Steals credentials from Web Browsers
- peterzx.exe (PID: 1824)
- STAR.exe (PID: 2916)
- bott.exe (PID: 764)
- RegSvcs.exe (PID: 3924)
- Accommodations.pif (PID: 2988)
STEALC has been detected (SURICATA)
- timeSync.exe (PID: 2432)
- nsvEF93.tmp (PID: 3592)
Connects to the CnC server
- timeSync.exe (PID: 2432)
- rgAcb2.exe (PID: 3084)
- bott.exe (PID: 764)
- Fnnox9_zFu.exe (PID: 2348)
- 2464713057.exe (PID: 5516)
- 1646118701.exe (PID: 3128)
- J2HSOLz.exe (PID: 6000)
- jsc.exe (PID: 5180)
- nsvEF93.tmp (PID: 3592)
- WeChat.exe (PID: 4532)
- screenrecorderext.exe (PID: 5928)
Run PowerShell with an invisible window
- powershell.exe (PID: 1020)
- powershell.exe (PID: 952)
Bypass execution policy to execute commands
- powershell.exe (PID: 1020)
- powershell.exe (PID: 952)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 3508)
- powershell.exe (PID: 3952)
- powershell.exe (PID: 5336)
AGENTTESLA has been detected (YARA)
- peterzx.exe (PID: 1824)
- RegSvcs.exe (PID: 3924)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 448)
AZORULT has been detected (SURICATA)
- rgAcb2.exe (PID: 3084)
- Fnnox9_zFu.exe (PID: 2348)
- J2HSOLz.exe (PID: 6000)
Changes the login/logoff helper path in the registry
- images.exe (PID: 3032)
Creates a writable file in the system directory
- images.exe (PID: 3032)
REDLINE has been detected (SURICATA)
- bott.exe (PID: 764)
- STAR.exe (PID: 2916)
Create files in the Startup directory
- STAR.exe (PID: 2916)
- Archevod_XWorm.exe (PID: 4152)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 5156)
- wscript.exe (PID: 5076)
- wscript.exe (PID: 5276)
Adds path to the Windows Defender exclusion list
- conhost.exe (PID: 1768)
- comSvc.exe (PID: 2948)
- more.exe (PID: 5480)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
Unusual connection from system programs
- vbc.exe (PID: 2304)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4156)
Changes Security Center notification settings
- 2464713057.exe (PID: 5516)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
METASTEALER has been detected (YARA)
- vbc.exe (PID: 2304)
PHORPIEX has been detected (SURICATA)
- 2464713057.exe (PID: 5516)
- 4363463463464363463463463.exe (PID: 2848)
- 1646118701.exe (PID: 3128)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
ASYNCRAT has been detected (SURICATA)
- 666.exe (PID: 5756)
RISEPRO has been detected (YARA)
- ladas.exe (PID: 896)
- StealerClient_Cpp_1_3.exe (PID: 1340)
- dota.exe (PID: 3268)
ASYNCRAT has been detected (MUTEX)
- more.exe (PID: 2512)
- images.exe (PID: 2208)
Changes powershell execution policy (Bypass)
- Archevod_XWorm.exe (PID: 4152)
Adds process to the Windows Defender exclusion list
- Archevod_XWorm.exe (PID: 4152)
AMADEY has been detected (SURICATA)
- MSI.CentralServer.exe (PID: 3640)
Deletes a file (SCRIPT)
- wscript.exe (PID: 5076)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1840)
- findstr.exe (PID: 2592)
ARECHCLIENT2 has been detected (SURICATA)
- jsc.exe (PID: 5180)
SOCKS5SYSTEMZ has been detected (SURICATA)
- screenrecorderext.exe (PID: 5928)
ASYNCRAT has been detected (YARA)
- 666.exe (PID: 5756)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2848)
- payload.exe (PID: 3500)
- peterzx.exe (PID: 1824)
- timeSync.exe (PID: 2432)
- net.exe (PID: 1860)
- data64_5.exe (PID: 2260)
- powershell.exe (PID: 1020)
- rgAcb2.exe (PID: 3084)
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- costa.exe (PID: 2584)
- powershell.exe (PID: 952)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- Fnnox9_zFu.exe (PID: 2348)
- fund.exe (PID: 3452)
- STAR.exe (PID: 2916)
- Update.exe (PID: 3508)
- wscript.exe (PID: 3152)
- conhost.exe (PID: 1768)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2100)
- RegSvcs.exe (PID: 3924)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 3352)
- powershell.exe (PID: 3452)
- powershell.exe (PID: 840)
- powershell.exe (PID: 880)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 2376)
- powershell.exe (PID: 124)
- powershell.exe (PID: 3660)
- comSvc.exe (PID: 2948)
- powershell.exe (PID: 2548)
- powershell.exe (PID: 1596)
- IMEDICTUPDATE.exe (PID: 4848)
- peinf.exe (PID: 4772)
- more.exe (PID: 5480)
- Client.exe (PID: 5532)
- r.exe (PID: 5744)
- 2464713057.exe (PID: 5516)
- J2HSOLz.exe (PID: 6000)
- univ.exe (PID: 6124)
- ama.exe (PID: 5416)
- 1646118701.exe (PID: 3128)
- powershell.exe (PID: 4432)
- 1215810780.exe (PID: 4660)
- MSI.CentralServer.exe (PID: 3640)
- more.exe (PID: 2512)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 3508)
- powershell.exe (PID: 5336)
- powershell.exe (PID: 3952)
- latestroc.exe (PID: 6100)
- InstallSetup8.exe (PID: 5800)
- GorgeousMovement.exe (PID: 2044)
- 308143995.exe (PID: 5944)
- beacon_wlan0.exe (PID: 4460)
- 1279328281.exe (PID: 4476)
- loader.exe (PID: 4136)
- powershell.exe (PID: 2652)
- rhsgn_protected.exe (PID: 5288)
- ARA.exe (PID: 5032)
- Accommodations.pif (PID: 2988)
- nsvEF93.tmp (PID: 3592)
- wscript.exe (PID: 5276)
- Msblockreview.exe (PID: 6140)
- latestroc.exe (PID: 6996)
- screenrecorderext.exe (PID: 5928)
- amd.exe (PID: 6548)
- WinlockerBuilderv5.exe (PID: 11060)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2848)
- peterzx.exe (PID: 1824)
- Update.exe (PID: 3508)
- RegSvcs.exe (PID: 3924)
- r.exe (PID: 5744)
- 666.exe (PID: 5756)
- WeChat.exe (PID: 4532)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2848)
- peterzx.exe (PID: 1824)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2848)
- payload.exe (PID: 3500)
- net.exe (PID: 1860)
- timeSync.exe (PID: 2432)
- rgAcb2.exe (PID: 3084)
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- costa.exe (PID: 2584)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- fund.exe (PID: 3452)
- Fnnox9_zFu.exe (PID: 2348)
- conhost.exe (PID: 1768)
- comSvc.exe (PID: 2948)
- peinf.exe (PID: 4772)
- IMEDICTUPDATE.exe (PID: 4848)
- STAR.exe (PID: 2916)
- more.exe (PID: 5480)
- Client.exe (PID: 5532)
- 2464713057.exe (PID: 5516)
- r.exe (PID: 5744)
- J2HSOLz.exe (PID: 6000)
- univ.exe (PID: 6124)
- ama.exe (PID: 5416)
- 1215810780.exe (PID: 4660)
- more.exe (PID: 2512)
- MSI.CentralServer.exe (PID: 3640)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
- latestroc.exe (PID: 6100)
- InstallSetup8.exe (PID: 5800)
- 1646118701.exe (PID: 3128)
- GorgeousMovement.exe (PID: 2044)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
- loader.exe (PID: 4136)
- ARA.exe (PID: 5032)
- rhsgn_protected.exe (PID: 5288)
- Accommodations.pif (PID: 2988)
- nsvEF93.tmp (PID: 3592)
- Msblockreview.exe (PID: 6140)
- amd.exe (PID: 6548)
- screenrecorderext.exe (PID: 5928)
- WinlockerBuilderv5.exe (PID: 11060)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2848)
- payload.exe (PID: 3500)
- peterzx.exe (PID: 1824)
- net.exe (PID: 1860)
- BBLb.exe (PID: 2248)
- dialer.exe (PID: 448)
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- costa.exe (PID: 2584)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- cp.exe (PID: 3104)
- dialer.exe (PID: 4000)
- fund.exe (PID: 3452)
- STAR.exe (PID: 2916)
- comSvc.exe (PID: 2948)
- conhost.exe (PID: 1768)
- IMEDICTUPDATE.exe (PID: 4848)
- 2464713057.exe (PID: 5516)
- peinf.exe (PID: 4772)
- Client.exe (PID: 5532)
- april.tmp (PID: 5724)
- april.exe (PID: 5716)
- screenrecorderext.exe (PID: 5824)
- dialer.exe (PID: 4932)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
- more.exe (PID: 5480)
- amert.exe (PID: 4656)
- univ.exe (PID: 6124)
- bin.exe (PID: 864)
- more.exe (PID: 2512)
- M5traider.exe (PID: 4800)
- latestroc.exe (PID: 6100)
- Archevod_XWorm.exe (PID: 4152)
- InstallSetup8.exe (PID: 5800)
- GorgeousMovement.exe (PID: 2044)
- cmd.exe (PID: 3868)
- loader.exe (PID: 4136)
- ARA.exe (PID: 5032)
- rhsgn_protected.exe (PID: 5288)
- Msblockreview.exe (PID: 6140)
- amd.exe (PID: 6548)
- svshost.exe (PID: 11444)
- WinlockerBuilderv5.exe (PID: 11060)
- jusched.exe (PID: 11560)
- upx_compresser.exe (PID: 12204)
Application launched itself
- peterzx.exe (PID: 2408)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 2148)
- net.exe (PID: 1860)
- data64_5.exe (PID: 3960)
- BBLb.exe (PID: 3324)
- rgAcb2.exe (PID: 908)
- lumma.exe (PID: 3060)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 292)
- AttributeString.exe (PID: 2648)
- native.exe (PID: 2316)
- MSBuild.exe (PID: 2128)
- Fnnox9_zFu.exe (PID: 2856)
- asdfg.exe (PID: 4500)
- net.exe (PID: 5092)
- ghjkl.exe (PID: 5240)
- J2HSOLz.exe (PID: 5980)
- more.exe (PID: 5480)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 1692)
- cmd.exe (PID: 924)
- cmd.exe (PID: 4272)
- images.exe (PID: 3984)
- upx_compresser.exe (PID: 12176)
- taskhost.exe (PID: 10852)
Checks for external IP
- peterzx.exe (PID: 1824)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2848)
- univ.exe (PID: 6124)
- InstallSetup8.exe (PID: 5800)
Windows Defender mutex has been found
- timeSync.exe (PID: 2432)
- nsvEF93.tmp (PID: 3592)
Accesses Microsoft Outlook profiles
- peterzx.exe (PID: 1824)
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- RegSvcs.exe (PID: 3924)
- dialer.exe (PID: 4932)
- Accommodations.pif (PID: 2988)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2848)
- 2464713057.exe (PID: 5516)
- 1215810780.exe (PID: 4660)
- MSI.CentralServer.exe (PID: 3640)
- InstallSetup8.exe (PID: 5800)
- 1646118701.exe (PID: 3128)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
- nsvEF93.tmp (PID: 3592)
Connects to SMTP port
- peterzx.exe (PID: 1824)
- RegSvcs.exe (PID: 3924)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- 4363463463464363463463463.exe (PID: 2848)
- dialer.exe (PID: 4932)
- WinlockerBuilderv5.exe (PID: 11060)
The process executes via Task Scheduler
- powershell.exe (PID: 1020)
- AttributeString.exe (PID: 2648)
- powershell.exe (PID: 952)
- msedge.exe (PID: 3272)
- msedge.exe (PID: 10832)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1020)
- powershell.exe (PID: 952)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2100)
- powershell.exe (PID: 3352)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 3452)
- powershell.exe (PID: 1560)
- powershell.exe (PID: 880)
- powershell.exe (PID: 3036)
- powershell.exe (PID: 2376)
- powershell.exe (PID: 124)
- powershell.exe (PID: 840)
- powershell.exe (PID: 3660)
- powershell.exe (PID: 2548)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 4432)
- powershell.exe (PID: 2192)
- powershell.exe (PID: 5336)
- powershell.exe (PID: 3952)
- powershell.exe (PID: 3508)
- powershell.exe (PID: 2652)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 2848)
- april.tmp (PID: 5724)
- univ.exe (PID: 6124)
- Archevod_XWorm.exe (PID: 4152)
- rhsgn_protected.exe (PID: 5288)
- svshost.exe (PID: 11444)
- WinlockerBuilderv5.exe (PID: 11060)
- jusched.exe (PID: 11560)
- upx_compresser.exe (PID: 12204)
Starts a Microsoft application from unusual location
- lumma1234.exe (PID: 1956)
- Archevod_XWorm.exe (PID: 4152)
- WinlockerBuilderv5.exe (PID: 11060)
- jusched.exe (PID: 11560)
- upx_compresser.exe (PID: 12176)
- upx_compresser.exe (PID: 12204)
Reads browser cookies
- dialer.exe (PID: 448)
- STAR.exe (PID: 2916)
- bott.exe (PID: 764)
- jsc.exe (PID: 5180)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- dialer.exe (PID: 4932)
Searches for installed software
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- STAR.exe (PID: 2916)
- bott.exe (PID: 764)
- dialer.exe (PID: 4932)
- 666.exe (PID: 5756)
- jsc.exe (PID: 5180)
- Accommodations.pif (PID: 2988)
Executed via WMI
- rgAcb2.exe (PID: 908)
- Fnnox9_zFu.exe (PID: 2856)
- schtasks.exe (PID: 2728)
- schtasks.exe (PID: 2092)
- schtasks.exe (PID: 2856)
- schtasks.exe (PID: 3500)
- schtasks.exe (PID: 2636)
- schtasks.exe (PID: 2744)
- schtasks.exe (PID: 2844)
- schtasks.exe (PID: 3892)
- schtasks.exe (PID: 4064)
- schtasks.exe (PID: 1624)
- schtasks.exe (PID: 1840)
- schtasks.exe (PID: 3352)
- schtasks.exe (PID: 3288)
- schtasks.exe (PID: 2864)
- schtasks.exe (PID: 3180)
- schtasks.exe (PID: 2760)
- schtasks.exe (PID: 3660)
- schtasks.exe (PID: 1560)
- schtasks.exe (PID: 2896)
- schtasks.exe (PID: 2232)
- schtasks.exe (PID: 1484)
- schtasks.exe (PID: 2968)
- schtasks.exe (PID: 2408)
- schtasks.exe (PID: 712)
- schtasks.exe (PID: 1936)
- schtasks.exe (PID: 3760)
- schtasks.exe (PID: 1504)
- schtasks.exe (PID: 3432)
- schtasks.exe (PID: 3108)
- schtasks.exe (PID: 3868)
- schtasks.exe (PID: 1736)
- schtasks.exe (PID: 2384)
- schtasks.exe (PID: 3412)
- schtasks.exe (PID: 3740)
- schtasks.exe (PID: 2312)
- schtasks.exe (PID: 3272)
- schtasks.exe (PID: 2540)
- schtasks.exe (PID: 1900)
- schtasks.exe (PID: 2068)
- J2HSOLz.exe (PID: 5980)
- schtasks.exe (PID: 2068)
- schtasks.exe (PID: 4356)
- schtasks.exe (PID: 1484)
- schtasks.exe (PID: 4716)
- schtasks.exe (PID: 5260)
- schtasks.exe (PID: 3988)
- schtasks.exe (PID: 1852)
- schtasks.exe (PID: 2532)
- schtasks.exe (PID: 5268)
- schtasks.exe (PID: 3896)
- schtasks.exe (PID: 2004)
- schtasks.exe (PID: 2340)
- schtasks.exe (PID: 4904)
- schtasks.exe (PID: 4852)
- schtasks.exe (PID: 4952)
- schtasks.exe (PID: 5332)
- schtasks.exe (PID: 1928)
- schtasks.exe (PID: 3816)
- schtasks.exe (PID: 5488)
- schtasks.exe (PID: 4280)
- schtasks.exe (PID: 4024)
- schtasks.exe (PID: 1636)
- schtasks.exe (PID: 5864)
- schtasks.exe (PID: 4792)
- schtasks.exe (PID: 6232)
- schtasks.exe (PID: 6204)
- schtasks.exe (PID: 6216)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2848)
- bott.exe (PID: 764)
- STAR.exe (PID: 2916)
- vbc.exe (PID: 2304)
- MSBuild.exe (PID: 1848)
- 666.exe (PID: 5756)
- 2464713057.exe (PID: 5516)
- RegSvcs.exe (PID: 5372)
- 1646118701.exe (PID: 3128)
- LostArk.exe (PID: 5612)
- Archevod_XWorm.exe (PID: 4152)
- beacon_wlan0.exe (PID: 4460)
- images.exe (PID: 2208)
- jsc.exe (PID: 5180)
- screenrecorderext.exe (PID: 5928)
Starts CMD.EXE for commands execution
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- images.exe (PID: 3032)
- wscript.exe (PID: 3152)
- RegAsm.exe (PID: 2532)
- Client.exe (PID: 5532)
- more.exe (PID: 2512)
- BroomSetup.exe (PID: 4192)
- cmd.exe (PID: 4272)
- GorgeousMovement.exe (PID: 2044)
- cmd.exe (PID: 924)
- wscript.exe (PID: 5276)
- Msblockreview.exe (PID: 6140)
Executing commands from a ".bat" file
- dusers.exe (PID: 2920)
- Users.exe (PID: 2636)
- wscript.exe (PID: 3152)
- Client.exe (PID: 5532)
- more.exe (PID: 2512)
- BroomSetup.exe (PID: 4192)
- wscript.exe (PID: 5276)
- Msblockreview.exe (PID: 6140)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3092)
- cmd.exe (PID: 1860)
- cmd.exe (PID: 4272)
Starts application with an unusual extension
- cmd.exe (PID: 1860)
- cmd.exe (PID: 4752)
- cmd.exe (PID: 4272)
- InstallSetup8.exe (PID: 5800)
The executable file from the user directory is run by the CMD process
- wmild.exe (PID: 1900)
- wmild.exe (PID: 2504)
- 666.exe (PID: 5756)
- images.exe (PID: 3984)
- Accommodations.pif (PID: 2988)
- Msblockreview.exe (PID: 6140)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1860)
Reads the BIOS version
- ladas.exe (PID: 896)
- amert.exe (PID: 4656)
- amd.exe (PID: 6548)
- Utsysc.exe (PID: 6764)
The process creates files with name similar to system file names
- images.exe (PID: 3032)
- 4363463463464363463463463.exe (PID: 2848)
- comSvc.exe (PID: 2948)
- bin.exe (PID: 864)
- Msblockreview.exe (PID: 6140)
- WinlockerBuilderv5.exe (PID: 11060)
Creates or modifies Windows services
- images.exe (PID: 3032)
The process executes VB scripts
- %40Natsu338_alice.exe (PID: 2044)
- IMEDICTUPDATE.exe (PID: 4848)
Script adds exclusion path to Windows Defender
- conhost.exe (PID: 1768)
- comSvc.exe (PID: 2948)
- more.exe (PID: 5480)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
Starts POWERSHELL.EXE for commands execution
- conhost.exe (PID: 1768)
- comSvc.exe (PID: 2948)
- more.exe (PID: 5480)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
Reads the date of Windows installation
- comSvc.exe (PID: 2948)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5076)
- wscript.exe (PID: 5156)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 5156)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 5076)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 5076)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3152)
- wscript.exe (PID: 5076)
- wscript.exe (PID: 5276)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5616)
- cmd.exe (PID: 4544)
Reads the Windows owner or organization settings
- april.tmp (PID: 5724)
Checks Windows Trust Settings
- r.exe (PID: 5744)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- r.exe (PID: 5744)
Starts itself from another location
- 1646118701.exe (PID: 3128)
- amd.exe (PID: 6548)
- WinlockerBuilderv5.exe (PID: 11060)
- upx_compresser.exe (PID: 12204)
Malware-specific behavior (creating "System.dll" in Temp)
- bin.exe (PID: 864)
Script adds exclusion process to Windows Defender
- Archevod_XWorm.exe (PID: 4152)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 5076)
Get information on the list of running processes
- cmd.exe (PID: 4272)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4272)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 3868)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6304)
Process creates executable files without a name
- WinlockerBuilderv5.exe (PID: 11060)
INFO
Reads the computer name
- 4363463463464363463463463.exe (PID: 2848)
- payload.exe (PID: 3500)
- data64_5.exe (PID: 3960)
- peterzx.exe (PID: 2408)
- net.exe (PID: 1860)
- peterzx.exe (PID: 1824)
- timeSync.exe (PID: 2432)
- BBLb.exe (PID: 3324)
- data64_5.exe (PID: 2260)
- BBLb.exe (PID: 2248)
- hncc.exe (PID: 1232)
- lumma1234.exe (PID: 1956)
- for.exe (PID: 2448)
- rgAcb2.exe (PID: 908)
- rgAcb2.exe (PID: 3084)
- native.exe (PID: 2316)
- AttributeString.exe (PID: 2648)
- dusers.exe (PID: 2920)
- AttributeString.exe (PID: 3892)
- Users.exe (PID: 2636)
- crypted.exe (PID: 2016)
- wmild.exe (PID: 1900)
- MSBuild.exe (PID: 2128)
- MSBuild.exe (PID: 1848)
- costa.exe (PID: 2584)
- wmild.exe (PID: 2504)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 3336)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- conhost.exe (PID: 1768)
- bott.exe (PID: 764)
- STAR.exe (PID: 2916)
- cp.exe (PID: 3104)
- Update.exe (PID: 3508)
- Fnnox9_zFu.exe (PID: 2856)
- Fnnox9_zFu.exe (PID: 2348)
- fund.exe (PID: 3452)
- qemu-ga.exe (PID: 2016)
- comSvc.exe (PID: 2948)
- vbc.exe (PID: 2304)
- kb^fr_ouverture.exe (PID: 4084)
- RegSvcs.exe (PID: 3924)
- dota.exe (PID: 3268)
- asdfg.exe (PID: 4500)
- IMEDICTUPDATE.exe (PID: 4848)
- net.exe (PID: 5092)
- ghjkl.exe (PID: 5240)
- Client.exe (PID: 5532)
- more.exe (PID: 5480)
- 666.exe (PID: 5756)
- april.tmp (PID: 5724)
- r.exe (PID: 5744)
- 2464713057.exe (PID: 5516)
- screenrecorderext.exe (PID: 5824)
- J2HSOLz.exe (PID: 6000)
- J2HSOLz.exe (PID: 5980)
- univ.exe (PID: 6124)
- yava.exe (PID: 3604)
- ama.exe (PID: 5416)
- bin.exe (PID: 864)
- daissss.exe (PID: 2120)
- 1646118701.exe (PID: 3128)
- more.exe (PID: 2512)
- amert.exe (PID: 4656)
- M5traider.exe (PID: 4800)
- 1215810780.exe (PID: 4660)
- peinf.exe (PID: 4772)
- Archevod_XWorm.exe (PID: 4152)
- MSI.CentralServer.exe (PID: 3640)
- images.exe (PID: 3984)
- RegSvcs.exe (PID: 5372)
- IMEDICTUPDATE.exe (PID: 5628)
- latestroc.exe (PID: 6100)
- LostArk.exe (PID: 5612)
- BroomSetup.exe (PID: 4192)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5848)
- InstallSetup8.exe (PID: 5800)
- hv.exe (PID: 6136)
- GorgeousMovement.exe (PID: 2044)
- 308143995.exe (PID: 5944)
- Accommodations.pif (PID: 2988)
- beacon_wlan0.exe (PID: 4460)
- 1279328281.exe (PID: 4476)
- loader.exe (PID: 4136)
- images.exe (PID: 2208)
- rhsgn_protected.exe (PID: 5288)
- ARA.exe (PID: 5032)
- nsvEF93.tmp (PID: 3592)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- msedge.exe (PID: 3272)
- WeChat.exe (PID: 4532)
- amd.exe (PID: 6548)
- screenrecorderext.exe (PID: 5928)
- latestroc.exe (PID: 6996)
- msedge.exe (PID: 10832)
- WinlockerBuilderv5.exe (PID: 11060)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2848)
- payload.exe (PID: 3500)
- peterzx.exe (PID: 2408)
- peterzx.exe (PID: 1824)
- data64_5.exe (PID: 3960)
- qt51crk.exe (PID: 748)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 2148)
- net.exe (PID: 1860)
- timeSync.exe (PID: 2432)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 2904)
- BBLb.exe (PID: 3324)
- net.exe (PID: 1368)
- data64_5.exe (PID: 2260)
- BBLb.exe (PID: 2248)
- hncc.exe (PID: 1232)
- lumma1234.exe (PID: 1956)
- RegAsm.exe (PID: 1652)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 3020)
- rgAcb2.exe (PID: 908)
- for.exe (PID: 2448)
- wmlaunch.exe (PID: 3768)
- rgAcb2.exe (PID: 3084)
- lumma.exe (PID: 3060)
- cp.exe (PID: 3104)
- native.exe (PID: 2316)
- lumma.exe (PID: 3056)
- AttributeString.exe (PID: 2648)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 292)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 1388)
- native.exe (PID: 1692)
- 659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe (PID: 1696)
- dusers.exe (PID: 2920)
- AttributeString.exe (PID: 3892)
- Users.exe (PID: 2636)
- crypted.exe (PID: 2016)
- RegAsm.exe (PID: 2148)
- chcp.com (PID: 2724)
- wmild.exe (PID: 1900)
- StealerClient_Cpp_1_4.exe (PID: 3200)
- wmild.exe (PID: 2504)
- MSBuild.exe (PID: 2128)
- MSBuild.exe (PID: 1848)
- costa.exe (PID: 2584)
- ladas.exe (PID: 896)
- fortnite2.exe (PID: 3368)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 3336)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- 891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe (PID: 3416)
- conhost.exe (PID: 1768)
- bott.exe (PID: 764)
- STAR.exe (PID: 2916)
- Update.exe (PID: 3508)
- Fnnox9_zFu.exe (PID: 2348)
- Fnnox9_zFu.exe (PID: 2856)
- qemu-ga.exe (PID: 2016)
- fund.exe (PID: 3452)
- comSvc.exe (PID: 2948)
- StealerClient_Cpp_1_3.exe (PID: 1340)
- %40Natsu338_alice.exe (PID: 2044)
- vbc.exe (PID: 2304)
- kb^fr_ouverture.exe (PID: 4084)
- RegSvcs.exe (PID: 3924)
- dota.exe (PID: 3268)
- asdfg.exe (PID: 4500)
- IMEDICTUPDATE.exe (PID: 4848)
- peinf.exe (PID: 4772)
- asdfg.exe (PID: 4680)
- net.exe (PID: 5092)
- net.exe (PID: 5228)
- ghjkl.exe (PID: 5240)
- dart.exe (PID: 5504)
- 2464713057.exe (PID: 5516)
- Client.exe (PID: 5532)
- ama.exe (PID: 5416)
- more.exe (PID: 5480)
- april.exe (PID: 5716)
- april.tmp (PID: 5724)
- r.exe (PID: 5744)
- 666.exe (PID: 5756)
- screenrecorderext.exe (PID: 5824)
- screenrecorderext.exe (PID: 5928)
- adm_atu.exe (PID: 6052)
- J2HSOLz.exe (PID: 5980)
- J2HSOLz.exe (PID: 6000)
- univ.exe (PID: 6124)
- yava.exe (PID: 3604)
- 1646118701.exe (PID: 3128)
- MSI.CentralServer.exe (PID: 3640)
- bin.exe (PID: 864)
- amert.exe (PID: 4656)
- 1215810780.exe (PID: 4660)
- current.exe (PID: 2036)
- daissss.exe (PID: 2120)
- 2819926445.exe (PID: 4628)
- more.exe (PID: 2512)
- M5traider.exe (PID: 4800)
- 1279117914.exe (PID: 1560)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 1692)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 4308)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
- RegSvcs.exe (PID: 5372)
- fileren.exe (PID: 5280)
- IMEDICTUPDATE.exe (PID: 5628)
- LostArk.exe (PID: 5612)
- latestroc.exe (PID: 6100)
- InstallSetup8.exe (PID: 5800)
- toolspub1.exe (PID: 5420)
- BroomSetup.exe (PID: 4192)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5848)
- hv.exe (PID: 6136)
- chcp.com (PID: 5500)
- GorgeousMovement.exe (PID: 2044)
- Accommodations.pif (PID: 2988)
- loader.exe (PID: 4136)
- 3301218282.exe (PID: 4328)
- beacon_wlan0.exe (PID: 4460)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
- images.exe (PID: 2208)
- rhsgn_protected.exe (PID: 5288)
- 407510414.exe (PID: 2996)
- ARA.exe (PID: 5032)
- nsvEF93.tmp (PID: 3592)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- msedge.exe (PID: 3272)
- WeChat.exe (PID: 4532)
- amd.exe (PID: 6548)
- Utsysc.exe (PID: 6764)
- latestroc.exe (PID: 6996)
- msedge.exe (PID: 10832)
- WinlockerBuilderv5.exe (PID: 11060)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2848)
- peterzx.exe (PID: 2408)
- payload.exe (PID: 3500)
- peterzx.exe (PID: 1824)
- net.exe (PID: 1860)
- BBLb.exe (PID: 3324)
- data64_5.exe (PID: 2260)
- timeSync.exe (PID: 2432)
- BBLb.exe (PID: 2248)
- hncc.exe (PID: 1232)
- rgAcb2.exe (PID: 908)
- wmlaunch.exe (PID: 3768)
- rgAcb2.exe (PID: 3084)
- AttributeString.exe (PID: 2648)
- native.exe (PID: 2316)
- AttributeString.exe (PID: 3892)
- MSBuild.exe (PID: 2128)
- MSBuild.exe (PID: 1848)
- costa.exe (PID: 2584)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 3336)
- bott.exe (PID: 764)
- STAR.exe (PID: 2916)
- images.exe (PID: 3032)
- conhost.exe (PID: 1768)
- Update.exe (PID: 3508)
- cp.exe (PID: 3104)
- Fnnox9_zFu.exe (PID: 2856)
- Fnnox9_zFu.exe (PID: 2348)
- comSvc.exe (PID: 2948)
- vbc.exe (PID: 2304)
- RegSvcs.exe (PID: 3924)
- IMEDICTUPDATE.exe (PID: 4848)
- asdfg.exe (PID: 4500)
- peinf.exe (PID: 4772)
- ghjkl.exe (PID: 5240)
- net.exe (PID: 5092)
- more.exe (PID: 5480)
- Client.exe (PID: 5532)
- 666.exe (PID: 5756)
- 2464713057.exe (PID: 5516)
- r.exe (PID: 5744)
- J2HSOLz.exe (PID: 6000)
- J2HSOLz.exe (PID: 5980)
- univ.exe (PID: 6124)
- yava.exe (PID: 3604)
- daissss.exe (PID: 2120)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
- amert.exe (PID: 4656)
- more.exe (PID: 2512)
- M5traider.exe (PID: 4800)
- MSI.CentralServer.exe (PID: 3640)
- Archevod_XWorm.exe (PID: 4152)
- images.exe (PID: 3984)
- RegSvcs.exe (PID: 5372)
- IMEDICTUPDATE.exe (PID: 5628)
- LostArk.exe (PID: 5612)
- latestroc.exe (PID: 6100)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 5848)
- InstallSetup8.exe (PID: 5800)
- 308143995.exe (PID: 5944)
- beacon_wlan0.exe (PID: 4460)
- 1279328281.exe (PID: 4476)
- Accommodations.pif (PID: 2988)
- images.exe (PID: 2208)
- nsvEF93.tmp (PID: 3592)
- hv.exe (PID: 6136)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- msedge.exe (PID: 3272)
- WeChat.exe (PID: 4532)
- latestroc.exe (PID: 6996)
- amd.exe (PID: 6548)
- WinlockerBuilderv5.exe (PID: 11060)
- msedge.exe (PID: 10832)
- screenrecorderext.exe (PID: 5928)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2848)
- peterzx.exe (PID: 1824)
- data64_5.exe (PID: 2260)
- rgAcb2.exe (PID: 3084)
- STAR.exe (PID: 2916)
- Fnnox9_zFu.exe (PID: 2348)
- bott.exe (PID: 764)
- Update.exe (PID: 3508)
- comSvc.exe (PID: 2948)
- RegSvcs.exe (PID: 3924)
- IMEDICTUPDATE.exe (PID: 4848)
- Client.exe (PID: 5532)
- 666.exe (PID: 5756)
- J2HSOLz.exe (PID: 6000)
- r.exe (PID: 5744)
- IMEDICTUPDATE.exe (PID: 5628)
- LostArk.exe (PID: 5612)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- latestroc.exe (PID: 6996)
- WinlockerBuilderv5.exe (PID: 11060)
Create files in a temporary directory
- payload.exe (PID: 3500)
- net.exe (PID: 1860)
- peterzx.exe (PID: 1824)
- costa.exe (PID: 2584)
- cp.exe (PID: 3104)
- conhost.exe (PID: 1768)
- IMEDICTUPDATE.exe (PID: 4848)
- peinf.exe (PID: 4772)
- Client.exe (PID: 5532)
- april.exe (PID: 5716)
- april.tmp (PID: 5724)
- adm_atu.exe (PID: 6052)
- 2464713057.exe (PID: 5516)
- bin.exe (PID: 864)
- 1646118701.exe (PID: 3128)
- univ.exe (PID: 6124)
- amert.exe (PID: 4656)
- more.exe (PID: 5480)
- more.exe (PID: 2512)
- M5traider.exe (PID: 4800)
- LostArk.exe (PID: 5612)
- latestroc.exe (PID: 6100)
- InstallSetup8.exe (PID: 5800)
- GorgeousMovement.exe (PID: 2044)
- images.exe (PID: 3984)
- 308143995.exe (PID: 5944)
- loader.exe (PID: 4136)
- rhsgn_protected.exe (PID: 5288)
- 1279328281.exe (PID: 4476)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- amd.exe (PID: 6548)
- WinlockerBuilderv5.exe (PID: 11060)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2848)
- peterzx.exe (PID: 1824)
- Update.exe (PID: 3508)
- RegSvcs.exe (PID: 3924)
- r.exe (PID: 5744)
- 666.exe (PID: 5756)
- WeChat.exe (PID: 4532)
Creates files or folders in the user directory
- peterzx.exe (PID: 1824)
- BBLb.exe (PID: 2248)
- dialer.exe (PID: 448)
- Users.exe (PID: 2636)
- RegAsm.exe (PID: 2532)
- images.exe (PID: 3032)
- dialer.exe (PID: 4000)
- STAR.exe (PID: 2916)
- conhost.exe (PID: 1768)
- peinf.exe (PID: 4772)
- Client.exe (PID: 5532)
- april.tmp (PID: 5724)
- r.exe (PID: 5744)
- dialer.exe (PID: 4932)
- 2464713057.exe (PID: 5516)
- univ.exe (PID: 6124)
- more.exe (PID: 5480)
- bin.exe (PID: 864)
- more.exe (PID: 2512)
- Archevod_XWorm.exe (PID: 4152)
- LostArk.exe (PID: 5612)
- BroomSetup.exe (PID: 4192)
- InstallSetup8.exe (PID: 5800)
- 1646118701.exe (PID: 3128)
- 308143995.exe (PID: 5944)
- 1279328281.exe (PID: 4476)
- ARA.exe (PID: 5032)
- Accommodations.pif (PID: 2988)
Checks proxy server information
- timeSync.exe (PID: 2432)
- rgAcb2.exe (PID: 3084)
- images.exe (PID: 3032)
- Fnnox9_zFu.exe (PID: 2348)
- peinf.exe (PID: 4772)
- r.exe (PID: 5744)
- 2464713057.exe (PID: 5516)
- J2HSOLz.exe (PID: 6000)
- univ.exe (PID: 6124)
- 1646118701.exe (PID: 3128)
- 1215810780.exe (PID: 4660)
- MSI.CentralServer.exe (PID: 3640)
- InstallSetup8.exe (PID: 5800)
- 308143995.exe (PID: 5944)
- beacon_wlan0.exe (PID: 4460)
- 1279328281.exe (PID: 4476)
- Accommodations.pif (PID: 2988)
- nsvEF93.tmp (PID: 3592)
- screenrecorderext.exe (PID: 5928)
Drops the executable file immediately after the start
- dialer.exe (PID: 448)
- dialer.exe (PID: 4000)
- dialer.exe (PID: 4932)
Reads product name
- rgAcb2.exe (PID: 3084)
- STAR.exe (PID: 2916)
- bott.exe (PID: 764)
- Fnnox9_zFu.exe (PID: 2348)
- comSvc.exe (PID: 2948)
- IMEDICTUPDATE.exe (PID: 4848)
- J2HSOLz.exe (PID: 6000)
- r.exe (PID: 5744)
- IMEDICTUPDATE.exe (PID: 5628)
- jsc.exe (PID: 5180)
- Msblockreview.exe (PID: 6140)
- latestroc.exe (PID: 6996)
Reads security settings of Internet Explorer
- explorer.exe (PID: 128)
Reads the Internet Settings
- explorer.exe (PID: 128)
Creates files in the program directory
- comSvc.exe (PID: 2948)
- screenrecorderext.exe (PID: 5824)
- screenrecorderext.exe (PID: 5928)
- Msblockreview.exe (PID: 6140)
Creates a software uninstall entry
- april.tmp (PID: 5724)
Process checks whether UAC notifications are on
- LostArk.exe (PID: 5612)
- amd.exe (PID: 6548)
- Utsysc.exe (PID: 6764)
Reads mouse settings
- Accommodations.pif (PID: 2988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AgentTesla
(PID) Process(1824) peterzx.exe
Protocolsmtp
Hostmail.processengrg.com
Port587
Usernameinfo@processengrg.com
PasswordBigbrain2022#
(PID) Process(3924) RegSvcs.exe
Protocolsmtp
Hostmail.kabeercommodities.com
Port587
Usernameexport@kabeercommodities.com
Passwordw{A6H.o&sz%g
MetaStealer
(PID) Process(2304) vbc.exe
C2 (1)5.42.65.101:48790
Botnet1006580135-26990097-alice
Options
ErrorMessage
Keys
XorPyrometry
RisePro
(PID) Process(896) ladas.exe
C2193.233.132.62
(PID) Process(3268) dota.exe
C2193.233.132.62
AsyncRat
(PID) Process(5756) 666.exe
C2 (3)127.0.0.1
qiefuwuqi.20242525.xyz
175.24.197.196
Ports (1)53576
BotnetDefault
VersionLMTEAM RAT 远控 v10.0.0
Options
AutoRuntrue
Mutexencffhopetwiqlwo
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICNzCCAaCgAwIBAgIVAJ63XcWUSwHUfcXzH/xfUvbn7AsDMA0GCSqGSIb3DQEBDQUAMGgxFjAUBgNVBAMMDUxNVEVBTSBTZXJ2ZXIxEzARBgNVBAsMCnF3cWRhbmNodW4xHzAdBgNVBAoMFlZlbm9tUkFUIEJ5IHF3cWRhbmNodW4xCzAJBgNVBAcMAlNIMQswCQYDVQQGEwJDTjAeFw0yMjA4MjYwOTI0NTBaFw0zMzA2MDQwOTI0NTBaMBMxETAPBgNVBAMMCFZlbm9tUkFUMIGfMA0GCSqGSIb3DQEB...
Server_SignatureKWBGGJAAfUXEt4htszXVxNx6rIZYwNWWTPactiBeZQI02tJn/heGesmMrlvcl5TCgrFBPEXT+LY1evi6tKfAJojHRJxMJiCIuzuMLzZSFCXL+/1Tyic+u3d8BgIkZqFG02uBHURbw0FGvZcH4r1o7kJhIyHsUGw9ZBrY5ZjdYXs=
Keys
AES2b84f4b7ac2be24e77cb2c2a6f70cd0327feb801dbd467a427d95e614f77912a
SaltVenomRATByVenom
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
442
Monitored processes
300
Malicious processes
86
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | comSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 128 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | "C:\Users\admin\Desktop\Files\07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe" | C:\Users\admin\Desktop\Files\07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 448 | "C:\Windows\system32\dialer.exe" | C:\Windows\System32\dialer.exe | net.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Phone Dialer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | schtasks.exe /create /tn "qemu-gaq" /sc MINUTE /mo 13 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\qemu-ga.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | "C:\Users\admin\Desktop\Files\qt51crk.exe" | C:\Users\admin\Desktop\Files\qt51crk.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 764 | "C:\Users\admin\AppData\Roaming\configurationValue\bott.exe" | C:\Users\admin\AppData\Roaming\configurationValue\bott.exe | RegAsm.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: XHP Exit code: 0 Version: 12.9.1.22 Modules
| |||||||||||||||
| 840 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/Recovery/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | comSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 864 | "C:\Users\admin\Desktop\Files\bin.exe" | C:\Users\admin\Desktop\Files\bin.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: filerede partshringsregelen knallerist Exit code: 0 Version: 3.4.0.0 Modules
| |||||||||||||||
| 880 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/Users/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | comSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
273 856
Read events
243 771
Write events
29 936
Delete events
149
Modification events
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2848) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
243
Suspicious files
93
Text files
88
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe | executable | |
MD5:5A78962AF28AD4733562FBBE0B73C8AE | SHA256:865B3DB67F0565E0B41E72AA036D78183C33DAB95BD4BE7B4F13AEBDA88AB0C0 | |||
| 3500 | payload.exe | C:\Users\admin\AppData\Local\Temp\runtime-bind.exe | executable | |
MD5:679F7BB9C60003A65A6A98D474F3FB0E | SHA256:FE0C2C6438A5ED2DD338A52678B1D5BE0A63DE608BD360437129976AE19EE1C1 | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 1824 | peterzx.exe | C:\Users\admin\AppData\Local\Temp\Cab7327.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Local\Temp\dul1ut3b.snq.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1824 | peterzx.exe | C:\Users\admin\AppData\Roaming\KaGeys\KaGeys.exe | executable | |
MD5:CFE973E132B12ABA1AA2C13560071969 | SHA256:2CE0AD043E6F2C693EB6D5A2274BBF80431A9FC337D72499384ACD5EF5D5CE34 | |||
| 1824 | peterzx.exe | C:\Users\admin\AppData\Local\Temp\Tar7328.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1824 | peterzx.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1020 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF188a59.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 2848 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\hncc.exe | executable | |
MD5:C227E22771466226949F8C53AF85465C | SHA256:440A17E8DBD0BFAD5F1587FE8C758E9461106EB7B04235477D4B7CAB156FCFBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
105
TCP/UDP connections
1 841
DNS requests
840
Threats
417
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2848 | 4363463463464363463463463.exe | GET | 200 | 60.220.213.207:80 | http://d1.udashi.com/soft/aqsd/5084/%E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe | unknown | executable | 1.91 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.8:80 | http://185.172.128.8/cp.exe | unknown | executable | 1.84 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/for.exe | unknown | executable | 1.57 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 94.53.120.109:80 | http://94.53.120.109/dusers.exe | unknown | executable | 207 Kb | unknown |
3084 | rgAcb2.exe | POST | 200 | 91.215.85.223:80 | http://parals.ac.ug/index.php | unknown | text | 4 b | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.19:80 | http://185.172.128.19/costa.exe | unknown | executable | 6.63 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://marksidfg.ug/native.exe | unknown | executable | 2.13 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 193.176.31.152:81 | http://193.176.31.152:81/amin.exe | unknown | binary | 354 b | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 195.20.16.46:80 | http://195.20.16.46/api/StealerClient_Cpp_1_4.exe | unknown | executable | 1.25 Mb | unknown |
2848 | 4363463463464363463463463.exe | GET | 200 | 172.67.175.19:80 | http://dlink.metallc.top/pages/peterzx.exe | unknown | executable | 843 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2848 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2848 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
2848 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2848 | 4363463463464363463463463.exe | 68.66.226.93:80 | thedoctorsgym.net | A2HOSTING | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2848 | 4363463463464363463463463.exe | 172.67.175.19:80 | dlink.metallc.top | CLOUDFLARENET | US | unknown |
2848 | 4363463463464363463463463.exe | 211.149.230.178:80 | hseda.com | CHINANET SiChuan Telecom Internet Data Center | CN | unknown |
2848 | 4363463463464363463463463.exe | 91.215.85.223:80 | hubvera.ac.ug | — | RU | unknown |
1824 | peterzx.exe | 172.67.74.152:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
thedoctorsgym.net |
| unknown |
dlink.metallc.top |
| unknown |
hseda.com |
| malicious |
hubvera.ac.ug |
| unknown |
api.ipify.org |
| shared |
ip-api.com |
| shared |
cdn.discordapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2848 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2848 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2848 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2848 | 4363463463464363463463463.exe | A Network Trojan was detected | ET HUNTING SUSPICIOUS Firesale gTLD EXE DL with no Referer June 13 2016 |
2848 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2848 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2848 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING Request to .TOP Domain with Minimal Headers |
2848 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2848 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
43 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
ladas.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
amert.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|