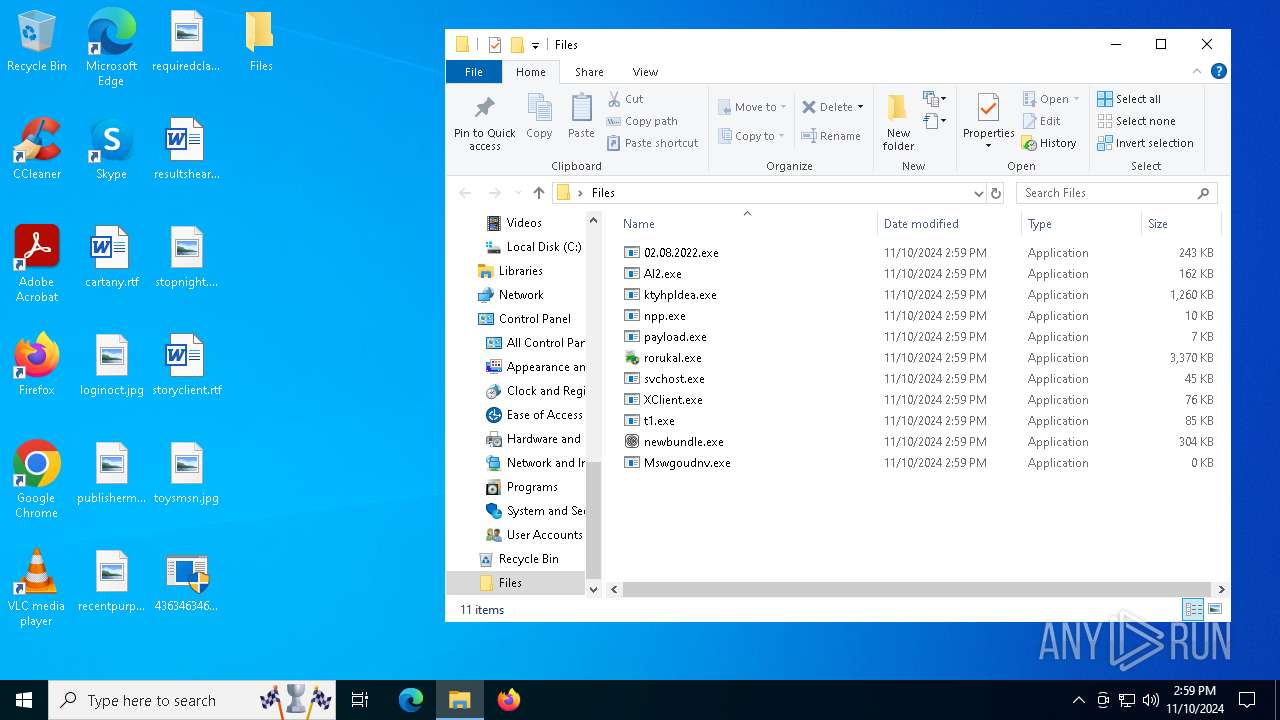
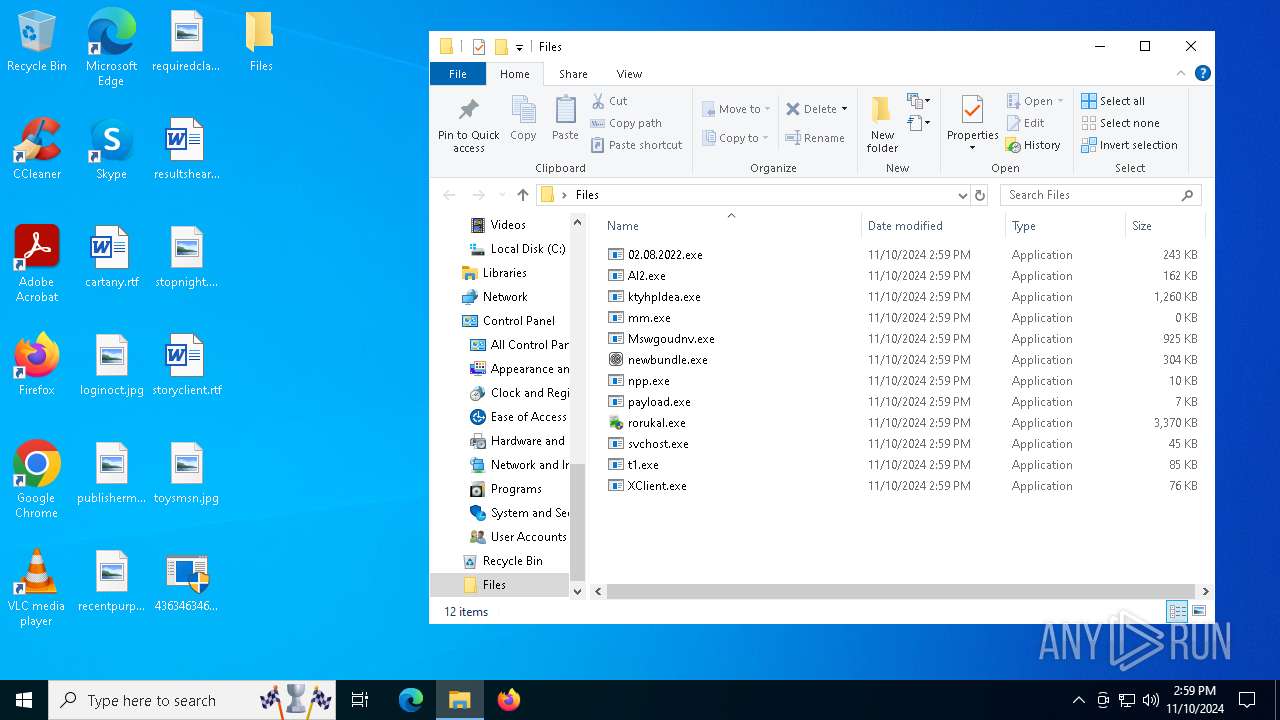
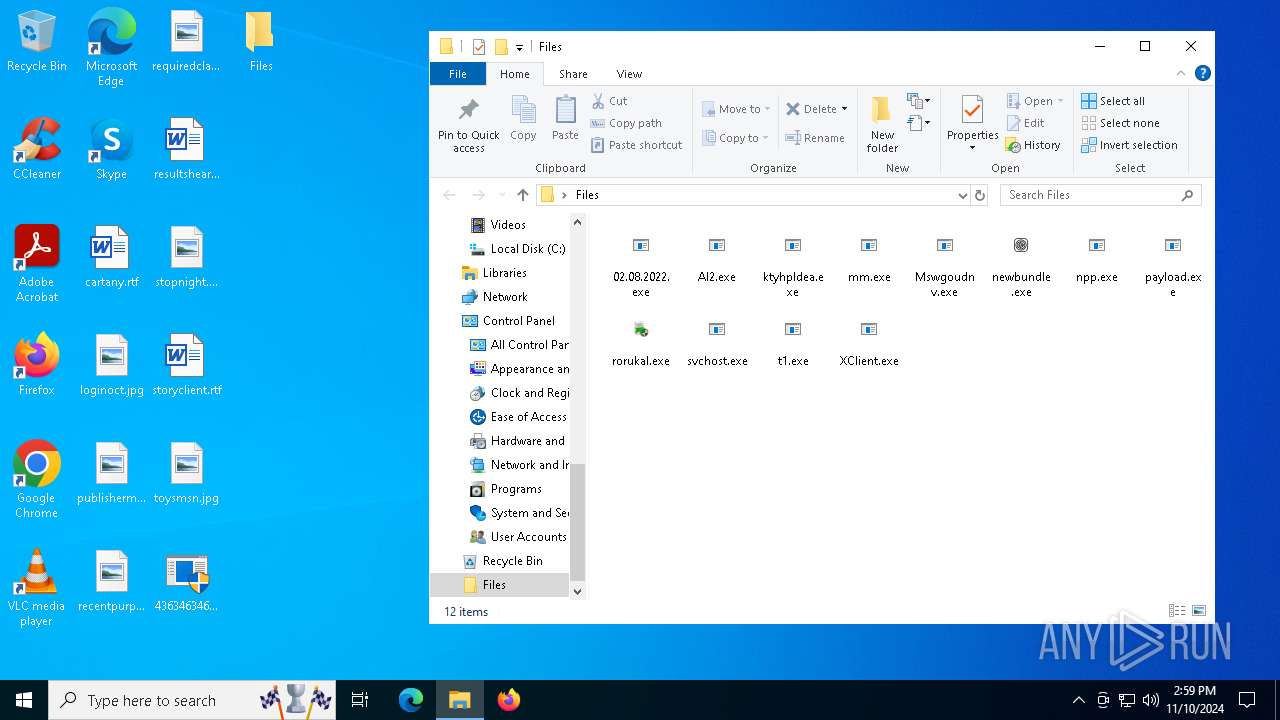
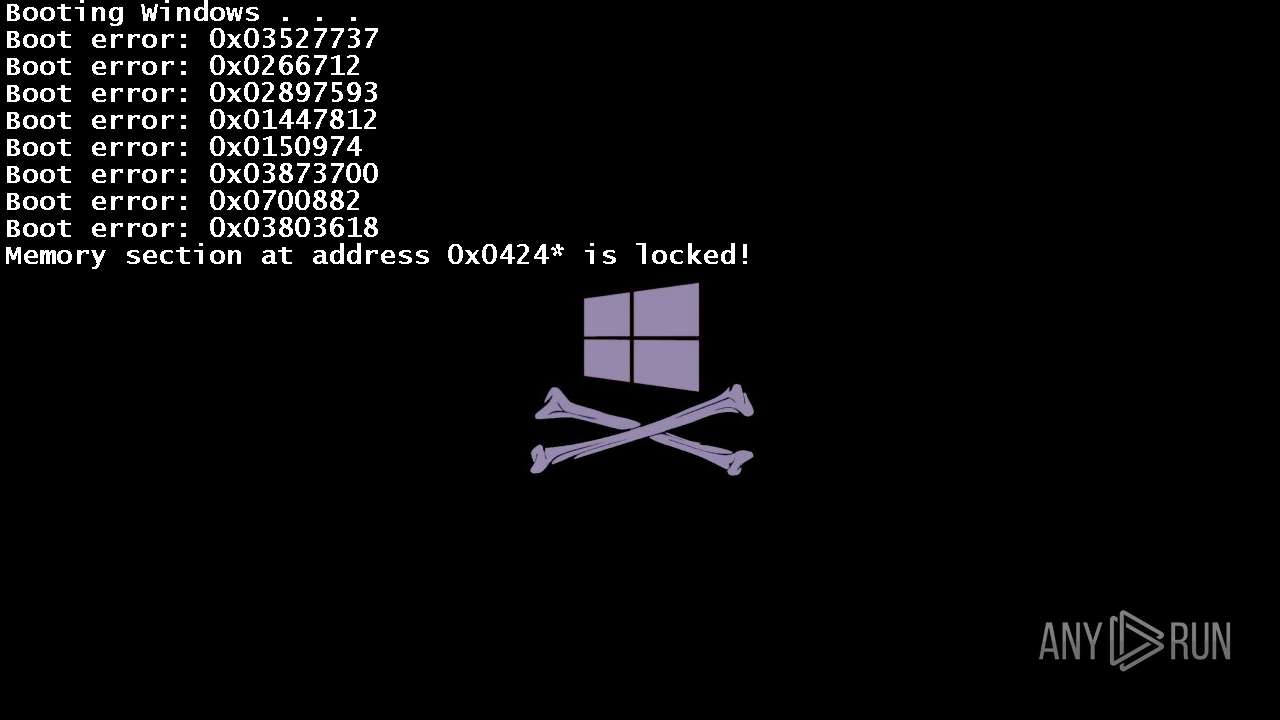
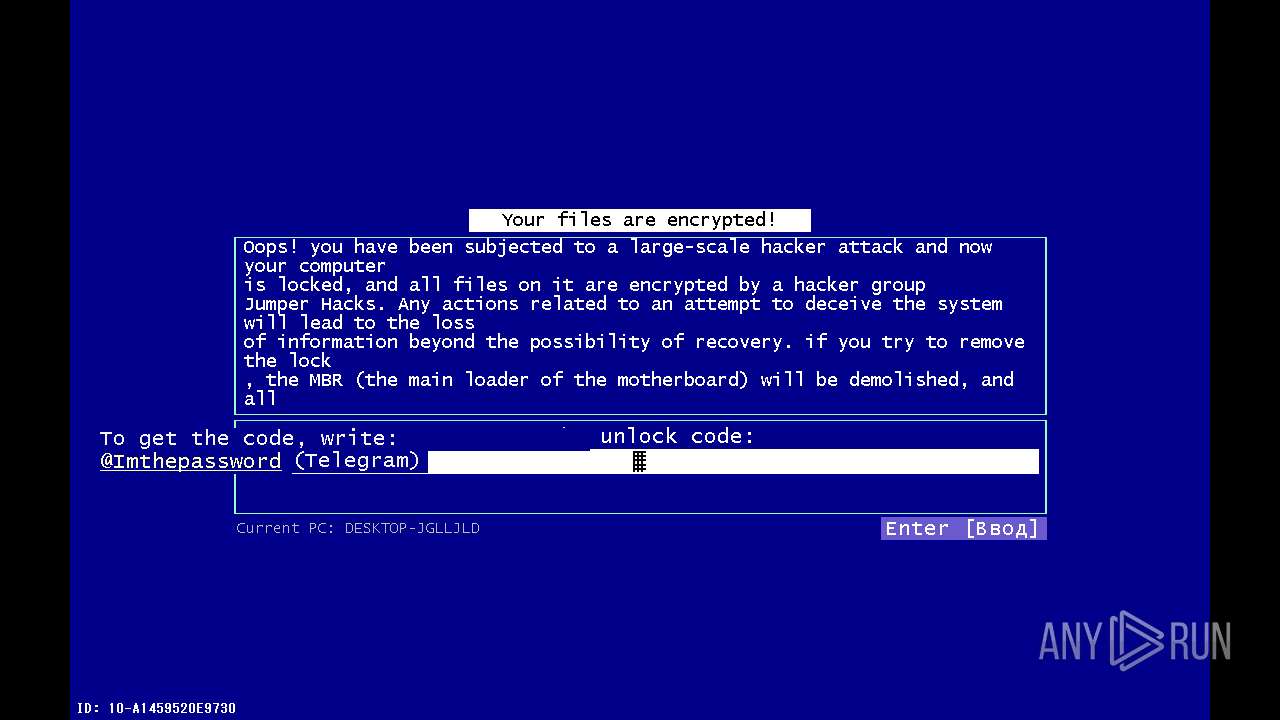
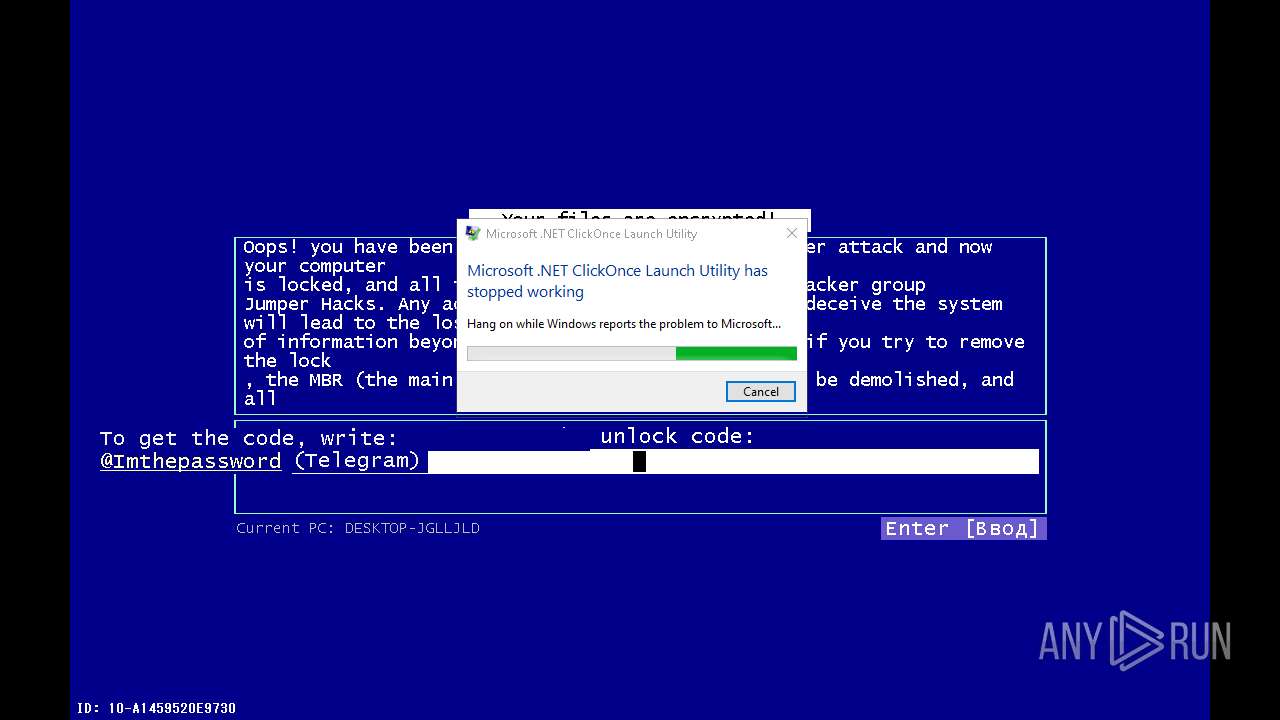
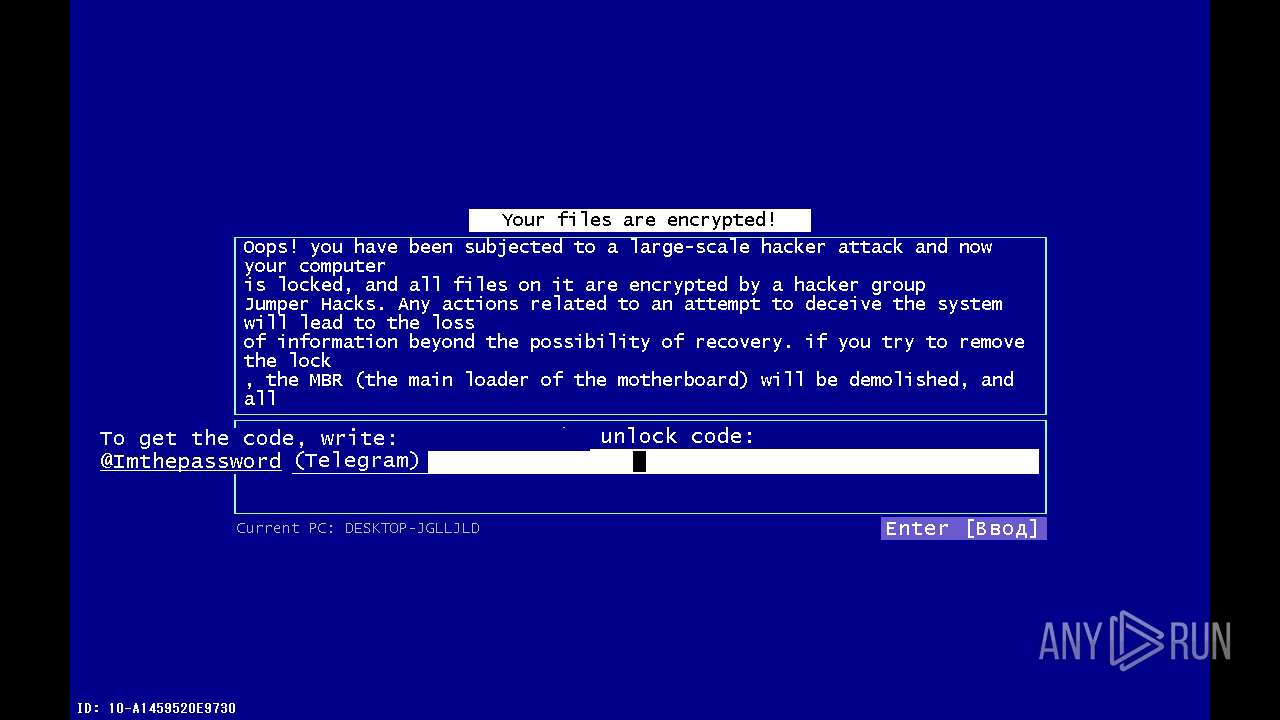
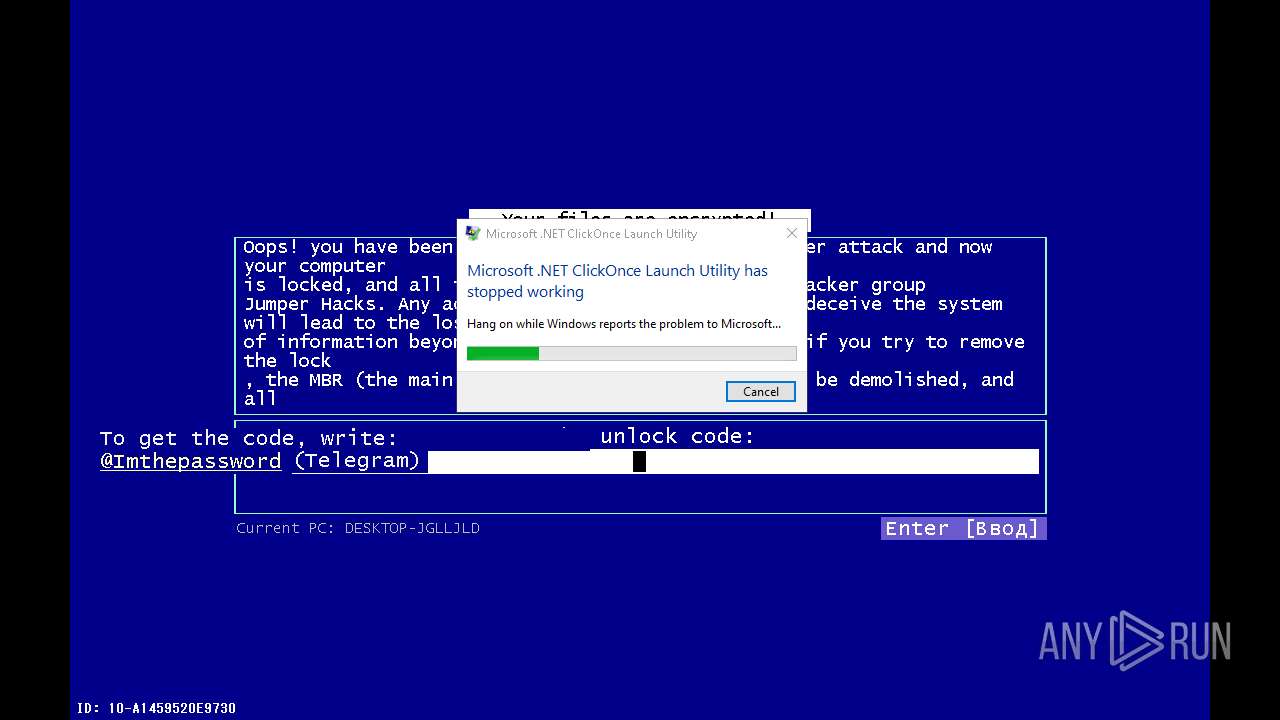
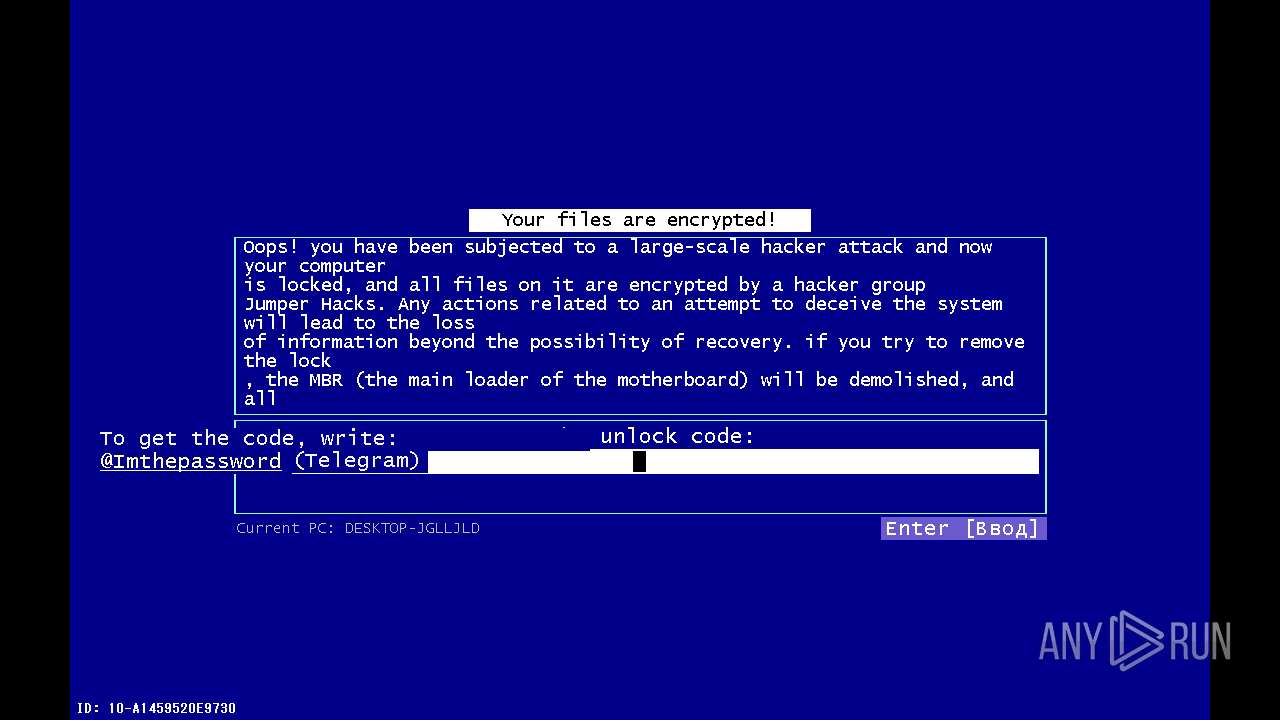
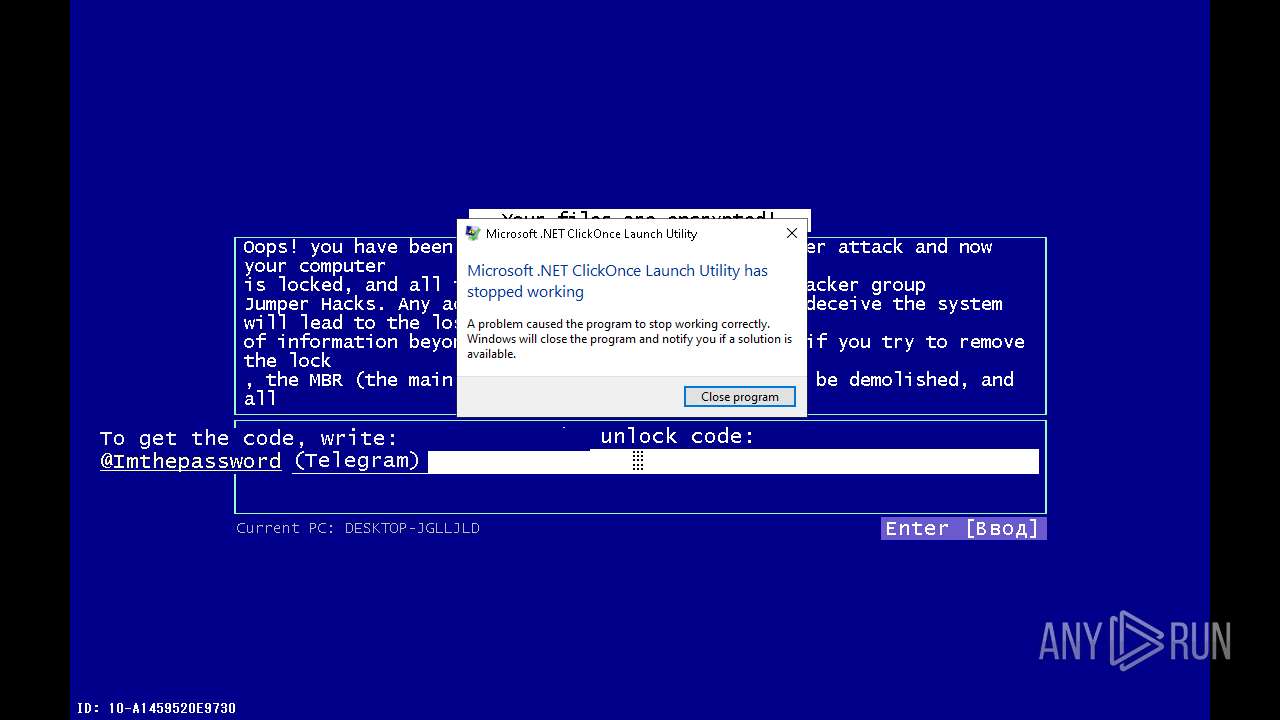
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/dd287a42-9940-4d21-9395-37c18bf045f5 |
| Verdict: | Malicious activity |
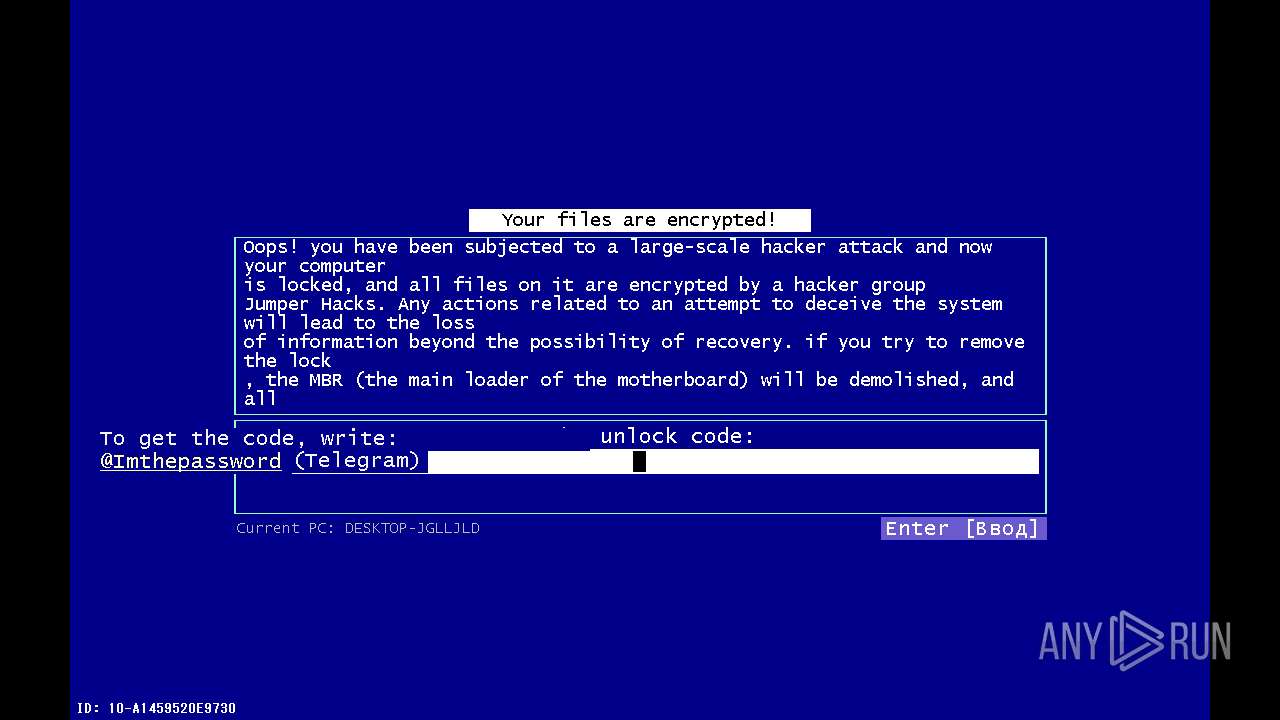
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 10, 2024, 14:59:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7228)
- powershell.exe (PID: 7488)
- powershell.exe (PID: 8052)
- powershell.exe (PID: 8652)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 4508)
- sysklnorbcv.exe (PID: 7360)
- cmd.exe (PID: 7984)
- sysppvrdnvs.exe (PID: 7452)
- cmd.exe (PID: 4812)
- sysvplervcs.exe (PID: 5032)
- cmd.exe (PID: 8504)
Changes powershell execution policy (Bypass)
- svchost.exe (PID: 4508)
XORed URL has been found (YARA)
- 4363463463464363463463463.exe (PID: 5956)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 5956)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 5956)
Adds process to the Windows Defender exclusion list
- svchost.exe (PID: 4508)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 4508)
- rage.exe (PID: 4872)
- ravage.exe (PID: 4948)
TAS17 has been detected
- Mswgoudnv.exe (PID: 8352)
XWORM has been detected (YARA)
- XClient.exe (PID: 6704)
LUMMA has been detected (SURICATA)
- ktyhpldea.exe (PID: 6176)
- svchost.exe (PID: 2172)
Connects to the CnC server
- svchost.exe (PID: 2172)
- sysklnorbcv.exe (PID: 7360)
- defnur.exe (PID: 7684)
- sysppvrdnvs.exe (PID: 7452)
PHORPIEX has been detected (SURICATA)
- svchost.exe (PID: 2172)
- sysklnorbcv.exe (PID: 7360)
- 4363463463464363463463463.exe (PID: 5956)
- sysppvrdnvs.exe (PID: 7452)
Stealers network behavior
- ktyhpldea.exe (PID: 6176)
AMADEY has been detected (SURICATA)
- defnur.exe (PID: 7684)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 7984)
- findstr.exe (PID: 6876)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 8644)
Starts NET.EXE for service management
- stail.tmp (PID: 6524)
- net.exe (PID: 6940)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 5956)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 5956)
- npp.exe (PID: 4684)
- ktyhpldea.exe (PID: 6176)
- t1.exe (PID: 6392)
- SLIRFA2KCXJ660GNIMB379DAOT.exe (PID: 7344)
- 1968717183.exe (PID: 7856)
- rorukal.exe (PID: 5564)
- svchost.exe (PID: 4508)
- defnur.exe (PID: 7684)
- Mswgoudnv.exe (PID: 8352)
- Mswgoudnv.exe (PID: 5948)
- 1253516836.exe (PID: 8596)
- mm.exe (PID: 8408)
- winupsecvmgr.exe (PID: 5296)
- random.exe (PID: 8480)
- t.exe (PID: 4772)
- file.exe (PID: 6268)
- 1313110010.exe (PID: 9168)
- SteamDetector.exe (PID: 8984)
- SteamDetector.exe (PID: 4708)
- cmd.exe (PID: 3904)
- rage.exe (PID: 4872)
- 2020.exe (PID: 5396)
- Irons.exe (PID: 7600)
- qsjxfirefkza.exe (PID: 7092)
- aaa.exe (PID: 5036)
- utility-inst.exe (PID: 4920)
- utility-inst.tmp (PID: 9016)
- msrv.exe (PID: 3824)
- bildnewl.exe (PID: 6980)
- stail.exe (PID: 2708)
- videopresentmaker32.exe (PID: 4708)
- stail.tmp (PID: 6524)
- AllNew.exe (PID: 7720)
Executes application which crashes
- XClient.exe (PID: 6704)
- ktyhpldea.exe (PID: 6176)
- AppLaunch.exe (PID: 8024)
- cmd.exe (PID: 8012)
- AppLaunch.exe (PID: 8072)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 6104)
- AppLaunch.exe (PID: 8828)
- AppLaunch.exe (PID: 2780)
Starts POWERSHELL.EXE for commands execution
- svchost.exe (PID: 4508)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 4812)
- 1313110010.exe (PID: 9168)
- winupsecvmgr.exe (PID: 5296)
- cmd.exe (PID: 8504)
Script adds exclusion path to Windows Defender
- svchost.exe (PID: 4508)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 4812)
- cmd.exe (PID: 8504)
Starts itself from another location
- t1.exe (PID: 6392)
- SLIRFA2KCXJ660GNIMB379DAOT.exe (PID: 7344)
- 1968717183.exe (PID: 7856)
- t.exe (PID: 4772)
- file.exe (PID: 6268)
- SteamDetector.exe (PID: 4708)
- rage.exe (PID: 4872)
- AllNew.exe (PID: 7720)
Manipulates environment variables
- powershell.exe (PID: 8076)
- powershell.exe (PID: 7340)
- powershell.exe (PID: 3964)
Starts CMD.EXE for commands execution
- sysklnorbcv.exe (PID: 7360)
- sysppvrdnvs.exe (PID: 7452)
- AppLaunch.exe (PID: 7568)
- 188431998.exe (PID: 8396)
- sysvplervcs.exe (PID: 5032)
- rorukal.exe (PID: 5564)
- 1257610417.exe (PID: 7884)
- PctOccurred.exe (PID: 4792)
- cmd.exe (PID: 3904)
- 2020.exe (PID: 7344)
- utility-inst.tmp (PID: 9016)
- msrv.exe (PID: 3824)
Script adds exclusion process to Windows Defender
- svchost.exe (PID: 4508)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 8072)
- cmd.exe (PID: 3844)
- cmd.exe (PID: 7440)
- cmd.exe (PID: 7508)
- cmd.exe (PID: 7520)
Process drops legitimate windows executable
- rorukal.exe (PID: 5564)
- 2020.exe (PID: 5396)
- stail.tmp (PID: 6524)
- 4363463463464363463463463.exe (PID: 5956)
Application launched itself
- AppLaunch.exe (PID: 8024)
- Mswgoudnv.exe (PID: 5948)
- AppLaunch.exe (PID: 1604)
- AppLaunch.exe (PID: 2736)
- AppLaunch.exe (PID: 2780)
- AppLaunch.exe (PID: 8072)
- AppLaunch.exe (PID: 8828)
- AppLaunch.exe (PID: 4952)
- AppLaunch.exe (PID: 9208)
- AppLaunch.exe (PID: 6300)
- AppLaunch.exe (PID: 3076)
- AppLaunch.exe (PID: 5404)
- AppLaunch.exe (PID: 4848)
- pimer_bbbcontents7.exe (PID: 8468)
- jarg.exe (PID: 6612)
- 2020.exe (PID: 5396)
- cmd.exe (PID: 3904)
- golden.exe (PID: 4812)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 7520)
Uses TASKKILL.EXE to kill process
- AppLaunch.exe (PID: 7568)
- aaa.exe (PID: 5036)
Checks for external IP
- svchost.exe (PID: 2172)
- XClient.exe (PID: 6704)
The process executes via Task Scheduler
- defnur.exe (PID: 9080)
- System.exe (PID: 9200)
- winupsecvmgr.exe (PID: 5296)
- defnur.exe (PID: 3600)
- System.exe (PID: 1604)
- jarg.exe (PID: 6612)
- ravage.exe (PID: 1344)
- defnur.exe (PID: 3948)
- System.exe (PID: 4816)
- jarg.exe (PID: 1156)
- defnur.exe (PID: 7424)
- Gxtuum.exe (PID: 8868)
- jarg.exe (PID: 7592)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8412)
- cmd.exe (PID: 8644)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8536)
- schtasks.exe (PID: 8736)
Contacting a server suspected of hosting an CnC
- ktyhpldea.exe (PID: 6176)
- svchost.exe (PID: 2172)
- defnur.exe (PID: 7684)
Potential Corporate Privacy Violation
- npp.exe (PID: 4684)
- 4363463463464363463463463.exe (PID: 5956)
- ktyhpldea.exe (PID: 6176)
- svchost.exe (PID: 2172)
- defnur.exe (PID: 7684)
Connects to unusual port
- AI2.exe (PID: 3912)
- newbundle.exe (PID: 4380)
- 4363463463464363463463463.exe (PID: 5956)
- payload.exe (PID: 4956)
- svchost.exe (PID: 4508)
Connects to the server without a host name
- sysppvrdnvs.exe (PID: 7452)
- 4363463463464363463463463.exe (PID: 5956)
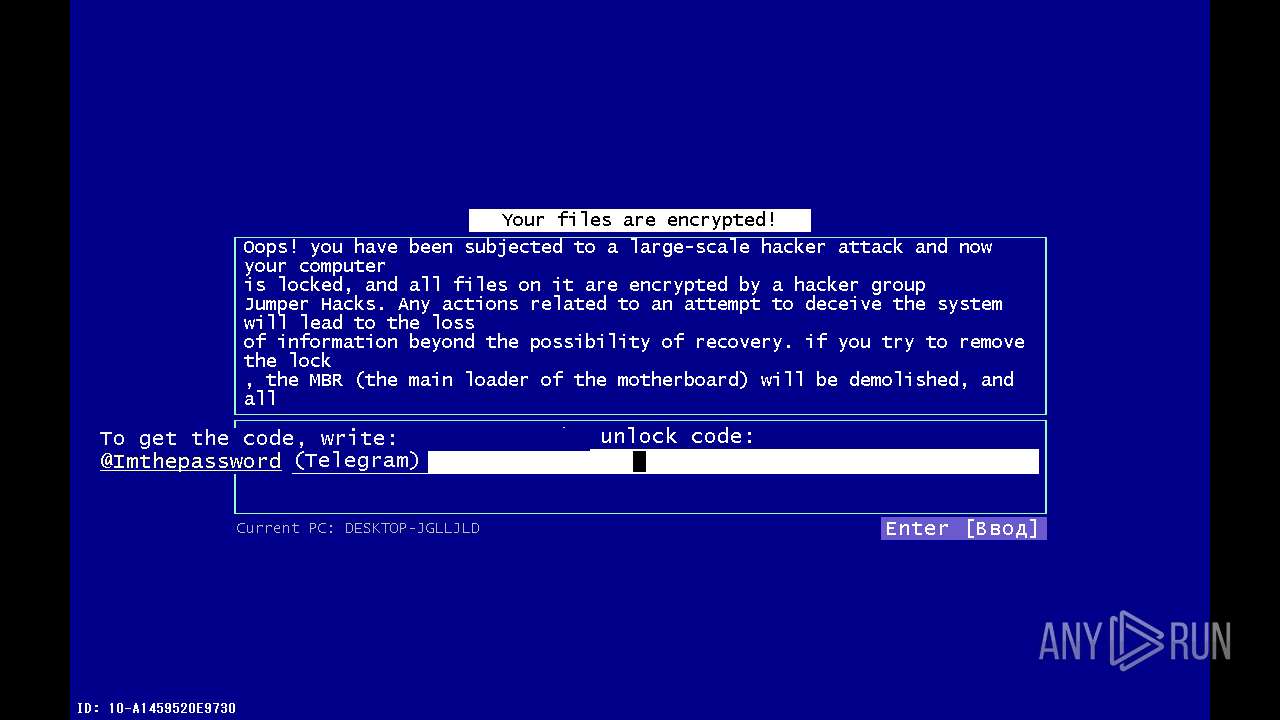
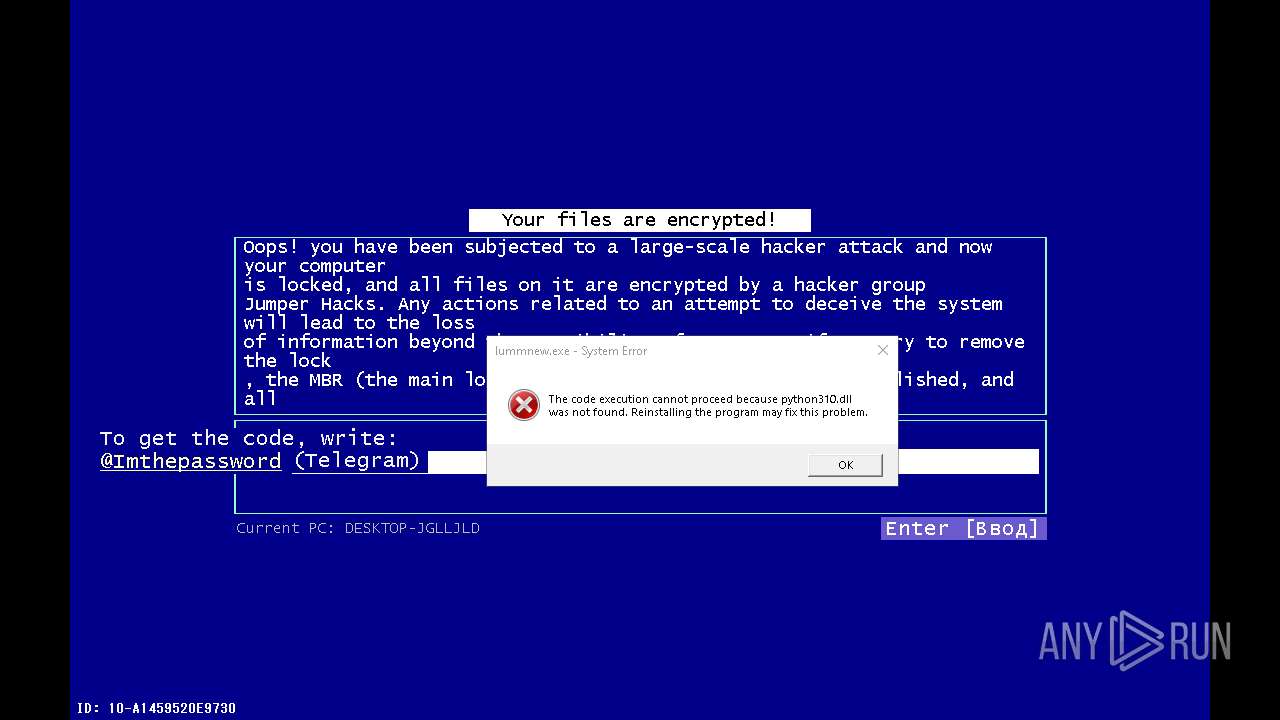
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 4508)
Executing commands from a ".bat" file
- rorukal.exe (PID: 5564)
- msrv.exe (PID: 3824)
- utility-inst.tmp (PID: 9016)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 5956)
Drops a system driver (possible attempt to evade defenses)
- winupsecvmgr.exe (PID: 5296)
- qsjxfirefkza.exe (PID: 7092)
Uses NETSH.EXE to add a firewall rule or allowed programs
- SteamDetector.exe (PID: 8984)
Executing commands from ".cmd" file
- PctOccurred.exe (PID: 4792)
Get information on the list of running processes
- cmd.exe (PID: 3904)
The executable file from the user directory is run by the CMD process
- Restructuring.pif (PID: 6300)
- winfile.exe (PID: 2380)
Starts application with an unusual extension
- cmd.exe (PID: 3904)
- explorer.exe (PID: 3700)
The process drops C-runtime libraries
- 2020.exe (PID: 5396)
- stail.tmp (PID: 6524)
Process drops python dynamic module
- 2020.exe (PID: 5396)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3904)
Uses powercfg.exe to modify the power settings
- Irons.exe (PID: 7600)
- qsjxfirefkza.exe (PID: 7092)
Starts SC.EXE for service management
- Irons.exe (PID: 7600)
Executes as Windows Service
- qsjxfirefkza.exe (PID: 7092)
Malware-specific behavior (creating "System.dll" in Temp)
- aaa.exe (PID: 5036)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7844)
Starts a Microsoft application from unusual location
- crypted8888.exe (PID: 8696)
INFO
Reads the computer name
- 4363463463464363463463463.exe (PID: 5956)
Disables trace logs
- 4363463463464363463463463.exe (PID: 5956)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 5956)
The process uses the downloaded file
- 4363463463464363463463463.exe (PID: 5956)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 5956)
Checks supported languages
- 4363463463464363463463463.exe (PID: 5956)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 5956)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 5956)
Attempting to use instant messaging service
- svchost.exe (PID: 2172)
- svchost.exe (PID: 4508)
Creates a new folder
- cmd.exe (PID: 7264)
Checks operating system version
- 2020.exe (PID: 7344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(5956) 4363463463464363463463463.exe
Decrypted-URLs (1)http://www.enigmaprotector.com/
XWorm
(PID) Process(6704) XClient.exe
C2return-carol.gl.at.ply.gg:53275
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexJw38N4UjbGjLvbSc
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
495
Monitored processes
327
Malicious processes
19
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LockApp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 780 | cmd /c copy /b ..\Medicines + ..\While + ..\Remained + ..\Bs + ..\Ak + ..\Statistical + ..\Entity + ..\Autumn + ..\Scott + ..\Keyboards y | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1084 | sc stop DoSvc | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\ProgramData\qnnk\jarg.exe" | C:\ProgramData\qnnk\jarg.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Mswgoudnv Exit code: 4294967295 Version: 1.0.0.0 | |||||||||||||||
| 1168 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | /c echo "XClient.exe" | C:\ProgramData\Microsoft\Windows\MSCaches\cmd.exe | — | forfiles.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 | |||||||||||||||
| 1176 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\AppData\Local\Temp\243587562342\ravage.exe" | C:\Users\admin\AppData\Local\Temp\243587562342\ravage.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM | |||||||||||||||
Total events
62 858
Read events
62 632
Write events
187
Delete events
39
Modification events
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5956) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
138
Suspicious files
114
Text files
76
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD1FF.tmp.WERInternalMetadata.xml | xml | |
MD5:8330FC2998224DFCCF50EF2F4B9CA10E | SHA256:6896012072952D81DF75BAC3367E3AD257610E041AFCFC7199FB52F2F8A0DFE3 | |||
| 4224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD097.tmp.dmp | binary | |
MD5:33A15ECBCA5DBCBB73974AF31BD65496 | SHA256:D9EF6A6FFB0FB7B0286EC68D9FFF5652686E92534E12A04CE7EF443AEB0AC851 | |||
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\ktyhpldea.exe | executable | |
MD5:E9A83661D98FCA881CD4497A985A20DE | SHA256:F8DBFF120F44CF68BCB802C11F24BBC506F11803E8745883A0F650DECEA1DB47 | |||
| 4224 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD220.tmp.xml | xml | |
MD5:885EA9346E201F16B5E18C347D48BECC | SHA256:A7C5945CF8FB6AFD5CE5B120C9503642FDE25156453D3A6C2C83172C5E84D6A1 | |||
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\rorukal.exe | executable | |
MD5:77ECAFEE1B0BA32BD4E3B90B6D92A81F | SHA256:14D8C36FBAB22C95764169E90E4985F90A171B201BB206BD6EA8883B492083E3 | |||
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\npp.exe | executable | |
MD5:8D8E6C7952A9DC7C0C73911C4DBC5518 | SHA256:FEB4C3AE4566F0ACBB9E0F55417B61FEFD89DC50A4E684DF780813FB01D61278 | |||
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\newbundle.exe | executable | |
MD5:58E8B2EB19704C5A59350D4FF92E5AB6 | SHA256:07D4B7768E13D79AC5F05F81167B29BB6FBF97828A289D8D11EEC38939846834 | |||
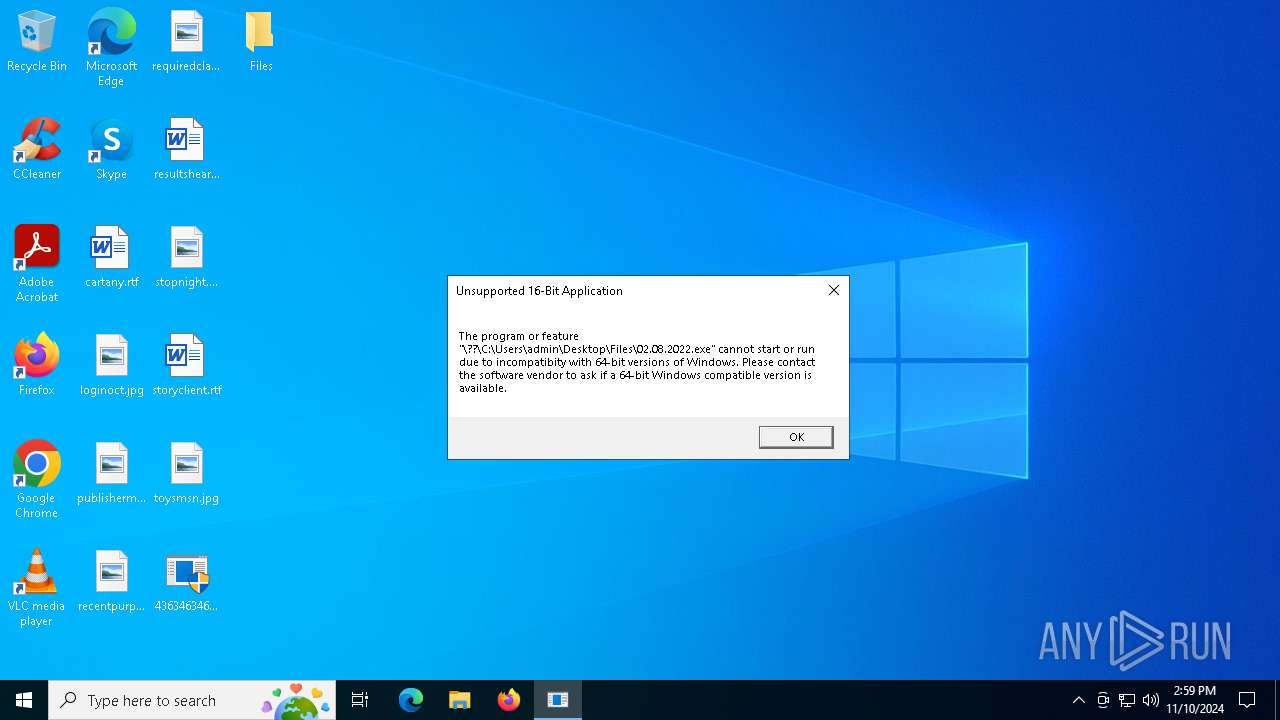
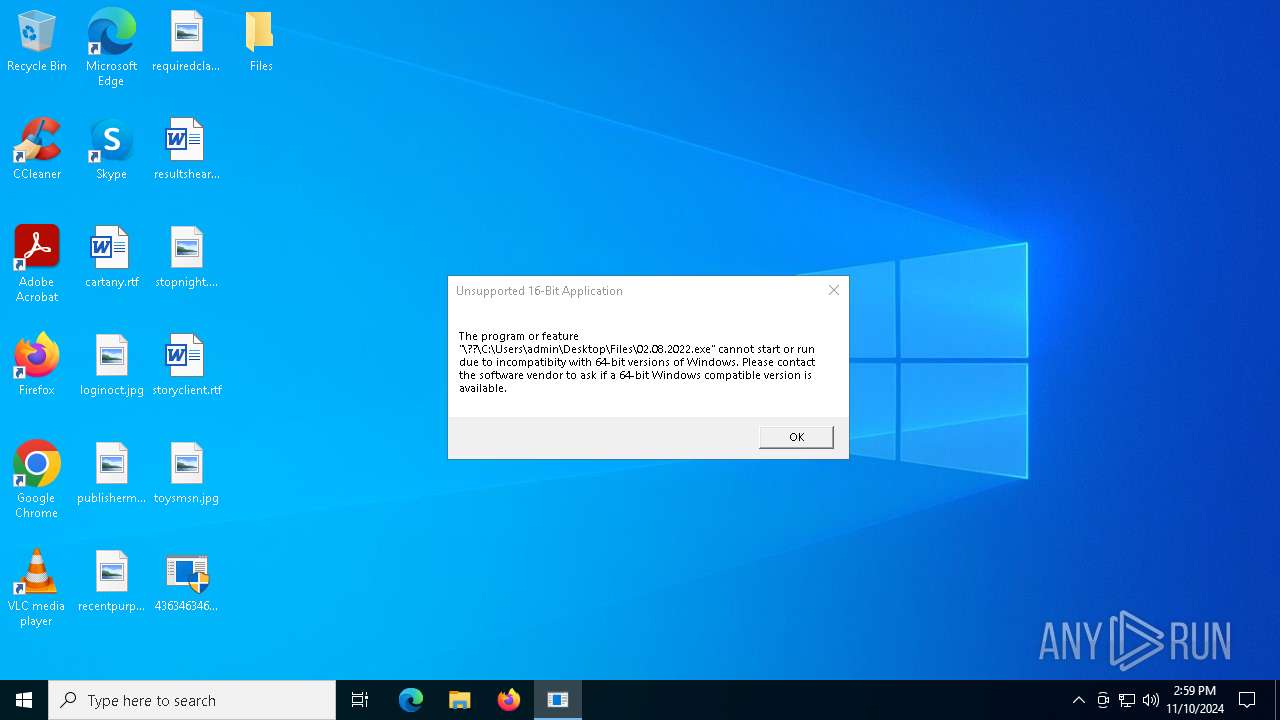
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\02.08.2022.exe | binary | |
MD5:BA72B61FC00FD577A85BB5FFE6F845C5 | SHA256:009AD8822395712E89FB5118B79A620E85B617E6FB7C51787A53A2F7416A2786 | |||
| 4380 | newbundle.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\76b53b3ec448f7ccdda2063b15d2bfc3_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:BBC8DA7D36DF3F91C460984C2ABE8419 | SHA256:0399CCF5E780949A63400736A46CCE7D1879903D0F45C6B7D194C960BA4DDDC2 | |||
| 5956 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\t1.exe | executable | |
MD5:A775D164CF76E9A9FF6AFD7EB1E3AB2E | SHA256:794BA0B949B2144057A1B68752D8FA324F1A211AFC2231328BE82D17F9308979 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
110
TCP/UDP connections
502
DNS requests
156
Threats
339
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6704 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
1880 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.217:80 | http://185.215.113.217/inc/rorukal.exe | unknown | — | — | unknown |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/AI2.exe | unknown | — | — | unknown |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5956 | 4363463463464363463463463.exe | GET | 200 | 144.34.162.13:80 | http://144.34.162.13/payload.exe | unknown | — | — | unknown |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://rddissisifigifidi.net/npp.exe | unknown | — | — | malicious |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://deauduafzgezzfgm.top/t1.exe | unknown | — | — | malicious |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/newbundle.exe | unknown | — | — | unknown |
5956 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.217:80 | http://185.215.113.217/inc/Mswgoudnv.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5640 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
— | — | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
— | — | 185.234.216.143:443 | — | — | RU | unknown |
6704 | XClient.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | shared |
1880 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| shared |
ip-api.com |
| shared |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5956 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
2172 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2172 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6704 | XClient.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6704 | XClient.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
5956 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5956 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
5956 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5956 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
41 ETPRO signatures available at the full report
Process | Message |
|---|---|
XClient.exe | CLR: Managed code called FailFast without specifying a reason.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
SLIRFA2KCXJ660GNIMB379DAOT.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
defnur.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
rorukal.exe | wanna die |
defnur.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|