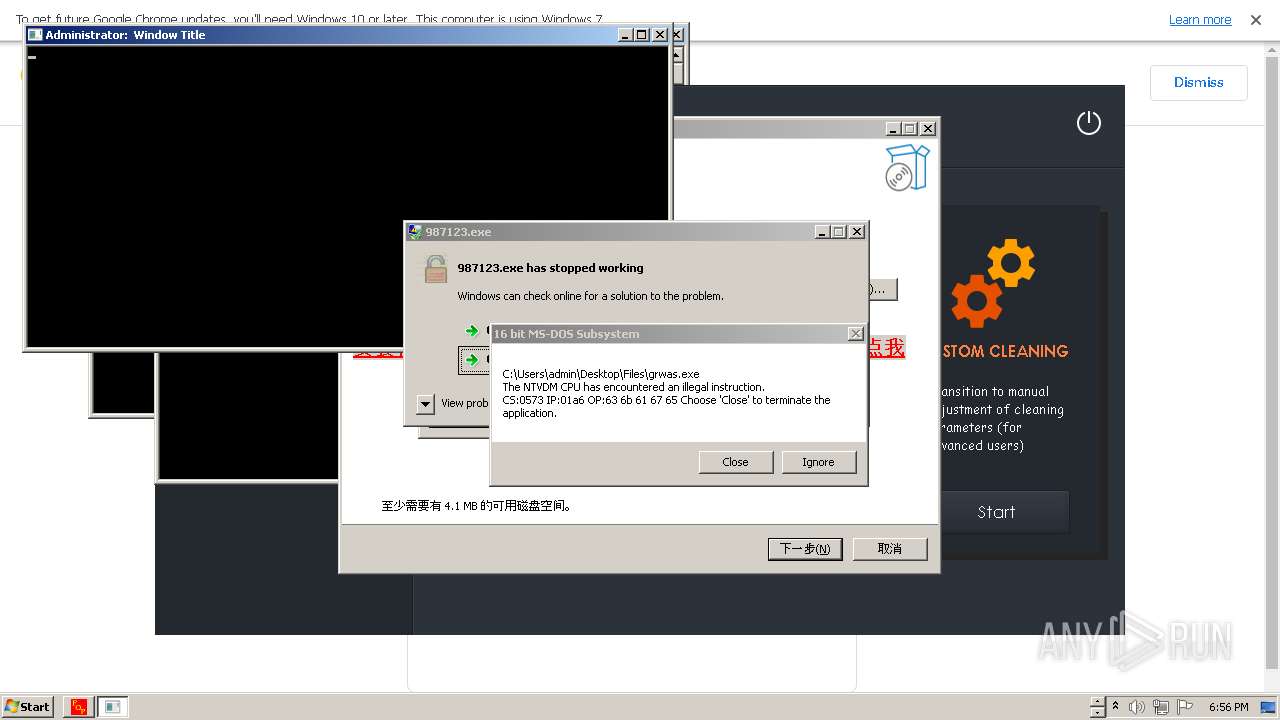
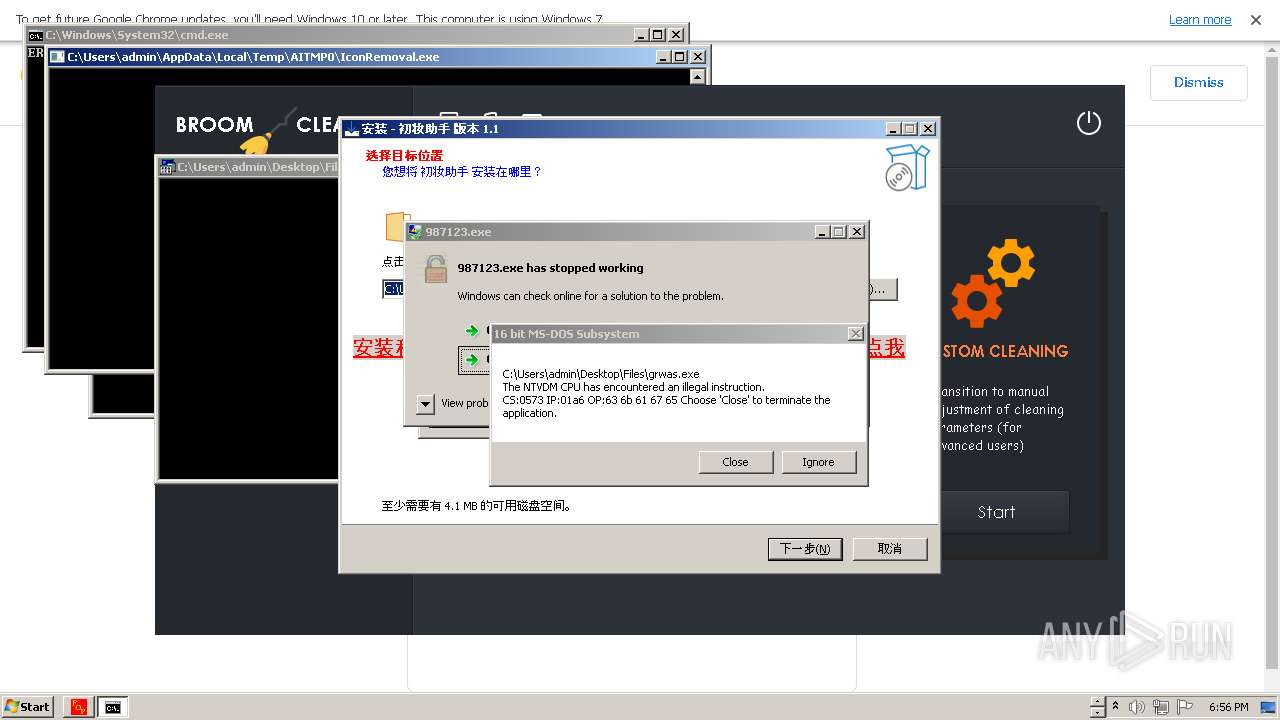
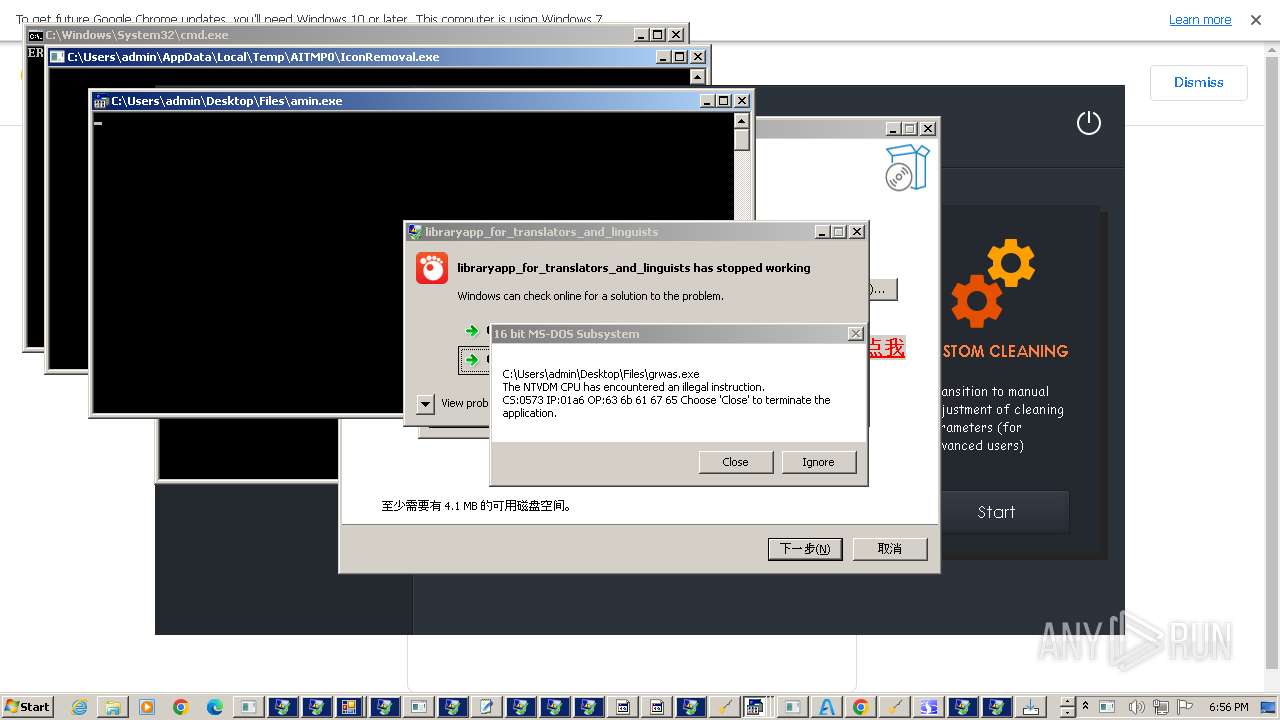
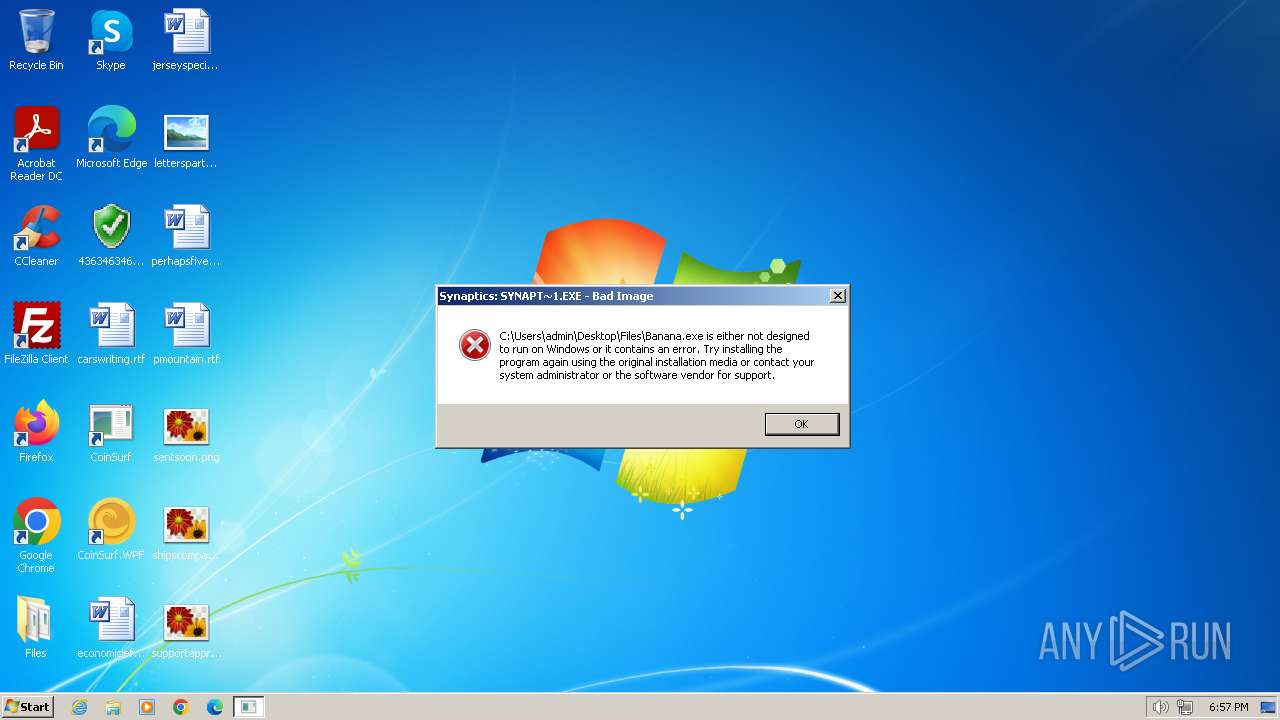
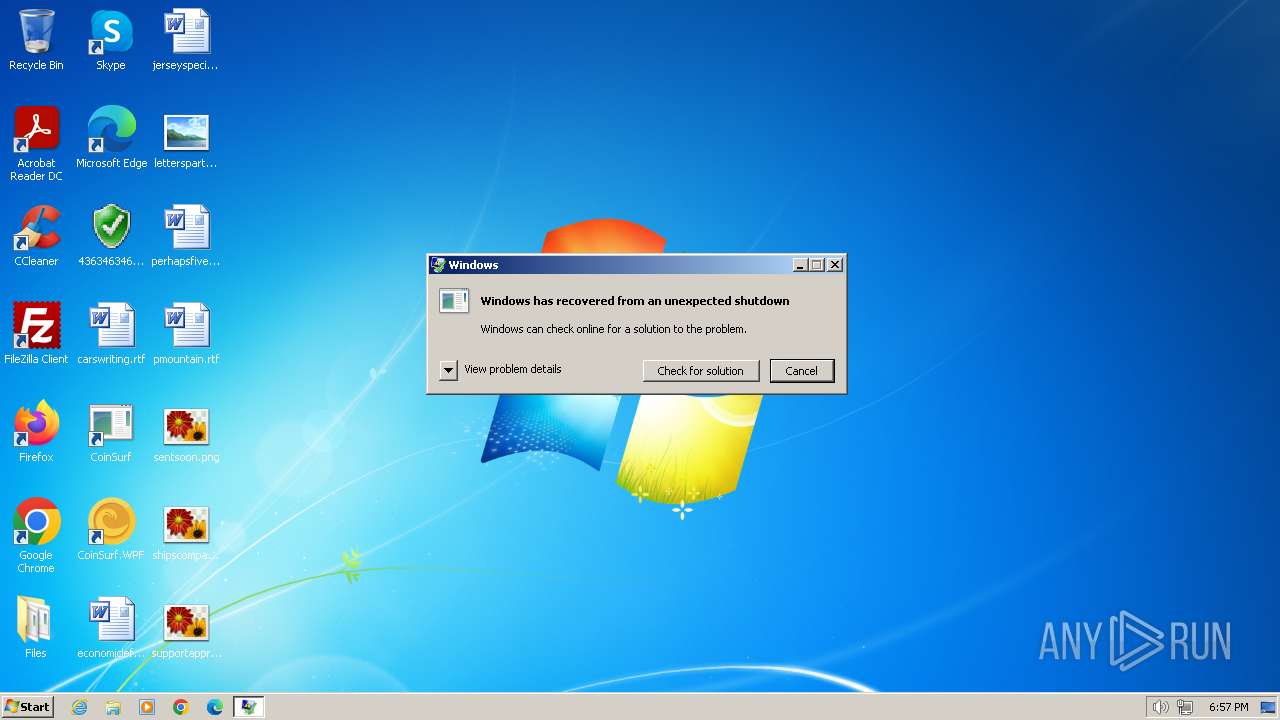
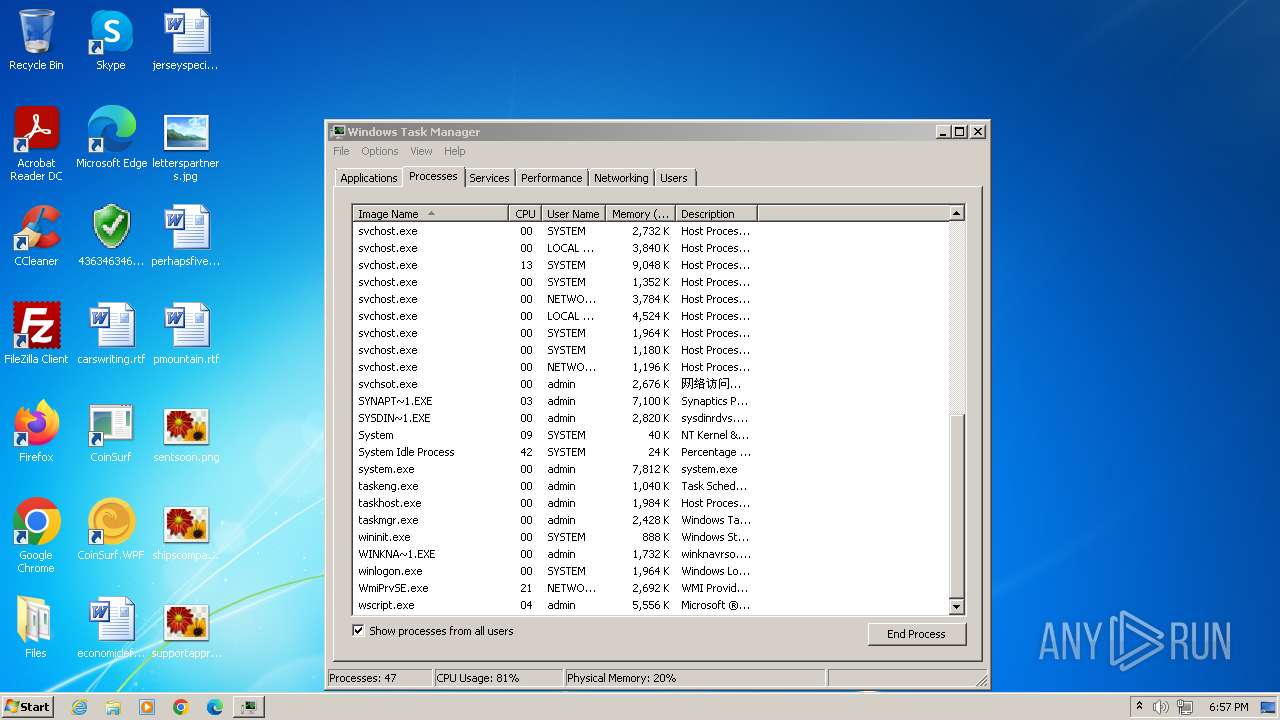
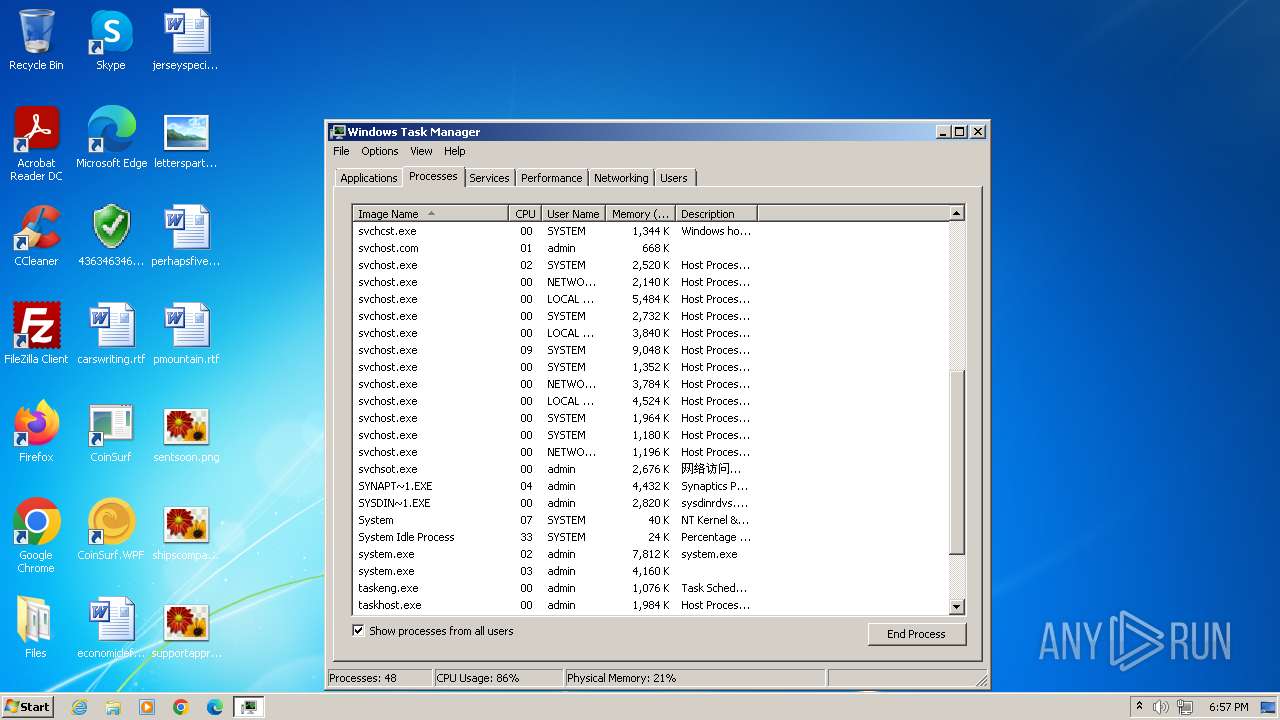
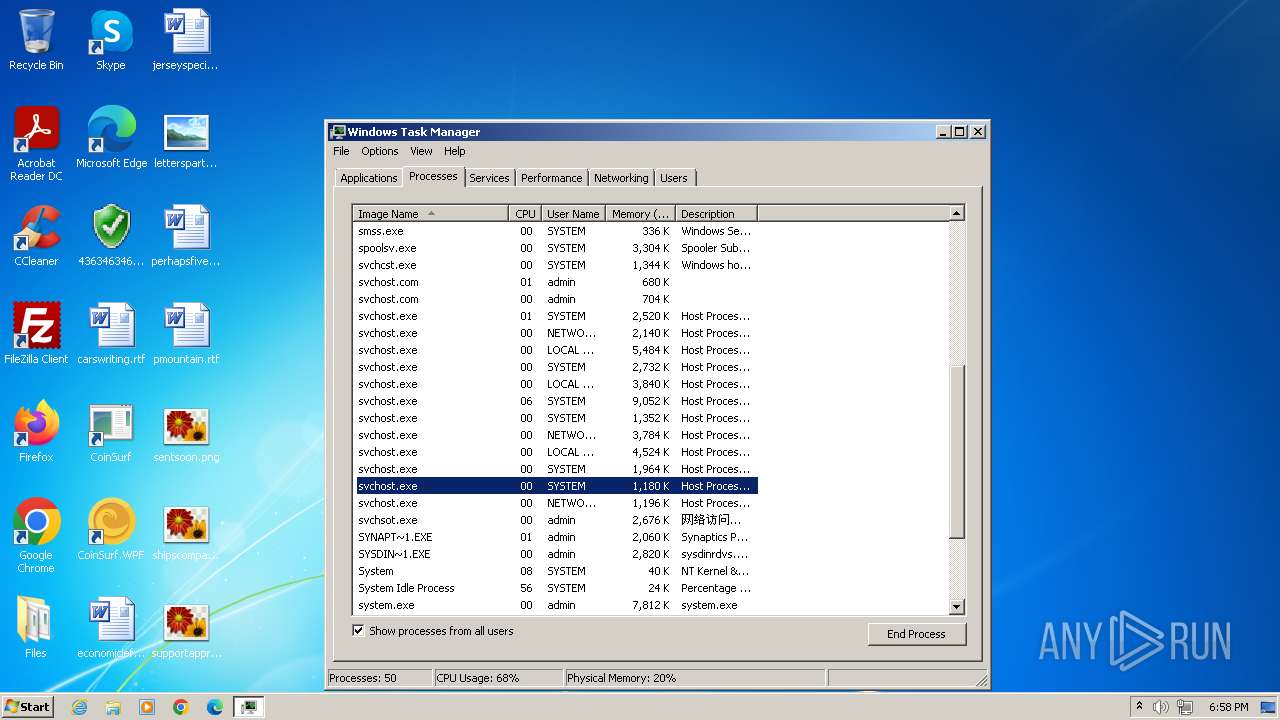
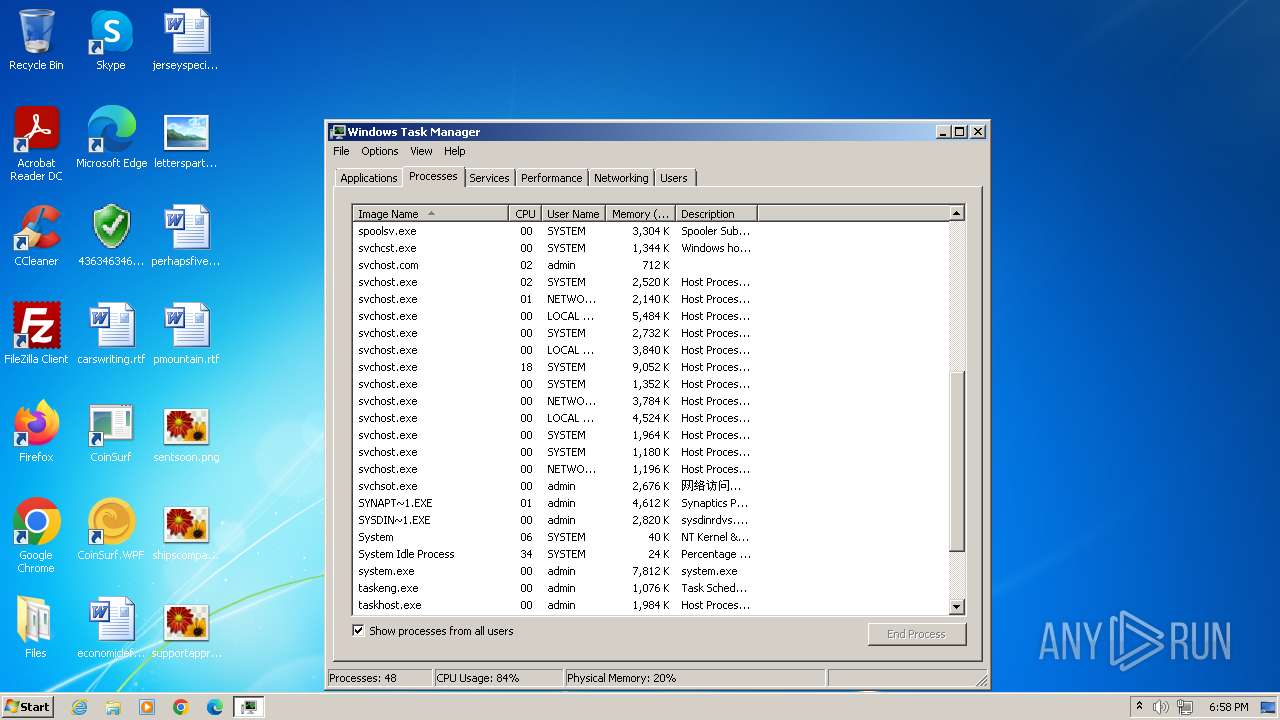
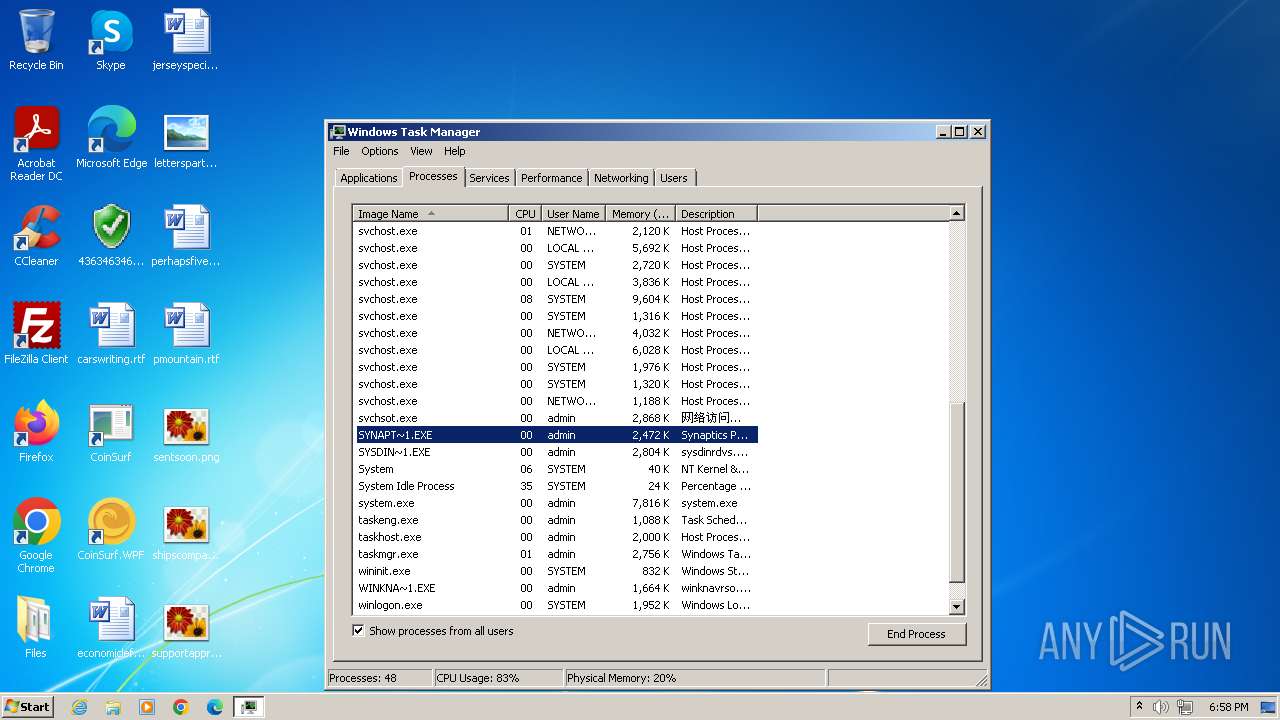
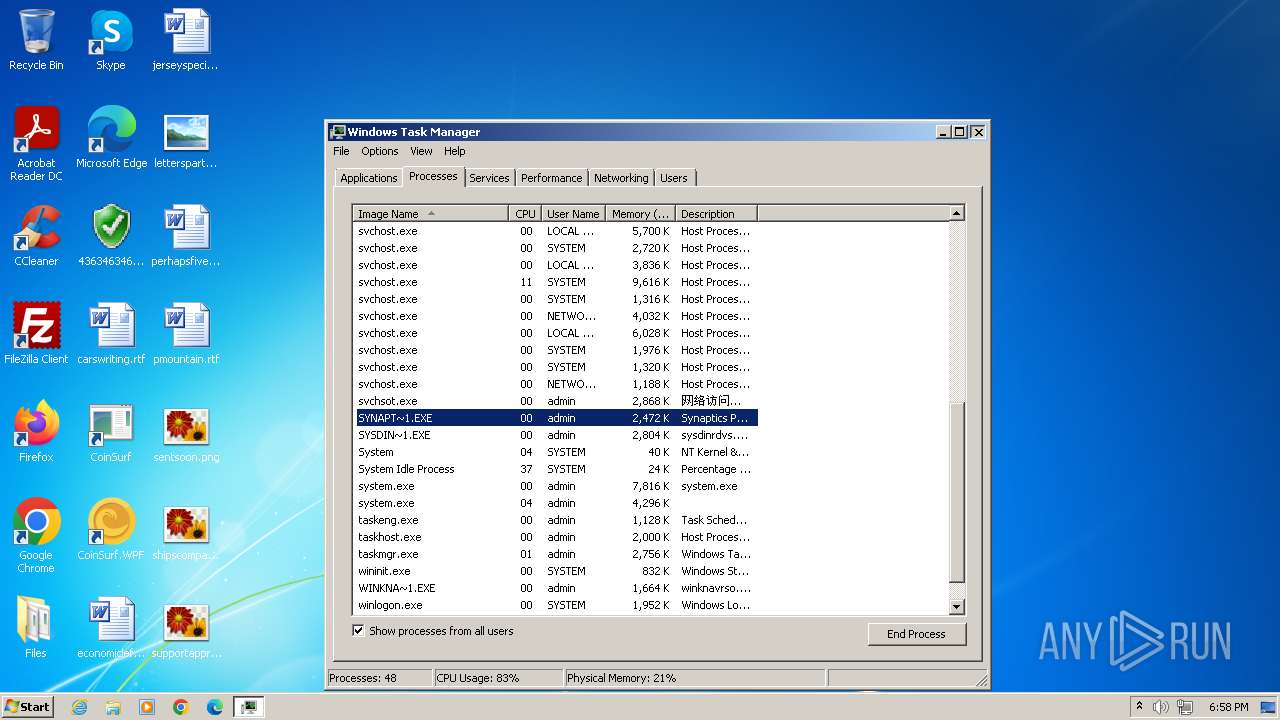
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/d4d485d3-27fb-4153-846b-04bb0f171945 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | February 29, 2024, 18:54:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
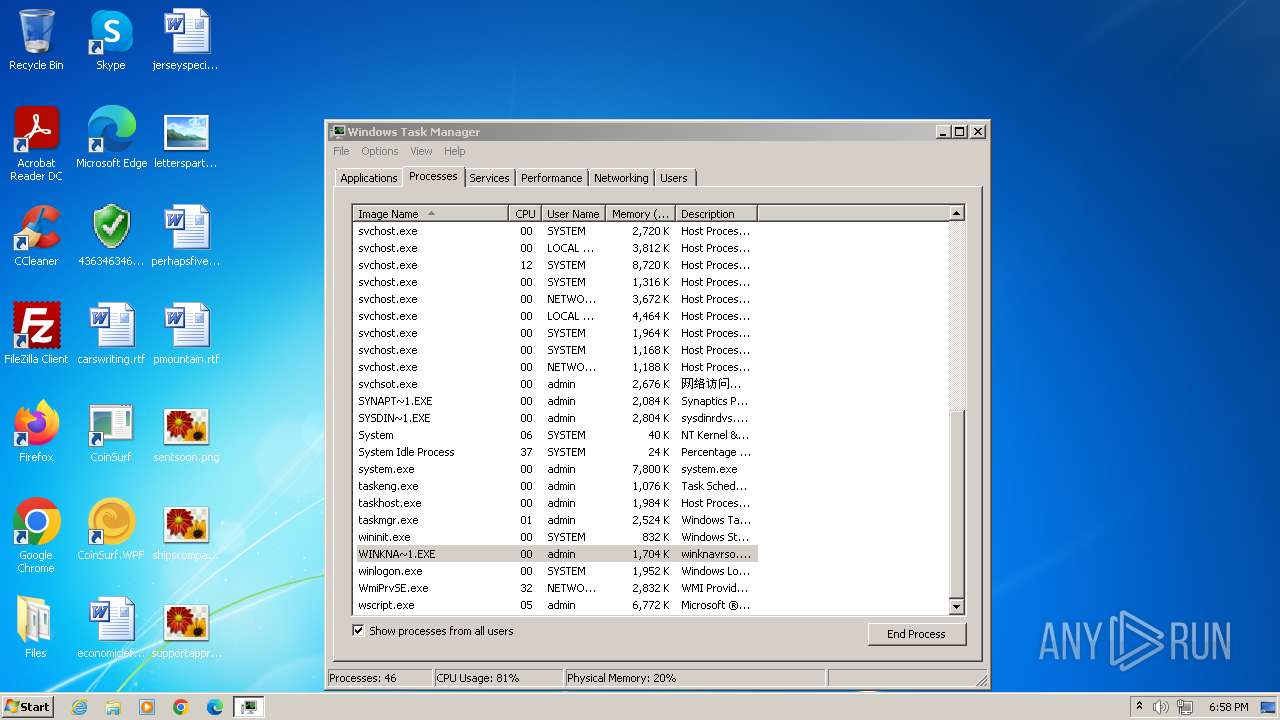
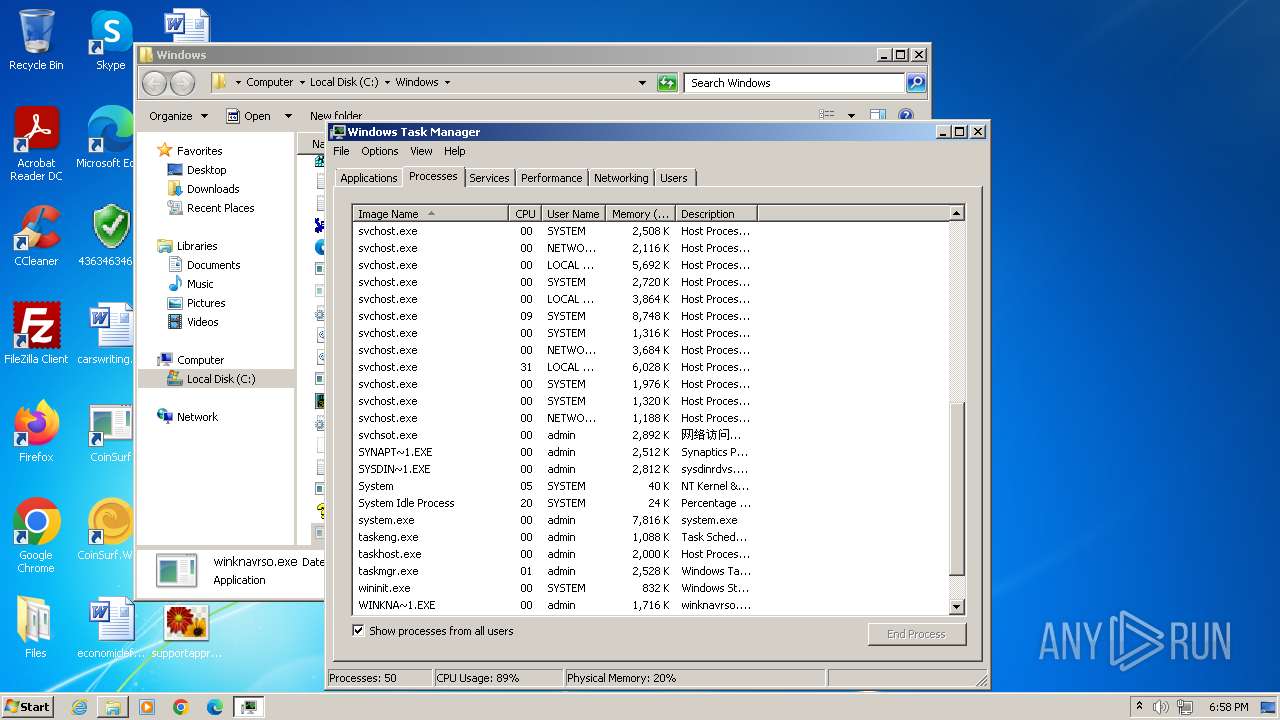
MALICIOUS
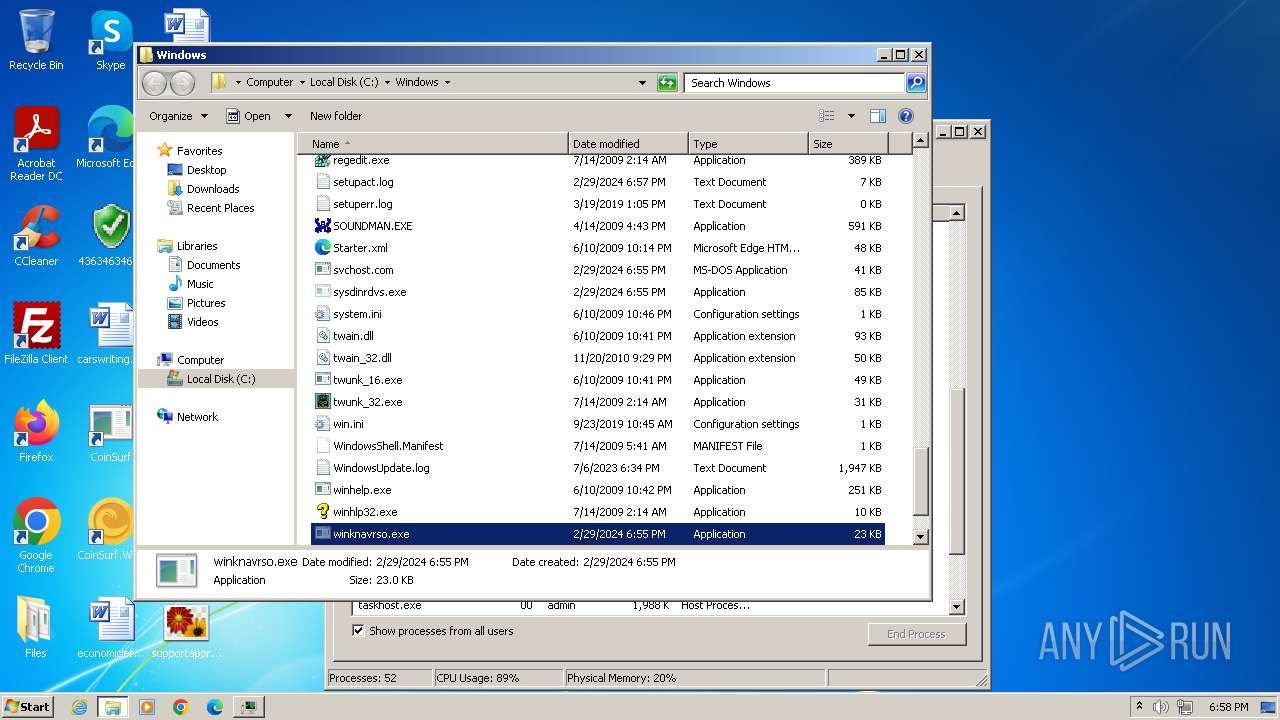
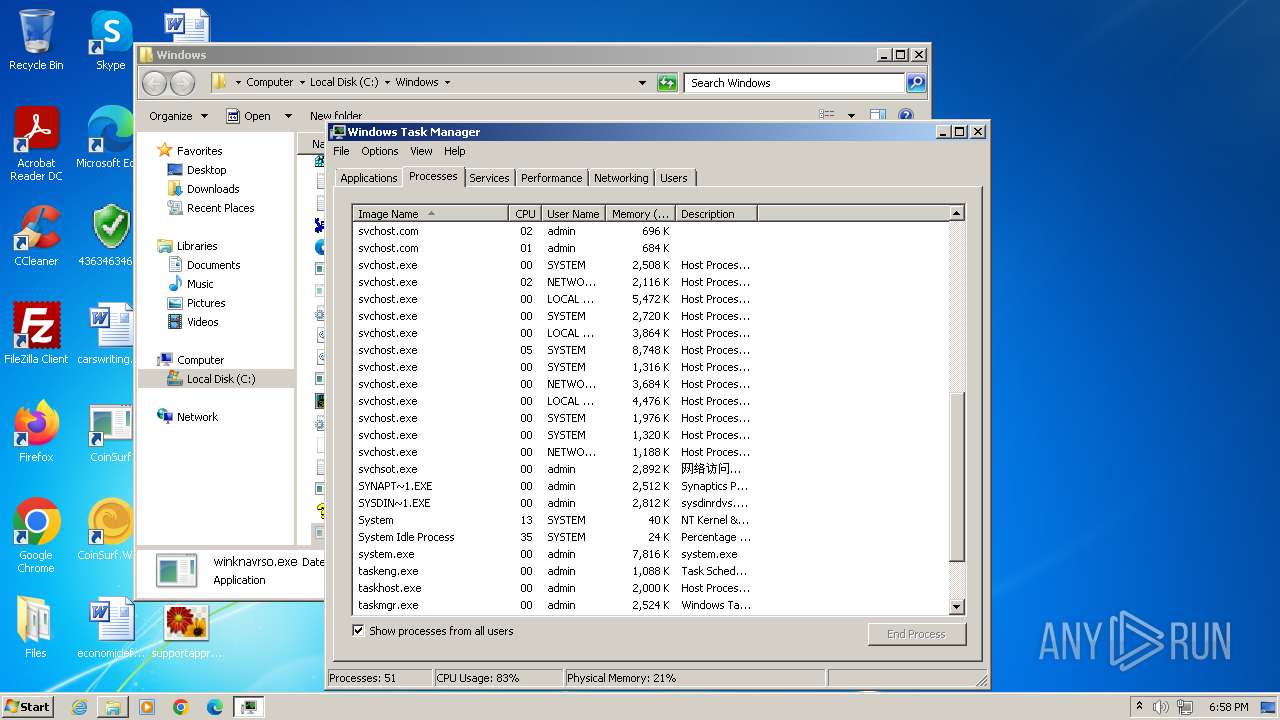
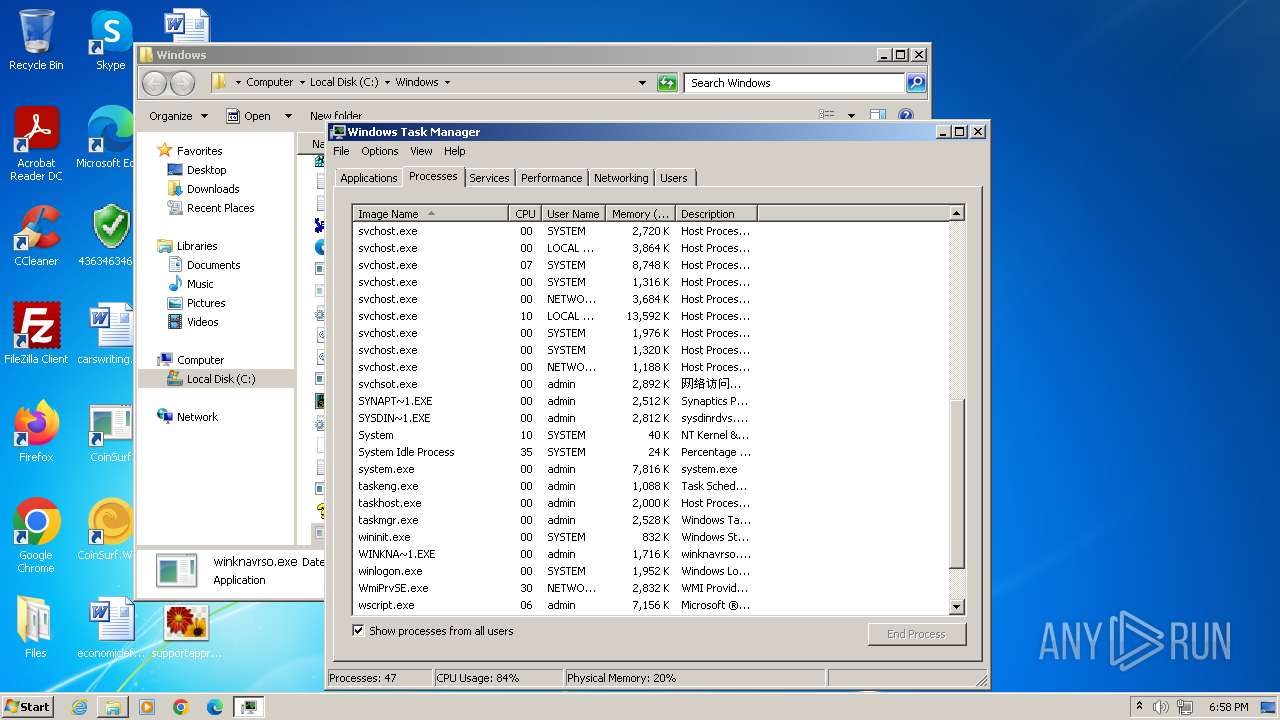
Drops the executable file immediately after the start
- svchost.com (PID: 3784)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2088)
- pinf.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 1796)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 3036)
- l.exe (PID: 1972)
- 1357116943.exe (PID: 696)
- 4363463463464363463463463.exe (PID: 3548)
- ghjkl.exe (PID: 4488)
- 4363463463464363463463463.exe (PID: 1544)
- BBLb.exe (PID: 4788)
- npp.exe (PID: 5112)
- msfiler.exe (PID: 4504)
- DCRatBuild.exe (PID: 5840)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3832)
- ContainerserverFontSavessession.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3780)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- v4install.exe (PID: 1384)
- svchost.com (PID: 4340)
- 2349315902.exe (PID: 4440)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- agentServerComponent.exe (PID: 2344)
- inte.exe (PID: 2512)
- InstallSetup_six.exe (PID: 4616)
- ransom_builder.exe (PID: 5116)
- cp.exe (PID: 4280)
- 2802015576.exe (PID: 5364)
- AttributeString.exe (PID: 5176)
- AttributeString.exe (PID: 5944)
- more.exe (PID: 5912)
- more.exe (PID: 6168)
- safman_setup.exe (PID: 7588)
- tpeinf.exe (PID: 7644)
- National.exe (PID: 4016)
- server.exe (PID: 7932)
- look2.exe (PID: 8024)
- HD_._cache_server.exe (PID: 2556)
- ._cache_server.exe (PID: 8012)
- InstallSetup9.exe (PID: 5928)
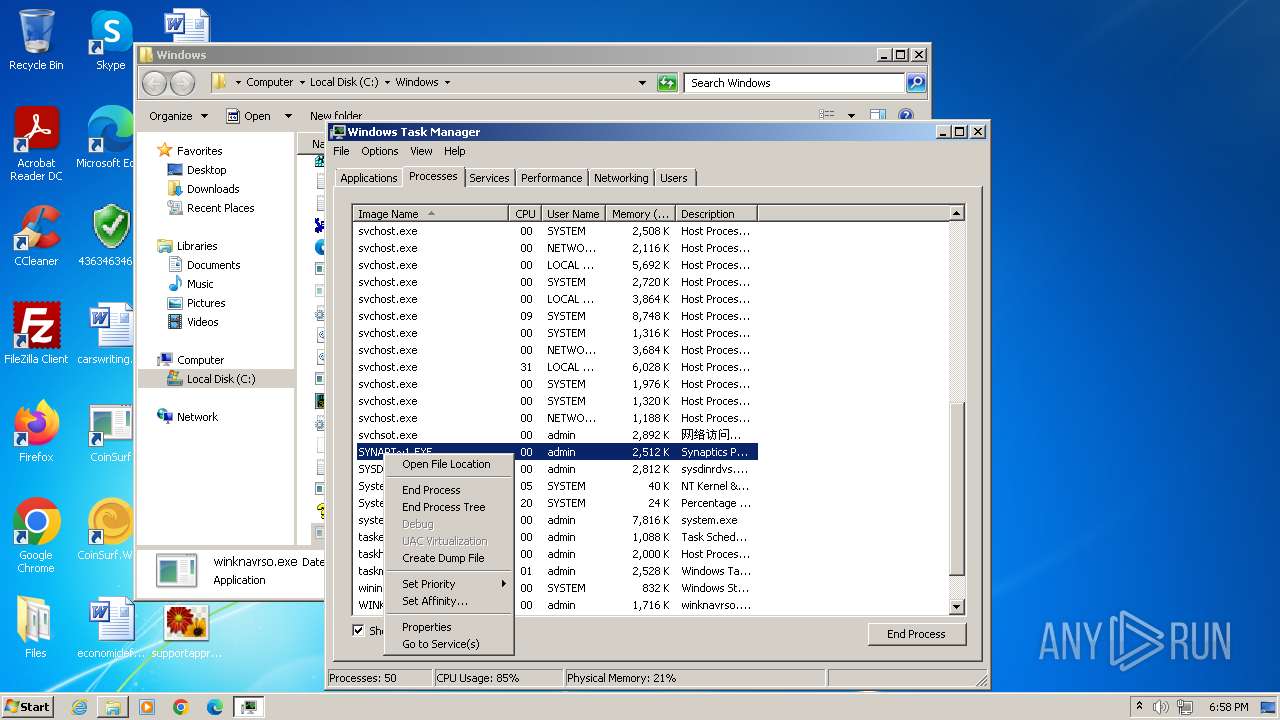
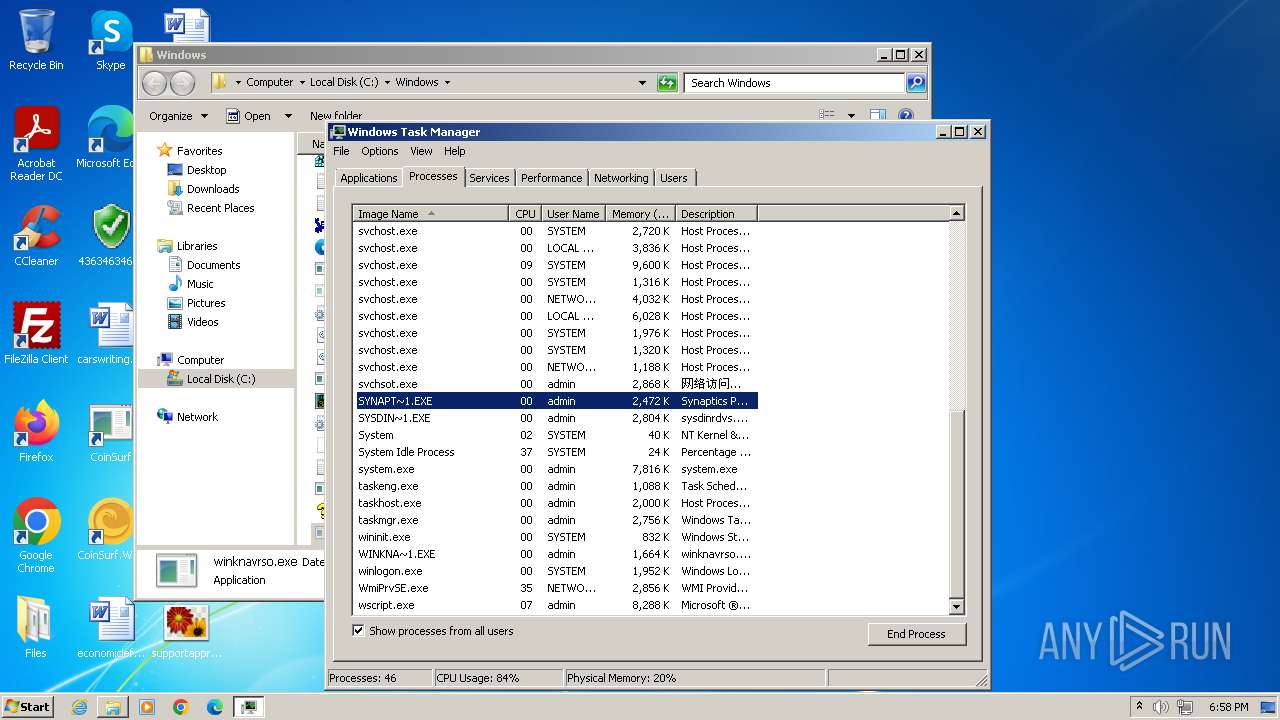
- Synaptics.exe (PID: 8100)
- NINJA.exe (PID: 6272)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 6712)
- 228.exe (PID: 7220)
- Setup2010u32.exe (PID: 6748)
- csaff.exe (PID: 4560)
- InstallSetup5.exe (PID: 6780)
- Update.exe (PID: 6084)
- svchost.com (PID: 2704)
- Synaptics.exe (PID: 2564)
Changes the autorun value in the registry
- clip.exe (PID: 1820)
- 1357116943.exe (PID: 696)
- 2349315902.exe (PID: 4440)
- 2802015576.exe (PID: 5364)
- server.exe (PID: 7932)
- HD_._cache_server.exe (PID: 2556)
- NINJA.exe (PID: 6272)
UAC/LUA settings modification
- miner.exe (PID: 2692)
Adds process to the Windows Defender exclusion list
- miner.exe (PID: 2692)
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
- svchost.com (PID: 2180)
- svchost.com (PID: 1156)
- mdnsresp.exe (PID: 2816)
Bypass execution policy to execute commands
- powershell.exe (PID: 2160)
- powershell.exe (PID: 1172)
- powershell.exe (PID: 4216)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5320)
- powershell.exe (PID: 5480)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 6644)
- powershell.exe (PID: 7708)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 2668)
- powershell.exe (PID: 2100)
Changes powershell execution policy (Bypass)
- socks5-clean.exe (PID: 2304)
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
- svchost.com (PID: 4052)
- svchost.com (PID: 2172)
- svchost.com (PID: 1156)
- svchost.com (PID: 2180)
Run PowerShell with an invisible window
- powershell.exe (PID: 2160)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 6644)
- powershell.exe (PID: 7708)
Changes Security Center notification settings
- 1357116943.exe (PID: 696)
- 2349315902.exe (PID: 4440)
- 2802015576.exe (PID: 5364)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 1336)
Adds path to the Windows Defender exclusion list
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
- svchost.com (PID: 3224)
- more.exe (PID: 5912)
- mdnsresp.exe (PID: 2816)
- svchost.com (PID: 2172)
- svchost.com (PID: 4052)
Create files in the Startup directory
- msfiler.exe (PID: 4504)
- NINJA.exe (PID: 6272)
Disables Windows Defender
- niks.exe (PID: 5584)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5872)
- wscript.exe (PID: 4420)
- wscript.exe (PID: 3932)
Actions looks like stealing of personal data
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- svchost.com (PID: 4340)
- chrome.exe (PID: 4664)
- chrome.exe (PID: 6112)
- chrome.exe (PID: 4556)
- msedge.exe (PID: 7352)
- msedge.exe (PID: 7620)
- msedge.exe (PID: 3320)
- msedge.exe (PID: 7808)
- chrome.exe (PID: 3588)
- chrome.exe (PID: 5588)
- msedge.exe (PID: 7816)
- chrome.exe (PID: 4136)
- msedge.exe (PID: 5104)
- chrome.exe (PID: 2360)
- msedge.exe (PID: 7732)
- msedge.exe (PID: 8000)
- chrome.exe (PID: 6608)
- chrome.exe (PID: 8060)
Changes the Windows auto-update feature
- niks.exe (PID: 5584)
PHORPIEX has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 3988)
- 1357116943.exe (PID: 696)
- 4363463463464363463463463.exe (PID: 3548)
- 2349315902.exe (PID: 4440)
- 4363463463464363463463463.exe (PID: 3832)
- 2802015576.exe (PID: 5364)
DcRAT is detected
- agentServerComponent.exe (PID: 2344)
Starts CMD.EXE for self-deleting
- svchost.com (PID: 5572)
- svchost.com (PID: 3044)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 2512)
- inte.exe (PID: 8076)
Connects to the CnC server
- 1357116943.exe (PID: 696)
- u3e4.0.exe (PID: 5108)
- u3k8.0.exe (PID: 6120)
- syncUpd.exe (PID: 6688)
- HD_._cache_server.exe (PID: 2556)
- 2802015576.exe (PID: 5364)
ASYNCRAT has been detected (MUTEX)
- more.exe (PID: 6168)
XWORM has been detected (YARA)
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
GH0ST mutex has been found
- look2.exe (PID: 8024)
Creates a writable file in the system directory
- look2.exe (PID: 8024)
- HD_._cache_server.exe (PID: 2556)
RISEPRO has been detected (YARA)
- StealerClient_Sharp_1_4.exe (PID: 4712)
- StealerClient_Cpp_1_3_1.exe (PID: 6104)
- StealerClient_Cpp_1_3.exe (PID: 4156)
- RetailerRise.exe (PID: 4564)
VIDAR has been detected (YARA)
- r.exe (PID: 4352)
ASYNCRAT has been detected (YARA)
- reo.exe (PID: 5676)
Checks whether a specified folder exists (SCRIPT)
- 7zipFOPBACKEND.exe (PID: 7944)
LUMMA has been detected (YARA)
- AppLaunch.exe (PID: 4760)
Deletes a file (SCRIPT)
- IconRemoval.exe (PID: 4132)
DCRAT has been detected (YARA)
- minuscrypt_crypted.exe (PID: 392)
LUMMA has been detected (SURICATA)
- AppLaunch.exe (PID: 4760)
STEALC has been detected (SURICATA)
- u3e4.0.exe (PID: 5108)
- u3k8.0.exe (PID: 6120)
- syncUpd.exe (PID: 6688)
DCRAT has been detected (SURICATA)
- AppLaunch.exe (PID: 6040)
GH0ST has been detected (SURICATA)
- HD_._cache_server.exe (PID: 2556)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2928)
- pinf.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- clip.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 3832)
- miner.exe (PID: 2692)
- powershell.exe (PID: 392)
- socks5-clean.exe (PID: 2304)
- build6_unencrypted.exe (PID: 1408)
- powershell.exe (PID: 1172)
- inte.exe (PID: 2512)
- powershell.exe (PID: 4216)
- msfiler.exe (PID: 4424)
- powershell.exe (PID: 4456)
- ghjkl.exe (PID: 4488)
- r.exe (PID: 4352)
- 1357116943.exe (PID: 696)
- msfiler.exe (PID: 4504)
- powershell.exe (PID: 5064)
- npp.exe (PID: 5112)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5320)
- powershell.exe (PID: 5480)
- more.exe (PID: 5912)
- DCRatBuild.exe (PID: 5840)
- powershell.exe (PID: 6012)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- wscript.exe (PID: 5872)
- v4install.exe (PID: 1384)
- Client.exe (PID: 4928)
- wscript.exe (PID: 4420)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- 2349315902.exe (PID: 4440)
- gookcom.exe (PID: 5188)
- InstallSetup_six.exe (PID: 4616)
- u3e4.0.exe (PID: 5108)
- data64_6.exe (PID: 4652)
- AppLaunch.exe (PID: 4760)
- u3k8.0.exe (PID: 6120)
- AttributeString.exe (PID: 5176)
- well.exe (PID: 4536)
- chrome.exe (PID: 4556)
- 2802015576.exe (PID: 5364)
- powershell.exe (PID: 4628)
- AppLaunch.exe (PID: 6040)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
- more.exe (PID: 6168)
- cmt.exe (PID: 7148)
- powershell.exe (PID: 6644)
- images.exe (PID: 7392)
- syncUpd.exe (PID: 6688)
- ama.exe (PID: 5712)
- tpeinf.exe (PID: 7644)
- server.exe (PID: 7932)
- inte.exe (PID: 8076)
- setup_wm.exe (PID: 6856)
- InstallSetup9.exe (PID: 5928)
- KB824105-x86-ENU.exe (PID: 2964)
- 228.exe (PID: 7220)
- MSI.CentralServer.exe (PID: 7508)
- Setup2010u32.exe (PID: 6748)
- powershell.exe (PID: 7708)
- InstallSetup5.exe (PID: 6780)
- fu.exe (PID: 4092)
- PCclear_Eng_mini.exe (PID: 6980)
- wscript.exe (PID: 3932)
- Update.exe (PID: 6084)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 3832)
- r.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- Client.exe (PID: 4928)
- data64_6.exe (PID: 4652)
- chrome.exe (PID: 4556)
- cmt.exe (PID: 7148)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- InstallSetup5.exe (PID: 6780)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3548)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2088)
- pei.exe (PID: 2980)
- pinf.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 2928)
- clip.exe (PID: 1820)
- l.exe (PID: 1972)
- 1357116943.exe (PID: 696)
- 4363463463464363463463463.exe (PID: 3548)
- ghjkl.exe (PID: 4488)
- 4363463463464363463463463.exe (PID: 1544)
- BBLb.exe (PID: 4788)
- msfiler.exe (PID: 4504)
- npp.exe (PID: 5112)
- DCRatBuild.exe (PID: 5840)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3832)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- ContainerserverFontSavessession.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3780)
- v4install.exe (PID: 1384)
- svchost.com (PID: 4340)
- 2349315902.exe (PID: 4440)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- agentServerComponent.exe (PID: 2344)
- inte.exe (PID: 2512)
- InstallSetup_six.exe (PID: 4616)
- ransom_builder.exe (PID: 5116)
- cp.exe (PID: 4280)
- 2802015576.exe (PID: 5364)
- AttributeString.exe (PID: 5176)
- AttributeString.exe (PID: 5944)
- more.exe (PID: 5912)
- more.exe (PID: 6168)
- safman_setup.exe (PID: 7588)
- tpeinf.exe (PID: 7644)
- server.exe (PID: 7932)
- ._cache_server.exe (PID: 8012)
- National.exe (PID: 4016)
- look2.exe (PID: 8024)
- Synaptics.exe (PID: 8100)
- HD_._cache_server.exe (PID: 2556)
- InstallSetup9.exe (PID: 5928)
- NINJA.exe (PID: 6272)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 6712)
- 228.exe (PID: 7220)
- Setup2010u32.exe (PID: 6748)
- csaff.exe (PID: 4560)
- Update.exe (PID: 6084)
- InstallSetup5.exe (PID: 6780)
- Synaptics.exe (PID: 2564)
- svchost.com (PID: 2704)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 3988)
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2928)
- miner.exe (PID: 2692)
- 4363463463464363463463463.exe (PID: 3548)
- socks5-clean.exe (PID: 2304)
- build6_unencrypted.exe (PID: 1408)
- inte.exe (PID: 2512)
- 4363463463464363463463463.exe (PID: 2248)
- ghjkl.exe (PID: 4488)
- msfiler.exe (PID: 4424)
- r.exe (PID: 4352)
- 1357116943.exe (PID: 696)
- msfiler.exe (PID: 4504)
- 4363463463464363463463463.exe (PID: 1796)
- DCRatBuild.exe (PID: 5840)
- more.exe (PID: 5912)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 1336)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- v4install.exe (PID: 1384)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 796)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- 2349315902.exe (PID: 4440)
- gookcom.exe (PID: 5188)
- InstallSetup_six.exe (PID: 4616)
- u3e4.0.exe (PID: 5108)
- 4363463463464363463463463.exe (PID: 848)
- AppLaunch.exe (PID: 4760)
- u3k8.0.exe (PID: 6120)
- 4363463463464363463463463.exe (PID: 2892)
- AttributeString.exe (PID: 5176)
- well.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 3784)
- more.exe (PID: 6168)
- syncUpd.exe (PID: 6688)
- 2802015576.exe (PID: 5364)
- images.exe (PID: 7392)
- ama.exe (PID: 5712)
- tpeinf.exe (PID: 7644)
- server.exe (PID: 7932)
- inte.exe (PID: 8076)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- 228.exe (PID: 7220)
- 4363463463464363463463463.exe (PID: 2124)
- MSI.CentralServer.exe (PID: 7508)
- Setup2010u32.exe (PID: 6748)
- InstallSetup5.exe (PID: 6780)
- fu.exe (PID: 4092)
- PCclear_Eng_mini.exe (PID: 6980)
- Update.exe (PID: 6084)
Process drops legitimate windows executable
- clip.exe (PID: 1820)
- Update.exe (PID: 6084)
The process creates files with name similar to system file names
- clip.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 3036)
- NINJA.exe (PID: 6272)
- Update.exe (PID: 6084)
Starts itself from another location
- clip.exe (PID: 1820)
- agentServerComponent.exe (PID: 4696)
- AttributeString.exe (PID: 5176)
- 2802015576.exe (PID: 5364)
Starts POWERSHELL.EXE for commands execution
- miner.exe (PID: 2692)
- build6_unencrypted.exe (PID: 1408)
- socks5-clean.exe (PID: 2304)
- msfiler.exe (PID: 4424)
- msfiler.exe (PID: 4504)
- svchost.com (PID: 5368)
- svchost.com (PID: 3224)
- svchost.com (PID: 2800)
- svchost.com (PID: 4052)
- svchost.com (PID: 2172)
- svchost.com (PID: 1156)
- svchost.com (PID: 2180)
Script adds exclusion process to Windows Defender
- miner.exe (PID: 2692)
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 392)
- powershell.exe (PID: 1172)
- powershell.exe (PID: 4216)
- powershell.exe (PID: 4456)
- powershell.exe (PID: 5064)
- powershell.exe (PID: 5204)
- powershell.exe (PID: 5480)
- powershell.exe (PID: 5320)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 4628)
- powershell.exe (PID: 6644)
- powershell.exe (PID: 7708)
The process executes Powershell scripts
- socks5-clean.exe (PID: 2304)
Script adds exclusion path to Windows Defender
- miner.exe (PID: 2692)
- build6_unencrypted.exe (PID: 1408)
- msfiler.exe (PID: 4504)
Base64-obfuscated command line is found
- msfiler.exe (PID: 4424)
- svchost.com (PID: 5368)
- svchost.com (PID: 2800)
Application launched itself
- msfiler.exe (PID: 4424)
- ghjkl.exe (PID: 4488)
- BBLb.exe (PID: 4680)
- Client.exe (PID: 4880)
- asdfg.exe (PID: 3500)
- AttributeString.exe (PID: 5660)
- chrome.exe (PID: 4556)
- more.exe (PID: 5912)
- net.exe (PID: 7128)
- ghjk.exe (PID: 1092)
- ghjkl.exe (PID: 7556)
- AttributeString.exe (PID: 7056)
- MSBuild.exe (PID: 7500)
- msedge.exe (PID: 7352)
- msedge.exe (PID: 3320)
- msedge.exe (PID: 7808)
- chrome.exe (PID: 5588)
- chrome.exe (PID: 8060)
- msedge.exe (PID: 5104)
- chrome.exe (PID: 2360)
- msedge.exe (PID: 8000)
- Synaptics.exe (PID: 2192)
- WerFault.exe (PID: 336)
- mdnsresp.exe (PID: 2208)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 784)
BASE64 encoded PowerShell command has been detected
- msfiler.exe (PID: 4424)
- svchost.com (PID: 2800)
Checks Windows Trust Settings
- r.exe (PID: 4352)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- InstallSetup5.exe (PID: 6780)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 5000)
Reads the BIOS version
- niks.exe (PID: 5584)
- new.exe (PID: 5292)
- amert.exe (PID: 6532)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 784)
The process executes via Task Scheduler
- powershell.exe (PID: 6012)
- AttributeString.exe (PID: 5176)
- powershell.exe (PID: 6644)
- AttributeString.exe (PID: 7056)
- powershell.exe (PID: 7708)
- sipnotify.exe (PID: 1468)
- ctfmon.exe (PID: 1464)
Starts application with an unusual extension
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 796)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- 4363463463464363463463463.exe (PID: 1544)
- inte.exe (PID: 2512)
- gookcom.exe (PID: 5188)
- 4363463463464363463463463.exe (PID: 784)
- InstallSetup_six.exe (PID: 4616)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 3988)
- well.exe (PID: 4536)
- AttributeString.exe (PID: 5176)
- cmd.exe (PID: 3200)
- more.exe (PID: 5912)
- 4363463463464363463463463.exe (PID: 3784)
- cmd.exe (PID: 6976)
- more.exe (PID: 6168)
- ama.exe (PID: 5712)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 1796)
- MSI.CentralServer.exe (PID: 7508)
- 4363463463464363463463463.exe (PID: 2124)
- inte.exe (PID: 8076)
- InstallSetup9.exe (PID: 5928)
- fu.exe (PID: 4092)
- wscript.exe (PID: 3932)
- Update.exe (PID: 6084)
- runonce.exe (PID: 1984)
- wscript.exe (PID: 2368)
- mdnsresp.exe (PID: 2816)
- mdnsresp.exe (PID: 2208)
Executing commands from a ".bat" file
- wscript.exe (PID: 5872)
- wscript.exe (PID: 4420)
- u3e4.1.exe (PID: 2776)
- u3k8.1.exe (PID: 4272)
- more.exe (PID: 6168)
- CleanUp Icons FOP.exe (PID: 7400)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5872)
- wscript.exe (PID: 4420)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5872)
- wscript.exe (PID: 4420)
- svchost.com (PID: 5572)
- u3e4.1.exe (PID: 2776)
- u3k8.1.exe (PID: 4272)
- more.exe (PID: 6168)
- NINJA.exe (PID: 6272)
- CleanUp Icons FOP.exe (PID: 7400)
- svchost.com (PID: 3044)
- system.exe (PID: 2220)
Connects to unusual port
- powershell.exe (PID: 2160)
- 4363463463464363463463463.exe (PID: 3548)
- build6_unencrypted.exe (PID: 1408)
- 4363463463464363463463463.exe (PID: 3832)
- msfiler.exe (PID: 4504)
- 1357116943.exe (PID: 696)
- powershell.exe (PID: 5384)
- reo.exe (PID: 5676)
- 4363463463464363463463463.exe (PID: 2892)
- HD_._cache_server.exe (PID: 2556)
- 2802015576.exe (PID: 5364)
- MSBuild.exe (PID: 7968)
- 4363463463464363463463463.exe (PID: 2832)
- LostArk.exe (PID: 6768)
- jsc.exe (PID: 5812)
Unusual connection from system programs
- powershell.exe (PID: 2160)
- powershell.exe (PID: 5384)
The Powershell connects to the Internet
- powershell.exe (PID: 2160)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- r.exe (PID: 4352)
- data64_6.exe (PID: 4652)
The executable file from the user directory is run by the CMD process
- agentServerComponent.exe (PID: 4696)
- images.exe (PID: 7392)
Potential TCP-based PowerShell reverse shell connection
- svchost.com (PID: 5368)
Suspicious use of symmetric encryption in PowerShell
- svchost.com (PID: 5368)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 392)
- cmd.exe (PID: 7768)
Windows Defender mutex has been found
- u3e4.0.exe (PID: 5108)
- u3k8.0.exe (PID: 6120)
- syncUpd.exe (PID: 6688)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
Starts a Microsoft application from unusual location
- setup_wm.exe (PID: 6856)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6996)
Reads the Windows owner or organization settings
- SAFMAN~1.tmp (PID: 7596)
- %E5%88~1.tmp (PID: 5484)
Reads the date of Windows installation
- server.exe (PID: 7932)
Suspicious files were dropped or overwritten
- look2.exe (PID: 8024)
Creates or modifies Windows services
- look2.exe (PID: 8024)
Detected use of alternative data streams (AltDS)
- NINJA.exe (PID: 6272)
The process executes VB scripts
- NINJA.exe (PID: 6272)
- system.exe (PID: 2220)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 6508)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6508)
- IconRemoval.exe (PID: 4132)
- 7zipFOPBACKEND.exe (PID: 7944)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 6508)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2104)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 848)
- miner.exe (PID: 2692)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- cayV0Deo9jSt417.exe (PID: 2308)
- taskhost.exe (PID: 584)
- inte.exe (PID: 2512)
- 4363463463464363463463463.exe (PID: 3832)
- l.exe (PID: 1972)
- Windows.exe (PID: 3616)
- 1357116943.exe (PID: 696)
- 2722617096.exe (PID: 116)
- build6_unencrypted.exe (PID: 1408)
- socks5-clean.exe (PID: 2304)
- r.exe (PID: 4352)
- msfiler.exe (PID: 4424)
- ghjkl.exe (PID: 4488)
- msfiler.exe (PID: 4504)
- BBLb.exe (PID: 4680)
- ghjkl.exe (PID: 4700)
- StealerClient_Sharp_1_4.exe (PID: 4712)
- BBLb.exe (PID: 4788)
- Client.exe (PID: 4880)
- Client.exe (PID: 4928)
- npp.exe (PID: 5112)
- 32.exe (PID: 5504)
- niks.exe (PID: 5584)
- 625825249.exe (PID: 5848)
- more.exe (PID: 5912)
- DCRatBuild.exe (PID: 5840)
- StealerClient_Cpp_1_3_1.exe (PID: 6104)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- svchost.com (PID: 4132)
- StealerClient_Cpp_1_3.exe (PID: 4156)
- ContainerserverFontSavessession.exe (PID: 1956)
- svchost.com (PID: 4340)
- svchost.com (PID: 4316)
- cp.exe (PID: 4280)
- svchost.com (PID: 4232)
- svchost.com (PID: 3972)
- InstallSetupNew.exe (PID: 4396)
- 2349315902.exe (PID: 4440)
- svchost.com (PID: 4412)
- v4install.exe (PID: 1384)
- svchost.com (PID: 2896)
- ghjk.exe (PID: 1092)
- ghjk.exe (PID: 4584)
- svchost.com (PID: 4476)
- RetailerRise.exe (PID: 4564)
- svchost.com (PID: 4588)
- svchost.com (PID: 4612)
- InstallSetup_six.exe (PID: 4616)
- svchost.com (PID: 2748)
- svchost.com (PID: 4804)
- agentServerComponent.exe (PID: 2344)
- SystemUpdate.exe (PID: 4864)
- agentServerComponent.exe (PID: 4696)
- u3e4.0.exe (PID: 5108)
- svchost.com (PID: 5096)
- svchost.com (PID: 5132)
- T1_Net.exe (PID: 5144)
- svchost.com (PID: 5252)
- new.exe (PID: 5292)
- svchost.com (PID: 5172)
- gookcom.exe (PID: 5188)
- svchost.com (PID: 5368)
- HvWV9sWWpvnzp.exe (PID: 5560)
- svchost.com (PID: 5572)
- svchost.com (PID: 5428)
- ransom_builder.exe (PID: 5116)
- svchost.com (PID: 5908)
- svchost.com (PID: 6064)
- lumma123142124.exe (PID: 6084)
- asdfg.exe (PID: 3500)
- 482521965.exe (PID: 864)
- svchost.com (PID: 2340)
- u3k8.0.exe (PID: 6120)
- svchost.com (PID: 5888)
- jeditor.exe (PID: 584)
- asdfg.exe (PID: 5900)
- svchost.com (PID: 1432)
- svchost.com (PID: 4320)
- svchost.com (PID: 2864)
- chdyz.exe (PID: 3652)
- svchost.com (PID: 2016)
- svchost.com (PID: 5944)
- RegAsm.exe (PID: 4032)
- National.exe (PID: 4016)
- svchost.com (PID: 3932)
- news_01.exe (PID: 5704)
- reo.exe (PID: 5676)
- ama.exe (PID: 5712)
- data64_6.exe (PID: 4652)
- svchost.com (PID: 3892)
- u3e4.1.exe (PID: 2776)
- svchost.com (PID: 4664)
- AppLaunch.exe (PID: 4760)
- AttributeString.exe (PID: 5176)
- 2802015576.exe (PID: 5364)
- svchost.com (PID: 4284)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 4248)
- svchost.com (PID: 1192)
- svchost.com (PID: 5804)
- minuscrypt_crypted.exe (PID: 392)
- AppLaunch.exe (PID: 6040)
- svchost.com (PID: 2624)
- u3k8.1.exe (PID: 4272)
- AttributeString.exe (PID: 5660)
- AttributeString.exe (PID: 5944)
- 1464739324.exe (PID: 5704)
- svchost.com (PID: 4628)
- well.exe (PID: 4536)
- svchost.com (PID: 5652)
- chrome.exe (PID: 4556)
- svchost.com (PID: 5196)
- svchost.com (PID: 4240)
- chrome.exe (PID: 4260)
- svchost.com (PID: 4676)
- chrome.exe (PID: 4664)
- chrome.exe (PID: 5172)
- chrome.exe (PID: 6012)
- chrome.exe (PID: 6112)
- chrome.exe (PID: 5112)
- chcp.com (PID: 5884)
- svchost.com (PID: 3224)
- svchost.com (PID: 3476)
- more.exe (PID: 6168)
- svchost.com (PID: 6384)
- chrome.exe (PID: 6372)
- svchost.com (PID: 6392)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
- svchost.com (PID: 6604)
- hv.exe (PID: 6616)
- svchost.com (PID: 6668)
- svchost.com (PID: 6676)
- svchost.com (PID: 6840)
- 755526995.exe (PID: 6848)
- setup_wm.exe (PID: 6856)
- chrome.exe (PID: 6868)
- syncUpd.exe (PID: 6688)
- svchost.com (PID: 6960)
- chcp.com (PID: 7020)
- chrome.exe (PID: 7040)
- svchost.com (PID: 6968)
- net.exe (PID: 7128)
- cmt.exe (PID: 7148)
- net.exe (PID: 7228)
- svchost.com (PID: 7060)
- images.exe (PID: 7392)
- chrome.exe (PID: 7448)
- MSI.CentralServer.exe (PID: 7508)
- svchost.com (PID: 7576)
- ghjkl.exe (PID: 7556)
- safman_setup.exe (PID: 7588)
- SAFMAN~1.tmp (PID: 7596)
- svchost.com (PID: 7496)
- svchost.com (PID: 7548)
- tpeinf.exe (PID: 7644)
- svchost.com (PID: 7636)
- svchost.com (PID: 7660)
- svchost.com (PID: 7652)
- cs_maltest.exe (PID: 7684)
- svchost.exe (PID: 7692)
- ghjkl.exe (PID: 7608)
- svchost.com (PID: 7624)
- svchost.com (PID: 7852)
- LM.exe (PID: 7860)
- 88795851.exe (PID: 7892)
- svchost.com (PID: 7900)
- svchost.com (PID: 7908)
- svchost.com (PID: 7924)
- ._cache_server.exe (PID: 8012)
- server.exe (PID: 7932)
- look2.exe (PID: 8024)
- MSBuild.exe (PID: 8044)
- svchost.com (PID: 8052)
- inte.exe (PID: 8076)
- Synaptics.exe (PID: 8100)
- HD_._cache_server.exe (PID: 2556)
- svchost.com (PID: 5920)
- InstallSetup9.exe (PID: 5928)
- 987123.exe (PID: 2100)
- svchost.com (PID: 6224)
- NINJA.exe (PID: 6272)
- svchost.com (PID: 6164)
- 2479520700.exe (PID: 6408)
- svchost.com (PID: 6488)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 6712)
- svchost.com (PID: 6736)
- %E5%88~1.tmp (PID: 5484)
- svchost.com (PID: 5488)
- svchost.com (PID: 2512)
- svchost.com (PID: 5188)
- KB824105-x86-ENU.exe (PID: 2964)
- AttributeString.exe (PID: 7056)
- svchost.com (PID: 5180)
- AttributeString.exe (PID: 6992)
- soft.exe (PID: 7200)
- 112711300.exe (PID: 6540)
- svchost.com (PID: 6528)
- 228.exe (PID: 7220)
- svchost.com (PID: 7364)
- Setup2010u32.exe (PID: 6748)
- LostArk.exe (PID: 6768)
- svchost.com (PID: 6804)
- svchost.com (PID: 6664)
- MSBuild.exe (PID: 7500)
- svchost.com (PID: 1348)
- CleanUp Icons FOP.exe (PID: 7400)
- svchost.com (PID: 7232)
- MSI.CentralServer.exe (PID: 7308)
- mode.com (PID: 7520)
- svchost.com (PID: 3044)
- jsc.exe (PID: 5812)
- MSBuild.exe (PID: 7968)
- 7zipFOPBACKEND.exe (PID: 7944)
- IconRemoval.exe (PID: 4132)
- csaff.exe (PID: 6140)
- svchost.com (PID: 4660)
- svchost.com (PID: 2292)
- csaff.exe (PID: 4560)
- svchost.com (PID: 7892)
- amert.exe (PID: 6532)
- svchost.com (PID: 6404)
- nsw673F.tmp (PID: 4252)
- Update.exe (PID: 6084)
- svchost.com (PID: 6332)
- InstallSetup5.exe (PID: 6780)
- svchost.com (PID: 6824)
- fu.exe (PID: 4092)
- svchost.com (PID: 5624)
- PCclear_Eng_mini.exe (PID: 6980)
- svchost.com (PID: 5164)
- svchost.com (PID: 6760)
- svchost.com (PID: 5736)
- msedge.exe (PID: 7352)
- svchost.com (PID: 448)
- svchost.com (PID: 7008)
- svchost.com (PID: 7304)
- msedge.exe (PID: 7808)
- chrome.exe (PID: 5588)
- svchost.com (PID: 5076)
- msedge.exe (PID: 5104)
- msedge.exe (PID: 7620)
- msedge.exe (PID: 3320)
- chrome.exe (PID: 3588)
- chrome.exe (PID: 8060)
- svchost.com (PID: 7956)
- msedge.exe (PID: 8000)
- chrome.exe (PID: 2360)
- msedge.exe (PID: 7816)
- chrome.exe (PID: 6608)
- svchost.com (PID: 7636)
- chrome.exe (PID: 8044)
- svchost.com (PID: 7772)
- svchost.com (PID: 2324)
- chrome.exe (PID: 4136)
- msedge.exe (PID: 7732)
- svchost.com (PID: 8048)
- svchost.com (PID: 8364)
- svchost.com (PID: 8380)
- svchost.com (PID: 8416)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2928)
- miner.exe (PID: 2692)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- cayV0Deo9jSt417.exe (PID: 2308)
- l.exe (PID: 1972)
- 4363463463464363463463463.exe (PID: 3832)
- Windows.exe (PID: 3616)
- build6_unencrypted.exe (PID: 1408)
- socks5-clean.exe (PID: 2304)
- msfiler.exe (PID: 4424)
- inte.exe (PID: 2512)
- ghjkl.exe (PID: 4488)
- msfiler.exe (PID: 4504)
- r.exe (PID: 4352)
- StealerClient_Sharp_1_4.exe (PID: 4712)
- BBLb.exe (PID: 4788)
- BBLb.exe (PID: 4680)
- Client.exe (PID: 4880)
- 1357116943.exe (PID: 696)
- Client.exe (PID: 4928)
- npp.exe (PID: 5112)
- niks.exe (PID: 5584)
- more.exe (PID: 5912)
- DCRatBuild.exe (PID: 5840)
- ContainerserverFontSavessession.exe (PID: 1956)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- v4install.exe (PID: 1384)
- ghjk.exe (PID: 1092)
- InstallSetupNew.exe (PID: 4396)
- agentServerComponent.exe (PID: 4696)
- agentServerComponent.exe (PID: 2344)
- SystemUpdate.exe (PID: 4864)
- T1_Net.exe (PID: 5144)
- gookcom.exe (PID: 5188)
- 2349315902.exe (PID: 4440)
- InstallSetup_six.exe (PID: 4616)
- new.exe (PID: 5292)
- u3e4.0.exe (PID: 5108)
- lumma123142124.exe (PID: 6084)
- asdfg.exe (PID: 3500)
- jeditor.exe (PID: 584)
- ransom_builder.exe (PID: 5116)
- u3k8.0.exe (PID: 6120)
- National.exe (PID: 4016)
- cp.exe (PID: 4280)
- chdyz.exe (PID: 3652)
- data64_6.exe (PID: 4652)
- HvWV9sWWpvnzp.exe (PID: 5560)
- u3e4.1.exe (PID: 2776)
- reo.exe (PID: 5676)
- AppLaunch.exe (PID: 4760)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 4248)
- AppLaunch.exe (PID: 6040)
- u3k8.1.exe (PID: 4272)
- AttributeString.exe (PID: 5176)
- AttributeString.exe (PID: 5660)
- AttributeString.exe (PID: 5944)
- well.exe (PID: 4536)
- chrome.exe (PID: 4556)
- chrome.exe (PID: 4260)
- chrome.exe (PID: 6112)
- more.exe (PID: 6168)
- 2802015576.exe (PID: 5364)
- chrome.exe (PID: 6372)
- hv.exe (PID: 6616)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
- setup_wm.exe (PID: 6856)
- cmt.exe (PID: 7148)
- syncUpd.exe (PID: 6688)
- chrome.exe (PID: 7040)
- net.exe (PID: 7128)
- images.exe (PID: 7392)
- ama.exe (PID: 5712)
- tpeinf.exe (PID: 7644)
- svchost.exe (PID: 7692)
- SAFMAN~1.tmp (PID: 7596)
- server.exe (PID: 7932)
- look2.exe (PID: 8024)
- Synaptics.exe (PID: 8100)
- inte.exe (PID: 8076)
- HD_._cache_server.exe (PID: 2556)
- InstallSetup9.exe (PID: 5928)
- NINJA.exe (PID: 6272)
- %E5%88~1.tmp (PID: 5484)
- KB824105-x86-ENU.exe (PID: 2964)
- AttributeString.exe (PID: 7056)
- ._cache_server.exe (PID: 8012)
- AttributeString.exe (PID: 6992)
- 228.exe (PID: 7220)
- MSI.CentralServer.exe (PID: 7508)
- Setup2010u32.exe (PID: 6748)
- ghjkl.exe (PID: 7556)
- LostArk.exe (PID: 6768)
- MSBuild.exe (PID: 7500)
- jsc.exe (PID: 5812)
- soft.exe (PID: 7200)
- 7zipFOPBACKEND.exe (PID: 7944)
- MSBuild.exe (PID: 7968)
- IconRemoval.exe (PID: 4132)
- csaff.exe (PID: 6140)
- Update.exe (PID: 6084)
- InstallSetup5.exe (PID: 6780)
- fu.exe (PID: 4092)
- msedge.exe (PID: 7352)
- PCclear_Eng_mini.exe (PID: 6980)
- chrome.exe (PID: 5588)
- amert.exe (PID: 6532)
- msedge.exe (PID: 3320)
- msedge.exe (PID: 7808)
- msedge.exe (PID: 5104)
- chrome.exe (PID: 8060)
- chrome.exe (PID: 2360)
- msedge.exe (PID: 8000)
Reads Environment values
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 3832)
- Windows.exe (PID: 3616)
- miner.exe (PID: 2692)
- ContainerserverFontSavessession.exe (PID: 1956)
- Client.exe (PID: 4928)
- agentServerComponent.exe (PID: 2344)
- r.exe (PID: 4352)
- reo.exe (PID: 5676)
- data64_6.exe (PID: 4652)
- chdyz.exe (PID: 3652)
- AppLaunch.exe (PID: 6040)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
- cmt.exe (PID: 7148)
- KB824105-x86-ENU.exe (PID: 2964)
- Setup2010u32.exe (PID: 6748)
- LostArk.exe (PID: 6768)
- jsc.exe (PID: 5812)
- 7zipFOPBACKEND.exe (PID: 7944)
- IconRemoval.exe (PID: 4132)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2928)
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- cayV0Deo9jSt417.exe (PID: 2308)
- 4363463463464363463463463.exe (PID: 3832)
- l.exe (PID: 1972)
- Windows.exe (PID: 3616)
- build6_unencrypted.exe (PID: 1408)
- inte.exe (PID: 2512)
- msfiler.exe (PID: 4424)
- msfiler.exe (PID: 4504)
- ghjkl.exe (PID: 4488)
- BBLb.exe (PID: 4680)
- r.exe (PID: 4352)
- BBLb.exe (PID: 4788)
- Client.exe (PID: 4880)
- 1357116943.exe (PID: 696)
- npp.exe (PID: 5112)
- miner.exe (PID: 2692)
- more.exe (PID: 5912)
- ContainerserverFontSavessession.exe (PID: 1956)
- Client.exe (PID: 4928)
- ghjk.exe (PID: 1092)
- 2349315902.exe (PID: 4440)
- agentServerComponent.exe (PID: 2344)
- T1_Net.exe (PID: 5144)
- SystemUpdate.exe (PID: 4864)
- gookcom.exe (PID: 5188)
- u3e4.0.exe (PID: 5108)
- asdfg.exe (PID: 3500)
- National.exe (PID: 4016)
- reo.exe (PID: 5676)
- data64_6.exe (PID: 4652)
- AppLaunch.exe (PID: 4760)
- new.exe (PID: 5292)
- u3k8.0.exe (PID: 6120)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 4248)
- AppLaunch.exe (PID: 6040)
- AttributeString.exe (PID: 5660)
- AttributeString.exe (PID: 5944)
- chrome.exe (PID: 4556)
- 2802015576.exe (PID: 5364)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 6412)
- more.exe (PID: 6168)
- cmt.exe (PID: 7148)
- net.exe (PID: 7128)
- syncUpd.exe (PID: 6688)
- images.exe (PID: 7392)
- ghjkl.exe (PID: 7556)
- tpeinf.exe (PID: 7644)
- server.exe (PID: 7932)
- inte.exe (PID: 8076)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- NINJA.exe (PID: 6272)
- KB824105-x86-ENU.exe (PID: 2964)
- AttributeString.exe (PID: 7056)
- AttributeString.exe (PID: 6992)
- LostArk.exe (PID: 6768)
- hv.exe (PID: 6616)
- MSBuild.exe (PID: 7500)
- jsc.exe (PID: 5812)
- 7zipFOPBACKEND.exe (PID: 7944)
- MSBuild.exe (PID: 7968)
- csaff.exe (PID: 6140)
- Update.exe (PID: 6084)
- InstallSetup5.exe (PID: 6780)
- PCclear_Eng_mini.exe (PID: 6980)
- msedge.exe (PID: 7352)
- msedge.exe (PID: 7808)
- msedge.exe (PID: 3320)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 2124)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 2692)
- 4363463463464363463463463.exe (PID: 696)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 3068)
- 4363463463464363463463463.exe (PID: 2744)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 492)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 664)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3352)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 584)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 116)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 2668)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 3464)
- 4363463463464363463463463.exe (PID: 3832)
- 4363463463464363463463463.exe (PID: 392)
- svchost.com (PID: 2292)
- svchost.com (PID: 2080)
- runonce.exe (PID: 1984)
- svchost.com (PID: 2060)
- svchost.com (PID: 2072)
- svchost.com (PID: 2136)
- svchost.com (PID: 2156)
- svchost.com (PID: 2168)
- svchost.com (PID: 2112)
- svchost.com (PID: 2144)
- wmpnscfg.exe (PID: 2952)
- wmpnscfg.exe (PID: 3372)
- svchost.com (PID: 2460)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 796)
- 4363463463464363463463463.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 1796)
- 4363463463464363463463463.exe (PID: 784)
- 4363463463464363463463463.exe (PID: 3780)
- 4363463463464363463463463.exe (PID: 3988)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2892)
- 4363463463464363463463463.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 848)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 3832)
- r.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2124)
- Client.exe (PID: 4928)
- data64_6.exe (PID: 4652)
- cmt.exe (PID: 7148)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- InstallSetup5.exe (PID: 6780)
Checks proxy server information
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- inte.exe (PID: 2512)
- r.exe (PID: 4352)
- 1357116943.exe (PID: 696)
- npp.exe (PID: 5112)
- 2349315902.exe (PID: 4440)
- u3e4.0.exe (PID: 5108)
- AppLaunch.exe (PID: 4760)
- u3k8.0.exe (PID: 6120)
- 2802015576.exe (PID: 5364)
- syncUpd.exe (PID: 6688)
- tpeinf.exe (PID: 7644)
- inte.exe (PID: 8076)
- InstallSetup9.exe (PID: 5928)
- setup_wm.exe (PID: 6856)
- InstallSetup5.exe (PID: 6780)
- PCclear_Eng_mini.exe (PID: 6980)
Create files in a temporary directory
- pei.exe (PID: 2980)
- pinf.exe (PID: 2776)
- l.exe (PID: 1972)
- 4363463463464363463463463.exe (PID: 2088)
- socks5-clean.exe (PID: 2304)
- ghjkl.exe (PID: 4488)
- npp.exe (PID: 5112)
- msfiler.exe (PID: 4504)
- Secure_Cloud_20240206000715989.exe (PID: 4204)
- 1357116943.exe (PID: 696)
- agentServerComponent.exe (PID: 4696)
- InstallSetupNew.exe (PID: 4396)
- powershell.exe (PID: 5384)
- ransom_builder.exe (PID: 5116)
- InstallSetup_six.exe (PID: 4616)
- cp.exe (PID: 4280)
- AttributeString.exe (PID: 5176)
- 2349315902.exe (PID: 4440)
- more.exe (PID: 5912)
- chrome.exe (PID: 4556)
- powershell.exe (PID: 4628)
- 2802015576.exe (PID: 5364)
- more.exe (PID: 6168)
- safman_setup.exe (PID: 7588)
- tpeinf.exe (PID: 7644)
- ._cache_server.exe (PID: 8012)
- National.exe (PID: 4016)
- InstallSetup9.exe (PID: 5928)
- Synaptics.exe (PID: 8100)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 6712)
- NINJA.exe (PID: 6272)
- 228.exe (PID: 7220)
- Setup2010u32.exe (PID: 6748)
- LostArk.exe (PID: 6768)
- CleanUp Icons FOP.exe (PID: 7400)
- InstallSetup5.exe (PID: 6780)
- Update.exe (PID: 6084)
Creates files or folders in the user directory
- pinf.exe (PID: 2776)
- pei.exe (PID: 2980)
- clip.exe (PID: 1820)
- r.exe (PID: 4352)
- BBLb.exe (PID: 4788)
- msfiler.exe (PID: 4504)
- 1357116943.exe (PID: 696)
- inte.exe (PID: 2512)
- v4install.exe (PID: 1384)
- reo.exe (PID: 5676)
- 2349315902.exe (PID: 4440)
- AttributeString.exe (PID: 5944)
- chrome.exe (PID: 4556)
- u3e4.1.exe (PID: 2776)
- more.exe (PID: 5912)
- chrome.exe (PID: 6112)
- more.exe (PID: 6168)
- tpeinf.exe (PID: 7644)
- InstallSetup9.exe (PID: 5928)
- NINJA.exe (PID: 6272)
- LostArk.exe (PID: 6768)
- inte.exe (PID: 8076)
- csaff.exe (PID: 4560)
- Update.exe (PID: 6084)
- msedge.exe (PID: 7352)
- msedge.exe (PID: 7808)
- msedge.exe (PID: 3320)
Drops the executable file immediately after the start
- clip.exe (PID: 1820)
Reads security settings of Internet Explorer
- clip.exe (PID: 1820)
- powershell.exe (PID: 5384)
- powershell.exe (PID: 4628)
Process checks whether UAC notifications are on
- miner.exe (PID: 2692)
- new.exe (PID: 5292)
- LostArk.exe (PID: 6768)
Reads product name
- ContainerserverFontSavessession.exe (PID: 1956)
- agentServerComponent.exe (PID: 2344)
- r.exe (PID: 4352)
- AppLaunch.exe (PID: 6040)
- Setup2010u32.exe (PID: 6748)
Reads mouse settings
- ransom_builder.exe (PID: 5116)
- well.exe (PID: 4536)
- NINJA.exe (PID: 6272)
- fu.exe (PID: 4092)
Process checks computer location settings
- chrome.exe (PID: 5172)
- chrome.exe (PID: 4556)
- chrome.exe (PID: 6012)
- chrome.exe (PID: 6868)
- msedge.exe (PID: 7352)
- msedge.exe (PID: 7808)
- msedge.exe (PID: 3320)
Creates files in the program directory
- server.exe (PID: 7932)
Reads CPU info
- HD_._cache_server.exe (PID: 2556)
Application launched itself
- msedge.exe (PID: 7756)
- msedge.exe (PID: 6736)
- msedge.exe (PID: 3240)
- msedge.exe (PID: 6700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(1408) build6_unencrypted.exe
C2163.5.215.245:9049
Keys
AESNk227ETNaBDg!
Options
Splitter<Agent>
USB drop name
Mutexr3SLo8kx59hai6gX
(PID) Process(4504) msfiler.exe
C25.182.87.154:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
MutexVMFidhoqn75fm5lJ
AsyncRat
(PID) Process(5676) reo.exe
C2 (1)82.115.223.244
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexfnpxcekdvtg
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureR5JBH2qOF7T5fwa7g4eE4qJ0CTWyADGjVvVqEpZLxqOz7ijIknIV9ddo6ba7ZkTKoBhHhGTgyJ6VkPBFfLs2Z002xZYx/yjole+Ba20yb0ZFTo0rvIGTC2W07sVYXYuBPDufInu02QMD/V3ZMybsQNohmDOnbjhQMcN3WkLsCWY=
Keys
AES3a20c7b13b8c19efdcfc7fdc4d6ed716151cf871d53115133cc297be7f298f08
SaltVenomRATByVenom
Lumma
(PID) Process(4760) AppLaunch.exe
C2gstatic-node.io
Options
LummaIDV566Iu--resame
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 681
Monitored processes
1 465
Malicious processes
120
Suspicious processes
43
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 116 | C:\Users\admin\AppData\Local\Temp\2722617096.exe | C:\Users\admin\AppData\Local\Temp\2722617096.exe | — | pei.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 120 | "C:\Windows\svchost.com" "C:\Users\admin\Desktop\Files\NINJA.exe" | C:\Windows\svchost.com | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 120 | "C:\Windows\svchost.com" "C:\Users\admin\Desktop\Files\NINJA.exe" | C:\Windows\svchost.com | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 120 | "C:\Windows\svchost.com" "C:\Users\admin\Desktop\Files\NINJA.exe" | C:\Windows\svchost.com | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 124 | "C:\Windows\svchost.com" "C:\Users\admin\Desktop\Files\NINJA.exe" | C:\Windows\svchost.com | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 128 | "C:\Windows\svchost.com" "C:\Users\admin\Desktop\Files\NINJA.exe" | C:\Windows\svchost.com | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 240 | C:\Users\admin\Desktop\Files\NINJA.exe | C:\Users\admin\Desktop\Files\NINJA.exe | — | svchost.com | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 240 | C:\Users\admin\Desktop\Files\NINJA.exe | C:\Users\admin\Desktop\Files\NINJA.exe | — | svchost.com | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 240 | C:\Users\admin\Desktop\Files\NINJA.exe | C:\Users\admin\Desktop\Files\NINJA.exe | — | svchost.com | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
Total events
464 725
Read events
462 465
Write events
2 102
Delete events
158
Modification events
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
927
Suspicious files
131
Text files
180
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\miner.exe | executable | |
MD5:CAFEAB1513FF424CC79CAECA170678D1 | SHA256:71F7D548C9EA57B8C9DCC3F426ADABDDDB4451E65837B63C4C25DC2A812717E2 | |||
| 2832 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\pinf.exe | executable | |
MD5:2EA6C5E97869622DFE70D2B34DAF564E | SHA256:5F28BBA8BD23CDB5C8A3FA018727BCF365EAF31C06B7BC8D3F3097A85DB037F3 | |||
| 2776 | pinf.exe | C:\Users\admin\AppData\Local\Temp\1357116943.exe | executable | |
MD5:BB3D7BD66C92454429A8C78BF64F977B | SHA256:94A66EEA65EDD08CA19BF6DB266058E81714312B6A51892298B461FFD8B90161 | |||
| 3988 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\pei.exe | executable | |
MD5:62B97CF4C0ABAFEDA36E3FC101A5A022 | SHA256:E172537ADCEE1FCDC8F16C23E43A5AC82C56A0347FA0197C08BE979438A534AB | |||
| 2980 | pei.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\newtpp[1].exe | executable | |
MD5:BB3D7BD66C92454429A8C78BF64F977B | SHA256:94A66EEA65EDD08CA19BF6DB266058E81714312B6A51892298B461FFD8B90161 | |||
| 1820 | clip.exe | C:\Users\admin\AppData\Roaming\System32\taskhost.exe | executable | |
MD5:04EBDDCC3A90B6512AEF4AA2EEE36624 | SHA256:1C4B1ACF31EC2DD48C746AD7CF2CC1404C76C7492BD15A6953F2CE6991496856 | |||
| 784 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\cayV0Deo9jSt417.exe | executable | |
MD5:AA3CDD5145D9FB980C061D2D8653FA8D | SHA256:41376827BA300374727D29048920CA2A2D9F20B929E964098181981581E47AF2 | |||
| 2928 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Windows.exe | executable | |
MD5:7E07020181EF731503973486D79D4FCC | SHA256:E75BBA7B3CC80766EFAE49E3314186E8A8B3094762AA491A7D2D15F95B2AC1A3 | |||
| 2088 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\l.exe | executable | |
MD5:073323EE4E37584DF5C4983BEC3D3EE3 | SHA256:15EA47A718B949BD9257EC7E2CD0B6E189105906DB776FBE6961AA4C53242FC2 | |||
| 2088 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\ghjkl.exe | executable | |
MD5:E11BBD79F37DF78A625E96D47DDBAD1F | SHA256:BFA28A771ABCAC8230B72EDDBA08508979D9621B4D83FB8CA74261B24900B07D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
137
TCP/UDP connections
352
DNS requests
111
Threats
515
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2592 | 4363463463464363463463463.exe | GET | 200 | 163.5.169.28:80 | http://163.5.169.28/fd1.exe | unknown | executable | 649 Kb | unknown |
796 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.19:80 | http://185.172.128.19/new/Miner-XMR1.exe | unknown | executable | 6.42 Mb | unknown |
2248 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://marksidfgs.ug/ghjkl.exe | unknown | executable | 2.13 Mb | unknown |
2832 | 4363463463464363463463463.exe | GET | — | 175.119.10.231:80 | http://brusuax.com/dl/buildz.exe | unknown | — | — | unknown |
2832 | 4363463463464363463463463.exe | GET | — | 175.119.10.231:80 | http://brusuax.com/dl/buildz.exe | unknown | — | — | unknown |
2832 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pinf.exe | unknown | executable | 9.50 Kb | unknown |
3988 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | executable | 9.50 Kb | unknown |
2980 | pei.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | executable | 79.5 Kb | unknown |
2776 | pinf.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | executable | 79.5 Kb | unknown |
2088 | 4363463463464363463463463.exe | GET | 200 | 5.42.65.115:80 | http://5.42.65.115/batushka/inte.exe | unknown | executable | 213 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3784 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2124 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2892 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
796 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2832 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2592 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2592 | 4363463463464363463463463.exe | 163.5.169.28:80 | — | Bursabil Teknoloji A.S. | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
github.com |
| shared |
brusuax.com |
| unknown |
raw.githubusercontent.com |
| shared |
marksidfgs.ug |
| unknown |
objects.githubusercontent.com |
| shared |
twizt.net |
| unknown |
bitbucket.org |
| shared |
carthagefire.net |
| malicious |
bbuseruploads.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2592 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2592 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
796 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
796 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
796 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
796 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
33 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The request was aborted: The connection was closed unexpectedly.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The request was aborted: The connection was closed unexpectedly.
|
4363463463464363463463463.exe | The request was aborted: The connection was closed unexpectedly.
|
4363463463464363463463463.exe | The underlying connection was closed: The connection was closed unexpectedly.
|
4363463463464363463463463.exe | The request was aborted: The connection was closed unexpectedly.
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | The remote server returned an error: (404) Not Found.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|