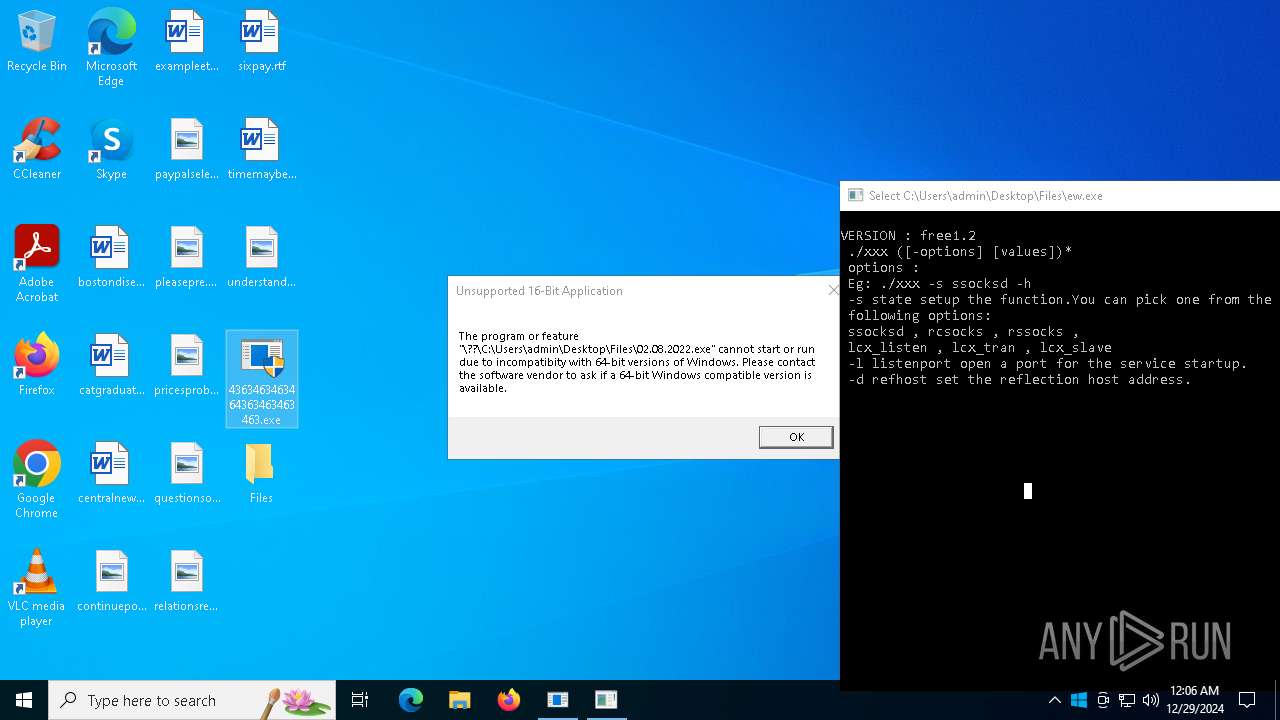
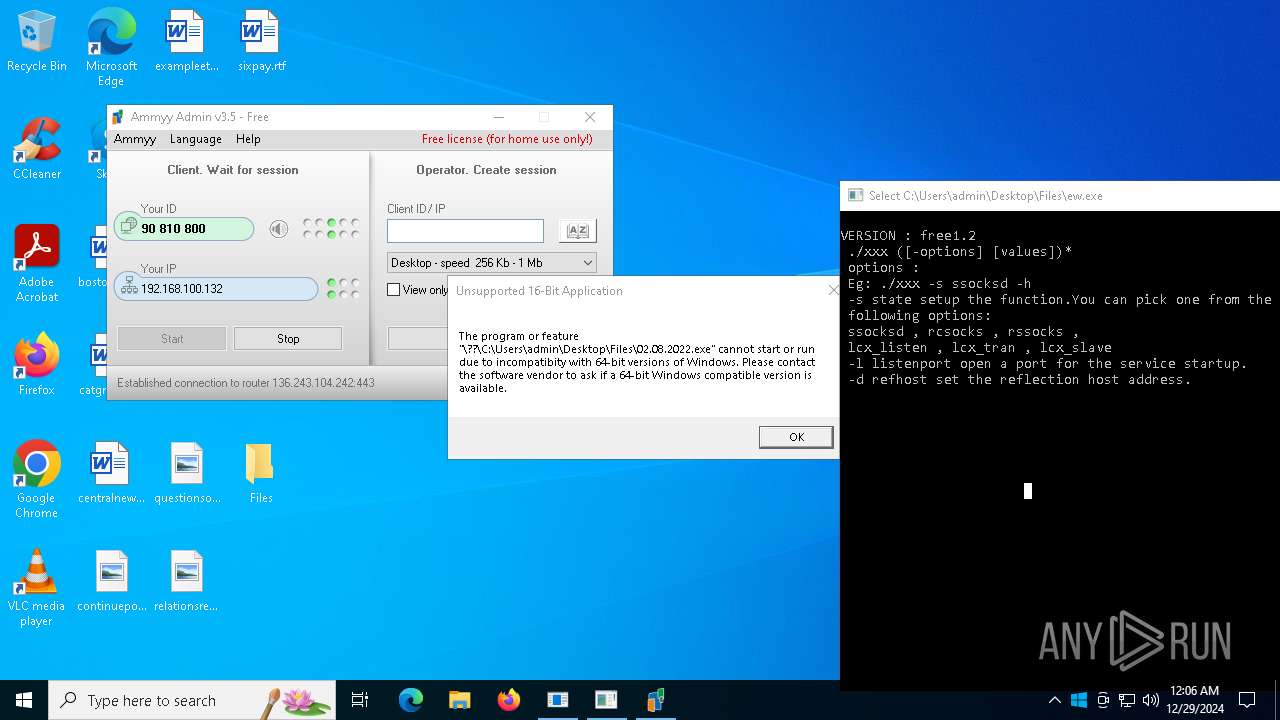
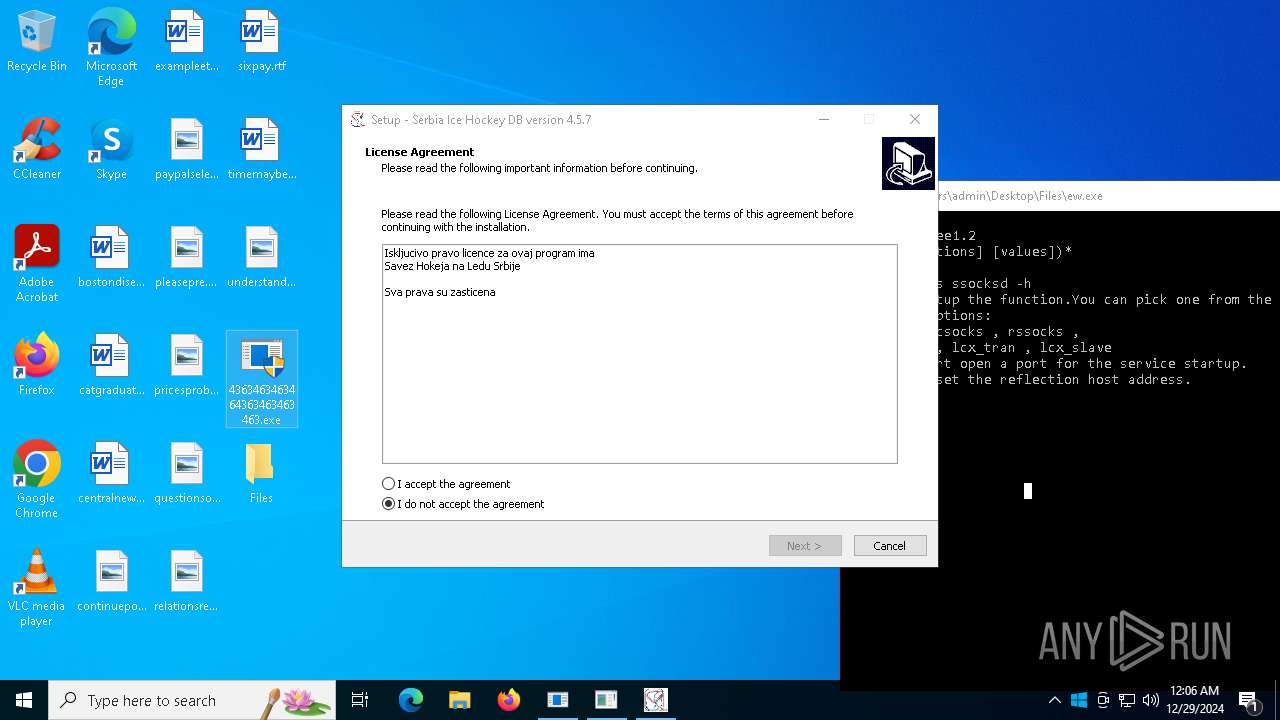
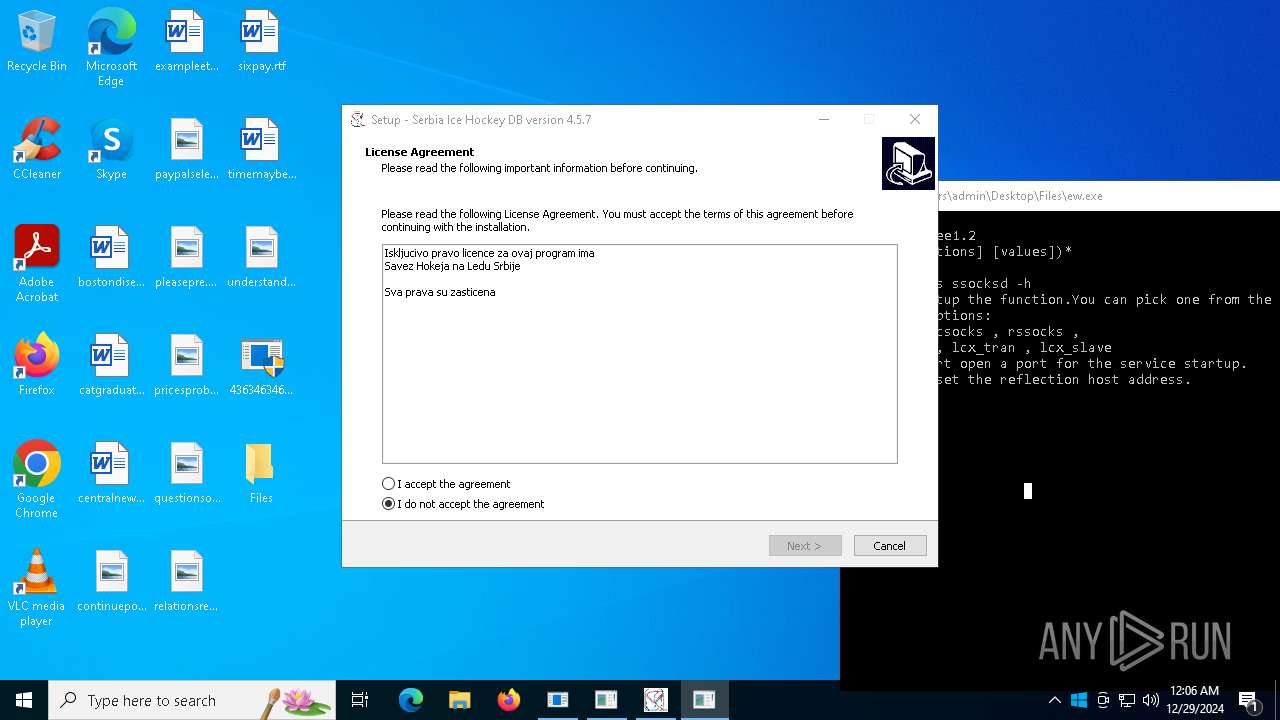
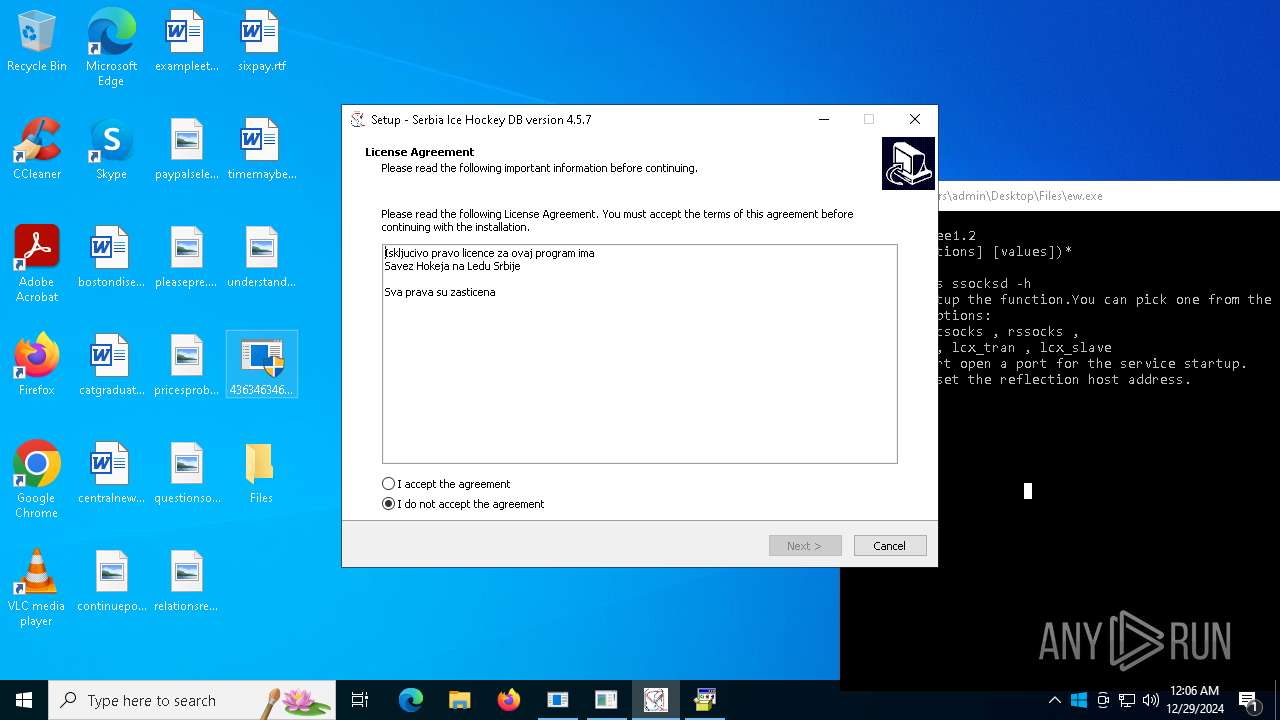
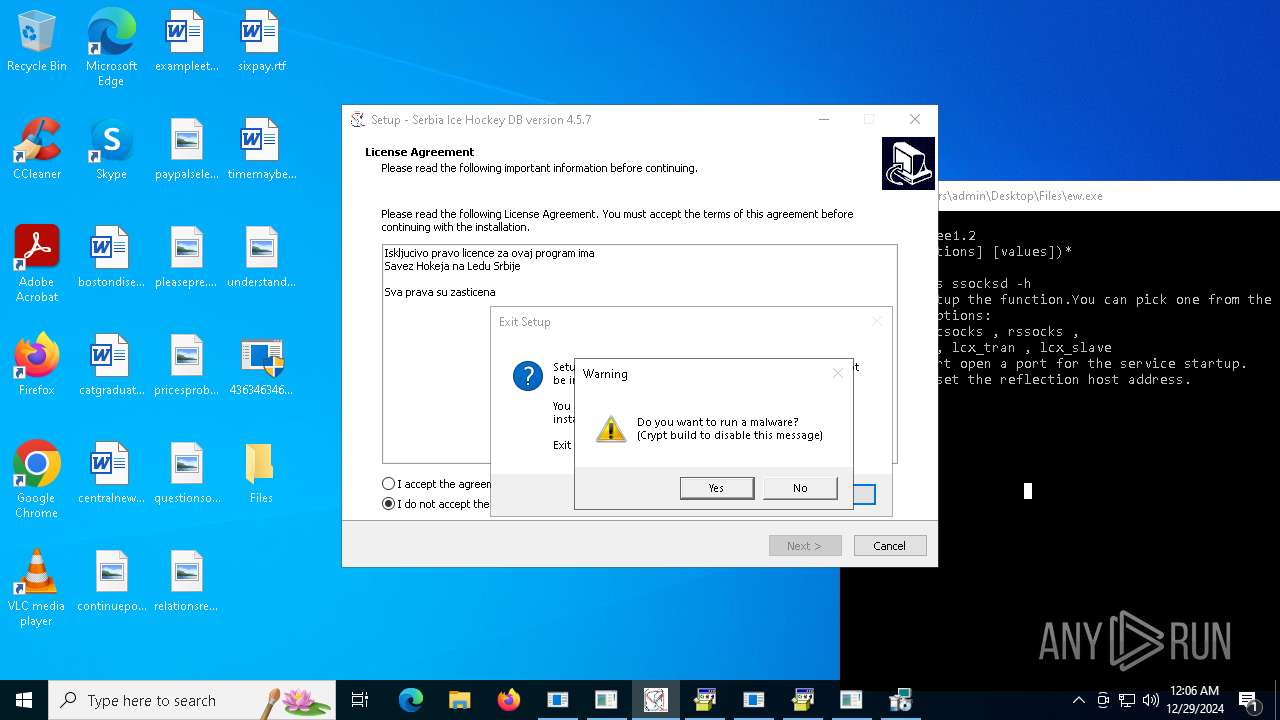
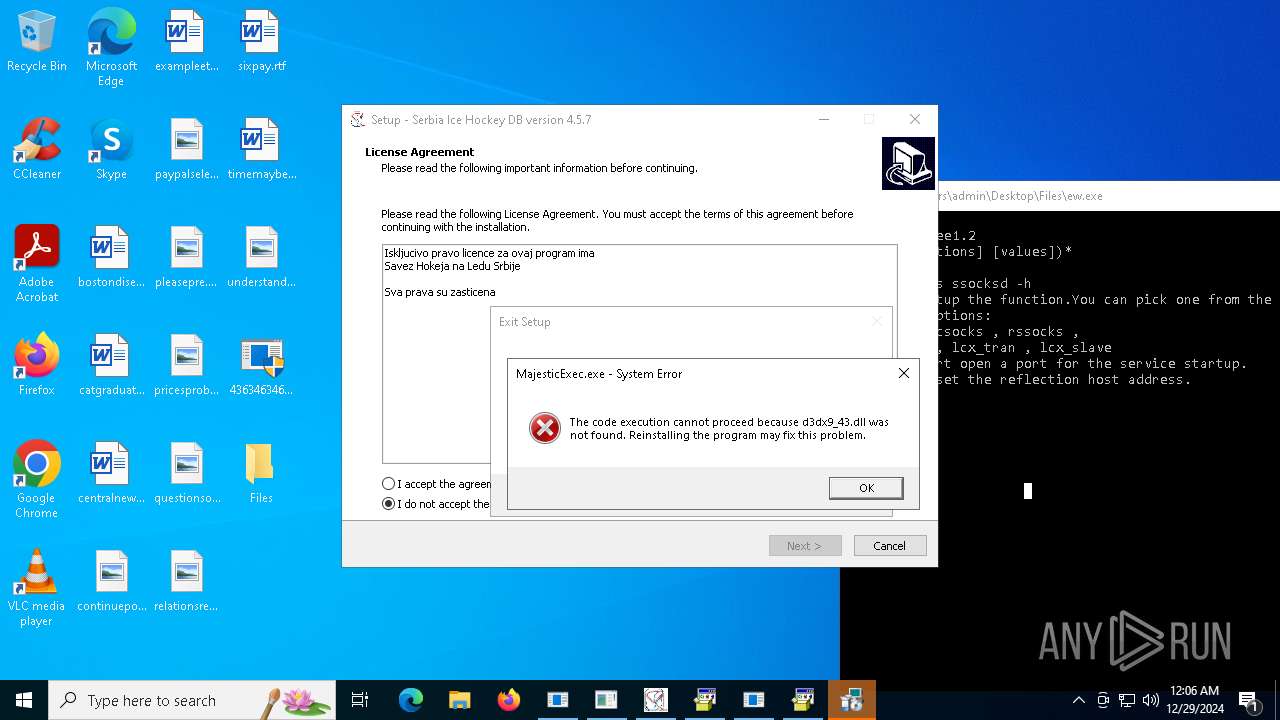
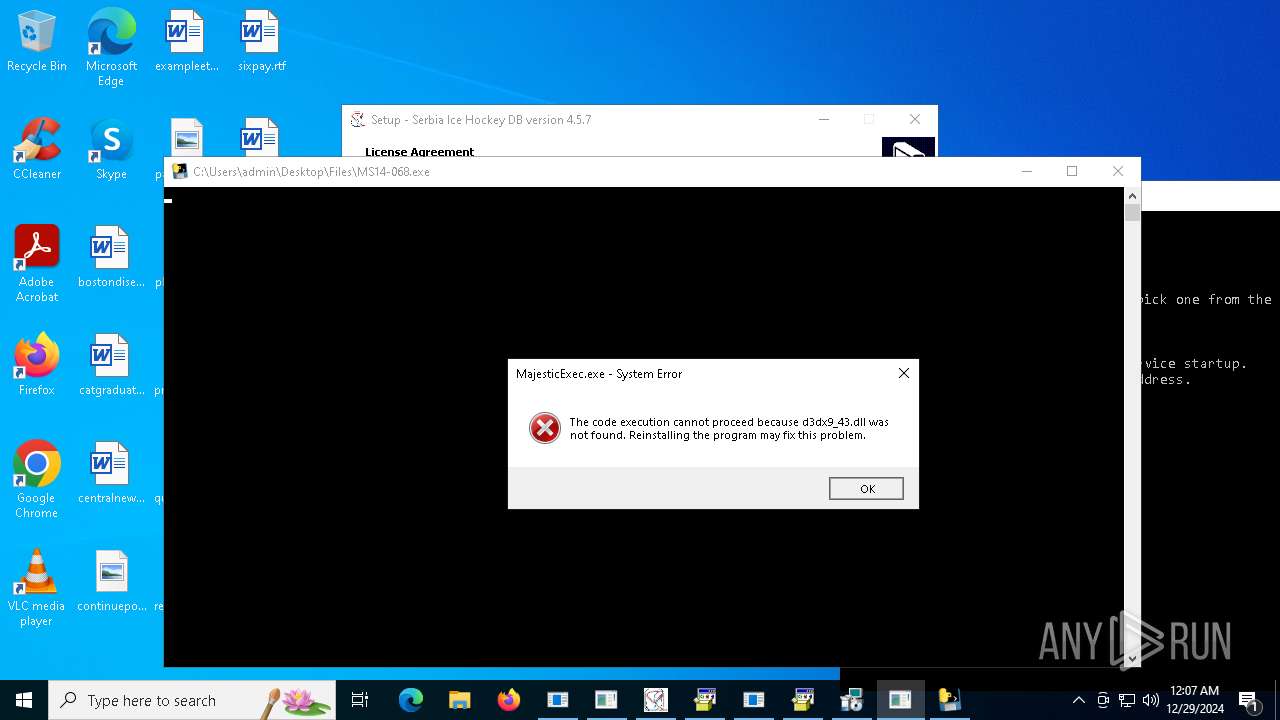
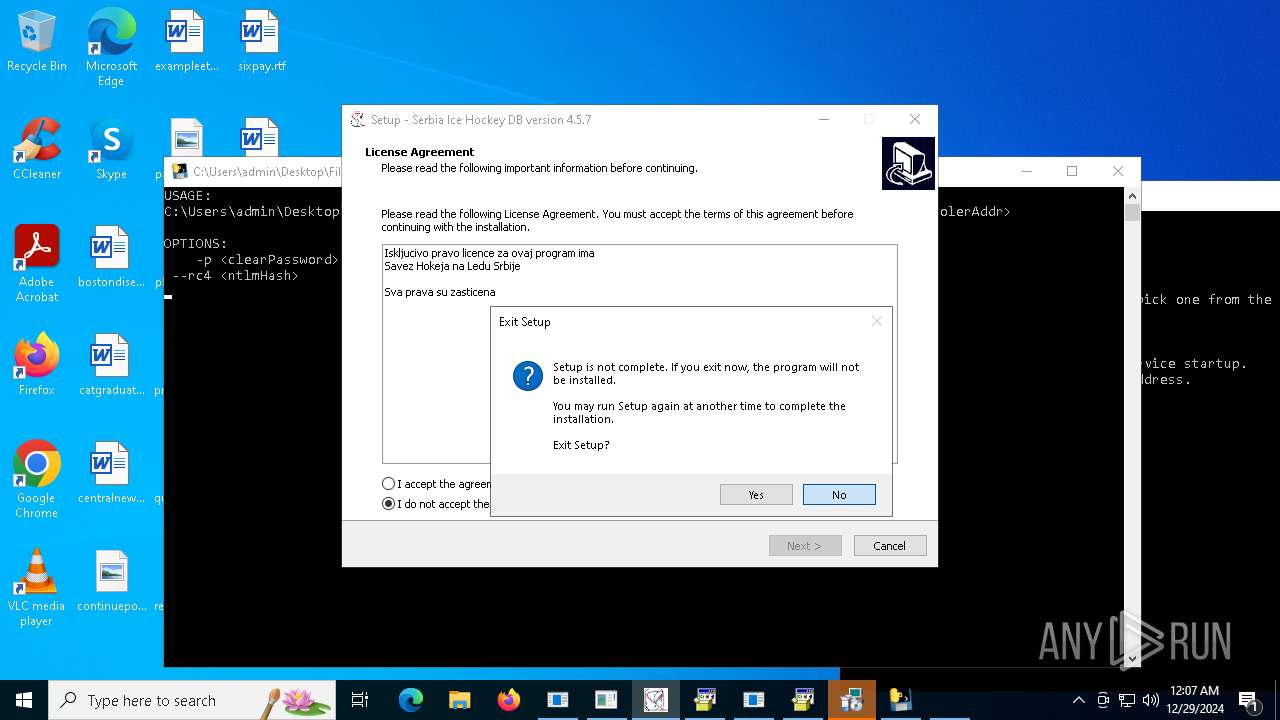
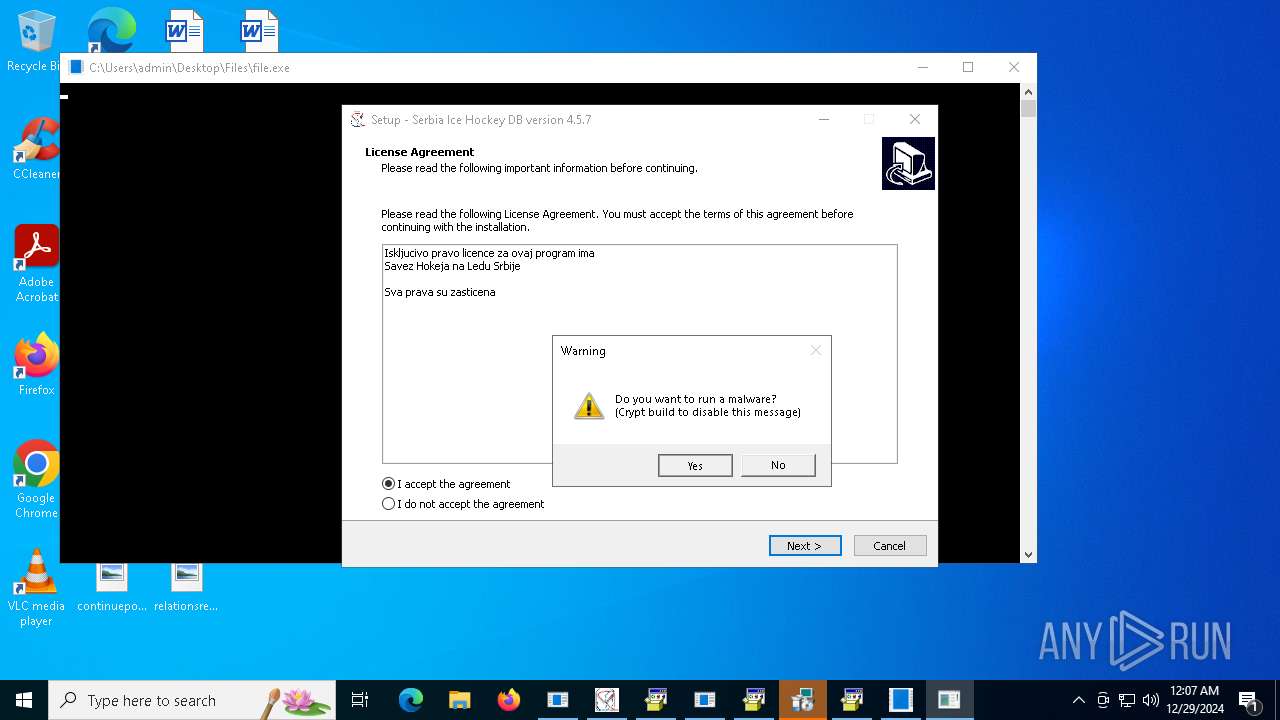
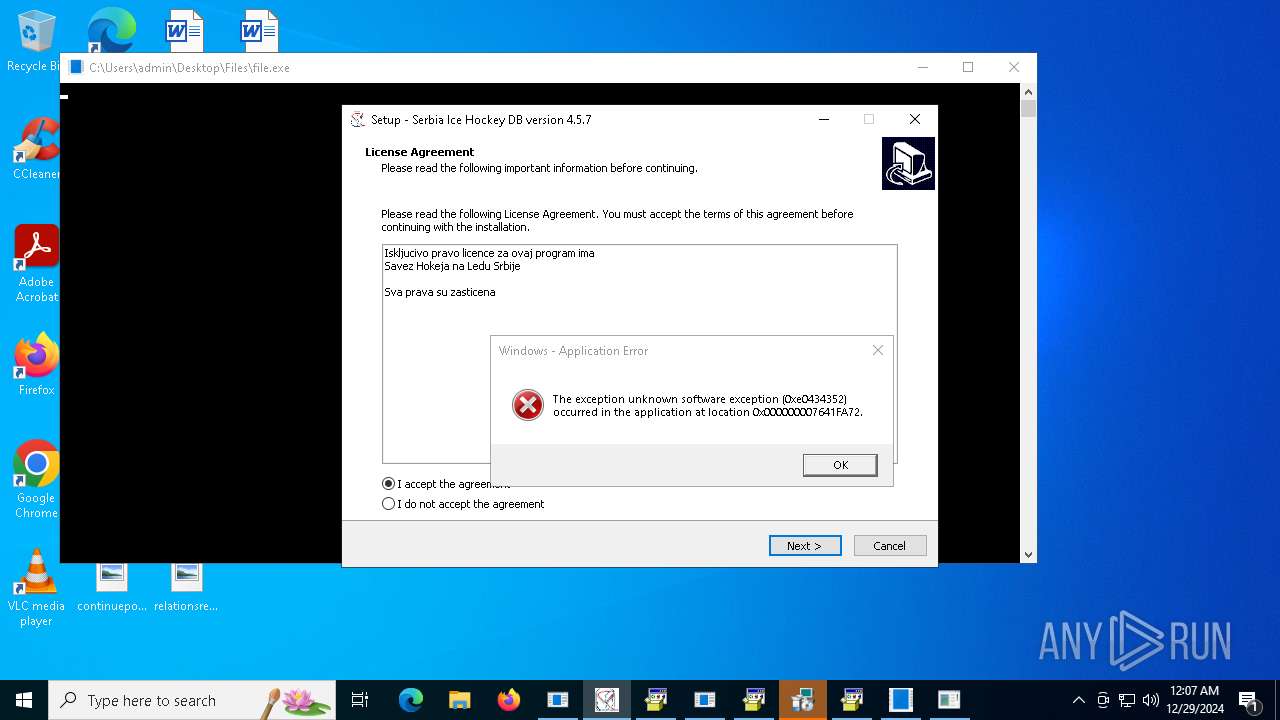
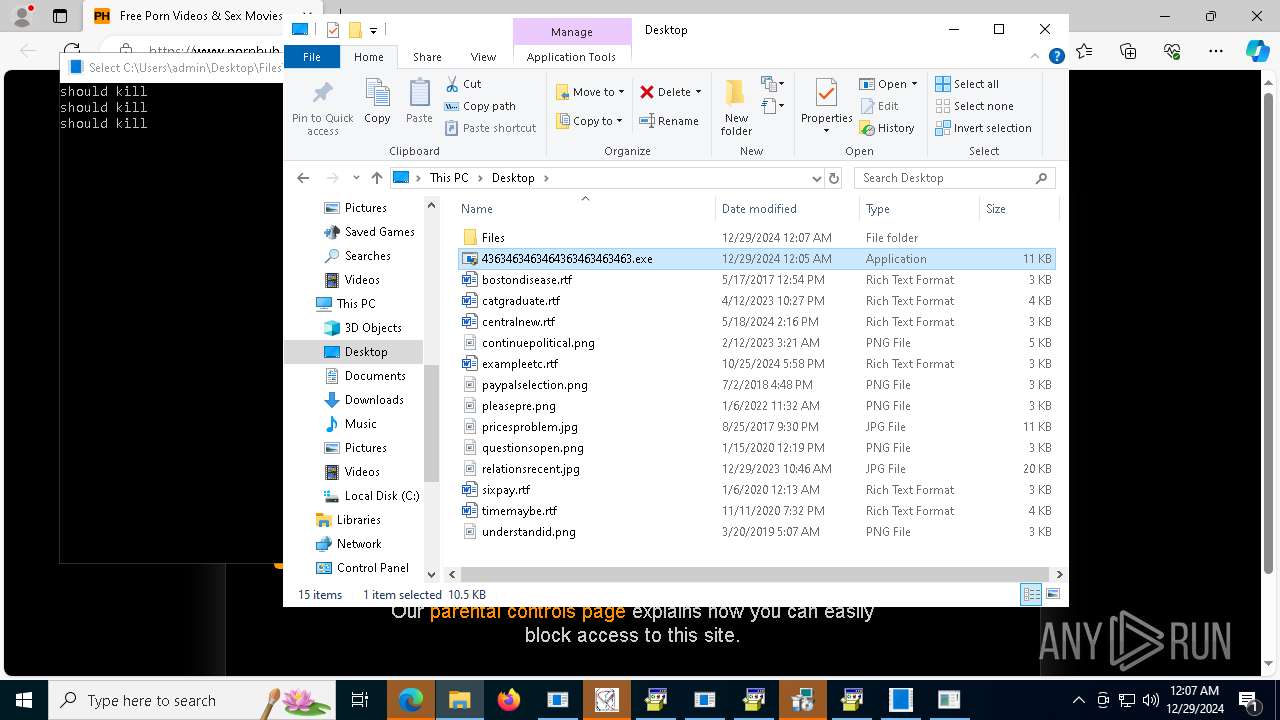
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/d4c43a95-2eeb-4707-9ce6-b130f5c77f1f |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | December 29, 2024, 00:05:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
PHORPIEX has been detected (SURICATA)
- svchost.exe (PID: 2192)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 7428)
Changes the autorun value in the registry
- vncgroups.exe (PID: 6572)
- idmans.exe (PID: 5036)
- winmsbt.exe (PID: 7708)
- curlapp64.exe (PID: 11356)
- uctgkfb7.exe (PID: 10320)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- boleto.exe (PID: 3568)
REMCOS has been detected
- idmans.exe (PID: 5036)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 7428)
- Discord.exe (PID: 7444)
- uctgkfb7.exe (PID: 10320)
- boleto.exe (PID: 3568)
- 4363463463464363463463463.exe (PID: 7792)
Connects to the CnC server
- 22.exe (PID: 6636)
- Ammyy.exe (PID: 8956)
- svchost.exe (PID: 2192)
- build6_unencrypted.exe (PID: 640)
- 4363463463464363463463463.exe (PID: 7428)
- SearchApp.exe (PID: 10252)
- 4363463463464363463463463.exe (PID: 6764)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6016)
StealC has been detected
- vorpgkadeg.exe (PID: 7996)
- 12.exe (PID: 20012)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- boleto.exe (PID: 3568)
- build6_unencrypted.exe (PID: 640)
- payload.exe (PID: 10756)
- OptiProV2.exe (PID: 12840)
Bypass execution policy to execute commands
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 8872)
- powershell.exe (PID: 8888)
- powershell.exe (PID: 8876)
- powershell.exe (PID: 9656)
- powershell.exe (PID: 7776)
- powershell.exe (PID: 10244)
- powershell.exe (PID: 10268)
- powershell.exe (PID: 10856)
- powershell.exe (PID: 14648)
- powershell.exe (PID: 14820)
- powershell.exe (PID: 8576)
- powershell.exe (PID: 16452)
- powershell.exe (PID: 21460)
Changes powershell execution policy (Bypass)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- boleto.exe (PID: 3568)
- build6_unencrypted.exe (PID: 640)
- OptiProV2.exe (PID: 12840)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 6820)
- joiner.exe (PID: 8012)
- server.exe (PID: 8316)
- svchost.exe (PID: 9240)
- server.exe (PID: 9652)
- svchost.exe (PID: 8484)
- server.exe (PID: 9652)
- svchost.exe (PID: 11188)
- 4363463463464363463463463.exe (PID: 9740)
- server.exe (PID: 9480)
- 856.exe (PID: 12388)
- 4363463463464363463463463.exe (PID: 6016)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6016)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6288)
NJRAT mutex has been found
- joiner.exe (PID: 8012)
- server.exe (PID: 8316)
- svchost.exe (PID: 9240)
- server.exe (PID: 9652)
- svchost.exe (PID: 8484)
- server.exe (PID: 9652)
- svchost.exe (PID: 11188)
- server.exe (PID: 9480)
- svchost.exe (PID: 16516)
- server.exe (PID: 18032)
ASYNCRAT has been detected (MUTEX)
- gagagggagagag.exe (PID: 7232)
SILVERFOX has been detected (SURICATA)
- 22.exe (PID: 6636)
ASYNCRAT has been detected (SURICATA)
- gagagggagagag.exe (PID: 7232)
DCRAT mutex has been found
- hyperBlockCrtCommon.exe (PID: 8212)
- SearchApp.exe (PID: 10252)
Actions looks like stealing of personal data
- gagagggagagag.exe (PID: 7232)
- kp8dnpa9.exe (PID: 8488)
- k360.exe (PID: 11236)
- alex2025.exe (PID: 11080)
- BitLockerToGo.exe (PID: 13580)
- v_dolg.exe (PID: 12392)
Steals credentials from Web Browsers
- gagagggagagag.exe (PID: 7232)
- kp8dnpa9.exe (PID: 8488)
- alex2025.exe (PID: 11080)
- BitLockerToGo.exe (PID: 13580)
AMMYY has been detected (SURICATA)
- Ammyy.exe (PID: 8956)
Create files in the Startup directory
- server.exe (PID: 8316)
- ptihjawdthas.exe (PID: 8048)
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 8516)
- WenzCord.exe (PID: 9520)
- 4363463463464363463463463.exe (PID: 7184)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 9088)
- cmd.exe (PID: 7172)
- Client.exe (PID: 9408)
- WenzCord.exe (PID: 9520)
- jgesfyhjsefa.exe (PID: 9472)
- WenzCord.exe (PID: 1348)
- WenzCord.exe (PID: 14384)
- client.exe (PID: 12700)
- Client.exe (PID: 3620)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 7184)
Executing a file with an untrusted certificate
- meshagent32-group.exe (PID: 10100)
- xdd.exe (PID: 13000)
Adds process to the Windows Defender exclusion list
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- build6_unencrypted.exe (PID: 640)
- boleto.exe (PID: 3568)
- OptiProV2.exe (PID: 12840)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6288)
- uctgkfb7.exe (PID: 10320)
- XClient.exe (PID: 7340)
- svchost.exe (PID: 1328)
- boleto.exe (PID: 3568)
RHADAMANTHYS has been detected (SURICATA)
- fontdrvhost.exe (PID: 7628)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- xdd.exe (PID: 13000)
Starts CMD.EXE for self-deleting
- feb9sxwk.exe (PID: 11144)
UAC/LUA settings modification
- reg.exe (PID: 10288)
CRYPTBOT has been found (auto)
- 4363463463464363463463463.exe (PID: 7792)
SYSTEMBC has been found (auto)
- 4363463463464363463463463.exe (PID: 8516)
LUMMA mutex has been found
- alex2025.exe (PID: 11080)
- v_dolg.exe (PID: 12392)
PETYA has been found (auto)
- 4363463463464363463463463.exe (PID: 8516)
Stealers network behavior
- svchost.exe (PID: 2192)
Changes Controlled Folder Access settings
- powershell.exe (PID: 18804)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 18804)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 18804)
Adds extension to the Windows Defender exclusion list
- xdd.exe (PID: 13000)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 18804)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 18804)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 18804)
Changes settings for real-time protection
- powershell.exe (PID: 18804)
XWORM has been detected
- svchost.exe (PID: 1328)
STEALERIUMSTEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 624)
XWORM has been detected (SURICATA)
- build6_unencrypted.exe (PID: 640)
- uctgkfb7.exe (PID: 10320)
REMCOS has been detected (SURICATA)
- idmans.exe (PID: 5036)
DARKCRYSTAL has been detected (SURICATA)
- SearchApp.exe (PID: 10252)
ZHARKBOT has been detected (SURICATA)
- svchost.exe (PID: 2192)
SUSPICIOUS
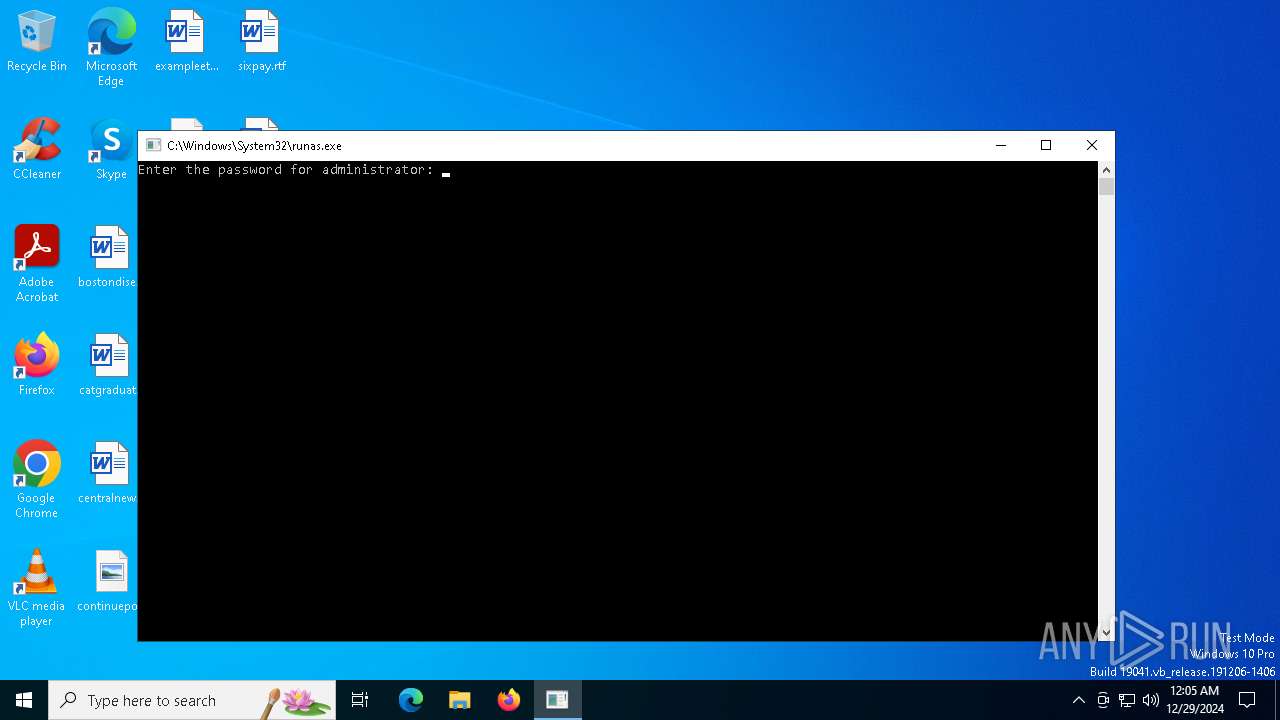
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 2632)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5320)
- 22.exe (PID: 6636)
- idmans.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6232)
- gagagggagagag.exe (PID: 7232)
- fern_wifi_recon%252.34.exe (PID: 8288)
- jgesfyhjsefa.exe (PID: 9472)
- 4363463463464363463463463.exe (PID: 7184)
- fontdrvhost.exe (PID: 7628)
- 4363463463464363463463463.exe (PID: 8816)
- 4363463463464363463463463.exe (PID: 7656)
- Client.exe (PID: 9408)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 5920)
- Discord.exe (PID: 10112)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 6820)
- MSBuild.exe (PID: 13056)
- 4363463463464363463463463.exe (PID: 8928)
- RegAsm.exe (PID: 11556)
- newbundle.exe (PID: 11200)
- build6_unencrypted.exe (PID: 640)
- 4363463463464363463463463.exe (PID: 13676)
- 5KNCHALAH.exe (PID: 9180)
- powershell.exe (PID: 14444)
- 4363463463464363463463463.exe (PID: 8516)
- uctgkfb7.exe (PID: 10320)
- 4363463463464363463463463.exe (PID: 624)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 7428)
- Ammyy.exe (PID: 8956)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 7184)
- svchost.exe (PID: 2192)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 16676)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 6820)
- hyperBlockCrtCommon.exe (PID: 8212)
- server.exe (PID: 8316)
- server.exe (PID: 9652)
- server.exe (PID: 9652)
- 4363463463464363463463463.exe (PID: 9740)
- server.exe (PID: 9480)
- 856.exe (PID: 12388)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 5320)
- onlysteal.exe (PID: 6968)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6576)
- vncgroups.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 624)
- contorax.exe (PID: 7504)
- 4363463463464363463463463.exe (PID: 7428)
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- Discord.exe (PID: 7444)
- 4363463463464363463463463.exe (PID: 6764)
- server.exe (PID: 8316)
- Client-built.exe (PID: 9088)
- 4363463463464363463463463.exe (PID: 8516)
- svchost.exe (PID: 9240)
- 4363463463464363463463463.exe (PID: 7656)
- utility-inst.exe (PID: 9796)
- utility-inst.tmp (PID: 9868)
- Installeraus.exe (PID: 9808)
- WenzCord.exe (PID: 9520)
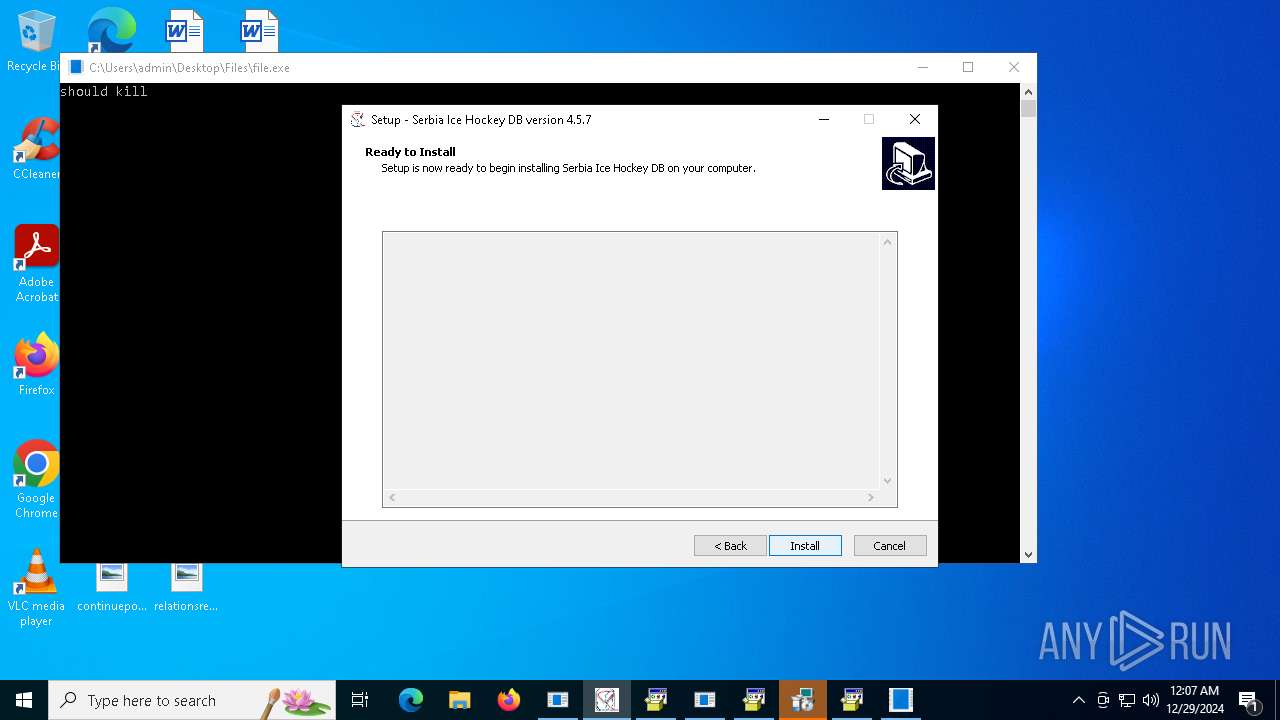
- SrbijaSetupHokej.tmp (PID: 8848)
- SrbijaSetupHokej.exe (PID: 10176)
- ptihjawdthas.exe (PID: 8048)
- server.exe (PID: 9652)
- DiscordSpotifyBypass.exe (PID: 9352)
- 4363463463464363463463463.exe (PID: 7184)
- svchost.exe (PID: 8484)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 8928)
- SearchApp.exe (PID: 10252)
- server.exe (PID: 9652)
- 4363463463464363463463463.exe (PID: 9740)
- feb9sxwk.exe (PID: 11144)
- svchost.exe (PID: 11188)
- wow.exe (PID: 8740)
- 87f3f2.exe (PID: 11872)
- foggy-mountains.exe (PID: 12748)
- uctgkfb7.exe (PID: 10320)
- uhigdbf.exe (PID: 12568)
- server.exe (PID: 9480)
- 4363463463464363463463463.exe (PID: 13676)
- svchost.exe (PID: 1328)
- boleto.exe (PID: 3568)
- 856.exe (PID: 12388)
- xdd.exe (PID: 13000)
- payload.exe (PID: 10756)
- OptiProV2.exe (PID: 12840)
- 4363463463464363463463463.exe (PID: 17280)
- aidans.dont.run.exe (PID: 9940)
- 4363463463464363463463463.exe (PID: 6016)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5320)
- onlysteal.exe (PID: 6968)
- 4363463463464363463463463.exe (PID: 2008)
- 22.exe (PID: 6636)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6576)
- vncgroups.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 5920)
- contorax.exe (PID: 7504)
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- 4363463463464363463463463.exe (PID: 7428)
- Discord.exe (PID: 7444)
- Ammyy.exe (PID: 8956)
- 4363463463464363463463463.exe (PID: 6764)
- server.exe (PID: 8316)
- svchost.exe (PID: 9240)
- 4363463463464363463463463.exe (PID: 7656)
- utility-inst.tmp (PID: 9868)
- ptihjawdthas.exe (PID: 8048)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 7184)
- server.exe (PID: 9652)
- svchost.exe (PID: 8484)
- pornhub_downloader.exe (PID: 10184)
- WenzCord.exe (PID: 1348)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 8928)
- DivineDialogue.exe (PID: 10316)
- 4363463463464363463463463.exe (PID: 8516)
- server.exe (PID: 9652)
- boleto.exe (PID: 3568)
- pornhub_downloader.exe (PID: 11092)
- 4363463463464363463463463.exe (PID: 9740)
- build6_unencrypted.exe (PID: 640)
- svchost.exe (PID: 11188)
- ShellExperienceHost.exe (PID: 9560)
- Unit.exe (PID: 13800)
- OptiProV2.exe (PID: 12840)
- uctgkfb7.exe (PID: 10320)
- WenzCord.exe (PID: 14384)
- uhigdbf.exe (PID: 12568)
- server.exe (PID: 9480)
- svchost.exe (PID: 16516)
- 4363463463464363463463463.exe (PID: 16676)
- 4363463463464363463463463.exe (PID: 17280)
- 856.exe (PID: 12388)
- stub.exe (PID: 19308)
- clamer.exe (PID: 18540)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6576)
- 22.exe (PID: 6636)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- SearchApp.exe (PID: 10252)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 7184)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 7184)
Starts itself from another location
- vncgroups.exe (PID: 6572)
- contorax.exe (PID: 7504)
- joiner.exe (PID: 8012)
- server.exe (PID: 8316)
- Client-built.exe (PID: 9088)
- svchost.exe (PID: 9240)
- WenzCord.exe (PID: 9520)
- server.exe (PID: 9652)
- svchost.exe (PID: 8484)
- server.exe (PID: 9652)
- svchost.exe (PID: 11188)
- client.exe (PID: 12700)
- server.exe (PID: 9480)
- svchost.exe (PID: 16516)
- 856.exe (PID: 12388)
Reads the date of Windows installation
- contorax.exe (PID: 7504)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- hyperBlockCrtCommon.exe (PID: 8212)
- boleto.exe (PID: 3568)
- build6_unencrypted.exe (PID: 640)
- WenzCord.exe (PID: 1348)
- WenzCord.exe (PID: 14384)
- clamer.exe (PID: 18540)
Reads the BIOS version
- random.exe (PID: 7584)
- v_dolg.exe (PID: 12392)
- petya.exe (PID: 1572)
- Lu4421.exe (PID: 21572)
Windows Defender mutex has been found
- vorpgkadeg.exe (PID: 7996)
- 12.exe (PID: 20012)
Checks for external IP
- svchost.exe (PID: 2192)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- Ammyy.exe (PID: 8956)
- boleto.exe (PID: 3568)
- jgesfyhjsefa.exe (PID: 9472)
Starts POWERSHELL.EXE for commands execution
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- boleto.exe (PID: 3568)
- build6_unencrypted.exe (PID: 640)
- cmd.exe (PID: 10348)
- payload.exe (PID: 10756)
- OptiProV2.exe (PID: 12840)
- xdd.exe (PID: 13000)
Script adds exclusion path to Windows Defender
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- boleto.exe (PID: 3568)
- build6_unencrypted.exe (PID: 640)
- payload.exe (PID: 10756)
- OptiProV2.exe (PID: 12840)
- xdd.exe (PID: 13000)
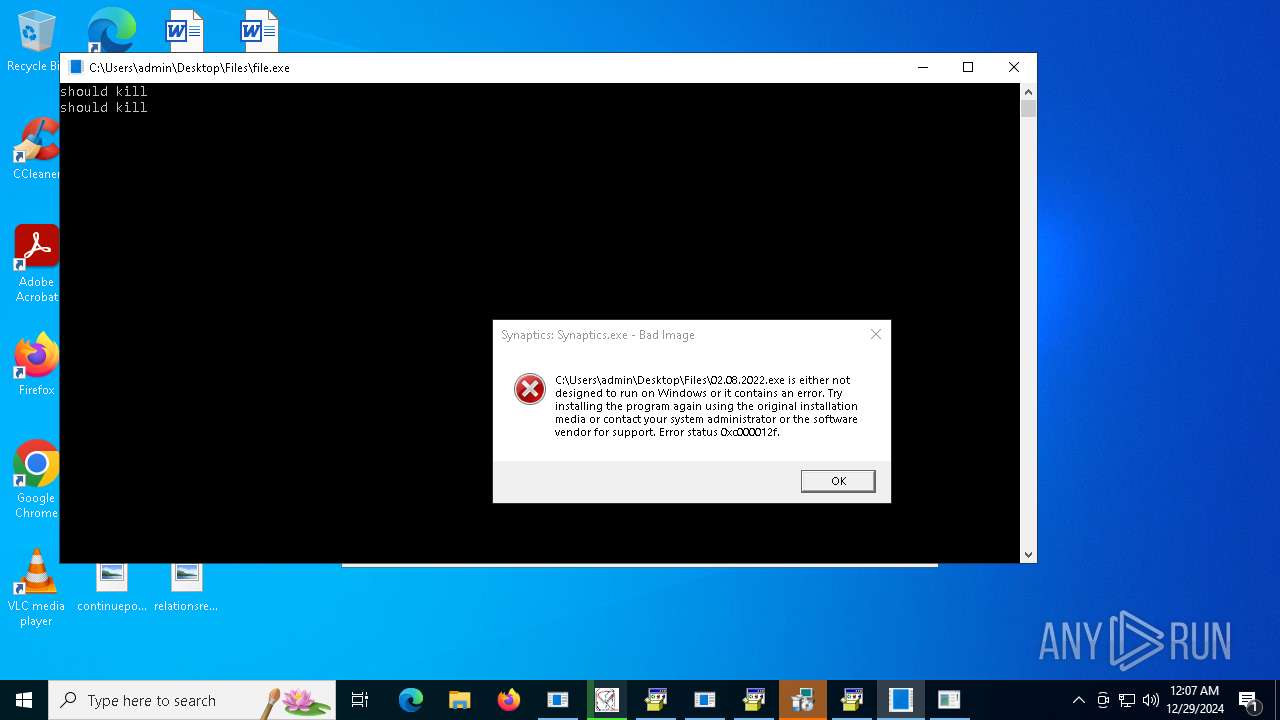
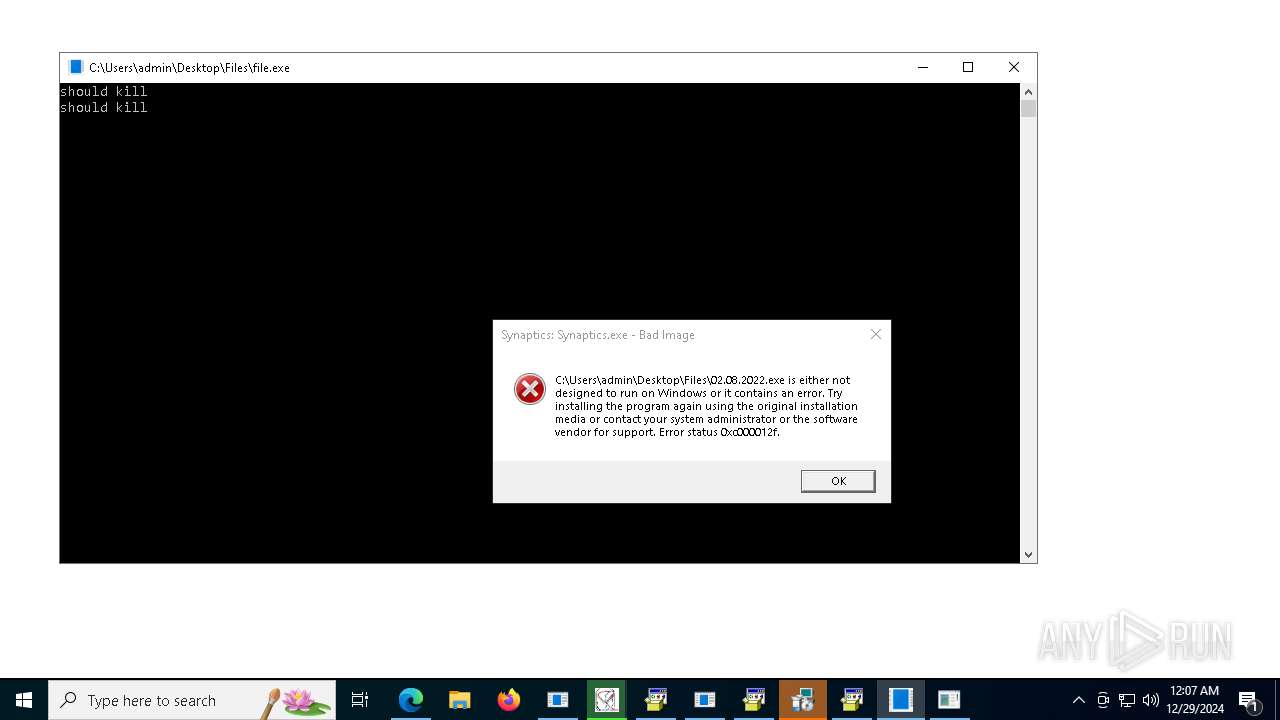
Executes application which crashes
- random.exe (PID: 7584)
- kp8dnpa9.exe (PID: 5192)
- popapoers.exe (PID: 10236)
- LoadNew.exe (PID: 15532)
- 12.exe (PID: 20012)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6288)
Contacting a server suspected of hosting an CnC
- 22.exe (PID: 6636)
- gagagggagagag.exe (PID: 7232)
- fontdrvhost.exe (PID: 7628)
- svchost.exe (PID: 2192)
- build6_unencrypted.exe (PID: 640)
- idmans.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 7428)
- uctgkfb7.exe (PID: 10320)
Executing commands from a ".bat" file
- wscript.exe (PID: 6288)
- hyperBlockCrtCommon.exe (PID: 8212)
- Discord.exe (PID: 7444)
- utility-inst.tmp (PID: 9868)
- pornhub_downloader.exe (PID: 10184)
- WenzCord.exe (PID: 1348)
- DivineDialogue.exe (PID: 10316)
- pornhub_downloader.exe (PID: 11092)
- 99awhy8l.exe (PID: 10572)
- WenzCord.exe (PID: 14384)
- uhigdbf.exe (PID: 12568)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6288)
- hyperBlockCrtCommon.exe (PID: 8212)
- Discord.exe (PID: 7444)
- utility-inst.tmp (PID: 9868)
- ptihjawdthas.exe (PID: 8048)
- pornhub_downloader.exe (PID: 10184)
- WenzCord.exe (PID: 1348)
- DivineDialogue.exe (PID: 10316)
- pornhub_downloader.exe (PID: 11092)
- feb9sxwk.exe (PID: 11144)
- cmd.exe (PID: 10348)
- 99awhy8l.exe (PID: 10572)
- WenzCord.exe (PID: 14384)
- uhigdbf.exe (PID: 12568)
Executes as Windows Service
- Ammyy.exe (PID: 8904)
Application launched itself
- Ammyy.exe (PID: 8904)
- kp8dnpa9.exe (PID: 5192)
- alex2025.exe (PID: 10516)
- cmd.exe (PID: 10348)
- zxcv.exe (PID: 10552)
- MS14-068.exe (PID: 21232)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 8316)
- server.exe (PID: 9652)
- server.exe (PID: 9652)
- server.exe (PID: 9480)
- 856.exe (PID: 12388)
Starts application with an unusual extension
- cmd.exe (PID: 8624)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 10844)
Probably fake Windows Update file has been dropped
- server.exe (PID: 8316)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- server.exe (PID: 8316)
- server.exe (PID: 9652)
- server.exe (PID: 9652)
- server.exe (PID: 9480)
- 856.exe (PID: 12388)
Creates file in the systems drive root
- server.exe (PID: 8316)
- server.exe (PID: 9652)
- server.exe (PID: 9652)
- server.exe (PID: 9480)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8484)
- cmd.exe (PID: 10052)
The process checks if it is being run in the virtual environment
- fontdrvhost.exe (PID: 7628)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 8624)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 10844)
Reads the Windows owner or organization settings
- utility-inst.tmp (PID: 9868)
- SrbijaSetupHokej.tmp (PID: 8848)
The executable file from the user directory is run by the CMD process
- Discord.exe (PID: 10112)
- WenzCord.exe (PID: 14384)
- clamer.exe (PID: 18540)
Script adds exclusion process to Windows Defender
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- build6_unencrypted.exe (PID: 640)
- boleto.exe (PID: 3568)
- OptiProV2.exe (PID: 12840)
The process drops C-runtime libraries
- DiscordSpotifyBypass.exe (PID: 9352)
Process drops python dynamic module
- DiscordSpotifyBypass.exe (PID: 9352)
Process drops legitimate windows executable
- DiscordSpotifyBypass.exe (PID: 9352)
- 4363463463464363463463463.exe (PID: 8516)
Starts a Microsoft application from unusual location
- zxcv.exe (PID: 10552)
- zxcv.exe (PID: 9988)
- zxcv.exe (PID: 10620)
- zxcv.exe (PID: 9152)
- zxcv.exe (PID: 9536)
- zxcv.exe (PID: 9116)
- zxcv.exe (PID: 2280)
- zxcv.exe (PID: 9404)
- zxcv.exe (PID: 8924)
- zxcv.exe (PID: 11156)
- zxcv.exe (PID: 10192)
- zxcv.exe (PID: 8616)
- zxcv.exe (PID: 9064)
- zxcv.exe (PID: 10272)
- zxcv.exe (PID: 10920)
- zxcv.exe (PID: 11004)
- zxcv.exe (PID: 10408)
- zxcv.exe (PID: 10780)
- zxcv.exe (PID: 9284)
- zxcv.exe (PID: 7888)
- zxcv.exe (PID: 10988)
- zxcv.exe (PID: 10788)
- zxcv.exe (PID: 10980)
- zxcv.exe (PID: 8164)
- zxcv.exe (PID: 11076)
- zxcv.exe (PID: 9236)
- zxcv.exe (PID: 9664)
- zxcv.exe (PID: 9348)
- zxcv.exe (PID: 10096)
- zxcv.exe (PID: 9100)
- zxcv.exe (PID: 7392)
- zxcv.exe (PID: 11204)
- zxcv.exe (PID: 8628)
- zxcv.exe (PID: 9520)
- zxcv.exe (PID: 8428)
- zxcv.exe (PID: 10596)
- zxcv.exe (PID: 11144)
- zxcv.exe (PID: 10568)
- zxcv.exe (PID: 8468)
- zxcv.exe (PID: 10908)
- zxcv.exe (PID: 9544)
- zxcv.exe (PID: 10144)
- zxcv.exe (PID: 10924)
- zxcv.exe (PID: 9812)
- zxcv.exe (PID: 9872)
- zxcv.exe (PID: 6828)
- zxcv.exe (PID: 10900)
- zxcv.exe (PID: 11196)
- zxcv.exe (PID: 9088)
- zxcv.exe (PID: 11192)
- zxcv.exe (PID: 7204)
- zxcv.exe (PID: 11232)
- zxcv.exe (PID: 8196)
- zxcv.exe (PID: 10648)
- zxcv.exe (PID: 8500)
- zxcv.exe (PID: 8736)
- zxcv.exe (PID: 10612)
- zxcv.exe (PID: 10288)
- zxcv.exe (PID: 9584)
- zxcv.exe (PID: 11404)
- zxcv.exe (PID: 11280)
- zxcv.exe (PID: 11292)
- zxcv.exe (PID: 11308)
- zxcv.exe (PID: 11340)
- zxcv.exe (PID: 11364)
- zxcv.exe (PID: 11376)
- zxcv.exe (PID: 11456)
- zxcv.exe (PID: 11416)
- zxcv.exe (PID: 11428)
- zxcv.exe (PID: 11444)
- zxcv.exe (PID: 11468)
- zxcv.exe (PID: 10012)
- zxcv.exe (PID: 11548)
- zxcv.exe (PID: 11496)
- zxcv.exe (PID: 11524)
- zxcv.exe (PID: 11532)
- zxcv.exe (PID: 11560)
- zxcv.exe (PID: 11596)
- zxcv.exe (PID: 11572)
- zxcv.exe (PID: 11588)
- zxcv.exe (PID: 11608)
- zxcv.exe (PID: 11616)
- zxcv.exe (PID: 11632)
- zxcv.exe (PID: 11648)
- zxcv.exe (PID: 11680)
- zxcv.exe (PID: 11664)
- zxcv.exe (PID: 11696)
- zxcv.exe (PID: 11476)
- zxcv.exe (PID: 11732)
- zxcv.exe (PID: 11744)
- zxcv.exe (PID: 11772)
- zxcv.exe (PID: 11804)
- zxcv.exe (PID: 11792)
- zxcv.exe (PID: 11816)
- zxcv.exe (PID: 11832)
- zxcv.exe (PID: 11908)
- zxcv.exe (PID: 11860)
- zxcv.exe (PID: 11880)
- zxcv.exe (PID: 11892)
- zxcv.exe (PID: 11932)
- zxcv.exe (PID: 11956)
- zxcv.exe (PID: 11704)
- zxcv.exe (PID: 11720)
- zxcv.exe (PID: 11756)
- zxcv.exe (PID: 11780)
- zxcv.exe (PID: 11852)
- zxcv.exe (PID: 12036)
- zxcv.exe (PID: 11988)
- zxcv.exe (PID: 12012)
- zxcv.exe (PID: 12020)
- zxcv.exe (PID: 12072)
- zxcv.exe (PID: 12104)
- zxcv.exe (PID: 12088)
- zxcv.exe (PID: 12112)
- zxcv.exe (PID: 12140)
- zxcv.exe (PID: 12152)
- zxcv.exe (PID: 12168)
- zxcv.exe (PID: 12180)
- zxcv.exe (PID: 11964)
- zxcv.exe (PID: 11972)
- zxcv.exe (PID: 12056)
- zxcv.exe (PID: 12124)
- zxcv.exe (PID: 8596)
- zxcv.exe (PID: 12264)
- zxcv.exe (PID: 11352)
- zxcv.exe (PID: 11412)
- zxcv.exe (PID: 11436)
- zxcv.exe (PID: 11452)
- zxcv.exe (PID: 11484)
- zxcv.exe (PID: 11488)
- zxcv.exe (PID: 11584)
- zxcv.exe (PID: 11516)
- zxcv.exe (PID: 12196)
- zxcv.exe (PID: 12212)
- zxcv.exe (PID: 12224)
- zxcv.exe (PID: 12232)
- zxcv.exe (PID: 12244)
- zxcv.exe (PID: 11268)
- zxcv.exe (PID: 11828)
- zxcv.exe (PID: 11916)
- zxcv.exe (PID: 11568)
- zxcv.exe (PID: 12004)
- zxcv.exe (PID: 10376)
- zxcv.exe (PID: 12084)
- zxcv.exe (PID: 12148)
- zxcv.exe (PID: 11656)
- zxcv.exe (PID: 11712)
- zxcv.exe (PID: 11752)
- zxcv.exe (PID: 11928)
- zxcv.exe (PID: 12100)
- zxcv.exe (PID: 11580)
- zxcv.exe (PID: 11692)
- zxcv.exe (PID: 9628)
- zxcv.exe (PID: 4264)
- zxcv.exe (PID: 12048)
- zxcv.exe (PID: 12164)
- zxcv.exe (PID: 12204)
- zxcv.exe (PID: 12256)
- zxcv.exe (PID: 12284)
- zxcv.exe (PID: 11252)
- zxcv.exe (PID: 1576)
- zxcv.exe (PID: 10892)
- zxcv.exe (PID: 11888)
- zxcv.exe (PID: 11996)
- zxcv.exe (PID: 6880)
- zxcv.exe (PID: 12292)
- zxcv.exe (PID: 12304)
- zxcv.exe (PID: 12316)
- zxcv.exe (PID: 12328)
- zxcv.exe (PID: 12340)
- zxcv.exe (PID: 12352)
- zxcv.exe (PID: 12364)
- zxcv.exe (PID: 12380)
- zxcv.exe (PID: 12400)
- zxcv.exe (PID: 12416)
- zxcv.exe (PID: 12432)
- zxcv.exe (PID: 12456)
- zxcv.exe (PID: 12468)
- zxcv.exe (PID: 12480)
- zxcv.exe (PID: 12496)
- zxcv.exe (PID: 12504)
- zxcv.exe (PID: 12516)
- zxcv.exe (PID: 12528)
- zxcv.exe (PID: 12548)
- zxcv.exe (PID: 12556)
- zxcv.exe (PID: 12576)
- zxcv.exe (PID: 12672)
- zxcv.exe (PID: 12712)
- zxcv.exe (PID: 12732)
- zxcv.exe (PID: 12776)
- zxcv.exe (PID: 12756)
- zxcv.exe (PID: 12784)
- zxcv.exe (PID: 12860)
- zxcv.exe (PID: 12808)
- zxcv.exe (PID: 12828)
- zxcv.exe (PID: 12876)
- zxcv.exe (PID: 12592)
- zxcv.exe (PID: 12620)
- zxcv.exe (PID: 12632)
- zxcv.exe (PID: 12644)
- zxcv.exe (PID: 12660)
- zxcv.exe (PID: 12688)
- zxcv.exe (PID: 12932)
- zxcv.exe (PID: 12972)
- zxcv.exe (PID: 12960)
- zxcv.exe (PID: 12988)
- zxcv.exe (PID: 13012)
- zxcv.exe (PID: 13064)
- zxcv.exe (PID: 12900)
- zxcv.exe (PID: 13144)
- zxcv.exe (PID: 13128)
- zxcv.exe (PID: 13152)
- zxcv.exe (PID: 13188)
- zxcv.exe (PID: 13080)
- zxcv.exe (PID: 13096)
- zxcv.exe (PID: 13268)
- zxcv.exe (PID: 13284)
- zxcv.exe (PID: 13296)
- zxcv.exe (PID: 12220)
- zxcv.exe (PID: 7336)
- zxcv.exe (PID: 12360)
- zxcv.exe (PID: 12440)
- zxcv.exe (PID: 12512)
- zxcv.exe (PID: 13208)
- zxcv.exe (PID: 13240)
- zxcv.exe (PID: 13252)
- zxcv.exe (PID: 1868)
- zxcv.exe (PID: 13036)
- zxcv.exe (PID: 11876)
- zxcv.exe (PID: 12584)
- zxcv.exe (PID: 6056)
- zxcv.exe (PID: 13040)
- zxcv.exe (PID: 9640)
- zxcv.exe (PID: 13200)
- zxcv.exe (PID: 12476)
- zxcv.exe (PID: 12824)
- zxcv.exe (PID: 10400)
- zxcv.exe (PID: 12652)
- zxcv.exe (PID: 13280)
- zxcv.exe (PID: 10356)
- zxcv.exe (PID: 1944)
- zxcv.exe (PID: 13544)
- zxcv.exe (PID: 13392)
- zxcv.exe (PID: 13448)
- zxcv.exe (PID: 13484)
- zxcv.exe (PID: 13472)
- zxcv.exe (PID: 13496)
- zxcv.exe (PID: 13572)
- zxcv.exe (PID: 13340)
- zxcv.exe (PID: 13888)
- zxcv.exe (PID: 13812)
- zxcv.exe (PID: 13784)
- zxcv.exe (PID: 13768)
- zxcv.exe (PID: 13844)
- zxcv.exe (PID: 13980)
- zxcv.exe (PID: 13900)
- zxcv.exe (PID: 13924)
- zxcv.exe (PID: 13948)
- zxcv.exe (PID: 13644)
- zxcv.exe (PID: 13716)
- zxcv.exe (PID: 13736)
- zxcv.exe (PID: 14096)
- zxcv.exe (PID: 14080)
- zxcv.exe (PID: 14240)
- zxcv.exe (PID: 14144)
- zxcv.exe (PID: 14120)
- zxcv.exe (PID: 14208)
- zxcv.exe (PID: 14172)
- zxcv.exe (PID: 14188)
- zxcv.exe (PID: 14224)
- zxcv.exe (PID: 14252)
- zxcv.exe (PID: 14264)
- zxcv.exe (PID: 14020)
- zxcv.exe (PID: 14060)
- zxcv.exe (PID: 14068)
- zxcv.exe (PID: 14112)
- zxcv.exe (PID: 13408)
- zxcv.exe (PID: 13776)
- zxcv.exe (PID: 13988)
- zxcv.exe (PID: 13852)
- zxcv.exe (PID: 13076)
- zxcv.exe (PID: 14180)
- zxcv.exe (PID: 14236)
- zxcv.exe (PID: 14284)
- zxcv.exe (PID: 13320)
- zxcv.exe (PID: 13308)
- zxcv.exe (PID: 13876)
- zxcv.exe (PID: 13652)
- zxcv.exe (PID: 13480)
- zxcv.exe (PID: 14108)
- zxcv.exe (PID: 13492)
- zxcv.exe (PID: 14272)
- zxcv.exe (PID: 11000)
- zxcv.exe (PID: 14324)
- zxcv.exe (PID: 9904)
- zxcv.exe (PID: 9856)
- zxcv.exe (PID: 11208)
- zxcv.exe (PID: 10972)
- zxcv.exe (PID: 11024)
- zxcv.exe (PID: 14392)
- zxcv.exe (PID: 14436)
- zxcv.exe (PID: 14360)
- zxcv.exe (PID: 14372)
- zxcv.exe (PID: 14416)
- zxcv.exe (PID: 14584)
- zxcv.exe (PID: 14608)
- zxcv.exe (PID: 14632)
- zxcv.exe (PID: 14676)
- zxcv.exe (PID: 14688)
- zxcv.exe (PID: 14460)
- zxcv.exe (PID: 14484)
- zxcv.exe (PID: 14504)
- zxcv.exe (PID: 14520)
- zxcv.exe (PID: 14540)
- zxcv.exe (PID: 14564)
- zxcv.exe (PID: 14572)
- zxcv.exe (PID: 14660)
- zxcv.exe (PID: 14748)
- zxcv.exe (PID: 14764)
- zxcv.exe (PID: 14776)
- zxcv.exe (PID: 14792)
- zxcv.exe (PID: 14812)
- zxcv.exe (PID: 14824)
- zxcv.exe (PID: 14868)
- zxcv.exe (PID: 14908)
- zxcv.exe (PID: 14696)
- zxcv.exe (PID: 14720)
- zxcv.exe (PID: 14732)
- zxcv.exe (PID: 14856)
- zxcv.exe (PID: 14888)
- zxcv.exe (PID: 15048)
- zxcv.exe (PID: 15024)
- zxcv.exe (PID: 15156)
- zxcv.exe (PID: 15064)
- zxcv.exe (PID: 15080)
- zxcv.exe (PID: 15092)
- zxcv.exe (PID: 15108)
- zxcv.exe (PID: 15128)
- zxcv.exe (PID: 15140)
- zxcv.exe (PID: 14916)
- zxcv.exe (PID: 14932)
- zxcv.exe (PID: 14956)
- zxcv.exe (PID: 14980)
- zxcv.exe (PID: 14996)
- zxcv.exe (PID: 15240)
- zxcv.exe (PID: 15284)
- zxcv.exe (PID: 15324)
- zxcv.exe (PID: 15336)
- zxcv.exe (PID: 15176)
- zxcv.exe (PID: 15184)
- zxcv.exe (PID: 15192)
- zxcv.exe (PID: 15212)
- zxcv.exe (PID: 15220)
- zxcv.exe (PID: 15268)
- zxcv.exe (PID: 15292)
- zxcv.exe (PID: 14528)
- zxcv.exe (PID: 14600)
- zxcv.exe (PID: 9448)
- zxcv.exe (PID: 14684)
- zxcv.exe (PID: 10232)
- zxcv.exe (PID: 14744)
- zxcv.exe (PID: 14340)
- zxcv.exe (PID: 14412)
- zxcv.exe (PID: 14472)
- zxcv.exe (PID: 14500)
- zxcv.exe (PID: 14428)
- zxcv.exe (PID: 15044)
- zxcv.exe (PID: 15088)
- zxcv.exe (PID: 9076)
- zxcv.exe (PID: 15164)
- zxcv.exe (PID: 11640)
- zxcv.exe (PID: 14276)
- zxcv.exe (PID: 14788)
- zxcv.exe (PID: 9120)
- zxcv.exe (PID: 9816)
- zxcv.exe (PID: 14552)
- zxcv.exe (PID: 15004)
- zxcv.exe (PID: 10384)
- zxcv.exe (PID: 13440)
- zxcv.exe (PID: 8680)
- zxcv.exe (PID: 10668)
- zxcv.exe (PID: 10816)
- zxcv.exe (PID: 14104)
- zxcv.exe (PID: 15204)
- zxcv.exe (PID: 15168)
- zxcv.exe (PID: 10660)
- zxcv.exe (PID: 10084)
- zxcv.exe (PID: 10852)
- zxcv.exe (PID: 9916)
- zxcv.exe (PID: 1476)
- zxcv.exe (PID: 10736)
- zxcv.exe (PID: 14944)
- zxcv.exe (PID: 14668)
- zxcv.exe (PID: 10344)
- zxcv.exe (PID: 9912)
- zxcv.exe (PID: 10220)
- zxcv.exe (PID: 15072)
- zxcv.exe (PID: 8480)
- zxcv.exe (PID: 14152)
- zxcv.exe (PID: 10936)
- zxcv.exe (PID: 12192)
- zxcv.exe (PID: 15344)
- zxcv.exe (PID: 14200)
- zxcv.exe (PID: 15356)
- zxcv.exe (PID: 14580)
- zxcv.exe (PID: 10264)
- zxcv.exe (PID: 7448)
- zxcv.exe (PID: 9692)
- zxcv.exe (PID: 10560)
- zxcv.exe (PID: 11320)
- zxcv.exe (PID: 12668)
- zxcv.exe (PID: 10976)
- zxcv.exe (PID: 13444)
- zxcv.exe (PID: 14884)
- zxcv.exe (PID: 14940)
- zxcv.exe (PID: 15320)
- zxcv.exe (PID: 10928)
- zxcv.exe (PID: 6412)
- zxcv.exe (PID: 10808)
- zxcv.exe (PID: 15152)
- zxcv.exe (PID: 10516)
- zxcv.exe (PID: 15364)
- zxcv.exe (PID: 15380)
- zxcv.exe (PID: 15388)
- zxcv.exe (PID: 15436)
- zxcv.exe (PID: 8456)
- zxcv.exe (PID: 14076)
- zxcv.exe (PID: 15316)
- zxcv.exe (PID: 11316)
- zxcv.exe (PID: 10836)
- zxcv.exe (PID: 15408)
- zxcv.exe (PID: 15492)
- zxcv.exe (PID: 15552)
- zxcv.exe (PID: 15568)
- zxcv.exe (PID: 15448)
- zxcv.exe (PID: 15460)
- zxcv.exe (PID: 15476)
- zxcv.exe (PID: 15524)
- zxcv.exe (PID: 15644)
- zxcv.exe (PID: 15656)
- zxcv.exe (PID: 15672)
- zxcv.exe (PID: 15700)
- zxcv.exe (PID: 15716)
- zxcv.exe (PID: 15740)
- zxcv.exe (PID: 15748)
- zxcv.exe (PID: 15768)
- zxcv.exe (PID: 15600)
- zxcv.exe (PID: 15612)
- zxcv.exe (PID: 15624)
- zxcv.exe (PID: 15920)
- zxcv.exe (PID: 15948)
- zxcv.exe (PID: 16028)
- zxcv.exe (PID: 15800)
- zxcv.exe (PID: 15816)
- zxcv.exe (PID: 15824)
- zxcv.exe (PID: 15868)
- zxcv.exe (PID: 15888)
- zxcv.exe (PID: 15932)
- zxcv.exe (PID: 15980)
- zxcv.exe (PID: 15996)
- zxcv.exe (PID: 16200)
- zxcv.exe (PID: 16212)
- zxcv.exe (PID: 16264)
- zxcv.exe (PID: 16360)
- zxcv.exe (PID: 16320)
- zxcv.exe (PID: 15400)
- zxcv.exe (PID: 16056)
- zxcv.exe (PID: 16084)
- zxcv.exe (PID: 16112)
- zxcv.exe (PID: 16140)
- zxcv.exe (PID: 16156)
- zxcv.exe (PID: 7880)
- zxcv.exe (PID: 9188)
- zxcv.exe (PID: 1828)
- zxcv.exe (PID: 9092)
- zxcv.exe (PID: 8796)
- zxcv.exe (PID: 15756)
- zxcv.exe (PID: 15844)
- zxcv.exe (PID: 15940)
- zxcv.exe (PID: 1544)
- zxcv.exe (PID: 7584)
- zxcv.exe (PID: 15908)
- zxcv.exe (PID: 16288)
- zxcv.exe (PID: 16404)
- zxcv.exe (PID: 16108)
- zxcv.exe (PID: 16280)
- zxcv.exe (PID: 16336)
- zxcv.exe (PID: 9804)
- zxcv.exe (PID: 3040)
- zxcv.exe (PID: 16124)
- zxcv.exe (PID: 16568)
- zxcv.exe (PID: 16616)
- zxcv.exe (PID: 16688)
- zxcv.exe (PID: 16660)
- zxcv.exe (PID: 16460)
- zxcv.exe (PID: 16536)
- zxcv.exe (PID: 16644)
- zxcv.exe (PID: 16824)
- zxcv.exe (PID: 16968)
- zxcv.exe (PID: 16916)
- zxcv.exe (PID: 17004)
- zxcv.exe (PID: 16980)
- zxcv.exe (PID: 16992)
- zxcv.exe (PID: 16712)
- zxcv.exe (PID: 16772)
- zxcv.exe (PID: 16804)
- zxcv.exe (PID: 16884)
- zxcv.exe (PID: 16892)
- zxcv.exe (PID: 17160)
- zxcv.exe (PID: 17208)
- zxcv.exe (PID: 17288)
- zxcv.exe (PID: 17236)
- zxcv.exe (PID: 17068)
- zxcv.exe (PID: 17040)
- zxcv.exe (PID: 17104)
- zxcv.exe (PID: 17088)
- zxcv.exe (PID: 17132)
- zxcv.exe (PID: 17196)
- zxcv.exe (PID: 17368)
- zxcv.exe (PID: 17352)
- zxcv.exe (PID: 1140)
- zxcv.exe (PID: 16420)
- zxcv.exe (PID: 1200)
- zxcv.exe (PID: 16332)
- zxcv.exe (PID: 13164)
- zxcv.exe (PID: 16500)
- zxcv.exe (PID: 17332)
- zxcv.exe (PID: 17380)
- zxcv.exe (PID: 16700)
- zxcv.exe (PID: 2800)
- zxcv.exe (PID: 5536)
- zxcv.exe (PID: 16252)
- zxcv.exe (PID: 15420)
- zxcv.exe (PID: 5576)
- zxcv.exe (PID: 16592)
- zxcv.exe (PID: 848)
- zxcv.exe (PID: 16852)
- zxcv.exe (PID: 16900)
- zxcv.exe (PID: 16940)
- zxcv.exe (PID: 15008)
- zxcv.exe (PID: 16484)
- zxcv.exe (PID: 17256)
- zxcv.exe (PID: 14988)
- zxcv.exe (PID: 2904)
- zxcv.exe (PID: 16552)
- zxcv.exe (PID: 16864)
- zxcv.exe (PID: 8584)
- zxcv.exe (PID: 17392)
- zxcv.exe (PID: 17100)
- zxcv.exe (PID: 2976)
- zxcv.exe (PID: 10588)
- zxcv.exe (PID: 3920)
- zxcv.exe (PID: 12956)
- zxcv.exe (PID: 10656)
- zxcv.exe (PID: 13020)
- zxcv.exe (PID: 16440)
- zxcv.exe (PID: 16396)
- zxcv.exe (PID: 16960)
- zxcv.exe (PID: 3000)
- zxcv.exe (PID: 17264)
- zxcv.exe (PID: 14384)
- zxcv.exe (PID: 5212)
- zxcv.exe (PID: 16784)
- zxcv.exe (PID: 16876)
- zxcv.exe (PID: 17296)
- zxcv.exe (PID: 13328)
- zxcv.exe (PID: 10076)
- zxcv.exe (PID: 16196)
- zxcv.exe (PID: 7924)
- zxcv.exe (PID: 14452)
- zxcv.exe (PID: 17184)
- zxcv.exe (PID: 7400)
- zxcv.exe (PID: 9552)
- zxcv.exe (PID: 11020)
- zxcv.exe (PID: 8360)
- zxcv.exe (PID: 8536)
- zxcv.exe (PID: 15964)
- zxcv.exe (PID: 17420)
- zxcv.exe (PID: 8384)
- zxcv.exe (PID: 8304)
- zxcv.exe (PID: 17140)
- zxcv.exe (PID: 16872)
- zxcv.exe (PID: 17524)
- zxcv.exe (PID: 17608)
- zxcv.exe (PID: 17552)
- zxcv.exe (PID: 17584)
- zxcv.exe (PID: 17620)
- zxcv.exe (PID: 17436)
- zxcv.exe (PID: 17452)
- zxcv.exe (PID: 17460)
- zxcv.exe (PID: 17476)
- zxcv.exe (PID: 17500)
- zxcv.exe (PID: 17716)
- zxcv.exe (PID: 17816)
- zxcv.exe (PID: 17732)
- zxcv.exe (PID: 17756)
- zxcv.exe (PID: 17764)
- zxcv.exe (PID: 17780)
- zxcv.exe (PID: 17804)
- zxcv.exe (PID: 17832)
- zxcv.exe (PID: 17636)
- zxcv.exe (PID: 17644)
- zxcv.exe (PID: 17656)
- zxcv.exe (PID: 17672)
- zxcv.exe (PID: 17688)
- zxcv.exe (PID: 17708)
- zxcv.exe (PID: 17944)
- zxcv.exe (PID: 17968)
- zxcv.exe (PID: 18000)
- zxcv.exe (PID: 18060)
- zxcv.exe (PID: 18040)
- zxcv.exe (PID: 17856)
- zxcv.exe (PID: 17872)
- zxcv.exe (PID: 17888)
- zxcv.exe (PID: 17912)
- zxcv.exe (PID: 17932)
- zxcv.exe (PID: 17988)
- zxcv.exe (PID: 18016)
- zxcv.exe (PID: 18208)
- zxcv.exe (PID: 18216)
- zxcv.exe (PID: 18284)
- zxcv.exe (PID: 18072)
- zxcv.exe (PID: 18092)
- zxcv.exe (PID: 18116)
- zxcv.exe (PID: 18140)
- zxcv.exe (PID: 18164)
- zxcv.exe (PID: 18184)
- zxcv.exe (PID: 18240)
- zxcv.exe (PID: 18268)
- zxcv.exe (PID: 18396)
- zxcv.exe (PID: 17472)
- zxcv.exe (PID: 17448)
- zxcv.exe (PID: 18292)
- zxcv.exe (PID: 18320)
- zxcv.exe (PID: 18344)
- zxcv.exe (PID: 18356)
- zxcv.exe (PID: 18372)
- zxcv.exe (PID: 18424)
- zxcv.exe (PID: 17536)
- zxcv.exe (PID: 17728)
- zxcv.exe (PID: 17976)
- zxcv.exe (PID: 17828)
- zxcv.exe (PID: 17884)
- zxcv.exe (PID: 16652)
- zxcv.exe (PID: 17616)
- zxcv.exe (PID: 17668)
- zxcv.exe (PID: 17700)
- zxcv.exe (PID: 17740)
- zxcv.exe (PID: 17980)
- zxcv.exe (PID: 18080)
- zxcv.exe (PID: 8544)
- zxcv.exe (PID: 18340)
- zxcv.exe (PID: 9860)
- zxcv.exe (PID: 17904)
- zxcv.exe (PID: 18088)
- zxcv.exe (PID: 15992)
- zxcv.exe (PID: 5400)
- zxcv.exe (PID: 9148)
- zxcv.exe (PID: 17220)
- zxcv.exe (PID: 10856)
- zxcv.exe (PID: 12052)
- zxcv.exe (PID: 17416)
- zxcv.exe (PID: 4120)
- zxcv.exe (PID: 17604)
- zxcv.exe (PID: 17724)
- zxcv.exe (PID: 17952)
- zxcv.exe (PID: 17752)
- zxcv.exe (PID: 14388)
- zxcv.exe (PID: 18556)
- zxcv.exe (PID: 18504)
- zxcv.exe (PID: 18572)
- zxcv.exe (PID: 18588)
- zxcv.exe (PID: 18440)
- zxcv.exe (PID: 18456)
- zxcv.exe (PID: 18476)
- zxcv.exe (PID: 18496)
- zxcv.exe (PID: 18640)
- zxcv.exe (PID: 18652)
- zxcv.exe (PID: 18680)
- zxcv.exe (PID: 18712)
- zxcv.exe (PID: 18600)
- zxcv.exe (PID: 18616)
- zxcv.exe (PID: 18736)
- zxcv.exe (PID: 18852)
- zxcv.exe (PID: 18864)
- zxcv.exe (PID: 18884)
- zxcv.exe (PID: 18896)
- zxcv.exe (PID: 18920)
- zxcv.exe (PID: 18760)
- zxcv.exe (PID: 18772)
- zxcv.exe (PID: 18796)
- zxcv.exe (PID: 18816)
- zxcv.exe (PID: 18836)
- zxcv.exe (PID: 18980)
- zxcv.exe (PID: 19028)
- zxcv.exe (PID: 18992)
- zxcv.exe (PID: 19008)
- zxcv.exe (PID: 19044)
- zxcv.exe (PID: 19056)
- zxcv.exe (PID: 19080)
- zxcv.exe (PID: 18928)
- zxcv.exe (PID: 18940)
- zxcv.exe (PID: 18948)
- zxcv.exe (PID: 18964)
- zxcv.exe (PID: 19152)
- zxcv.exe (PID: 19168)
- zxcv.exe (PID: 19204)
- zxcv.exe (PID: 19252)
- zxcv.exe (PID: 19224)
- zxcv.exe (PID: 19240)
- zxcv.exe (PID: 19268)
- zxcv.exe (PID: 19096)
- zxcv.exe (PID: 19112)
- zxcv.exe (PID: 19128)
- zxcv.exe (PID: 19188)
- zxcv.exe (PID: 19360)
- zxcv.exe (PID: 19412)
- zxcv.exe (PID: 19388)
- zxcv.exe (PID: 19420)
- zxcv.exe (PID: 19280)
- zxcv.exe (PID: 19300)
- zxcv.exe (PID: 19312)
- zxcv.exe (PID: 19332)
- zxcv.exe (PID: 19344)
- zxcv.exe (PID: 19372)
- zxcv.exe (PID: 19440)
- zxcv.exe (PID: 18468)
- zxcv.exe (PID: 18484)
- zxcv.exe (PID: 10072)
- zxcv.exe (PID: 17348)
- zxcv.exe (PID: 16628)
- zxcv.exe (PID: 18632)
- zxcv.exe (PID: 18612)
- zxcv.exe (PID: 19400)
- zxcv.exe (PID: 236)
- zxcv.exe (PID: 17344)
- zxcv.exe (PID: 16488)
- zxcv.exe (PID: 18704)
- zxcv.exe (PID: 18752)
- zxcv.exe (PID: 18824)
- zxcv.exe (PID: 18860)
- zxcv.exe (PID: 18876)
- zxcv.exe (PID: 18956)
- zxcv.exe (PID: 16600)
- zxcv.exe (PID: 16424)
- zxcv.exe (PID: 16368)
- zxcv.exe (PID: 18672)
- zxcv.exe (PID: 19160)
- zxcv.exe (PID: 16300)
- zxcv.exe (PID: 15308)
- zxcv.exe (PID: 19276)
- zxcv.exe (PID: 19220)
- zxcv.exe (PID: 19000)
- zxcv.exe (PID: 19024)
- zxcv.exe (PID: 19004)
- zxcv.exe (PID: 19068)
- zxcv.exe (PID: 16272)
- zxcv.exe (PID: 15312)
- zxcv.exe (PID: 19180)
- zxcv.exe (PID: 10056)
- zxcv.exe (PID: 19140)
- zxcv.exe (PID: 18648)
- zxcv.exe (PID: 18708)
- zxcv.exe (PID: 18808)
- zxcv.exe (PID: 18972)
- zxcv.exe (PID: 19040)
- zxcv.exe (PID: 14712)
- zxcv.exe (PID: 6480)
- zxcv.exe (PID: 19328)
- zxcv.exe (PID: 19408)
- zxcv.exe (PID: 19448)
- zxcv.exe (PID: 18728)
- zxcv.exe (PID: 18492)
- zxcv.exe (PID: 8108)
- zxcv.exe (PID: 16004)
- zxcv.exe (PID: 10172)
- zxcv.exe (PID: 18176)
- zxcv.exe (PID: 19092)
- zxcv.exe (PID: 19396)
- zxcv.exe (PID: 19264)
- zxcv.exe (PID: 18520)
- zxcv.exe (PID: 14292)
- zxcv.exe (PID: 9924)
- zxcv.exe (PID: 9656)
- zxcv.exe (PID: 16104)
- zxcv.exe (PID: 15780)
- zxcv.exe (PID: 19216)
- zxcv.exe (PID: 15200)
- zxcv.exe (PID: 18524)
- zxcv.exe (PID: 12820)
- zxcv.exe (PID: 9352)
- zxcv.exe (PID: 15960)
- zxcv.exe (PID: 16192)
- zxcv.exe (PID: 16052)
- zxcv.exe (PID: 18384)
- zxcv.exe (PID: 18580)
- zxcv.exe (PID: 17268)
- zxcv.exe (PID: 18528)
- zxcv.exe (PID: 16100)
- zxcv.exe (PID: 19020)
- zxcv.exe (PID: 18056)
- zxcv.exe (PID: 16296)
- zxcv.exe (PID: 19148)
- zxcv.exe (PID: 16096)
- zxcv.exe (PID: 18960)
- zxcv.exe (PID: 15904)
- zxcv.exe (PID: 15512)
- zxcv.exe (PID: 16248)
- zxcv.exe (PID: 7404)
- zxcv.exe (PID: 16064)
- zxcv.exe (PID: 16612)
- zxcv.exe (PID: 17148)
- zxcv.exe (PID: 16976)
- zxcv.exe (PID: 18024)
- zxcv.exe (PID: 9096)
- zxcv.exe (PID: 17696)
- zxcv.exe (PID: 15680)
- zxcv.exe (PID: 18916)
- zxcv.exe (PID: 15812)
- zxcv.exe (PID: 15516)
- zxcv.exe (PID: 16400)
- zxcv.exe (PID: 17252)
- zxcv.exe (PID: 16308)
- zxcv.exe (PID: 16812)
- zxcv.exe (PID: 17880)
- zxcv.exe (PID: 16836)
- zxcv.exe (PID: 19472)
- zxcv.exe (PID: 14844)
- zxcv.exe (PID: 15724)
- zxcv.exe (PID: 8404)
- zxcv.exe (PID: 17024)
- zxcv.exe (PID: 15372)
- zxcv.exe (PID: 16492)
- zxcv.exe (PID: 19556)
- zxcv.exe (PID: 19572)
- zxcv.exe (PID: 19620)
- zxcv.exe (PID: 19636)
- zxcv.exe (PID: 19484)
- zxcv.exe (PID: 19500)
- zxcv.exe (PID: 19520)
- zxcv.exe (PID: 19532)
- zxcv.exe (PID: 19544)
- zxcv.exe (PID: 19580)
- zxcv.exe (PID: 19760)
- zxcv.exe (PID: 19796)
- zxcv.exe (PID: 19816)
- zxcv.exe (PID: 19844)
- zxcv.exe (PID: 19860)
- zxcv.exe (PID: 19652)
- zxcv.exe (PID: 19680)
- zxcv.exe (PID: 19696)
- zxcv.exe (PID: 19712)
- zxcv.exe (PID: 19744)
- zxcv.exe (PID: 19828)
- zxcv.exe (PID: 19944)
- zxcv.exe (PID: 19956)
- zxcv.exe (PID: 19968)
- zxcv.exe (PID: 19980)
- zxcv.exe (PID: 19872)
- zxcv.exe (PID: 19888)
- zxcv.exe (PID: 19904)
- zxcv.exe (PID: 19916)
- zxcv.exe (PID: 19932)
- zxcv.exe (PID: 20068)
- zxcv.exe (PID: 20092)
- zxcv.exe (PID: 20108)
- zxcv.exe (PID: 20124)
- zxcv.exe (PID: 19992)
- zxcv.exe (PID: 20004)
- zxcv.exe (PID: 20032)
- zxcv.exe (PID: 20048)
- zxcv.exe (PID: 20136)
- zxcv.exe (PID: 20208)
- zxcv.exe (PID: 20220)
- zxcv.exe (PID: 20240)
- zxcv.exe (PID: 20164)
- zxcv.exe (PID: 20148)
- zxcv.exe (PID: 20172)
- zxcv.exe (PID: 20192)
- zxcv.exe (PID: 20200)
- zxcv.exe (PID: 20352)
- zxcv.exe (PID: 20324)
- zxcv.exe (PID: 20336)
- zxcv.exe (PID: 20388)
- zxcv.exe (PID: 20364)
- zxcv.exe (PID: 20248)
- zxcv.exe (PID: 20264)
- zxcv.exe (PID: 20276)
- zxcv.exe (PID: 20284)
- zxcv.exe (PID: 20296)
- zxcv.exe (PID: 20316)
- zxcv.exe (PID: 19480)
- zxcv.exe (PID: 19728)
- zxcv.exe (PID: 19836)
- zxcv.exe (PID: 20408)
- zxcv.exe (PID: 20428)
- zxcv.exe (PID: 20440)
- zxcv.exe (PID: 20476)
- zxcv.exe (PID: 20464)
- zxcv.exe (PID: 19568)
- zxcv.exe (PID: 19672)
- zxcv.exe (PID: 20100)
- zxcv.exe (PID: 20020)
- zxcv.exe (PID: 20144)
- zxcv.exe (PID: 20232)
- zxcv.exe (PID: 20188)
- zxcv.exe (PID: 20260)
- zxcv.exe (PID: 20452)
- zxcv.exe (PID: 20376)
- zxcv.exe (PID: 20404)
- zxcv.exe (PID: 19896)
- zxcv.exe (PID: 19976)
- zxcv.exe (PID: 19924)
- zxcv.exe (PID: 5780)
- zxcv.exe (PID: 1228)
- zxcv.exe (PID: 20040)
- zxcv.exe (PID: 14248)
- zxcv.exe (PID: 9964)
- zxcv.exe (PID: 19880)
- zxcv.exe (PID: 20184)
- zxcv.exe (PID: 13840)
- zxcv.exe (PID: 13944)
- zxcv.exe (PID: 13996)
- zxcv.exe (PID: 13972)
- zxcv.exe (PID: 20472)
- zxcv.exe (PID: 19644)
- zxcv.exe (PID: 3076)
- zxcv.exe (PID: 14000)
- zxcv.exe (PID: 20508)
- zxcv.exe (PID: 20488)
- zxcv.exe (PID: 20552)
- zxcv.exe (PID: 13976)
- zxcv.exe (PID: 19564)
- zxcv.exe (PID: 19676)
- zxcv.exe (PID: 20080)
- zxcv.exe (PID: 14012)
- zxcv.exe (PID: 13968)
- zxcv.exe (PID: 20516)
- zxcv.exe (PID: 20536)
- zxcv.exe (PID: 20636)
- zxcv.exe (PID: 20652)
- zxcv.exe (PID: 20668)
- zxcv.exe (PID: 20680)
- zxcv.exe (PID: 20716)
- zxcv.exe (PID: 20568)
- zxcv.exe (PID: 20584)
- zxcv.exe (PID: 20592)
- zxcv.exe (PID: 20604)
- zxcv.exe (PID: 20620)
- zxcv.exe (PID: 20696)
- zxcv.exe (PID: 20704)
- zxcv.exe (PID: 20820)
- zxcv.exe (PID: 20844)
- zxcv.exe (PID: 20832)
- zxcv.exe (PID: 20860)
- zxcv.exe (PID: 20884)
- zxcv.exe (PID: 20872)
- zxcv.exe (PID: 20724)
- zxcv.exe (PID: 20740)
- zxcv.exe (PID: 20748)
- zxcv.exe (PID: 20772)
- zxcv.exe (PID: 20784)
- zxcv.exe (PID: 20800)
- zxcv.exe (PID: 20972)
- zxcv.exe (PID: 21016)
- zxcv.exe (PID: 21024)
- zxcv.exe (PID: 21040)
- zxcv.exe (PID: 20896)
- zxcv.exe (PID: 20908)
- zxcv.exe (PID: 20916)
- zxcv.exe (PID: 20928)
- zxcv.exe (PID: 20944)
- zxcv.exe (PID: 20960)
- zxcv.exe (PID: 20980)
- zxcv.exe (PID: 21000)
- zxcv.exe (PID: 21144)
- zxcv.exe (PID: 21164)
- zxcv.exe (PID: 21180)
- zxcv.exe (PID: 21196)
- zxcv.exe (PID: 21208)
- zxcv.exe (PID: 21048)
- zxcv.exe (PID: 21060)
- zxcv.exe (PID: 21072)
- zxcv.exe (PID: 21092)
- zxcv.exe (PID: 21112)
- zxcv.exe (PID: 21124)
- zxcv.exe (PID: 21280)
- zxcv.exe (PID: 21300)
- zxcv.exe (PID: 21328)
- zxcv.exe (PID: 21320)
- zxcv.exe (PID: 21236)
- zxcv.exe (PID: 21220)
- zxcv.exe (PID: 21252)
- zxcv.exe (PID: 21264)
- zxcv.exe (PID: 21288)
- zxcv.exe (PID: 21340)
- zxcv.exe (PID: 21352)
- zxcv.exe (PID: 21364)
- zxcv.exe (PID: 21372)
- zxcv.exe (PID: 21428)
- zxcv.exe (PID: 21396)
- zxcv.exe (PID: 21444)
- zxcv.exe (PID: 21420)
- zxcv.exe (PID: 21408)
- zxcv.exe (PID: 21452)
- zxcv.exe (PID: 21484)
- zxcv.exe (PID: 20816)
- zxcv.exe (PID: 20880)
- zxcv.exe (PID: 20000)
- zxcv.exe (PID: 20580)
- zxcv.exe (PID: 20524)
- zxcv.exe (PID: 3632)
- zxcv.exe (PID: 20676)
- zxcv.exe (PID: 20736)
- zxcv.exe (PID: 20808)
- zxcv.exe (PID: 20924)
- zxcv.exe (PID: 20968)
- zxcv.exe (PID: 21008)
- zxcv.exe (PID: 20156)
- zxcv.exe (PID: 10940)
- zxcv.exe (PID: 21136)
- zxcv.exe (PID: 21216)
- zxcv.exe (PID: 21036)
- zxcv.exe (PID: 16928)
- zxcv.exe (PID: 21056)
- zxcv.exe (PID: 17520)
- zxcv.exe (PID: 18152)
- zxcv.exe (PID: 21160)
- zxcv.exe (PID: 6240)
- zxcv.exe (PID: 21500)
- zxcv.exe (PID: 20692)
- zxcv.exe (PID: 20904)
- zxcv.exe (PID: 20576)
- zxcv.exe (PID: 21296)
- zxcv.exe (PID: 19772)
- zxcv.exe (PID: 19776)
- zxcv.exe (PID: 20416)
- zxcv.exe (PID: 21244)
- zxcv.exe (PID: 20952)
- zxcv.exe (PID: 14968)
- zxcv.exe (PID: 20308)
- zxcv.exe (PID: 21108)
- zxcv.exe (PID: 21192)
- zxcv.exe (PID: 6936)
- zxcv.exe (PID: 13884)
- zxcv.exe (PID: 16164)
- zxcv.exe (PID: 7060)
- zxcv.exe (PID: 7096)
- zxcv.exe (PID: 6976)
- zxcv.exe (PID: 16504)
- zxcv.exe (PID: 18148)
- zxcv.exe (PID: 19688)
- zxcv.exe (PID: 20344)
- zxcv.exe (PID: 21540)
- zxcv.exe (PID: 21604)
- zxcv.exe (PID: 21584)
- zxcv.exe (PID: 20348)
- zxcv.exe (PID: 20648)
- zxcv.exe (PID: 19708)
- zxcv.exe (PID: 21508)
- zxcv.exe (PID: 21524)
- zxcv.exe (PID: 21556)
- zxcv.exe (PID: 21620)
- zxcv.exe (PID: 21660)
- zxcv.exe (PID: 21776)
- zxcv.exe (PID: 21792)
- zxcv.exe (PID: 21820)
- zxcv.exe (PID: 21836)
- zxcv.exe (PID: 21640)
- zxcv.exe (PID: 21864)
- zxcv.exe (PID: 21884)
- zxcv.exe (PID: 21904)
- zxcv.exe (PID: 21916)
- zxcv.exe (PID: 21976)
- zxcv.exe (PID: 21992)
- zxcv.exe (PID: 22128)
- zxcv.exe (PID: 22084)
- zxcv.exe (PID: 22152)
- zxcv.exe (PID: 22008)
- zxcv.exe (PID: 22028)
- zxcv.exe (PID: 22044)
- zxcv.exe (PID: 22060)
- zxcv.exe (PID: 22072)
- zxcv.exe (PID: 22140)
- zxcv.exe (PID: 22256)
- zxcv.exe (PID: 22284)
- zxcv.exe (PID: 22304)
- zxcv.exe (PID: 22176)
- zxcv.exe (PID: 22188)
- zxcv.exe (PID: 22208)
- zxcv.exe (PID: 22228)
- zxcv.exe (PID: 22312)
- zxcv.exe (PID: 22424)
- zxcv.exe (PID: 22488)
- zxcv.exe (PID: 22468)
- zxcv.exe (PID: 22336)
- zxcv.exe (PID: 22360)
- zxcv.exe (PID: 22388)
- zxcv.exe (PID: 22404)
- zxcv.exe (PID: 19604)
- zxcv.exe (PID: 20456)
- zxcv.exe (PID: 18844)
- zxcv.exe (PID: 19692)
- zxcv.exe (PID: 22512)
- zxcv.exe (PID: 6864)
- zxcv.exe (PID: 14536)
- zxcv.exe (PID: 13140)
- zxcv.exe (PID: 13584)
- zxcv.exe (PID: 21852)
- zxcv.exe (PID: 21568)
- zxcv.exe (PID: 21632)
- zxcv.exe (PID: 3584)
- zxcv.exe (PID: 21764)
- zxcv.exe (PID: 21900)
- zxcv.exe (PID: 22164)
- zxcv.exe (PID: 22296)
- zxcv.exe (PID: 22328)
- zxcv.exe (PID: 21804)
- zxcv.exe (PID: 21844)
- zxcv.exe (PID: 22068)
- zxcv.exe (PID: 22112)
- zxcv.exe (PID: 22368)
- zxcv.exe (PID: 22096)
- zxcv.exe (PID: 22204)
- zxcv.exe (PID: 4716)
- zxcv.exe (PID: 16908)
- zxcv.exe (PID: 12444)
- zxcv.exe (PID: 19340)
- zxcv.exe (PID: 22476)
- zxcv.exe (PID: 22524)
- zxcv.exe (PID: 21520)
- zxcv.exe (PID: 20180)
- zxcv.exe (PID: 21808)
- zxcv.exe (PID: 22020)
- zxcv.exe (PID: 21204)
- zxcv.exe (PID: 9416)
- zxcv.exe (PID: 21896)
- zxcv.exe (PID: 12804)
- zxcv.exe (PID: 3532)
- zxcv.exe (PID: 22464)
- zxcv.exe (PID: 19452)
- zxcv.exe (PID: 17232)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 10348)
Adds/modifies Windows certificates
- newbundle.exe (PID: 11200)
- powershell.exe (PID: 10244)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 10348)
Downloads file from URI via Powershell
- powershell.exe (PID: 14444)
Found IP address in command line
- powershell.exe (PID: 14444)
Checks Windows Trust Settings
- Unit.exe (PID: 13800)
Script adds exclusion extension to Windows Defender
- xdd.exe (PID: 13000)
Manipulates environment variables
- powershell.exe (PID: 18692)
Script disables Windows Defender's IPS
- payload.exe (PID: 10756)
Script disables Windows Defender's real-time protection
- payload.exe (PID: 10756)
The process executes via Task Scheduler
- Windows.exe (PID: 13832)
- service.exe (PID: 21312)
INFO
Manual execution by a user
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6648)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 4136)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5240)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6768)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6920)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6032)
- 4363463463464363463463463.exe (PID: 6596)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 2092)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 6236)
- 4363463463464363463463463.exe (PID: 6984)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6556)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 7044)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 520)
- 4363463463464363463463463.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 7372)
- 4363463463464363463463463.exe (PID: 7660)
- 4363463463464363463463463.exe (PID: 7792)
- 4363463463464363463463463.exe (PID: 8352)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8776)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 9036)
- 4363463463464363463463463.exe (PID: 7656)
- 4363463463464363463463463.exe (PID: 9580)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 9972)
- 4363463463464363463463463.exe (PID: 8816)
- 4363463463464363463463463.exe (PID: 12944)
- 4363463463464363463463463.exe (PID: 13676)
- msedge.exe (PID: 9512)
- 4363463463464363463463463.exe (PID: 16284)
- 4363463463464363463463463.exe (PID: 5392)
- 4363463463464363463463463.exe (PID: 16520)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 16676)
- 4363463463464363463463463.exe (PID: 17280)
Reads the computer name
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 5920)
- svchost.exe (PID: 1328)
- onlysteal.exe (PID: 6968)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6764)
- 22.exe (PID: 6636)
- idmans.exe (PID: 5036)
- vncgroups.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7184)
- gagagggagagag.exe (PID: 7232)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 7428)
- contorax.exe (PID: 7504)
- winmsbt.exe (PID: 7708)
- 4363463463464363463463463.exe (PID: 7792)
- vorpgkadeg.exe (PID: 7996)
- joiner.exe (PID: 8012)
- Discord.exe (PID: 7444)
- hyperBlockCrtCommon.exe (PID: 8212)
- server.exe (PID: 8316)
- 4363463463464363463463463.exe (PID: 8516)
- Ammyy.exe (PID: 8872)
- Ammyy.exe (PID: 8904)
- Ammyy.exe (PID: 8956)
- 4363463463464363463463463.exe (PID: 8928)
- Client-built.exe (PID: 9088)
- boleto.exe (PID: 3568)
- 4363463463464363463463463.exe (PID: 7656)
- SGVP%20Client%20program.exe (PID: 8940)
- MK.exe (PID: 8840)
- 5KNCHALAH.exe (PID: 9180)
- svchost.exe (PID: 9240)
- Client.exe (PID: 9408)
- jgesfyhjsefa.exe (PID: 9472)
- server.exe (PID: 9652)
- WenzCord.exe (PID: 9520)
- 4363463463464363463463463.exe (PID: 9740)
- utility-inst.tmp (PID: 9868)
- aidans.dont.run.exe (PID: 9940)
- Discord.exe (PID: 10112)
- meshagent32-group.exe (PID: 10100)
- SrbijaSetupHokej.tmp (PID: 8848)
- 4363463463464363463463463.exe (PID: 8816)
- WenzCord.exe (PID: 1348)
- ptihjawdthas.exe (PID: 8048)
- build6_unencrypted.exe (PID: 640)
- svchost.exe (PID: 8484)
- DiscordSpotifyBypass.exe (PID: 9352)
- pornhub_downloader.exe (PID: 10184)
- kp8dnpa9.exe (PID: 8488)
- server.exe (PID: 9652)
- popapoers.exe (PID: 10236)
- SearchApp.exe (PID: 10252)
- DivineDialogue.exe (PID: 10316)
- runtime.exe (PID: 10324)
- alex2025.exe (PID: 11080)
- svchost.exe (PID: 11188)
- pornhub_downloader.exe (PID: 11092)
- k360.exe (PID: 11236)
- server.exe (PID: 9480)
- 99awhy8l.exe (PID: 10572)
- ShellExperienceHost.exe (PID: 9560)
- curlapp64.exe (PID: 11356)
- RegAsm.exe (PID: 11556)
- newbundle.exe (PID: 11200)
- 87f3f2.exe (PID: 11872)
- wow.exe (PID: 8740)
- OptiProV2.exe (PID: 12840)
- MSBuild.exe (PID: 13056)
- client.exe (PID: 12700)
- v_dolg.exe (PID: 12392)
- 856.exe (PID: 12388)
- uctgkfb7.exe (PID: 10320)
- petya.exe (PID: 1572)
- clcs.exe (PID: 11072)
- BitLockerToGo.exe (PID: 13580)
- WenzCord.exe (PID: 14384)
- uhigdbf.exe (PID: 12568)
- payload.exe (PID: 10756)
- foggy-mountains.exe (PID: 12748)
- 4363463463464363463463463.exe (PID: 13676)
- steamerx.exe (PID: 14592)
- LoadNew.exe (PID: 15532)
- Client.exe (PID: 3620)
- svchost.exe (PID: 16516)
- 4363463463464363463463463.exe (PID: 17280)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 16676)
- server.exe (PID: 18032)
- hs.exe (PID: 18548)
- clamer.exe (PID: 18540)
- 12.exe (PID: 20012)
- svchost.exe (PID: 10496)
- newwork.tmp (PID: 21952)
- mountain-pasture.exe (PID: 20024)
Checks supported languages
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- svchost.exe (PID: 1328)
- onlysteal.exe (PID: 6968)
- kp8dnpa9.exe (PID: 5192)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 2008)
- 22.exe (PID: 6636)
- 4363463463464363463463463.exe (PID: 6232)
- agent.exe (PID: 6476)
- vncgroups.exe (PID: 6572)
- gagagggagagag.exe (PID: 7232)
- 4363463463464363463463463.exe (PID: 7184)
- idmans.exe (PID: 5036)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 7428)
- contorax.exe (PID: 7504)
- ew.exe (PID: 7596)
- winmsbt.exe (PID: 7708)
- random.exe (PID: 7584)
- vorpgkadeg.exe (PID: 7996)
- 4363463463464363463463463.exe (PID: 7792)
- Discord.exe (PID: 7444)
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- fern_wifi_recon%252.34.exe (PID: 8288)
- 4363463463464363463463463.exe (PID: 8516)
- server.exe (PID: 8316)
- Ammyy.exe (PID: 8872)
- Ammyy.exe (PID: 8904)
- Client-built.exe (PID: 9088)
- chcp.com (PID: 9060)
- Ammyy.exe (PID: 8956)
- 4363463463464363463463463.exe (PID: 7656)
- SGVP%20Client%20program.exe (PID: 8940)
- MK.exe (PID: 8840)
- 5KNCHALAH.exe (PID: 9180)
- Client.exe (PID: 9408)
- svchost.exe (PID: 9240)
- WenzCord.exe (PID: 9520)
- utility-inst.exe (PID: 9796)
- Installeraus.exe (PID: 9808)
- aidans.dont.run.exe (PID: 9940)
- utility-inst.tmp (PID: 9868)
- Discord.exe (PID: 10112)
- meshagent32-group.exe (PID: 10100)
- boleto.exe (PID: 3568)
- SrbijaSetupHokej.exe (PID: 10176)
- 4363463463464363463463463.exe (PID: 8816)
- SrbijaSetupHokej.tmp (PID: 8848)
- ptihjawdthas.exe (PID: 8048)
- WenzCord.exe (PID: 1348)
- 4363463463464363463463463.exe (PID: 6764)
- blackload.exe (PID: 10224)
- jgesfyhjsefa.exe (PID: 9472)
- DiscordSpotifyBypass.exe (PID: 9352)
- server.exe (PID: 9652)
- build6_unencrypted.exe (PID: 640)
- kp8dnpa9.exe (PID: 8488)
- svchost.exe (PID: 8484)
- pornhub_downloader.exe (PID: 10184)
- loader.exe (PID: 8392)
- popapoers.exe (PID: 10236)
- server.exe (PID: 9652)
- SearchApp.exe (PID: 10252)
- runtime.exe (PID: 10324)
- 7777.exe (PID: 9372)
- chcp.com (PID: 10268)
- DivineDialogue.exe (PID: 10316)
- alex2025.exe (PID: 10516)
- zxcv.exe (PID: 10552)
- alex2025.exe (PID: 11080)
- pornhub_downloader.exe (PID: 11092)
- k360.exe (PID: 11236)
- 4363463463464363463463463.exe (PID: 9740)
- svchost.exe (PID: 11188)
- wow.exe (PID: 8740)
- ShellExperienceHost.exe (PID: 9560)
- curlapp64.exe (PID: 11356)
- RegAsm.exe (PID: 11556)
- newbundle.exe (PID: 11200)
- v_dolg.exe (PID: 12392)
- server.exe (PID: 9480)
- uhigdbf.exe (PID: 12568)
- 87f3f2.exe (PID: 11872)
- OptiProV2.exe (PID: 12840)
- MSBuild.exe (PID: 13056)
- 4363463463464363463463463.exe (PID: 8928)
- 856.exe (PID: 12388)
- petya.exe (PID: 1572)
- client.exe (PID: 12700)
- xdd.exe (PID: 13000)
- uctgkfb7.exe (PID: 10320)
- 99awhy8l.exe (PID: 10572)
- BitLockerToGo.exe (PID: 13580)
- Unit.exe (PID: 13800)
- clcs.exe (PID: 11072)
- WenzCord.exe (PID: 14384)
- payload.exe (PID: 10756)
- 4363463463464363463463463.exe (PID: 13676)
- steamerx.exe (PID: 14592)
- LoadNew.exe (PID: 15532)
- Client.exe (PID: 3620)
- lummetc.exe (PID: 16472)
- svchost.exe (PID: 16516)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 17280)
- 4363463463464363463463463.exe (PID: 16676)
- server.exe (PID: 18032)
- clamer.exe (PID: 18540)
- chcp.com (PID: 18488)
- hs.exe (PID: 18548)
- hashed.exe (PID: 19072)
- 12.exe (PID: 20012)
- mountain-pasture.exe (PID: 20024)
- Lu4421.exe (PID: 21572)
- stub.exe (PID: 19308)
- newwork.exe (PID: 21592)
- newwork.tmp (PID: 21952)
- MS14-068.exe (PID: 21232)
- build_2024-07-27_00-41.exe (PID: 22264)
- rstxdhuj.exe (PID: 22372)
- svchost.exe (PID: 10496)
- MS14-068.exe (PID: 22460)
Disables trace logs
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 7792)
- winmsbt.exe (PID: 7708)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 7656)
- 4363463463464363463463463.exe (PID: 9740)
- boleto.exe (PID: 3568)
- jgesfyhjsefa.exe (PID: 9472)
- 4363463463464363463463463.exe (PID: 8816)
- SearchApp.exe (PID: 10252)
- payload.exe (PID: 10756)
- powershell.exe (PID: 14444)
- 4363463463464363463463463.exe (PID: 16676)
- 4363463463464363463463463.exe (PID: 17320)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7184)
- XClient.exe (PID: 7340)
- idmans.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 7428)
- contorax.exe (PID: 7504)
- svchost.exe (PID: 1328)
- winmsbt.exe (PID: 7708)
- 4363463463464363463463463.exe (PID: 7792)
- hyperBlockCrtCommon.exe (PID: 8212)
- gagagggagagag.exe (PID: 7232)
- Discord.exe (PID: 7444)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 7656)
- Client-built.exe (PID: 9088)
- SGVP%20Client%20program.exe (PID: 8940)
- 5KNCHALAH.exe (PID: 9180)
- WenzCord.exe (PID: 9520)
- boleto.exe (PID: 3568)
- jgesfyhjsefa.exe (PID: 9472)
- Client.exe (PID: 9408)
- 4363463463464363463463463.exe (PID: 9740)
- aidans.dont.run.exe (PID: 9940)
- WenzCord.exe (PID: 1348)
- 4363463463464363463463463.exe (PID: 8816)
- Discord.exe (PID: 10112)
- build6_unencrypted.exe (PID: 640)
- SearchApp.exe (PID: 10252)
- runtime.exe (PID: 10324)
- RegAsm.exe (PID: 11556)
- newbundle.exe (PID: 11200)
- MSBuild.exe (PID: 13056)
- OptiProV2.exe (PID: 12840)
- uctgkfb7.exe (PID: 10320)
- client.exe (PID: 12700)
- Unit.exe (PID: 13800)
- steamerx.exe (PID: 14592)
- 4363463463464363463463463.exe (PID: 13676)
- WenzCord.exe (PID: 14384)
- Client.exe (PID: 3620)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 16676)
- 4363463463464363463463463.exe (PID: 17280)
- rstxdhuj.exe (PID: 22372)
- MS14-068.exe (PID: 22460)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6764)
- 22.exe (PID: 6636)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7428)
- winmsbt.exe (PID: 7708)
- 4363463463464363463463463.exe (PID: 7792)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 8516)
- Ammyy.exe (PID: 8872)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 7656)
- boleto.exe (PID: 3568)
- 4363463463464363463463463.exe (PID: 9740)
- utility-inst.tmp (PID: 9868)
- jgesfyhjsefa.exe (PID: 9472)
- 4363463463464363463463463.exe (PID: 8816)
- SearchApp.exe (PID: 10252)
- WerFault.exe (PID: 9704)
- mshta.exe (PID: 10524)
- Unit.exe (PID: 13800)
- payload.exe (PID: 10756)
- 4363463463464363463463463.exe (PID: 13676)
- powershell.exe (PID: 14444)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 17280)
- 4363463463464363463463463.exe (PID: 16676)
- stub.exe (PID: 19308)
- WerFault.exe (PID: 16624)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 7020)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6016)
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6776)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 6232)
- 4363463463464363463463463.exe (PID: 7184)
- winmsbt.exe (PID: 7708)
- 4363463463464363463463463.exe (PID: 6764)
- 4363463463464363463463463.exe (PID: 7428)
- gagagggagagag.exe (PID: 7232)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 7656)
- 4363463463464363463463463.exe (PID: 8816)
- kp8dnpa9.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 8928)
- alex2025.exe (PID: 11080)
- 4363463463464363463463463.exe (PID: 9740)
- 4363463463464363463463463.exe (PID: 7792)
- WerFault.exe (PID: 9704)
- WerFault.exe (PID: 9464)
- Unit.exe (PID: 13800)
- BitLockerToGo.exe (PID: 13580)
- v_dolg.exe (PID: 12392)
- payload.exe (PID: 10756)
- 4363463463464363463463463.exe (PID: 13676)
- LoadNew.exe (PID: 15532)
- 4363463463464363463463463.exe (PID: 17320)
- 4363463463464363463463463.exe (PID: 16676)
- 4363463463464363463463463.exe (PID: 17280)
- lummetc.exe (PID: 16472)
- WerFault.exe (PID: 16624)
The process uses the downloaded file
- 4363463463464363463463463.exe (PID: 6200)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 5320)
- onlysteal.exe (PID: 6968)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6888)
- 4363463463464363463463463.exe (PID: 6576)
- vncgroups.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 7020)
- contorax.exe (PID: 7504)
- 4363463463464363463463463.exe (PID: 5920)
- svchost.exe (PID: 1328)
- wscript.exe (PID: 6288)
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- Discord.exe (PID: 7444)
- 4363463463464363463463463.exe (PID: 7428)
- server.exe (PID: 8316)
- Client-built.exe (PID: 9088)
- SGVP%20Client%20program.exe (PID: 8940)
- Client.exe (PID: 9408)
- WenzCord.exe (PID: 9520)
- boleto.exe (PID: 3568)
- jgesfyhjsefa.exe (PID: 9472)
- WenzCord.exe (PID: 1348)
- 4363463463464363463463463.exe (PID: 6764)
- server.exe (PID: 9652)
- 4363463463464363463463463.exe (PID: 7184)
- build6_unencrypted.exe (PID: 640)
- pornhub_downloader.exe (PID: 10184)
- 4363463463464363463463463.exe (PID: 624)
- 4363463463464363463463463.exe (PID: 8516)
- DivineDialogue.exe (PID: 10316)
- mshta.exe (PID: 10524)
- server.exe (PID: 9652)
- pornhub_downloader.exe (PID: 11092)
- svchost.exe (PID: 11188)
- 4363463463464363463463463.exe (PID: 7792)
- client.exe (PID: 12700)
- XClient.exe (PID: 7340)
- WenzCord.exe (PID: 14384)
- server.exe (PID: 9480)
- Client.exe (PID: 3620)
- svchost.exe (PID: 16516)
- OptiProV2.exe (PID: 12840)
- clamer.exe (PID: 18540)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 7428)
- Installeraus.exe (PID: 9808)
- DiscordSpotifyBypass.exe (PID: 9352)
- 4363463463464363463463463.exe (PID: 8516)
- feb9sxwk.exe (PID: 11144)
- 4363463463464363463463463.exe (PID: 8928)
- xdd.exe (PID: 13000)
- SrbijaSetupHokej.tmp (PID: 8848)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 5320)
- 4363463463464363463463463.exe (PID: 6200)
- onlysteal.exe (PID: 6968)
- 4363463463464363463463463.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 6888)
- vncgroups.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 6576)
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 7020)
- contorax.exe (PID: 7504)
- svchost.exe (PID: 1328)
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- Ammyy.exe (PID: 8956)
- 4363463463464363463463463.exe (PID: 7428)
- Discord.exe (PID: 7444)
- server.exe (PID: 8316)
- svchost.exe (PID: 9240)
- 4363463463464363463463463.exe (PID: 5920)
- 4363463463464363463463463.exe (PID: 7656)
- boleto.exe (PID: 3568)
- ptihjawdthas.exe (PID: 8048)
- XClient.exe (PID: 7340)
- 4363463463464363463463463.exe (PID: 6764)
- server.exe (PID: 9652)
- svchost.exe (PID: 8484)
- pornhub_downloader.exe (PID: 10184)
- 4363463463464363463463463.exe (PID: 624)
- WenzCord.exe (PID: 1348)
- 4363463463464363463463463.exe (PID: 7184)
- pornhub_downloader.exe (PID: 11092)
- server.exe (PID: 9652)
- 4363463463464363463463463.exe (PID: 9740)
- build6_unencrypted.exe (PID: 640)
- svchost.exe (PID: 11188)
- 4363463463464363463463463.exe (PID: 8516)
- 4363463463464363463463463.exe (PID: 8928)
- 4363463463464363463463463.exe (PID: 7792)
- 99awhy8l.exe (PID: 10572)
- WenzCord.exe (PID: 14384)
- server.exe (PID: 9480)
- svchost.exe (PID: 16516)
- 4363463463464363463463463.exe (PID: 13676)
- 4363463463464363463463463.exe (PID: 16676)
- 856.exe (PID: 12388)
- 4363463463464363463463463.exe (PID: 17280)
- clamer.exe (PID: 18540)
Sends debugging messages
- 4363463463464363463463463.exe (PID: 6820)
- 4363463463464363463463463.exe (PID: 6888)
- random.exe (PID: 7584)
- popapoers.exe (PID: 10236)
- 4363463463464363463463463.exe (PID: 7428)
- 4363463463464363463463463.exe (PID: 8516)
- petya.exe (PID: 1572)
Drops encrypted VBS script (Microsoft Script Encoder)
- onlysteal.exe (PID: 6968)
- wscript.exe (PID: 6288)
Creates files in the program directory
- vncgroups.exe (PID: 6572)
- contorax.exe (PID: 7504)
- hyperBlockCrtCommon.exe (PID: 8212)
- Ammyy.exe (PID: 8872)
- server.exe (PID: 8316)
- SGVP%20Client%20program.exe (PID: 8940)
Creates files or folders in the user directory
- 22.exe (PID: 6636)
- joiner.exe (PID: 8012)
- Discord.exe (PID: 7444)
- server.exe (PID: 8316)
- Client-built.exe (PID: 9088)
- Installeraus.exe (PID: 9808)
- WenzCord.exe (PID: 9520)
- ptihjawdthas.exe (PID: 8048)
- jgesfyhjsefa.exe (PID: 9472)
- server.exe (PID: 9652)
- server.exe (PID: 9652)
- 87f3f2.exe (PID: 11872)
- newbundle.exe (PID: 11200)
- RegAsm.exe (PID: 11556)
- Unit.exe (PID: 13800)
- WerFault.exe (PID: 9464)
- WerFault.exe (PID: 9704)
- server.exe (PID: 9480)
- boleto.exe (PID: 3568)
- 856.exe (PID: 12388)
Reads Environment values
- winmsbt.exe (PID: 7708)
- svchost.exe (PID: 1328)
- XClient.exe (PID: 7340)
- hyperBlockCrtCommon.exe (PID: 8212)
- Client-built.exe (PID: 9088)
- SGVP%20Client%20program.exe (PID: 8940)
- Client.exe (PID: 9408)
- WenzCord.exe (PID: 9520)
- 22.exe (PID: 6636)
- boleto.exe (PID: 3568)
- WenzCord.exe (PID: 1348)
- SearchApp.exe (PID: 10252)
- WenzCord.exe (PID: 14384)
- payload.exe (PID: 10756)
- Client.exe (PID: 3620)
- 5KNCHALAH.exe (PID: 9180)
Create files in a temporary directory
- joiner.exe (PID: 8012)
- hyperBlockCrtCommon.exe (PID: 8212)
- Discord.exe (PID: 7444)
- server.exe (PID: 8316)
- svchost.exe (PID: 9240)
- server.exe (PID: 9652)
- utility-inst.exe (PID: 9796)
- Installeraus.exe (PID: 9808)
- utility-inst.tmp (PID: 9868)
- SrbijaSetupHokej.exe (PID: 10176)
- SrbijaSetupHokej.tmp (PID: 8848)
- svchost.exe (PID: 8484)
- DiscordSpotifyBypass.exe (PID: 9352)
- pornhub_downloader.exe (PID: 10184)
- server.exe (PID: 9652)
- WenzCord.exe (PID: 1348)
- DivineDialogue.exe (PID: 10316)
- pornhub_downloader.exe (PID: 11092)
- svchost.exe (PID: 11188)
- server.exe (PID: 9480)
- wow.exe (PID: 8740)
- 99awhy8l.exe (PID: 10572)
- foggy-mountains.exe (PID: 12748)
- 856.exe (PID: 12388)
- uhigdbf.exe (PID: 12568)
- svchost.exe (PID: 16516)
- hs.exe (PID: 18548)
- svchost.exe (PID: 10496)
- newwork.exe (PID: 21592)
- MS14-068.exe (PID: 21232)
- clamer.exe (PID: 18540)
Changes the display of characters in the console
- cmd.exe (PID: 8624)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 10844)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 6764)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 8872)
- powershell.exe (PID: 8876)
- powershell.exe (PID: 8888)
- powershell.exe (PID: 9656)
- powershell.exe (PID: 7776)
- powershell.exe (PID: 10268)
- powershell.exe (PID: 10244)
- powershell.exe (PID: 10856)
- powershell.exe (PID: 14648)
- powershell.exe (PID: 14820)
- powershell.exe (PID: 8576)
- powershell.exe (PID: 16304)
- powershell.exe (PID: 16452)
- powershell.exe (PID: 18692)
Reads product name
- 22.exe (PID: 6636)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8160)
- powershell.exe (PID: 7892)
- powershell.exe (PID: 8872)
- powershell.exe (PID: 8888)
- powershell.exe (PID: 8876)
- powershell.exe (PID: 9656)
- powershell.exe (PID: 7776)
- powershell.exe (PID: 10268)
- powershell.exe (PID: 10244)
- powershell.exe (PID: 10856)
- powershell.exe (PID: 14648)
- powershell.exe (PID: 14820)
- powershell.exe (PID: 8576)
- powershell.exe (PID: 16304)
- powershell.exe (PID: 16452)
- powershell.exe (PID: 18804)
- powershell.exe (PID: 18692)
Reads Internet Explorer settings
- mshta.exe (PID: 10524)
Application launched itself
- msedge.exe (PID: 13044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 665
Monitored processes
1 507
Malicious processes
72
Suspicious processes
21
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Users\admin\Desktop\Files\zxcv.exe" | C:\Users\admin\Desktop\Files\zxcv.exe | — | zxcv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 624 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 624 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 640 | "C:\Users\admin\Desktop\Files\build6_unencrypted.exe" | C:\Users\admin\Desktop\Files\build6_unencrypted.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\Users\admin\Desktop\Files\zxcv.exe" | C:\Users\admin\Desktop\Files\zxcv.exe | — | zxcv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\Desktop\Files\zxcv.exe" | C:\Users\admin\Desktop\Files\zxcv.exe | — | zxcv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | "C:\Users\admin\Desktop\Files\zxcv.exe" | C:\Users\admin\Desktop\Files\zxcv.exe | — | zxcv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\Desktop\Files\zxcv.exe" | C:\Users\admin\Desktop\Files\zxcv.exe | — | zxcv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
209 079
Read events
208 745
Write events
315
Delete events
19
Modification events
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6888) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
189
Suspicious files
141
Text files
71
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6820 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svchost.exe | executable | |
MD5:E281C07B2469B7943ABD04F9C39D2D81 | SHA256:0DE3CC456FD163B597841CF6932B879D87FE0FFDBACBF52336C6CBFBB943BBAD | |||
| 6888 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\vncgroups.exe | executable | |
MD5:532ABCCDFE34F585BE8EEC40BDC7972D | SHA256:0BE4487462EDE94362A2CE208E7C256E1C2D6ACF361B6CDA72FBAA2A3A66E6B8 | |||
| 6572 | vncgroups.exe | C:\ProgramData\idmans\idmans.exe | executable | |
MD5:532ABCCDFE34F585BE8EEC40BDC7972D | SHA256:0BE4487462EDE94362A2CE208E7C256E1C2D6ACF361B6CDA72FBAA2A3A66E6B8 | |||
| 6200 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\onlysteal.exe | executable | |
MD5:8F81AC89B9F6DBCCF07A86AF59FAA6BA | SHA256:766B497466955F86E0D049C25AA6F99880D230ACBB8D1141408FE0E8169FB46A | |||
| 2008 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\22.exe | executable | |
MD5:301DAF49CF3821D82A515D447326026A | SHA256:7197DC2E6243B3AA6BA71825C04B381A98922982DE4232BB27474EB69BA43A28 | |||
| 6820 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\XClient.exe | executable | |
MD5:CF14FAC9FA45E4989AD1DB2910ED98FD | SHA256:3DF057F43A8C20C88FE2A2266AC09414FCF9DAC4037E9A4F6E95AB66E6409636 | |||
| 6636 | 22.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\1[1].bin | binary | |
MD5:8DB5BA6BB040A5EC4ABF85B25FEF7291 | SHA256:FA2B12EA83C959801A319B92E73409B1912A080D464E5AFD612DA02C3D38AC6D | |||
| 6576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\agent.exe | executable | |
MD5:AFF07019035BBFE5BAC96D943FADB530 | SHA256:C2E367C6F38B6276680526550403573A74E4DB2F2469C7936AFC2B935781FEB6 | |||
| 6888 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\ew.exe | executable | |
MD5:D76E1525C8998795867A17ED33573552 | SHA256:F4DD44BC19C19056794D29151A5B1BB76AFD502388622E24C863A8494AF147DD | |||
| 7504 | contorax.exe | C:\ProgramData\Microsoft Subsystem Framework\winmsbt.exe | executable | |
MD5:771B8E84BA4F0215298D9DADFE5A10BF | SHA256:3F074FB6A883663F2937FD9435FC90F8D31CEABE496627D40B3813DBCC472ED0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
134
TCP/UDP connections
634
DNS requests
250
Threats
433
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 92.123.37.9:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 2.18.79.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5320 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.209:80 | http://185.215.113.209/inc/kp8dnpa9.exe | unknown | — | — | malicious |
6200 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.16:80 | http://185.215.113.16/inc/onlysteal.exe | unknown | — | — | malicious |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 92.123.37.9:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 92.123.37.9:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6016 | 4363463463464363463463463.exe | GET | — | 183.57.21.131:8095 | http://183.57.21.131:8095/TMS_C028.exe | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.18.79.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.79.138:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 95.101.23.43:443 | www.bing.com | Akamai International B.V. | AT | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5776 | svchost.exe | 2.18.79.138:80 | crl.microsoft.com | Akamai International B.V. | AT | whitelisted |
— | — | 2.18.79.138:80 | crl.microsoft.com | Akamai International B.V. | AT | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.18.79.138:80 | crl.microsoft.com | Akamai International B.V. | AT | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 92.123.37.9:80 | www.microsoft.com | AKAMAI-AS | AT | whitelisted |
— | — | 92.123.37.9:80 | www.microsoft.com | AKAMAI-AS | AT | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| shared |
github.com |
| shared |
twizthash.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5320 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
5320 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6200 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
5320 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6200 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
5320 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5320 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6200 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6200 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6200 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
19 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
random.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
popapoers.exe | This assembly was protected by demo version of ArmDot more than 7 days ago
Buy full version at https://www.armdot.com/order.html |
popapoers.exe | "
|
popapoers.exe | CLR: Managed code called FailFast, saying " |
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|