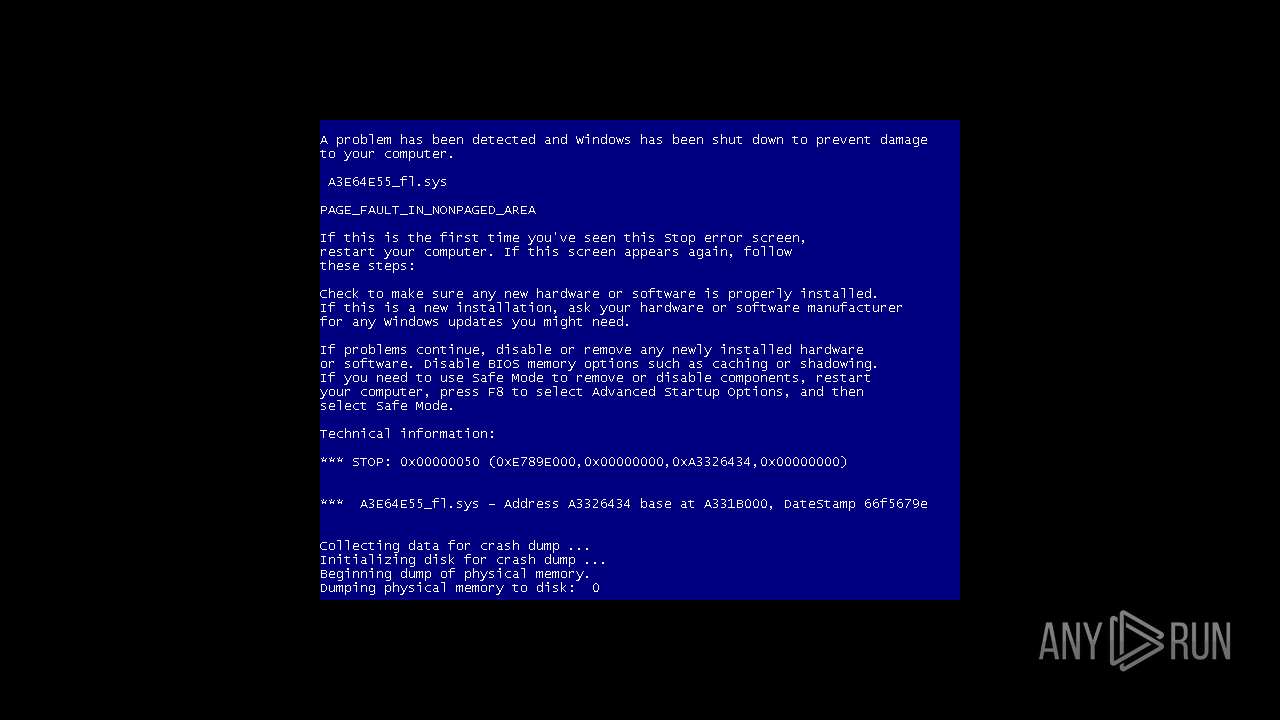
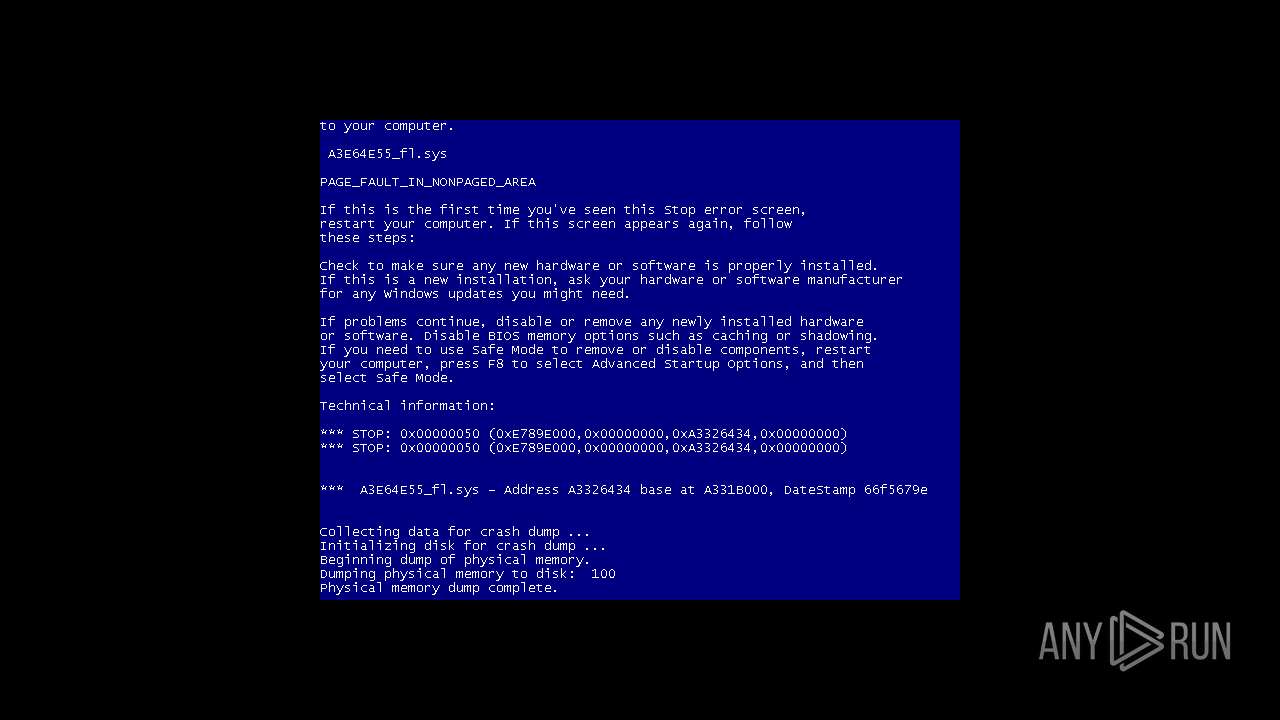
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/d0daee64-6c10-4286-a637-b187cc5a686f |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | November 14, 2024, 23:43:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Amadey has been detected
- Gxtuum.exe (PID: 900)
- Offnewhere.exe (PID: 2408)
Bypass execution policy to execute commands
- powershell.exe (PID: 764)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 3472)
- powershell.exe (PID: 2784)
Changes powershell execution policy (Bypass)
- svchost.exe (PID: 3696)
Connects to the CnC server
- Gxtuum.exe (PID: 900)
AMADEY has been detected (SURICATA)
- Gxtuum.exe (PID: 900)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 1964)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 3696)
- sysvplervcs.exe (PID: 2548)
- cmd.exe (PID: 2832)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 1964)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 3696)
- svchost.exe (PID: 2532)
Executing a file with an untrusted certificate
- hhnjqu9y.exe (PID: 2256)
- crypted2.exe (PID: 2904)
- crypted2.exe (PID: 3124)
- crypted2.exe (PID: 3652)
- crypted2.exe (PID: 1672)
- crypted2.exe (PID: 3080)
- crypted2.exe (PID: 3904)
- crypted2.exe (PID: 3172)
- crypted2.exe (PID: 1820)
- crypted2.exe (PID: 4076)
- crypted2.exe (PID: 3828)
- crypted2.exe (PID: 924)
- crypted2.exe (PID: 3332)
- crypted2.exe (PID: 1076)
- crypted2.exe (PID: 2032)
- crypted2.exe (PID: 3240)
- crypted2.exe (PID: 1524)
- crypted2.exe (PID: 1800)
- crypted2.exe (PID: 1828)
- crypted2.exe (PID: 2284)
- crypted2.exe (PID: 3980)
- crypted2.exe (PID: 3152)
- crypted2.exe (PID: 764)
- crypted2.exe (PID: 3780)
- crypted2.exe (PID: 3920)
- crypted2.exe (PID: 2736)
- crypted2.exe (PID: 2036)
- crypted2.exe (PID: 2068)
- crypted2.exe (PID: 3160)
- crypted2.exe (PID: 1604)
- crypted2.exe (PID: 3504)
- crypted2.exe (PID: 2888)
- crypted2.exe (PID: 2940)
- crypted2.exe (PID: 1156)
- crypted2.exe (PID: 2704)
- crypted2.exe (PID: 2452)
- crypted2.exe (PID: 2300)
- crypted2.exe (PID: 2208)
- crypted2.exe (PID: 1264)
- crypted2.exe (PID: 3400)
- crypted2.exe (PID: 184)
- crypted2.exe (PID: 1796)
- crypted2.exe (PID: 1804)
- crypted2.exe (PID: 4052)
- crypted2.exe (PID: 3736)
- crypted2.exe (PID: 1660)
- crypted2.exe (PID: 3452)
- crypted2.exe (PID: 2432)
- crypted2.exe (PID: 2464)
- crypted2.exe (PID: 2696)
- crypted2.exe (PID: 2040)
- crypted2.exe (PID: 444)
- crypted2.exe (PID: 3196)
- crypted2.exe (PID: 2388)
- crypted2.exe (PID: 4060)
- crypted2.exe (PID: 1976)
- crypted2.exe (PID: 3340)
- crypted2.exe (PID: 2652)
- crypted2.exe (PID: 1464)
- crypted2.exe (PID: 3732)
- crypted2.exe (PID: 2500)
- crypted2.exe (PID: 3868)
- crypted2.exe (PID: 2544)
- crypted2.exe (PID: 3820)
- crypted2.exe (PID: 976)
- crypted2.exe (PID: 3908)
- crypted2.exe (PID: 3300)
- crypted2.exe (PID: 2924)
- crypted2.exe (PID: 3372)
- crypted2.exe (PID: 2984)
- crypted2.exe (PID: 3184)
- crypted2.exe (PID: 3996)
- crypted2.exe (PID: 4068)
- crypted2.exe (PID: 1588)
- crypted2.exe (PID: 3140)
- crypted2.exe (PID: 2180)
- crypted2.exe (PID: 2720)
- crypted2.exe (PID: 1580)
- crypted2.exe (PID: 3284)
- crypted2.exe (PID: 740)
- crypted2.exe (PID: 2088)
- crypted2.exe (PID: 3304)
- crypted2.exe (PID: 3808)
- crypted2.exe (PID: 3508)
- crypted2.exe (PID: 1160)
- crypted2.exe (PID: 2164)
- crypted2.exe (PID: 4120)
- crypted2.exe (PID: 4132)
- crypted2.exe (PID: 4144)
- crypted2.exe (PID: 4168)
- crypted2.exe (PID: 4156)
- crypted2.exe (PID: 4192)
- crypted2.exe (PID: 4200)
- crypted2.exe (PID: 4224)
- crypted2.exe (PID: 2484)
- crypted2.exe (PID: 3148)
- crypted2.exe (PID: 892)
- crypted2.exe (PID: 936)
- crypted2.exe (PID: 4108)
- crypted2.exe (PID: 4276)
- crypted2.exe (PID: 4352)
- crypted2.exe (PID: 4300)
- crypted2.exe (PID: 4316)
- crypted2.exe (PID: 4384)
- crypted2.exe (PID: 4336)
- crypted2.exe (PID: 4360)
- crypted2.exe (PID: 4372)
- crypted2.exe (PID: 4420)
- crypted2.exe (PID: 4396)
- crypted2.exe (PID: 4408)
- crypted2.exe (PID: 4212)
- crypted2.exe (PID: 4236)
- crypted2.exe (PID: 4248)
- crypted2.exe (PID: 4260)
- crypted2.exe (PID: 4284)
- crypted2.exe (PID: 4480)
- crypted2.exe (PID: 4492)
- crypted2.exe (PID: 4508)
- crypted2.exe (PID: 4604)
- crypted2.exe (PID: 4532)
- crypted2.exe (PID: 4520)
- crypted2.exe (PID: 4544)
- crypted2.exe (PID: 4556)
- crypted2.exe (PID: 4568)
- crypted2.exe (PID: 4580)
- crypted2.exe (PID: 4592)
- crypted2.exe (PID: 4628)
- crypted2.exe (PID: 4616)
- crypted2.exe (PID: 4432)
- crypted2.exe (PID: 4444)
- crypted2.exe (PID: 4460)
- crypted2.exe (PID: 4472)
- crypted2.exe (PID: 4700)
- crypted2.exe (PID: 4712)
- crypted2.exe (PID: 4744)
- crypted2.exe (PID: 4732)
- crypted2.exe (PID: 4756)
- crypted2.exe (PID: 4824)
- crypted2.exe (PID: 4772)
- crypted2.exe (PID: 4836)
- crypted2.exe (PID: 4812)
- crypted2.exe (PID: 4860)
- crypted2.exe (PID: 4852)
- crypted2.exe (PID: 4872)
- crypted2.exe (PID: 4640)
- crypted2.exe (PID: 4676)
- crypted2.exe (PID: 4664)
- crypted2.exe (PID: 4688)
- crypted2.exe (PID: 4800)
- crypted2.exe (PID: 4924)
- crypted2.exe (PID: 4944)
- crypted2.exe (PID: 4972)
- crypted2.exe (PID: 4932)
- crypted2.exe (PID: 4956)
- crypted2.exe (PID: 4980)
- crypted2.exe (PID: 4996)
- crypted2.exe (PID: 5004)
- crypted2.exe (PID: 5016)
- crypted2.exe (PID: 5028)
- crypted2.exe (PID: 5040)
- crypted2.exe (PID: 5076)
- crypted2.exe (PID: 5056)
- crypted2.exe (PID: 5064)
- crypted2.exe (PID: 4884)
- crypted2.exe (PID: 4896)
- crypted2.exe (PID: 4908)
- crypted2.exe (PID: 5136)
- crypted2.exe (PID: 5152)
- crypted2.exe (PID: 5164)
- crypted2.exe (PID: 5220)
- crypted2.exe (PID: 5256)
- crypted2.exe (PID: 5204)
- crypted2.exe (PID: 5244)
- crypted2.exe (PID: 5304)
- crypted2.exe (PID: 5284)
- crypted2.exe (PID: 5264)
- crypted2.exe (PID: 5316)
- crypted2.exe (PID: 5344)
- crypted2.exe (PID: 5328)
- crypted2.exe (PID: 5088)
- crypted2.exe (PID: 5100)
- crypted2.exe (PID: 5112)
- crypted2.exe (PID: 5124)
- crypted2.exe (PID: 5232)
- crypted2.exe (PID: 5396)
- crypted2.exe (PID: 5472)
- crypted2.exe (PID: 5424)
- crypted2.exe (PID: 5440)
- crypted2.exe (PID: 5508)
- crypted2.exe (PID: 5484)
- crypted2.exe (PID: 5532)
- crypted2.exe (PID: 5524)
- crypted2.exe (PID: 5544)
- crypted2.exe (PID: 5568)
- crypted2.exe (PID: 5556)
- crypted2.exe (PID: 5592)
- crypted2.exe (PID: 5580)
- crypted2.exe (PID: 5604)
- crypted2.exe (PID: 5356)
- crypted2.exe (PID: 5368)
- crypted2.exe (PID: 5384)
- crypted2.exe (PID: 5452)
- crypted2.exe (PID: 5500)
- crypted2.exe (PID: 5616)
- crypted2.exe (PID: 5640)
- crypted2.exe (PID: 5652)
- crypted2.exe (PID: 5676)
- crypted2.exe (PID: 5668)
- crypted2.exe (PID: 5688)
- crypted2.exe (PID: 5700)
- crypted2.exe (PID: 5712)
- crypted2.exe (PID: 5736)
- crypted2.exe (PID: 5744)
- crypted2.exe (PID: 5756)
- crypted2.exe (PID: 5772)
- crypted2.exe (PID: 5784)
- crypted2.exe (PID: 5792)
- crypted2.exe (PID: 5632)
- crypted2.exe (PID: 5856)
- crypted2.exe (PID: 5868)
- crypted2.exe (PID: 5904)
- crypted2.exe (PID: 5892)
- crypted2.exe (PID: 5940)
- crypted2.exe (PID: 5916)
- crypted2.exe (PID: 5928)
- crypted2.exe (PID: 5952)
- crypted2.exe (PID: 5968)
- crypted2.exe (PID: 5976)
- crypted2.exe (PID: 6000)
- crypted2.exe (PID: 5988)
- crypted2.exe (PID: 6024)
- crypted2.exe (PID: 6012)
- crypted2.exe (PID: 5804)
- crypted2.exe (PID: 5816)
- crypted2.exe (PID: 5840)
- crypted2.exe (PID: 5880)
- crypted2.exe (PID: 6072)
- crypted2.exe (PID: 6060)
- crypted2.exe (PID: 6084)
- crypted2.exe (PID: 6096)
- crypted2.exe (PID: 6108)
- crypted2.exe (PID: 6120)
- crypted2.exe (PID: 4220)
- crypted2.exe (PID: 6132)
- crypted2.exe (PID: 4104)
- crypted2.exe (PID: 4176)
- crypted2.exe (PID: 4140)
- crypted2.exe (PID: 4256)
- crypted2.exe (PID: 4296)
- crypted2.exe (PID: 6036)
- crypted2.exe (PID: 6048)
- crypted2.exe (PID: 4576)
- crypted2.exe (PID: 4528)
- crypted2.exe (PID: 4600)
- crypted2.exe (PID: 4780)
- crypted2.exe (PID: 4648)
- crypted2.exe (PID: 4720)
- crypted2.exe (PID: 4684)
- crypted2.exe (PID: 4792)
- crypted2.exe (PID: 4848)
- crypted2.exe (PID: 4940)
- crypted2.exe (PID: 4904)
- crypted2.exe (PID: 4992)
- crypted2.exe (PID: 4416)
- crypted2.exe (PID: 4344)
- crypted2.exe (PID: 4380)
- crypted2.exe (PID: 4452)
- crypted2.exe (PID: 4488)
- crypted2.exe (PID: 5096)
- crypted2.exe (PID: 5172)
- crypted2.exe (PID: 5132)
- crypted2.exe (PID: 5240)
- crypted2.exe (PID: 5404)
- crypted2.exe (PID: 5276)
- crypted2.exe (PID: 5324)
- crypted2.exe (PID: 5444)
- crypted2.exe (PID: 5496)
- crypted2.exe (PID: 5540)
- crypted2.exe (PID: 5576)
- crypted2.exe (PID: 5648)
- crypted2.exe (PID: 5612)
- crypted2.exe (PID: 5696)
- crypted2.exe (PID: 5036)
- crypted2.exe (PID: 5072)
- crypted2.exe (PID: 5376)
- crypted2.exe (PID: 5800)
- crypted2.exe (PID: 5900)
- crypted2.exe (PID: 5936)
- crypted2.exe (PID: 5996)
- crypted2.exe (PID: 6056)
- crypted2.exe (PID: 6020)
- crypted2.exe (PID: 4128)
- crypted2.exe (PID: 2192)
- crypted2.exe (PID: 6116)
- crypted2.exe (PID: 4244)
- crypted2.exe (PID: 4368)
- crypted2.exe (PID: 4504)
- crypted2.exe (PID: 4564)
- crypted2.exe (PID: 4708)
- crypted2.exe (PID: 5720)
- crypted2.exe (PID: 5768)
- crypted2.exe (PID: 5836)
- crypted2.exe (PID: 1356)
- crypted2.exe (PID: 4968)
- crypted2.exe (PID: 5160)
- crypted2.exe (PID: 5312)
- crypted2.exe (PID: 5520)
- crypted2.exe (PID: 5480)
- crypted2.exe (PID: 5628)
- crypted2.exe (PID: 5924)
- crypted2.exe (PID: 5764)
- crypted2.exe (PID: 3032)
- crypted2.exe (PID: 5252)
- crypted2.exe (PID: 6080)
- crypted2.exe (PID: 4920)
- crypted2.exe (PID: 4292)
- crypted2.exe (PID: 4468)
- crypted2.exe (PID: 5964)
- crypted2.exe (PID: 5024)
- crypted2.exe (PID: 6176)
- crypted2.exe (PID: 6200)
- crypted2.exe (PID: 6208)
- crypted2.exe (PID: 6232)
- crypted2.exe (PID: 6220)
- crypted2.exe (PID: 6244)
- crypted2.exe (PID: 6256)
- crypted2.exe (PID: 6268)
- crypted2.exe (PID: 6284)
- crypted2.exe (PID: 6320)
- crypted2.exe (PID: 6296)
- crypted2.exe (PID: 6308)
- crypted2.exe (PID: 6344)
- crypted2.exe (PID: 6356)
- crypted2.exe (PID: 5752)
- crypted2.exe (PID: 4208)
- crypted2.exe (PID: 5888)
- crypted2.exe (PID: 6336)
- crypted2.exe (PID: 6392)
- crypted2.exe (PID: 6416)
- crypted2.exe (PID: 6440)
- crypted2.exe (PID: 6428)
- crypted2.exe (PID: 6464)
- crypted2.exe (PID: 6452)
- crypted2.exe (PID: 6556)
- crypted2.exe (PID: 6500)
- crypted2.exe (PID: 6488)
- crypted2.exe (PID: 6540)
- crypted2.exe (PID: 6524)
- crypted2.exe (PID: 6368)
- crypted2.exe (PID: 6408)
- crypted2.exe (PID: 6476)
- crypted2.exe (PID: 6380)
- crypted2.exe (PID: 6512)
- crypted2.exe (PID: 6604)
- crypted2.exe (PID: 6752)
- crypted2.exe (PID: 6616)
- crypted2.exe (PID: 6652)
- crypted2.exe (PID: 6640)
- crypted2.exe (PID: 6672)
- crypted2.exe (PID: 6696)
- crypted2.exe (PID: 6712)
- crypted2.exe (PID: 6720)
- crypted2.exe (PID: 6740)
- crypted2.exe (PID: 6568)
- crypted2.exe (PID: 6584)
- crypted2.exe (PID: 6592)
- crypted2.exe (PID: 6628)
- crypted2.exe (PID: 6684)
- crypted2.exe (PID: 6812)
- crypted2.exe (PID: 6836)
- crypted2.exe (PID: 6848)
- crypted2.exe (PID: 6876)
- crypted2.exe (PID: 6896)
- crypted2.exe (PID: 6908)
- crypted2.exe (PID: 6924)
- crypted2.exe (PID: 6936)
- crypted2.exe (PID: 6968)
- crypted2.exe (PID: 6944)
- crypted2.exe (PID: 6776)
- crypted2.exe (PID: 6788)
- crypted2.exe (PID: 6800)
- crypted2.exe (PID: 6764)
- crypted2.exe (PID: 6824)
- crypted2.exe (PID: 6864)
- crypted2.exe (PID: 6888)
- crypted2.exe (PID: 7004)
- crypted2.exe (PID: 6992)
- crypted2.exe (PID: 7044)
- crypted2.exe (PID: 7028)
- crypted2.exe (PID: 7016)
- crypted2.exe (PID: 7132)
- crypted2.exe (PID: 7100)
- crypted2.exe (PID: 7116)
- crypted2.exe (PID: 7164)
- crypted2.exe (PID: 7140)
- crypted2.exe (PID: 7152)
- crypted2.exe (PID: 6956)
- crypted2.exe (PID: 6980)
- crypted2.exe (PID: 7056)
- crypted2.exe (PID: 7084)
- crypted2.exe (PID: 7228)
- crypted2.exe (PID: 7252)
- crypted2.exe (PID: 7264)
- crypted2.exe (PID: 7276)
- crypted2.exe (PID: 7308)
- crypted2.exe (PID: 7316)
- crypted2.exe (PID: 7360)
- crypted2.exe (PID: 7332)
- crypted2.exe (PID: 7340)
- crypted2.exe (PID: 7188)
- crypted2.exe (PID: 7176)
- crypted2.exe (PID: 7200)
- crypted2.exe (PID: 7216)
- crypted2.exe (PID: 7240)
- crypted2.exe (PID: 7292)
- crypted2.exe (PID: 7428)
- crypted2.exe (PID: 7416)
- crypted2.exe (PID: 7440)
- crypted2.exe (PID: 7456)
- crypted2.exe (PID: 7468)
- crypted2.exe (PID: 7480)
- crypted2.exe (PID: 7488)
- crypted2.exe (PID: 7500)
- crypted2.exe (PID: 7512)
- crypted2.exe (PID: 7368)
- crypted2.exe (PID: 7380)
- crypted2.exe (PID: 7392)
- crypted2.exe (PID: 7404)
- crypted2.exe (PID: 7528)
- crypted2.exe (PID: 7616)
- crypted2.exe (PID: 7644)
- crypted2.exe (PID: 7652)
- crypted2.exe (PID: 7676)
- crypted2.exe (PID: 7664)
- crypted2.exe (PID: 7688)
- crypted2.exe (PID: 7704)
- crypted2.exe (PID: 7712)
- crypted2.exe (PID: 7724)
- crypted2.exe (PID: 7736)
- crypted2.exe (PID: 7540)
- crypted2.exe (PID: 7552)
- crypted2.exe (PID: 7564)
- crypted2.exe (PID: 7576)
- crypted2.exe (PID: 7588)
- crypted2.exe (PID: 7600)
- crypted2.exe (PID: 7624)
- crypted2.exe (PID: 7784)
- crypted2.exe (PID: 7772)
- crypted2.exe (PID: 7800)
- crypted2.exe (PID: 7848)
- crypted2.exe (PID: 7808)
- crypted2.exe (PID: 7824)
- crypted2.exe (PID: 7832)
- crypted2.exe (PID: 7888)
- crypted2.exe (PID: 7864)
- crypted2.exe (PID: 7940)
- crypted2.exe (PID: 7896)
- crypted2.exe (PID: 7912)
- crypted2.exe (PID: 7924)
- crypted2.exe (PID: 7748)
- crypted2.exe (PID: 7760)
- crypted2.exe (PID: 8004)
- crypted2.exe (PID: 8020)
- crypted2.exe (PID: 8056)
- crypted2.exe (PID: 8028)
- crypted2.exe (PID: 8040)
- crypted2.exe (PID: 8072)
- crypted2.exe (PID: 8084)
- crypted2.exe (PID: 8092)
- crypted2.exe (PID: 8104)
- crypted2.exe (PID: 8116)
- crypted2.exe (PID: 8176)
- crypted2.exe (PID: 8140)
- crypted2.exe (PID: 8156)
- crypted2.exe (PID: 8132)
- crypted2.exe (PID: 8168)
- crypted2.exe (PID: 7968)
- crypted2.exe (PID: 7980)
- crypted2.exe (PID: 7992)
- crypted2.exe (PID: 6196)
- crypted2.exe (PID: 6240)
- crypted2.exe (PID: 6292)
- crypted2.exe (PID: 6328)
- crypted2.exe (PID: 6844)
- crypted2.exe (PID: 6388)
- crypted2.exe (PID: 6708)
- crypted2.exe (PID: 6424)
- crypted2.exe (PID: 6460)
- crypted2.exe (PID: 6636)
- crypted2.exe (PID: 6508)
- crypted2.exe (PID: 6600)
- crypted2.exe (PID: 6564)
- crypted2.exe (PID: 7000)
- crypted2.exe (PID: 6760)
- crypted2.exe (PID: 6784)
- crypted2.exe (PID: 6916)
- crypted2.exe (PID: 8188)
- crypted2.exe (PID: 6364)
- crypted2.exe (PID: 7052)
- crypted2.exe (PID: 7108)
- crypted2.exe (PID: 7040)
- crypted2.exe (PID: 7148)
- crypted2.exe (PID: 7068)
- crypted2.exe (PID: 7476)
- crypted2.exe (PID: 7448)
- crypted2.exe (PID: 7236)
- crypted2.exe (PID: 7300)
- crypted2.exe (PID: 7376)
- crypted2.exe (PID: 7328)
- crypted2.exe (PID: 7412)
- crypted2.exe (PID: 7520)
- crypted2.exe (PID: 6964)
- crypted2.exe (PID: 7196)
- crypted2.exe (PID: 7284)
- crypted2.exe (PID: 7612)
- crypted2.exe (PID: 7720)
- crypted2.exe (PID: 7964)
- crypted2.exe (PID: 7696)
- crypted2.exe (PID: 7756)
- crypted2.exe (PID: 7792)
- crypted2.exe (PID: 7820)
- crypted2.exe (PID: 8112)
- crypted2.exe (PID: 7860)
- crypted2.exe (PID: 7976)
- crypted2.exe (PID: 7920)
- crypted2.exe (PID: 8016)
- crypted2.exe (PID: 8052)
- crypted2.exe (PID: 8148)
- crypted2.exe (PID: 7560)
- crypted2.exe (PID: 7660)
- crypted2.exe (PID: 6552)
- crypted2.exe (PID: 6772)
- crypted2.exe (PID: 7092)
- crypted2.exe (PID: 7076)
- crypted2.exe (PID: 7324)
- crypted2.exe (PID: 3484)
- crypted2.exe (PID: 7684)
- crypted2.exe (PID: 7744)
- crypted2.exe (PID: 7908)
- crypted2.exe (PID: 7872)
- crypted2.exe (PID: 6404)
- crypted2.exe (PID: 6184)
- crypted2.exe (PID: 8064)
- crypted2.exe (PID: 5340)
- crypted2.exe (PID: 5292)
- crypted2.exe (PID: 7208)
- crypted2.exe (PID: 3956)
- crypted2.exe (PID: 7548)
- crypted2.exe (PID: 6884)
- crypted2.exe (PID: 7224)
- crypted2.exe (PID: 7844)
- crypted2.exe (PID: 6264)
- crypted2.exe (PID: 7816)
- crypted2.exe (PID: 8204)
- crypted2.exe (PID: 8216)
- crypted2.exe (PID: 8228)
- crypted2.exe (PID: 8252)
- crypted2.exe (PID: 7508)
- crypted2.exe (PID: 8080)
- crypted2.exe (PID: 5468)
- crypted2.exe (PID: 4832)
- crypted2.exe (PID: 8312)
- crypted2.exe (PID: 8324)
- crypted2.exe (PID: 8352)
- crypted2.exe (PID: 8336)
- crypted2.exe (PID: 8360)
- crypted2.exe (PID: 8372)
- crypted2.exe (PID: 8408)
- crypted2.exe (PID: 8384)
- crypted2.exe (PID: 8240)
- crypted2.exe (PID: 8264)
- crypted2.exe (PID: 8288)
- crypted2.exe (PID: 8276)
- crypted2.exe (PID: 8300)
- crypted2.exe (PID: 8396)
- crypted2.exe (PID: 8532)
- crypted2.exe (PID: 8504)
- crypted2.exe (PID: 8516)
- crypted2.exe (PID: 8560)
- crypted2.exe (PID: 8576)
- crypted2.exe (PID: 8432)
- crypted2.exe (PID: 8448)
- crypted2.exe (PID: 8456)
- crypted2.exe (PID: 8468)
- crypted2.exe (PID: 8480)
- crypted2.exe (PID: 8492)
- crypted2.exe (PID: 8540)
- crypted2.exe (PID: 8592)
- crypted2.exe (PID: 8628)
- ucloud.exe (PID: 2548)
- crypted2.exe (PID: 5828)
- crypted2.exe (PID: 8420)
XWORM has been detected (YARA)
- svchost.exe (PID: 3696)
Starts NET.EXE for service management
- net.exe (PID: 3304)
- stail.tmp (PID: 2028)
Adds process to the Windows Defender exclusion list
- svchost.exe (PID: 3696)
AMADEY has been detected (YARA)
- Gxtuum.exe (PID: 900)
QUASAR has been detected (YARA)
- Client.exe (PID: 2384)
PHORPIEX has been detected (YARA)
- sysvplervcs.exe (PID: 2548)
VIDAR has been detected (YARA)
- noll.exe (PID: 3708)
REDLINE has been detected (YARA)
- penis.exe (PID: 3588)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 1964)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 1964)
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
- stail.exe (PID: 3128)
- avidenta.exe (PID: 1144)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 3608)
- stail.tmp (PID: 2028)
- m.exe (PID: 2164)
- zwyw.exe (PID: 2468)
- stories.exe (PID: 2408)
- cmd.exe (PID: 924)
- rpuycbukt.exe (PID: 1648)
- stories.tmp (PID: 828)
- ardara.exe (PID: 2532)
- rpuycbukt.exe (PID: 3620)
- peinf.exe (PID: 1852)
- A.I_1003H.exe (PID: 4024)
- A.I.exe (PID: 2056)
- powershell.exe (PID: 1796)
- rundll32.exe (PID: 2652)
- npp.exe (PID: 3168)
- tt.exe (PID: 3484)
- 314358577.exe (PID: 1712)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 1964)
- rsreport.exe (PID: 3720)
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
- svchost.exe (PID: 3696)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 1964)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 1964)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 1964)
- Gxtuum.exe (PID: 900)
- svchost.exe (PID: 1060)
Starts itself from another location
- Offnewhere.exe (PID: 2408)
- m.exe (PID: 2164)
- ardara.exe (PID: 2532)
- tt.exe (PID: 3484)
- 726714815.exe (PID: 6532)
- 314358577.exe (PID: 1712)
Reads the Internet Settings
- Offnewhere.exe (PID: 2408)
- 4363463463464363463463463.exe (PID: 1964)
- rsreport.exe (PID: 3720)
- svchost.exe (PID: 3696)
- Gxtuum.exe (PID: 900)
- powershell.exe (PID: 2784)
- powershell.exe (PID: 764)
Starts a Microsoft application from unusual location
- svchost.exe (PID: 3696)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 1964)
- Gxtuum.exe (PID: 900)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 1964)
- svchost.exe (PID: 3696)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 1964)
- Gxtuum.exe (PID: 900)
Contacting a server suspected of hosting an CnC
- Gxtuum.exe (PID: 900)
Script adds exclusion path to Windows Defender
- svchost.exe (PID: 3696)
- cmd.exe (PID: 2832)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 764)
Script adds exclusion process to Windows Defender
- svchost.exe (PID: 3696)
Starts POWERSHELL.EXE for commands execution
- svchost.exe (PID: 3696)
- cmd.exe (PID: 2832)
- hhnjqu9y.exe (PID: 2256)
- ucloud.exe (PID: 2548)
Checks for external IP
- svchost.exe (PID: 1060)
- svchost.exe (PID: 3696)
The process executes via Task Scheduler
- svchost.exe (PID: 3148)
- svchost.exe (PID: 3564)
- ctfmon.exe (PID: 2192)
- sipnotify.exe (PID: 2224)
- svchost.exe (PID: 3684)
- svchost.exe (PID: 2480)
Process drops legitimate windows executable
- stail.tmp (PID: 2028)
- peinf.exe (PID: 1852)
- A.I.exe (PID: 2056)
The process drops C-runtime libraries
- stail.tmp (PID: 2028)
Malware-specific behavior (creating "System.dll" in Temp)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 3608)
Starts CMD.EXE for commands execution
- sysvplervcs.exe (PID: 2548)
- DeliciousPart.exe (PID: 3612)
- cmd.exe (PID: 924)
Manipulates environment variables
- powershell.exe (PID: 2052)
Starts SC.EXE for service management
- cmd.exe (PID: 3292)
Executing commands from a ".bat" file
- DeliciousPart.exe (PID: 3612)
Get information on the list of running processes
- cmd.exe (PID: 924)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 924)
Application launched itself
- cmd.exe (PID: 924)
- crypted2.exe (PID: 2904)
- WerFault.exe (PID: 2396)
There is functionality for enable RDP (YARA)
- Gxtuum.exe (PID: 900)
There is functionality for taking screenshot (YARA)
- TMS_C062.exe (PID: 2324)
- POS_C161.exe (PID: 996)
- %E8%99%9A%E6%8B%9F%E6%9C%BA%E6%8E%92%E5%88%97.exe (PID: 4040)
Drops a system driver (possible attempt to evade defenses)
- rpuycbukt.exe (PID: 3620)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 1920)
Executes as Windows Service
- VSSVC.exe (PID: 2964)
- ScreenConnect.ClientService.exe (PID: 7024)
INFO
Disables trace logs
- 4363463463464363463463463.exe (PID: 1964)
- svchost.exe (PID: 3696)
Reads the computer name
- 4363463463464363463463463.exe (PID: 1964)
- rsreport.exe (PID: 3720)
- svchost.exe (PID: 3696)
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 1964)
Reads Environment values
- 4363463463464363463463463.exe (PID: 1964)
- svchost.exe (PID: 3696)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 1964)
- rsreport.exe (PID: 3720)
- svchost.exe (PID: 3696)
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
Checks supported languages
- 4363463463464363463463463.exe (PID: 1964)
- rsreport.exe (PID: 3720)
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
- svchost.exe (PID: 3696)
Checks proxy server information
- rsreport.exe (PID: 3720)
- Gxtuum.exe (PID: 900)
The process uses the downloaded file
- 4363463463464363463463463.exe (PID: 1964)
- Offnewhere.exe (PID: 2408)
- svchost.exe (PID: 3696)
- powershell.exe (PID: 764)
- powershell.exe (PID: 2784)
Create files in a temporary directory
- Offnewhere.exe (PID: 2408)
- Gxtuum.exe (PID: 900)
Sends debugging messages
- 4363463463464363463463463.exe (PID: 1964)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 764)
- powershell.exe (PID: 2784)
Creates files or folders in the user directory
- Gxtuum.exe (PID: 900)
Manual execution by a user
- wmpnscfg.exe (PID: 3716)
- runonce.exe (PID: 2344)
- IMEKLMG.EXE (PID: 2492)
- IMEKLMG.EXE (PID: 2500)
- sysmablsvr.exe (PID: 2520)
- svchost.exe (PID: 2532)
- ucloud.exe (PID: 2548)
- %E8%99%9A%E6%8B%9F%E6%9C%BA%E6%8E%92%E5%88%97.exe (PID: 2588)
- wmpnscfg.exe (PID: 3284)
- wmpnscfg.exe (PID: 3308)
Themida protector has been detected
- hhnjqu9y.exe (PID: 2256)
Creates a new folder
- cmd.exe (PID: 1164)
UPX packer has been detected
- %E8%99%9A%E6%8B%9F%E6%9C%BA%E6%8E%92%E5%88%97.exe (PID: 4040)
Mpress packer has been detected
- zwyw.exe (PID: 2468)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3356)
- msiexec.exe (PID: 1512)
Application launched itself
- msiexec.exe (PID: 1512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(3696) svchost.exe
C2HITROL-60505.portmap.host:60505
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameProtection
MutexUKX3WvWDYch66MMo
Amadey
(PID) Process(900) Gxtuum.exe
C2185.215.113.36
URLhttp://185.215.113.36/Dem7kTu/index.php
Version5.04
Options
Drop directory23a0892ef8
Drop nameGxtuum.exe
Strings (125)/Plugins/
Startup
cmd /C RMDIR /s/q
"
Content-Type: application/octet-stream
?scr=1
ar:
:::
st=s
kernel32.dll
Main
VideoID
&&
S-%lu-
2025
pc:
exe
#
GetNativeSystemInfo
lv:
------
SOFTWARE\Microsoft\Windows NT\CurrentVersion
2022
/Dem7kTu/index.php
DefaultSettings.YResolution
shutdown -s -t 0
clip.dll
Content-Disposition: form-data; name="data"; filename="
2019
cmd
wb
%-lu
/k
random
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Content-Type: multipart/form-data; boundary=----
id:
\
Norton
-unicode-
os:
0000043f
sd:
Programs
23a0892ef8
cred.dll|clip.dll|
5.04
rb
Kaspersky Lab
0123456789
00000422
e1
ProgramData\
https://
" && timeout 1 && del
-executionpolicy remotesigned -File "
av:
"taskkill /f /im "
\0000
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
vs:
AVAST Software
00000423
Keyboard Layout\Preload
d1
WinDefender
<c>
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
POST
Content-Type: application/x-www-form-urlencoded
185.215.113.36
ESET
=
e2
dm:
%USERPROFILE%
cred.dll
Powershell.exe
Doctor Web
<d>
SYSTEM\ControlSet001\Services\BasicDisplay\Video
rundll32.exe
zip
2016
r=
bi:
Rem
e3
ProductName
AVG
+++
dll
Avira
og:
-%lu
Panda Security
.jpg
" && ren
shell32.dll
abcdefghijklmnopqrstuvwxyz0123456789-_
360TotalSecurity
Comodo
&& Exit"
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
\App
GET
/quiet
&unit=
msi
|
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Gxtuum.exe
Bitdefender
CurrentBuild
--
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
http://
DefaultSettings.XResolution
------
ps1
ComputerName
00000419
"
un:
Sophos
Quasar
(PID) Process(2384) Client.exe
Version1.4.1
C2 (3)89.213.56.109:80
89.213.56.109:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex98b3deca-7447-4862-905a-28f904856d31
StartupQuasar Client Startup
TagKurban
LogDirLogs
SignatureLHHeAKMkL1ly9ilruSSCS3865uZwawxeAhgbVNJjF0JkMBOPYS1VpXyoWmjGDq9Jk/EFz/e8Y/UkfyFAhT5CxMjMOd/GT7HhQ4enR5PH45XEp5W1VO4w0MQlnUQYggeJdDBTs3bBIZW5Xf+btj+m9rXklEog99WBE095L/sW1s1+QUFeGU6lX33oBSDVvpJYdDGW+PH697Lxro400hD6M/VpFObuaVJ1goJC5eIeyNOV1C8kTfSmdBQa89a9SMzUUMQiMoHiRJgB8wlygbbBw0tcoDEvcVRliGoCBFujxyEQ...
CertificateMIIE9DCCAtygAwIBAgIQAM7Qe6Z0O6xyJcPNalQ8XzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTAwOTA4MzMwNVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAsqQvz/yrropTMvKpZzMaXSErOLUrL5WwHscVQAruqpID0md0kxpR+43VVekY1oQ0NUN5t29y...
Vidar
(PID) Process(3708) noll.exe
C2https://t.me/ae5ed
URLhttps://steamcommunity.com/profiles/76561199780418869
RC40123456789ABCDEF
RedLine
(PID) Process(3588) penis.exe
C2 (1)185.215.113.67:33160
Botnet091024
Options
ErrorMessage
Keys
XorCoercibly
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
819
Monitored processes
699
Malicious processes
20
Suspicious processes
594
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 444 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 740 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 764 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\Files\svchost.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 764 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 828 | "C:\Users\admin\AppData\Local\Temp\is-CTGT1.tmp\stories.tmp" /SL5="$102C8,5263804,721408,C:\Users\admin\Desktop\Files\stories.exe" | C:\Users\admin\AppData\Local\Temp\is-CTGT1.tmp\stories.tmp | stories.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 | |||||||||||||||
| 892 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\23a0892ef8\Gxtuum.exe" | C:\Users\admin\AppData\Local\Temp\23a0892ef8\Gxtuum.exe | Offnewhere.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
Amadey(PID) Process(900) Gxtuum.exe C2185.215.113.36 URLhttp://185.215.113.36/Dem7kTu/index.php Version5.04 Options Drop directory23a0892ef8 Drop nameGxtuum.exe Strings (125)/Plugins/ Startup cmd /C RMDIR /s/q "
Content-Type: application/octet-stream ?scr=1 ar: ::: st=s kernel32.dll Main VideoID && S-%lu- 2025 pc: exe # GetNativeSystemInfo lv: ------ SOFTWARE\Microsoft\Windows NT\CurrentVersion 2022 /Dem7kTu/index.php DefaultSettings.YResolution shutdown -s -t 0 clip.dll Content-Disposition: form-data; name="data"; filename=" 2019 cmd wb %-lu /k random SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ Content-Type: multipart/form-data; boundary=---- id: \ Norton -unicode- os: 0000043f sd: Programs 23a0892ef8 cred.dll|clip.dll| 5.04 rb Kaspersky Lab 0123456789 00000422 e1 ProgramData\ https:// " && timeout 1 && del -executionpolicy remotesigned -File " av: "taskkill /f /im " \0000 SOFTWARE\Microsoft\Windows\CurrentVersion\Run vs: AVAST Software 00000423 Keyboard Layout\Preload d1 WinDefender <c> SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders POST Content-Type: application/x-www-form-urlencoded 185.215.113.36 ESET = e2 dm: %USERPROFILE% cred.dll Powershell.exe Doctor Web <d> SYSTEM\ControlSet001\Services\BasicDisplay\Video rundll32.exe zip 2016 r= bi: Rem e3 ProductName AVG +++ dll Avira og: -%lu Panda Security .jpg " && ren shell32.dll abcdefghijklmnopqrstuvwxyz0123456789-_ 360TotalSecurity Comodo && Exit" SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce \App GET /quiet &unit= msi | SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders Gxtuum.exe Bitdefender CurrentBuild -- rundll32 SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName http:// DefaultSettings.XResolution ------ ps1 ComputerName 00000419 " un: Sophos | |||||||||||||||
| 924 | "C:\Windows\System32\cmd.exe" /c move Tall Tall.bat & Tall.bat | C:\Windows\System32\cmd.exe | DeliciousPart.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 924 | "C:\Users\admin\Desktop\Files\crypted2.exe" | C:\Users\admin\Desktop\Files\crypted2.exe | — | crypted2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 | |||||||||||||||
Total events
14 737
Read events
14 545
Write events
173
Delete events
19
Modification events
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1964) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
127
Suspicious files
268
Text files
1 045
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1964 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svchost.exe | — | |
MD5:— | SHA256:— | |||
| 2408 | Offnewhere.exe | C:\Windows\Tasks\Gxtuum.job | binary | |
MD5:9459A3D73039096862E7AE66C6DA5716 | SHA256:126FA23663D6F8E20384185D349D056C3D636EA819908FBF7B5D8632DF567B49 | |||
| 3696 | svchost.exe | C:\Users\admin\AppData\Roaming\svchost.exe | — | |
MD5:— | SHA256:— | |||
| 1964 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Offnewhere.exe | executable | |
MD5:C07E06E76DE584BCDDD59073A4161DBB | SHA256:CF67A50598EE170E0D8596F4E22F79CF70E1283B013C3E33E36094E1905BA8D9 | |||
| 1964 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\donut.exe | executable | |
MD5:2A516C444620354C81FD32EF1B498D1B | SHA256:EE68D7DEB7CEFDFCA66C078D6036D7AA3AA7AFCC62B282999034B4A1FAED890D | |||
| 764 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4vr5lnvq.g4e.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 764 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ze2vpfb1.ssj.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1964 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\si.exe | executable | |
MD5:52FC73BF68BA53D9A2E6DC1E38FDD155 | SHA256:651C40EAC524FF5749CFD5D80705D6E2B3D52831E4539B7D2642267B913D0701 | |||
| 1964 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\rsreport.exe | executable | |
MD5:CE786255B793D4EBAC5A747EEB5A533C | SHA256:0B45FA2A1937577F8F7EC7A3CE5B551B24F8667A2ACC931EF8A9AB2431E4FDE2 | |||
| 2784 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ruywvbhp.lty.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
208
DNS requests
35
Threats
193
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1964 | 4363463463464363463463463.exe | GET | 200 | 1.180.210.62:80 | http://download.suxiazai.com/for_down/2013/new/dlls/rse/rsreport.exe | unknown | — | — | malicious |
3720 | rsreport.exe | GET | 404 | 211.103.159.80:80 | http://center.rising.com.cn/urg.asp?v=rsebase&t=rse&a=0 | unknown | — | — | unknown |
1964 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.36:80 | http://185.215.113.36/Offnewhere.exe | unknown | — | — | malicious |
3696 | svchost.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
900 | Gxtuum.exe | POST | 200 | 185.215.113.36:80 | http://185.215.113.36/Dem7kTu/index.php | unknown | — | — | malicious |
900 | Gxtuum.exe | POST | 200 | 185.215.113.36:80 | http://185.215.113.36/Dem7kTu/index.php | unknown | — | — | malicious |
1964 | 4363463463464363463463463.exe | GET | 200 | 150.158.13.117:22222 | http://150.158.13.117:22222/02.08.2022.exe | unknown | — | — | unknown |
900 | Gxtuum.exe | GET | 200 | 185.215.113.36:80 | http://185.215.113.36/Javvvum.exe | unknown | — | — | malicious |
— | — | GET | 200 | 60.191.208.187:820 | http://123.ywxww.net:820/svchost.exe | unknown | — | — | unknown |
1964 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.217:80 | http://185.215.113.217/inc/DeliciousPart.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1964 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1964 | 4363463463464363463463463.exe | 1.180.210.62:80 | download.suxiazai.com | Chinanet | CN | malicious |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1964 | 4363463463464363463463463.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
3720 | rsreport.exe | 211.103.159.80:80 | center.rising.com.cn | Beijing Dian-Xin-Tong Network Technologies Co., Ltd. | CN | unknown |
1964 | 4363463463464363463463463.exe | 185.202.113.6:443 | — | BitCommand LLC | AM | unknown |
1964 | 4363463463464363463463463.exe | 185.215.113.36:80 | — | 1337team Limited | SC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
download.suxiazai.com |
| malicious |
raw.githubusercontent.com |
| shared |
center.rising.com.cn |
| unknown |
ip-api.com |
| shared |
home.sevjs17sr.top |
| unknown |
github.com |
| shared |
objects.githubusercontent.com |
| shared |
HITROL-60505.portmap.host |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1964 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1964 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1964 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1964 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1964 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1964 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
900 | Gxtuum.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
1060 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1060 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
40 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|