| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/bac49d23-3d89-49d9-9f72-d3f557d84a69 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 16, 2025, 09:46:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Starts SC.EXE for service management
- cmd.exe (PID: 1996)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2408)
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
- Client-built.exe (PID: 3880)
- Sentil.exe (PID: 2956)
- spectrum.exe (PID: 2340)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 892)
- cmd.exe (PID: 1500)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
Changes Windows Defender settings
- cmd.exe (PID: 1500)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 3880)
- svchost.exe (PID: 892)
- runtime.exe (PID: 948)
- Sentil.exe (PID: 2956)
- Client1.exe (PID: 2884)
- cmd.exe (PID: 3200)
- msgde.exe (PID: 3792)
- Client.exe (PID: 3968)
- Java Updater.exe (PID: 1996)
- spectrum.exe (PID: 2340)
ASYNCRAT has been detected (MUTEX)
- Solara_Protect.exe (PID: 1504)
- Windows.exe (PID: 2600)
- AsyncClient.exe (PID: 120)
- aaa%20(3).exe (PID: 3884)
HAVOC has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
QUASAR has been detected (YARA)
- Client1.exe (PID: 2884)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1080)
- gold.rim.exe (PID: 2892)
Connects to the CnC server
- svchost.exe (PID: 1080)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
- 4363463463464363463463463.exe (PID: 2408)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
- msgde.exe (PID: 3792)
REMCOS has been detected
- benpolatalemdar.exe (PID: 3340)
REMCOS mutex has been found
- benpolatalemdar.exe (PID: 3340)
Bypass execution policy to execute commands
- powershell.exe (PID: 3852)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 2968)
- powershell.exe (PID: 2732)
- powershell.exe (PID: 3520)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2224)
- powershell.exe (PID: 2688)
- powershell.exe (PID: 4068)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
- boleto.exe (PID: 2320)
Changes powershell execution policy (Bypass)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2408)
- 4363463463464363463463463.exe (PID: 2408)
- dayum.exe (PID: 3292)
Adds process to the Windows Defender exclusion list
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
NJRAT mutex has been found
- 856.exe (PID: 3888)
- svchost.exe (PID: 2668)
NJRAT has been found (auto)
- 856.exe (PID: 3888)
Uses Task Scheduler to run other applications
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
Changes the autorun value in the registry
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
Create files in the Startup directory
- stub.exe (PID: 4008)
XWORM has been detected (YARA)
- XClient.exe (PID: 4016)
- boleto.exe (PID: 2320)
ASYNCRAT has been detected (YARA)
- Windows.exe (PID: 2600)
REMCOS has been detected (YARA)
- benpolatalemdar.exe (PID: 3340)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2408)
- gold.rim.exe (PID: 2892)
- installer_ver19.02.exe (PID: 3580)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2408)
- random.exe (PID: 2024)
- Solara_Protect.exe (PID: 1504)
- stub.exe (PID: 4008)
- 856.exe (PID: 3888)
- boleto.exe (PID: 2320)
- ZubovLekciya.exe (PID: 2508)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2408)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2408)
- random.exe (PID: 2024)
- powershell.exe (PID: 1400)
- svchost.exe (PID: 892)
- Solara_Protect.exe (PID: 1504)
- stub.exe (PID: 4008)
- powershell.exe (PID: 3852)
- powershell.exe (PID: 2364)
- boleto.exe (PID: 2320)
- powershell.exe (PID: 2968)
- 856.exe (PID: 3888)
- powershell.exe (PID: 3520)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 2732)
- ZubovLekciya.exe (PID: 2508)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
- mshta.exe (PID: 2480)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2408)
- runtime.exe (PID: 948)
- Windows.exe (PID: 2600)
- Client1.exe (PID: 2884)
- benpolatalemdar.exe (PID: 3340)
- System32.exe (PID: 3756)
- Client.exe (PID: 3968)
- Java Updater.exe (PID: 1996)
- systempreter.exe (PID: 1952)
- powershell.exe (PID: 3236)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
Creates file in the systems drive root
- ntvdm.exe (PID: 2056)
- 856.exe (PID: 3888)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2408)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2408)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2408)
- random.exe (PID: 2024)
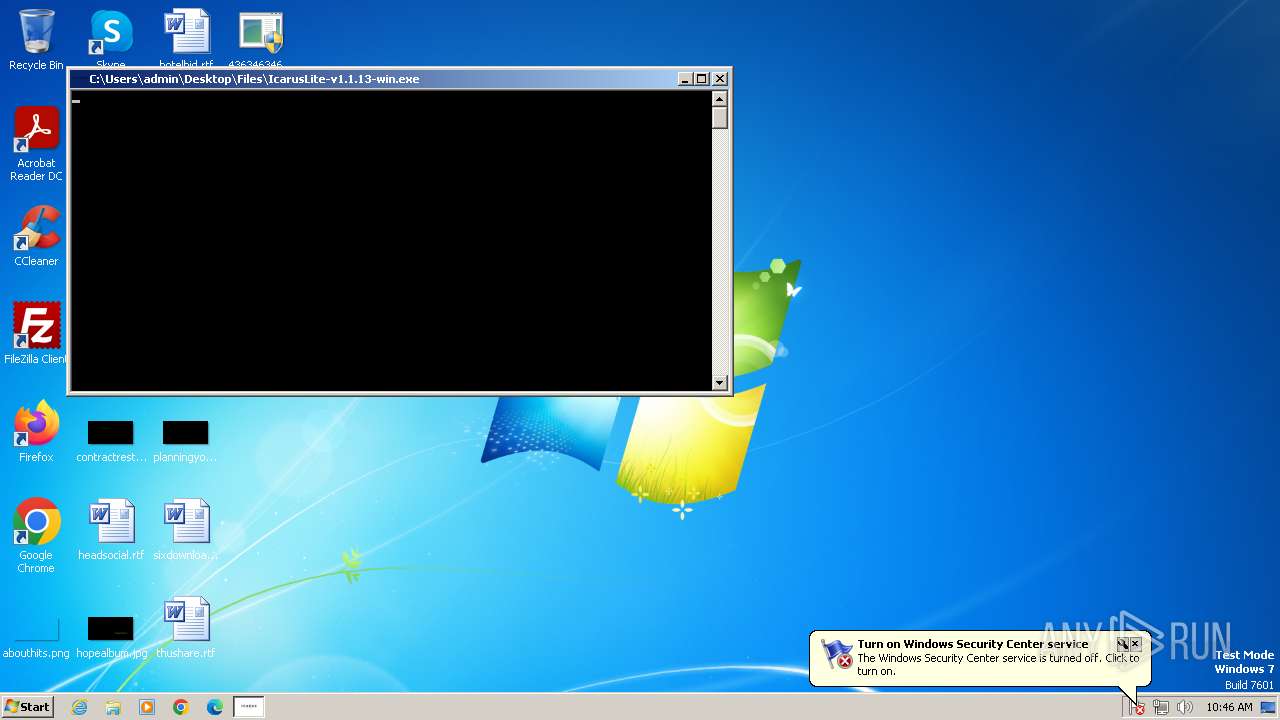
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- Client-built.exe (PID: 3880)
- svchost.exe (PID: 892)
- Sentil.exe (PID: 2956)
- Solara_Protect.exe (PID: 1504)
- msgde.exe (PID: 3792)
- spectrum.exe (PID: 2340)
- 856.exe (PID: 3888)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- ZubovLekciya.exe (PID: 2508)
- w1u.exe (PID: 3388)
- dayum.exe (PID: 3292)
- Portcrt.exe (PID: 2008)
- namu832.exe (PID: 556)
The process creates files with name similar to system file names
- random.exe (PID: 2024)
- 4363463463464363463463463.exe (PID: 2408)
- svchost.exe (PID: 892)
- 856.exe (PID: 3888)
Starts CMD.EXE for commands execution
- random.exe (PID: 2024)
- cmd.exe (PID: 2016)
- cmd.exe (PID: 1996)
- svchost.exe (PID: 892)
- Solara_Protect.exe (PID: 1504)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
- cmd.exe (PID: 1120)
- wscript.exe (PID: 2360)
Executing commands from a ".bat" file
- random.exe (PID: 2024)
- cmd.exe (PID: 2016)
- Solara_Protect.exe (PID: 1504)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
- wscript.exe (PID: 2360)
Application launched itself
- cmd.exe (PID: 2016)
- cmd.exe (PID: 1996)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- installer_ver19.02.exe (PID: 3404)
- gold.rim.exe (PID: 4080)
- cmd.exe (PID: 1120)
Starts application with an unusual extension
- cmd.exe (PID: 1996)
Drops 7-zip archiver for unpacking
- random.exe (PID: 2024)
Get information on the list of running processes
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2732)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1996)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2408)
Stops a currently running service
- sc.exe (PID: 3212)
- sc.exe (PID: 3380)
- sc.exe (PID: 3236)
- sc.exe (PID: 3032)
- sc.exe (PID: 2856)
- sc.exe (PID: 3408)
- sc.exe (PID: 2064)
- sc.exe (PID: 2808)
- sc.exe (PID: 3784)
- sc.exe (PID: 1124)
- sc.exe (PID: 4068)
- sc.exe (PID: 2892)
- sc.exe (PID: 3968)
- sc.exe (PID: 4004)
- sc.exe (PID: 756)
- sc.exe (PID: 1488)
Starts SC.EXE for service management
- cmd.exe (PID: 1996)
Windows service management via SC.EXE
- sc.exe (PID: 3144)
- sc.exe (PID: 3216)
- sc.exe (PID: 3420)
- sc.exe (PID: 3268)
- sc.exe (PID: 3412)
- sc.exe (PID: 2976)
- sc.exe (PID: 3284)
- sc.exe (PID: 3352)
- sc.exe (PID: 3364)
- sc.exe (PID: 3756)
- sc.exe (PID: 3780)
- sc.exe (PID: 3340)
- sc.exe (PID: 3792)
- sc.exe (PID: 3680)
- sc.exe (PID: 3904)
- sc.exe (PID: 4012)
- sc.exe (PID: 1168)
- sc.exe (PID: 2876)
- sc.exe (PID: 912)
- sc.exe (PID: 1072)
- sc.exe (PID: 2756)
- sc.exe (PID: 2628)
- sc.exe (PID: 3540)
- sc.exe (PID: 4008)
- sc.exe (PID: 4048)
- sc.exe (PID: 1632)
- sc.exe (PID: 1576)
- sc.exe (PID: 1060)
- sc.exe (PID: 1812)
- sc.exe (PID: 1772)
- sc.exe (PID: 2196)
- sc.exe (PID: 3840)
- sc.exe (PID: 1596)
- sc.exe (PID: 576)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1996)
- cmd.exe (PID: 1120)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 2428)
- schtasks.exe (PID: 656)
- schtasks.exe (PID: 2380)
- schtasks.exe (PID: 1564)
- schtasks.exe (PID: 2704)
Process drops legitimate windows executable
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- 4363463463464363463463463.exe (PID: 2408)
The process drops C-runtime libraries
- IcarusLite-v1.1.13-win.exe (PID: 3492)
Process drops python dynamic module
- IcarusLite-v1.1.13-win.exe (PID: 3492)
Loads Python modules
- IcarusLite-v1.1.13-win.exe (PID: 2392)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1500)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1500)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- cmd.exe (PID: 1120)
- LunaInjector.exe (PID: 2412)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1400)
- powershell.exe (PID: 3852)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 2968)
- powershell.exe (PID: 3520)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2476)
- powershell.exe (PID: 2732)
Starts itself from another location
- Client-built.exe (PID: 3880)
- Sentil.exe (PID: 2956)
- msgde.exe (PID: 3792)
- spectrum.exe (PID: 2340)
- 856.exe (PID: 3888)
- dayum.exe (PID: 3292)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3112)
The executable file from the user directory is run by the CMD process
- Windows.exe (PID: 2600)
There is functionality for taking screenshot (YARA)
- Client1.exe (PID: 2884)
- benpolatalemdar.exe (PID: 3340)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 1080)
- gold.rim.exe (PID: 2892)
Script adds exclusion process to Windows Defender
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
Checks for external IP
- svchost.exe (PID: 1080)
- boleto.exe (PID: 2320)
- LunaInjector.exe (PID: 2412)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- 856.exe (PID: 3888)
Uses NETSH.EXE to add a firewall rule or allowed programs
- 856.exe (PID: 3888)
Runs shell command (SCRIPT)
- mshta.exe (PID: 2480)
Downloads file from URI via Powershell
- powershell.exe (PID: 3236)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1120)
Found IP address in command line
- powershell.exe (PID: 3236)
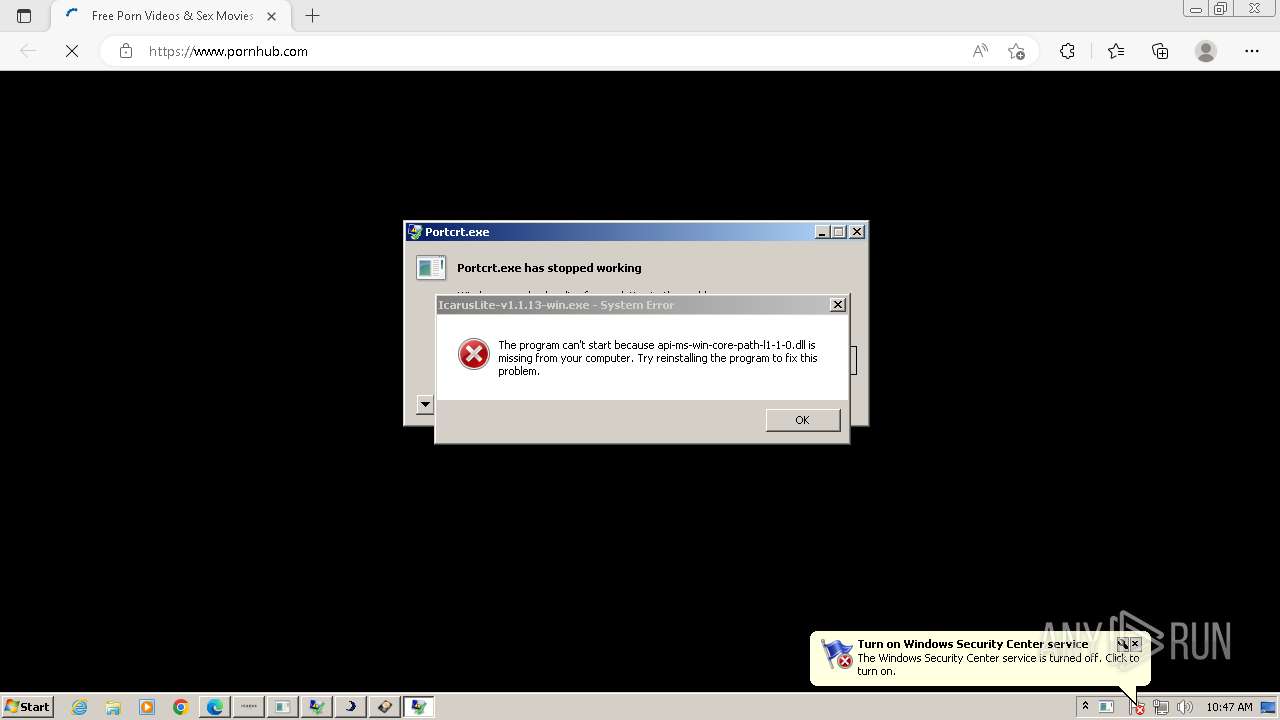
Executes application which crashes
- CZXZDDS22.exe (PID: 1060)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2408)
- chcp.com (PID: 2912)
- random.exe (PID: 2024)
- mode.com (PID: 2516)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- IcarusLite-v1.1.13-win.exe (PID: 2392)
- Client-built.exe (PID: 3880)
- svchost.exe (PID: 892)
- Solara_Protect.exe (PID: 1504)
- runtime.exe (PID: 948)
- Sentil.exe (PID: 2956)
- Client1.exe (PID: 2884)
- Windows.exe (PID: 2600)
- uac_bypass.exe (PID: 3388)
- AsyncClient.exe (PID: 120)
- installer_ver19.02.exe (PID: 3404)
- installer_ver19.02.exe (PID: 3580)
- file.exe (PID: 3128)
- System32.exe (PID: 3756)
- gold.rim.exe (PID: 2892)
- gold.rim.exe (PID: 4080)
- msgde.exe (PID: 3792)
- XClient.exe (PID: 4016)
- stub.exe (PID: 4008)
- benpolatalemdar.exe (PID: 3340)
- Client.exe (PID: 3968)
- CZXZDDS22.exe (PID: 1060)
- boleto.exe (PID: 2320)
- spectrum.exe (PID: 2340)
- 856.exe (PID: 3888)
- aaa%20(3).exe (PID: 3884)
- systempreter.exe (PID: 1952)
- Java Updater.exe (PID: 1996)
- svchost.exe (PID: 2668)
- ZubovLekciya.exe (PID: 2508)
- av_downloader1.1.exe (PID: 2848)
- Neverlose%20Loader.exe (PID: 2544)
- av_downloader1.1.exe (PID: 1028)
Disables trace logs
- 4363463463464363463463463.exe (PID: 2408)
- svchost.exe (PID: 892)
- boleto.exe (PID: 2320)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2408)
- gold.rim.exe (PID: 2892)
- installer_ver19.02.exe (PID: 3580)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2408)
- random.exe (PID: 2024)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- Client-built.exe (PID: 3880)
- svchost.exe (PID: 892)
- Solara_Protect.exe (PID: 1504)
- runtime.exe (PID: 948)
- Sentil.exe (PID: 2956)
- Windows.exe (PID: 2600)
- file.exe (PID: 3128)
- installer_ver19.02.exe (PID: 3580)
- System32.exe (PID: 3756)
- AsyncClient.exe (PID: 120)
- gold.rim.exe (PID: 2892)
- gold.rim.exe (PID: 4080)
- benpolatalemdar.exe (PID: 3340)
- XClient.exe (PID: 4016)
- stub.exe (PID: 4008)
- msgde.exe (PID: 3792)
- Client.exe (PID: 3968)
- CZXZDDS22.exe (PID: 1060)
- boleto.exe (PID: 2320)
- spectrum.exe (PID: 2340)
- aaa%20(3).exe (PID: 3884)
- systempreter.exe (PID: 1952)
- 856.exe (PID: 3888)
- Java Updater.exe (PID: 1996)
- svchost.exe (PID: 2668)
- Client1.exe (PID: 2884)
- ZubovLekciya.exe (PID: 2508)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
- Neverlose%20Loader.exe (PID: 2544)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2408)
- Client-built.exe (PID: 3880)
- svchost.exe (PID: 892)
- runtime.exe (PID: 948)
- Sentil.exe (PID: 2956)
- Client1.exe (PID: 2884)
- benpolatalemdar.exe (PID: 3340)
- msgde.exe (PID: 3792)
- Client.exe (PID: 3968)
- spectrum.exe (PID: 2340)
- Java Updater.exe (PID: 1996)
- boleto.exe (PID: 2320)
- Neverlose%20Loader.exe (PID: 2544)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2408)
- svchost.exe (PID: 892)
- Client-built.exe (PID: 3880)
- Sentil.exe (PID: 2956)
- runtime.exe (PID: 948)
- Solara_Protect.exe (PID: 1504)
- Client1.exe (PID: 2884)
- Windows.exe (PID: 2600)
- file.exe (PID: 3128)
- System32.exe (PID: 3756)
- gold.rim.exe (PID: 2892)
- AsyncClient.exe (PID: 120)
- msgde.exe (PID: 3792)
- Client.exe (PID: 3968)
- installer_ver19.02.exe (PID: 3580)
- XClient.exe (PID: 4016)
- CZXZDDS22.exe (PID: 1060)
- boleto.exe (PID: 2320)
- spectrum.exe (PID: 2340)
- stub.exe (PID: 4008)
- 856.exe (PID: 3888)
- Java Updater.exe (PID: 1996)
- aaa%20(3).exe (PID: 3884)
- systempreter.exe (PID: 1952)
- svchost.exe (PID: 2668)
- Neverlose%20Loader.exe (PID: 2544)
The sample compiled with english language support
- random.exe (PID: 2024)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- 4363463463464363463463463.exe (PID: 2408)
Changes the display of characters in the console
- cmd.exe (PID: 1996)
Create files in a temporary directory
- random.exe (PID: 2024)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- svchost.exe (PID: 892)
- Solara_Protect.exe (PID: 1504)
- 856.exe (PID: 3888)
- svchost.exe (PID: 2668)
- av_downloader1.1.exe (PID: 2848)
- av_downloader1.1.exe (PID: 1028)
Checks operating system version
- cmd.exe (PID: 1996)
Starts MODE.COM to configure console settings
- mode.com (PID: 2516)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1400)
- powershell.exe (PID: 3852)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 2968)
- powershell.exe (PID: 3520)
- powershell.exe (PID: 3368)
- powershell.exe (PID: 2732)
- powershell.exe (PID: 2476)
Creates files or folders in the user directory
- Sentil.exe (PID: 2956)
- 856.exe (PID: 3888)
- spectrum.exe (PID: 2340)
- stub.exe (PID: 4008)
- boleto.exe (PID: 2320)
PyInstaller has been detected (YARA)
- IcarusLite-v1.1.13-win.exe (PID: 3492)
- IcarusLite-v1.1.13-win.exe (PID: 2392)
Reads product name
- benpolatalemdar.exe (PID: 3340)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 2408)
Creates files in the program directory
- stub.exe (PID: 4008)
Drops encrypted VBS script (Microsoft Script Encoder)
- ZubovLekciya.exe (PID: 2508)
Reads Internet Explorer settings
- mshta.exe (PID: 2480)
Application launched itself
- msedge.exe (PID: 3072)
- msedge.exe (PID: 656)
Manual execution by a user
- msedge.exe (PID: 656)
The sample compiled with korean language support
- 4363463463464363463463463.exe (PID: 2408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(2884) Client1.exe
Version1.4.1
C2 (2)73.62.14.5:4782
Sub_DirSubDir
Install_NameClient1.exe
Mutex3aaa11be-d135-4877-a61e-c409c29a7a60
StartupStartup
TagOffice04
LogDirLogs
SignatureEdBsB69NrhYROGjMirEw1pe15mwZjJy+fpGVF2aEbnAFOtUvB+inXlq8CBJsHyw2rIpTOfp4iJoePBYs9NdmFCd3gos2x+OqODgudinjtlJ3MQljnn0DPtxxorYuDf5VUKr0n15ASslFNr8Z6jDUIHZBaCbxs4uO8NaqMeStXJzf+YByrEcyZU6gOjyIIGfrpqBLqq1isNVIZONqJkRwLltRhrSgtDWEaDv4HiaDfFr2uEXgYvWN1iOqsoCHi9ioLMItlaTygAnKjrljjlADQAyWj/m8/7eKUkbRes7c3Axb...
CertificateMIIE9DCCAtygAwIBAgIQANfZS7y4agM8ac9WWr3FiTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDYxMTE4MjE0MFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAivzXGPouAW3xLRhzxtOI9wrlH+Nk0QndGLi3B5yS0nGPq3CY6D/70xUT+I042LxX3VBF1fiU...
AsyncRat
(PID) Process(2600) Windows.exe
C2 (1)anyone-blogging.gl.at.ply.gg
Ports (1)22284
Version| CRACKED BY https://t.me/xworm_v2
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%Temp%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz...
Server_SignatureUIeKsq8FTvB20ZCQ0bPYnM9E03AtqOZ8dUfHU0hr3TmGGhwfdIryp62gPj79UN3BI7VZ6KLYcmyTjASy+OtLscjdtHVrt+CTZhTnIu2IsOyAR4wiacg6EcJYXdLoYx09eu2KuJfYDaOLgocti+cMu29r7+5xQFqpaxit5r1wyE0T9Dm7hqFdWRJtofJdgRejwhj+5y9wSuHv3qn3QnwA1pscd+8aLcq4NdakgxwAa4RlNQtDxsSXDkjmOcL6dZHFVHudbWWfBwuCpr07h2DNE1HMmZqHC7MQPlSeEnl0LCKA...
Keys
AES2674d00a7bd03523741e9f183917d7f5238967a0a29311ccb30f2d3db7ac3f54
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
XWorm
(PID) Process(4016) XClient.exe
C2127.0.0.1:8080
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameHSN
MutexaVbGJnLt4HRONX59
(PID) Process(2320) boleto.exe
C2camp.zapto.org:7771
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameUSB.exe
MutexLik1yXLTNv5MjKg0
Remcos
(PID) Process(3340) benpolatalemdar.exe
C2 (1)tr3.localto.net:40505
BotnetHost
Options
Connect_interval5
Install_flagFalse
Install_HKCU\RunTrue
Setup_path%APPDATA%
Copy_fileremcos.exe
Startup_valueremcos
Hide_fileFalse
Mutex_nameremcos_inmfeqsiajtnbkp
Keylog_flag0
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreens
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_diraudio
Connect_delay0
Copy_dirremcos
Keylog_dirremcos
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
304
Monitored processes
227
Malicious processes
33
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\Files\AsyncClient.exe" | C:\Users\admin\Desktop\Files\AsyncClient.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 320 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1292 --field-trial-handle=1324,i,8608188639203629833,10328220979127980845,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 328 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 372 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 556 | "C:\Users\admin\Desktop\Files\namu832.exe" | C:\Users\admin\Desktop\Files\namu832.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: ESTsoft Corp. Integrity Level: HIGH Description: ALZip Self Extractor Version: 14, 12, 2, 0 Modules
| |||||||||||||||
| 576 | sc start VMTools | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | "schtasks" /create /tn "msgde" /sc ONLOGON /tr "C:\Windows\system32\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | msgde.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | schtasks /Delete /TN "Microsoft\Windows\AppID\SmartScreenSpecific" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 656 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --enable-features=msMicrosoftRootStoreUsed --flag-switches-end --do-not-de-elevate https://www.pornhub.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 704 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
48 435
Read events
47 708
Write events
710
Delete events
17
Modification events
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2408) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
80
Suspicious files
74
Text files
50
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\02.08.2022.exe | binary | |
MD5:D71413201612714215C98F0213FCFE3D | SHA256:AC1682C973BD144F884EF170058A68FDC3597FD94EC420A7785AD5A5084FCDEA | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\V9IoxD9.bat | text | |
MD5:350D172630B12F10564C78EEF37E3F95 | SHA256:73BC1BD40DCB68AC6DBF25FFB5E0B708F43FD4CA8A17D08647EEB89641B37062 | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\Work\7z.exe | executable | |
MD5:426CCB645E50A3143811CFA0E42E2BA6 | SHA256:CF878BFBD9ED93DC551AC038AFF8A8BBA4C935DDF8D48E62122BDDFDB3E08567 | |||
| 2408 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\random.exe | executable | |
MD5:842A29AD745E2C28221AEBB44392AC62 | SHA256:AD4E201282EC072E43B317071DA6146935303A0DD3D426506B7983DEB4AE8645 | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\Work\DKTolz.zip | compressed | |
MD5:6B617C0196FE449E27C84532EC2C38E7 | SHA256:E3528C57765074D5D73021F747B26EDEFA15227D0F1A3B80A6CDEF21322C99CA | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\Work\cecho.exe | executable | |
MD5:E783BC59D0ED6CFBD8891F94AE23D1B3 | SHA256:5C1211559DDA10592CFEDD57681F18F4A702410816D36EDA95AEE6C74E3C6A47 | |||
| 2056 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs4050.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2056 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs4070.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\Work\nircmd.exe | executable | |
MD5:4A9DA765FD91E80DECFD2C9FE221E842 | SHA256:2E81E048AB419FDC6E5F4336A951BD282ED6B740048DC38D7673678EE3490CDA | |||
| 2024 | random.exe | C:\Users\admin\AppData\Local\Temp\Work\NSudoLG.exe | executable | |
MD5:423129DDB24FB923F35B2DD5787B13DD | SHA256:5094AD359D8CF6DC5324598605C35F68519CC5AF9C7ED5427E02A6B28121E4C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
1 654
DNS requests
64
Threats
75
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2408 | 4363463463464363463463463.exe | GET | 200 | 47.120.13.85:8889 | http://47.120.13.85:8889/02.08.2022.exe | unknown | — | — | unknown |
2408 | 4363463463464363463463463.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/off/random.exe | unknown | — | — | unknown |
2408 | 4363463463464363463463463.exe | GET | — | 47.113.74.51:80 | http://zlonline.oss-cn-shenzhen.aliyuncs.com/web/img/231DD3BD495A42B6A479FB7F210BA69B.exe | unknown | — | — | unknown |
2408 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/cosmicdevv/Icarus-Lite/releases/download/v1.1.13/IcarusLite-v1.1.13-win.exe | unknown | — | — | whitelisted |
892 | svchost.exe | GET | 200 | 142.250.186.132:80 | http://www.google.com/ | unknown | — | — | whitelisted |
2408 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/yusuf216/sshport/raw/refs/heads/main/benpolatalemdar.exe | unknown | — | — | whitelisted |
2408 | 4363463463464363463463463.exe | GET | 200 | 143.198.186.79:8000 | http://143.198.186.79:8000/client.exe | unknown | — | — | unknown |
2408 | 4363463463464363463463463.exe | GET | 200 | 158.101.35.62:9000 | http://158.101.35.62:9000/xblkpfZ8Y4.exe | unknown | — | — | unknown |
2408 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/XerusSploit/Spectrum/raw/refs/heads/main/spectrum.exe | unknown | — | — | whitelisted |
2408 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/Babskai/vir-s/raw/refs/heads/main/aaa%20(3).exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2408 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2408 | 4363463463464363463463463.exe | 47.120.13.85:8889 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2408 | 4363463463464363463463463.exe | 185.156.72.121:80 | — | Tov Vaiz Partner | RU | unknown |
2408 | 4363463463464363463463463.exe | 47.113.74.51:80 | zlonline.oss-cn-shenzhen.aliyuncs.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2408 | 4363463463464363463463463.exe | 140.82.121.3:80 | github.com | GITHUB | US | whitelisted |
2408 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
zlonline.oss-cn-shenzhen.aliyuncs.com |
| unknown |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
media.githubusercontent.com |
| unknown |
www.google.com |
| whitelisted |
anyone-blogging.gl.at.ply.gg |
| malicious |
a17rrr1.oss-cn-hongkong.aliyuncs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2408 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2408 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2408 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 34 |
2408 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2408 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1080 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2408 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2408 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
CZXZDDS22.exe | Error - |