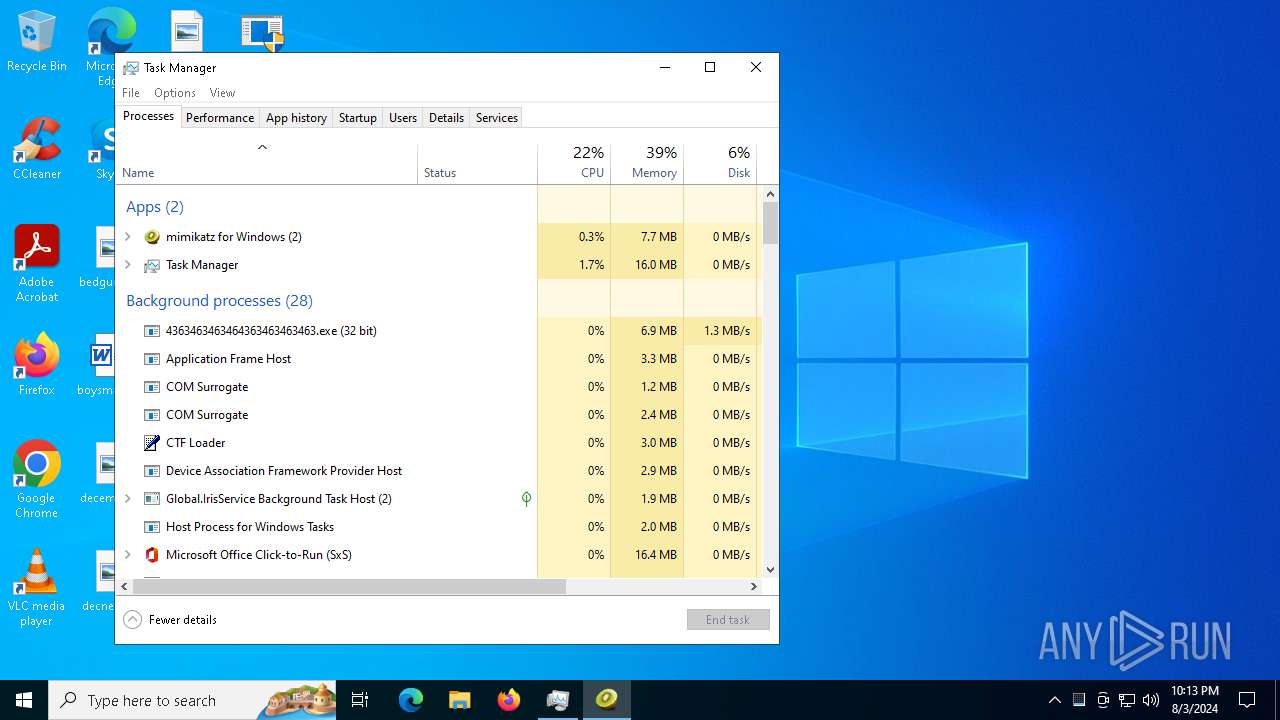
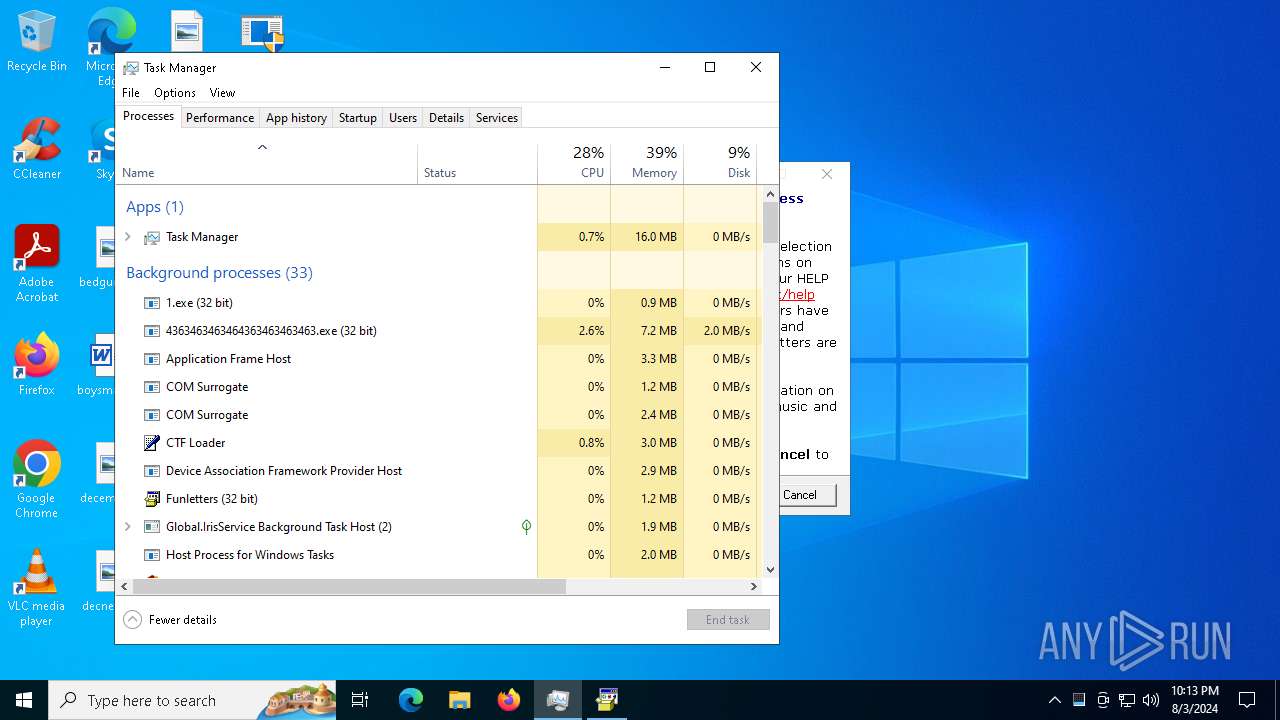
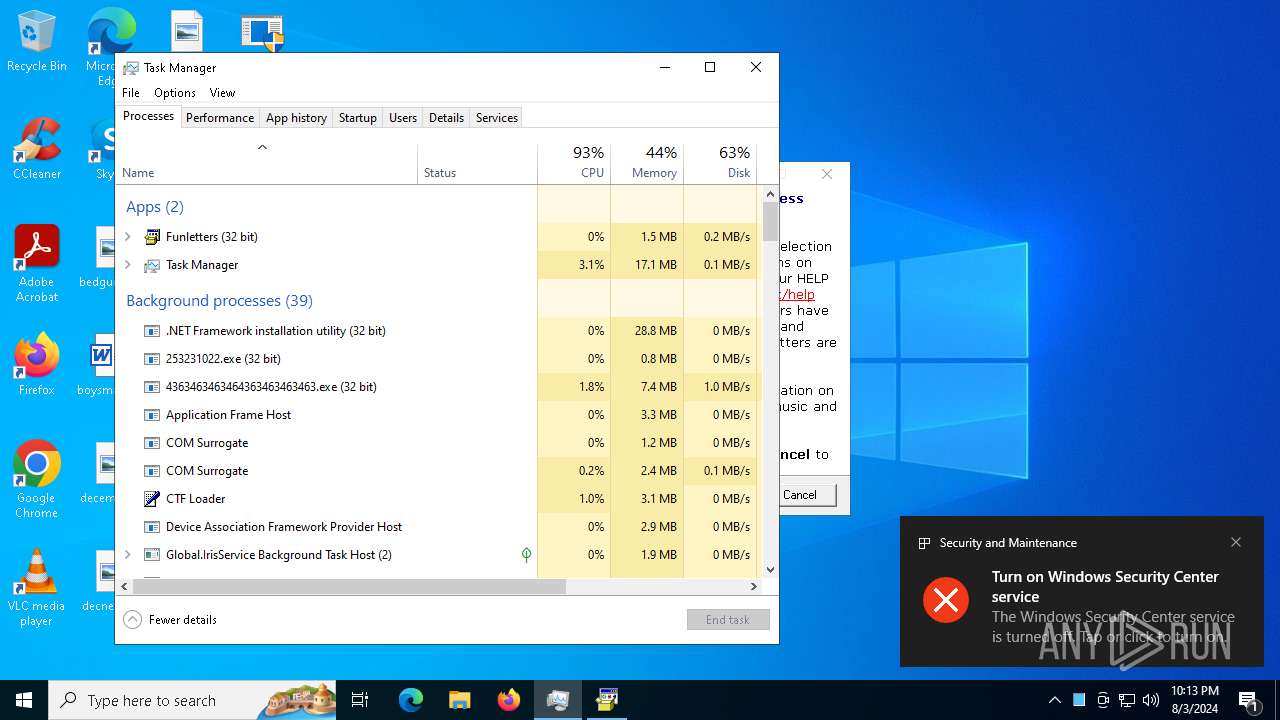
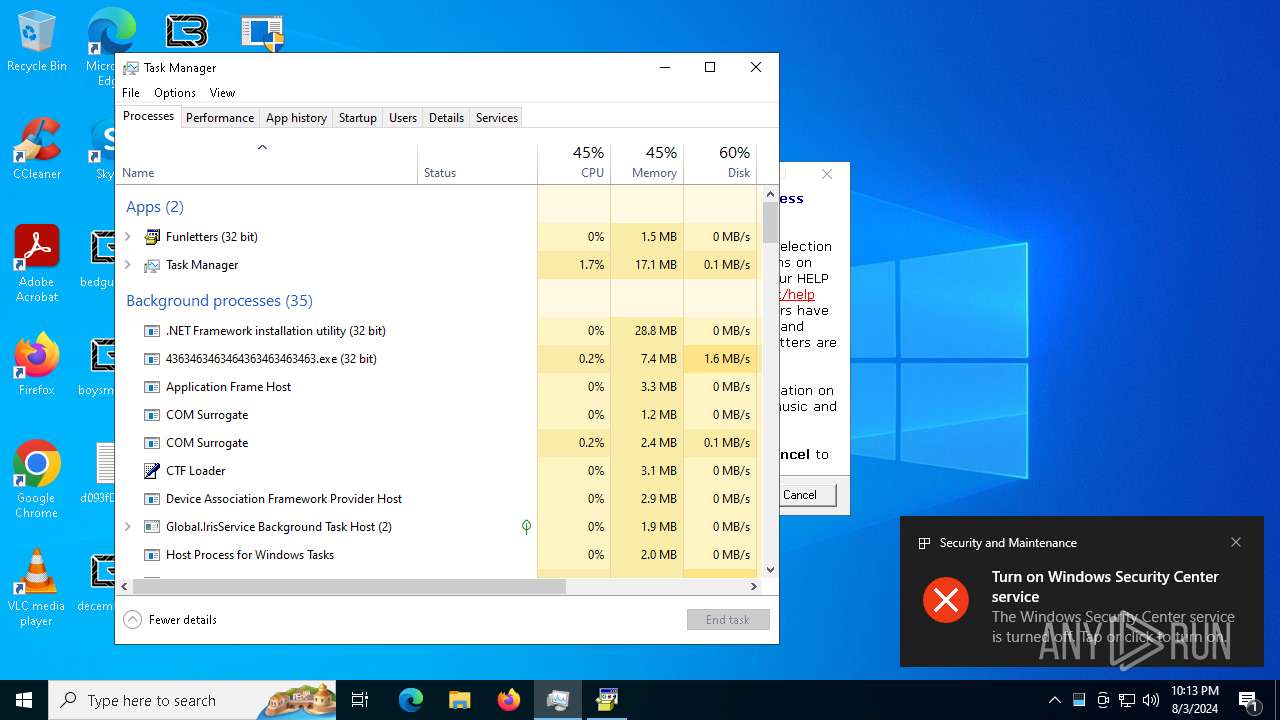
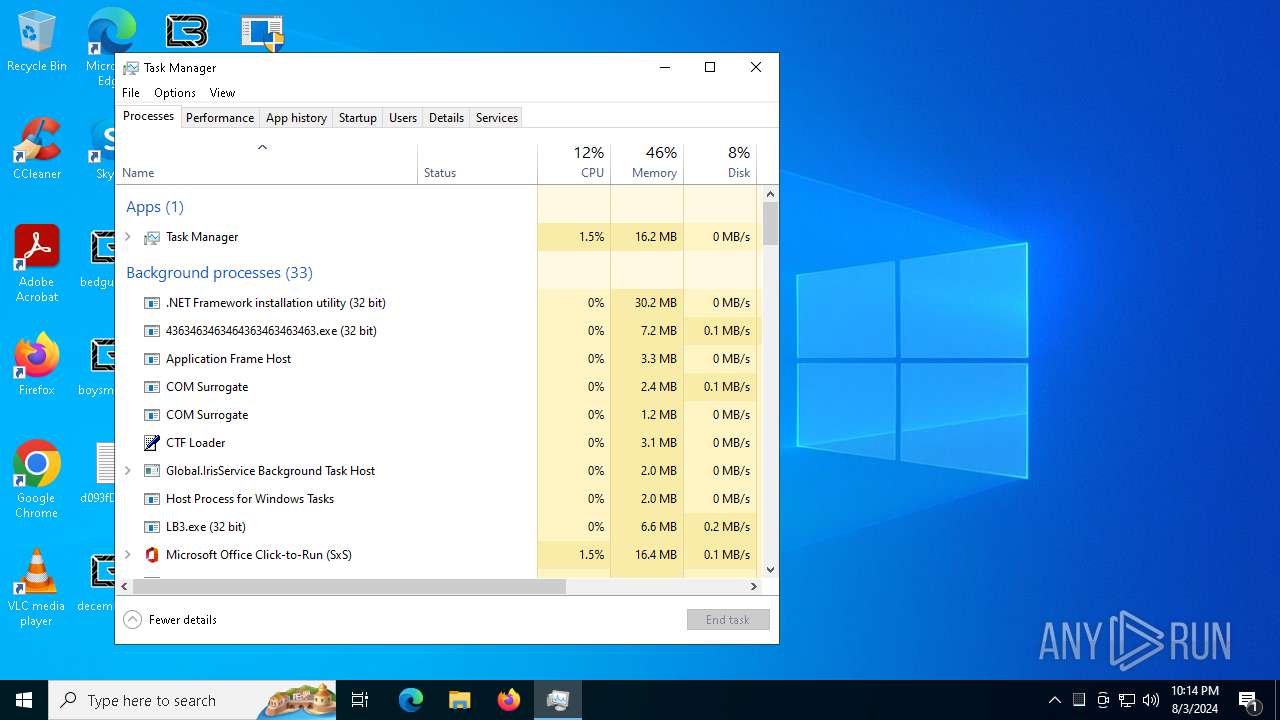
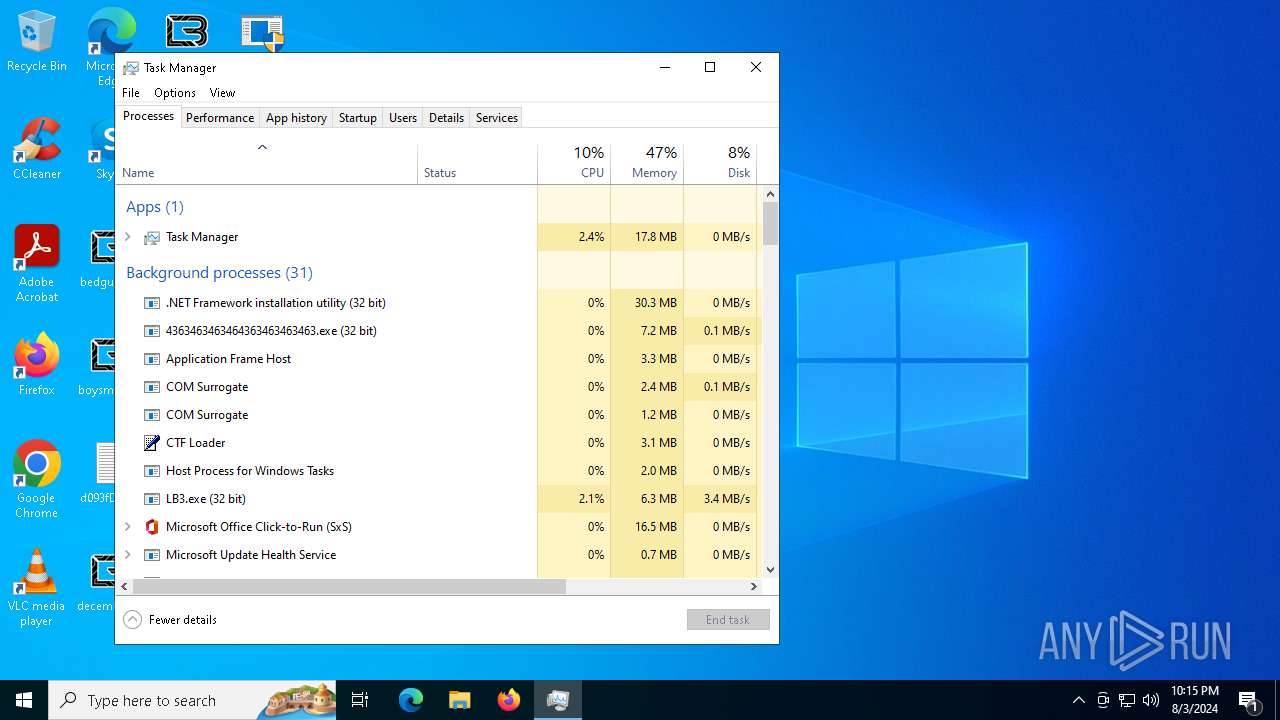
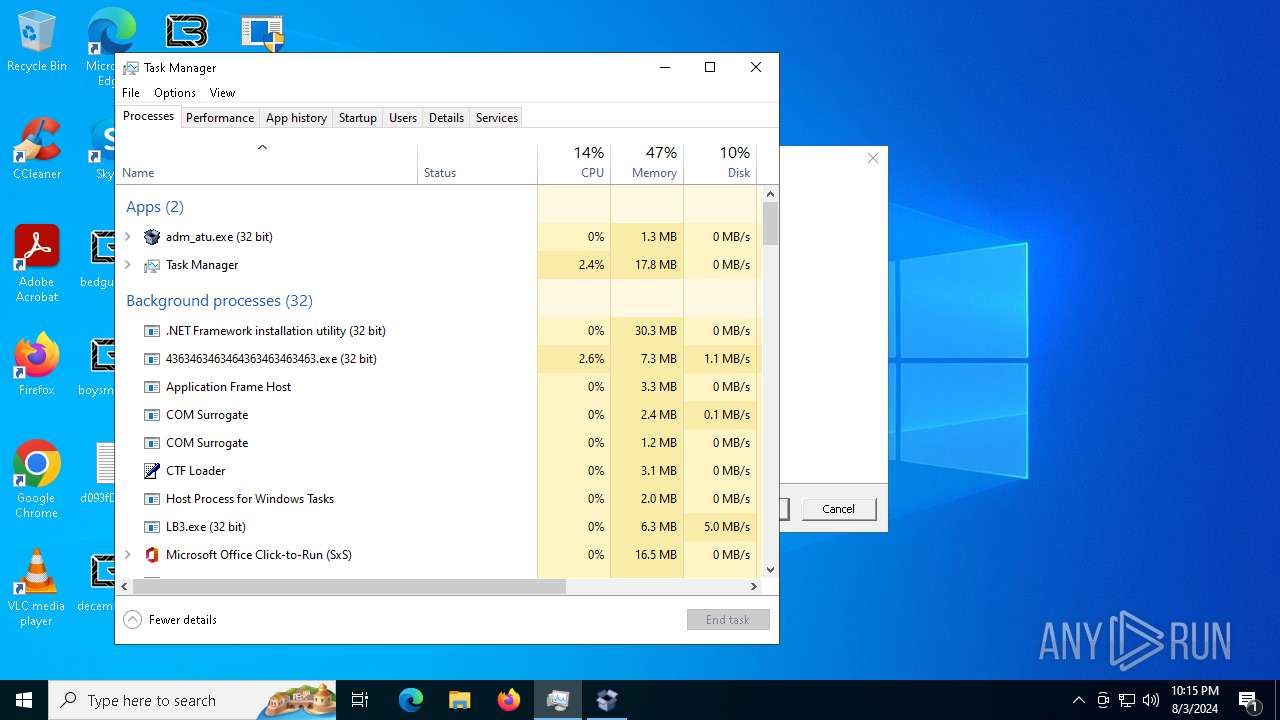
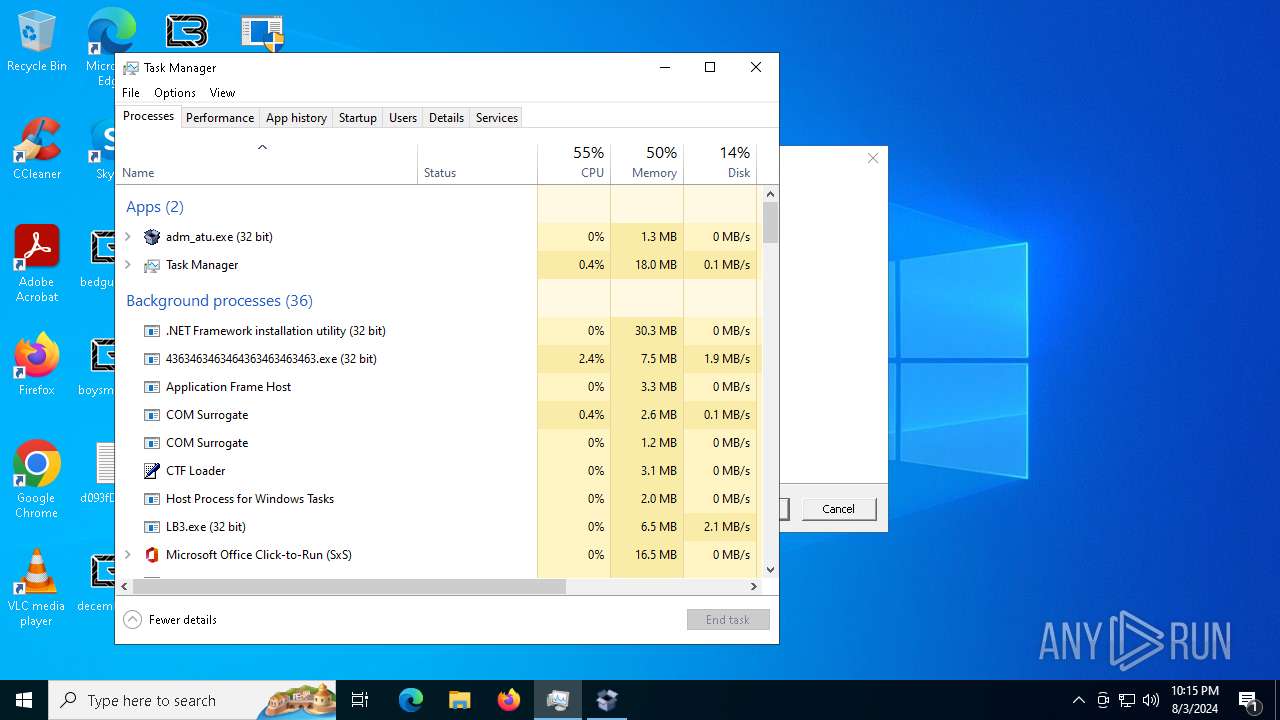
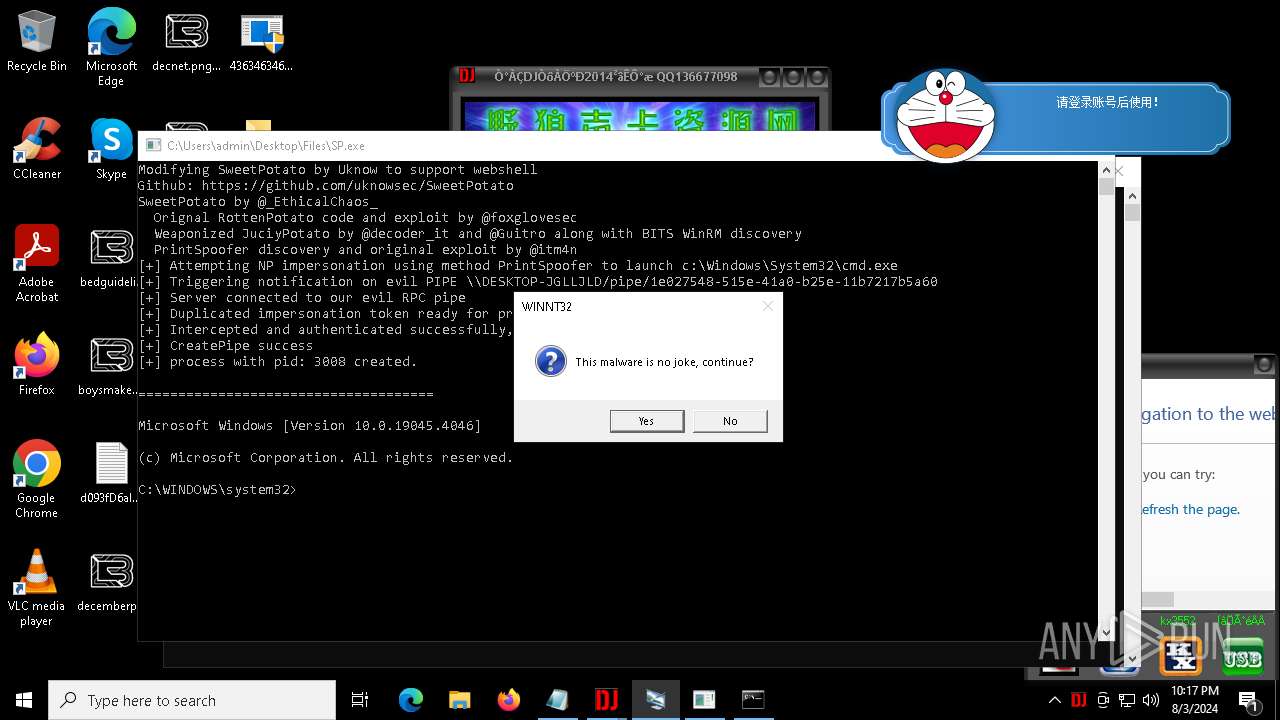
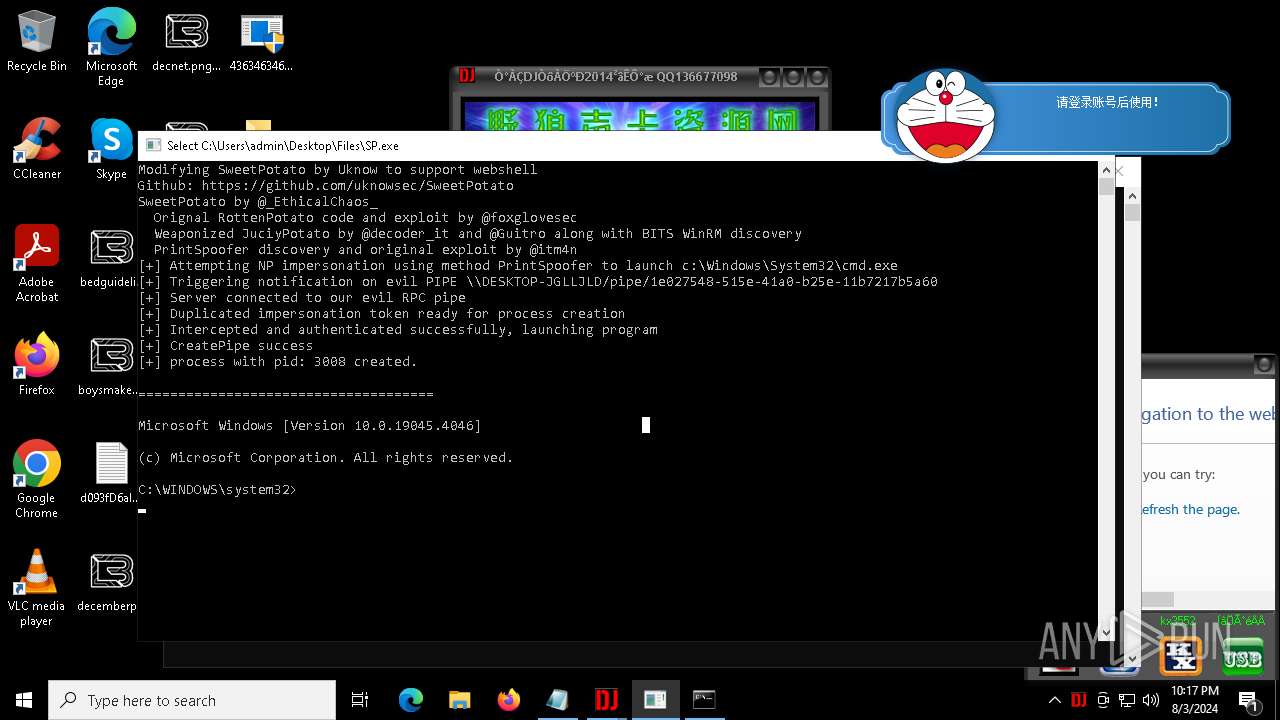
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/babd9424-419b-4d37-8d6f-99298293f8bd |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 03, 2024, 22:13:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 6380)
- m.exe (PID: 6552)
- pi.exe (PID: 1116)
- mountain-pasture.exe (PID: 6204)
- 1.exe (PID: 3164)
- LB3.exe (PID: 6184)
- nxmr.exe (PID: 6948)
- pered.exe (PID: 7764)
- 171824798.exe (PID: 7816)
- wupgrdsv.exe (PID: 7712)
- 1646416317.exe (PID: 4260)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- 1826814013.exe (PID: 5916)
- sysmysldrv.exe (PID: 1184)
- wupgrdsv.exe (PID: 7876)
- Build.exe (PID: 7832)
- tpeinf.exe (PID: 5500)
- adm_atu.exe (PID: 1492)
- Miner.exe (PID: 7428)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- whrbuflqwhah.exe (PID: 7084)
- smell-the-roses.exe (PID: 3972)
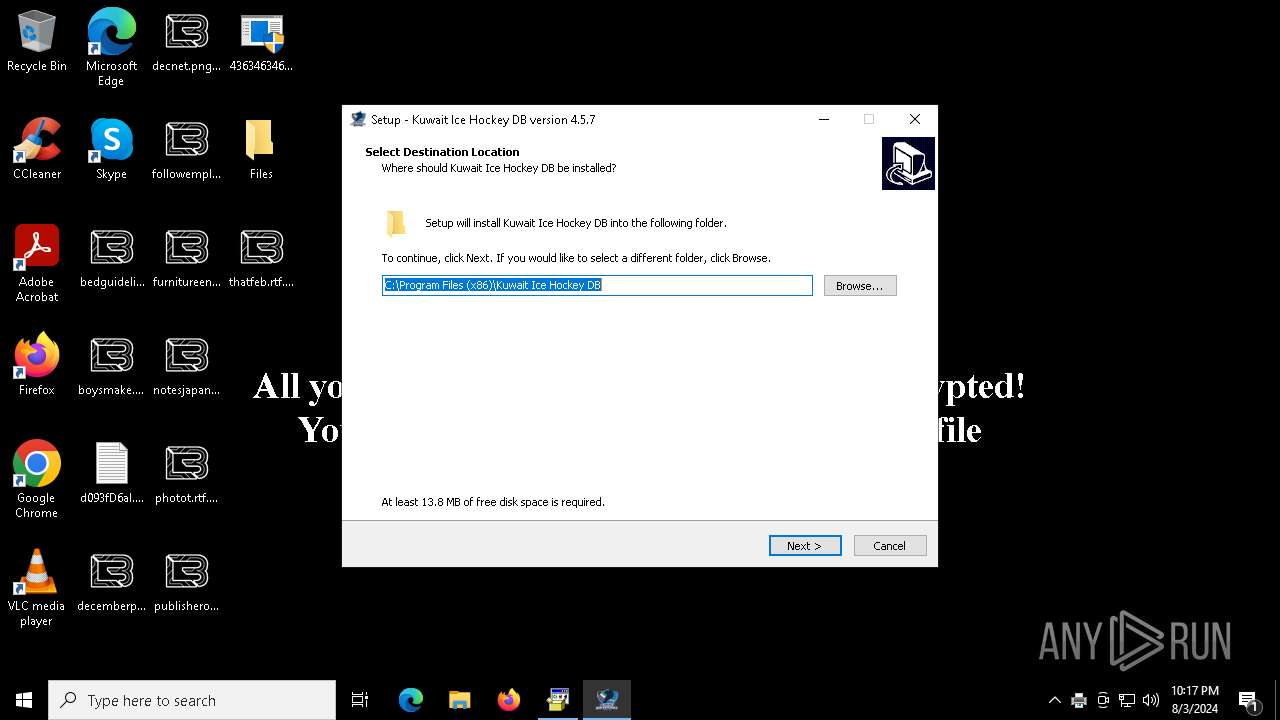
- KuwaitSetupHockey.exe (PID: 7856)
- KuwaitSetupHockey.tmp (PID: 6532)
- pei.exe (PID: 2400)
- msiexec.exe (PID: 5400)
- AUTOKEY.exe (PID: 6644)
- XClient.exe (PID: 7764)
- npp.exe (PID: 7876)
- random.exe (PID: 2208)
- NoEscape.exe (PID: 3972)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6380)
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 6380)
Changes the autorun value in the registry
- m.exe (PID: 6552)
- pi.exe (PID: 1116)
- 1.exe (PID: 3164)
- 171824798.exe (PID: 7816)
Creates or modifies Windows services
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
Attempt to connect to SMB server
- System (PID: 4)
Changes appearance of the Explorer extensions
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
Changes the Windows auto-update feature
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
Changes Security Center notification settings
- sysmablsvr.exe (PID: 6696)
- sylsplvc.exe (PID: 7040)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
PHORPIEX has been detected (SURICATA)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- svchost.exe (PID: 2256)
- sylsplvc.exe (PID: 7040)
- 4363463463464363463463463.exe (PID: 6380)
- sysmysldrv.exe (PID: 1184)
Connects to the CnC server
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- notepad.exe (PID: 6536)
- sysmysldrv.exe (PID: 1184)
- server.exe (PID: 7936)
- notepad.exe (PID: 8060)
- axplong.exe (PID: 3276)
Adds path to the Windows Defender exclusion list
- sysarddrvs.exe (PID: 320)
- cmd.exe (PID: 2456)
- sysmysldrv.exe (PID: 1184)
- cmd.exe (PID: 3164)
- XClient.exe (PID: 7764)
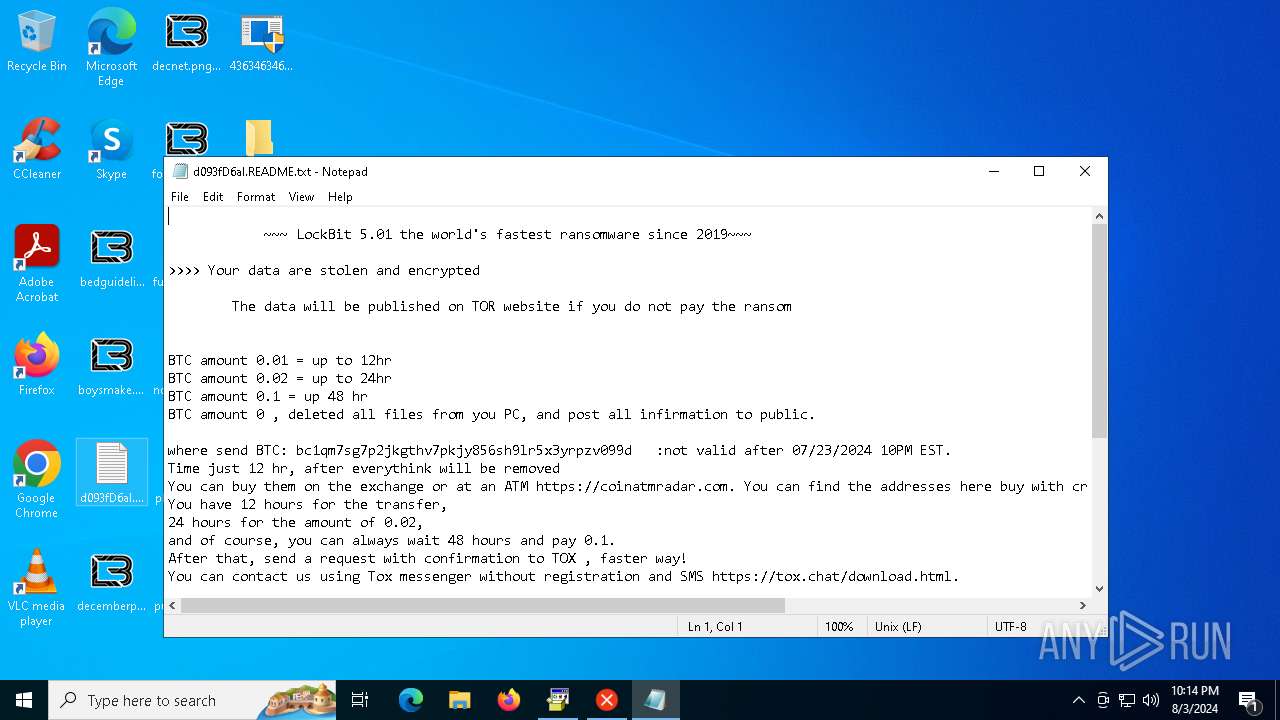
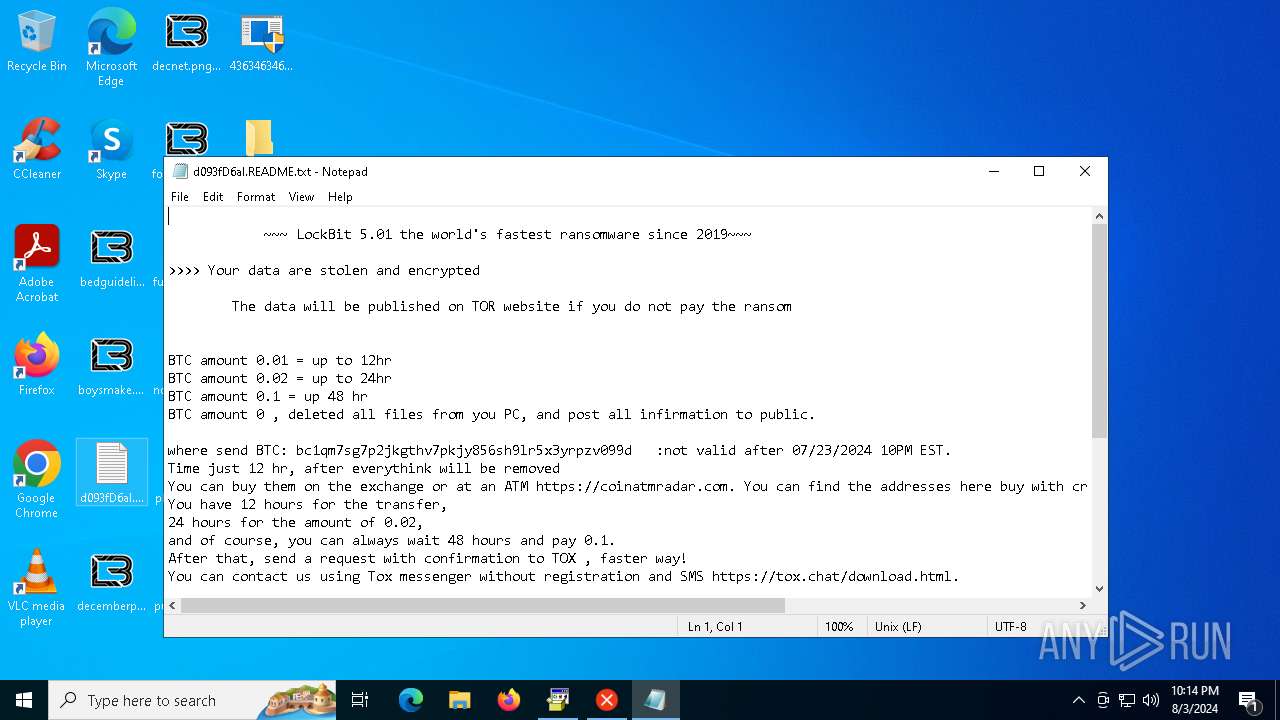
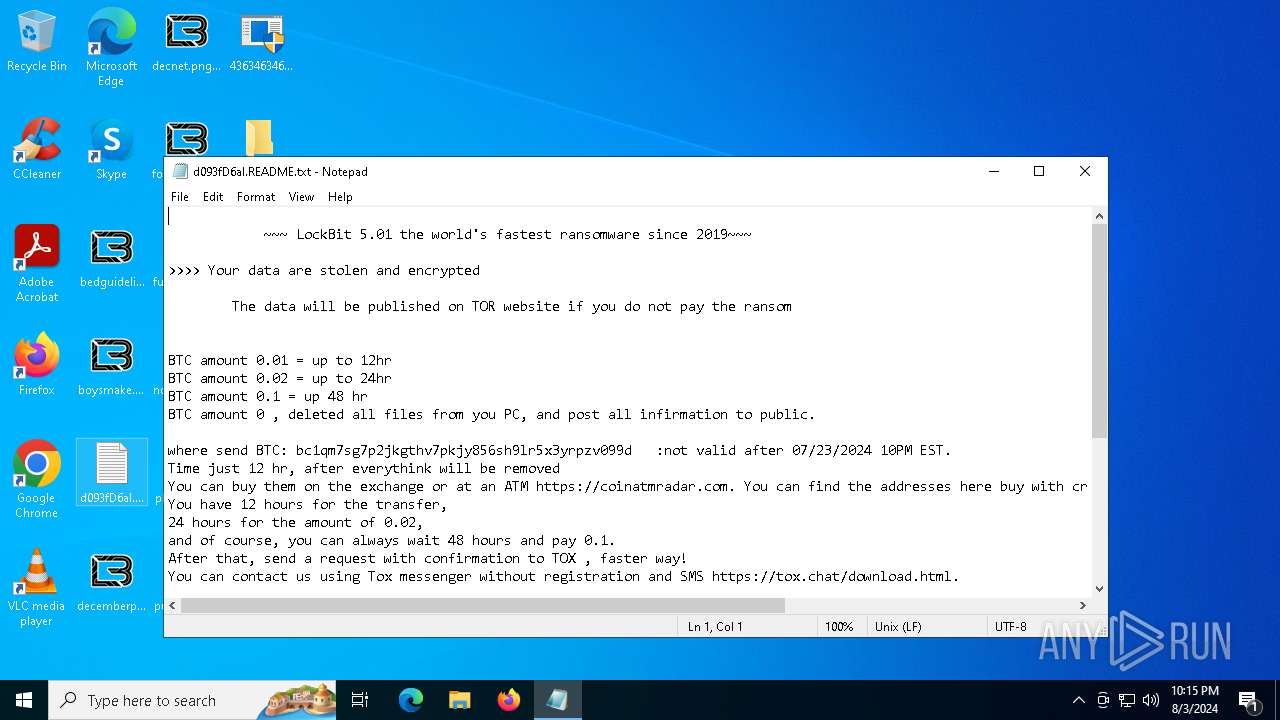
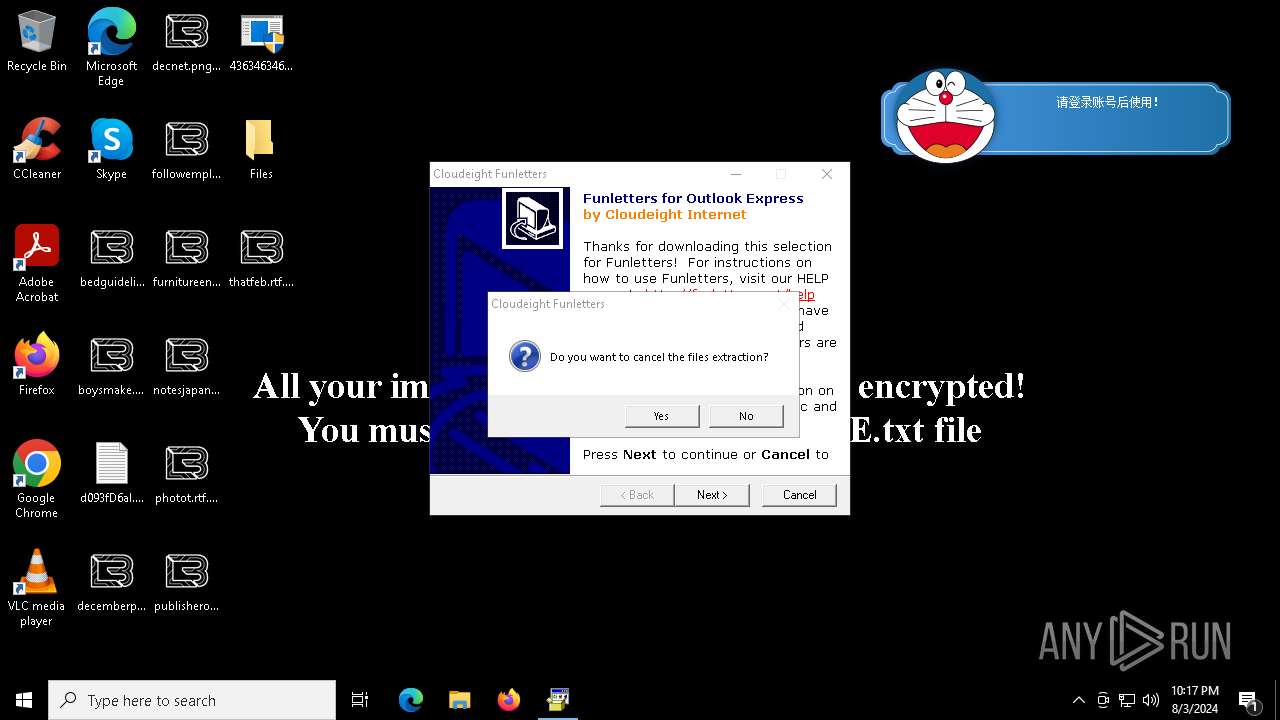
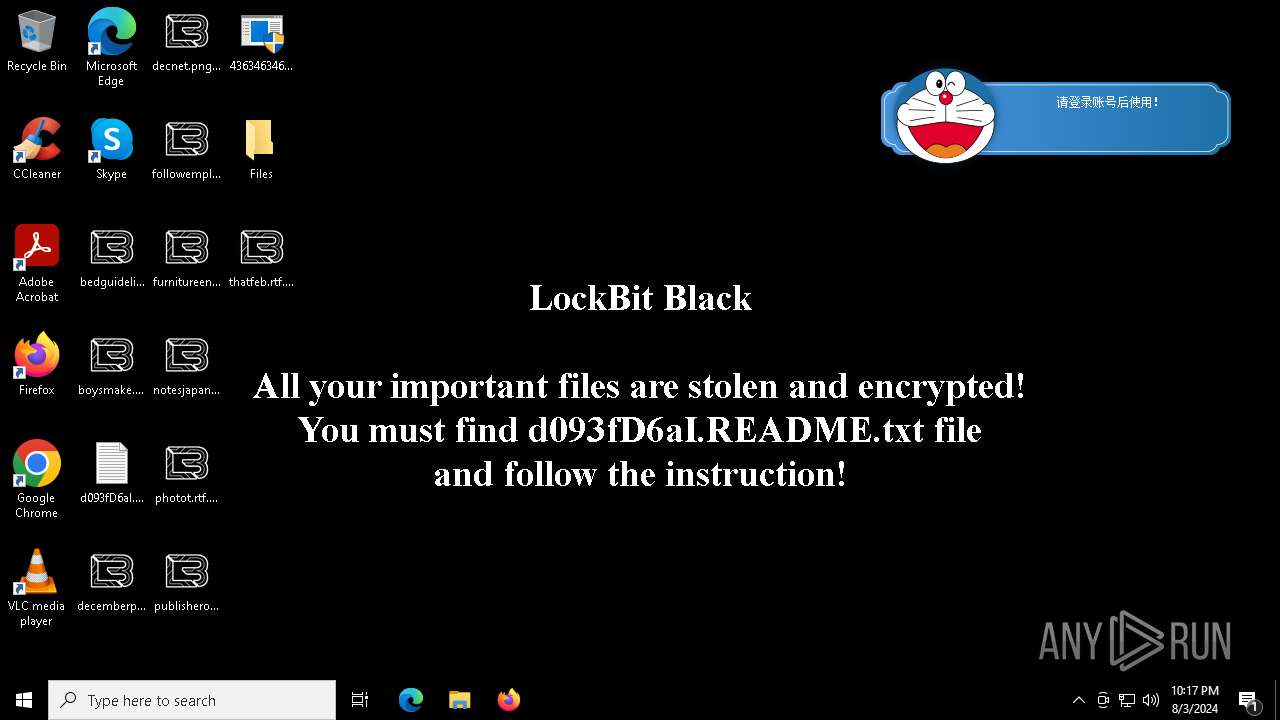
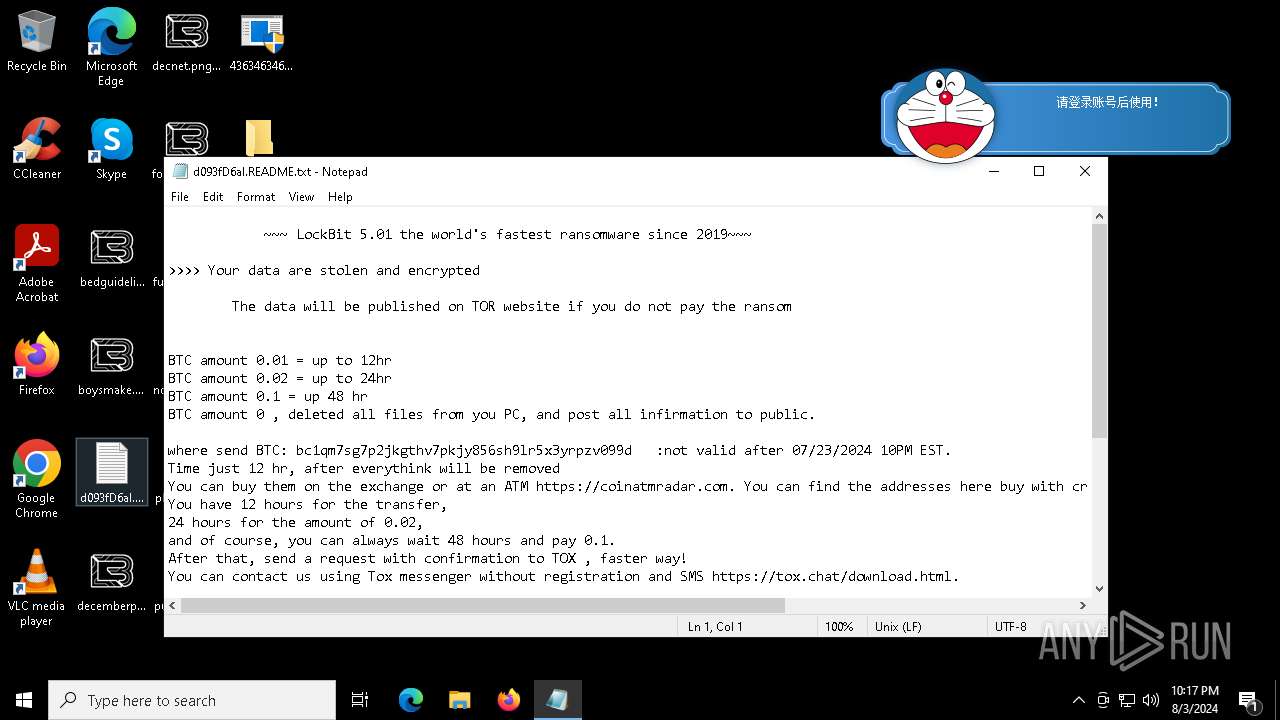
Renames files like ransomware
- LB3.exe (PID: 6184)
Steals credentials from Web Browsers
- LB3.exe (PID: 6184)
- server.exe (PID: 7936)
- Stealer.exe (PID: 7408)
- vbc.exe (PID: 5204)
MINER has been detected (SURICATA)
- notepad.exe (PID: 6536)
- notepad.exe (PID: 8060)
- svchost.exe (PID: 2256)
SILVER has been detected (YARA)
- ok.exe (PID: 6600)
Actions looks like stealing of personal data
- LB3.exe (PID: 6184)
- 1756312756.exe (PID: 8040)
- server.exe (PID: 7936)
- 4363463463464363463463463.exe (PID: 6380)
- postbox.exe (PID: 7340)
- peinf.exe (PID: 752)
- vbc.exe (PID: 5204)
- NoEscape.exe (PID: 3972)
PHORPIEX has been detected (YARA)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
METASTEALER has been detected (YARA)
- InstallUtil.exe (PID: 6664)
Stealers network behavior
- server.exe (PID: 7936)
XFILES has been detected (SURICATA)
- server.exe (PID: 7936)
[YARA] LockBit is detected
- LB3.exe (PID: 6184)
Starts CMD.EXE for self-deleting
- Stealer.exe (PID: 7408)
Adds extension to the Windows Defender exclusion list
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
Application was injected by another process
- winlogon.exe (PID: 684)
- svchost.exe (PID: 1036)
- dwm.exe (PID: 852)
- svchost.exe (PID: 1408)
- svchost.exe (PID: 476)
- lsass.exe (PID: 768)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 1200)
- svchost.exe (PID: 1272)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1508)
- svchost.exe (PID: 1472)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 2160)
- svchost.exe (PID: 1588)
- svchost.exe (PID: 1816)
- svchost.exe (PID: 2072)
- svchost.exe (PID: 2000)
- svchost.exe (PID: 1864)
- svchost.exe (PID: 1872)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 2344)
- svchost.exe (PID: 2184)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 2312)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 2496)
- spoolsv.exe (PID: 2592)
- svchost.exe (PID: 1796)
- svchost.exe (PID: 1628)
- svchost.exe (PID: 2968)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 3056)
- OfficeClickToRun.exe (PID: 2656)
- svchost.exe (PID: 3496)
- svchost.exe (PID: 3200)
- svchost.exe (PID: 3888)
- svchost.exe (PID: 3304)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 3260)
- svchost.exe (PID: 3340)
- svchost.exe (PID: 4332)
- svchost.exe (PID: 4300)
- svchost.exe (PID: 3408)
- ctfmon.exe (PID: 4356)
- sihost.exe (PID: 4112)
- svchost.exe (PID: 2692)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 4140)
- svchost.exe (PID: 4808)
- RuntimeBroker.exe (PID: 4244)
- MoUsoCoreWorker.exe (PID: 2120)
- svchost.exe (PID: 4532)
- dllhost.exe (PID: 5568)
- RuntimeBroker.exe (PID: 5560)
- dllhost.exe (PID: 3312)
- svchost.exe (PID: 5416)
- RuntimeBroker.exe (PID: 776)
- UserOOBEBroker.exe (PID: 2744)
- ApplicationFrameHost.exe (PID: 4052)
- svchost.exe (PID: 5036)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 5256)
- svchost.exe (PID: 5236)
- explorer.exe (PID: 4552)
- svchost.exe (PID: 4920)
- WmiPrvSE.exe (PID: 2384)
- RuntimeBroker.exe (PID: 5960)
- svchost.exe (PID: 5084)
- TrustedInstaller.exe (PID: 5744)
- audiodg.exe (PID: 7232)
- WmiPrvSE.exe (PID: 7544)
- svchost.exe (PID: 6876)
- svchost.exe (PID: 1824)
- uhssvc.exe (PID: 536)
- svchost.exe (PID: 2700)
- taskhostw.exe (PID: 2468)
- svchost.exe (PID: 6080)
- svchost.exe (PID: 6756)
- RuntimeBroker.exe (PID: 4324)
- Integrator.exe (PID: 8096)
- conhost.exe (PID: 7828)
- Integrator.exe (PID: 7420)
- conhost.exe (PID: 2680)
- svchost.exe (PID: 7632)
- WmiPrvSE.exe (PID: 3540)
- svchost.exe (PID: 7156)
- LogonUI.exe (PID: 4688)
- dllhost.exe (PID: 8092)
Runs injected code in another process
- dialer.exe (PID: 6128)
- dialer.exe (PID: 400)
Modifies hosts file to block updates
- Miner.exe (PID: 7428)
Attempting to connect via SSH
- 123.exe (PID: 4828)
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
- 2014-06-12_djylh.exe (PID: 4144)
Bypass execution policy to execute commands
- powershell.exe (PID: 1356)
- powershell.exe (PID: 1716)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 8180)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 7764)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 7764)
XWORM has been detected (YARA)
- XClient.exe (PID: 7764)
Create files in the Startup directory
- XClient.exe (PID: 7764)
AMADEY has been detected (SURICATA)
- axplong.exe (PID: 3276)
Disables the Shutdown in the Start menu
- NoEscape.exe (PID: 3972)
Changes the login/logoff helper path in the registry
- NoEscape.exe (PID: 3972)
UAC/LUA settings modification
- NoEscape.exe (PID: 3972)
SUSPICIOUS
Adds/modifies Windows certificates
- lsass.exe (PID: 768)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 6380)
- System (PID: 4)
- pered.exe (PID: 7840)
- notepad.exe (PID: 6536)
- 1826814013.exe (PID: 5916)
- notepad.exe (PID: 8060)
- 1646416317.exe (PID: 4260)
- tpeinf.exe (PID: 5500)
- 123.exe (PID: 4828)
- Downaqzh.exe (PID: 7264)
- AUTOKEY.exe (PID: 6644)
- DownSysSoft.exe (PID: 4280)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 6380)
- m.exe (PID: 6552)
- pi.exe (PID: 1116)
- mountain-pasture.exe (PID: 6204)
- 1.exe (PID: 3164)
- nxmr.exe (PID: 6948)
- pered.exe (PID: 7764)
- 171824798.exe (PID: 7816)
- wupgrdsv.exe (PID: 7712)
- 1646416317.exe (PID: 4260)
- 1826814013.exe (PID: 5916)
- wupgrdsv.exe (PID: 7876)
- Build.exe (PID: 7832)
- tpeinf.exe (PID: 5500)
- adm_atu.exe (PID: 1492)
- Miner.exe (PID: 7428)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- whrbuflqwhah.exe (PID: 7084)
- LB3.exe (PID: 6184)
- smell-the-roses.exe (PID: 3972)
- KuwaitSetupHockey.exe (PID: 7856)
- KuwaitSetupHockey.tmp (PID: 6532)
- pei.exe (PID: 2400)
- AUTOKEY.exe (PID: 6644)
- XClient.exe (PID: 7764)
- random.exe (PID: 2208)
- npp.exe (PID: 7876)
- NoEscape.exe (PID: 3972)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 6380)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- ShellExperienceHost.exe (PID: 3184)
- sylsplvc.exe (PID: 7040)
- 253231022.exe (PID: 4340)
- sysmysldrv.exe (PID: 1184)
- 1646416317.exe (PID: 4260)
- 1826814013.exe (PID: 5916)
- Build.exe (PID: 7832)
- Stealer.exe (PID: 7408)
- tpeinf.exe (PID: 5500)
- ONENOTE.EXE (PID: 7424)
- 970E.tmp (PID: 7752)
- Downaqzh.exe (PID: 7264)
- Integrator.exe (PID: 8096)
- pei.exe (PID: 2400)
- Integrator.exe (PID: 7420)
- AUTOKEY.exe (PID: 6644)
- XClient.exe (PID: 7764)
- 2014-06-12_djylh.exe (PID: 4144)
- DownSysSoft.exe (PID: 4280)
- random.exe (PID: 2208)
- npp.exe (PID: 7876)
- axplong.exe (PID: 3276)
Reads the date of Windows installation
- 4363463463464363463463463.exe (PID: 6380)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
- server.exe (PID: 7936)
- Build.exe (PID: 7832)
- Stealer.exe (PID: 7408)
- 970E.tmp (PID: 7752)
- ONENOTE.EXE (PID: 7424)
- XClient.exe (PID: 7764)
- random.exe (PID: 2208)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 6380)
- 1826814013.exe (PID: 5916)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 6380)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- sysmysldrv.exe (PID: 1184)
- 1826814013.exe (PID: 5916)
- axplong.exe (PID: 3276)
Connects to unusual port
- ok.exe (PID: 6600)
- aaa.exe (PID: 2532)
- InstallUtil.exe (PID: 6664)
- notepad.exe (PID: 6536)
- sylsplvc.exe (PID: 7040)
- notepad.exe (PID: 8060)
- sysmablsvr.exe (PID: 6696)
- sysmysldrv.exe (PID: 1184)
- sysarddrvs.exe (PID: 320)
- 4363463463464363463463463.exe (PID: 6380)
- dialer.exe (PID: 6784)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- 123.exe (PID: 4828)
- Downaqzh.exe (PID: 7264)
- vbc.exe (PID: 5204)
- DownSysSoft.exe (PID: 4280)
- XClient.exe (PID: 7764)
Starts itself from another location
- m.exe (PID: 6552)
- pi.exe (PID: 1116)
- 1.exe (PID: 3164)
- 171824798.exe (PID: 7816)
- sysmysldrv.exe (PID: 1184)
- random.exe (PID: 2208)
Creates or modifies Windows services
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
Starts CMD.EXE for commands execution
- sysarddrvs.exe (PID: 320)
- pered.exe (PID: 7840)
- sysmysldrv.exe (PID: 1184)
- Stealer.exe (PID: 7408)
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
- 970E.tmp (PID: 7752)
- SP.exe (PID: 6940)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 1076)
- ONENOTE.EXE (PID: 7424)
- svchost.exe (PID: 3220)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 4552)
- cmd.exe (PID: 2456)
- cmd.exe (PID: 3164)
- Build.exe (PID: 7832)
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
- XClient.exe (PID: 7764)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 2456)
- cmd.exe (PID: 3164)
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
- XClient.exe (PID: 7764)
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 6184)
- explorer.exe (PID: 4552)
Creates files like ransomware instruction
- LB3.exe (PID: 6184)
The process executes via Task Scheduler
- wupgrdsv.exe (PID: 7712)
- wupgrdsv.exe (PID: 7876)
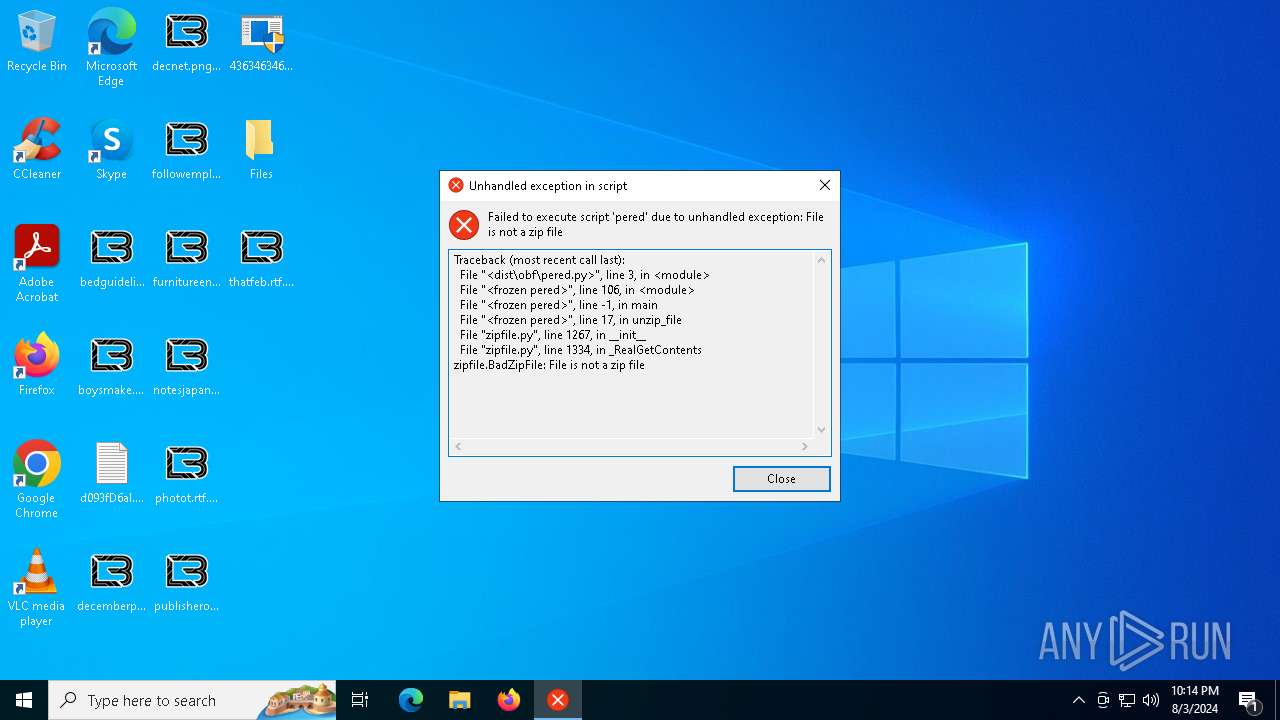
Process drops python dynamic module
- pered.exe (PID: 7764)
The process drops C-runtime libraries
- pered.exe (PID: 7764)
- msiexec.exe (PID: 5400)
Loads Python modules
- pered.exe (PID: 7840)
Process drops legitimate windows executable
- pered.exe (PID: 7764)
- msiexec.exe (PID: 5400)
- AUTOKEY.exe (PID: 6644)
Application launched itself
- pered.exe (PID: 7764)
Drops a system driver (possible attempt to evade defenses)
- wupgrdsv.exe (PID: 7712)
- whrbuflqwhah.exe (PID: 7084)
Crypto Currency Mining Activity Detected
- notepad.exe (PID: 6536)
- svchost.exe (PID: 2256)
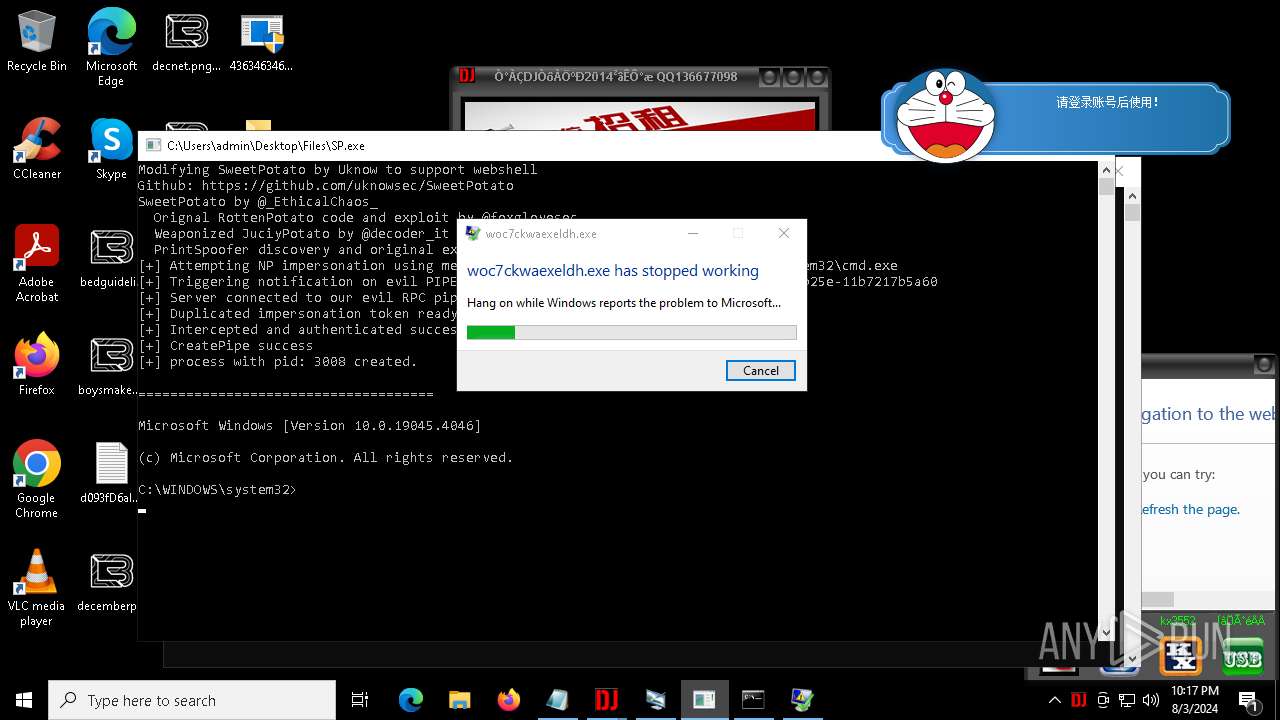
Executes application which crashes
- 1756312756.exe (PID: 8040)
- peinf.exe (PID: 752)
- woc7ckwaexeldh.exe (PID: 3684)
Contacting a server suspected of hosting an CnC
- server.exe (PID: 7936)
- axplong.exe (PID: 3276)
Base64-obfuscated command line is found
- Build.exe (PID: 7832)
Checks Windows Trust Settings
- Stealer.exe (PID: 7408)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
BASE64 encoded PowerShell command has been detected
- Build.exe (PID: 7832)
Searches for installed software
- Stealer.exe (PID: 7408)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6540)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 6380)
Process uninstalls Windows update
- wusa.exe (PID: 6748)
- wusa.exe (PID: 3540)
Script adds exclusion extension to Windows Defender
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
Starts SC.EXE for service management
- Miner.exe (PID: 7428)
- whrbuflqwhah.exe (PID: 7084)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Stealer.exe (PID: 7408)
Executes as Windows Service
- whrbuflqwhah.exe (PID: 7084)
There is functionality for taking screenshot (YARA)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- AUTOKEY.exe (PID: 6644)
- 2014-06-12_djylh.exe (PID: 4144)
Changes the desktop background image
- LB3.exe (PID: 6184)
Hides command output
- cmd.exe (PID: 7960)
Starts application with an unusual extension
- LB3.exe (PID: 6184)
Identifying current user with WHOAMI command
- 123.exe (PID: 4828)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5400)
- KuwaitSetupHockey.tmp (PID: 6532)
Creates file in the systems drive root
- ONENOTE.EXE (PID: 7424)
Reads the BIOS version
- AUTOKEY.exe (PID: 6644)
- random.exe (PID: 2208)
- axplong.exe (PID: 3276)
Checks for external IP
- svchost.exe (PID: 2256)
- XClient.exe (PID: 7764)
Reads Microsoft Outlook installation path
- 2014-06-12_djylh.exe (PID: 4144)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 7764)
There is functionality for communication over UDP network (YARA)
- postbox.exe (PID: 7340)
Found regular expressions for crypto-addresses (YARA)
- postbox.exe (PID: 7340)
Reads Internet Explorer settings
- 2014-06-12_djylh.exe (PID: 4144)
The process executes VB scripts
- woc7ckwaexeldh.exe (PID: 3684)
Possibly patching Antimalware Scan Interface function (YARA)
- WmiPrvSE.exe (PID: 3540)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
- Taskmgr.exe (PID: 6728)
- notepad.exe (PID: 6012)
- notepad.exe (PID: 7664)
- notepad.exe (PID: 7924)
- Taskmgr.exe (PID: 7676)
- notepad.exe (PID: 7472)
- splwow64.exe (PID: 7288)
- printfilterpipelinesvc.exe (PID: 4344)
- RuntimeBroker.exe (PID: 5560)
- notepad.exe (PID: 6540)
- LogonUI.exe (PID: 4688)
- dllhost.exe (PID: 8092)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 6380)
- sysmablsvr.exe (PID: 6696)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- 253231022.exe (PID: 4340)
- pered.exe (PID: 7840)
- sysmysldrv.exe (PID: 1184)
- 1646416317.exe (PID: 4260)
- 1826814013.exe (PID: 5916)
- WerFault.exe (PID: 1920)
- server.exe (PID: 7936)
- Stealer.exe (PID: 7408)
- tpeinf.exe (PID: 5500)
- ONENOTE.EXE (PID: 7424)
- Downaqzh.exe (PID: 7264)
- pei.exe (PID: 2400)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
- AUTOKEY.exe (PID: 6644)
- WerFault.exe (PID: 7272)
- XClient.exe (PID: 7764)
- 2014-06-12_djylh.exe (PID: 4144)
- WerFault.exe (PID: 4208)
- DownSysSoft.exe (PID: 4280)
- npp.exe (PID: 7876)
- axplong.exe (PID: 3276)
Manual execution by a user
- Taskmgr.exe (PID: 6672)
- Taskmgr.exe (PID: 6728)
- powershell.exe (PID: 1076)
- schtasks.exe (PID: 7644)
- powershell.exe (PID: 8092)
- notepad.exe (PID: 6012)
- notepad.exe (PID: 6536)
- notepad.exe (PID: 7664)
- notepad.exe (PID: 7924)
- powershell.exe (PID: 2456)
- Taskmgr.exe (PID: 7676)
- schtasks.exe (PID: 3376)
- Taskmgr.exe (PID: 6908)
- notepad.exe (PID: 8060)
- powershell.exe (PID: 5588)
- notepad.exe (PID: 7472)
- notepad.exe (PID: 6540)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 6380)
- lsass.exe (PID: 768)
- WerFault.exe (PID: 1920)
- server.exe (PID: 7936)
- Stealer.exe (PID: 7408)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
- WerFault.exe (PID: 7272)
- WerFault.exe (PID: 4208)
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 6380)
- sysarddrvs.exe (PID: 320)
- sysmysldrv.exe (PID: 1184)
- Build.exe (PID: 7832)
- Stealer.exe (PID: 7408)
- 970E.tmp (PID: 7752)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
- XClient.exe (PID: 7764)
- random.exe (PID: 2208)
Checks supported languages
- lolMiner.exe (PID: 6784)
- aaa.exe (PID: 2532)
- ok.exe (PID: 6600)
- m.exe (PID: 6552)
- pp.exe (PID: 5504)
- mimikatz.exe (PID: 5880)
- twztl.exe (PID: 1860)
- pi.exe (PID: 1116)
- sysmablsvr.exe (PID: 6696)
- 1.exe (PID: 3164)
- nxmr.exe (PID: 6948)
- t1.exe (PID: 5240)
- t.exe (PID: 5916)
- sylsplvc.exe (PID: 7040)
- mountain-pasture.exe (PID: 6204)
- tdrpload.exe (PID: 4592)
- InstallUtil.exe (PID: 6664)
- sysarddrvs.exe (PID: 320)
- cock.exe (PID: 7020)
- a.exe (PID: 876)
- LB3.exe (PID: 6184)
- TrustedInstaller.exe (PID: 5744)
- 4363463463464363463463463.exe (PID: 6380)
- RoguePotato.exe (PID: 1116)
- ShellExperienceHost.exe (PID: 3184)
- 253231022.exe (PID: 4340)
- wupgrdsv.exe (PID: 7712)
- pered.exe (PID: 7764)
- 1257123776.exe (PID: 7792)
- 171824798.exe (PID: 7816)
- pered.exe (PID: 7840)
- 2553519440.exe (PID: 7744)
- t2.exe (PID: 7976)
- server.exe (PID: 7936)
- sysmysldrv.exe (PID: 1184)
- 1558510602.exe (PID: 6752)
- 2434814736.exe (PID: 7888)
- 1646416317.exe (PID: 4260)
- 1756312756.exe (PID: 8040)
- 224695542.exe (PID: 8008)
- 1826814013.exe (PID: 5916)
- 319221664.exe (PID: 7152)
- 138332224.exe (PID: 8080)
- 3231730757.exe (PID: 8048)
- 1854232839.exe (PID: 8156)
- 326373082.exe (PID: 8100)
- 1625010004.exe (PID: 6940)
- wupgrdsv.exe (PID: 7876)
- 1160710827.exe (PID: 7048)
- 2055213134.exe (PID: 1860)
- adm_atu.exe (PID: 1492)
- s.exe (PID: 7132)
- Build.exe (PID: 7832)
- tpeinf.exe (PID: 5500)
- Miner.exe (PID: 7428)
- Stealer.exe (PID: 7408)
- 38959858.exe (PID: 7076)
- whrbuflqwhah.exe (PID: 7084)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- ONENOTE.EXE (PID: 7424)
- OfficeClickToRun.exe (PID: 2656)
- 970E.tmp (PID: 7752)
- 123.exe (PID: 4828)
- Downaqzh.exe (PID: 7264)
- smell-the-roses.exe (PID: 3972)
- o.exe (PID: 7984)
- Integrator.exe (PID: 8096)
- KuwaitSetupHockey.exe (PID: 7856)
- msiexec.exe (PID: 5400)
- KuwaitSetupHockey.tmp (PID: 6532)
- pei.exe (PID: 2400)
- msiexec.exe (PID: 7668)
- r.exe (PID: 6268)
- 150356380.exe (PID: 4744)
- ONENOTEM.EXE (PID: 1276)
- Integrator.exe (PID: 7420)
- AUTOKEY.exe (PID: 6644)
- peinf.exe (PID: 752)
- postbox.exe (PID: 7340)
- Downdd.exe (PID: 4008)
- XClient.exe (PID: 7764)
- crypted.exe (PID: 8056)
- tt.exe (PID: 7432)
- RegAsm.exe (PID: 4440)
- 2014-06-12_djylh.exe (PID: 4144)
- woc7ckwaexeldh.exe (PID: 3684)
- NoEscape.exe (PID: 3972)
- SP.exe (PID: 6940)
- vbc.exe (PID: 5204)
- DownSysSoft.exe (PID: 4280)
- npp.exe (PID: 7876)
- random.exe (PID: 2208)
- Project_8.exe (PID: 7652)
- axplong.exe (PID: 3276)
- 913914196.exe (PID: 4540)
Creates files in the program directory
- MoUsoCoreWorker.exe (PID: 2120)
- LB3.exe (PID: 6184)
- svchost.exe (PID: 6876)
- Miner.exe (PID: 7428)
- svchost.exe (PID: 7632)
- NoEscape.exe (PID: 3972)
Reads the computer name
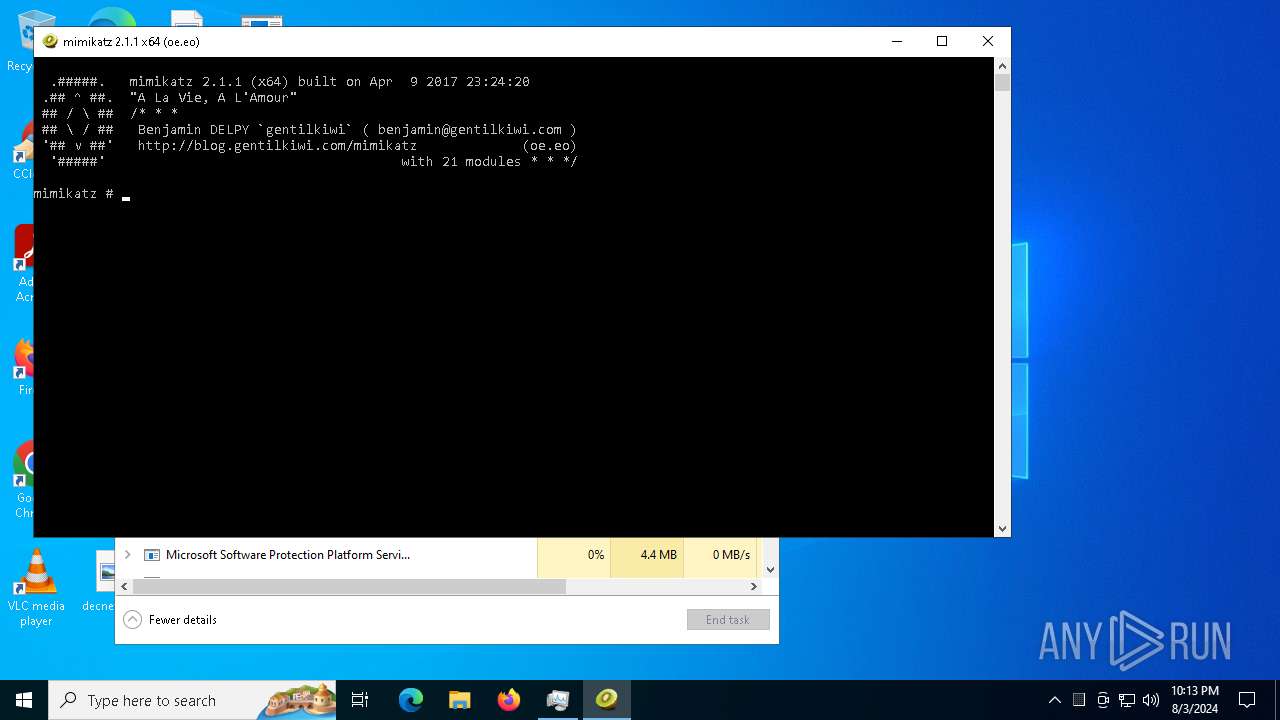
- aaa.exe (PID: 2532)
- mimikatz.exe (PID: 5880)
- mountain-pasture.exe (PID: 6204)
- sysmablsvr.exe (PID: 6696)
- InstallUtil.exe (PID: 6664)
- LB3.exe (PID: 6184)
- TrustedInstaller.exe (PID: 5744)
- sysarddrvs.exe (PID: 320)
- 4363463463464363463463463.exe (PID: 6380)
- ShellExperienceHost.exe (PID: 3184)
- 253231022.exe (PID: 4340)
- sylsplvc.exe (PID: 7040)
- pered.exe (PID: 7764)
- pered.exe (PID: 7840)
- sysmysldrv.exe (PID: 1184)
- 1646416317.exe (PID: 4260)
- 1826814013.exe (PID: 5916)
- server.exe (PID: 7936)
- adm_atu.exe (PID: 1492)
- Build.exe (PID: 7832)
- Stealer.exe (PID: 7408)
- tpeinf.exe (PID: 5500)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- 970E.tmp (PID: 7752)
- ONENOTE.EXE (PID: 7424)
- 123.exe (PID: 4828)
- smell-the-roses.exe (PID: 3972)
- Integrator.exe (PID: 8096)
- Downaqzh.exe (PID: 7264)
- KuwaitSetupHockey.tmp (PID: 6532)
- msiexec.exe (PID: 5400)
- msiexec.exe (PID: 7668)
- pei.exe (PID: 2400)
- ONENOTEM.EXE (PID: 1276)
- Integrator.exe (PID: 7420)
- AUTOKEY.exe (PID: 6644)
- postbox.exe (PID: 7340)
- XClient.exe (PID: 7764)
- crypted.exe (PID: 8056)
- 2014-06-12_djylh.exe (PID: 4144)
- NoEscape.exe (PID: 3972)
- SP.exe (PID: 6940)
- vbc.exe (PID: 5204)
- DownSysSoft.exe (PID: 4280)
- npp.exe (PID: 7876)
- random.exe (PID: 2208)
- axplong.exe (PID: 3276)
Reads the time zone
- WmiPrvSE.exe (PID: 2384)
- svchost.exe (PID: 2692)
- lsass.exe (PID: 768)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 2656)
- explorer.exe (PID: 4552)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- ONENOTEM.EXE (PID: 1276)
- Integrator.exe (PID: 7420)
- RuntimeBroker.exe (PID: 5560)
Create files in a temporary directory
- mountain-pasture.exe (PID: 6204)
- sysmablsvr.exe (PID: 6696)
- 253231022.exe (PID: 4340)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- pered.exe (PID: 7764)
- wupgrdsv.exe (PID: 7712)
- 1646416317.exe (PID: 4260)
- sysmysldrv.exe (PID: 1184)
- 1826814013.exe (PID: 5916)
- LB3.exe (PID: 6184)
- wupgrdsv.exe (PID: 7876)
- adm_atu.exe (PID: 1492)
- Build.exe (PID: 7832)
- tpeinf.exe (PID: 5500)
- ONENOTE.EXE (PID: 7424)
- smell-the-roses.exe (PID: 3972)
- Downaqzh.exe (PID: 7264)
- KuwaitSetupHockey.tmp (PID: 6532)
- KuwaitSetupHockey.exe (PID: 7856)
- pei.exe (PID: 2400)
- AUTOKEY.exe (PID: 6644)
- 2014-06-12_djylh.exe (PID: 4144)
- DownSysSoft.exe (PID: 4280)
- npp.exe (PID: 7876)
- random.exe (PID: 2208)
Creates files or folders in the user directory
- sysmablsvr.exe (PID: 6696)
- LB3.exe (PID: 6184)
- sysarddrvs.exe (PID: 320)
- sylsplvc.exe (PID: 7040)
- pered.exe (PID: 7840)
- wupgrdsv.exe (PID: 7712)
- sysmysldrv.exe (PID: 1184)
- 1646416317.exe (PID: 4260)
- 1826814013.exe (PID: 5916)
- WerFault.exe (PID: 1920)
- Build.exe (PID: 7832)
- Stealer.exe (PID: 7408)
- tpeinf.exe (PID: 5500)
- printfilterpipelinesvc.exe (PID: 4344)
- explorer.exe (PID: 4552)
- ONENOTE.EXE (PID: 7424)
- Downaqzh.exe (PID: 7264)
- AUTOKEY.exe (PID: 6644)
- WerFault.exe (PID: 7272)
- 2014-06-12_djylh.exe (PID: 4144)
- DownSysSoft.exe (PID: 4280)
- XClient.exe (PID: 7764)
- NoEscape.exe (PID: 3972)
- WerFault.exe (PID: 4208)
Reads the machine GUID from the registry
- InstallUtil.exe (PID: 6664)
- 4363463463464363463463463.exe (PID: 6380)
- pered.exe (PID: 7840)
- sylsplvc.exe (PID: 7040)
- server.exe (PID: 7936)
- sysmablsvr.exe (PID: 6696)
- sysmysldrv.exe (PID: 1184)
- Build.exe (PID: 7832)
- sysarddrvs.exe (PID: 320)
- Stealer.exe (PID: 7408)
- LB3.exe (PID: 6184)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
- AUTOKEY.exe (PID: 6644)
- XClient.exe (PID: 7764)
- 2014-06-12_djylh.exe (PID: 4144)
- SP.exe (PID: 6940)
Reads Environment values
- 4363463463464363463463463.exe (PID: 6380)
- Stealer.exe (PID: 7408)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- msiexec.exe (PID: 7668)
- AUTOKEY.exe (PID: 6644)
- Integrator.exe (PID: 7420)
- XClient.exe (PID: 7764)
- 2014-06-12_djylh.exe (PID: 4144)
- random.exe (PID: 2208)
- axplong.exe (PID: 3276)
Disables trace logs
- 4363463463464363463463463.exe (PID: 6380)
- XClient.exe (PID: 7764)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2580)
- powershell.exe (PID: 1076)
- powershell.exe (PID: 7356)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 1716)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 8180)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1076)
- powershell.exe (PID: 2580)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 1076)
- powershell.exe (PID: 2456)
- powershell.exe (PID: 5588)
- powershell.exe (PID: 7356)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 7424)
- powershell.exe (PID: 1716)
- powershell.exe (PID: 8180)
Checks operating system version
- pered.exe (PID: 7840)
Reads product name
- Stealer.exe (PID: 7408)
- ONENOTE.EXE (PID: 7424)
Reads Windows Product ID
- WmiPrvSE.exe (PID: 2384)
Reads CPU info
- Stealer.exe (PID: 7408)
- ONENOTE.EXE (PID: 7424)
- Integrator.exe (PID: 8096)
- Integrator.exe (PID: 7420)
UPX packer has been detected
- adm_atu.exe (PID: 1492)
- 3R%BC%BC%CA%F5.exe (PID: 7228)
- dialer.exe (PID: 6784)
- 123.exe (PID: 4828)
- 2014-06-12_djylh.exe (PID: 4144)
Attempting to use instant messaging service
- Stealer.exe (PID: 7408)
Drops the executable file immediately after the start
- svchost.exe (PID: 2968)
Reads mouse settings
- Downaqzh.exe (PID: 7264)
- Downdd.exe (PID: 4008)
- DownSysSoft.exe (PID: 4280)
Creates a software uninstall entry
- msiexec.exe (PID: 5400)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5400)
Application launched itself
- msiexec.exe (PID: 5400)
Process checks whether UAC notifications are on
- AUTOKEY.exe (PID: 6644)
Themida protector has been detected
- AUTOKEY.exe (PID: 6644)
Process checks Internet Explorer phishing filters
- 2014-06-12_djylh.exe (PID: 4144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
MetaStealer
(PID) Process(6664) InstallUtil.exe
C2 (1)5.42.65.101:48790
Botnet740675865-26990097-packlab
Options
ErrorMessage
Keys
XorPyrometry
XWorm
(PID) Process(7764) XClient.exe
C2154.197.69.157:1433
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.4
MutexV3fxvi2xf7WP9bW6
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
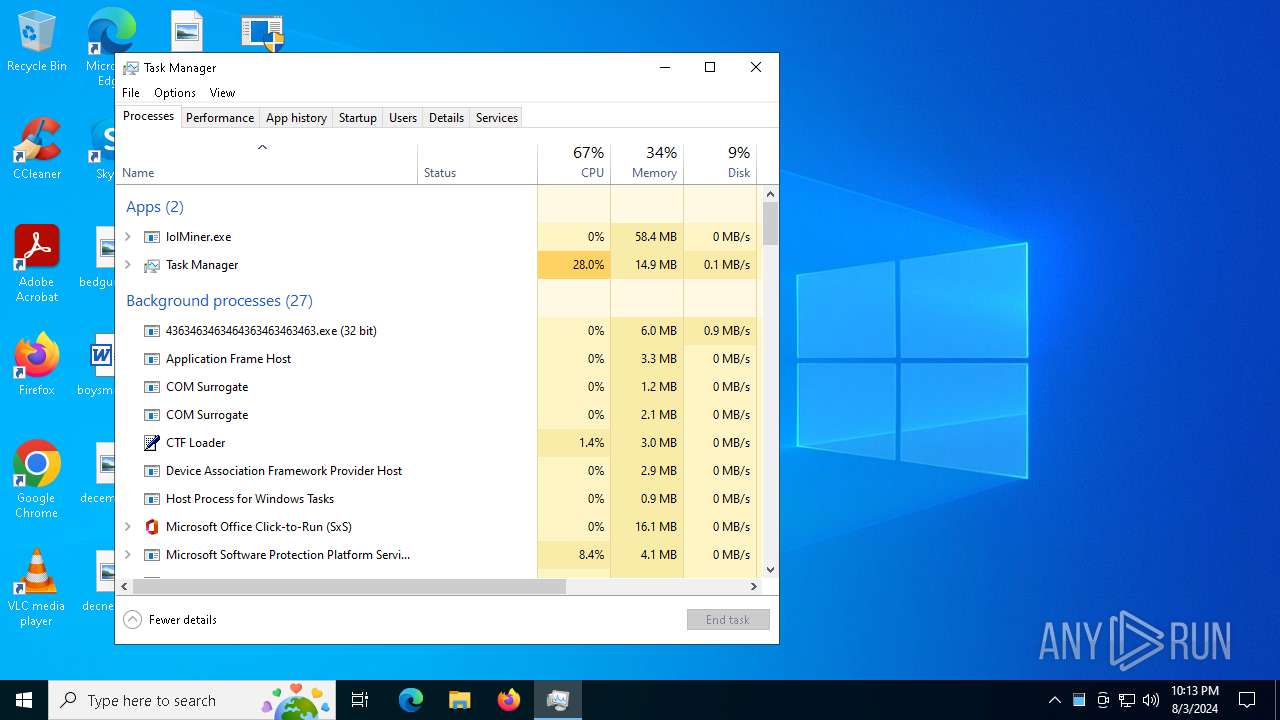
Total processes
372
Monitored processes
310
Malicious processes
130
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4 | System | [System Process] | |||||||||||||
User: SYSTEM Integrity Level: SYSTEM | |||||||||||||||
| 320 | C:\WINDOWS\sysarddrvs.exe | C:\Windows\sysarddrvs.exe | 1.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 400 | C:\WINDOWS\system32\dialer.exe | C:\Windows\System32\dialer.exe | — | whrbuflqwhah.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Phone Dialer Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | "C:\Program Files\Microsoft Update Health Tools\uhssvc.exe" | C:\Program Files\Microsoft Update Health Tools\uhssvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Update Health Service Version: 10.0.19041.3626 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Desktop\Files\peinf.exe" | C:\Users\admin\Desktop\Files\peinf.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 768 | C:\WINDOWS\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Exit code: 1073807364 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cock.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
341 180
Read events
335 283
Write events
5 329
Delete events
568
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001500000000000000620065006400670075006900640065006C0069006E00650073002E006A00700067003E00200020000000100000000000000062006F00790073006D0061006B0065002E007200740066003E002000200000001B0000000000000064006500630065006D006200650072007000750062006C00690063006100740069006F006E002E006A00700067003E002000200000000E000000000000006400650063006E00650074002E0070006E0067003E00200020000000160000000000000066006F006C006C006F00770065006D0070006C006F007900650065002E0070006E0067003E0020002000000013000000000000006600750072006E006900740075007200650065006E002E007200740066003E0020002000000012000000000000006E006F007400650073006A006100700061006E002E007200740066003E002000200000000E00000000000000700068006F0074006F0074002E007200740066003E0020002000000014000000000000007000750062006C00690073006800650072006F00750072002E007200740066003E002000200000000F0000000000000074006800610074006600650062002E007200740066003E00200020000000210000000000000034003300360033003400360033003400360033003400360034003300360033003400360033003400360033003400360033002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001300000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A0401100000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000080410000A0401200 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010013000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001500000000000000620065006400670075006900640065006C0069006E00650073002E006A00700067003E00200020000000100000000000000062006F00790073006D0061006B0065002E007200740066003E002000200000001B0000000000000064006500630065006D006200650072007000750062006C00690063006100740069006F006E002E006A00700067003E002000200000000E000000000000006400650063006E00650074002E0070006E0067003E00200020000000160000000000000066006F006C006C006F00770065006D0070006C006F007900650065002E0070006E0067003E0020002000000013000000000000006600750072006E006900740075007200650065006E002E007200740066003E0020002000000012000000000000006E006F007400650073006A006100700061006E002E007200740066003E002000200000000E00000000000000700068006F0074006F0074002E007200740066003E0020002000000014000000000000007000750062006C00690073006800650072006F00750072002E007200740066003E002000200000000F0000000000000074006800610074006600650062002E007200740066003E00200020000000210000000000000034003300360033003400360033003400360033003400360034003300360033003400360033003400360033003400360033002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001300000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A0401100000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000004040000000001200 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 78ABAE6600000000 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D69B561148F01C77C54578C10926DF5B856976AD |
Value: | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB0281400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9532000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (768) lsass.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800001D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D0020005200330000001400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB0282000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (6380) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6380) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
172
Suspicious files
2 497
Text files
2 314
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1620 | svchost.exe | C:\Windows\Prefetch\CONSENT.EXE-531BD9EA.pf | binary | |
MD5:117180F4DF5CBEC2988B697CAF0068BF | SHA256:379A62D9216CE7D14B35AFD6B2945944A8DF9F4C31A5CACE5E946C51864205C2 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\HOST.EXE-F5D74C61.pf | binary | |
MD5:37075EA53A828E38DCEA84B15402DF0B | SHA256:0BC990A481DEE02D10EF0AD100325BC48CC2F0E090FD2A274C6DAC5DF8F88FE8 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SPPSVC.EXE-B0F8131B.pf | binary | |
MD5:635E185EABF93DB671134660CFF74F3A | SHA256:91CBD9DB1E779DC0A7118760A9AACB565CCD137EF6DAF613D9D14B9CD979D767 | |||
| 6380 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\lolMiner.exe | executable | |
MD5:03AB160D92DD13E549A778A844D008B4 | SHA256:8846C90B130F131059261045607983827E68AA26E699C591FB7E4A9235389E4E | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\4363463463464363463463463.EXE-40DA11F3.pf | binary | |
MD5:5A02EB5FB3106A9DDE7AC94777C00BA9 | SHA256:942D2D0919AC4089B11BF296406CCC4241CE6281156A98CF892F074CCFE2DB21 | |||
| 4920 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:AC924B85DD97A35FEF34B31739A01FD3 | SHA256:2DCD5B83858E965B7E2397974730B7D8ED2360C3D47A8BEA931E9E225B0E1421 | |||
| 4920 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:E98A64AA32A892FBCAE3125FCEDDEAC3 | SHA256:C041FD3A35D3804FF39B877A68BD51153F62040B0A43052BA9FE6CEAC0364A84 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-0C2D202C.pf | binary | |
MD5:B1D40AA2504D69FEF5CA8DD963F3648D | SHA256:E2DDD7DE8C2EA22D5BBBE1428B6B12E4BEF16DBC169593B36EBEEA69A08A0C21 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\LOLMINER.EXE-2334E9C9.pf | binary | |
MD5:F693BC09F15BBCF3138D2298C35BF78B | SHA256:F4339117CD54ABBA6811FA9C231C15FA5FE80181553112092FF1646A935B75A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
113
TCP/UDP connections
584
DNS requests
81
Threats
301
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4920 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6380 | 4363463463464363463463463.exe | GET | 200 | 147.45.47.81:80 | http://147.45.47.81/lolMiner.exe | unknown | — | — | suspicious |
6380 | 4363463463464363463463463.exe | GET | 200 | 185.208.158.176:80 | http://185.208.158.176/ok.exe | unknown | — | — | suspicious |
4920 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7104 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6380 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://72ec8d09-fce8-4272-9829-f4a17ae33269.random.fihsifuiiusuiuduf.com/aaa.exe | unknown | — | — | malicious |
6380 | 4363463463464363463463463.exe | GET | 200 | 101.42.158.190:80 | http://101.42.158.190/mimikatz.exe | unknown | — | — | unknown |
6380 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pp.exe | unknown | — | — | unknown |
7152 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4056 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1116 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6380 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
6380 | 4363463463464363463463463.exe | 147.45.47.81:80 | — | OOO FREEnet Group | RU | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6380 | 4363463463464363463463463.exe | 185.208.158.176:80 | — | — | US | unknown |
4056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
72ec8d09-fce8-4272-9829-f4a17ae33269.random.fihsifuiiusuiuduf.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6380 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
6380 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 23 |
6380 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6380 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6380 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
45 ETPRO signatures available at the full report
Process | Message |
|---|---|
splwow64.exe | Invalid parameter passed to C runtime function.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
random.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
axplong.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|