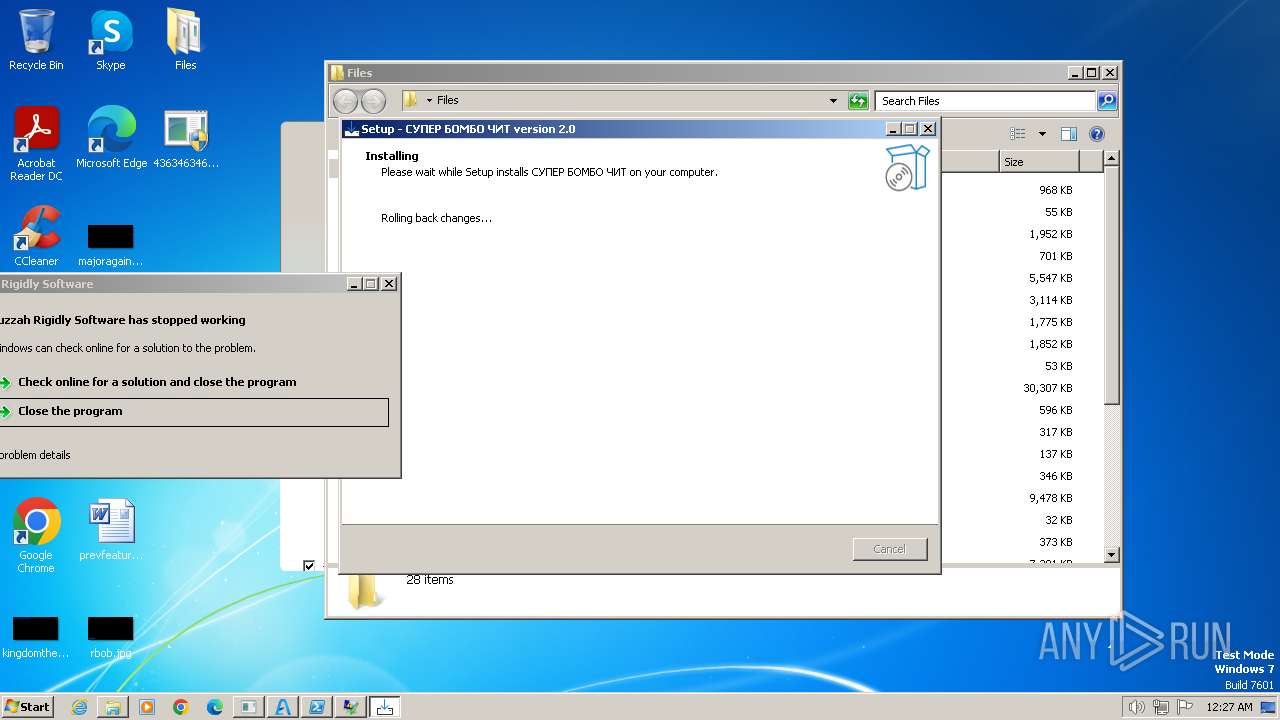
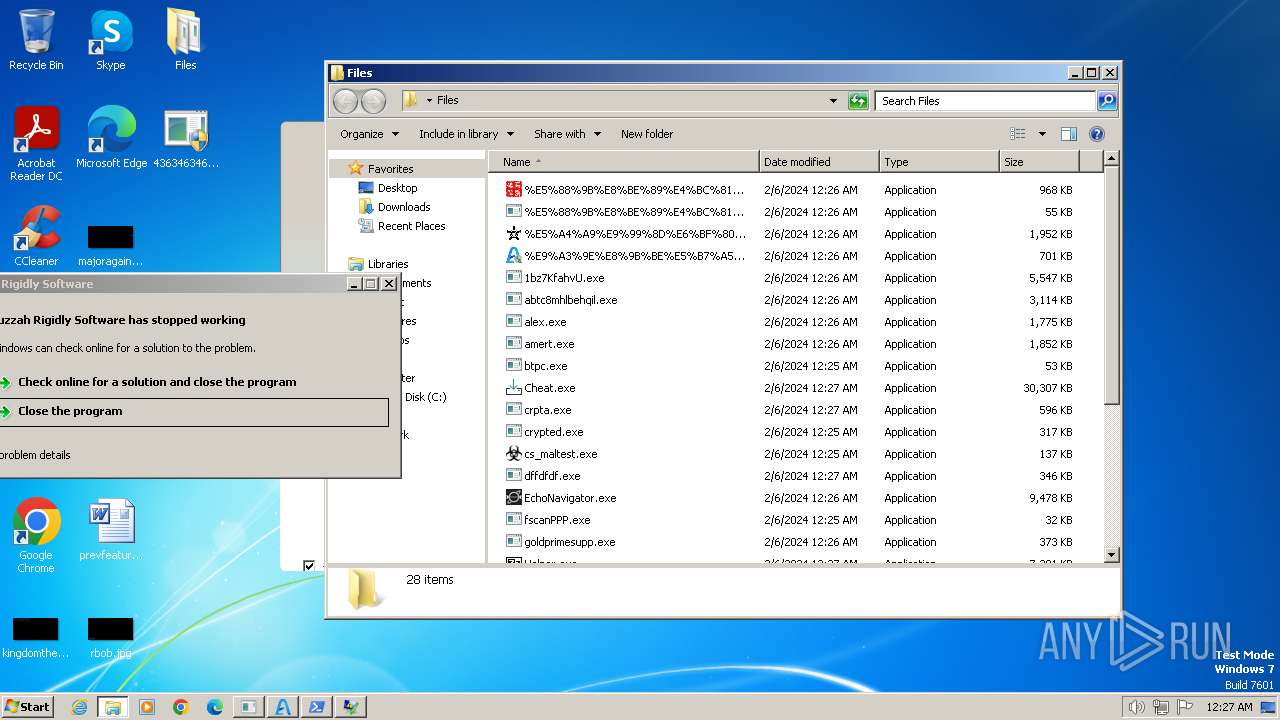
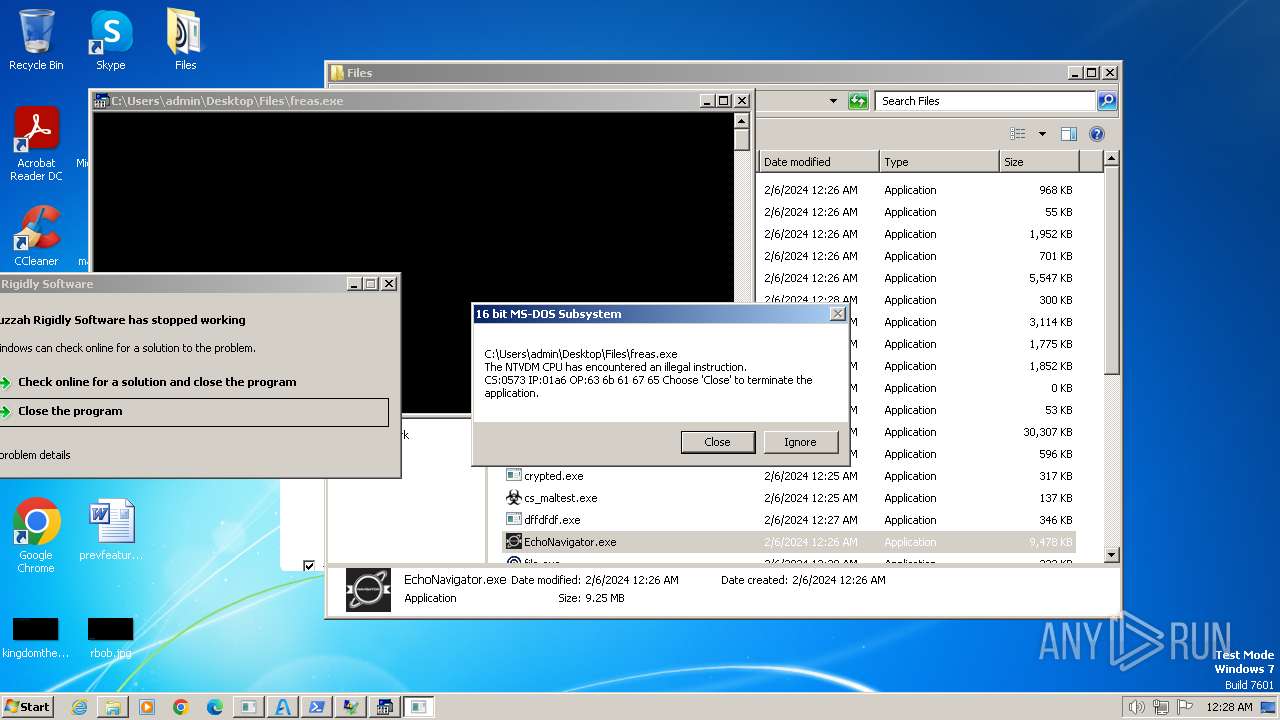
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/891dac07-cc41-4139-a411-325991c016e9 |
| Verdict: | Malicious activity |
| Threats: | The Arechclient2 malware is a sophisticated .NET-based Remote Access Trojan (RAT) that collects sensitive information, such as browser credentials, from infected computers. It employs various stealth techniques, including Base64 encoding to obscure its code and the ability to pause activities to evade automated security tools. The malware also can adjust Windows Defender settings and uses code injection to manipulate legitimate processes. |
| Analysis date: | February 06, 2024, 00:24:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- amert.exe (PID: 3724)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
- Helper.exe (PID: 2776)
- NeonRank.exe (PID: 3444)
- cmd.exe (PID: 2948)
- Cheat.exe (PID: 1236)
- plugins.exe (PID: 2156)
- Cheat.tmp (PID: 2248)
- AquariumScreening.exe (PID: 2828)
- cmd.exe (PID: 3296)
- Carpet.pif (PID: 3880)
- Amadey.exe (PID: 3572)
- npp86Installerx64.exe (PID: 2124)
- firefoxsunny.exe (PID: 1796)
- cmd.exe (PID: 840)
- America.pif (PID: 2576)
- asdfg.exe (PID: 2624)
- BBLb.exe (PID: 748)
- Awwnbpxqsf.exe (PID: 3892)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
LUMMA has been detected (YARA)
- crypted.exe (PID: 3600)
REDLINE has been detected (YARA)
- vbc.exe (PID: 3644)
- new.exe (PID: 2228)
- alex.exe (PID: 1860)
- 2024.exe (PID: 3244)
HIJACKLOADER has been detected (YARA)
- svchost.exe (PID: 3436)
Changes powershell execution policy (Bypass)
- EchoNavigator.exe (PID: 2304)
Bypass execution policy to execute commands
- powershell.exe (PID: 2340)
- powershell.exe (PID: 3132)
Actions looks like stealing of personal data
- crypted.exe (PID: 3600)
- RegAsm.exe (PID: 2312)
- InstallUtil.exe (PID: 2004)
Signature: RAMNIT has been detected
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
- DesktopLayer.exe (PID: 3404)
- iexplore.exe (PID: 568)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 568)
Connects to the CnC server
- iexplore.exe (PID: 568)
- RegAsm.exe (PID: 2312)
- RegAsm.exe (PID: 2836)
- InstallUtil.exe (PID: 2004)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 2312)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 2312)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1880)
- findstr.exe (PID: 3640)
- findstr.exe (PID: 3640)
- findstr.exe (PID: 2692)
- findstr.exe (PID: 2092)
- findstr.exe (PID: 2372)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 568)
VIDAR has been detected (YARA)
- InstallUtil.exe (PID: 2984)
Create files in the Startup directory
- cmd.exe (PID: 2260)
- cmd.exe (PID: 2396)
ASYNCRAT has been detected (YARA)
- windows.exe (PID: 1624)
Run PowerShell with an invisible window
- powershell.exe (PID: 3132)
Raccoon mutex has been detected
- 2.3.1.1.exe (PID: 952)
Disables Windows Defender
- niks.exe (PID: 3936)
RACCOON has been detected (YARA)
- 2.3.1.1.exe (PID: 952)
Changes the Windows auto-update feature
- niks.exe (PID: 3936)
ARECHCLIENT2 has been detected (SURICATA)
- InstallUtil.exe (PID: 2004)
SUSPICIOUS
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- amert.exe (PID: 3724)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
- Helper.exe (PID: 2776)
- NeonRank.exe (PID: 3444)
- cmd.exe (PID: 2948)
- Cheat.exe (PID: 1236)
- Cheat.tmp (PID: 2248)
- plugins.exe (PID: 2156)
- AquariumScreening.exe (PID: 2828)
- cmd.exe (PID: 3296)
- Carpet.pif (PID: 3880)
- Amadey.exe (PID: 3572)
- npp86Installerx64.exe (PID: 2124)
- firefoxsunny.exe (PID: 1796)
- cmd.exe (PID: 840)
- asdfg.exe (PID: 2624)
- America.pif (PID: 2576)
- BBLb.exe (PID: 748)
- Awwnbpxqsf.exe (PID: 3892)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- Helper.exe (PID: 2776)
- InstallUtil.exe (PID: 2984)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2628)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- powershell.exe (PID: 2340)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- NeonRank.exe (PID: 3444)
- InstallUtil.exe (PID: 2984)
- VLTKTanthuTN.exe (PID: 3628)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- asdfg.exe (PID: 2624)
- powershell.exe (PID: 3132)
- 2.3.1.1.exe (PID: 952)
- VLTKNhatRac.exe (PID: 2184)
- RegAsm.exe (PID: 2836)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2628)
- Helper.exe (PID: 2776)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- RegAsm.exe (PID: 2836)
The process executes VB scripts
- new.exe (PID: 2228)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2628)
- RegAsm.exe (PID: 2312)
- 2024.exe (PID: 3244)
- file.exe (PID: 3868)
- windows.exe (PID: 1624)
- VLTKTanthuTN.exe (PID: 3628)
- VLTKNhatRac.exe (PID: 2184)
- InstallUtil.exe (PID: 2004)
Searches for installed software
- crypted.exe (PID: 3600)
- RegAsm.exe (PID: 2312)
- InstallUtil.exe (PID: 2004)
Reads browser cookies
- crypted.exe (PID: 3600)
- RegAsm.exe (PID: 2312)
- InstallUtil.exe (PID: 2004)
The process hide an interactive prompt from the user
- EchoNavigator.exe (PID: 2304)
The process hides Powershell's copyright startup banner
- EchoNavigator.exe (PID: 2304)
The process executes Powershell scripts
- EchoNavigator.exe (PID: 2304)
Starts POWERSHELL.EXE for commands execution
- EchoNavigator.exe (PID: 2304)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
The Powershell connects to the Internet
- powershell.exe (PID: 2340)
Reads the BIOS version
- amert.exe (PID: 3724)
Unusual connection from system programs
- powershell.exe (PID: 2340)
Starts itself from another location
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
The process bypasses the loading of PowerShell profile settings
- EchoNavigator.exe (PID: 2304)
Checks Windows Trust Settings
- Helper.exe (PID: 2776)
- InstallUtil.exe (PID: 2984)
Reads the Windows owner or organization settings
- Helper.exe (PID: 2776)
- Cheat.tmp (PID: 2248)
Reads security settings of Internet Explorer
- Helper.exe (PID: 2776)
- InstallUtil.exe (PID: 2984)
Starts CMD.EXE for commands execution
- NeonRank.exe (PID: 3444)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2512)
- firefoxsunny.exe (PID: 1796)
- cmd.exe (PID: 3036)
- America.pif (PID: 2576)
- AquariumScreening.exe (PID: 2828)
Get information on the list of running processes
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 3036)
Executing commands from a ".bat" file
- NeonRank.exe (PID: 3444)
- AquariumScreening.exe (PID: 2828)
- firefoxsunny.exe (PID: 1796)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 3036)
Application launched itself
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 3036)
- asdfg.exe (PID: 2624)
- BBLb.exe (PID: 2208)
- Awwnbpxqsf.exe (PID: 3892)
- AttributeString.exe (PID: 1816)
Starts application with an unusual extension
- cmd.exe (PID: 1748)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 3036)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1748)
- cmd.exe (PID: 3036)
- cmd.exe (PID: 2512)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 3296)
- Carpet.pif (PID: 3880)
- cmd.exe (PID: 840)
- America.pif (PID: 2576)
The executable file from the user directory is run by the CMD process
- Taxes.pif (PID: 3436)
- Carpet.pif (PID: 3880)
- America.pif (PID: 2576)
The process drops C-runtime libraries
- Cheat.tmp (PID: 2248)
Process drops legitimate windows executable
- Cheat.tmp (PID: 2248)
- 4363463463464363463463463.exe (PID: 1384)
- Carpet.pif (PID: 3880)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- InstallUtil.exe (PID: 2984)
Executes as Windows Service
- VSSVC.exe (PID: 2936)
Starts a Microsoft application from unusual location
- npp86Installerx64.exe (PID: 2124)
- jsc.exe (PID: 2760)
The process executes via Task Scheduler
- powershell.exe (PID: 3132)
- AttributeString.exe (PID: 1816)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3132)
Process uses IPCONFIG to get network configuration information
- America.pif (PID: 2576)
Connects to FTP
- VLTKNhatRac.exe (PID: 2184)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2628)
- vbc.exe (PID: 3644)
- new.exe (PID: 2228)
- cs_maltest.exe (PID: 3632)
- svchost.exe (PID: 3436)
- crypted.exe (PID: 3600)
- EchoNavigator.exe (PID: 2304)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
- amert.exe (PID: 3724)
- alex.exe (PID: 1860)
- 4363463463464363463463463.exe (PID: 1384)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
- DesktopLayer.exe (PID: 3404)
- goldprimesupp.exe (PID: 1592)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 296)
- RegAsm.exe (PID: 2312)
- Helper.exe (PID: 2776)
- NeonRank.exe (PID: 3444)
- Taxes.pif (PID: 3436)
- Cheat.exe (PID: 1236)
- Cheat.tmp (PID: 2248)
- plugins.exe (PID: 2156)
- dffdfdf.exe (PID: 1992)
- crpta.exe (PID: 2172)
- InstallUtil.exe (PID: 2984)
- windows.exe (PID: 1624)
- 2024.exe (PID: 3244)
- file.exe (PID: 3868)
- AquariumScreening.exe (PID: 2828)
- Amadey.exe (PID: 3572)
- Carpet.pif (PID: 3880)
- InstallSetup2.exe (PID: 3000)
- firefoxsunny.exe (PID: 1796)
- Awwnbpxqsf.exe (PID: 3892)
- VLTKTanthuTN.exe (PID: 3628)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- npp86Installerx64.exe (PID: 2124)
- America.pif (PID: 2576)
- asdfg.exe (PID: 2624)
- BBLb.exe (PID: 2208)
- gold1201001.exe (PID: 3236)
- BBLb.exe (PID: 748)
- 83f32a3d2dc9e3d9903f395a20b8ddd74a1f35487c6dffd67d9d9a014961f9d0.exe (PID: 2092)
- 2.3.1.1.exe (PID: 952)
- jsc.exe (PID: 2760)
- niks.exe (PID: 3936)
- cp.exe (PID: 3992)
- flt_shovemydiscoupyourarse.exe (PID: 664)
- AttributeString.exe (PID: 1816)
- hv.exe (PID: 1584)
- RegAsm.exe (PID: 2836)
- VLTKNhatRac.exe (PID: 2184)
- InstallUtil.exe (PID: 2004)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2628)
- svchost.exe (PID: 3436)
- vbc.exe (PID: 3644)
- crypted.exe (PID: 3600)
- 4363463463464363463463463.exe (PID: 1384)
- EchoNavigator.exe (PID: 2304)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
- amert.exe (PID: 3724)
- alex.exe (PID: 1860)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- goldprimesupp.exe (PID: 1592)
- RegAsm.exe (PID: 2312)
- Helper.exe (PID: 2776)
- NeonRank.exe (PID: 3444)
- Taxes.pif (PID: 3436)
- Cheat.tmp (PID: 2248)
- plugins.exe (PID: 2156)
- dffdfdf.exe (PID: 1992)
- crpta.exe (PID: 2172)
- InstallUtil.exe (PID: 2984)
- windows.exe (PID: 1624)
- 2024.exe (PID: 3244)
- file.exe (PID: 3868)
- Amadey.exe (PID: 3572)
- Carpet.pif (PID: 3880)
- VLTKTanthuTN.exe (PID: 3628)
- InstallSetup2.exe (PID: 3000)
- Awwnbpxqsf.exe (PID: 3892)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- asdfg.exe (PID: 2624)
- BBLb.exe (PID: 2208)
- BBLb.exe (PID: 748)
- America.pif (PID: 2576)
- gold1201001.exe (PID: 3236)
- jsc.exe (PID: 2760)
- cp.exe (PID: 3992)
- niks.exe (PID: 3936)
- flt_shovemydiscoupyourarse.exe (PID: 664)
- AttributeString.exe (PID: 1816)
- 2.3.1.1.exe (PID: 952)
- hv.exe (PID: 1584)
- VLTKNhatRac.exe (PID: 2184)
- RegAsm.exe (PID: 2836)
- InstallUtil.exe (PID: 2004)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2628)
- 4363463463464363463463463.exe (PID: 1384)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
- RegAsm.exe (PID: 2312)
- Helper.exe (PID: 2776)
- VLTKTanthuTN.exe (PID: 3628)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- jsc.exe (PID: 2760)
- InstallUtil.exe (PID: 2984)
- VLTKNhatRac.exe (PID: 2184)
- RegAsm.exe (PID: 2836)
- InstallUtil.exe (PID: 2004)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2628)
- vbc.exe (PID: 3644)
- 4363463463464363463463463.exe (PID: 1384)
- EchoNavigator.exe (PID: 2304)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 1696)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- RegAsm.exe (PID: 2312)
- Helper.exe (PID: 2776)
- alex.exe (PID: 1860)
- dffdfdf.exe (PID: 1992)
- crpta.exe (PID: 2172)
- plugins.exe (PID: 2156)
- InstallUtil.exe (PID: 2984)
- 2024.exe (PID: 3244)
- file.exe (PID: 3868)
- windows.exe (PID: 1624)
- VLTKTanthuTN.exe (PID: 3628)
- InstallSetup2.exe (PID: 3000)
- Awwnbpxqsf.exe (PID: 3892)
- Amadey.exe (PID: 3572)
- npp.8.6.2.Installer.x64.exe (PID: 3976)
- asdfg.exe (PID: 2624)
- BBLb.exe (PID: 2208)
- gold1201001.exe (PID: 3236)
- BBLb.exe (PID: 748)
- jsc.exe (PID: 2760)
- 2.3.1.1.exe (PID: 952)
- cp.exe (PID: 3992)
- AttributeString.exe (PID: 1816)
- hv.exe (PID: 1584)
- VLTKNhatRac.exe (PID: 2184)
- RegAsm.exe (PID: 2836)
- InstallUtil.exe (PID: 2004)
Create files in a temporary directory
- 4363463463464363463463463.exe (PID: 2628)
- EchoNavigator.exe (PID: 2304)
- amert.exe (PID: 3724)
- NeonRank.exe (PID: 3444)
- plugins.exe (PID: 2156)
- AquariumScreening.exe (PID: 2828)
- Amadey.exe (PID: 3572)
- Cheat.exe (PID: 1236)
- firefoxsunny.exe (PID: 1796)
- npp86Installerx64.exe (PID: 2124)
- asdfg.exe (PID: 2624)
- jsc.exe (PID: 2760)
- Carpet.pif (PID: 3880)
- niks.exe (PID: 3936)
- InstallUtil.exe (PID: 2004)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 3368)
- 4363463463464363463463463.exe (PID: 1384)
- cmd.exe (PID: 2260)
- jsc.exe (PID: 2760)
Creates files in the program directory
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 3984)
- iexplore.exe (PID: 568)
- Cheat.tmp (PID: 2248)
- RegAsm.exe (PID: 2836)
Checks proxy server information
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 2176)
- InstallUtil.exe (PID: 2984)
- 2.3.1.1.exe (PID: 952)
Reads product name
- RegAsm.exe (PID: 2312)
- InstallUtil.exe (PID: 2984)
- InstallUtil.exe (PID: 2004)
Creates files or folders in the user directory
- Helper.exe (PID: 2776)
- InstallUtil.exe (PID: 2984)
- Carpet.pif (PID: 3880)
- America.pif (PID: 2576)
- BBLb.exe (PID: 748)
- Awwnbpxqsf.exe (PID: 3892)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3688)
Reads mouse settings
- Taxes.pif (PID: 3436)
- Carpet.pif (PID: 3880)
- America.pif (PID: 2576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(3600) crypted.exe
C2185.99.133.246
Options
LummaIDNMlPqS
BuildLummaC2, Build 20233101
RedLine
(PID) Process(3644) vbc.exe
C2 (2)chardhesha.xyz:81
jalocliche.xyz:81
Botneteasy11211
Options
ErrorMessage
Keys
XorScleral
(PID) Process(1860) alex.exe
C2 (1)185.172.128.33:8924
Botnet@oleh_ps
Options
ErrorMessage
Keys
XorPutschist
(PID) Process(3244) 2024.exe
C2 (1)195.20.16.103:20440
Botnet2024
Options
ErrorMessage
Keys
XorSitfast
AsyncRat
(PID) Process(1624) windows.exe
C2 (2)127.0.0.1
185.169.180.209
Ports (1)1604
BotnetDefault
Version1.0.7
Options
AutoRunfalse
MutexDcRatMutex_qwqdanchun
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICKTCCAZKgAwIBAgIVAJLa5o5uunlhTPkS6D+ElxUOlWixMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBWRldmlsMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjIxMjA3MTIyMDQ2WhcNMzMwOTE1MTIyMDQ2WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_Signaturea/vMif/Q/wROCLRLshsH5tdoi+Vlji48gVFCa2VO+0Mi3MT8STZSGo95k4fDVFGiTiIGr7B2EhGwgMykEzcIVzPu+MHddHH9o1DoVp70IcluTvaqbnwP6R0/XXw895bcG1+IddLTw9afHFS1e3DA9Lea3idYXBHpMtuN0qmg/i0=
Keys
AES3090d3c207571fa6adc20ce48c901a29e80712e1d8b4ac5e633b2fa213ce8d20
SaltDcRatByqwqdanchun
Raccoon
(PID) Process(952) 2.3.1.1.exe
C2 (1)http://185.16.39.253:80
Keys
xorafed87781b48070c555e77a16d871208
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
232
Monitored processes
128
Malicious processes
37
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Users\admin\Desktop\Files\%E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe" | C:\Users\admin\Desktop\Files\%E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: 天降激光炮(Www.Tianxwl.Com) Integrity Level: HIGH Description: 天降之激光炮 Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
| 296 | C:\Windows\system32\ipconfig.exe | C:\Windows\System32\ipconfig.exe | America.pif | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 492 | C:\Users\admin\Desktop\Files\asdfg.exe | C:\Users\admin\Desktop\Files\asdfg.exe | — | asdfg.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 560 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | DesktopLayer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 4294967295 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 568 | C:\Users\admin\Desktop\Files\asdfg.exe | C:\Users\admin\Desktop\Files\asdfg.exe | — | asdfg.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\Desktop\Files\flt_shovemydiscoupyourarse.exe" | C:\Users\admin\Desktop\Files\flt_shovemydiscoupyourarse.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 712 | cmd /c copy /b Learn + Did + Chorus 11183\c | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 712 | C:\Users\admin\Desktop\Files\Awwnbpxqsf.exe | C:\Users\admin\Desktop\Files\Awwnbpxqsf.exe | — | Awwnbpxqsf.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
39 948
Read events
39 546
Write events
388
Delete events
14
Modification events
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 1400000001000000140000005D6CA352CEFC713CBBC5E21F663C3639FD19D4D70300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB60F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D8200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2628) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
92
Suspicious files
39
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2304 | EchoNavigator.exe | C:\Users\admin\AppData\Local\Temp\Echo Navigator\loading.gif | — | |
MD5:— | SHA256:— | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\AppData\Local\Temp\Tar5B83.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\cs_maltest.exe | executable | |
MD5:AB13D611D84B1A1D9FFBD21AC130A858 | SHA256:7B021B996B65F29CAE4896C11D3A31874E2D5C4CE8A7A212C8BEDF7DCAE0F8AE | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:CEF2ADCE525834CFAA0AB6CB37E64D2E | SHA256:00234C07AFE82B605C5CA1BC833A9656600A670B8CE10203133A550B476FB635 | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\loader.exe | executable | |
MD5:EB84BD84A313CF1D5FABB31294817A6D | SHA256:4B6F4B00740277A3F5739AD99672EDE8B0031C11313C5AC824D873EE506C9545 | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\new.exe | executable | |
MD5:BD5DFCF6A71E40A07B8B19BBE0A1A69B | SHA256:8752CC9BBA740D06FA96D7D409F6F936AB7E1F02CCD24C598C7BCEAF33BA9037 | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\AppData\Local\Temp\Cab5B82.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1384 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\EchoNavigator.exe | executable | |
MD5:5DF01F9E45F5E3C30A3534A4BE701AED | SHA256:BE569B1DC8758A791C81D7A4D9D653018E02F1206BC6E18D246A9D4DADE25D39 | |||
| 2628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\X1.exe | executable | |
MD5:528B0C3DA07891F258F33408EDB3B780 | SHA256:B5AD236F3AD54F2C46B4567892330C553FE20F8C0EA85F26FE47CBD88AA555D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
205
DNS requests
49
Threats
194
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2628 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.121:80 | http://185.172.128.121/svchost.exe | unknown | executable | 5.98 Mb | unknown |
2628 | 4363463463464363463463463.exe | GET | 200 | 47.99.151.68:1302 | http://47.99.151.68:1302/loader.exe | unknown | executable | 324 Kb | unknown |
2628 | 4363463463464363463463463.exe | GET | 200 | 47.99.151.68:1302 | http://47.99.151.68:1302/fscanPPP.exe | unknown | executable | 28.1 Mb | unknown |
2628 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/X1.exe | unknown | executable | 2.48 Mb | unknown |
2628 | 4363463463464363463463463.exe | GET | 403 | 185.88.60.242:80 | http://nerve.untergrund.net/releases/zorke_release/zorke_asciiverter_v1.00/zke-ascv.exe | unknown | html | 347 b | unknown |
1384 | 4363463463464363463463463.exe | GET | 200 | 211.97.81.229:80 | http://d1.udashi.com/soft/bgrj/5694/%E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe | unknown | executable | 968 Kb | unknown |
— | — | GET | 301 | 140.82.121.3:80 | http://github.com/macigaiga/cstest/raw/master/cs_maltest.exe | unknown | — | — | unknown |
1384 | 4363463463464363463463463.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/mine/amert.exe | unknown | executable | 1.81 Mb | unknown |
2176 | %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe | GET | — | 104.193.88.126:80 | http://hi.baidu.com/8youyu8888/item/eb4fbac9be30f77389ad9e99 | unknown | — | — | unknown |
1384 | 4363463463464363463463463.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/lego/alex.exe | unknown | executable | 1.73 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2628 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2628 | 4363463463464363463463463.exe | 193.233.132.167:80 | — | ATT-INTERNET4 | US | unknown |
2628 | 4363463463464363463463463.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2628 | 4363463463464363463463463.exe | 185.88.60.242:80 | nerve.untergrund.net | Nerdherrschaft GmbH | DE | unknown |
2628 | 4363463463464363463463463.exe | 185.172.128.121:80 | — | OOO Nadym Svyaz Service | RU | unknown |
2628 | 4363463463464363463463463.exe | 104.192.141.1:443 | bitbucket.org | AMAZON-02 | US | unknown |
2628 | 4363463463464363463463463.exe | 52.217.233.41:443 | bbuseruploads.s3.amazonaws.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| shared |
nerve.untergrund.net |
| unknown |
bitbucket.org |
| shared |
bbuseruploads.s3.amazonaws.com |
| shared |
1ecosolution.it |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
github.com |
| shared |
chardhesha.xyz |
| unknown |
jalocliche.xyz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2628 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
2628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING Suspicious svchost.exe in URI - Possible Process Dump/Trojan Download |
2628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
23 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
crypted.exe | cjPAklAQi13H263v1j7 |
crypted.exe | 228760fS035gg7F047o |
crypted.exe | 1b25CoNXS52S84Bv2jW |
crypted.exe | k2odLbKQG21iGbHJxp4 |
crypted.exe | 88W0D1a1bF0WVmQ0mW5 |
crypted.exe | hhMNk36uyy8u5FwtkMd |
crypted.exe | YIPoM7y866D1p3j3cQp |