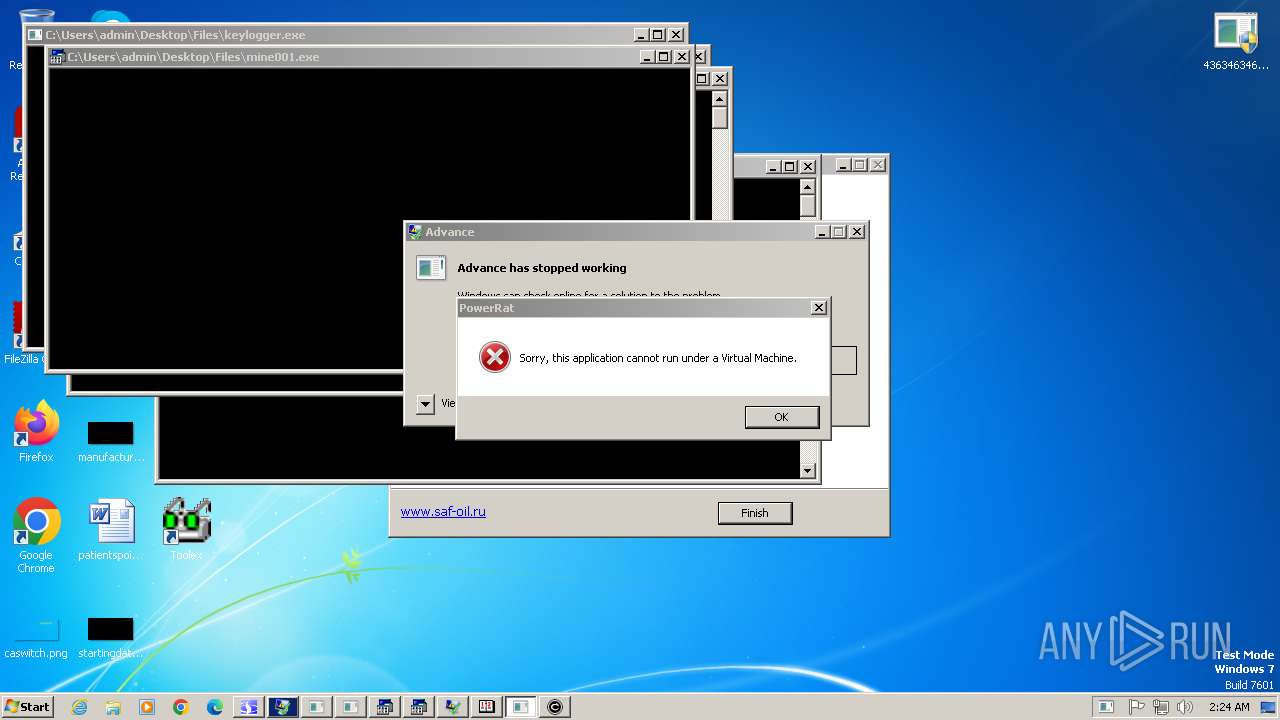
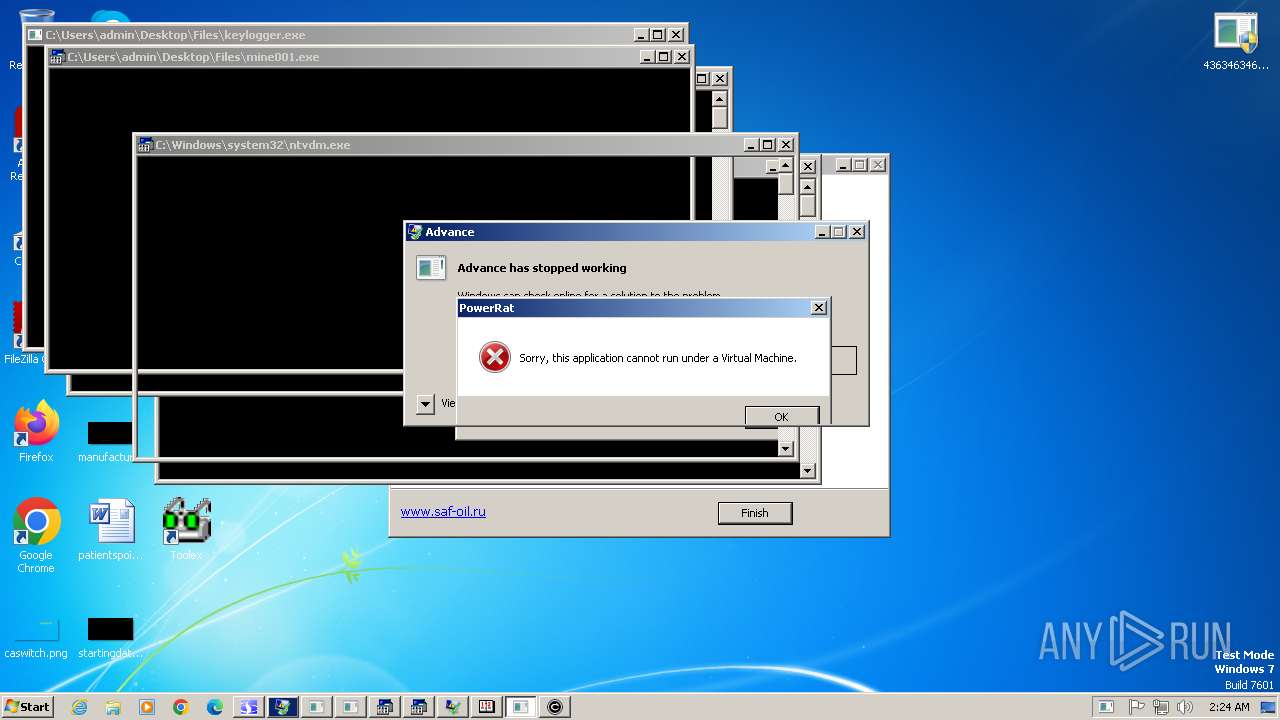
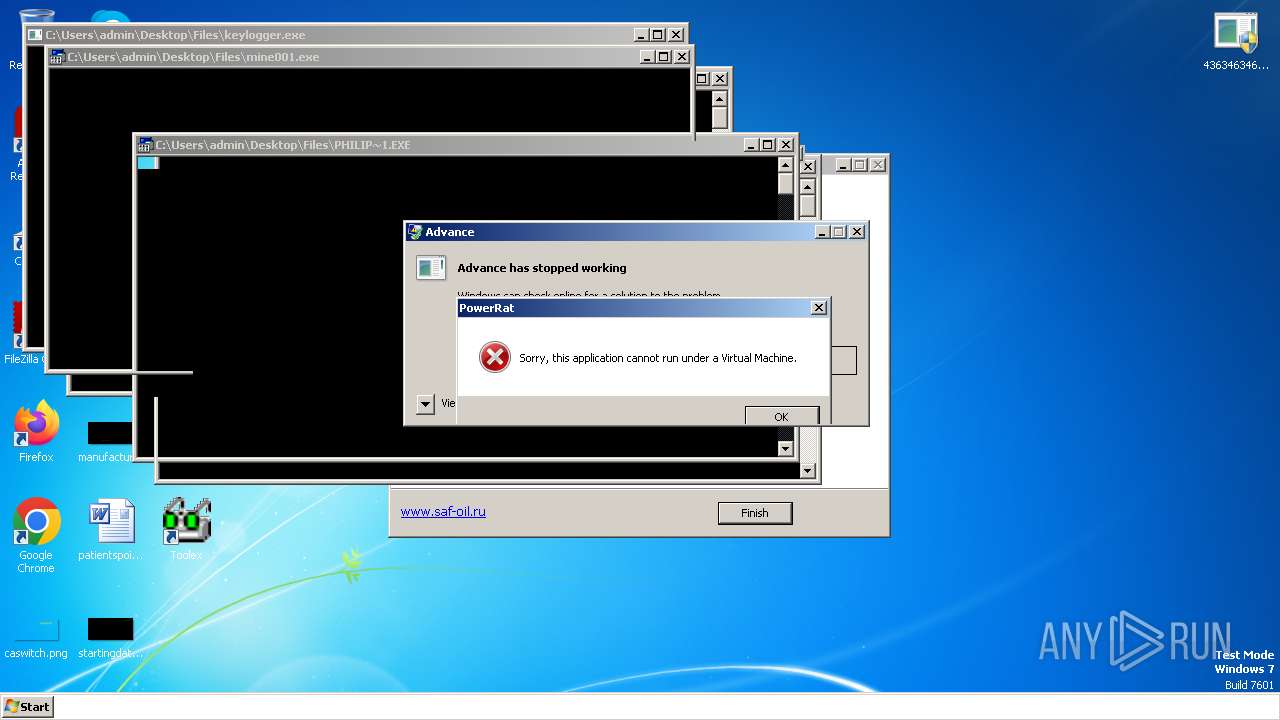
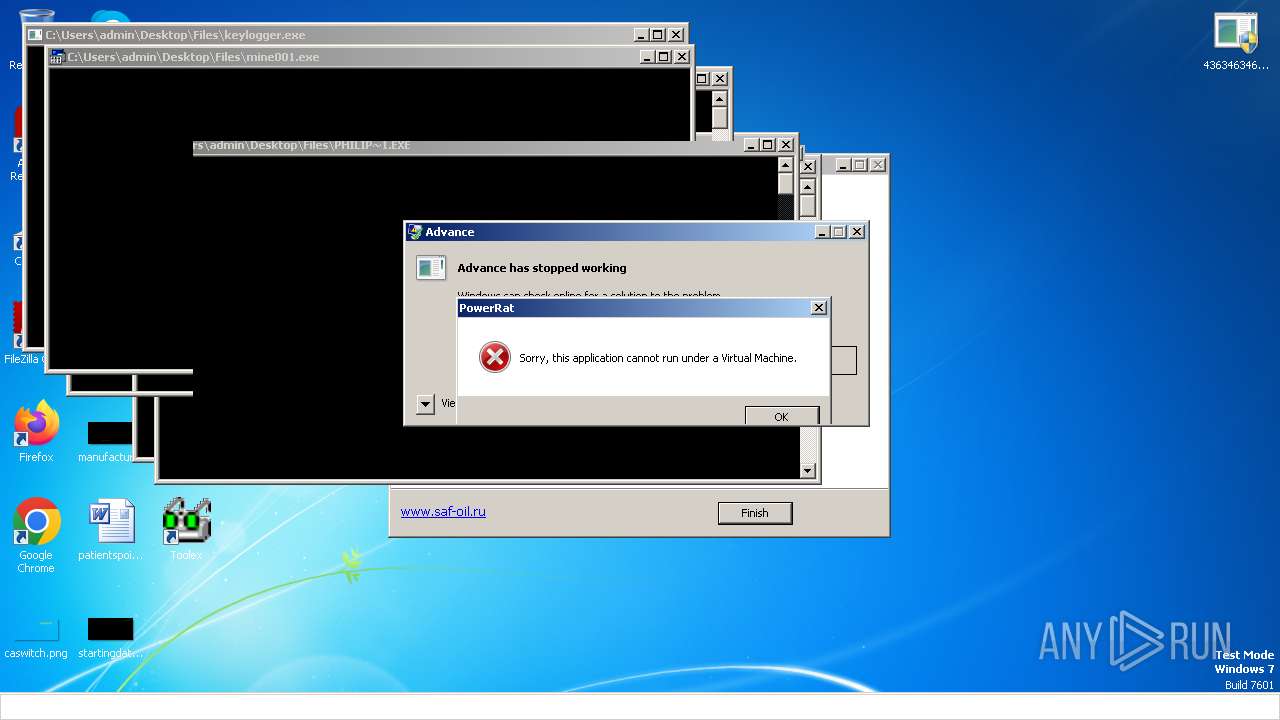
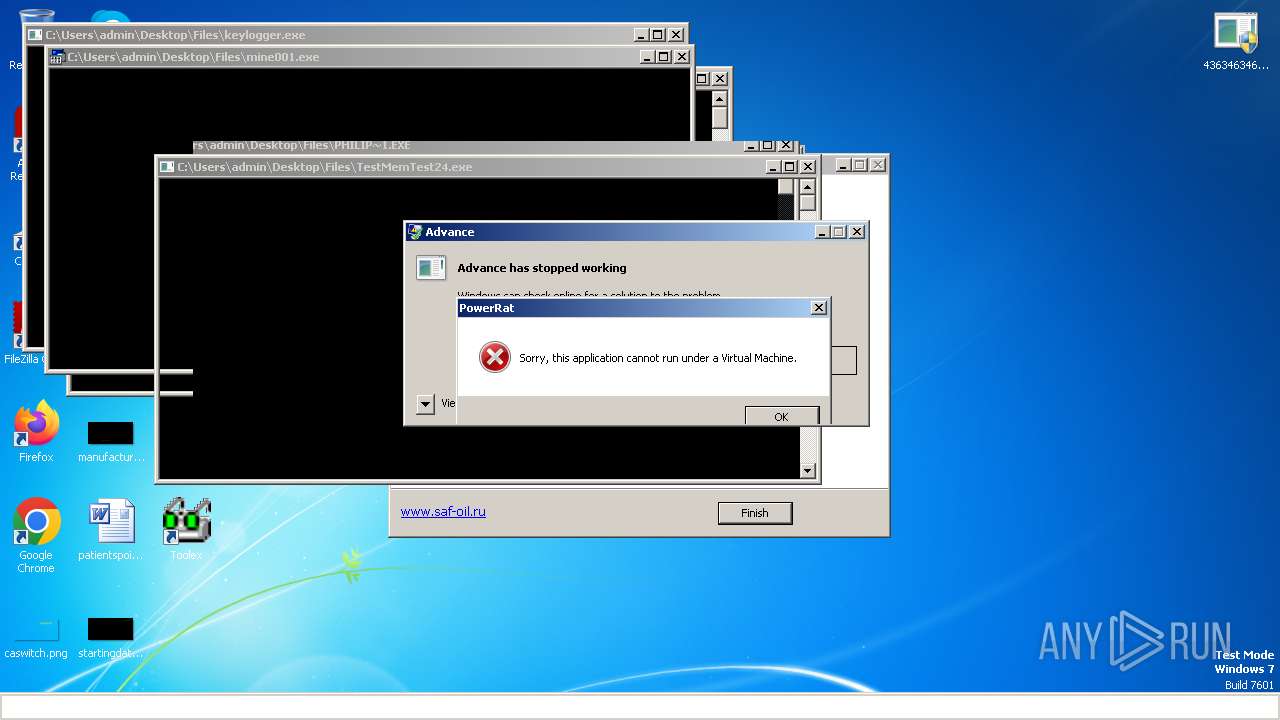
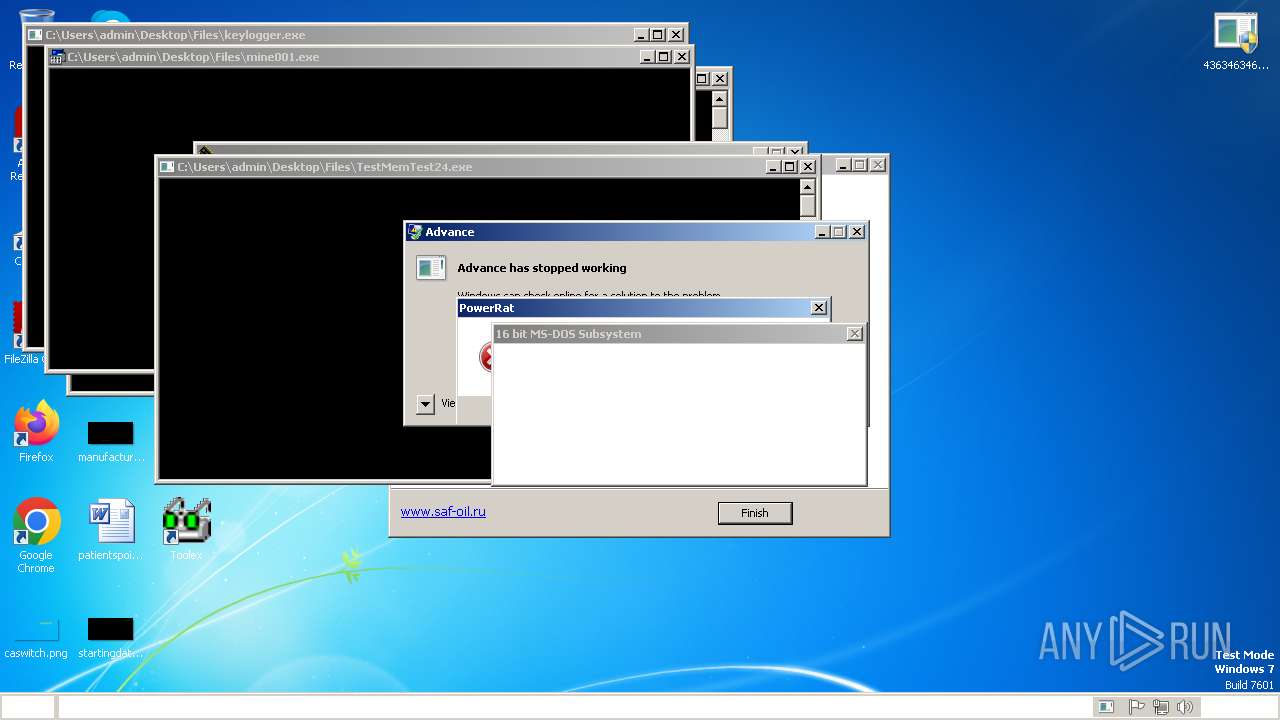
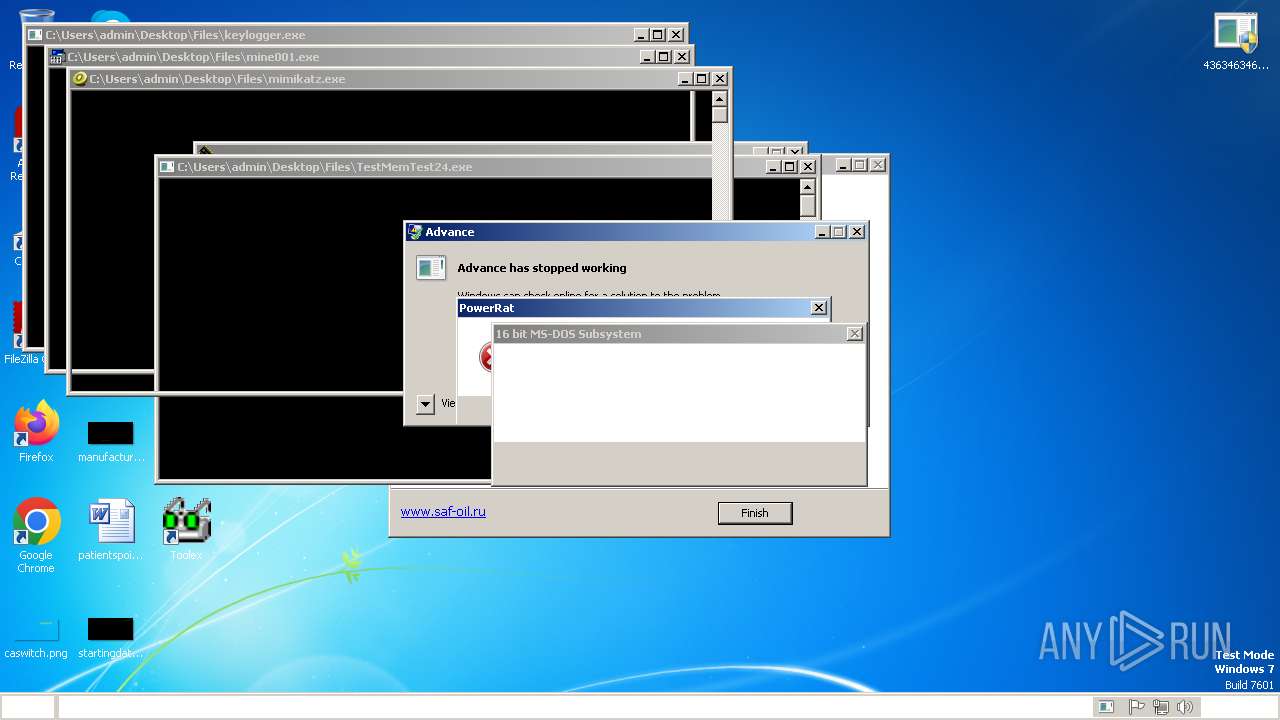
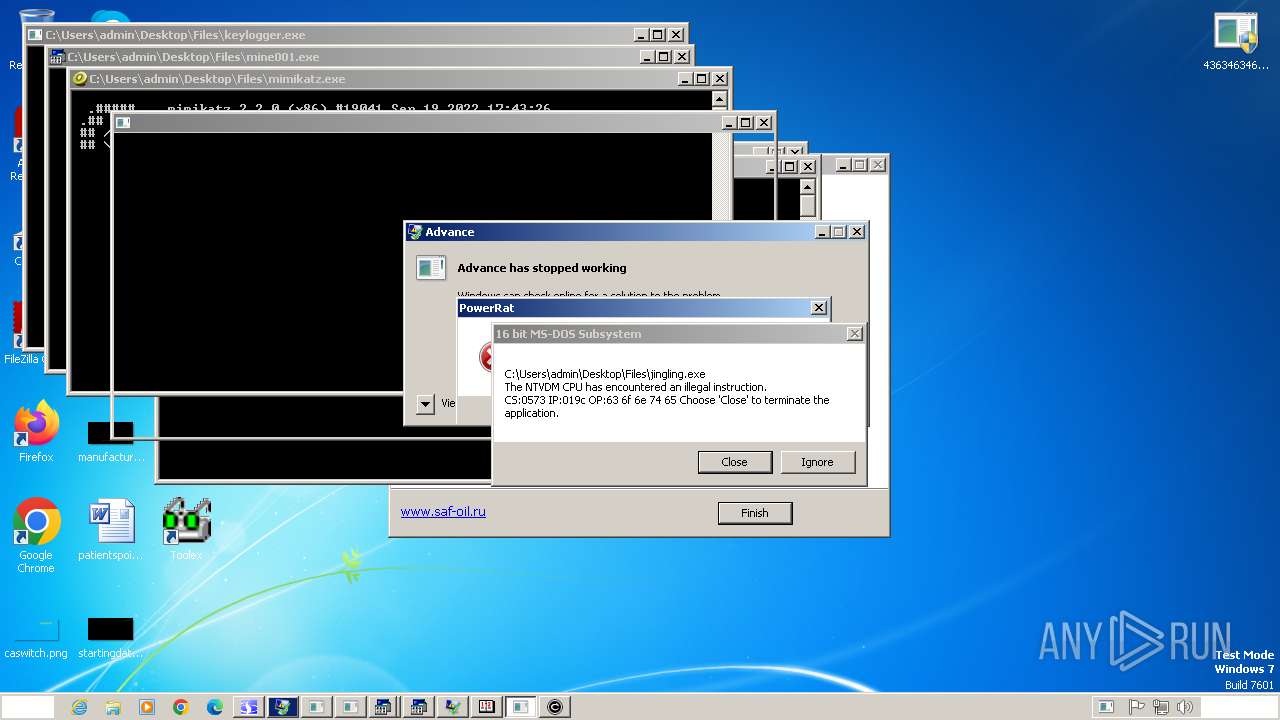
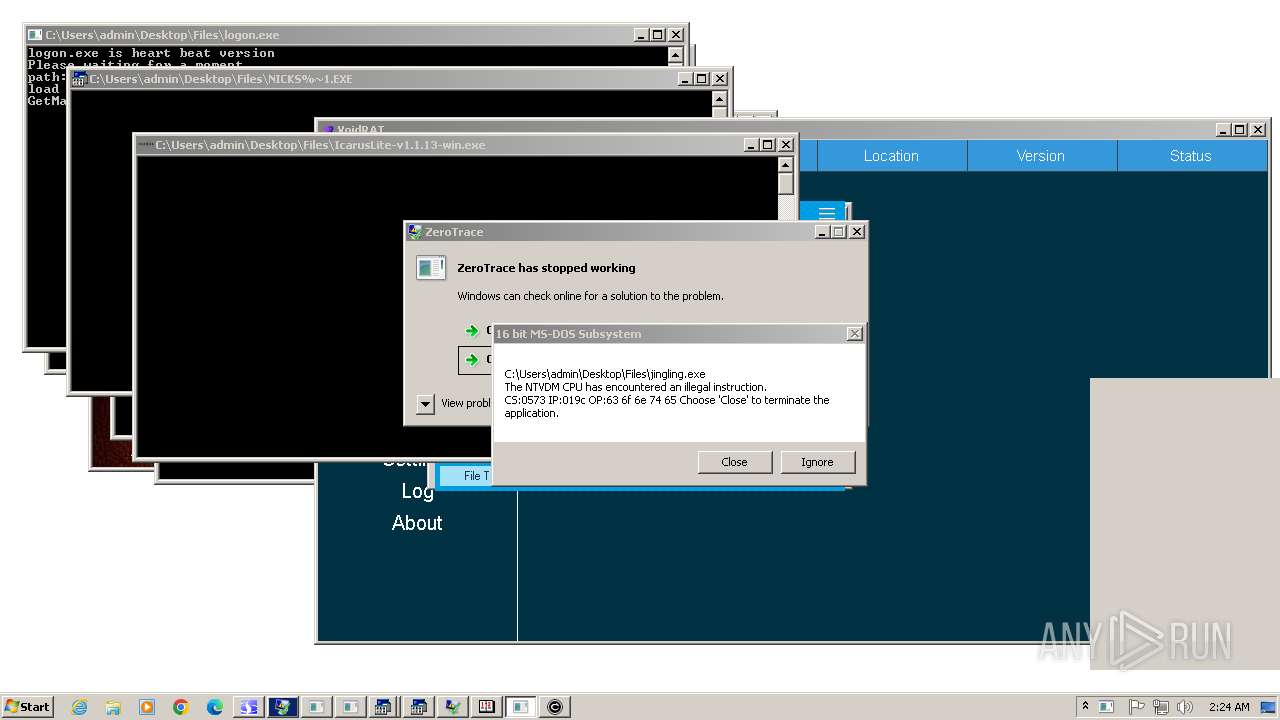
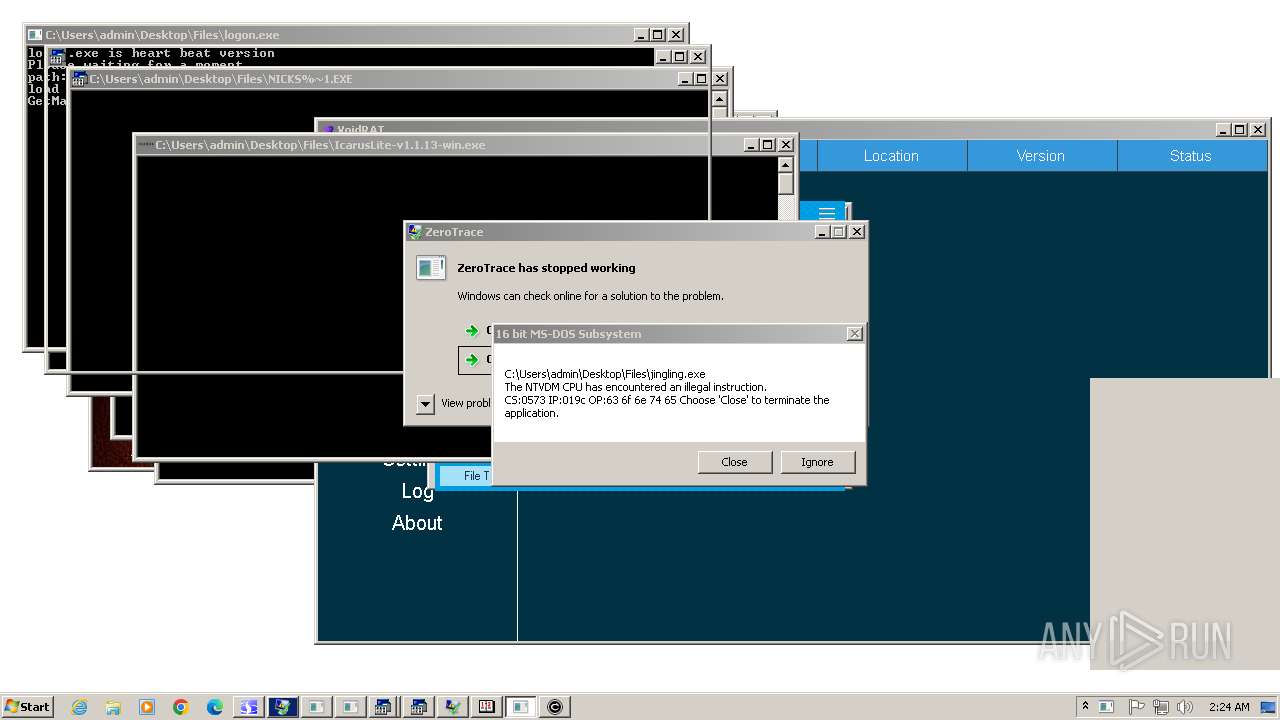
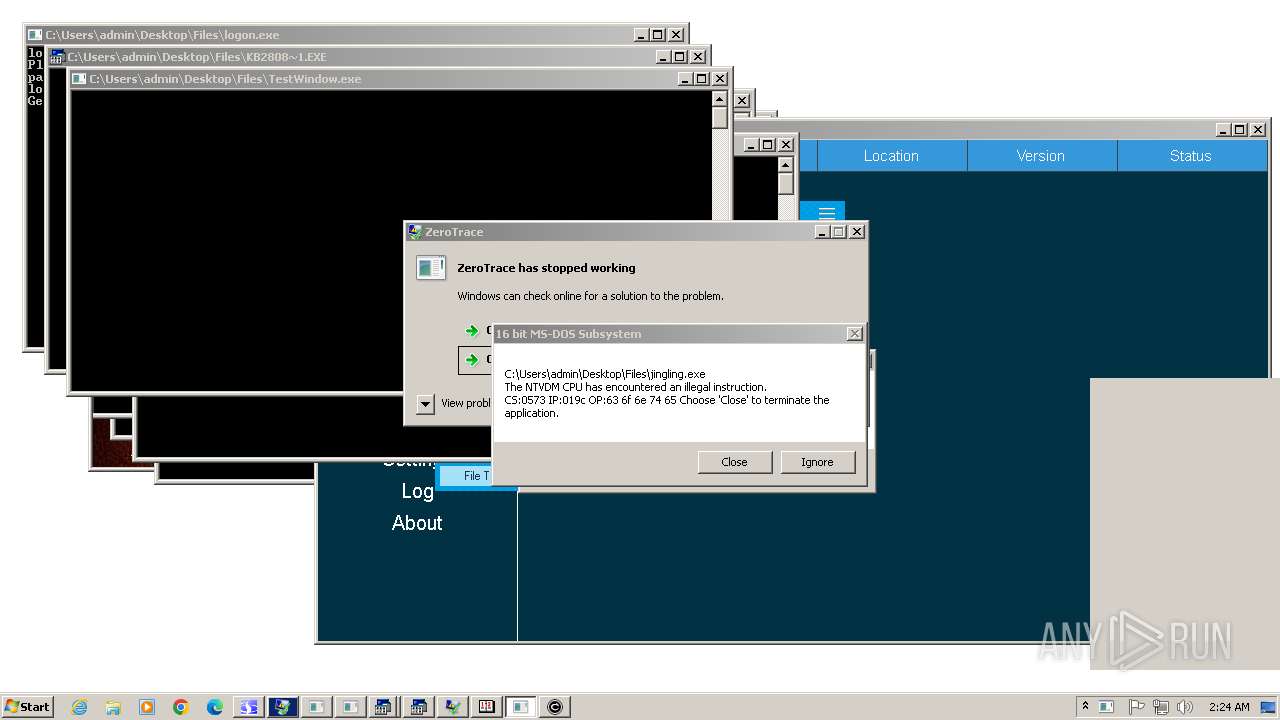
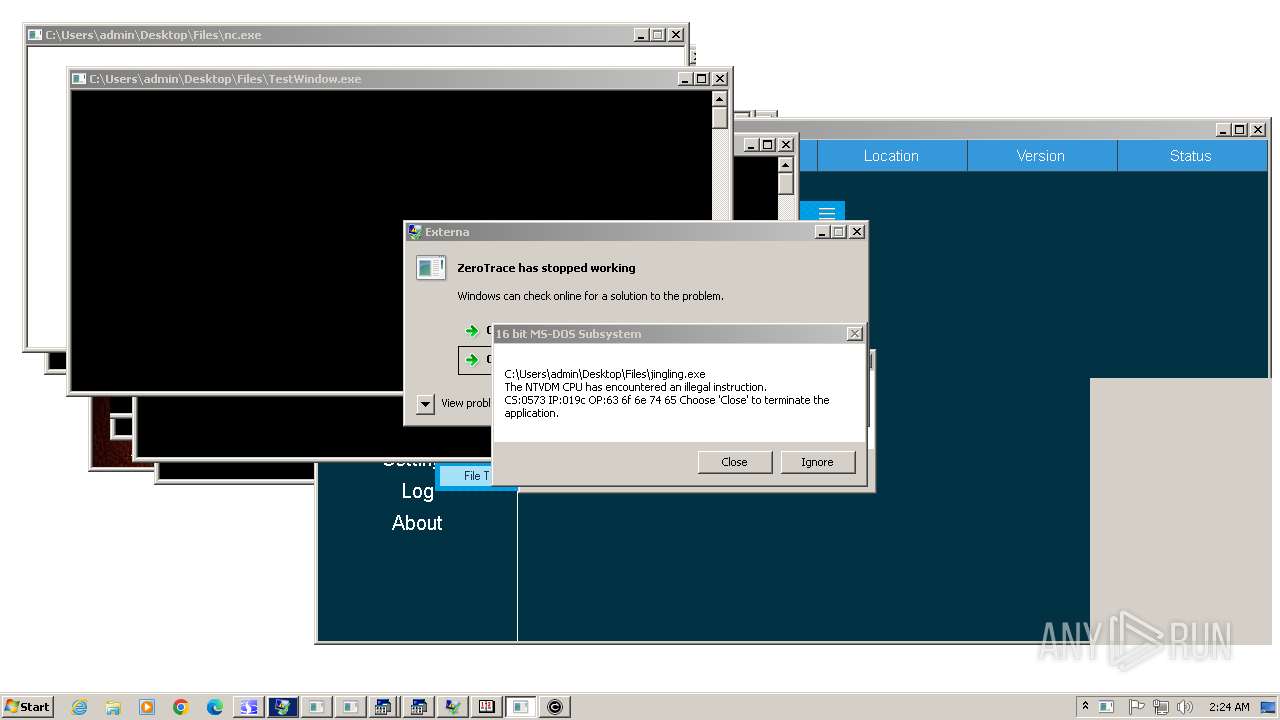
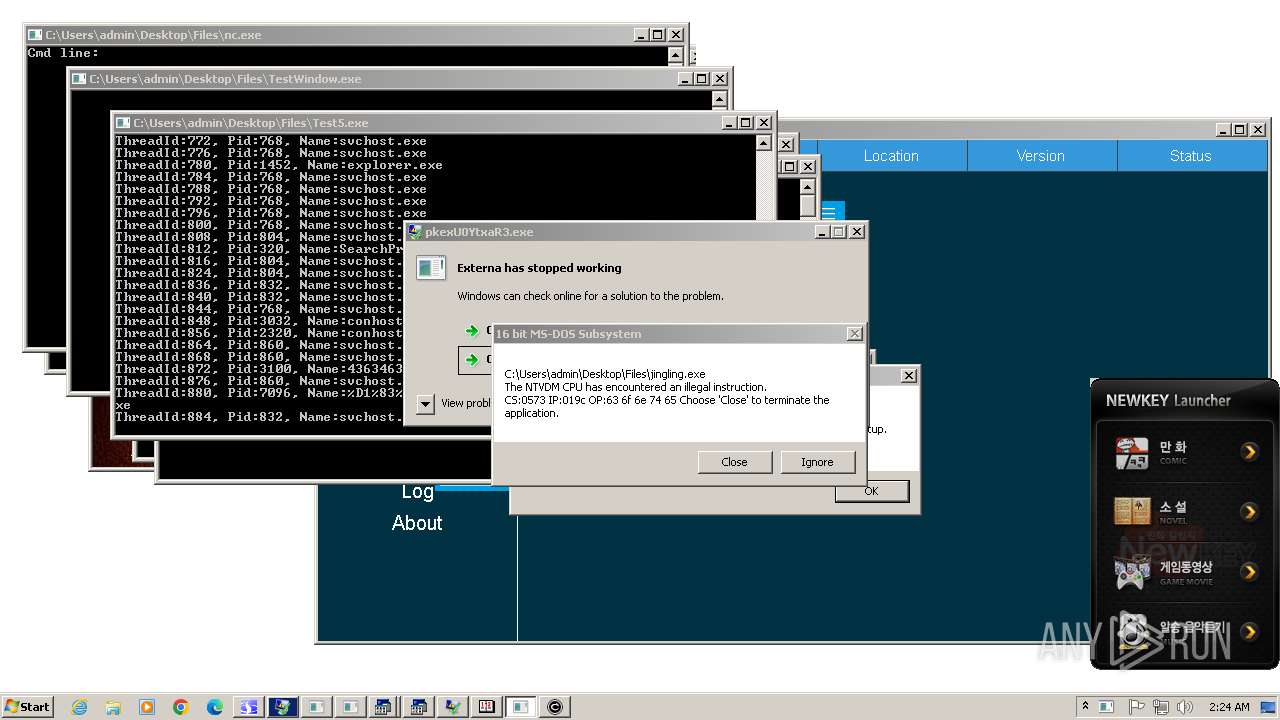
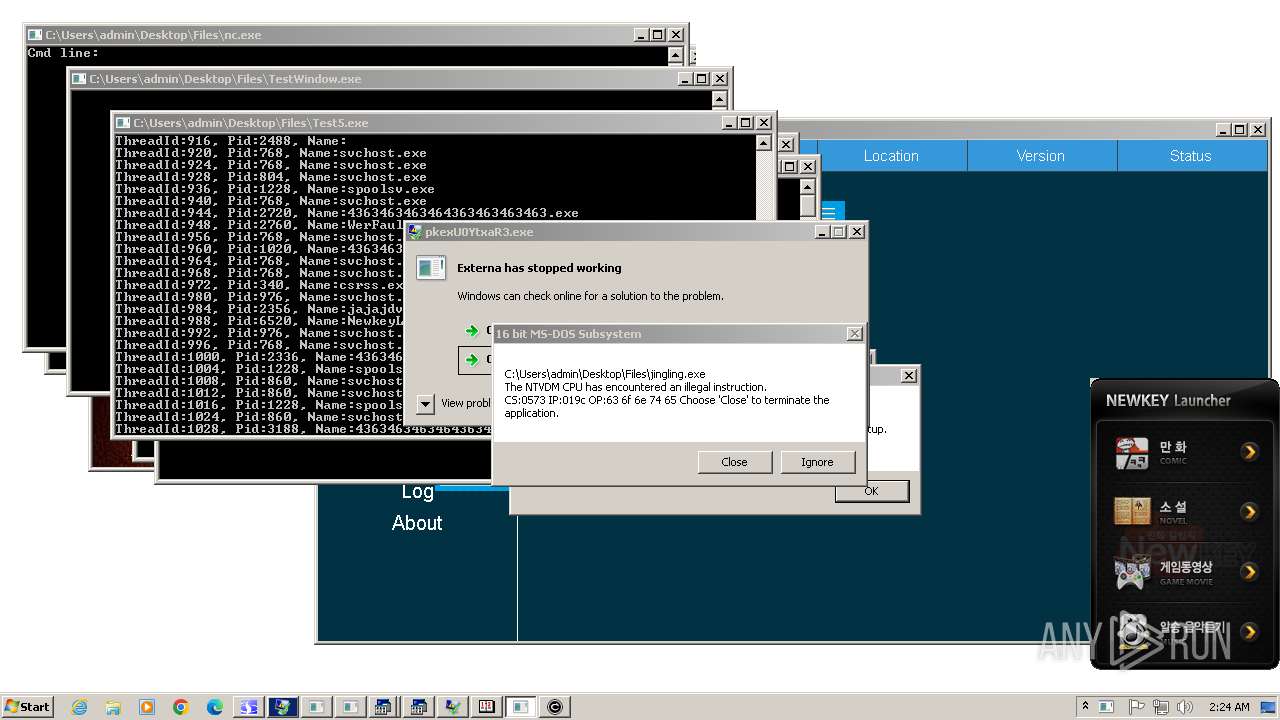
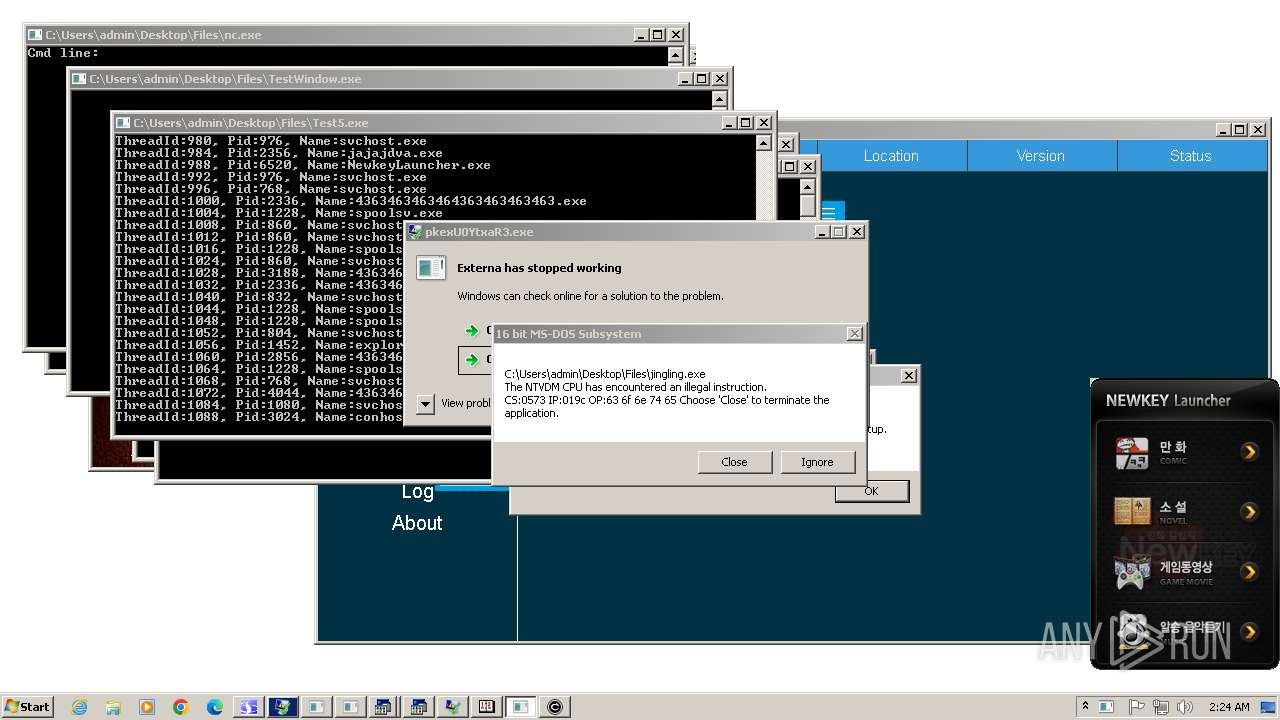
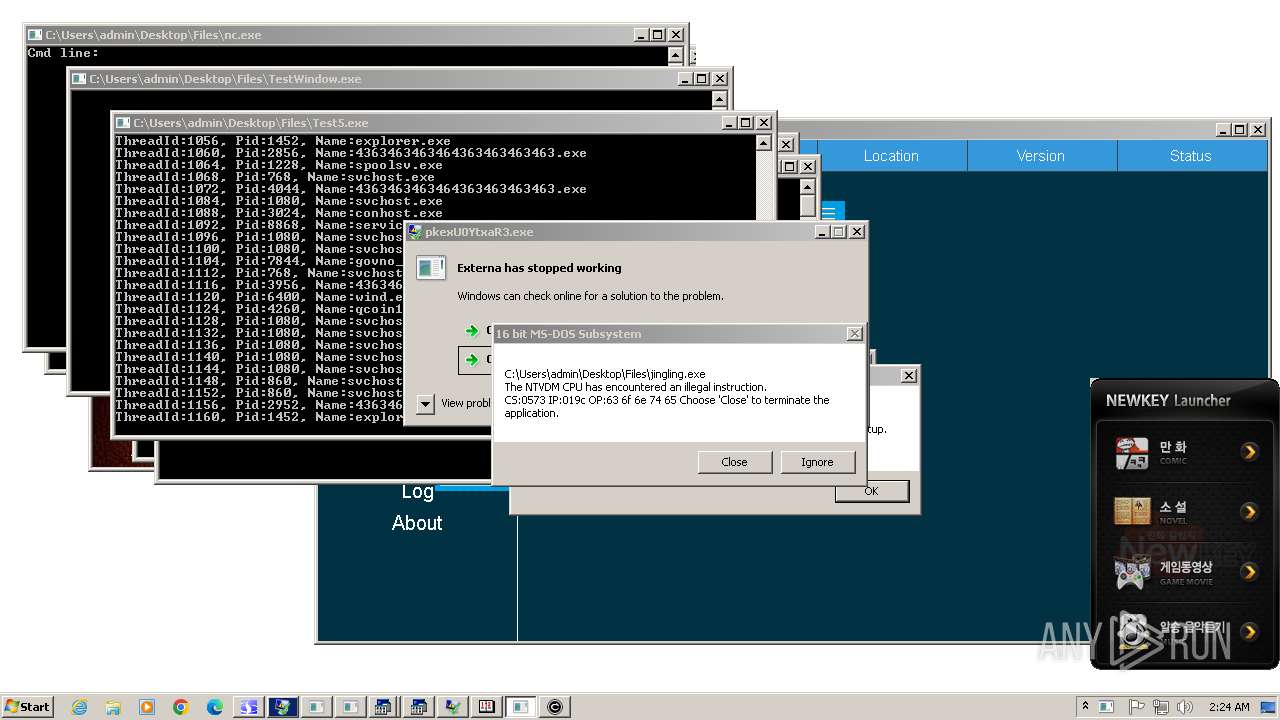
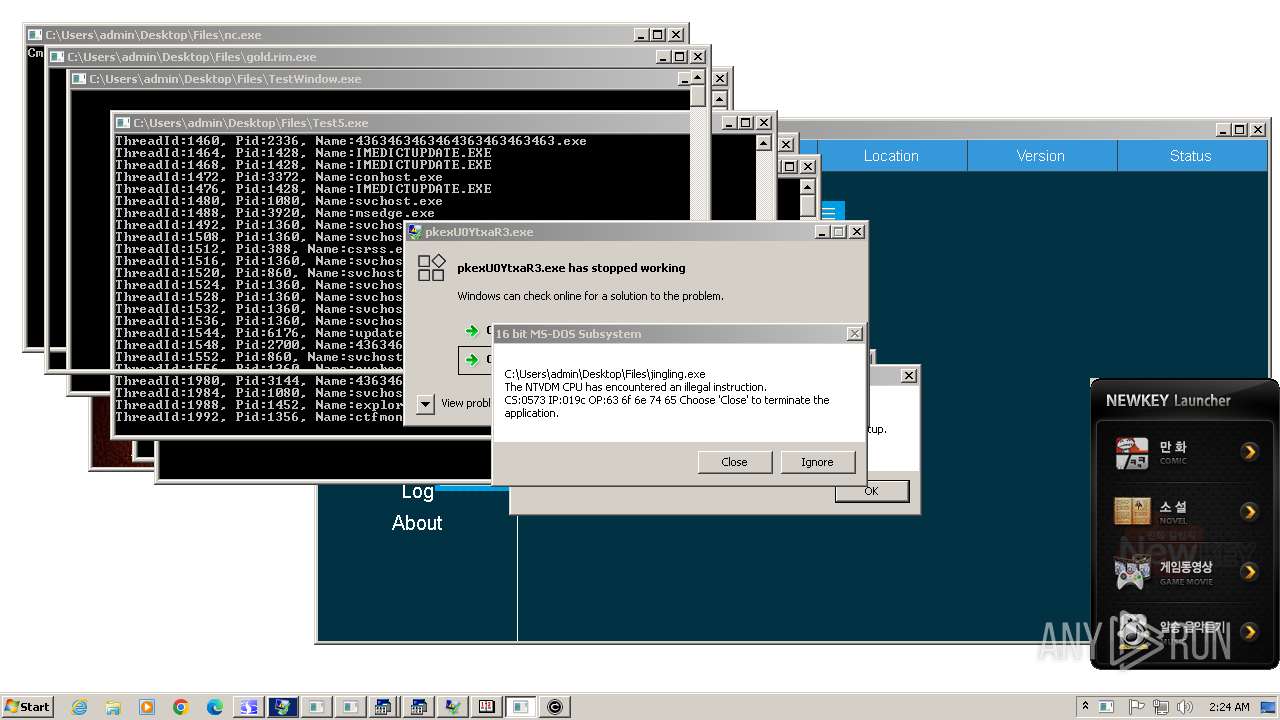
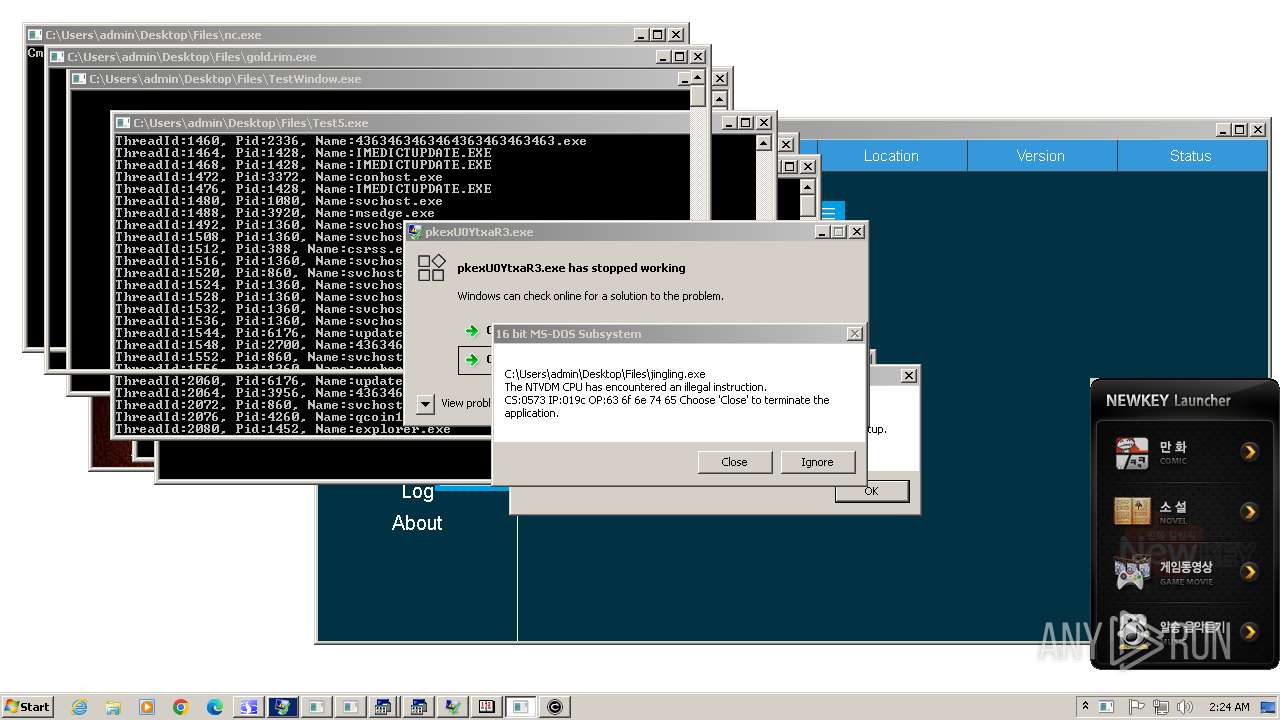
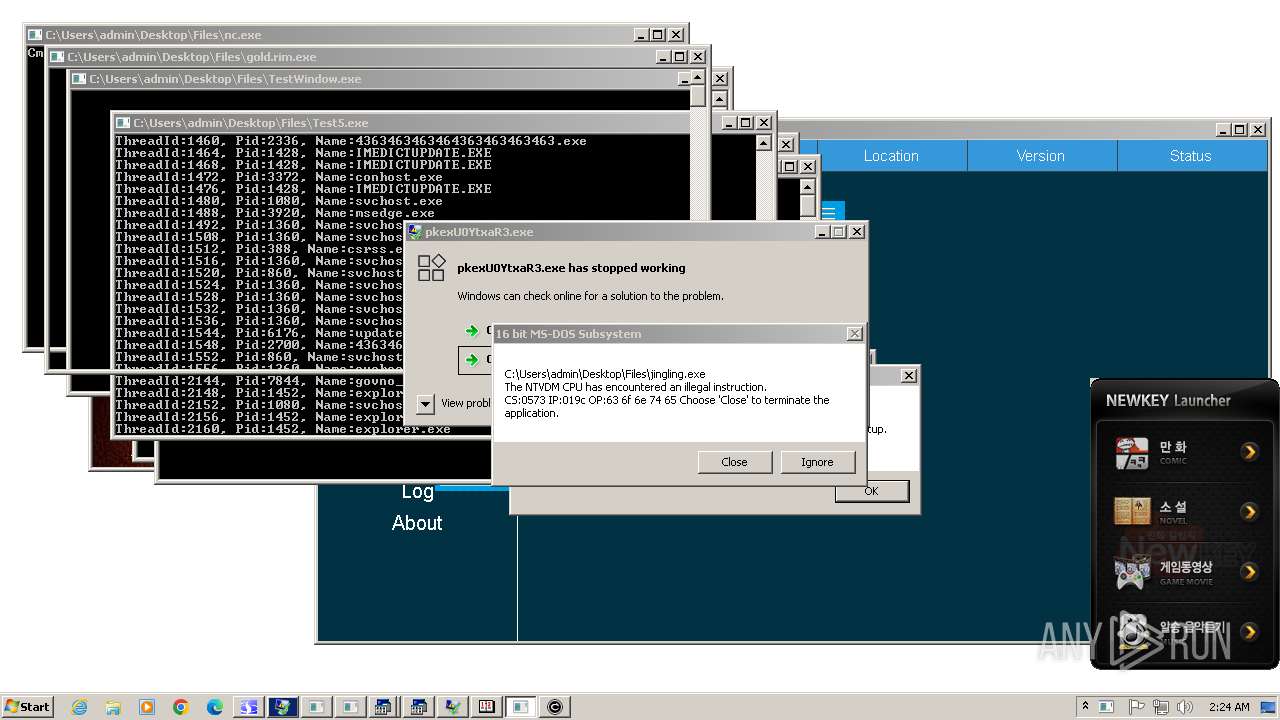
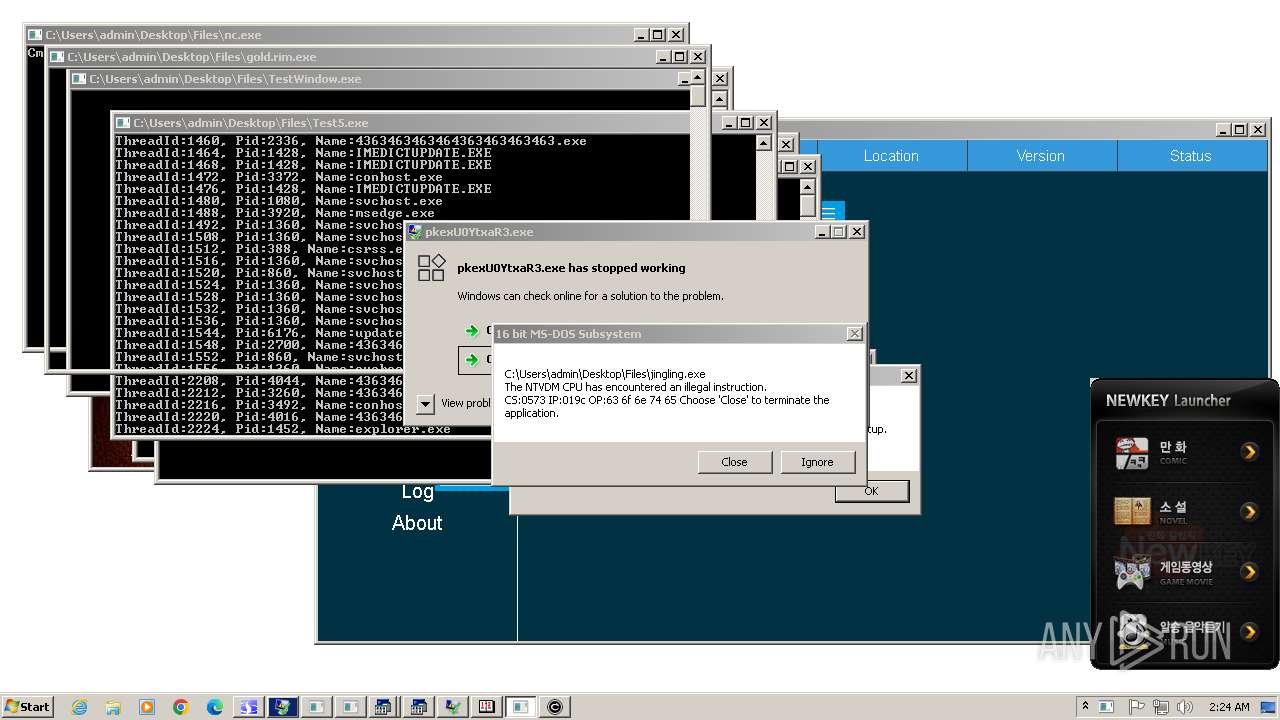
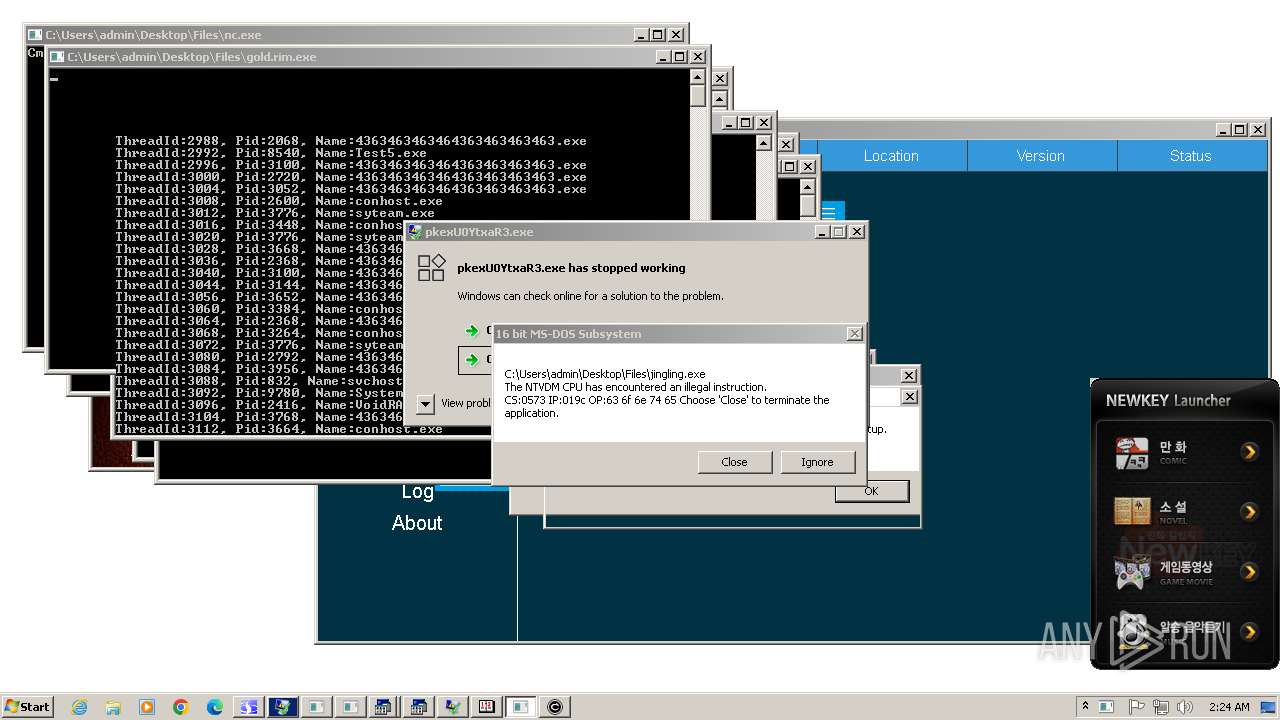
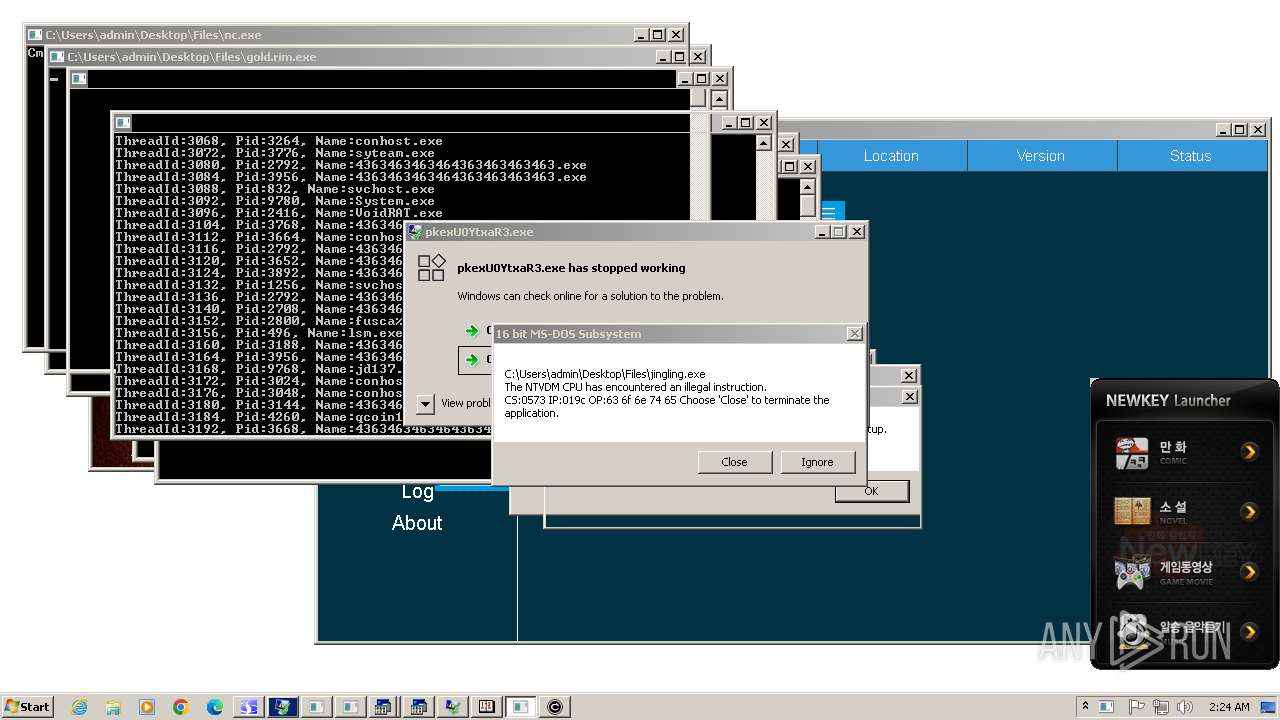
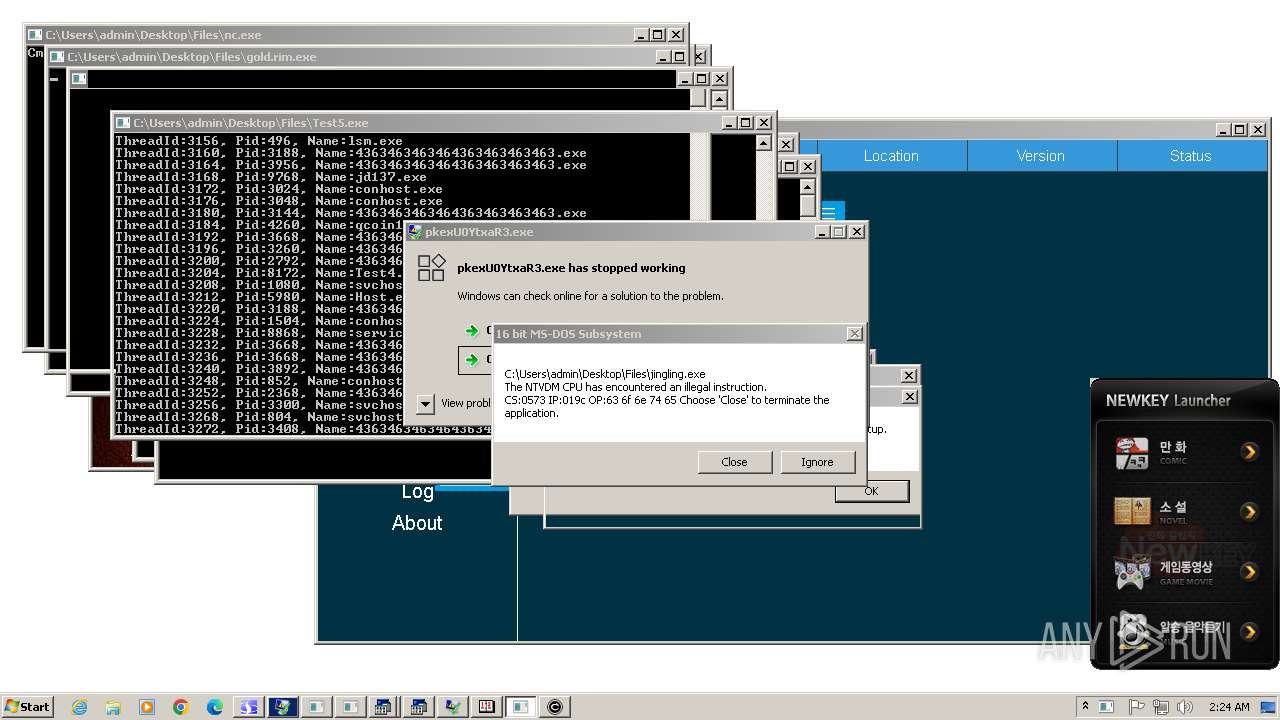
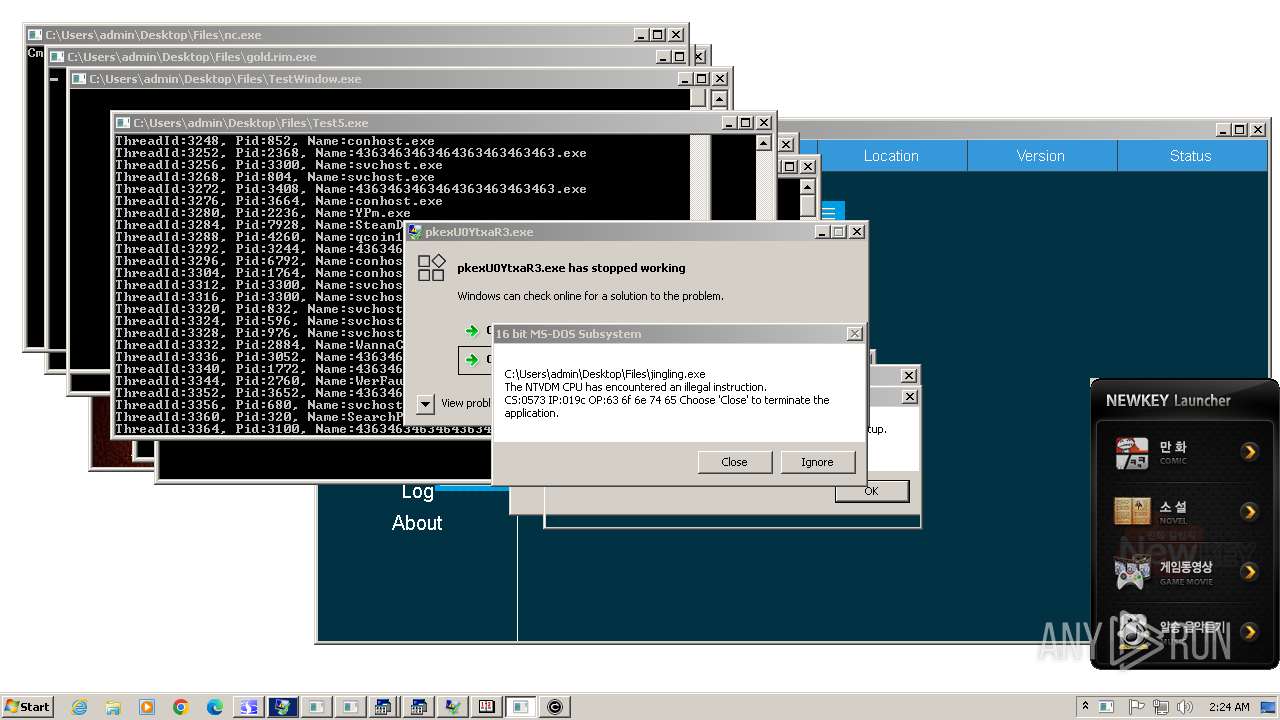
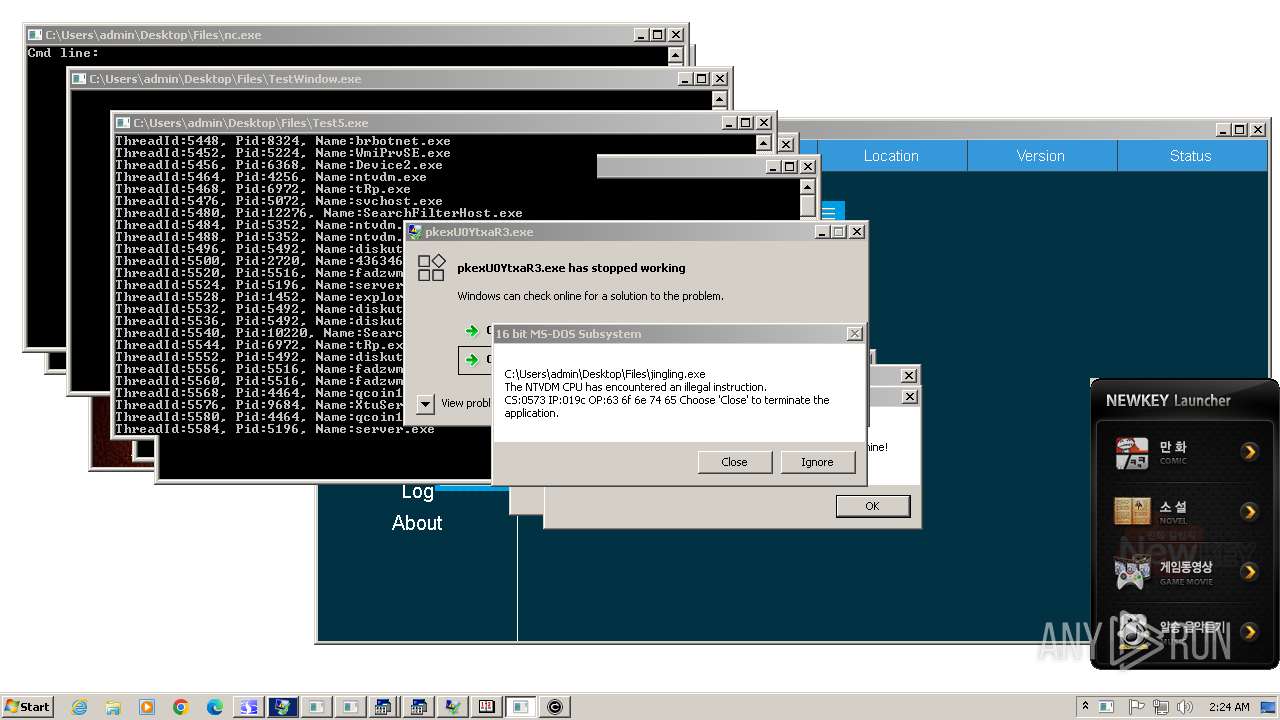
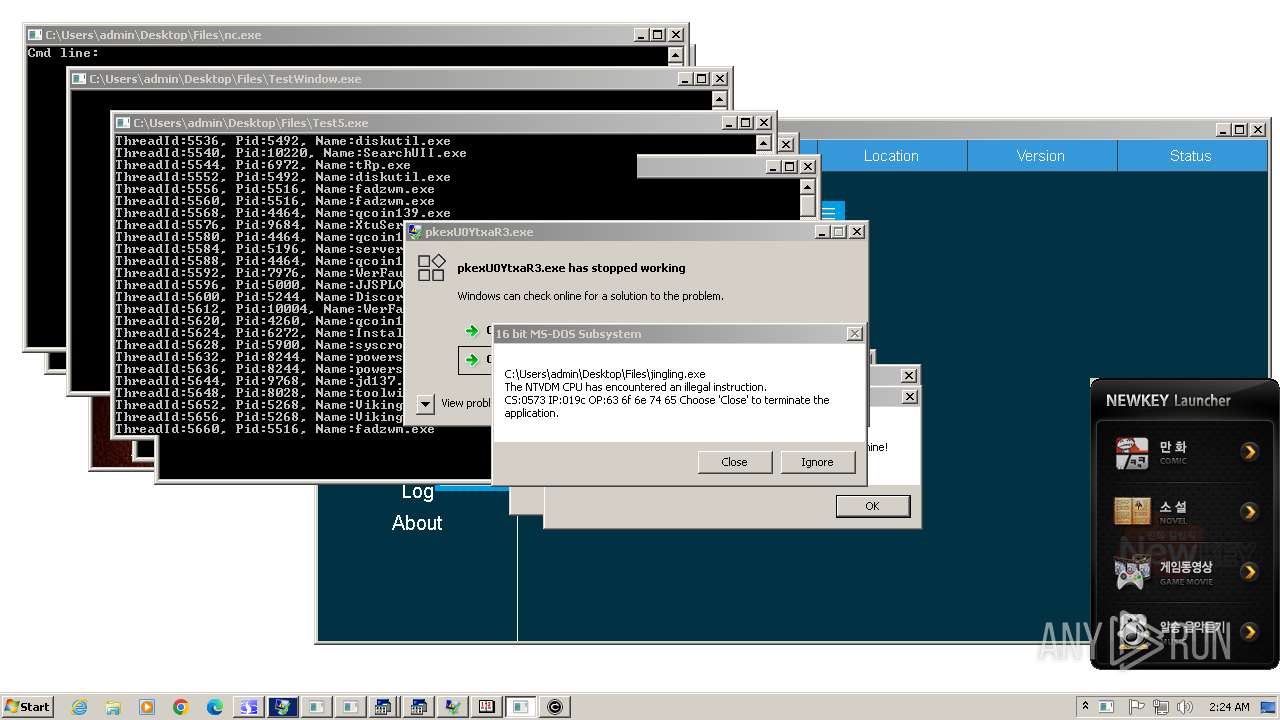
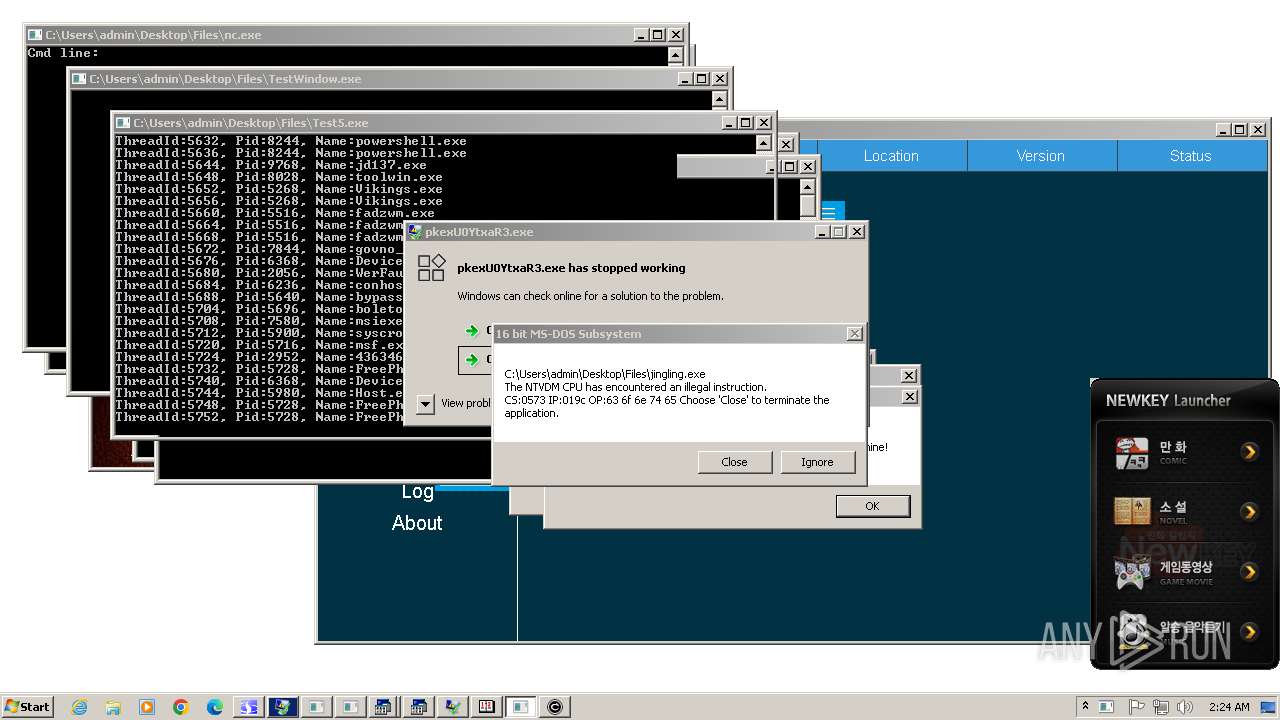
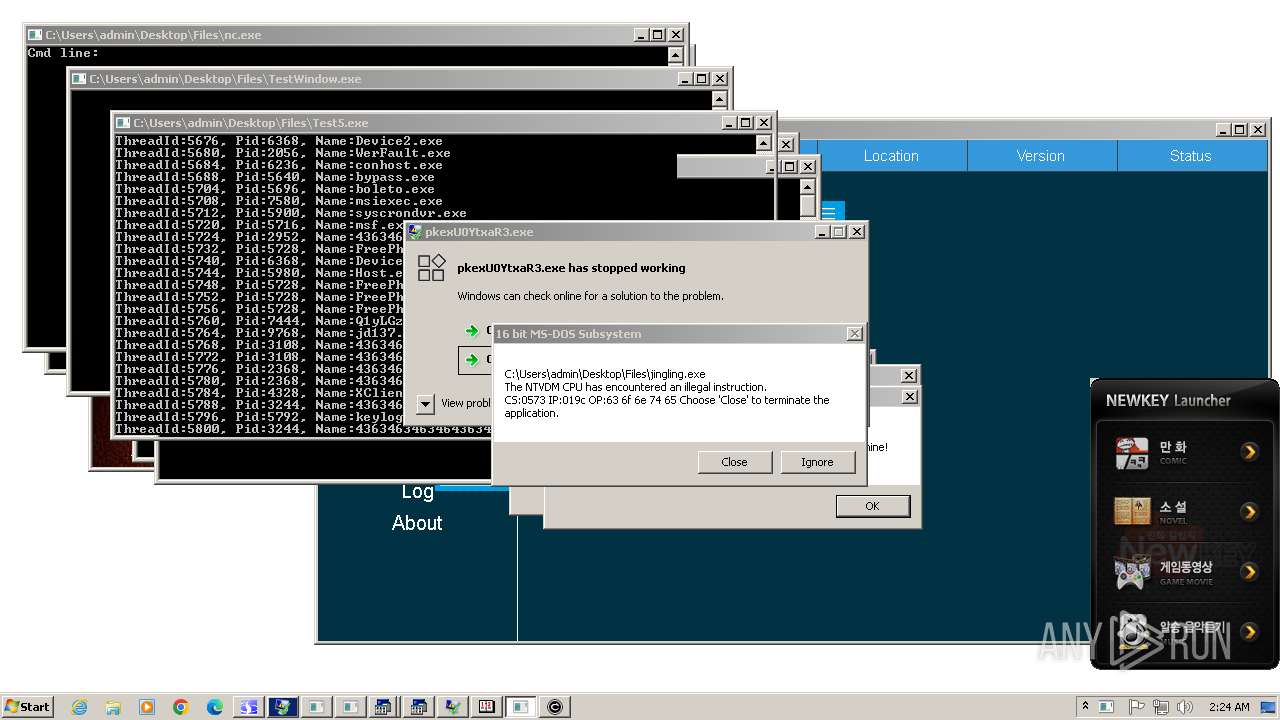
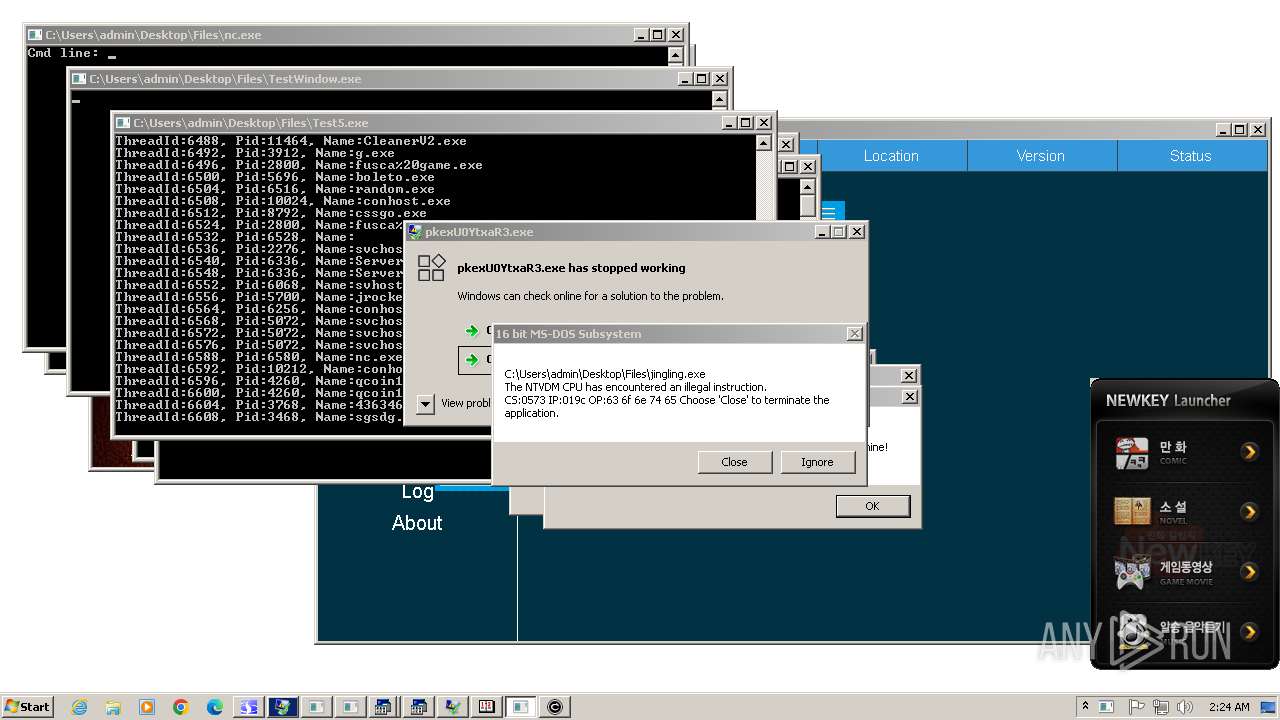
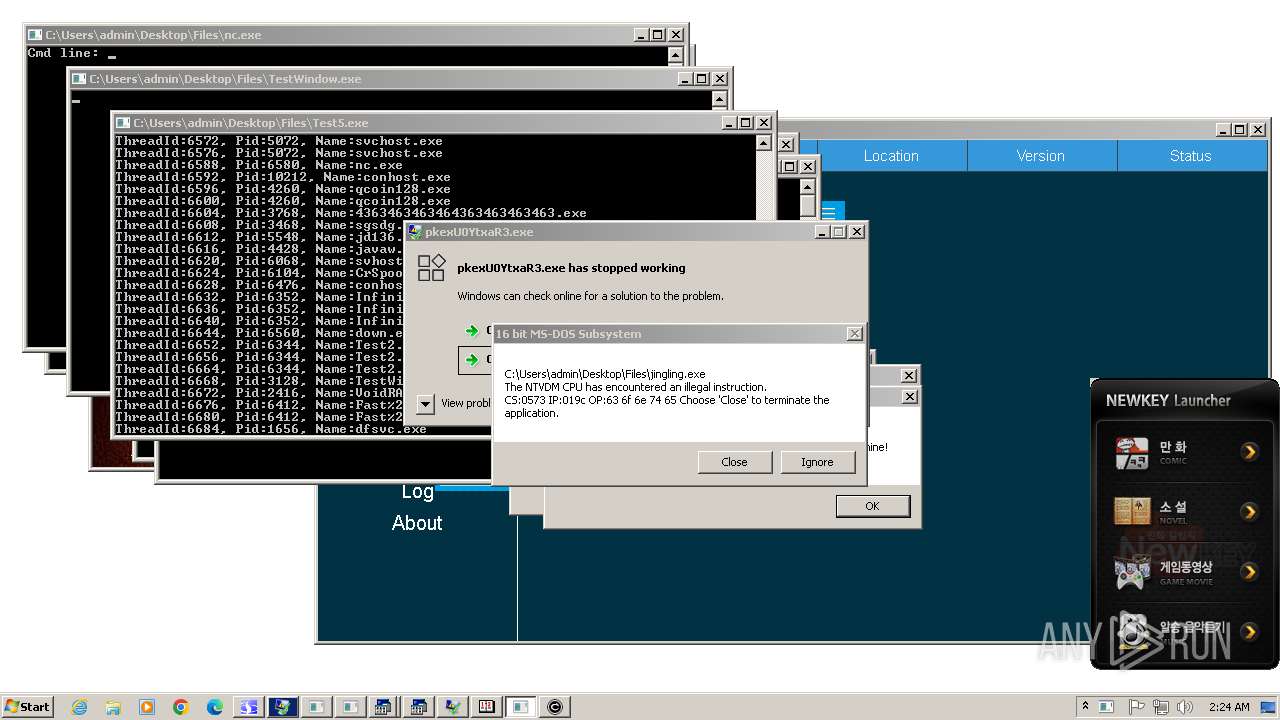
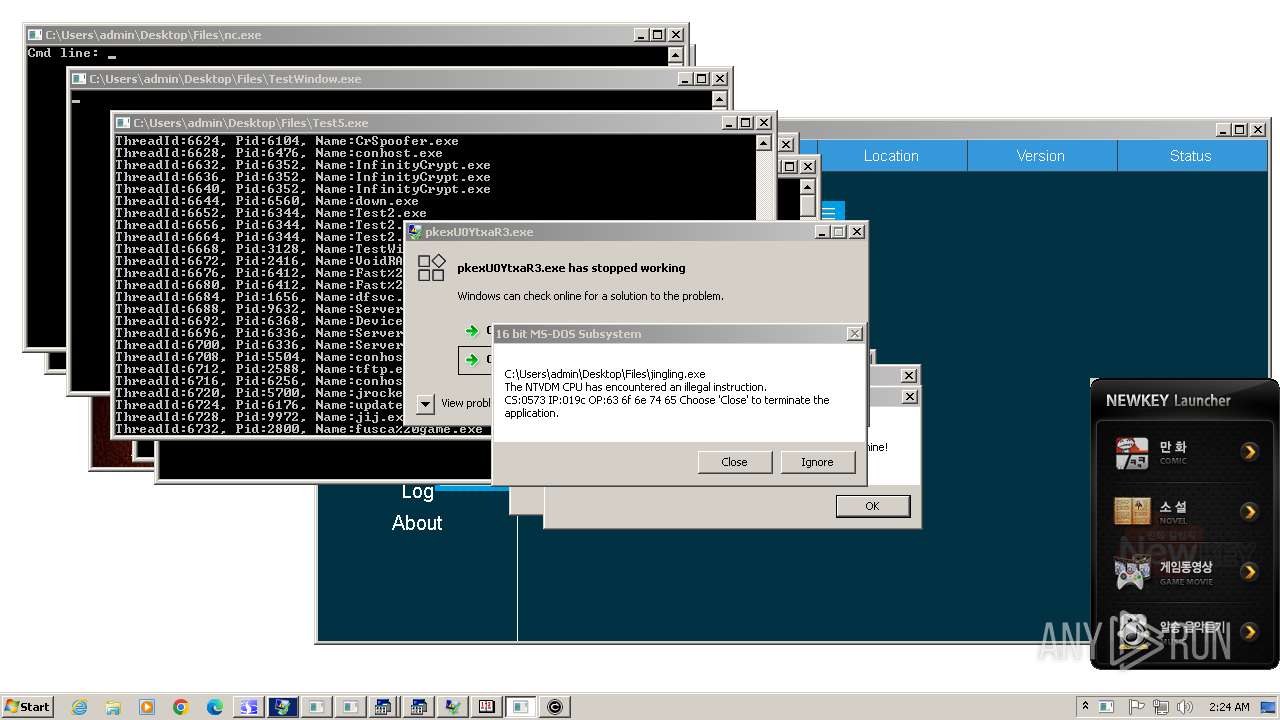
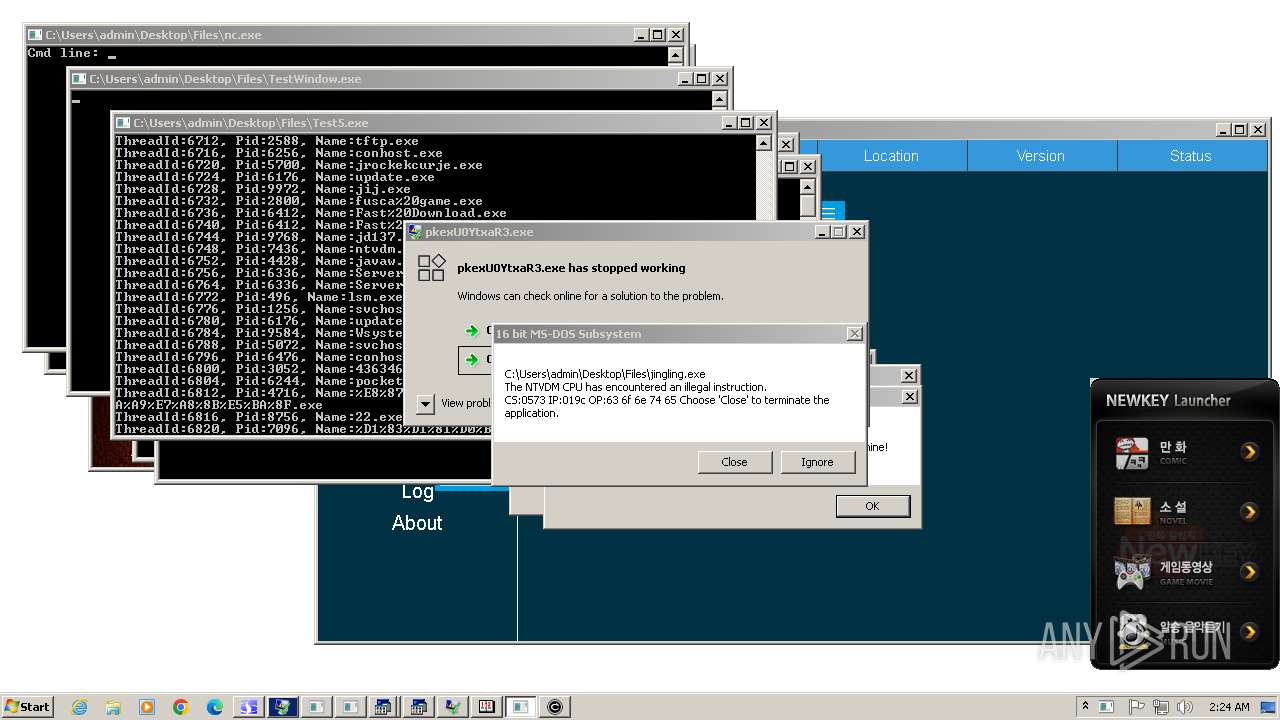
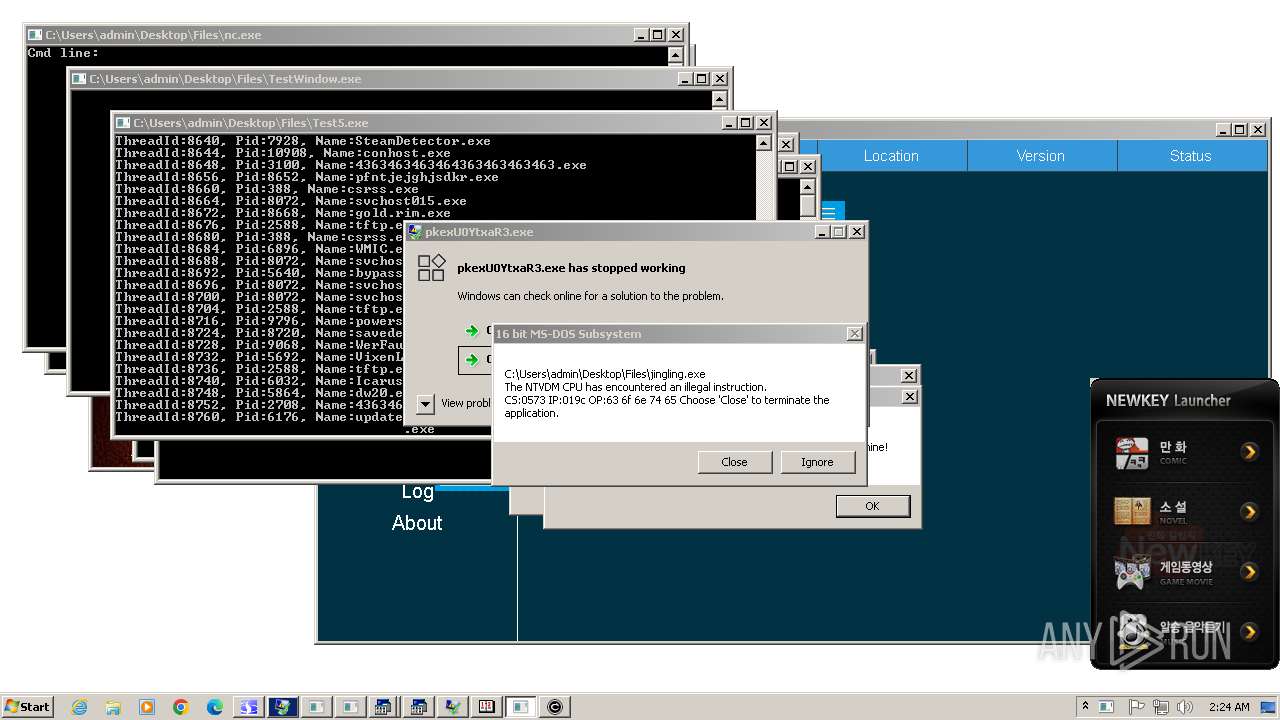
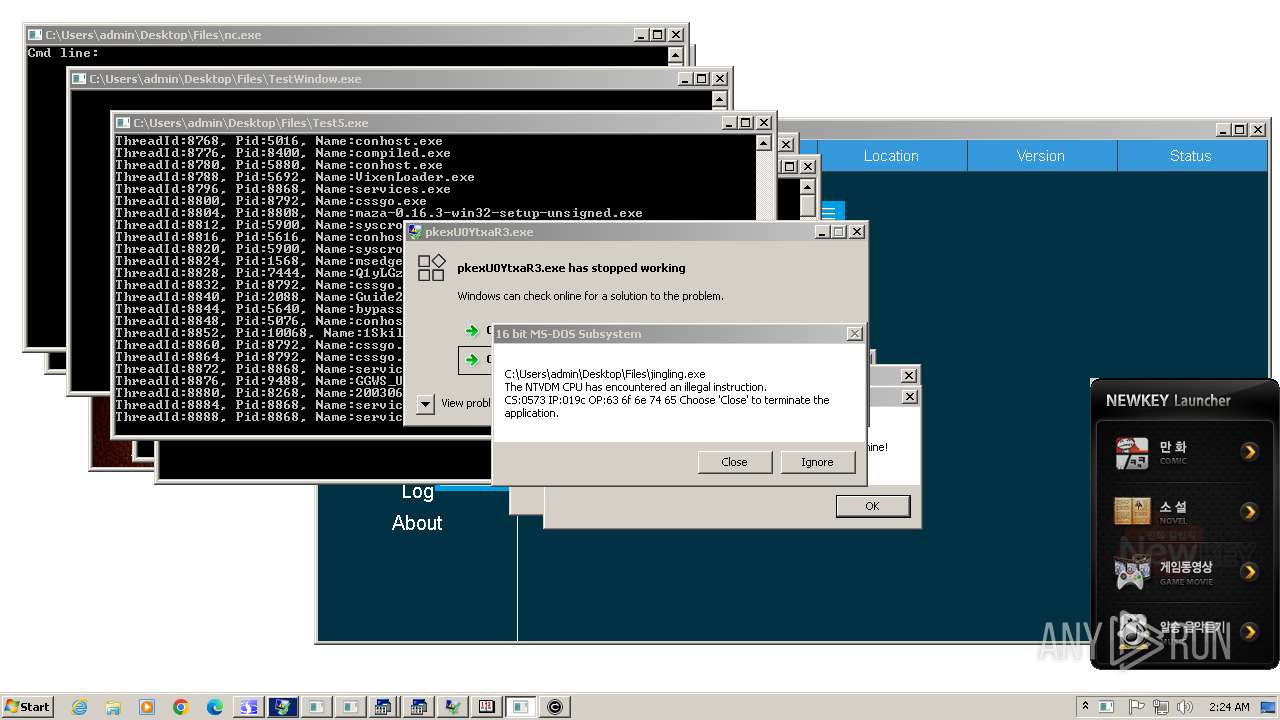
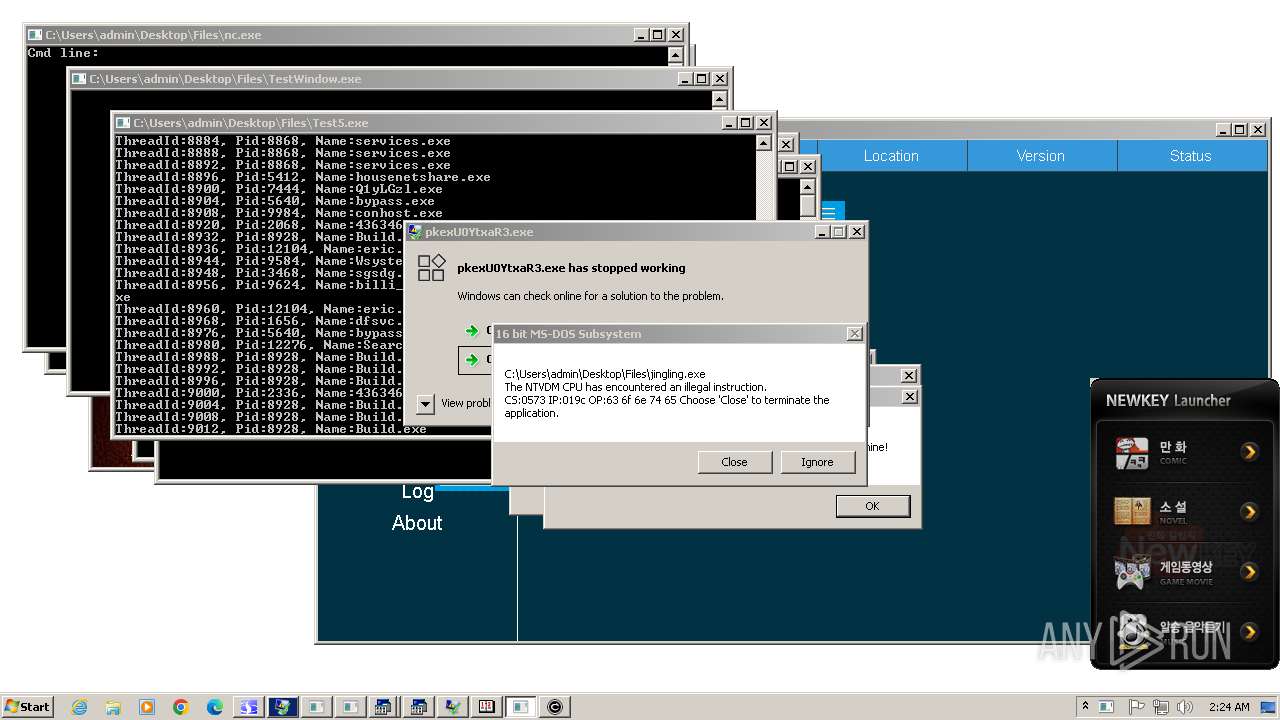
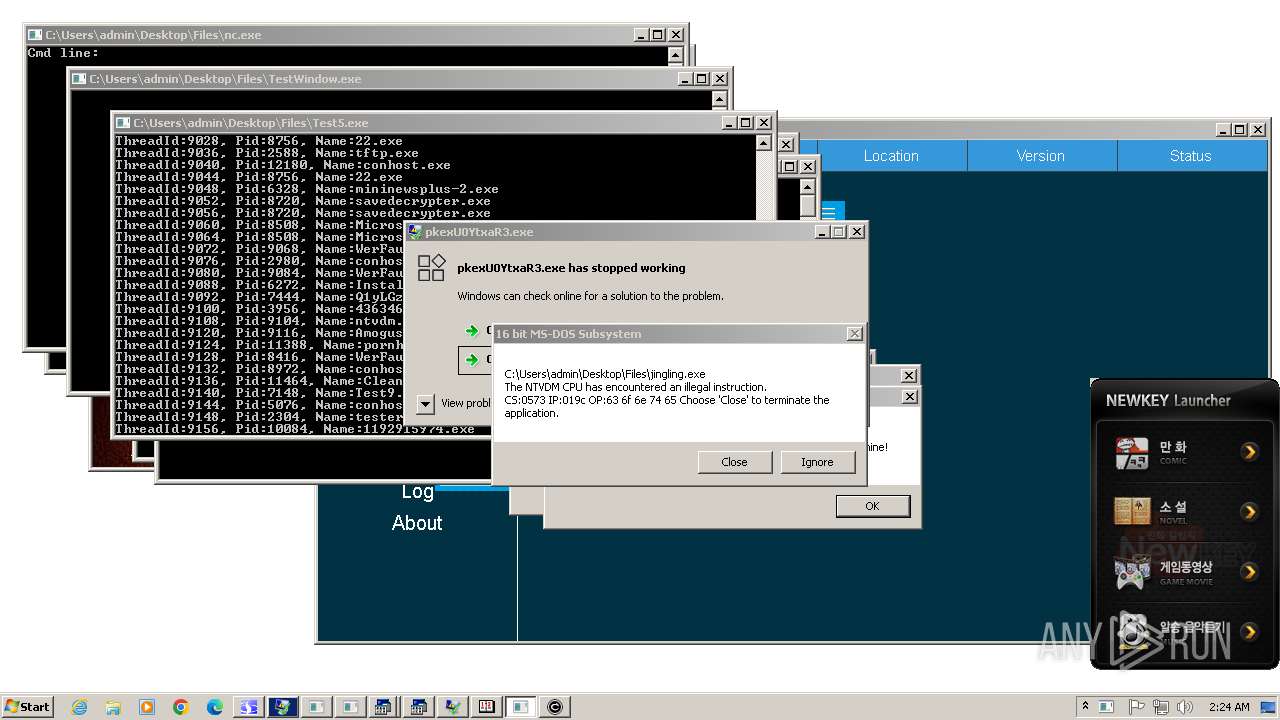
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/833def51-8c0f-4117-bcce-3c315769054c |
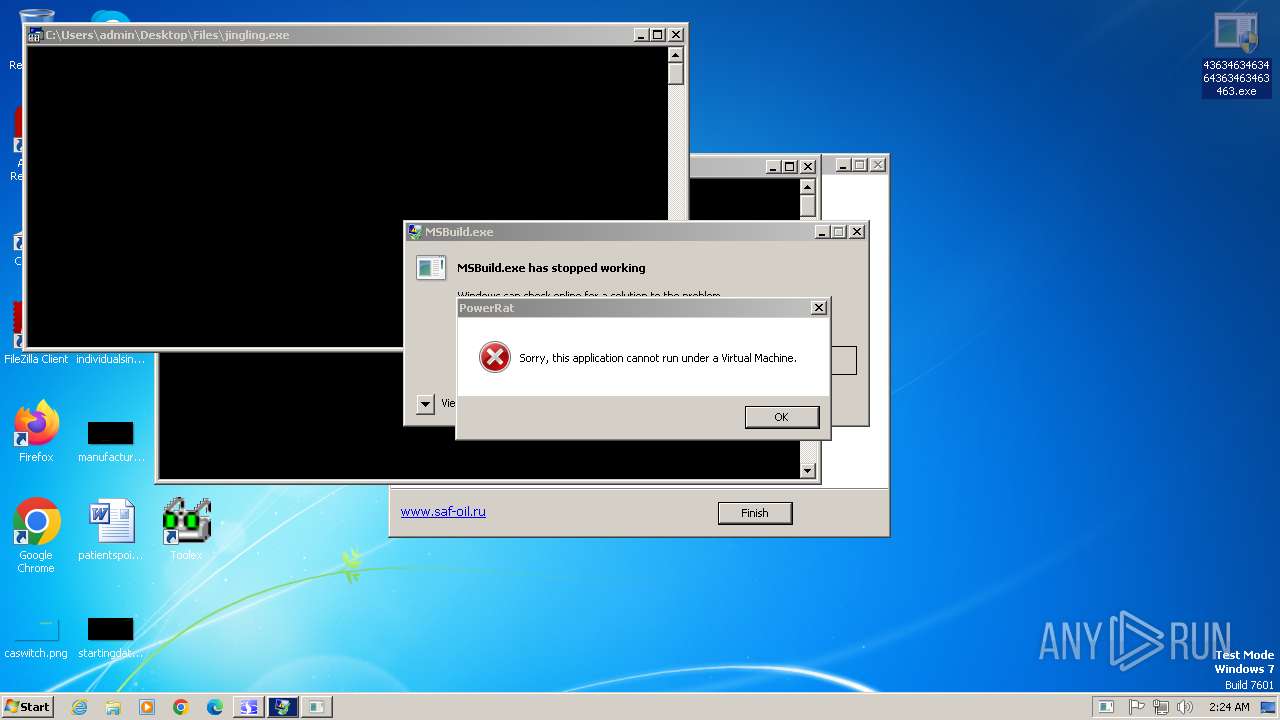
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 01:23:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
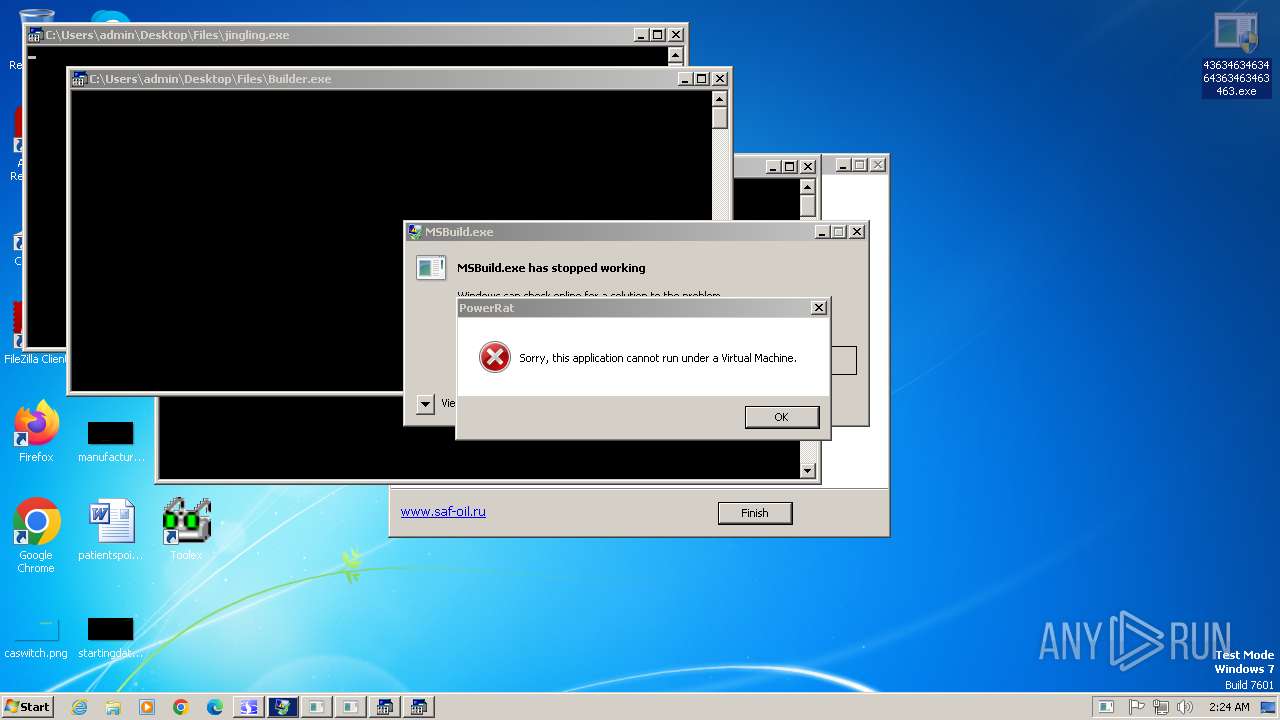
MALICIOUS
QUASARRAT has been found (auto)
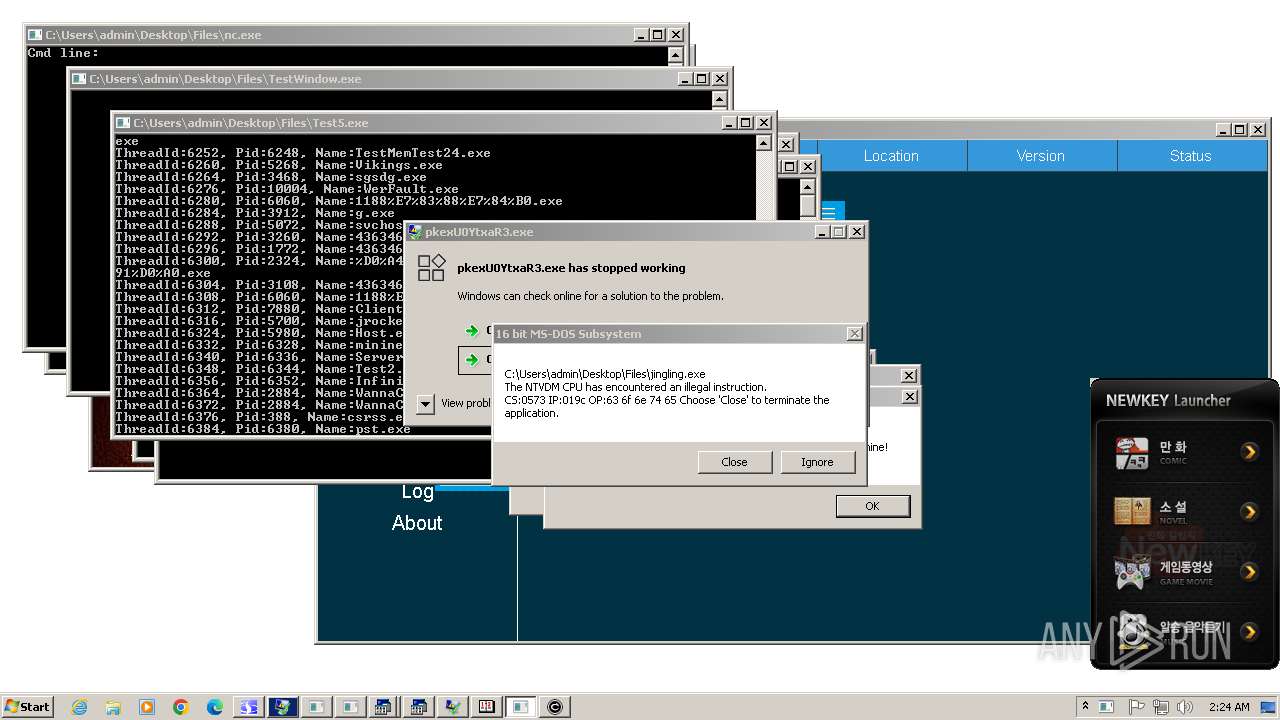
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2336)
- Sentil.exe (PID: 7588)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 1772)
- example_win32_dx11.exe (PID: 4860)
- svhost.exe (PID: 6068)
- Creal.exe (PID: 7260)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3052)
- Client-built-Playit.exe (PID: 7880)
- CollosalLoader.exe (PID: 7500)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3188)
- RuntimeBroker.exe (PID: 8408)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 2612)
- Client.exe (PID: 3076)
- cmd.exe (PID: 1380)
- svchost.exe (PID: 2276)
- diskutil.exe (PID: 5492)
- MinerBTC.exe (PID: 7216)
- Sentil.exe (PID: 7588)
- jrockekcurje.exe (PID: 5700)
- JUSCHED.EXE (PID: 7768)
- svhost.exe (PID: 6068)
- Creal.exe (PID: 7260)
- Client.exe (PID: 8296)
- VsGraphicsResources.exe (PID: 8112)
- Client-built-Playit.exe (PID: 7880)
- CollosalLoader.exe (PID: 7500)
- 80.exe (PID: 7908)
- Shopzilla.pif (PID: 8464)
- RuntimeBroker.exe (PID: 8408)
- cmd.exe (PID: 1664)
- quasarat.exe (PID: 11232)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 1020)
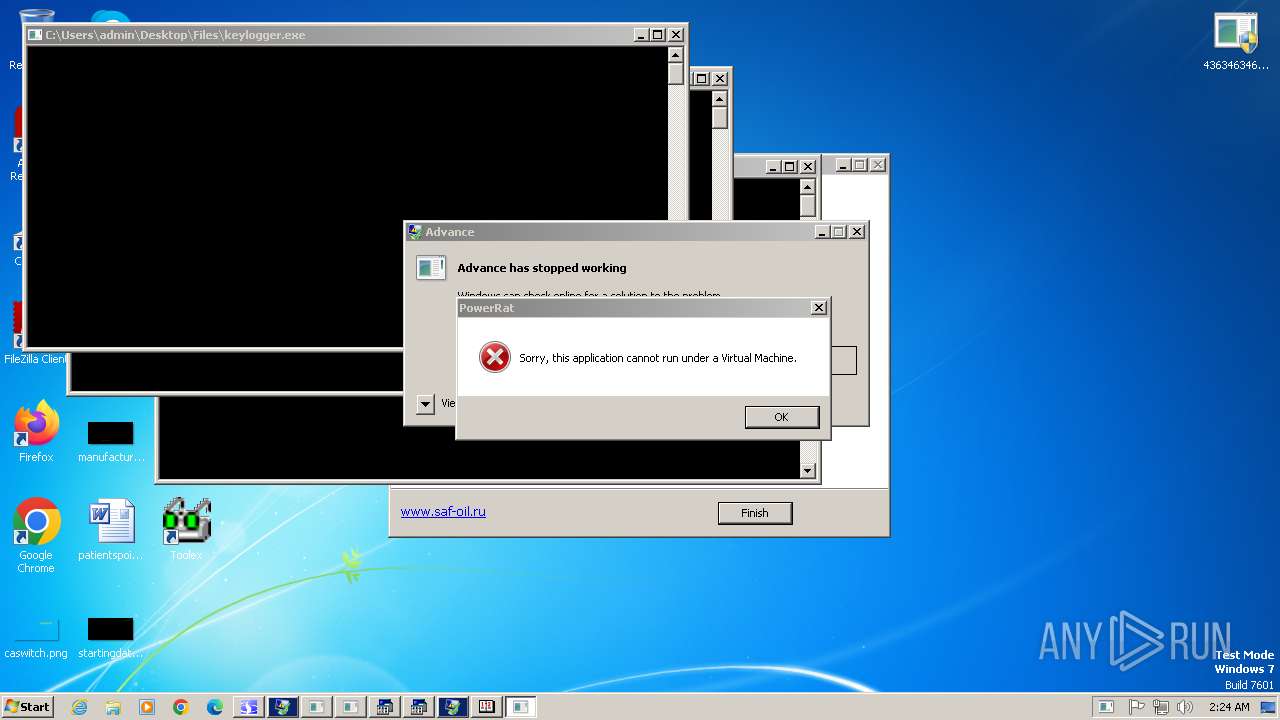
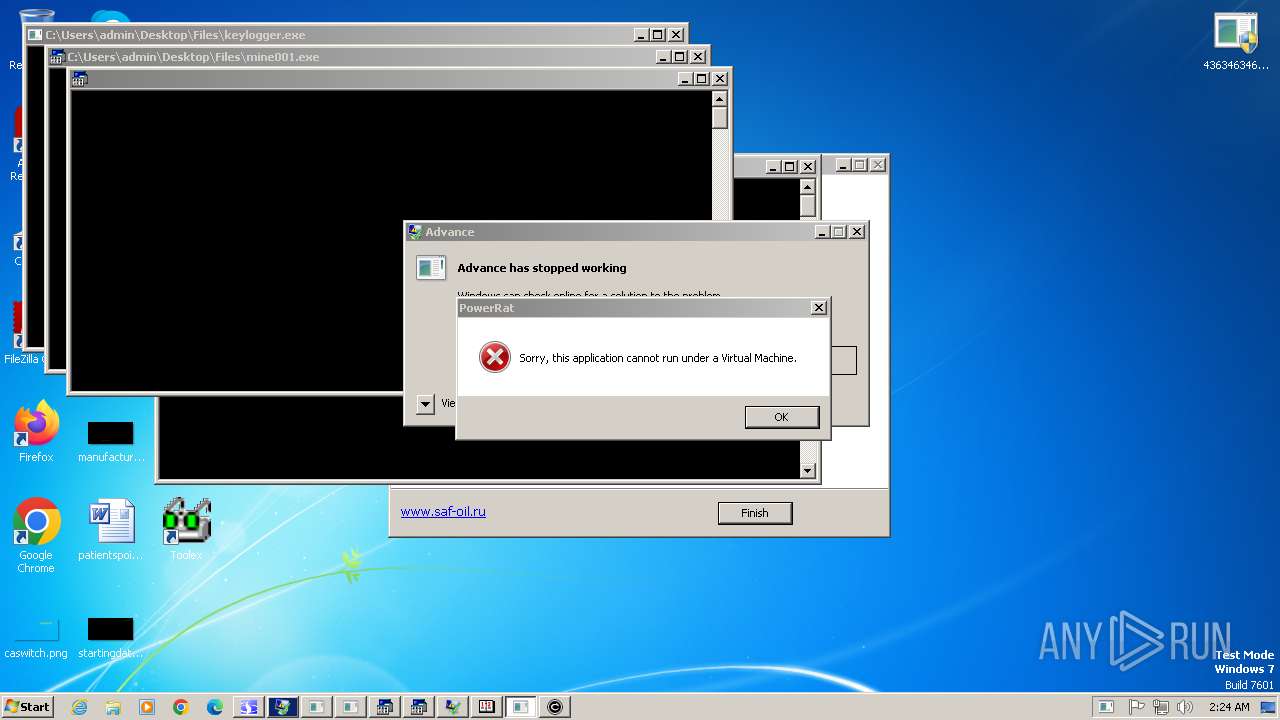
ASYNCRAT has been detected (MUTEX)
- image%20logger.exe (PID: 1648)
- syteam.exe (PID: 3776)
ASYNCRAT has been found (auto)
- image%20logger.exe (PID: 1648)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3668)
Connects to the CnC server
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3052)
- svchost.exe (PID: 1080)
- govno__dlya_jertwy.exe (PID: 7844)
- syscrondvr.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 2336)
- iexplore.exe (PID: 13208)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2952)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3260)
REDLINE has been found (auto)
- 4363463463464363463463463.exe (PID: 4016)
Executing a file with an untrusted certificate
- crypted.41.exe (PID: 4252)
- crypted.41.exe (PID: 4508)
- 1188%E7%83%88%E7%84%B0.exe (PID: 6060)
- mininewsplus-2.exe (PID: 6328)
- LatestLeave.exe (PID: 6808)
- 32.exe (PID: 7352)
- YearReload.exe (PID: 8152)
- InstallerPack_20.1.23770_win64.exe (PID: 6272)
- client.exe (PID: 8440)
- brbotnet.exe (PID: 8324)
- ClientRun.exe (PID: 9560)
- 3911_wz.exe (PID: 9748)
- Q1yLGzl.exe (PID: 7444)
- Nationalbankdirektrernes.exe (PID: 8148)
- haozip.convertimg.exe (PID: 4872)
- Guide2018.exe (PID: 2088)
- alex111111.exe (PID: 8836)
- alex111111.exe (PID: 5564)
- alex111111.exe (PID: 5424)
- td.exe (PID: 10548)
- vc17x64.exe (PID: 10260)
- Dashboard.exe (PID: 7544)
- vc17x64.exe (PID: 124)
- B0B34B3375B144C680A0456FFDD639A0.exe (PID: 344)
- compiled.exe (PID: 8400)
- Te.exe (PID: 13240)
- mixseven.exe (PID: 12524)
- witheFile.exe (PID: 13796)
- FOi.exe (PID: 5716)
- SeetrolClient.exe (PID: 14284)
- goldik121212.exe (PID: 7184)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2792)
- njSilent.exe (PID: 4560)
- 4363463463464363463463463.exe (PID: 4128)
- 4363463463464363463463463.exe (PID: 2336)
- svchost.exe (PID: 5072)
- Bloxflip%20Predictor.exe (PID: 4564)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3260)
- njrat.exe (PID: 9524)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3188)
- main.exe (PID: 11740)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 3652)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3100)
- LauncherLoader.exe (PID: 3576)
- mixten.exe (PID: 8124)
- 4363463463464363463463463.exe (PID: 4016)
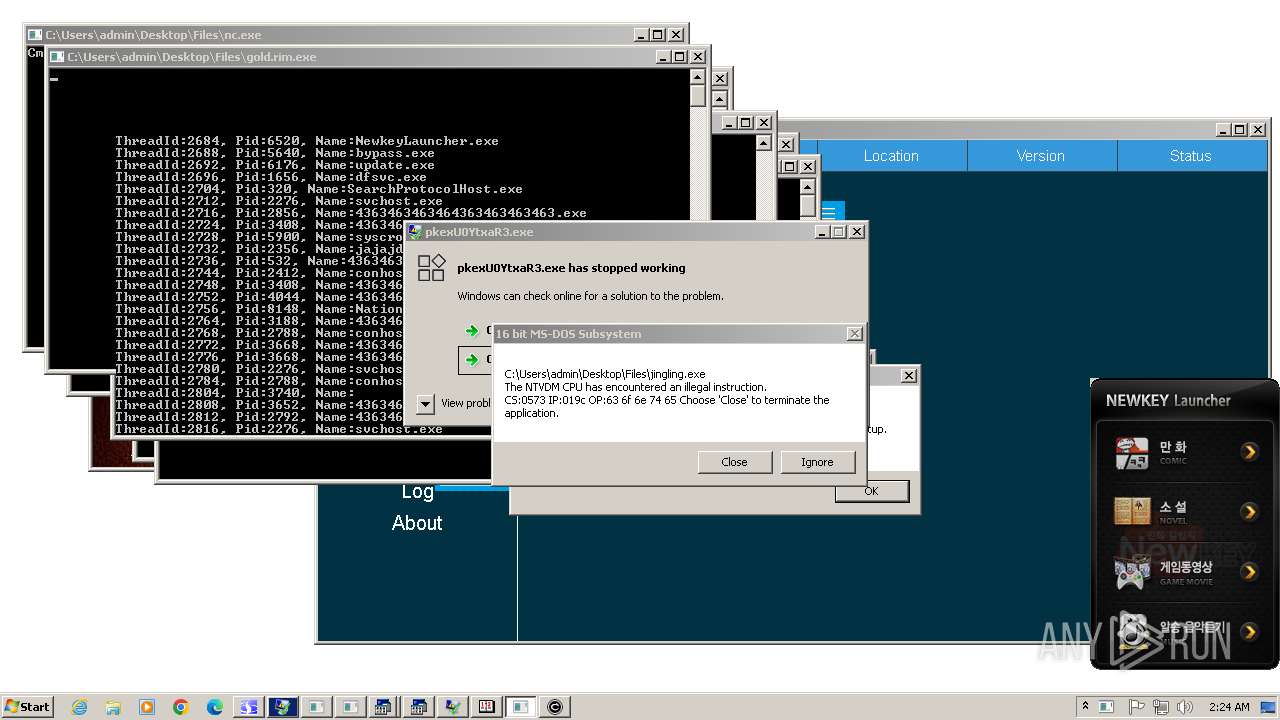
- NewkeyLauncher.exe (PID: 6520)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 2856)
Adds path to the Windows Defender exclusion list
- svchost.exe (PID: 2276)
- cmd.exe (PID: 4588)
- Vikings.exe (PID: 5268)
- powershell.exe (PID: 5460)
- XClient.exe (PID: 4328)
- powershell.exe (PID: 5892)
- Host.exe (PID: 5980)
- powershell.exe (PID: 7152)
- tRp.exe (PID: 6972)
- boleto.exe (PID: 5696)
Changes Windows Defender settings
- cmd.exe (PID: 4588)
- Vikings.exe (PID: 5268)
- powershell.exe (PID: 5460)
- XClient.exe (PID: 4328)
- powershell.exe (PID: 5892)
- Host.exe (PID: 5980)
- powershell.exe (PID: 7152)
- tRp.exe (PID: 6972)
- boleto.exe (PID: 5696)
Stealers network behavior
- svchost.exe (PID: 1080)
QUASAR has been detected (YARA)
- Client.exe (PID: 3076)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 2068)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 4128)
- govno__dlya_jertwy.exe (PID: 7844)
- 4363463463464363463463463.exe (PID: 3408)
- SteamDetector.exe (PID: 7092)
- SteamDetector.exe (PID: 7928)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3892)
- ApiUpdater.exe (PID: 12944)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1080)
- cronikxqqq.exe (PID: 5304)
- Q1yLGzl.exe (PID: 7444)
- alex111111.exe (PID: 5424)
- gold.rim.exe (PID: 10160)
BABADEDA has been found (auto)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3244)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 3052)
- diskutil.exe (PID: 5492)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 3408)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2700)
ASYNCRAT has been detected (YARA)
- syteam.exe (PID: 3776)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 4328)
- Host.exe (PID: 5980)
- tRp.exe (PID: 6972)
- boleto.exe (PID: 5696)
Bypass execution policy to execute commands
- powershell.exe (PID: 580)
- powershell.exe (PID: 6932)
- powershell.exe (PID: 8184)
- powershell.exe (PID: 6712)
- powershell.exe (PID: 6152)
- powershell.exe (PID: 8244)
- powershell.exe (PID: 9796)
- powershell.exe (PID: 9280)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 10988)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 4328)
- Host.exe (PID: 5980)
- tRp.exe (PID: 6972)
DCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 3108)
DISCORDTOKEN has been found (auto)
- 4363463463464363463463463.exe (PID: 3052)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 7920)
- findstr.exe (PID: 4756)
NJRAT has been detected (SURICATA)
- govno__dlya_jertwy.exe (PID: 7844)
COINMINER has been found (auto)
- 4363463463464363463463463.exe (PID: 3408)
- sgsdg.exe (PID: 3468)
Starts CertUtil for downloading files
- cmd.exe (PID: 1664)
ADESSTEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 4016)
PHORPIEX has been detected (SURICATA)
- syscrondvr.exe (PID: 5900)
PHEMEDRONE has been found (auto)
- 4363463463464363463463463.exe (PID: 3244)
RUSTYSTEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 3848)
Signed with known abused certificate
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 3244)
NANOCORE has been found (auto)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3188)
LUMAR has been detected (SURICATA)
- MetaTrader.exe (PID: 3216)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 1080)
TOFSEE has been found (auto)
- 4363463463464363463463463.exe (PID: 3108)
SCHOOLBOY has been found (auto)
- 4363463463464363463463463.exe (PID: 3892)
ASYNCRAT has been detected (SURICATA)
- ckjg.exe (PID: 1036)
AZORULT has been found (auto)
- 4363463463464363463463463.exe (PID: 2720)
COBALTSTRIKE has been found (auto)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 532)
XWORM has been found (auto)
- 4363463463464363463463463.exe (PID: 3244)
- done12312.exe (PID: 10612)
METASPLOIT has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 1020)
METERPRETER has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 1020)
DARKCOMET has been found (auto)
- 4363463463464363463463463.exe (PID: 1164)
METASPLOIT has been found (auto)
- 4363463463464363463463463.exe (PID: 1164)
CLICKFIX has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2068)
- svchost.exe (PID: 1080)
SMOKE has been found (auto)
- 4363463463464363463463463.exe (PID: 3408)
Uses Task Scheduler to run other applications
- done12312.exe (PID: 10612)
- savedecrypter.exe (PID: 8720)
LOADER has been found (auto)
- 4363463463464363463463463.exe (PID: 3668)
VIDAR has been found (auto)
- 4363463463464363463463463.exe (PID: 3956)
REMCOS has been found (auto)
- 4363463463464363463463463.exe (PID: 2856)
- FXServer.exe (PID: 13940)
FORMBOOK has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2336)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 13208)
STEALERIUM has been found (auto)
- 4363463463464363463463463.exe (PID: 2720)
QUASAR has been detected (SURICATA)
- quasarat.exe (PID: 11232)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2720)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- safman_setup.exe (PID: 2508)
- safman_setup.tmp (PID: 2388)
- jajajdva.exe (PID: 2356)
- image%20logger.exe (PID: 1648)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3260)
- qrtb.exe (PID: 5316)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3144)
- diskutil.exe (PID: 5492)
- svchost.exe (PID: 2276)
- njSilent.exe (PID: 4560)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 4128)
- trojan.exe (PID: 5904)
- 4363463463464363463463463.exe (PID: 1164)
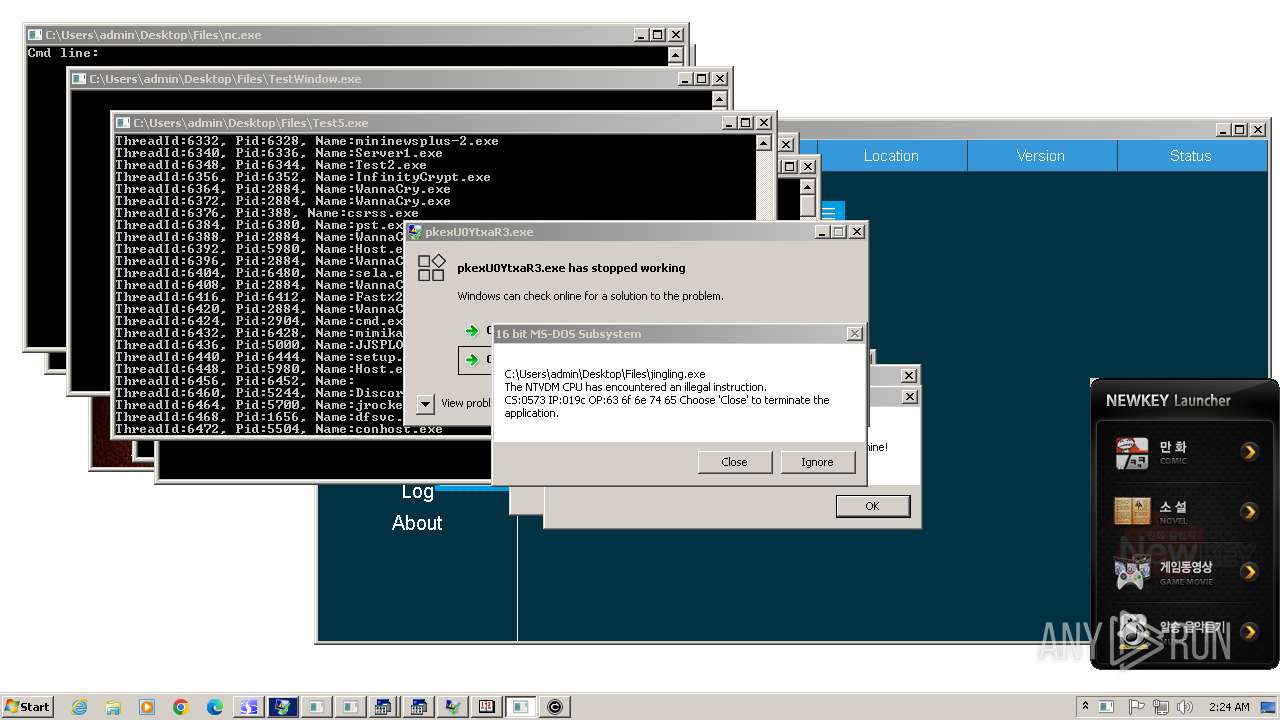
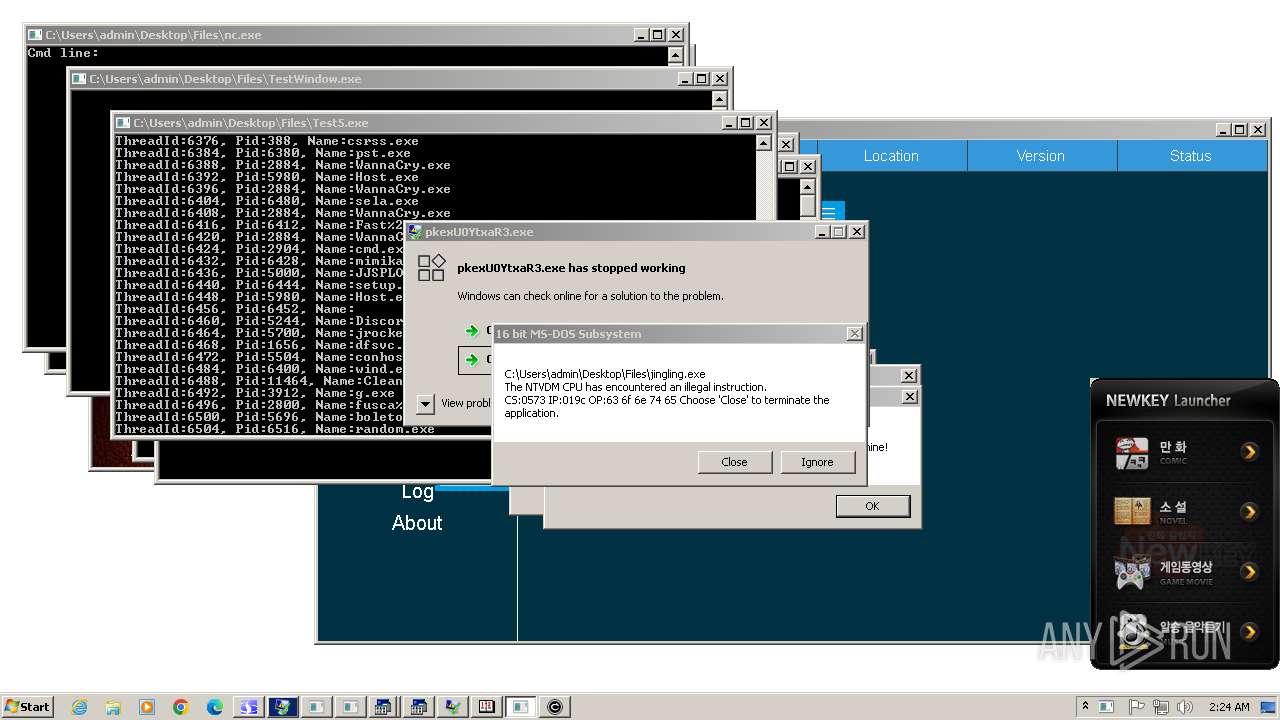
- WannaCry.exe (PID: 2884)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3100)
- svchost.exe (PID: 5072)
- icacls.exe (PID: 6152)
- vncgroups.exe (PID: 6944)
- Bloxflip%20Predictor.exe (PID: 4564)
- CritScript.exe (PID: 7352)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 2952)
- haozip_tiny.201805.exe (PID: 7480)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3892)
- newtpp.exe (PID: 7912)
- cmd.exe (PID: 7136)
- LauncherLoader.exe (PID: 3576)
- rlol.exe (PID: 6924)
- qwsrv3.3.exe (PID: 7056)
- govno__dlya_jertwy.exe (PID: 7844)
- Sentil.exe (PID: 7588)
- SteamDetector.exe (PID: 7092)
- JUSCHED.EXE (PID: 7768)
- example_win32_dx11.exe (PID: 4860)
- pocketrar350sc.exe (PID: 6244)
- svhost.exe (PID: 6068)
- Creal.exe (PID: 7260)
- mixten.exe (PID: 8124)
- cmd.exe (PID: 5964)
- rlol.tmp (PID: 7600)
- sgsdg.exe (PID: 3468)
- 4363463463464363463463463.exe (PID: 2368)
- %E8%87%AA%E5%8A%A8%E6%9B%B4%E6%96%B0%E8%BE%85%E5%8A%A9%E7%A8%8B%E5%BA%8F.exe (PID: 4716)
- qwsrv3.3.tmp (PID: 7572)
- inst77player_1.0.0.1.exe (PID: 8088)
- client.exe (PID: 8440)
- cabal.exe (PID: 3580)
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- VsGraphicsResources.exe (PID: 8112)
- NewkeyLauncher.exe (PID: 6520)
- Client-built-Playit.exe (PID: 7880)
- CollosalLoader.exe (PID: 7500)
- SteamDetector.exe (PID: 7928)
- 80.exe (PID: 7908)
- services.exe (PID: 8868)
- XMZTSVYE_l10_wix4_dash.exe (PID: 4672)
- Adobe_Setup.exe (PID: 5460)
- XMZTSVYE_l10_wix4_dash.exe (PID: 7432)
- sgsdg.exe (PID: 8952)
- IMG001.exe (PID: 10044)
- tester.exe (PID: 2304)
- qm2014chs.exe (PID: 7008)
- njrat.exe (PID: 9524)
- haozip.convertimg.exe (PID: 4872)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 10520)
- Shopzilla.pif (PID: 8464)
- Q1yLGzl.exe (PID: 7444)
- ljgksdtihd.exe (PID: 11312)
- vc17x64.exe (PID: 124)
- taskmoder.exe (PID: 11844)
- 163.exe (PID: 6936)
- done12312.exe (PID: 10612)
- XBinderOutput.exe (PID: 5976)
- esign-app.exe (PID: 12056)
- ui.exe (PID: 10860)
- RuntimeBroker.exe (PID: 8408)
- eric.exe (PID: 12104)
- main.exe (PID: 11740)
- IMG001.exe (PID: 11212)
- c4284a2a6c1b60247944a03cbaf930c5.exe (PID: 12612)
- server.exe (PID: 5196)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 13416)
- ApiUpdater.exe (PID: 12944)
- 1192915974.exe (PID: 10084)
- FXServer.exe (PID: 13940)
- ClientRun.exe (PID: 9560)
- ChromeSetup.exe (PID: 9808)
- 444.exe (PID: 7828)
- td.exe (PID: 10548)
- savedecrypter.exe (PID: 8720)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2336)
- image%20logger.exe (PID: 1648)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 2068)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2336)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1772)
- calendar.exe (PID: 5024)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 4016)
- LauncherLoader.exe (PID: 3576)
- cabal.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 4128)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3244)
- NewkeyLauncher.exe (PID: 6520)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- jeditor.exe (PID: 11148)
- td.exe (PID: 10548)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2336)
- image%20logger.exe (PID: 1648)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3052)
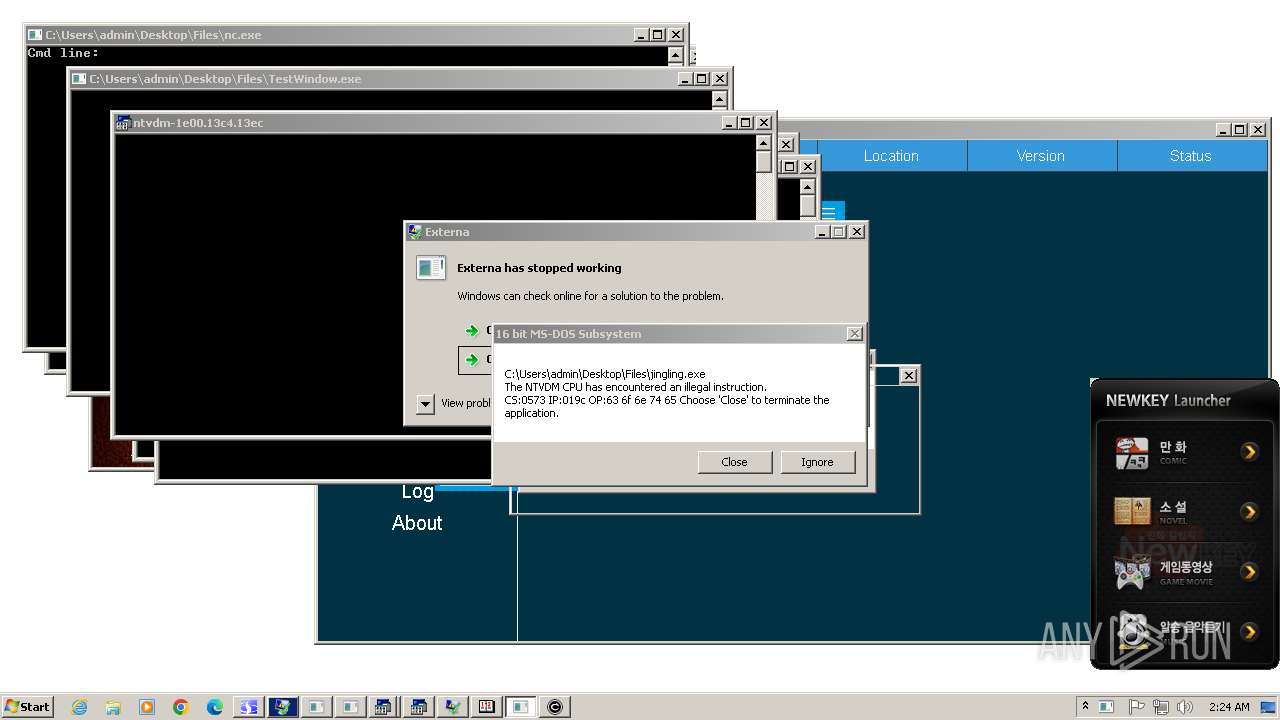
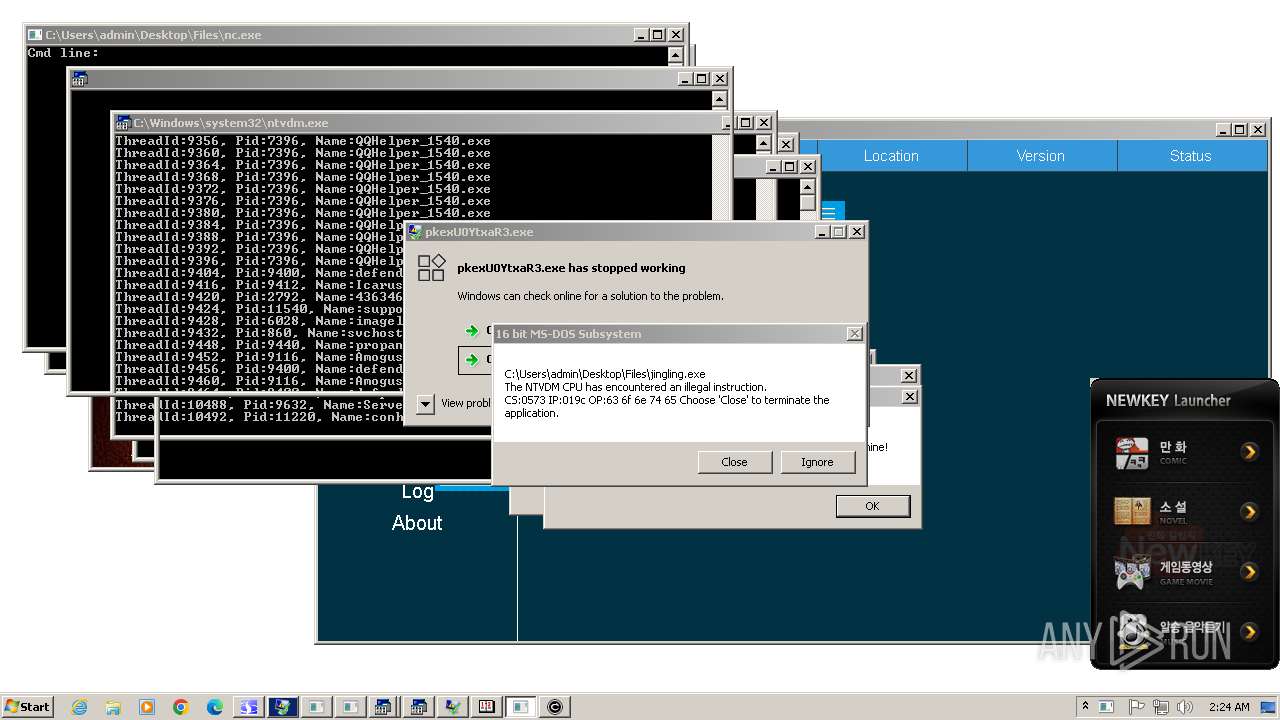
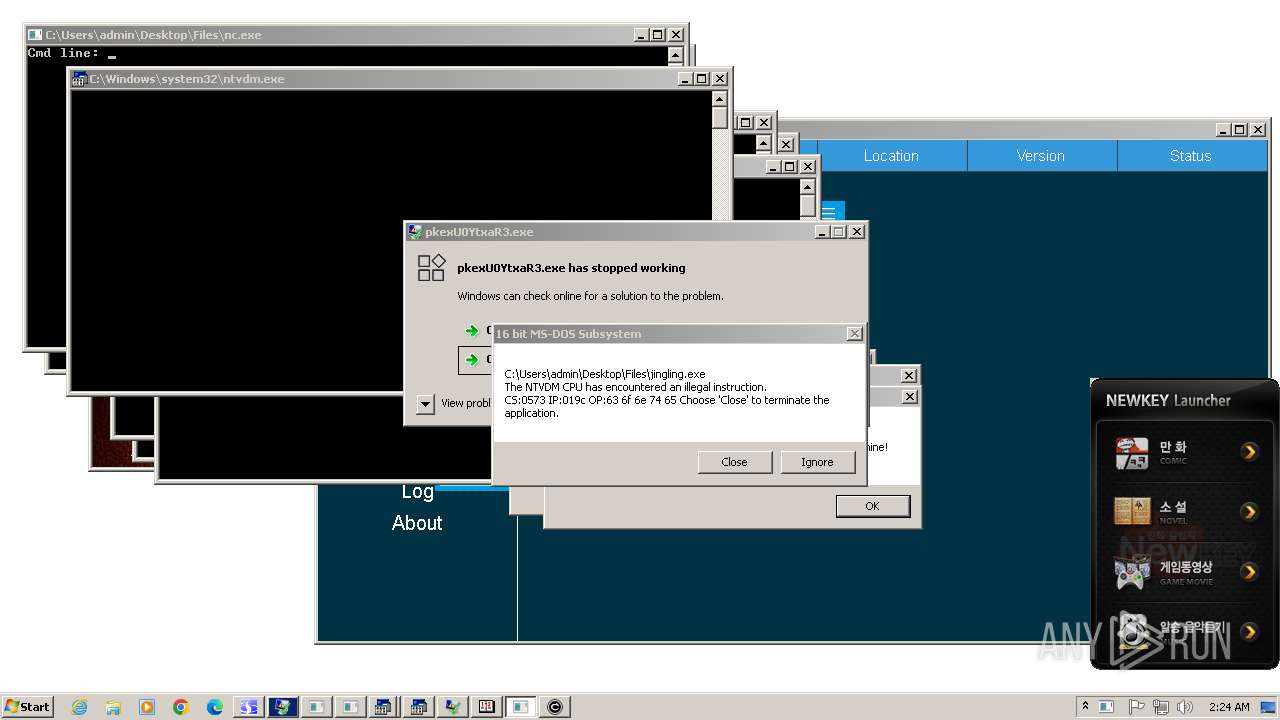
Creates file in the systems drive root
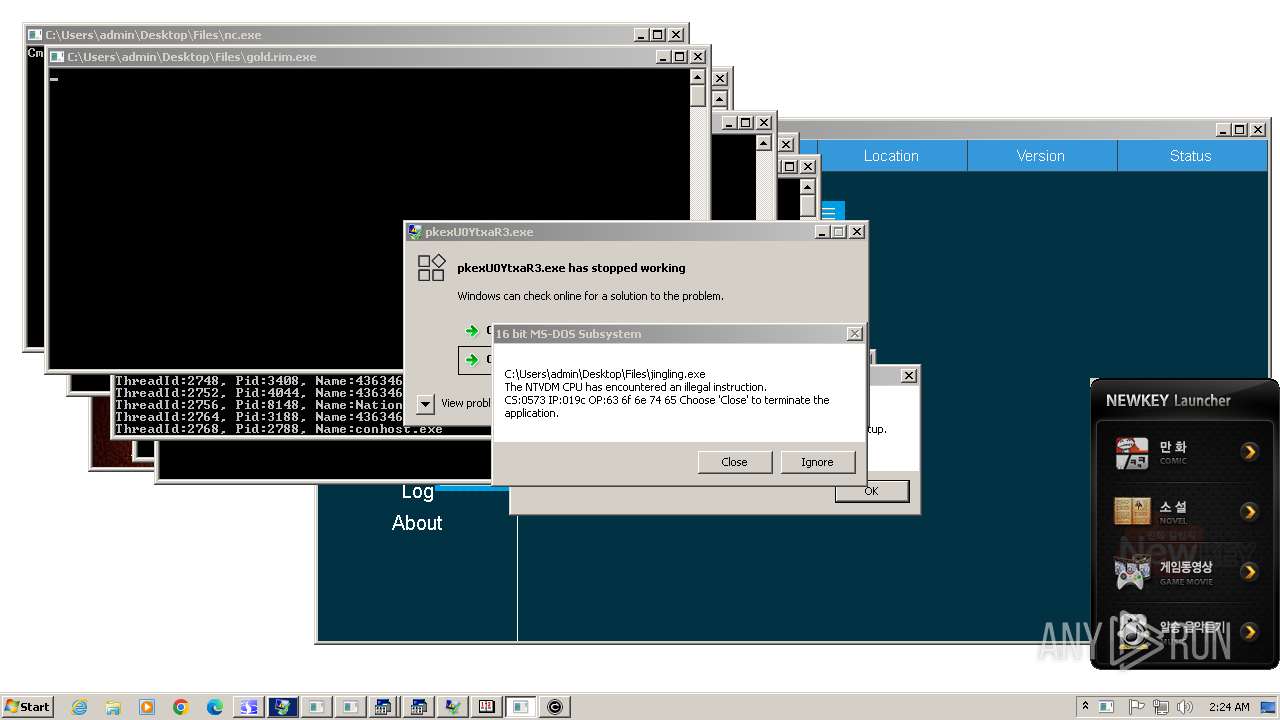
- ntvdm.exe (PID: 3444)
Starts itself from another location
- Client-built.exe (PID: 2612)
- njSilent.exe (PID: 4560)
- trojan.exe (PID: 5904)
- vncgroups.exe (PID: 6944)
- Bloxflip%20Predictor.exe (PID: 4564)
- newtpp.exe (PID: 7912)
- example_win32_dx11.exe (PID: 4860)
- SteamDetector.exe (PID: 7092)
- Creal.exe (PID: 7260)
- 80.exe (PID: 7908)
- XMZTSVYE_l10_wix4_dash.exe (PID: 4672)
- njrat.exe (PID: 9524)
- IMG001.exe (PID: 10044)
- main.exe (PID: 11740)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 13416)
Reads the Windows owner or organization settings
- safman_setup.tmp (PID: 2388)
Connects to unusual port
- Client.exe (PID: 3076)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3052)
- msf.exe (PID: 5716)
- 4363463463464363463463463.exe (PID: 3408)
- fadzwm.exe (PID: 5516)
- 4363463463464363463463463.exe (PID: 532)
- CPDB.exe (PID: 5324)
- 4363463463464363463463463.exe (PID: 3108)
- kali_tools.exe (PID: 5100)
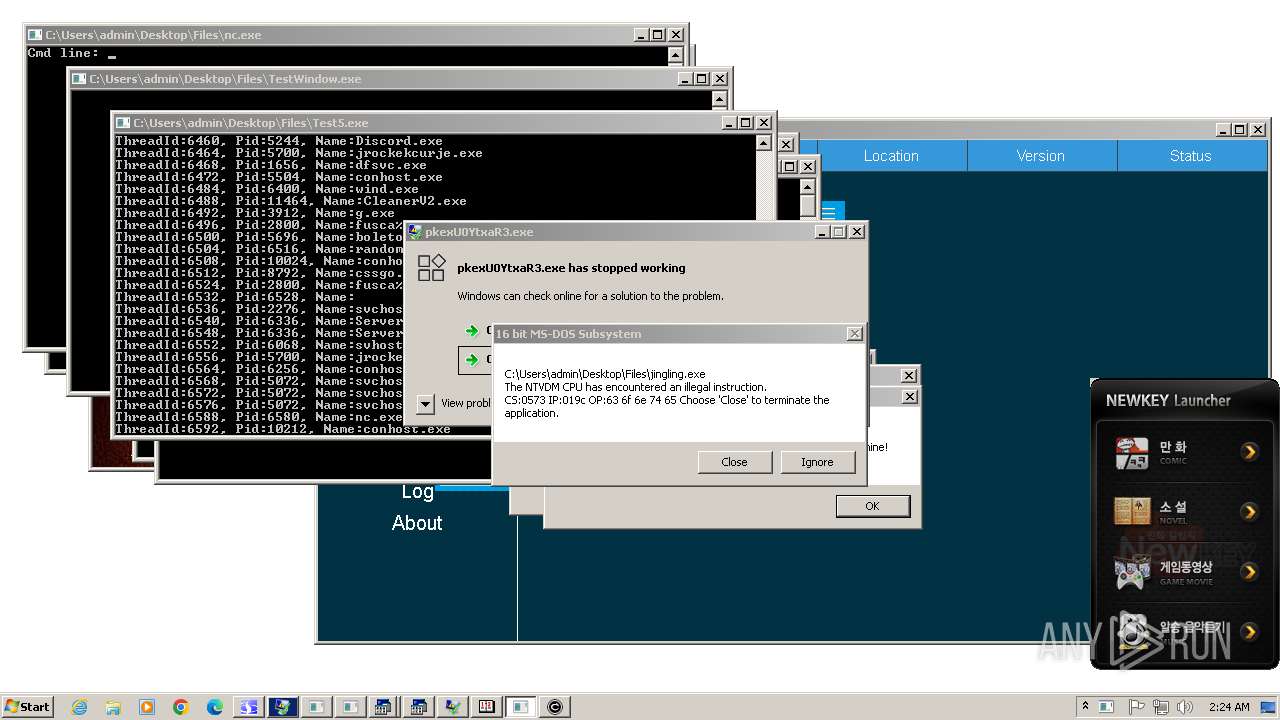
- Discord.exe (PID: 5244)
- CrSpoofer.exe (PID: 6104)
- 4363463463464363463463463.exe (PID: 2700)
- idmans.exe (PID: 7072)
- svchost.exe (PID: 5072)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3768)
- connector1.exe (PID: 7704)
- MinerBTC.exe (PID: 7216)
- 4363463463464363463463463.exe (PID: 2856)
- Lamno.exe (PID: 7340)
- wind.exe (PID: 6400)
- %D1%83%D1%81%D0%B5%D1%80%D0%BB%D0%BE%D0%BD%D0%B32.exe (PID: 7096)
- govno__dlya_jertwy.exe (PID: 7844)
- jrockekcurje.exe (PID: 5700)
- prueba.exe (PID: 8000)
- 4363463463464363463463463.exe (PID: 3244)
- Device2.exe (PID: 6368)
- 4363463463464363463463463.exe (PID: 2708)
- certutil.exe (PID: 7740)
- access.exe (PID: 8276)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3144)
- MetaTrader.exe (PID: 3216)
- services.exe (PID: 8868)
- 4363463463464363463463463.exe (PID: 1020)
- ckjg.exe (PID: 1036)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- 22.exe (PID: 8756)
- fern_wifi_recon%252.34.exe (PID: 9520)
- Server.exe (PID: 9632)
- syscrondvr.exe (PID: 5900)
- benpolatalemdar.exe (PID: 10564)
- toolwin.exe (PID: 8028)
- ljgksdtihd.exe (PID: 11312)
- 4363463463464363463463463.exe (PID: 4128)
- 1223.exe (PID: 4200)
- systempreter.exe (PID: 2580)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 4044)
- quasarat.exe (PID: 11232)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3052)
- diskutil.exe (PID: 5492)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3144)
- WannaCry.exe (PID: 2884)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 2856)
- rlol.tmp (PID: 7600)
- qwsrv3.3.tmp (PID: 7572)
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- cabal.exe (PID: 3580)
- client.exe (PID: 8440)
- 4363463463464363463463463.exe (PID: 3848)
- services.exe (PID: 8868)
- 4363463463464363463463463.exe (PID: 3892)
- XMZTSVYE_l10_wix4_dash.exe (PID: 7432)
- tester.exe (PID: 2304)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2952)
- vc17x64.exe (PID: 124)
- ui.exe (PID: 10860)
- 1192915974.exe (PID: 10084)
- ClientRun.exe (PID: 9560)
- iexplore.exe (PID: 13208)
Starts a Microsoft application from unusual location
- jajajdva.exe (PID: 2356)
- diskutil.exe (PID: 5492)
- WannaCry.exe (PID: 2884)
- taskdl.exe (PID: 6400)
- taskdl.exe (PID: 7332)
- client.exe (PID: 8440)
- services.exe (PID: 8868)
- taskdl.exe (PID: 8628)
- taskdl.exe (PID: 3296)
- Server.exe (PID: 9632)
- taskdl.exe (PID: 10696)
- Dashboard.exe (PID: 7544)
- vc17x64.exe (PID: 10260)
- taskdl.exe (PID: 10364)
- vc17x64.exe (PID: 124)
- taskdl.exe (PID: 11660)
- taskdl.exe (PID: 14228)
Starts CMD.EXE for commands execution
- image%20logger.exe (PID: 1648)
- svchost.exe (PID: 2276)
- av_downloader.exe (PID: 4888)
- qrtb.exe (PID: 5316)
- QuizPokemon.exe (PID: 5012)
- WannaCry.exe (PID: 2884)
- Lamno.exe (PID: 5124)
- 80.exe (PID: 5932)
- av_downloader.exe (PID: 7040)
- cmd.exe (PID: 5964)
- Client.exe (PID: 8296)
- svchost.exe (PID: 7884)
- IMG001.exe (PID: 10044)
- Wsystem.exe (PID: 9584)
- IMG001.exe (PID: 11212)
- pornhub_downloader.exe (PID: 11388)
- main.exe (PID: 11740)
- ApiUpdater.exe (PID: 12944)
- Terminal_9235.exe (PID: 4000)
- FXServer.exe (PID: 13940)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1396)
- cmd.exe (PID: 5964)
Executing commands from a ".bat" file
- image%20logger.exe (PID: 1648)
- av_downloader.exe (PID: 4888)
- WannaCry.exe (PID: 2884)
- av_downloader.exe (PID: 7040)
- svchost.exe (PID: 7884)
- Client.exe (PID: 8296)
- pornhub_downloader.exe (PID: 11388)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 3108)
- LauncherLoader.exe (PID: 3576)
- 4363463463464363463463463.exe (PID: 2700)
- cabal.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 2708)
- %D1%83%D1%81%D0%B5%D1%80%D0%BB%D0%BE%D0%BD%D0%B32.exe (PID: 7096)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 4128)
- 4363463463464363463463463.exe (PID: 3244)
- NewkeyLauncher.exe (PID: 6520)
- 4363463463464363463463463.exe (PID: 2368)
- svchost.exe (PID: 1080)
- calendar.exe (PID: 5024)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 2068)
- jeditor.exe (PID: 11148)
The executable file from the user directory is run by the CMD process
- syteam.exe (PID: 3776)
- Shopzilla.pif (PID: 8464)
- Client.exe (PID: 13884)
- svchost.exe (PID: 10952)
Contacting a server suspected of hosting an CnC
- 4363463463464363463463463.exe (PID: 3668)
- svchost.exe (PID: 1080)
- cronikxqqq.exe (PID: 5304)
- 4363463463464363463463463.exe (PID: 3052)
- govno__dlya_jertwy.exe (PID: 7844)
- syscrondvr.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 4016)
- Q1yLGzl.exe (PID: 7444)
- ckjg.exe (PID: 1036)
- 4363463463464363463463463.exe (PID: 3100)
- alex111111.exe (PID: 5424)
- gold.rim.exe (PID: 10160)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2336)
- iexplore.exe (PID: 13208)
- 4363463463464363463463463.exe (PID: 2952)
- quasarat.exe (PID: 11232)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2720)
- cabal.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3144)
- Lamno.exe (PID: 5124)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3244)
- syscrondvr.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 4128)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3188)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 532)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4588)
- Vikings.exe (PID: 5268)
- powershell.exe (PID: 5460)
- XClient.exe (PID: 4328)
- powershell.exe (PID: 5892)
- Host.exe (PID: 5980)
- powershell.exe (PID: 7152)
- tRp.exe (PID: 6972)
- boleto.exe (PID: 5696)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4588)
- Vikings.exe (PID: 5268)
- powershell.exe (PID: 5460)
- XClient.exe (PID: 4328)
- powershell.exe (PID: 5892)
- Host.exe (PID: 5980)
- powershell.exe (PID: 7152)
- tRp.exe (PID: 6972)
- boleto.exe (PID: 5696)
- ljgksdtihd.exe (PID: 11312)
Application launched itself
- crypted.41.exe (PID: 4252)
- cronikxqqq.exe (PID: 5164)
- powershell.exe (PID: 5460)
- powershell.exe (PID: 5892)
- installsbot.crypt.exe (PID: 7084)
- Lamno.exe (PID: 5124)
- powershell.exe (PID: 7152)
- g.exe (PID: 6216)
- 80.exe (PID: 5932)
- cmd.exe (PID: 5964)
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- alex111111.exe (PID: 8836)
- gold.rim.exe (PID: 8668)
- tester.exe (PID: 2304)
- done12312.exe (PID: 10372)
- AA_v3.exe (PID: 11072)
- vc17x64.exe (PID: 10260)
- client2.exe (PID: 6932)
- msiexec.exe (PID: 8560)
There is functionality for taking screenshot (YARA)
- Client.exe (PID: 3076)
Executes as Windows Service
- fadzwm.exe (PID: 5516)
- g.exe (PID: 6216)
- AA_v3.exe (PID: 11072)
Hides command output
- cmd.exe (PID: 5584)
Executing commands from ".cmd" file
- QuizPokemon.exe (PID: 5012)
Checks for external IP
- XClient.exe (PID: 4328)
- svchost.exe (PID: 1080)
- FreePhotoShop%20Meme%20Coin%20Packs.exe (PID: 5728)
- Host.exe (PID: 5980)
- jrockekcurje.exe (PID: 5700)
- tRp.exe (PID: 6972)
- sgsdg.exe (PID: 3468)
- Creal.exe (PID: 7260)
- CefSharp.BrowsersSubprocess.exe (PID: 8284)
- boleto.exe (PID: 5696)
- Build.exe (PID: 8928)
- Client.exe (PID: 8296)
- bypass.exe (PID: 5640)
- cssgo.exe (PID: 8792)
- quasarat.exe (PID: 11232)
Uses ATTRIB.EXE to modify file attributes
- WannaCry.exe (PID: 2884)
- Bloxflip%20Predictor.exe (PID: 4564)
- cmd.exe (PID: 1664)
Uses ICACLS.EXE to modify access control lists
- WannaCry.exe (PID: 2884)
Uses NETSH.EXE to add a firewall rule or allowed programs
- fusca%20game.exe (PID: 2800)
- svchost.exe (PID: 5072)
- govno__dlya_jertwy.exe (PID: 7844)
- SteamDetector.exe (PID: 7928)
- server.exe (PID: 5196)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 4328)
- Host.exe (PID: 5980)
- tRp.exe (PID: 6972)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6868)
- cmd.exe (PID: 1664)
- cmd.exe (PID: 13812)
- cmd.exe (PID: 13376)
Malware-specific behavior (creating "System.dll" in Temp)
- haozip_tiny.201805.exe (PID: 7480)
- haozip.convertimg.exe (PID: 4872)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 3408)
Get information on the list of running processes
- cmd.exe (PID: 5964)
Identifying current user with WHOAMI command
- %D1%83%D1%81%D0%B5%D1%80%D0%BB%D0%BE%D0%BD%D0%B32.exe (PID: 7096)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5964)
Drops 7-zip archiver for unpacking
- cabal.exe (PID: 3580)
Suspicious file concatenation
- cmd.exe (PID: 8208)
Starts the AutoIt3 executable file
- cmd.exe (PID: 5964)
Starts application with an unusual extension
- cmd.exe (PID: 5964)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 5116)
The process drops C-runtime libraries
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- XMZTSVYE_l10_wix4_dash.exe (PID: 7432)
- tester.exe (PID: 2304)
- ui.exe (PID: 10860)
Possible Social Engineering Attempted
- svchost.exe (PID: 1080)
Process drops python dynamic module
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- tester.exe (PID: 2304)
- ui.exe (PID: 10860)
PUTTY has been detected
- svc1.exe (PID: 3888)
- svc1.exe (PID: 3888)
Node.exe was dropped
- 4363463463464363463463463.exe (PID: 2068)
Uses WMIC.EXE to obtain computer system information
- ckjg.exe (PID: 1036)
Connects to FTP
- tftp.exe (PID: 2588)
- tftp.exe (PID: 12516)
Creates new registry property (POWERSHELL)
- powershell.exe (PID: 3504)
Found strings related to reading or modifying Windows Defender settings
- Wsystem.exe (PID: 9584)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5116)
- cmd.exe (PID: 7744)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2904)
The process executes VB scripts
- taskmoder.exe (PID: 11844)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 11408)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- safman_setup.exe (PID: 2508)
- safman_setup.tmp (PID: 2388)
- image%20logger.exe (PID: 1648)
- Client.exe (PID: 3076)
- jajajdva.exe (PID: 2356)
- syteam.exe (PID: 3776)
- news_01.exe (PID: 3696)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2856)
- aaa%20(3).exe (PID: 124)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 2708)
- cabal.exe (PID: 3580)
- SWID_reader.exe (PID: 1484)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2720)
- test1.exe (PID: 2724)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3408)
- svchost.exe (PID: 2276)
- 4363463463464363463463463.exe (PID: 3848)
- crypted.41.exe (PID: 4252)
- 4363463463464363463463463.exe (PID: 4128)
- XClient.exe (PID: 4328)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- Client.exe (PID: 3076)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2952)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- Client.exe (PID: 3076)
- image%20logger.exe (PID: 1648)
- syteam.exe (PID: 3776)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3052)
- cabal.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3188)
- aaa%20(3).exe (PID: 124)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 1164)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2336)
- Client-built.exe (PID: 2612)
- Client.exe (PID: 3076)
- safman_setup.tmp (PID: 2388)
- image%20logger.exe (PID: 1648)
- jajajdva.exe (PID: 2356)
- syteam.exe (PID: 3776)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2856)
- aaa%20(3).exe (PID: 124)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 532)
- cabal.exe (PID: 3580)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3244)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 2720)
Disables trace logs
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3892)
Creates files or folders in the user directory
- Client-built.exe (PID: 2612)
- 4363463463464363463463463.exe (PID: 2336)
- jajajdva.exe (PID: 2356)
Create files in a temporary directory
- safman_setup.exe (PID: 2508)
- image%20logger.exe (PID: 1648)
- test1.exe (PID: 2724)
The sample compiled with russian language support
- safman_setup.tmp (PID: 2388)
- 4363463463464363463463463.exe (PID: 2952)
- qwsrv3.3.tmp (PID: 7572)
- 1192915974.exe (PID: 10084)
- ChromeSetup.exe (PID: 9808)
Creates a software uninstall entry
- safman_setup.tmp (PID: 2388)
Creates files in the program directory
- safman_setup.tmp (PID: 2388)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 3816)
- 4363463463464363463463463.exe (PID: 3668)
- 4363463463464363463463463.exe (PID: 3292)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3364)
- 4363463463464363463463463.exe (PID: 2784)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4084)
- 4363463463464363463463463.exe (PID: 2876)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 1580)
- 4363463463464363463463463.exe (PID: 548)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2812)
- 4363463463464363463463463.exe (PID: 2840)
- 4363463463464363463463463.exe (PID: 1484)
- 4363463463464363463463463.exe (PID: 2212)
- 4363463463464363463463463.exe (PID: 3124)
- 4363463463464363463463463.exe (PID: 2576)
- 4363463463464363463463463.exe (PID: 3016)
- 4363463463464363463463463.exe (PID: 128)
- 4363463463464363463463463.exe (PID: 3432)
- 4363463463464363463463463.exe (PID: 524)
- 4363463463464363463463463.exe (PID: 2276)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2052)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3792)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 3104)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 2276)
- 4363463463464363463463463.exe (PID: 2988)
- 4363463463464363463463463.exe (PID: 2368)
- 4363463463464363463463463.exe (PID: 2916)
- 4363463463464363463463463.exe (PID: 2204)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 4128)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 4044)
- 4363463463464363463463463.exe (PID: 3188)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 1772)
- 4363463463464363463463463.exe (PID: 2720)
- qrtb.exe (PID: 5316)
- 4363463463464363463463463.exe (PID: 3848)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3768)
- icacls.exe (PID: 6152)
- 4363463463464363463463463.exe (PID: 2708)
- rlol.exe (PID: 6924)
- qwsrv3.3.exe (PID: 7056)
- 4363463463464363463463463.exe (PID: 3144)
- 4363463463464363463463463.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 2952)
- 4363463463464363463463463.exe (PID: 3956)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 10520)
- 4363463463464363463463463.exe (PID: 2068)
- 163.exe (PID: 6936)
- 4363463463464363463463463.exe (PID: 4128)
- 4363463463464363463463463.exe (PID: 2792)
- 1192915974.exe (PID: 10084)
- ChromeSetup.exe (PID: 9808)
- td.exe (PID: 10548)
- 4363463463464363463463463.exe (PID: 2856)
The sample compiled with english language support
- safman_setup.tmp (PID: 2388)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2720)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2068)
- 4363463463464363463463463.exe (PID: 3408)
- 4363463463464363463463463.exe (PID: 532)
- 4363463463464363463463463.exe (PID: 3144)
- WannaCry.exe (PID: 2884)
- 4363463463464363463463463.exe (PID: 2792)
- 4363463463464363463463463.exe (PID: 3108)
- 4363463463464363463463463.exe (PID: 2336)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3100)
- cabal.exe (PID: 3580)
- mixten.exe (PID: 8124)
- rlol.tmp (PID: 7600)
- qwsrv3.3.tmp (PID: 7572)
- IcarusLite-v1.1.13-win.exe (PID: 6032)
- 4363463463464363463463463.exe (PID: 3260)
- client.exe (PID: 8440)
- 4363463463464363463463463.exe (PID: 3652)
- 4363463463464363463463463.exe (PID: 3848)
- XMZTSVYE_l10_wix4_dash.exe (PID: 4672)
- 4363463463464363463463463.exe (PID: 3892)
- 4363463463464363463463463.exe (PID: 3052)
- XMZTSVYE_l10_wix4_dash.exe (PID: 7432)
- 4363463463464363463463463.exe (PID: 3668)
- tester.exe (PID: 2304)
- 4363463463464363463463463.exe (PID: 2700)
- 4363463463464363463463463.exe (PID: 2952)
- Shopzilla.pif (PID: 8464)
- 4363463463464363463463463.exe (PID: 1164)
- vc17x64.exe (PID: 124)
- 4363463463464363463463463.exe (PID: 1772)
- ui.exe (PID: 10860)
- c4284a2a6c1b60247944a03cbaf930c5.exe (PID: 12612)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 13416)
- 1192915974.exe (PID: 10084)
- ClientRun.exe (PID: 9560)
- iexplore.exe (PID: 13208)
- ChromeSetup.exe (PID: 9808)
Detects InnoSetup installer (YARA)
- safman_setup.exe (PID: 2508)
- safman_setup.tmp (PID: 2388)
Compiled with Borland Delphi (YARA)
- safman_setup.tmp (PID: 2388)
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3052)
- 4363463463464363463463463.exe (PID: 2708)
- 4363463463464363463463463.exe (PID: 1020)
The sample compiled with korean language support
- 4363463463464363463463463.exe (PID: 4016)
- 4363463463464363463463463.exe (PID: 3260)
- LauncherLoader.exe (PID: 3576)
- client.exe (PID: 8440)
- NewkeyLauncher.exe (PID: 6520)
- 4363463463464363463463463.exe (PID: 1772)
- ClientRun.exe (PID: 9560)
- ChromeSetup.exe (PID: 9808)
The sample compiled with turkish language support
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 3408)
- ChromeSetup.exe (PID: 9808)
Creates a new folder
- cmd.exe (PID: 5100)
Application launched itself
- msedge.exe (PID: 3920)
Changes the display of characters in the console
- cmd.exe (PID: 5116)
- cmd.exe (PID: 7744)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7580)
- iexplore.exe (PID: 13208)
The sample compiled with arabic language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with czech language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with bulgarian language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with german language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with polish language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with portuguese language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with swedish language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with slovak language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with spanish language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with french language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with Indonesian language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with Italian language support
- ChromeSetup.exe (PID: 9808)
The sample compiled with japanese language support
- ChromeSetup.exe (PID: 9808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(3076) Client.exe
Version1.4.1
C2 (2)192.168.181.84:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex1ed20179-691a-4881-806d-c5d12340d8e9
StartupQuasar Client Startup
TagOffice04
LogDirLogs
SignatureCT1m/O/1jvn+7v+64PqcgWZOSnx7XHx4eu5IXtO3UODYhODL23FxYFVsxHGpWShxrTKhPB5Jw2/KkQwxIDCigANcNFsCrSmUjWvkwnl0P+slb1X/1hXQnCejEoo9ktrGTa4lHkWuPPvALVxkg45iHSMcfoxCb7s7v61xZpdjWXk+3MGmroHWUv2f3dD9+2u9aSVXdDWSil2NE7wrtqy0gjcMzkkViw70ITzwxktORRZZFZGIDT0SEoXWPoKeknxi5rXlWn1ka7DRhfLM9MQJZf/Yk73hml0Wo7AeOmtonX8m...
CertificateMIIE9DCCAtygAwIBAgIQALAePc6T34SzQs5umdrEeTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTIwMjAzNTc1NloYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAqtanyzzulvPG4gUiOec9Z0lwKaOWvV9EpexaUcrvqOmxwnFtiizQIvtw5Ogqbcbk14EVJ3/2...
AsyncRat
(PID) Process(3776) syteam.exe
C2 (1)18.141.204.5
Ports (1)80
Version0.5.7B
BotnetDefault
Options
AutoRuntrue
MutexAsyncMutex_6SI8OkPnk
InstallFolder%Temp%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAIQIWleL0frBIeSQnuAJuTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwMzIyMDMyODIxWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKX5mwRbyfv2cMBQSb31Ov/ZLK9YMWp68guIQ9AGKqyfGCo0xK9xsD4RQYo8ukDIvCwxawZHu/j4...
Server_SignatureSlw1S0CB1MQ0Vr7eeR5UA3J0XHOjJfspjFdk9C6rTOXRPzGxJH9uSNOY0Ql6J2roa9jMR/bJB/E/i8GIoDD7e//tlmVxAGgqJ8fn3DRgSNMnXjztqGPEKSPRVKbTzOIbMV0KnS5/cT9+Qf69BLeEpIEuljR+S5KIvCYMorbzyFu+5p3mwc9iZ+1WmC5qCncICclFsrnOVGu1Aqc2FuRKtRIWBfJtszgh5m5zKgCJzFL6jpOifEdmqY/uzB1/lkug0Iwc9e/YN3Q0xCmXM+mO5FeoC9MJGXNYzRFbagGG/bNA...
Keys
AESf2b2168fe19a40d2a006ef4a806ae1da93537f874c52238edc371debd2b651da
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
914
Monitored processes
628
Malicious processes
117
Suspicious processes
50
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\Desktop\Files\aaa%20(3).exe" | C:\Users\admin\Desktop\Files\aaa%20(3).exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 124 | "C:\Users\admin\Desktop\Files\vc17x64.exe" -burn.unelevated BurnPipe.{0136E0B2-CCC3-4DB7-BB92-9C427683494A} {2844AFE8-2DB1-4D2A-9F15-FACFDDD07FE2} 10260 | C:\Users\admin\Desktop\Files\vc17x64.exe | vc17x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2017 Redistributable (x64) - 14.10.25008 Version: 14.10.25008.0 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 184 | schtasks.exe /create /tn "MindTechPro360" /tr "wscript //B 'C:\Users\admin\AppData\Local\TechMind360 Innovations Co\MindTechPro360.js'" /sc onlogon /F /RL HIGHEST | C:\Windows\System32\schtasks.exe | — | Shopzilla.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 288 | "schtasks" /create /tn "Quasar Client Startup" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 344 | "C:\Users\admin\Desktop\Files\B0B34B3375B144C680A0456FFDD639A0.exe" | C:\Users\admin\Desktop\Files\B0B34B3375B144C680A0456FFDD639A0.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 532 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 548 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 580 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\Files\XClient.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | XClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
399 304
Read events
395 201
Write events
3 938
Delete events
165
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6D3E3157 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D69B561148F01C77C54578C10926DF5B856976AD |
Value: | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 5C000000010000000400000000080000530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB0282000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
Value: | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000497904B0EB8719AC47B0BC11519B74D0090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3491D00000001000000100000002E0D6875874A44C820912E85E964CFDB140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B40B000000010000001C0000005300650063007400690067006F002000280041004100410029000000620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF41900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA253000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2336) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
727
Suspicious files
2 044
Text files
1 179
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3444 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs2B52.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Client-built.exe | executable | |
MD5:6D6B0853A2AAC3F0FE8403826E778CFD | SHA256:89FA63D15ED2D1EFECB7CEA57600721B74F90E2F83E213F556759E788133A75D | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\safman_setup.exe | executable | |
MD5:5A7B4D6DE8B2812145390820A44F968A | SHA256:1B6FE9BE14D7228399C7131D42D6A32F90055BE38F3EF22B48B167DC070B8B58 | |||
| 3444 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs2B41.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\30D802E0E248FEE17AAF4A62594CC75A | binary | |
MD5:6353032CEA6A3163E602CA5DDC123654 | SHA256:46ADC4D6921D0637F998A254560E959A92DF2EB935C302F53946549CC0B09CAF | |||
| 2612 | Client-built.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:6D6B0853A2AAC3F0FE8403826E778CFD | SHA256:89FA63D15ED2D1EFECB7CEA57600721B74F90E2F83E213F556759E788133A75D | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\loader.exe | executable | |
MD5:E68E90150A7C7988436F9814416F50B4 | SHA256:70A0F07A778BD5AD82FA219A7B73A94175BEC448203E1A8A162C93FCA4549668 | |||
| 2336 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\image%20logger.exe | executable | |
MD5:520E6035E15A9422E1C4CBADA69263AA | SHA256:99A06D8A9EDA7BA2D19DA54C2759A783E20922A73A4893CACCC220CDAA27A883 | |||
| 3552 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs4F93.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2388 | safman_setup.tmp | C:\SAF\SAFMan\UnInstall\unins000.exe | executable | |
MD5:2E6D853F3A3EADF91FF38A3391ECB2D3 | SHA256:AC898547B027016504BDDDBD78485ED1E17E1B3120B91233527DEDB8DA08DD1B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
299
TCP/UDP connections
7 960
DNS requests
330
Threats
1 000
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3052 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/Deroxs/PowerRat-leak/raw/refs/heads/main/PowerRat.exe | unknown | — | — | whitelisted |
4044 | 4363463463464363463463463.exe | GET | 200 | 101.72.254.91:80 | http://download.kaobeitu.com/kaobeitu/mini/v1.0.7.16/mini_04.exe | unknown | — | — | malicious |
3956 | 4363463463464363463463463.exe | GET | 200 | 60.191.208.187:820 | http://ftp.ywxww.net:820/PCHunter64.exe | unknown | — | — | unknown |
2336 | 4363463463464363463463463.exe | GET | 200 | 154.29.78.35:80 | http://tirtasentosa.com/give/ukbros001.exe | unknown | — | — | unknown |
2336 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.4:80 | http://github.com/kidxnox/image-logger/raw/refs/heads/main/image%20logger.exe | unknown | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | GET | 200 | 172.64.149.23:80 | http://crt.sectigo.com/SectigoRSADomainValidationSecureServerCA.crt | unknown | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | GET | 200 | 114.55.100.165:19998 | http://114.55.100.165:19998/02.08.2022.exe | unknown | — | — | unknown |
2336 | 4363463463464363463463463.exe | GET | 200 | 101.72.254.91:80 | http://download.kaobeitu.com/kaobeitu/news/v1.0.7.31/news_01.exe | unknown | — | — | malicious |
3652 | 4363463463464363463463463.exe | GET | 200 | 43.226.39.44:5988 | http://43.226.39.44:5988/test1.exe | unknown | — | — | unknown |
4044 | 4363463463464363463463463.exe | GET | 200 | 217.15.164.94:80 | http://217.15.164.94/update/client/cabal.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | 4363463463464363463463463.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
2336 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2336 | 4363463463464363463463463.exe | 154.29.78.35:80 | tirtasentosa.com | COGENT-174 | US | malicious |
2336 | 4363463463464363463463463.exe | 45.130.41.158:443 | www.saf-oil.ru | Beget LLC | RU | malicious |
2336 | 4363463463464363463463463.exe | 140.82.121.4:80 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
tirtasentosa.com |
| unknown |
www.saf-oil.ru |
| malicious |
softwarebreakers.info |
| malicious |
crt.sectigo.com |
| whitelisted |
download.kaobeitu.com |
| malicious |
www.kokopellz.4fan.cz |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2336 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2336 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2336 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3668 | 4363463463464363463463463.exe | Malware Command and Control Activity Detected | ET MALWARE Supershell CnC Activity |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
3668 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3956 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3956 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
3956 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|