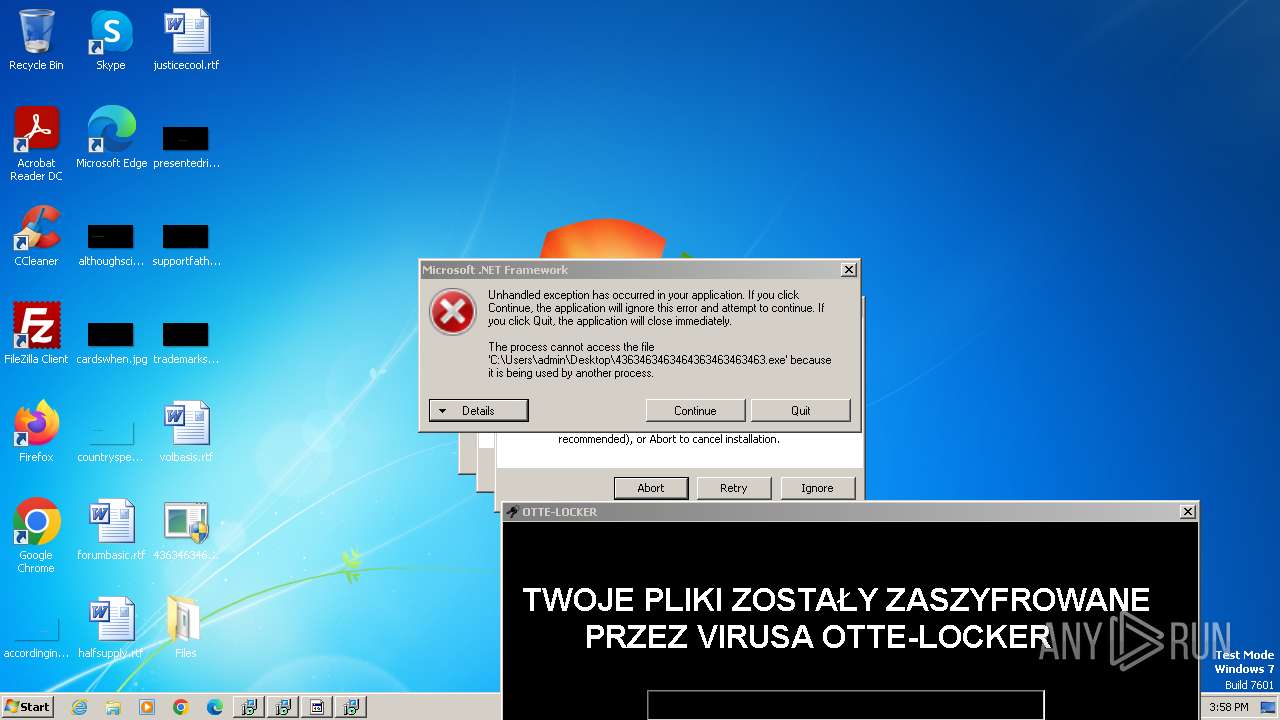
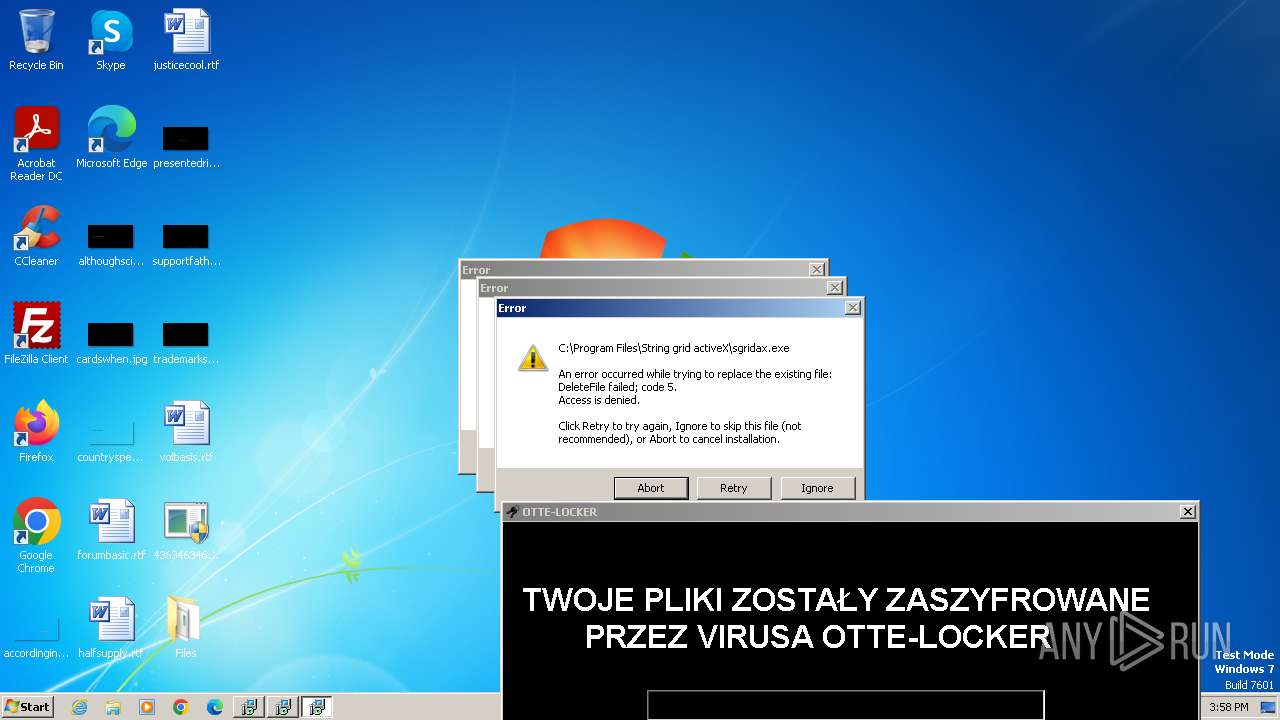
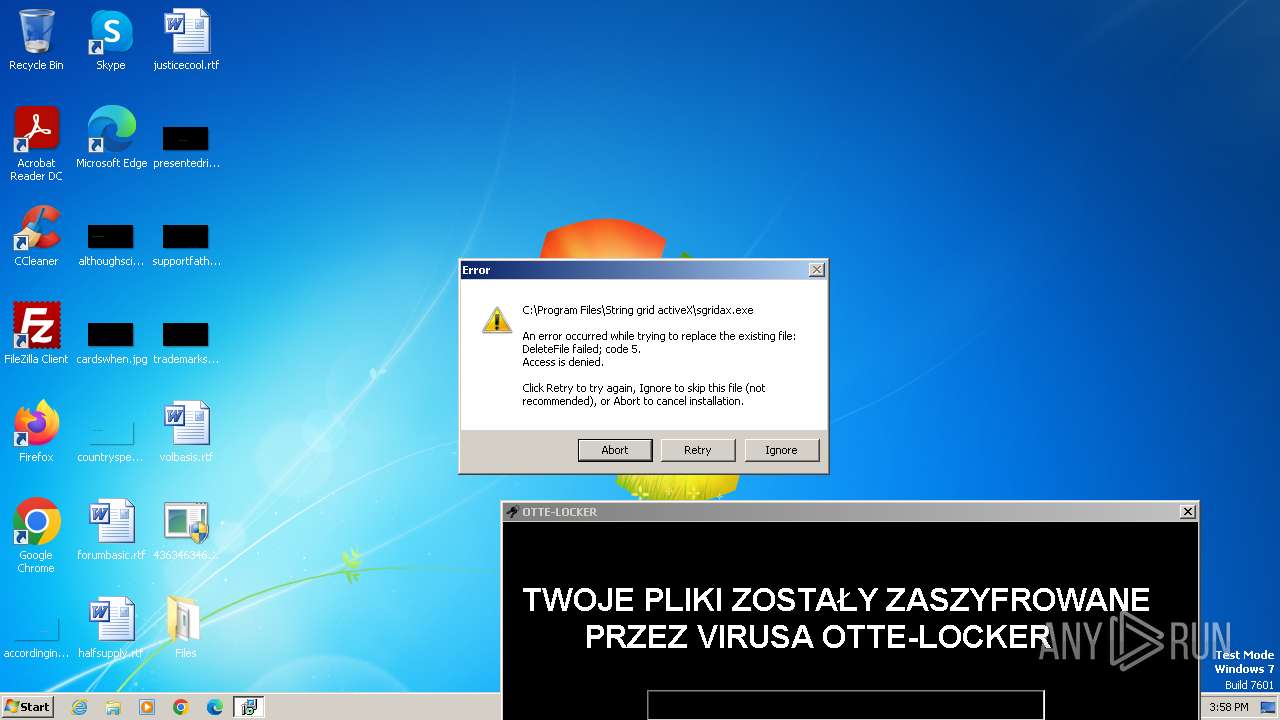
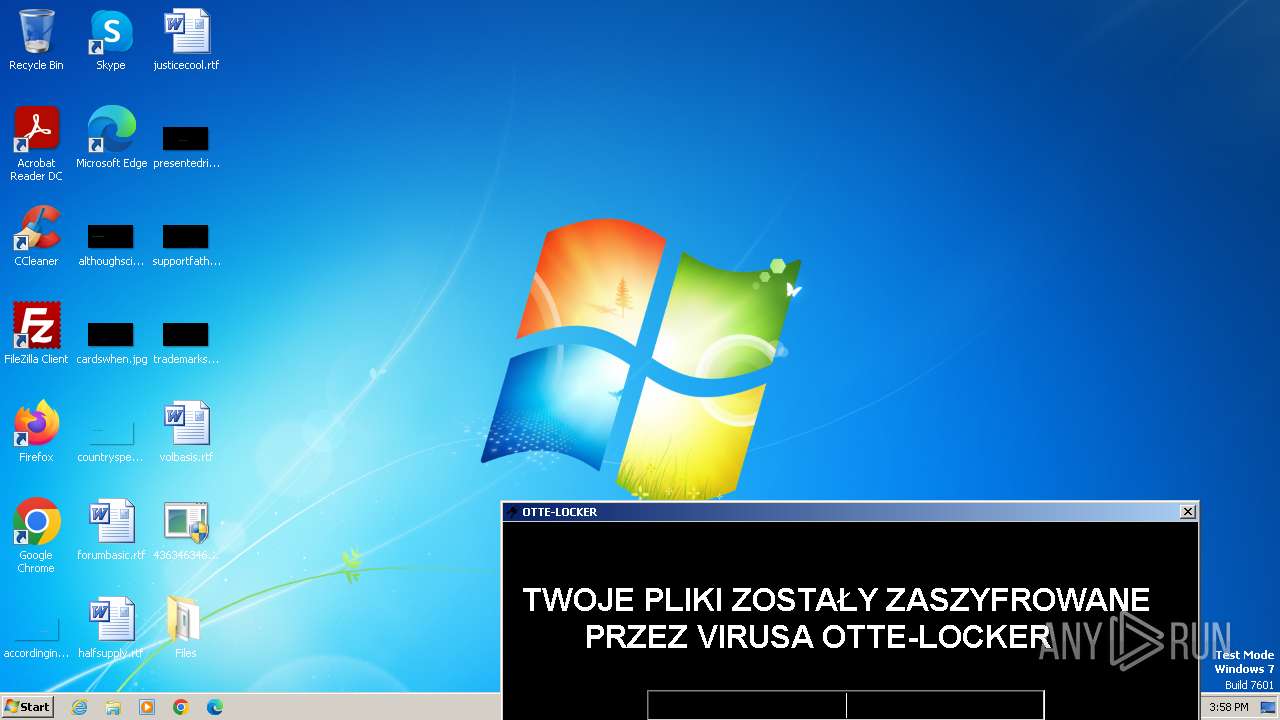
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/7b3d4c2b-0a66-4bf9-b1d4-b09cef2f717d |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 29, 2023, 15:56:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2256)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2240)
- cmd.exe (PID: 2548)
Create files in the Startup directory
- rest.exe (PID: 2900)
- Amdau.exe (PID: 1904)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2916)
Risepro uses scheduled tasks to run itself
- cmd.exe (PID: 2548)
- cmd.exe (PID: 2916)
REMCOS has been detected (YARA)
- 6.exe (PID: 2328)
Steals credentials from Web Browsers
- rest.exe (PID: 2900)
- 5xb6nM0.exe (PID: 2564)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 3040)
- 1701610814-Dvnzfr.exe (PID: 3608)
- dialer.exe (PID: 2540)
- fcc.exe (PID: 5708)
- 5xb6nM0.exe (PID: 2564)
- rest.exe (PID: 2900)
REDLINE has been detected (YARA)
- againn.exe (PID: 2596)
ASYNCRAT has been detected (YARA)
- calc.exe (PID: 3064)
NANOCORE has been detected (YARA)
- CasPol.exe (PID: 4068)
AMADEY has been detected (YARA)
- jsc.exe (PID: 2452)
Changes the login/logoff helper path in the registry
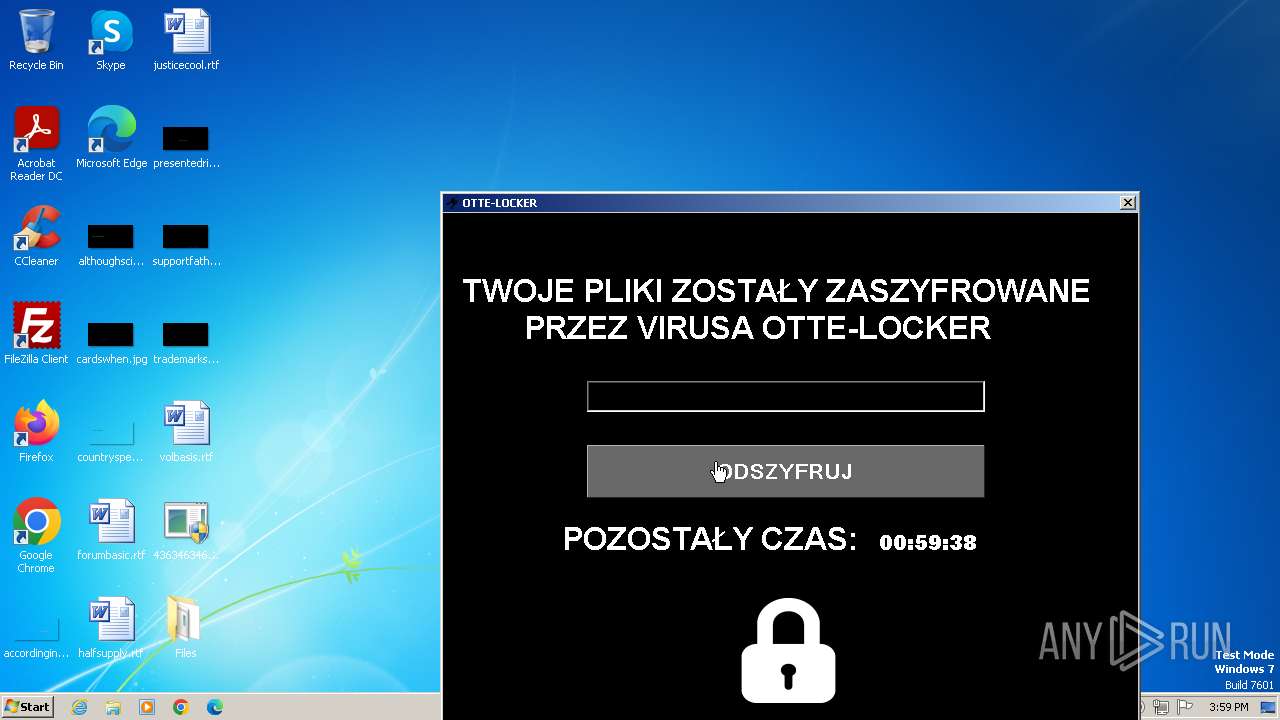
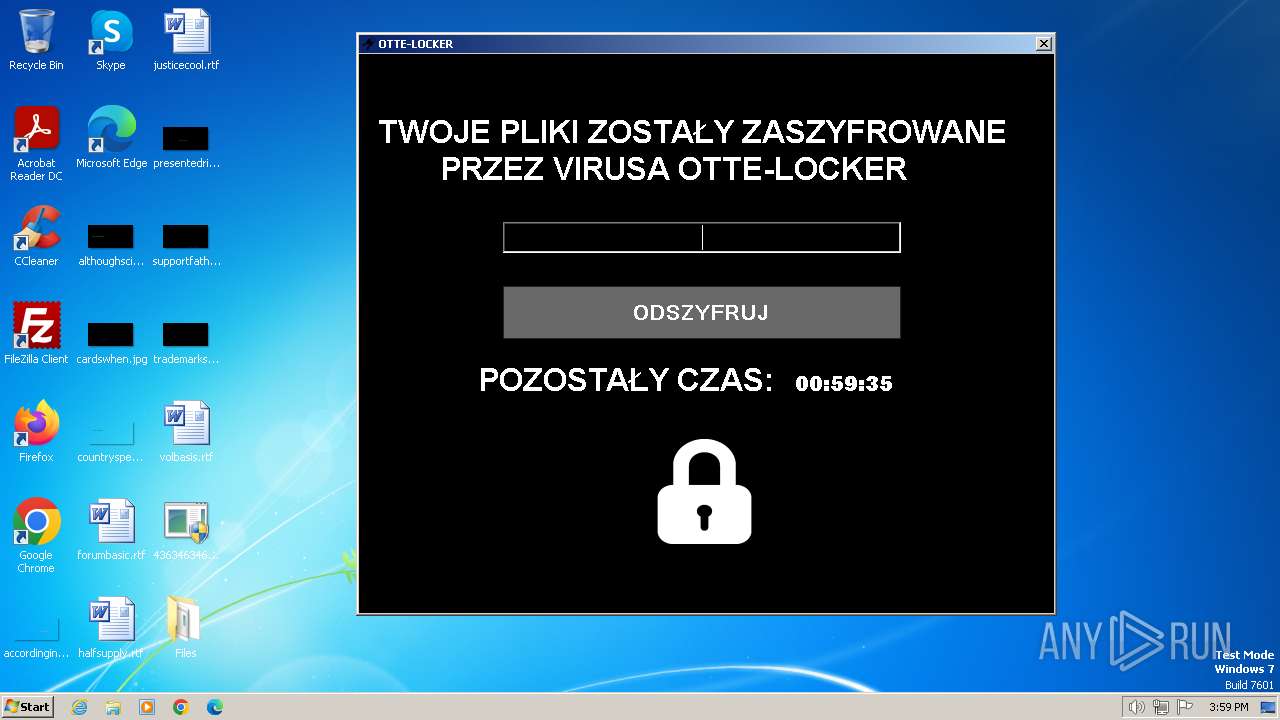
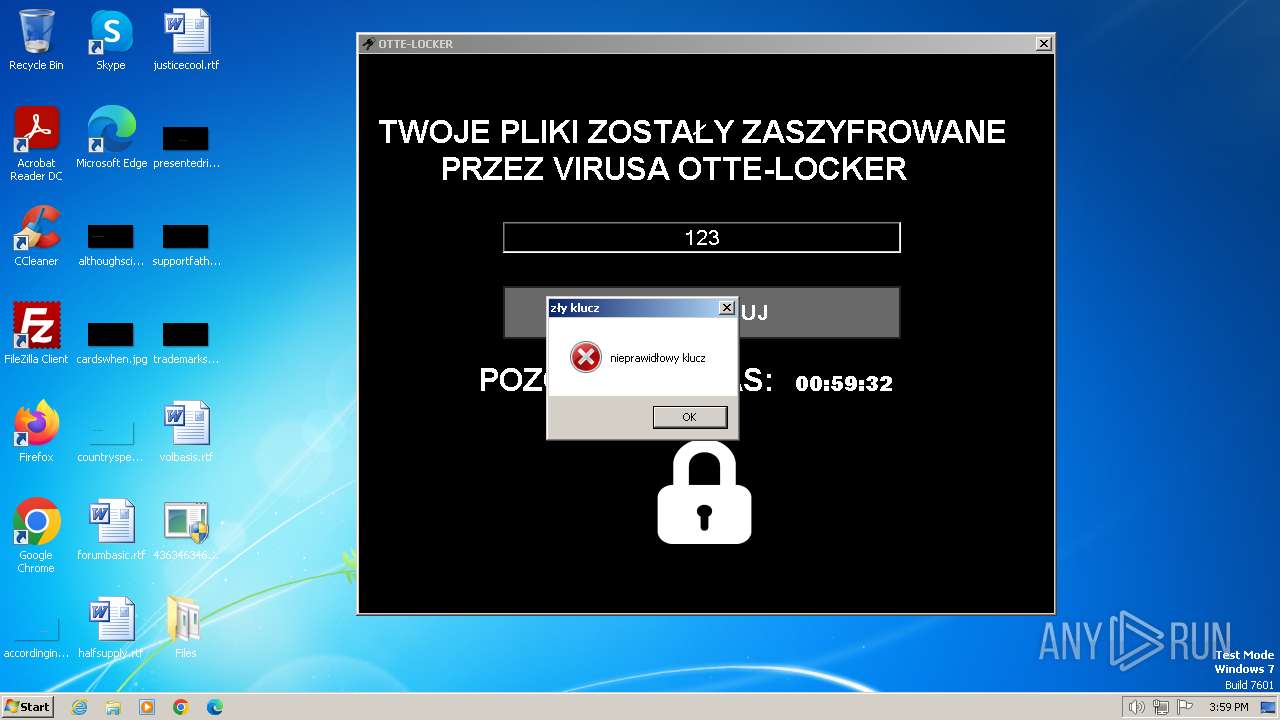
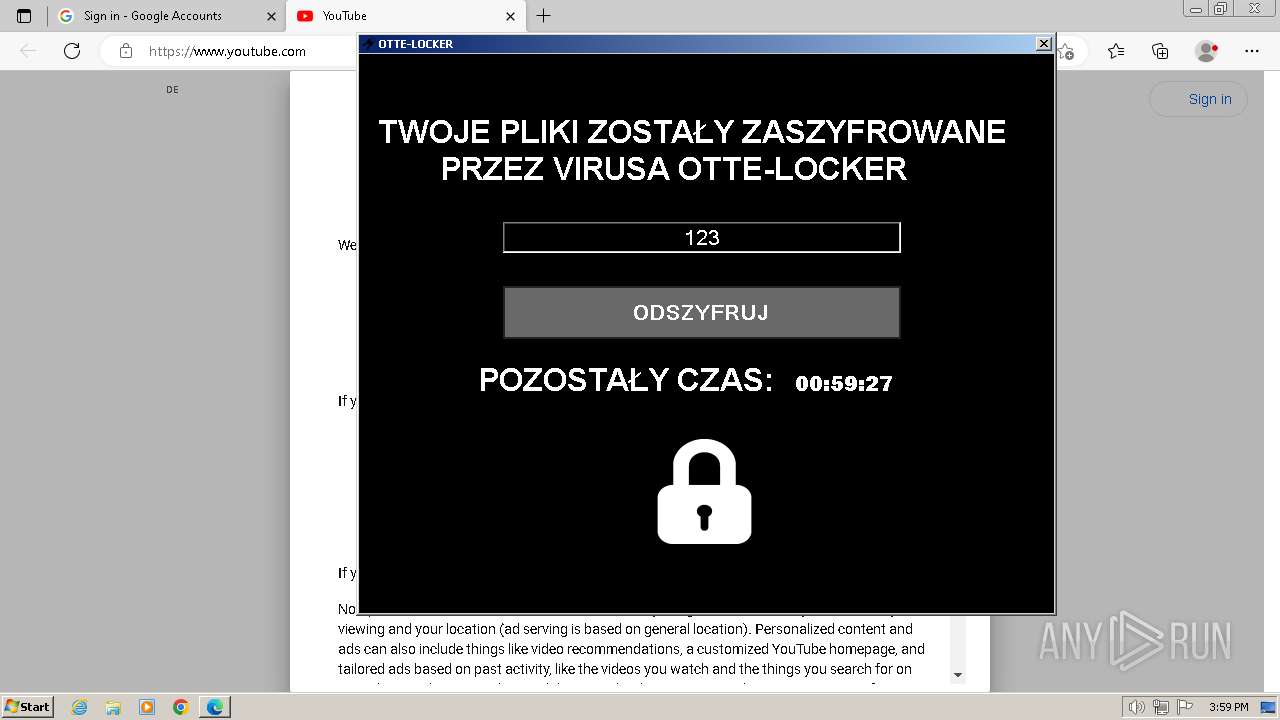
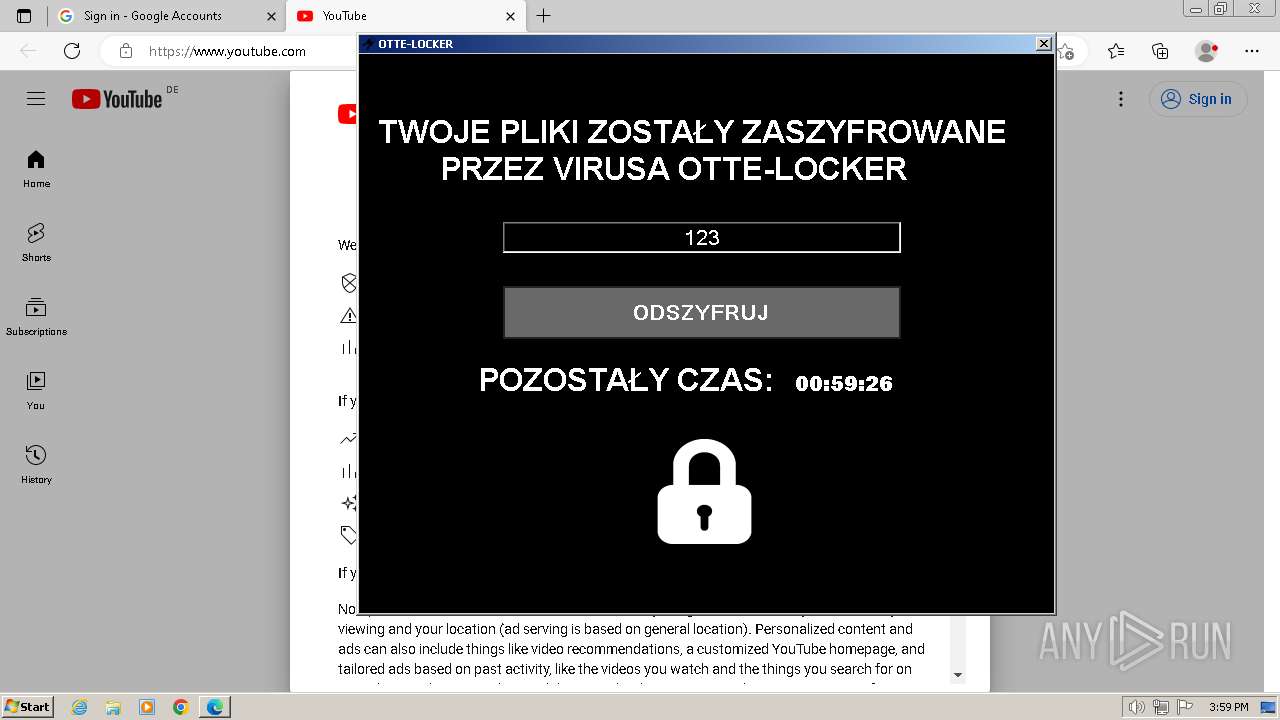
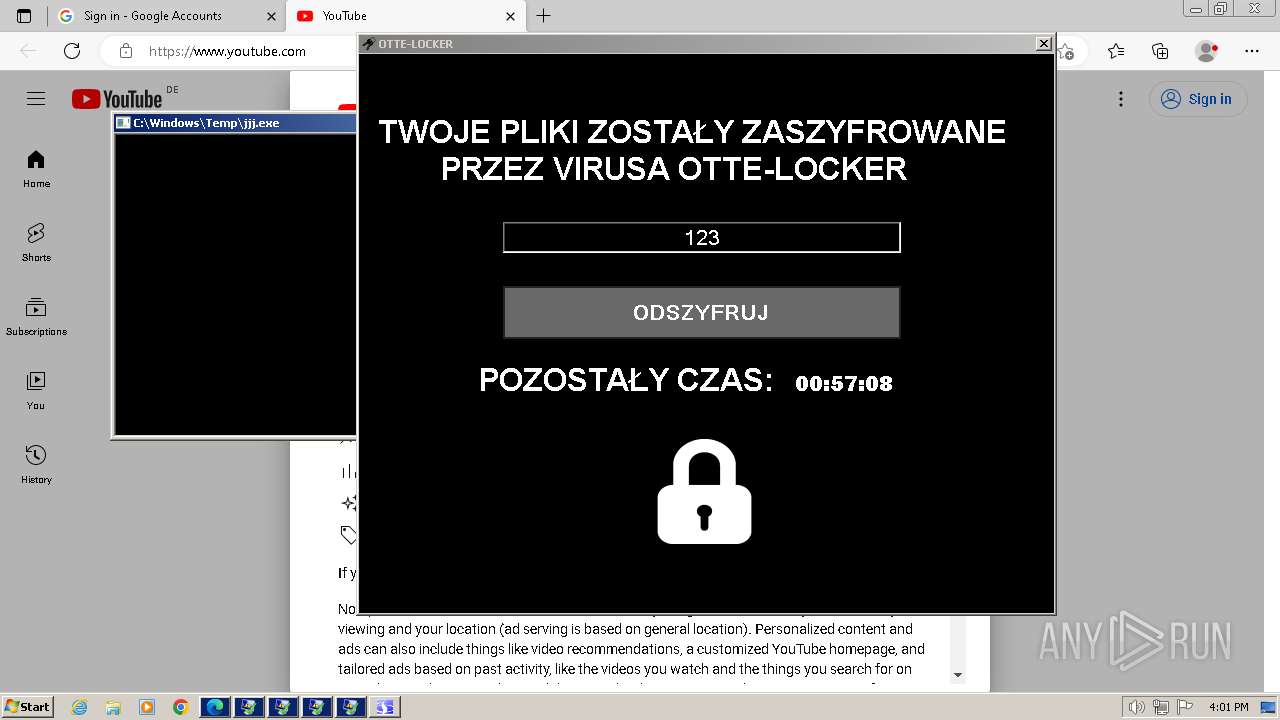
- Otte-Locker.exe (PID: 2136)
Disables Windows Defender
- 5xb6nM0.exe (PID: 2564)
RISEPRO has been detected (YARA)
- 5xb6nM0.exe (PID: 2564)
LUMMA has been detected (YARA)
- AppLaunch.exe (PID: 1956)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 5664)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 5664)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 5664)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2256)
- rest.exe (PID: 2900)
- Vpeswawqko.exe (PID: 1528)
- 5xb6nM0.exe (PID: 2564)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2256)
- peinf.exe (PID: 2440)
- cbchr.exe (PID: 2740)
- sysplorsv.exe (PID: 3072)
- rest.exe (PID: 2900)
- CasPol.exe (PID: 4068)
- pdf.exe (PID: 2208)
- OpenAndClose.exe (PID: 2076)
- jsc.exe (PID: 2452)
- Vpeswawqko.exe (PID: 1528)
- sgridax.exe (PID: 1544)
- Journal.exe (PID: 1924)
- ghjk.exe (PID: 1864)
- 2DR9527.exe (PID: 560)
- powershell.exe (PID: 1268)
- 5xb6nM0.exe (PID: 2564)
- powershell.exe (PID: 3100)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E6%9C%8D%E5%8A%A1%E7%AB%AF_sos.exe (PID: 2660)
- 6c)h7-RX{f.exe (PID: 584)
- sgridax.exe (PID: 3188)
- AppLaunch.exe (PID: 1956)
- powershell.exe (PID: 4596)
- conhost.exe (PID: 5192)
- cmd.exe (PID: 5272)
- ghjkl.exe (PID: 5324)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 5512)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2256)
Reads the Windows owner or organization settings
- tuc3.tmp (PID: 1808)
- tuc4.tmp (PID: 2756)
- tuc5.tmp (PID: 2856)
- tuc7.tmp (PID: 2300)
- tuc2.tmp (PID: 2492)
- safman_setup.tmp (PID: 5168)
Starts CMD.EXE for commands execution
- cbchr.exe (PID: 2740)
- rest.exe (PID: 2900)
- conhost.exe (PID: 5192)
- fcc.exe (PID: 5708)
Executing commands from a ".bat" file
- cbchr.exe (PID: 2740)
- conhost.exe (PID: 5192)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2388)
Searches for installed software
- tuc4.tmp (PID: 2756)
- RegAsm.exe (PID: 3040)
- rest.exe (PID: 2900)
- tuc5.tmp (PID: 2856)
- tuc7.tmp (PID: 2300)
- tuc2.tmp (PID: 2492)
- dialer.exe (PID: 2540)
- 5xb6nM0.exe (PID: 2564)
Reads browser cookies
- RegAsm.exe (PID: 3040)
Accesses Microsoft Outlook profiles
- rest.exe (PID: 2900)
- dialer.exe (PID: 2540)
- 5xb6nM0.exe (PID: 2564)
The process executes VB scripts
- pdf.exe (PID: 2208)
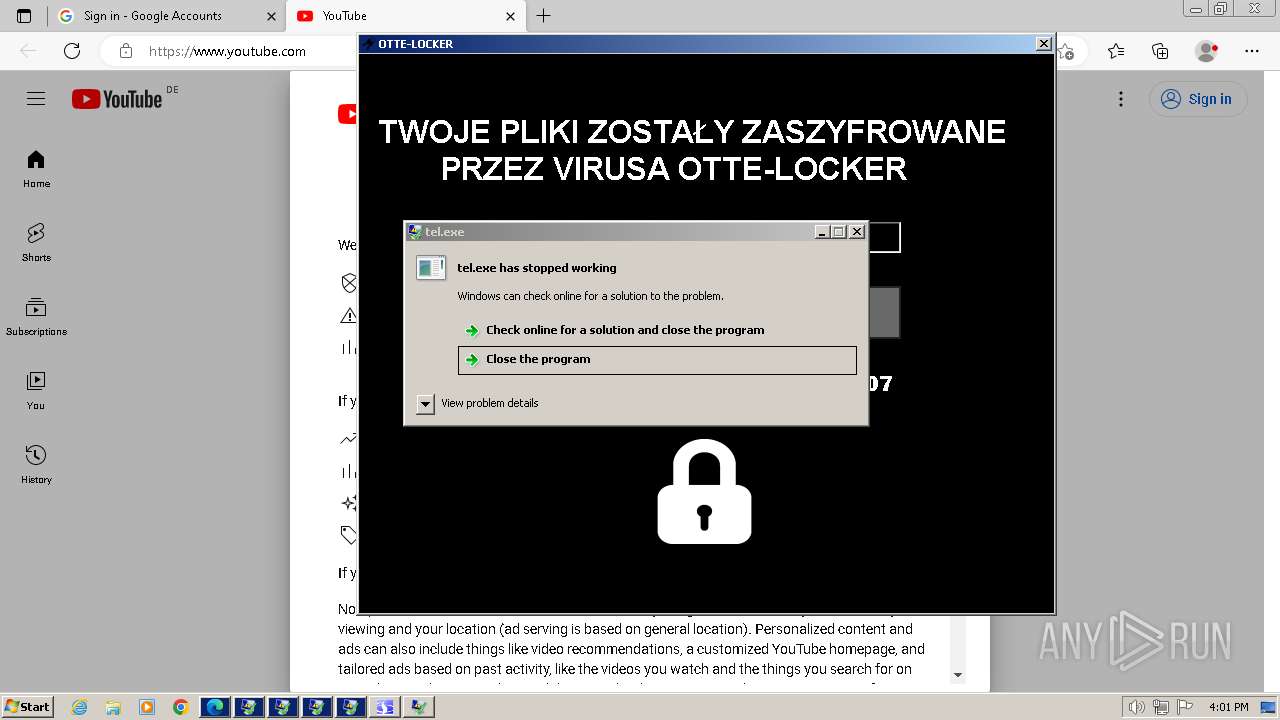
- tel.exe (PID: 5676)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 5512)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2256)
Changes the desktop background image
- Otte-Locker.exe (PID: 2136)
Query Microsoft Defender preferences
- 5xb6nM0.exe (PID: 2564)
Starts POWERSHELL.EXE for commands execution
- 5xb6nM0.exe (PID: 2564)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2540)
- dialer.exe (PID: 5856)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1268)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 4596)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 2540)
Reads the BIOS version
- new.exe (PID: 2764)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5272)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2256)
- 987123.exe (PID: 1584)
- tuc3.exe (PID: 1848)
- tuc3.tmp (PID: 1808)
- sgridax.exe (PID: 1796)
- hv.exe (PID: 1748)
- peinf.exe (PID: 2440)
- sgridax.exe (PID: 1544)
- 6.exe (PID: 2328)
- cbchr.exe (PID: 2740)
- 513723952.exe (PID: 2808)
- tuc4.exe (PID: 1556)
- tuc4.tmp (PID: 2756)
- againn.exe (PID: 2596)
- rest.exe (PID: 2900)
- 659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe (PID: 908)
- calc.exe (PID: 3064)
- sysplorsv.exe (PID: 3072)
- sgridax.exe (PID: 3128)
- RegAsm.exe (PID: 3040)
- pinguin.exe (PID: 3180)
- sgridax.exe (PID: 3188)
- QubpyznbC7neo.exe (PID: 1016)
- CasPol.exe (PID: 4068)
- pdf.exe (PID: 2208)
- vbc.exe (PID: 1056)
- OpenAndClose.exe (PID: 2076)
- aiitoo.exe (PID: 2948)
- v1220-55000.exe (PID: 3276)
- tuc5.exe (PID: 3336)
- tuc5.tmp (PID: 2856)
- tuc7.exe (PID: 2088)
- tuc7.tmp (PID: 2300)
- Vpeswawqko.exe (PID: 1528)
- Amdau.exe (PID: 1904)
- jsc.exe (PID: 2452)
- Otte-Locker.exe (PID: 2136)
- tuc2.exe (PID: 2308)
- tuc2.tmp (PID: 2492)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 952)
- ghjk.exe (PID: 1864)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 2784)
- Journal.exe (PID: 1924)
- BLduscfibj.exe (PID: 3576)
- ghjk.exe (PID: 3804)
- BLduscfibj.exe (PID: 2152)
- Gu2HY45.exe (PID: 2348)
- jw3Bi12.exe (PID: 2340)
- foxi.exe (PID: 3896)
- 2DR9527.exe (PID: 560)
- 5xb6nM0.exe (PID: 2564)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 2380)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E6%9C%8D%E5%8A%A1%E7%AB%AF_sos.exe (PID: 2660)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 920)
- 891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe (PID: 604)
- new.exe (PID: 2764)
- 1701610814-Dvnzfr.exe (PID: 3608)
- idrB5Event.exe (PID: 1316)
- wmprph.exe (PID: 3100)
- 6c)h7-RX{f.exe (PID: 2496)
- 6c)h7-RX{f.exe (PID: 584)
- AppLaunch.exe (PID: 1956)
- StringIds.exe (PID: 4320)
- StringIds.exe (PID: 4344)
- MSBuild.exe (PID: 4488)
- safman_setup.exe (PID: 5160)
- safman_setup.tmp (PID: 5168)
- MSBuild.exe (PID: 4524)
- soft.exe (PID: 5240)
- conhost.exe (PID: 5192)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 5248)
- mode.com (PID: 5296)
- ghjkl.exe (PID: 5324)
- ghjkl.exe (PID: 5384)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 5408)
- BLduscfibj.exe (PID: 5428)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 5512)
- BLduscfibj.exe (PID: 5360)
- fcc.exe (PID: 5708)
- tel.exe (PID: 5676)
- jjj.exe (PID: 5740)
- vbc.exe (PID: 5796)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2256)
- tuc3.tmp (PID: 1808)
- sgridax.exe (PID: 1796)
- hv.exe (PID: 1748)
- peinf.exe (PID: 2440)
- 6.exe (PID: 2328)
- cbchr.exe (PID: 2740)
- tuc4.tmp (PID: 2756)
- rest.exe (PID: 2900)
- againn.exe (PID: 2596)
- calc.exe (PID: 3064)
- pinguin.exe (PID: 3180)
- RegAsm.exe (PID: 3040)
- sgridax.exe (PID: 3128)
- sysplorsv.exe (PID: 3072)
- QubpyznbC7neo.exe (PID: 1016)
- CasPol.exe (PID: 4068)
- pdf.exe (PID: 2208)
- vbc.exe (PID: 1056)
- OpenAndClose.exe (PID: 2076)
- tuc5.tmp (PID: 2856)
- Amdau.exe (PID: 1904)
- tuc7.tmp (PID: 2300)
- Vpeswawqko.exe (PID: 1528)
- jsc.exe (PID: 2452)
- Otte-Locker.exe (PID: 2136)
- tuc2.tmp (PID: 2492)
- sgridax.exe (PID: 1544)
- ghjk.exe (PID: 1864)
- Journal.exe (PID: 1924)
- BLduscfibj.exe (PID: 3576)
- BLduscfibj.exe (PID: 2152)
- 2DR9527.exe (PID: 560)
- 5xb6nM0.exe (PID: 2564)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E6%9C%8D%E5%8A%A1%E7%AB%AF_sos.exe (PID: 2660)
- new.exe (PID: 2764)
- 1701610814-Dvnzfr.exe (PID: 3608)
- 6c)h7-RX{f.exe (PID: 2496)
- 6c)h7-RX{f.exe (PID: 584)
- sgridax.exe (PID: 3188)
- AppLaunch.exe (PID: 1956)
- StringIds.exe (PID: 4320)
- StringIds.exe (PID: 4344)
- MSBuild.exe (PID: 4488)
- MSBuild.exe (PID: 4524)
- safman_setup.tmp (PID: 5168)
- conhost.exe (PID: 5192)
- ghjkl.exe (PID: 5324)
- BLduscfibj.exe (PID: 5360)
- BLduscfibj.exe (PID: 5428)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 5512)
- fcc.exe (PID: 5708)
- vbc.exe (PID: 5796)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2256)
- 6.exe (PID: 2328)
- cbchr.exe (PID: 2740)
- rest.exe (PID: 2900)
- calc.exe (PID: 3064)
- RegAsm.exe (PID: 3040)
- Vpeswawqko.exe (PID: 1528)
- 5xb6nM0.exe (PID: 2564)
- 1701610814-Dvnzfr.exe (PID: 3608)
- 6c)h7-RX{f.exe (PID: 584)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2256)
- peinf.exe (PID: 2440)
- cbchr.exe (PID: 2740)
- againn.exe (PID: 2596)
- rest.exe (PID: 2900)
- calc.exe (PID: 3064)
- RegAsm.exe (PID: 3040)
- hv.exe (PID: 1748)
- sysplorsv.exe (PID: 3072)
- QubpyznbC7neo.exe (PID: 1016)
- CasPol.exe (PID: 4068)
- pdf.exe (PID: 2208)
- vbc.exe (PID: 1056)
- Vpeswawqko.exe (PID: 1528)
- Otte-Locker.exe (PID: 2136)
- Amdau.exe (PID: 1904)
- jsc.exe (PID: 2452)
- sgridax.exe (PID: 1544)
- ghjk.exe (PID: 1864)
- Journal.exe (PID: 1924)
- BLduscfibj.exe (PID: 3576)
- BLduscfibj.exe (PID: 2152)
- 5xb6nM0.exe (PID: 2564)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E6%9C%8D%E5%8A%A1%E7%AB%AF_sos.exe (PID: 2660)
- wmprph.exe (PID: 3100)
- 1701610814-Dvnzfr.exe (PID: 3608)
- 6c)h7-RX{f.exe (PID: 2496)
- 6c)h7-RX{f.exe (PID: 584)
- sgridax.exe (PID: 3188)
- new.exe (PID: 2764)
- AppLaunch.exe (PID: 1956)
- StringIds.exe (PID: 4320)
- StringIds.exe (PID: 4344)
- MSBuild.exe (PID: 4488)
- MSBuild.exe (PID: 4524)
- ghjkl.exe (PID: 5324)
- BLduscfibj.exe (PID: 5360)
- BLduscfibj.exe (PID: 5428)
- vbc.exe (PID: 5796)
Create files in a temporary directory
- 4363463463464363463463463.exe (PID: 2256)
- tuc3.exe (PID: 1848)
- tuc3.tmp (PID: 1808)
- peinf.exe (PID: 2440)
- cbchr.exe (PID: 2740)
- tuc4.exe (PID: 1556)
- tuc4.tmp (PID: 2756)
- rest.exe (PID: 2900)
- hv.exe (PID: 1748)
- RegAsm.exe (PID: 3040)
- pdf.exe (PID: 2208)
- tuc5.exe (PID: 3336)
- tuc5.tmp (PID: 2856)
- tuc7.exe (PID: 2088)
- tuc7.tmp (PID: 2300)
- tuc2.exe (PID: 2308)
- tuc2.tmp (PID: 2492)
- ghjk.exe (PID: 1864)
- foxi.exe (PID: 3896)
- Gu2HY45.exe (PID: 2348)
- jw3Bi12.exe (PID: 2340)
- 5xb6nM0.exe (PID: 2564)
- safman_setup.exe (PID: 5160)
- ghjkl.exe (PID: 5324)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2256)
Drops the executable file immediately after the start
- tuc3.exe (PID: 1848)
- 4363463463464363463463463.exe (PID: 2256)
- tuc3.tmp (PID: 1808)
- sgridax.exe (PID: 1796)
- peinf.exe (PID: 2440)
- cbchr.exe (PID: 2740)
- tuc4.exe (PID: 1556)
- tuc4.tmp (PID: 2756)
- 513723952.exe (PID: 2808)
- rest.exe (PID: 2900)
- hv.exe (PID: 1748)
- pdf.exe (PID: 2208)
- tuc5.exe (PID: 3336)
- tuc7.exe (PID: 2088)
- tuc7.tmp (PID: 2300)
- tuc5.tmp (PID: 2856)
- Amdau.exe (PID: 1904)
- tuc2.exe (PID: 2308)
- tuc2.tmp (PID: 2492)
- ghjk.exe (PID: 1864)
- foxi.exe (PID: 3896)
- Gu2HY45.exe (PID: 2348)
- jw3Bi12.exe (PID: 2340)
- BLduscfibj.exe (PID: 2152)
- 5xb6nM0.exe (PID: 2564)
- dialer.exe (PID: 2540)
- safman_setup.exe (PID: 5160)
- conhost.exe (PID: 5192)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 5512)
Process drops legitimate windows executable
- tuc3.tmp (PID: 1808)
- tuc4.tmp (PID: 2756)
- tuc5.tmp (PID: 2856)
- tuc7.tmp (PID: 2300)
- tuc2.tmp (PID: 2492)
- 4363463463464363463463463.exe (PID: 2256)
- foxi.exe (PID: 3896)
- Gu2HY45.exe (PID: 2348)
Creates files in the program directory
- tuc3.tmp (PID: 1808)
- sgridax.exe (PID: 1796)
- tuc4.tmp (PID: 2756)
- rest.exe (PID: 2900)
- sgridax.exe (PID: 1544)
- tuc5.tmp (PID: 2856)
- tuc7.tmp (PID: 2300)
- tuc2.tmp (PID: 2492)
Drops 7-zip archiver for unpacking
- tuc3.tmp (PID: 1808)
- tuc4.tmp (PID: 2756)
- tuc5.tmp (PID: 2856)
- tuc7.tmp (PID: 2300)
- tuc2.tmp (PID: 2492)
- conhost.exe (PID: 5192)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2256)
- peinf.exe (PID: 2440)
- sysplorsv.exe (PID: 3072)
Reads product name
- 6.exe (PID: 2328)
- RegAsm.exe (PID: 3040)
- 6c)h7-RX{f.exe (PID: 584)
Checks proxy server information
- peinf.exe (PID: 2440)
- sysplorsv.exe (PID: 3072)
- jsc.exe (PID: 2452)
- sgridax.exe (PID: 1544)
- Journal.exe (PID: 1924)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E6%9C%8D%E5%8A%A1%E7%AB%AF_sos.exe (PID: 2660)
- 6c)h7-RX{f.exe (PID: 584)
- sgridax.exe (PID: 3188)
- AppLaunch.exe (PID: 1956)
Writes files like Keylogger logs
- 4363463463464363463463463.exe (PID: 2256)
- 6.exe (PID: 2328)
Connects to unusual port
- 6.exe (PID: 2328)
- rest.exe (PID: 2900)
- againn.exe (PID: 2596)
- RegAsm.exe (PID: 3040)
- calc.exe (PID: 3064)
- sysplorsv.exe (PID: 3072)
- CasPol.exe (PID: 4068)
- vbc.exe (PID: 1056)
- 4363463463464363463463463.exe (PID: 2256)
- sgridax.exe (PID: 1544)
- Journal.exe (PID: 1924)
- 5xb6nM0.exe (PID: 2564)
- MSBuild.exe (PID: 4524)
- vbc.exe (PID: 5796)
- fcc.exe (PID: 5708)
Creates files or folders in the user directory
- peinf.exe (PID: 2440)
- cbchr.exe (PID: 2740)
- rest.exe (PID: 2900)
- CasPol.exe (PID: 4068)
- Amdau.exe (PID: 1904)
- BLduscfibj.exe (PID: 2152)
- dialer.exe (PID: 2540)
- fcc.exe (PID: 5708)
Starts itself from another location
- 513723952.exe (PID: 2808)
The executable file from the user directory is run by the CMD process
- calc.exe (PID: 3064)
RISEPRO has been detected (SURICATA)
- rest.exe (PID: 2900)
- 5xb6nM0.exe (PID: 2564)
Connects to the CnC server
- RegAsm.exe (PID: 3040)
- rest.exe (PID: 2900)
- sysplorsv.exe (PID: 3072)
- sgridax.exe (PID: 1544)
- 5xb6nM0.exe (PID: 2564)
- sgridax.exe (PID: 3188)
- 6c)h7-RX{f.exe (PID: 584)
ARECHCLIENT2 has been detected (SURICATA)
- RegAsm.exe (PID: 3040)
Checks for external IP
- rest.exe (PID: 2900)
- 5xb6nM0.exe (PID: 2564)
Steals credentials
- rest.exe (PID: 2900)
- 5xb6nM0.exe (PID: 2564)
PHORPIEX has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2256)
- sysplorsv.exe (PID: 3072)
Process checks are UAC notifies on
- CasPol.exe (PID: 4068)
- new.exe (PID: 2764)
Application launched itself
- chrome.exe (PID: 2168)
- msedge.exe (PID: 1656)
- msedge.exe (PID: 2880)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 952)
- ghjk.exe (PID: 1864)
- BLduscfibj.exe (PID: 3576)
- msedge.exe (PID: 1628)
- msedge.exe (PID: 1588)
- msedge.exe (PID: 2572)
- msedge.exe (PID: 1656)
- msedge.exe (PID: 2028)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 2380)
- 6c)h7-RX{f.exe (PID: 2496)
- StringIds.exe (PID: 4320)
- MSBuild.exe (PID: 4488)
- ghjkl.exe (PID: 5324)
- 865b3db67f0565e0b41e72aa036d78183c33dab95bd4be7b4f13aebda88ab0c0.exe (PID: 5248)
- BLduscfibj.exe (PID: 5360)
Manual execution by a user
- msedge.exe (PID: 2880)
- msedge.exe (PID: 1656)
- msedge.exe (PID: 2028)
Unusual connection from system programs
- vbc.exe (PID: 1056)
- wscript.exe (PID: 5664)
- vbc.exe (PID: 5796)
SOCKS5SYSTEMZ has been detected (SURICATA)
- sgridax.exe (PID: 1544)
- sgridax.exe (PID: 3188)
Reads mouse settings
- 2DR9527.exe (PID: 560)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 2540)
Bypass execution policy to execute commands
- powershell.exe (PID: 3100)
- powershell.exe (PID: 4596)
Run PowerShell with an invisible window
- powershell.exe (PID: 3100)
- powershell.exe (PID: 4596)
The process executes via Task Scheduler
- powershell.exe (PID: 3100)
- StringIds.exe (PID: 4320)
- powershell.exe (PID: 4596)
Executed via WMI
- 6c)h7-RX{f.exe (PID: 2496)
LUMMA has been detected (SURICATA)
- AppLaunch.exe (PID: 1956)
AZORULT has been detected (SURICATA)
- 6c)h7-RX{f.exe (PID: 584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(2328) 6.exe
C2 (9)hendersonk1.hopto.org:2404
henderson1.camdvr.org:2404
centplus1.serveftp.com:2404
harrywlike.ddns.net:2404
genekol.nsupdate.info:2404
harrywlike1.ddns.net:2404
hendersonk2022.hopto.org:2404
genekol1.nsupdate.info:2404
generem.camdvr.org:2404
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\ShellGY99V
Setup_path%APPDATA%
Copy_filesonic.exe
Startup_valuefuckuuuuu
Hide_fileFalse
Mutex_namegsgjdwg-1J0WWM
Keylog_flag1
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_namenotepad;solitaire;
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_dirMicRecords
Connect_delay0
Copy_diryakkk
Keylog_dirchrome
Max_keylog_file20000
RedLine
(PID) Process(2596) againn.exe
C2 (1)45.15.156.2:25096
Botnettest
Options
ErrorMessage
Keys
XorRammers
AsyncRat
(PID) Process(3064) calc.exe
C2 (1)89.23.100.93
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexoonrejgwedvxwse
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureQjWeZe4F4TuWy0hUx2CJx3viPXMuRkFhkXGrVGT29pa7LM+06mEXhUkglBWpLmYPaFBKG5FEqOime2j0+7Cf0hyosj2teh9TnTiRihwU6ooSTFBg9MLZW6DOqN3NYbQAxzaJZu29Z/KHkeaWOVYrTDURnnk62Z+gzdMHhMH1F5k=
Keys
AES30514d0354cda998b840312f75ae05f11383b533e04a6b2d1084a39d2adc412e
SaltVenomRATByVenom
Nanocore
(PID) Process(4068) CasPol.exe
BuildTime2023-12-21 08:15:54.000408
Version1.2.2.0
Mutex4c987240-839f-4536-835a-ac14ff0793a6
DefaultGroupDec
PrimaryConnectionHostglobron.duckdns.org
BackupConnectionHostglobron.duckdns.org
ConnectionPort9192
RunOnStartupFalse
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Amadey
(PID) Process(2452) jsc.exe
C2 (1)http://45.9.74.182
Version3.86
Options
Drop directoryS-%lu-
Drop name%-lu
Strings (119)-%lu
f3f10bd848
bstyoops.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
Lumma
(PID) Process(1956) AppLaunch.exe
C2gstatic-node.io
Options
LummaIDV566Iu--resame
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
264
Monitored processes
171
Malicious processes
29
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4676 --field-trial-handle=1296,i,15166462791264661332,10579114871268910820,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 560 | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\2DR9527.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\2DR9527.exe | — | jw3Bi12.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 584 | C:\Users\admin\AppData\Local\Microsoft\6c)h7-RX{f.exe | C:\Users\admin\AppData\Local\Microsoft\6c)h7-RX{f.exe | 6c)h7-RX{f.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 604 | "C:\Users\admin\Desktop\Files\891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe" | C:\Users\admin\Desktop\Files\891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 632 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2284 --field-trial-handle=1424,i,9201935788751032586,16804763396901112074,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 4294967295 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 848 | C:\Windows\system32\net1 helpmsg 29 | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 880 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4088 --field-trial-handle=1296,i,15166462791264661332,10579114871268910820,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 908 | "C:\Users\admin\Desktop\Files\659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe" | C:\Users\admin\Desktop\Files\659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe" | C:\Users\admin\Desktop\Files\3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe | — | 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
61 468
Read events
60 705
Write events
761
Delete events
2
Modification events
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA662000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F007400200058003100000014000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E309000000010000000C000000300A06082B06010505070301030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E80F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000000CD2F9E0DA1773E9ED864DA5E370E74E0F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F63030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E809000000010000000C000000300A06082B060105050703011D000000010000001000000073B6876195F5D18E048510422AEF04E314000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E0B000000010000001A0000004900530052004700200052006F006F007400200058003100000062000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C61900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA620000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2256) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2440) peinf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
477
Suspicious files
475
Text files
180
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2256 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2256 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:EF3BAE87B08C9C4B3598F8C596E58644 | SHA256:736E977A99495C2239CB70DD9B0F986560C133D178D75EB90B7545EF44B094D9 | |||
| 1808 | tuc3.tmp | C:\Program Files\String grid activeX\is-QGS7O.tmp | executable | |
MD5:88442841B57E8E01D4911EF91C468841 | SHA256:D971CC89CB7C4287EF1AE4171244A00EA1BBB9B1DD9C9F44FFABF7F2C892024F | |||
| 1808 | tuc3.tmp | C:\Program Files\String grid activeX\bin\x86\bassape.dll | executable | |
MD5:C7A50ACE28DDE05B897E000FA398BBCE | SHA256:F02979610F9BE2F267AA3260BB3DF0F79EEEB6F491A77EBBE719A44814602BCC | |||
| 1808 | tuc3.tmp | C:\Program Files\String grid activeX\unins000.exe | executable | |
MD5:88442841B57E8E01D4911EF91C468841 | SHA256:D971CC89CB7C4287EF1AE4171244A00EA1BBB9B1DD9C9F44FFABF7F2C892024F | |||
| 1808 | tuc3.tmp | C:\Users\admin\AppData\Local\Temp\is-6I22F.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1848 | tuc3.exe | C:\Users\admin\AppData\Local\Temp\is-91DR2.tmp\tuc3.tmp | executable | |
MD5:A7662827ECAEB4FC68334F6B8791B917 | SHA256:05F159722D6905719D2D6F340981A293F40AB8A0D2D4A282C948066809D4AF6D | |||
| 1808 | tuc3.tmp | C:\Users\admin\AppData\Local\Temp\is-6I22F.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 1808 | tuc3.tmp | C:\Program Files\String grid activeX\bin\x86\is-BGQOG.tmp | executable | |
MD5:C7A50ACE28DDE05B897E000FA398BBCE | SHA256:F02979610F9BE2F267AA3260BB3DF0F79EEEB6F491A77EBBE719A44814602BCC | |||
| 1808 | tuc3.tmp | C:\Program Files\String grid activeX\bin\x86\is-U1AOG.tmp | executable | |
MD5:9FF783BB73F8868FA6599CDE65ED21D7 | SHA256:E0234AF5F71592C472439536E710BA8105D62DFA68722965DF87FED50BAB1816 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
607
DNS requests
174
Threats
309
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3072 | sysplorsv.exe | GET | 404 | 185.215.113.66:80 | http://185.215.113.66/7 | unknown | html | 564 b | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 209.145.51.44:80 | http://vmi1159541.contaboserver.net/RobluxCoins.exe | unknown | executable | 976 Kb | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.160:80 | http://185.172.128.160/hv.exe | unknown | executable | 7.11 Mb | unknown |
2440 | peinf.exe | GET | 200 | 185.215.113.84:80 | http://185.215.113.84/newtpp.exe | unknown | executable | 80.0 Kb | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://185.215.113.84/peinf.exe | unknown | executable | 7.00 Kb | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 109.107.182.3:80 | http://109.107.182.3/hugo/rest.exe | unknown | executable | 1.46 Mb | unknown |
2440 | peinf.exe | GET | 200 | 185.215.113.84:80 | http://185.215.113.84/peinstall.php | unknown | executable | 80.0 Kb | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1093903907778293 | unknown | compressed | 65.2 Kb | unknown |
2256 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.113:80 | http://185.172.128.113/pinguin.exe | unknown | executable | 9.73 Mb | unknown |
3072 | sysplorsv.exe | GET | 404 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | html | 564 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2256 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2256 | 4363463463464363463463463.exe | 91.215.85.209:443 | medfioytrkdkcodlskeej.net | — | RU | unknown |
2256 | 4363463463464363463463463.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2256 | 4363463463464363463463463.exe | 172.67.168.30:443 | needs.hitsturbo.com | CLOUDFLARENET | US | unknown |
2256 | 4363463463464363463463463.exe | 209.145.51.44:80 | vmi1159541.contaboserver.net | CONTABO | US | malicious |
2256 | 4363463463464363463463463.exe | 185.172.128.160:80 | — | OOO Nadym Svyaz Service | RU | unknown |
2256 | 4363463463464363463463463.exe | 82.157.254.217:8080 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
medfioytrkdkcodlskeej.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
needs.hitsturbo.com |
| malicious |
vmi1159541.contaboserver.net |
| malicious |
raw.githubusercontent.com |
| shared |
github.com |
| shared |
hendersonk1.hopto.org |
| malicious |
henderson1.camdvr.org |
| unknown |
centplus1.serveftp.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
2256 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2256 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
2256 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2256 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2256 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2256 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2256 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2256 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2256 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
22 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|