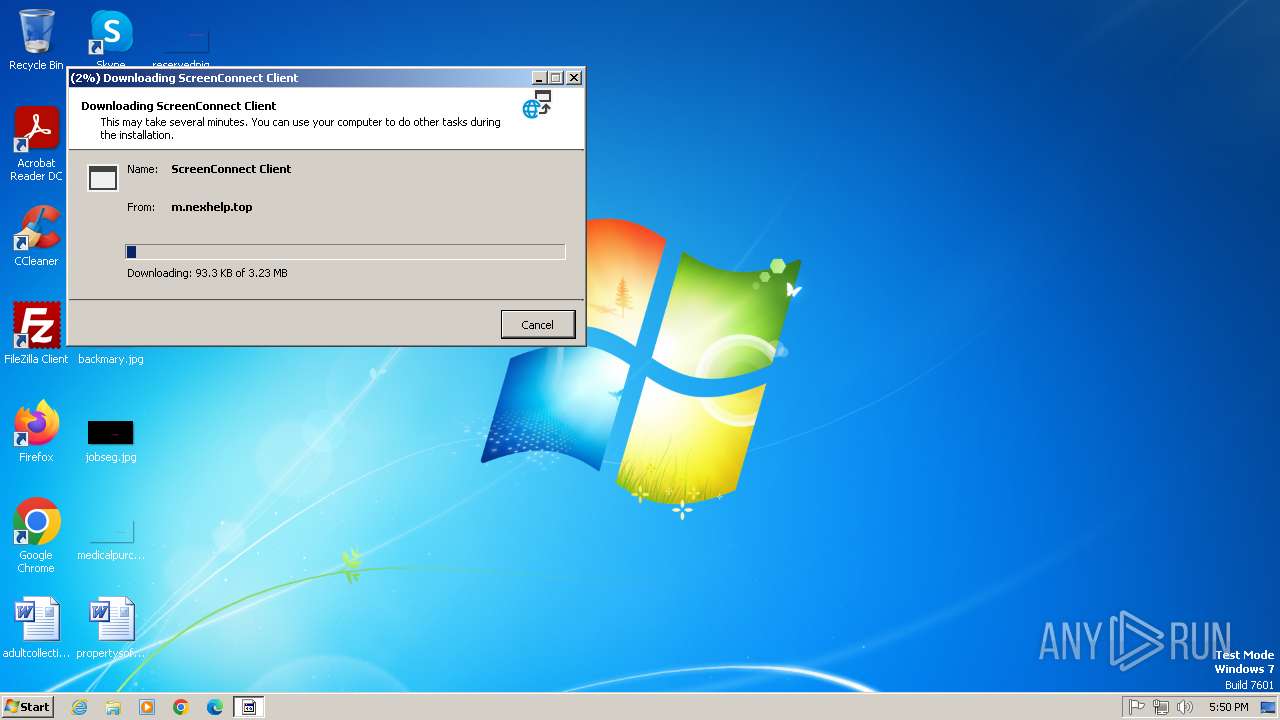
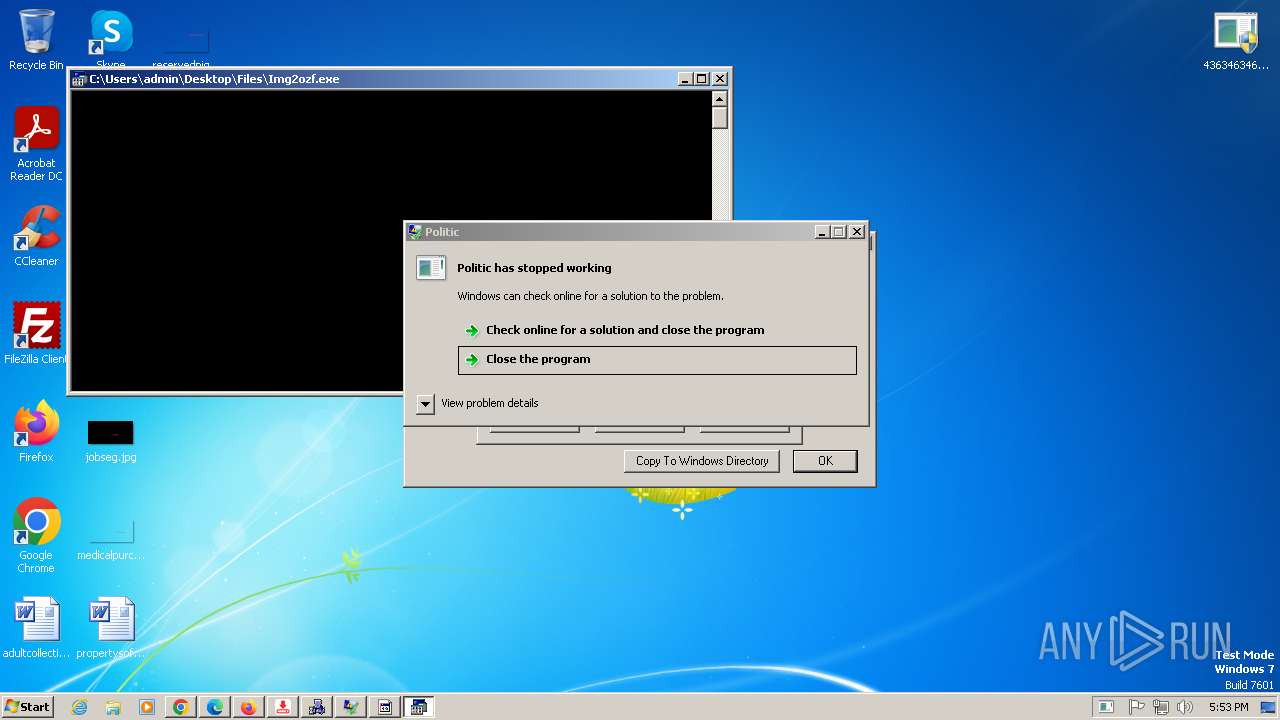
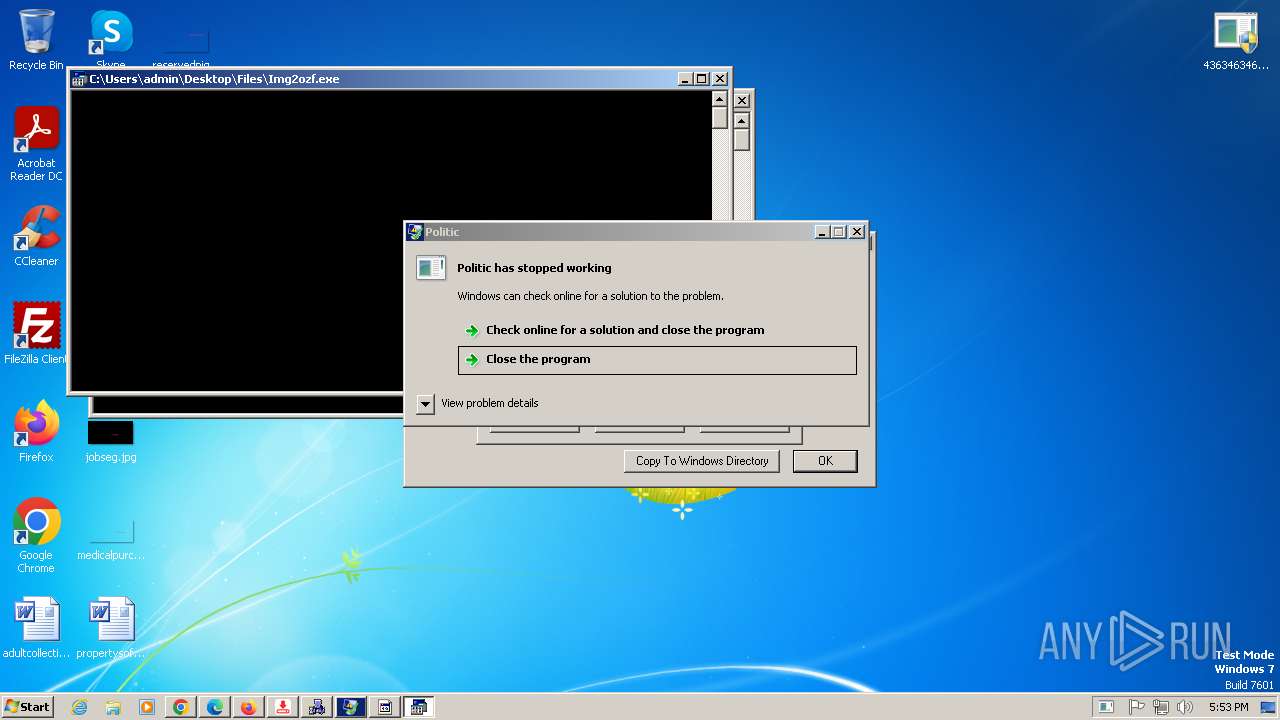
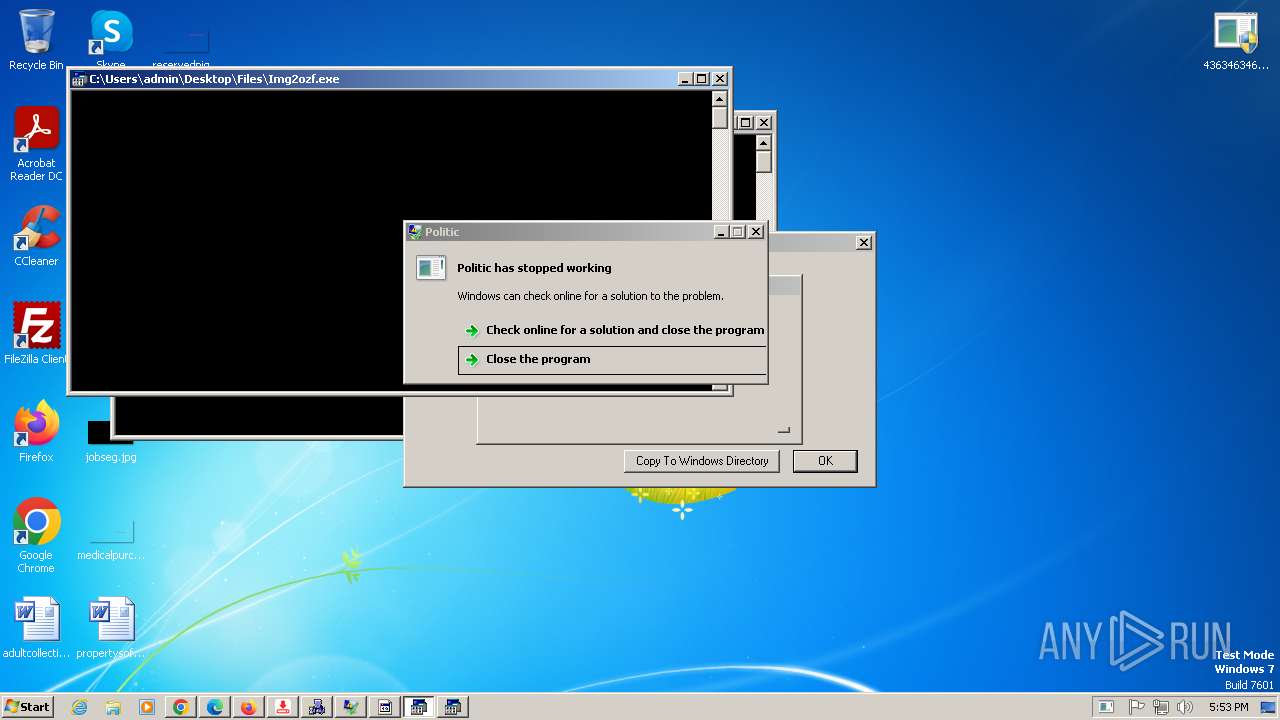
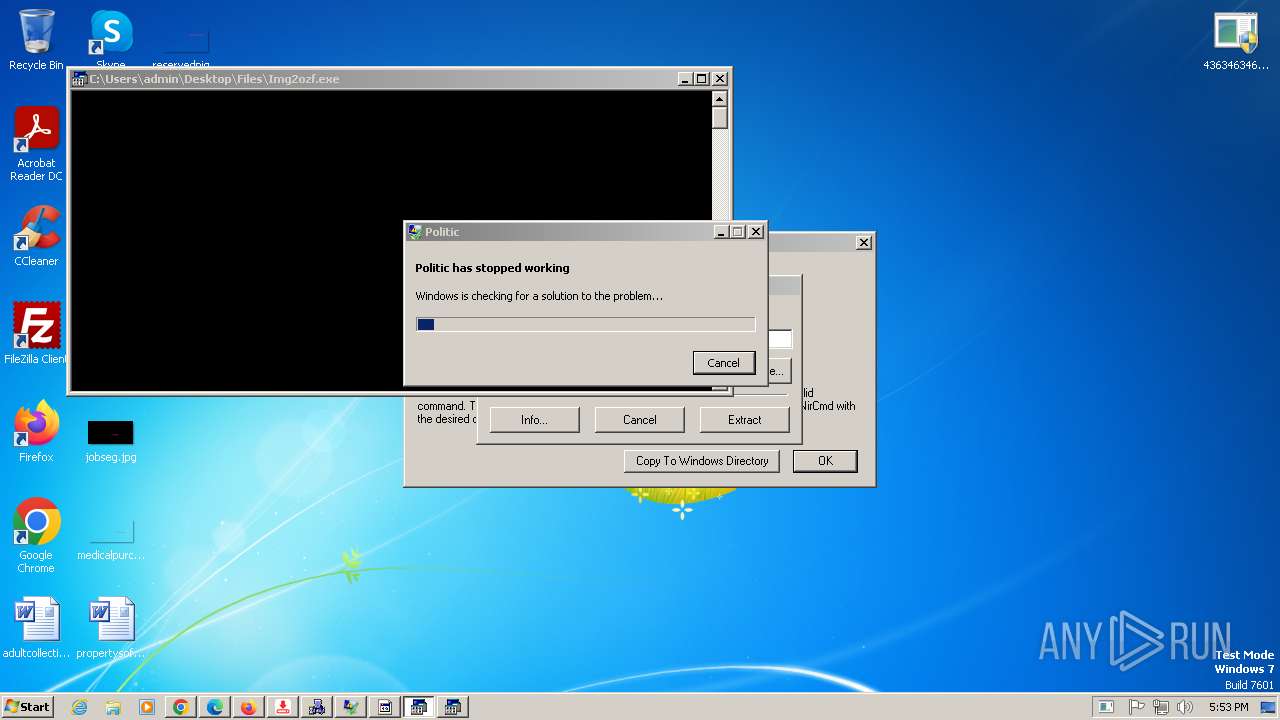
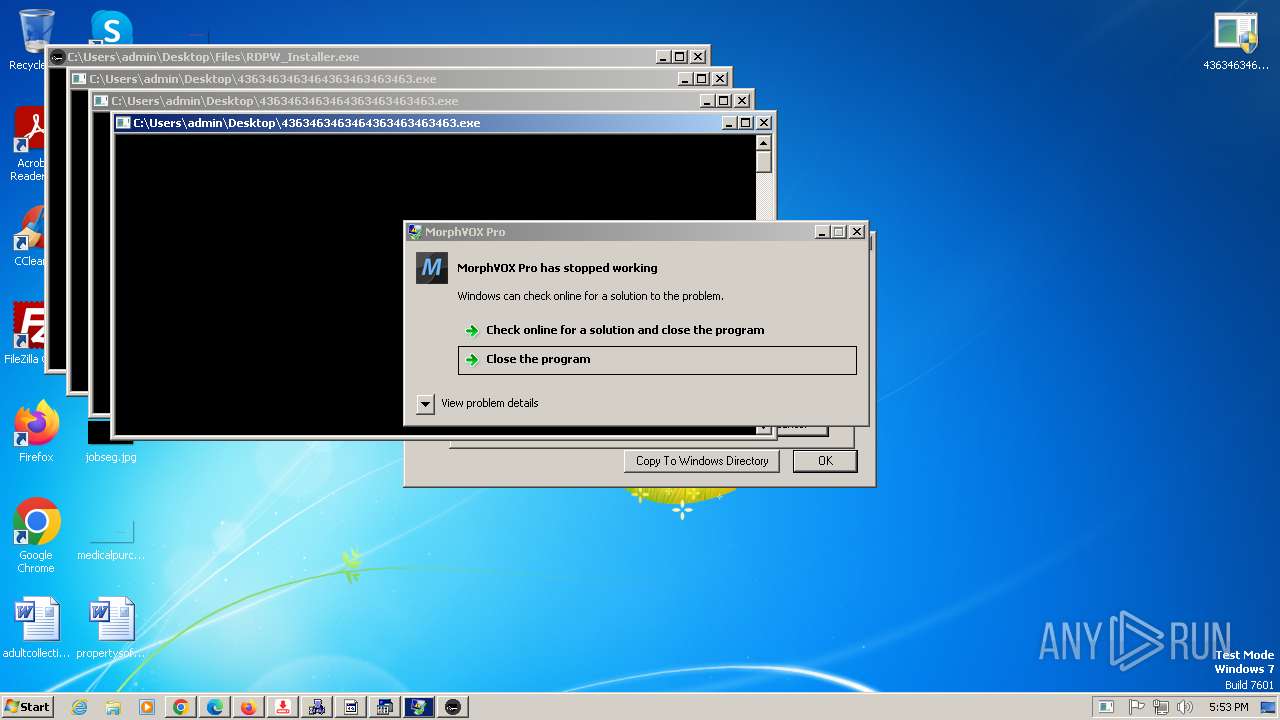
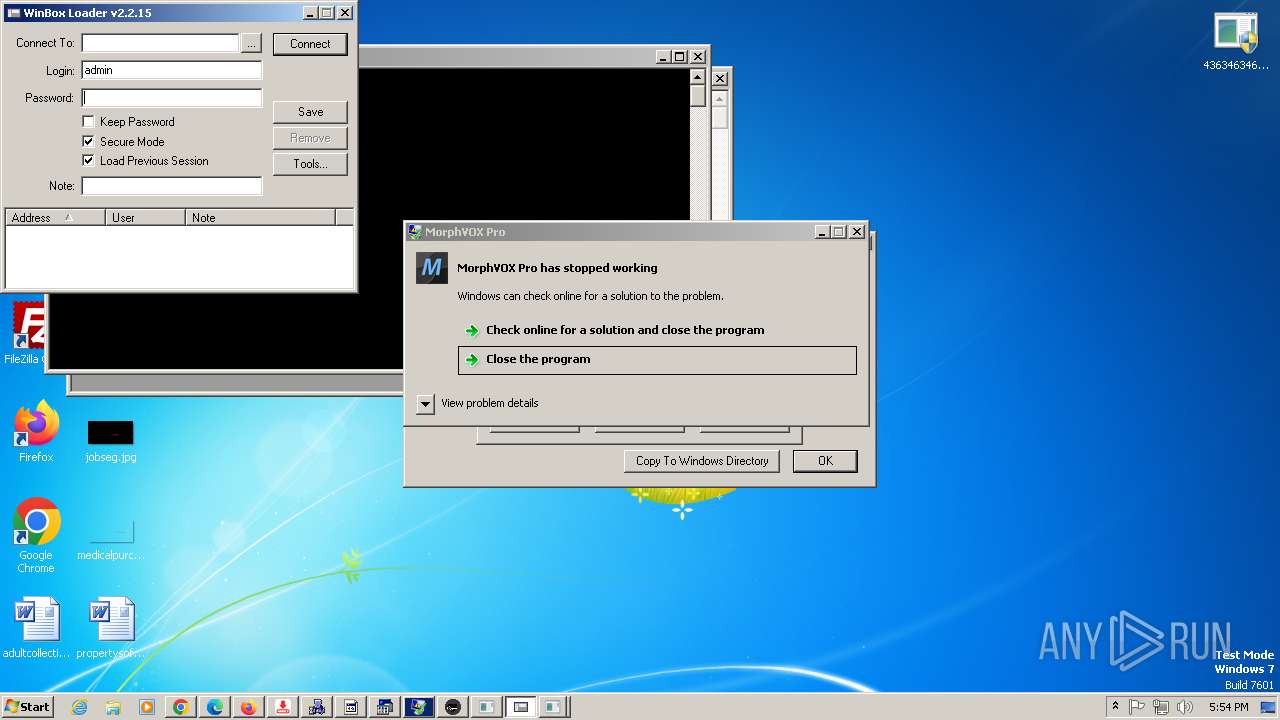
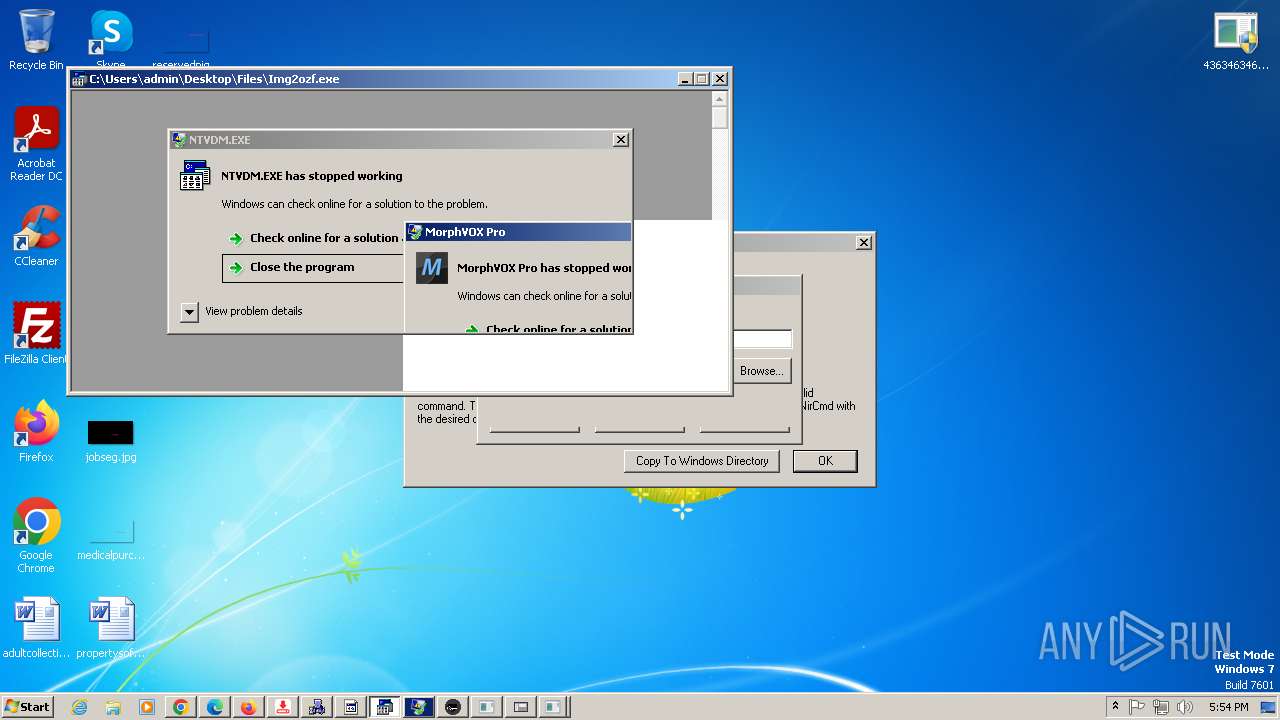
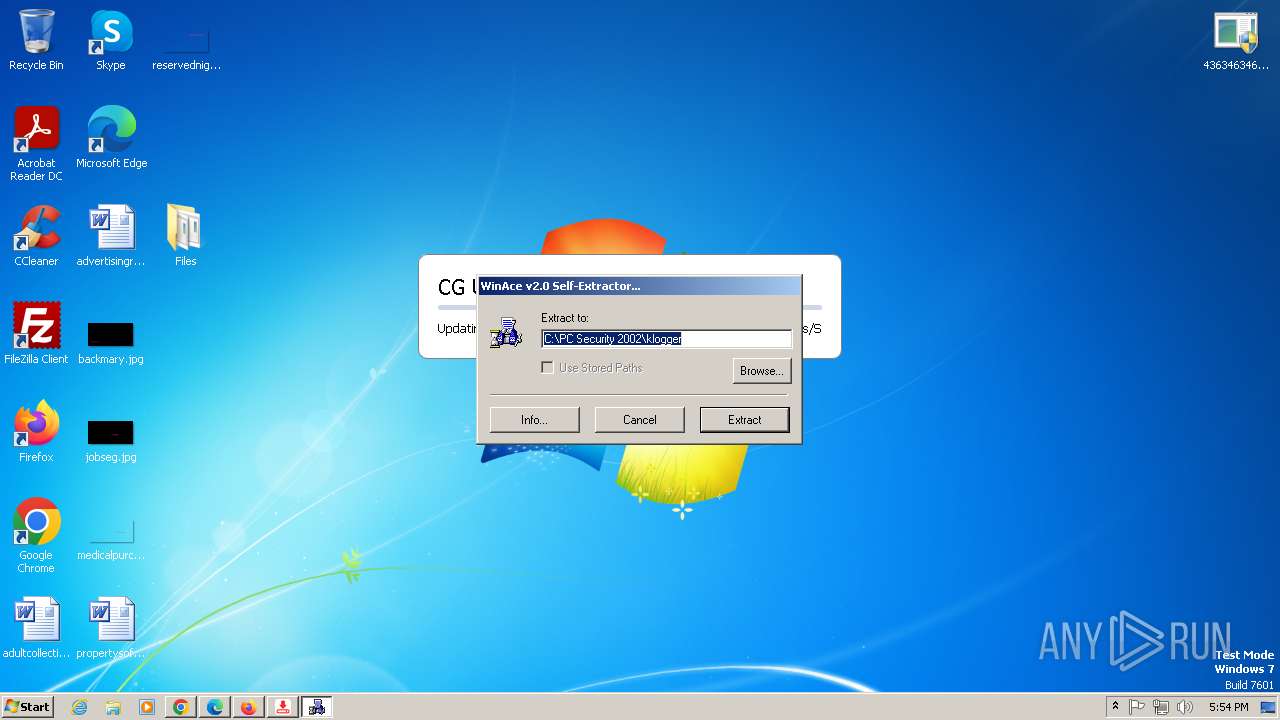
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/7968480c-8197-4e5c-bb2f-5a55a8c1e2b0 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 21, 2025, 16:50:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 4840)
- Client-built-Playit.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 3260)
- RuntimeBroker.exe (PID: 7172)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 2908)
- Amogus.exe (PID: 6836)
- installer.exe.exe (PID: 6072)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 1800)
- Client.exe (PID: 2960)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- JUSCHED.EXE (PID: 4868)
- jusched.exe (PID: 5404)
- cmd.exe (PID: 4564)
- Client.exe (PID: 4140)
- VsGraphicsResources2.exe (PID: 6092)
- vsjitdebuggerui.exe (PID: 1760)
- Client-built-Playit.exe (PID: 5036)
- System32.exe (PID: 6348)
- RuntimeBroker.exe (PID: 7172)
- Client.exe (PID: 7648)
- Amogus.exe (PID: 6836)
- installer.exe.exe (PID: 6072)
- Client.exe (PID: 2248)
- RuntimeBroker.exe (PID: 2180)
- Win64.exe (PID: 2228)
- vsjitdebuggerui.exe (PID: 2192)
- System32.exe (PID: 2164)
- jusched.exe (PID: 2172)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 128)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.WindowsClient.exe (PID: 3316)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 128)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 8828)
Changes the autorun value in the registry
- qq.exe (PID: 4688)
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- done12312.exe (PID: 6588)
- Server.exe (PID: 7864)
- winserv.exe (PID: 2512)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
- Server.exe (PID: 2484)
SVCSTEALER mutex has been found
- qq.exe (PID: 4688)
- winserv.exe (PID: 2512)
Executing a file with an untrusted certificate
- brbotnet.exe (PID: 4532)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- Ywtencv.exe (PID: 10000)
Actions looks like stealing of personal data
- brbotnet.exe (PID: 4532)
- brbotnet.exe (PID: 4532)
- random.exe (PID: 7400)
- random.exe (PID: 7400)
Bypass execution policy to execute commands
- powershell.exe (PID: 5088)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 5692)
- powershell.exe (PID: 6624)
- powershell.exe (PID: 6992)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6848)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 6784)
- powershell.exe (PID: 7612)
- powershell.exe (PID: 6004)
- powershell.exe (PID: 9788)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Installer.exe (PID: 7460)
Changes Windows Defender settings
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Installer.exe (PID: 7460)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
LUMMA has been found (auto)
- 4363463463464363463463463.exe (PID: 6012)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
ASYNCRAT has been detected (MUTEX)
- AsyncClient.exe (PID: 4656)
QUASAR has been detected (YARA)
- Neverlose%20Loader.exe (PID: 3172)
REMCOS has been found (auto)
- 4363463463464363463463463.exe (PID: 6012)
REMCOS mutex has been found
- benpolatalemdar.exe (PID: 5396)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- done12312.exe (PID: 6588)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 6012)
- boleto.exe (PID: 5648)
REMCOS has been detected
- benpolatalemdar.exe (PID: 5396)
Create files in the Startup directory
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- Fast%20Download.exe (PID: 7392)
- done12312.exe (PID: 6588)
- boleto.exe (PID: 2596)
- Wave.exe (PID: 2524)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 5416)
XWORM has been detected (SURICATA)
- XClient.exe (PID: 1384)
- done12312.exe (PID: 6588)
- boleto.exe (PID: 5648)
- done12312.exe (PID: 2864)
- boleto.exe (PID: 2596)
XWORM has been found (auto)
- 4363463463464363463463463.exe (PID: 3456)
- done12312.exe (PID: 6588)
NJRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 3260)
- njrat.exe (PID: 8620)
- 4363463463464363463463463.exe (PID: 128)
Connects to the CnC server
- svchost.exe (PID: 1080)
- msedge.exe (PID: 1976)
- Server.exe (PID: 7864)
- Device2.exe (PID: 7632)
- Server1.exe (PID: 9852)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1080)
- msedge.exe (PID: 1976)
- random.exe (PID: 7400)
- 7IPCJFu.exe (PID: 7220)
FORMBOOK has been found (auto)
- 4363463463464363463463463.exe (PID: 4800)
- NJRAT%20DANGEROUS.exe (PID: 7688)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3260)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7148)
Runs injected code in another process
- powershell.exe (PID: 7148)
- powershell.exe (PID: 1352)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2908)
Application was injected by another process
- winlogon.exe (PID: 436)
- winlogon.exe (PID: 448)
LUMMA mutex has been found
- random.exe (PID: 7400)
Steals credentials from Web Browsers
- random.exe (PID: 7400)
QUASAR has been found (auto)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 3260)
NJRAT mutex has been found
- Server.exe (PID: 7864)
- Fast%20Download.exe (PID: 7392)
- Server.exe (PID: 2484)
- Server.exe (PID: 2572)
XRED has been found (auto)
- 4363463463464363463463463.exe (PID: 5416)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7736)
AMADEY mutex has been found
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
NJRAT has been detected (SURICATA)
- Server.exe (PID: 7864)
- Device2.exe (PID: 7632)
- Server1.exe (PID: 9852)
NjRAT is detected
- Device2.exe (PID: 7632)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 7628)
TOFSEE has been found (auto)
- 4363463463464363463463463.exe (PID: 3260)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 128)
- dfsvc.exe (PID: 2968)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5604)
- $77svchost.exe (PID: 4492)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- 4363463463464363463463463.exe (PID: 6176)
- random.exe (PID: 7400)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8820)
- 4363463463464363463463463.exe (PID: 8780)
- 7IPCJFu.exe (PID: 7220)
- $77svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 2356)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 128)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4840)
- svchost.exe (PID: 1080)
- 4363463463464363463463463.exe (PID: 4800)
- Update.exe (PID: 6304)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 3260)
- random.exe (PID: 7400)
- audi.exe (PID: 8168)
- wic.exe (PID: 9412)
- 4363463463464363463463463.exe (PID: 3456)
- svchost.exe (PID: 1096)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 128)
- Client.exe (PID: 2960)
- dfsvc.exe (PID: 2968)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 4308)
- Client.exe (PID: 5832)
- CritScript.exe (PID: 4616)
- 4363463463464363463463463.exe (PID: 3260)
- XClient.exe (PID: 1384)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 5100)
- powershell.exe (PID: 5088)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 5868)
- 4363463463464363463463463.exe (PID: 3456)
- svchost.exe (PID: 5604)
- powershell.exe (PID: 5692)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 5416)
- Client.exe (PID: 4140)
- boleto.exe (PID: 5648)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 4840)
- $77svchost.exe (PID: 4492)
- 4363463463464363463463463.exe (PID: 6176)
- 4363463463464363463463463.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 4800)
- powershell.exe (PID: 6624)
- QuizPokemon.exe (PID: 6796)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6992)
- Agentnov.exe (PID: 7548)
- done12312.exe (PID: 6588)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Installer.exe (PID: 7460)
- WMIC.exe (PID: 5592)
- IMG001.exe (PID: 6972)
- WMIC.exe (PID: 4924)
- WMIC.exe (PID: 4512)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 6848)
- audi.exe (PID: 8168)
- wscript.exe (PID: 7736)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8820)
- WinIntoruntime.exe (PID: 7456)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- njrat.exe (PID: 8620)
- cHSzTDjVl.exe (PID: 5668)
- wic.exe (PID: 9412)
- powershell.exe (PID: 7612)
- 4363463463464363463463463.exe (PID: 8668)
- powershell.exe (PID: 6784)
- tftp.exe (PID: 9936)
- sipnotify.exe (PID: 2056)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
- $77svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 2356)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 128)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 3260)
- random.exe (PID: 7400)
- 4363463463464363463463463.exe (PID: 6116)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 128)
- support.client.exe (PID: 3444)
- dfsvc.exe (PID: 2968)
- 4363463463464363463463463.exe (PID: 6116)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 128)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 4800)
- Update.exe (PID: 6304)
- random.exe (PID: 7400)
- audi.exe (PID: 8168)
- wic.exe (PID: 9412)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- dfsvc.exe (PID: 2968)
- qq.exe (PID: 4688)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 5900)
- CritScript.exe (PID: 4616)
- JUSCHED.EXE (PID: 4868)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 3260)
- svchost.exe (PID: 5604)
- XClient.exe (PID: 1384)
- 4363463463464363463463463.exe (PID: 3456)
- VsGraphicsResources2.exe (PID: 6092)
- 4363463463464363463463463.exe (PID: 4840)
- Client-built-Playit.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5724)
- boleto.exe (PID: 5648)
- Agentnov.exe (PID: 7548)
- RuntimeBroker.exe (PID: 7172)
- Update.exe (PID: 6304)
- done12312.exe (PID: 6588)
- rah.exe (PID: 7636)
- IMG001.exe (PID: 6972)
- Amogus.exe (PID: 6836)
- random.exe (PID: 7400)
- installer.exe.exe (PID: 6072)
- audi.exe (PID: 8168)
- WinIntoruntime.exe (PID: 7456)
- RDPW_Installer.exe (PID: 7156)
- 1.exe (PID: 8920)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- njrat.exe (PID: 8620)
- wic.exe (PID: 9412)
- 4363463463464363463463463.exe (PID: 8828)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- winserv.exe (PID: 2512)
Starts itself from another location
- Client-built.exe (PID: 1800)
- JUSCHED.EXE (PID: 4868)
- VsGraphicsResources2.exe (PID: 6092)
- Client-built-Playit.exe (PID: 5036)
- rah.exe (PID: 7636)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- njrat.exe (PID: 8620)
- IMG001.exe (PID: 6972)
Reads security settings of Internet Explorer
- dfsvc.exe (PID: 2968)
- Client.exe (PID: 2960)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 128)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 6012)
- CritScript.exe (PID: 4616)
- XClient.exe (PID: 1384)
- svchost.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 3456)
- Client.exe (PID: 4140)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4840)
- boleto.exe (PID: 5648)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 2908)
- QuizPokemon.exe (PID: 6796)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 4800)
- Agentnov.exe (PID: 7548)
- done12312.exe (PID: 6588)
- IMG001.exe (PID: 6972)
- audi.exe (PID: 8168)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- WinIntoruntime.exe (PID: 7456)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- cHSzTDjVl.exe (PID: 5668)
- njrat.exe (PID: 8620)
- wic.exe (PID: 9412)
- Installer.exe (PID: 7460)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 128)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 5900)
- jusched.exe (PID: 5404)
- benpolatalemdar.exe (PID: 5396)
- asdasdasdasdasd.exe (PID: 5296)
- 4363463463464363463463463.exe (PID: 6012)
- XClient.exe (PID: 1384)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 5604)
- vsjitdebuggerui.exe (PID: 1760)
- System32.exe (PID: 6348)
- connector1.exe (PID: 6480)
- 4363463463464363463463463.exe (PID: 4800)
- service.exe (PID: 7752)
- EmmetPROD.exe (PID: 5432)
- 4363463463464363463463463.exe (PID: 5416)
- done12312.exe (PID: 6588)
- boleto.exe (PID: 5648)
- Server.exe (PID: 7864)
- SubDir.exe (PID: 5304)
- 4363463463464363463463463.exe (PID: 8764)
- Device2.exe (PID: 7632)
- payload.exe (PID: 9484)
- Server1.exe (PID: 9852)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
- Wave.exe (PID: 2524)
Reads Internet Explorer settings
- dfsvc.exe (PID: 2968)
The process creates files with name similar to system file names
- dfsvc.exe (PID: 2968)
- 4363463463464363463463463.exe (PID: 3260)
- svchost.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 4800)
Executing commands from a ".bat" file
- Client.exe (PID: 2960)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- svchost.exe (PID: 5604)
- Client.exe (PID: 4140)
- wscript.exe (PID: 7736)
- RDPW_Installer.exe (PID: 7156)
- WinIntoruntime.exe (PID: 7456)
- Win64.exe (PID: 2228)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2420)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 4900)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 5584)
- cmd.exe (PID: 10120)
- cmd.exe (PID: 1124)
The executable file from the user directory is run by the CMD process
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- Client.exe (PID: 4140)
- $77svchost.exe (PID: 4492)
- Client.exe (PID: 7648)
- WinIntoruntime.exe (PID: 7456)
Starts CMD.EXE for commands execution
- Client.exe (PID: 2960)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- svchost.exe (PID: 5604)
- Client.exe (PID: 4140)
- QuizPokemon.exe (PID: 6796)
- EmmetPROD.exe (PID: 5432)
- IMG001.exe (PID: 6972)
- wscript.exe (PID: 7736)
- RDPW_Installer.exe (PID: 7156)
- WinIntoruntime.exe (PID: 7456)
- wic.exe (PID: 9412)
- Win64.exe (PID: 2228)
Starts application with an unusual extension
- cmd.exe (PID: 2420)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 4900)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 5584)
- cmd.exe (PID: 10120)
Detects ScreenConnect RAT (YARA)
- ScreenConnect.WindowsClient.exe (PID: 3316)
There is functionality for taking screenshot (YARA)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Neverlose%20Loader.exe (PID: 3172)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 128)
- qq.exe (PID: 4688)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 4840)
- RDPW_Installer.exe (PID: 7156)
- 4363463463464363463463463.exe (PID: 3260)
- winserv.exe (PID: 2512)
Starts a Microsoft application from unusual location
- qq.exe (PID: 4688)
- 235T1TS.exe (PID: 7068)
- Destover.exe (PID: 8332)
Found regular expressions for crypto-addresses (YARA)
- qq.exe (PID: 4688)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Installer.exe (PID: 7460)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 5088)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 5692)
- powershell.exe (PID: 6624)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6992)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 6848)
- powershell.exe (PID: 6784)
- powershell.exe (PID: 7612)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 1384)
- boleto.exe (PID: 5648)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5424)
Windows Defender mutex has been found
- perviy.exe (PID: 5740)
Checks for external IP
- svchost.exe (PID: 1080)
- boleto.exe (PID: 5648)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Installer.exe (PID: 7460)
- svchost.exe (PID: 1096)
- boleto.exe (PID: 2596)
Contacting a server suspected of hosting an CnC
- XClient.exe (PID: 1384)
- svchost.exe (PID: 1080)
- msedge.exe (PID: 1976)
- random.exe (PID: 7400)
- boleto.exe (PID: 5648)
- done12312.exe (PID: 6588)
- Server.exe (PID: 7864)
- 7IPCJFu.exe (PID: 7220)
- Device2.exe (PID: 7632)
- Server1.exe (PID: 9852)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
Application launched itself
- done12312.exe (PID: 6560)
- done12312.exe (PID: 2564)
- done12312.exe (PID: 2656)
Invokes assembly entry point (POWERSHELL)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 1352)
Executing commands from ".cmd" file
- QuizPokemon.exe (PID: 6796)
The process executes via Task Scheduler
- powershell.exe (PID: 7148)
- done12312.exe (PID: 6872)
- Wave.exe (PID: 6544)
- boleto.exe (PID: 8720)
- System32.exe (PID: 2164)
- RuntimeBroker.exe (PID: 2180)
- Win64.exe (PID: 2228)
- jusched.exe (PID: 2172)
- vsjitdebuggerui.exe (PID: 2192)
- Client.exe (PID: 2248)
- $77svchost.exe (PID: 2256)
- Client.exe (PID: 2268)
- powershell.exe (PID: 1352)
- ctfmon.exe (PID: 400)
- sipnotify.exe (PID: 2056)
Reads the BIOS version
- 7IPCJFu.exe (PID: 7220)
- random.exe (PID: 7400)
Possible Social Engineering Attempted
- svchost.exe (PID: 1080)
Creates file in the systems drive root
- ntvdm.exe (PID: 7816)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 8144)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 8144)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6624)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 8144)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 8144)
Searches for installed software
- random.exe (PID: 7400)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7736)
Reads the date of Windows installation
- 1.exe (PID: 8920)
Get information on the list of running processes
- cmd.exe (PID: 7060)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- tftp.exe (PID: 9936)
Uses ATTRIB.EXE to modify file attributes
- Fast%20Download.exe (PID: 7392)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Server1.exe (PID: 9852)
The system shut down or reboot
- cmd.exe (PID: 8248)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7060)
Connects to FTP
- tftp.exe (PID: 9936)
INFO
Reads Environment values
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- Client.exe (PID: 2960)
- dfsvc.exe (PID: 2968)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 1488)
- Client.exe (PID: 116)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5756)
- Client.exe (PID: 5832)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- Neverlose%20Loader.exe (PID: 3172)
- JUSCHED.EXE (PID: 4868)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4952)
- jusched.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- Client.exe (PID: 4140)
- asdasdasdasdasd.exe (PID: 5296)
- VsGraphicsResources2.exe (PID: 6092)
- benpolatalemdar.exe (PID: 5396)
- 4363463463464363463463463.exe (PID: 5724)
- CleanerV2.exe (PID: 3820)
- 4363463463464363463463463.exe (PID: 5344)
- boleto.exe (PID: 5648)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4800)
- vsjitdebuggerui.exe (PID: 1760)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5604)
- Client-built-Playit.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 6176)
- $77svchost.exe (PID: 4492)
- System32.exe (PID: 6348)
- RuntimeBroker.exe (PID: 7172)
- Client.exe (PID: 7648)
- Test2.exe (PID: 7584)
- rah.exe (PID: 7636)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Amogus.exe (PID: 6836)
- SubDir.exe (PID: 5304)
- installer.exe.exe (PID: 6072)
- WinIntoruntime.exe (PID: 7456)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8820)
- cHSzTDjVl.exe (PID: 5668)
- Device2.exe (PID: 7632)
- Server1.exe (PID: 9852)
- 4363463463464363463463463.exe (PID: 8668)
- 4363463463464363463463463.exe (PID: 9352)
- vsjitdebuggerui.exe (PID: 2192)
- Win64.exe (PID: 2228)
- RuntimeBroker.exe (PID: 2180)
- jusched.exe (PID: 2172)
- Client.exe (PID: 2268)
- Client.exe (PID: 2248)
- boleto.exe (PID: 2596)
- System32.exe (PID: 2164)
- $77svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 2356)
Checks supported languages
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- support.client.exe (PID: 3444)
- Client.exe (PID: 2960)
- dfsvc.exe (PID: 2968)
- chcp.com (PID: 2652)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Client.exe (PID: 872)
- chcp.com (PID: 3200)
- Client.exe (PID: 3232)
- chcp.com (PID: 3756)
- Client.exe (PID: 3784)
- chcp.com (PID: 4092)
- Client.exe (PID: 3424)
- chcp.com (PID: 2636)
- Client.exe (PID: 116)
- chcp.com (PID: 3920)
- Client.exe (PID: 1488)
- chcp.com (PID: 3748)
- Client.exe (PID: 4420)
- chcp.com (PID: 4640)
- qq.exe (PID: 4688)
- Client.exe (PID: 4800)
- chcp.com (PID: 4932)
- Client.exe (PID: 5212)
- 4363463463464363463463463.exe (PID: 5756)
- chcp.com (PID: 5364)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5900)
- Client.exe (PID: 5832)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 4308)
- chcp.com (PID: 4648)
- Neverlose%20Loader.exe (PID: 3172)
- brbotnet.exe (PID: 4532)
- XClient.exe (PID: 1384)
- AsyncClient.exe (PID: 4656)
- JUSCHED.EXE (PID: 4868)
- 4363463463464363463463463.exe (PID: 3260)
- CritScript.exe (PID: 4616)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4952)
- jusched.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 3456)
- svchost.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 4840)
- Client.exe (PID: 4140)
- asdasdasdasdasd.exe (PID: 5296)
- benpolatalemdar.exe (PID: 5396)
- $77svchost.exe (PID: 4492)
- boleto.exe (PID: 5648)
- VsGraphicsResources2.exe (PID: 6092)
- CleanerV2.exe (PID: 3820)
- 4363463463464363463463463.exe (PID: 5724)
- perviy.exe (PID: 5740)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 4800)
- vsjitdebuggerui.exe (PID: 1760)
- chcp.com (PID: 5852)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 5604)
- Client-built-Playit.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 6176)
- Update.exe (PID: 6304)
- System32.exe (PID: 6348)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- connector1.exe (PID: 6480)
- done12312.exe (PID: 6588)
- hack1226.exe (PID: 6576)
- done12312.exe (PID: 6560)
- QuizPokemon.exe (PID: 6796)
- Install.exe (PID: 6948)
- RuntimeBroker.exe (PID: 7172)
- 235T1TS.exe (PID: 7068)
- random.exe (PID: 7400)
- 7IPCJFu.exe (PID: 7220)
- Installer.exe (PID: 7460)
- Client.exe (PID: 7648)
- Agentnov.exe (PID: 7548)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- service.exe (PID: 7752)
- Fast%20Download.exe (PID: 7392)
- nircmd.exe (PID: 7804)
- Server.exe (PID: 7864)
- EmmetPROD.exe (PID: 5432)
- rah.exe (PID: 7636)
- Test2.exe (PID: 7584)
- Amogus.exe (PID: 6836)
- IMG001.exe (PID: 6972)
- audi.exe (PID: 8168)
- installer.exe.exe (PID: 6072)
- SubDir.exe (PID: 5304)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- WinIntoruntime.exe (PID: 7456)
- njrat.exe (PID: 8620)
- RDPW_Installer.exe (PID: 7156)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8748)
- 1.exe (PID: 8920)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8820)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8800)
- Server1.exe (PID: 9852)
- winbox.exe (PID: 9864)
- tftp.exe (PID: 9936)
- 2.exe (PID: 10216)
- Device2.exe (PID: 7632)
- 3.exe (PID: 8264)
- cHSzTDjVl.exe (PID: 5668)
- chcp.com (PID: 8432)
- Server.exe (PID: 8460)
- wic.exe (PID: 9412)
- payload.exe (PID: 9484)
- 4363463463464363463463463.exe (PID: 8668)
- newfour.exe (PID: 10192)
- done12312.exe (PID: 6872)
- 4363463463464363463463463.exe (PID: 9352)
- Wave.exe (PID: 6544)
- boleto.exe (PID: 8720)
- system32.exe (PID: 6276)
- uu.exe (PID: 9412)
- IMG001.exe (PID: 4144)
- RambledMime.exe (PID: 3600)
- intro.avi.exe (PID: 8440)
- Destover.exe (PID: 8332)
- 3e3ev3.exe (PID: 8144)
- Ywtencv.exe (PID: 10000)
- cronikxqqq.exe (PID: 9184)
- G1.exe (PID: 10212)
- XMZTSVYE_l10_wix4_dash.exe (PID: 10180)
- jusched.exe (PID: 2172)
- System32.exe (PID: 2164)
- $77svchost.exe (PID: 2256)
- Client.exe (PID: 2248)
- RuntimeBroker.exe (PID: 2180)
- IMEKLMG.EXE (PID: 2460)
- IMEKLMG.EXE (PID: 2468)
- winserv.exe (PID: 2512)
- Win64.exe (PID: 2228)
- boleto.exe (PID: 2540)
- Wave.exe (PID: 2524)
- done12312.exe (PID: 2564)
- Server.exe (PID: 2572)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2656)
- vsjitdebuggerui.exe (PID: 2192)
- Server.exe (PID: 2484)
- cbas.exe (PID: 2636)
- Wave.exe (PID: 2668)
- Client.exe (PID: 2268)
- done12312.exe (PID: 2864)
- done12312.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2356)
Disables trace logs
- 4363463463464363463463463.exe (PID: 128)
- dfsvc.exe (PID: 2968)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 5416)
- boleto.exe (PID: 5648)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 6176)
- $77svchost.exe (PID: 4492)
- Installer.exe (PID: 7460)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8820)
- 4363463463464363463463463.exe (PID: 8668)
- boleto.exe (PID: 2596)
- $77svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 2356)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 128)
- dfsvc.exe (PID: 2968)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 5604)
- $77svchost.exe (PID: 4492)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- 4363463463464363463463463.exe (PID: 6176)
- random.exe (PID: 7400)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8820)
- 7IPCJFu.exe (PID: 7220)
- 4363463463464363463463463.exe (PID: 8668)
- $77svchost.exe (PID: 2256)
- 4363463463464363463463463.exe (PID: 2356)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- support.client.exe (PID: 3444)
- Client.exe (PID: 2960)
- dfsvc.exe (PID: 2968)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- 4363463463464363463463463.exe (PID: 5496)
- Client.exe (PID: 5832)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- Neverlose%20Loader.exe (PID: 3172)
- XClient.exe (PID: 1384)
- brbotnet.exe (PID: 4532)
- JUSCHED.EXE (PID: 4868)
- 4363463463464363463463463.exe (PID: 3260)
- AsyncClient.exe (PID: 4656)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 5100)
- jusched.exe (PID: 5404)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- svchost.exe (PID: 5604)
- asdasdasdasdasd.exe (PID: 5296)
- Client.exe (PID: 4140)
- boleto.exe (PID: 5648)
- CleanerV2.exe (PID: 3820)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 5344)
- VsGraphicsResources2.exe (PID: 6092)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 4800)
- vsjitdebuggerui.exe (PID: 1760)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 6176)
- Client-built-Playit.exe (PID: 5036)
- Update.exe (PID: 6304)
- $77svchost.exe (PID: 4492)
- System32.exe (PID: 6348)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- done12312.exe (PID: 6588)
- Install.exe (PID: 6948)
- RuntimeBroker.exe (PID: 7172)
- random.exe (PID: 7400)
- Client.exe (PID: 7648)
- Installer.exe (PID: 7460)
- rah.exe (PID: 7636)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Fast%20Download.exe (PID: 7392)
- Test2.exe (PID: 7584)
- Amogus.exe (PID: 6836)
- installer.exe.exe (PID: 6072)
- audi.exe (PID: 8168)
- SubDir.exe (PID: 5304)
- WinIntoruntime.exe (PID: 7456)
- Server.exe (PID: 7864)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8740)
- 1.exe (PID: 8920)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8748)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- 4363463463464363463463463.exe (PID: 8820)
- Server1.exe (PID: 9852)
- cHSzTDjVl.exe (PID: 5668)
- wic.exe (PID: 9412)
- Device2.exe (PID: 7632)
- IMG001.exe (PID: 6972)
- njrat.exe (PID: 8620)
- 4363463463464363463463463.exe (PID: 8668)
- Wave.exe (PID: 2668)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2540)
- done12312.exe (PID: 2856)
- done12312.exe (PID: 2864)
- boleto.exe (PID: 2596)
- $77svchost.exe (PID: 2256)
- Win64.exe (PID: 2228)
- RuntimeBroker.exe (PID: 2180)
- Client.exe (PID: 2268)
- Client.exe (PID: 2248)
- System32.exe (PID: 2164)
- Server.exe (PID: 2572)
- jusched.exe (PID: 2172)
- vsjitdebuggerui.exe (PID: 2192)
- 4363463463464363463463463.exe (PID: 2356)
- Server.exe (PID: 2484)
Reads the computer name
- 4363463463464363463463463.exe (PID: 128)
- Client-built.exe (PID: 1800)
- support.client.exe (PID: 3444)
- dfsvc.exe (PID: 2968)
- Client.exe (PID: 2960)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 1488)
- Client.exe (PID: 116)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 5496)
- Client.exe (PID: 5832)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4308)
- Neverlose%20Loader.exe (PID: 3172)
- XClient.exe (PID: 1384)
- brbotnet.exe (PID: 4532)
- AsyncClient.exe (PID: 4656)
- CritScript.exe (PID: 4616)
- JUSCHED.EXE (PID: 4868)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4952)
- jusched.exe (PID: 5404)
- svchost.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 4840)
- Client.exe (PID: 4140)
- asdasdasdasdasd.exe (PID: 5296)
- boleto.exe (PID: 5648)
- VsGraphicsResources2.exe (PID: 6092)
- $77svchost.exe (PID: 4492)
- benpolatalemdar.exe (PID: 5396)
- 4363463463464363463463463.exe (PID: 5724)
- CleanerV2.exe (PID: 3820)
- perviy.exe (PID: 5740)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 5344)
- vsjitdebuggerui.exe (PID: 1760)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5604)
- Client-built-Playit.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 6176)
- Update.exe (PID: 6304)
- System32.exe (PID: 6348)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- done12312.exe (PID: 6560)
- done12312.exe (PID: 6588)
- Install.exe (PID: 6948)
- QuizPokemon.exe (PID: 6796)
- RuntimeBroker.exe (PID: 7172)
- 7IPCJFu.exe (PID: 7220)
- 235T1TS.exe (PID: 7068)
- Installer.exe (PID: 7460)
- Agentnov.exe (PID: 7548)
- random.exe (PID: 7400)
- Client.exe (PID: 7648)
- NJRAT%20DANGEROUS.exe (PID: 7688)
- Server.exe (PID: 7864)
- Test2.exe (PID: 7584)
- rah.exe (PID: 7636)
- Fast%20Download.exe (PID: 7392)
- Amogus.exe (PID: 6836)
- IMG001.exe (PID: 6972)
- installer.exe.exe (PID: 6072)
- SubDir.exe (PID: 5304)
- audi.exe (PID: 8168)
- IYDT631V1VD8X7KEIEVZY64UGI3.exe (PID: 5864)
- WinIntoruntime.exe (PID: 7456)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8808)
- 1.exe (PID: 8920)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8820)
- Server1.exe (PID: 9852)
- cHSzTDjVl.exe (PID: 5668)
- njrat.exe (PID: 8620)
- wic.exe (PID: 9412)
- Device2.exe (PID: 7632)
- 4363463463464363463463463.exe (PID: 8668)
- newfour.exe (PID: 10192)
- 4363463463464363463463463.exe (PID: 9352)
- tftp.exe (PID: 9936)
- RuntimeBroker.exe (PID: 2180)
- IMEKLMG.EXE (PID: 2468)
- IMEKLMG.EXE (PID: 2460)
- Server.exe (PID: 2484)
- $77svchost.exe (PID: 2256)
- Win64.exe (PID: 2228)
- boleto.exe (PID: 2540)
- Wave.exe (PID: 2524)
- done12312.exe (PID: 2564)
- Server.exe (PID: 2572)
- done12312.exe (PID: 2656)
- jusched.exe (PID: 2172)
- Wave.exe (PID: 2668)
- vsjitdebuggerui.exe (PID: 2192)
- boleto.exe (PID: 2596)
- done12312.exe (PID: 2864)
- done12312.exe (PID: 2856)
- System32.exe (PID: 2164)
- Client.exe (PID: 2268)
- Client.exe (PID: 2248)
Creates files or folders in the user directory
- Client-built.exe (PID: 1800)
- dfsvc.exe (PID: 2968)
- ScreenConnect.WindowsClient.exe (PID: 3316)
- qq.exe (PID: 4688)
- JUSCHED.EXE (PID: 4868)
- svchost.exe (PID: 5604)
- XClient.exe (PID: 1384)
- Client-built-Playit.exe (PID: 5036)
- Update.exe (PID: 6304)
- boleto.exe (PID: 5648)
- Agentnov.exe (PID: 7548)
- done12312.exe (PID: 6588)
- System32.exe (PID: 6348)
- Fast%20Download.exe (PID: 7392)
- rah.exe (PID: 7636)
- installer.exe.exe (PID: 6072)
- audi.exe (PID: 8168)
- WinIntoruntime.exe (PID: 7456)
- vsjitdebuggerui.exe (PID: 1760)
- jusched.exe (PID: 5404)
- Server1.exe (PID: 9852)
- IMG001.exe (PID: 6972)
- wic.exe (PID: 9412)
- NJRAT%20DANGEROUS.exe (PID: 7688)
Checks proxy server information
- dfsvc.exe (PID: 2968)
- audi.exe (PID: 8168)
- cHSzTDjVl.exe (PID: 5668)
- wic.exe (PID: 9412)
- tftp.exe (PID: 9936)
Create files in a temporary directory
- dfsvc.exe (PID: 2968)
- Client.exe (PID: 2960)
- Client.exe (PID: 872)
- Client.exe (PID: 3232)
- Client.exe (PID: 3784)
- Client.exe (PID: 3424)
- Client.exe (PID: 116)
- Client.exe (PID: 1488)
- Client.exe (PID: 4420)
- Client.exe (PID: 4800)
- Client.exe (PID: 5212)
- Client.exe (PID: 5832)
- brbotnet.exe (PID: 4532)
- CritScript.exe (PID: 4616)
- svchost.exe (PID: 5604)
- Client.exe (PID: 4140)
- QuizPokemon.exe (PID: 6796)
- InstallerPack_20.1.23770_win64.exe (PID: 6508)
- IMG001.exe (PID: 6972)
- random.exe (PID: 7400)
- RDPW_Installer.exe (PID: 7156)
- WinIntoruntime.exe (PID: 7456)
- Server1.exe (PID: 9852)
- njrat.exe (PID: 8620)
- Win64.exe (PID: 2228)
Process checks whether UAC notifications are on
- dfsvc.exe (PID: 2968)
- IMEKLMG.EXE (PID: 2468)
- IMEKLMG.EXE (PID: 2460)
Changes the display of characters in the console
- cmd.exe (PID: 2420)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 2616)
- cmd.exe (PID: 1088)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 4004)
- cmd.exe (PID: 1500)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 4900)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 5584)
- cmd.exe (PID: 10120)
SCREENCONNECT has been detected
- ScreenConnect.WindowsClient.exe (PID: 3316)
Manual execution by a user
- firefox.exe (PID: 3900)
- msedge.exe (PID: 2608)
- chrome.exe (PID: 852)
- 4363463463464363463463463.exe (PID: 5648)
- 4363463463464363463463463.exe (PID: 5756)
- 4363463463464363463463463.exe (PID: 5496)
- 4363463463464363463463463.exe (PID: 5864)
- 4363463463464363463463463.exe (PID: 5900)
- 4363463463464363463463463.exe (PID: 6072)
- 4363463463464363463463463.exe (PID: 6116)
- 4363463463464363463463463.exe (PID: 4200)
- 4363463463464363463463463.exe (PID: 5976)
- 4363463463464363463463463.exe (PID: 6012)
- 4363463463464363463463463.exe (PID: 4308)
- 4363463463464363463463463.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 4856)
- 4363463463464363463463463.exe (PID: 5052)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4952)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 6092)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 1124)
- 4363463463464363463463463.exe (PID: 6004)
- 4363463463464363463463463.exe (PID: 5724)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 5344)
- 4363463463464363463463463.exe (PID: 5144)
- 4363463463464363463463463.exe (PID: 5416)
- 4363463463464363463463463.exe (PID: 5104)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 3028)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5168)
- 4363463463464363463463463.exe (PID: 268)
- 4363463463464363463463463.exe (PID: 5044)
- 4363463463464363463463463.exe (PID: 5604)
- 4363463463464363463463463.exe (PID: 4196)
- 4363463463464363463463463.exe (PID: 6176)
- 4363463463464363463463463.exe (PID: 6720)
- 4363463463464363463463463.exe (PID: 7840)
- 4363463463464363463463463.exe (PID: 7516)
- 4363463463464363463463463.exe (PID: 7536)
- 4363463463464363463463463.exe (PID: 7632)
- 4363463463464363463463463.exe (PID: 7640)
- 4363463463464363463463463.exe (PID: 5584)
- 4363463463464363463463463.exe (PID: 7760)
- 4363463463464363463463463.exe (PID: 7212)
- 4363463463464363463463463.exe (PID: 8252)
- 4363463463464363463463463.exe (PID: 8264)
- 4363463463464363463463463.exe (PID: 8740)
- 4363463463464363463463463.exe (PID: 8756)
- 4363463463464363463463463.exe (PID: 8748)
- 4363463463464363463463463.exe (PID: 8792)
- 4363463463464363463463463.exe (PID: 8800)
- 4363463463464363463463463.exe (PID: 8808)
- 4363463463464363463463463.exe (PID: 8828)
- 4363463463464363463463463.exe (PID: 8820)
- 4363463463464363463463463.exe (PID: 8780)
- 4363463463464363463463463.exe (PID: 8764)
- 4363463463464363463463463.exe (PID: 8772)
- 4363463463464363463463463.exe (PID: 6824)
- 4363463463464363463463463.exe (PID: 8668)
- 4363463463464363463463463.exe (PID: 7468)
- 4363463463464363463463463.exe (PID: 9352)
- IMEKLMG.EXE (PID: 2460)
- IMEKLMG.EXE (PID: 2468)
- Server.exe (PID: 2484)
- winserv.exe (PID: 2512)
- done12312.exe (PID: 2564)
- Server.exe (PID: 2572)
- boleto.exe (PID: 2596)
- Wave.exe (PID: 2524)
- boleto.exe (PID: 2540)
- done12312.exe (PID: 2656)
- Wave.exe (PID: 2668)
- cbas.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3916)
- 4363463463464363463463463.exe (PID: 2356)
Application launched itself
- firefox.exe (PID: 3900)
- chrome.exe (PID: 852)
- msedge.exe (PID: 2608)
- firefox.exe (PID: 3892)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 128)
- qq.exe (PID: 4688)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 5100)
- 4363463463464363463463463.exe (PID: 4840)
- 4363463463464363463463463.exe (PID: 4800)
- 4363463463464363463463463.exe (PID: 3456)
- Update.exe (PID: 6304)
- 4363463463464363463463463.exe (PID: 5416)
- RDPW_Installer.exe (PID: 7156)
- 4363463463464363463463463.exe (PID: 3260)
- winserv.exe (PID: 2512)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5088)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 5692)
- powershell.exe (PID: 6624)
- powershell.exe (PID: 6824)
- powershell.exe (PID: 6992)
- powershell.exe (PID: 7412)
- powershell.exe (PID: 6848)
Reads product name
- benpolatalemdar.exe (PID: 5396)
- WinIntoruntime.exe (PID: 7456)
- cHSzTDjVl.exe (PID: 5668)
Drops encrypted VBS script (Microsoft Script Encoder)
- Agentnov.exe (PID: 7548)
NirSoft software is detected
- nircmd.exe (PID: 7804)
The sample compiled with polish language support
- 4363463463464363463463463.exe (PID: 4800)
Attempting to connect via WebSocket
- EmmetPROD.exe (PID: 5432)
The sample compiled with turkish language support
- audi.exe (PID: 8168)
Creates files in the program directory
- audi.exe (PID: 8168)
The sample compiled with chinese language support
- audi.exe (PID: 8168)
- wic.exe (PID: 9412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(3172) Neverlose%20Loader.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameNeverlose Loader.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
621
Monitored processes
348
Malicious processes
110
Suspicious processes
30
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | cmd.exe | ||||||||||||
User: admin Company: Discord Integrity Level: HIGH Description: Discord Exit code: 0 Version: 0.3.2.5 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 1073807364 Version: 0.0.0.0 Modules
| |||||||||||||||
| 400 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 436 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | winlogon.exe | C:\Windows\System32\winlogon.exe | smss.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 692 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 872 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | cmd.exe | ||||||||||||
User: admin Company: Discord Integrity Level: HIGH Description: Discord Exit code: 0 Version: 0.3.2.5 Modules
| |||||||||||||||
Total events
235 865
Read events
233 576
Write events
2 214
Delete events
75
Modification events
| (PID) Process: | (1080) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: D4DA6DE94CE9 | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D69B561148F01C77C54578C10926DF5B856976AD |
Value: | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 5C000000010000000400000000080000530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB0282000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (128) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
161
Suspicious files
971
Text files
233
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 128 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\support.client.exe | executable | |
MD5:1972B9941619379564774B7AE3C0F173 | SHA256:B92BD4B002F78EB1C2B62E8DAD361B5691A01FEB1FF7CC693C80DF09F2E59664 | |||
| 2968 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\CQQOWQV7.COD\8D7JXZHQ.P32.application | xml | |
MD5:9AC4954D33E063FDEF5236004D57442E | SHA256:CE37639F366DA772331216865047D422F00A6B0BC46BE4FDB7F0E151DF0D0DA9 | |||
| 1800 | Client-built.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:FA5F99FF110280EFE85F4663CFB3D6B8 | SHA256:5B41A8AC5A68AB33E4891EA03533E8EA650C16DD669D277DECAE2F00217A1E4D | |||
| 2968 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\BBEW1LPE.OG5\CXDL0M0W.BO4\ScreenConnect.WindowsClient.exe.manifest | xml | |
MD5:59009C4F246E6528BA70C6F65EE5DD0C | SHA256:E272B0496A6350E84FC34140476F9EF1BF51612ABCBF6014C3CA07E0ABE12EA1 | |||
| 128 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\cam.exe | executable | |
MD5:7B6595A5FE71F1CD99118177CB4F156E | SHA256:48F3D614D7A5BB1D98DE0387AF6F48FB8D08F892982821BBE9FD7DC867185454 | |||
| 128 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Client-built.exe | executable | |
MD5:FA5F99FF110280EFE85F4663CFB3D6B8 | SHA256:5B41A8AC5A68AB33E4891EA03533E8EA650C16DD669D277DECAE2F00217A1E4D | |||
| 128 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\BootstrapperNew.exe | executable | |
MD5:A36750FE814C6CD0A94312EBAF85E07E | SHA256:933ACDB61D5D05BB55CD56957312B677719AC237A2DAAE0F1DAF9D70DC68F2DE | |||
| 2968 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\932a2db58c237abd381d22df4c63a04a_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
| 2968 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C56C4404C4DEF0DC88E5FCD9F09CB2F1 | binary | |
MD5:E0888461DCE6148EC1D222A0F52AA118 | SHA256:46AE06BF34896C8D84154D431DB5CF7E27D6DA49DDF193574350486C476CF631 | |||
| 2968 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\BBEW1LPE.OG5\CXDL0M0W.BO4\ScreenConnect.WindowsBackstageShell.exe | executable | |
MD5:E34E8690E53141EE6914238252FA9988 | SHA256:B2B1125EC8B482BE4447C848EE45F83AB8FE8C4A25D110C5761166C961FF3EA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
101
TCP/UDP connections
444
DNS requests
332
Threats
243
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
128 | 4363463463464363463463463.exe | GET | 200 | 195.211.191.93:80 | http://195.211.191.93/cam.exe | unknown | — | — | unknown |
128 | 4363463463464363463463463.exe | GET | — | 60.22.23.50:9898 | http://60.22.23.50:9898/ykwsyyt/help/HDDrive1095_XinAnPlug3030_20230619_inno.exe | unknown | — | — | unknown |
3892 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3892 | firefox.exe | POST | 200 | 2.18.121.27:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3892 | firefox.exe | POST | 200 | 2.18.121.21:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3892 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
2968 | dfsvc.exe | GET | 200 | 2.17.190.73:80 | http://cacerts.digicert.com/DigiCertTrustedG4CodeSigningRSA4096SHA3842021CA1.crt | unknown | — | — | whitelisted |
3892 | firefox.exe | POST | 200 | 2.18.121.21:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3892 | firefox.exe | POST | 200 | 142.251.36.3:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
3892 | firefox.exe | POST | 200 | 142.251.36.3:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
128 | 4363463463464363463463463.exe | 151.101.206.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
128 | 4363463463464363463463463.exe | 195.211.191.93:80 | — | WINDSTREAM | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
128 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
128 | 4363463463464363463463463.exe | 172.66.47.197:443 | c0e5b87c.solaraweb-alj.pages.dev | CLOUDFLARENET | US | shared |
128 | 4363463463464363463463463.exe | 104.21.64.90:443 | m.nexhelp.top | CLOUDFLARENET | — | unknown |
2968 | dfsvc.exe | 104.21.64.90:443 | m.nexhelp.top | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
c0e5b87c.solaraweb-alj.pages.dev |
| shared |
m.nexhelp.top |
| malicious |
tiwanlinm.duckdns.org |
| unknown |
cacerts.digicert.com |
| whitelisted |
havocc.ddns.net |
| malicious |
variols.sirhelp.top |
| unknown |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
128 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
128 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
128 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
128 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
128 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
128 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 39 |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1080 | svchost.exe | Misc activity | ET INFO DNS Query to Cloudflare Page Developer Domain (pages .dev) |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |
128 | 4363463463464363463463463.exe | Misc activity | ET INFO Observed Cloudflare Page Developer Domain (pages .dev in TLS SNI) |
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
4363463463464363463463463.exe | The remote name could not be resolved: 'tiwanlinm.duckdns.org'
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status Originated: -1073741772
*** Source File: d:\iso_whid\x86fre\base\isolation\win32\isoreg_direct.cpp, line 1127
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|