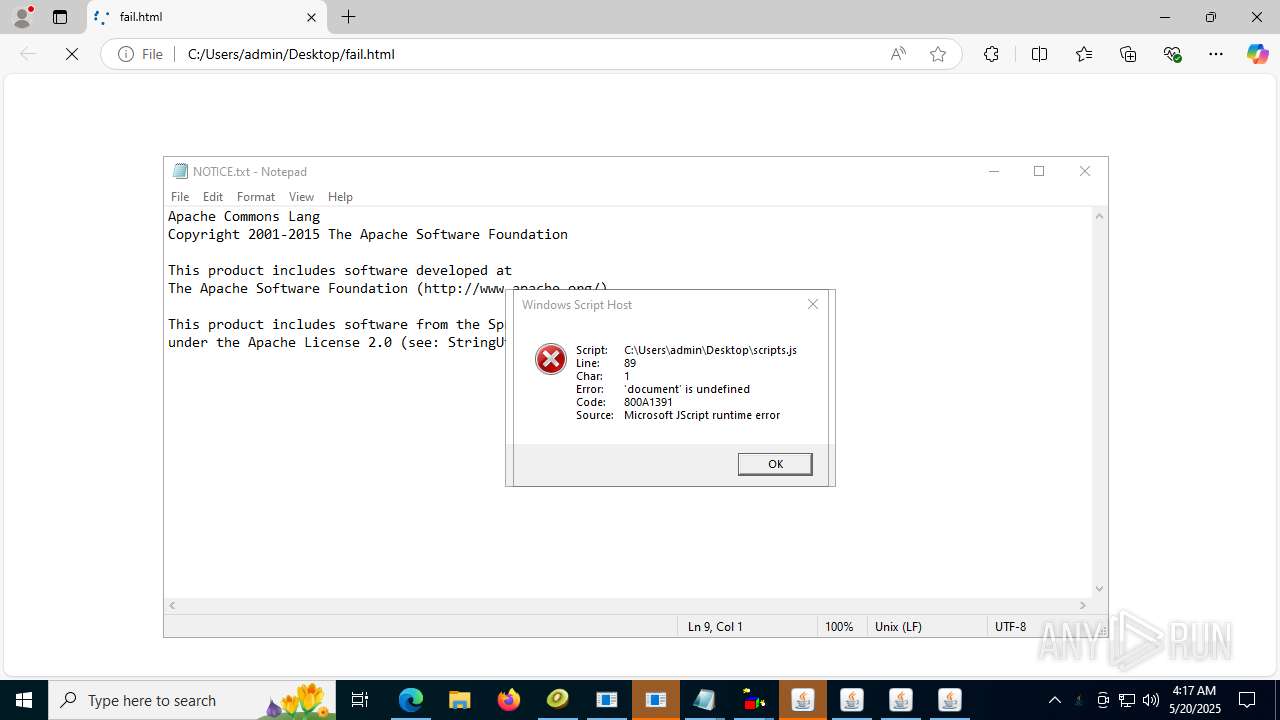
| File name: | 4363463463464363463463463.bin |
| Full analysis: | https://app.any.run/tasks/714f15f0-5bd3-48f3-acd0-4cd13859a8fc |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 20, 2025, 04:15:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
STEALER has been found (auto)
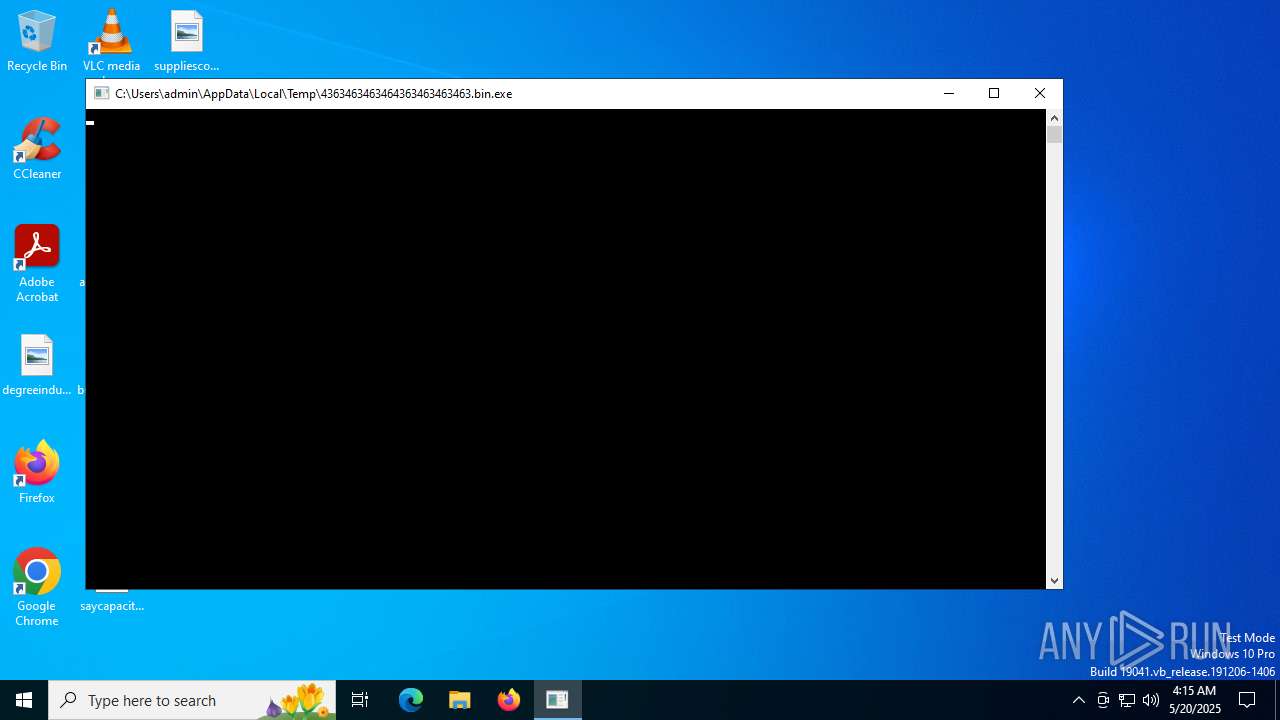
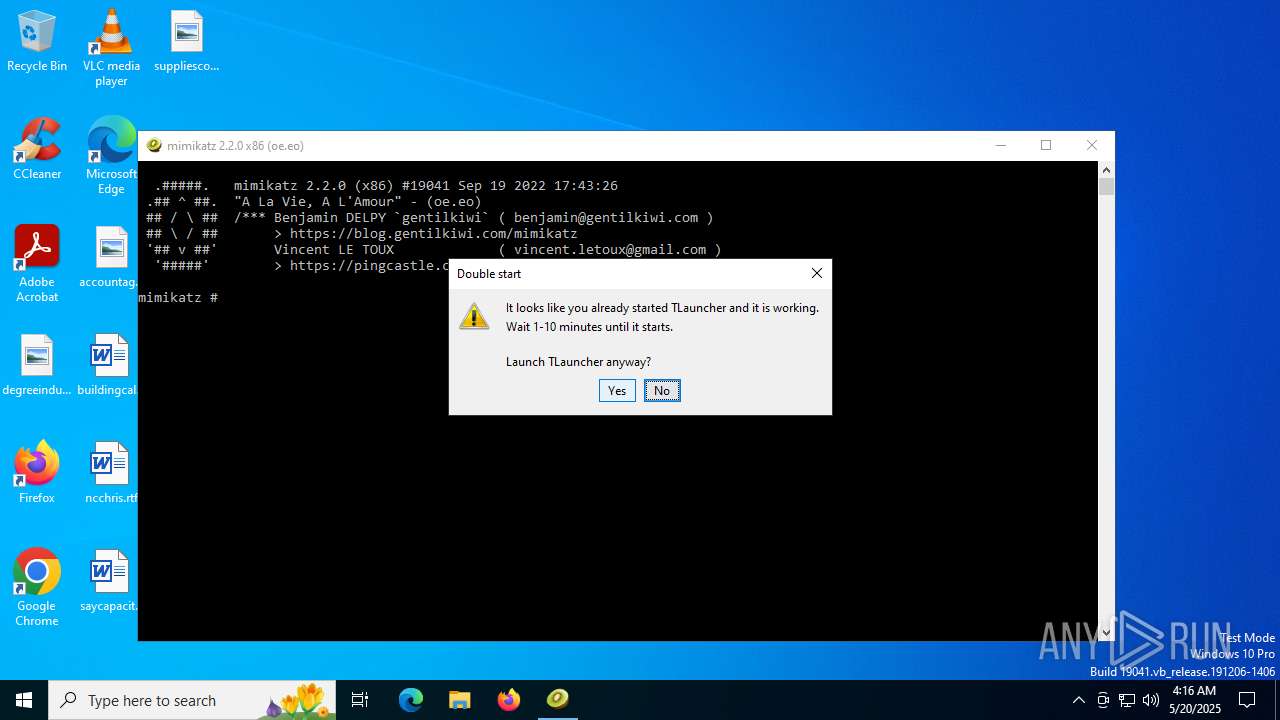
- 4363463463464363463463463.bin.exe (PID: 2680)
Executing a file with an untrusted certificate
- TestLAB.exe (PID: 6900)
- TestLAB.exe (PID: 6260)
- CompoundsTrim.exe (PID: 7544)
- OperaAirSetup.exe (PID: 8716)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.bin.exe (PID: 2680)
QUASARRAT has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 2680)
- Java32.exe (PID: 9428)
FORMBOOK has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 2680)
RHADAMANTHYS has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 2680)
QUASAR has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 2680)
- intro.avi.exe (PID: 9488)
Uses Task Scheduler to autorun other applications
- Client-built8.exe (PID: 8852)
- intro.avi.exe (PID: 9488)
Changes powershell execution policy (Bypass)
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
Adds path to the Windows Defender exclusion list
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
Changes Windows Defender settings
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
Bypass execution policy to execute commands
- powershell.exe (PID: 10376)
- powershell.exe (PID: 10364)
SUSPICIOUS
Executable content was dropped or overwritten
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.exe (PID: 6900)
- TestLAB.tmp (PID: 1700)
- TestLAB.exe (PID: 6260)
- TestLAB.tmp (PID: 3672)
- Minecraft.exe (PID: 1488)
- Client-built8.exe (PID: 8852)
- Java32.exe (PID: 9428)
- intro.avi.exe (PID: 9488)
Reads security settings of Internet Explorer
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.tmp (PID: 1700)
- Minecraft.exe (PID: 1488)
- Minecraft.exe (PID: 4236)
- Minecraft.exe (PID: 6636)
- Minecraft.exe (PID: 424)
- Minecraft.exe (PID: 7040)
- Minecraft.exe (PID: 4832)
- Minecraft.exe (PID: 2760)
- Minecraft.exe (PID: 3832)
- Minecraft.exe (PID: 684)
- Minecraft.exe (PID: 7248)
- Minecraft.exe (PID: 7444)
- CompoundsTrim.exe (PID: 7544)
- Minecraft.exe (PID: 7676)
- Minecraft.exe (PID: 7896)
- Minecraft.exe (PID: 8172)
- Minecraft.exe (PID: 4044)
Reads the Windows owner or organization settings
- TestLAB.tmp (PID: 1700)
- TestLAB.tmp (PID: 3672)
Process drops legitimate windows executable
- TestLAB.tmp (PID: 1700)
- TestLAB.tmp (PID: 3672)
- 4363463463464363463463463.bin.exe (PID: 2680)
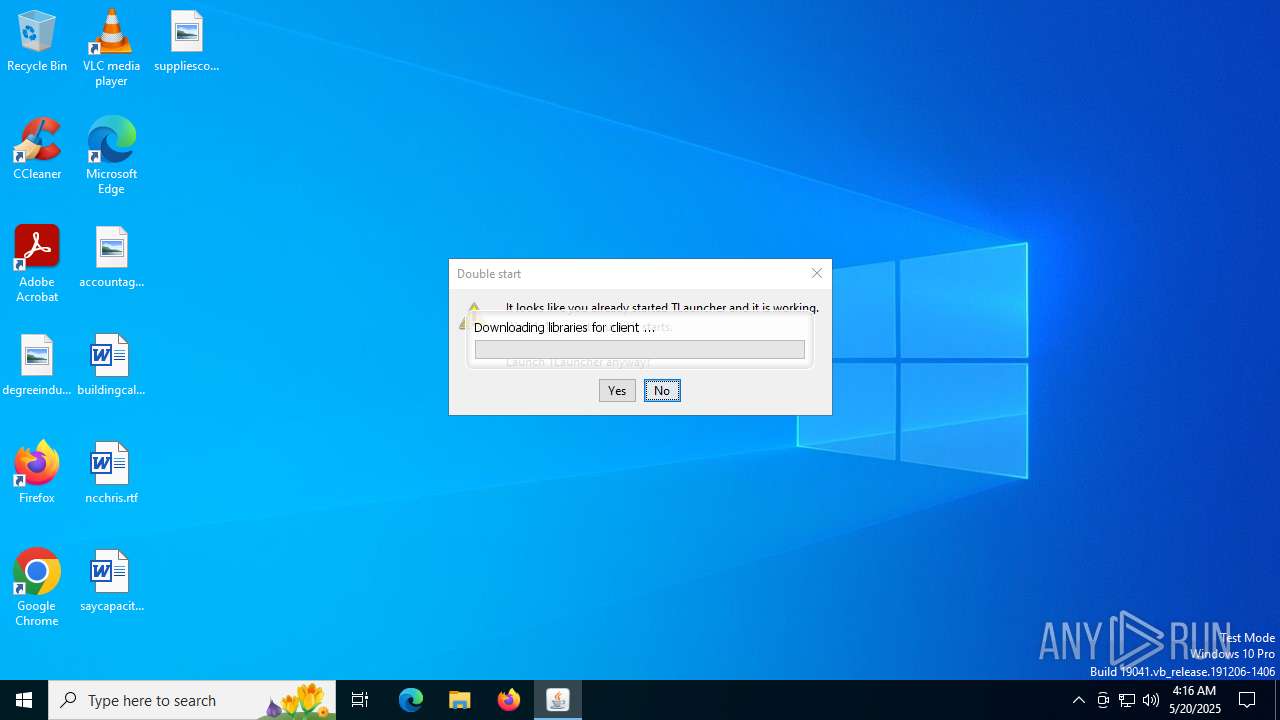
Checks for Java to be installed
- TLauncher.exe (PID: 2192)
- TLauncher.exe (PID: 3932)
- TLauncher.exe (PID: 1632)
- TLauncher.exe (PID: 6392)
- TLauncher.exe (PID: 4700)
- TLauncher.exe (PID: 4844)
- TLauncher.exe (PID: 3932)
- TLauncher.exe (PID: 7072)
- TLauncher.exe (PID: 7208)
- TLauncher.exe (PID: 7656)
- TLauncher.exe (PID: 7412)
- TLauncher.exe (PID: 7888)
- TLauncher.exe (PID: 8096)
- TLauncher.exe (PID: 7472)
- TLauncher.exe (PID: 4104)
Application launched itself
- Minecraft.exe (PID: 4236)
- Minecraft.exe (PID: 6636)
- Minecraft.exe (PID: 424)
- Minecraft.exe (PID: 7040)
- Minecraft.exe (PID: 4832)
- Minecraft.exe (PID: 2760)
- Minecraft.exe (PID: 3832)
- Minecraft.exe (PID: 684)
- Minecraft.exe (PID: 7248)
- Minecraft.exe (PID: 7444)
- Minecraft.exe (PID: 7676)
- Minecraft.exe (PID: 7896)
- javaw.exe (PID: 4460)
- Minecraft.exe (PID: 8172)
- Minecraft.exe (PID: 4044)
- Minecraft.exe (PID: 7472)
- Minecraft.exe (PID: 8388)
- Minecraft.exe (PID: 8564)
- Minecraft.exe (PID: 8756)
- Minecraft.exe (PID: 9160)
- javaw.exe (PID: 7444)
- javaw.exe (PID: 8328)
- Minecraft.exe (PID: 5432)
- javaw.exe (PID: 8576)
- Minecraft.exe (PID: 9592)
- Minecraft.exe (PID: 1100)
- Minecraft.exe (PID: 10864)
- Minecraft.exe (PID: 9680)
- javaw.exe (PID: 8128)
- javaw.exe (PID: 8720)
- Minecraft.exe (PID: 11424)
- Minecraft.exe (PID: 12136)
- Minecraft.exe (PID: 7960)
- Minecraft.exe (PID: 10468)
- javaw.exe (PID: 11324)
- Minecraft.exe (PID: 10412)
- javaw.exe (PID: 12020)
- Minecraft.exe (PID: 12944)
- Minecraft.exe (PID: 13852)
Process requests binary or script from the Internet
- 4363463463464363463463463.bin.exe (PID: 2680)
- javaw.exe (PID: 4460)
Potential Corporate Privacy Violation
- 4363463463464363463463463.bin.exe (PID: 2680)
- svchost.exe (PID: 2200)
Connects to unusual port
- 4363463463464363463463463.bin.exe (PID: 2680)
- Client-built.exe (PID: 8344)
Executing commands from a ".bat" file
- CompoundsTrim.exe (PID: 7544)
- java.exe (PID: 10476)
- Client.exe (PID: 3944)
- systemware.exe (PID: 10440)
Starts CMD.EXE for commands execution
- CompoundsTrim.exe (PID: 7544)
- javaw.exe (PID: 1232)
- javaw.exe (PID: 7444)
- javaw.exe (PID: 7600)
- javaw.exe (PID: 8328)
- javaw.exe (PID: 8576)
- javaw.exe (PID: 8720)
- javaw.exe (PID: 7908)
- javaw.exe (PID: 9108)
- javaw.exe (PID: 8128)
- java.exe (PID: 10476)
- Client.exe (PID: 3944)
- javaw.exe (PID: 11324)
- javaw.exe (PID: 12020)
- systemware.exe (PID: 10440)
- javaw.exe (PID: 11124)
Drops 7-zip archiver for unpacking
- TestLAB.tmp (PID: 3672)
Starts a Microsoft application from unusual location
- XClient.exe (PID: 8512)
Starts application with an unusual extension
- cmd.exe (PID: 8820)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 9172)
- cmd.exe (PID: 8700)
- cmd.exe (PID: 8560)
- cmd.exe (PID: 10124)
- cmd.exe (PID: 9684)
- cmd.exe (PID: 10048)
- cmd.exe (PID: 10768)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 12264)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 12412)
- cmd.exe (PID: 11700)
- cmd.exe (PID: 2312)
Uses WMIC.EXE to obtain quick Fix Engineering (patches) data
- cmd.exe (PID: 8820)
- cmd.exe (PID: 8700)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 9172)
- cmd.exe (PID: 8560)
- cmd.exe (PID: 10124)
- cmd.exe (PID: 9684)
- cmd.exe (PID: 10048)
- cmd.exe (PID: 10768)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 11700)
- cmd.exe (PID: 12412)
Checks for external IP
- svchost.exe (PID: 2200)
- Client-built.exe (PID: 8344)
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
- intro.avi.exe (PID: 9488)
- systemware.exe (PID: 10440)
Script adds exclusion path to Windows Defender
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
Starts POWERSHELL.EXE for commands execution
- NJRAT%20DANGEROUS.exe (PID: 8436)
- XClient.exe (PID: 8512)
Starts itself from another location
- intro.avi.exe (PID: 9488)
Executes application which crashes
- systemware.exe (PID: 10440)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7972)
- cmd.exe (PID: 12264)
INFO
Reads the computer name
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.tmp (PID: 1700)
- TestLAB.tmp (PID: 3672)
- Minecraft.exe (PID: 1488)
- Minecraft.exe (PID: 4236)
- Minecraft.exe (PID: 6636)
- Minecraft.exe (PID: 424)
- javaw.exe (PID: 5848)
- Minecraft.exe (PID: 7040)
- javaw.exe (PID: 4460)
- Minecraft.exe (PID: 4832)
- javaw.exe (PID: 1356)
- Minecraft.exe (PID: 2760)
- javaw.exe (PID: 1508)
- Minecraft.exe (PID: 3832)
- javaw.exe (PID: 6208)
- Minecraft.exe (PID: 684)
- javaw.exe (PID: 316)
- Minecraft.exe (PID: 7248)
- javaw.exe (PID: 3392)
- CompoundsTrim.exe (PID: 7544)
- Minecraft.exe (PID: 7444)
- javaw.exe (PID: 1232)
- Minecraft.exe (PID: 7676)
- javaw.exe (PID: 7260)
- Minecraft.exe (PID: 7896)
- javaw.exe (PID: 7428)
- Minecraft.exe (PID: 8172)
- javaw.exe (PID: 7668)
- javaw.exe (PID: 7908)
- Minecraft.exe (PID: 4044)
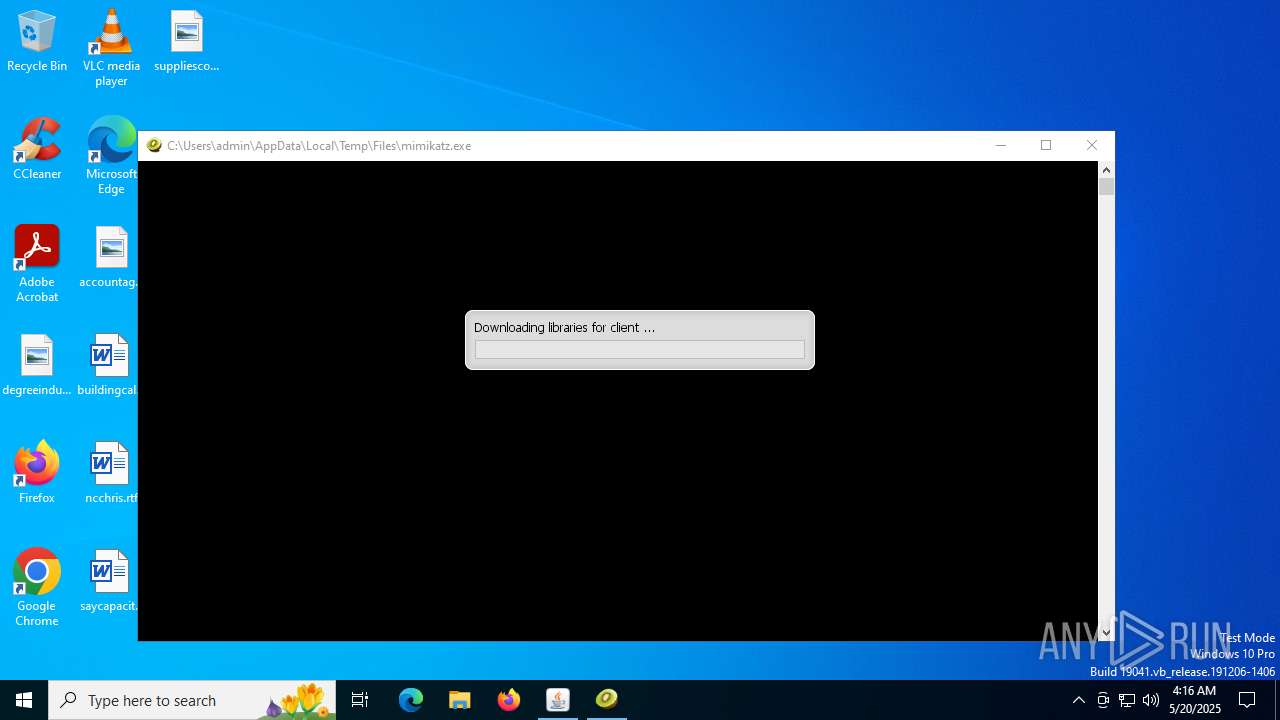
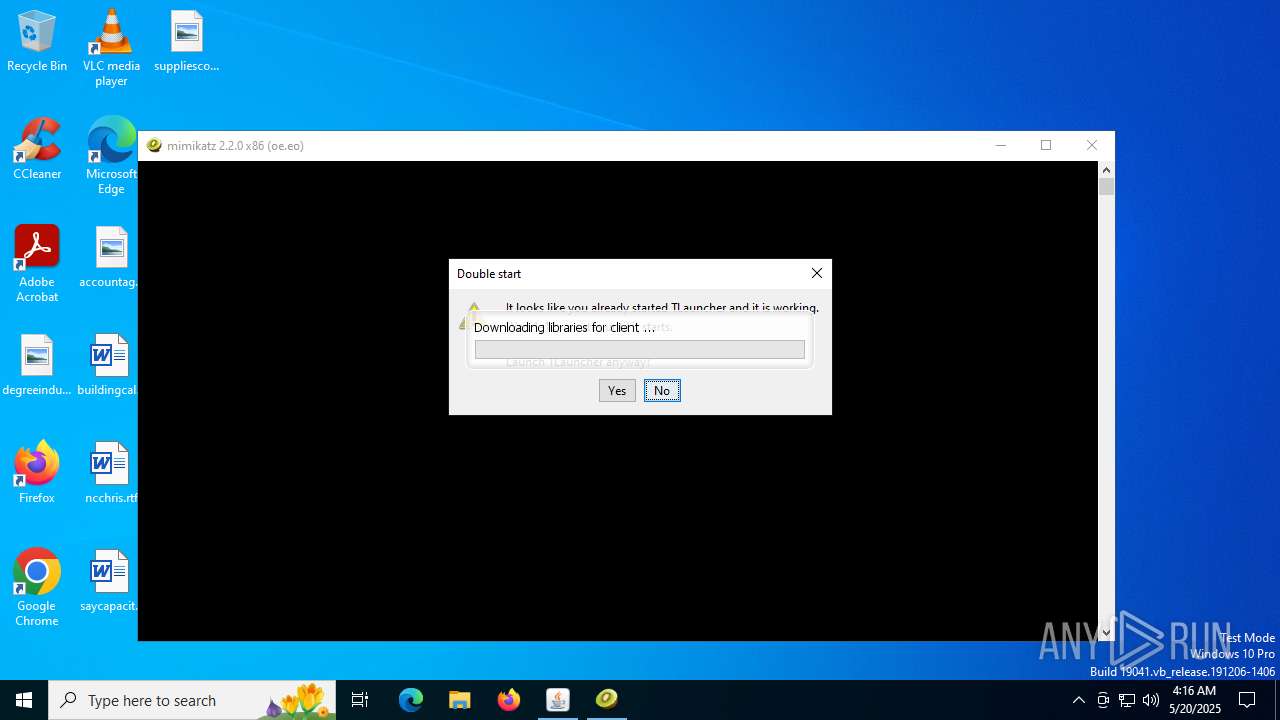
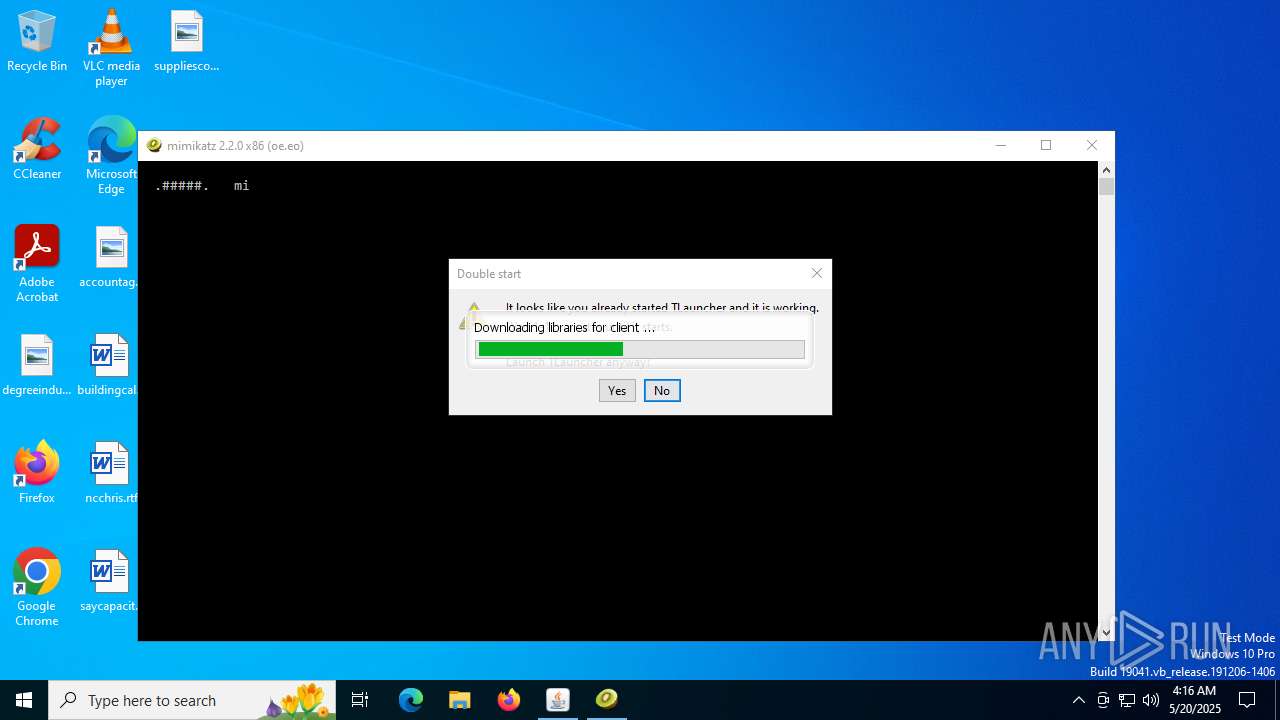
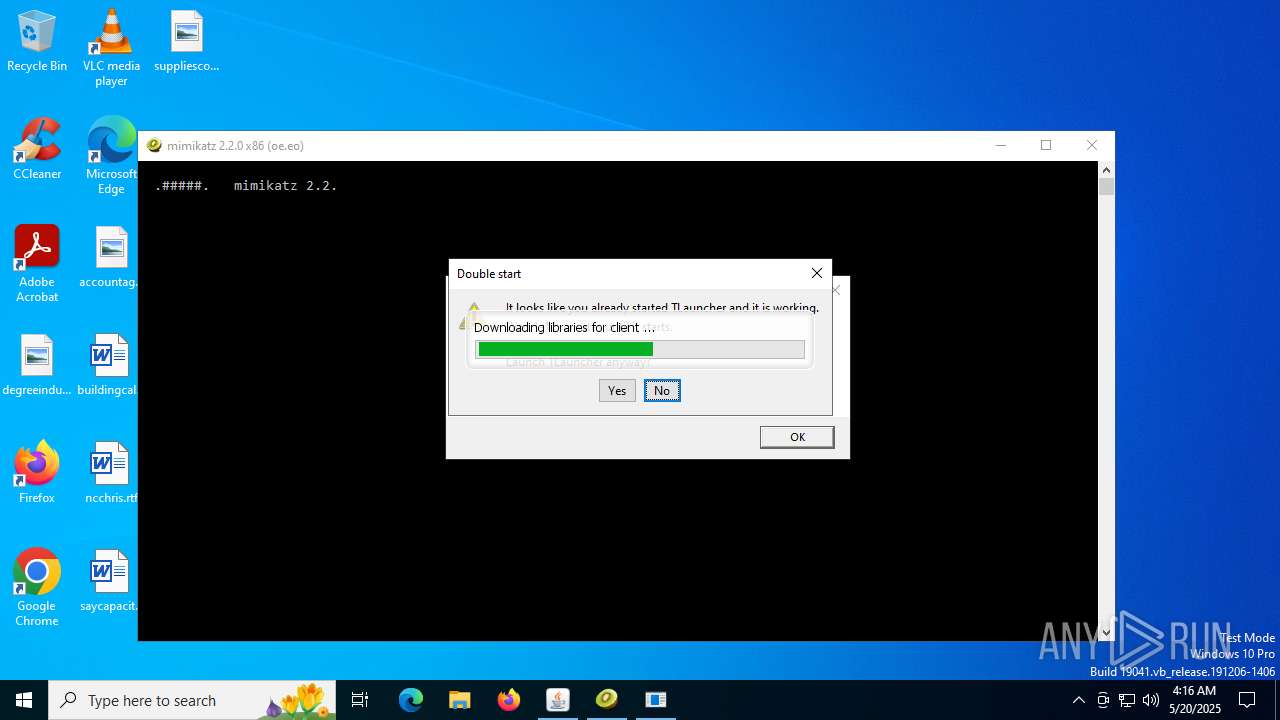
- mimikatz.exe (PID: 2320)
Reads the software policy settings
- 4363463463464363463463463.bin.exe (PID: 2680)
Reads the machine GUID from the registry
- 4363463463464363463463463.bin.exe (PID: 2680)
- javaw.exe (PID: 5848)
- javaw.exe (PID: 1356)
- javaw.exe (PID: 4460)
Create files in a temporary directory
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.exe (PID: 6900)
- TestLAB.tmp (PID: 1700)
- TestLAB.tmp (PID: 3672)
- TestLAB.exe (PID: 6260)
- Minecraft.exe (PID: 1488)
- javaw.exe (PID: 5848)
- Minecraft.exe (PID: 4236)
- javaw.exe (PID: 4460)
- Minecraft.exe (PID: 6636)
- Minecraft.exe (PID: 424)
- javaw.exe (PID: 1508)
- Minecraft.exe (PID: 7040)
- Minecraft.exe (PID: 4832)
- javaw.exe (PID: 6208)
- javaw.exe (PID: 316)
- Minecraft.exe (PID: 2760)
- javaw.exe (PID: 1356)
- javaw.exe (PID: 3392)
- Minecraft.exe (PID: 3832)
- javaw.exe (PID: 7260)
- Minecraft.exe (PID: 7248)
- javaw.exe (PID: 1232)
- Minecraft.exe (PID: 684)
- Minecraft.exe (PID: 7444)
- javaw.exe (PID: 7428)
- CompoundsTrim.exe (PID: 7544)
- javaw.exe (PID: 7668)
- Minecraft.exe (PID: 7676)
- javaw.exe (PID: 7908)
- javaw.exe (PID: 8128)
- Minecraft.exe (PID: 8172)
- javaw.exe (PID: 7284)
- javaw.exe (PID: 7444)
- Minecraft.exe (PID: 4044)
- javaw.exe (PID: 7600)
- Minecraft.exe (PID: 7472)
Checks supported languages
- TestLAB.tmp (PID: 1700)
- TestLAB.exe (PID: 6900)
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.exe (PID: 6260)
- TestLAB.tmp (PID: 3672)
- Minecraft.exe (PID: 1488)
- TLauncher.exe (PID: 2192)
- javaw.exe (PID: 5848)
- Minecraft.exe (PID: 4236)
- TLauncher.exe (PID: 3932)
- javaw.exe (PID: 4460)
- Minecraft.exe (PID: 6636)
- TLauncher.exe (PID: 1632)
- javaw.exe (PID: 1356)
- Minecraft.exe (PID: 424)
- TLauncher.exe (PID: 6392)
- javaw.exe (PID: 1508)
- Minecraft.exe (PID: 7040)
- TLauncher.exe (PID: 4700)
- javaw.exe (PID: 6208)
- Minecraft.exe (PID: 4832)
- TLauncher.exe (PID: 4844)
- javaw.exe (PID: 316)
- Minecraft.exe (PID: 2760)
- TLauncher.exe (PID: 3932)
- javaw.exe (PID: 3392)
- Minecraft.exe (PID: 3832)
- TLauncher.exe (PID: 7072)
- Minecraft.exe (PID: 684)
- javaw.exe (PID: 1232)
- TLauncher.exe (PID: 7208)
- mimikatz.exe (PID: 2320)
- Minecraft.exe (PID: 7248)
- javaw.exe (PID: 7260)
- TLauncher.exe (PID: 7412)
- javaw.exe (PID: 7428)
- Minecraft.exe (PID: 7444)
- CompoundsTrim.exe (PID: 7544)
- TLauncher.exe (PID: 7656)
- javaw.exe (PID: 7668)
- Minecraft.exe (PID: 7676)
- javaw.exe (PID: 7908)
- TLauncher.exe (PID: 7888)
- javaw.exe (PID: 8128)
- TLauncher.exe (PID: 8096)
- Minecraft.exe (PID: 8172)
- javaw.exe (PID: 7284)
- Minecraft.exe (PID: 7896)
- TLauncher.exe (PID: 7472)
- javaw.exe (PID: 7444)
- TLauncher.exe (PID: 4104)
- Minecraft.exe (PID: 4044)
- Minecraft.exe (PID: 7472)
- javaw.exe (PID: 7600)
Process checks computer location settings
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.tmp (PID: 1700)
- Minecraft.exe (PID: 1488)
- Minecraft.exe (PID: 4236)
- Minecraft.exe (PID: 6636)
- Minecraft.exe (PID: 424)
- Minecraft.exe (PID: 7040)
- Minecraft.exe (PID: 4832)
- Minecraft.exe (PID: 2760)
- Minecraft.exe (PID: 3832)
- Minecraft.exe (PID: 684)
- Minecraft.exe (PID: 7248)
- Minecraft.exe (PID: 7444)
- CompoundsTrim.exe (PID: 7544)
- Minecraft.exe (PID: 7676)
- Minecraft.exe (PID: 7896)
- Minecraft.exe (PID: 4044)
- Minecraft.exe (PID: 8172)
Disables trace logs
- 4363463463464363463463463.bin.exe (PID: 2680)
Checks proxy server information
- 4363463463464363463463463.bin.exe (PID: 2680)
The sample compiled with english language support
- TestLAB.tmp (PID: 1700)
- 4363463463464363463463463.bin.exe (PID: 2680)
- TestLAB.tmp (PID: 3672)
- Minecraft.exe (PID: 1488)
Application based on Java
- javaw.exe (PID: 5848)
- javaw.exe (PID: 4460)
- javaw.exe (PID: 1356)
- javaw.exe (PID: 1508)
- javaw.exe (PID: 6208)
- javaw.exe (PID: 316)
- javaw.exe (PID: 1232)
- javaw.exe (PID: 3392)
- javaw.exe (PID: 7260)
- javaw.exe (PID: 7428)
- javaw.exe (PID: 7908)
- javaw.exe (PID: 7668)
- javaw.exe (PID: 8128)
- javaw.exe (PID: 7444)
- javaw.exe (PID: 7600)
- javaw.exe (PID: 8328)
- javaw.exe (PID: 8576)
- javaw.exe (PID: 8720)
- javaw.exe (PID: 9108)
- javaw.exe (PID: 8252)
- javaw.exe (PID: 9612)
- javaw.exe (PID: 8088)
- javaw.exe (PID: 10620)
- javaw.exe (PID: 9120)
- javaw.exe (PID: 11324)
- javaw.exe (PID: 12020)
- javaw.exe (PID: 11124)
- javaw.exe (PID: 7256)
- javaw.exe (PID: 10324)
- javaw.exe (PID: 12868)
- javaw.exe (PID: 14160)
- javaw.exe (PID: 12948)
Creates files in the program directory
- javaw.exe (PID: 5848)
Creates files or folders in the user directory
- javaw.exe (PID: 4460)
- javaw.exe (PID: 5848)
- TestLAB.tmp (PID: 3672)
Changes the display of characters in the console
- cmd.exe (PID: 8700)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 8820)
- cmd.exe (PID: 9172)
- cmd.exe (PID: 8560)
- cmd.exe (PID: 10048)
- cmd.exe (PID: 9684)
- cmd.exe (PID: 10124)
- cmd.exe (PID: 10768)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 12264)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 12412)
- cmd.exe (PID: 11700)
- cmd.exe (PID: 2312)
Manual execution by a user
- notepad.exe (PID: 9780)
- OpenWith.exe (PID: 10164)
- OpenWith.exe (PID: 9772)
- OpenWith.exe (PID: 10016)
- Client.exe (PID: 3944)
- OpenWith.exe (PID: 10396)
- java.exe (PID: 10476)
- OpenWith.exe (PID: 10784)
- OpenWith.exe (PID: 9208)
- OpenWith.exe (PID: 10756)
- OpenWith.exe (PID: 11180)
- OpenWith.exe (PID: 11188)
- wscript.exe (PID: 11760)
- msedge.exe (PID: 12000)
- notepad.exe (PID: 12200)
- OpenWith.exe (PID: 3952)
- OpenWith.exe (PID: 10652)
- OpenWith.exe (PID: 12040)
- intro.avi.exe (PID: 11488)
- wscript.exe (PID: 11592)
- OpenWith.exe (PID: 6812)
- OpenWith.exe (PID: 10372)
- OpenWith.exe (PID: 9592)
- OpenWith.exe (PID: 12468)
- OpenWith.exe (PID: 12680)
- systemware.exe (PID: 12796)
- OpenWith.exe (PID: 13088)
- OpenWith.exe (PID: 12604)
- OpenWith.exe (PID: 13480)
- OpenWith.exe (PID: 13688)
- OpenWith.exe (PID: 10868)
- OpenWith.exe (PID: 13872)
- OpenWith.exe (PID: 13960)
- OpenWith.exe (PID: 13136)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- Java32.exe (PID: 9428)
- systemware.exe (PID: 10440)
Application launched itself
- msedge.exe (PID: 12000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
389
Monitored processes
251
Malicious processes
10
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\TLauncher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | TLauncher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 424 | "C:\Users\admin\AppData\Local\Temp\Minecraft.exe" | C:\Users\admin\AppData\Local\Temp\Minecraft.exe | — | Minecraft.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.69 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\Minecraft.exe" | C:\Users\admin\AppData\Local\Temp\Minecraft.exe | — | Minecraft.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.69 Modules
| |||||||||||||||
| 1100 | "C:\Users\admin\AppData\Local\Temp\Minecraft.exe" | C:\Users\admin\AppData\Local\Temp\Minecraft.exe | — | Minecraft.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.69 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\TLauncher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | TLauncher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 4 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\TLauncher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | TLauncher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 4 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\AppData\Local\Temp\Files\Minecraft.exe" | C:\Users\admin\AppData\Local\Temp\Files\Minecraft.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.69 Modules
| |||||||||||||||
| 1508 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\TLauncher.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | TLauncher.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\AppData\Local\Temp\TLauncher.exe" | C:\Users\admin\AppData\Local\Temp\TLauncher.exe | — | Minecraft.exe | |||||||||||
User: admin Company: TLauncher Inc. Integrity Level: HIGH Description: TLauncher Exit code: 0 Version: 2.69 Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\AppData\Local\Temp\is-GHFB0.tmp\TestLAB.tmp" /SL5="$D0330,13626613,119296,C:\Users\admin\AppData\Local\Temp\Files\TestLAB.exe" | C:\Users\admin\AppData\Local\Temp\is-GHFB0.tmp\TestLAB.tmp | TestLAB.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
143 631
Read events
143 458
Write events
166
Delete events
7
Modification events
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2680) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
49
Suspicious files
38
Text files
82
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1700 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-KHKMJ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1700 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-KHKMJ.tmp\_isetup\_isdecmp.dll | executable | |
MD5:A813D18268AFFD4763DDE940246DC7E5 | SHA256:E19781AABE466DD8779CB9C8FA41BBB73375447066BB34E876CF388A6ED63C64 | |||
| 2680 | 4363463463464363463463463.bin.exe | C:\Users\admin\AppData\Local\Temp\Files\TestLAB.exe | executable | |
MD5:39C2F63970A0B2B1942E7072A6C648DC | SHA256:DC6AC7C9A0EE76114089B9D56EBEEA20A6B23FE4B39B8114191F149031105D36 | |||
| 3672 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-QV4G3.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1700 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-KHKMJ.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 1700 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-KHKMJ.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3672 | TestLAB.tmp | C:\Users\admin\AppData\Local\Temp\is-QV4G3.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4460 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 1488 | Minecraft.exe | C:\Users\admin\AppData\Local\Temp\Minecraft.exe | executable | |
MD5:845F34004E79C682C2882D25DB8E0B7D | SHA256:D807A8276EDEA3C4B471E2D54706515F5E475CA718E4A04EC3DCFC5C781B420C | |||
| 4460 | javaw.exe | C:\Users\admin\AppData\Roaming\.tlauncher\doubleRunningProtection.txt | text | |
MD5:6FB42E76EFE8EABCB75345E542EE1EA5 | SHA256:7D98683C0D9CB2F330B33B4550AD6ABA393B1618897FAB3153AE56BADEB00544 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
56
DNS requests
38
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8872 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8512 | XClient.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
9488 | intro.avi.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
8344 | Client-built.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
8872 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8436 | NJRAT%20DANGEROUS.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
5532 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2680 | 4363463463464363463463463.bin.exe | GET | 200 | 120.25.163.165:8080 | http://120.25.163.165:8080/mimikatz_trunk/Win32/mimikatz.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1936 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2680 | 4363463463464363463463463.bin.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2680 | 4363463463464363463463463.bin.exe | 35.209.91.196:443 | www.littlemoroccanthings.com | GOOGLE | US | unknown |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5532 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5532 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
www.littlemoroccanthings.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2680 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2680 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2680 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2680 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2680 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4460 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
4460 | javaw.exe | Misc activity | ET INFO JAVA - Java Archive Download By Vulnerable Client |
4460 | javaw.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
4460 | javaw.exe | Misc activity | ET INFO JAVA - Java Archive Download By Vulnerable Client |
Process | Message |
|---|---|
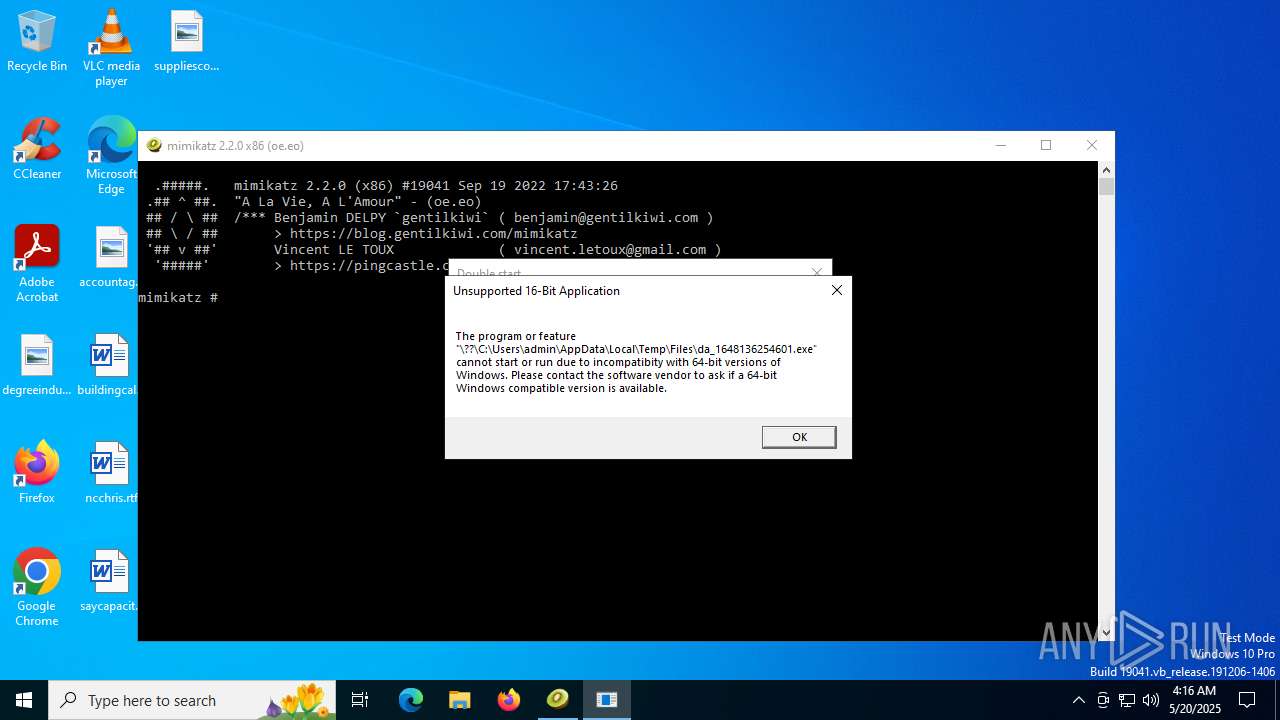
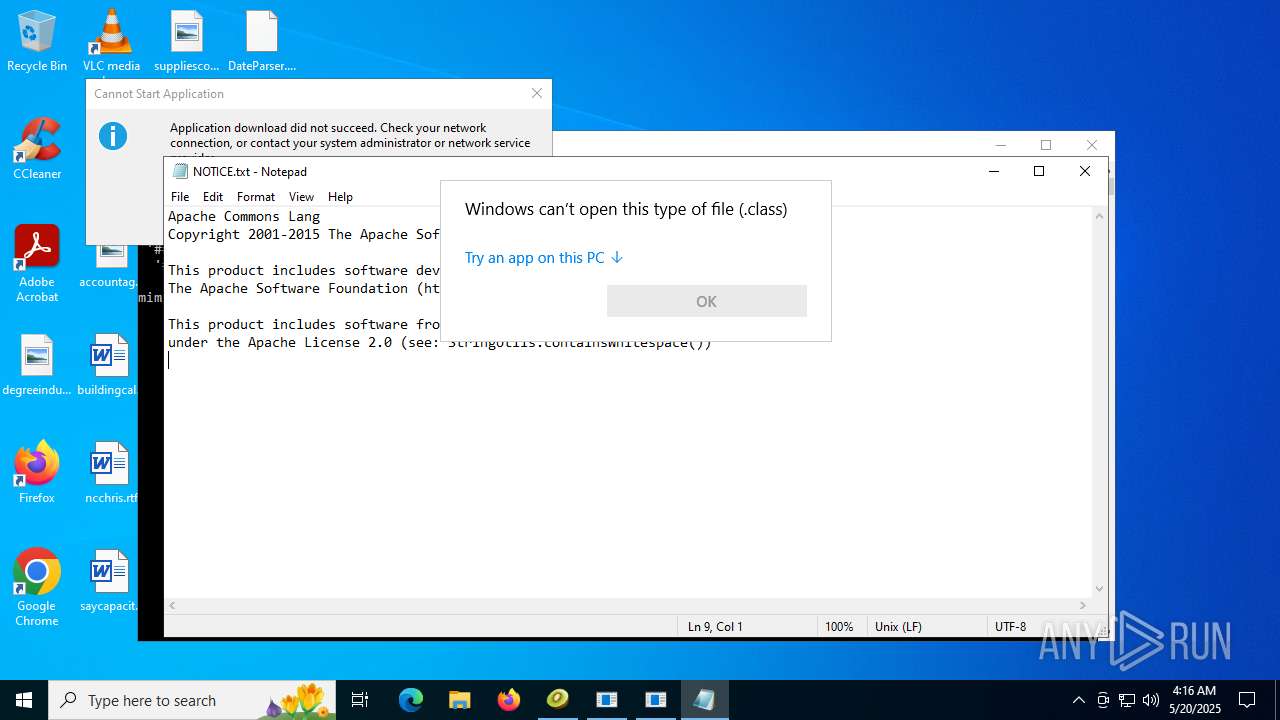
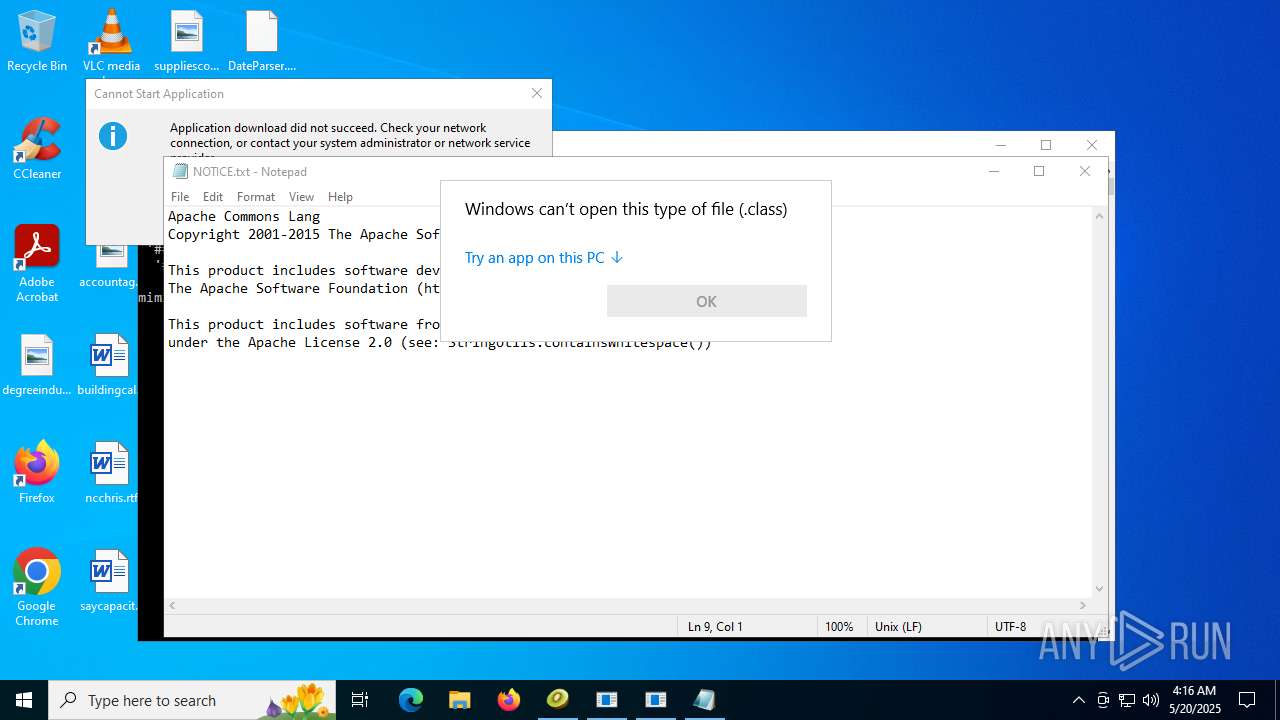
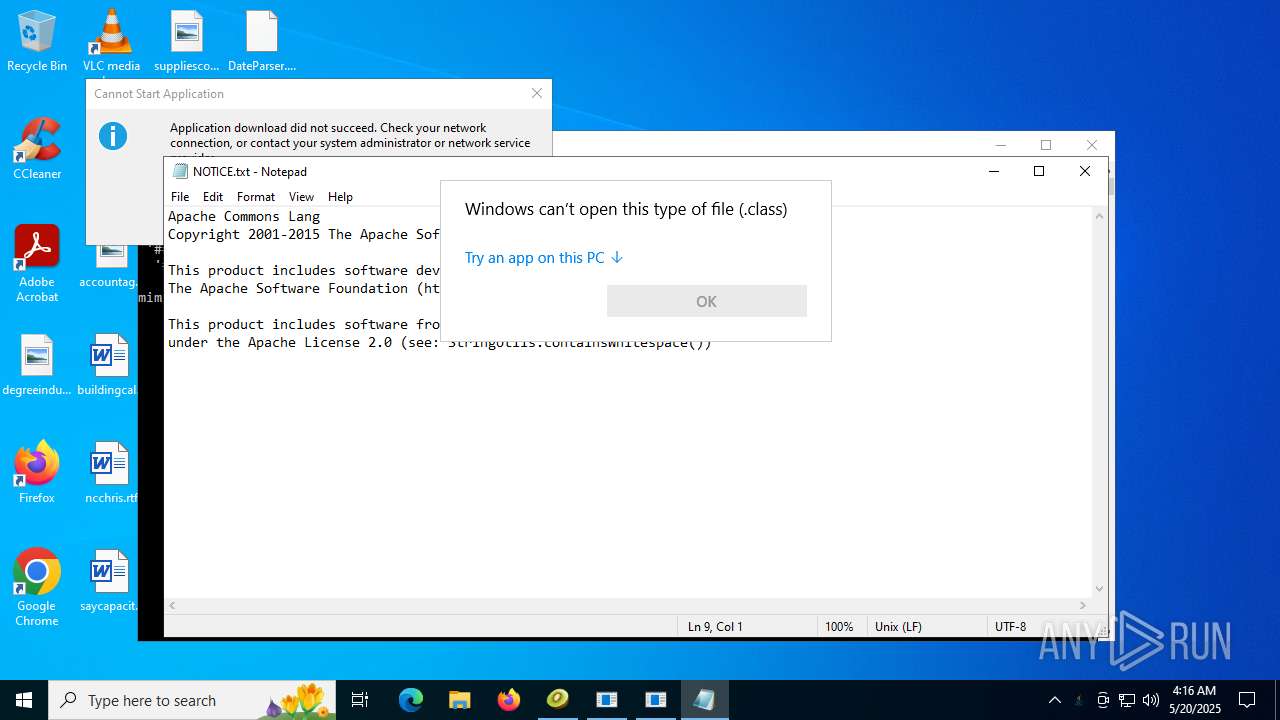
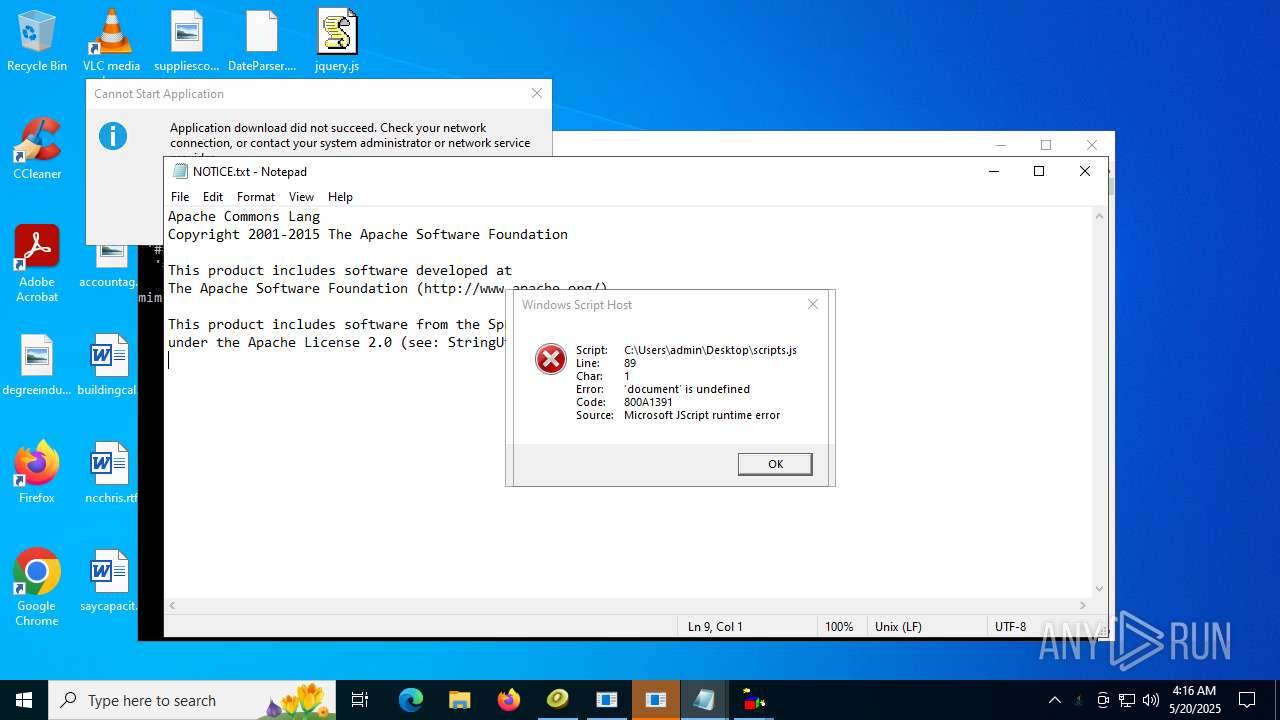
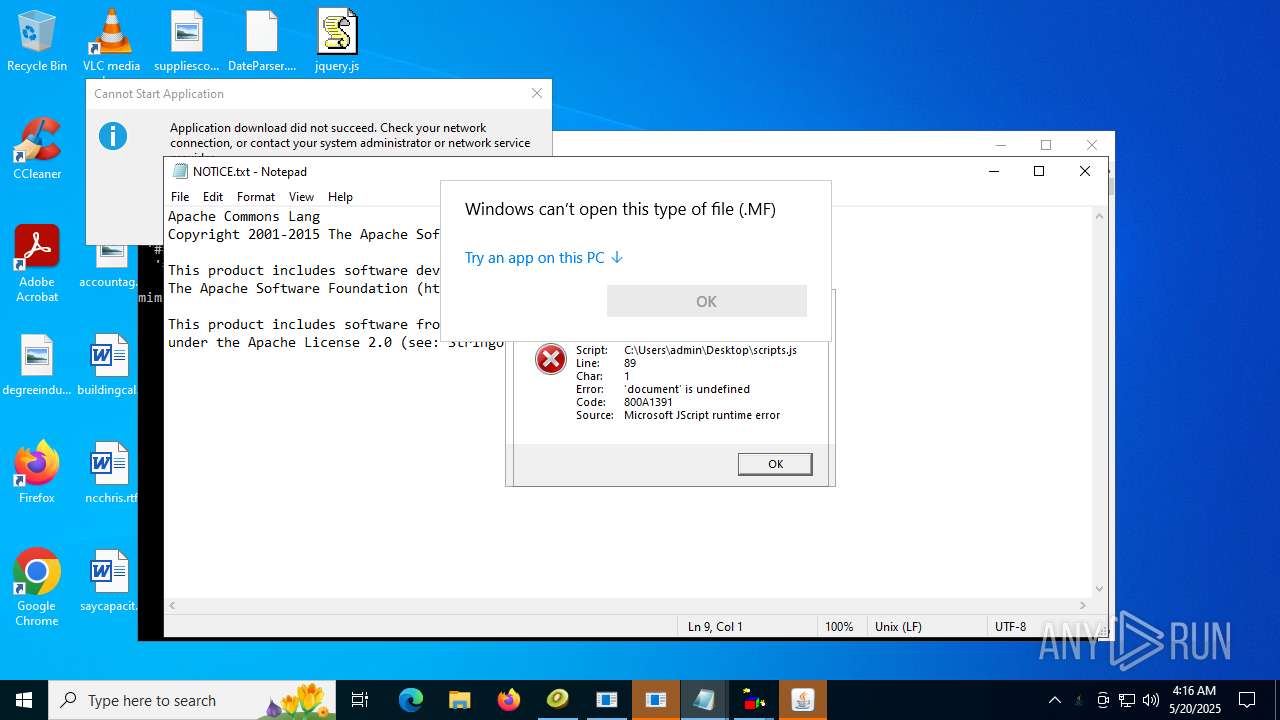
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|