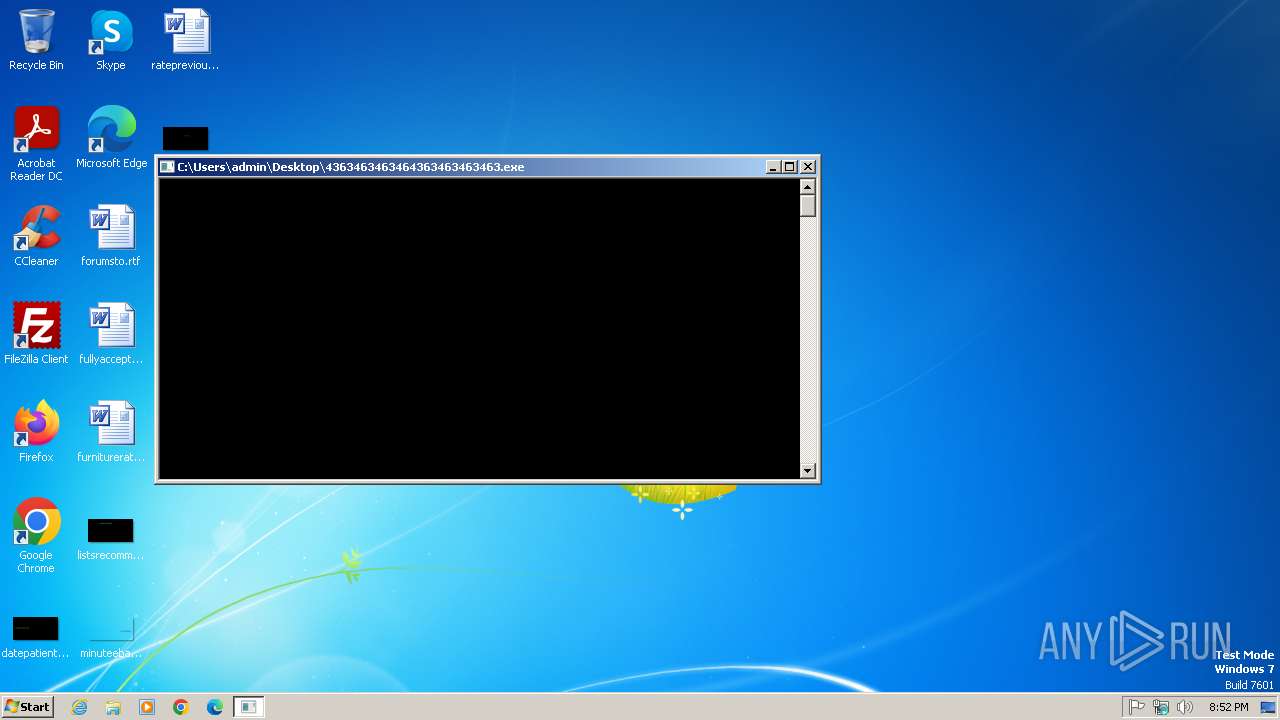
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/6bd6c754-1855-4fa5-b3f7-edb73b70e099 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 20, 2025, 19:52:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
QUASARRAT has been found (auto)
- svhost.exe (PID: 3096)
- 4363463463464363463463463.exe (PID: 2576)
Uses Task Scheduler to autorun other applications
- svhost.exe (PID: 3096)
- svhost.exe (PID: 2872)
COBALTSTRIKE has been found (auto)
- 4363463463464363463463463.exe (PID: 2576)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 2576)
- 4363463463464363463463463.exe (PID: 2576)
METASPLOIT has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2576)
METERPRETER has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2576)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 2576)
- 4363463463464363463463463.exe (PID: 2576)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 3688)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2576)
Changes Windows Defender settings
- XClient.exe (PID: 3072)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- VClientssss.exe (PID: 4060)
Bypass execution policy to execute commands
- powershell.exe (PID: 3292)
- powershell.exe (PID: 3644)
- powershell.exe (PID: 2880)
- powershell.exe (PID: 1588)
- powershell.exe (PID: 1884)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 1996)
- powershell.exe (PID: 2956)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2576)
- 4363463463464363463463463.exe (PID: 2576)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 3912)
Changes Controlled Folder Access settings
- powershell.exe (PID: 3912)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 3912)
Changes settings for real-time protection
- powershell.exe (PID: 3912)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 3912)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 3912)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 3912)
Create files in the Startup directory
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- XClient.exe (PID: 3072)
Actions looks like stealing of personal data
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Steals credentials from Web Browsers
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Changes the autorun value in the registry
- XClient.exe (PID: 3072)
- newtpp.exe (PID: 288)
PHORPIEX has been detected (SURICATA)
- syscrondvr.exe (PID: 2868)
Connects to the CnC server
- syscrondvr.exe (PID: 2868)
Executing a file with an untrusted certificate
- _na.exe (PID: 2088)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2576)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2576)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2576)
- client.exe (PID: 3684)
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2576)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2576)
- client.exe (PID: 3684)
- powershell.exe (PID: 3688)
- XClient.exe (PID: 3072)
- powershell.exe (PID: 3292)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- powershell.exe (PID: 3644)
- powershell.exe (PID: 2880)
- WMIC.exe (PID: 1196)
- VClientssss.exe (PID: 4060)
- powershell.exe (PID: 1588)
- powershell.exe (PID: 1884)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 1996)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2576)
- svhost.exe (PID: 2872)
- CPDB.exe (PID: 3204)
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
- systempreter.exe (PID: 2460)
- Microsoft_Hardware_Launch.exe (PID: 2968)
Reads the Windows owner or organization settings
- wnbsqv3008.tmp (PID: 3856)
Creates file in the systems drive root
- ntvdm.exe (PID: 1460)
Executable content was dropped or overwritten
- wnbsqv3008.exe (PID: 2564)
- 4363463463464363463463463.exe (PID: 2576)
- svhost.exe (PID: 3096)
- powershell.exe (PID: 3688)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- XClient.exe (PID: 3072)
- newtpp.exe (PID: 288)
- wnbsqv3008.tmp (PID: 3856)
- FreeYoutubeDownloader.exe (PID: 3804)
- VClientssss.exe (PID: 4060)
- rundll32.exe (PID: 1832)
- 444.exe (PID: 1060)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2576)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2576)
- svhost.exe (PID: 3096)
Starts itself from another location
- svhost.exe (PID: 3096)
- newtpp.exe (PID: 288)
- 444.exe (PID: 1060)
Reads the BIOS version
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2576)
- syscrondvr.exe (PID: 2868)
Windows Defender mutex has been found
- vtoroy.exe (PID: 3820)
- tretiy.exe (PID: 3304)
Base64-obfuscated command line is found
- client.exe (PID: 3684)
Starts POWERSHELL.EXE for commands execution
- client.exe (PID: 3684)
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
BASE64 encoded PowerShell command has been detected
- client.exe (PID: 3684)
Checks for Java to be installed
- eeq.exe (PID: 3116)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3644)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 2880)
- powershell.exe (PID: 1588)
- powershell.exe (PID: 1884)
- powershell.exe (PID: 2236)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 2576)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 3072)
- VClientssss.exe (PID: 4060)
Uses WMIC.EXE to obtain Windows Installer data
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 1196)
Script disables Windows Defender's real-time protection
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Script disables Windows Defender's IPS
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Uses ATTRIB.EXE to modify file attributes
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Checks for external IP
- svchost.exe (PID: 1080)
- VClientssss.exe (PID: 4060)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Modifies hosts file to alter network resolution
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Drops a system driver (possible attempt to evade defenses)
- wnbsqv3008.tmp (PID: 3856)
The process executes via Task Scheduler
- Terraria-Multiplayer-Fix-Online.exe (PID: 4028)
Contacting a server suspected of hosting an CnC
- syscrondvr.exe (PID: 2868)
Application launched itself
- msiexec.exe (PID: 3560)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Microsoft_Hardware_Launch.exe (PID: 2968)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 2908)
Executes as Windows Service
- VSSVC.exe (PID: 2392)
INFO
Reads the computer name
- 4363463463464363463463463.exe (PID: 2576)
- wnbsqv3008.tmp (PID: 3856)
- javaw.exe (PID: 2024)
- svhost.exe (PID: 3096)
- steamerx.exe (PID: 2384)
- poY.exe (PID: 1548)
- svhost.exe (PID: 2872)
- vtoroy.exe (PID: 3820)
- client.exe (PID: 3684)
- XClient.exe (PID: 3072)
- tretiy.exe (PID: 3304)
- sigmasigma.exe (PID: 2780)
- VClientssss.exe (PID: 4060)
- CPDB.exe (PID: 3204)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2576)
- wnbsqv3008.exe (PID: 2564)
- wnbsqv3008.tmp (PID: 3856)
- eeq.exe (PID: 3116)
- steamerx.exe (PID: 2384)
- svhost.exe (PID: 3096)
- poY.exe (PID: 1548)
- svhost.exe (PID: 2872)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- winbox.exe (PID: 3344)
- vtoroy.exe (PID: 3820)
- client.exe (PID: 3684)
- XClient.exe (PID: 3072)
- tretiy.exe (PID: 3304)
- donut.exe (PID: 3656)
- PAETools.exe (PID: 3276)
- sigmasigma.exe (PID: 2780)
- javaw.exe (PID: 2024)
- CPDB.exe (PID: 3204)
- newtpp.exe (PID: 288)
- FreeYoutubeDownloader.exe (PID: 3804)
- syscrondvr.exe (PID: 2868)
- VClientssss.exe (PID: 4060)
Disables trace logs
- 4363463463464363463463463.exe (PID: 2576)
- powershell.exe (PID: 3688)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- VClientssss.exe (PID: 4060)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2576)
- svhost.exe (PID: 3096)
- svhost.exe (PID: 2872)
- sigmasigma.exe (PID: 2780)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- VClientssss.exe (PID: 4060)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2576)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2576)
- javaw.exe (PID: 2024)
- steamerx.exe (PID: 2384)
- svhost.exe (PID: 3096)
- svhost.exe (PID: 2872)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- XClient.exe (PID: 3072)
- sigmasigma.exe (PID: 2780)
- CPDB.exe (PID: 3204)
- VClientssss.exe (PID: 4060)
Create files in a temporary directory
- wnbsqv3008.exe (PID: 2564)
- javaw.exe (PID: 2024)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
- FreeYoutubeDownloader.exe (PID: 3804)
Creates files in the program directory
- javaw.exe (PID: 2024)
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Creates files or folders in the user directory
- svhost.exe (PID: 3096)
- XClient.exe (PID: 3072)
Detects InnoSetup installer (YARA)
- wnbsqv3008.exe (PID: 2564)
- wnbsqv3008.tmp (PID: 3856)
Compiled with Borland Delphi (YARA)
- wnbsqv3008.tmp (PID: 3856)
Process checks whether UAC notifications are on
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 2760)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3644)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 2880)
- powershell.exe (PID: 1588)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 1884)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 1760)
- powershell.exe (PID: 1996)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 2576)
The sample compiled with chinese language support
- wnbsqv3008.tmp (PID: 3856)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
128
Monitored processes
62
Malicious processes
9
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | "C:\Users\admin\Desktop\Files\newtpp.exe" | C:\Users\admin\Desktop\Files\newtpp.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 752 | "C:\Windows\System32\schtasks.exe" /create /f /RL HIGHEST /sc minute /mo 1 /tn "Terraria-Multiplayer-Fix-Online" /tr "C:\Users\admin\AppData\Local\Terraria-Multiplayer-Fix-Online.exe" | C:\Windows\System32\schtasks.exe | — | XClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\Files\Important%20Document.exe" | C:\Users\admin\Desktop\Files\Important%20Document.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1060 | "C:\Users\admin\Desktop\Files\444.exe" | C:\Users\admin\Desktop\Files\444.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | "wmic.exe" csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | Trojan.Malpack.Themida%20(Anti%20VM).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1408 | netsh firewall add allowedprogram "C:\Users\admin\Desktop\Files\Microsoft_Hardware_Launch.exe" "Microsoft_Hardware_Launch.exe" ENABLE | C:\Windows\System32\netsh.exe | — | Microsoft_Hardware_Launch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1460 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\Desktop\Files\poY.exe" | C:\Users\admin\Desktop\Files\poY.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Client Version: 1.0.0.0 Modules
| |||||||||||||||
| 1588 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess 'Terraria-Multiplayer-Fix-Online.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | XClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
43 085
Read events
42 630
Write events
439
Delete events
16
Modification events
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2576) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
67
Suspicious files
40
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\wnbsqv3008.exe | executable | |
MD5:BC8CACD01AA943FBFBF9880D970C56AB | SHA256:6AB14C6E948BA0DF9AE1C257A15F84F206A23726337FF740CD47858237FE1EE7 | |||
| 2564 | wnbsqv3008.exe | C:\Users\admin\AppData\Local\Temp\is-CGB5M.tmp\wnbsqv3008.tmp | executable | |
MD5:1AFBD25DB5C9A90FE05309F7C4FBCF09 | SHA256:3BB0EE5569FE5453C6B3FA25AA517B925D4F8D1F7BA3475E58FA09C46290658C | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\TORRENTOLD-1.exe | executable | |
MD5:949102FCD293934060C6F3572ADC46FE | SHA256:796CE3E06BC10916427B847A1B6C2F1EAA9904F95DB66E35C28CEBEC34EFC9C5 | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\eeq.exe | executable | |
MD5:0D98176B534852FF9B44EA2B6B0DD223 | SHA256:E02CDA46CEB82557B52CCA99D31D2F62F743EB9333BA67E9CB482357767AC773 | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svhost.exe | executable | |
MD5:E3CFE28100238A1001C8CCA4AF39C574 | SHA256:78F9C811E589FF1F25D363080CE8D338FA68F6D2A220B1DD0360E799BBC17A12 | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\steamerx.exe | executable | |
MD5:695E9D580533372FB131ED51F8321C06 | SHA256:CFBCAE5F183D4F254603B0C2FCB66A9DA2D8DB663C92D9203E525F41704F4C89 | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\poY.exe | executable | |
MD5:AB8751627BFC89B03E3028A2964527C2 | SHA256:021A7A7FE712917F995989014AE8FFE46C6192DC66D81423E3C126C1B06F95C5 | |||
| 1460 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs223A.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2576 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\1.exe | executable | |
MD5:7D66D21A9B41E1004BAC03DB42431EC6 | SHA256:9085F21C1B1530BBA6A058781FF7EBF33928DBECFE39FFB7BD2FC34344AC6BDB | |||
| 2024 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:A36FA6BA8AA9A789A5444440CD90D9F5 | SHA256:785597B0623482E522E2F164696555351A299B5FF24A6F502A0E1581ADC46D62 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
46
DNS requests
27
Threats
64
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2576 | 4363463463464363463463463.exe | GET | 200 | 47.116.181.251:1111 | http://47.116.181.251:1111/02.08.2022.exe | unknown | — | — | unknown |
2576 | 4363463463464363463463463.exe | GET | 200 | 87.121.84.254:80 | http://fox-news-checker.cc/1337/TORRENTOLD-1.exe | unknown | — | — | unknown |
2576 | 4363463463464363463463463.exe | GET | 200 | 196.251.66.192:80 | http://gdx.o7lab.me/1.exe | unknown | — | — | malicious |
2576 | 4363463463464363463463463.exe | GET | 200 | 117.72.36.133:80 | http://e4l4.com/beacon_x64.exe | unknown | — | — | unknown |
2576 | 4363463463464363463463463.exe | GET | 200 | 176.122.27.90:9999 | http://176.122.27.90:9999/sup.exe | unknown | — | — | malicious |
2576 | 4363463463464363463463463.exe | GET | 200 | 1.220.192.90:80 | http://sanghyun.nfile.net/files/sanghyun-guest.exe | unknown | — | — | unknown |
2576 | 4363463463464363463463463.exe | GET | 200 | 39.106.158.243:80 | http://soft.110route.com/PAETools.exe | unknown | — | — | malicious |
2576 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/venisz/Roblox-Coding-Tutorial/raw/refs/heads/gang/VClientssss.exe | unknown | — | — | whitelisted |
2760 | Trojan.Malpack.Themida%20(Anti%20VM).exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
2576 | 4363463463464363463463463.exe | GET | 200 | 185.156.72.39:80 | http://185.156.72.39/newtpp.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2576 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2576 | 4363463463464363463463463.exe | 47.116.181.251:1111 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2576 | 4363463463464363463463463.exe | 117.24.12.150:443 | soft.wsyhn.com | Quanzhou | CN | unknown |
2576 | 4363463463464363463463463.exe | 87.121.84.254:80 | fox-news-checker.cc | SKAT TV Ltd. | BG | unknown |
2576 | 4363463463464363463463463.exe | 89.163.145.170:443 | envs.sh | myLoc managed IT AG | DE | unknown |
2576 | 4363463463464363463463463.exe | 47.79.66.205:443 | a12xxx1.oss-cn-hongkong.aliyuncs.com | WINDSTREAM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
soft.wsyhn.com |
| malicious |
fox-news-checker.cc |
| unknown |
envs.sh |
| unknown |
a12xxx1.oss-cn-hongkong.aliyuncs.com |
| unknown |
raw.githubusercontent.com |
| whitelisted |
gdx.o7lab.me |
| malicious |
e4l4.com |
| unknown |
github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2576 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2576 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2576 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
2576 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1080 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
2576 | 4363463463464363463463463.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2576 | 4363463463464363463463463.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
2576 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 42 |
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The underlying connection was closed: An unexpected error occurred on a send.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|