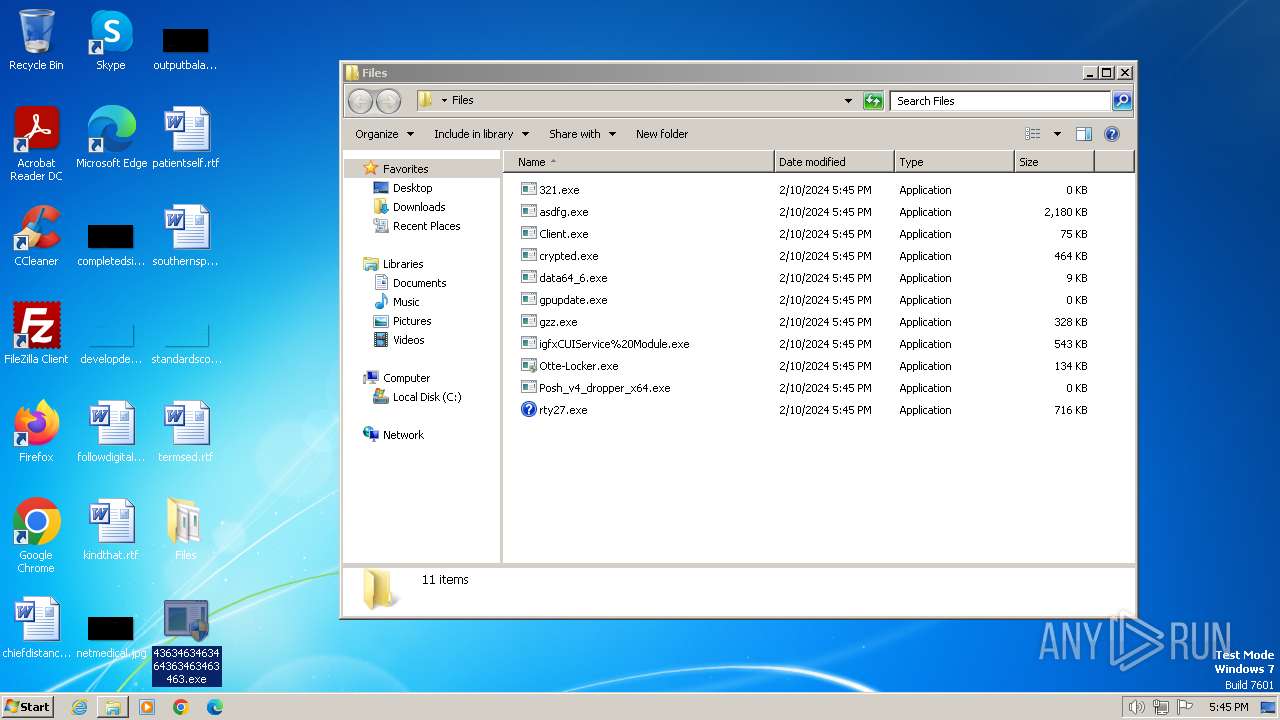
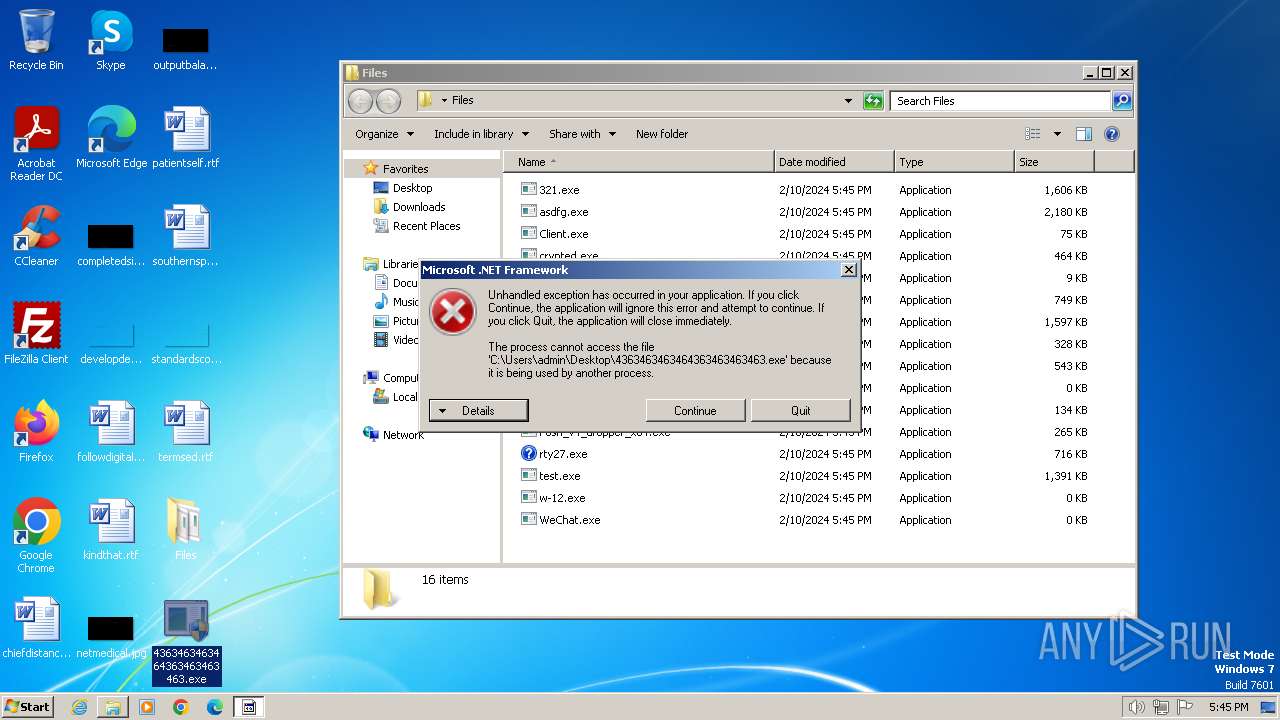
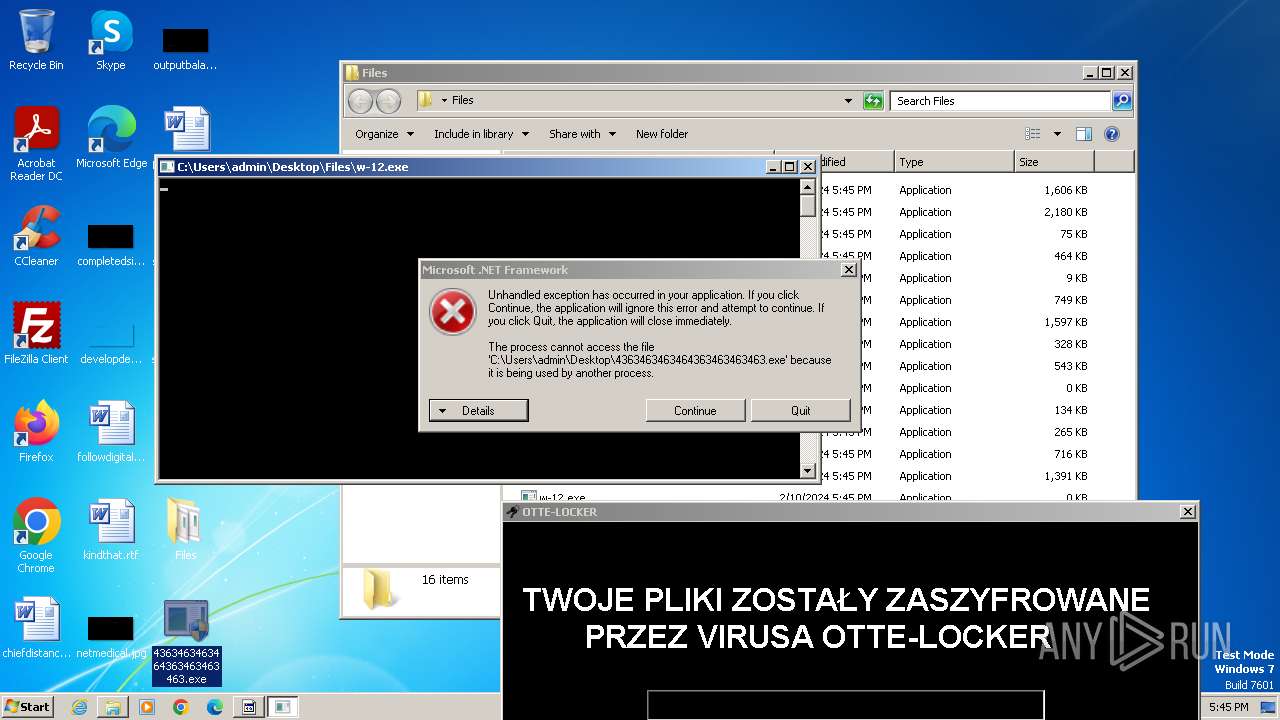
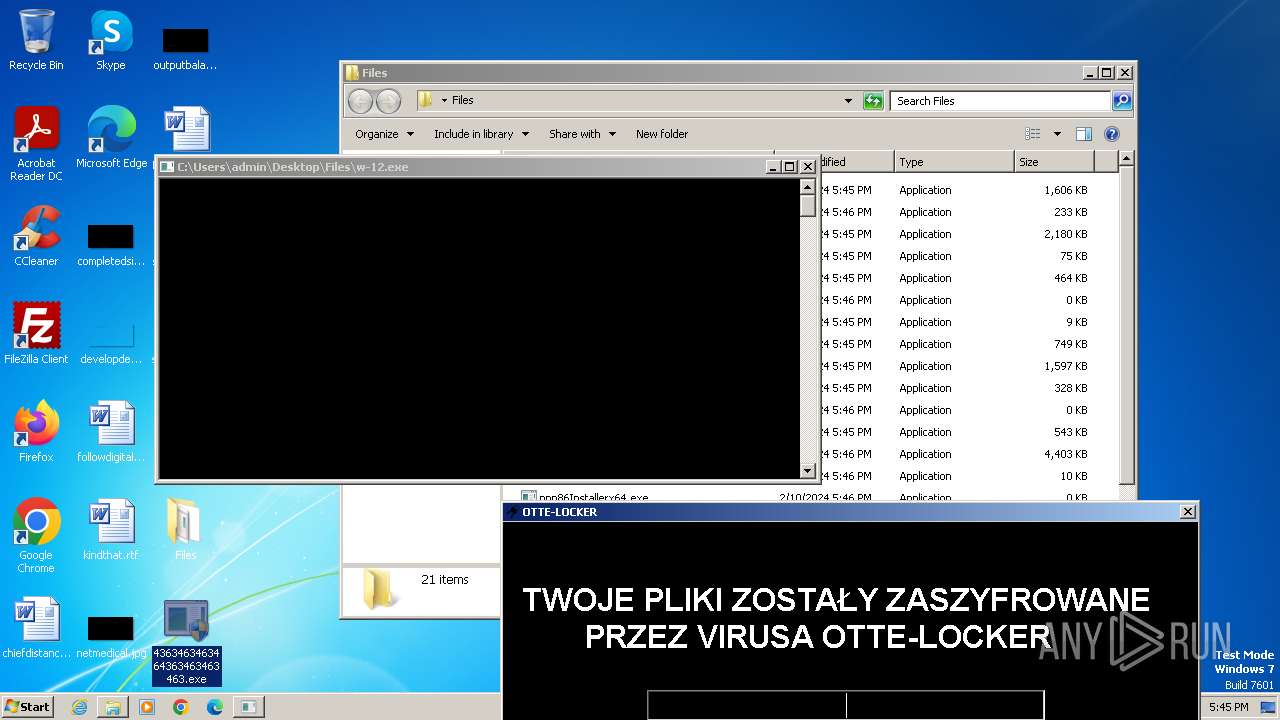
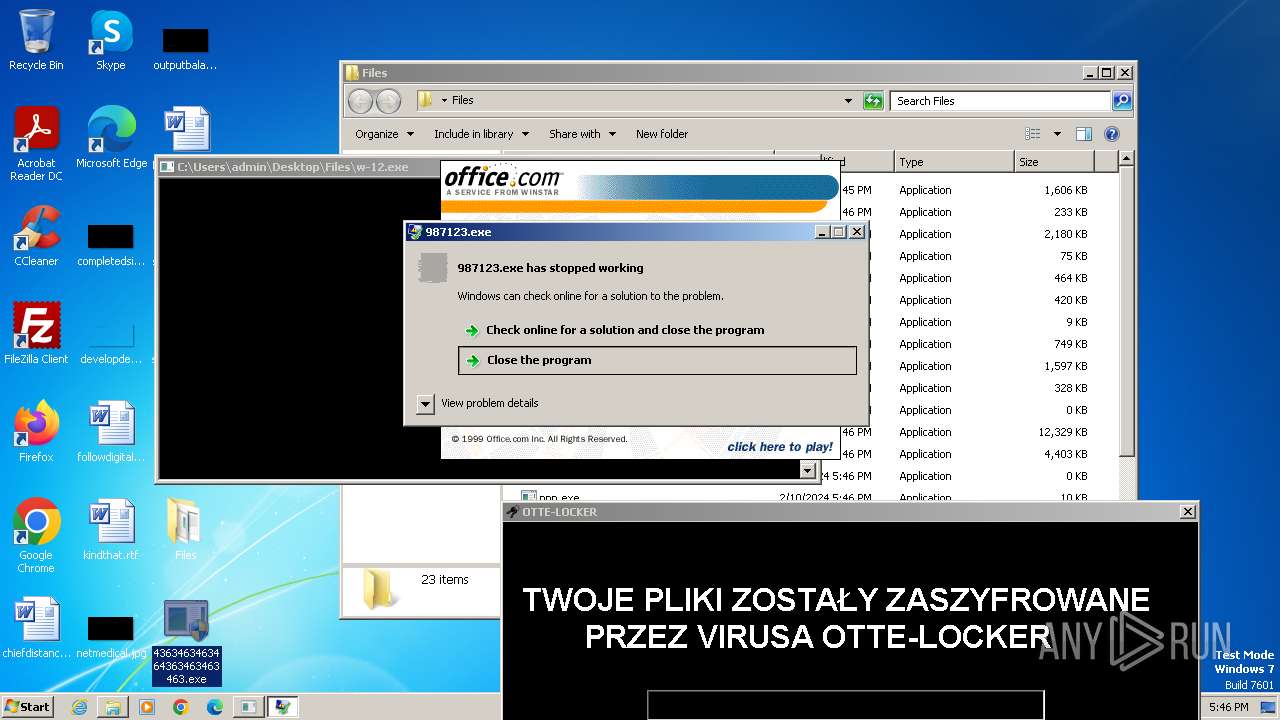
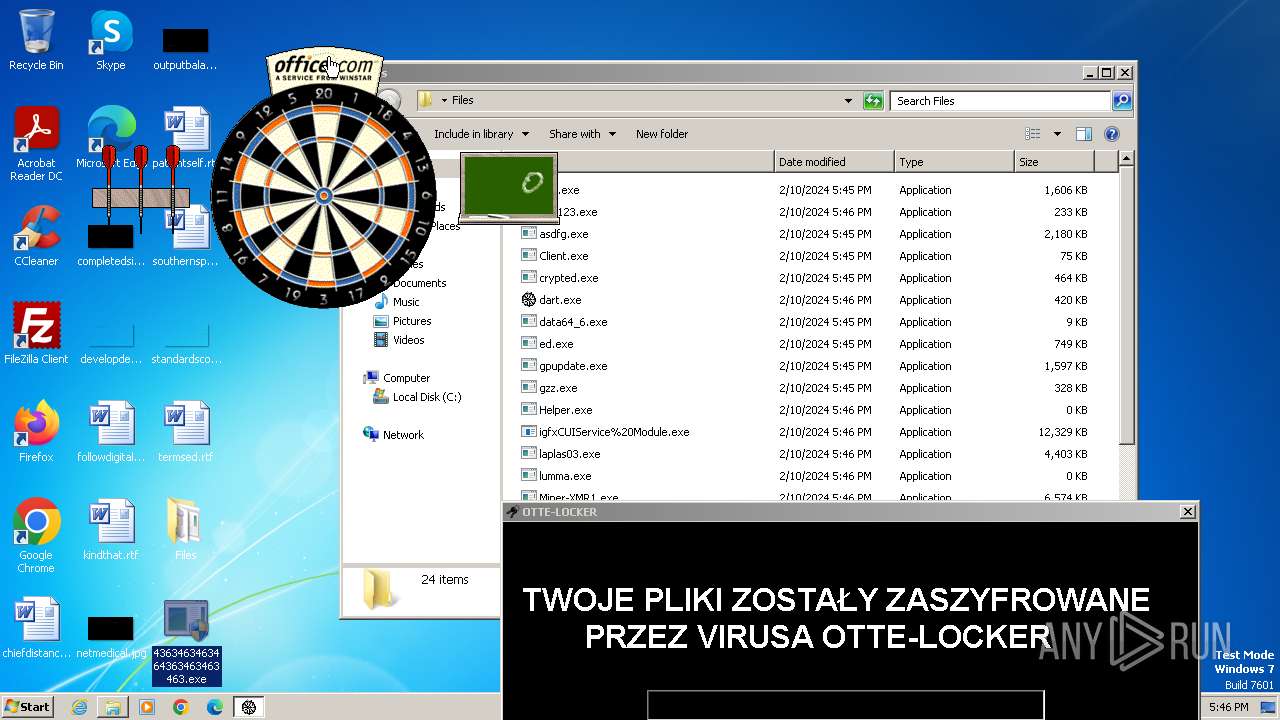
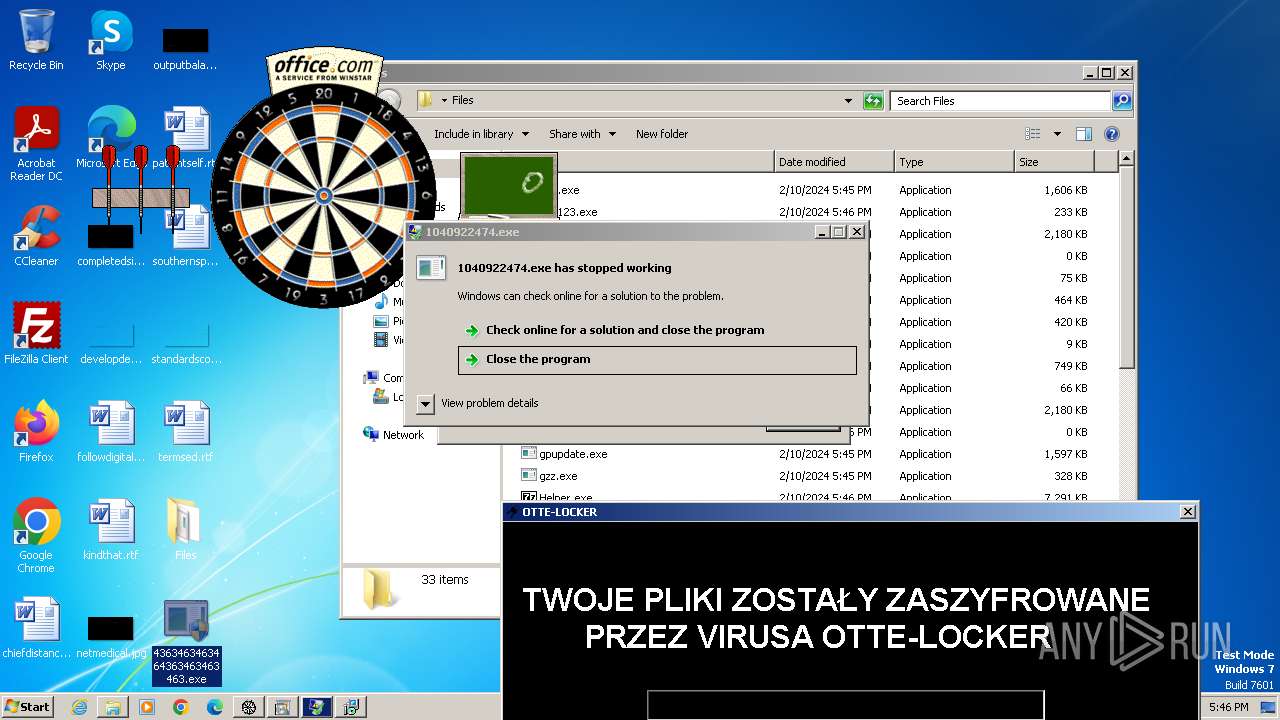
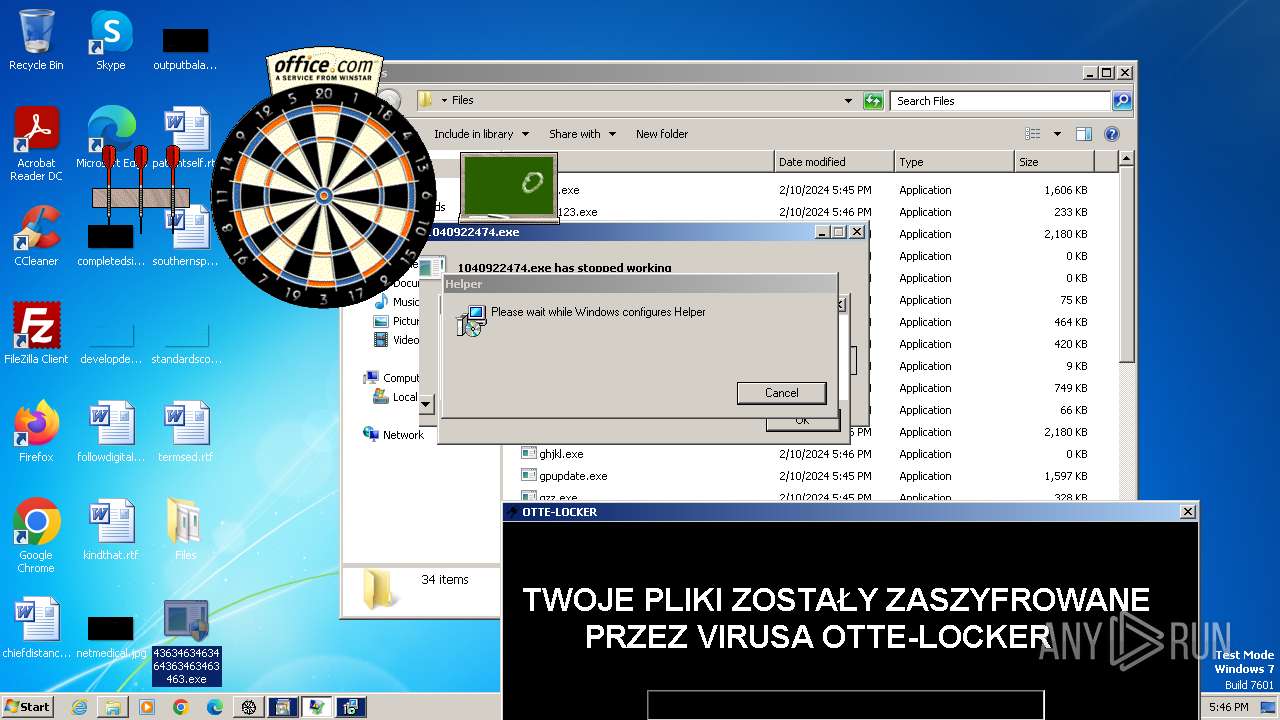
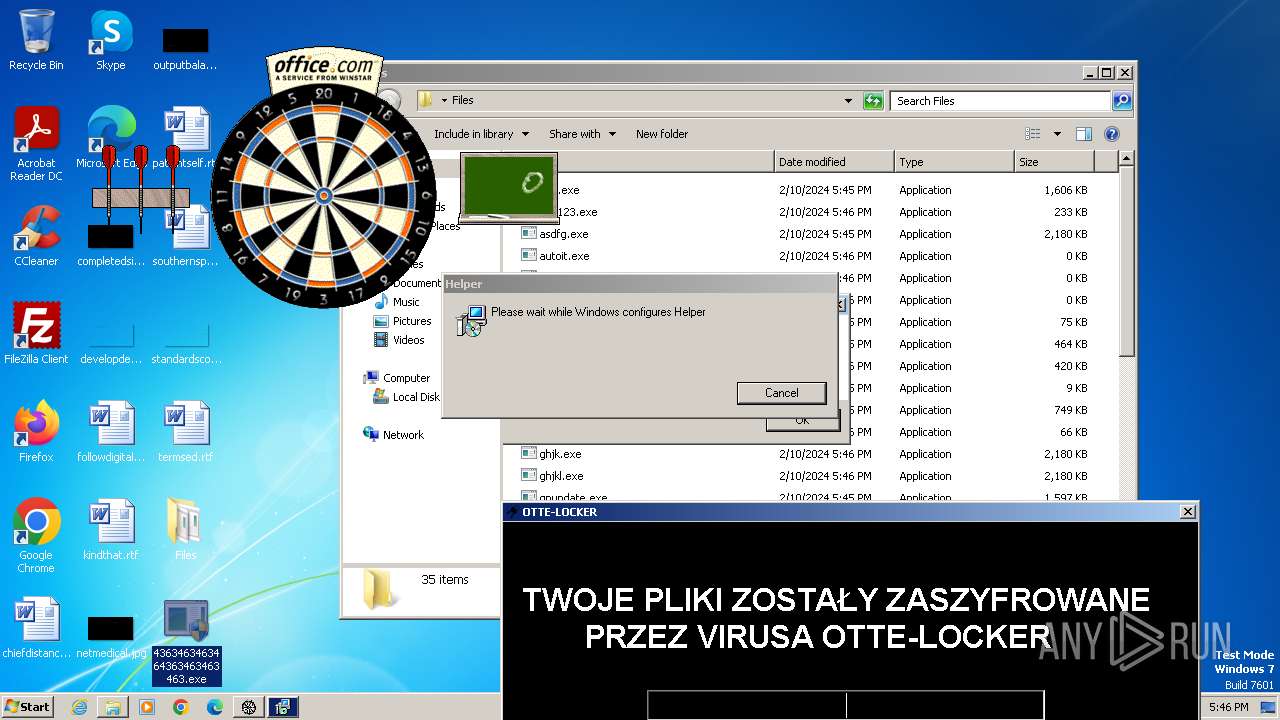
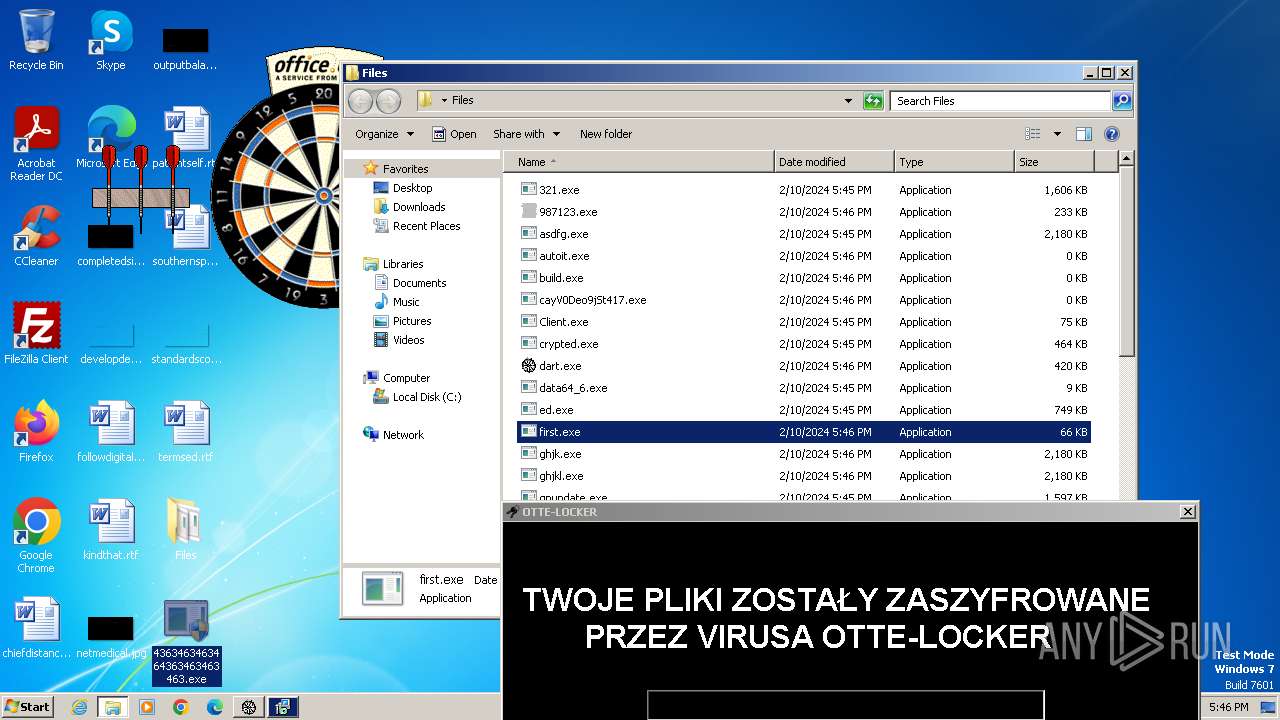
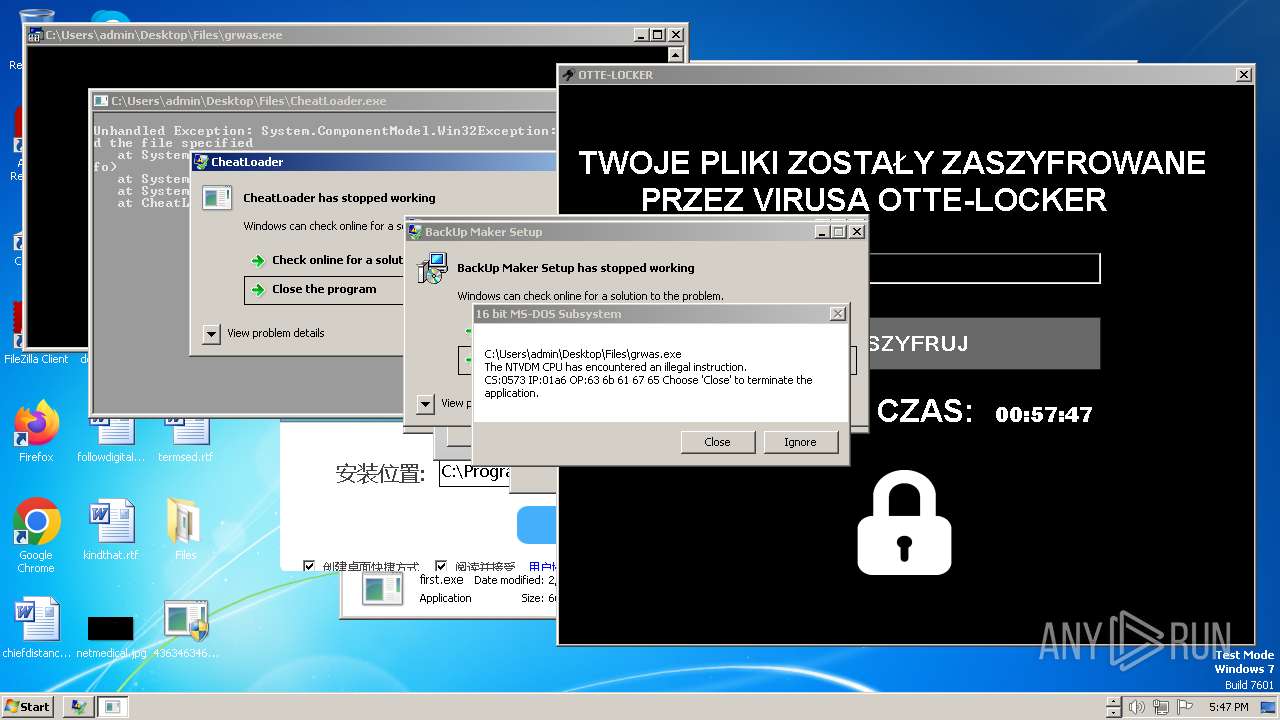
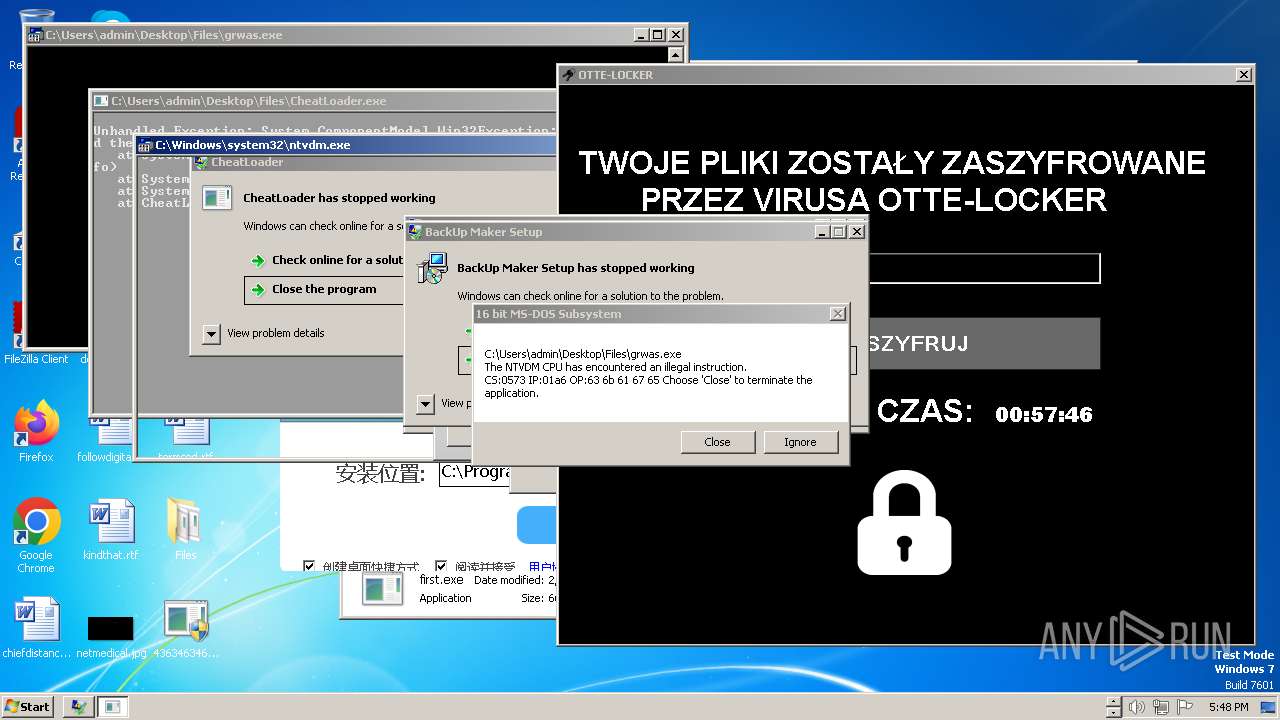
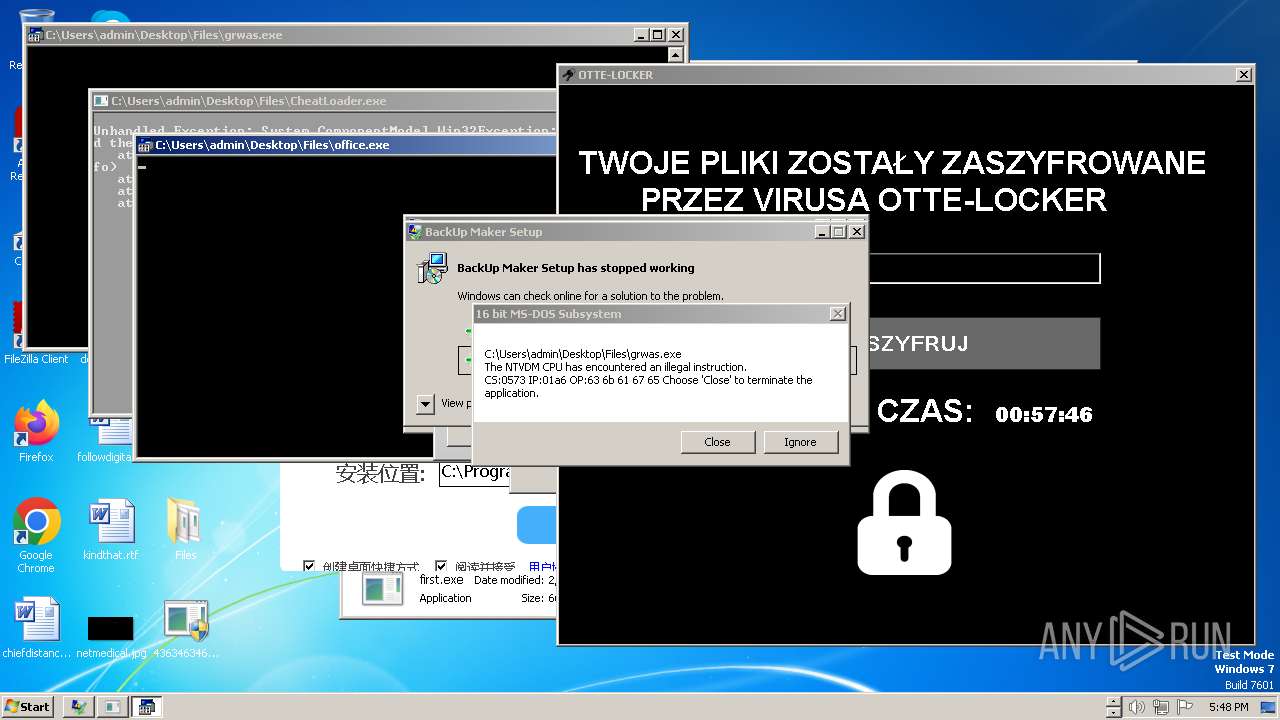
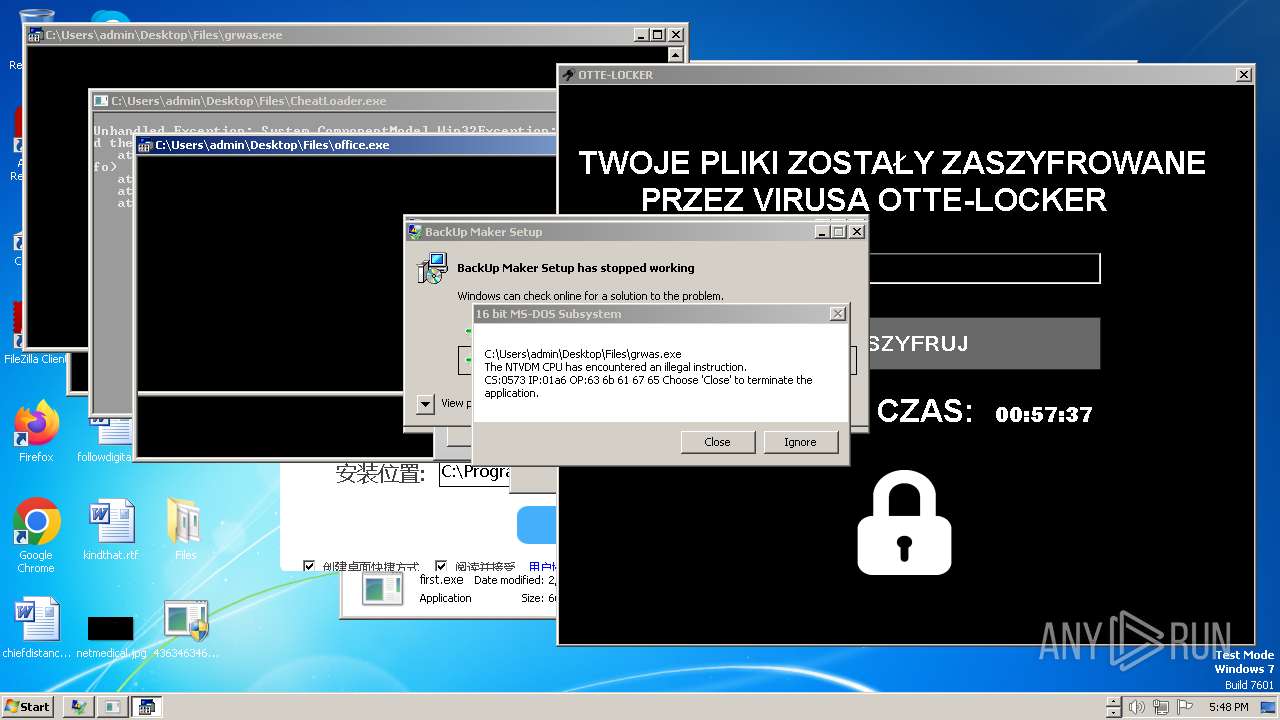
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/6720b85b-9c53-4a12-b1dc-73052a78477d |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | February 10, 2024, 17:45:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
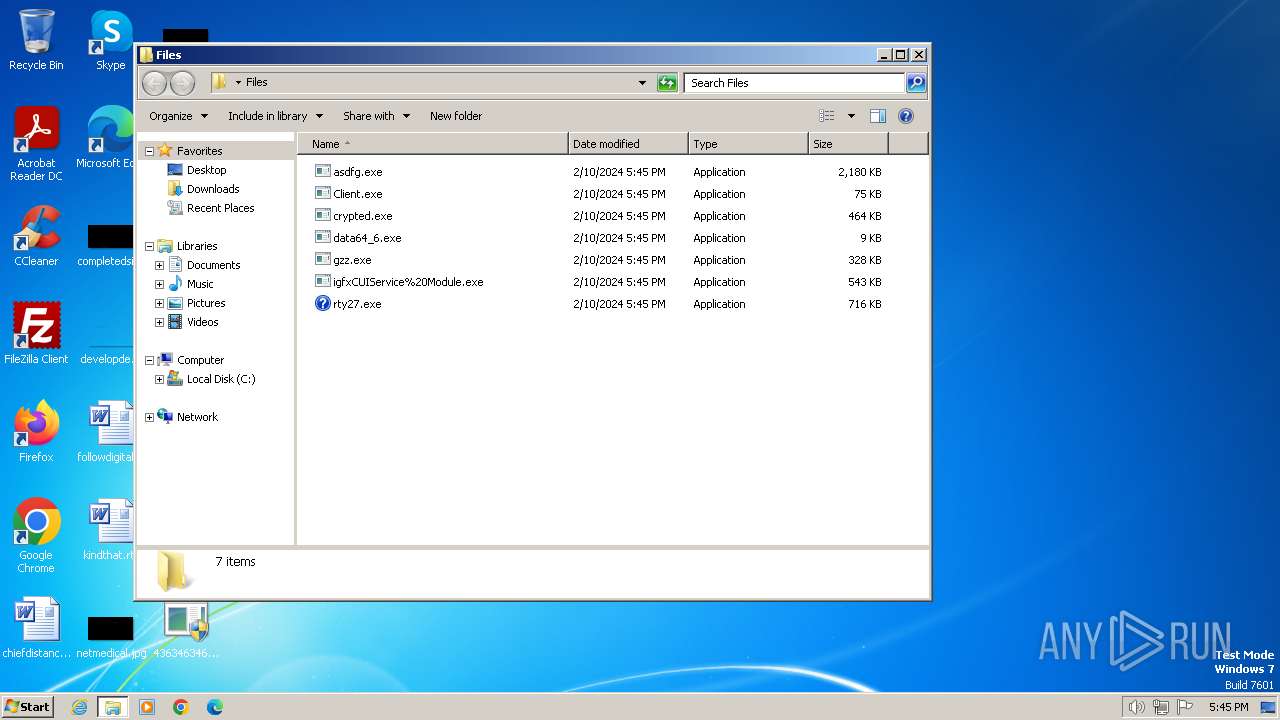
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3216)
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- BBLb.exe (PID: 2440)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- 2591814628.exe (PID: 3732)
- npp.exe (PID: 3920)
- npp86Installerx64.exe (PID: 1972)
- RegAsm.exe (PID: 3684)
- STAR.exe (PID: 2444)
- univ.exe (PID: 3440)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- 3322713636.exe (PID: 2488)
- Setup2010u32.exe (PID: 2864)
- may.exe (PID: 2068)
- tpeinf.exe (PID: 1404)
- mpveasyplayer.exe (PID: 2712)
- may.tmp (PID: 3980)
- PluginFlash.exe (PID: 4184)
- v2.exe (PID: 4108)
- v4install.exe (PID: 4944)
- GorgeousMovement.exe (PID: 5188)
- cp.exe (PID: 1408)
- cmd.exe (PID: 5396)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- agentServerComponent.exe (PID: 5508)
- cluton.exe (PID: 6116)
- Temp2.exe (PID: 4868)
- hv.exe (PID: 5648)
- RegAsm.exe (PID: 3736)
- build3.exe (PID: 2260)
- conhost.exe (PID: 4476)
- pei.exe (PID: 4104)
- lve5.exe (PID: 6244)
- _VTI_CNF.exe (PID: 6460)
- cluton.exe (PID: 4188)
- server.exe (PID: 7020)
- look2.exe (PID: 7492)
- Horpxuoxm.exe (PID: 1852)
- HD_._cache_server.exe (PID: 7552)
- ._cache_server.exe (PID: 7444)
- Winlock.exe (PID: 4312)
- Synaptics.exe (PID: 7616)
- april.exe (PID: 3356)
- Horpxuoxm.exe (PID: 7692)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 6128)
- april.tmp (PID: 6852)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 7404)
- amert.exe (PID: 6396)
- InstallSetup9.exe (PID: 7344)
- yhdl.exe (PID: 3492)
- jet.exe (PID: 3140)
- smell-the-roses.exe (PID: 5996)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2432)
- Temp2.exe (PID: 4868)
- asg.exe (PID: 5200)
Bypass execution policy to execute commands
- powershell.exe (PID: 840)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 920)
- powershell.exe (PID: 2448)
- powershell.exe (PID: 5900)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 7492)
- powershell.exe (PID: 5420)
- powershell.exe (PID: 5148)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
Run PowerShell with an invisible window
- powershell.exe (PID: 840)
- powershell.exe (PID: 920)
- powershell.exe (PID: 7472)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 2000)
Changes the login/logoff helper path in the registry
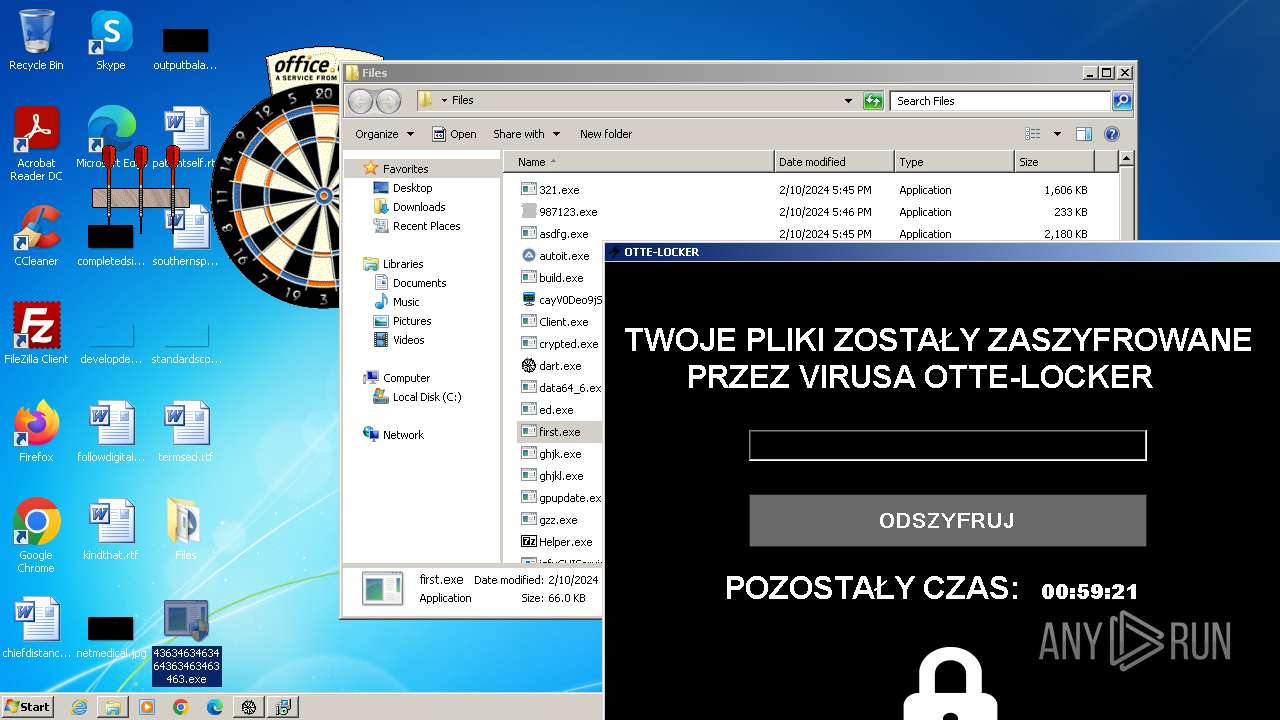
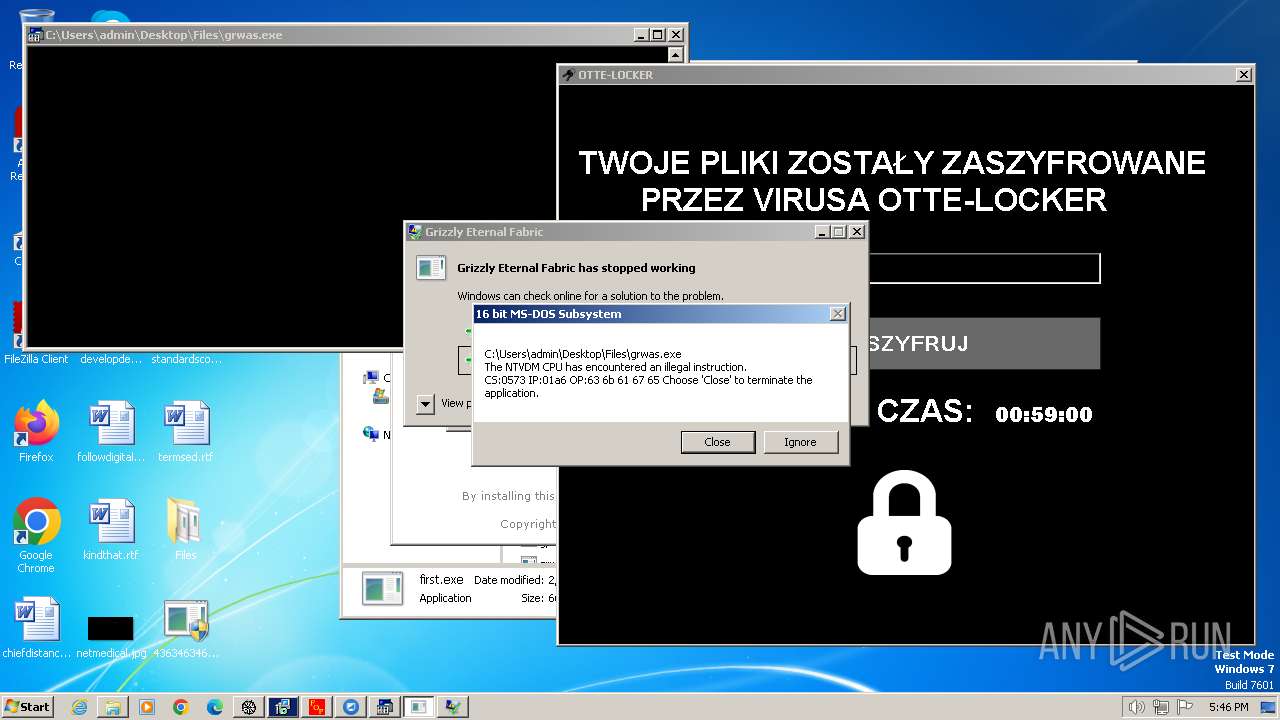
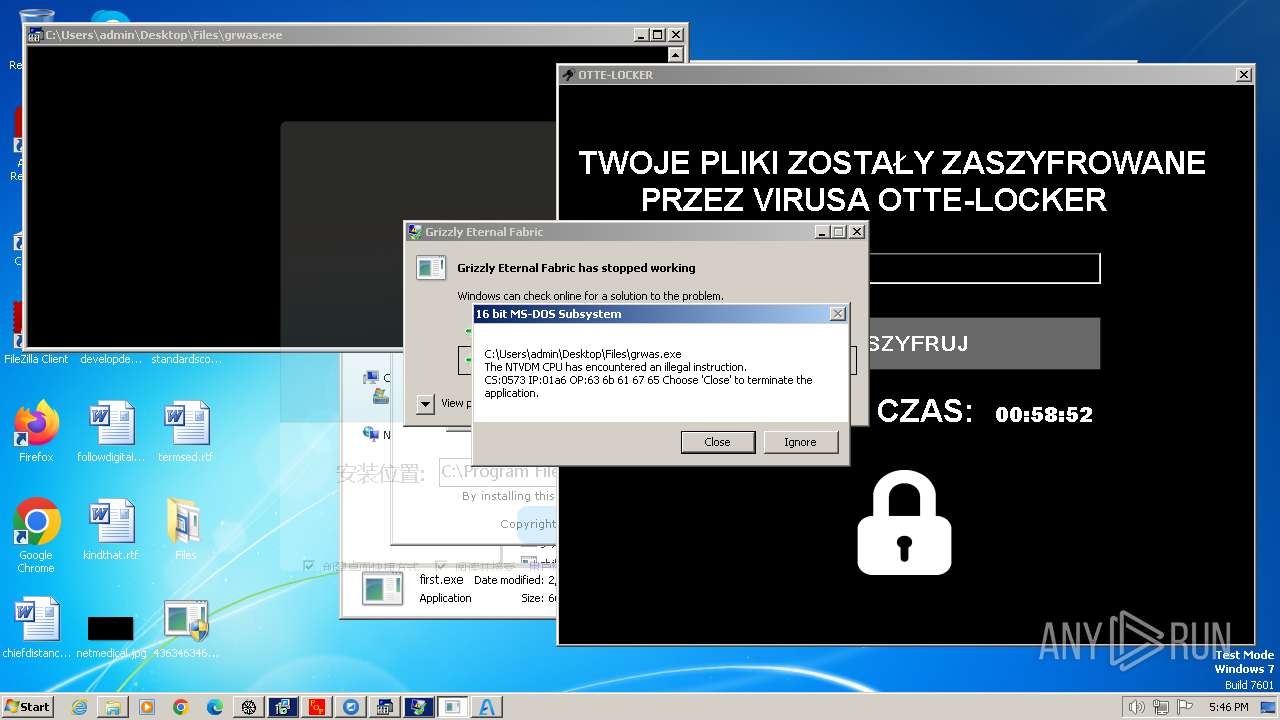
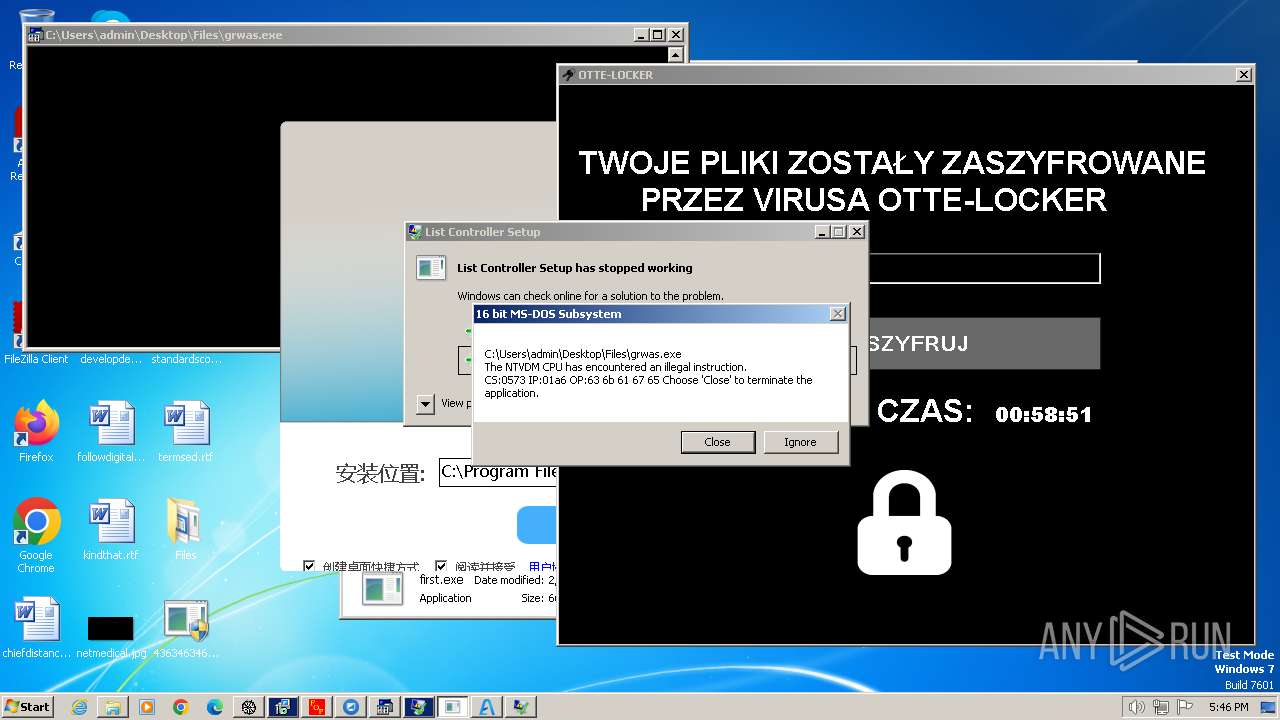
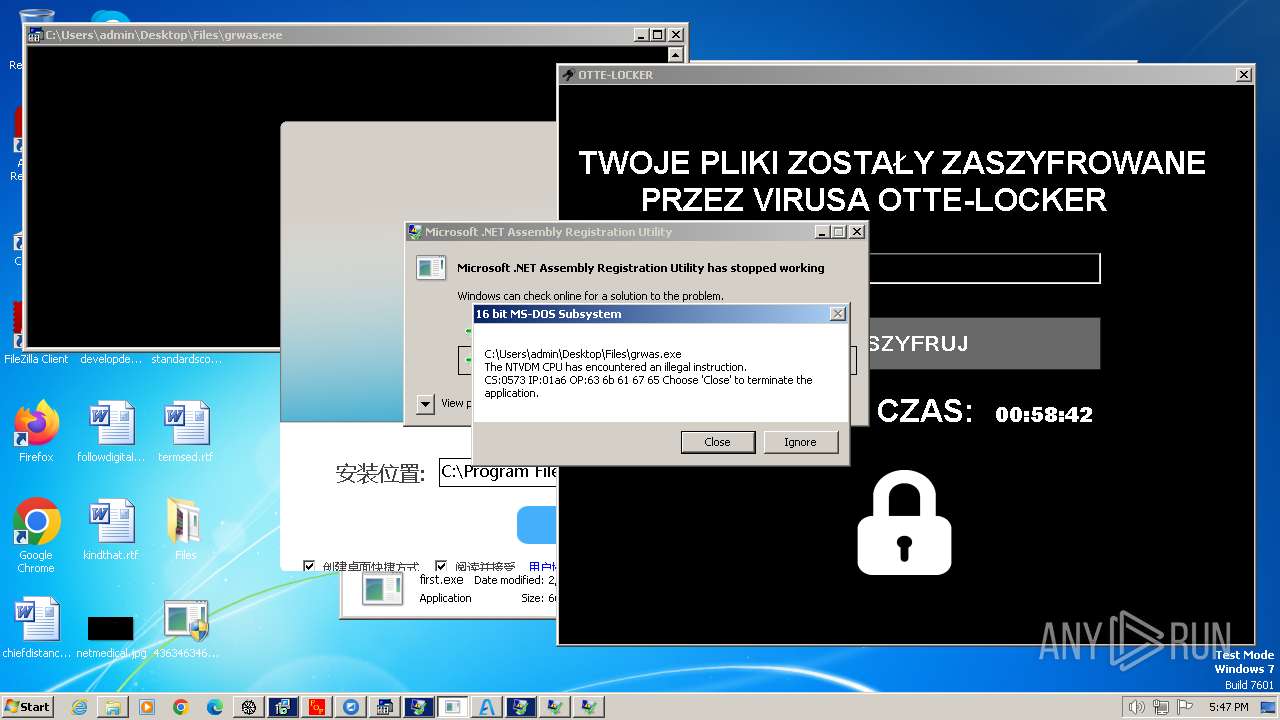
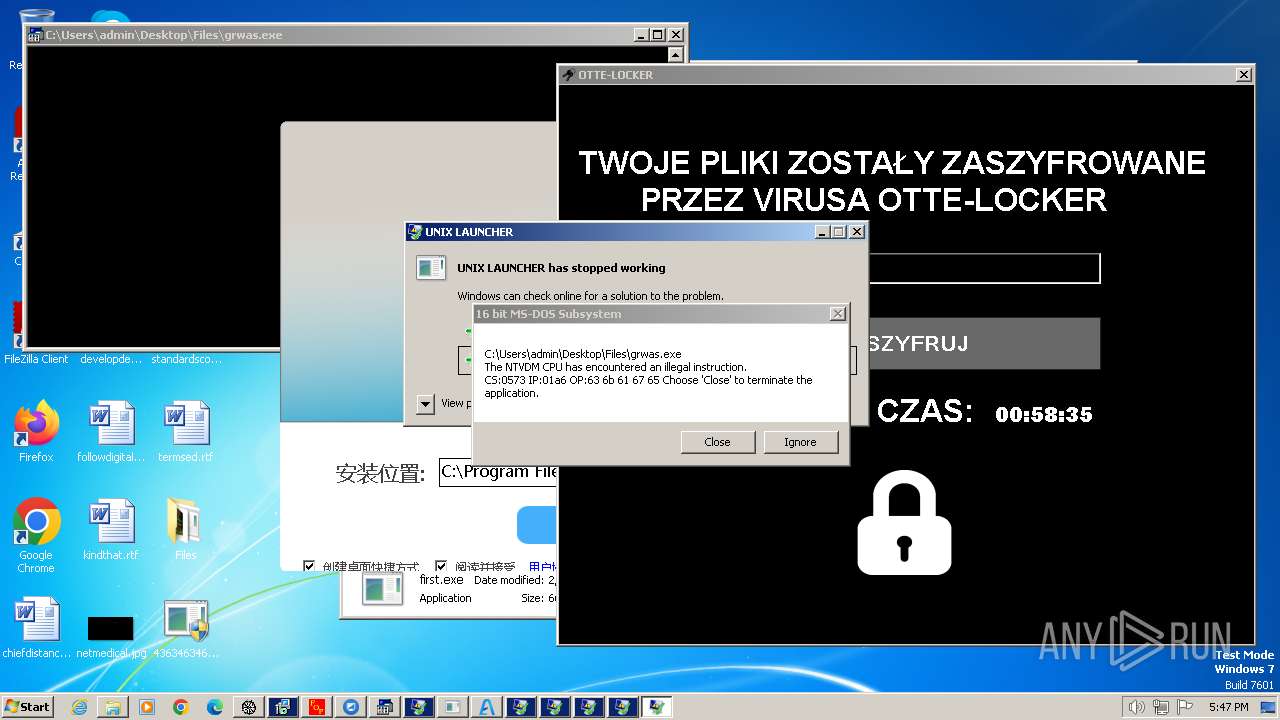
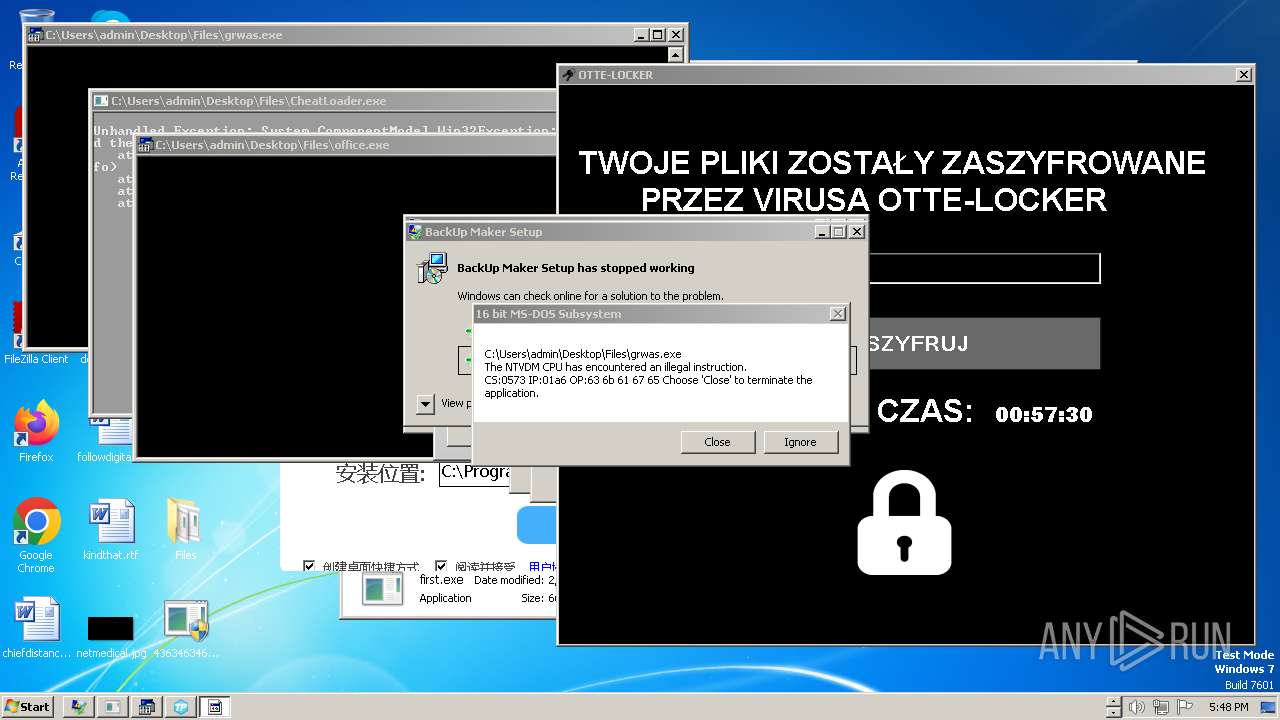
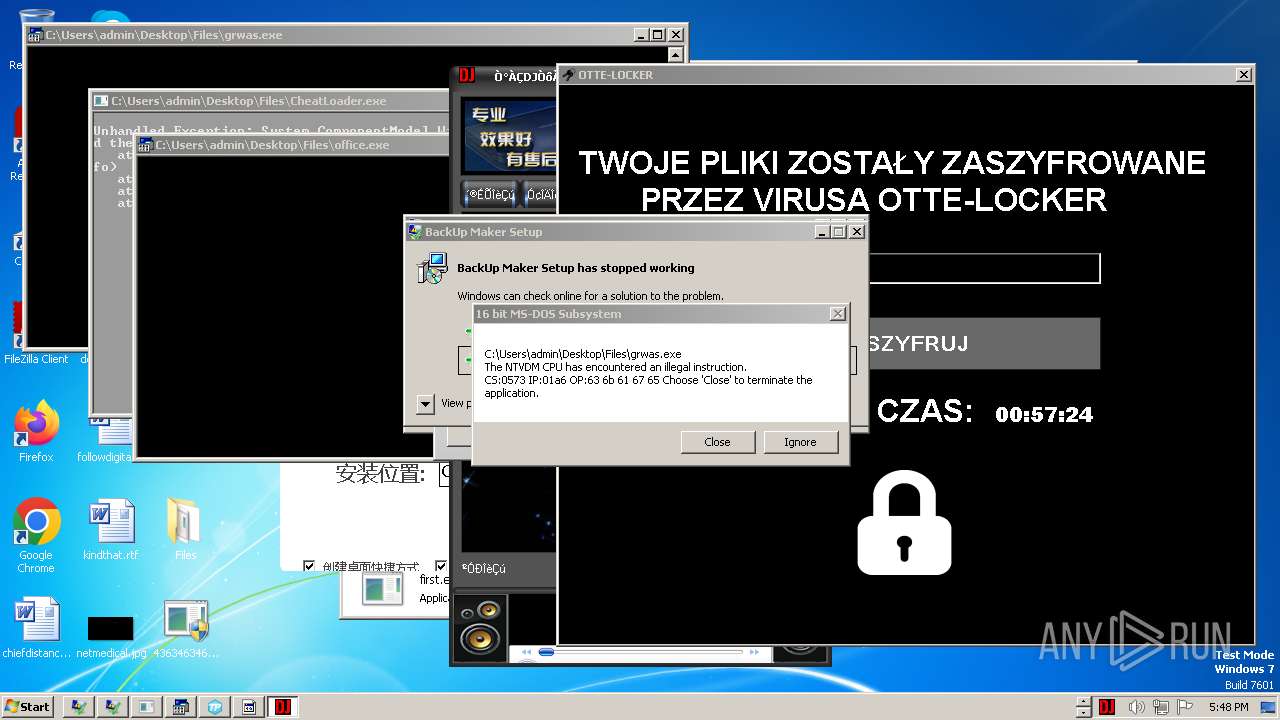
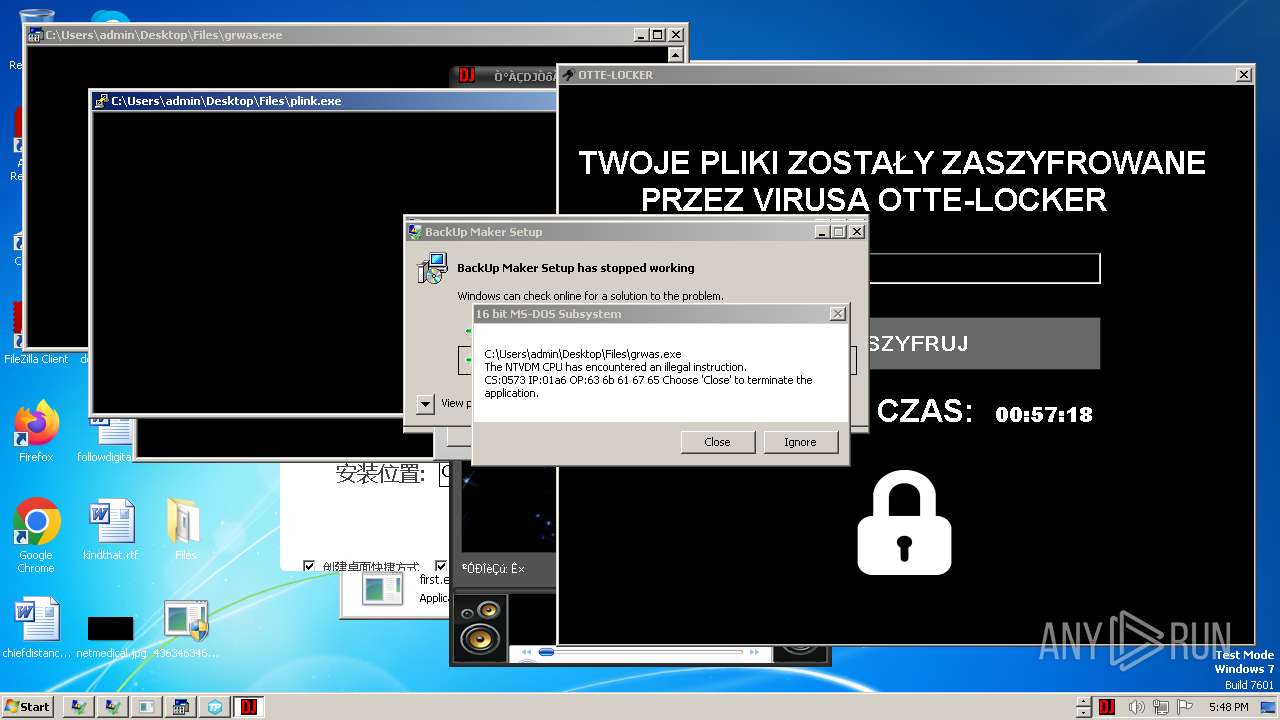
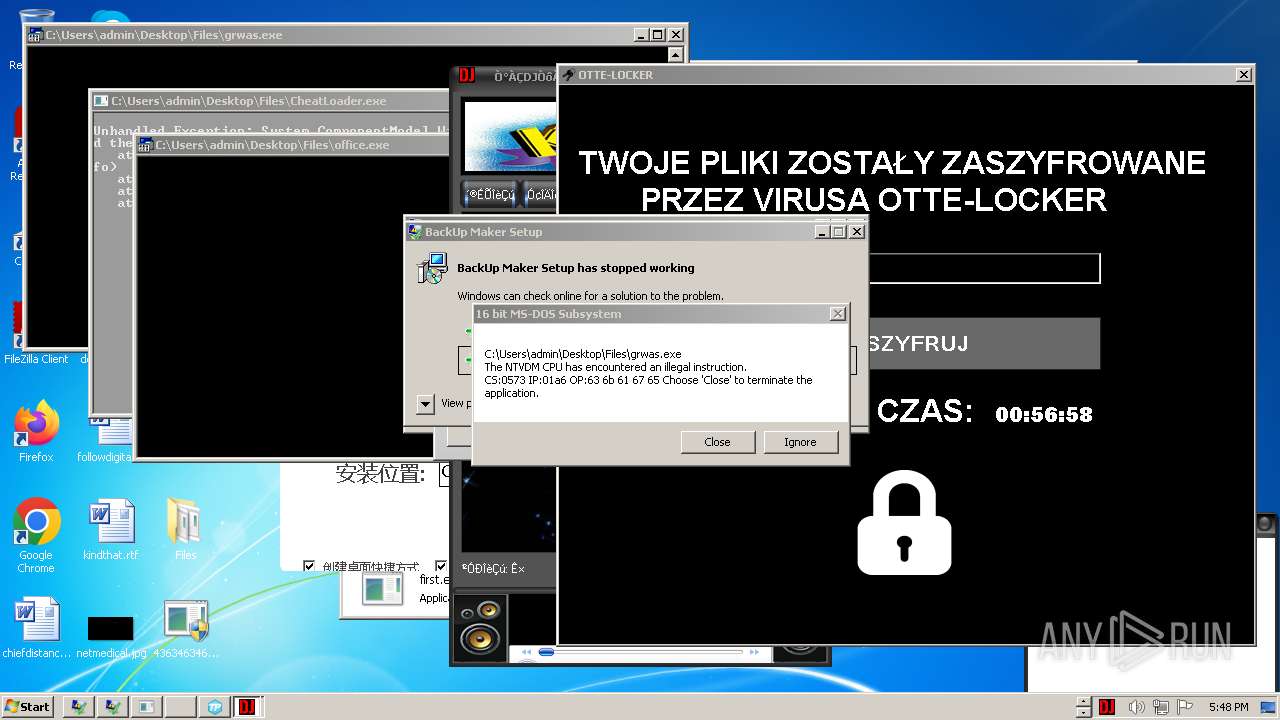
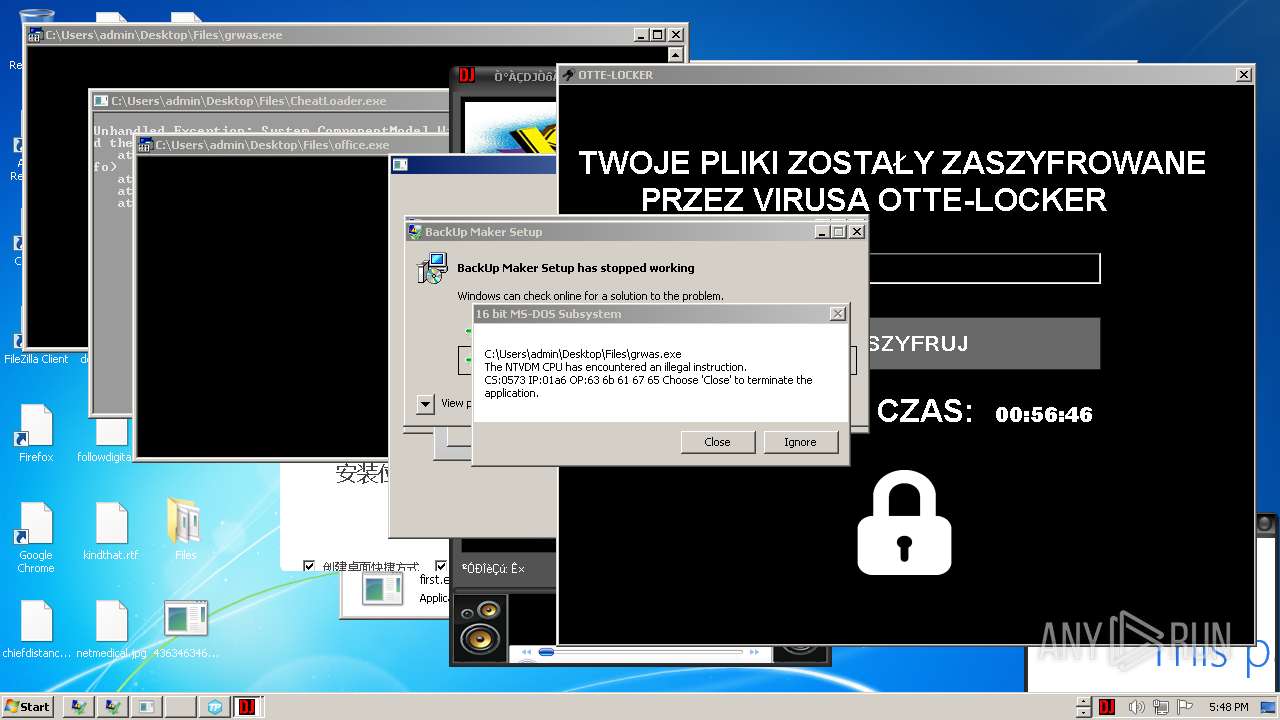
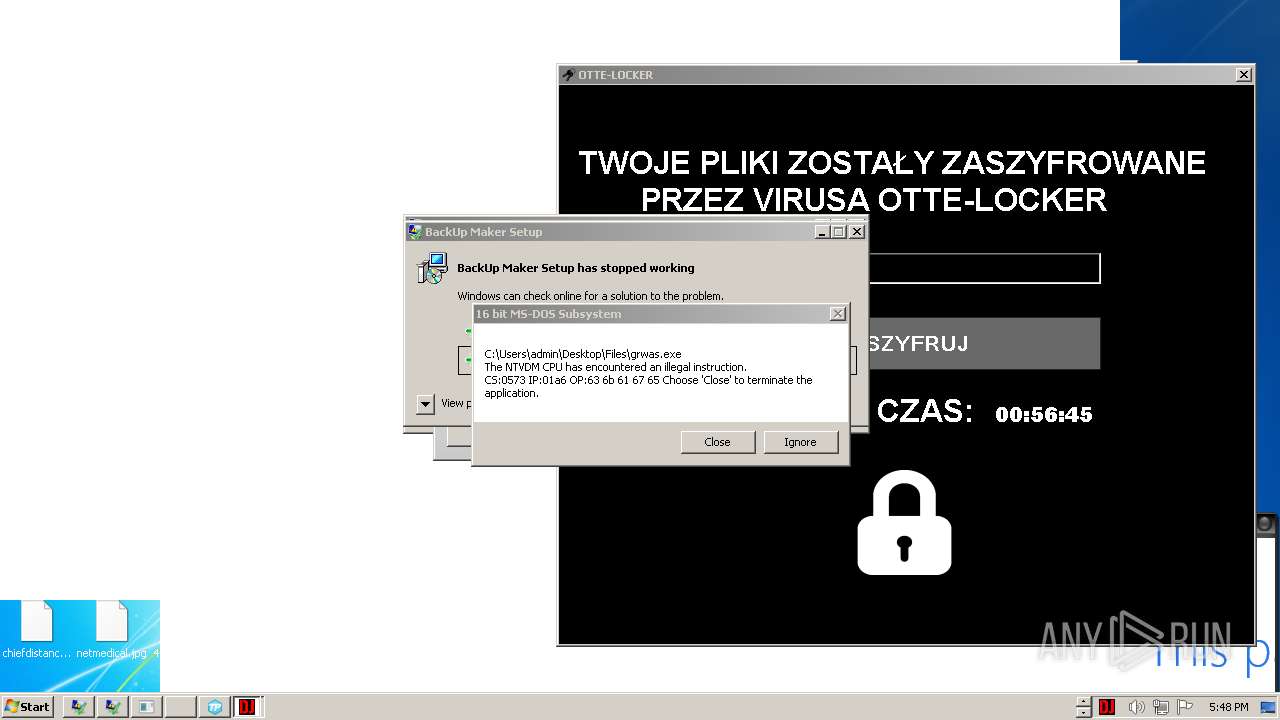
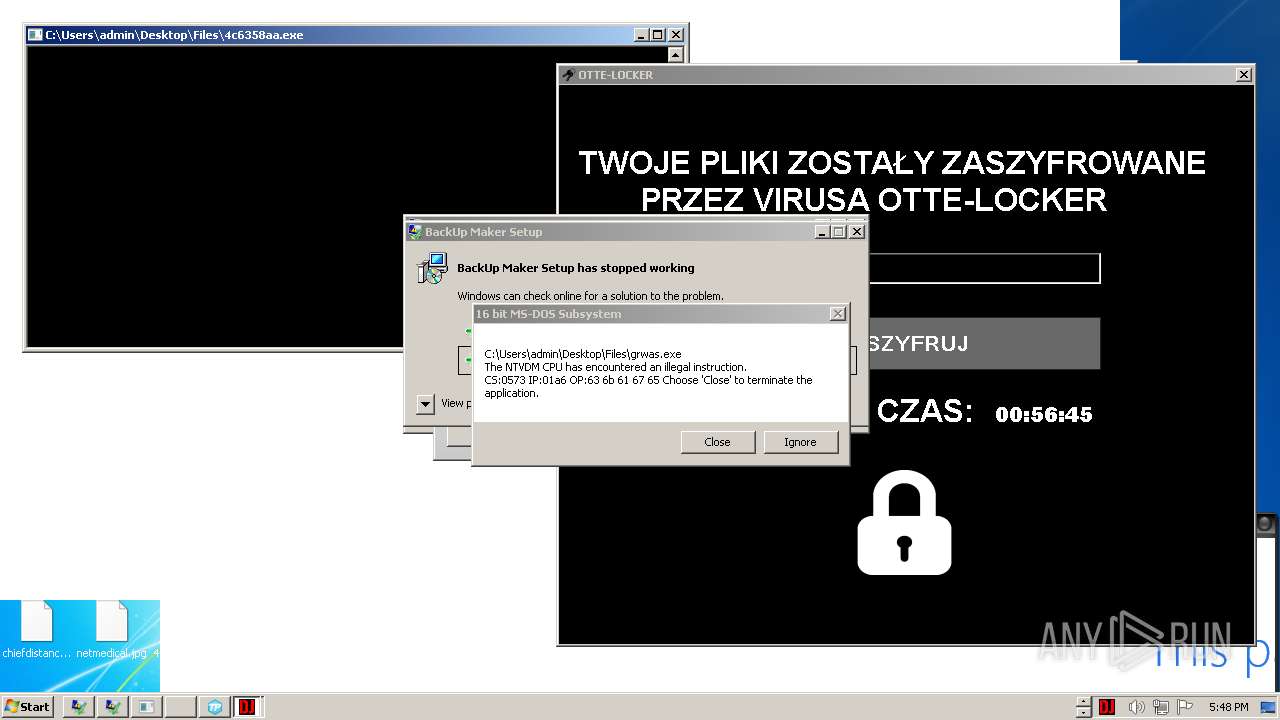
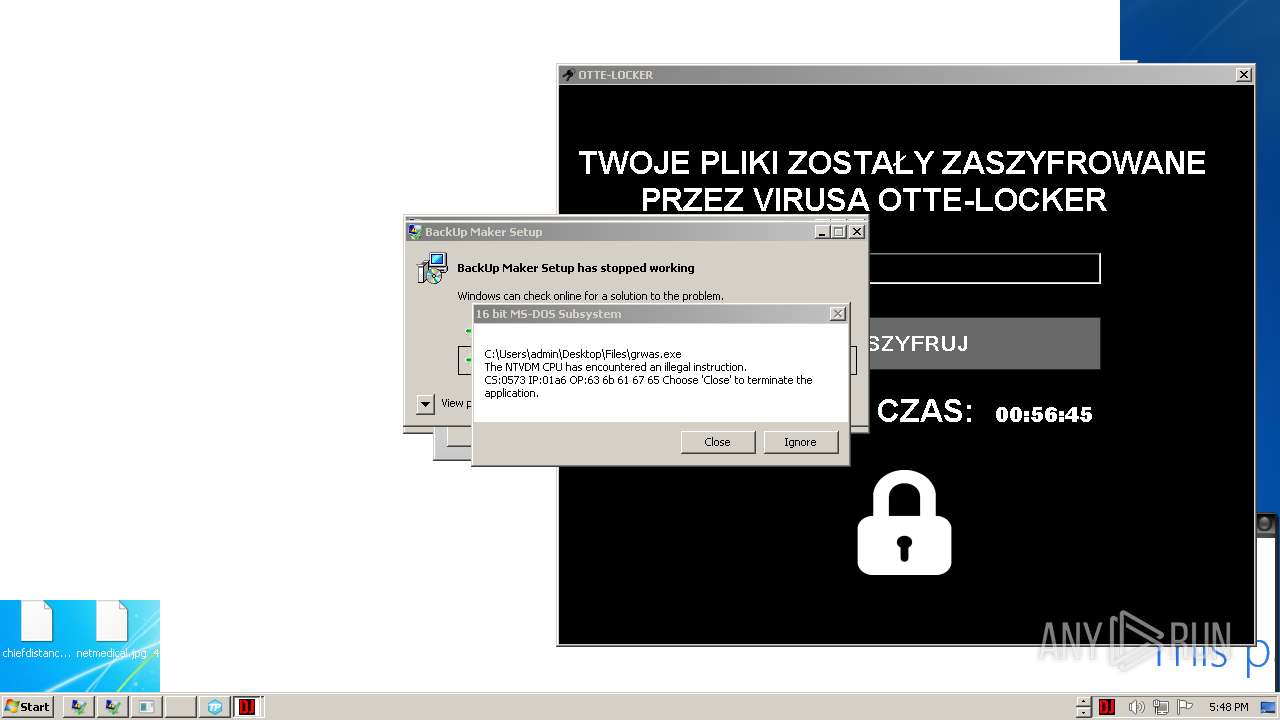
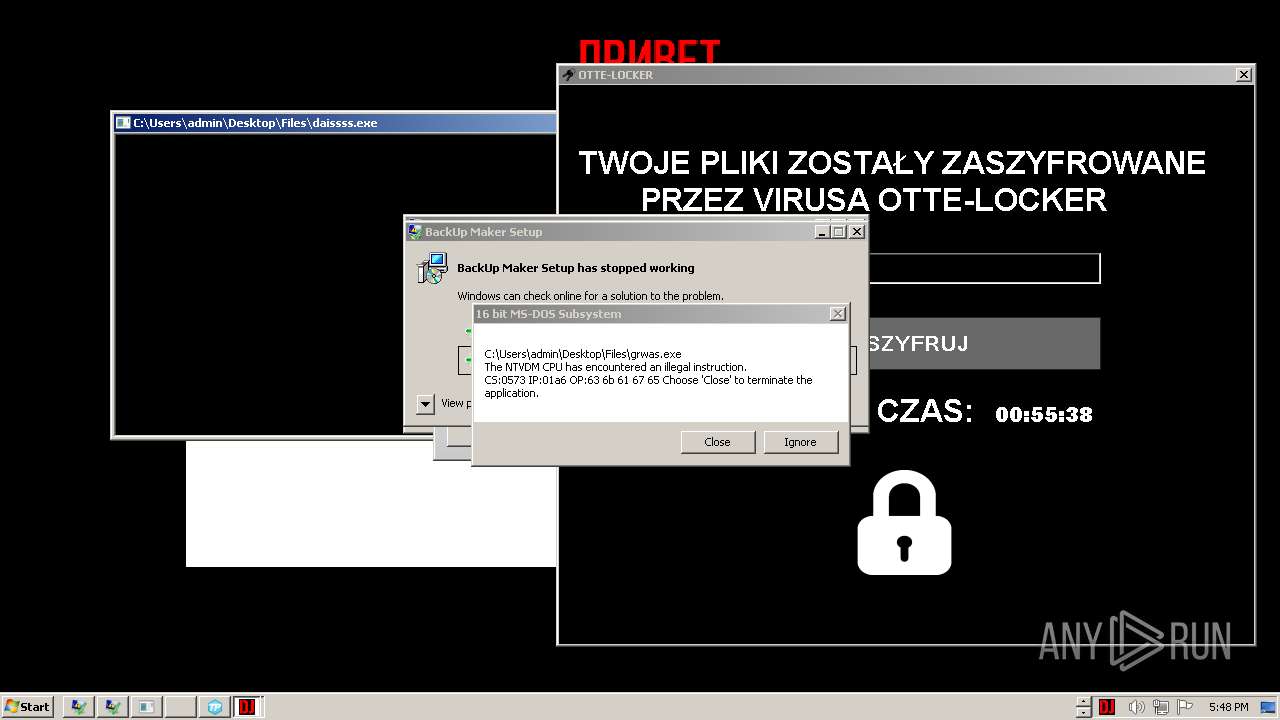
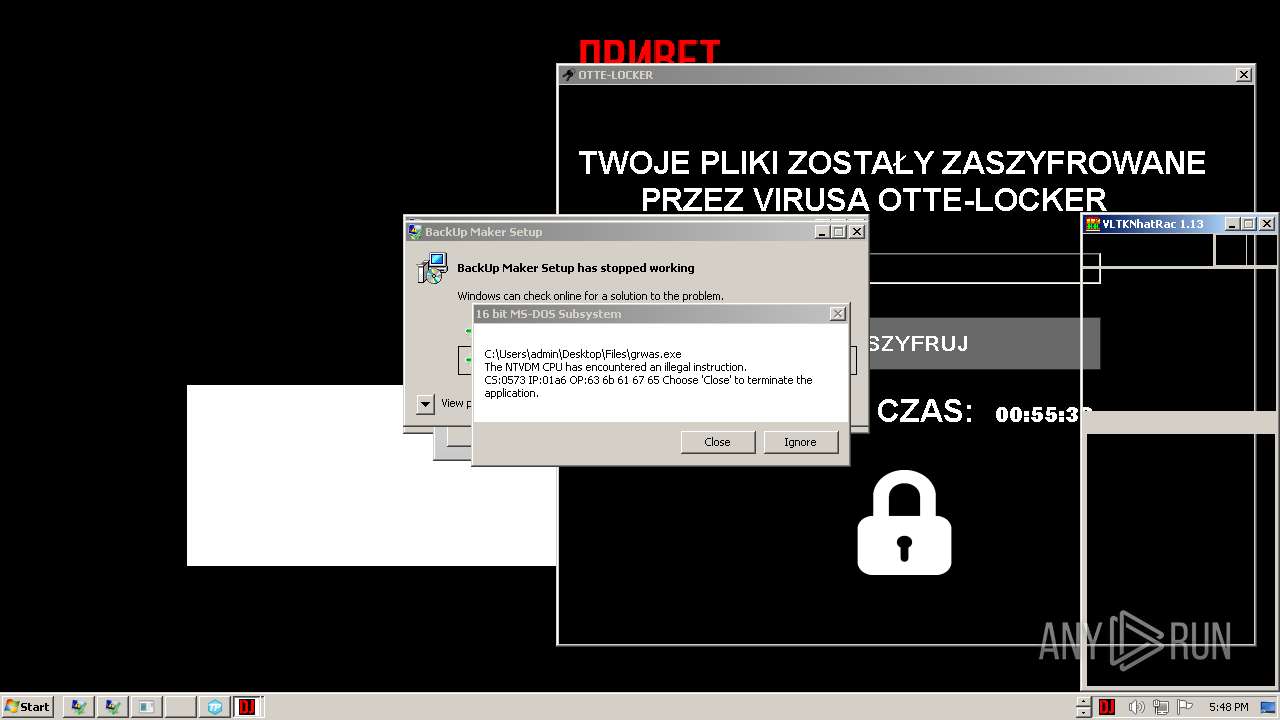
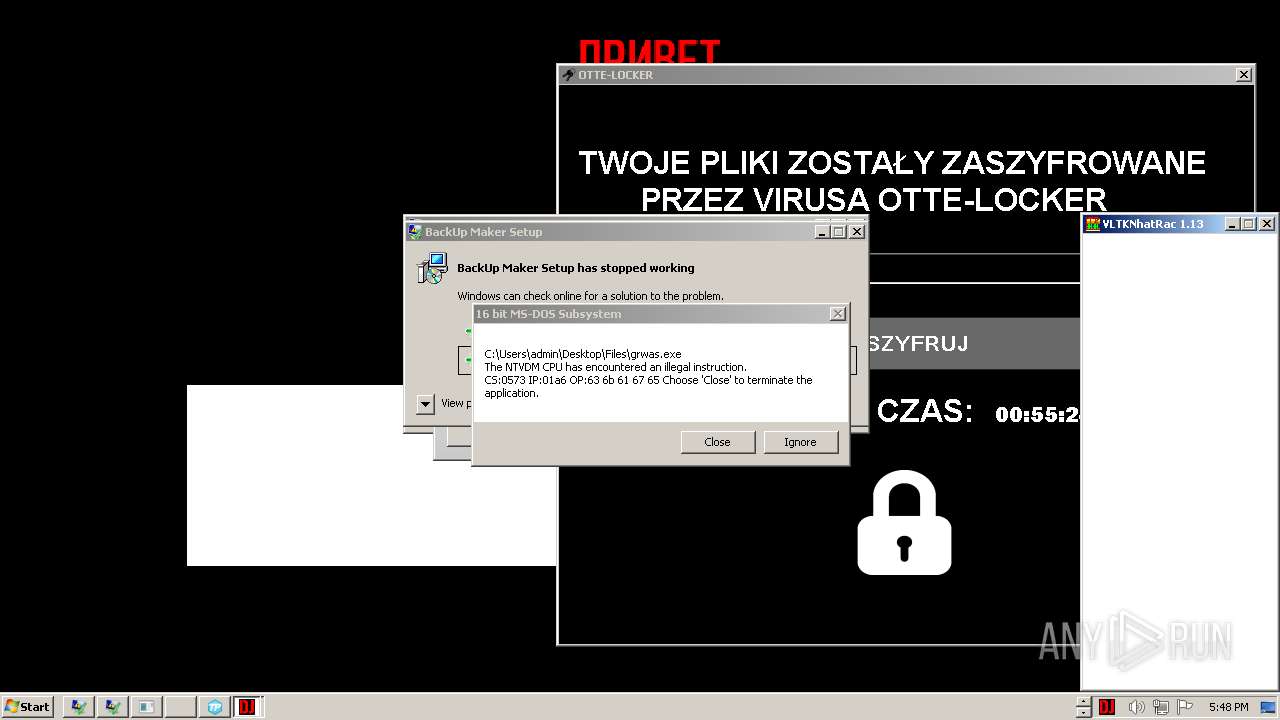
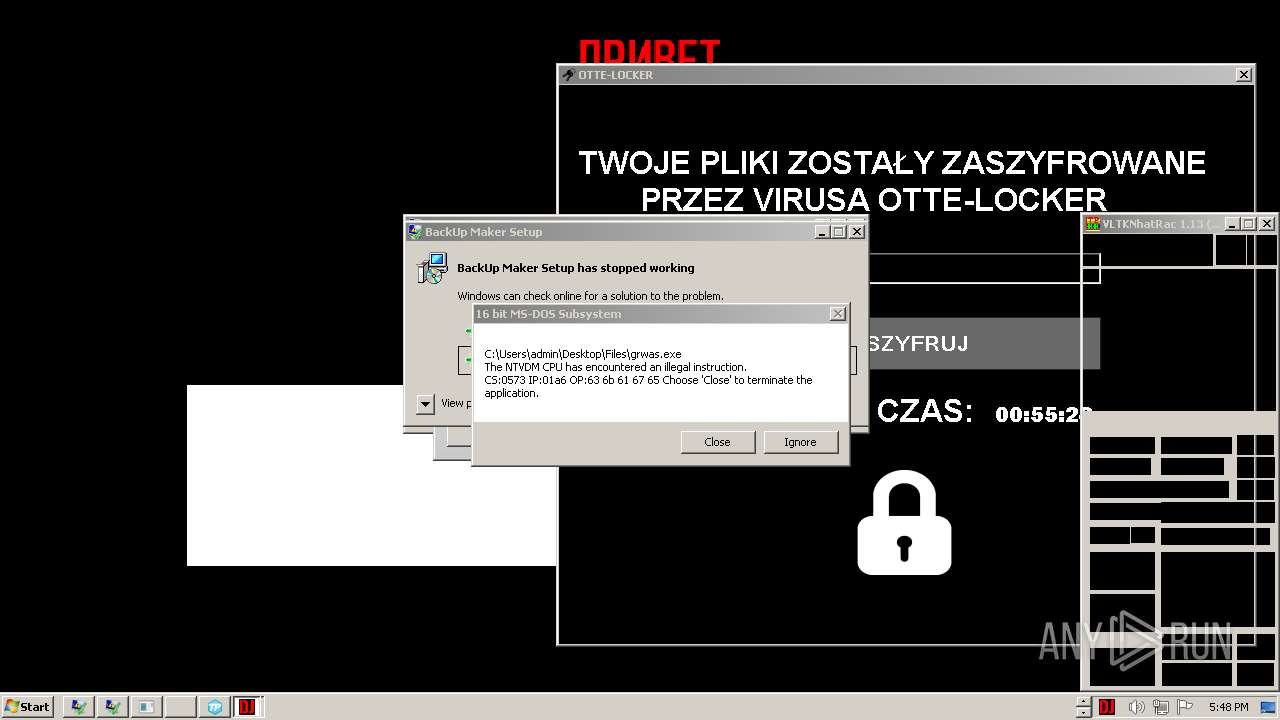
- Otte-Locker.exe (PID: 3760)
- _VTI_CNF.exe (PID: 6460)
ASYNCRAT has been detected (SURICATA)
- 666.exe (PID: 3404)
Actions looks like stealing of personal data
- dialer.exe (PID: 2000)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- dialer.exe (PID: 1352)
- cluton.exe (PID: 4188)
- Accommodations.pif (PID: 5420)
- jsc.exe (PID: 3684)
- dialer.exe (PID: 6000)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- kehu.exe (PID: 2764)
- 4363463463464363463463463.exe (PID: 3216)
- RegAsm.exe (PID: 6216)
- ._cache_server.exe (PID: 7444)
- dialer.exe (PID: 8148)
Changes the autorun value in the registry
- 2591814628.exe (PID: 3732)
- npp86Installerx64.exe (PID: 1972)
- first.exe (PID: 696)
- 3322713636.exe (PID: 2488)
- PluginFlash.exe (PID: 4184)
- _VTI_CNF.exe (PID: 6460)
- HD_._cache_server.exe (PID: 7552)
- server.exe (PID: 7020)
- Horpxuoxm.exe (PID: 7692)
Connects to the CnC server
- WeChat.exe (PID: 3060)
- jS-tD.exe (PID: 2060)
- bott.exe (PID: 2332)
- 2591814628.exe (PID: 3732)
- RT2q.exe (PID: 2540)
- build6_unencrypted.exe (PID: 6060)
- syncUpd.exe (PID: 5668)
- jsc.exe (PID: 3684)
- bott.exe (PID: 2968)
- uWVU7[5[).exe (PID: 5988)
- kehu.exe (PID: 2764)
- RegAsm.exe (PID: 6216)
- lve5.exe (PID: 6244)
- HD_._cache_server.exe (PID: 7552)
- mpveasyplayer.exe (PID: 3384)
- Horpxuoxm.exe (PID: 7692)
Changes Security Center notification settings
- 2591814628.exe (PID: 3732)
- 3322713636.exe (PID: 2488)
AZORULT has been detected (SURICATA)
- jS-tD.exe (PID: 2060)
- RT2q.exe (PID: 2540)
- uWVU7[5[).exe (PID: 5988)
Steals credentials from Web Browsers
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- cluton.exe (PID: 4188)
- Accommodations.pif (PID: 5420)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- RegAsm.exe (PID: 6216)
Create files in the Startup directory
- STAR.exe (PID: 2444)
- first.exe (PID: 696)
- dllhost.exe (PID: 4812)
- Horpxuoxm.exe (PID: 1852)
- Winlock.exe (PID: 4312)
REDLINE has been detected (SURICATA)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- kehu.exe (PID: 2764)
- RegAsm.exe (PID: 6216)
Changes powershell execution policy (Bypass)
- first.exe (PID: 696)
- EchoNavigator.exe (PID: 5776)
- build6_unencrypted.exe (PID: 6060)
- Archevod_XWorm.exe (PID: 6812)
Adds process to the Windows Defender exclusion list
- first.exe (PID: 696)
- build6_unencrypted.exe (PID: 6060)
- Archevod_XWorm.exe (PID: 6812)
Adds path to the Windows Defender exclusion list
- first.exe (PID: 696)
- build6_unencrypted.exe (PID: 6060)
- Archevod_XWorm.exe (PID: 6812)
PHORPIEX has been detected (SURICATA)
- 2591814628.exe (PID: 3732)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 3216)
Deletes a file (SCRIPT)
- IconRemoval.exe (PID: 2712)
ASYNCRAT has been detected (YARA)
- 666.exe (PID: 3404)
- reo.exe (PID: 2128)
Checks whether a specified folder exists (SCRIPT)
- 7zipFOPBACKEND.exe (PID: 1316)
XWORM has been detected (YARA)
- first.exe (PID: 696)
- build6_unencrypted.exe (PID: 6060)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 4496)
Starts CMD.EXE for self-deleting
- inte.exe (PID: 4496)
- Accommodations.pif (PID: 5420)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 5304)
- findstr.exe (PID: 5348)
DcRAT is detected
- agentServerComponent.exe (PID: 5508)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4996)
Raccoon mutex has been detected
- 2.3.1.1.exe (PID: 5228)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
Unusual connection from system programs
- vbc.exe (PID: 5212)
STEALC has been detected (SURICATA)
- syncUpd.exe (PID: 5668)
XWORM has been detected (SURICATA)
- build6_unencrypted.exe (PID: 6060)
Lokibot is detected
- cluton.exe (PID: 4188)
Creates a writable file in the system directory
- Temp2.exe (PID: 4868)
- _VTI_CNF.exe (PID: 6460)
- look2.exe (PID: 7492)
- HD_._cache_server.exe (PID: 7552)
- Winlock.exe (PID: 4312)
Deletes the SafeBoot registry key
- 7e207560.exe (PID: 1888)
ARECHCLIENT2 has been detected (SURICATA)
- jsc.exe (PID: 3684)
AMADEY has been detected (SURICATA)
- MSI.CentralServer.exe (PID: 6140)
PURPLEFOX has been detected (SURICATA)
- lve5.exe (PID: 6244)
REDLINE has been detected (YARA)
- v2.exe (PID: 4108)
- dsdasda.exe (PID: 2360)
- M5traider.exe (PID: 5164)
- RegSvcs.exe (PID: 4684)
- vbc.exe (PID: 5212)
- RegSvcs.exe (PID: 5796)
GH0ST has been detected (SURICATA)
- HD_._cache_server.exe (PID: 7552)
SOCKS5SYSTEMZ has been detected (SURICATA)
- mpveasyplayer.exe (PID: 3384)
RISEPRO has been detected (YARA)
- pixxxxx.exe (PID: 4176)
- ladas.exe (PID: 4396)
Renames files like ransomware
- abc.exe (PID: 7792)
VIDAR has been detected (YARA)
- InstallUtil.exe (PID: 5068)
BLACKNET has been detected (SURICATA)
- Horpxuoxm.exe (PID: 7692)
LOKIBOT has been detected (YARA)
- cluton.exe (PID: 4188)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3216)
- data64_6.exe (PID: 2340)
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- 4363463463464363463463463.exe (PID: 2588)
- powershell.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 1956)
- npp.exe (PID: 3920)
- jS-tD.exe (PID: 2060)
- 4363463463464363463463463.exe (PID: 2424)
- Journal.exe (PID: 2504)
- RegAsm.exe (PID: 3684)
- npp.8.6.2.Installer.x64.exe (PID: 2064)
- 2591814628.exe (PID: 3732)
- STAR.exe (PID: 2444)
- univ.exe (PID: 3440)
- first.exe (PID: 696)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 2448)
- powershell.exe (PID: 920)
- 3322713636.exe (PID: 2488)
- Setup2010u32.exe (PID: 2864)
- RT2q.exe (PID: 2540)
- tpeinf.exe (PID: 1404)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- inte.exe (PID: 4496)
- InstallUtil.exe (PID: 5068)
- v4install.exe (PID: 4944)
- GorgeousMovement.exe (PID: 5188)
- wscript.exe (PID: 4996)
- syncUpd.exe (PID: 5668)
- 1230.exe (PID: 5720)
- ama.exe (PID: 4712)
- build6_unencrypted.exe (PID: 6060)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 5900)
- powershell.exe (PID: 2416)
- fortnite3.exe (PID: 4952)
- 2.3.1.1.exe (PID: 5228)
- Accommodations.pif (PID: 5420)
- cluton.exe (PID: 4188)
- Temp2.exe (PID: 4868)
- 7e207560.exe (PID: 1888)
- MSI.CentralServer.exe (PID: 6140)
- data64_5.exe (PID: 5348)
- asg.exe (PID: 5200)
- RegAsm.exe (PID: 3736)
- uWVU7[5[).exe (PID: 5988)
- pei.exe (PID: 4104)
- _VTI_CNF.exe (PID: 6460)
- 2014-06-12_djylh.exe (PID: 6764)
- baseline.exe (PID: 7028)
- plink.exe (PID: 7036)
- server.exe (PID: 7020)
- gookcom.exe (PID: 7276)
- Horpxuoxm.exe (PID: 7692)
- mpveasyplayer.exe (PID: 3384)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- Winlock.exe (PID: 4312)
- Archevod_XWorm.exe (PID: 6812)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 3216)
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- BBLb.exe (PID: 2440)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1956)
- npp.exe (PID: 3920)
- 2591814628.exe (PID: 3732)
- dialer.exe (PID: 2000)
- 4363463463464363463463463.exe (PID: 2424)
- npp86Installerx64.exe (PID: 1972)
- RegAsm.exe (PID: 3684)
- STAR.exe (PID: 2444)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- 3322713636.exe (PID: 2488)
- Setup2010u32.exe (PID: 2864)
- dialer.exe (PID: 1352)
- may.exe (PID: 2068)
- may.tmp (PID: 3980)
- tpeinf.exe (PID: 1404)
- mpveasyplayer.exe (PID: 2712)
- PluginFlash.exe (PID: 4184)
- v2.exe (PID: 4108)
- v4install.exe (PID: 4944)
- univ.exe (PID: 3440)
- GorgeousMovement.exe (PID: 5188)
- cp.exe (PID: 1408)
- cmd.exe (PID: 5396)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- agentServerComponent.exe (PID: 5508)
- cluton.exe (PID: 6116)
- Temp2.exe (PID: 4868)
- dllhost.exe (PID: 4812)
- hv.exe (PID: 5648)
- build3.exe (PID: 2260)
- RegAsm.exe (PID: 3736)
- dialer.exe (PID: 6000)
- conhost.exe (PID: 4476)
- pei.exe (PID: 4104)
- lve5.exe (PID: 6244)
- _VTI_CNF.exe (PID: 6460)
- cluton.exe (PID: 4188)
- server.exe (PID: 7020)
- look2.exe (PID: 7492)
- ._cache_server.exe (PID: 7444)
- Horpxuoxm.exe (PID: 1852)
- HD_._cache_server.exe (PID: 7552)
- Synaptics.exe (PID: 7616)
- Winlock.exe (PID: 4312)
- april.exe (PID: 3356)
- Horpxuoxm.exe (PID: 7692)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 7404)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 6128)
- april.tmp (PID: 6852)
- jet.exe (PID: 3140)
- InstallSetup9.exe (PID: 7344)
- yhdl.exe (PID: 3492)
- smell-the-roses.exe (PID: 5996)
- amert.exe (PID: 6396)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2588)
- Helper.exe (PID: 2568)
- 4363463463464363463463463.exe (PID: 2424)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 3216)
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2424)
- npp.exe (PID: 3920)
- jS-tD.exe (PID: 2060)
- Journal.exe (PID: 2504)
- RegAsm.exe (PID: 3684)
- 2591814628.exe (PID: 3732)
- STAR.exe (PID: 2444)
- univ.exe (PID: 3440)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- 3322713636.exe (PID: 2488)
- Setup2010u32.exe (PID: 2864)
- RT2q.exe (PID: 2540)
- inte.exe (PID: 4496)
- InstallUtil.exe (PID: 5068)
- v4install.exe (PID: 4944)
- GorgeousMovement.exe (PID: 5188)
- syncUpd.exe (PID: 5668)
- 1230.exe (PID: 5720)
- ama.exe (PID: 4712)
- build6_unencrypted.exe (PID: 6060)
- fortnite3.exe (PID: 4952)
- 2.3.1.1.exe (PID: 5228)
- Accommodations.pif (PID: 5420)
- MSI.CentralServer.exe (PID: 6140)
- RegAsm.exe (PID: 3736)
- uWVU7[5[).exe (PID: 5988)
- _VTI_CNF.exe (PID: 6460)
- 2014-06-12_djylh.exe (PID: 6764)
- server.exe (PID: 7020)
- plink.exe (PID: 7036)
- gookcom.exe (PID: 7276)
- Horpxuoxm.exe (PID: 7692)
- mpveasyplayer.exe (PID: 3384)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- Winlock.exe (PID: 4312)
- Archevod_XWorm.exe (PID: 6812)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3216)
- data64_6.exe (PID: 2340)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- 666.exe (PID: 3404)
- WeChat.exe (PID: 3060)
- Helper.exe (PID: 2568)
- InstallUtil.exe (PID: 5068)
Application launched itself
- asdfg.exe (PID: 2408)
- BBLb.exe (PID: 3180)
- jS-tD.exe (PID: 1824)
- AttributeString.exe (PID: 2380)
- lumma.exe (PID: 2448)
- MSBuild.exe (PID: 2948)
- ghjk.exe (PID: 4020)
- ghjkl.exe (PID: 4056)
- RT2q.exe (PID: 3928)
- cmd.exe (PID: 5288)
- cmd.exe (PID: 5264)
- zxcvb.exe (PID: 4788)
- native.exe (PID: 5276)
- cluton.exe (PID: 6116)
- soft.exe (PID: 1072)
- data64_5.exe (PID: 4856)
- 7e207560.exe (PID: 5388)
- net.exe (PID: 3076)
- build3.exe (PID: 5016)
- uWVU7[5[).exe (PID: 1832)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 4856)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 4324)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4856)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 4856)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 6172)
- Gsoymaq.exe (PID: 6328)
- Horpxuoxm.exe (PID: 1852)
- ghost.exe (PID: 7800)
- WindowsUpdate.exe (PID: 7808)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- data64_6.exe (PID: 2340)
- InstallUtil.exe (PID: 5068)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 1956)
- 666.exe (PID: 3404)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- Journal.exe (PID: 2504)
- reo.exe (PID: 2128)
- first.exe (PID: 696)
- 2591814628.exe (PID: 3732)
- RegSvcs.exe (PID: 4684)
- 4363463463464363463463463.exe (PID: 2424)
- RegSvcs.exe (PID: 5796)
- vbc.exe (PID: 5212)
- build6_unencrypted.exe (PID: 6060)
- asg.exe (PID: 5200)
- jsc.exe (PID: 3684)
- bott.exe (PID: 2968)
- STAR.exe (PID: 6116)
- Screensaver.exe (PID: 4380)
- kehu.exe (PID: 2764)
- AppLaunch.exe (PID: 5772)
- RegAsm.exe (PID: 6216)
- lve5.exe (PID: 6244)
- baseline.exe (PID: 7028)
- LostArk.exe (PID: 6984)
- HD_._cache_server.exe (PID: 7552)
- powershell.exe (PID: 7472)
- dialer.exe (PID: 8148)
- Recorder.exe (PID: 6744)
Starts CMD.EXE for commands execution
- Client.exe (PID: 2688)
- RegAsm.exe (PID: 3684)
- CleanUp Icons FOP.exe (PID: 3212)
- inte.exe (PID: 4496)
- GorgeousMovement.exe (PID: 5188)
- cmd.exe (PID: 5264)
- cmd.exe (PID: 5288)
- wscript.exe (PID: 4996)
- Accommodations.pif (PID: 5420)
- RegAsm.exe (PID: 3736)
- _VTI_CNF.exe (PID: 6460)
- Winlock.exe (PID: 4312)
Executing commands from a ".bat" file
- Client.exe (PID: 2688)
- CleanUp Icons FOP.exe (PID: 3212)
- wscript.exe (PID: 4996)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1112)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2000)
- 4363463463464363463463463.exe (PID: 1956)
- dialer.exe (PID: 1352)
- dialer.exe (PID: 6000)
- dialer.exe (PID: 8148)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2424)
- univ.exe (PID: 3440)
The executable file from the user directory is run by the CMD process
- 666.exe (PID: 3404)
- Accommodations.pif (PID: 5420)
- agentServerComponent.exe (PID: 5508)
The process executes via Task Scheduler
- powershell.exe (PID: 840)
- AttributeString.exe (PID: 2380)
- powershell.exe (PID: 920)
- mstsca.exe (PID: 4280)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 840)
- powershell.exe (PID: 3504)
- powershell.exe (PID: 920)
- powershell.exe (PID: 2448)
- powershell.exe (PID: 2416)
- powershell.exe (PID: 3076)
Changes the desktop background image
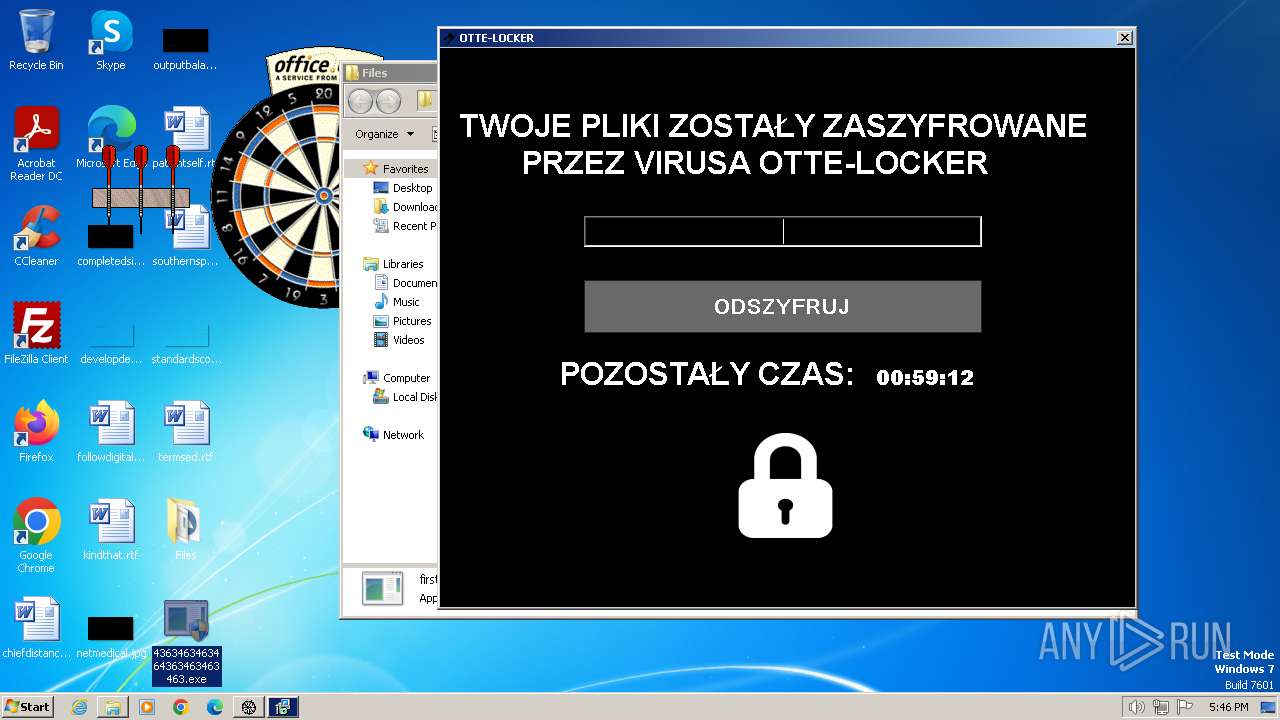
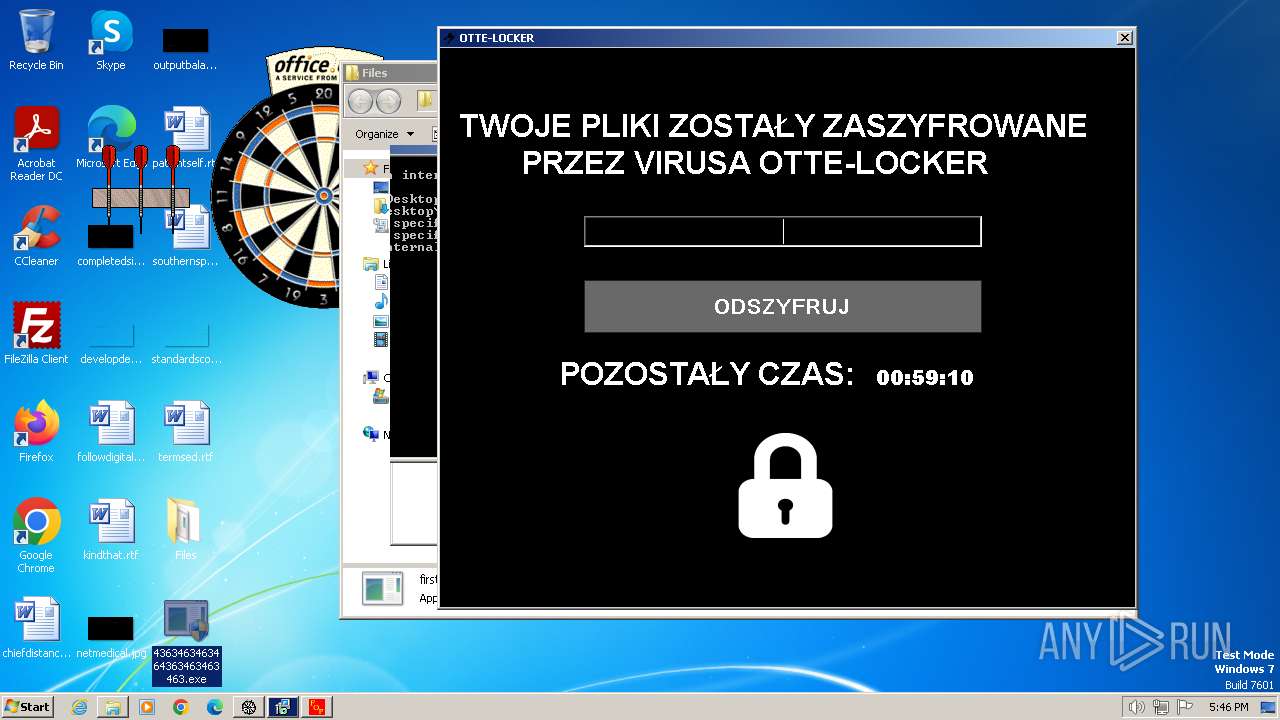
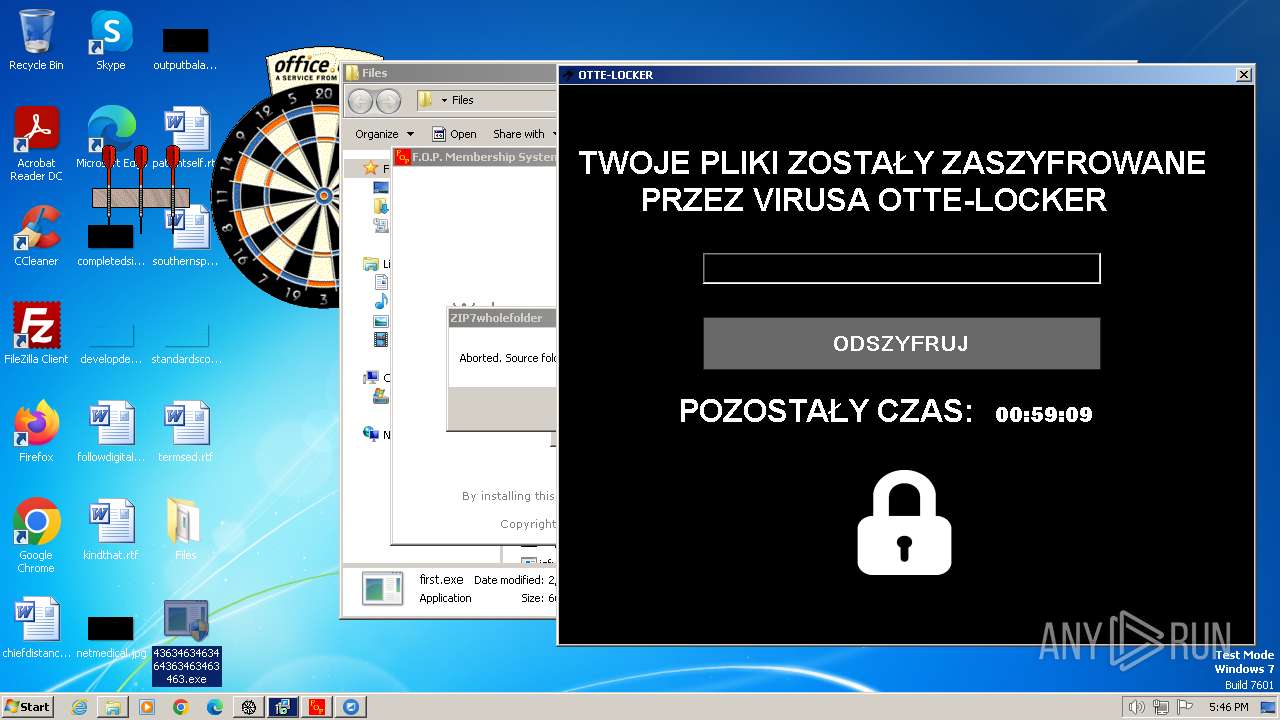
- Otte-Locker.exe (PID: 3760)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3216)
- 2591814628.exe (PID: 3732)
- inte.exe (PID: 4496)
- Horpxuoxm.exe (PID: 7692)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 2000)
- dialer.exe (PID: 1352)
- cluton.exe (PID: 4188)
- dialer.exe (PID: 6000)
- dialer.exe (PID: 8148)
Reads browser cookies
- dialer.exe (PID: 2000)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- RegAsm.exe (PID: 6216)
- kehu.exe (PID: 2764)
- dialer.exe (PID: 8148)
Searches for installed software
- dialer.exe (PID: 2000)
- 666.exe (PID: 3404)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- dialer.exe (PID: 1352)
- Accommodations.pif (PID: 5420)
- dialer.exe (PID: 6000)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- kehu.exe (PID: 2764)
- RegAsm.exe (PID: 6216)
- dialer.exe (PID: 8148)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 2000)
- dialer.exe (PID: 1352)
- Accommodations.pif (PID: 5420)
- cluton.exe (PID: 4188)
- dialer.exe (PID: 6000)
- dialer.exe (PID: 8148)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 1956)
- univ.exe (PID: 3440)
- may.tmp (PID: 3980)
- 4363463463464363463463463.exe (PID: 2424)
- april.tmp (PID: 6852)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 3216)
- PluginFlash.exe (PID: 4184)
- 4363463463464363463463463.exe (PID: 1956)
- conhost.exe (PID: 4476)
- _VTI_CNF.exe (PID: 6460)
- 4363463463464363463463463.exe (PID: 2424)
Starts a Microsoft application from unusual location
- npp86Installerx64.exe (PID: 1972)
- lumma1234.exe (PID: 4828)
- f88253a.exe (PID: 6108)
- Archevod_XWorm.exe (PID: 6812)
Executed via WMI
- jS-tD.exe (PID: 1824)
- RT2q.exe (PID: 3928)
- uWVU7[5[).exe (PID: 1832)
Starts POWERSHELL.EXE for commands execution
- first.exe (PID: 696)
- EchoNavigator.exe (PID: 5776)
- build6_unencrypted.exe (PID: 6060)
- hv.exe (PID: 5648)
- gookcom.exe (PID: 7276)
- Archevod_XWorm.exe (PID: 6812)
Script adds exclusion process to Windows Defender
- first.exe (PID: 696)
- build6_unencrypted.exe (PID: 6060)
- Archevod_XWorm.exe (PID: 6812)
Script adds exclusion path to Windows Defender
- first.exe (PID: 696)
- build6_unencrypted.exe (PID: 6060)
- Archevod_XWorm.exe (PID: 6812)
Checks Windows Trust Settings
- Helper.exe (PID: 2568)
- InstallUtil.exe (PID: 5068)
Reads the Windows owner or organization settings
- Helper.exe (PID: 2568)
- may.tmp (PID: 3980)
Executes as Windows Service
- VSSVC.exe (PID: 2000)
- 7e207560.exe (PID: 5388)
- Gsoymaq.exe (PID: 6328)
Checks for external IP
- first.exe (PID: 696)
- Temp2.exe (PID: 4868)
- asg.exe (PID: 5200)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3264)
Creates FileSystem object to access computer's file system (SCRIPT)
- 7zipFOPBACKEND.exe (PID: 1316)
- IconRemoval.exe (PID: 2712)
The process executes VB scripts
- PluginFlash.exe (PID: 4184)
- iexplore.exe (PID: 4236)
- xyodgsih.exe (PID: 3080)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- 2014-06-12_djylh.exe (PID: 6764)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4744)
Get information on the list of running processes
- cmd.exe (PID: 5288)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 5396)
Starts application with an unusual extension
- cmd.exe (PID: 5288)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5288)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5288)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4996)
Windows Defender mutex has been found
- syncUpd.exe (PID: 5668)
The process hide an interactive prompt from the user
- EchoNavigator.exe (PID: 5776)
The process hides Powershell's copyright startup banner
- EchoNavigator.exe (PID: 5776)
The process bypasses the loading of PowerShell profile settings
- EchoNavigator.exe (PID: 5776)
The process executes Powershell scripts
- EchoNavigator.exe (PID: 5776)
Unusual connection from system programs
- powershell.exe (PID: 5900)
- powershell.exe (PID: 7472)
The Powershell connects to the Internet
- powershell.exe (PID: 5900)
- powershell.exe (PID: 7472)
Reads the BIOS version
- ladas.exe (PID: 4396)
- micro.exe (PID: 5004)
- brg.exe (PID: 4216)
- amert.exe (PID: 6396)
Reads Mozilla Firefox installation path
- cluton.exe (PID: 4188)
Starts itself from another location
- Temp2.exe (PID: 4868)
- Horpxuoxm.exe (PID: 7692)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6Srv.exe (PID: 6128)
Malware-specific behavior (creating "System.dll" in Temp)
- conhost.exe (PID: 4476)
Creates or modifies Windows services
- lve5.exe (PID: 6244)
- _VTI_CNF.exe (PID: 6460)
- look2.exe (PID: 7492)
Reads Microsoft Outlook installation path
- 2014-06-12_djylh.exe (PID: 6764)
Reads the date of Windows installation
- server.exe (PID: 7020)
Potential TCP-based PowerShell reverse shell connection
- gookcom.exe (PID: 7276)
Suspicious files were dropped or overwritten
- look2.exe (PID: 7492)
Suspicious use of symmetric encryption in PowerShell
- gookcom.exe (PID: 7276)
Base64-obfuscated command line is found
- gookcom.exe (PID: 7276)
Write to the desktop.ini file (may be used to cloak folders)
- abc.exe (PID: 7792)
Creates files like ransomware instruction
- abc.exe (PID: 7792)
Creates files in the driver directory
- Winlock.exe (PID: 4312)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7172)
INFO
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3216)
- data64_6.exe (PID: 2340)
- asdfg.exe (PID: 2408)
- BBLb.exe (PID: 3180)
- Client.exe (PID: 2688)
- BBLb.exe (PID: 2440)
- 666.exe (PID: 3404)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 2588)
- Otte-Locker.exe (PID: 3760)
- 4363463463464363463463463.exe (PID: 1956)
- ed.exe (PID: 1072)
- npp.exe (PID: 3920)
- WeChat.exe (PID: 3060)
- wmpnscfg.exe (PID: 3972)
- jS-tD.exe (PID: 1824)
- jS-tD.exe (PID: 2060)
- npp.8.6.2.Installer.x64.exe (PID: 2064)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- Journal.exe (PID: 2504)
- reo.exe (PID: 2128)
- AttributeString.exe (PID: 2348)
- 2591814628.exe (PID: 3732)
- AttributeString.exe (PID: 2380)
- univ.exe (PID: 3440)
- MSBuild.exe (PID: 2948)
- MSBuild.exe (PID: 3304)
- ghjk.exe (PID: 4020)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- ghjkl.exe (PID: 4056)
- cayV0Deo9jSt417.exe (PID: 2136)
- 3322713636.exe (PID: 2488)
- 7zipFOPBACKEND.exe (PID: 1316)
- RT2q.exe (PID: 3928)
- RT2q.exe (PID: 2540)
- hncc.exe (PID: 3944)
- tpeinf.exe (PID: 1404)
- v2.exe (PID: 4108)
- dsdasda.exe (PID: 2360)
- SuburbansKamacite.exe (PID: 2660)
- PluginFlash.exe (PID: 4184)
- inte.exe (PID: 4496)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- 1234daisaaaaa.exe (PID: 4588)
- RegSvcs.exe (PID: 4684)
- plugins.exe (PID: 1848)
- InstallUtil.exe (PID: 5068)
- WatchDog.exe (PID: 5028)
- M5traider.exe (PID: 5164)
- agentServerComponent.exe (PID: 5508)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- syncUpd.exe (PID: 5668)
- 1230.exe (PID: 5720)
- RegSvcs.exe (PID: 5796)
- EchoNavigator.exe (PID: 5776)
- Windows.exe (PID: 5980)
- build6_unencrypted.exe (PID: 6060)
- zxcvb.exe (PID: 4788)
- vbc.exe (PID: 5212)
- 2.3.1.1.exe (PID: 5228)
- fortnite3.exe (PID: 4952)
- xyodgsih.exe (PID: 3080)
- native.exe (PID: 5276)
- Accommodations.pif (PID: 5420)
- cluton.exe (PID: 4188)
- Temp2.exe (PID: 4868)
- html.exe (PID: 2080)
- asg.exe (PID: 5200)
- net.exe (PID: 3076)
- data64_5.exe (PID: 5348)
- hv.exe (PID: 5648)
- MSI.CentralServer.exe (PID: 6140)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- bott.exe (PID: 2968)
- uWVU7[5[).exe (PID: 1832)
- uWVU7[5[).exe (PID: 5988)
- CheatLoader.exe (PID: 3336)
- kehu.exe (PID: 2764)
- pei.exe (PID: 4104)
- Horpxuoxm.exe (PID: 1852)
- brg.exe (PID: 4216)
- AppLaunch.exe (PID: 5772)
- RegAsm.exe (PID: 6216)
- _VTI_CNF.exe (PID: 6460)
- National.exe (PID: 6644)
- 2014-06-12_djylh.exe (PID: 6764)
- server.exe (PID: 7020)
- LostArk.exe (PID: 6984)
- baseline.exe (PID: 7028)
- gookcom.exe (PID: 7276)
- Horpxuoxm.exe (PID: 7692)
- VLTKNhatRac.exe (PID: 7964)
- mpveasyplayer.exe (PID: 3384)
- Temp1.exe (PID: 7872)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- NBYS%20AH.NET.exe (PID: 6664)
- abc.exe (PID: 7792)
- Archevod_XWorm.exe (PID: 6812)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3216)
- data64_6.exe (PID: 2340)
- crypted.exe (PID: 2232)
- BBLb.exe (PID: 3180)
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- BBLb.exe (PID: 2440)
- 666.exe (PID: 3404)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- Otte-Locker.exe (PID: 3760)
- 4363463463464363463463463.exe (PID: 1956)
- 321.exe (PID: 3236)
- ed.exe (PID: 1072)
- npp.exe (PID: 3920)
- WeChat.exe (PID: 3060)
- jS-tD.exe (PID: 1824)
- jS-tD.exe (PID: 2060)
- RegAsm.exe (PID: 3684)
- Journal.exe (PID: 2504)
- svchost.exe (PID: 1236)
- npp.8.6.2.Installer.x64.exe (PID: 2064)
- bott.exe (PID: 2332)
- reo.exe (PID: 2128)
- STAR.exe (PID: 2444)
- 2591814628.exe (PID: 3732)
- AttributeString.exe (PID: 2348)
- AttributeString.exe (PID: 2380)
- qemu-ga.exe (PID: 3376)
- univ.exe (PID: 3440)
- MSBuild.exe (PID: 2948)
- MSBuild.exe (PID: 3304)
- ghjk.exe (PID: 4020)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- ghjkl.exe (PID: 4056)
- cayV0Deo9jSt417.exe (PID: 2136)
- 3322713636.exe (PID: 2488)
- plugins.exe (PID: 1848)
- Setup2010u32.exe (PID: 2864)
- IconRemoval.exe (PID: 2712)
- 7zipFOPBACKEND.exe (PID: 1316)
- RT2q.exe (PID: 3928)
- RT2q.exe (PID: 2540)
- may.tmp (PID: 3980)
- hncc.exe (PID: 3944)
- tpeinf.exe (PID: 1404)
- dsdasda.exe (PID: 2360)
- SuburbansKamacite.exe (PID: 2660)
- v2.exe (PID: 4108)
- mpveasyplayer.exe (PID: 2712)
- PluginFlash.exe (PID: 4184)
- vbc.exe (PID: 4200)
- inte.exe (PID: 4496)
- 1234daisaaaaa.exe (PID: 4588)
- RegSvcs.exe (PID: 4684)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- v4install.exe (PID: 4944)
- lumma1234.exe (PID: 4828)
- WatchDog.exe (PID: 5028)
- InstallUtil.exe (PID: 5068)
- M5traider.exe (PID: 5164)
- cp.exe (PID: 1408)
- GorgeousMovement.exe (PID: 5188)
- Accommodations.pif (PID: 5420)
- agentServerComponent.exe (PID: 5508)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- syncUpd.exe (PID: 5668)
- hv.exe (PID: 5648)
- 1230.exe (PID: 5720)
- RegSvcs.exe (PID: 5796)
- Windows.exe (PID: 5980)
- EchoNavigator.exe (PID: 5776)
- build6_unencrypted.exe (PID: 6060)
- ama.exe (PID: 4712)
- zxcvb.exe (PID: 4788)
- fortnite3.exe (PID: 4952)
- xyodgsih.exe (PID: 3080)
- 2.3.1.1.exe (PID: 5228)
- vbc.exe (PID: 5212)
- native.exe (PID: 5276)
- i.exe (PID: 6044)
- cluton.exe (PID: 6116)
- f88253a.exe (PID: 6108)
- cluton.exe (PID: 4188)
- for.exe (PID: 5336)
- data64_5.exe (PID: 4856)
- Temp2.exe (PID: 4868)
- html.exe (PID: 2080)
- asg.exe (PID: 5200)
- data64_5.exe (PID: 5348)
- 7e207560.exe (PID: 1888)
- MSI.CentralServer.exe (PID: 6140)
- 7e207560.exe (PID: 5388)
- net.exe (PID: 3076)
- 7e207560.exe (PID: 5696)
- %E4%BA%94%E5%91%B3%E4%BC%A0%E5%A5%87.exe (PID: 4212)
- jsc.exe (PID: 3684)
- RegAsm.exe (PID: 3736)
- bott.exe (PID: 2968)
- STAR.exe (PID: 6116)
- uWVU7[5[).exe (PID: 1832)
- uWVU7[5[).exe (PID: 5988)
- pinguin.exe (PID: 5964)
- conhost.exe (PID: 4476)
- brg.exe (PID: 4216)
- CheatLoader.exe (PID: 3336)
- pei.exe (PID: 4104)
- kehu.exe (PID: 2764)
- Horpxuoxm.exe (PID: 1852)
- AppLaunch.exe (PID: 5772)
- Goldprime.exe (PID: 3084)
- TEST3.exe (PID: 5296)
- lve5.exe (PID: 6244)
- Gsoymaq.exe (PID: 6328)
- RegAsm.exe (PID: 6216)
- Gsoymaq.exe (PID: 6400)
- _VTI_CNF.exe (PID: 6460)
- National.exe (PID: 6644)
- baseline.exe (PID: 7028)
- 2014-06-12_djylh.exe (PID: 6764)
- LostArk.exe (PID: 6984)
- gookcom.exe (PID: 7276)
- server.exe (PID: 7020)
- plink.exe (PID: 7036)
- look2.exe (PID: 7492)
- HD_._cache_server.exe (PID: 7552)
- Synaptics.exe (PID: 7616)
- Horpxuoxm.exe (PID: 7692)
- ._cache_server.exe (PID: 7444)
- VLTKNhatRac.exe (PID: 7964)
- mpveasyplayer.exe (PID: 3384)
- dota.exe (PID: 8124)
- Temp1.exe (PID: 7872)
- 5d3e8177e87cc.exe (PID: 6164)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- Winlock.exe (PID: 4312)
- amert.exe (PID: 6396)
- NBYS%20AH.NET.exe (PID: 6664)
- 4c6358aa.exe (PID: 6172)
- abc.exe (PID: 7792)
- Archevod_XWorm.exe (PID: 6812)
Checks supported languages
- data64_6.exe (PID: 2340)
- 4363463463464363463463463.exe (PID: 3216)
- crypted.exe (PID: 2232)
- RegAsm.exe (PID: 4004)
- Client.exe (PID: 2688)
- asdfg.exe (PID: 2064)
- BBLb.exe (PID: 2440)
- asdfg.exe (PID: 2408)
- BBLb.exe (PID: 3180)
- 666.exe (PID: 3404)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- Otte-Locker.exe (PID: 3760)
- 321.exe (PID: 3236)
- w-12.exe (PID: 3000)
- WeChat.exe (PID: 3060)
- ed.exe (PID: 1072)
- npp.exe (PID: 3920)
- dart.exe (PID: 3952)
- 987123.exe (PID: 3420)
- wmpnscfg.exe (PID: 3972)
- 2591814628.exe (PID: 3732)
- jS-tD.exe (PID: 1824)
- npp86Installerx64.exe (PID: 1972)
- jS-tD.exe (PID: 2060)
- RegAsm.exe (PID: 3684)
- svchost.exe (PID: 1236)
- Journal.exe (PID: 2504)
- npp.8.6.2.Installer.x64.exe (PID: 2064)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- reo.exe (PID: 2128)
- AttributeString.exe (PID: 2348)
- AttributeString.exe (PID: 2380)
- qemu-ga.exe (PID: 3376)
- lumma.exe (PID: 2448)
- lumma.exe (PID: 4056)
- univ.exe (PID: 3440)
- MSBuild.exe (PID: 2948)
- MSBuild.exe (PID: 3304)
- ghjk.exe (PID: 4020)
- ghjk.exe (PID: 3012)
- first.exe (PID: 696)
- 1040922474.exe (PID: 2744)
- Helper.exe (PID: 2568)
- ghjkl.exe (PID: 4056)
- 3322713636.exe (PID: 2488)
- ghjkl.exe (PID: 2660)
- cayV0Deo9jSt417.exe (PID: 2136)
- 96224645.exe (PID: 3020)
- plugins.exe (PID: 1848)
- Setup2010u32.exe (PID: 2864)
- mode.com (PID: 1348)
- CleanUp Icons FOP.exe (PID: 3212)
- IconRemoval.exe (PID: 2712)
- 7zipFOPBACKEND.exe (PID: 1316)
- RT2q.exe (PID: 3928)
- RT2q.exe (PID: 2540)
- may.exe (PID: 2068)
- may.tmp (PID: 3980)
- tpeinf.exe (PID: 1404)
- mpveasyplayer.exe (PID: 2712)
- SuburbansKamacite.exe (PID: 2660)
- hncc.exe (PID: 3944)
- dsdasda.exe (PID: 2360)
- v2.exe (PID: 4108)
- cp.exe (PID: 1408)
- 3238231219.exe (PID: 4140)
- pixxxxx.exe (PID: 4176)
- PluginFlash.exe (PID: 4184)
- mpveasyplayer.exe (PID: 3384)
- vbc.exe (PID: 4200)
- news_01.exe (PID: 4300)
- vbc.exe (PID: 4452)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- inte.exe (PID: 4496)
- 1234daisaaaaa.exe (PID: 4588)
- RegSvcs.exe (PID: 4684)
- ama.exe (PID: 4712)
- osminogs.exe (PID: 4820)
- lumma1234.exe (PID: 4828)
- RegAsm.exe (PID: 4892)
- v4install.exe (PID: 4944)
- InstallUtil.exe (PID: 5068)
- WatchDog.exe (PID: 5028)
- M5traider.exe (PID: 5164)
- GorgeousMovement.exe (PID: 5188)
- Accommodations.pif (PID: 5420)
- agentServerComponent.exe (PID: 5508)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- hv.exe (PID: 5648)
- syncUpd.exe (PID: 5668)
- 1230.exe (PID: 5720)
- i.exe (PID: 6044)
- Windows.exe (PID: 5980)
- EchoNavigator.exe (PID: 5776)
- RegSvcs.exe (PID: 5796)
- build6_unencrypted.exe (PID: 6060)
- MSI.CentralServer.exe (PID: 6140)
- ladas.exe (PID: 4396)
- zxcvb.exe (PID: 4788)
- fortnite3.exe (PID: 4952)
- xyodgsih.exe (PID: 3080)
- 2.3.1.1.exe (PID: 5228)
- vbc.exe (PID: 5212)
- native.exe (PID: 5276)
- soft.exe (PID: 1072)
- micro.exe (PID: 5004)
- native.exe (PID: 5396)
- LM.exe (PID: 5320)
- f88253a.exe (PID: 6108)
- cluton.exe (PID: 6116)
- cluton.exe (PID: 4188)
- soft.exe (PID: 3884)
- html.exe (PID: 2080)
- for.exe (PID: 5336)
- data64_5.exe (PID: 4856)
- Temp2.exe (PID: 4868)
- data64_5.exe (PID: 5348)
- 7e207560.exe (PID: 1888)
- net.exe (PID: 3076)
- asg.exe (PID: 5200)
- 7e207560.exe (PID: 5696)
- net.exe (PID: 1368)
- 7e207560.exe (PID: 5388)
- %E4%BA%94%E5%91%B3%E4%BC%A0%E5%A5%87.exe (PID: 4212)
- build3.exe (PID: 5016)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- build3.exe (PID: 2260)
- RegAsm.exe (PID: 3736)
- bott.exe (PID: 2968)
- uWVU7[5[).exe (PID: 1832)
- uWVU7[5[).exe (PID: 5988)
- pinguin.exe (PID: 5964)
- conhost.exe (PID: 4476)
- brg.exe (PID: 4216)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 4856)
- CheatLoader.exe (PID: 3336)
- Screensaver.exe (PID: 4380)
- mstsca.exe (PID: 4280)
- kehu.exe (PID: 2764)
- pei.exe (PID: 4104)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 4856)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 5812)
- TEST3.exe (PID: 5296)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 4324)
- 534219300.exe (PID: 2300)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 1924)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 3772)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 4856)
- AppLaunch.exe (PID: 5772)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 6172)
- Goldprime.exe (PID: 3084)
- Horpxuoxm.exe (PID: 1852)
- lve5.exe (PID: 6244)
- Gsoymaq.exe (PID: 6328)
- RegAsm.exe (PID: 6216)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 6252)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 6384)
- Gsoymaq.exe (PID: 6400)
- _VTI_CNF.exe (PID: 6460)
- National.exe (PID: 6644)
- 2014-06-12_djylh.exe (PID: 6764)
- server.exe (PID: 7020)
- LostArk.exe (PID: 6984)
- baseline.exe (PID: 7028)
- gookcom.exe (PID: 7276)
- ._cache_server.exe (PID: 7444)
- plink.exe (PID: 7036)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 7336)
- look2.exe (PID: 7492)
- HD_._cache_server.exe (PID: 7552)
- Synaptics.exe (PID: 7616)
- Horpxuoxm.exe (PID: 7692)
- abc.exe (PID: 7792)
- ghost.exe (PID: 7800)
- stale.exe (PID: 7812)
- look2.exe (PID: 7864)
- ghost.exe (PID: 7840)
- Temp1.exe (PID: 7872)
- VLTKNhatRac.exe (PID: 7964)
- MSBuild.exe (PID: 8060)
- dota.exe (PID: 8124)
- 5d3e8177e87cc.exe (PID: 6164)
- Winlock.exe (PID: 4312)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- adm_atu.exe (PID: 4568)
- NBYS%20AH.NET.exe (PID: 6664)
- 4c6358aa.exe (PID: 6172)
- amert.exe (PID: 6396)
- Recorder.exe (PID: 6744)
- april.exe (PID: 3356)
- chdyz.exe (PID: 2480)
- april.tmp (PID: 6852)
- Archevod_XWorm.exe (PID: 6812)
- Vpeswawqko.exe (PID: 7160)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 7404)
- RegAsm.exe (PID: 7516)
Reads Environment values
- 4363463463464363463463463.exe (PID: 3216)
- data64_6.exe (PID: 2340)
- Client.exe (PID: 2688)
- 666.exe (PID: 3404)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- jS-tD.exe (PID: 2060)
- npp.8.6.2.Installer.x64.exe (PID: 2064)
- STAR.exe (PID: 2444)
- reo.exe (PID: 2128)
- bott.exe (PID: 2332)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- Setup2010u32.exe (PID: 2864)
- IconRemoval.exe (PID: 2712)
- 7zipFOPBACKEND.exe (PID: 1316)
- RT2q.exe (PID: 2540)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 4480)
- agentServerComponent.exe (PID: 5508)
- Windows.exe (PID: 5980)
- Temp2.exe (PID: 4868)
- InstallUtil.exe (PID: 5068)
- data64_5.exe (PID: 5348)
- asg.exe (PID: 5200)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- uWVU7[5[).exe (PID: 5988)
- bott.exe (PID: 2968)
- kehu.exe (PID: 2764)
- RegAsm.exe (PID: 6216)
- 2014-06-12_djylh.exe (PID: 6764)
- LostArk.exe (PID: 6984)
- Horpxuoxm.exe (PID: 7692)
Reads the software policy settings
- data64_6.exe (PID: 2340)
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- 666.exe (PID: 3404)
- WeChat.exe (PID: 3060)
- Helper.exe (PID: 2568)
- msiexec.exe (PID: 1584)
- InstallUtil.exe (PID: 5068)
Create files in a temporary directory
- asdfg.exe (PID: 2408)
- Client.exe (PID: 2688)
- 4363463463464363463463463.exe (PID: 2424)
- npp.exe (PID: 3920)
- npp86Installerx64.exe (PID: 1972)
- 2591814628.exe (PID: 3732)
- Setup2010u32.exe (PID: 2864)
- CleanUp Icons FOP.exe (PID: 3212)
- may.tmp (PID: 3980)
- may.exe (PID: 2068)
- tpeinf.exe (PID: 1404)
- vbc.exe (PID: 4200)
- v2.exe (PID: 4108)
- GorgeousMovement.exe (PID: 5188)
- cp.exe (PID: 1408)
- univ.exe (PID: 3440)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 5536)
- EchoNavigator.exe (PID: 5776)
- cluton.exe (PID: 6116)
- jsc.exe (PID: 3684)
- conhost.exe (PID: 4476)
- pei.exe (PID: 4104)
- 2014-06-12_djylh.exe (PID: 6764)
- LostArk.exe (PID: 6984)
- ._cache_server.exe (PID: 7444)
- stale.exe (PID: 7812)
- Synaptics.exe (PID: 7616)
- Winlock.exe (PID: 4312)
- adm_atu.exe (PID: 4568)
- april.exe (PID: 3356)
Creates files or folders in the user directory
- Client.exe (PID: 2688)
- BBLb.exe (PID: 2440)
- npp.exe (PID: 3920)
- dialer.exe (PID: 2000)
- RegAsm.exe (PID: 3684)
- STAR.exe (PID: 2444)
- 2591814628.exe (PID: 3732)
- univ.exe (PID: 3440)
- first.exe (PID: 696)
- Helper.exe (PID: 2568)
- dialer.exe (PID: 1352)
- may.tmp (PID: 3980)
- PluginFlash.exe (PID: 4184)
- v4install.exe (PID: 4944)
- inte.exe (PID: 4496)
- InstallUtil.exe (PID: 5068)
- Accommodations.pif (PID: 5420)
- cluton.exe (PID: 4188)
- dllhost.exe (PID: 4812)
- asg.exe (PID: 5200)
- hv.exe (PID: 5648)
- RegAsm.exe (PID: 3736)
- build3.exe (PID: 2260)
- dialer.exe (PID: 6000)
- conhost.exe (PID: 4476)
- _VTI_CNF.exe (PID: 6460)
- 2014-06-12_djylh.exe (PID: 6764)
- LostArk.exe (PID: 6984)
- Horpxuoxm.exe (PID: 1852)
- Winlock.exe (PID: 4312)
- Horpxuoxm.exe (PID: 7692)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2760)
- 4363463463464363463463463.exe (PID: 2516)
- 4363463463464363463463463.exe (PID: 2424)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3256)
Checks proxy server information
- npp.exe (PID: 3920)
- jS-tD.exe (PID: 2060)
- Journal.exe (PID: 2504)
- 2591814628.exe (PID: 3732)
- univ.exe (PID: 3440)
- 3322713636.exe (PID: 2488)
- RT2q.exe (PID: 2540)
- tpeinf.exe (PID: 1404)
- inte.exe (PID: 4496)
- InstallUtil.exe (PID: 5068)
- syncUpd.exe (PID: 5668)
- 1230.exe (PID: 5720)
- 2.3.1.1.exe (PID: 5228)
- fortnite3.exe (PID: 4952)
- Accommodations.pif (PID: 5420)
- 7e207560.exe (PID: 1888)
- MSI.CentralServer.exe (PID: 6140)
- uWVU7[5[).exe (PID: 5988)
- pei.exe (PID: 4104)
- _VTI_CNF.exe (PID: 6460)
- 2014-06-12_djylh.exe (PID: 6764)
- baseline.exe (PID: 7028)
- plink.exe (PID: 7036)
- mpveasyplayer.exe (PID: 3384)
- 2-3-1_2023-12-14_13-35.exe (PID: 6116)
- Winlock.exe (PID: 4312)
Drops the executable file immediately after the start
- dialer.exe (PID: 2000)
- dialer.exe (PID: 1352)
- dllhost.exe (PID: 4812)
- dialer.exe (PID: 6000)
Reads product name
- jS-tD.exe (PID: 2060)
- STAR.exe (PID: 2444)
- bott.exe (PID: 2332)
- Setup2010u32.exe (PID: 2864)
- RT2q.exe (PID: 2540)
- agentServerComponent.exe (PID: 5508)
- InstallUtil.exe (PID: 5068)
- jsc.exe (PID: 3684)
- STAR.exe (PID: 6116)
- uWVU7[5[).exe (PID: 5988)
- bott.exe (PID: 2968)
- kehu.exe (PID: 2764)
- RegAsm.exe (PID: 6216)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1584)
Creates a software uninstall entry
- may.tmp (PID: 3980)
Creates files in the program directory
- mpveasyplayer.exe (PID: 2712)
- 7e207560.exe (PID: 1888)
- mpveasyplayer.exe (PID: 3384)
- lve5.exe (PID: 6244)
- server.exe (PID: 7020)
- abc.exe (PID: 7792)
Reads mouse settings
- Accommodations.pif (PID: 5420)
Process checks whether UAC notifications are on
- brg.exe (PID: 4216)
- LostArk.exe (PID: 6984)
Reads CPU info
- lve5.exe (PID: 6244)
- HD_._cache_server.exe (PID: 7552)
Dropped object may contain TOR URL's
- abc.exe (PID: 7792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3404) 666.exe
C2 (3)127.0.0.1
qiefuwuqi.20242525.xyz
175.24.197.196
Ports (1)53576
BotnetDefault
VersionLMTEAM RAT 远控 v10.0.0
Options
AutoRuntrue
Mutexencffhopetwiqlwo
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICNzCCAaCgAwIBAgIVAJ63XcWUSwHUfcXzH/xfUvbn7AsDMA0GCSqGSIb3DQEBDQUAMGgxFjAUBgNVBAMMDUxNVEVBTSBTZXJ2ZXIxEzARBgNVBAsMCnF3cWRhbmNodW4xHzAdBgNVBAoMFlZlbm9tUkFUIEJ5IHF3cWRhbmNodW4xCzAJBgNVBAcMAlNIMQswCQYDVQQGEwJDTjAeFw0yMjA4MjYwOTI0NTBaFw0zMzA2MDQwOTI0NTBaMBMxETAPBgNVBAMMCFZlbm9tUkFUMIGfMA0GCSqGSIb3DQEB...
Server_SignatureKWBGGJAAfUXEt4htszXVxNx6rIZYwNWWTPactiBeZQI02tJn/heGesmMrlvcl5TCgrFBPEXT+LY1evi6tKfAJojHRJxMJiCIuzuMLzZSFCXL+/1Tyic+u3d8BgIkZqFG02uBHURbw0FGvZcH4r1o7kJhIyHsUGw9ZBrY5ZjdYXs=
Keys
AES2b84f4b7ac2be24e77cb2c2a6f70cd0327feb801dbd467a427d95e614f77912a
SaltVenomRATByVenom
(PID) Process(2128) reo.exe
C2 (1)82.115.223.244
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexfnpxcekdvtg
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureR5JBH2qOF7T5fwa7g4eE4qJ0CTWyADGjVvVqEpZLxqOz7ijIknIV9ddo6ba7ZkTKoBhHhGTgyJ6VkPBFfLs2Z002xZYx/yjole+Ba20yb0ZFTo0rvIGTC2W07sVYXYuBPDufInu02QMD/V3ZMybsQNohmDOnbjhQMcN3WkLsCWY=
Keys
AES3a20c7b13b8c19efdcfc7fdc4d6ed716151cf871d53115133cc297be7f298f08
SaltVenomRATByVenom
XWorm
(PID) Process(696) first.exe
C291.92.249.37:9049
Keys
AES5548
Options
Splitter<Agent>
USB drop name
MutexaMtkXNimPlkESDx9
(PID) Process(6060) build6_unencrypted.exe
C2163.5.215.245:9049
Keys
AESNk227ETNaBDg!
Options
Splitter<Agent>
USB drop name
Mutexr3SLo8kx59hai6gX
RedLine
(PID) Process(4108) v2.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
(PID) Process(4684) RegSvcs.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
(PID) Process(5212) vbc.exe
C2 (1)91.92.244.55:13002
BotnetEmpressLogs
Options
ErrorMessage
Keys
XorTeemed
LokiBot
(PID) Process(4188) cluton.exe
C2http://bauxx.xyz/mtk1/w2/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
474
Monitored processes
309
Malicious processes
104
Suspicious processes
30
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Users\admin\Desktop\Files\first.exe" | C:\Users\admin\Desktop\Files\first.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
XWorm(PID) Process(696) first.exe C291.92.249.37:9049 Keys AES5548 Options Splitter<Agent> USB drop name MutexaMtkXNimPlkESDx9 | |||||||||||||||
| 840 | powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAOwAgAEEAZABkAC0ATQBwAFAAcgBlAGYAZQByAGUAbgBjAGUAIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAcgBvAGMAZQBzAHMAIABBAHQAdAByAGkAYgB1AHQAZQBTAHQAcgBpAG4AZwAuAGUAeABlADsA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 920 | powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAOwAgAEEAZABkAC0ATQBwAFAAcgBlAGYAZQByAGUAbgBjAGUAIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAcgBvAGMAZQBzAHMAIABBAHQAdAByAGkAYgB1AHQAZQBTAHQAcgBpAG4AZwAuAGUAeABlADsA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\Desktop\Files\ed.exe" | C:\Users\admin\Desktop\Files\ed.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Mileages Integrity Level: HIGH Description: Leftwards Gran Sensationally Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\Desktop\Files\soft.exe" | C:\Users\admin\Desktop\Files\soft.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1112 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmp1587.tmp.bat"" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1196 | C:\Windows\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\is64.bat | C:\Windows\System32\cmd.exe | — | CleanUp Icons FOP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\Files\svchost.exe" | C:\Users\admin\Desktop\Files\svchost.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Intel Integrity Level: HIGH Description: Intel® Driver & Support Assistant Exit code: 3221225477 Version: 23.4.39.9 Modules
| |||||||||||||||
| 1316 | C:\Windows\system32\cmd.exe /c mode con:cols=0080 lines=0025 | C:\Windows\System32\cmd.exe | — | CleanUp Icons FOP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1316 | "C:\Users\admin\AppData\Local\Temp\AITMP0\7zipFOPBACKEND.exe" /s %1 | C:\Users\admin\AppData\Local\Temp\AITMP0\7zipFOPBACKEND.exe | — | Setup2010u32.exe | |||||||||||
User: admin Integrity Level: HIGH Description: 7zip FOP backend Data Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
478 705
Read events
360 166
Write events
118 275
Delete events
264
Modification events
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
585
Suspicious files
174
Text files
329
Unknown types
106
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\gzz.exe | executable | |
MD5:7D9C852903DE2A824AA3F80DD1AB2B89 | SHA256:A777C77555A33B8263F836C5A029047FDEB74FD1F9ABB69D0B8F2A2B3D572583 | |||
| 2440 | BBLb.exe | C:\Users\admin\AppData\Local\TypeId\bcfsmn\AttributeString.exe | executable | |
MD5:71EB1BC6E6DA380C1CB552D78B391B2A | SHA256:CEFA92EE6CC2FAD86C49DD37D57FF8AFCB9B9ABEF0A110689E6D771394256BD6 | |||
| 2408 | asdfg.exe | C:\Users\admin\AppData\Local\Temp\BBLb.exe | executable | |
MD5:71EB1BC6E6DA380C1CB552D78B391B2A | SHA256:CEFA92EE6CC2FAD86C49DD37D57FF8AFCB9B9ABEF0A110689E6D771394256BD6 | |||
| 2688 | Client.exe | C:\Users\admin\AppData\Roaming\MyData\DataLogs.conf | text | |
MD5:CF759E4C5F14FE3EEC41B87ED756CEA8 | SHA256:C9F9F193409217F73CC976AD078C6F8BF65D3AABCF5FAD3E5A47536D47AA6761 | |||
| 840 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF182a37.TMP | binary | |
MD5:0268C3470C936E6FBAC2945B9E1C2099 | SHA256:DF2AF58E8879B48826D8A418ED3B02CC8D484BCFC231C5B7A11BD153ED3998E9 | |||
| 840 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zwkzrqzn.x50.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 840 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 2424 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:61E37C50B6F6779DB2119FB22AECA6E2 | SHA256:A6B67F3C8FA8212520E1F569A9D8783503B34C73EAAA4BD3EB2FF53DC7270D4B | |||
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\data64_6.exe | executable | |
MD5:D0D5020D6C7CB8142CF4970B3882AFFC | SHA256:08FA07C28724CB7A64F936EFA29B42446786F4A8F40DC311DD1BD5F3FE8D704A | |||
| 2424 | 4363463463464363463463463.exe | C:\Users\admin\AppData\Local\Temp\Tar35C2.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
243
TCP/UDP connections
655
DNS requests
116
Threats
817
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3216 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://marksidfgs.ug/asdfg.exe | unknown | executable | 2.13 Mb | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 47.99.151.68:1302 | http://47.99.151.68:1302/gzz.exe | unknown | executable | 327 Kb | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 154.92.15.189:80 | http://ji.alie3ksgff.com/ef/rty27.exe | unknown | executable | 715 Kb | unknown |
2588 | 4363463463464363463463463.exe | GET | 200 | 20.169.49.77:80 | http://20.169.49.77/gpupdate.exe | unknown | executable | 1.56 Mb | unknown |
1956 | 4363463463464363463463463.exe | GET | 200 | 185.234.216.64:8000 | http://185.234.216.64:8000/Posh_v4_dropper_x64.exe | unknown | executable | 264 Kb | unknown |
2424 | 4363463463464363463463463.exe | GET | 200 | 62.109.150.108:80 | http://starozitnictvi-znojmo.cz/ed.exe | unknown | executable | 748 Kb | unknown |
2588 | 4363463463464363463463463.exe | GET | 200 | 188.114.97.3:80 | http://walkinglate.com/w/w-12.exe | unknown | executable | 3.32 Mb | unknown |
2424 | 4363463463464363463463463.exe | GET | 200 | 184.24.77.206:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2ce8919ccf05c243 | unknown | compressed | 65.2 Kb | unknown |
1956 | 4363463463464363463463463.exe | GET | 200 | 82.157.254.217:8080 | http://82.157.254.217:8080/WeChat.exe | unknown | executable | 1.85 Mb | unknown |
2424 | 4363463463464363463463463.exe | GET | 200 | 31.41.244.146:80 | http://31.41.244.146/Downnnnloads/laplas03.exe | unknown | executable | 4.30 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3216 | 4363463463464363463463463.exe | 47.99.151.68:1302 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3216 | 4363463463464363463463463.exe | 68.66.226.93:80 | thedoctorsgym.net | A2HOSTING | US | unknown |
3216 | 4363463463464363463463463.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
2340 | data64_6.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
3216 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
3216 | 4363463463464363463463463.exe | 91.215.85.223:80 | marksidfgs.ug | — | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
thedoctorsgym.net |
| unknown |
github.com |
| shared |
api.telegram.org |
| shared |
raw.githubusercontent.com |
| shared |
marksidfgs.ug |
| unknown |
ji.alie3ksgff.com |
| malicious |
pastratas.ac.ug |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
pouya.blob.core.windows.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3216 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1080 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2340 | data64_6.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
93 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
WeChat.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2010 Oreans Technologies ---
------------------------------------------------
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|