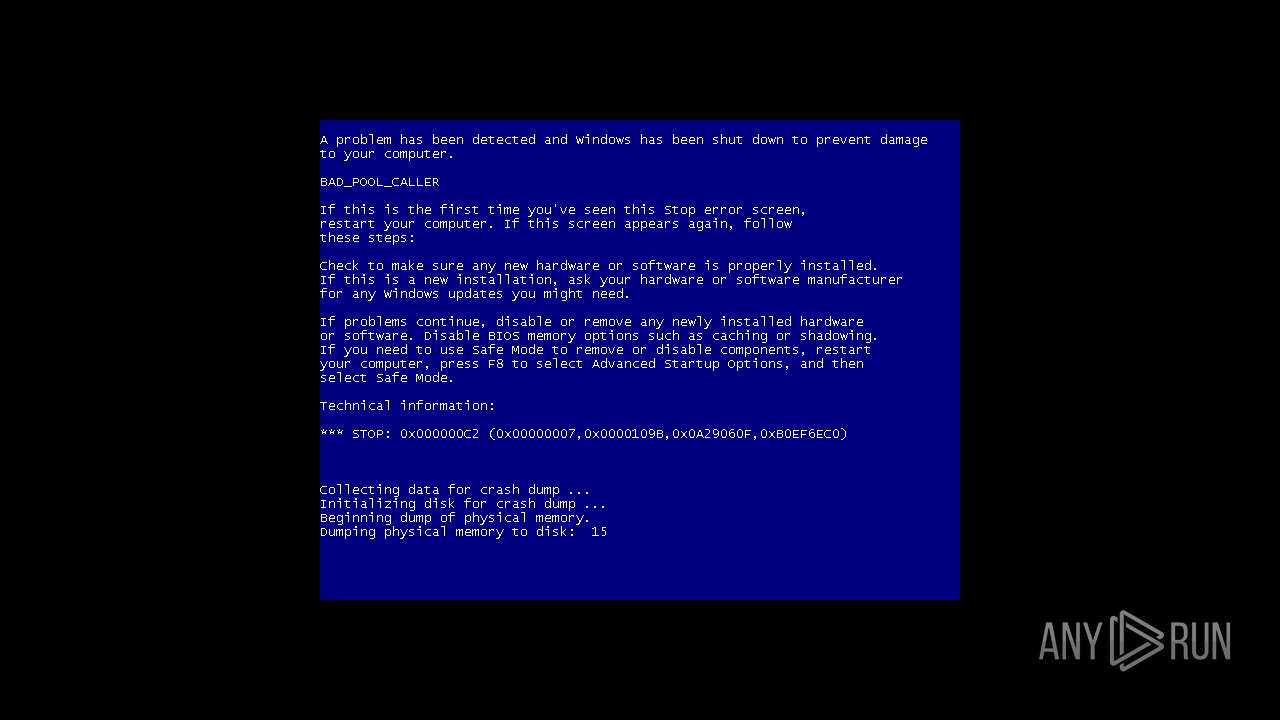
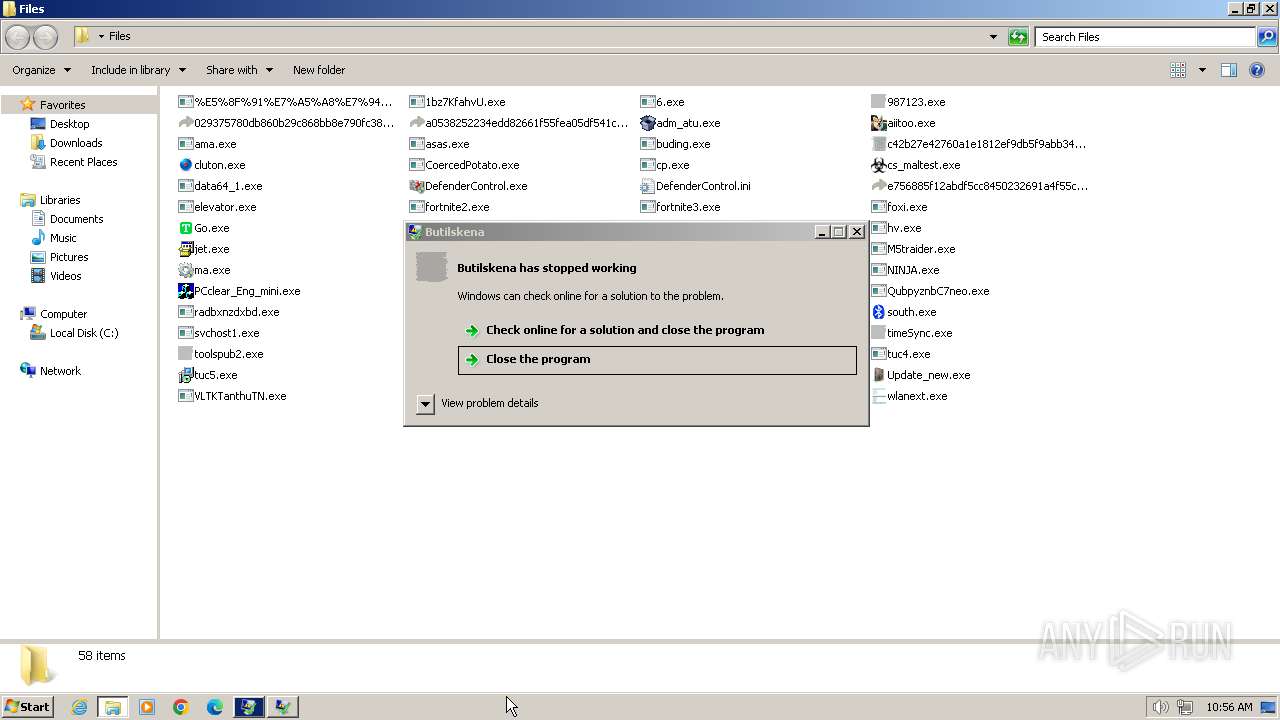
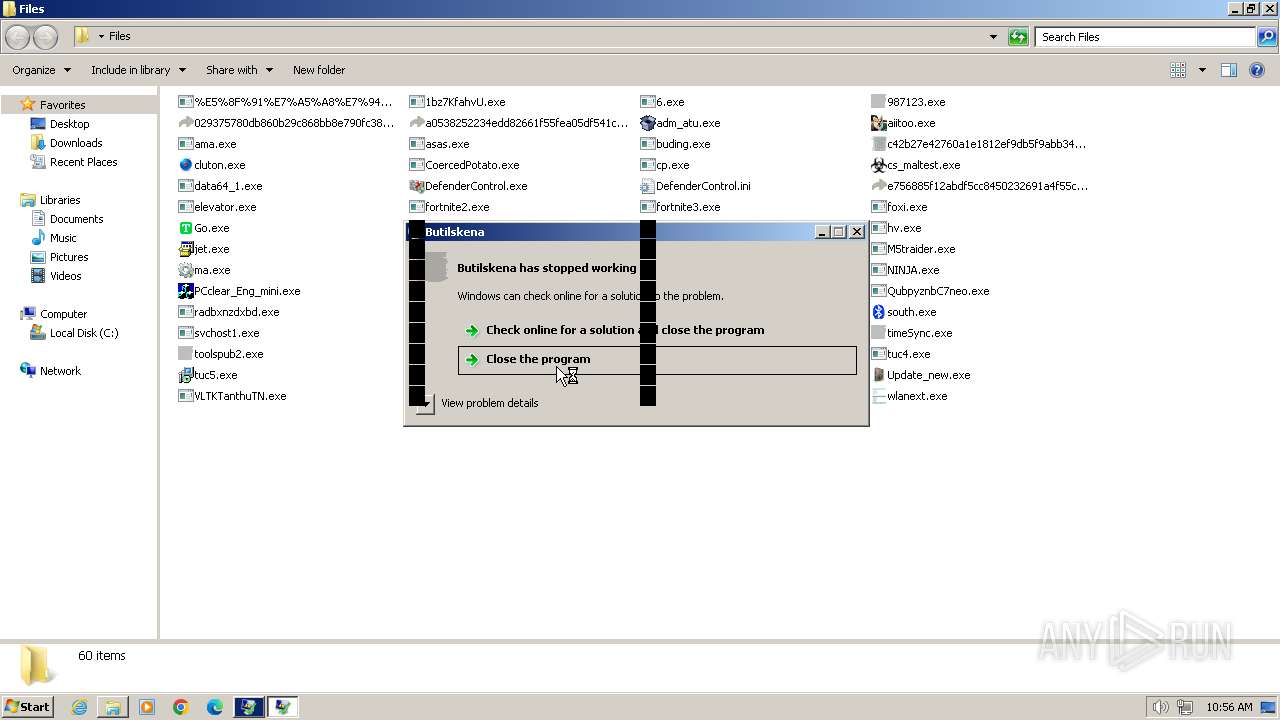
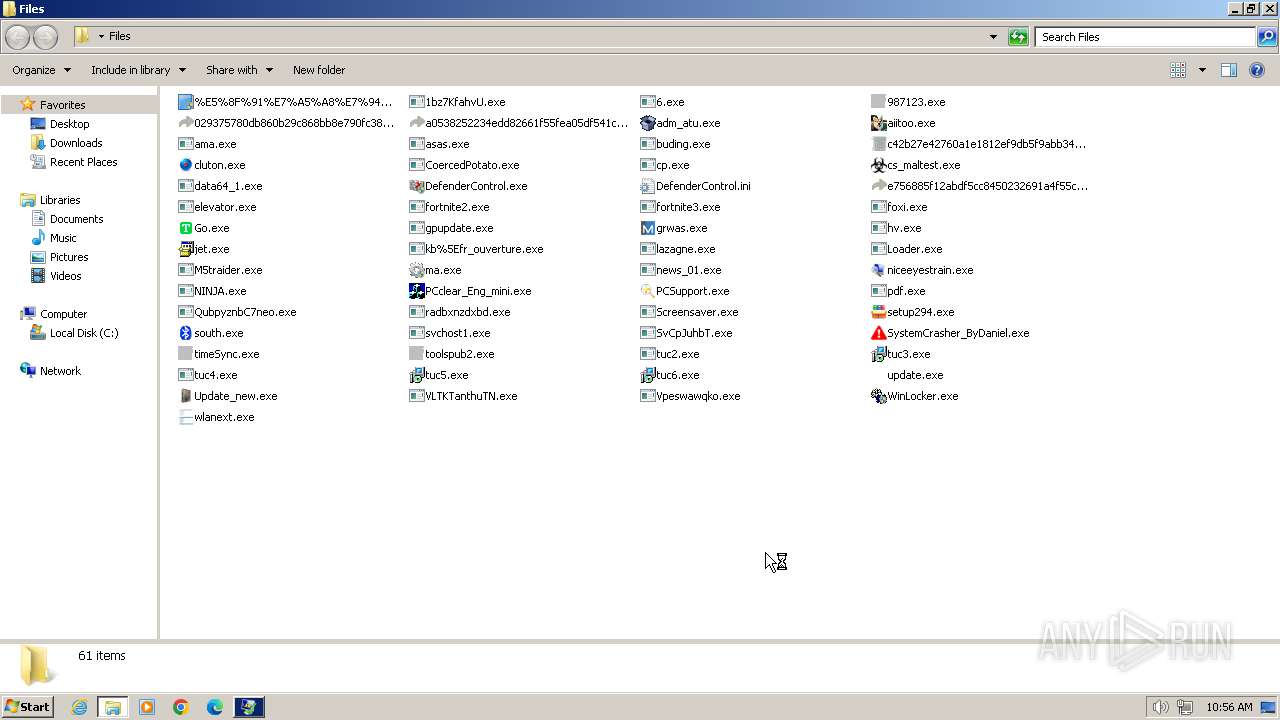
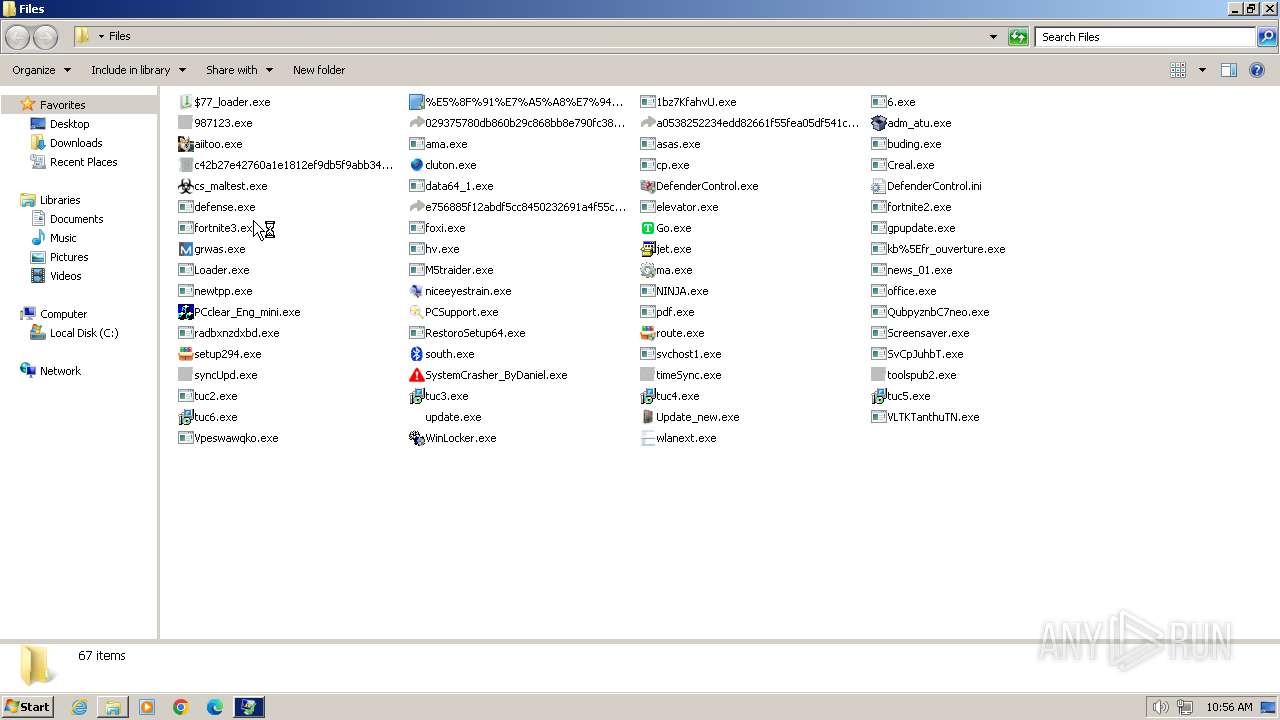
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/5a4d9bd5-e1dd-45fd-8065-b4cfb42fe4bc |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | December 31, 2023, 10:54:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2064)
Steals credentials from Web Browsers
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
Actions looks like stealing of personal data
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
- 1701610814-Dvnzfr.exe (PID: 1020)
Lokibot is detected
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
Registers / Runs the DLL via REGSVR32.EXE
- setup294.exe (PID: 3548)
Detected an obfuscated command line used with Guloader
- powershell.exe (PID: 2960)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3624)
Adds path to the Windows Defender exclusion list
- savesinto.exe (PID: 2516)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2808)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 3672)
- sipnotify.exe (PID: 1940)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 3244)
- Vpeswawqko.exe (PID: 3864)
- Update_new.exe (PID: 3856)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 2532)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 1932)
- timeSync.exe (PID: 3032)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3672)
- WinLocker.exe (PID: 3868)
- PCclear_Eng_mini.exe (PID: 124)
- 4363463463464363463463463.exe (PID: 2808)
- fortnite3.exe (PID: 1860)
- CasPol.exe (PID: 2972)
- cluton.exe (PID: 2776)
- 2MC2787.exe (PID: 3032)
- sipnotify.exe (PID: 1940)
- 4363463463464363463463463.exe (PID: 2532)
- runonce.exe (PID: 2140)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3000)
- setup294.exe (PID: 3548)
- Vpeswawqko.exe (PID: 3864)
- wlanext.exe (PID: 3828)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E7%BB%88%E7%AB%AF_sos.exe (PID: 3964)
- syncUpd.exe (PID: 2756)
- data64_1.exe (PID: 3672)
- route.exe (PID: 3312)
- wscript.exe (PID: 3624)
- sysplorsv.exe (PID: 1932)
- conhost.exe (PID: 2544)
- Update_new.exe (PID: 3856)
Starts CMD.EXE for commands execution
- WinLocker.exe (PID: 3868)
- wscript.exe (PID: 3624)
- conhost.exe (PID: 2544)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4064)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4064)
Creates or modifies Windows services
- lve.exe (PID: 3860)
- Vnloubk.exe (PID: 1984)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 4064)
Reads the Windows owner or organization settings
- tuc6.tmp (PID: 3244)
- tuc4.tmp (PID: 2628)
Reads Mozilla Firefox installation path
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
Loads DLL from Mozilla Firefox
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
Accesses Microsoft Outlook profiles
- cluton.exe (PID: 2776)
- south.exe (PID: 3952)
Executing commands from a ".bat" file
- WinLocker.exe (PID: 3868)
- wscript.exe (PID: 3624)
- conhost.exe (PID: 2544)
Starts POWERSHELL.EXE for commands execution
- wlanext.exe (PID: 3828)
- powershell.exe (PID: 3928)
- savesinto.exe (PID: 2516)
Reads the BIOS version
- Update_new.exe (PID: 3856)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 3244)
- savesinto.exe (PID: 2516)
Base64-obfuscated command line is found
- powershell.exe (PID: 3928)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3624)
The process executes VB scripts
- pdf.exe (PID: 2732)
The process checks if it is being run in the virtual environment
- regsvr32.exe (PID: 3588)
Script adds exclusion path to Windows Defender
- savesinto.exe (PID: 2516)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2808)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2860)
- timeSync.exe (PID: 3032)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3672)
- jet.exe (PID: 2108)
- PCSupport.exe (PID: 3836)
- lve.exe (PID: 3860)
- Vnloubk.exe (PID: 3780)
- WinLocker.exe (PID: 3868)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 3912)
- PCclear_Eng_mini.exe (PID: 124)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 764)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 1900)
- cs_maltest.exe (PID: 2760)
- Screensaver.exe (PID: 2724)
- Vnloubk.exe (PID: 2056)
- fortnite3.exe (PID: 1860)
- CasPol.exe (PID: 2972)
- DefenderControl.exe (PID: 2492)
- QubpyznbC7neo.exe (PID: 2376)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 1644)
- javararplugin.exe (PID: 3096)
- tuc6.exe (PID: 3308)
- tuc6.tmp (PID: 3244)
- javararplugin.exe (PID: 3056)
- cluton.exe (PID: 2812)
- cluton.exe (PID: 2776)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 3436)
- aiitoo.exe (PID: 3648)
- winvnc.exe (PID: 3500)
- foxi.exe (PID: 2640)
- XK8El19.exe (PID: 3620)
- XK1qf04.exe (PID: 2496)
- 2MC2787.exe (PID: 3032)
- 5WI7gh8.exe (PID: 864)
- Vnloubk.exe (PID: 1984)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 552)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3132)
- wmpnscfg.exe (PID: 3428)
- setup294.exe (PID: 3548)
- wmpnscfg.exe (PID: 3376)
- wmpnscfg.exe (PID: 3492)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 3612)
- data64_1.exe (PID: 3672)
- toolspub2.exe (PID: 3632)
- 987123.exe (PID: 3688)
- toolspub2.exe (PID: 3620)
- wlanext.exe (PID: 3828)
- Update_new.exe (PID: 3856)
- Vpeswawqko.exe (PID: 3864)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 3700)
- south.exe (PID: 3804)
- fortnite2.exe (PID: 3812)
- south.exe (PID: 3952)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E7%BB%88%E7%AB%AF_sos.exe (PID: 3964)
- newtpp.exe (PID: 2184)
- tuc4.exe (PID: 2032)
- tuc4.tmp (PID: 2628)
- syncUpd.exe (PID: 2756)
- kb%5Efr_ouverture.exe (PID: 4080)
- sysplorsv.exe (PID: 1932)
- route.exe (PID: 3312)
- pdf.exe (PID: 2732)
- savesinto.exe (PID: 2516)
- vbc.exe (PID: 2504)
- defense.exe (PID: 3764)
- qt51crk.exe (PID: 3844)
- conhost.exe (PID: 2544)
- 1701610814-Dvnzfr.exe (PID: 1020)
- ransom_builder.exe (PID: 2860)
- l.exe (PID: 2848)
- javararplugin.exe (PID: 2172)
- south.exe (PID: 2472)
- RestoroSetup64.exe (PID: 1712)
- tuc7.exe (PID: 4092)
- 659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe (PID: 1980)
- javararplugin.exe (PID: 1812)
- T1_Net.exe (PID: 4152)
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2436)
- jet.exe (PID: 2108)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- WinLocker.exe (PID: 3868)
- lve.exe (PID: 3860)
- 4363463463464363463463463.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 3116)
- tuc6.tmp (PID: 3244)
- tuc6.exe (PID: 3308)
- javararplugin.exe (PID: 3096)
- cluton.exe (PID: 2812)
- 4363463463464363463463463.exe (PID: 1596)
- PCSupport.exe (PID: 3836)
- XK8El19.exe (PID: 3620)
- XK1qf04.exe (PID: 2496)
- foxi.exe (PID: 2640)
- 4363463463464363463463463.exe (PID: 2532)
- setup294.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 3244)
- tuc4.exe (PID: 2032)
- tuc4.tmp (PID: 2628)
- newtpp.exe (PID: 2184)
- route.exe (PID: 3312)
- south.exe (PID: 3952)
- savesinto.exe (PID: 2516)
- conhost.exe (PID: 2544)
- javararplugin.exe (PID: 2172)
- 4363463463464363463463463.exe (PID: 3000)
- tuc7.exe (PID: 4092)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2808)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 1932)
- timeSync.exe (PID: 3032)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3672)
- PCSupport.exe (PID: 3836)
- lve.exe (PID: 3860)
- WinLocker.exe (PID: 3868)
- Vnloubk.exe (PID: 3780)
- PCclear_Eng_mini.exe (PID: 124)
- Vnloubk.exe (PID: 2056)
- fortnite3.exe (PID: 1860)
- QubpyznbC7neo.exe (PID: 2376)
- CasPol.exe (PID: 2972)
- DefenderControl.exe (PID: 2492)
- tuc6.tmp (PID: 3244)
- javararplugin.exe (PID: 3096)
- cluton.exe (PID: 2812)
- winvnc.exe (PID: 3500)
- cluton.exe (PID: 2776)
- 2MC2787.exe (PID: 3032)
- Vnloubk.exe (PID: 1984)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3132)
- wmpnscfg.exe (PID: 3492)
- setup294.exe (PID: 3548)
- wmpnscfg.exe (PID: 3376)
- wmpnscfg.exe (PID: 3428)
- wlanext.exe (PID: 3828)
- Vpeswawqko.exe (PID: 3864)
- Update_new.exe (PID: 3856)
- tuc4.tmp (PID: 2628)
- syncUpd.exe (PID: 2756)
- kb%5Efr_ouverture.exe (PID: 4080)
- data64_1.exe (PID: 3672)
- south.exe (PID: 3952)
- pdf.exe (PID: 2732)
- savesinto.exe (PID: 2516)
- route.exe (PID: 3312)
- sysplorsv.exe (PID: 1932)
- defense.exe (PID: 3764)
- vbc.exe (PID: 2504)
- l.exe (PID: 2848)
- conhost.exe (PID: 2544)
- 1701610814-Dvnzfr.exe (PID: 1020)
- javararplugin.exe (PID: 2172)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E7%BB%88%E7%AB%AF_sos.exe (PID: 3964)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 1932)
- timeSync.exe (PID: 3032)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2808)
- PCclear_Eng_mini.exe (PID: 124)
- 4363463463464363463463463.exe (PID: 2436)
- fortnite3.exe (PID: 1860)
- QubpyznbC7neo.exe (PID: 2376)
- CasPol.exe (PID: 2972)
- cluton.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 3244)
- Vpeswawqko.exe (PID: 3864)
- Update_new.exe (PID: 3856)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E7%BB%88%E7%AB%AF_sos.exe (PID: 3964)
- syncUpd.exe (PID: 2756)
- south.exe (PID: 3952)
- data64_1.exe (PID: 3672)
- pdf.exe (PID: 2732)
- vbc.exe (PID: 2504)
- defense.exe (PID: 3764)
- savesinto.exe (PID: 2516)
- sysplorsv.exe (PID: 1932)
- 1701610814-Dvnzfr.exe (PID: 1020)
- l.exe (PID: 2848)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 2100)
- 4363463463464363463463463.exe (PID: 2808)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 3244)
- Vpeswawqko.exe (PID: 3864)
- savesinto.exe (PID: 2516)
- Update_new.exe (PID: 3856)
- 1701610814-Dvnzfr.exe (PID: 1020)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 1596)
- 4363463463464363463463463.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2668)
- 4363463463464363463463463.exe (PID: 2296)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 1748)
- 4363463463464363463463463.exe (PID: 2560)
- 4363463463464363463463463.exe (PID: 2808)
- 4363463463464363463463463.exe (PID: 2452)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 2508)
- 4363463463464363463463463.exe (PID: 2860)
- 4363463463464363463463463.exe (PID: 948)
- 4363463463464363463463463.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2676)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2768)
- 4363463463464363463463463.exe (PID: 3496)
- 4363463463464363463463463.exe (PID: 3672)
- 4363463463464363463463463.exe (PID: 2812)
- 4363463463464363463463463.exe (PID: 2100)
- runonce.exe (PID: 2140)
- 4363463463464363463463463.exe (PID: 2456)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2736)
- 4363463463464363463463463.exe (PID: 2620)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 2956)
- 4363463463464363463463463.exe (PID: 3000)
- 4363463463464363463463463.exe (PID: 2848)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3208)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3084)
- 4363463463464363463463463.exe (PID: 3132)
- wmpnscfg.exe (PID: 3492)
- wmpnscfg.exe (PID: 3428)
- wmpnscfg.exe (PID: 3376)
Checks proxy server information
- timeSync.exe (PID: 3032)
- PCclear_Eng_mini.exe (PID: 124)
- %E5%8F%91%E7%A5%A8%E7%94%B5%E8%84%91%E7%89%88-%E7%BB%88%E7%AB%AF_sos.exe (PID: 3964)
- syncUpd.exe (PID: 2756)
- fortnite3.exe (PID: 1860)
- data64_1.exe (PID: 3672)
- sysplorsv.exe (PID: 1932)
Create files in a temporary directory
- jet.exe (PID: 2108)
- DefenderControl.exe (PID: 2492)
- tuc6.exe (PID: 3308)
- tuc6.tmp (PID: 3244)
- 4363463463464363463463463.exe (PID: 1596)
- cluton.exe (PID: 2812)
- foxi.exe (PID: 2640)
- XK8El19.exe (PID: 3620)
- XK1qf04.exe (PID: 2496)
- WerFault.exe (PID: 2176)
- setup294.exe (PID: 3548)
- 4363463463464363463463463.exe (PID: 2532)
- wlanext.exe (PID: 3828)
- tuc4.tmp (PID: 2628)
- tuc4.exe (PID: 2032)
- tuc7.exe (PID: 4092)
Creates files in the program directory
- lve.exe (PID: 3860)
- tuc6.tmp (PID: 3244)
- javararplugin.exe (PID: 3096)
- tuc4.tmp (PID: 2628)
- savesinto.exe (PID: 2516)
- javararplugin.exe (PID: 2172)
Creates files or folders in the user directory
- PCSupport.exe (PID: 3836)
- CasPol.exe (PID: 2972)
- cluton.exe (PID: 2776)
- wlanext.exe (PID: 3828)
- south.exe (PID: 3952)
Executes as Windows Service
- Vnloubk.exe (PID: 3780)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 3296)
- tuc6.tmp (PID: 3244)
- foxi.exe (PID: 2640)
- XK8El19.exe (PID: 3620)
- 4363463463464363463463463.exe (PID: 3244)
- tuc4.tmp (PID: 2628)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 3116)
- 4363463463464363463463463.exe (PID: 2436)
- 4363463463464363463463463.exe (PID: 2592)
- PCSupport.exe (PID: 3836)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 3244)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2888)
- 4363463463464363463463463.exe (PID: 3000)
Connects to the CnC server
- timeSync.exe (PID: 3032)
- lve.exe (PID: 3860)
- Vnloubk.exe (PID: 1984)
- syncUpd.exe (PID: 2756)
- sysplorsv.exe (PID: 1932)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 3296)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2656)
- 4363463463464363463463463.exe (PID: 3244)
- sysplorsv.exe (PID: 1932)
Application launched itself
- Vnloubk.exe (PID: 3780)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 3912)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 764)
- cluton.exe (PID: 2812)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 1644)
- msedge.exe (PID: 3232)
- msedge.exe (PID: 1628)
- msedge.exe (PID: 3188)
- WerFault.exe (PID: 2168)
- toolspub2.exe (PID: 3620)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 3612)
- south.exe (PID: 3804)
- powershell.exe (PID: 3928)
STEALC has been detected (SURICATA)
- timeSync.exe (PID: 3032)
- syncUpd.exe (PID: 2756)
Reads CPU info
- lve.exe (PID: 3860)
- Vnloubk.exe (PID: 1984)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 3296)
- lve.exe (PID: 3860)
- Screensaver.exe (PID: 2724)
- CasPol.exe (PID: 2972)
- Vnloubk.exe (PID: 1984)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2772)
- Update_new.exe (PID: 3856)
- vbc.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 2888)
- sysplorsv.exe (PID: 1932)
- 4363463463464363463463463.exe (PID: 3244)
Process checks are UAC notifies on
- CasPol.exe (PID: 2972)
- Update_new.exe (PID: 3856)
Reads mouse settings
- DefenderControl.exe (PID: 2492)
- 2MC2787.exe (PID: 3032)
- ransom_builder.exe (PID: 2860)
Drops 7-zip archiver for unpacking
- tuc6.tmp (PID: 3244)
- tuc4.tmp (PID: 2628)
- conhost.exe (PID: 2544)
PURPLEFOX has been detected (SURICATA)
- lve.exe (PID: 3860)
- Vnloubk.exe (PID: 1984)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1940)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1940)
- ctfmon.exe (PID: 1920)
Reads the time zone
- runonce.exe (PID: 2140)
Drop NetSupport executable file
- 4363463463464363463463463.exe (PID: 2532)
Starts itself from another location
- newtpp.exe (PID: 2184)
Changes the registry key values via Powershell
- powershell.exe (PID: 3928)
Reads product name
- savesinto.exe (PID: 2516)
Unusual connection from system programs
- vbc.exe (PID: 2504)
Executed via WMI
- schtasks.exe (PID: 2520)
- schtasks.exe (PID: 3956)
- schtasks.exe (PID: 2328)
- schtasks.exe (PID: 996)
- schtasks.exe (PID: 2260)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 4048)
- schtasks.exe (PID: 3216)
- schtasks.exe (PID: 4088)
- schtasks.exe (PID: 3440)
- schtasks.exe (PID: 1908)
- schtasks.exe (PID: 2736)
- schtasks.exe (PID: 4092)
- schtasks.exe (PID: 3428)
- schtasks.exe (PID: 3432)
- schtasks.exe (PID: 3256)
- schtasks.exe (PID: 3240)
- schtasks.exe (PID: 2636)
- schtasks.exe (PID: 2428)
- schtasks.exe (PID: 2972)
- schtasks.exe (PID: 1708)
- schtasks.exe (PID: 1716)
- schtasks.exe (PID: 3492)
- schtasks.exe (PID: 2396)
- schtasks.exe (PID: 3704)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 996)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 1688)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 2952)
- schtasks.exe (PID: 3572)
- schtasks.exe (PID: 2400)
- schtasks.exe (PID: 3796)
- schtasks.exe (PID: 2760)
- schtasks.exe (PID: 4088)
- schtasks.exe (PID: 1020)
- schtasks.exe (PID: 1808)
- schtasks.exe (PID: 3312)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 2736)
- schtasks.exe (PID: 3776)
- schtasks.exe (PID: 1784)
- schtasks.exe (PID: 3356)
- schtasks.exe (PID: 3440)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 2900)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 2084)
- schtasks.exe (PID: 2972)
- schtasks.exe (PID: 2400)
- schtasks.exe (PID: 3428)
- schtasks.exe (PID: 1688)
- schtasks.exe (PID: 2732)
- schtasks.exe (PID: 2128)
- schtasks.exe (PID: 936)
- schtasks.exe (PID: 3692)
PHORPIEX has been detected (SURICATA)
- sysplorsv.exe (PID: 1932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
352
Monitored processes
206
Malicious processes
37
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\Desktop\Files\PCclear_Eng_mini.exe" | C:\Users\admin\Desktop\Files\PCclear_Eng_mini.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: PCclear_Eng_mini MFC 응용 프로그램 Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 296 | Attrib +h *.* | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | "C:\Users\admin\Desktop\Files\a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe" | C:\Users\admin\Desktop\Files\a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe | — | a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 572 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 764 | "C:\Users\admin\Desktop\Files\a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe" | C:\Users\admin\Desktop\Files\a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 864 | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\5WI7gh8.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\5WI7gh8.exe | — | XK1qf04.exe | |||||||||||
User: admin Company: Polymod Inc. Integrity Level: HIGH Description: PolymodXT v1.3 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 936 | schtasks.exe /create /tn "Doublepulsar-1.3.1D" /sc MINUTE /mo 7 /tr "'C:\Program Files\Windows NT\TableTextService\Doublepulsar-1.3.1.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 936 | schtasks.exe /create /tn "servicess" /sc MINUTE /mo 5 /tr "'C:\hypersavesIntoRuntime\services.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 996 | schtasks.exe /create /tn "WerFaultW" /sc MINUTE /mo 7 /tr "'C:\Windows\Help\WerFault.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
106 690
Read events
105 697
Write events
989
Delete events
4
Modification events
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA662000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F007400200058003100000014000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E309000000010000000C000000300A06082B06010505070301030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E80F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000000CD2F9E0DA1773E9ED864DA5E370E74E0F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F63030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E809000000010000000C000000300A06082B060105050703011D000000010000001000000073B6876195F5D18E048510422AEF04E314000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E0B000000010000001A0000004900530052004700200052006F006F007400200058003100000062000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C61900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA620000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (1596) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1928) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1748) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2592) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2808) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
242
Suspicious files
47
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2100 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\timeSync.exe | executable | |
MD5:8EB8EFD8AF5CBC0DBCE9685E937C8E00 | SHA256:FB27A781ECB3F41878D869B93500552C7C78CD153C4157F67B6D4D2C7AE0D8D0 | |||
| 2108 | jet.exe | C:\Users\admin\AppData\Local\Temp\GS1C6D.tmp | executable | |
MD5:7D46EA623EBA5073B7E3A2834FE58CC9 | SHA256:4EBF13835A117A2551D80352CA532F6596E6F2729E41B3DE7015DB558429DEA5 | |||
| 3296 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\jet.exe | executable | |
MD5:1CD1DEFD8E963254A5F0D84AEC85A75E | SHA256:5CC691DDB8ACCD10A0EEADDC6D6F3853E2DAC335E452140C26DD02BA312CD1A8 | |||
| 3296 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Loader.exe | executable | |
MD5:4FF01CBC0D241BECC42C762C7ABA5F43 | SHA256:0110E1C3C1BD79626A55E770490D4CEBA396E907C4CFF4EC8D7C7293F6915E5D | |||
| 2768 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\ma.exe | executable | |
MD5:907A671E767F823DCB0B6045E18A423E | SHA256:EBFE53AD7E5D2A25B57D2E253B2C68D09208E03C2A22DDC23340D0522E5E338E | |||
| 2108 | jet.exe | C:\Users\admin\AppData\Local\Temp\gs1C8D.tmp | binary | |
MD5:E667DC95FC4777DFE2922456CCAB51E8 | SHA256:2F15F2CCDC2F8E6E2F5A2969E97755590F0BEA72F03D60A59AF8F9DD0284D15F | |||
| 3868 | WinLocker.exe | C:\Users\admin\Desktop\Files\WinLocker.exe_ | executable | |
MD5:E7F59A2129300DC874D60E8B927EDBA4 | SHA256:6E590D9214E8D824147463C5039418E928A2B6F3C3B4A4E4F33724EDC2877B3C | |||
| 3860 | lve.exe | C:\Program Files\Microsoft Oeswuy\Vnloubk.exe | executable | |
MD5:82182C7F430666ECD80649A3C9D4B06A | SHA256:F9A0484222A37B48F410A2A1B6CFC204D0C6A3F722CA69AA0773C2C4F67BEA35 | |||
| 3868 | WinLocker.exe | C:\Setup.bat | text | |
MD5:68A72616B6BACE8B60EE2D624FFDAE61 | SHA256:4BF535356C2E018FDA9D48DD210FA56856F788FBC8F00A78C77E613D0DEFDA39 | |||
| 2972 | CasPol.exe | C:\Users\admin\AppData\Roaming\90059C37-1320-41A4-B58D-2B75A9850D2F\run.dat | text | |
MD5:8B196B40BBD5D8993D1F831CC901D025 | SHA256:5A559DEC9CF74D010CA2D03A3703356D39060511B5F000D482F7FC7BF969CED6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
168
DNS requests
68
Threats
217
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1928 | 4363463463464363463463463.exe | GET | 200 | 20.169.49.77:80 | http://20.169.49.77/gpupdate.exe | unknown | executable | 1.56 Mb | unknown |
3296 | 4363463463464363463463463.exe | GET | 200 | 208.122.221.162:80 | http://funletters.net/scenic/scenic1/jet.exe | unknown | executable | 75.2 Kb | unknown |
3296 | 4363463463464363463463463.exe | GET | 200 | 164.155.231.101:16 | http://164.155.231.101:16/lve.exe | unknown | executable | 114 Kb | unknown |
1932 | 4363463463464363463463463.exe | GET | 200 | 209.145.51.44:80 | http://209.145.51.44/elevator.exe | unknown | executable | 315 Kb | unknown |
3836 | PCSupport.exe | GET | 200 | 115.71.237.171:80 | http://support.clz.kr//soft_hair/winvnc.exe | unknown | executable | 1.72 Mb | unknown |
2808 | 4363463463464363463463463.exe | GET | — | 104.21.46.59:80 | http://needs.hitsturbo.com/order/tuc3.exe | unknown | — | — | unknown |
2592 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.8:80 | http://185.172.128.8/ma.exe | unknown | executable | 4.08 Mb | unknown |
2100 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.53:80 | http://185.172.128.53/timeSync.exe | unknown | executable | 162 Kb | unknown |
2436 | 4363463463464363463463463.exe | GET | 200 | 202.66.173.109:80 | http://www.bcmnursing.com/QubpyznbC7neo.exe | unknown | executable | 1.02 Mb | unknown |
3116 | 4363463463464363463463463.exe | GET | 200 | 211.110.226.148:80 | http://down.pcclear.com/active/PCclear_Eng_mini.exe | unknown | executable | 32.0 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2064 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2064 | 4363463463464363463463463.exe | 186.225.153.226:443 | palharesinformatica.com.br | Sinal Br Telecom Ltda | BR | unknown |
1596 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1596 | 4363463463464363463463463.exe | 172.67.168.30:443 | cream.hitsturbo.com | CLOUDFLARENET | US | unknown |
1928 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1748 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1928 | 4363463463464363463463463.exe | 20.169.49.77:80 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
palharesinformatica.com.br |
| unknown |
cream.hitsturbo.com |
| malicious |
bitbucket.org |
| shared |
needs.hitsturbo.com |
| malicious |
bbuseruploads.s3.amazonaws.com |
| shared |
www.bcmnursing.com |
| unknown |
support.clz.kr |
| unknown |
kimyen.net |
| unknown |
padlet-uploads.storage.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1928 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1928 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1928 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1928 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1928 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2592 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2592 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2592 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
11 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|