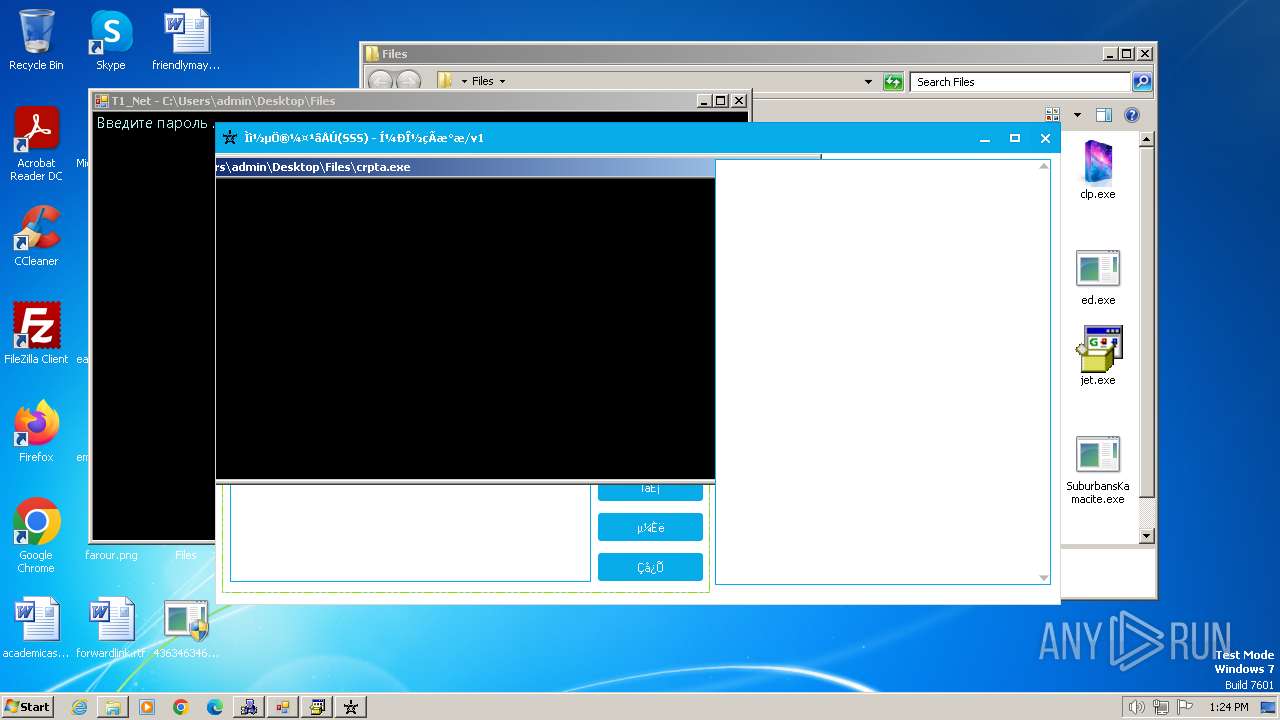
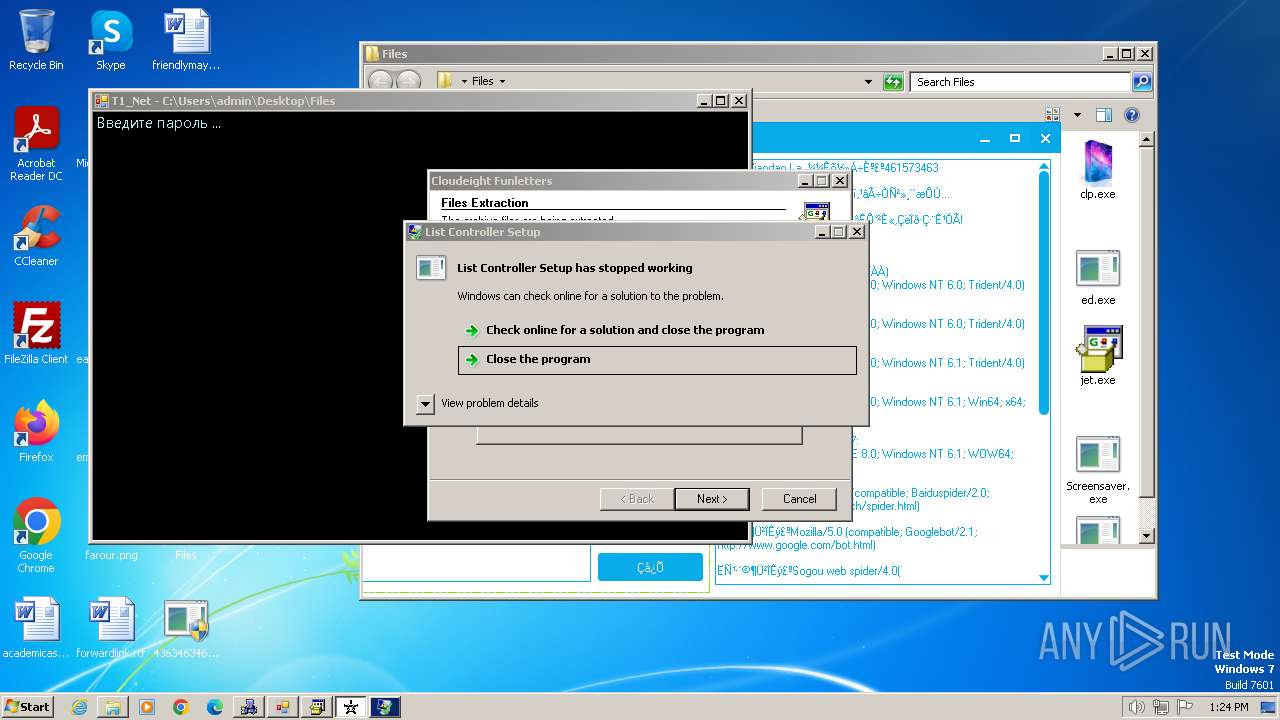
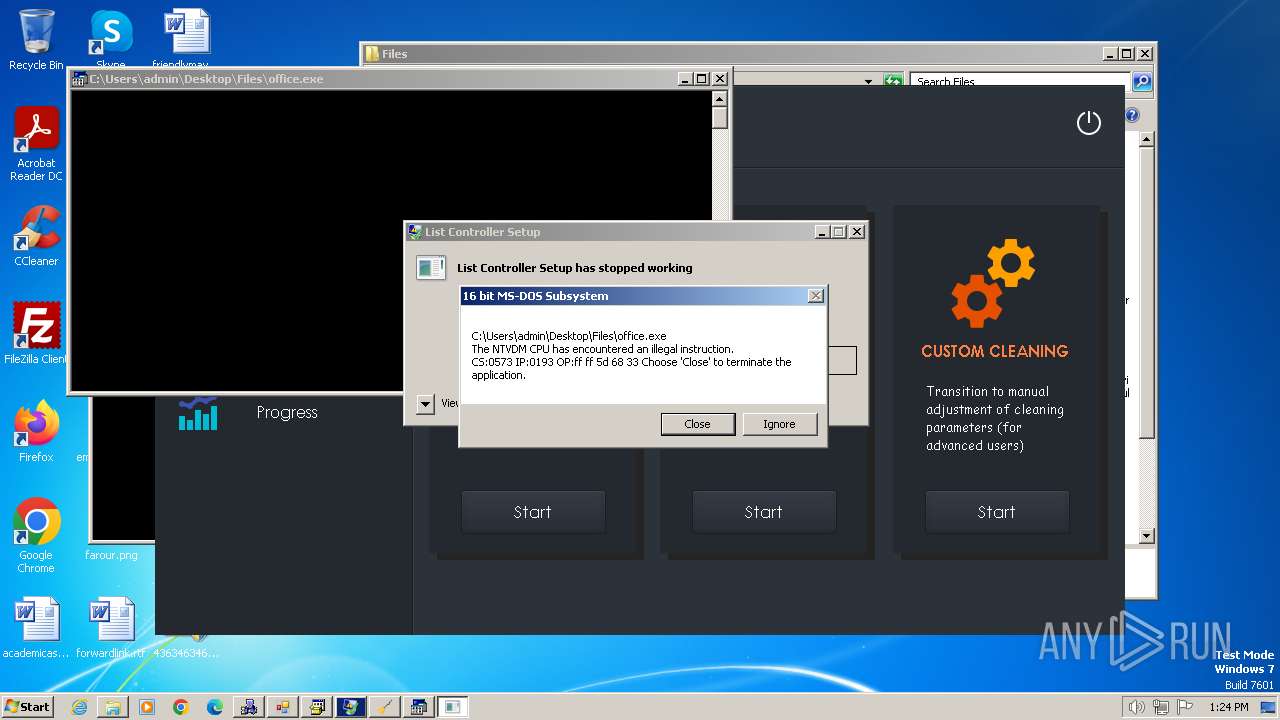
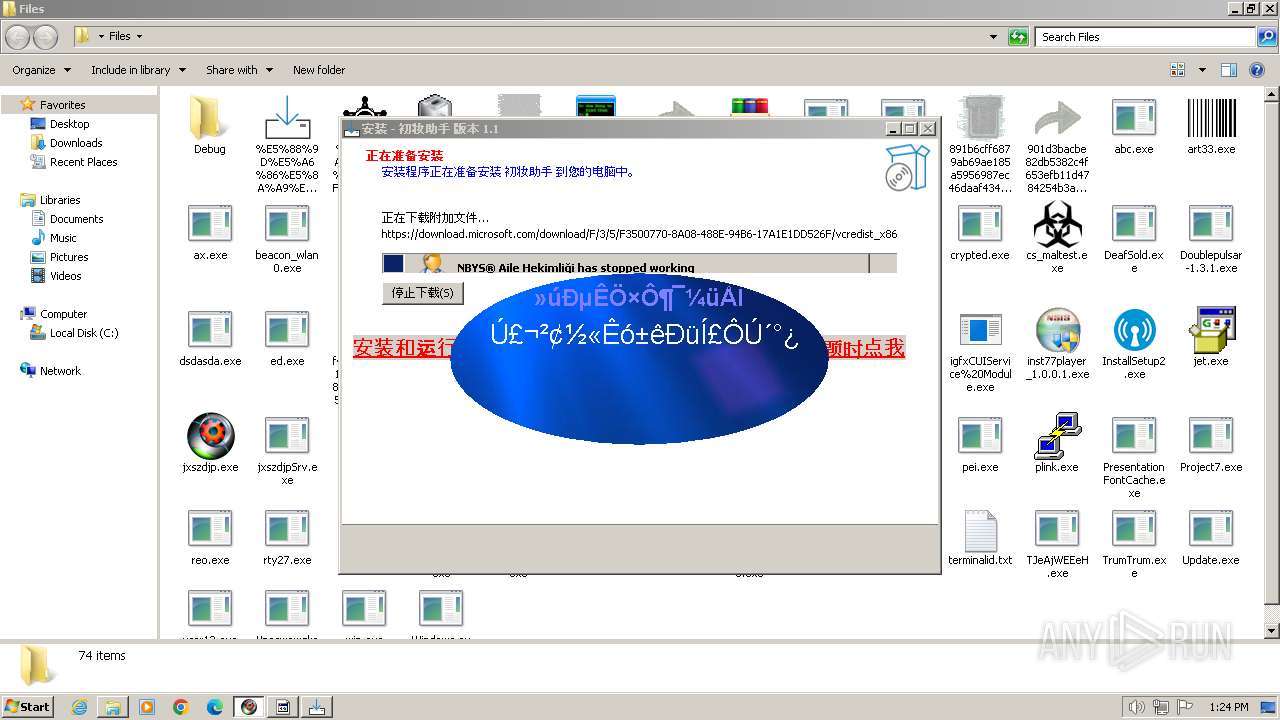
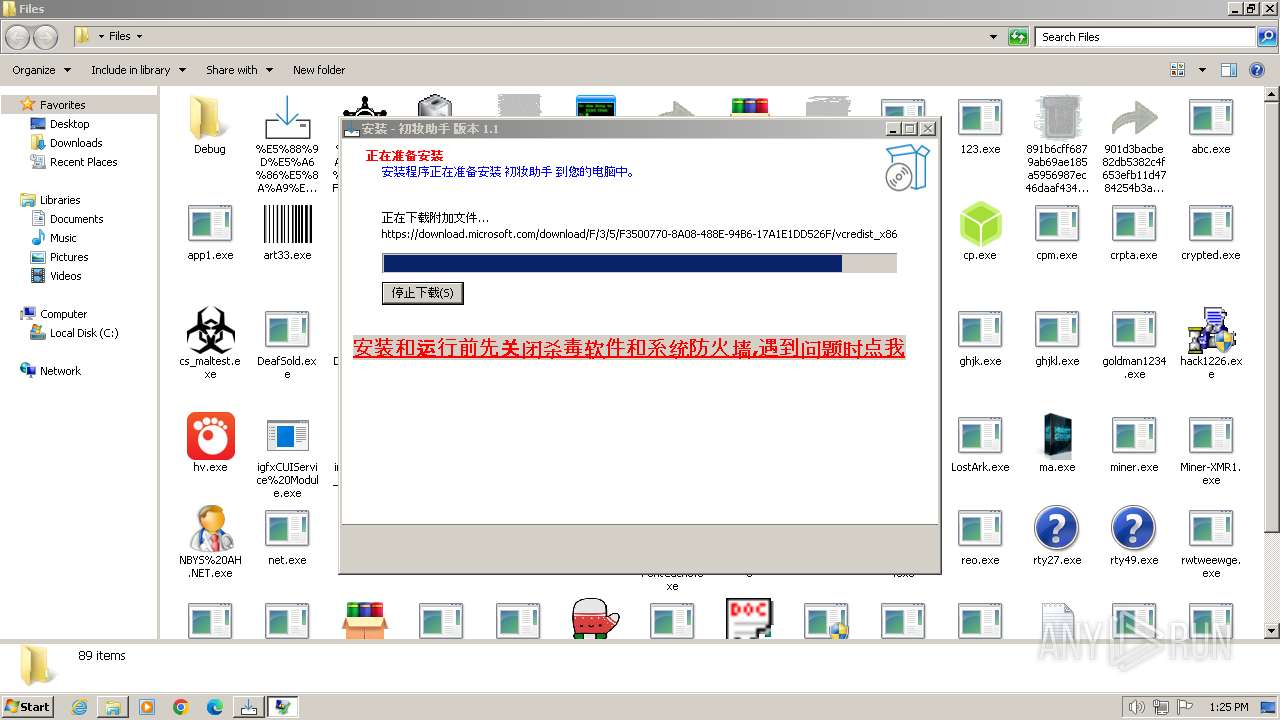
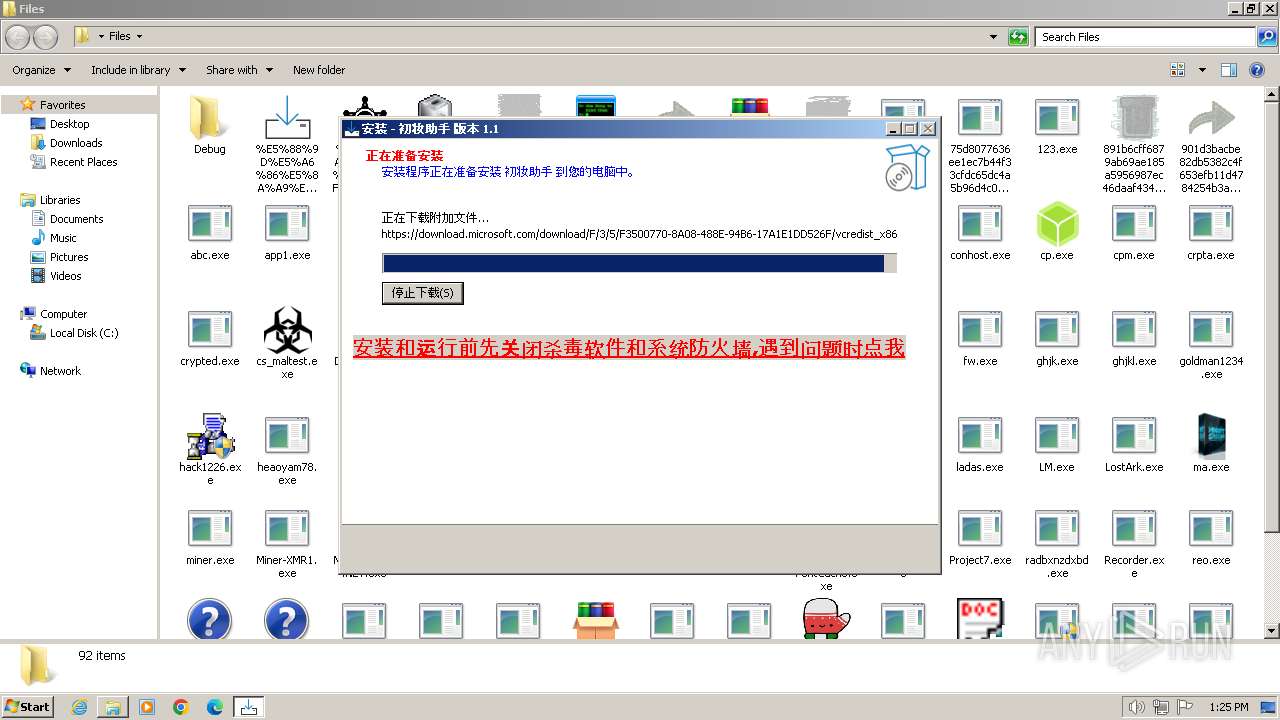
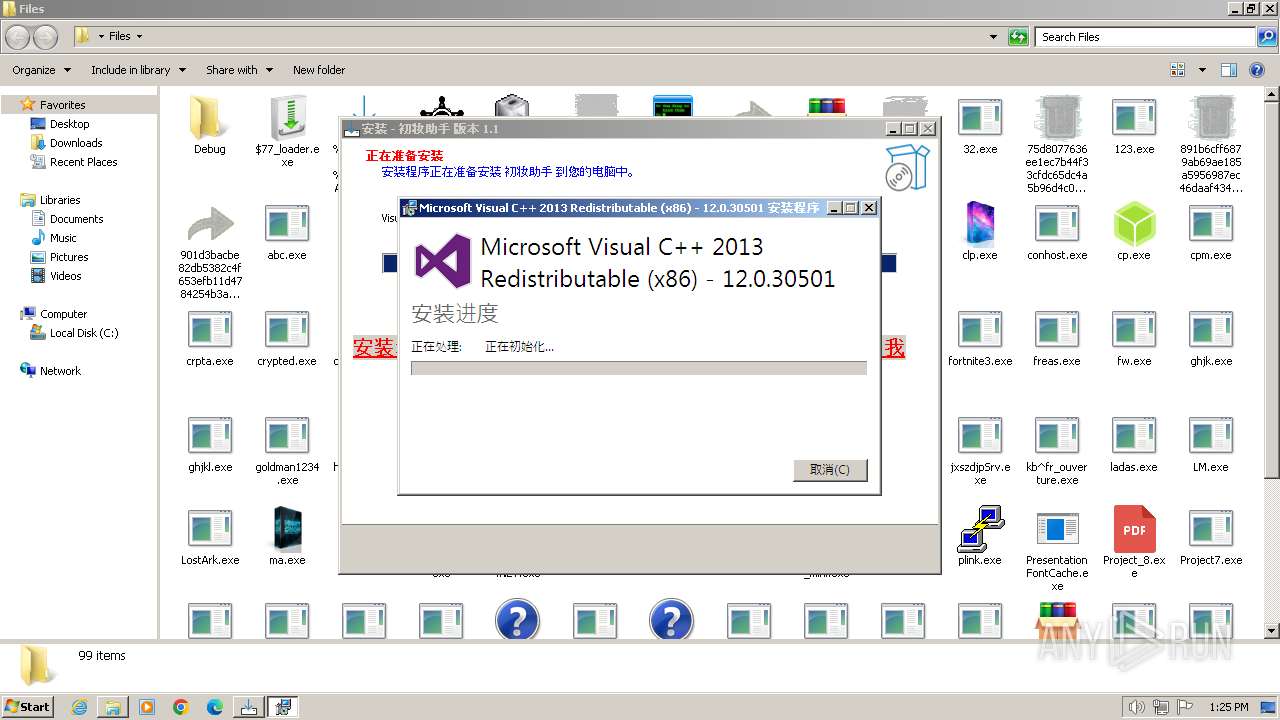
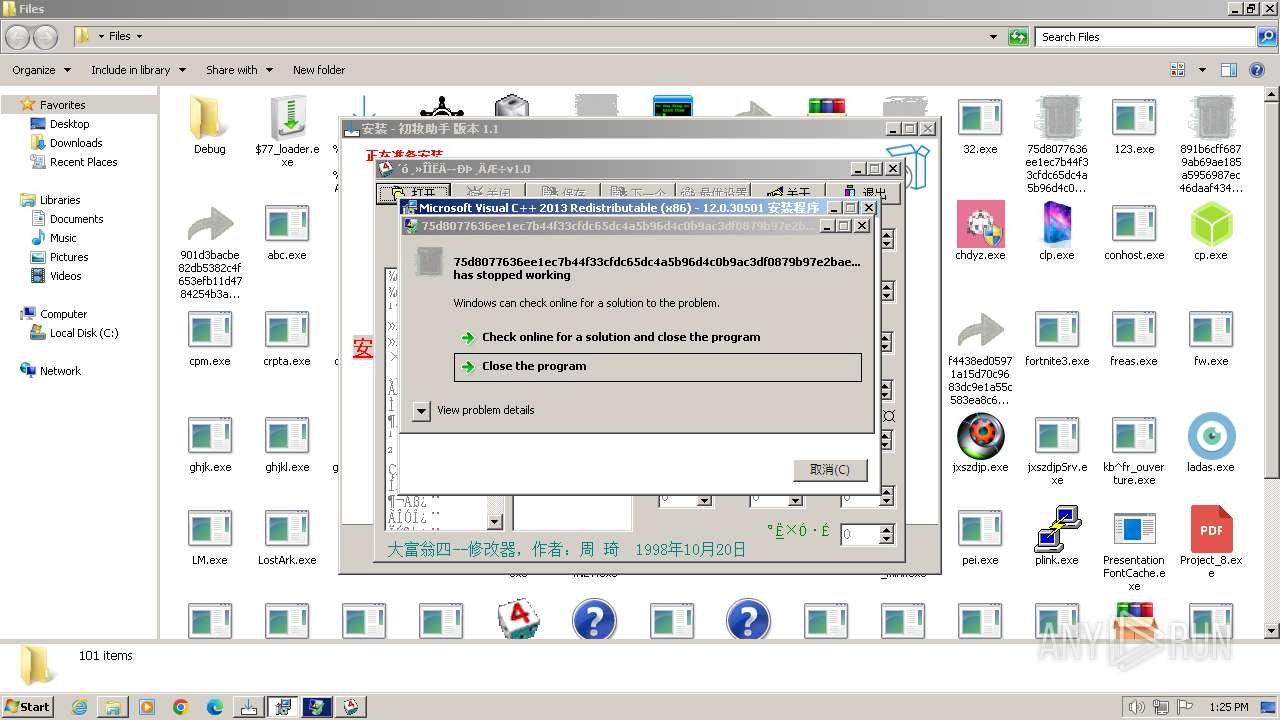
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/4ea922c5-943d-4cf7-8250-e9a1fc193745 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 12, 2024, 13:23:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- Temp2.exe (PID: 3748)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- 4363463463464363463463463.exe (PID: 840)
- InstallSetup2.exe (PID: 1112)
- jet.exe (PID: 2740)
- 4363463463464363463463463.exe (PID: 2588)
- payload.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 3072)
- inst77player_1.0.0.1.exe (PID: 2788)
- pei.exe (PID: 2732)
- 1656932762.exe (PID: 3504)
- miner.exe (PID: 3904)
- cp.exe (PID: 3756)
- jxszdjp.exe (PID: 2652)
- jxszdjpSrv.exe (PID: 900)
- hack1226.exe (PID: 2240)
- 4363463463464363463463463.exe (PID: 2420)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 4884)
- asdfg.exe (PID: 4964)
- 2880911004.exe (PID: 4868)
- BBLb.exe (PID: 5092)
- build.exe (PID: 4348)
- 80063188.exe (PID: 5408)
- conhost.exe (PID: 3392)
- hv.exe (PID: 4844)
- ax.exe (PID: 4388)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- vcredist2013.exe (PID: 4804)
- ladas.exe (PID: 3960)
- xzw.exe (PID: 4712)
- setup294.exe (PID: 4428)
- fw.exe (PID: 1852)
- tpeinf.exe (PID: 5656)
- plug.exe (PID: 5696)
- Client.exe (PID: 3012)
- v4install.exe (PID: 5816)
- Archevod_XWorm.exe (PID: 2876)
- NeonRank.exe (PID: 5656)
- win.exe (PID: 116)
- cbchr.exe (PID: 5092)
- chaospc.exe (PID: 6036)
- chaospcap.exe (PID: 4380)
- npp.exe (PID: 2028)
- peinf.exe (PID: 4804)
- agentServerComponent.exe (PID: 4088)
- cmd.exe (PID: 5872)
- l.exe (PID: 5072)
- superz.exe (PID: 3016)
- amert.exe (PID: 5368)
- InstallSetup3.exe (PID: 5104)
- april.exe (PID: 884)
- april.tmp (PID: 2184)
- yhdl.exe (PID: 4836)
- Winlock.exe (PID: 6140)
- RegAsm.exe (PID: 1900)
- more.exe (PID: 1308)
- Client-built.exe (PID: 4008)
- AUTOKEY.exe (PID: 5180)
- NPFInstall.exe (PID: 5072)
- stub.exe (PID: 3056)
- svchosl.exe (PID: 4116)
- drvinst.exe (PID: 5300)
- svchost.exe (PID: 4172)
- stub.exe (PID: 4364)
- STAR.exe (PID: 5036)
- stub.exe (PID: 2536)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 1628)
Creates a writable file in the system directory
- Temp2.exe (PID: 3748)
- chaospcap.exe (PID: 4380)
- drvinst.exe (PID: 5300)
Uses Task Scheduler to autorun other applications
- Temp2.exe (PID: 3748)
- asg.exe (PID: 2444)
- ladas.exe (PID: 3960)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 5136)
- Client-built.exe (PID: 4008)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3776)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3776)
Actions looks like stealing of personal data
- fcc.exe (PID: 2596)
- RegAsm.exe (PID: 2172)
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
- RegSvcs.exe (PID: 3892)
- dialer.exe (PID: 5136)
- jsc.exe (PID: 5248)
- STAR.exe (PID: 5036)
- dialer.exe (PID: 7000)
Steals credentials from Web Browsers
- fcc.exe (PID: 2596)
- RegAsm.exe (PID: 2172)
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
- RegSvcs.exe (PID: 3892)
- STAR.exe (PID: 5036)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3776)
Adds process to the Windows Defender exclusion list
- miner.exe (PID: 3904)
- Archevod_XWorm.exe (PID: 2876)
- build6_unencrypted.exe (PID: 7256)
- svchost.com (PID: 7664)
UAC/LUA settings modification
- miner.exe (PID: 3904)
Unusual connection from system programs
- wscript.exe (PID: 3776)
- vbc.exe (PID: 2320)
- vbc.exe (PID: 3472)
- vbc.exe (PID: 3972)
Remcos is detected
- 6.exe (PID: 3940)
REMCOS has been detected (SURICATA)
- 6.exe (PID: 3940)
Changes the autorun value in the registry
- 1656932762.exe (PID: 3504)
- 2880911004.exe (PID: 4868)
- 80063188.exe (PID: 5408)
- 23.exe (PID: 5376)
- ladas.exe (PID: 3960)
- win.exe (PID: 116)
- Archevod_XWorm.exe (PID: 2876)
Raccoon mutex has been detected
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- 2.3.1.1.exe (PID: 6008)
Changes Security Center notification settings
- 1656932762.exe (PID: 3504)
- 2880911004.exe (PID: 4868)
- 80063188.exe (PID: 5408)
Signature: RAMNIT has been detected
- jxszdjp.exe (PID: 2652)
- DesktopLayer.exe (PID: 2548)
- jxszdjpSrv.exe (PID: 900)
- iexplore.exe (PID: 948)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 2172)
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
- STAR.exe (PID: 5036)
- bott.exe (PID: 6120)
Connects to the CnC server
- RegAsm.exe (PID: 2172)
- iexplore.exe (PID: 948)
- 1656932762.exe (PID: 3504)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- nsa94.tmp (PID: 3260)
- 2880911004.exe (PID: 4868)
- jsc.exe (PID: 5248)
- fw.exe (PID: 1852)
- X89.exe (PID: 3600)
- svchosl.exe (PID: 4116)
- 2.3.1.1.exe (PID: 6008)
- xzw.exe (PID: 4712)
- bott.exe (PID: 6120)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 948)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 948)
QUASAR has been detected (YARA)
- asg.exe (PID: 2444)
- Client-built.exe (PID: 4008)
REDLINE has been detected (YARA)
- vbc.exe (PID: 3472)
- vbc.exe (PID: 2320)
- vbc.exe (PID: 3972)
- heaoyam78.exe (PID: 3976)
- for.exe (PID: 480)
- RegAsm.exe (PID: 1900)
GH0ST has been detected (SURICATA)
- 32.exe (PID: 4236)
STEALC has been detected (SURICATA)
- nsa94.tmp (PID: 3260)
NANOCORE has been detected (YARA)
- LostArk.exe (PID: 3536)
PHORPIEX has been detected (SURICATA)
- 1656932762.exe (PID: 3504)
- 4363463463464363463463463.exe (PID: 1628)
- 80063188.exe (PID: 5408)
- 2880911004.exe (PID: 4868)
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2420)
RACCOON has been detected (SURICATA)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- 2.3.1.1.exe (PID: 6008)
REMCOS has been detected (YARA)
- 6.exe (PID: 3940)
Steals credentials
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
ASYNCRAT has been detected (YARA)
- reo.exe (PID: 2208)
- 666.exe (PID: 5484)
- calc.exe (PID: 5728)
COBALTSTRIKE has been detected (YARA)
- abc.exe (PID: 1976)
- beacon_wlan0.exe (PID: 4564)
- beacon_certutil.exe (PID: 2128)
Run PowerShell with an invisible window
- powershell.exe (PID: 5604)
- powershell.exe (PID: 5912)
- powershell.exe (PID: 4416)
Bypass execution policy to execute commands
- powershell.exe (PID: 5604)
- powershell.exe (PID: 5912)
- powershell.exe (PID: 4416)
- powershell.exe (PID: 5908)
- powershell.exe (PID: 3264)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 2384)
- powershell.exe (PID: 8104)
Adds path to the Windows Defender exclusion list
- conhost.exe (PID: 3392)
- Archevod_XWorm.exe (PID: 2876)
- more.exe (PID: 1308)
- build6_unencrypted.exe (PID: 7256)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 5136)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 3892)
Changes powershell execution policy (Bypass)
- socks5-clean.exe (PID: 5860)
- Archevod_XWorm.exe (PID: 2876)
- svchost.com (PID: 7664)
Starts CMD.EXE for self-deleting
- inte.exe (PID: 5752)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
RISEPRO has been detected (YARA)
- StealerClient_Cpp_1_3_1.exe (PID: 4376)
- StealerClient_Cpp_1_4.exe (PID: 4384)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 5752)
- inte.exe (PID: 8168)
ARECHCLIENT2 has been detected (SURICATA)
- jsc.exe (PID: 5248)
NITOL has been detected (YARA)
- xzw.exe (PID: 4712)
- Suaeweq.exe (PID: 5528)
- Suaeweq.exe (PID: 1020)
LAPLASCLIPPER has been detected (YARA)
- svcservice.exe (PID: 2480)
XWORM has been detected (YARA)
- Archevod_XWorm.exe (PID: 2876)
- msedge.exe (PID: 4404)
AZORULT has been detected (SURICATA)
- X89.exe (PID: 3600)
Create files in the Startup directory
- Archevod_XWorm.exe (PID: 2876)
- STAR.exe (PID: 5036)
RISEPRO has been detected (SURICATA)
- ladas.exe (PID: 3960)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 3060)
- findstr.exe (PID: 5976)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5144)
DcRAT is detected
- agentServerComponent.exe (PID: 4088)
ASYNCRAT has been detected (SURICATA)
- 666.exe (PID: 5484)
GH0STCRINGE has been detected (SURICATA)
- xzw.exe (PID: 4712)
BANLOAD has been detected (SURICATA)
- svchosl.exe (PID: 4116)
Deletes the SafeBoot registry key
- 7e207560.exe (PID: 6848)
ASYNCRAT has been detected (MUTEX)
- more.exe (PID: 7480)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 2588)
- Update.exe (PID: 3720)
- build.exe (PID: 4348)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- asdjijjjjj.exe (PID: 5224)
- RegSvcs.exe (PID: 3892)
- data64_6.exe (PID: 4400)
- ladas.exe (PID: 3960)
- 666.exe (PID: 5484)
- NPFInstall.exe (PID: 5072)
- Update_new.exe (PID: 6052)
- RegAsm.exe (PID: 2736)
- data64_1.exe (PID: 5016)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 4092)
- certutil.exe (PID: 3844)
- certutil.exe (PID: 5676)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 2420)
- plink.exe (PID: 3016)
- Temp2.exe (PID: 3748)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- asg.exe (PID: 2444)
- miner.exe (PID: 3904)
- powershell.exe (PID: 3504)
- InstallSetup2.exe (PID: 1112)
- fortnite3.exe (PID: 4032)
- payload.exe (PID: 2776)
- pei.exe (PID: 2732)
- Update.exe (PID: 3720)
- abc.exe (PID: 1976)
- nsa94.tmp (PID: 3260)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- jet.exe (PID: 2740)
- 1656932762.exe (PID: 3504)
- build.exe (PID: 4348)
- conhost.exe (PID: 3392)
- beacon_wlan0.exe (PID: 4564)
- Vpeswawqko.exe (PID: 4924)
- asdfg.exe (PID: 4964)
- asdjijjjjj.exe (PID: 5224)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- 2880911004.exe (PID: 4868)
- powershell.exe (PID: 5604)
- 80063188.exe (PID: 5408)
- RegSvcs.exe (PID: 3892)
- powershell.exe (PID: 4300)
- powershell.exe (PID: 4560)
- socks5-clean.exe (PID: 5860)
- inte.exe (PID: 5752)
- 23.exe (PID: 5376)
- fw.exe (PID: 1852)
- ax.exe (PID: 4388)
- data64_6.exe (PID: 4400)
- PCclear_Eng_mini.exe (PID: 5088)
- svcservice.exe (PID: 2480)
- xzw.exe (PID: 4712)
- X89.exe (PID: 3600)
- setup294.exe (PID: 4428)
- control.exe (PID: 5640)
- tpeinf.exe (PID: 5656)
- Archevod_XWorm.exe (PID: 2876)
- powershell.exe (PID: 4416)
- powershell.exe (PID: 5908)
- first.exe (PID: 5660)
- Client.exe (PID: 3012)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 3264)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
- svchosl.exe (PID: 4116)
- powershell.exe (PID: 2384)
- more.exe (PID: 1308)
- cbchr.exe (PID: 5092)
- v4install.exe (PID: 5816)
- NeonRank.exe (PID: 5656)
- beacon_certutil.exe (PID: 2128)
- 2.3.1.1.exe (PID: 6008)
- npp.exe (PID: 2028)
- peinf.exe (PID: 4804)
- wscript.exe (PID: 5144)
- superz.exe (PID: 3016)
- baseline.exe (PID: 2904)
- yhdl.exe (PID: 4836)
- RegAsm.exe (PID: 1900)
- timeSync.exe (PID: 4360)
- InstallSetup3.exe (PID: 5104)
- stub.exe (PID: 4364)
- mspaint.exe (PID: 4900)
- stub.exe (PID: 2536)
- 7e207560.exe (PID: 6848)
- stub.exe (PID: 6816)
- Update_new.exe (PID: 6052)
- STAR.exe (PID: 5036)
- powershell.exe (PID: 2868)
- 炎黄大陆.exe (PID: 5680)
- stub.exe (PID: 7336)
- build6_unencrypted.exe (PID: 7256)
- Journal.exe (PID: 7624)
- RegAsm.exe (PID: 2736)
- more.exe (PID: 7480)
- inte.exe (PID: 8168)
- stub.exe (PID: 8000)
- data64_1.exe (PID: 5016)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- fortnite3.exe (PID: 4032)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- miner.exe (PID: 3904)
- 4363463463464363463463463.exe (PID: 840)
- InstallSetup2.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 3072)
- payload.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 2588)
- pei.exe (PID: 2732)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- nsa94.tmp (PID: 3260)
- 1656932762.exe (PID: 3504)
- conhost.exe (PID: 3392)
- 4363463463464363463463463.exe (PID: 2420)
- asdfg.exe (PID: 4964)
- build.exe (PID: 4348)
- 80063188.exe (PID: 5408)
- 4363463463464363463463463.exe (PID: 3216)
- inte.exe (PID: 5752)
- socks5-clean.exe (PID: 5860)
- 23.exe (PID: 5376)
- fw.exe (PID: 1852)
- ax.exe (PID: 4388)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- PCclear_Eng_mini.exe (PID: 5088)
- svcservice.exe (PID: 2480)
- X89.exe (PID: 3600)
- 2880911004.exe (PID: 4868)
- xzw.exe (PID: 4712)
- setup294.exe (PID: 4428)
- Archevod_XWorm.exe (PID: 2876)
- Suaeweq.exe (PID: 5528)
- Client.exe (PID: 3012)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
- more.exe (PID: 1308)
- cbchr.exe (PID: 5092)
- v4install.exe (PID: 5816)
- NeonRank.exe (PID: 5656)
- 2.3.1.1.exe (PID: 6008)
- peinf.exe (PID: 4804)
- superz.exe (PID: 3016)
- Suaeweq.exe (PID: 1020)
- yhdl.exe (PID: 4836)
- RegAsm.exe (PID: 1900)
- timeSync.exe (PID: 4360)
- InstallSetup3.exe (PID: 5104)
- stub.exe (PID: 4364)
- stub.exe (PID: 2536)
- stub.exe (PID: 6816)
- NPFInstall.exe (PID: 5072)
- STAR.exe (PID: 5036)
- stub.exe (PID: 7336)
- build6_unencrypted.exe (PID: 7256)
- 炎黄大陆.exe (PID: 5680)
- Journal.exe (PID: 7624)
- more.exe (PID: 7480)
- stub.exe (PID: 8000)
- inte.exe (PID: 8168)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- Temp2.exe (PID: 3748)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- 4363463463464363463463463.exe (PID: 840)
- InstallSetup2.exe (PID: 1112)
- jet.exe (PID: 2740)
- 4363463463464363463463463.exe (PID: 3072)
- payload.exe (PID: 2776)
- 4363463463464363463463463.exe (PID: 2588)
- inst77player_1.0.0.1.exe (PID: 2788)
- pei.exe (PID: 2732)
- 1656932762.exe (PID: 3504)
- miner.exe (PID: 3904)
- cp.exe (PID: 3756)
- jxszdjpSrv.exe (PID: 900)
- hack1226.exe (PID: 2240)
- jxszdjp.exe (PID: 2652)
- 4363463463464363463463463.exe (PID: 2420)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 4884)
- asdfg.exe (PID: 4964)
- BBLb.exe (PID: 5092)
- build.exe (PID: 4348)
- 80063188.exe (PID: 5408)
- conhost.exe (PID: 3392)
- 4363463463464363463463463.exe (PID: 3216)
- hv.exe (PID: 4844)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- ax.exe (PID: 4388)
- vcredist2013.exe (PID: 4804)
- dialer.exe (PID: 5136)
- 2880911004.exe (PID: 4868)
- ladas.exe (PID: 3960)
- xzw.exe (PID: 4712)
- setup294.exe (PID: 4428)
- fw.exe (PID: 1852)
- tpeinf.exe (PID: 5656)
- plug.exe (PID: 5696)
- Client.exe (PID: 3012)
- Archevod_XWorm.exe (PID: 2876)
- v4install.exe (PID: 5816)
- win.exe (PID: 116)
- NeonRank.exe (PID: 5656)
- cbchr.exe (PID: 5092)
- chaospc.exe (PID: 6036)
- chaospcap.exe (PID: 4380)
- npp.exe (PID: 2028)
- peinf.exe (PID: 4804)
- agentServerComponent.exe (PID: 4088)
- cmd.exe (PID: 5872)
- amert.exe (PID: 5368)
- l.exe (PID: 5072)
- superz.exe (PID: 3016)
- InstallSetup3.exe (PID: 5104)
- april.exe (PID: 884)
- april.tmp (PID: 2184)
- yhdl.exe (PID: 4836)
- Winlock.exe (PID: 6140)
- RegAsm.exe (PID: 1900)
- more.exe (PID: 1308)
- Client-built.exe (PID: 4008)
- AUTOKEY.exe (PID: 5180)
- NPFInstall.exe (PID: 5072)
- stub.exe (PID: 3056)
- svchosl.exe (PID: 4116)
- drvinst.exe (PID: 5300)
- svchost.exe (PID: 4172)
- stub.exe (PID: 4364)
- STAR.exe (PID: 5036)
- stub.exe (PID: 2536)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- ax.exe (PID: 4388)
- 4363463463464363463463463.exe (PID: 2588)
- win.exe (PID: 116)
- chaospcap.exe (PID: 4380)
- stub.exe (PID: 3056)
- 4363463463464363463463463.exe (PID: 3072)
Application launched itself
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 3388)
- soft.exe (PID: 1192)
- asdfg.exe (PID: 4964)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 4876)
- BBLb.exe (PID: 5032)
- ghjk.exe (PID: 5296)
- net.exe (PID: 4976)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 5368)
- vcredist2013.exe (PID: 4340)
- AttributeString.exe (PID: 4488)
- X89.exe (PID: 5160)
- MSBuild.exe (PID: 2156)
- lumma.exe (PID: 6064)
- native.exe (PID: 3464)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 5824)
- Suaeweq.exe (PID: 5528)
- zxcvb.exe (PID: 5444)
- cmd.exe (PID: 6044)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 4232)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 3580)
- asdfg.exe (PID: 6756)
- 7e207560.exe (PID: 7124)
- more.exe (PID: 1308)
Starts itself from another location
- Temp2.exe (PID: 3748)
- jxszdjpSrv.exe (PID: 900)
- build.exe (PID: 4348)
- 2880911004.exe (PID: 4868)
- 23.exe (PID: 5376)
- stub.exe (PID: 2536)
- svchost.com (PID: 6384)
- stub.exe (PID: 6816)
- svchost.com (PID: 6976)
- stub.exe (PID: 7336)
- svchost.com (PID: 7600)
- stub.exe (PID: 8000)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 1628)
- fcc.exe (PID: 2596)
- Screensaver.exe (PID: 4052)
- vbc.exe (PID: 3472)
- vbc.exe (PID: 2320)
- asg.exe (PID: 2444)
- 6.exe (PID: 3940)
- reo.exe (PID: 2208)
- LostArk.exe (PID: 3536)
- vbc.exe (PID: 3972)
- abc.exe (PID: 1976)
- RegAsm.exe (PID: 2172)
- 32.exe (PID: 4236)
- build.exe (PID: 4348)
- beacon_wlan0.exe (PID: 4564)
- 4363463463464363463463463.exe (PID: 840)
- asdjijjjjj.exe (PID: 5224)
- 1656932762.exe (PID: 3504)
- powershell.exe (PID: 5912)
- 2880911004.exe (PID: 4868)
- jsc.exe (PID: 5248)
- fw.exe (PID: 1852)
- Recorder.exe (PID: 4108)
- heaoyam78.exe (PID: 3976)
- ladas.exe (PID: 3960)
- 4363463463464363463463463.exe (PID: 3232)
- 666.exe (PID: 5484)
- win.exe (PID: 116)
- calc.exe (PID: 5728)
- Archevod_XWorm.exe (PID: 2876)
- baseline.exe (PID: 2904)
- bott.exe (PID: 6120)
- STAR.exe (PID: 5036)
- svchosl.exe (PID: 4116)
- 1.exe (PID: 4728)
- Update_new.exe (PID: 6052)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 2588)
- Journal.exe (PID: 7624)
- RegAsm.exe (PID: 7864)
- xzw.exe (PID: 4712)
The process executes VB scripts
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- tel.exe (PID: 1768)
- jjj.exe (PID: 3068)
- c4fc1686ecf325a5432309a2fec15357f6ff849252747ef44de7b4f1f4d4d1c2.exe (PID: 2868)
Reads browser cookies
- fcc.exe (PID: 2596)
- RegAsm.exe (PID: 2172)
- jsc.exe (PID: 5248)
- STAR.exe (PID: 5036)
Starts CMD.EXE for commands execution
- fcc.exe (PID: 2596)
- BroomSetup.exe (PID: 3308)
- inte.exe (PID: 5752)
- plug.exe (PID: 5696)
- Client.exe (PID: 3012)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
- cbchr.exe (PID: 5092)
- NeonRank.exe (PID: 5656)
- wscript.exe (PID: 5144)
- cmd.exe (PID: 6044)
Starts POWERSHELL.EXE for commands execution
- miner.exe (PID: 3904)
- conhost.exe (PID: 3392)
- socks5-clean.exe (PID: 5860)
- Archevod_XWorm.exe (PID: 2876)
- more.exe (PID: 1308)
- svchost.com (PID: 7664)
Script adds exclusion process to Windows Defender
- miner.exe (PID: 3904)
- Archevod_XWorm.exe (PID: 2876)
Script adds exclusion path to Windows Defender
- miner.exe (PID: 3904)
- conhost.exe (PID: 3392)
- Archevod_XWorm.exe (PID: 2876)
- more.exe (PID: 1308)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3504)
- powershell.exe (PID: 5604)
- powershell.exe (PID: 4300)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 5908)
- powershell.exe (PID: 4416)
- powershell.exe (PID: 3604)
- powershell.exe (PID: 3264)
- powershell.exe (PID: 2384)
- powershell.exe (PID: 2868)
Checks for external IP
- Temp2.exe (PID: 3748)
- asg.exe (PID: 2444)
- ladas.exe (PID: 3960)
- first.exe (PID: 5660)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 3216)
- svchosl.exe (PID: 4116)
- InstallSetup3.exe (PID: 5104)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- miner.exe (PID: 3904)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 3072)
- 1656932762.exe (PID: 3504)
- 4363463463464363463463463.exe (PID: 2420)
- 80063188.exe (PID: 5408)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 840)
- svchosl.exe (PID: 4116)
- mspaint.exe (PID: 4900)
- InstallSetup3.exe (PID: 5104)
- inte.exe (PID: 8168)
Writes files like Keylogger logs
- 4363463463464363463463463.exe (PID: 3232)
- 6.exe (PID: 3940)
Executing commands from a ".bat" file
- BroomSetup.exe (PID: 3308)
- plug.exe (PID: 5696)
- Client.exe (PID: 3012)
- cbchr.exe (PID: 5092)
- wscript.exe (PID: 5144)
- NeonRank.exe (PID: 5656)
Starts application with an unusual extension
- cmd.exe (PID: 3504)
- InstallSetup2.exe (PID: 1112)
- chaospcap.exe (PID: 4380)
- cmd.exe (PID: 6044)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 3072)
- stub.exe (PID: 2536)
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 840)
- stub.exe (PID: 6816)
- STAR.exe (PID: 5036)
- 4363463463464363463463463.exe (PID: 2420)
- build6_unencrypted.exe (PID: 7256)
- stub.exe (PID: 7336)
- more.exe (PID: 7480)
- stub.exe (PID: 8000)
Windows Defender mutex has been found
- nsa94.tmp (PID: 3260)
- timeSync.exe (PID: 4360)
Searches for installed software
- RegAsm.exe (PID: 2172)
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
- dialer.exe (PID: 5136)
- jsc.exe (PID: 5248)
- vcredist2013.exe (PID: 4340)
- vcredist2013.exe (PID: 4804)
- 666.exe (PID: 5484)
- timeSync.exe (PID: 4360)
- STAR.exe (PID: 5036)
- dialer.exe (PID: 7000)
Reads the Windows owner or organization settings
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- april.tmp (PID: 2184)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 5136)
- 4363463463464363463463463.exe (PID: 840)
- rundll32.exe (PID: 3376)
- dialer.exe (PID: 7000)
The process executes via Task Scheduler
- powershell.exe (PID: 5604)
- AttributeString.exe (PID: 4488)
- powershell.exe (PID: 4416)
- msedge.exe (PID: 4404)
- msedge.exe (PID: 7724)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 3892)
- dialer.exe (PID: 5136)
- dialer.exe (PID: 7000)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 5136)
- dialer.exe (PID: 7000)
The process executes Powershell scripts
- socks5-clean.exe (PID: 5860)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4716)
- cmd.exe (PID: 3124)
Connects to SMTP port
- RegSvcs.exe (PID: 3892)
Process drops legitimate windows executable
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- vcredist2013.exe (PID: 4804)
- 4363463463464363463463463.exe (PID: 2588)
- fw.exe (PID: 1852)
- Archevod_XWorm.exe (PID: 2876)
- april.tmp (PID: 2184)
- AUTOKEY.exe (PID: 5180)
- stub.exe (PID: 3056)
- svchost.exe (PID: 4172)
Starts a Microsoft application from unusual location
- vcredist2013.exe (PID: 4340)
- vcredist2013.exe (PID: 4804)
- Archevod_XWorm.exe (PID: 2876)
Executed via WMI
- X89.exe (PID: 5160)
Reads the BIOS version
- ladas.exe (PID: 3960)
- amert.exe (PID: 5368)
- AUTOKEY.exe (PID: 5180)
- Update_new.exe (PID: 6052)
- new.exe (PID: 7608)
Unusual connection from system programs
- powershell.exe (PID: 5912)
Executes as Windows Service
- VSSVC.exe (PID: 3776)
- Suaeweq.exe (PID: 5528)
- svchost.exe (PID: 4172)
- 7e207560.exe (PID: 7124)
The Powershell connects to the Internet
- powershell.exe (PID: 5912)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 5640)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 5280)
- cmd.exe (PID: 6044)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- data64_6.exe (PID: 4400)
- data64_1.exe (PID: 5016)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5128)
- cmd.exe (PID: 4232)
The executable file from the user directory is run by the CMD process
- 666.exe (PID: 5484)
- calc.exe (PID: 5728)
- agentServerComponent.exe (PID: 4088)
- Taxes.pif (PID: 2936)
Process uses ARP to discover network configuration
- win.exe (PID: 116)
Uses ROUTE.EXE to obtain the routing table information
- win.exe (PID: 116)
Get information on the list of running processes
- cmd.exe (PID: 6044)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6044)
Uses REG/REGEDIT.EXE to modify registry
- chaospc.exe (PID: 6036)
Malware-specific behavior (creating "System.dll" in Temp)
- chaospcap.exe (PID: 4380)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5144)
Creates or modifies Windows services
- xzw.exe (PID: 4712)
Drops a system driver (possible attempt to evade defenses)
- chaospcap.exe (PID: 4380)
- NPFInstall.exe (PID: 5072)
- drvinst.exe (PID: 5300)
Creates a software uninstall entry
- chaospcap.exe (PID: 4380)
- yhdl.exe (PID: 4836)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 5872)
Changes the Home page of Internet Explorer
- svchosl.exe (PID: 4116)
Changes the title of the Internet Explorer window
- svchosl.exe (PID: 4116)
Creates files in the driver directory
- drvinst.exe (PID: 5300)
Checks Windows Trust Settings
- drvinst.exe (PID: 5300)
- NPFInstall.exe (PID: 5072)
Reads Microsoft Outlook installation path
- 炎黄大陆.exe (PID: 5680)
INFO
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- ed.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 668)
- Temp2.exe (PID: 3748)
- asg.exe (PID: 2444)
- vbc.exe (PID: 2320)
- vbc.exe (PID: 3472)
- Windows.exe (PID: 2920)
- fortnite3.exe (PID: 4032)
- dsdasda.exe (PID: 796)
- T1_Net.exe (PID: 3400)
- reo.exe (PID: 2208)
- 6.exe (PID: 3940)
- crpta.exe (PID: 2944)
- miner.exe (PID: 3904)
- payload.exe (PID: 2776)
- LostArk.exe (PID: 3536)
- Update.exe (PID: 3720)
- pei.exe (PID: 2732)
- SystemUpdate.exe (PID: 1928)
- InstallSetup2.exe (PID: 1112)
- conhost.exe (PID: 3392)
- abc.exe (PID: 1976)
- vbc.exe (PID: 3972)
- nsa94.tmp (PID: 3260)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- RegAsm.exe (PID: 2172)
- 1656932762.exe (PID: 3504)
- build.exe (PID: 4348)
- beacon_wlan0.exe (PID: 4564)
- Vpeswawqko.exe (PID: 4924)
- BBLb.exe (PID: 5032)
- asdfg.exe (PID: 4964)
- BBLb.exe (PID: 5092)
- asdjijjjjj.exe (PID: 5224)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- NBYS%20AH.NET.exe (PID: 5364)
- ghjk.exe (PID: 5296)
- 80063188.exe (PID: 5408)
- 2880911004.exe (PID: 4868)
- RegSvcs.exe (PID: 3892)
- net.exe (PID: 4976)
- inte.exe (PID: 5752)
- wmlaunch.exe (PID: 5628)
- hv.exe (PID: 4844)
- jsc.exe (PID: 5248)
- fw.exe (PID: 1852)
- data64_6.exe (PID: 4400)
- heaoyam78.exe (PID: 3976)
- WatchDog.exe (PID: 4368)
- vcredist2013.exe (PID: 4340)
- AttributeString.exe (PID: 4488)
- svcservice.exe (PID: 2480)
- X89.exe (PID: 5160)
- AttributeString.exe (PID: 5080)
- PCclear_Eng_mini.exe (PID: 5088)
- X89.exe (PID: 3600)
- xzw.exe (PID: 4712)
- MSBuild.exe (PID: 2156)
- MSBuild.exe (PID: 4128)
- ladas.exe (PID: 3960)
- Archevod_XWorm.exe (PID: 2876)
- tpeinf.exe (PID: 5656)
- first.exe (PID: 5660)
- Client.exe (PID: 3012)
- Suaeweq.exe (PID: 5528)
- native.exe (PID: 3464)
- cbchr.exe (PID: 5092)
- more.exe (PID: 1308)
- 666.exe (PID: 5484)
- calc.exe (PID: 5728)
- beacon_certutil.exe (PID: 2128)
- 2.3.1.1.exe (PID: 6008)
- zxcvb.exe (PID: 5444)
- npp.exe (PID: 2028)
- agentServerComponent.exe (PID: 4088)
- peinf.exe (PID: 4804)
- l.exe (PID: 5072)
- Suaeweq.exe (PID: 1020)
- superz.exe (PID: 3016)
- c53cfff621a84792162f70e790980e38.exe (PID: 1032)
- hncc.exe (PID: 4664)
- baseline.exe (PID: 2904)
- Client-built.exe (PID: 4008)
- yhdl.exe (PID: 4836)
- timeSync.exe (PID: 4360)
- msedge.exe (PID: 4404)
- STAR.exe (PID: 5036)
- bott.exe (PID: 6120)
- AUTOKEY.exe (PID: 5180)
- InstallSetup3.exe (PID: 5104)
- NPFInstall.exe (PID: 5072)
- 1.exe (PID: 4728)
- drvinst.exe (PID: 5300)
- svchosl.exe (PID: 4116)
- data64_1.exe (PID: 5016)
- Update_new.exe (PID: 6052)
- asdfg.exe (PID: 6756)
- RegAsm.exe (PID: 2736)
- more.exe (PID: 7480)
- build6_unencrypted.exe (PID: 7256)
- Journal.exe (PID: 7624)
- RegAsm.exe (PID: 7864)
- msedge.exe (PID: 7724)
- light.exe (PID: 3572)
- inte.exe (PID: 8168)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 2184)
- 4363463463464363463463463.exe (PID: 3956)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 3404)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 480)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 2516)
- 4363463463464363463463463.exe (PID: 2108)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 1264)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 2268)
- 4363463463464363463463463.exe (PID: 668)
- msedge.exe (PID: 1992)
- msedge.exe (PID: 5980)
- mspaint.exe (PID: 4900)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- ed.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 668)
- Temp2.exe (PID: 3748)
- plink.exe (PID: 3016)
- miner.exe (PID: 3904)
- fortnite3.exe (PID: 4032)
- asg.exe (PID: 2444)
- crypted.exe (PID: 3304)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- fcc.exe (PID: 2596)
- vbc.exe (PID: 2320)
- vbc.exe (PID: 3472)
- Windows.exe (PID: 2920)
- dsdasda.exe (PID: 796)
- 6.exe (PID: 3940)
- T1_Net.exe (PID: 3400)
- InstallSetup2.exe (PID: 1112)
- BroomSetup.exe (PID: 3308)
- reo.exe (PID: 2208)
- crpta.exe (PID: 2944)
- Update.exe (PID: 3720)
- payload.exe (PID: 2776)
- LostArk.exe (PID: 3536)
- SystemUpdate.exe (PID: 1928)
- pei.exe (PID: 2732)
- inst77player_1.0.0.1.exe (PID: 2788)
- vbc.exe (PID: 3972)
- conhost.exe (PID: 3392)
- abc.exe (PID: 1976)
- nsa94.tmp (PID: 3260)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- cp.exe (PID: 3756)
- RegAsm.exe (PID: 2172)
- jet.exe (PID: 2740)
- 1656932762.exe (PID: 3504)
- 32.exe (PID: 4236)
- build.exe (PID: 4348)
- rwtweewge.exe (PID: 3524)
- beacon_wlan0.exe (PID: 4564)
- hv.exe (PID: 4844)
- Vpeswawqko.exe (PID: 4924)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- asdfg.exe (PID: 4964)
- BBLb.exe (PID: 5032)
- BBLb.exe (PID: 5092)
- asdjijjjjj.exe (PID: 5224)
- ghjk.exe (PID: 5296)
- chdyz.exe (PID: 5288)
- 2880911004.exe (PID: 4868)
- NBYS%20AH.NET.exe (PID: 5364)
- 80063188.exe (PID: 5408)
- RegSvcs.exe (PID: 3892)
- net.exe (PID: 4976)
- Everything.exe (PID: 3016)
- kb^fr_ouverture.exe (PID: 4432)
- 23.exe (PID: 5376)
- socks5-clean.exe (PID: 5860)
- inte.exe (PID: 5752)
- jsc.exe (PID: 5248)
- fw.exe (PID: 1852)
- ax.exe (PID: 4388)
- WatchDog.exe (PID: 4368)
- heaoyam78.exe (PID: 3976)
- data64_6.exe (PID: 4400)
- vcredist2013.exe (PID: 4340)
- vcredist2013.exe (PID: 4804)
- AttributeString.exe (PID: 4488)
- PCclear_Eng_mini.exe (PID: 5088)
- AttributeString.exe (PID: 5080)
- X89.exe (PID: 5160)
- svcservice.exe (PID: 2480)
- X89.exe (PID: 3600)
- xzw.exe (PID: 4712)
- MSBuild.exe (PID: 2156)
- MSBuild.exe (PID: 4128)
- ladas.exe (PID: 3960)
- setup294.exe (PID: 4428)
- Archevod_XWorm.exe (PID: 2876)
- tpeinf.exe (PID: 5656)
- first.exe (PID: 5660)
- Suaeweq.exe (PID: 5528)
- Client.exe (PID: 3012)
- native.exe (PID: 3464)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
- svchosl.exe (PID: 4116)
- cbchr.exe (PID: 5092)
- radbxnzdxbd.exe (PID: 5392)
- more.exe (PID: 1308)
- 666.exe (PID: 5484)
- v4install.exe (PID: 5816)
- win.exe (PID: 116)
- NeonRank.exe (PID: 5656)
- calc.exe (PID: 5728)
- beacon_certutil.exe (PID: 2128)
- chaospcap.exe (PID: 4380)
- 2.3.1.1.exe (PID: 6008)
- npp.exe (PID: 2028)
- zxcvb.exe (PID: 5444)
- agentServerComponent.exe (PID: 4088)
- amert.exe (PID: 5368)
- peinf.exe (PID: 4804)
- NPFInstall.exe (PID: 2176)
- l.exe (PID: 5072)
- Taxes.pif (PID: 2936)
- superz.exe (PID: 3016)
- Suaeweq.exe (PID: 1020)
- InstallSetup3.exe (PID: 5104)
- c53cfff621a84792162f70e790980e38.exe (PID: 1032)
- baseline.exe (PID: 2904)
- NPFInstall.exe (PID: 1544)
- for.exe (PID: 480)
- hncc.exe (PID: 4664)
- Client-built.exe (PID: 4008)
- flt_shovemydiscoupyourarse.exe (PID: 5196)
- RegAsm.exe (PID: 1900)
- yhdl.exe (PID: 4836)
- msedge.exe (PID: 4404)
- timeSync.exe (PID: 4360)
- Winlock.exe (PID: 6140)
- STAR.exe (PID: 5036)
- AUTOKEY.exe (PID: 5180)
- BroomSetup.exe (PID: 3616)
- 1.exe (PID: 4728)
- bott.exe (PID: 6120)
- NPFInstall.exe (PID: 5072)
- data64_1.exe (PID: 5016)
- drvinst.exe (PID: 5300)
- svchost.exe (PID: 2912)
- svchost.exe (PID: 4172)
- crypted_d786fd3e.exe (PID: 4444)
- InstallSetup9.exe (PID: 3124)
- stub.exe (PID: 4364)
- Update_new.exe (PID: 6052)
- InstallSetup7.exe (PID: 5444)
- DefenderControl.exe (PID: 4140)
- stub.exe (PID: 2536)
- asdfg.exe (PID: 6756)
- stub.exe (PID: 6816)
- 7e207560.exe (PID: 6848)
- 7e207560.exe (PID: 7124)
- 7e207560.exe (PID: 7144)
- pinguin.exe (PID: 6916)
- RegAsm.exe (PID: 2736)
- build6_unencrypted.exe (PID: 7256)
- more.exe (PID: 7480)
- stub.exe (PID: 7336)
- jopacrypt.exe (PID: 5092)
- Journal.exe (PID: 7624)
- 炎黄大陆.exe (PID: 5680)
- qemu-ga.exe (PID: 7580)
- lumma123142124.exe (PID: 2912)
- new.exe (PID: 7608)
- msedge.exe (PID: 7724)
- RegAsm.exe (PID: 7864)
- data64_5.exe (PID: 316)
- inte.exe (PID: 8168)
- stub.exe (PID: 8000)
- light.exe (PID: 3572)
Checks supported languages
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- plink.exe (PID: 3016)
- ed.exe (PID: 1192)
- Temp2.exe (PID: 3748)
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 3388)
- miner.exe (PID: 3904)
- fortnite3.exe (PID: 4032)
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 2044)
- asg.exe (PID: 2444)
- crypted.exe (PID: 3304)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 4004)
- RegAsm.exe (PID: 3960)
- fcc.exe (PID: 2596)
- tel.exe (PID: 1768)
- jjj.exe (PID: 3068)
- vbc.exe (PID: 2320)
- hack1226.exe (PID: 2240)
- vbc.exe (PID: 3472)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 4016)
- Screensaver.exe (PID: 4052)
- cs_maltest.exe (PID: 3740)
- Windows.exe (PID: 2920)
- 901d3bacbe82db5382c4f653efb11d4784254b3ad727530c73ae327b734c1a4b.exe (PID: 4008)
- cp.exe (PID: 3756)
- dsdasda.exe (PID: 796)
- svchost.exe (PID: 3060)
- 6.exe (PID: 3940)
- 891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe (PID: 2960)
- reo.exe (PID: 2208)
- T1_Net.exe (PID: 3400)
- BroomSetup.exe (PID: 3308)
- InstallSetup2.exe (PID: 1112)
- jet.exe (PID: 2740)
- crpta.exe (PID: 2944)
- payload.exe (PID: 2776)
- Update.exe (PID: 3720)
- LostArk.exe (PID: 3536)
- chcp.com (PID: 1976)
- SystemUpdate.exe (PID: 1928)
- LM.exe (PID: 2268)
- c4fc1686ecf325a5432309a2fec15357f6ff849252747ef44de7b4f1f4d4d1c2.exe (PID: 2868)
- inst77player_1.0.0.1.exe (PID: 2788)
- pei.exe (PID: 2732)
- vbc.exe (PID: 3972)
- conhost.exe (PID: 3392)
- abc.exe (PID: 1976)
- 1656932762.exe (PID: 3504)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 3544)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- soft.exe (PID: 1192)
- nsa94.tmp (PID: 3260)
- rwtweewge.exe (PID: 3524)
- RegAsm.exe (PID: 2172)
- jxszdjp.exe (PID: 2652)
- jxszdjpSrv.exe (PID: 900)
- DesktopLayer.exe (PID: 2548)
- 32.exe (PID: 4236)
- build.exe (PID: 4348)
- beacon_wlan0.exe (PID: 4564)
- soft.exe (PID: 4780)
- hv.exe (PID: 4844)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 4876)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 4884)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- Vpeswawqko.exe (PID: 4924)
- 2880911004.exe (PID: 4868)
- BBLb.exe (PID: 5032)
- asdfg.exe (PID: 5048)
- asdfg.exe (PID: 4964)
- BBLb.exe (PID: 5092)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 5076)
- asdjijjjjj.exe (PID: 5224)
- chdyz.exe (PID: 5288)
- ghjk.exe (PID: 5296)
- ghjk.exe (PID: 5396)
- 80063188.exe (PID: 5408)
- NBYS%20AH.NET.exe (PID: 5364)
- 2392218037.exe (PID: 2960)
- RegSvcs.exe (PID: 3892)
- 303458278.exe (PID: 4772)
- net.exe (PID: 4976)
- 1464916922.exe (PID: 2100)
- StealerClient_Cpp_1_3_1.exe (PID: 4376)
- kb^fr_ouverture.exe (PID: 4432)
- Project_8.exe (PID: 5660)
- 23.exe (PID: 5376)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 5368)
- Everything.exe (PID: 3016)
- socks5-clean.exe (PID: 5860)
- inte.exe (PID: 5752)
- wmlaunch.exe (PID: 5628)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 4228)
- jsc.exe (PID: 5248)
- fw.exe (PID: 1852)
- ax.exe (PID: 4388)
- 75d8077636ee1ec7b44f33cfdc65dc4a5b96d4c0b9ac3df0879b97e2bae1f9dd.exe (PID: 4800)
- Recorder.exe (PID: 4108)
- xzw.exe (PID: 4712)
- heaoyam78.exe (PID: 3976)
- vcredist2013.exe (PID: 4804)
- data64_6.exe (PID: 4400)
- WatchDog.exe (PID: 4368)
- vcredist2013.exe (PID: 4340)
- AttributeString.exe (PID: 4488)
- PCclear_Eng_mini.exe (PID: 5088)
- svcservice.exe (PID: 2480)
- AttributeString.exe (PID: 5080)
- X89.exe (PID: 5160)
- 1989831995.exe (PID: 4040)
- ladas.exe (PID: 3960)
- X89.exe (PID: 3600)
- MSBuild.exe (PID: 2156)
- MSBuild.exe (PID: 4128)
- richedit.exe (PID: 2788)
- Suaeweq.exe (PID: 5528)
- cb0e88abe7aee128ff8635e44df9797d0224aff000d03fc5d9166e575b50f4a1.exe (PID: 920)
- StealerClient_Cpp_1_4.exe (PID: 4384)
- setup294.exe (PID: 4428)
- Archevod_XWorm.exe (PID: 2876)
- bc_memories_from_the_mcp.exe (PID: 5612)
- tpeinf.exe (PID: 5656)
- 1262523516.exe (PID: 5400)
- 685321782.exe (PID: 1316)
- plug.exe (PID: 5696)
- first.exe (PID: 5660)
- 202184320.exe (PID: 4816)
- Client.exe (PID: 3012)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 2624)
- native.exe (PID: 3464)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 5824)
- 2967112945.exe (PID: 4420)
- lumma.exe (PID: 6064)
- lumma.exe (PID: 3396)
- radbxnzdxbd.exe (PID: 5392)
- svchosl.exe (PID: 4116)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 5644)
- cbchr.exe (PID: 5092)
- 666.exe (PID: 5484)
- more.exe (PID: 1308)
- v4install.exe (PID: 5816)
- win.exe (PID: 116)
- NeonRank.exe (PID: 5656)
- beacon_certutil.exe (PID: 2128)
- amert.exe (PID: 5368)
- 2.3.1.1.exe (PID: 6008)
- calc.exe (PID: 5728)
- chaospcap.exe (PID: 4380)
- npp.exe (PID: 2028)
- peinf.exe (PID: 4804)
- chaospc.exe (PID: 6036)
- zxcvb.exe (PID: 5444)
- agentServerComponent.exe (PID: 4088)
- Suaeweq.exe (PID: 1020)
- ns261A.tmp (PID: 5112)
- NPFInstall.exe (PID: 2176)
- l.exe (PID: 5072)
- 926924771.exe (PID: 5044)
- ns3156.tmp (PID: 5800)
- 1746625232.exe (PID: 5436)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 4232)
- ns333B.tmp (PID: 4860)
- Taxes.pif (PID: 2936)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 6140)
- ns3550.tmp (PID: 5572)
- NPFInstall.exe (PID: 6088)
- superz.exe (PID: 3016)
- news2_01.exe (PID: 6112)
- april.exe (PID: 884)
- ns3CE2.tmp (PID: 5520)
- NPFInstall.exe (PID: 1544)
- InstallSetup3.exe (PID: 5104)
- Client-built.exe (PID: 4008)
- baseline.exe (PID: 2904)
- for.exe (PID: 480)
- flt_shovemydiscoupyourarse.exe (PID: 5196)
- c53cfff621a84792162f70e790980e38.exe (PID: 1032)
- april.tmp (PID: 2184)
- BroomSetup.exe (PID: 3616)
- hncc.exe (PID: 4664)
- AUTOKEY.exe (PID: 5180)
- msedge.exe (PID: 4404)
- RegAsm.exe (PID: 1900)
- yhdl.exe (PID: 4836)
- Winlock.exe (PID: 6140)
- timeSync.exe (PID: 4360)
- 659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe (PID: 4600)
- stale.exe (PID: 4136)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 3580)
- ns6F8C.tmp (PID: 5996)
- bott.exe (PID: 6120)
- NPFInstall.exe (PID: 5072)
- STAR.exe (PID: 5036)
- 1.exe (PID: 4728)
- data64_1.exe (PID: 5016)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 4800)
- idrB5Event.exe (PID: 480)
- InstallSetup9.exe (PID: 3124)
- stub.exe (PID: 3056)
- crypted_d786fd3e.exe (PID: 4444)
- svchost.exe (PID: 2912)
- drvinst.exe (PID: 5300)
- InstallSetup7.exe (PID: 5444)
- DefenderControl.exe (PID: 4140)
- stub.exe (PID: 4364)
- Update_new.exe (PID: 6052)
- 炎黄大陆.exe (PID: 5680)
- svchost.exe (PID: 4172)
- stub.exe (PID: 2536)
- svchost.exe (PID: 5376)
- svchost.com (PID: 6344)
- svchost.com (PID: 6220)
- stub.exe (PID: 4756)
- svchost.com (PID: 6364)
- svchost.com (PID: 6384)
- 83f32a3d2dc9e3d9903f395a20b8ddd74a1f35487c6dffd67d9d9a014961f9d0.exe (PID: 6336)
- svchost.com (PID: 6540)
- svchost.com (PID: 6532)
- svchost.com (PID: 6460)
- svchost.com (PID: 6716)
- asdfg.exe (PID: 6756)
- svchost.com (PID: 6796)
- stub.exe (PID: 6816)
- svchost.com (PID: 6596)
- svchost.com (PID: 6904)
- pinguin.exe (PID: 6916)
- svchost.com (PID: 6976)
- asdfg.exe (PID: 6856)
- 7e207560.exe (PID: 6848)
- svchost.com (PID: 7092)
- 7e207560.exe (PID: 7124)
- 7e207560.exe (PID: 7144)
- RegAsm.exe (PID: 2736)
- svchost.com (PID: 7316)
- svchost.com (PID: 7308)
- svchost.com (PID: 7376)
- stub.exe (PID: 7336)
- svchost.com (PID: 7344)
- more.exe (PID: 7480)
- build6_unencrypted.exe (PID: 7256)
- svchost.com (PID: 7232)
- PCSupport.exe (PID: 7572)
- jopacrypt.exe (PID: 5092)
- Journal.exe (PID: 7624)
- svchost.com (PID: 7664)
- svchost.com (PID: 7600)
- qemu-ga.exe (PID: 7580)
- brg.exe (PID: 2888)
- new.exe (PID: 7608)
- lumma123142124.exe (PID: 2912)
- msedge.exe (PID: 7724)
- svchost.com (PID: 7796)
- svchost.com (PID: 7832)
- RegAsm.exe (PID: 7864)
- svchost.com (PID: 7808)
- light.exe (PID: 3572)
- svchost.com (PID: 8008)
- RegAsm.exe (PID: 8032)
- stub.exe (PID: 8000)
- data64_5.exe (PID: 316)
- svchost.com (PID: 8156)
- inte.exe (PID: 8168)
- InstallSetup8.exe (PID: 5972)
- svchost.com (PID: 8120)
- svchost.com (PID: 3420)
- svchost.com (PID: 3412)
- svchost.com (PID: 4284)
- svchost.com (PID: 4852)
- lve5.exe (PID: 5056)
- svchost.com (PID: 6256)
- ama.exe (PID: 5740)
- svchost.com (PID: 5768)
- StealerClient_Cpp_1_3.exe (PID: 7268)
Reads Environment values
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 2588)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 668)
- Temp2.exe (PID: 3748)
- asg.exe (PID: 2444)
- Windows.exe (PID: 2920)
- 6.exe (PID: 3940)
- reo.exe (PID: 2208)
- LostArk.exe (PID: 3536)
- miner.exe (PID: 3904)
- Update.exe (PID: 3720)
- build.exe (PID: 4348)
- RegAsm.exe (PID: 2172)
- Vpeswawqko.exe (PID: 4924)
- asdjijjjjj.exe (PID: 5224)
- chdyz.exe (PID: 5288)
- RegSvcs.exe (PID: 3892)
- jsc.exe (PID: 5248)
- data64_6.exe (PID: 4400)
- X89.exe (PID: 3600)
- Client.exe (PID: 3012)
- first.exe (PID: 5660)
- cbchr.exe (PID: 5092)
- 666.exe (PID: 5484)
- calc.exe (PID: 5728)
- chaospcap.exe (PID: 4380)
- agentServerComponent.exe (PID: 4088)
- Client-built.exe (PID: 4008)
- timeSync.exe (PID: 4360)
- AUTOKEY.exe (PID: 5180)
- bott.exe (PID: 6120)
- STAR.exe (PID: 5036)
- Update_new.exe (PID: 6052)
- RegAsm.exe (PID: 2736)
- data64_1.exe (PID: 5016)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 3216)
- 4363463463464363463463463.exe (PID: 3072)
- 4363463463464363463463463.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 3232)
- 4363463463464363463463463.exe (PID: 4092)
- 4363463463464363463463463.exe (PID: 840)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 2420)
- 4363463463464363463463463.exe (PID: 2588)
- Update.exe (PID: 3720)
- build.exe (PID: 4348)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- asdjijjjjj.exe (PID: 5224)
- RegSvcs.exe (PID: 3892)
- data64_6.exe (PID: 4400)
- ladas.exe (PID: 3960)
- 666.exe (PID: 5484)
- drvinst.exe (PID: 5300)
- NPFInstall.exe (PID: 5072)
- Update_new.exe (PID: 6052)
- RegAsm.exe (PID: 2736)
- data64_1.exe (PID: 5016)
Checks proxy server information
- plink.exe (PID: 3016)
- fortnite3.exe (PID: 4032)
- InstallSetup2.exe (PID: 1112)
- pei.exe (PID: 2732)
- abc.exe (PID: 1976)
- 2-3-1_2023-12-14_13-35.exe (PID: 3416)
- nsa94.tmp (PID: 3260)
- 1656932762.exe (PID: 3504)
- beacon_wlan0.exe (PID: 4564)
- 2880911004.exe (PID: 4868)
- 80063188.exe (PID: 5408)
- inte.exe (PID: 5752)
- fw.exe (PID: 1852)
- PCclear_Eng_mini.exe (PID: 5088)
- svcservice.exe (PID: 2480)
- X89.exe (PID: 3600)
- xzw.exe (PID: 4712)
- tpeinf.exe (PID: 5656)
- Suaeweq.exe (PID: 5528)
- beacon_certutil.exe (PID: 2128)
- 2.3.1.1.exe (PID: 6008)
- peinf.exe (PID: 4804)
- npp.exe (PID: 2028)
- Suaeweq.exe (PID: 1020)
- baseline.exe (PID: 2904)
- yhdl.exe (PID: 4836)
- timeSync.exe (PID: 4360)
- InstallSetup3.exe (PID: 5104)
- svchosl.exe (PID: 4116)
- mspaint.exe (PID: 4900)
- 7e207560.exe (PID: 6848)
- Journal.exe (PID: 7624)
- inte.exe (PID: 8168)
Creates files or folders in the user directory
- fcc.exe (PID: 2596)
- asg.exe (PID: 2444)
- reo.exe (PID: 2208)
- LostArk.exe (PID: 3536)
- BroomSetup.exe (PID: 3308)
- pei.exe (PID: 2732)
- InstallSetup2.exe (PID: 1112)
- 1656932762.exe (PID: 3504)
- BBLb.exe (PID: 5092)
- 80063188.exe (PID: 5408)
- conhost.exe (PID: 3392)
- 23.exe (PID: 5376)
- inte.exe (PID: 5752)
- ax.exe (PID: 4388)
- dialer.exe (PID: 5136)
- ladas.exe (PID: 3960)
- Client.exe (PID: 3012)
- Archevod_XWorm.exe (PID: 2876)
- v4install.exe (PID: 5816)
- cbchr.exe (PID: 5092)
- peinf.exe (PID: 4804)
- stale.exe (PID: 4136)
- RegAsm.exe (PID: 1900)
- more.exe (PID: 1308)
- Client-built.exe (PID: 4008)
- yhdl.exe (PID: 4836)
- STAR.exe (PID: 5036)
- InstallSetup3.exe (PID: 5104)
- inte.exe (PID: 8168)
Process checks whether UAC notifications are on
- miner.exe (PID: 3904)
- LostArk.exe (PID: 3536)
- AUTOKEY.exe (PID: 5180)
- Update_new.exe (PID: 6052)
- new.exe (PID: 7608)
Create files in a temporary directory
- 4363463463464363463463463.exe (PID: 840)
- InstallSetup2.exe (PID: 1112)
- jet.exe (PID: 2740)
- payload.exe (PID: 2776)
- LostArk.exe (PID: 3536)
- inst77player_1.0.0.1.exe (PID: 2788)
- pei.exe (PID: 2732)
- miner.exe (PID: 3904)
- cp.exe (PID: 3756)
- 1656932762.exe (PID: 3504)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 4884)
- build.exe (PID: 4348)
- asdfg.exe (PID: 4964)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 4916)
- 2880911004.exe (PID: 4868)
- asdjijjjjj.exe (PID: 5224)
- 80063188.exe (PID: 5408)
- conhost.exe (PID: 3392)
- socks5-clean.exe (PID: 5860)
- hv.exe (PID: 4844)
- jsc.exe (PID: 5248)
- vcredist2013.exe (PID: 4804)
- ladas.exe (PID: 3960)
- setup294.exe (PID: 4428)
- tpeinf.exe (PID: 5656)
- Client.exe (PID: 3012)
- radbxnzdxbd.exe (PID: 5392)
- cbchr.exe (PID: 5092)
- NeonRank.exe (PID: 5656)
- chaospcap.exe (PID: 4380)
- npp.exe (PID: 2028)
- peinf.exe (PID: 4804)
- amert.exe (PID: 5368)
- l.exe (PID: 5072)
- superz.exe (PID: 3016)
- InstallSetup3.exe (PID: 5104)
- april.exe (PID: 884)
- april.tmp (PID: 2184)
- Winlock.exe (PID: 6140)
- AUTOKEY.exe (PID: 5180)
- NPFInstall.exe (PID: 5072)
- stub.exe (PID: 4364)
- mspaint.exe (PID: 4900)
- more.exe (PID: 1308)
- DefenderControl.exe (PID: 4140)
Reads product name
- 6.exe (PID: 3940)
- RegAsm.exe (PID: 2172)
- build.exe (PID: 4348)
- asdjijjjjj.exe (PID: 5224)
- jsc.exe (PID: 5248)
- X89.exe (PID: 3600)
- agentServerComponent.exe (PID: 4088)
- timeSync.exe (PID: 4360)
- bott.exe (PID: 6120)
- STAR.exe (PID: 5036)
Creates files in the program directory
- jxszdjpSrv.exe (PID: 900)
- jet.exe (PID: 2740)
- iexplore.exe (PID: 948)
- ladas.exe (PID: 3960)
- xzw.exe (PID: 4712)
- win.exe (PID: 116)
- chaospcap.exe (PID: 4380)
- NPFInstall.exe (PID: 2176)
- yhdl.exe (PID: 4836)
- 7e207560.exe (PID: 6848)
Application launched itself
- msedge.exe (PID: 2424)
- msedge.exe (PID: 1992)
- msedge.exe (PID: 5772)
- msedge.exe (PID: 5980)
Reads CPU info
- 32.exe (PID: 4236)
- xzw.exe (PID: 4712)
- timeSync.exe (PID: 4360)
Drops the executable file immediately after the start
- dialer.exe (PID: 5136)
Reads security settings of Internet Explorer
- control.exe (PID: 5640)
Reads mouse settings
- Taxes.pif (PID: 2936)
- DefenderControl.exe (PID: 4140)
Adds/modifies Windows certificates
- drvinst.exe (PID: 5300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3472) vbc.exe
C2 (1)149.28.205.74:2470
Botnetsocicalbot
Options
ErrorMessage
Keys
XorOvercloud
(PID) Process(2320) vbc.exe
C2 (1)51.210.137.6:47909
BotnetLogsDiller Cloud (Telegram: @logsdillabot)
Options
ErrorMessage
Keys
XorConformity
(PID) Process(3972) vbc.exe
C2 (1)62.233.51.177:14107
Botnetadel
Options
ErrorMessage
Keys
XorSneerers
(PID) Process(480) for.exe
C2 (1)185.172.128.33:8924
Botnet@logscloudyt_bot
Options
ErrorMessage
Keys
XorConsumer
(PID) Process(1900) RegAsm.exe
C2 (1)185.172.128.33:8924
Botnet@logscloudyt_bot
Options
ErrorMessage
Keys
XorConsumer
Nanocore
(PID) Process(3536) LostArk.exe
KeyboardLoggingTrue
BuildTime2023-11-14 15:50:39.647800
Version1.2.2.0
Mutex6f5daffa-fc40-4bef-9872-fc117fab9294
DefaultGroupDefault
PrimaryConnectionHost43.143.228.239
BackupConnectionHost43.143.228.239
ConnectionPort7766
RunOnStartupFalse
RequestElevationFalse
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlTrue
SetCriticalProcessTrue
PreventSystemSleepTrue
ActivateAwayModeTrue
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
Remcos
(PID) Process(3940) 6.exe
C2 (9)hendersonk1.hopto.org:2404
henderson1.camdvr.org:2404
centplus1.serveftp.com:2404
harrywlike.ddns.net:2404
genekol.nsupdate.info:2404
harrywlike1.ddns.net:2404
hendersonk2022.hopto.org:2404
genekol1.nsupdate.info:2404
generem.camdvr.org:2404
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\ShellGY99V
Setup_path%APPDATA%
Copy_filesonic.exe
Startup_valuefuckuuuuu
Hide_fileFalse
Mutex_namegsgjdwg-1J0WWM
Keylog_flag1
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_namenotepad;solitaire;
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_dirMicRecords
Connect_delay0
Copy_diryakkk
Keylog_dirchrome
Max_keylog_file20000
AsyncRat
(PID) Process(2208) reo.exe
C2 (1)82.115.223.244
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexfnpxcekdvtg
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureR5JBH2qOF7T5fwa7g4eE4qJ0CTWyADGjVvVqEpZLxqOz7ijIknIV9ddo6ba7ZkTKoBhHhGTgyJ6VkPBFfLs2Z002xZYx/yjole+Ba20yb0ZFTo0rvIGTC2W07sVYXYuBPDufInu02QMD/V3ZMybsQNohmDOnbjhQMcN3WkLsCWY=
Keys
AES3a20c7b13b8c19efdcfc7fdc4d6ed716151cf871d53115133cc297be7f298f08
SaltVenomRATByVenom
(PID) Process(5484) 666.exe
C2 (3)127.0.0.1
qiefuwuqi.20242525.xyz
175.24.197.196
Ports (1)53576
BotnetDefault
VersionLMTEAM RAT 远控 v10.0.0
Options
AutoRuntrue
Mutexencffhopetwiqlwo
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICNzCCAaCgAwIBAgIVAJ63XcWUSwHUfcXzH/xfUvbn7AsDMA0GCSqGSIb3DQEBDQUAMGgxFjAUBgNVBAMMDUxNVEVBTSBTZXJ2ZXIxEzARBgNVBAsMCnF3cWRhbmNodW4xHzAdBgNVBAoMFlZlbm9tUkFUIEJ5IHF3cWRhbmNodW4xCzAJBgNVBAcMAlNIMQswCQYDVQQGEwJDTjAeFw0yMjA4MjYwOTI0NTBaFw0zMzA2MDQwOTI0NTBaMBMxETAPBgNVBAMMCFZlbm9tUkFUMIGfMA0GCSqGSIb3DQEB...
Server_SignatureKWBGGJAAfUXEt4htszXVxNx6rIZYwNWWTPactiBeZQI02tJn/heGesmMrlvcl5TCgrFBPEXT+LY1evi6tKfAJojHRJxMJiCIuzuMLzZSFCXL+/1Tyic+u3d8BgIkZqFG02uBHURbw0FGvZcH4r1o7kJhIyHsUGw9ZBrY5ZjdYXs=
Keys
AES2b84f4b7ac2be24e77cb2c2a6f70cd0327feb801dbd467a427d95e614f77912a
SaltVenomRATByVenom
(PID) Process(5728) calc.exe
C2 (1)89.23.100.93
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexoonrejgwedvxwse
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureQjWeZe4F4TuWy0hUx2CJx3viPXMuRkFhkXGrVGT29pa7LM+06mEXhUkglBWpLmYPaFBKG5FEqOime2j0+7Cf0hyosj2teh9TnTiRihwU6ooSTFBg9MLZW6DOqN3NYbQAxzaJZu29Z/KHkeaWOVYrTDURnnk62Z+gzdMHhMH1F5k=
Keys
AES30514d0354cda998b840312f75ae05f11383b533e04a6b2d1084a39d2adc412e
SaltVenomRATByVenom
CobalStrike
(PID) Process(1976) abc.exe
C2 (1)23.94.0.126/dot.gif
BeaconTypeHTTP
Port5656
SleepTime60000
MaxGetSize1048576
Jitter0
MaxDNS255
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDHXb15AVj1pjZAKxyNCMYZa+eR
Y/uLpqnj1NdS+BFAXao4GI9MAOUBEvtfcf9Y7T9HkDnGrX5EoNqZuPVWng916WMb
ktrRaZudOdTp4TK+xtfHvF5uVRSdl94lBG6lAzuH65xUZCdcclTT2iY52bUqvOOn
RyYzHBvi57nmVei+swIDAQAB
-----END PUBLIC KEY-----
UserAgentMozilla/5.0 (compatible; MSIE 10.0; Windows NT 6.1; WOW64; Trident/6.0)
HttpPostUri/submit.php
HttpGet_Metadata
SessionId (2)base64
header: Cookie
HttpPost_Metadata
ConstHeaders (1)Content-Type: application/octet-stream
SessionId (1)parameter: id
Output (1)print
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\rundll32.exe
Spawnto_x64%windir%\sysnative\rundll32.exe
CryptoScheme0
DNS_Idle0.0.0.0
DNS_Sleep0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark0
bStageCleanupFalse
bCFGCautionFalse
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXTrue
bProcInject_MinAllocSize0
ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_Stub187ab8f98098de95714613f8544c9613
ProcInject_AllocationMethodVirtualAllocEx
(PID) Process(4564) beacon_wlan0.exe
C2 (1)23.94.0.126/dpixel
BeaconTypeHTTP
Port5656
SleepTime60000
MaxGetSize1048576
Jitter0
MaxDNS255
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDHXb15AVj1pjZAKxyNCMYZa+eR
Y/uLpqnj1NdS+BFAXao4GI9MAOUBEvtfcf9Y7T9HkDnGrX5EoNqZuPVWng916WMb
ktrRaZudOdTp4TK+xtfHvF5uVRSdl94lBG6lAzuH65xUZCdcclTT2iY52bUqvOOn
RyYzHBvi57nmVei+swIDAQAB
-----END PUBLIC KEY-----
UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; BOIE9;SVSE)
HttpPostUri/submit.php
HttpGet_Metadata
SessionId (2)base64
header: Cookie
HttpPost_Metadata
ConstHeaders (1)Content-Type: application/octet-stream
SessionId (1)parameter: id
Output (1)print
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\rundll32.exe
Spawnto_x64%windir%\sysnative\rundll32.exe
CryptoScheme0
DNS_Idle0.0.0.0
DNS_Sleep0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark0
bStageCleanupFalse
bCFGCautionFalse
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXTrue
bProcInject_MinAllocSize0
ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_Stub187ab8f98098de95714613f8544c9613
ProcInject_AllocationMethodVirtualAllocEx
(PID) Process(2128) beacon_certutil.exe
C2 (1)192.168.253.77/visit.js
BeaconTypeHTTP
Port80
SleepTime60000
MaxGetSize1048576
Jitter0
MaxDNS255
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCVwARobrGhqWCXN/XRIuNZ5q5+
Uov2bznkq3vNktBADqbVMtaPY/im4uErVCP4+xAAcCh8y+JWcNVWTDg12265g1Im
QIXqvVCswMcVRDod5yrIoaFM4jNtgwQkeEC9txwhC+ZGqvbnc+0uXTU43VAGfMH8
0vPecohI7MLV6sujSwIDAQAB
-----END PUBLIC KEY-----
UserAgentMozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0; NP09; NP09; MAAU)
HttpPostUri/submit.php
HttpGet_Metadata
SessionId (2)base64
header: Cookie
HttpPost_Metadata
ConstHeaders (1)Content-Type: application/octet-stream
SessionId (1)parameter: id
Output (1)print
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\rundll32.exe
Spawnto_x64%windir%\sysnative\rundll32.exe
CryptoScheme0
DNS_Idle0.0.0.0
DNS_Sleep0
HttpGet_VerbGET
HttpPost_VerbPOST
HttpPostChunk0
Watermark0
bStageCleanupFalse
bCFGCautionFalse
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXTrue
bProcInject_MinAllocSize0
ProcInject_PrependAppend_x86000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_PrependAppend_x64000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000...
ProcInject_Stub187ab8f98098de95714613f8544c9613
ProcInject_AllocationMethodVirtualAllocEx
AgentTesla
(PID) Process(3892) RegSvcs.exe
Protocolsmtp
Hostmail.kabeercommodities.com
Port587
Usernameexport@kabeercommodities.com
Passwordw{A6H.o&sz%g
LaplasClipper
(PID) Process(2480) svcservice.exe
C2 (1)http://45.159.189.105
Options
API Keyec991afa49df4efe459cfb97dc0f831257f3b06880dca401726b96cab6cb269a
Strings (6)^XZ]Z_]^]e459cfb97dc0f831257f3b06880dca401726b96cab6cb269Z
ec991afa49df4ef^X]Y_X]257f3b06880dca401726b96cab6cb269a
^XZ]Z_]^]e459cfb97dc0f831]Y_XZ1726b96cab6cb269Z
x86_64-SSE4-AVX2
/bot/online?guid
/bot/get?address
XWorm
(PID) Process(2876) Archevod_XWorm.exe
C2canadian-perspectives.gl.at.ply.gg:33203
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameScammers
MutexTLsk4Xp0P8GNpwQw
Quasar
(PID) Process(4008) Client-built.exe
Version1.4.1
C2 (2)91.92.254.40:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex56928f7b-c5c9-4b24-af59-8c509ce1d27e
StartupWindows System
TagOffice04
LogDirLogs
SignatureCeYV8lX1NamhFqmPLVBDADuQSrMo0kQ0aWmxnDh4MBNXPFWN7WMlFJcwTn0BagiqpaCjQWPhrC+B0xa8h1tsTEQJFuLoGn8PBCC0TjsMstDtUtoql4BKX+9rFPdKNfWPqBLm7sAEDWbYUYGgOz1OlHGCS0t7MDlhdovxK8jeWJ+swE0SMGKIEUvmd8UDULE+dSvkDgDzfUDQfKZDJ+l9XlQ9R+4+2AZTmgBb7ADv7g12BxWdRlb1ELw+t04BiglXiZwP1pWdcA73pN0YTEeFs8qbKT+WmXuTuWwGMufarNNn...
CertificateMIIE9DCCAtygAwIBAgIQAPfYIoZ22LcKgTqBDTL7xzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDEwNjE3MDUzNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAlc37TNMpuOx/OXIAkf5qVsg0rM8Tms8+Tooakdutaa4+mH0cyJaoMm1Zc0GQ2jvfTovqZRVn...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
609
Monitored processes
415
Malicious processes
140
Suspicious processes
27
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\Files\win.exe" | C:\Users\admin\Desktop\Files\win.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 120 | "schtasks" /create /tn "WSUS Update Client" /sc ONLOGON /tr "C:\Users\admin\Desktop\Files\Temp2.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Temp2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | "C:\Users\admin\Desktop\Files\data64_5.exe" | C:\Users\admin\Desktop\Files\data64_5.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\Desktop\Files\for.exe" | C:\Users\admin\Desktop\Files\for.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Guardrails Aloin Cogent Integrity Level: HIGH Description: List Controller Setup Exit code: 0 Version: 1.0.0.0 Modules
RedLine(PID) Process(480) for.exe C2 (1)185.172.128.33:8924 Botnet@logscloudyt_bot Options ErrorMessage Keys XorConsumer | |||||||||||||||
| 480 | "C:\Users\admin\Desktop\Files\idrB5Event.exe" | C:\Users\admin\Desktop\Files\idrB5Event.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: iTop Integrity Level: HIGH Description: iTop Black Friday Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 796 | "C:\Users\admin\Desktop\Files\dsdasda.exe" | C:\Users\admin\Desktop\Files\dsdasda.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Performance Booster Integrity Level: HIGH Description: Grizzly Eternal Fabric Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 840 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\Temp\april.exe" | C:\Users\admin\AppData\Local\Temp\april.exe | superz.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: WebSocket connection routine Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
491 864
Read events
488 867
Write events
2 662
Delete events
335
Modification events
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
264
Suspicious files
244
Text files
149
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3232 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\svchost.exe | executable | |
MD5:A4D0F1FC59C798520A9733366B3E5D38 | SHA256:C162762C875E3F77E5BA98ACFE55D0A6177F9CFF23010C5DE537BE7BBC7E5417 | |||
| 2596 | fcc.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4092 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\fortnite3.exe | executable | |
MD5:ED0A563D3D57D03356187C1A2FBCCE3F | SHA256:ED78295A1B60B7053383C7F2A4837C62CB5625D7D57B5F4121DF45660A000C65 | |||
| 668 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe | executable | |
MD5:8E34D5CF7E39F355CDAA0A9BA0533901 | SHA256:F4438ED05971A15D70C9683DC9E1A55C583EA8C61039E9E85EB391CA6E3FA0AE | |||
| 2444 | asg.exe | C:\Users\admin\AppData\Roaming\WSUS Logs\02-12-2024 | binary | |
MD5:EF246BE9F8D9F1BC8CE1E196D091D414 | SHA256:35CB28A4681A856C46DA04531AEE703DC95CC8F801E7803F3BAFDD1B8578F7CE | |||
| 4092 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Temp2.exe | executable | |
MD5:5EBE890F034F15D9500328551B76A01E | SHA256:3588657707CD5B04586693C6600BE0159B321B258F48953F824FAA876F6B8566 | |||
| 1628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\plink.exe | executable | |
MD5:7E559DC4E162F6AAEE6A034FA2D9C838 | SHA256:4C2E05ACAD9E625BA60CA90FA7CCE6A1B11A147E00F43E0F29225FAEFF6B54AA | |||
| 4004 | 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe | C:\Windows\Temp\tel.exe | executable | |
MD5:89A44C83A4CB4AE7C59C5AFDE077EF7A | SHA256:8FB82C9BE07771A2F7A7A436F01283387516A8223AA7F6DADAC71403066D8D83 | |||
| 1628 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\ed.exe | executable | |
MD5:25CA432628E62C0C1C9DA458A8A92BCA | SHA256:F4D0F5FE6A6D8A08AF49798B15856A79D9DD5319D1EF4BEAC63883379EA17E71 | |||
| 3232 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\hack1226.exe | executable | |
MD5:D259A1C0C84BBEEFB84D11146BD0EBE5 | SHA256:8DE12184A006D3340241492BACA0BA1034182B08D3C6A0F09C0AF99D539BD48B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
187
TCP/UDP connections
15 394
DNS requests
179
Threats
797
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3216 | 4363463463464363463463463.exe | GET | — | 91.215.85.223:80 | http://marksidfg.ug/ghjkl.exe | unknown | — | — | unknown |
— | — | GET | 200 | 107.161.183.211:80 | http://mail.alphaassessoriato.com.br/clp.exe | unknown | executable | 1.13 Mb | unknown |
1628 | 4363463463464363463463463.exe | GET | 200 | 5.148.32.222:6789 | http://5.148.32.222:6789/plink.exe | unknown | executable | 312 Kb | unknown |
3232 | 4363463463464363463463463.exe | GET | 200 | 62.109.150.108:80 | http://starozitnictvi-znojmo.cz/ed.exe | unknown | executable | 748 Kb | unknown |
1628 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.121:80 | http://185.172.128.121/svchost.exe | unknown | executable | 5.98 Mb | unknown |
840 | 4363463463464363463463463.exe | GET | 200 | 123.139.99.35:80 | http://d1.udashi.com/soft/aqsd/5084/%E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe | unknown | executable | 1.91 Mb | unknown |
3748 | Temp2.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 293 b | unknown |
4092 | 4363463463464363463463463.exe | GET | 200 | 43.143.228.239:80 | http://43.143.228.239/LostArk.exe | unknown | executable | 203 Kb | unknown |
2596 | fcc.exe | POST | 200 | 65.21.213.208:3000 | http://65.21.213.208:3000/check | unknown | — | — | unknown |
3232 | 4363463463464363463463463.exe | GET | 200 | 208.86.224.90:80 | http://cd.textfiles.com/hmatrix/Data/hack1226.exe | unknown | — | 63.7 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3216 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3216 | 4363463463464363463463463.exe | 91.215.85.223:80 | marksidfg.ug | — | RU | unknown |
2420 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2420 | 4363463463464363463463463.exe | 104.192.141.1:443 | bitbucket.org | AMAZON-02 | US | unknown |
3072 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3072 | 4363463463464363463463463.exe | 107.161.183.211:80 | mail.alphaassessoriato.com.br | DIMENOC | US | unknown |
2420 | 4363463463464363463463463.exe | 3.5.29.187:443 | bbuseruploads.s3.amazonaws.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
marksidfg.ug |
| unknown |
bitbucket.org |
| shared |
mail.alphaassessoriato.com.br |
| unknown |
bbuseruploads.s3.amazonaws.com |
| shared |
starozitnictvi-znojmo.cz |
| unknown |
github.com |
| shared |
muzzumilruheel.com |
| malicious |
raw.githubusercontent.com |
| shared |
d1.udashi.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3072 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3072 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3072 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3072 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1628 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3232 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3232 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
1628 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
51 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
2-3-1_2023-12-14_13-35.exe | tw0xu14w8 |
2-3-1_2023-12-14_13-35.exe | tf9fnyzeu |
2-3-1_2023-12-14_13-35.exe | tv8nwi2ye |
2-3-1_2023-12-14_13-35.exe | tv8nwi2ye |