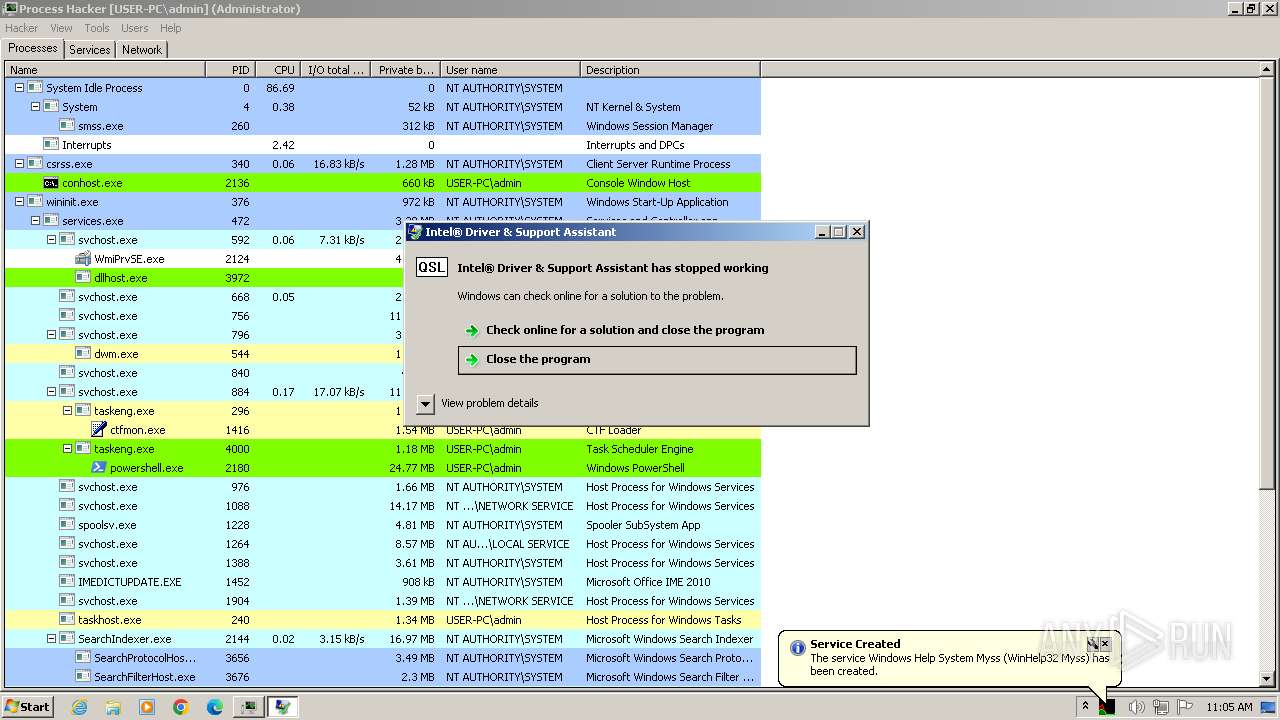
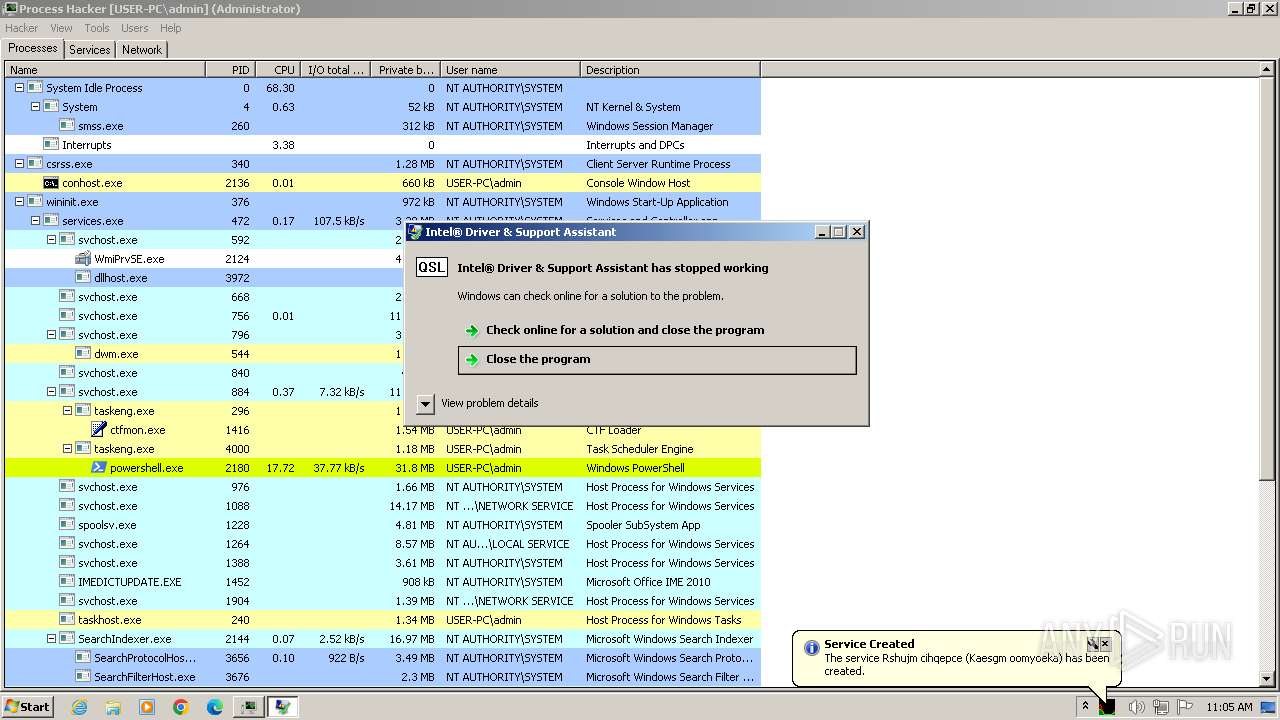
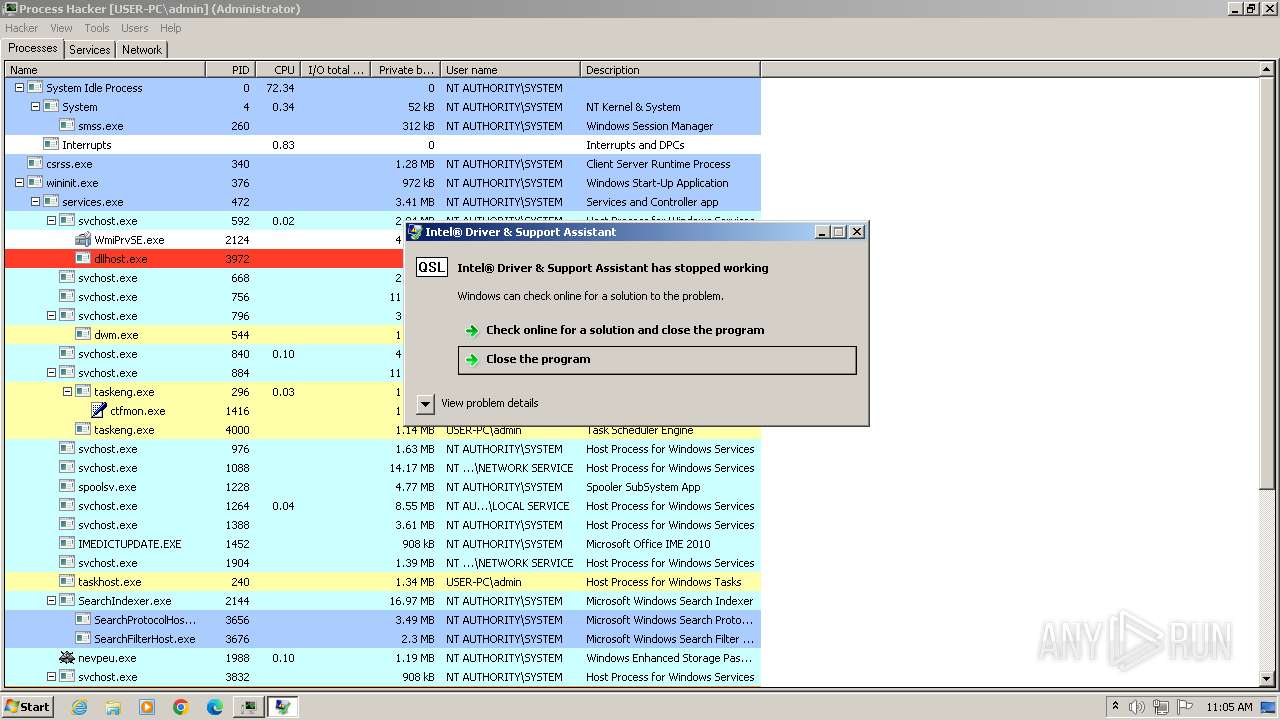
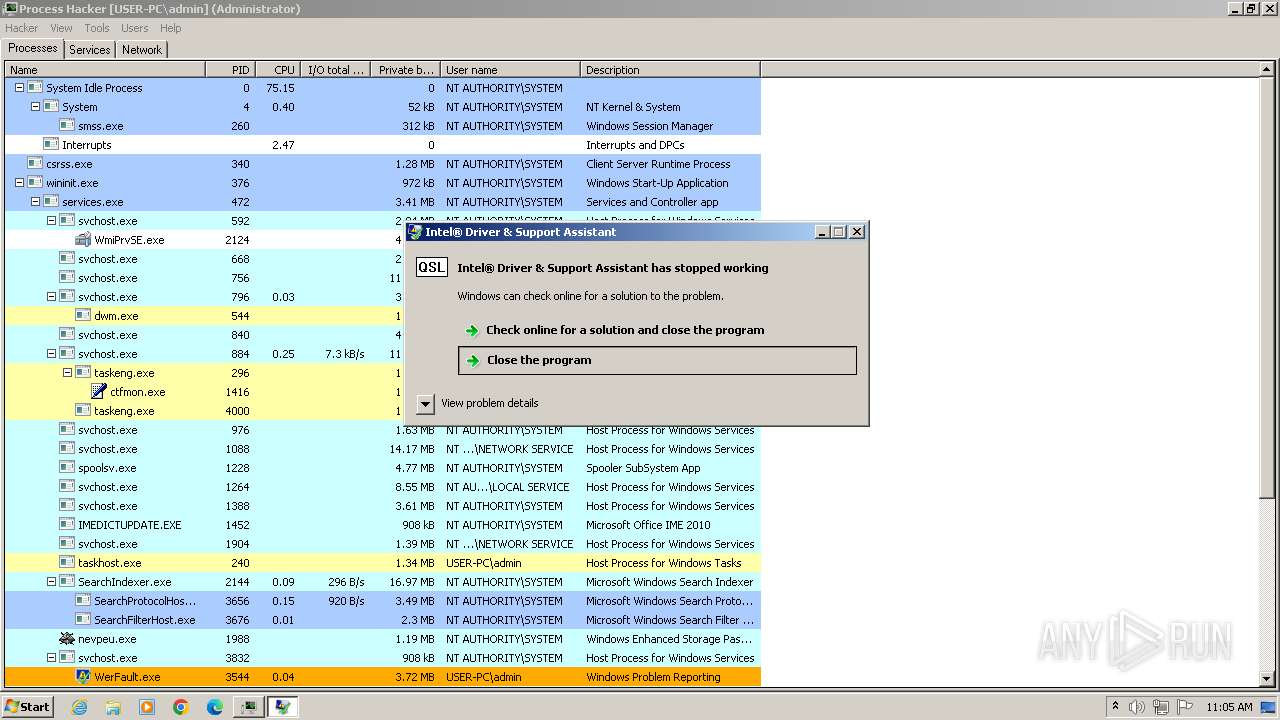
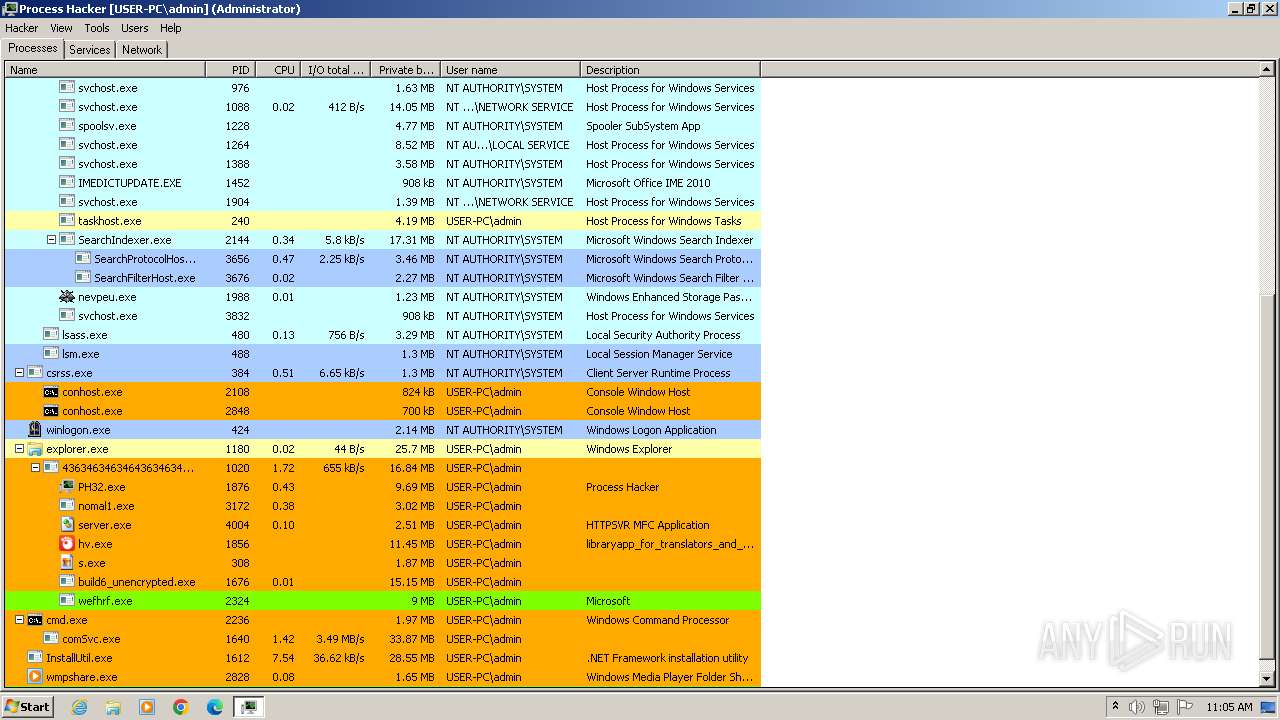
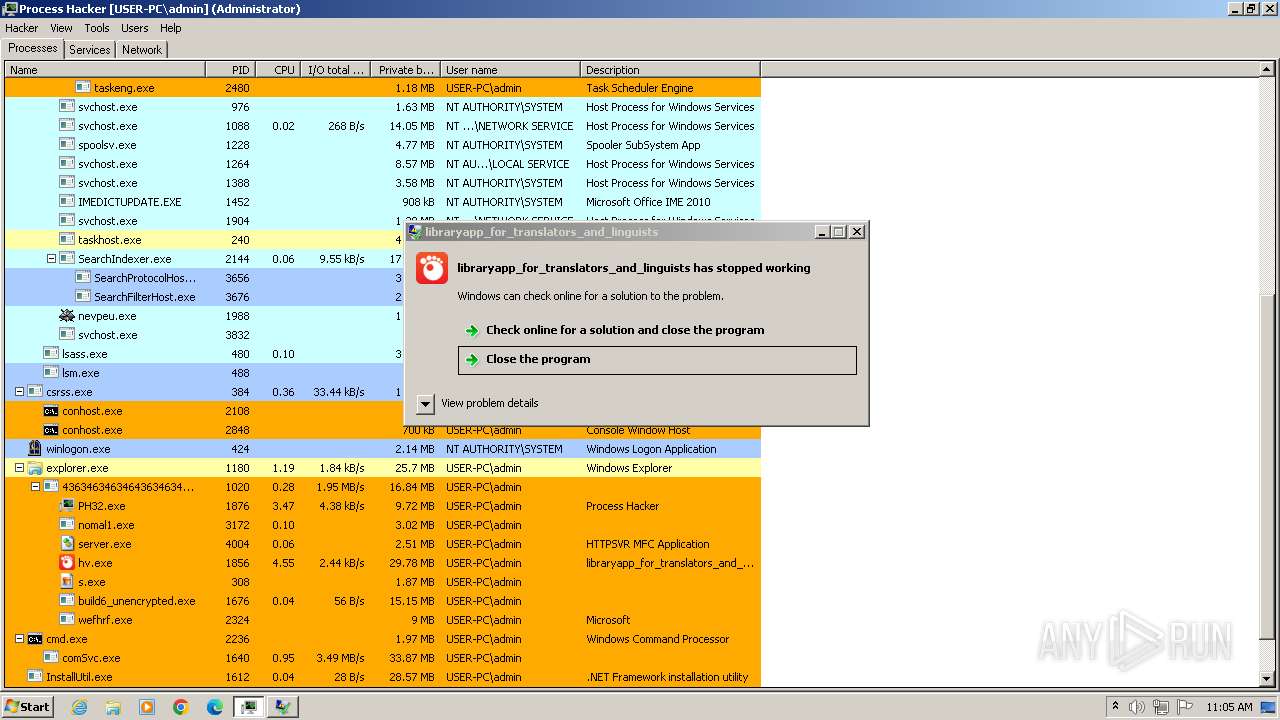
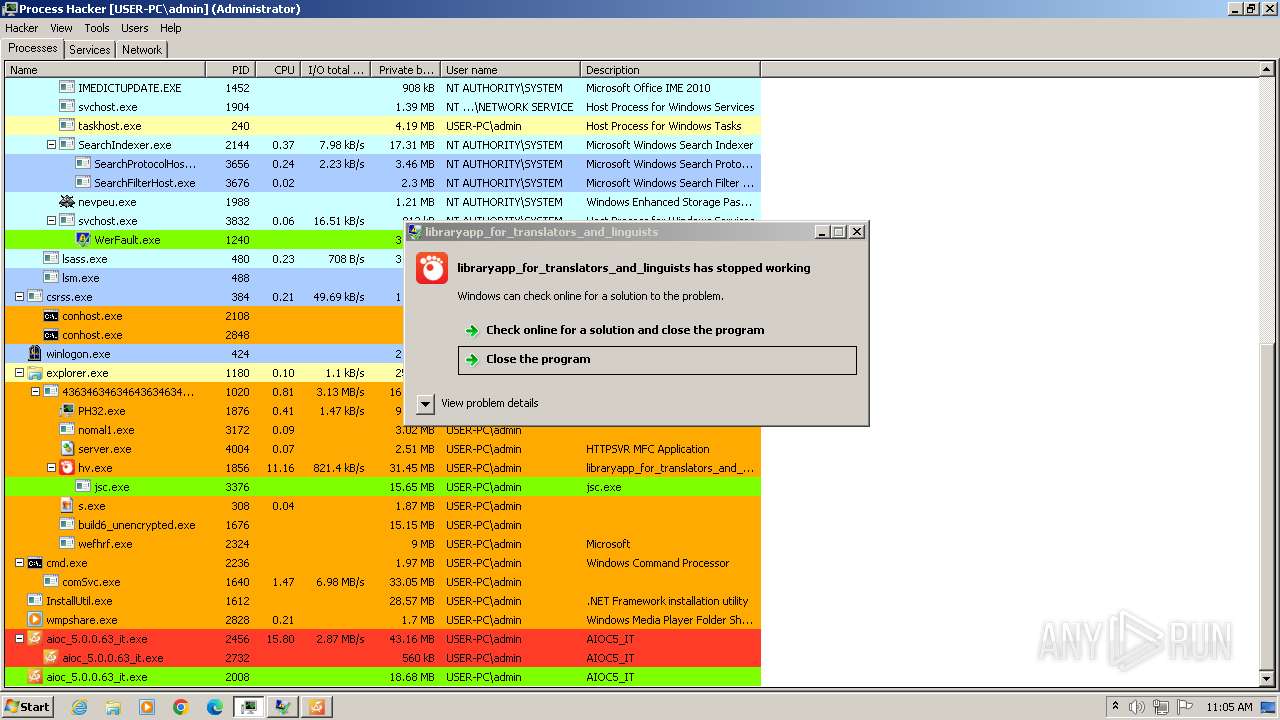
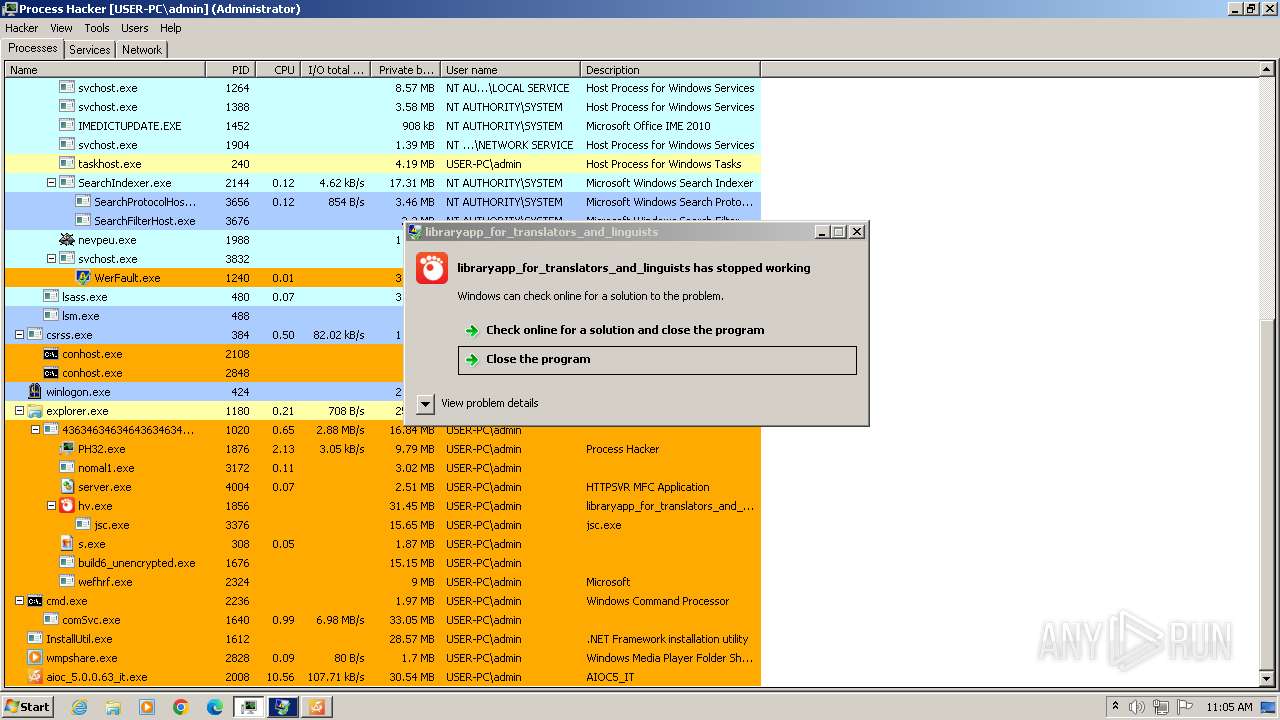
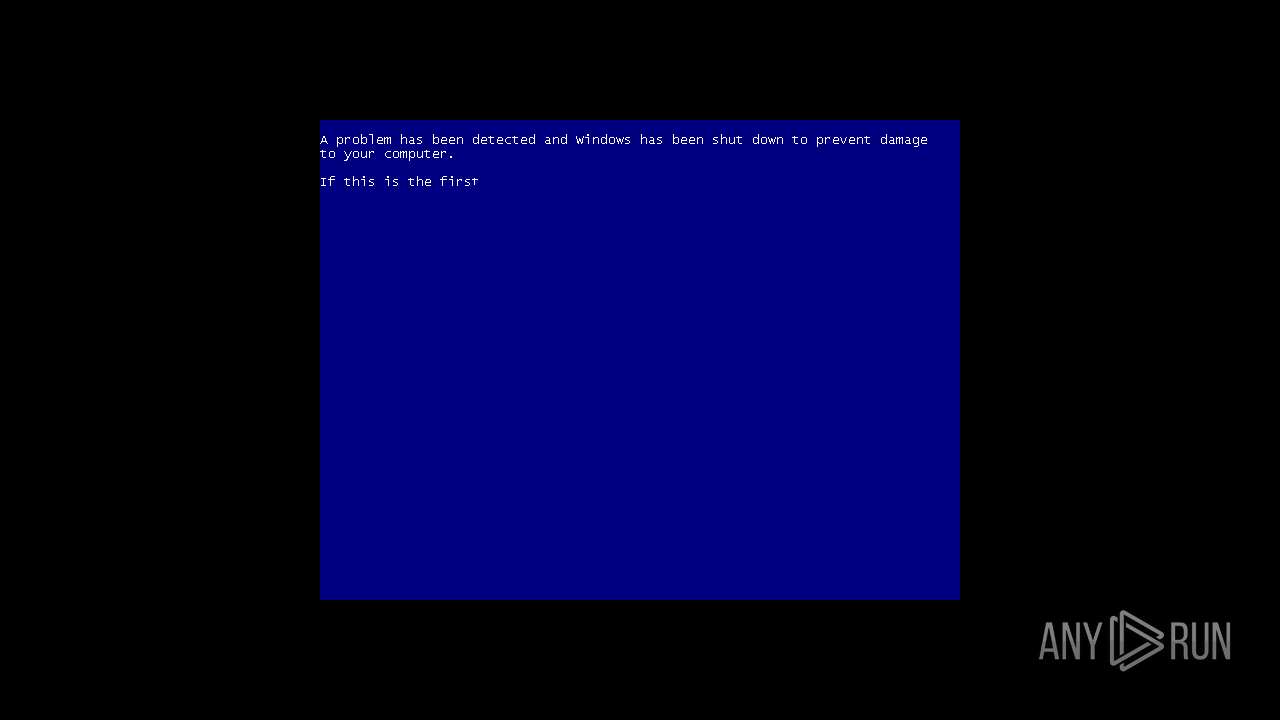
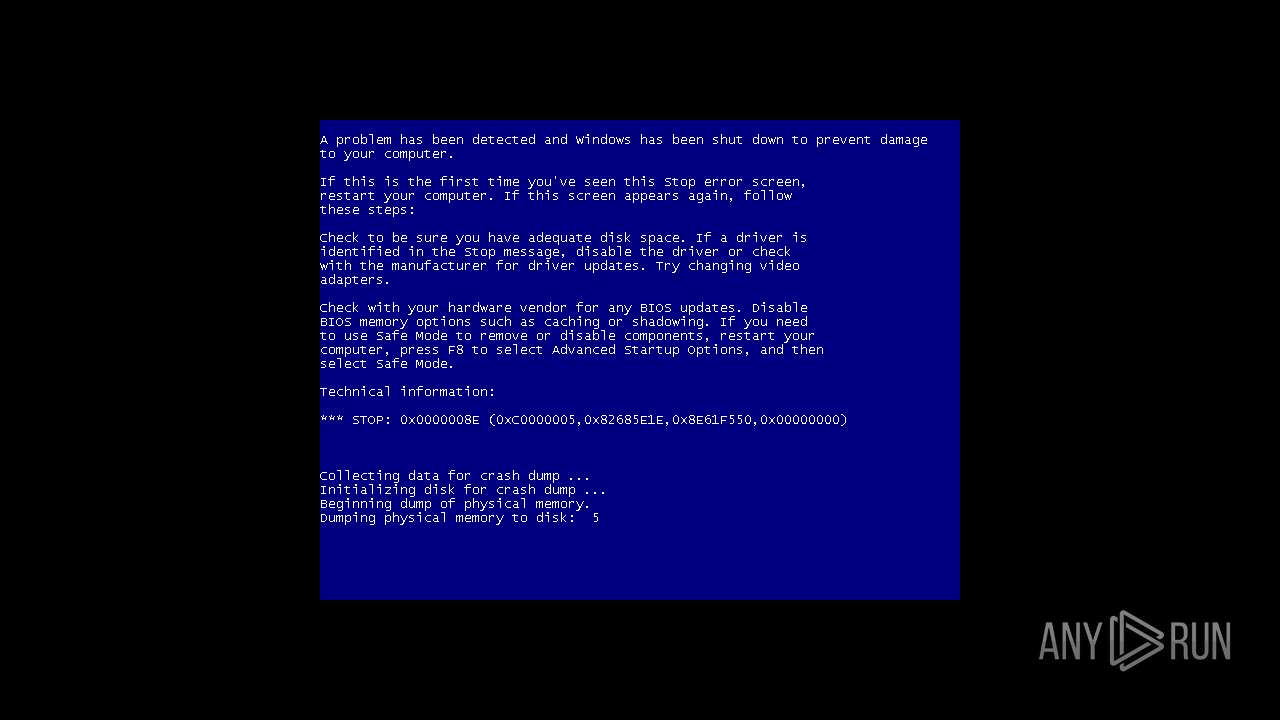
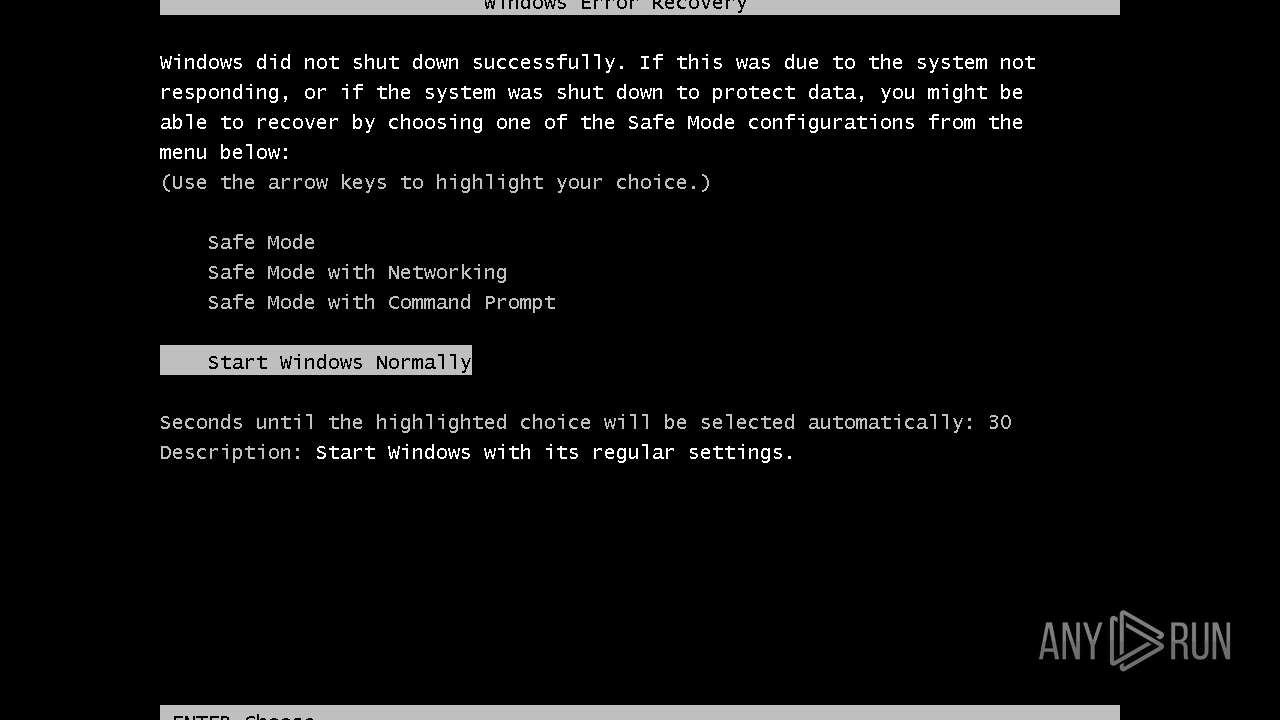
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/4824bc44-3886-4849-a421-465e0e5097a3 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 11, 2024, 10:04:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
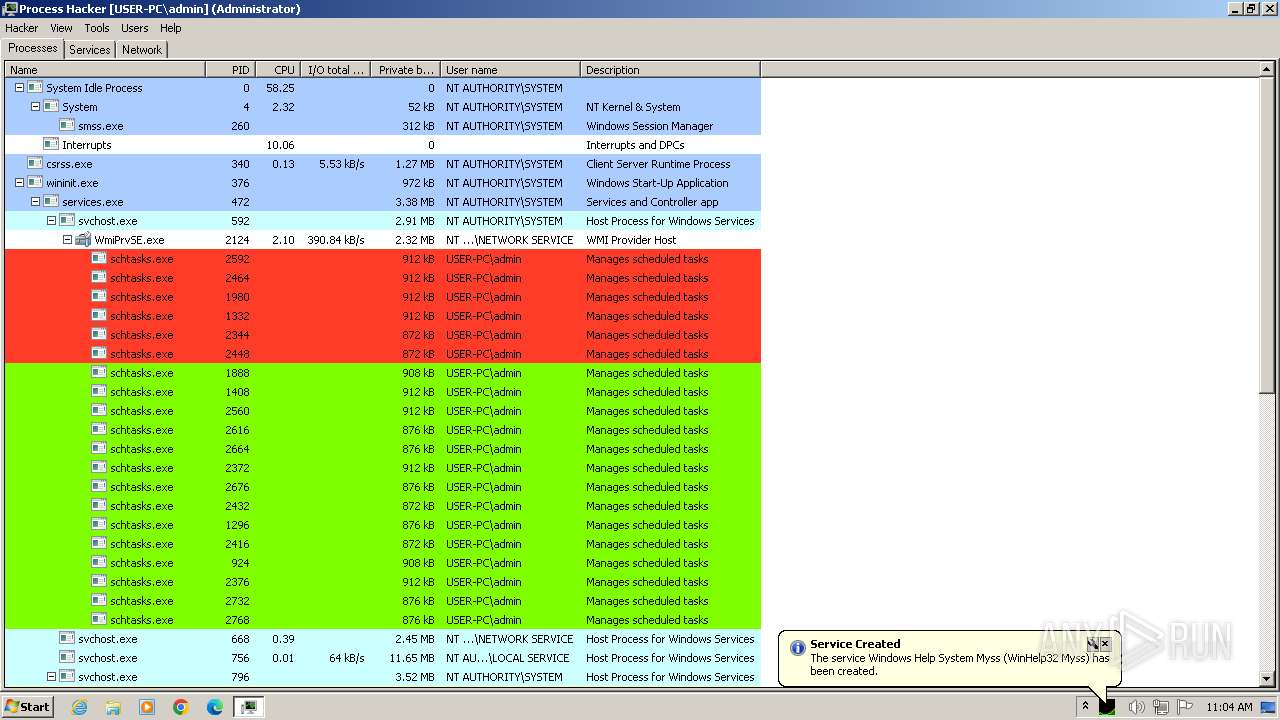
MALICIOUS
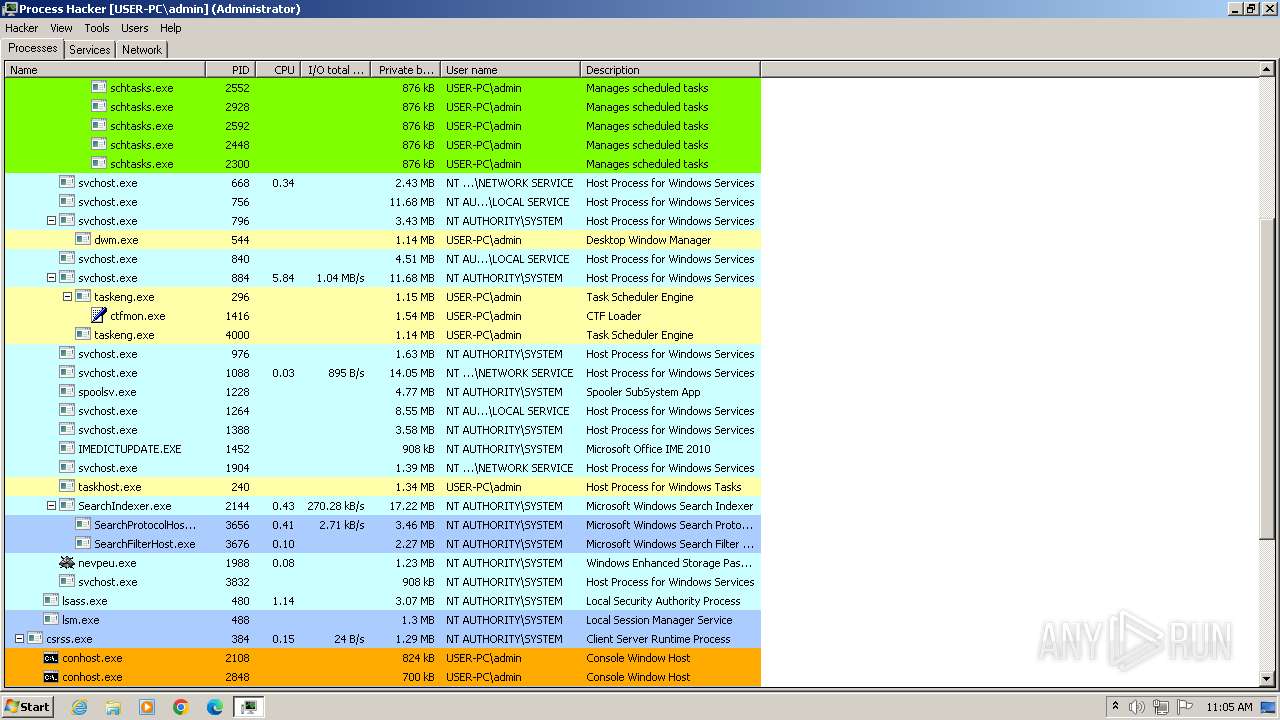
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 1020)
- loader.exe (PID: 308)
- ARA.exe (PID: 1236)
- rhsgn_protected.exe (PID: 728)
- svcyr.exe (PID: 1424)
- Msblockreview.exe (PID: 1548)
- nomal1.exe (PID: 3172)
- ghjkl.exe (PID: 3180)
- BLHisbnd.exe (PID: 3440)
- server.exe (PID: 4004)
- fund.exe (PID: 2556)
- comSvc.exe (PID: 1640)
- aioc_5.0.0.63_it.exe (PID: 2764)
- hv.exe (PID: 1856)
- aioc_5.0.0.63_it.exe (PID: 2456)
- conhost.exe (PID: 2224)
- 4363463463464363463463463.exe (PID: 2272)
- whserver.exe (PID: 3740)
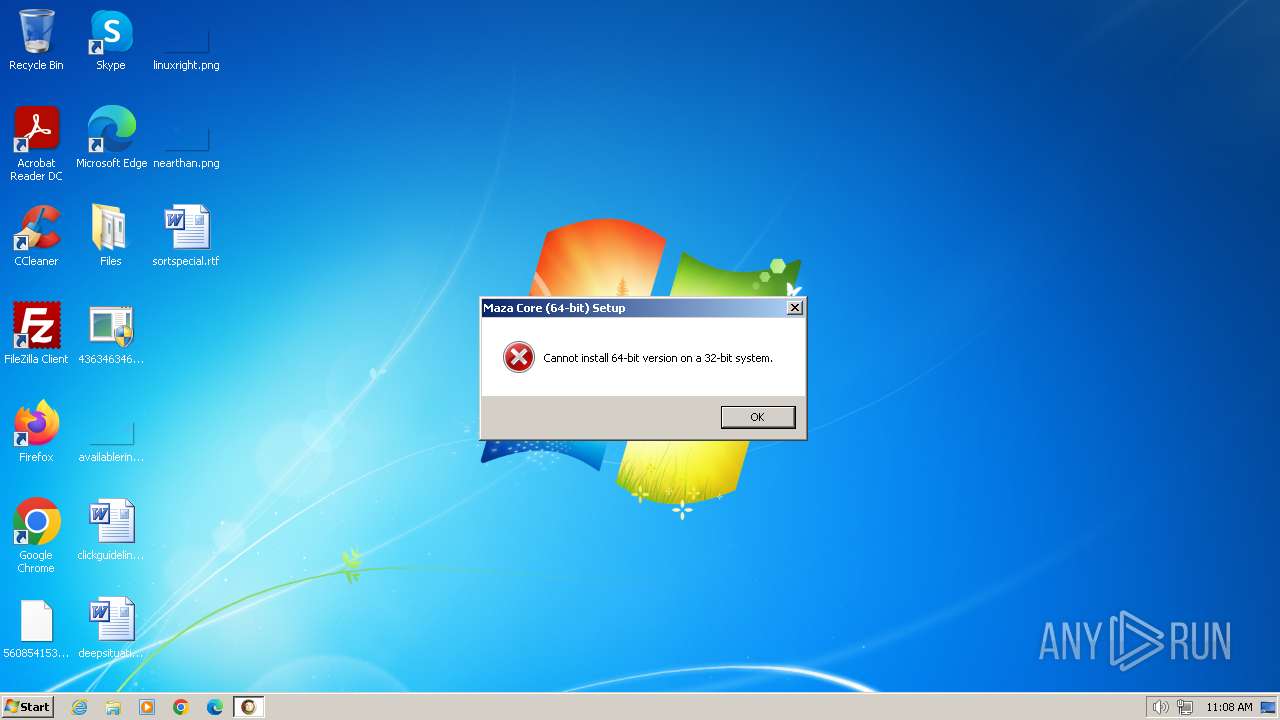
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- first.exe (PID: 2992)
- build3.exe (PID: 4084)
- newpinf.exe (PID: 2836)
- libcefzs.exe (PID: 2732)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1616)
- wscript.exe (PID: 2472)
- wscript.exe (PID: 1736)
- wscript.exe (PID: 4088)
Changes the autorun value in the registry
- nomal1.exe (PID: 3172)
- s.exe (PID: 308)
- s.exe (PID: 2664)
- whserver.exe (PID: 3740)
- clip.exe (PID: 3300)
- first.exe (PID: 2992)
- build.exe (PID: 564)
- NewB.exe (PID: 3460)
Bypass execution policy to execute commands
- powershell.exe (PID: 2180)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 2324)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 3524)
- powershell.exe (PID: 776)
Run PowerShell with an invisible window
- powershell.exe (PID: 2180)
- powershell.exe (PID: 3048)
HIJACKLOADER has been detected (YARA)
- svchost.exe (PID: 3552)
Changes powershell execution policy (Bypass)
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
GH0ST has been detected (SURICATA)
- s.exe (PID: 308)
Connects to the CnC server
- s.exe (PID: 308)
- Uiekeum.exe (PID: 1756)
- 1YETQ46xB5.exe (PID: 1768)
- NewB.exe (PID: 3460)
- u1gc.0.exe (PID: 504)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- dialer.exe (PID: 3136)
Adds process to the Windows Defender exclusion list
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
Adds path to the Windows Defender exclusion list
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
Actions looks like stealing of personal data
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- 4363463463464363463463463.exe (PID: 2272)
- Discord.exe (PID: 1928)
- newpinf.exe (PID: 2836)
- dialer.exe (PID: 3136)
Generic malware mutex has been detected
- hv.exe (PID: 1856)
PURPLEFOX has been detected (SURICATA)
- Uiekeum.exe (PID: 1756)
Deletes a file (SCRIPT)
- wscript.exe (PID: 4088)
Creates a writable file in the system directory
- whserver.exe (PID: 3740)
AZORULT has been detected (SURICATA)
- 1YETQ46xB5.exe (PID: 1768)
Create files in the Startup directory
- first.exe (PID: 2992)
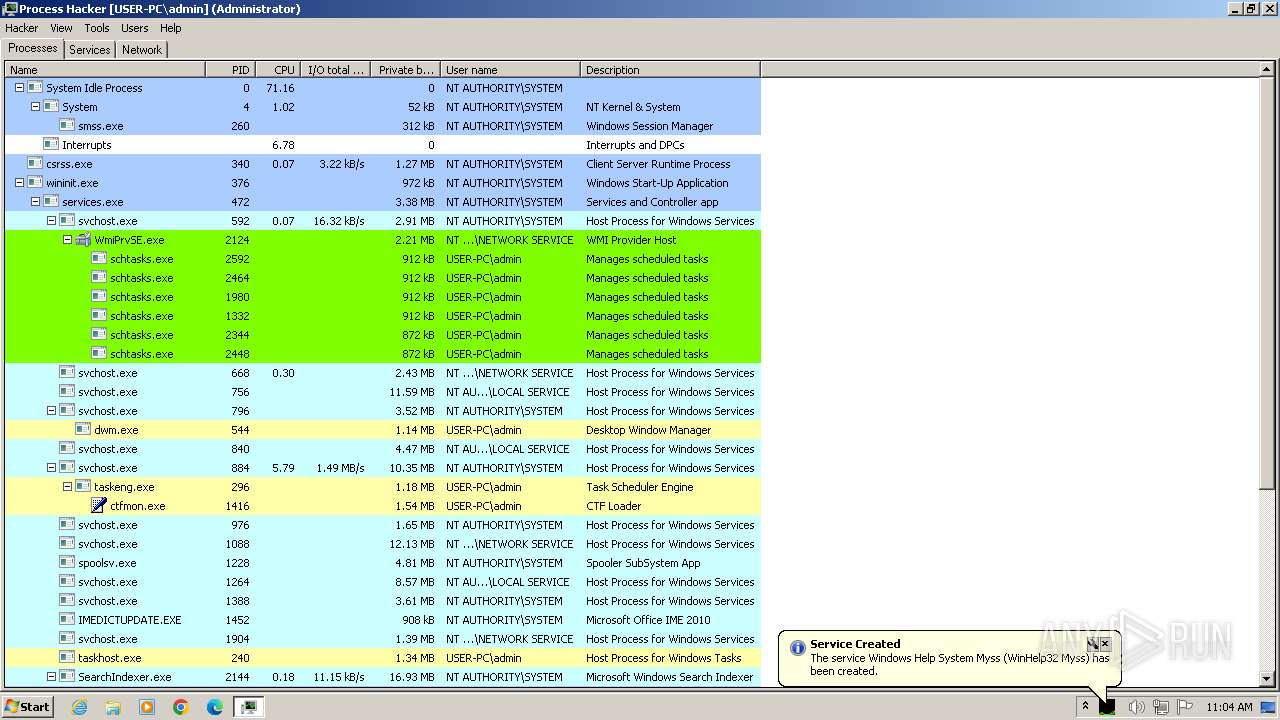
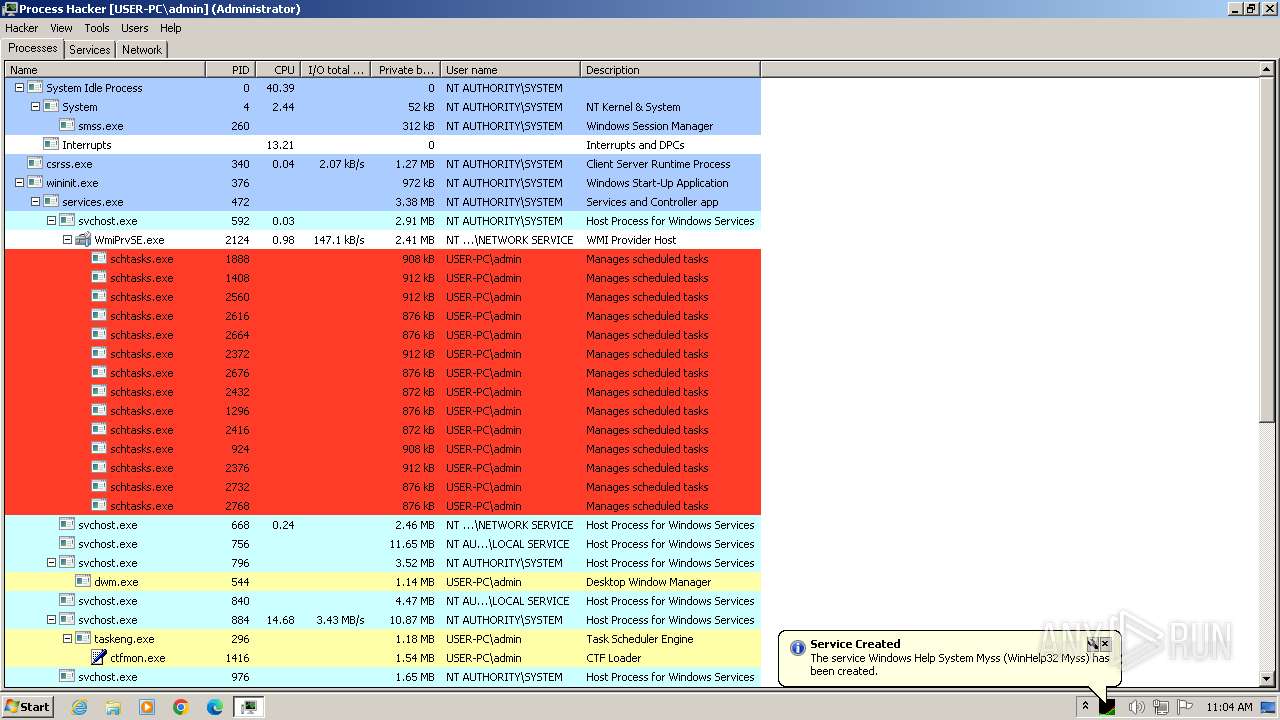
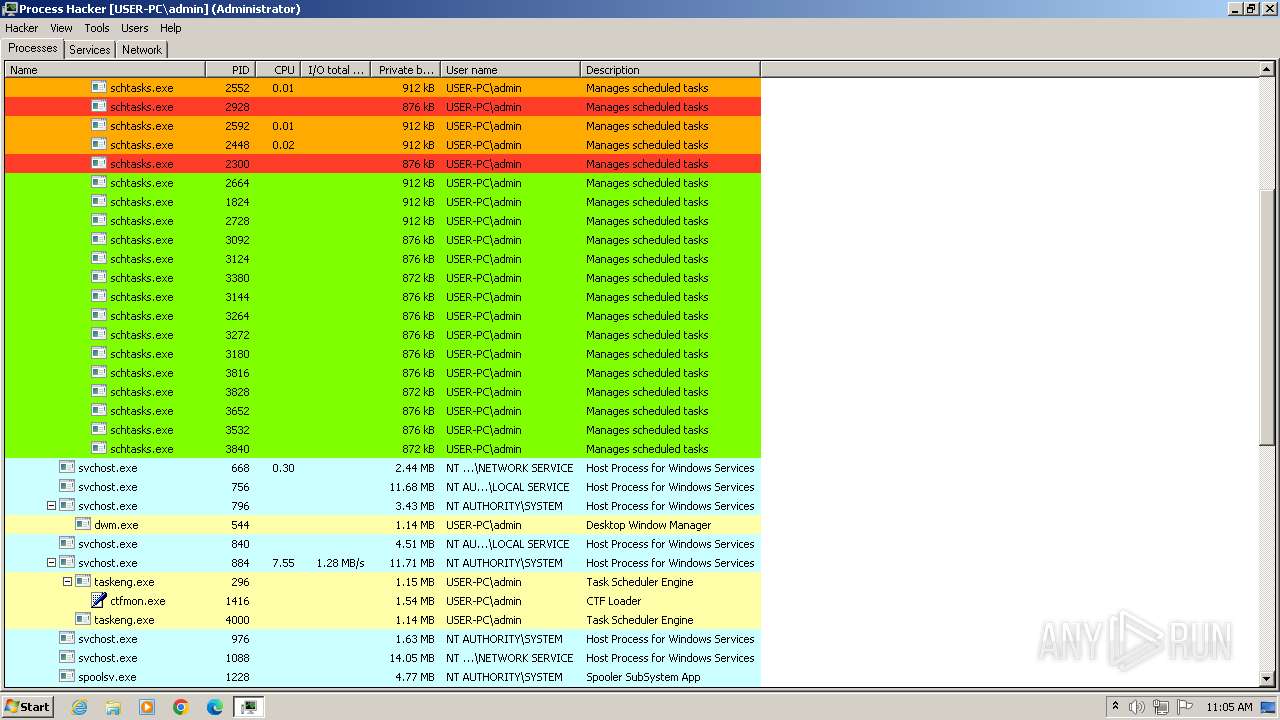
RaccoonClipper scheduled task has been detected
- schtasks.exe (PID: 2228)
- schtasks.exe (PID: 2660)
- schtasks.exe (PID: 1692)
Starts CMD.EXE for self-deleting
- libcefzs.exe (PID: 2732)
DJVU mutex has been found
- build.exe (PID: 2192)
Stop is detected
- build.exe (PID: 2192)
Amadey has been detected
- NewB.exe (PID: 3460)
- NewB.exe (PID: 304)
AMADEY has been detected (SURICATA)
- NewB.exe (PID: 3460)
STEALC has been detected (SURICATA)
- u1gc.0.exe (PID: 504)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- taskeng.exe (PID: 2968)
- sipnotify.exe (PID: 2152)
- taskeng.exe (PID: 2244)
- 4363463463464363463463463.exe (PID: 2272)
- Discord.exe (PID: 1928)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 1020)
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ARA.exe (PID: 1236)
- wscript.exe (PID: 1616)
- Msblockreview.exe (PID: 1548)
- taskeng.exe (PID: 2968)
- ghjkl.exe (PID: 3180)
- powershell.exe (PID: 2180)
- build6_unencrypted.exe (PID: 1676)
- fund.exe (PID: 2556)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 2324)
- wscript.exe (PID: 2472)
- U1HBUcV.exe (PID: 3204)
- aioc_5.0.0.63_it.exe (PID: 2764)
- aioc_5.0.0.63_it.exe (PID: 2732)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2008)
- powershell.exe (PID: 3048)
- sipnotify.exe (PID: 2152)
- runonce.exe (PID: 2520)
- conhost.exe (PID: 2224)
- taskeng.exe (PID: 2244)
- 4363463463464363463463463.exe (PID: 2272)
- 1YETQ46xB5.exe (PID: 1768)
- clip.exe (PID: 3300)
- first.exe (PID: 2992)
- powershell.exe (PID: 776)
- powershell.exe (PID: 3524)
- Discord.exe (PID: 1928)
- ec$o.exe (PID: 1108)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
- u1gc.0.exe (PID: 504)
- u1gc.1.exe (PID: 1252)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ARA.exe (PID: 1236)
- Msblockreview.exe (PID: 1548)
- ghjkl.exe (PID: 3180)
- build6_unencrypted.exe (PID: 1676)
- fund.exe (PID: 2556)
- U1HBUcV.exe (PID: 3204)
- aioc_5.0.0.63_it.exe (PID: 2764)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2732)
- aioc_5.0.0.63_it.exe (PID: 2008)
- conhost.exe (PID: 2224)
- 4363463463464363463463463.exe (PID: 2272)
- 1YETQ46xB5.exe (PID: 1768)
- first.exe (PID: 2992)
- ec$o.exe (PID: 1108)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
- u1gc.0.exe (PID: 504)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- 4363463463464363463463463.exe (PID: 2272)
Checks Windows Trust Settings
- PH32.exe (PID: 1876)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2272)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 1020)
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ARA.exe (PID: 1236)
- svcyr.exe (PID: 1424)
- Msblockreview.exe (PID: 1548)
- nomal1.exe (PID: 3172)
- ghjkl.exe (PID: 3180)
- BLHisbnd.exe (PID: 3440)
- server.exe (PID: 4004)
- fund.exe (PID: 2556)
- comSvc.exe (PID: 1640)
- dialer.exe (PID: 3572)
- aioc_5.0.0.63_it.exe (PID: 2764)
- aioc_5.0.0.63_it.exe (PID: 2456)
- hv.exe (PID: 1856)
- conhost.exe (PID: 2224)
- 4363463463464363463463463.exe (PID: 2272)
- whserver.exe (PID: 3740)
- dialer.exe (PID: 3788)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- clip.exe (PID: 3300)
- first.exe (PID: 2992)
- build3.exe (PID: 4084)
- dialer.exe (PID: 3136)
- newpinf.exe (PID: 2836)
- libcefzs.exe (PID: 2732)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 1020)
- nomal1.exe (PID: 3172)
- server.exe (PID: 4004)
- s.exe (PID: 308)
- build6_unencrypted.exe (PID: 1676)
- InstallUtil.exe (PID: 1612)
- jsc.exe (PID: 3376)
- Uiekeum.exe (PID: 1756)
- s.exe (PID: 2664)
- 4363463463464363463463463.exe (PID: 2272)
- whserver.exe (PID: 3740)
- first.exe (PID: 2992)
- Discord.exe (PID: 1928)
- Uwoph.exe (PID: 2376)
Process drops legitimate windows executable
- rhsgn_protected.exe (PID: 728)
- 4363463463464363463463463.exe (PID: 1020)
- svcyr.exe (PID: 1424)
- aioc_5.0.0.63_it.exe (PID: 2456)
- clip.exe (PID: 3300)
- newpinf.exe (PID: 2836)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 1020)
- 4363463463464363463463463.exe (PID: 2272)
- build.exe (PID: 2192)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
Starts a Microsoft application from unusual location
- svcyr.exe (PID: 1424)
- svcyr.exe (PID: 284)
The executable file from the user directory is run by the CMD process
- Msblockreview.exe (PID: 1548)
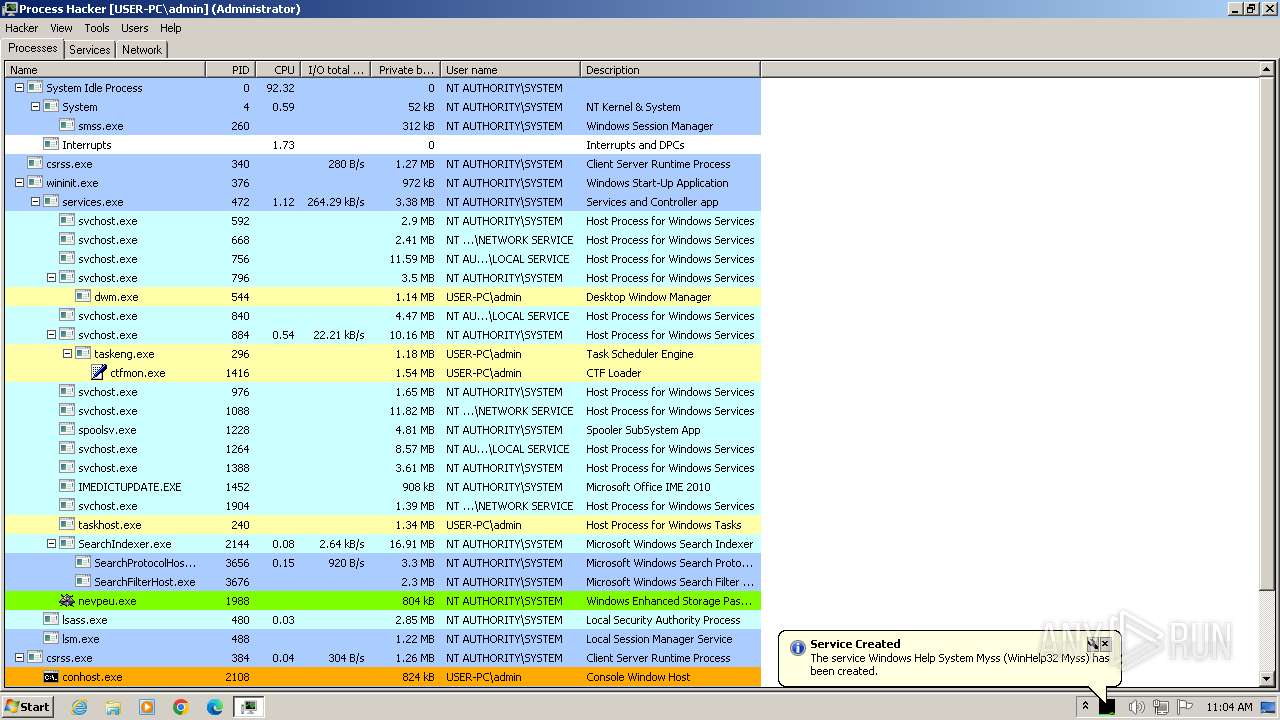
Executes as Windows Service
- nevpeu.exe (PID: 1988)
- Uiekeum.exe (PID: 4016)
Creates or modifies Windows services
- svcyr.exe (PID: 1424)
- server.exe (PID: 4004)
- Uiekeum.exe (PID: 1756)
Executing commands from a ".bat" file
- wscript.exe (PID: 1616)
- wscript.exe (PID: 2472)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1616)
- wscript.exe (PID: 2472)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2732)
- aioc_5.0.0.63_it.exe (PID: 2008)
- libcefzs.exe (PID: 2732)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1616)
- wscript.exe (PID: 2472)
- wscript.exe (PID: 4088)
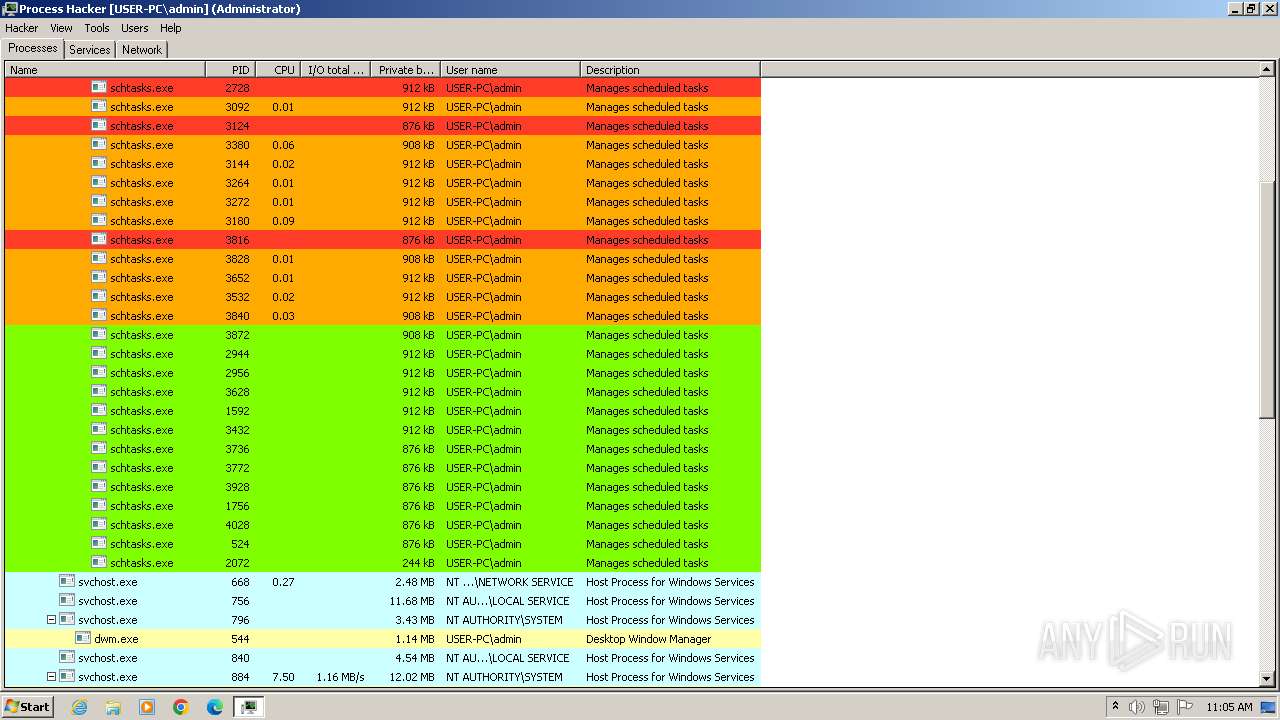
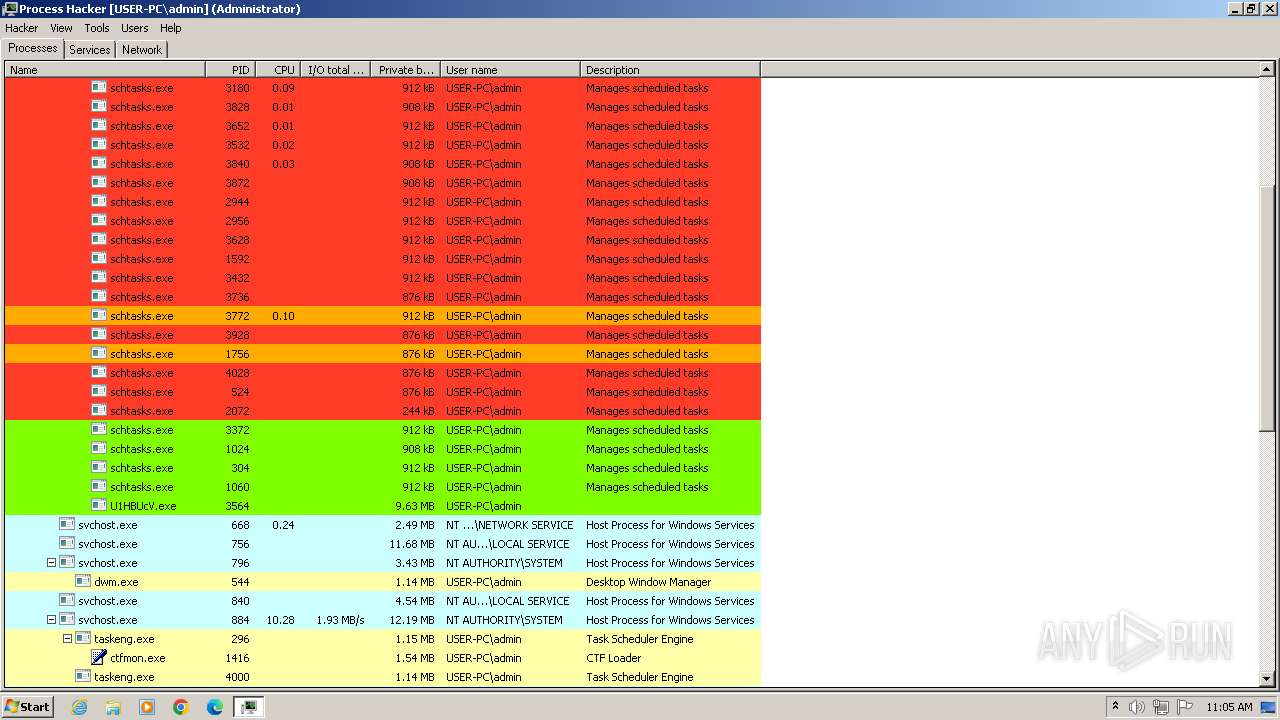
Executed via WMI
- schtasks.exe (PID: 1940)
- schtasks.exe (PID: 2080)
- schtasks.exe (PID: 188)
- schtasks.exe (PID: 1332)
- schtasks.exe (PID: 2524)
- schtasks.exe (PID: 2512)
- schtasks.exe (PID: 2556)
- schtasks.exe (PID: 2592)
- schtasks.exe (PID: 2464)
- schtasks.exe (PID: 1980)
- schtasks.exe (PID: 2448)
- schtasks.exe (PID: 1696)
- schtasks.exe (PID: 1888)
- schtasks.exe (PID: 1008)
- schtasks.exe (PID: 1612)
- schtasks.exe (PID: 856)
- schtasks.exe (PID: 600)
- schtasks.exe (PID: 2076)
- schtasks.exe (PID: 2324)
- schtasks.exe (PID: 676)
- schtasks.exe (PID: 2560)
- schtasks.exe (PID: 2692)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 1408)
- schtasks.exe (PID: 2392)
- schtasks.exe (PID: 2664)
- schtasks.exe (PID: 2616)
- schtasks.exe (PID: 2372)
- schtasks.exe (PID: 1296)
- schtasks.exe (PID: 2676)
- schtasks.exe (PID: 2432)
- schtasks.exe (PID: 924)
- schtasks.exe (PID: 2768)
- schtasks.exe (PID: 2416)
- schtasks.exe (PID: 2376)
- schtasks.exe (PID: 2732)
- schtasks.exe (PID: 2780)
- schtasks.exe (PID: 2552)
- schtasks.exe (PID: 2748)
- schtasks.exe (PID: 2784)
- schtasks.exe (PID: 2884)
- schtasks.exe (PID: 2804)
- schtasks.exe (PID: 2544)
- schtasks.exe (PID: 2924)
- schtasks.exe (PID: 2908)
- schtasks.exe (PID: 2872)
- schtasks.exe (PID: 2544)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 2796)
- schtasks.exe (PID: 2088)
- schtasks.exe (PID: 2776)
- schtasks.exe (PID: 2876)
- schtasks.exe (PID: 2412)
- schtasks.exe (PID: 3016)
- schtasks.exe (PID: 2908)
- schtasks.exe (PID: 2964)
- schtasks.exe (PID: 2552)
- schtasks.exe (PID: 2928)
- schtasks.exe (PID: 2592)
- schtasks.exe (PID: 2448)
- schtasks.exe (PID: 2664)
- schtasks.exe (PID: 2300)
- schtasks.exe (PID: 2660)
- schtasks.exe (PID: 1240)
- schtasks.exe (PID: 1824)
- schtasks.exe (PID: 1296)
- schtasks.exe (PID: 2728)
- schtasks.exe (PID: 3040)
- schtasks.exe (PID: 3144)
- schtasks.exe (PID: 3092)
- schtasks.exe (PID: 3380)
- schtasks.exe (PID: 3124)
- schtasks.exe (PID: 3272)
- schtasks.exe (PID: 3264)
- schtasks.exe (PID: 3180)
- schtasks.exe (PID: 3828)
- schtasks.exe (PID: 3816)
- schtasks.exe (PID: 3532)
- schtasks.exe (PID: 3652)
- schtasks.exe (PID: 3840)
- schtasks.exe (PID: 3872)
- schtasks.exe (PID: 924)
- schtasks.exe (PID: 3628)
- schtasks.exe (PID: 3432)
- schtasks.exe (PID: 3928)
- schtasks.exe (PID: 3736)
- schtasks.exe (PID: 3772)
- schtasks.exe (PID: 4008)
- schtasks.exe (PID: 1756)
- schtasks.exe (PID: 4028)
- schtasks.exe (PID: 2072)
- schtasks.exe (PID: 1628)
- schtasks.exe (PID: 3372)
- schtasks.exe (PID: 1768)
- schtasks.exe (PID: 1024)
- schtasks.exe (PID: 304)
- schtasks.exe (PID: 1060)
- schtasks.exe (PID: 2944)
- schtasks.exe (PID: 2956)
- schtasks.exe (PID: 1592)
- schtasks.exe (PID: 524)
- U1HBUcV.exe (PID: 3564)
- schtasks.exe (PID: 728)
- 1YETQ46xB5.exe (PID: 2352)
- ec$o.exe (PID: 848)
The process creates files with name similar to system file names
- Msblockreview.exe (PID: 1548)
- 4363463463464363463463463.exe (PID: 1020)
- comSvc.exe (PID: 1640)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- clip.exe (PID: 3300)
Starts itself from another location
- Msblockreview.exe (PID: 1548)
- aioc_5.0.0.63_it.exe (PID: 2764)
- clip.exe (PID: 3300)
Contacting a server suspected of hosting an CnC
- 4363463463464363463463463.exe (PID: 1020)
- s.exe (PID: 308)
- dialer.exe (PID: 3572)
- Uiekeum.exe (PID: 1756)
- dialer.exe (PID: 3788)
- 1YETQ46xB5.exe (PID: 1768)
- dialer.exe (PID: 3136)
- NewB.exe (PID: 3460)
- u1gc.0.exe (PID: 504)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 1020)
- taskeng.exe (PID: 2968)
- taskeng.exe (PID: 2244)
- 4363463463464363463463463.exe (PID: 2272)
- chdyz.exe (PID: 2440)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
- u1gc.0.exe (PID: 504)
Application launched itself
- ghjkl.exe (PID: 3180)
- BLHisbnd.exe (PID: 3280)
- Uiekeum.exe (PID: 4016)
- U1HBUcV.exe (PID: 3564)
- Tags.exe (PID: 2524)
- InstallUtil.exe (PID: 1928)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2732)
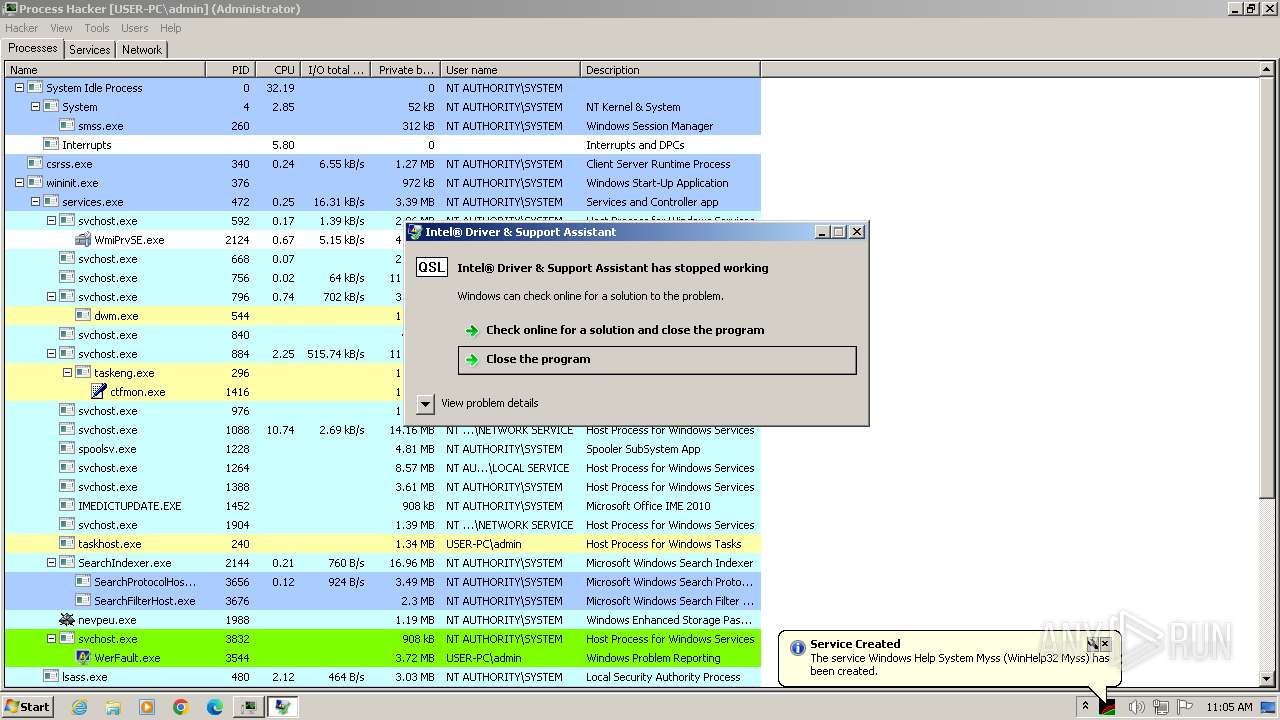
- WerFault.exe (PID: 2544)
- asdfg.exe (PID: 3852)
- 1YETQ46xB5.exe (PID: 2352)
- ghjk.exe (PID: 2780)
- build3.exe (PID: 1864)
- ghjk.exe (PID: 3264)
- ec$o.exe (PID: 848)
- build.exe (PID: 2352)
- build.exe (PID: 564)
- build.exe (PID: 3428)
- build2.exe (PID: 2148)
- build3.exe (PID: 788)
- mstsca.exe (PID: 3796)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- dialer.exe (PID: 3136)
The process executes via Task Scheduler
- powershell.exe (PID: 2180)
- Tags.exe (PID: 2524)
- powershell.exe (PID: 3048)
- winlogon.exe (PID: 1792)
- ntvdm.exe (PID: 2192)
- sipnotify.exe (PID: 2152)
- spoolsv.exe (PID: 2140)
- wininit.exe (PID: 2184)
- conhost.exe (PID: 2224)
- dwm.exe (PID: 2216)
- hv.exe (PID: 2172)
- taskeng.exe (PID: 2244)
- ctfmon.exe (PID: 2300)
- SearchFilterHost.exe (PID: 2236)
- nevpeu.exe (PID: 2312)
- taskhost.exe (PID: 2324)
- services.exe (PID: 1456)
- System.exe (PID: 1644)
- ctfmon.exe (PID: 2096)
- explorer.exe (PID: 2104)
- PH32.exe (PID: 2400)
- Msblockreview.exe (PID: 2380)
- SearchProtocolHost.exe (PID: 2372)
- 4363463463464363463463463.exe (PID: 2392)
- cmd.exe (PID: 2412)
- NewB.exe (PID: 304)
- mstsca.exe (PID: 3796)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2180)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 2324)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 776)
- powershell.exe (PID: 3524)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- dialer.exe (PID: 3136)
Reads browser cookies
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
Searches for installed software
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- dialer.exe (PID: 3136)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- dialer.exe (PID: 3136)
Script adds exclusion process to Windows Defender
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
Starts POWERSHELL.EXE for commands execution
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
The mutex name appears to contain an IP address
- s.exe (PID: 308)
- s.exe (PID: 2664)
Script adds exclusion path to Windows Defender
- build6_unencrypted.exe (PID: 1676)
- first.exe (PID: 2992)
Likely accesses (executes) a file from the Public directory
- schtasks.exe (PID: 2592)
- schtasks.exe (PID: 2448)
- schtasks.exe (PID: 2300)
- wininit.exe (PID: 2184)
Uses TASKKILL.EXE to kill process
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2732)
- aioc_5.0.0.63_it.exe (PID: 2008)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2640)
- cmd.exe (PID: 2972)
- cmd.exe (PID: 1836)
- build.exe (PID: 564)
Creates file in the systems drive root
- ntvdm.exe (PID: 2192)
The process executes VB scripts
- conhost.exe (PID: 2224)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 1736)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 4088)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 4088)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4088)
- wscript.exe (PID: 1736)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 4088)
Malware-specific behavior (creating "System.dll" in Temp)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
Mutex name with non-standard characters
- newpinf.exe (PID: 2836)
Checks for external IP
- build.exe (PID: 564)
- build.exe (PID: 2192)
Hides command output
- cmd.exe (PID: 3788)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3788)
Reads the date of Windows installation
- u1gc.1.exe (PID: 1252)
Windows Defender mutex has been found
- u1gc.0.exe (PID: 504)
INFO
Reads the computer name
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ARA.exe (PID: 1236)
- svcyr.exe (PID: 1424)
- Msblockreview.exe (PID: 1548)
- wmpnscfg.exe (PID: 1112)
- taskeng.exe (PID: 2968)
- nomal1.exe (PID: 3172)
- ghjkl.exe (PID: 3180)
- BLHisbnd.exe (PID: 3280)
- BLHisbnd.exe (PID: 3440)
- svchost.exe (PID: 3552)
- server.exe (PID: 4004)
- Uiekeum.exe (PID: 4016)
- hv.exe (PID: 1856)
- Uiekeum.exe (PID: 552)
- svcyr.exe (PID: 284)
- s.exe (PID: 308)
- build6_unencrypted.exe (PID: 1676)
- fund.exe (PID: 2556)
- comSvc.exe (PID: 1640)
- U1HBUcV.exe (PID: 3564)
- U1HBUcV.exe (PID: 3204)
- InstallUtil.exe (PID: 1928)
- InstallUtil.exe (PID: 1612)
- aioc_5.0.0.63_it.exe (PID: 2764)
- Tags.exe (PID: 2524)
- Tags.exe (PID: 2656)
- aioc_5.0.0.63_it.exe (PID: 2456)
- wefhrf.exe (PID: 2324)
- aioc_5.0.0.63_it.exe (PID: 2732)
- jsc.exe (PID: 3376)
- PrimaryScreen.exe (PID: 3764)
- aioc_5.0.0.63_it.exe (PID: 2008)
- PrimaryScreen.exe (PID: 3404)
- PrimaryScreen.exe (PID: 2664)
- PrimaryScreen.exe (PID: 1440)
- Uiekeum.exe (PID: 1756)
- IMEKLMG.EXE (PID: 2640)
- s.exe (PID: 2664)
- IMEKLMG.EXE (PID: 2632)
- wmpnscfg.exe (PID: 3004)
- wininit.exe (PID: 2184)
- System.exe (PID: 1644)
- dwm.exe (PID: 2216)
- nevpeu.exe (PID: 2312)
- PH32.exe (PID: 2400)
- cmd.exe (PID: 2412)
- wmpnscfg.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2392)
- ctfmon.exe (PID: 2300)
- taskeng.exe (PID: 2244)
- SearchProtocolHost.exe (PID: 2372)
- Msblockreview.exe (PID: 2380)
- winlogon.exe (PID: 1792)
- SearchFilterHost.exe (PID: 2236)
- explorer.exe (PID: 2104)
- services.exe (PID: 1456)
- conhost.exe (PID: 2224)
- hv.exe (PID: 2172)
- spoolsv.exe (PID: 2140)
- taskhost.exe (PID: 2324)
- 4363463463464363463463463.exe (PID: 2272)
- asdfg.exe (PID: 3852)
- conhost.exe (PID: 3372)
- whserver.exe (PID: 3740)
- 1YETQ46xB5.exe (PID: 2352)
- 1YETQ46xB5.exe (PID: 1768)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- cayV0Deo9jSt417.exe (PID: 2724)
- ghjk.exe (PID: 2780)
- first.exe (PID: 2992)
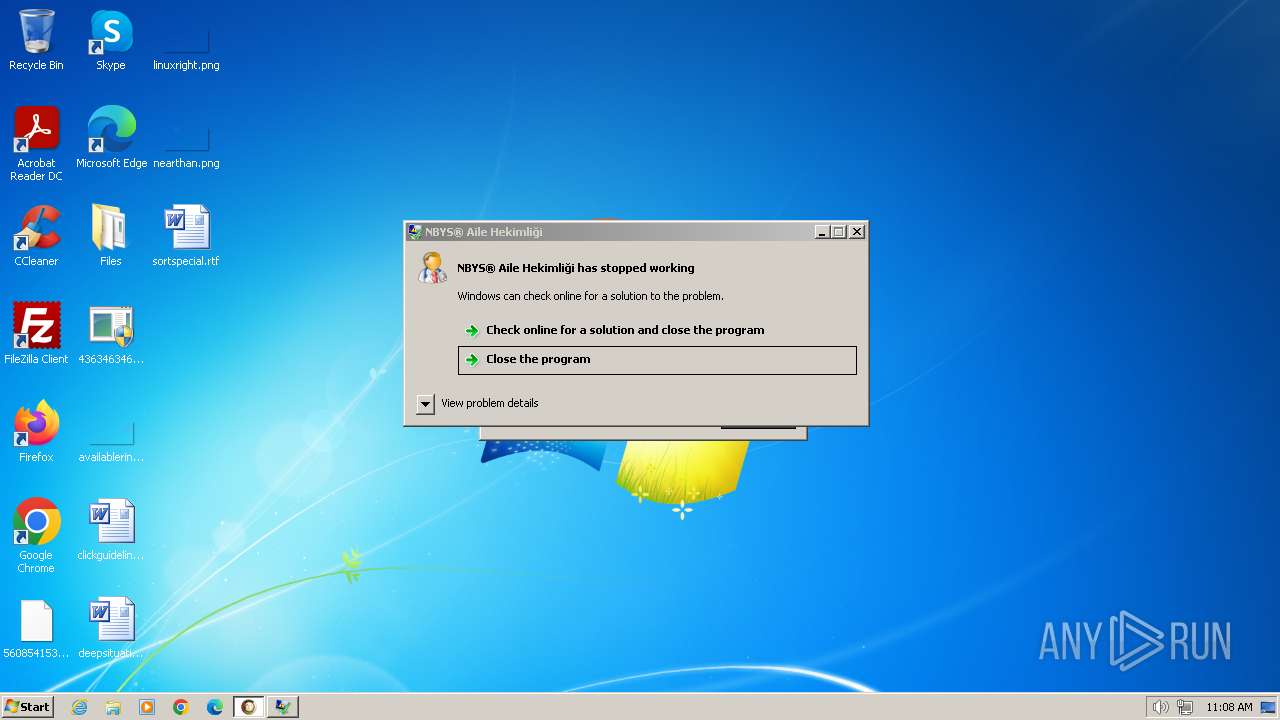
- NBYS%20AH.NET.exe (PID: 3144)
- Discord.exe (PID: 1928)
- ghjk.exe (PID: 3264)
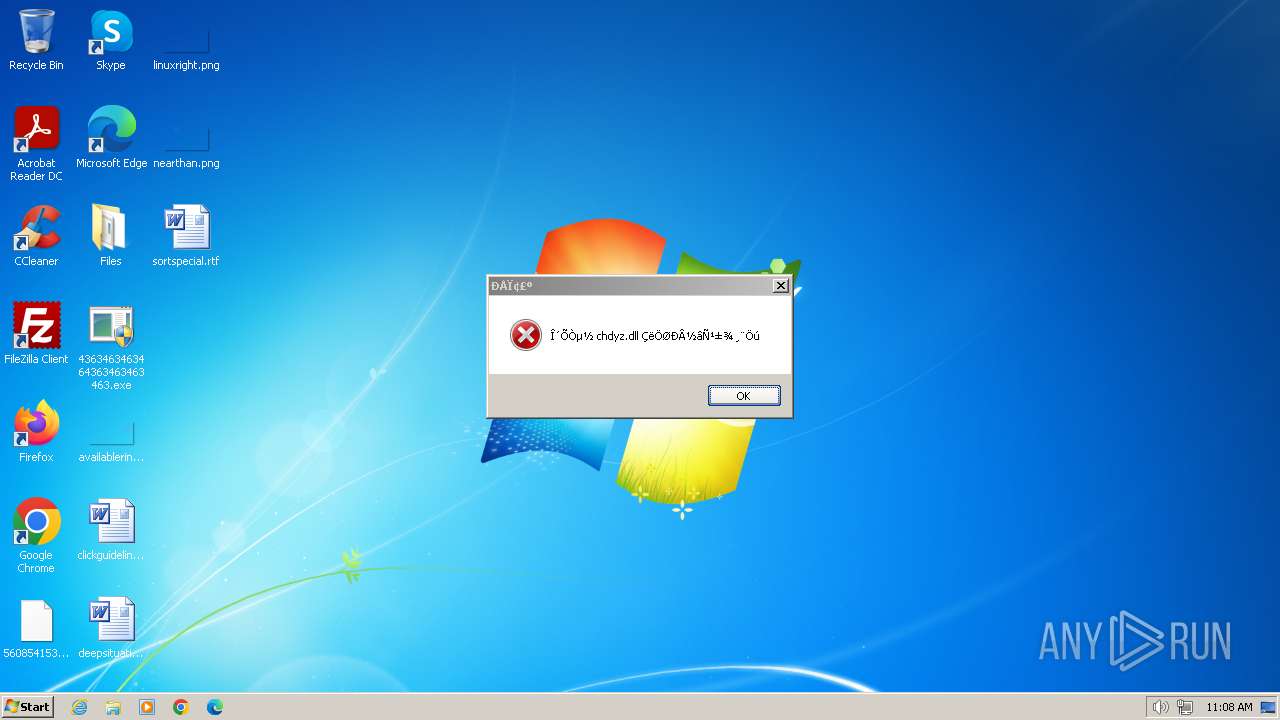
- chdyz.exe (PID: 2440)
- ec$o.exe (PID: 848)
- ec$o.exe (PID: 1108)
- build.exe (PID: 564)
- libcefzs.exe (PID: 2732)
- build.exe (PID: 2192)
- Uwoph.exe (PID: 2376)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
- u1gc.1.exe (PID: 1252)
- u1gc.0.exe (PID: 504)
Checks supported languages
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ARA.exe (PID: 1236)
- svcyr.exe (PID: 1424)
- Msblockreview.exe (PID: 1548)
- wmpnscfg.exe (PID: 1112)
- taskeng.exe (PID: 2968)
- nomal1.exe (PID: 3172)
- ghjkl.exe (PID: 3180)
- ghjkl.exe (PID: 3252)
- BLHisbnd.exe (PID: 3440)
- svchost.exe (PID: 3552)
- BLHisbnd.exe (PID: 3280)
- Uiekeum.exe (PID: 4016)
- server.exe (PID: 4004)
- hv.exe (PID: 1856)
- Uiekeum.exe (PID: 552)
- svcyr.exe (PID: 284)
- s.exe (PID: 308)
- build6_unencrypted.exe (PID: 1676)
- fund.exe (PID: 2556)
- wmpshare.exe (PID: 2828)
- comSvc.exe (PID: 1640)
- U1HBUcV.exe (PID: 3564)
- U1HBUcV.exe (PID: 3204)
- Tags.exe (PID: 2656)
- InstallUtil.exe (PID: 1612)
- aioc_5.0.0.63_it.exe (PID: 2764)
- Tags.exe (PID: 2524)
- InstallUtil.exe (PID: 1928)
- aioc_5.0.0.63_it.exe (PID: 2456)
- wefhrf.exe (PID: 2324)
- aioc_5.0.0.63_it.exe (PID: 2732)
- PrimaryScreen.exe (PID: 3764)
- aioc_5.0.0.63_it.exe (PID: 2008)
- jsc.exe (PID: 3376)
- PrimaryScreen.exe (PID: 2664)
- Uiekeum.exe (PID: 1756)
- PrimaryScreen.exe (PID: 3404)
- PrimaryScreen.exe (PID: 1440)
- ctfmon.exe (PID: 2300)
- wininit.exe (PID: 2184)
- spoolsv.exe (PID: 2140)
- winlogon.exe (PID: 1792)
- 4363463463464363463463463.exe (PID: 2392)
- nevpeu.exe (PID: 2312)
- hv.exe (PID: 2172)
- System.exe (PID: 1644)
- taskhost.exe (PID: 2324)
- dwm.exe (PID: 2216)
- taskeng.exe (PID: 2244)
- PH32.exe (PID: 2400)
- conhost.exe (PID: 2224)
- SearchFilterHost.exe (PID: 2236)
- explorer.exe (PID: 2104)
- services.exe (PID: 1456)
- cmd.exe (PID: 2412)
- Msblockreview.exe (PID: 2380)
- SearchProtocolHost.exe (PID: 2372)
- IMEKLMG.EXE (PID: 2632)
- s.exe (PID: 2664)
- IMEKLMG.EXE (PID: 2640)
- wmpnscfg.exe (PID: 3004)
- wmpnscfg.exe (PID: 2980)
- 4363463463464363463463463.exe (PID: 2272)
- asdfg.exe (PID: 3852)
- asdfg.exe (PID: 3212)
- whserver.exe (PID: 3740)
- conhost.exe (PID: 3372)
- 1YETQ46xB5.exe (PID: 2352)
- wmpnscfg.exe (PID: 3276)
- 1YETQ46xB5.exe (PID: 1768)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- %E5%85%81%E8%AE%B8%E6%B3%A8%E9%94%80@121.62.63.92.exe (PID: 3688)
- cayV0Deo9jSt417.exe (PID: 2724)
- ghjk.exe (PID: 2780)
- first.exe (PID: 2992)
- ghjk.exe (PID: 2152)
- taskhost.exe (PID: 2104)
- NBYS%20AH.NET.exe (PID: 3144)
- build3.exe (PID: 1864)
- crypted_87ddcda6.exe (PID: 3816)
- Discord.exe (PID: 1928)
- build3.exe (PID: 4084)
- ghjk.exe (PID: 3264)
- ghjk.exe (PID: 2396)
- chdyz.exe (PID: 2440)
- ec$o.exe (PID: 848)
- ec$o.exe (PID: 1108)
- newpinf.exe (PID: 2836)
- build.exe (PID: 2352)
- %E7%A6%81%E6%AD%A2%E6%B3%A8%E9%94%80@198.44.165.124.exe (PID: 1456)
- build.exe (PID: 564)
- libcefzs.exe (PID: 2732)
- build.exe (PID: 3428)
- Uwoph.exe (PID: 2376)
- update.exe (PID: 2744)
- build.exe (PID: 2192)
- build3.exe (PID: 788)
- PAETools.exe (PID: 3952)
- build2.exe (PID: 2148)
- build2.exe (PID: 1232)
- ISetup8.exe (PID: 1884)
- NewB.exe (PID: 3460)
- build3.exe (PID: 3328)
- mstsca.exe (PID: 3796)
- NewB.exe (PID: 304)
- u1gc.0.exe (PID: 504)
- u1gc.1.exe (PID: 1252)
- mstsca.exe (PID: 868)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 1020)
- Msblockreview.exe (PID: 1548)
- PH32.exe (PID: 1876)
- taskeng.exe (PID: 2968)
- ghjkl.exe (PID: 3180)
- BLHisbnd.exe (PID: 3280)
- BLHisbnd.exe (PID: 3440)
- build6_unencrypted.exe (PID: 1676)
- wmpshare.exe (PID: 2828)
- comSvc.exe (PID: 1640)
- U1HBUcV.exe (PID: 3564)
- U1HBUcV.exe (PID: 3204)
- Tags.exe (PID: 2524)
- Tags.exe (PID: 2656)
- InstallUtil.exe (PID: 1612)
- InstallUtil.exe (PID: 1928)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2764)
- hv.exe (PID: 1856)
- aioc_5.0.0.63_it.exe (PID: 2732)
- jsc.exe (PID: 3376)
- aioc_5.0.0.63_it.exe (PID: 2008)
- conhost.exe (PID: 2224)
- 4363463463464363463463463.exe (PID: 2392)
- wininit.exe (PID: 2184)
- nevpeu.exe (PID: 2312)
- cmd.exe (PID: 2412)
- SearchProtocolHost.exe (PID: 2372)
- services.exe (PID: 1456)
- spoolsv.exe (PID: 2140)
- taskhost.exe (PID: 2324)
- SearchFilterHost.exe (PID: 2236)
- hv.exe (PID: 2172)
- Msblockreview.exe (PID: 2380)
- ctfmon.exe (PID: 2300)
- System.exe (PID: 1644)
- PH32.exe (PID: 2400)
- dwm.exe (PID: 2216)
- explorer.exe (PID: 2104)
- taskeng.exe (PID: 2244)
- winlogon.exe (PID: 1792)
- asdfg.exe (PID: 3852)
- 4363463463464363463463463.exe (PID: 2272)
- conhost.exe (PID: 3372)
- wmpnscfg.exe (PID: 3276)
- 1YETQ46xB5.exe (PID: 2352)
- 1YETQ46xB5.exe (PID: 1768)
- ghjk.exe (PID: 2780)
- cayV0Deo9jSt417.exe (PID: 2724)
- first.exe (PID: 2992)
- NBYS%20AH.NET.exe (PID: 3144)
- Discord.exe (PID: 1928)
- ghjk.exe (PID: 3264)
- ec$o.exe (PID: 848)
- ec$o.exe (PID: 1108)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
- u1gc.0.exe (PID: 504)
- u1gc.1.exe (PID: 1252)
Reads Environment values
- 4363463463464363463463463.exe (PID: 1020)
- Msblockreview.exe (PID: 1548)
- taskeng.exe (PID: 2968)
- comSvc.exe (PID: 1640)
- U1HBUcV.exe (PID: 3204)
- jsc.exe (PID: 3376)
- aioc_5.0.0.63_it.exe (PID: 2008)
- 4363463463464363463463463.exe (PID: 2392)
- conhost.exe (PID: 2224)
- nevpeu.exe (PID: 2312)
- ctfmon.exe (PID: 2300)
- Msblockreview.exe (PID: 2380)
- System.exe (PID: 1644)
- spoolsv.exe (PID: 2140)
- taskhost.exe (PID: 2324)
- hv.exe (PID: 2172)
- PH32.exe (PID: 2400)
- explorer.exe (PID: 2104)
- wininit.exe (PID: 2184)
- SearchProtocolHost.exe (PID: 2372)
- dwm.exe (PID: 2216)
- taskeng.exe (PID: 2244)
- winlogon.exe (PID: 1792)
- cmd.exe (PID: 2412)
- services.exe (PID: 1456)
- SearchFilterHost.exe (PID: 2236)
- 4363463463464363463463463.exe (PID: 2272)
- conhost.exe (PID: 3372)
- 1YETQ46xB5.exe (PID: 1768)
- first.exe (PID: 2992)
- Discord.exe (PID: 1928)
- chdyz.exe (PID: 2440)
- ec$o.exe (PID: 1108)
- build2.exe (PID: 1232)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 1020)
- PH32.exe (PID: 1876)
- taskeng.exe (PID: 2968)
- sipnotify.exe (PID: 2152)
- taskeng.exe (PID: 2244)
- 4363463463464363463463463.exe (PID: 2272)
- Discord.exe (PID: 1928)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
Create files in a temporary directory
- loader.exe (PID: 308)
- rhsgn_protected.exe (PID: 728)
- ghjkl.exe (PID: 3180)
- taskeng.exe (PID: 2968)
- hv.exe (PID: 1856)
- WerFault.exe (PID: 2552)
- conhost.exe (PID: 2224)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 3556)
- NewB.exe (PID: 3460)
- ISetup8.exe (PID: 1884)
- u1gc.1.exe (PID: 1252)
Creates files or folders in the user directory
- ARA.exe (PID: 1236)
- BLHisbnd.exe (PID: 3440)
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- clip.exe (PID: 3300)
- first.exe (PID: 2992)
- build3.exe (PID: 4084)
- dialer.exe (PID: 3136)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
Reads product name
- Msblockreview.exe (PID: 1548)
- taskeng.exe (PID: 2968)
- comSvc.exe (PID: 1640)
- U1HBUcV.exe (PID: 3204)
- hv.exe (PID: 2172)
- cmd.exe (PID: 2412)
- System.exe (PID: 1644)
- wininit.exe (PID: 2184)
- taskhost.exe (PID: 2324)
- services.exe (PID: 1456)
- spoolsv.exe (PID: 2140)
- Msblockreview.exe (PID: 2380)
- PH32.exe (PID: 2400)
- SearchProtocolHost.exe (PID: 2372)
- 4363463463464363463463463.exe (PID: 2392)
- taskeng.exe (PID: 2244)
- SearchFilterHost.exe (PID: 2236)
- nevpeu.exe (PID: 2312)
- explorer.exe (PID: 2104)
- dwm.exe (PID: 2216)
- conhost.exe (PID: 2224)
- ctfmon.exe (PID: 2300)
- winlogon.exe (PID: 1792)
- conhost.exe (PID: 3372)
- 1YETQ46xB5.exe (PID: 1768)
- ec$o.exe (PID: 1108)
- build2.exe (PID: 1232)
Creates files in the program directory
- Msblockreview.exe (PID: 1548)
- server.exe (PID: 4004)
- comSvc.exe (PID: 1640)
- aioc_5.0.0.63_it.exe (PID: 2456)
- aioc_5.0.0.63_it.exe (PID: 2764)
- build2.exe (PID: 1232)
- u1gc.1.exe (PID: 1252)
Manual execution by a user
- wmpnscfg.exe (PID: 1112)
- runonce.exe (PID: 2520)
- s.exe (PID: 2664)
- IMEKLMG.EXE (PID: 2632)
- IMEKLMG.EXE (PID: 2640)
- rundll32.exe (PID: 2692)
- wmpnscfg.exe (PID: 2980)
- wmpnscfg.exe (PID: 3004)
- 4363463463464363463463463.exe (PID: 2856)
- 4363463463464363463463463.exe (PID: 2272)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2180)
- powershell.exe (PID: 1596)
- powershell.exe (PID: 2324)
- powershell.exe (PID: 3048)
- powershell.exe (PID: 776)
- powershell.exe (PID: 3524)
Reads CPU info
- server.exe (PID: 4004)
- s.exe (PID: 308)
- Uiekeum.exe (PID: 1756)
- s.exe (PID: 2664)
- whserver.exe (PID: 3740)
- Uwoph.exe (PID: 2376)
Drops the executable file immediately after the start
- dialer.exe (PID: 3572)
- dialer.exe (PID: 3788)
- clip.exe (PID: 3300)
- dialer.exe (PID: 3136)
Checks proxy server information
- U1HBUcV.exe (PID: 3204)
- 1YETQ46xB5.exe (PID: 1768)
- ec$o.exe (PID: 1108)
- build.exe (PID: 564)
- build.exe (PID: 2192)
- build2.exe (PID: 1232)
- NewB.exe (PID: 3460)
- u1gc.0.exe (PID: 504)
- u1gc.1.exe (PID: 1252)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 2152)
- runonce.exe (PID: 2520)
- clip.exe (PID: 3300)
Reads the time zone
- runonce.exe (PID: 2520)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2640)
- IMEKLMG.EXE (PID: 2632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
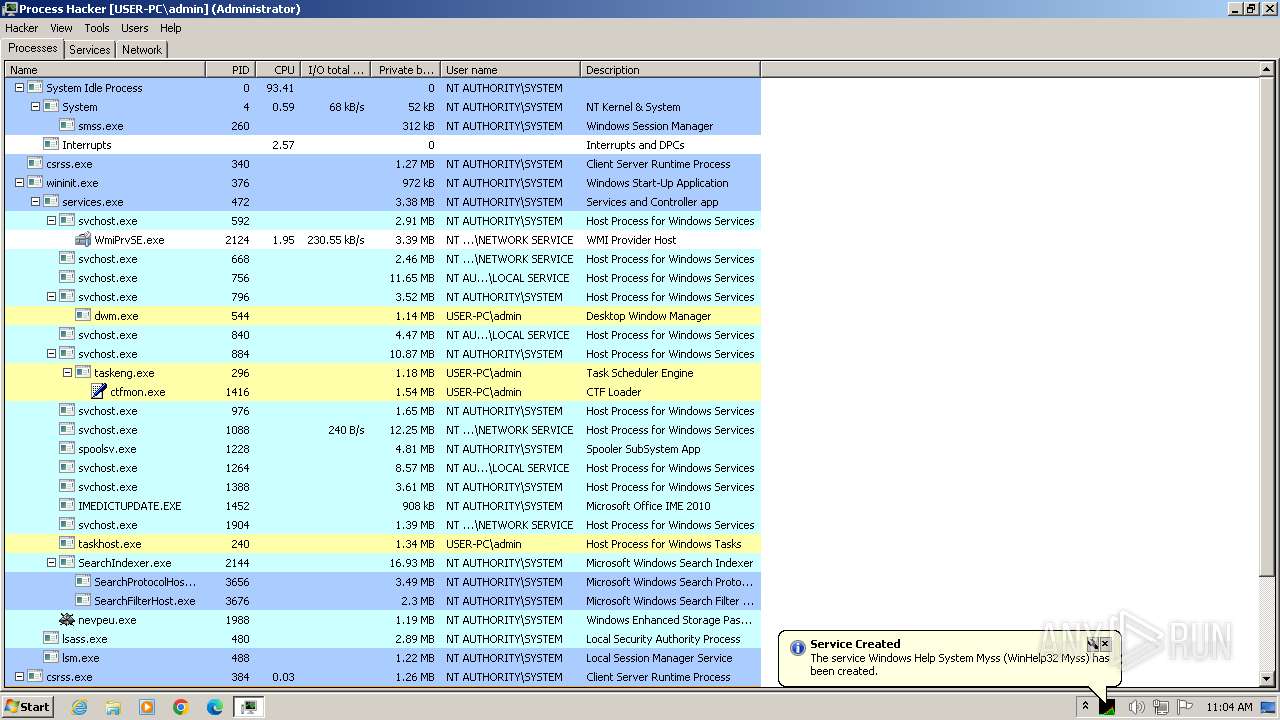
Total processes
407
Monitored processes
256
Malicious processes
59
Suspicious processes
40
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | schtasks.exe /create /tn "winlogonw" /sc MINUTE /mo 13 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\winlogon.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\Users\admin\Desktop\Files\svcyr.exe" | C:\Users\admin\Desktop\Files\svcyr.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Enhanced Storage Password Authentication Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | schtasks.exe /create /tn "csrssc" /sc MINUTE /mo 14 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\csrss.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | C:\Users\admin\Desktop\Files\NewB.exe | C:\Users\admin\Desktop\Files\NewB.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 308 | "C:\Users\admin\Desktop\Files\loader.exe" | C:\Users\admin\Desktop\Files\loader.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 308 | "C:\Users\admin\Desktop\Files\s.exe" | C:\Users\admin\Desktop\Files\s.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 316 | ICACLS "C:\Program Files\AIOC5" /grant:r Everyone:(OI)(CI)(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 504 | "C:\Users\admin\AppData\Local\Temp\u1gc.0.exe" | C:\Users\admin\AppData\Local\Temp\u1gc.0.exe | ISetup8.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 524 | schtasks.exe /create /tn "dwmd" /sc MINUTE /mo 13 /tr "'C:\Users\All Users\Templates\dwm.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | "C:\Program Files\Microsoft Yimvuz\Uiekeum.exe" Win7 | C:\Program Files\Microsoft Yimvuz\Uiekeum.exe | — | Uiekeum.exe | |||||||||||
User: SYSTEM Company: Microsoft, Inc. Integrity Level: SYSTEM Description: HTTPSVR MFC Application Exit code: 0 Version: 2, 0, 0, 1 Modules
| |||||||||||||||
Total events
144 697
Read events
143 729
Write events
887
Delete events
81
Modification events
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1020) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
148
Suspicious files
40
Text files
53
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ARA.exe | executable | |
MD5:FB10155E44F99861B4F315842AAD8117 | SHA256:118F5BA14837745EEF57BF35ED413AAF13945E8651EBF361304A86B28B0A532C | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ebehmoni.dll | executable | |
MD5:D9CE7153A878749C59AF90BE5952AEC2 | SHA256:60EF7CDADC1778AA08855810233B6887741A9291F36296F20C024A2B2F44D18A | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\concrt140.dll | executable | |
MD5:119DBAD74C457A2D692CE6765028E88B | SHA256:5F6A435A4A1DA4BBBF8ADB80BD7A81F263FF98D0193AF4ED8E15D39F803DE06E | |||
| 1424 | svcyr.exe | C:\Users\admin\AppData\Local\Temp\c706ec | executable | |
MD5:7EDC4B4B6593BD68C65CD155B8755F26 | SHA256:DCD92EC043CB491B3DE3E4F73FBE35041274A9B81D48B4377C8C9A8157C95590 | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\cfgres.dll | executable | |
MD5:F4C9CF4A73F3ACD5A4EF1F60F9297145 | SHA256:81B4575928B6D753306848C2F9217BA076D3C0643CB20F378CD883CDB4FDD329 | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\eamsi.dll | executable | |
MD5:CCFE48E3AAF6A7ADF5643D90CDE3439C | SHA256:5E1F9CBC0F1CA645183F26E25463679AA89CD22A29D427C000AEA0E1E9C11903 | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\DMON.dll | executable | |
MD5:58F7761BE8678A189604E2B61C7D7AEB | SHA256:F759CEF48A4E798BEC5AC8BAF10376E1E024E0A128B4B4A5B45F289EE31207DF | |||
| 728 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ebehmonl.dll | executable | |
MD5:2686070D4A4B5C7401B7AF185ABD71BF | SHA256:11F686ACA158EF40459B0CF92F117186B63765151BDF4295C268AE5DADCABE2A | |||
| 1236 | ARA.exe | C:\Users\admin\AppData\Roaming\reviewintobrokerHost\WJgXY0RCE6WdWGoPyLk7f.bat | text | |
MD5:62416939CBA1A6B6C67A4D907E563F09 | SHA256:1BC255D6927643C2F628AE5AB09D83694B99992BC70B2289348FCA9C966D97AA | |||
| 1236 | ARA.exe | C:\Users\admin\AppData\Roaming\reviewintobrokerHost\aUs3pwix5Vd1U6IYzTsfZ9E8dEV3MF.vbe | vbe | |
MD5:5050104B6A1222B401DE71F0079FD122 | SHA256:43C7B034403C39D71802A2EFC7558648C229544B3337D4298498A0D503151A46 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
63
TCP/UDP connections
158
DNS requests
46
Threats
291
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1020 | 4363463463464363463463463.exe | GET | 200 | 185.234.216.64:8000 | http://185.234.216.64:8000/PH32.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 160.181.160.187:8888 | http://160.181.160.187:8888/svcyr.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 92.60.39.76:9993 | http://92.60.39.76:9993/wr.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | — | 121.177.29.204:8080 | http://121.177.29.204:8080/nomal1.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 103.164.63.79:80 | http://www.aokdemc.com/setup%E4%B8%8B%E8%BD%BD%E5%90%8D%E5%8D%95%E7%9B%AE%E5%BD%956001.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://marksidfgs.ug/ghjkl.exe | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.121:80 | http://185.172.128.121/svchost.exe | unknown | — | — | unknown |
2968 | taskeng.exe | GET | 301 | 23.227.193.58:80 | http://23.227.193.58/trackwordpressdleCentral.php?nTpz4tBkEffHSxvJX2feX5v=PFt&EW3lilo=8ZvGO6YDsWpwXo96D7U&e0f29c517e1a609644d46d762ae60a99=e89d1129f5ab2e60dc88598472194209&da16ae8a37fa2943455b333d7e17db89=QZ4MDOiBTNwQWZ4MTOjhTOiNTYyMzMyUGMjFGN1ETMhZzMiJGN5UWM&nTpz4tBkEffHSxvJX2feX5v=PFt&EW3lilo=8ZvGO6YDsWpwXo96D7U | unknown | — | — | unknown |
1020 | 4363463463464363463463463.exe | GET | 200 | 43.226.35.175:80 | http://43.226.35.175/server.exe | unknown | — | — | unknown |
2968 | taskeng.exe | GET | 200 | 95.100.146.43:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fb6f5b5aeaf0aab2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1020 | 4363463463464363463463463.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1020 | 4363463463464363463463463.exe | 185.234.216.64:8000 | — | — | RU | unknown |
1020 | 4363463463464363463463463.exe | 210.19.94.140:443 | www.maxmoney.com | TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Al | MY | unknown |
1020 | 4363463463464363463463463.exe | 160.181.160.187:8888 | — | Technology Business Development Limited | AE | unknown |
1020 | 4363463463464363463463463.exe | 92.60.39.76:9993 | — | netcup GmbH | DE | unknown |
1020 | 4363463463464363463463463.exe | 121.177.29.204:8080 | rornfl12.duckdns.org | Korea Telecom | KR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
www.maxmoney.com |
| unknown |
v8.ter.tf |
| unknown |
www.aokdemc.com |
| unknown |
marksidfgs.ug |
| unknown |
rornfl12.duckdns.org |
| unknown |
www.osijek1862.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
manulop.ug |
| unknown |
github.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1020 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 33 |
1020 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1020 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1020 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1020 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1020 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
— | — | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
— | — | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
— | — | A Network Trojan was detected | ET HUNTING Rejetto HTTP File Sever Response |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
29 ETPRO signatures available at the full report
Process | Message |
|---|---|
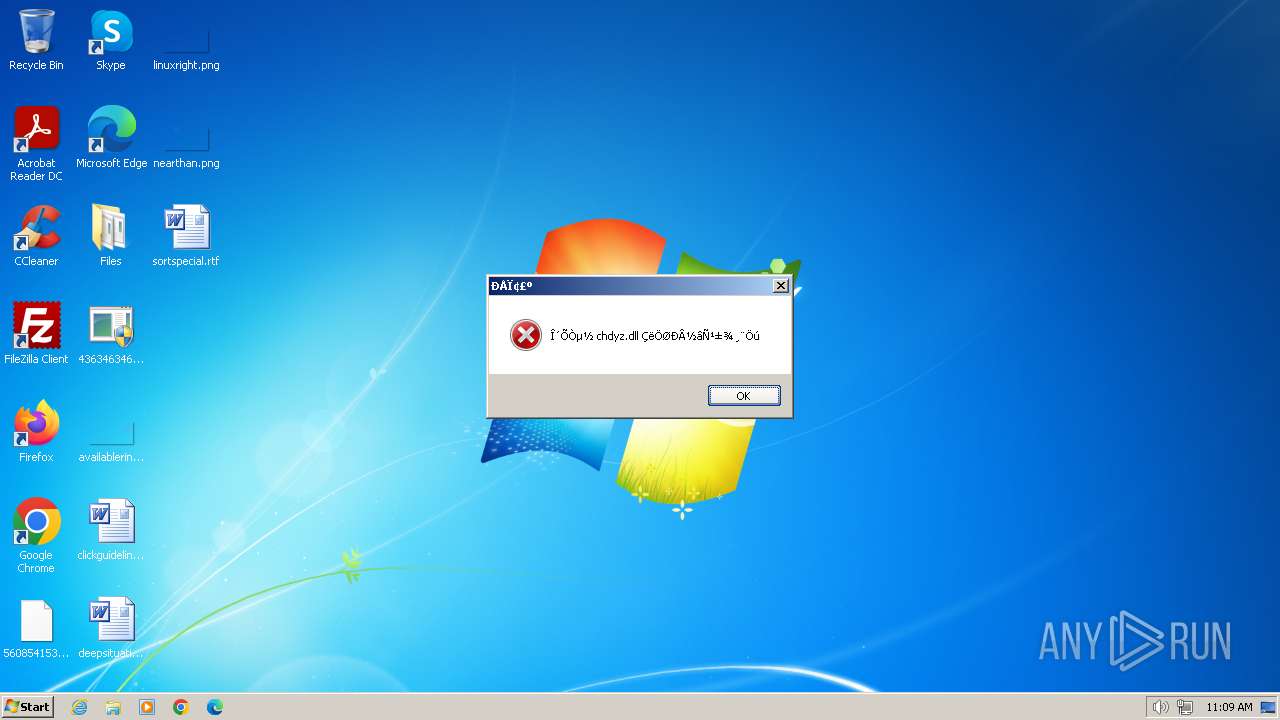
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | An exception occurred during a WebClient request.
|