| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/31afca0e-72d3-42a3-ae38-ecce406e9c58 |
| Verdict: | Malicious activity |
| Threats: | Arkei is a stealer type malware capable of collecting passwords, autosaved forms, cryptocurrency wallet credentials, and files. |
| Analysis date: | February 13, 2024, 18:37:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 2852)
- asdfg.exe (PID: 2692)
- NeonRank.exe (PID: 696)
- cmd.exe (PID: 1556)
- BBLb.exe (PID: 3724)
- ama.exe (PID: 3508)
- inst77player_1.0.0.1.exe (PID: 3792)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 1168)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- vcredist2013.exe (PID: 3720)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1844)
- findstr.exe (PID: 1236)
Run PowerShell with an invisible window
- powershell.exe (PID: 2020)
- powershell.exe (PID: 3728)
Bypass execution policy to execute commands
- powershell.exe (PID: 2020)
- powershell.exe (PID: 3728)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2852)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 2112)
Connects to the CnC server
- 6dAEd.exe (PID: 3140)
- 991sN.exe (PID: 2316)
Actions looks like stealing of personal data
- dialer.exe (PID: 2112)
- dialer.exe (PID: 3396)
AZORULT has been detected (SURICATA)
- 6dAEd.exe (PID: 3140)
- 991sN.exe (PID: 2316)
Remcos is detected
- 6.exe (PID: 1832)
REMCOS has been detected (SURICATA)
- 6.exe (PID: 1832)
ARKEI has been detected (YARA)
- build.exe (PID: 4072)
REMCOS has been detected (YARA)
- 6.exe (PID: 1832)
METASTEALER has been detected (YARA)
- easy.exe (PID: 2408)
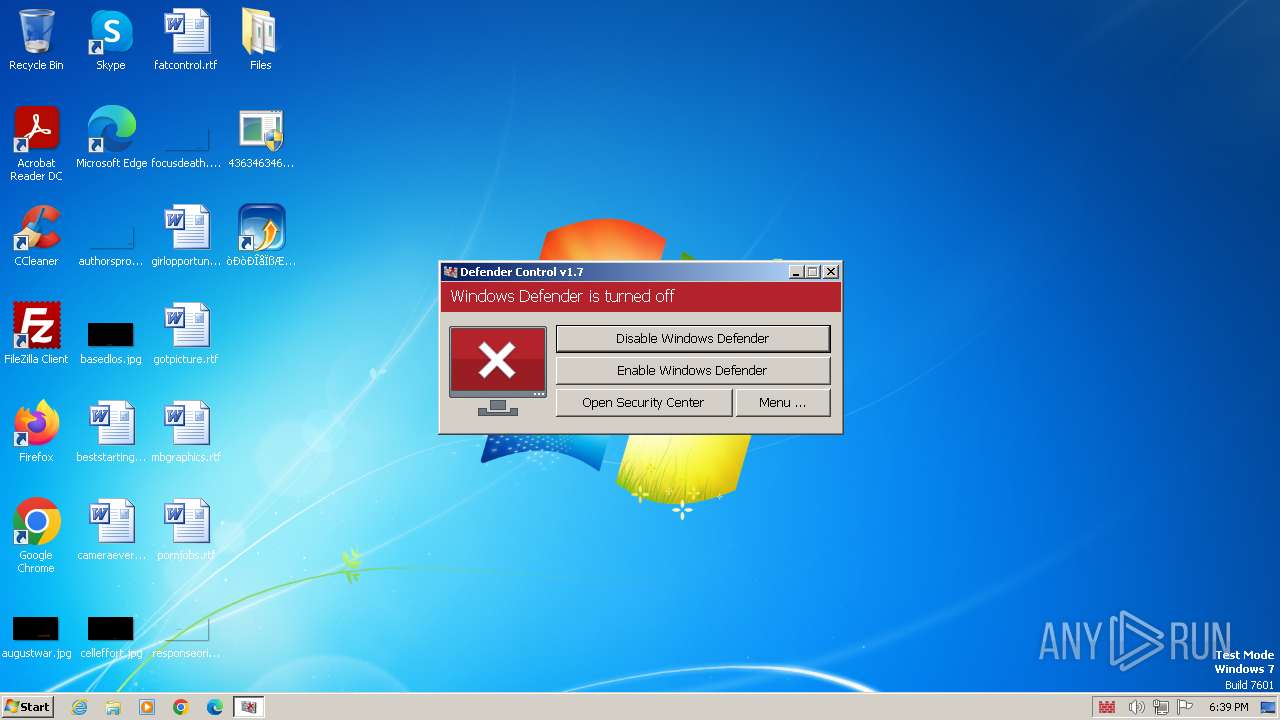
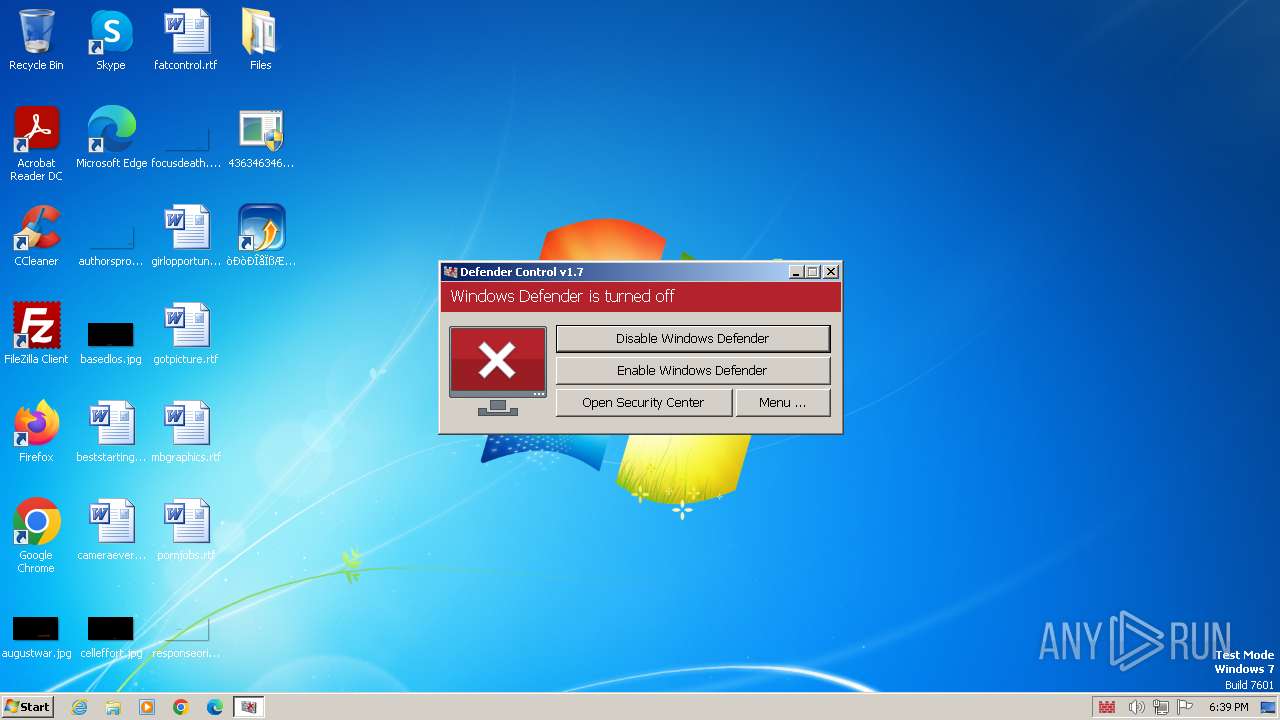
Disables Windows Defender
- DefenderControl.exe (PID: 3348)
- DefenderControl.exe (PID: 3164)
Creates or modifies Windows services
- DefenderControl.exe (PID: 3348)
- DefenderControl.exe (PID: 3164)
- DefenderControl.exe (PID: 1584)
AZORULT has been detected (YARA)
- 991sN.exe (PID: 2316)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2852)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- data64_1.exe (PID: 3940)
- build.exe (PID: 4072)
- data64_6.exe (PID: 3588)
- setup_wm.exe (PID: 1340)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2852)
- asdfg.exe (PID: 2692)
- NeonRank.exe (PID: 696)
- cmd.exe (PID: 1556)
- BBLb.exe (PID: 3724)
- dialer.exe (PID: 2112)
- ama.exe (PID: 3508)
- inst77player_1.0.0.1.exe (PID: 3792)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 1168)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- vcredist2013.exe (PID: 3720)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
- dialer.exe (PID: 3396)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2852)
- baseline.exe (PID: 2328)
- asdfg.exe (PID: 2692)
- NeonRank.exe (PID: 696)
- powershell.exe (PID: 2020)
- 6dAEd.exe (PID: 3140)
- inst77player.exe (PID: 3456)
- powershell.exe (PID: 3728)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- data64_1.exe (PID: 3940)
- autoupdate.exe (PID: 2588)
- build.exe (PID: 4072)
- data64_6.exe (PID: 3588)
- setup_wm.exe (PID: 1340)
- 991sN.exe (PID: 2316)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2852)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2852)
- asdfg.exe (PID: 2692)
- NeonRank.exe (PID: 696)
- 6dAEd.exe (PID: 3140)
- inst77player.exe (PID: 3456)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- build.exe (PID: 4072)
- setup_wm.exe (PID: 1340)
- 991sN.exe (PID: 2316)
Application launched itself
- asdfg.exe (PID: 2692)
- cmd.exe (PID: 2372)
- BBLb.exe (PID: 2896)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2900)
- 6dAEd.exe (PID: 3312)
- AttributeString.exe (PID: 908)
- MSBuild.exe (PID: 3268)
- vcredist2013.exe (PID: 1992)
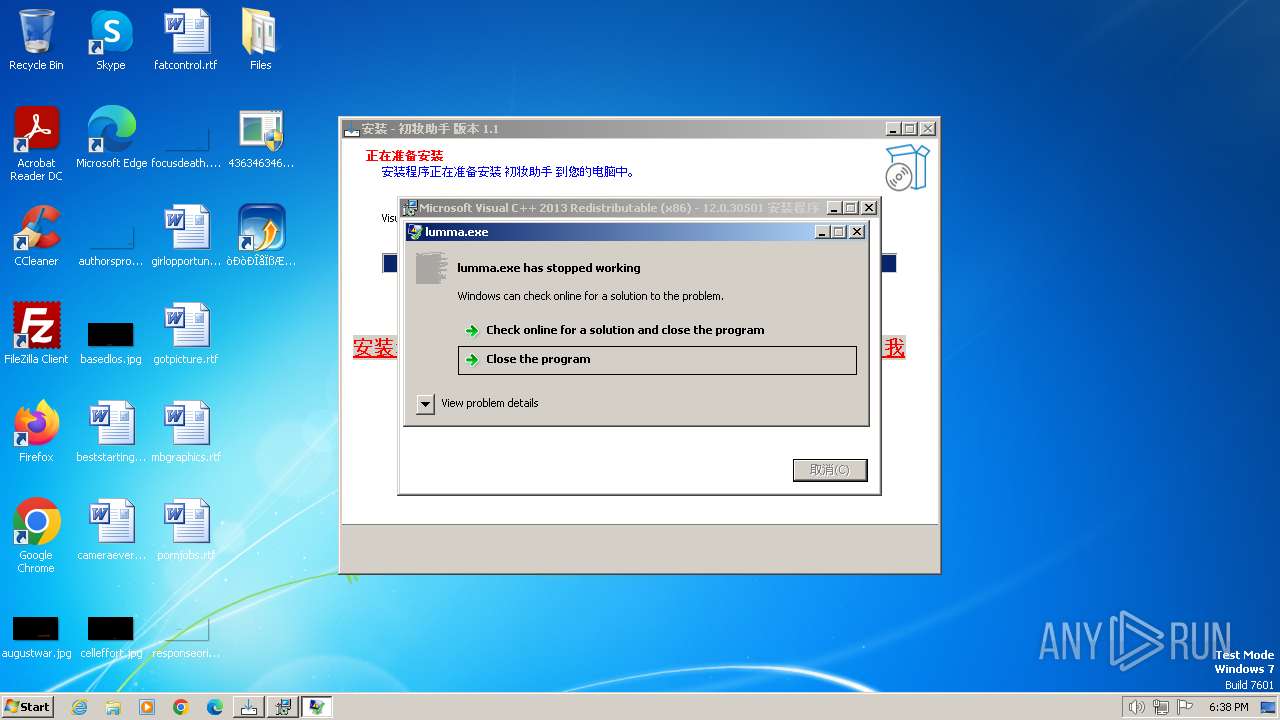
- lumma.exe (PID: 3708)
- net.exe (PID: 3040)
- native.exe (PID: 2900)
- DefenderControl.exe (PID: 3348)
- 991sN.exe (PID: 3996)
Get information on the list of running processes
- cmd.exe (PID: 2372)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2372)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2372)
- NeonRank.exe (PID: 696)
The executable file from the user directory is run by the CMD process
- Taxes.pif (PID: 3544)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2372)
Executing commands from a ".bat" file
- NeonRank.exe (PID: 696)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 1556)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 2112)
- dialer.exe (PID: 3396)
Connects to unusual port
- baseline.exe (PID: 2328)
- 4363463463464363463463463.exe (PID: 2852)
- MSBuild.exe (PID: 3548)
- 6.exe (PID: 1832)
- easy.exe (PID: 2408)
The process executes via Task Scheduler
- powershell.exe (PID: 2020)
- AttributeString.exe (PID: 908)
- powershell.exe (PID: 3728)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2020)
- powershell.exe (PID: 3728)
Reads browser cookies
- dialer.exe (PID: 2112)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 2112)
- dialer.exe (PID: 3396)
Executed via WMI
- 6dAEd.exe (PID: 3312)
- 991sN.exe (PID: 3996)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 2112)
- dialer.exe (PID: 3396)
Searches for installed software
- dialer.exe (PID: 2112)
- vcredist2013.exe (PID: 3720)
- vcredist2013.exe (PID: 1992)
- dialer.exe (PID: 3396)
Starts application with an unusual extension
- cmd.exe (PID: 2372)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2852)
Creates a software uninstall entry
- inst77player_1.0.0.1.exe (PID: 3792)
Reads the Windows owner or organization settings
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- data64_1.exe (PID: 3940)
- build.exe (PID: 4072)
- data64_6.exe (PID: 3588)
Process drops legitimate windows executable
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- vcredist2013.exe (PID: 3720)
- 4363463463464363463463463.exe (PID: 2852)
Starts a Microsoft application from unusual location
- vcredist2013.exe (PID: 1992)
- vcredist2013.exe (PID: 3720)
- setup_wm.exe (PID: 1340)
Writes files like Keylogger logs
- 4363463463464363463463463.exe (PID: 2852)
- 6.exe (PID: 1832)
Executes as Windows Service
- VSSVC.exe (PID: 2388)
Checks Windows Trust Settings
- build.exe (PID: 4072)
- setup_wm.exe (PID: 1340)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2852)
- 991sN.exe (PID: 2316)
- build.exe (PID: 4072)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 2852)
- asdfg.exe (PID: 2692)
- baseline.exe (PID: 2328)
- BBLb.exe (PID: 2896)
- asdfg.exe (PID: 1496)
- NeonRank.exe (PID: 696)
- ama.exe (PID: 3508)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2900)
- BBLb.exe (PID: 3724)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 2384)
- Taxes.pif (PID: 3544)
- wmlaunch.exe (PID: 920)
- 6dAEd.exe (PID: 3312)
- 6dAEd.exe (PID: 3140)
- AttributeString.exe (PID: 908)
- inst77player_1.0.0.1.exe (PID: 3792)
- inst77player.exe (PID: 3456)
- AttributeString.exe (PID: 3044)
- MSBuild.exe (PID: 3268)
- MSBuild.exe (PID: 3548)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 1168)
- vcredist2013.exe (PID: 1992)
- data64_1.exe (PID: 3940)
- vcredist2013.exe (PID: 3720)
- 6.exe (PID: 1832)
- lumma.exe (PID: 3772)
- autoupdate.exe (PID: 2588)
- build.exe (PID: 4072)
- net.exe (PID: 3040)
- net.exe (PID: 4056)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
- DefenderControl.exe (PID: 3348)
- easy.exe (PID: 2408)
- native.exe (PID: 2900)
- native.exe (PID: 3808)
- data64_6.exe (PID: 3588)
- setup_wm.exe (PID: 1340)
- lumma.exe (PID: 3708)
- DefenderControl.exe (PID: 3164)
- DefenderControl.exe (PID: 1584)
- 991sN.exe (PID: 3996)
- 991sN.exe (PID: 2316)
Reads the computer name
- baseline.exe (PID: 2328)
- 4363463463464363463463463.exe (PID: 2852)
- asdfg.exe (PID: 2692)
- BBLb.exe (PID: 2896)
- BBLb.exe (PID: 3724)
- NeonRank.exe (PID: 696)
- Taxes.pif (PID: 3544)
- 6dAEd.exe (PID: 3312)
- 6dAEd.exe (PID: 3140)
- ama.exe (PID: 3508)
- AttributeString.exe (PID: 908)
- inst77player_1.0.0.1.exe (PID: 3792)
- inst77player.exe (PID: 3456)
- AttributeString.exe (PID: 3044)
- MSBuild.exe (PID: 3268)
- MSBuild.exe (PID: 3548)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- data64_1.exe (PID: 3940)
- vcredist2013.exe (PID: 3720)
- vcredist2013.exe (PID: 1992)
- autoupdate.exe (PID: 2588)
- 6.exe (PID: 1832)
- build.exe (PID: 4072)
- net.exe (PID: 3040)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
- DefenderControl.exe (PID: 3348)
- native.exe (PID: 2900)
- easy.exe (PID: 2408)
- data64_6.exe (PID: 3588)
- setup_wm.exe (PID: 1340)
- DefenderControl.exe (PID: 3164)
- DefenderControl.exe (PID: 1584)
- 991sN.exe (PID: 3996)
- 991sN.exe (PID: 2316)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2852)
- 6dAEd.exe (PID: 3140)
- data64_1.exe (PID: 3940)
- autoupdate.exe (PID: 2588)
- 6.exe (PID: 1832)
- data64_6.exe (PID: 3588)
- 991sN.exe (PID: 2316)
Checks proxy server information
- baseline.exe (PID: 2328)
- 6dAEd.exe (PID: 3140)
- inst77player.exe (PID: 3456)
- build.exe (PID: 4072)
- setup_wm.exe (PID: 1340)
- 991sN.exe (PID: 2316)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2852)
- baseline.exe (PID: 2328)
- asdfg.exe (PID: 2692)
- BBLb.exe (PID: 2896)
- BBLb.exe (PID: 3724)
- wmlaunch.exe (PID: 920)
- 6dAEd.exe (PID: 3140)
- 6dAEd.exe (PID: 3312)
- AttributeString.exe (PID: 908)
- AttributeString.exe (PID: 3044)
- MSBuild.exe (PID: 3268)
- MSBuild.exe (PID: 3548)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- data64_1.exe (PID: 3940)
- vcredist2013.exe (PID: 1992)
- autoupdate.exe (PID: 2588)
- 6.exe (PID: 1832)
- build.exe (PID: 4072)
- inst77player.exe (PID: 3456)
- net.exe (PID: 3040)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
- native.exe (PID: 2900)
- data64_6.exe (PID: 3588)
- easy.exe (PID: 2408)
- setup_wm.exe (PID: 1340)
- 991sN.exe (PID: 3996)
- 991sN.exe (PID: 2316)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2852)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- data64_1.exe (PID: 3940)
- build.exe (PID: 4072)
- data64_6.exe (PID: 3588)
- setup_wm.exe (PID: 1340)
Create files in a temporary directory
- asdfg.exe (PID: 2692)
- NeonRank.exe (PID: 696)
- ama.exe (PID: 3508)
- inst77player_1.0.0.1.exe (PID: 3792)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe (PID: 1168)
- vcredist2013.exe (PID: 3720)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 3172)
- DefenderControl.exe (PID: 3348)
Creates files or folders in the user directory
- BBLb.exe (PID: 3724)
- dialer.exe (PID: 2112)
- inst77player_1.0.0.1.exe (PID: 3792)
- autoupdate.exe (PID: 2588)
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
- build.exe (PID: 4072)
- dialer.exe (PID: 3396)
Reads mouse settings
- Taxes.pif (PID: 3544)
- DefenderControl.exe (PID: 3348)
- DefenderControl.exe (PID: 3164)
- DefenderControl.exe (PID: 1584)
Drops the executable file immediately after the start
- dialer.exe (PID: 2112)
- dialer.exe (PID: 3396)
Reads product name
- 6dAEd.exe (PID: 3140)
- 6.exe (PID: 1832)
- 991sN.exe (PID: 2316)
Creates files in the program directory
- inst77player_1.0.0.1.exe (PID: 3792)
Creates a software uninstall entry
- %E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.tmp (PID: 3392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(1832) 6.exe
C2 (9)hendersonk1.hopto.org:2404
henderson1.camdvr.org:2404
centplus1.serveftp.com:2404
harrywlike.ddns.net:2404
genekol.nsupdate.info:2404
harrywlike1.ddns.net:2404
hendersonk2022.hopto.org:2404
genekol1.nsupdate.info:2404
generem.camdvr.org:2404
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\ShellGY99V
Setup_path%APPDATA%
Copy_filesonic.exe
Startup_valuefuckuuuuu
Hide_fileFalse
Mutex_namegsgjdwg-1J0WWM
Keylog_flag1
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_namenotepad;solitaire;
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_dirMicRecords
Connect_delay0
Copy_diryakkk
Keylog_dirchrome
Max_keylog_file20000
Arkei
(PID) Process(4072) build.exe
C2 (1)https://t.me/deadftx
Strings (31)46"-vli
2>SR'
IF6FU5*
CQHBTE'#K
TG;4NC
^!onp?
ikj
=ecd"
w=!{tzn
JLXAB
cF2RY\^NH
uibydg
0qz-myG@
c48e{vejsfCo
R0/^5#!9LWP*U?GA2
3WQ98F8WRA'10/I\?
HU%QQ2DK\Y1]!3FV9
>+=OF_V]EO!#5U+
pdb<-\
\% lj3E$
N*JWA1
> ZH@V
"E0@Q1\_OSM]$
DU\ACTQZ*
1D<_ZEMMVEV
-EXH-U@:
eD3U69$NCBTE<
UDJT*SMX)4
K YC-/B4A-:
FDRPQ
^VYGWU
MetaStealer
(PID) Process(2408) easy.exe
C2 (1)5.42.65.101:48790
Botnet325904615-26990097-easy
Options
ErrorMessage
Keys
XorPyrometry
azorult
(PID) Process(2316) 991sN.exe
Hostshttp://195.245.112.115/index.php
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
141
Monitored processes
60
Malicious processes
30
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | "C:\Users\admin\Desktop\Files\NeonRank.exe" | C:\Users\admin\Desktop\Files\NeonRank.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 908 | C:\Users\admin\AppData\Local\TypeId\renxwnji\AttributeString.exe | C:\Users\admin\AppData\Local\TypeId\renxwnji\AttributeString.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Windows Media Player\wmlaunch.exe" | C:\Program Files\Windows Media Player\wmlaunch.exe | — | dialer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Media Player Launcher Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\Files\%E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe" | C:\Users\admin\Desktop\Files\%E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: 初妆助手 Integrity Level: HIGH Description: 初妆助手 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1236 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | "C:\Users\admin\Desktop\Files\setup_wm.exe" | C:\Users\admin\Desktop\Files\setup_wm.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Configuration Utility Exit code: 0 Version: 12.0.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1496 | C:\Users\admin\Desktop\Files\asdfg.exe | C:\Users\admin\Desktop\Files\asdfg.exe | asdfg.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1556 | cmd /c copy /b Compound + Injection + Emotions + Worm + Participants + Richmond 4096\Taxes.pif | C:\Windows\System32\cmd.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
64 167
Read events
63 346
Write events
739
Delete events
82
Modification events
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2852) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
37
Suspicious files
22
Text files
35
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Bathrooms | text | |
MD5:1730EAEBB468F5EB2EB028FEBF54AE06 | SHA256:6BB1EB00577143D94353505D3FAA833A6E11A1B1E7A89665374546B6C4224D18 | |||
| 2852 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\baseline.exe | executable | |
MD5:ED144CAEBBC81B2914858FA9A59388FB | SHA256:0034D86B2E202EEE69EF00B3551753F133278BD26E0EE0F486F0CC7E3DC61032 | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Compound | executable | |
MD5:F763B8E9BBA9221A1683238D61C7D049 | SHA256:D636D9543514FFC8EF80980E52E425A7031383274ABC22AFCA077EAB72ACFF06 | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Assured | text | |
MD5:D1D04D0889C995208BFD51027D6BBFB2 | SHA256:FEB509566E97E0B401FA0C358410C4E30A2CA737E97AB53BA85AA8B7233039E2 | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Declare | text | |
MD5:2894B437EB1F14BB3DC2D0995DC8238E | SHA256:5B151A88F51C5AFD71E1437D61D0B5E4E8354B60570EC7EB57FF115314AC00AD | |||
| 2852 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe | executable | |
MD5:B7FD5FB6D18A968E7014F73AA81A4005 | SHA256:A0538252234EDD82661F55FEA05DF541C095A9F74368D8DCA1582D797A1D084A | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Richmond | binary | |
MD5:7CEF207172CBDF6768101F8A2602F787 | SHA256:6C3482C9F62DA91208F4F67FE2A41211F8A2A7929BFDA4841495D20D29BF1E9C | |||
| 3724 | BBLb.exe | C:\Users\admin\AppData\Local\TypeId\renxwnji\AttributeString.exe | executable | |
MD5:71EB1BC6E6DA380C1CB552D78B391B2A | SHA256:CEFA92EE6CC2FAD86C49DD37D57FF8AFCB9B9ABEF0A110689E6D771394256BD6 | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Emotions | binary | |
MD5:4DD712F3AC47D2632B1FA470891858C9 | SHA256:025BDBD4ACD0829141281AD412F7BA59E21D253C19FDECE25304A7EACA592BA8 | |||
| 696 | NeonRank.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Participants | binary | |
MD5:96C01CB0CAF4A239B2CDAC79372C249B | SHA256:1BD9E4921D3E304CBBDBE7E169C090F023940C3901C3F30076AA805AAE46A6F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
128
DNS requests
39
Threats
72
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2852 | 4363463463464363463463463.exe | GET | 200 | 104.192.108.17:80 | http://softdl.360tpcdn.com/inst77player/inst77player_1.0.0.1.exe | unknown | executable | 281 Kb | unknown |
2852 | 4363463463464363463463463.exe | GET | 200 | 163.171.130.139:80 | http://static.cz01.cn/setup/%E5%88%9D%E5%A6%86%E5%8A%A9%E6%89%8B.exe | unknown | executable | 2.23 Mb | unknown |
2852 | 4363463463464363463463463.exe | GET | 200 | 68.66.226.93:80 | http://thedoctorsgym.net/10/data64_1.exe | unknown | executable | 9.00 Kb | unknown |
4072 | build.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | binary | 1.98 Kb | unknown |
4072 | build.exe | GET | 304 | 23.48.23.62:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8949edd576c54a9e | unknown | — | — | unknown |
4072 | build.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | binary | 2.01 Kb | unknown |
4072 | build.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2852 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://hubvera.ac.ug/net.exe | unknown | executable | 2.13 Mb | unknown |
1080 | svchost.exe | GET | 200 | 2.18.121.71:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f183bcfd71f5ea6b | unknown | compressed | 65.2 Kb | unknown |
2852 | 4363463463464363463463463.exe | GET | 200 | 68.66.226.93:80 | http://thedoctorsgym.net/12/data64_6.exe | unknown | executable | 9.00 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2852 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2852 | 4363463463464363463463463.exe | 193.117.208.148:80 | — | Virtual1 Limited | GB | unknown |
2852 | 4363463463464363463463463.exe | 91.215.85.223:80 | lastimaners.ug | — | RU | unknown |
2328 | baseline.exe | 193.117.208.148:7800 | — | Virtual1 Limited | GB | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2852 | 4363463463464363463463463.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
2852 | 4363463463464363463463463.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2852 | 4363463463464363463463463.exe | 185.172.128.32:80 | — | OOO Nadym Svyaz Service | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
lastimaners.ug |
| unknown |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
JDkGqaSrgKXZ.JDkGqaSrgKXZ |
| unknown |
pastratas.ac.ug |
| unknown |
parals.ac.ug |
| unknown |
softdl.360tpcdn.com |
| unknown |
u.yinyuehome.com |
| unknown |
nickshort.ug |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2852 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2852 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2852 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2852 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2852 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2852 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2852 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2852 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2852 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2852 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
17 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | Unable to connect to the remote server
|
4363463463464363463463463.exe | Unable to connect to the remote server
|