| File name: | 4363463463464363463463463.bin |
| Full analysis: | https://app.any.run/tasks/309ac908-1a56-4537-bce8-ca6eca0be84a |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 03:19:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
NJRAT has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
- Server.exe (PID: 2320)
- njrat.exe (PID: 3860)
- main.exe (PID: 5416)
- dllhost.exe (PID: 1268)
- 856.exe (PID: 7984)
- svchost.exe (PID: 6824)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.bin.exe (PID: 4044)
Changes the autorun value in the registry
- Server.exe (PID: 2320)
- Java Updater.exe (PID: 5124)
- Java Updater.exe (PID: 4320)
NJRAT has been detected (YARA)
- Server.exe (PID: 2320)
NjRAT is detected
- Server.exe (PID: 2320)
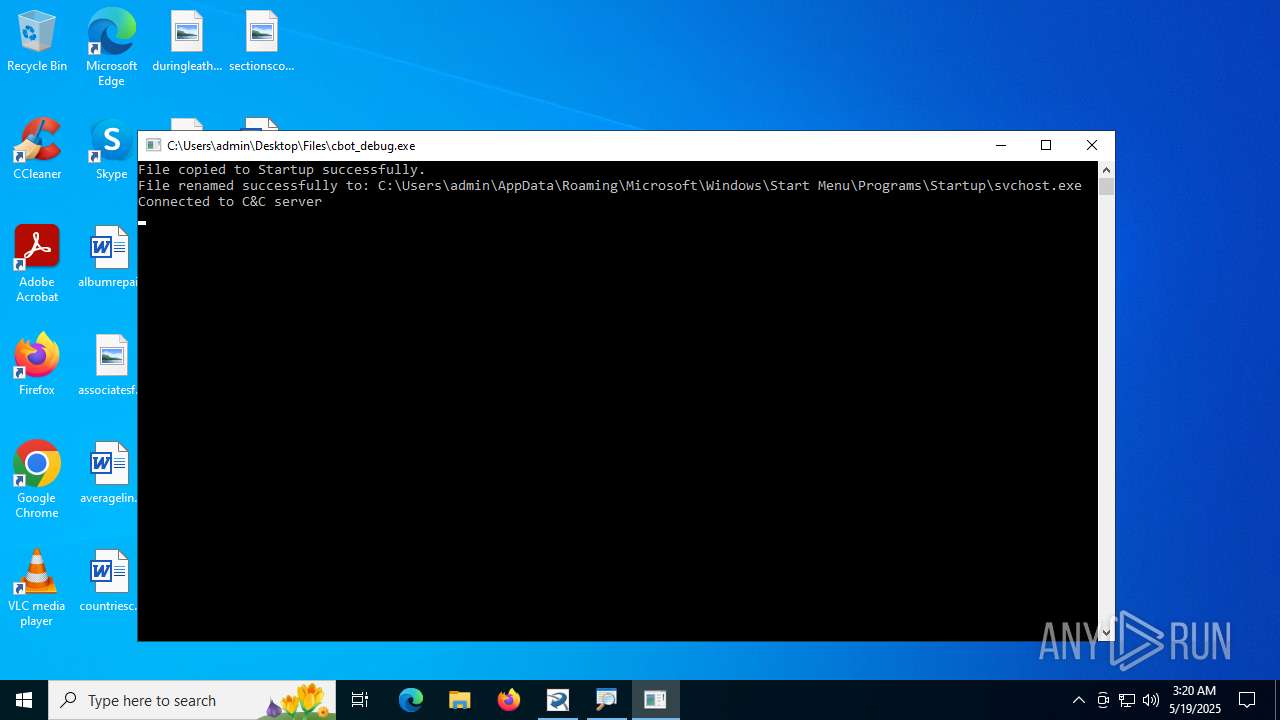
Create files in the Startup directory
- Server.exe (PID: 2320)
- cbot_debug.exe (PID: 4168)
QUASARRAT has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
- spectrum.exe (PID: 6164)
- 4363463463464363463463463.bin.exe (PID: 4044)
- Client-built.exe (PID: 2404)
- CollosalLoader.exe (PID: 4664)
- 4363463463464363463463463.bin.exe (PID: 4044)
- Sentil.exe (PID: 1136)
- Quas_Autre_ncrypt.exe (PID: 4800)
- svhost.exe (PID: 7640)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 2404)
- cmd.exe (PID: 5236)
- runtime.exe (PID: 5240)
- MSWinpreference.exe (PID: 2180)
- Sentil.exe (PID: 1136)
- Client1.exe (PID: 3716)
- Clients.exe (PID: 1044)
- Clients.exe (PID: 7240)
- svhost.exe (PID: 5680)
- Clients.exe (PID: 8652)
- Clients.exe (PID: 8424)
- Clients.exe (PID: 6016)
- Clients.exe (PID: 9844)
ASYNCRAT has been found (auto)
- Terminal_9235.exe (PID: 2384)
- XClient.exe (PID: 4088)
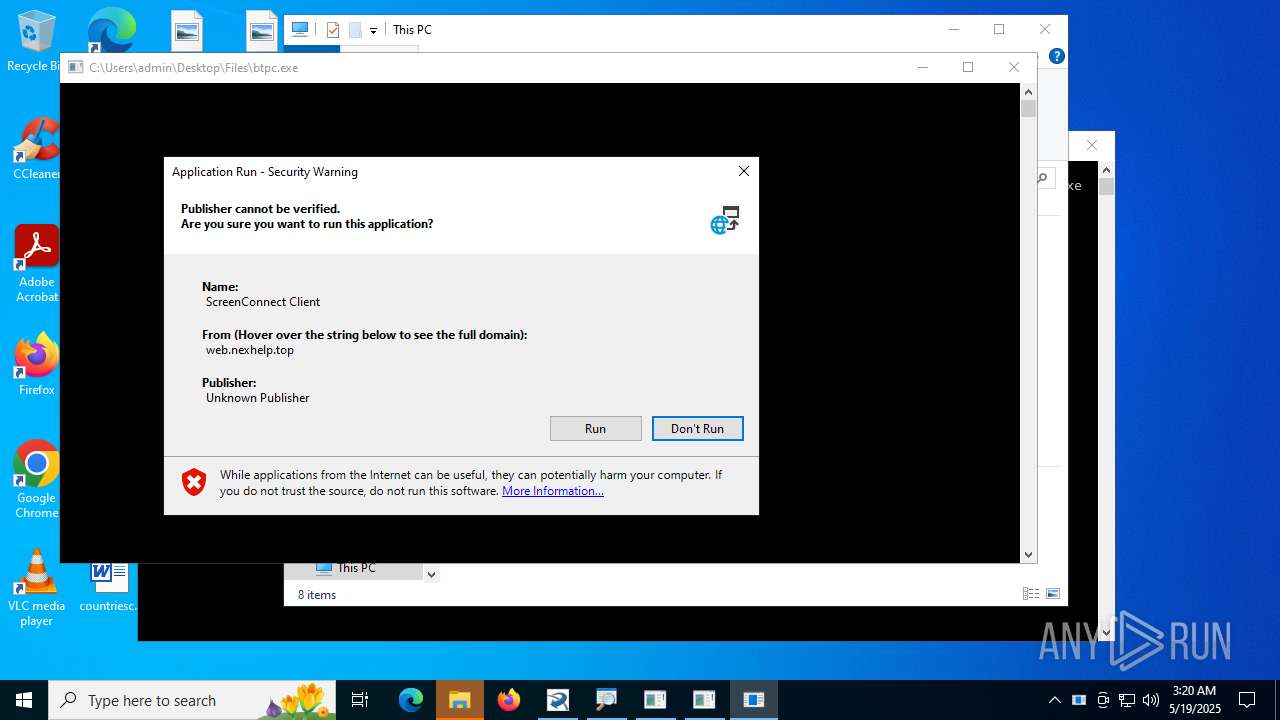
Executing a file with an untrusted certificate
- random.exe (PID: 5584)
- 1188%E7%83%88%E7%84%B0.exe (PID: 7684)
- mixseven.exe (PID: 7256)
RAT has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
QUASAR has been detected (YARA)
- Java Updater.exe (PID: 7032)
ASYNCRAT has been detected (MUTEX)
- aaa%20(3).exe (PID: 4900)
- 333.exe (PID: 5840)
STEALER has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
LUMMA has been detected (SURICATA)
- MSBuild.exe (PID: 1812)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 1340)
Connects to the CnC server
- svchost.exe (PID: 2200)
- 4363463463464363463463463.bin.exe (PID: 4044)
GCLEANER has been detected (SURICATA)
- random.exe (PID: 5584)
HAVOC has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
Changes Windows Defender settings
- XClient.exe (PID: 4088)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 4088)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 4088)
Bypass execution policy to execute commands
- powershell.exe (PID: 7496)
- powershell.exe (PID: 1012)
- powershell.exe (PID: 7724)
- powershell.exe (PID: 7900)
Uses Task Scheduler to run other applications
- dllhost.exe (PID: 1268)
- svchost.exe (PID: 6824)
- XClient.exe (PID: 4088)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 4088)
LOADER has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
Stealers network behavior
- svchost.exe (PID: 2200)
GENERIC has been found (auto)
- 4363463463464363463463463.bin.exe (PID: 4044)
- mixseven.exe (PID: 7256)
- random.exe (PID: 5584)
SUSPICIOUS
Reads security settings of Internet Explorer
- 4363463463464363463463463.bin.exe (PID: 4044)
- njrat.exe (PID: 3860)
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
Executable content was dropped or overwritten
- 4363463463464363463463463.bin.exe (PID: 4044)
- Server.exe (PID: 2320)
- spectrum.exe (PID: 6164)
- njrat.exe (PID: 3860)
- svchost.exe (PID: 6820)
- cbot_debug.exe (PID: 4168)
- Client-built.exe (PID: 2404)
- Terminal_9235.exe (PID: 2384)
- CollosalLoader.exe (PID: 4664)
- Quas_Autre_ncrypt.exe (PID: 4800)
- Sentil.exe (PID: 1136)
- taskmoder.exe (PID: 4004)
- main.exe (PID: 5416)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 1584)
- DRIVEapplet.exe (PID: 5708)
- dfsvc.exe (PID: 2188)
- dllhost.exe (PID: 1268)
- Hl2dm_Updater.exe (PID: 8176)
- Hl2dm_Updater.exe (PID: 7700)
- zal.exe (PID: 1044)
- raw_cbot_debug.exe (PID: 7336)
- 5vJ.exe (PID: 5068)
- svhost.exe (PID: 7640)
- mixseven.exe (PID: 7256)
- random.exe (PID: 5584)
- 856.exe (PID: 7984)
- svchost.exe (PID: 6824)
- XClient.exe (PID: 4088)
Process requests binary or script from the Internet
- 4363463463464363463463463.bin.exe (PID: 4044)
- 1188%E7%83%88%E7%84%B0.exe (PID: 7684)
- Hl2dm_Updater.exe (PID: 7700)
- Hl2dm_Updater.exe (PID: 8176)
Potential Corporate Privacy Violation
- 4363463463464363463463463.bin.exe (PID: 4044)
- Hl2dm_Updater.exe (PID: 8176)
- Hl2dm_Updater.exe (PID: 7700)
- %E6%A4%8D%E7%89%A9%E5%A4%A7%E6%88%98%E5%83%B5%E5%B0%B82%E4%BF%AE%E6%94%B9%E5%99%A8.exe (PID: 7520)
- random.exe (PID: 5584)
- svchost.exe (PID: 2200)
Starts itself from another location
- njrat.exe (PID: 3860)
- spectrum.exe (PID: 6164)
- Client-built.exe (PID: 2404)
- CollosalLoader.exe (PID: 4664)
- Quas_Autre_ncrypt.exe (PID: 4800)
- Sentil.exe (PID: 1136)
- main.exe (PID: 5416)
- svhost.exe (PID: 7640)
- 856.exe (PID: 7984)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Server.exe (PID: 2320)
- mos%20ssssttttt.exe (PID: 3860)
- 856.exe (PID: 7984)
- svchost.exe (PID: 6824)
The process creates files with name similar to system file names
- 4363463463464363463463463.bin.exe (PID: 4044)
- svchost.exe (PID: 6820)
There is functionality for taking screenshot (YARA)
- RemotelyAnywhere11.exe (PID: 856)
- Java Updater.exe (PID: 7032)
Connects to unusual port
- Server.exe (PID: 2320)
- 4363463463464363463463463.bin.exe (PID: 4044)
- Java Updater.exe (PID: 7032)
- cbot_debug.exe (PID: 4168)
- runtime.exe (PID: 5240)
- MSWinpreference.exe (PID: 2180)
- Java Updater.exe (PID: 5124)
- Java Updater.exe (PID: 4320)
- 333.exe (PID: 5840)
- Steanings.exe (PID: 4224)
- Client1.exe (PID: 3716)
- fontdrvhost.exe (PID: 7324)
- dialer.exe (PID: 7436)
- dllhost.exe (PID: 1268)
- %E6%A4%8D%E7%89%A9%E5%A4%A7%E6%88%98%E5%83%B5%E5%B0%B82%E4%BF%AE%E6%94%B9%E5%99%A8.exe (PID: 7520)
- svhost.exe (PID: 5680)
- raw_cbot_debug.exe (PID: 7336)
- aaa%20(3).exe (PID: 4900)
Starts a Microsoft application from unusual location
- cbot_debug.exe (PID: 4168)
- dais.exe (PID: 7952)
- raw_cbot_debug.exe (PID: 7336)
Reads the date of Windows installation
- svchost.exe (PID: 6820)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
- Clients.exe (PID: 1636)
- Clients.exe (PID: 6284)
- main.exe (PID: 5416)
- client.exe (PID: 7216)
- Clients.exe (PID: 1044)
- Clients.exe (PID: 7892)
- Clients.exe (PID: 7240)
- zal.exe (PID: 1044)
- Clients.exe (PID: 8100)
- qhfuhb3t.ezf.exe (PID: 5544)
- Clients.exe (PID: 8652)
- Clients.exe (PID: 5748)
- Clients.exe (PID: 8424)
- Clients.exe (PID: 6016)
- Clients.exe (PID: 9844)
- Clients.exe (PID: 7580)
Executing commands from a ".bat" file
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
- Clients.exe (PID: 1636)
- Clients.exe (PID: 6284)
- Clients.exe (PID: 1044)
- Clients.exe (PID: 7892)
- Clients.exe (PID: 7240)
- zal.exe (PID: 1044)
- Clients.exe (PID: 8100)
- qhfuhb3t.ezf.exe (PID: 5544)
- Clients.exe (PID: 8652)
- Clients.exe (PID: 5748)
- Clients.exe (PID: 9844)
- Clients.exe (PID: 8424)
- Clients.exe (PID: 6016)
- Clients.exe (PID: 7580)
Process drops legitimate windows executable
- 4363463463464363463463463.bin.exe (PID: 4044)
- cbot_debug.exe (PID: 4168)
- raw_cbot_debug.exe (PID: 7336)
Connects to the server without a host name
- 4363463463464363463463463.bin.exe (PID: 4044)
- random.exe (PID: 5584)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4224)
- cmd.exe (PID: 6180)
The executable file from the user directory is run by the CMD process
- $77svchost.exe (PID: 3556)
- client.exe (PID: 984)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- mos%20ssssttttt.exe (PID: 3860)
- 856.exe (PID: 7984)
- svchost.exe (PID: 6824)
Starts application with an unusual extension
- cmd.exe (PID: 1832)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 5996)
- cmd.exe (PID: 8584)
- cmd.exe (PID: 4852)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 5092)
The process executes VB scripts
- taskmoder.exe (PID: 4004)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1832)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 5996)
- cmd.exe (PID: 8584)
- cmd.exe (PID: 4852)
- cmd.exe (PID: 5092)
- cmd.exe (PID: 9316)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 7072)
- dllhost.exe (PID: 1268)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 1812)
- 4363463463464363463463463.bin.exe (PID: 4044)
- MSBuild.exe (PID: 1340)
Malware-specific behavior (creating "System.dll" in Temp)
- maza-0.16.3-win64-setup-unsigned.exe (PID: 1584)
Checks for external IP
- XClient.exe (PID: 4088)
- svchost.exe (PID: 2200)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 4088)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 4088)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7228)
- schtasks.exe (PID: 8236)
- schtasks.exe (PID: 8856)
- schtasks.exe (PID: 4860)
- schtasks.exe (PID: 7840)
- schtasks.exe (PID: 9588)
Executes application which crashes
- MSBuild.exe (PID: 6260)
- support.client.exe (PID: 2144)
Identifying current user with WHOAMI command
- %E6%A4%8D%E7%89%A9%E5%A4%A7%E6%88%98%E5%83%B5%E5%B0%B82%E4%BF%AE%E6%94%B9%E5%99%A8.exe (PID: 7520)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 4088)
The process executes via Task Scheduler
- dllhost.exe (PID: 2140)
- StUpdate.exe (PID: 9708)
- Setup.exe (PID: 9720)
- dllhost.exe (PID: 9772)
- StUpdate.exe (PID: 8708)
- dllhost.exe (PID: 9332)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.bin.exe (PID: 4044)
INFO
Reads the machine GUID from the registry
- 4363463463464363463463463.bin.exe (PID: 4044)
- Server.exe (PID: 2320)
- spectrum.exe (PID: 6164)
- cbot_debug.exe (PID: 4168)
- CollosalLoader.exe (PID: 4664)
- Client-built.exe (PID: 2404)
- svchost.exe (PID: 6820)
- Java Updater.exe (PID: 7032)
- Terminal_9235.exe (PID: 2384)
- spectrum.exe (PID: 5992)
- MSWinpreference.exe (PID: 2180)
- Java Updater.exe (PID: 5124)
- runtime.exe (PID: 4132)
- runtime.exe (PID: 5240)
- MSWinpreference.exe (PID: 7068)
- $77svchost.exe (PID: 1496)
- $77svchost.exe (PID: 3556)
- client.exe (PID: 5028)
- mos%20ssssttttt.exe (PID: 3860)
- 333.exe (PID: 5840)
- Java Updater.exe (PID: 4320)
- client.exe (PID: 984)
- aaa%20(3).exe (PID: 4900)
- Quas_Autre_ncrypt.exe (PID: 4800)
Disables trace logs
- 4363463463464363463463463.bin.exe (PID: 4044)
- $77svchost.exe (PID: 1496)
Reads the computer name
- 4363463463464363463463463.bin.exe (PID: 4044)
- njrat.exe (PID: 3860)
- Server.exe (PID: 2320)
- Server.exe (PID: 7132)
- spectrum.exe (PID: 6164)
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
- Java Updater.exe (PID: 7032)
- ScanPort.exe (PID: 3780)
- Client-built.exe (PID: 2404)
- RemotelyAnywhere11.exe (PID: 856)
- CollosalLoader.exe (PID: 4664)
- runtime.exe (PID: 5240)
- spectrum.exe (PID: 5992)
- MSWinpreference.exe (PID: 2180)
- Java Updater.exe (PID: 5124)
- $77svchost.exe (PID: 1496)
- client.exe (PID: 5028)
- MSWinpreference.exe (PID: 7068)
- runtime.exe (PID: 4132)
- $77svchost.exe (PID: 3556)
- DRIVEapplet.exe (PID: 5708)
- Java Updater.exe (PID: 4320)
- client.exe (PID: 984)
- mos%20ssssttttt.exe (PID: 3860)
- 333.exe (PID: 5840)
- aaa%20(3).exe (PID: 4900)
- Sentil.exe (PID: 1136)
- Quas_Autre_ncrypt.exe (PID: 4800)
Checks proxy server information
- 4363463463464363463463463.bin.exe (PID: 4044)
- $77svchost.exe (PID: 1496)
Process checks computer location settings
- 4363463463464363463463463.bin.exe (PID: 4044)
- njrat.exe (PID: 3860)
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
Checks supported languages
- njrat.exe (PID: 3860)
- 4363463463464363463463463.bin.exe (PID: 4044)
- RemotelyAnywhere11.exe (PID: 856)
- Server.exe (PID: 2320)
- Server.exe (PID: 7132)
- news2_02.exe (PID: 1732)
- svchost.exe (PID: 6820)
- spectrum.exe (PID: 6164)
- Terminal_9235.exe (PID: 2384)
- Java Updater.exe (PID: 7032)
- Client-built.exe (PID: 2404)
- cbot_debug.exe (PID: 4168)
- CollosalLoader.exe (PID: 4664)
- ScanPort.exe (PID: 3780)
- runtime.exe (PID: 5240)
- spectrum.exe (PID: 5992)
- $77svchost.exe (PID: 1496)
- Java Updater.exe (PID: 5124)
- MSWinpreference.exe (PID: 2180)
- MSWinpreference.exe (PID: 7068)
- runtime.exe (PID: 4132)
- $77svchost.exe (PID: 3556)
- client.exe (PID: 5028)
- client.exe (PID: 984)
- DRIVEapplet.exe (PID: 5708)
- Java Updater.exe (PID: 4320)
- mos%20ssssttttt.exe (PID: 3860)
- 333.exe (PID: 5840)
- random.exe (PID: 5584)
- mini_04.exe (PID: 6832)
- aaa%20(3).exe (PID: 4900)
- Quas_Autre_ncrypt.exe (PID: 4800)
- Sentil.exe (PID: 1136)
Reads the software policy settings
- 4363463463464363463463463.bin.exe (PID: 4044)
- $77svchost.exe (PID: 1496)
Auto-launch of the file from Registry key
- Server.exe (PID: 2320)
- Java Updater.exe (PID: 5124)
- Java Updater.exe (PID: 4320)
Manual execution by a user
- Server.exe (PID: 7132)
- spectrum.exe (PID: 5992)
- $77svchost.exe (PID: 1496)
- Java Updater.exe (PID: 5124)
- client.exe (PID: 5028)
- runtime.exe (PID: 4132)
- MSWinpreference.exe (PID: 7068)
- Java Updater.exe (PID: 4320)
- Clients.exe (PID: 6284)
- Client1.exe (PID: 5928)
Creates files or folders in the user directory
- Server.exe (PID: 2320)
- spectrum.exe (PID: 6164)
- svchost.exe (PID: 6820)
- cbot_debug.exe (PID: 4168)
- Terminal_9235.exe (PID: 2384)
- CollosalLoader.exe (PID: 4664)
- mos%20ssssttttt.exe (PID: 3860)
Auto-launch of the file from Startup directory
- Server.exe (PID: 2320)
- cbot_debug.exe (PID: 4168)
Reads Environment values
- spectrum.exe (PID: 6164)
- Java Updater.exe (PID: 7032)
- Client-built.exe (PID: 2404)
- CollosalLoader.exe (PID: 4664)
- runtime.exe (PID: 5240)
- Java Updater.exe (PID: 5124)
- spectrum.exe (PID: 5992)
- MSWinpreference.exe (PID: 2180)
- runtime.exe (PID: 4132)
- MSWinpreference.exe (PID: 7068)
- $77svchost.exe (PID: 1496)
- Java Updater.exe (PID: 4320)
- Quas_Autre_ncrypt.exe (PID: 4800)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- spectrum.exe (PID: 6164)
- Java Updater.exe (PID: 7032)
- cmd.exe (PID: 4968)
- CollosalLoader.exe (PID: 4664)
- Clients.exe (PID: 1636)
- Quas_Autre_ncrypt.exe (PID: 4800)
- svhost.exe (PID: 7640)
- Clients.exe (PID: 5748)
- Clients.exe (PID: 7580)
Create files in a temporary directory
- njrat.exe (PID: 3860)
- svchost.exe (PID: 6820)
- Terminal_9235.exe (PID: 2384)
- mos%20ssssttttt.exe (PID: 3860)
The sample compiled with english language support
- 4363463463464363463463463.bin.exe (PID: 4044)
- cbot_debug.exe (PID: 4168)
- raw_cbot_debug.exe (PID: 7336)
- Hl2dm_Updater.exe (PID: 7700)
- mixseven.exe (PID: 7256)
The sample compiled with chinese language support
- 4363463463464363463463463.bin.exe (PID: 4044)
Creates files in the program directory
- Quas_Autre_ncrypt.exe (PID: 4800)
Changes the display of characters in the console
- cmd.exe (PID: 1832)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 7712)
- cmd.exe (PID: 2404)
- cmd.exe (PID: 7432)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 7744)
- cmd.exe (PID: 5996)
- cmd.exe (PID: 8584)
- cmd.exe (PID: 4852)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 5092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(2320) Server.exe
C210.0.0.16
Ports1177
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\c7c410475d4d33dd6b97dc1e4dc051b8
Splitter|'|'|
Version0.7d
Quasar
(PID) Process(7032) Java Updater.exe
Version1.4.0
C2 (5)192.168.31.99:4782
2001:4bc9:1f98:a4e::676:4782
255.255.255.0:4782
fe80::cabf:4cff:fe84:9572%17:4782
Sub_DirSubDir
Install_NameJava Updater.exe
Mutex1f65a787-81b8-4955-95e4-b7751e10cd50
StartupJava Updater
TagOffice04
LogDirLogs
SignatureIpoC4G3VyXpCX73v8GLDgGX/ZD0uyJLyqReXAqvKNH4BzMk3aCKHatwBDnXbtrYfH96ChJhU2qLyWTlHJUq+HoFp5tRNEGlBaYc4IVl0lEBCjQsDf3wMCaU/2Ns/z3lVzh7AYhfCMb7L/mgf/ZfDTlEJasxUBvBxHVeahyU9WD2HTH2ZyabAt3fHWrcnpoZWMA40Zn+F5whQw5O7VIRpO5BFmYGBosHkSSeFe56cyRhha4rXQLWUx6ghioEm4px39T6OhjYSHUIArYzIM7z7hcOTAbXEgoZ7o6mG/GfLaECs...
CertificateMIIE9DCCAtygAwIBAgIQALWSoR4pE9fOZHv3Ui7LYTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIyMTEyNDEwMTk1M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhOEJcBCuOOX0MDmITV+fSJpkL4NBxf1/CNJoEpUamratcDd5r9kc9hO+9tpd7DnFmZc5JQTa...
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
493
Monitored processes
328
Malicious processes
29
Suspicious processes
27
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
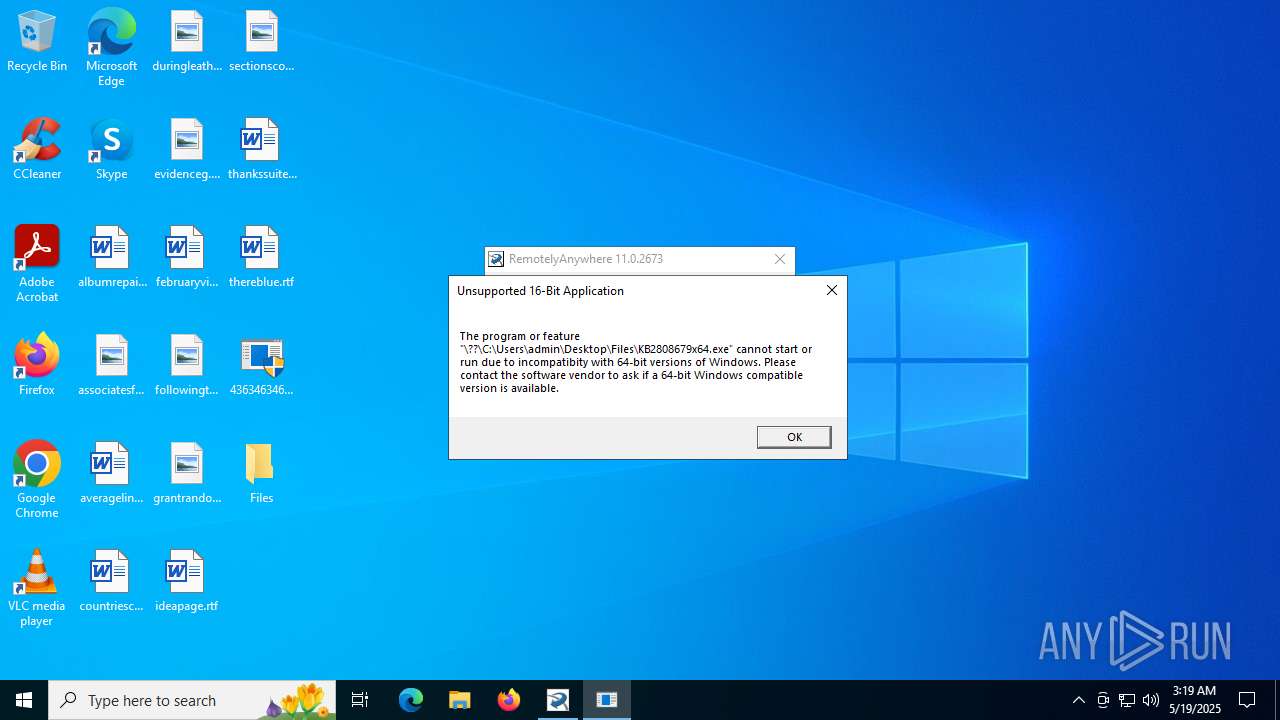
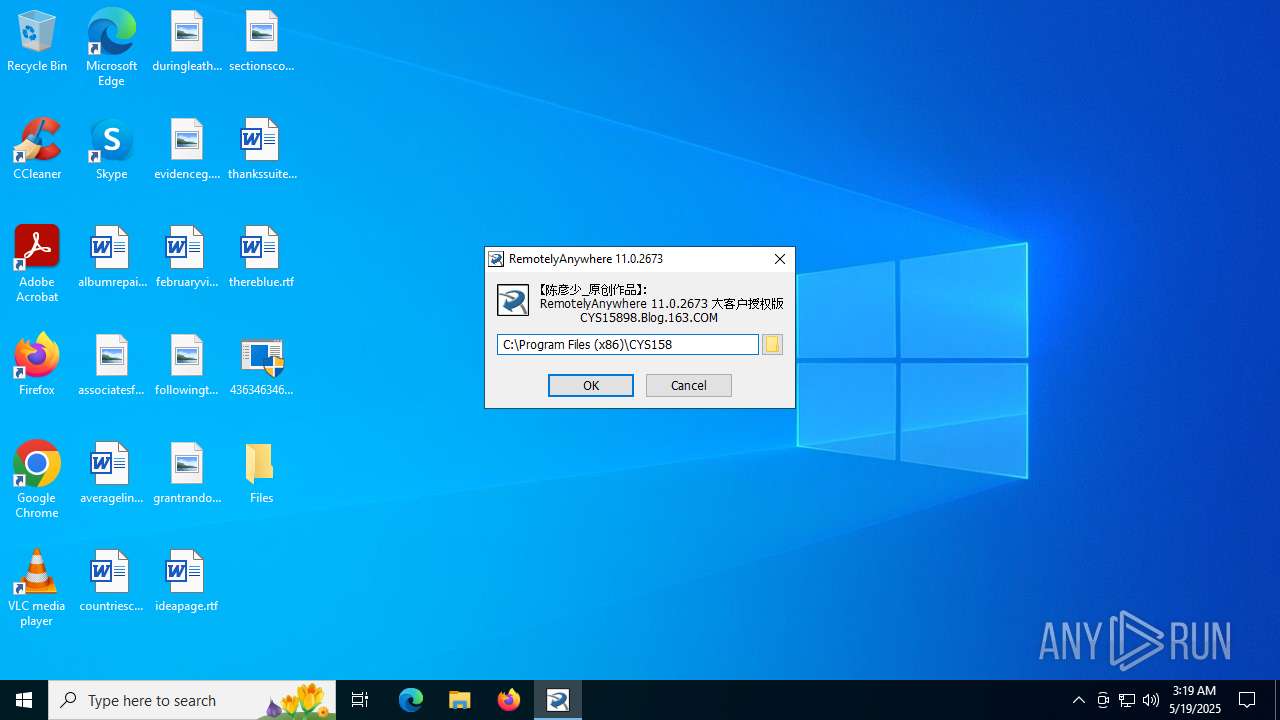
| 856 | "C:\Users\admin\Desktop\Files\RemotelyAnywhere11.exe" | C:\Users\admin\Desktop\Files\RemotelyAnywhere11.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: HIGH Description: 7z Setup SFX (x86) Version: 1.4.1.2100 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 4294967295 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | "C:\Users\admin\AppData\Roaming\client.exe" | C:\Users\admin\AppData\Roaming\client.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Digital Services Multi-Tool Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1012 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass Add-MpPreference -ExclusionProcess 'XClient.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | XClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Program Files\SubDare\Clients.exe" | C:\Program Files\SubDare\Clients.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Exit code: 0 Version: 1.4.1 Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\Desktop\Files\zal.exe" | C:\Users\admin\Desktop\Files\zal.exe | 4363463463464363463463463.bin.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\Files\setup.exe" | C:\Users\admin\Desktop\Files\setup.exe | — | 4363463463464363463463463.bin.exe | |||||||||||
User: admin Company: Daniel Pistelli Integrity Level: HIGH Description: Common File Format Explorer Exit code: 0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 1136 | "schtasks" /create /tn "Skype" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\MSWinpreference.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | CollosalLoader.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
191 183
Read events
189 831
Write events
1 329
Delete events
23
Modification events
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (4044) 4363463463464363463463463.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
144
Suspicious files
123
Text files
92
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\RemotelyAnywhere11.exe | executable | |
MD5:284EA9A4093393C540D00B3A0802FA1C | SHA256:87A2D394EE9E70B9B269AF24EE47A5EEDC797E2115629812471E4316F149480B | |||
| 3860 | njrat.exe | C:\Users\admin\AppData\Local\Temp\Server.exe | executable | |
MD5:8A71E8EBF8C24D8F7B48A29FC023815E | SHA256:36882AFAFF37F70BE8D2566F1B4F8A05764C27305F4809002F1EE2822B6D8EA5 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\spectrum.exe | executable | |
MD5:1441905FC4082EE6055EA39F5875A6C5 | SHA256:1B05C4D74E0D17A983F9B91AA706A7A60F37EC270B7E2433D6798AFA1C7BE766 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\ScanPort.exe | executable | |
MD5:36C6F6FEE875B519A81284FAFB3E41B1 | SHA256:6F83E3F9C38108DBEA18AE72954C4157520EB105EAD4182F4C863574CCE824E1 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\svchost.exe | executable | |
MD5:DA4B81BD7225F06FA1FF1A6C0F50C69F | SHA256:01C295A6690C48FF3196FF3EF0FEF7383BDBA9BEAA6DADF8426E689263BE5E20 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\KB2808679x64.exe | compressed | |
MD5:466FF3292FDD6E33A9A3B40821FAECF1 | SHA256:20A90D3D1BAB871B73A42E5488A2DA462F7E06CAB96BEB8B9E0C033E8F0E5877 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\Terminal_9235.exe | executable | |
MD5:7BC2E6B25BFAFE16708196E844DC1476 | SHA256:A72A243CA862F09C197A135B15CC3081B7635CB1C78BB7F92DAA932B78754B06 | |||
| 4168 | cbot_debug.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\cbot_debug.exe | executable | |
MD5:984F4BD2FB821583A9AF79A26D091D56 | SHA256:25171039CB6453F0BEC289800C09858BAF1D496BAD4647AD0DD1984B97E3792E | |||
| 2320 | Server.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\c7c410475d4d33dd6b97dc1e4dc051b8.exe | executable | |
MD5:8A71E8EBF8C24D8F7B48A29FC023815E | SHA256:36882AFAFF37F70BE8D2566F1B4F8A05764C27305F4809002F1EE2822B6D8EA5 | |||
| 4044 | 4363463463464363463463463.bin.exe | C:\Users\admin\Desktop\Files\news2_02.exe | executable | |
MD5:3D56A9374DE3382BD4C698DDA152BEDE | SHA256:D9B7003644FE59EEBD75CD9F0B8364FD73230512E99F795FAB8E2E0F93B8ED04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
118
TCP/UDP connections
427
DNS requests
101
Threats
203
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | 4363463463464363463463463.bin.exe | GET | — | 60.191.208.187:820 | http://ftp.ywxww.net:820/RemotelyAnywhere11.exe | unknown | — | — | unknown |
6960 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1840 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6804 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4044 | 4363463463464363463463463.bin.exe | GET | 301 | 140.82.121.3:80 | http://github.com/tiraUnderCode/rev/raw/main/Client-built.exe | unknown | — | — | whitelisted |
1520 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4044 | 4363463463464363463463463.bin.exe | GET | 200 | 59.83.212.226:80 | http://download.pdf00.cn/kszip/news2/v1.0.7.31/news2_02.exe | unknown | — | — | malicious |
1520 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4044 | 4363463463464363463463463.bin.exe | GET | 301 | 140.82.121.3:80 | http://github.com/XerusSploit/Spectrum/raw/refs/heads/main/spectrum.exe | unknown | — | — | whitelisted |
4044 | 4363463463464363463463463.bin.exe | GET | 200 | 51.38.140.180:80 | http://51.38.140.180/cbot/cbot_debug.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2424 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1840 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1840 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4044 | 4363463463464363463463463.bin.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
4044 | 4363463463464363463463463.bin.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
ftp.ywxww.net |
| unknown |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
4044 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4044 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4044 | 4363463463464363463463463.bin.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4044 | 4363463463464363463463463.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
Process | Message |
|---|---|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.bin.exe | An exception occurred during a WebClient request.
|
4363463463464363463463463.bin.exe | The remote server returned an error: (403) Forbidden.
|
4363463463464363463463463.bin.exe | The specified executable is not a valid application for this OS platform.
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 230
|
4363463463464363463463463.bin.exe | The file or directory is corrupted and unreadable
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741772
*** Source File: onecore\com\netfx\windowsbuilt\iso_legacy\base\isolation\win32\isoreg_direct.cpp, line 1127
|