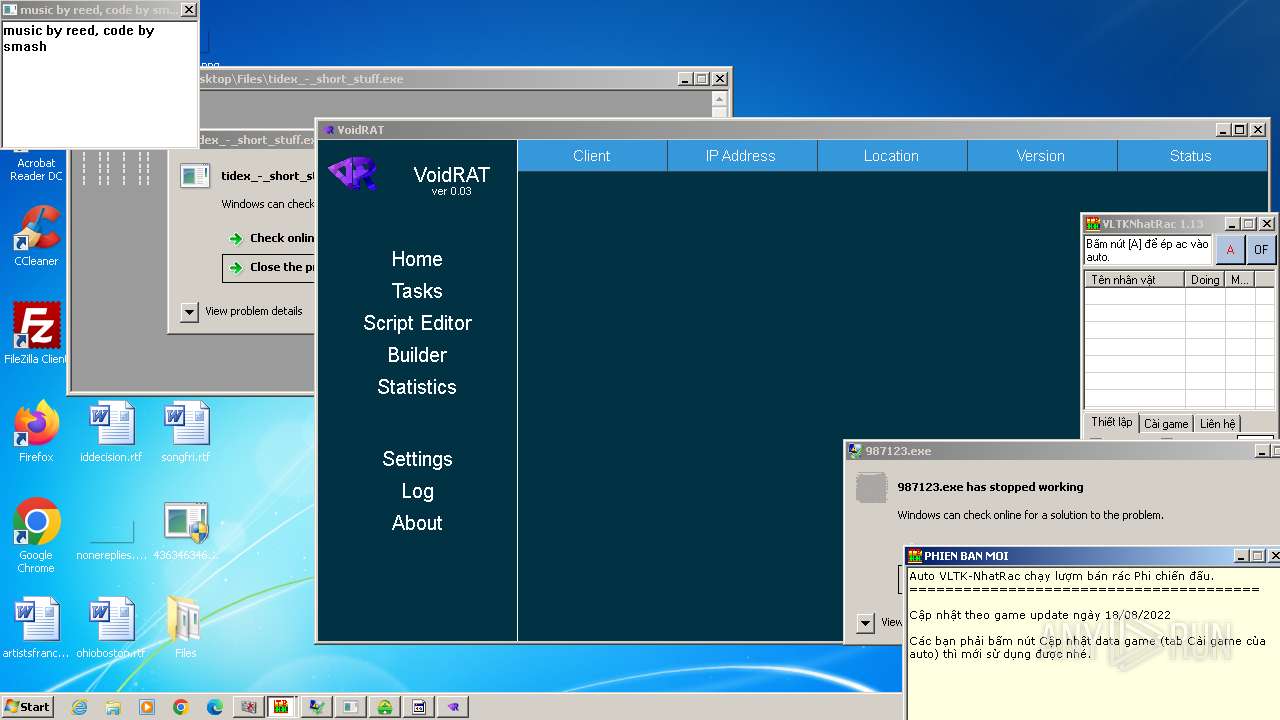
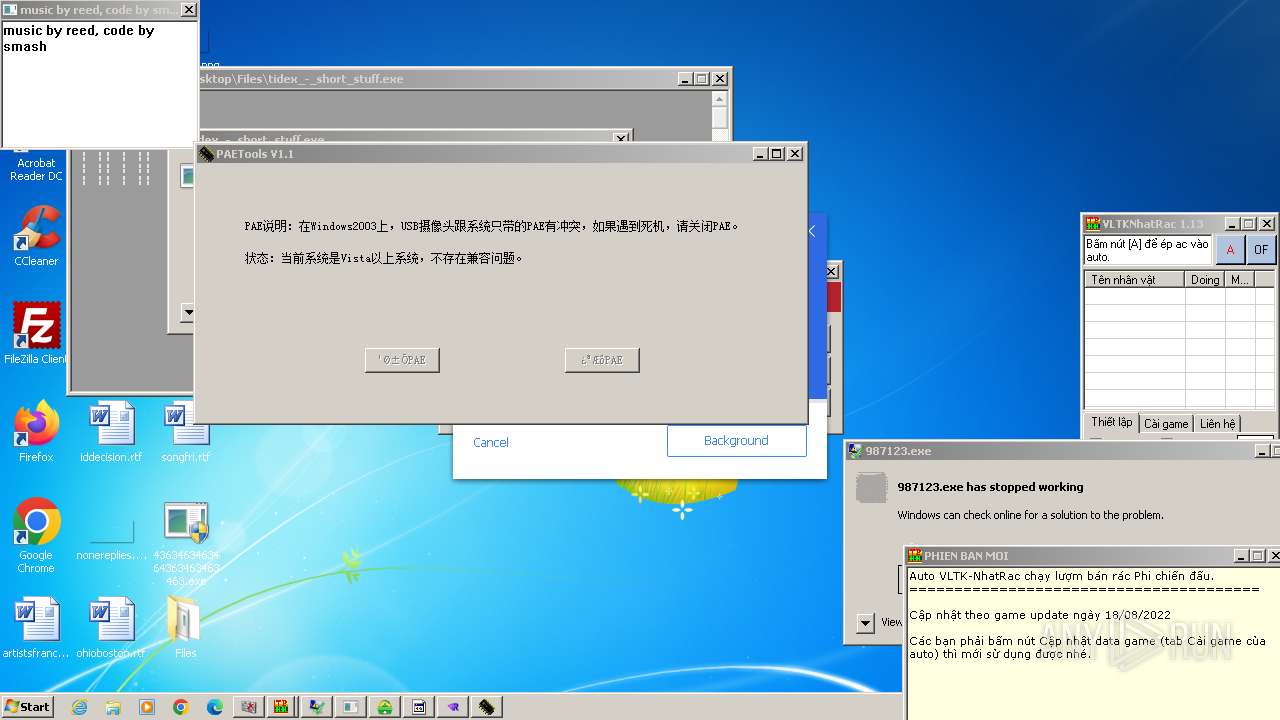
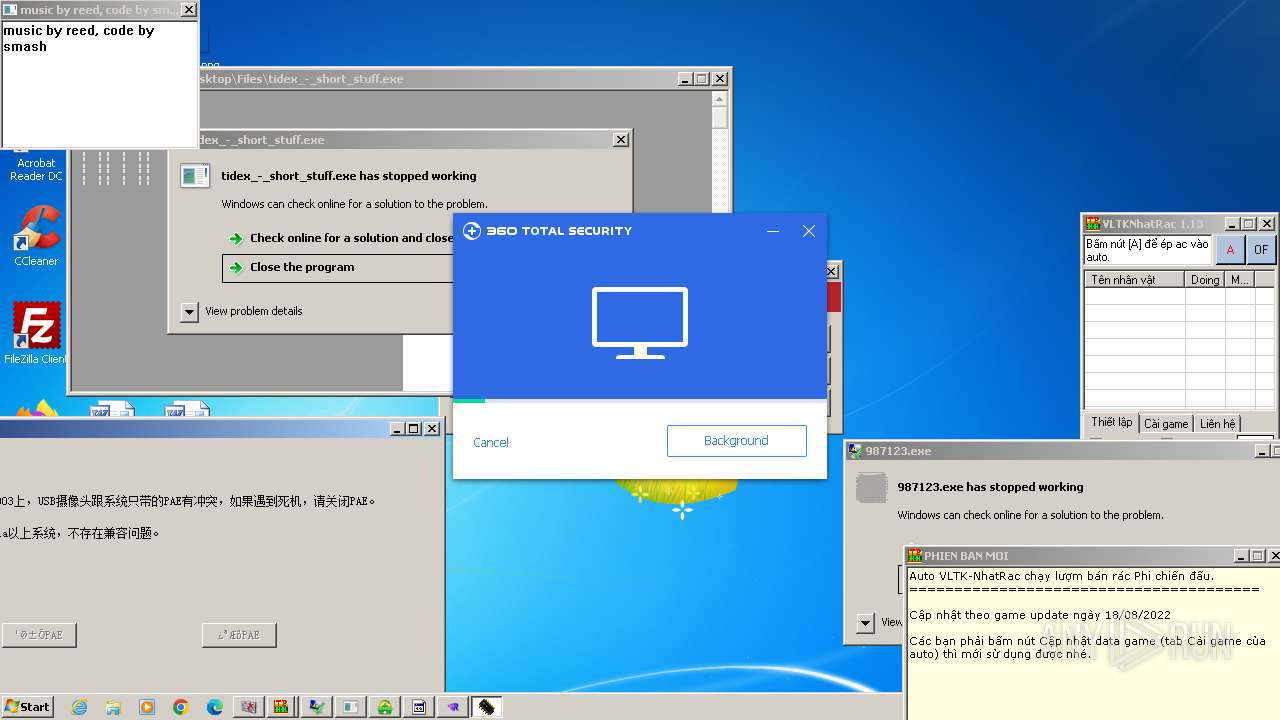
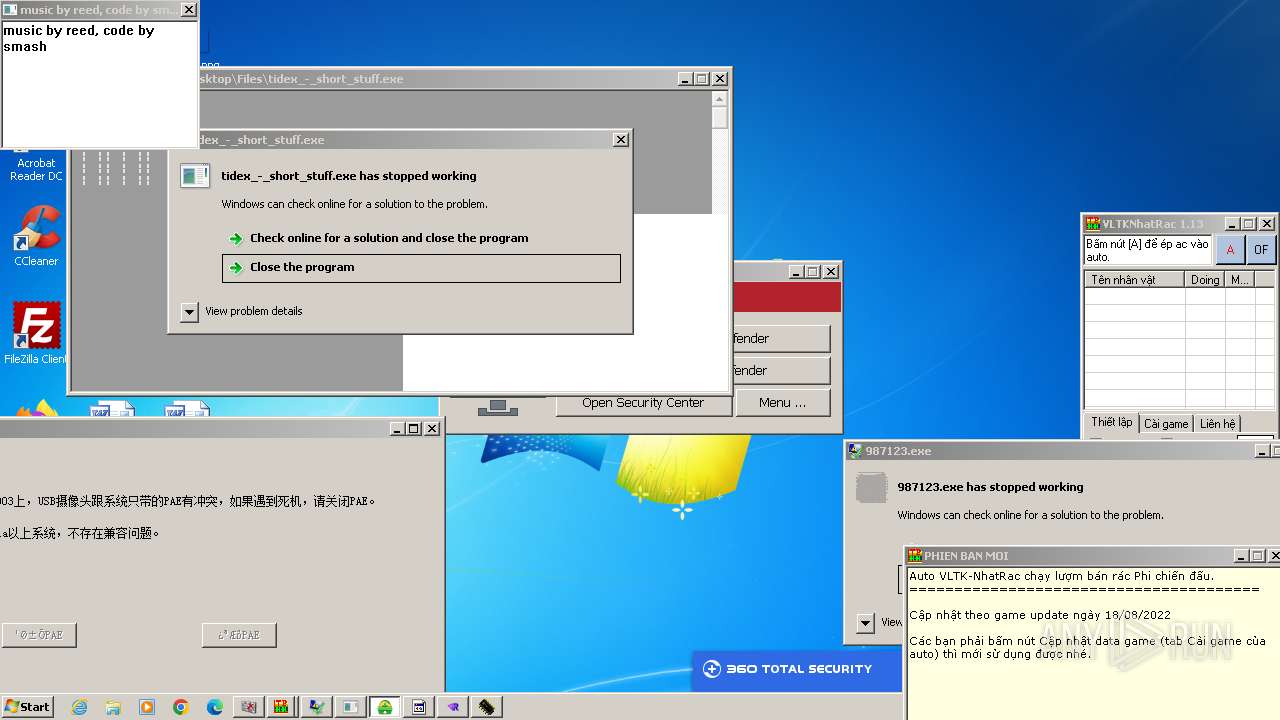
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/0af726b1-ebc7-43e3-91b9-6234d8d0aa86 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | December 29, 2023, 19:34:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
Bypass execution policy to execute commands
- powershell.exe (PID: 3260)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 1972)
- powershell.exe (PID: 4348)
- powershell.exe (PID: 4228)
Run PowerShell with an invisible window
- powershell.exe (PID: 3260)
Changes powershell execution policy (Bypass)
- socks5-clean.exe (PID: 1628)
- Archevod_XWorm.exe (PID: 3632)
Create files in the Startup directory
- rest.exe (PID: 2932)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 3056)
- Temp3.exe (PID: 4068)
- Windows Security Client.exe (PID: 3116)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2368)
- Archevod_XWorm.exe (PID: 3632)
Risepro uses scheduled tasks to run itself
- cmd.exe (PID: 3056)
- cmd.exe (PID: 2368)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 1408)
- rest.exe (PID: 2932)
Creates a writable file in the system directory
- Temp3.exe (PID: 4068)
Creates or modifies Windows services
- DefenderControl.exe (PID: 2988)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 1408)
- dialer.exe (PID: 3652)
- rest.exe (PID: 2932)
Adds path to the Windows Defender exclusion list
- Archevod_XWorm.exe (PID: 3632)
Adds process to the Windows Defender exclusion list
- Archevod_XWorm.exe (PID: 3632)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2544)
- 4363463463464363463463463.exe (PID: 2532)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- rest.exe (PID: 2932)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
- ghjkl.exe (PID: 2804)
- socks5-clean.exe (PID: 1628)
- DNS2.exe (PID: 2772)
- plink.exe (PID: 3656)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- VLTKNhatRac.exe (PID: 3312)
- powershell.exe (PID: 2436)
- 2k.exe (PID: 1816)
- rest.exe (PID: 2932)
- sysplorsv.exe (PID: 4044)
- DefenderControl.exe (PID: 2988)
- Temp3.exe (PID: 4068)
- Archevod_XWorm.exe (PID: 3632)
- Windows Security Client.exe (PID: 3116)
- powershell.exe (PID: 1972)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 4228)
- powershell.exe (PID: 4348)
- MSASCui.exe (PID: 240)
The process creates files with name similar to system file names
- PluginFlash.exe (PID: 584)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 2532)
The process executes VB scripts
- PluginFlash.exe (PID: 584)
- iexplore.exe (PID: 1236)
Reads the Windows owner or organization settings
- tuc2.tmp (PID: 796)
The process executes Powershell scripts
- socks5-clean.exe (PID: 1628)
Starts POWERSHELL.EXE for commands execution
- socks5-clean.exe (PID: 1628)
- Archevod_XWorm.exe (PID: 3632)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 3652)
Checks Windows Trust Settings
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
Reads security settings of Internet Explorer
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
Starts CMD.EXE for commands execution
- rest.exe (PID: 2932)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2436)
Searches for installed software
- RegAsm.exe (PID: 1408)
- dialer.exe (PID: 3652)
- rest.exe (PID: 2932)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 3652)
Reads browser cookies
- dialer.exe (PID: 3652)
- RegAsm.exe (PID: 1408)
Accesses Microsoft Outlook profiles
- dialer.exe (PID: 3652)
- rest.exe (PID: 2932)
Reads the BIOS version
- Update_new.exe (PID: 1812)
Script adds exclusion path to Windows Defender
- Archevod_XWorm.exe (PID: 3632)
Script adds exclusion process to Windows Defender
- Archevod_XWorm.exe (PID: 3632)
INFO
Reads the computer name
- 4363463463464363463463463.exe (PID: 2064)
- PluginFlash.exe (PID: 584)
- vbc.exe (PID: 1836)
- tuc2.tmp (PID: 796)
- 4363463463464363463463463.exe (PID: 984)
- ghjkl.exe (PID: 2804)
- XViewAXControl.exe (PID: 2644)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
- BLduscfibj.exe (PID: 3016)
- BLduscfibj.exe (PID: 3208)
- DefenderControl.exe (PID: 2988)
- socks5-clean.exe (PID: 1628)
- DNS2.exe (PID: 2772)
- VLTKNhatRac.exe (PID: 3312)
- plink.exe (PID: 3656)
- tidex_-_short_stuff.exe (PID: 1976)
- Ulpktkx.exe (PID: 2628)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- rest.exe (PID: 2932)
- hv.exe (PID: 1044)
- flt_shovemydiscoupyourarse.exe (PID: 3020)
- RegAsm.exe (PID: 1408)
- autorun.exe (PID: 2664)
- 2k.exe (PID: 1816)
- sysplorsv.exe (PID: 4044)
- NBYS%20AH.NET.exe (PID: 4080)
- Update_new.exe (PID: 1812)
- Archevod_XWorm.exe (PID: 3632)
- Temp3.exe (PID: 4068)
- MSASCui.exe (PID: 240)
- Windows Security Client.exe (PID: 3116)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2064)
- PluginFlash.exe (PID: 584)
- vbc.exe (PID: 1836)
- vbc.exe (PID: 1560)
- tuc2.exe (PID: 632)
- tuc2.tmp (PID: 796)
- XViewAXControl.exe (PID: 2644)
- XViewAXControl.exe (PID: 2576)
- 4363463463464363463463463.exe (PID: 984)
- ghjkl.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
- BLduscfibj.exe (PID: 3016)
- ghjkl.exe (PID: 1028)
- BLduscfibj.exe (PID: 3208)
- DefenderControl.exe (PID: 2988)
- socks5-clean.exe (PID: 1628)
- plink.exe (PID: 3656)
- DNS2.exe (PID: 2772)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 3328)
- VLTKNhatRac.exe (PID: 3312)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 1168)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 3856)
- 987123.exe (PID: 3980)
- tidex_-_short_stuff.exe (PID: 1976)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 1748)
- Ulpktkx.exe (PID: 2628)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- hv.exe (PID: 1044)
- newtpp.exe (PID: 2432)
- rest.exe (PID: 2932)
- flt_shovemydiscoupyourarse.exe (PID: 3020)
- autorun.exe (PID: 2664)
- sysplorsv.exe (PID: 4044)
- rise.exe (PID: 1592)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 844)
- VoidRAT.exe (PID: 3760)
- RegAsm.exe (PID: 1408)
- 2k.exe (PID: 4068)
- 2k.exe (PID: 1816)
- PAETools.exe (PID: 3452)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 1624)
- cs_maltest.exe (PID: 2952)
- 75d8077636ee1ec7b44f33cfdc65dc4a5b96d4c0b9ac3df0879b97e2bae1f9dd.exe (PID: 2728)
- Update_new.exe (PID: 1812)
- Archevod_XWorm.exe (PID: 3632)
- Temp3.exe (PID: 4068)
- NBYS%20AH.NET.exe (PID: 4080)
- Windows Security Client.exe (PID: 3116)
- MSASCui.exe (PID: 240)
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 2064)
- PluginFlash.exe (PID: 584)
- tuc2.exe (PID: 632)
- XViewAXControl.exe (PID: 2644)
- tuc2.tmp (PID: 796)
- ghjkl.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 1192)
- BLduscfibj.exe (PID: 3208)
- DNS2.exe (PID: 2772)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- 4363463463464363463463463.exe (PID: 2544)
- rest.exe (PID: 2932)
- newtpp.exe (PID: 2432)
- Temp3.exe (PID: 4068)
- Archevod_XWorm.exe (PID: 3632)
- dialer.exe (PID: 3652)
- tuc6.exe (PID: 4944)
- tuc6.tmp (PID: 4968)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2064)
- PluginFlash.exe (PID: 584)
- 4363463463464363463463463.exe (PID: 984)
- ghjkl.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- BLduscfibj.exe (PID: 3016)
- BLduscfibj.exe (PID: 3208)
- 4363463463464363463463463.exe (PID: 2544)
- DNS2.exe (PID: 2772)
- VLTKNhatRac.exe (PID: 3312)
- plink.exe (PID: 3656)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- rest.exe (PID: 2932)
- RegAsm.exe (PID: 1408)
- 2k.exe (PID: 1816)
- sysplorsv.exe (PID: 4044)
- NBYS%20AH.NET.exe (PID: 4080)
- Update_new.exe (PID: 1812)
- Archevod_XWorm.exe (PID: 3632)
- Windows Security Client.exe (PID: 3116)
- Temp3.exe (PID: 4068)
- MSASCui.exe (PID: 240)
Creates files or folders in the user directory
- PluginFlash.exe (PID: 584)
- DNS2.exe (PID: 2772)
- BLduscfibj.exe (PID: 3208)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- rest.exe (PID: 2932)
- Archevod_XWorm.exe (PID: 3632)
- Windows Security Client.exe (PID: 3116)
Reads Environment values
- 4363463463464363463463463.exe (PID: 2064)
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
- VLTKNhatRac.exe (PID: 3312)
- rest.exe (PID: 2932)
- RegAsm.exe (PID: 1408)
- Temp3.exe (PID: 4068)
- Windows Security Client.exe (PID: 3116)
Create files in a temporary directory
- vbc.exe (PID: 1836)
- tuc2.exe (PID: 632)
- tuc2.tmp (PID: 796)
- ghjkl.exe (PID: 2804)
- DefenderControl.exe (PID: 2988)
- socks5-clean.exe (PID: 1628)
- 4363463463464363463463463.exe (PID: 1192)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- rest.exe (PID: 2932)
- MSASCui.exe (PID: 240)
Drops 7-zip archiver for unpacking
- tuc2.tmp (PID: 796)
- tuc6.tmp (PID: 4968)
Process drops legitimate windows executable
- tuc2.tmp (PID: 796)
- 4363463463464363463463463.exe (PID: 2532)
- Archevod_XWorm.exe (PID: 3632)
- tuc6.tmp (PID: 4968)
Creates files in the program directory
- tuc2.tmp (PID: 796)
- XViewAXControl.exe (PID: 2644)
- DNS2.exe (PID: 2772)
- rest.exe (PID: 2932)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 2908)
- 4363463463464363463463463.exe (PID: 1388)
- 4363463463464363463463463.exe (PID: 2672)
- 4363463463464363463463463.exe (PID: 1192)
- 4363463463464363463463463.exe (PID: 2532)
- 4363463463464363463463463.exe (PID: 2544)
- 4363463463464363463463463.exe (PID: 2896)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 984)
- 4363463463464363463463463.exe (PID: 2064)
- DNS2.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2544)
- 4363463463464363463463463.exe (PID: 1192)
Application launched itself
- ghjkl.exe (PID: 2804)
- BLduscfibj.exe (PID: 3016)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 3328)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 3856)
- 2k.exe (PID: 4068)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 844)
- DV7HCk[$A%.exe (PID: 4536)
- StringIds.exe (PID: 4996)
Reads mouse settings
- DefenderControl.exe (PID: 2988)
Checks proxy server information
- DNS2.exe (PID: 2772)
- plink.exe (PID: 3656)
- 360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe (PID: 864)
- 2k.exe (PID: 1816)
- sysplorsv.exe (PID: 4044)
Connects to unusual port
- powershell.exe (PID: 3260)
- 4363463463464363463463463.exe (PID: 984)
- DNS2.exe (PID: 2772)
- 4363463463464363463463463.exe (PID: 2532)
- VLTKNhatRac.exe (PID: 3312)
- plink.exe (PID: 3656)
- Ulpktkx.exe (PID: 2628)
- rest.exe (PID: 2932)
- rise.exe (PID: 1592)
- RegAsm.exe (PID: 1408)
- Update_new.exe (PID: 1812)
- Windows Security Client.exe (PID: 3116)
The Powershell connects to the Internet
- powershell.exe (PID: 3260)
Unusual connection from system programs
- powershell.exe (PID: 3260)
DUPZOM has been detected (SURICATA)
- DNS2.exe (PID: 2772)
SERVSTART has been detected (SURICATA)
- DNS2.exe (PID: 2772)
Starts itself from another location
- DNS2.exe (PID: 2772)
- newtpp.exe (PID: 2432)
- Temp3.exe (PID: 4068)
Reads CPU info
- Ulpktkx.exe (PID: 2628)
Bypass execution policy to execute commands
- powershell.exe (PID: 2436)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2544)
- 4363463463464363463463463.exe (PID: 1192)
- sysplorsv.exe (PID: 4044)
The process executes via Task Scheduler
- powershell.exe (PID: 2436)
- StringIds.exe (PID: 4996)
Run PowerShell with an invisible window
- powershell.exe (PID: 2436)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 3652)
RISEPRO has been detected (SURICATA)
- rest.exe (PID: 2932)
Connects to FTP
- VLTKNhatRac.exe (PID: 3312)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 1408)
Connects to the CnC server
- RegAsm.exe (PID: 1408)
- rest.exe (PID: 2932)
- sysplorsv.exe (PID: 4044)
Reads product name
- RegAsm.exe (PID: 1408)
Steals credentials
- rest.exe (PID: 2932)
Process checks are UAC notifies on
- Update_new.exe (PID: 1812)
Checks for external IP
- rest.exe (PID: 2932)
- Temp3.exe (PID: 4068)
- Windows Security Client.exe (PID: 3116)
PHORPIEX has been detected (SURICATA)
- sysplorsv.exe (PID: 4044)
Executed via WMI
- DV7HCk[$A%.exe (PID: 4536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 09:29:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
168
Monitored processes
82
Malicious processes
16
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Windows Defender\MSASCui.exe" | C:\Program Files\Windows Defender\MSASCui.exe | DefenderControl.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Defender User Interface Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Users\admin\Desktop\Files\PluginFlash.exe" | C:\Users\admin\Desktop\Files\PluginFlash.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Title Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 632 | "C:\Users\admin\Desktop\Files\tuc2.exe" | C:\Users\admin\Desktop\Files\tuc2.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Integrity Level: HIGH Description: XView ActiveX Control Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 796 | "C:\Users\admin\AppData\Local\Temp\is-2SCT5.tmp\tuc2.tmp" /SL5="$301BC,4176061,54272,C:\Users\admin\Desktop\Files\tuc2.exe" | C:\Users\admin\AppData\Local\Temp\is-2SCT5.tmp\tuc2.tmp | — | tuc2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 844 | "C:\Users\admin\Desktop\Files\e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe" | C:\Users\admin\Desktop\Files\e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 864 | "C:\Users\admin\Desktop\Files\360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe" | C:\Users\admin\Desktop\Files\360TS_Setup_Mini_WW.Marketator.CPI20230401_6.6.0.1054.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Online Installer Exit code: 0 Version: 6, 6, 0, 1054 Modules
| |||||||||||||||
| 984 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1028 | C:\Users\admin\Desktop\Files\ghjkl.exe | C:\Users\admin\Desktop\Files\ghjkl.exe | ghjkl.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\Desktop\Files\hv.exe" | C:\Users\admin\Desktop\Files\hv.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Description: for_the_best_streamers_with_optimization Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\Files\07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe" | C:\Users\admin\Desktop\Files\07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe | — | 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
51 636
Read events
51 054
Write events
561
Delete events
21
Modification events
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C0190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B1400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA953030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD0F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703082000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D69B561148F01C77C54578C10926DF5B856976AD |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000C5DFB849CA051355EE2DBA1AC33EB028090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000200000005229BA15B31B0C6F4CCA89C2985177974327D1B689A3B935A0BD975532AF22AB030000000100000014000000D69B561148F01C77C54578C10926DF5B856976AD1D000000010000001000000001728E1ECF7A9D86FB3CEC8948ABA9531400000001000000140000008FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC620000000100000020000000CBB522D7B7F127AD6A0113865BDF1CD4102E7D0759AF635A7CF4720DC963C53B0B000000010000003000000047006C006F00620061006C005300690067006E00200052006F006F00740020004300410020002D002000520033000000190000000100000010000000D0FD3C9C380D7B65E26B9A3FEDD39B8F530000000100000040000000303E301F06092B06010401A032010130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C02000000001000000630300003082035F30820247A003020102020B04000000000121585308A2300D06092A864886F70D01010B0500304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E301E170D3039303331383130303030305A170D3239303331383130303030305A304C3120301E060355040B1317476C6F62616C5369676E20526F6F74204341202D20523331133011060355040A130A476C6F62616C5369676E311330110603550403130A476C6F62616C5369676E30820122300D06092A864886F70D01010105000382010F003082010A0282010100CC2576907906782216F5C083B684CA289EFD057611C5AD8872FC460243C7B28A9D045F24CB2E4BE1608246E152AB0C8147706CDD64D1EBF52CA30F823D0C2BAE97D7B614861079BB3B1380778C08E149D26A622F1F5EFA9668DF892795389F06D73EC9CB26590D73DEB0C8E9260E8315C6EF5B8BD20460CA49A628F6693BF6CBC82891E59D8A615737AC7414DC74E03AEE722F2E9CFBD0BBBFF53D00E10633E8822BAE53A63A16738CDD410E203AC0B4A7A1E9B24F902E3260E957CBB904926868E538266075B29F77FF9114EFAE2049FCAD401548D1023161195EB897EFAD77B7649A7ABF5FC113EF9B62FB0D6CE0546916A903DA6EE983937176C6698582170203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E041604148FF04B7FA82E4524AE4D50FA639A8BDEE2DD1BBC300D06092A864886F70D01010B050003820101004B40DBC050AAFEC80CEFF796544549BB96000941ACB3138686280733CA6BE674B9BA002DAEA40AD3F5F1F10F8ABF73674A83C7447B78E0AF6E6C6F03298E333945C38EE4B9576CAAFC1296EC53C62DE4246CB99463FBDC536867563E83B8CF3521C3C968FECEDAC253AACC908AE9F05D468C95DD7A58281A2F1DDECD0037418FED446DD75328977EF367041E15D78A96B4D3DE4C27A44C1B737376F41799C21F7A0EE32D08AD0A1C2CFF3CAB550E0F917E36EBC35749BEE12E2D7C608BC3415113239DCEF7326B9401A899E72C331F3A3B25D28640CE3B2C8678C9612F14BAEEDB556FDF84EE05094DBD28D872CED36250651EEB92978331D9B3B5CA47583F5F | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2064) 4363463463464363463463463.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1236) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1236) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1236) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
211
Suspicious files
92
Text files
137
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1236 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\admin8 | text | |
MD5:F5183BED252C9701477E9F70A52D8C46 | SHA256:6A481A0B51BA759BF2664936C540C1108CB9397F4949B0C073A7EF4ADFF7CAE0 | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\Roaming\adminlog.dat | text | |
MD5:BF3DBA41023802CF6D3F8C5FD683A0C7 | SHA256:4A8E75390856BF822F492F7F605CA0C21F1905172F6D3EF610162533C140507D | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\admin7 | text | |
MD5:F5183BED252C9701477E9F70A52D8C46 | SHA256:6A481A0B51BA759BF2664936C540C1108CB9397F4949B0C073A7EF4ADFF7CAE0 | |||
| 2064 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\tuc2.exe | executable | |
MD5:603CC2628BB60BE8CEF76C8ABAA300B4 | SHA256:C2A03E755C9D6E2F1ED60FA16BF0F07471F9DA67A0D26C6426EF29E190A33E0C | |||
| 796 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-0D14I.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 796 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-0D14I.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 1836 | vbc.exe | C:\Users\admin\AppData\Local\Temp\admin2.txt | binary | |
MD5:349FAE7EFC5995953CA17F396FA94981 | SHA256:5AE1AF9379CE1FA1419AE126458E23698C902E69FD9C891F3ADF3B8123921756 | |||
| 796 | tuc2.tmp | C:\Users\admin\AppData\Local\Temp\is-0D14I.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 584 | PluginFlash.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:039A35282F6BDC426BB5DF5990D16DAA | SHA256:10214EC31EEFE2EABD38262E9A404F781949BD09FF3831FFD3A9D9F9C8A277EB | |||
| 632 | tuc2.exe | C:\Users\admin\AppData\Local\Temp\is-2SCT5.tmp\tuc2.tmp | executable | |
MD5:A7662827ECAEB4FC68334F6B8791B917 | SHA256:05F159722D6905719D2D6F340981A293F40AB8A0D2D4A282C948066809D4AF6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
112
DNS requests
72
Threats
205
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2544 | 4363463463464363463463463.exe | GET | 200 | 185.215.113.84:80 | http://185.215.113.84/newtpp.exe | unknown | executable | 80.0 Kb | unknown |
984 | 4363463463464363463463463.exe | GET | 200 | 77.91.124.172:3350 | http://77.91.124.172:3350/rise.exe | unknown | executable | 1.62 Mb | unknown |
2064 | 4363463463464363463463463.exe | GET | 200 | 212.27.63.115:80 | http://habbotips.free.fr/PluginFlash.exe | unknown | executable | 1.04 Mb | unknown |
2064 | 4363463463464363463463463.exe | GET | 200 | 172.67.168.30:80 | http://never.hitsturbo.com/order/tuc2.exe | unknown | executable | 4.22 Mb | unknown |
2064 | 4363463463464363463463463.exe | GET | 200 | 91.215.85.223:80 | http://partadino.ac.ug/ghjkl.exe | unknown | executable | 1.36 Mb | unknown |
2544 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.8:80 | http://185.172.128.8/hv.exe | unknown | executable | 5.88 Mb | unknown |
984 | 4363463463464363463463463.exe | GET | 200 | 103.255.237.239:80 | http://kimyen.net/upload/VLTKNhatRac.exe | unknown | executable | 1.19 Mb | unknown |
2532 | 4363463463464363463463463.exe | GET | 301 | 104.192.141.1:80 | http://bitbucket.org/pavelalekseev11/346346/downloads/socks5-clean.exe | unknown | — | — | unknown |
984 | 4363463463464363463463463.exe | GET | 200 | 5.133.65.53:80 | http://5.133.65.53/Oracle/$77_loader.exe | unknown | executable | 397 Kb | unknown |
2532 | 4363463463464363463463463.exe | GET | 200 | 164.155.231.101:16 | http://164.155.231.101:16/DNS2.exe | unknown | executable | 9.10 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2064 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2064 | 4363463463464363463463463.exe | 212.27.63.115:80 | habbotips.free.fr | Free SAS | FR | unknown |
2064 | 4363463463464363463463463.exe | 172.67.168.30:80 | never.hitsturbo.com | CLOUDFLARENET | US | unknown |
2064 | 4363463463464363463463463.exe | 91.215.85.223:80 | partadino.ac.ug | — | RU | unknown |
984 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
984 | 4363463463464363463463463.exe | 103.255.237.239:80 | kimyen.net | VNPT Corp | VN | unknown |
2064 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
habbotips.free.fr |
| unknown |
never.hitsturbo.com |
| malicious |
partadino.ac.ug |
| unknown |
teemy.no-ip.org |
| unknown |
kimyen.net |
| unknown |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
bitbucket.org |
| shared |
bbuseruploads.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2064 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2064 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2064 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2064 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2064 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2064 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2064 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2064 | 4363463463464363463463463.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2064 | 4363463463464363463463463.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 8 |
2064 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
21 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|