| File name: | 4363463463464363463463463.exe |
| Full analysis: | https://app.any.run/tasks/029dd45c-6a5c-4703-9792-fa20fd06e68d |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 29, 2024, 20:18:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
DCRAT has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3216)
Drops the executable file immediately after the start
- 4363463463464363463463463.exe (PID: 3216)
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- 99268908.exe (PID: 1948)
- test.exe (PID: 3880)
- natcontroler.exe (PID: 3792)
- natcontroler.exe (PID: 2316)
- pocketrar350sc.exe (PID: 3428)
- cp.exe (PID: 3904)
- adm_atu.exe (PID: 3140)
- AnyDesk.exe (PID: 2468)
- 070.exe (PID: 1832)
- is-QHASC.tmp (PID: 312)
- cmd.exe (PID: 2348)
- cddvdrunner2333.exe (PID: 3492)
- 1.exe (PID: 1412)
- yhdl.exe (PID: 1364)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
- crt.tmp (PID: 5372)
- crt.exe (PID: 5356)
- vkfreeaudiosaver32_64.exe (PID: 5604)
- jxszdjp.exe (PID: 7640)
- jxszdjpSrv.exe (PID: 7652)
- Powershell.exe (PID: 7252)
- deep.exe (PID: 8540)
- random.exe (PID: 8236)
- dbzclientUpdate.exe (PID: 8940)
- ade4f437.exe (PID: 6652)
- twztl.exe (PID: 8616)
XWORM has been detected (YARA)
- ii.exe (PID: 940)
- 1.exe (PID: 1412)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe (PID: 3216)
GCLEANER has been detected (SURICATA)
- ISetup4.exe (PID: 2740)
Amadey has been detected
- Amadey.exe (PID: 2384)
- Hkbsse.exe (PID: 2780)
AMADEY has been detected (SURICATA)
- Hkbsse.exe (PID: 2780)
- axplong.exe (PID: 8672)
Connects to the CnC server
- Hkbsse.exe (PID: 2780)
- redline123123.exe (PID: 1816)
- sysmablsvr.exe (PID: 3568)
- iexplore.exe (PID: 7676)
- axplong.exe (PID: 8672)
Changes the autorun value in the registry
- 99268908.exe (PID: 1948)
- natcontroler.exe (PID: 3792)
- clip.exe (PID: 2248)
- 1.exe (PID: 1412)
- twztl.exe (PID: 8616)
METASTEALER has been detected (SURICATA)
- redline123123.exe (PID: 1816)
Changes appearance of the Explorer extensions
- sysmablsvr.exe (PID: 3568)
- syslmgrsvc.exe (PID: 9072)
Changes the Windows auto-update feature
- sysmablsvr.exe (PID: 3568)
- syslmgrsvc.exe (PID: 9072)
Creates or modifies Windows services
- sysmablsvr.exe (PID: 3568)
- syslmgrsvc.exe (PID: 9072)
Changes Security Center notification settings
- sysmablsvr.exe (PID: 3568)
- syslmgrsvc.exe (PID: 9072)
Actions looks like stealing of personal data
- peinf.exe (PID: 2964)
- redline123123.exe (PID: 1816)
- RegSvcs.exe (PID: 3652)
REDLINE has been detected (SURICATA)
- redline123123.exe (PID: 1816)
Steals credentials from Web Browsers
- redline123123.exe (PID: 1816)
- RegSvcs.exe (PID: 3652)
- Rent.pif (PID: 3432)
AMADEY has been detected (YARA)
- Hkbsse.exe (PID: 2780)
Create files in the Startup directory
- dllhost.exe (PID: 740)
- 1.exe (PID: 1412)
- Powershell.exe (PID: 7252)
Starts NET.EXE for service management
- net.exe (PID: 3248)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 1228)
- net.exe (PID: 1652)
- net.exe (PID: 3072)
- cmd.exe (PID: 1280)
- net.exe (PID: 2024)
- cmd.exe (PID: 3324)
- net.exe (PID: 3236)
- cmd.exe (PID: 2884)
- net.exe (PID: 1816)
- cmd.exe (PID: 3048)
BLACKMOON has been detected (YARA)
- XFHD.exe (PID: 1164)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 3652)
AGENTTESLA has been detected (SURICATA)
- RegSvcs.exe (PID: 3652)
QUASAR has been detected (YARA)
- 02.exe (PID: 368)
Adds path to the Windows Defender exclusion list
- 1.exe (PID: 1412)
Changes powershell execution policy (Bypass)
- 1.exe (PID: 1412)
- msa.exe (PID: 7224)
Bypass execution policy to execute commands
- powershell.exe (PID: 3004)
- powershell.exe (PID: 1948)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 1808)
- Powershell.exe (PID: 7252)
Adds process to the Windows Defender exclusion list
- 1.exe (PID: 1412)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 3140)
- findstr.exe (PID: 2024)
Uses Task Scheduler to run other applications
- 1.exe (PID: 1412)
VIDAR has been detected (YARA)
- Rent.pif (PID: 3432)
Starts CMD.EXE for self-deleting
- Rent.pif (PID: 3432)
Signature: RAMNIT has been detected
- jxszdjpSrv.exe (PID: 7652)
- DesktopLayer.exe (PID: 7660)
- iexplore.exe (PID: 7676)
- jxszdjp.exe (PID: 7640)
Changes the login/logoff helper path in the registry
- iexplore.exe (PID: 7676)
RAMNIT has been detected (SURICATA)
- iexplore.exe (PID: 7676)
SUSPICIOUS
Reads the Internet Settings
- 4363463463464363463463463.exe (PID: 3216)
- DownSysSoft.exe (PID: 3328)
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- pei.exe (PID: 1228)
- Amadey.exe (PID: 2384)
- Hkbsse.exe (PID: 2780)
- test.exe (PID: 3880)
- sysmablsvr.exe (PID: 3568)
- powershell.exe (PID: 4092)
- Downty.exe (PID: 2924)
- Downaqzh.exe (PID: 2716)
- RegSvcs.exe (PID: 3652)
- pocketrar350sc.exe (PID: 3428)
- clip.exe (PID: 2248)
- vi.exe (PID: 2004)
- QQ.exe (PID: 3236)
- ama.exe (PID: 3240)
- AnyDesk.exe (PID: 2060)
- MSI.CentralServer.exe (PID: 3868)
- powershell.exe (PID: 3004)
- 1.exe (PID: 1412)
- powershell.exe (PID: 1948)
- 228.exe (PID: 548)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 2364)
- yhdl.exe (PID: 1364)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- cmd.exe (PID: 6740)
- deep.exe (PID: 8540)
- random.exe (PID: 8236)
- axplong.exe (PID: 8672)
Reads settings of System Certificates
- 4363463463464363463463463.exe (PID: 3216)
- Hkbsse.exe (PID: 2780)
- Downty.exe (PID: 2924)
- RegSvcs.exe (PID: 3652)
- vi.exe (PID: 2004)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- axplong.exe (PID: 8672)
Adds/modifies Windows certificates
- 4363463463464363463463463.exe (PID: 3216)
- Hkbsse.exe (PID: 2780)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe (PID: 3216)
- DownSysSoft.exe (PID: 3328)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- Downaqzh.exe (PID: 2716)
- AnyDesk.exe (PID: 2468)
- ade4f437.exe (PID: 6652)
Application launched itself
- ii.exe (PID: 1044)
- natcontroler.exe (PID: 3792)
- look.exe (PID: 3740)
- unmxr.exe (PID: 2796)
- fud.exe (PID: 2860)
- AnyDesk.exe (PID: 2260)
- nn.exe (PID: 2848)
- unmxr.exe (PID: 3528)
- cmd.exe (PID: 2348)
- msa.exe (PID: 7224)
- unmxr.exe (PID: 5680)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe (PID: 3216)
- ISetup4.exe (PID: 2740)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- 炎黄大陆.exe (PID: 4476)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe (PID: 3216)
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- 99268908.exe (PID: 1948)
- test.exe (PID: 3880)
- natcontroler.exe (PID: 3792)
- natcontroler.exe (PID: 2316)
- dllhost.exe (PID: 740)
- pocketrar350sc.exe (PID: 3428)
- cp.exe (PID: 3904)
- clip.exe (PID: 2248)
- adm_atu.exe (PID: 3140)
- AnyDesk.exe (PID: 2468)
- is-QHASC.tmp (PID: 312)
- 070.exe (PID: 1832)
- cmd.exe (PID: 2348)
- cddvdrunner2333.exe (PID: 3492)
- 1.exe (PID: 1412)
- yhdl.exe (PID: 1364)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
- crt.exe (PID: 5356)
- crt.tmp (PID: 5372)
- vkfreeaudiosaver32_64.exe (PID: 5604)
- Powershell.exe (PID: 7252)
- jxszdjp.exe (PID: 7640)
- jxszdjpSrv.exe (PID: 7652)
- deep.exe (PID: 8540)
- random.exe (PID: 8236)
- dbzclientUpdate.exe (PID: 8940)
- twztl.exe (PID: 8616)
Connects to the server without a host name
- 4363463463464363463463463.exe (PID: 3216)
- ISetup4.exe (PID: 2740)
- Hkbsse.exe (PID: 2780)
- sysmablsvr.exe (PID: 3568)
- axplong.exe (PID: 8672)
- ade4f437.exe (PID: 6652)
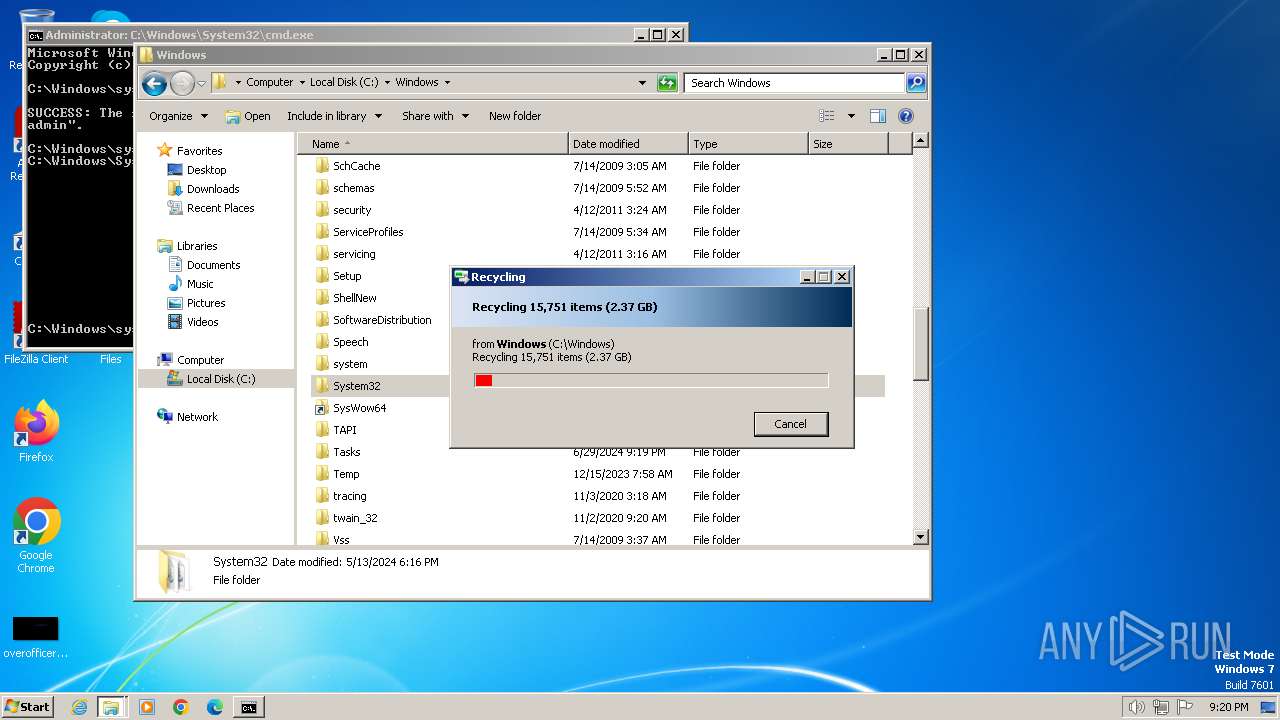
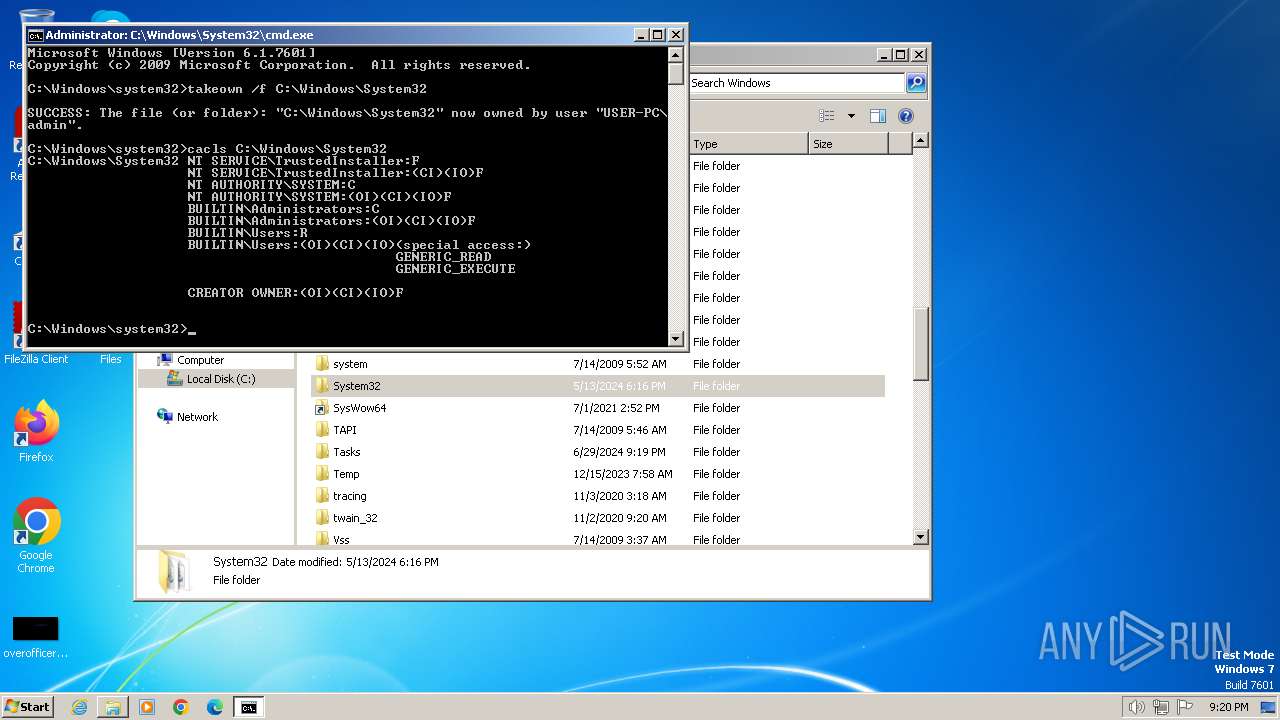
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3096)
- cmd.exe (PID: 3984)
Connects to unusual port
- ii.exe (PID: 940)
- 4363463463464363463463463.exe (PID: 3216)
- DownSysSoft.exe (PID: 3328)
- redline123123.exe (PID: 1816)
- MSBuild.exe (PID: 1748)
- Downaqzh.exe (PID: 2716)
- sysmablsvr.exe (PID: 3568)
- 02.exe (PID: 368)
- %E4%B8%AD%E9%A9%B0%E6%95%B0%E6%94%B9300.exe (PID: 3340)
- QQ.exe (PID: 3236)
- unmxr.exe (PID: 3412)
- 1.exe (PID: 1412)
- Rent.pif (PID: 3432)
- ade4f437.exe (PID: 6652)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3984)
Reads security settings of Internet Explorer
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- 4363463463464363463463463.exe (PID: 3216)
- DownSysSoft.exe (PID: 3328)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- test.exe (PID: 3880)
- sysmablsvr.exe (PID: 3568)
- Downty.exe (PID: 2924)
- Downaqzh.exe (PID: 2716)
- pocketrar350sc.exe (PID: 3428)
- vi.exe (PID: 2004)
- QQ.exe (PID: 3236)
- ama.exe (PID: 3240)
- MSI.CentralServer.exe (PID: 3868)
- 1.exe (PID: 1412)
- 228.exe (PID: 548)
- yhdl.exe (PID: 1364)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- deep.exe (PID: 8540)
- random.exe (PID: 8236)
- axplong.exe (PID: 8672)
Starts itself from another location
- Amadey.exe (PID: 2384)
- 99268908.exe (PID: 1948)
- clip.exe (PID: 2248)
- jxszdjpSrv.exe (PID: 7652)
- twztl.exe (PID: 8616)
- random.exe (PID: 8236)
Checks Windows Trust Settings
- Hkbsse.exe (PID: 2780)
- Downty.exe (PID: 2924)
- vi.exe (PID: 2004)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- axplong.exe (PID: 8672)
Contacting a server suspected of hosting an CnC
- Hkbsse.exe (PID: 2780)
- iexplore.exe (PID: 7676)
- axplong.exe (PID: 8672)
The process checks if it is being run in the virtual environment
- 4363463463464363463463463.exe (PID: 3216)
Creates or modifies Windows services
- sysmablsvr.exe (PID: 3568)
- syslmgrsvc.exe (PID: 9072)
Starts POWERSHELL.EXE for commands execution
- test.exe (PID: 3880)
- 1.exe (PID: 1412)
- msa.exe (PID: 7224)
BASE64 encoded PowerShell command has been detected
- test.exe (PID: 3880)
Base64-obfuscated command line is found
- test.exe (PID: 3880)
Searches for installed software
- redline123123.exe (PID: 1816)
- Rent.pif (PID: 3432)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3004)
- powershell.exe (PID: 1948)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 2364)
Reads browser cookies
- redline123123.exe (PID: 1816)
The process connected to a server suspected of theft
- redline123123.exe (PID: 1816)
- RegSvcs.exe (PID: 3652)
Starts CMD.EXE for commands execution
- XFHD.exe (PID: 1164)
- 228.exe (PID: 548)
- cmd.exe (PID: 2348)
- clear.exe (PID: 6976)
- Rent.pif (PID: 3432)
Starts SC.EXE for service management
- cmd.exe (PID: 972)
- cmd.exe (PID: 7044)
- cmd.exe (PID: 6992)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe (PID: 3216)
Uses RUNDLL32.EXE to load library
- XFHD.exe (PID: 1164)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 3652)
The process executes via Task Scheduler
- unmxr.exe (PID: 2796)
- unmxr.exe (PID: 3528)
- XClient.exe (PID: 5692)
- unmxr.exe (PID: 5680)
Checks for external IP
- RegSvcs.exe (PID: 3652)
Connects to SMTP port
- RegSvcs.exe (PID: 3652)
- unmxr.exe (PID: 3412)
Reads Microsoft Outlook installation path
- pocketrar350sc.exe (PID: 3428)
- 炎黄大陆.exe (PID: 4476)
Reads Internet Explorer settings
- pocketrar350sc.exe (PID: 3428)
- 炎黄大陆.exe (PID: 4476)
Creates file in the systems drive root
- cp.exe (PID: 3904)
- ama.exe (PID: 3240)
- MSI.CentralServer.exe (PID: 3868)
Creates a software uninstall entry
- uninstall.exe (PID: 3692)
- yhdl.exe (PID: 1364)
The process creates files with name similar to system file names
- clip.exe (PID: 2248)
- 4363463463464363463463463.exe (PID: 3216)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
Process drops legitimate windows executable
- clip.exe (PID: 2248)
- is-QHASC.tmp (PID: 312)
- crt.tmp (PID: 5372)
- 4363463463464363463463463.exe (PID: 3216)
Script adds exclusion path to Windows Defender
- 1.exe (PID: 1412)
Script adds exclusion process to Windows Defender
- 1.exe (PID: 1412)
Reads the Windows owner or organization settings
- is-QHASC.tmp (PID: 312)
- crt.tmp (PID: 5372)
Executing commands from ".cmd" file
- 228.exe (PID: 548)
Get information on the list of running processes
- cmd.exe (PID: 2348)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2348)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2348)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2348)
Suspicious file concatenation
- cmd.exe (PID: 3012)
The executable file from the user directory is run by the CMD process
- Rent.pif (PID: 3432)
Starts application with an unusual extension
- cmd.exe (PID: 2348)
Malware-specific behavior (creating "System.dll" in Temp)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
The process drops C-runtime libraries
- crt.tmp (PID: 5372)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6768)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Rent.pif (PID: 3432)
Reads the BIOS version
- random.exe (PID: 8236)
- axplong.exe (PID: 8672)
Drops 7-zip archiver for unpacking
- dbzclientUpdate.exe (PID: 8940)
INFO
Checks supported languages
- 4363463463464363463463463.exe (PID: 3216)
- ii.exe (PID: 940)
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- idrB5Event.exe (PID: 2316)
- DownSysSoft.exe (PID: 3328)
- ii.exe (PID: 1044)
- ISetup4.exe (PID: 2740)
- Windows.exe (PID: 2296)
- natcontroler.exe (PID: 3792)
- Downdd.exe (PID: 2812)
- pei.exe (PID: 1228)
- Amadey.exe (PID: 2384)
- peinf.exe (PID: 2964)
- Hkbsse.exe (PID: 2780)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3648)
- 1.exe (PID: 3644)
- newfile_setup.exe (PID: 2872)
- redline123123.exe (PID: 1816)
- 99268908.exe (PID: 1948)
- MSBuild.exe (PID: 1748)
- fileosn.exe (PID: 3432)
- sysmablsvr.exe (PID: 3568)
- MSBuild.exe (PID: 3308)
- test.exe (PID: 3880)
- Shortcutter.exe (PID: 3088)
- legs.exe (PID: 3844)
- 2630511039.exe (PID: 2320)
- 254948785.exe (PID: 2196)
- natcontroler.exe (PID: 2316)
- html.exe (PID: 2388)
- Downty.exe (PID: 2924)
- 996132205.exe (PID: 1648)
- XFHD.exe (PID: 1164)
- Downaqzh.exe (PID: 2716)
- look.exe (PID: 3740)
- gywervcyuj.exe (PID: 3128)
- RegSvcs.exe (PID: 3652)
- cp.exe (PID: 3904)
- look.exe (PID: 2844)
- DelHosts.exe (PID: 3164)
- unmxr.exe (PID: 2796)
- pocketrar350sc.exe (PID: 3428)
- 02.exe (PID: 368)
- ZinTask.exe (PID: 3492)
- crypted_c360a5b7.exe (PID: 4024)
- %E4%B8%AD%E9%A9%B0%E6%95%B0%E6%94%B9300.exe (PID: 3340)
- unmxr.exe (PID: 3412)
- fud.exe (PID: 2860)
- uninstall.exe (PID: 3692)
- AdvancedRun.exe (PID: 2916)
- fud.exe (PID: 3068)
- cayV0Deo9jSt417.exe (PID: 1136)
- taskhost.exe (PID: 3892)
- adm_atu.exe (PID: 3140)
- ama.exe (PID: 3240)
- vi.exe (PID: 2004)
- unmxr.exe (PID: 3528)
- QQ.exe (PID: 3236)
- AnyDesk.exe (PID: 2260)
- svchost.exe (PID: 1020)
- AnyDesk.exe (PID: 2468)
- MSI.CentralServer.exe (PID: 3868)
- AnyDesk.exe (PID: 2060)
- unmxr.exe (PID: 2784)
- 1.exe (PID: 1412)
- nn.exe (PID: 2848)
- nn.exe (PID: 3692)
- 070.exe (PID: 1832)
- 228.exe (PID: 548)
- is-QHASC.tmp (PID: 312)
- cddvdrunner2333.exe (PID: 3492)
- yhdl.exe (PID: 1364)
- cddvdrunner2333.exe (PID: 3828)
- Rent.pif (PID: 3432)
- 炎黄大陆.exe (PID: 4476)
- crt.exe (PID: 5356)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
- XClient.exe (PID: 5692)
- victor.exe (PID: 5420)
- vkfreeaudiosaver32_64.exe (PID: 5604)
- crt.tmp (PID: 5372)
- unmxr.exe (PID: 5680)
- vkfreeaudiosaver32_64.exe (PID: 5888)
- ade4f437.exe (PID: 6652)
- msa.exe (PID: 7224)
- DownChrome.exe (PID: 7164)
- clear.exe (PID: 6976)
- jxszdjpSrv.exe (PID: 7652)
- msa.exe (PID: 7448)
- DesktopLayer.exe (PID: 7660)
- unmxr.exe (PID: 7460)
- jxszdjp.exe (PID: 7640)
- deep.exe (PID: 8540)
- twztl.exe (PID: 8616)
- da_protected.exe (PID: 8596)
- random.exe (PID: 8236)
- dbzclientUpdate.exe (PID: 8940)
- qt51crk.exe (PID: 9024)
- axplong.exe (PID: 8672)
- syslmgrsvc.exe (PID: 9072)
Reads the computer name
- ii.exe (PID: 1044)
- 4363463463464363463463463.exe (PID: 3216)
- ii.exe (PID: 940)
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3648)
- ISetup4.exe (PID: 2740)
- DownSysSoft.exe (PID: 3328)
- Windows.exe (PID: 2296)
- natcontroler.exe (PID: 3792)
- Downdd.exe (PID: 2812)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- newfile_setup.exe (PID: 2872)
- redline123123.exe (PID: 1816)
- MSBuild.exe (PID: 1748)
- fileosn.exe (PID: 3432)
- test.exe (PID: 3880)
- Shortcutter.exe (PID: 3088)
- sysmablsvr.exe (PID: 3568)
- natcontroler.exe (PID: 2316)
- Downty.exe (PID: 2924)
- html.exe (PID: 2388)
- Downaqzh.exe (PID: 2716)
- look.exe (PID: 3740)
- look.exe (PID: 2844)
- RegSvcs.exe (PID: 3652)
- unmxr.exe (PID: 2796)
- DelHosts.exe (PID: 3164)
- XFHD.exe (PID: 1164)
- pocketrar350sc.exe (PID: 3428)
- 02.exe (PID: 368)
- cp.exe (PID: 3904)
- AdvancedRun.exe (PID: 2916)
- fud.exe (PID: 2860)
- fud.exe (PID: 3068)
- cayV0Deo9jSt417.exe (PID: 1136)
- uninstall.exe (PID: 3692)
- vi.exe (PID: 2004)
- svchost.exe (PID: 1020)
- unmxr.exe (PID: 3528)
- QQ.exe (PID: 3236)
- AnyDesk.exe (PID: 2060)
- AnyDesk.exe (PID: 2468)
- ama.exe (PID: 3240)
- AnyDesk.exe (PID: 2260)
- MSI.CentralServer.exe (PID: 3868)
- nn.exe (PID: 2848)
- nn.exe (PID: 3692)
- unmxr.exe (PID: 3412)
- 1.exe (PID: 1412)
- is-QHASC.tmp (PID: 312)
- 228.exe (PID: 548)
- yhdl.exe (PID: 1364)
- cddvdrunner2333.exe (PID: 3492)
- Rent.pif (PID: 3432)
- 炎黄大陆.exe (PID: 4476)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
- XClient.exe (PID: 5692)
- unmxr.exe (PID: 5680)
- crt.tmp (PID: 5372)
- vkfreeaudiosaver32_64.exe (PID: 5604)
- ade4f437.exe (PID: 6652)
- clear.exe (PID: 6976)
- msa.exe (PID: 7224)
- msa.exe (PID: 7448)
- random.exe (PID: 8236)
- deep.exe (PID: 8540)
- axplong.exe (PID: 8672)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe (PID: 3216)
- ii.exe (PID: 940)
- ii.exe (PID: 1044)
- 288c47bbc1871b439df19ff4df68f076.exe (PID: 3648)
- DownSysSoft.exe (PID: 3328)
- natcontroler.exe (PID: 3792)
- Windows.exe (PID: 2296)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- newfile_setup.exe (PID: 2872)
- redline123123.exe (PID: 1816)
- MSBuild.exe (PID: 1748)
- fileosn.exe (PID: 3432)
- Shortcutter.exe (PID: 3088)
- sysmablsvr.exe (PID: 3568)
- Downty.exe (PID: 2924)
- html.exe (PID: 2388)
- Downaqzh.exe (PID: 2716)
- RegSvcs.exe (PID: 3652)
- look.exe (PID: 3740)
- look.exe (PID: 2844)
- unmxr.exe (PID: 2796)
- pocketrar350sc.exe (PID: 3428)
- 02.exe (PID: 368)
- fud.exe (PID: 2860)
- cayV0Deo9jSt417.exe (PID: 1136)
- fud.exe (PID: 3068)
- uninstall.exe (PID: 3692)
- vi.exe (PID: 2004)
- unmxr.exe (PID: 3528)
- QQ.exe (PID: 3236)
- AnyDesk.exe (PID: 2468)
- AnyDesk.exe (PID: 2260)
- MSI.CentralServer.exe (PID: 3868)
- nn.exe (PID: 2848)
- 1.exe (PID: 1412)
- nn.exe (PID: 3692)
- yhdl.exe (PID: 1364)
- 炎黄大陆.exe (PID: 4476)
- XClient.exe (PID: 5692)
- Rent.pif (PID: 3432)
- unmxr.exe (PID: 5680)
- msa.exe (PID: 7224)
- msa.exe (PID: 7448)
- random.exe (PID: 8236)
- axplong.exe (PID: 8672)
Disables trace logs
- 4363463463464363463463463.exe (PID: 3216)
- RegSvcs.exe (PID: 3652)
Reads the software policy settings
- 4363463463464363463463463.exe (PID: 3216)
- Hkbsse.exe (PID: 2780)
- Downty.exe (PID: 2924)
- RegSvcs.exe (PID: 3652)
- vi.exe (PID: 2004)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- axplong.exe (PID: 8672)
Reads Environment values
- 4363463463464363463463463.exe (PID: 3216)
- Windows.exe (PID: 2296)
- redline123123.exe (PID: 1816)
- RegSvcs.exe (PID: 3652)
- 02.exe (PID: 368)
- vi.exe (PID: 2004)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
Manual execution by a user
- cmd.exe (PID: 3096)
- cmd.exe (PID: 3984)
- explorer.exe (PID: 744)
Reads mouse settings
- DownSysSoft.exe (PID: 3328)
- Downdd.exe (PID: 2812)
- Downty.exe (PID: 2924)
- Downaqzh.exe (PID: 2716)
- gywervcyuj.exe (PID: 3128)
- DelHosts.exe (PID: 3164)
- Rent.pif (PID: 3432)
- clear.exe (PID: 6976)
- DownChrome.exe (PID: 7164)
- dbzclientUpdate.exe (PID: 8940)
Create files in a temporary directory
- 288c47bbc1871b439df19ff4df68f00076.exe (PID: 3552)
- DownSysSoft.exe (PID: 3328)
- Amadey.exe (PID: 2384)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- sysmablsvr.exe (PID: 3568)
- Downaqzh.exe (PID: 2716)
- gywervcyuj.exe (PID: 3128)
- pocketrar350sc.exe (PID: 3428)
- cp.exe (PID: 3904)
- adm_atu.exe (PID: 3140)
- is-QHASC.tmp (PID: 312)
- 070.exe (PID: 1832)
- crt.exe (PID: 5356)
- maza-0.16.3-win32-setup-unsigned.exe (PID: 4948)
- crt.tmp (PID: 5372)
- 1.exe (PID: 1412)
- deep.exe (PID: 8540)
- random.exe (PID: 8236)
- dbzclientUpdate.exe (PID: 8940)
- axplong.exe (PID: 8672)
Checks proxy server information
- DownSysSoft.exe (PID: 3328)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- sysmablsvr.exe (PID: 3568)
- Downty.exe (PID: 2924)
- Downaqzh.exe (PID: 2716)
- pocketrar350sc.exe (PID: 3428)
- vi.exe (PID: 2004)
- QQ.exe (PID: 3236)
- MSI.CentralServer.exe (PID: 3868)
- yhdl.exe (PID: 1364)
- 炎黄大陆.exe (PID: 4476)
- Rent.pif (PID: 3432)
- axplong.exe (PID: 8672)
Creates files or folders in the user directory
- DownSysSoft.exe (PID: 3328)
- pei.exe (PID: 1228)
- Hkbsse.exe (PID: 2780)
- test.exe (PID: 3880)
- sysmablsvr.exe (PID: 3568)
- natcontroler.exe (PID: 3792)
- dllhost.exe (PID: 740)
- Downaqzh.exe (PID: 2716)
- Downty.exe (PID: 2924)
- clip.exe (PID: 2248)
- vi.exe (PID: 2004)
- AnyDesk.exe (PID: 2260)
- is-QHASC.tmp (PID: 312)
- 228.exe (PID: 548)
- 1.exe (PID: 1412)
- yhdl.exe (PID: 1364)
- 炎黄大陆.exe (PID: 4476)
- crt.tmp (PID: 5372)
- Rent.pif (PID: 3432)
- axplong.exe (PID: 8672)
Reads product name
- redline123123.exe (PID: 1816)
- vi.exe (PID: 2004)
- Rent.pif (PID: 3432)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 3004)
- powershell.exe (PID: 1948)
- powershell.exe (PID: 2364)
- powershell.exe (PID: 1808)
.NET Reactor protector has been detected
- natcontroler.exe (PID: 3792)
- MSBuild.exe (PID: 1748)
- unmxr.exe (PID: 3528)
- unmxr.exe (PID: 5680)
Creates files in the program directory
- natcontroler.exe (PID: 2316)
- pocketrar350sc.exe (PID: 3428)
- uninstall.exe (PID: 3692)
- cddvdrunner2333.exe (PID: 3492)
- yhdl.exe (PID: 1364)
- Rent.pif (PID: 3432)
- vkfreeaudiosaver32_64.exe (PID: 5604)
- iexplore.exe (PID: 7676)
- jxszdjpSrv.exe (PID: 7652)
Drops the executable file immediately after the start
- dllhost.exe (PID: 740)
- clip.exe (PID: 2248)
UPX packer has been detected
- XFHD.exe (PID: 1164)
- pocketrar350sc.exe (PID: 3428)
- jxszdjp.exe (PID: 7640)
NirSoft software is detected
- AdvancedRun.exe (PID: 2916)
Reads security settings of Internet Explorer
- clip.exe (PID: 2248)
Reads CPU info
- AnyDesk.exe (PID: 2260)
- Rent.pif (PID: 3432)
Process checks computer location settings
- AnyDesk.exe (PID: 2060)
- AnyDesk.exe (PID: 2468)
Creates a software uninstall entry
- is-QHASC.tmp (PID: 312)
- crt.tmp (PID: 5372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(940) ii.exe
C264.226.123.178:6098
Keys
AESh4cker
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
Mutex1z0ENxCLSR3XRSre
(PID) Process(1412) 1.exe
C264.23.249.117:6098
Keys
AEShacker
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexqBm7HSWbfhJrOf6O
Amadey
(PID) Process(2780) Hkbsse.exe
C2185.172.128.116
URLhttp://185.172.128.116/Mb3GvQs8/index.php
Version4.30
Options
Drop directoryb66a8ae076
Drop nameHkbsse.exe
Strings (113)2019
un:
.jpg
Content-Type: application/x-www-form-urlencoded
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
vs:
4.30
Avira
&unit=
=
-executionpolicy remotesigned -File "
<c>
:::
Hkbsse.exe
rundll32
" && timeout 1 && del
POST
dm:
ESET
2022
Comodo
"taskkill /f /im "
st=s
-%lu
Bitdefender
2016
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
&& Exit"
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
d1
Powershell.exe
ComputerName
sd:
" && ren
<d>
r=
\App
ProgramData\
https://
WinDefender
#
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
id:
pc:
/k
Content-Type: multipart/form-data; boundary=----
VideoID
wb
rb
lv:
Startup
------
\0000
AVAST Software
GetNativeSystemInfo
rundll32.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
cmd /C RMDIR /s/q
Main
ProductName
\
SOFTWARE\Microsoft\Windows NT\CurrentVersion
av:
+++
-unicode-
&&
e0
cmd
bi:
DefaultSettings.XResolution
AVG
os:
--
Norton
S-%lu-
?scr=1
Content-Disposition: form-data; name="data"; filename="
"
kernel32.dll
GET
DefaultSettings.YResolution
SYSTEM\ControlSet001\Services\BasicDisplay\Video
185.172.128.116
|
ps1
/Plugins/
dll
og:
b66a8ae076
Sophos
%-lu
Programs
/Mb3GvQs8/index.php
abcdefghijklmnopqrstuvwxyz0123456789-_
random
------
Panda Security
0123456789
cred.dll|clip.dll|
Rem
CurrentBuild
http://
Kaspersky Lab
ar:
%USERPROFILE%
shell32.dll
360TotalSecurity
Doctor Web
e1
AgentTesla
(PID) Process(3652) RegSvcs.exe
Protocolsmtp
Hostmail.adlinesgh.com
Port587
Usernameinfo@adlinesgh.com
PasswordGhana@1235
Quasar
(PID) Process(368) 02.exe
Version1.4.1
C2 (2)10.109.9.184:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex1916cb83-b99a-4ecb-a054-4e009de2edc6
StartupQuasar Client Startup
TagOffice04
LogDirLogs
SignatureS5kJMt5nU47unDWiBFqQ/F6Ory6eEJ4Rj+OOQP4pMTVxCE6AbGdNuFoOr7UKUF60TKaD5CujSj9xo4PESxKvKuhEGZ2PwOUhJIRy+GJI5zJv/5mYOE65uNkRI/e6IcqhdHDvKfB5yQuu06vbiO4miwjKQyYKPj4vZt3pE64bDNrJAVT19DtFAqvXFdU/eh00ay9zvkq5QL/a/jVyJM0MdoG3CA/XBh9J06DBDbRYmCFrxVD0jgsXwm+Mmn8f4j4jD8TUwBGAQjjQB23mvFLeVoFztDTxNMvwdBbFLh78wIdp...
CertificateMIIE9DCCAtygAwIBAgIQALduapGI+R7nMhHl0zdMDzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDQxNzA2NTQyMVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmGvFCw9Z1qCePNsxG9bTQvltXwYQ7aIrJkHQQs/aJrOMeGtUiO5A72zDw9e/+O2DTHtTUlaT...
Vidar
(PID) Process(3432) Rent.pif
C2https://t.me/k0mono
URLhttps://steamcommunity.com/profiles/76561199686524322
RC42910114286690104117195131148
Strings (316)GetProcAddress
LoadLibraryA
lstrcatA
OpenEventA
CreateEventA
CloseHandle
Sleep
GetUserDefaultLangID
VirtualAllocExNuma
VirtualFree
GetSystemInfo
VirtualAlloc
HeapAlloc
GetComputerNameA
lstrcpyA
GetProcessHeap
GetCurrentProcess
lstrlenA
ExitProcess
GlobalMemoryStatusEx
GetSystemTime
SystemTimeoFileTime
advapi32.dll
gdi32.dll
user32.dll
crypt32.dll
ntdll.dll
GetUserNameA
CreateDCA
GetDeviceCaps
ReleaseDC
CryptStringToBinaryA
sscanf
NtQueryInformationProcess
VMwareVMware
HAL9TH
JohnDoe
DISPLAY
%hu/%hu/%hu
GetEnvironmentVaribleA
GetFileAttributesA
GlobalLock
HeapFree
GetFileSize
GlobalSize
CreateToolhelp32Snpshot
IsWow64Process
Process32Next
GetLocalTime
FreeLibrary
GetTimeZoneInformation
GetSystemPowerStatus
GetVolumeInformationA
GetWindowsDirectoryA
Process32First
GetLocaleInfoA
GetUserDefaultLocaleName
GetModuleFileNameA
DeleteFileA
FindNextFileA
LocalFree
FindClose
SetEnvironmentVaribleA
LocalAlloc
GetFileSizeEx
ReadFile
SetFilePointer
WriteFile
CreateFileA
FindFirstFileA
CopyFileA
VirtualProtect
GetLogicalProcessorInformaionEx
GetLastError
lstrcpynA
MultiByteToWideChar
GlobalFree
WideCharToMultiByte
GlobalAlloc
OpenProcess
TerminateProcess
GetCurrentProcessId
gdiplus.dll
ole32.dll
bcrypt.dll
wininet.dll
shlwapi.dll
shell32.dll
psapi.dll
rstrtmgr.dll
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
CreateCompatibleDC
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
GetHGlobalFromStrem
CreateStreamOnHGlobal
CoUninitialize
CoInitialize
CoCreateInstance
BCryptGenerateSymmetricKey
BCryptCloseAlgorithmProvider
BCryptDecrypt
BCryptSetProperty
BCryptDestroyKey
BCryptOpenAlgorithmProvider
GetWindowRect
GetDesktopWindow
GetDC
CloseWindow
wsprintfA
EnumDisplayDevicesA
GetKeyboardLayoutList
CharToOemW
wsprintfW
RegQueryValueExA
RegEnumKeyExA
RegOpenKeyExA
RegCloseKey
RegEnumValueA
CryptBinaryToStringA
CryptUnprotectData
SHGetFolderPathA
ShellExecuteExA
InternetOpenUrlA
InternetConnectA
InternetCloseHandle
InternetOpenA
HttpSendRequestA
HttpOpenRequestA
InternetReadFile
InternetCrackUrA
StrCmpCA
StrStrA
StrCmpCW
PathMatchSpecA
GetModuleFileNameExA
RmStartSession
RmRegisterResources
RmGetList
RmEndSession
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
PATH
C:\\ProgramData\\nss3.dll
NSS_Init
NSS_Shutdown
PK11_GetInternaKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
C:\\ProgramData\\
SELECT origin_url, username_value, password_value FROM logins
Soft:
profile:
Host:
Login:
Password:
Opera
OperaGX
Network
Cookies
.txt
TRUE
SELECT HOS_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
FALSE
Autofill
SELECT name, vaue FROM auofill
History
SELECT url FROM urls LIMIT 1000
CC
Name:
SELECT name_on_card, expiration_month, expirtion_year, card_number_encrypted FROM credit_cards
Month:
Year:
Card:
Cookies
Login Data
Web Data
History
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT host, isHttpOnly, path, isSecur, expiry, name, value FROM moz_cookies
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places LIMIT 1000
cookies.sqlite
formhistory.sqlite
places.sqlite
Plugins
Local Extension Settings
Sync Extension Settings
IndexedDB
Opera Stable
Opera GX Stable
CURRENT
chrome-extension_
_0.indexeddb.leveldb
Local State
profiles.ini
chrome
opera
firefox
Wallets
%08lX%04lX%lu
SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion
ProductName
x32
x64
%d/%d/%d %d:%d:%d
DisplayName
HARDWARE\\DESCRIPTION\\Sysem\\CentralProcessor\\0
ProcessorNameString
SOFTWARE\\Microsoft\\Windows\\CurrentVrsion\\Uninstall
DisplayVersion
freebl3.dll
mozglue.dll
msvcp140.dll
nss3.dll
softokn3.dll
vcruntime140.dl
\\Temp\\
.exe
runas
open
/c start
%DESKTOP%
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DOCUMENTS%
%PROGRAMFILES%
%PROGRAMFILES_86%
%RECENT%
*.lnk
Files
\\discord\\
\\Local Storage\\leveldb\\CURRENT
\\Local Storage\\leveldb
\\Telegram Desktop\\
key_datas
D877F783D5D3EF8C*
map*
A7FDF864FBC10B77*
A92DAA6EA6F891F2*
F8806DD0C461824F*
Telegram
Tox
*.tox
*.ini
Password
\\Outlook\\accounts.txt
Software\\Microsoft\\Windows NT\\CurrentVersion\\Windows Messaging Subsystem\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676\\
Pidgin
Software\\Microsoft\\Office\\13.\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676\\
Software\\Microsoft\\Office\\14.\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676\\
Software\\Microsoft\\Office\15.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676\\
\\.purple\\
Software\\Microsoft\\Office\16.0\\Outlook\\Profiles\\Outlook\\9375CFF0413111d3B88A00104B2A6676\\
accounts.xml
Software\\Microsoft\\Windows Messaging Subsystem\\Profiles\\9375CFF0413111d3B88A00104B2A6676\\
00000001
00000002
00000003
00000004
dQw4w9WgXcQ
token:
Software\\Valve\\Steam
SteamPath
\\config\\
ssfn*
config.vdf
DialogConfig.vdf
DialogConfigOverlay*.vdf
libraryfolders.vdf
loginusers.vdf
\\Steam\\
sqlite3.dll
browsers
done
Soft
\\Discord\\tokens.txt
/c timeout /t 5 & del /f /q "
" & del "C:\\ProgrmData\\*.dll"" & xit
C:\\Windows\\system32\\cmd.exe
https
Content-Type: multipart/form-data; boundary=----
POST
HTTP/1.1
Content-Disposition: form-data; name="
hwid
build
token
file_name
file
message
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
screenshot.jpg
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
274
Monitored processes
156
Malicious processes
45
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | C:\Windows\system32\net1 start "Desktop Window Manager Session Manager" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 312 | "C:\Users\admin\AppData\Local\Temp\is-PDAAP.tmp\is-QHASC.tmp" /SL4 $6025E "C:\Users\admin\Desktop\Files\070.exe" 3710753 52224 | C:\Users\admin\AppData\Local\Temp\is-PDAAP.tmp\is-QHASC.tmp | 070.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.43.0.0 Modules
| |||||||||||||||
| 368 | "C:\Users\admin\Desktop\Files\02.exe" | C:\Users\admin\Desktop\Files\02.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Version: 1.4.1 Modules
Quasar(PID) Process(368) 02.exe Version1.4.1 C2 (2)10.109.9.184:4782 Sub_DirSubDir Install_NameClient.exe Mutex1916cb83-b99a-4ecb-a054-4e009de2edc6 StartupQuasar Client Startup TagOffice04 LogDirLogs SignatureS5kJMt5nU47unDWiBFqQ/F6Ory6eEJ4Rj+OOQP4pMTVxCE6AbGdNuFoOr7UKUF60TKaD5CujSj9xo4PESxKvKuhEGZ2PwOUhJIRy+GJI5zJv/5mYOE65uNkRI/e6IcqhdHDvKfB5yQuu06vbiO4miwjKQyYKPj4vZt3pE64bDNrJAVT19DtFAqvXFdU/eh00ay9zvkq5QL/a/jVyJM0MdoG3CA/XBh9J06DBDbRYmCFrxVD0jgsXwm+Mmn8f4j4jD8TUwBGAQjjQB23mvFLeVoFztDTxNMvwdBbFLh78wIdp... CertificateMIIE9DCCAtygAwIBAgIQALduapGI+R7nMhHl0zdMDzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDQxNzA2NTQyMVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmGvFCw9Z1qCePNsxG9bTQvltXwYQ7aIrJkHQQs/aJrOMeGtUiO5A72zDw9e/+O2DTHtTUlaT... | |||||||||||||||
| 548 | "C:\Users\admin\Desktop\Files\228.exe" | C:\Users\admin\Desktop\Files\228.exe | — | 4363463463464363463463463.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 740 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 744 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | C:\Windows\system32\net1 stop "Desktop Window Manager Session Manager" | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 940 | "C:\Users\admin\Desktop\Files\ii.exe" | C:\Users\admin\Desktop\Files\ii.exe | ii.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: FotFin Version: 1.0.0.0 Modules
XWorm(PID) Process(940) ii.exe C264.226.123.178:6098 Keys AESh4cker Options Splitter<Xwormmm> Sleep time3 USB drop nameXWorm V5.6 Mutex1z0ENxCLSR3XRSre | |||||||||||||||
| 972 | cmd /c sc config "UxSms" start= demand | C:\Windows\System32\cmd.exe | — | XFHD.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\Files\svchost.exe" | C:\Users\admin\Desktop\Files\svchost.exe | 4363463463464363463463463.exe | ||||||||||||
User: admin Company: Intel Integrity Level: HIGH Description: Intel® Driver & Support Assistant Exit code: 3221225477 Version: 23.4.39.9 Modules
| |||||||||||||||
Total events
120 864
Read events
119 897
Write events
786
Delete events
181
Modification events
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3216) 4363463463464363463463463.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
140
Suspicious files
126
Text files
72
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3552 | 288c47bbc1871b439df19ff4df68f00076.exe | C:\Users\admin\AppData\Local\Temp\ISetup4.exe | executable | |
MD5:44F814BE76122897EF325F8938F8E4CF | SHA256:2899D533753918409AB910B70BA92F8740F76C8E8AC74F4C890E53B258E3BFF6 | |||
| 3328 | DownSysSoft.exe | C:\Users\admin\AppData\Local\Temp\List | text | |
MD5:FC23051837F44A36F5E703A468766DBE | SHA256:CCE751048E0D0C230C84F9D95537F34E568D68F80358EC747C5F024EE9926627 | |||
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Windows.exe | executable | |
MD5:9AF0B7CA55FE8970D0259163C88B92AE | SHA256:060E9A06574030B5328A957074E1BB39B3B7FC0744930A377FAA03A793D1BE98 | |||
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\peinf.exe | executable | |
MD5:AE8041A8904075D07B24A4FBD358B172 | SHA256:E035A6E7ACC559553C782539B20BC32FC767C385319902D963A395AE7A9C3934 | |||
| 1228 | pei.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\newtpp[1].exe | executable | |
MD5:4505DAF4C08FC8E8E1380911E98588AA | SHA256:A2139600C569365149894405D411EA1401BAFC8C7E8AF1983D046CF087269C40 | |||
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\Amadey.exe | executable | |
MD5:07101CAC5B9477BA636CD8CA7B9932CB | SHA256:488385CD54D14790B03FA7C7DC997EBEA3F7B2A8499E5927EB437A3791102A77 | |||
| 2384 | Amadey.exe | C:\Windows\Tasks\Hkbsse.job | binary | |
MD5:C0B5C7C088D220E148E428FB3CC3B09D | SHA256:EB7EC082737EE3BFE1B480BE724C00666F570FF25FD94109D01E6E3E53DCE431 | |||
| 2780 | Hkbsse.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:C6F91F68CEBFE8ECF6C2272983486BAB | SHA256:021A748DD0C1B8983BC0059E8D3E2DAA611D89DAE99026E363A25F56C6EBCB65 | |||
| 3552 | 288c47bbc1871b439df19ff4df68f00076.exe | C:\Users\admin\AppData\Local\Temp\288c47bbc1871b439df19ff4df68f076.exe | executable | |
MD5:43B4B9050E5B237DE2D1412DE8781F36 | SHA256:97BB5C78C753AA5E39FFC3D4C1058F584D0241E9B19AFF20A248F1F159FDCA6D | |||
| 3216 | 4363463463464363463463463.exe | C:\Users\admin\Desktop\Files\%E7%9B%AE%E5%BD%95%E8%A1%A8%E6%A0%BC%E5%90%8D%E5%8D%956001.exe | executable | |
MD5:E34E2A710F0A16B80E71A62177960AC7 | SHA256:5C7732875644CD8E7F9DD11101BA19B5732AE2DA57E72A88F79D07F8814A457B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
166
TCP/UDP connections
1 748
DNS requests
888
Threats
853
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 2.16.164.67:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/servoces64.exe | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.113:80 | http://185.172.128.113/ma.exe | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | — | 91.215.85.223:80 | http://lastimaners.ug/ghjk.exe | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 185.172.128.20:80 | http://185.172.128.20/288c47bbc1871b439df19ff4df68f00076.exe | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/zardsystemschange.exe | unknown | — | — | unknown |
3216 | 4363463463464363463463463.exe | GET | 200 | 152.199.23.214:80 | http://update.itopvpn.com/dl/idr/v3/Pub/idrB5Event.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | 4363463463464363463463463.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3216 | 4363463463464363463463463.exe | 77.91.77.80:80 | — | Foton Telecom CJSC | RU | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | 4363463463464363463463463.exe | 43.153.49.49:8888 | — | Tencent Building, Kejizhongyi Avenue | US | unknown |
1372 | svchost.exe | 2.16.164.67:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
lastimaners.ug |
| unknown |
www.akwwmw.com |
| unknown |
update.itopvpn.com |
| unknown |
github.com |
| shared |
wieie.cn |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3216 | 4363463463464363463463463.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3216 | 4363463463464363463463463.exe | Misc activity | ET INFO Packed Executable Download |
3216 | 4363463463464363463463463.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
30 ETPRO signatures available at the full report
Process | Message |
|---|---|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The request was aborted: Could not create SSL/TLS secure channel.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe | The specified executable is not a valid application for this OS platform.
|