| File name: | Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.7z |
| Full analysis: | https://app.any.run/tasks/330d27a5-86cb-4a4a-969e-86e4f6ef213f |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | March 08, 2025, 15:06:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 49B469A7067F6EAC45D7CC141D331891 |
| SHA1: | E1BFBE9222CCD829C390358EB0D23AA6BB877982 |
| SHA256: | 2F7F2CF6AD1F35CBF76A2E061E4F62458C3A5B7D727ABE216EF9C1031377F9E6 |
| SSDEEP: | 98304:VikntQlJGiM4JYyrSMxURPYzIClXIfyjWUPOPQgDk+VcK0q0rK+12P7KjXAP+4uA:dIam4gjPmN/IfOJ/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2384)
Create files in the Startup directory
- dllhost.exe (PID: 728)
Changes the autorun value in the registry
- dllhost.exe (PID: 728)
XMRIG has been detected (YARA)
- dllhost.exe (PID: 728)
SUSPICIOUS
The process creates files with name similar to system file names
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
Reads security settings of Internet Explorer
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
- ShellExperienceHost.exe (PID: 6744)
Executable content was dropped or overwritten
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
- dllhost.exe (PID: 728)
Executes application which crashes
- VAPE V4.exe (PID: 4892)
ANYDESK has been found
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
There is functionality for taking screenshot (YARA)
- dllhost.exe (PID: 728)
Process drops legitimate windows executable
- dllhost.exe (PID: 728)
Connects to unusual port
- AppLaunch.exe (PID: 1096)
There is functionality for VM detection VirtualBox (YARA)
- dllhost.exe (PID: 728)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4756)
- BackgroundTransferHost.exe (PID: 2268)
- BackgroundTransferHost.exe (PID: 5408)
- BackgroundTransferHost.exe (PID: 896)
- BackgroundTransferHost.exe (PID: 6080)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 5408)
- slui.exe (PID: 2108)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 5408)
- dllhost.exe (PID: 728)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2384)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 5408)
Reads the computer name
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
- AppLaunch.exe (PID: 1096)
- ShellExperienceHost.exe (PID: 6744)
- dllhost.exe (PID: 728)
Manual execution by a user
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
Create files in a temporary directory
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
The sample compiled with english language support
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
Checks supported languages
- dllhost.exe (PID: 728)
- AppLaunch.exe (PID: 1096)
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
- VAPE V4.exe (PID: 4892)
- ShellExperienceHost.exe (PID: 6744)
Process checks computer location settings
- Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe (PID: 4180)
Enigma protector has been detected
- dllhost.exe (PID: 728)
Compiled with Borland Delphi (YARA)
- dllhost.exe (PID: 728)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 1096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:10:26 12:03:42+00:00 |
| ArchivedFileName: | Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe |
Total processes
154
Monitored processes
15
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\AppData\Local\Temp\dllhost.exe" | C:\Users\admin\AppData\Local\Temp\dllhost.exe | Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: svchost Exit code: 4294967295 Version: 1.3.1.3 Modules
| |||||||||||||||
| 896 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4892 -s 248 | C:\Windows\SysWOW64\WerFault.exe | — | VAPE V4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | VAPE V4.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2108 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
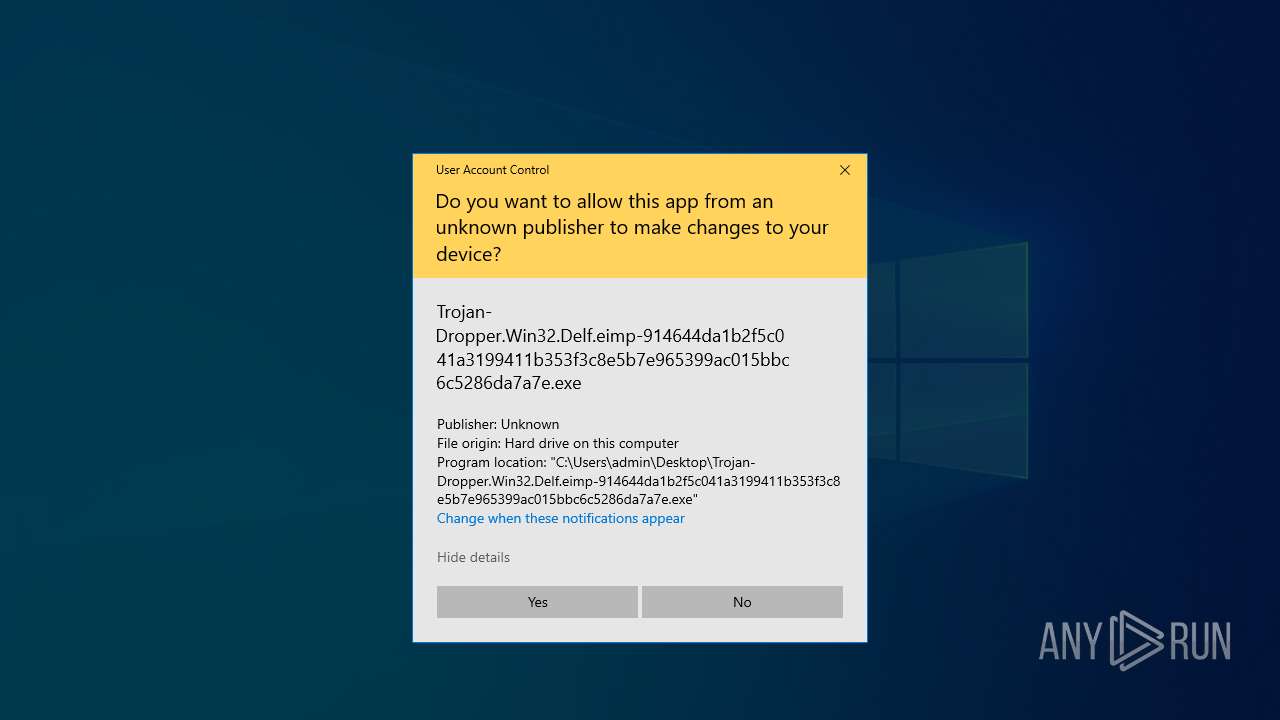
| 4180 | "C:\Users\admin\Desktop\Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe" | C:\Users\admin\Desktop\Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4488 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 560
Read events
8 497
Write events
60
Delete events
3
Modification events
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.7z | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (896) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
4
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5408 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\6b40dff1-6351-4b8e-b2ea-640d350d064d.down_data | — | |
MD5:— | SHA256:— | |||
| 1040 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_VAPE V4.exe_b3fe25516fcdbaa7f08bb39763b3861cfa672ef0_dc33386c_478678e5-11be-4f11-a96e-2bc83c9d4715\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4180 | Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe | C:\Users\admin\AppData\Local\Temp\dllhost.exe | executable | |
MD5:D3B312DC4459EDAE7159835BCD374B9F | SHA256:4B515944CFB60F4FA648B09CD4F2556C3D77C381189F5E85FD6B6D9E20A974FD | |||
| 5408 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\6b40dff1-6351-4b8e-b2ea-640d350d064d.7459cec3-bb0e-4dd8-a656-e555be773570.down_meta | binary | |
MD5:FCF2ECB9FF7EE21C5244527E323C64D0 | SHA256:43DADB96C96257A07FFECC63C6168E525A45B6EC31215F0CCA169EAFBE066926 | |||
| 5408 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:AD7A7F2CD8F6B61032EE00693F5E9D43 | SHA256:A4E66657A4625D0CF6407A5655E107A3DC9020F083CF764B184526C09442854F | |||
| 4180 | Trojan-Dropper.Win32.Delf.eimp-914644da1b2f5c041a3199411b353f3c8e5b7e965399ac015bbc6c5286da7a7e.exe | C:\Users\admin\AppData\Local\Temp\VAPE V4.exe | executable | |
MD5:EDA712F5CCA6547E36D2937B9D89FAD0 | SHA256:860EABC945B4A99255E1BDBCFCC19A6EBF605612D809678ECD329E6F17C4F961 | |||
| 1040 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERB67.tmp.dmp | binary | |
MD5:7ADF45410869B2056572FE4AEA15A3A9 | SHA256:36A40A7AE43CE9C2C544E9EC9FF4CCCC9BEF4E7271C5ACA37CECCAB5B2DAF810 | |||
| 1040 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1079.tmp.WERInternalMetadata.xml | binary | |
MD5:648CDC2825C93E4269D638BBD0730121 | SHA256:86C8BED364B0083AD36684B2F85A77184DE225D430893E3F48AE3378BA4A8DFE | |||
| 5408 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\638f7c67-a5b6-46ce-9bdc-6485765ddbbd.7459cec3-bb0e-4dd8-a656-e555be773570.down_meta | binary | |
MD5:FCF2ECB9FF7EE21C5244527E323C64D0 | SHA256:43DADB96C96257A07FFECC63C6168E525A45B6EC31215F0CCA169EAFBE066926 | |||
| 5408 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:8CC6D943FA8704F155856AC0E47960B3 | SHA256:26AFEC748851244ECD9B8ACE832962FDB08CD4B9D3E6C666E1F5525768164081 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
32
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1244 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5408 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1244 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1244 | backgroundTaskHost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |