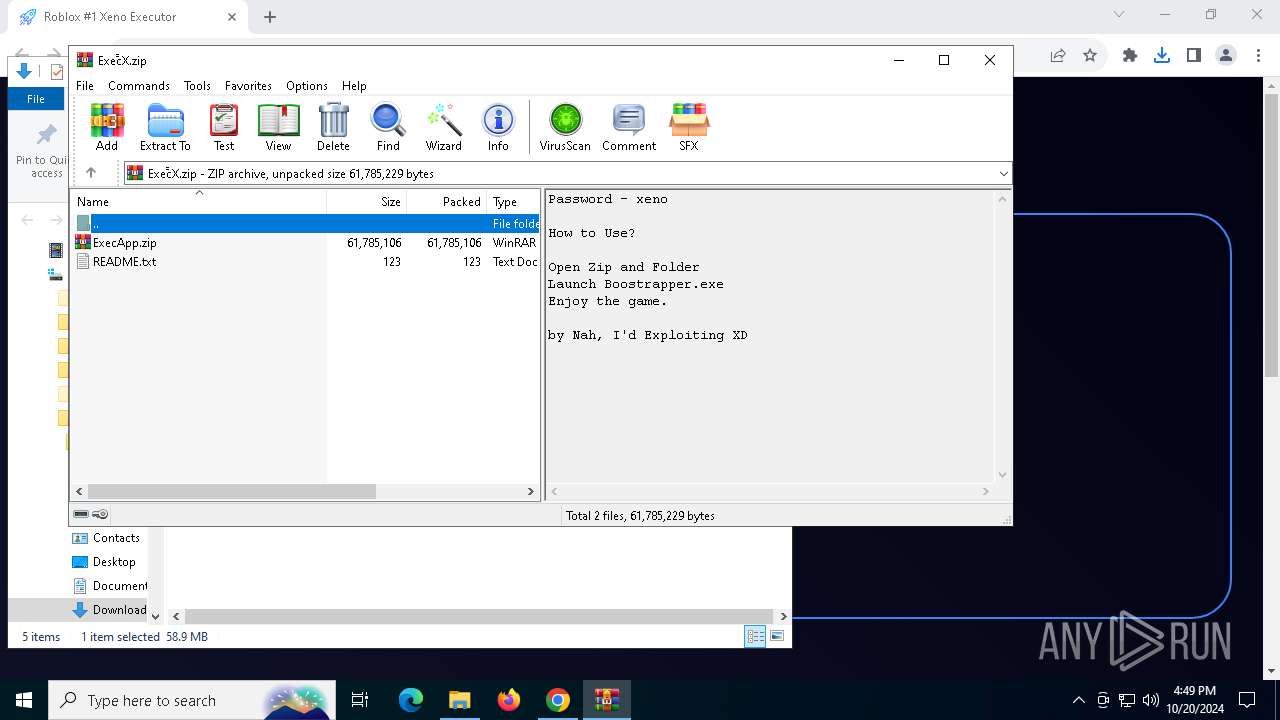
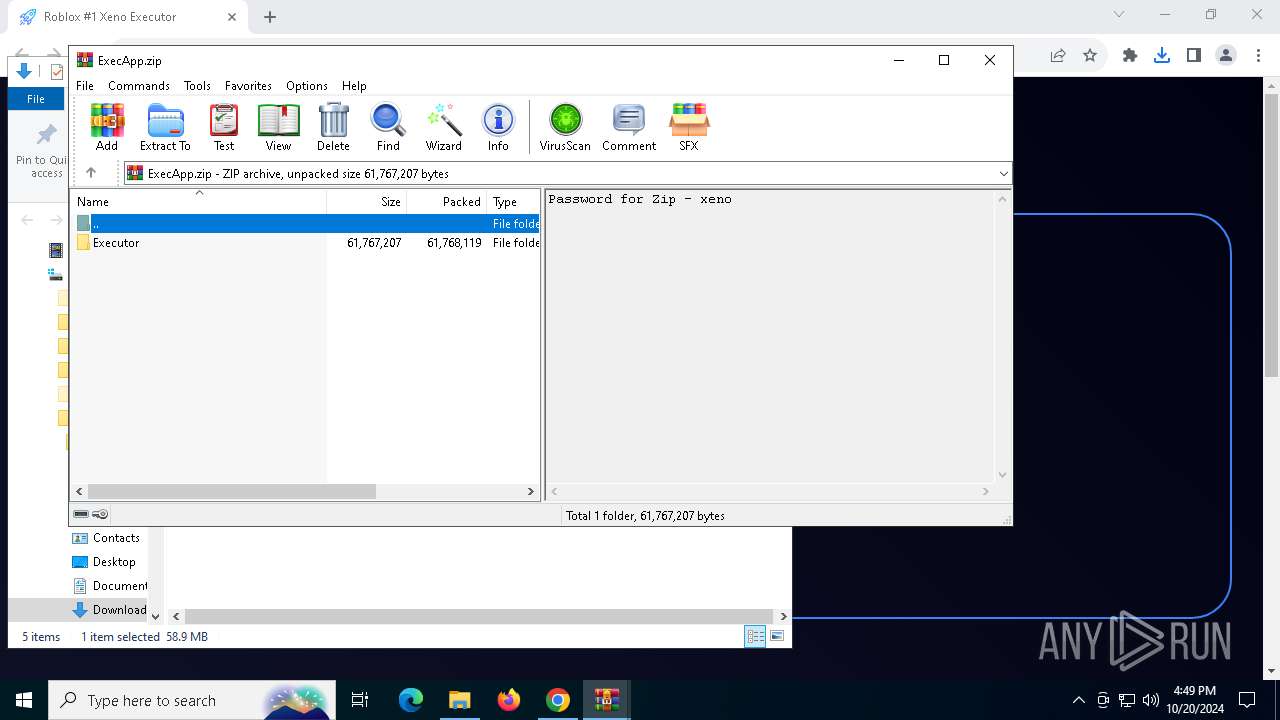
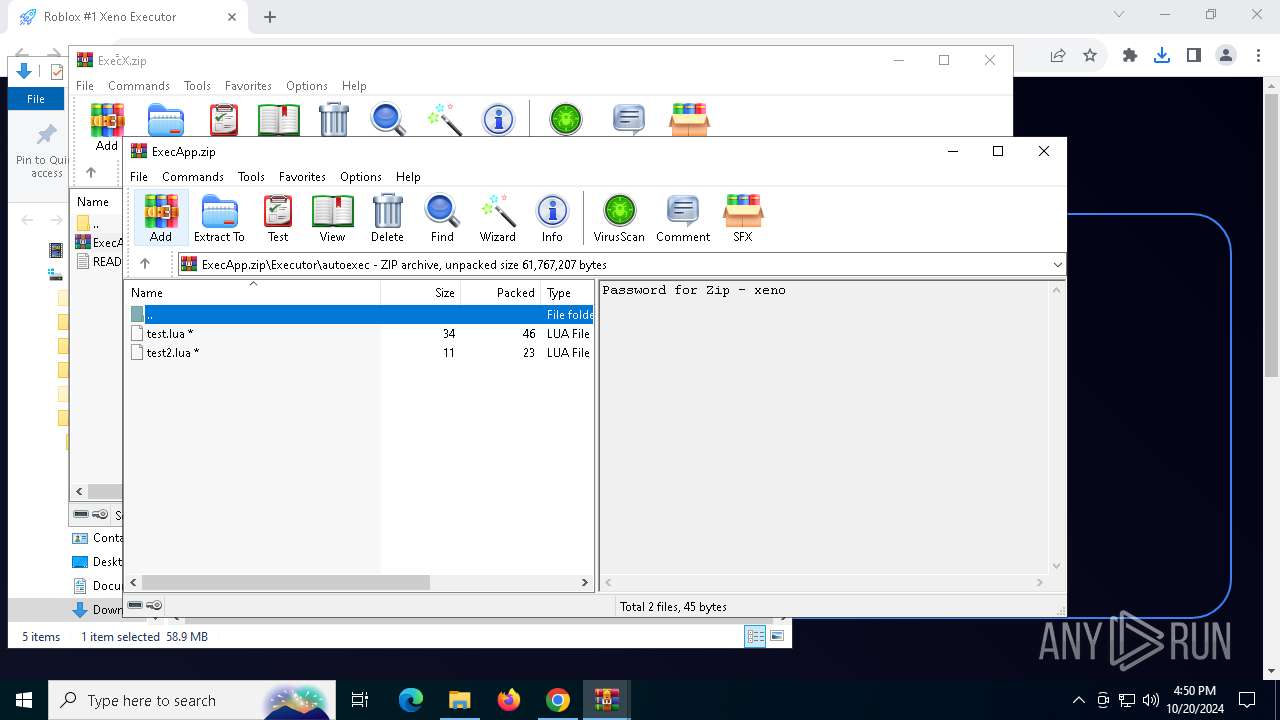
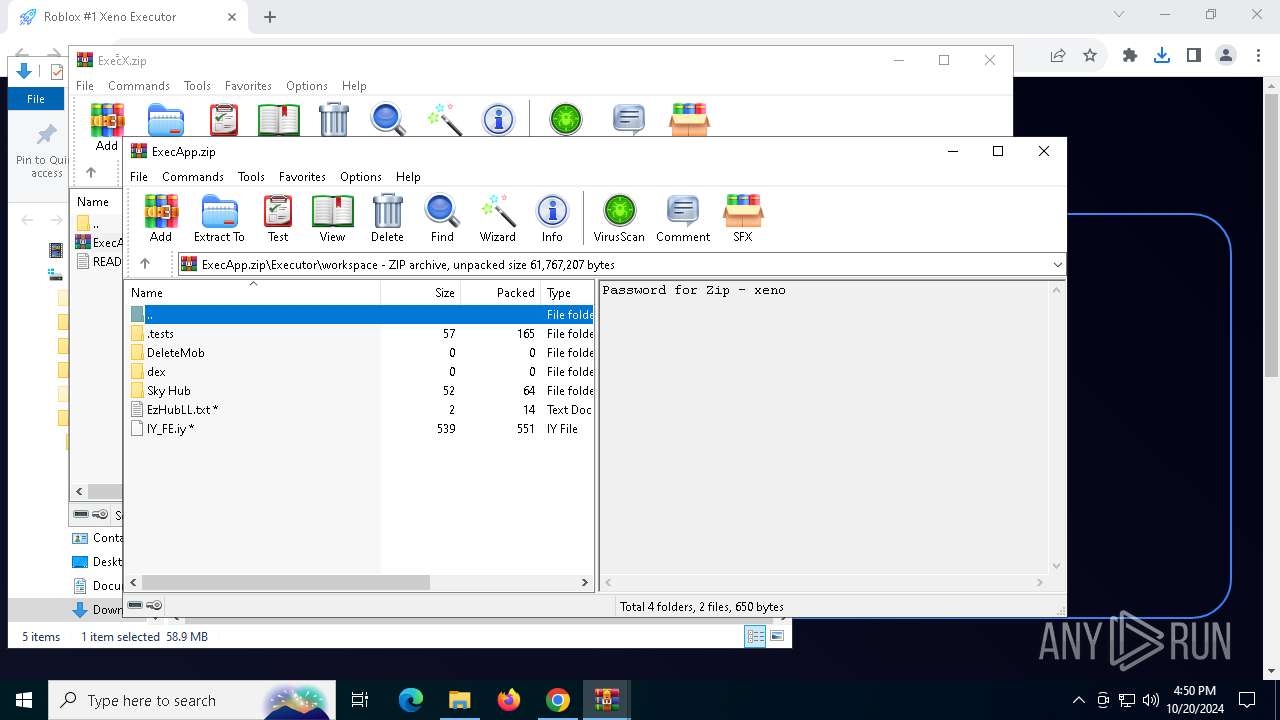
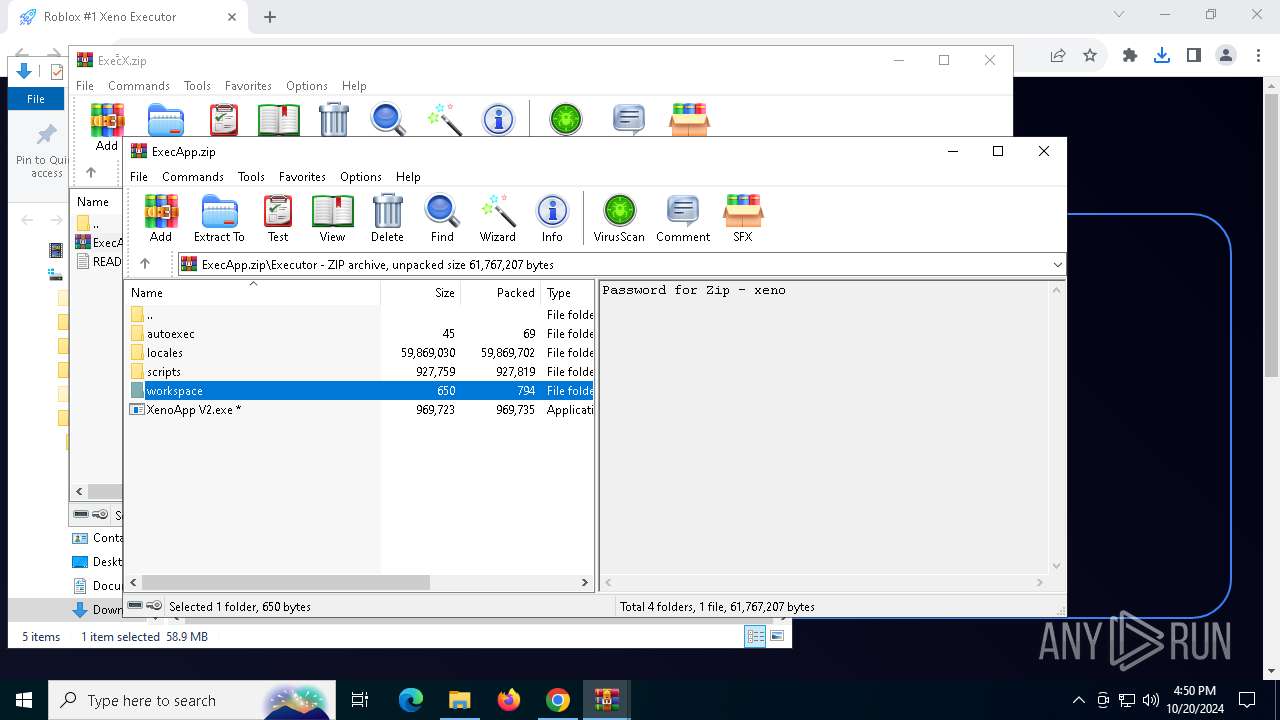
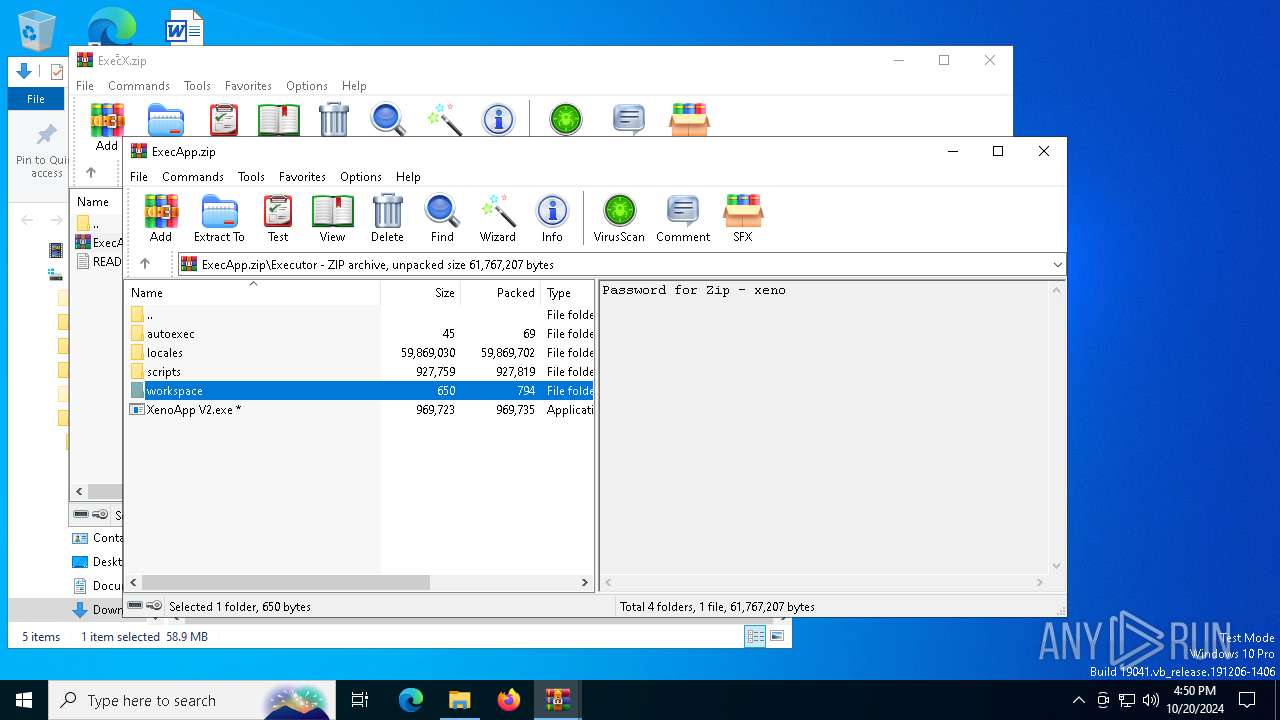
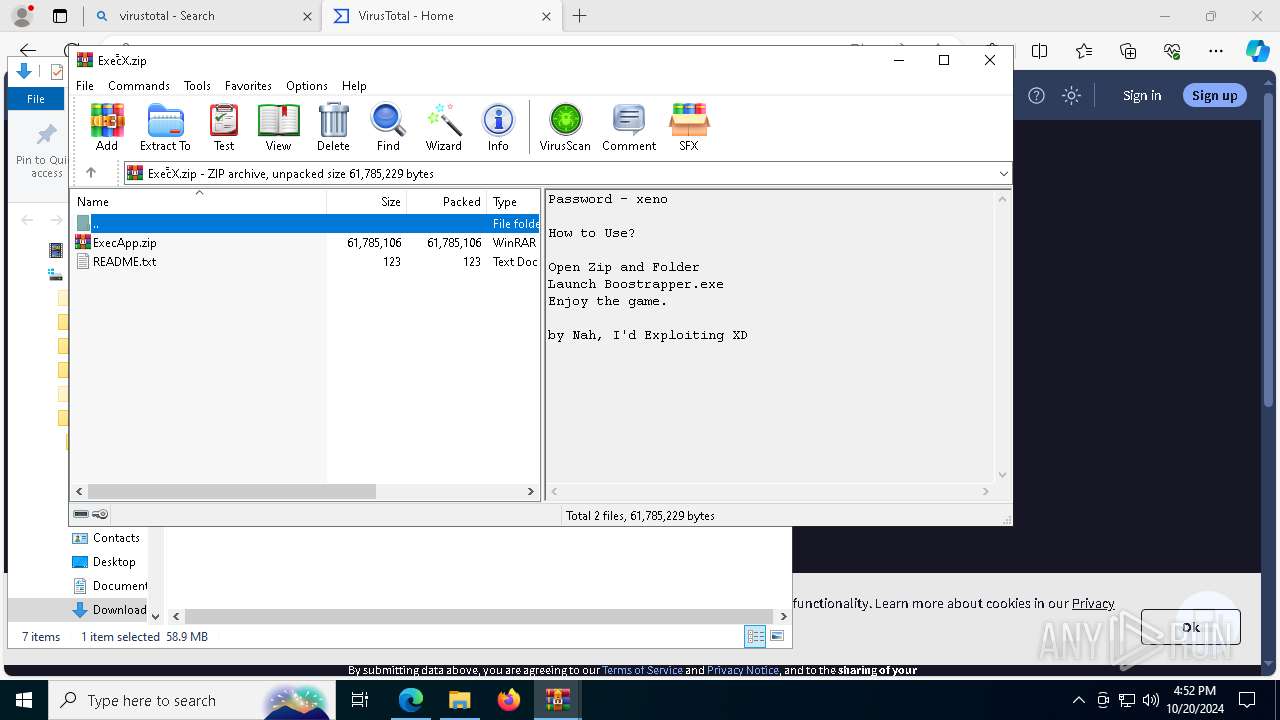
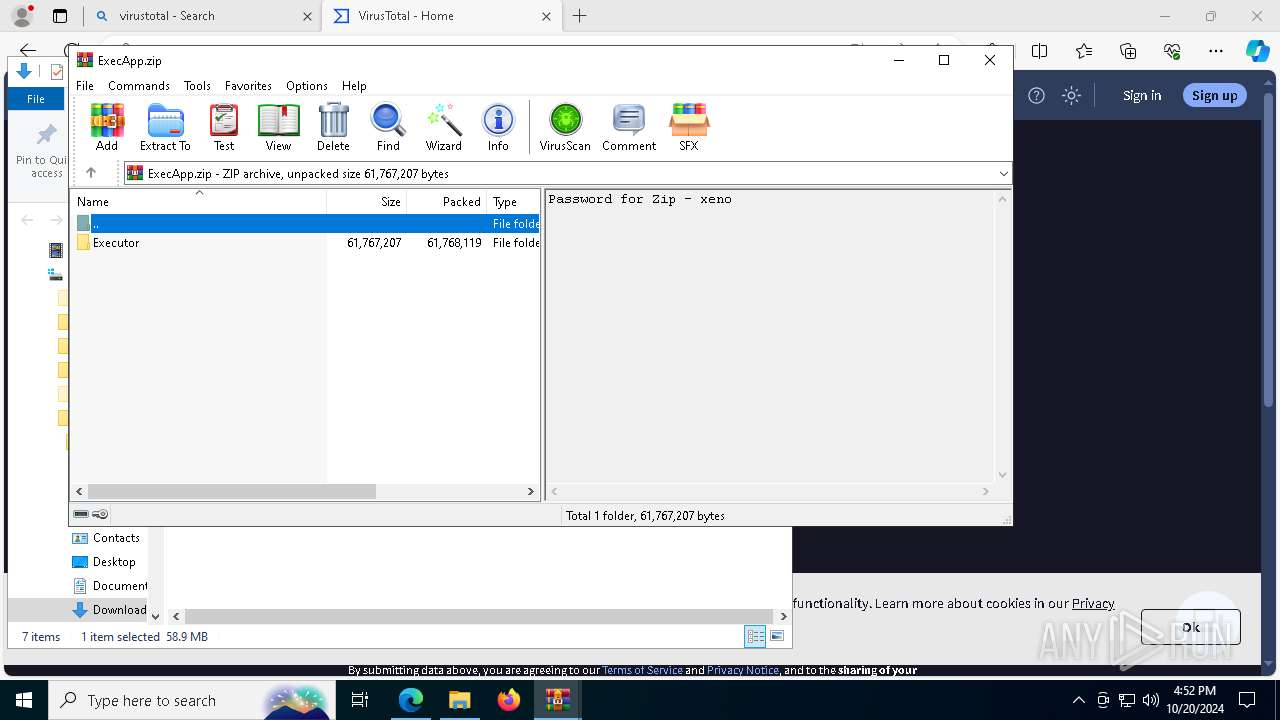
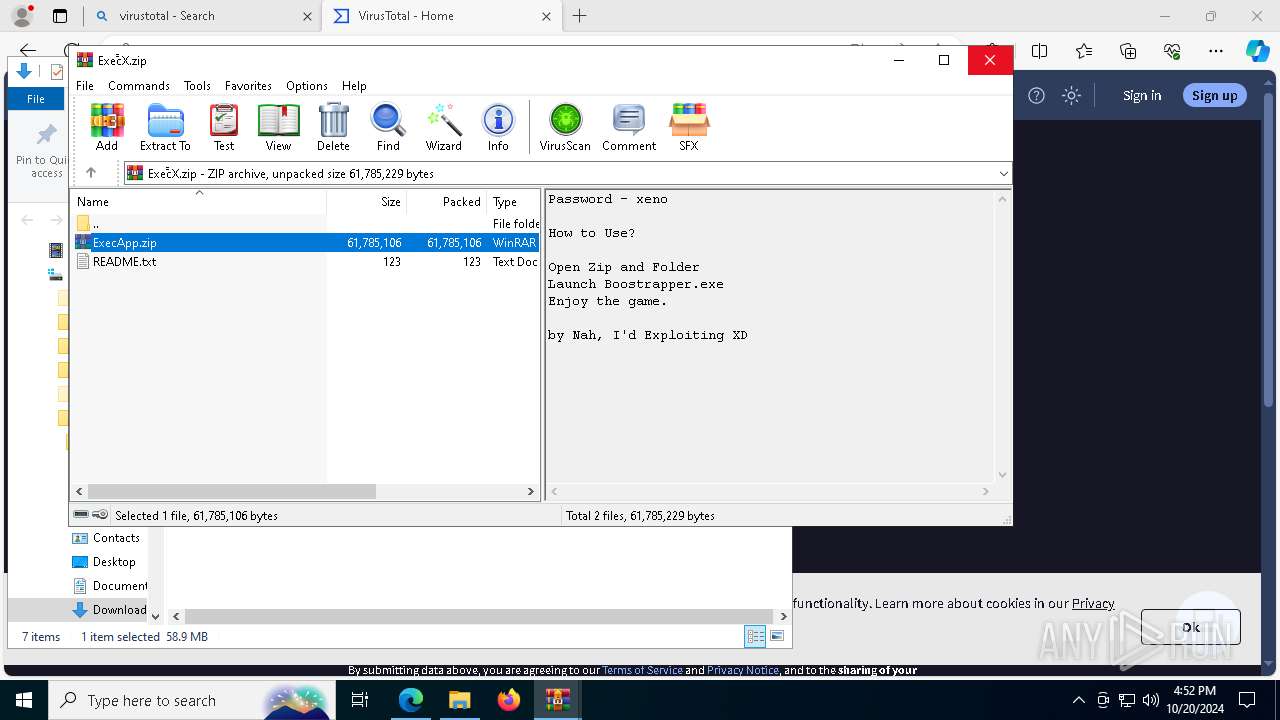
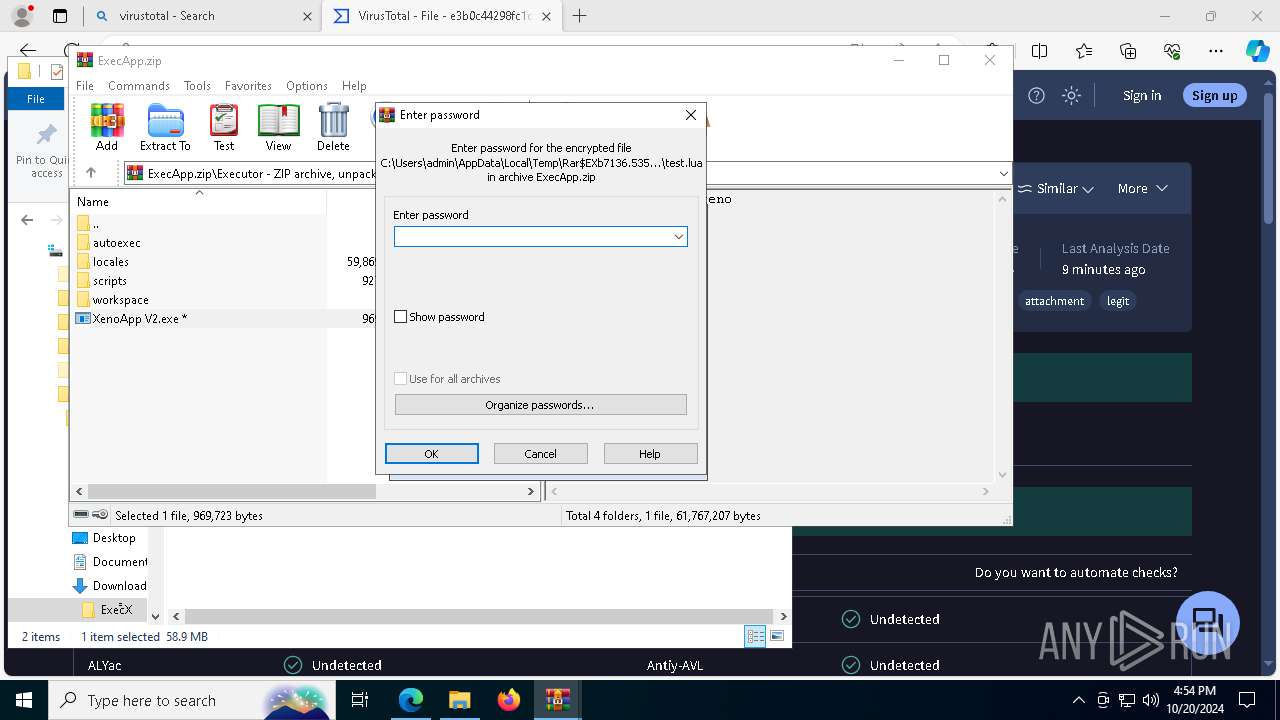
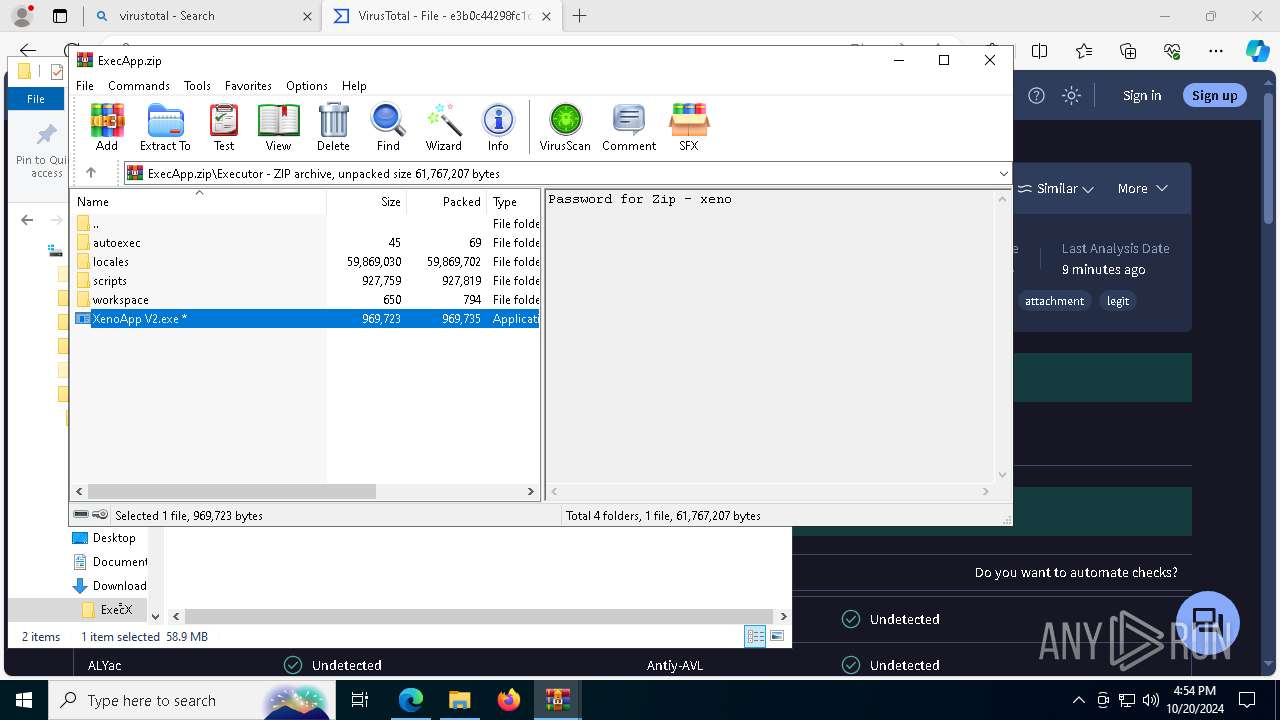
| URL: | deveonyx.cc/xeno |
| Full analysis: | https://app.any.run/tasks/a6ad8b54-e7fb-49be-86bc-00828d7a2be4 |
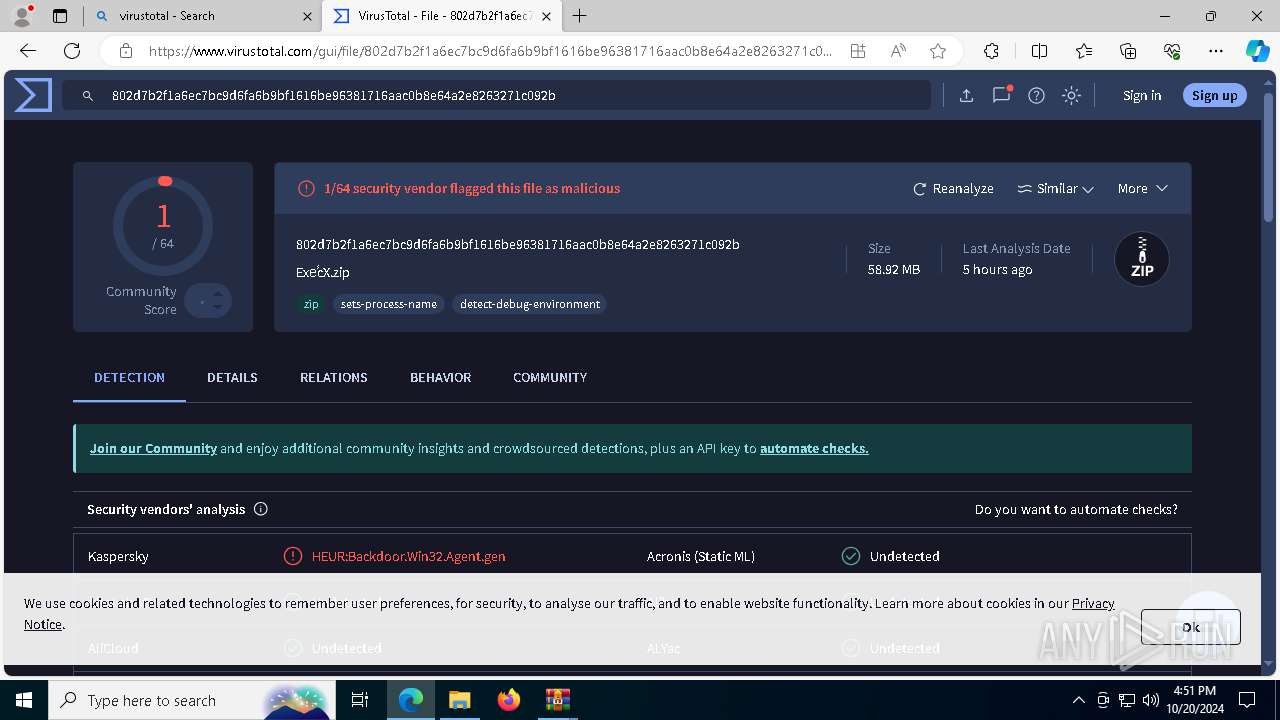
| Verdict: | Malicious activity |
| Threats: | MetaStealer is an info-stealing malware primarily targeting sensitive data like login credentials, payment details, and browser history. It typically infects systems via phishing emails or malicious downloads and can exfiltrate data to a command and control (C2) server. MetaStealer is known for its stealthy techniques, including evasion and persistence mechanisms, which make it difficult to detect. This malware has been actively used in various cyberattacks, particularly for financial theft and credential harvesting from individuals and organizations. |
| Analysis date: | October 20, 2024, 16:49:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7A46FFCF1A0D70B680FFEDFD8E404D8E |
| SHA1: | 444F605E345357F6A689258265745F2689CE363F |
| SHA256: | 2EF456C0C4CB57F96CC6A5DCC7C072B3B0245C100F56BEA37F2F6031E420B504 |
| SSDEEP: | 3:5KodLRbK:5KoJtK |
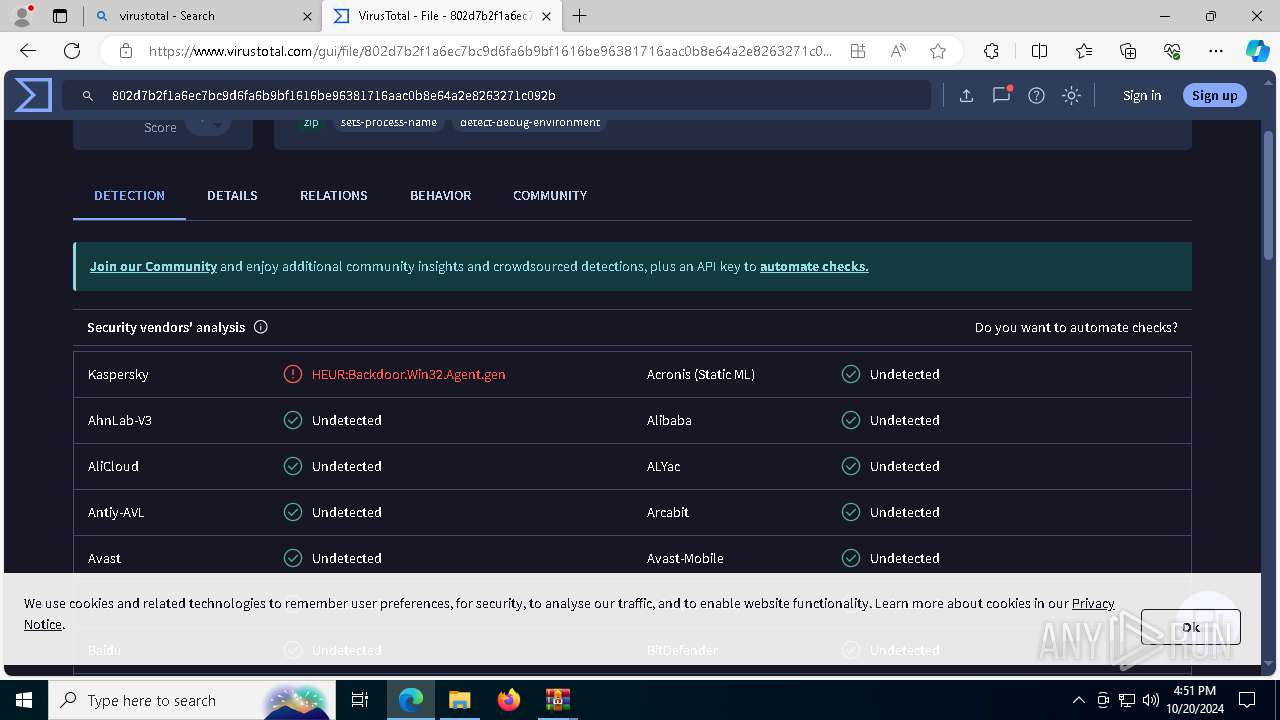
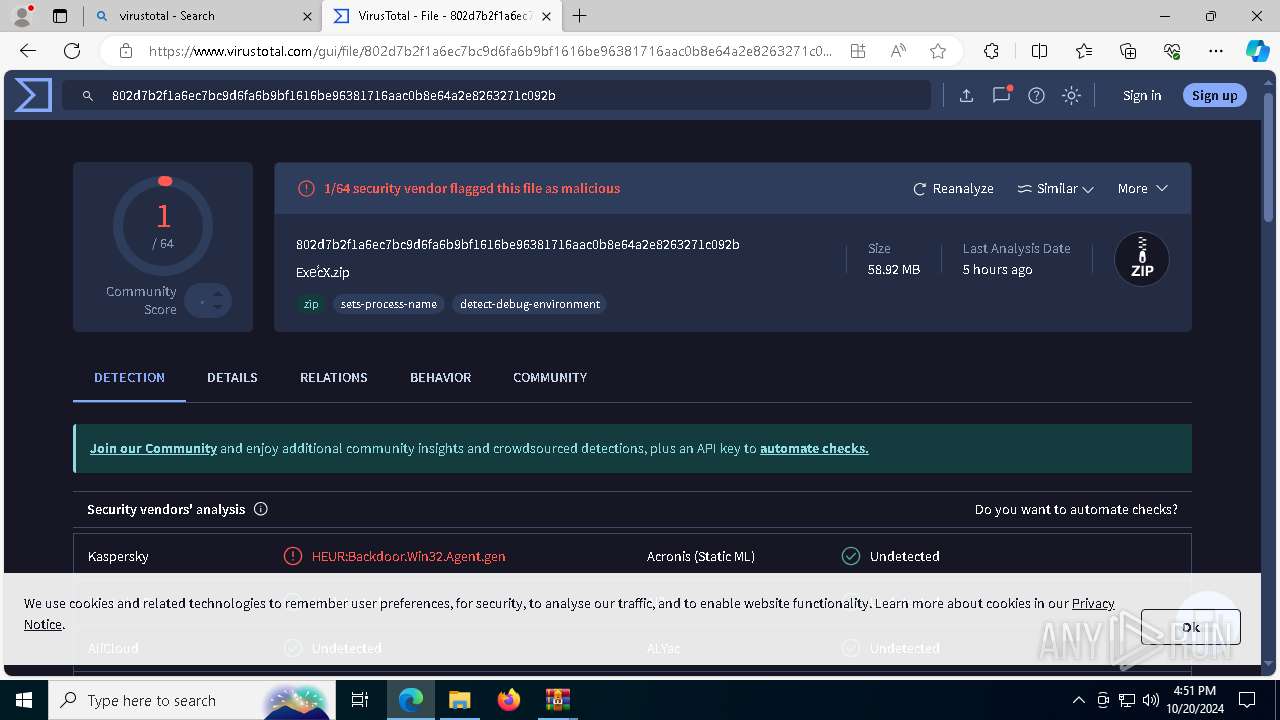
MALICIOUS
Connects to the CnC server
- RegAsm.exe (PID: 8108)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 8108)
METASTEALER has been detected (SURICATA)
- RegAsm.exe (PID: 8108)
REDLINE has been detected (YARA)
- RegAsm.exe (PID: 8108)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 8108)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 8108)
SUSPICIOUS
Loads DLL from Mozilla Firefox
- default-browser-agent.exe (PID: 7396)
The process executes via Task Scheduler
- default-browser-agent.exe (PID: 7396)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6792)
- WinRAR.exe (PID: 7284)
- XenoApp V2.exe (PID: 7692)
- WinRAR.exe (PID: 6176)
Application launched itself
- WinRAR.exe (PID: 6792)
- cmd.exe (PID: 712)
- WinRAR.exe (PID: 6176)
- cmd.exe (PID: 8060)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 712)
- cmd.exe (PID: 8060)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 712)
- XenoApp V2.exe (PID: 5444)
- cmd.exe (PID: 8060)
- XenoApp V2.exe (PID: 7692)
Get information on the list of running processes
- cmd.exe (PID: 712)
- cmd.exe (PID: 8060)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 712)
Starts application with an unusual extension
- cmd.exe (PID: 712)
- cmd.exe (PID: 8060)
Executable content was dropped or overwritten
- cmd.exe (PID: 712)
- Democracy.pif (PID: 7908)
The executable file from the user directory is run by the CMD process
- Democracy.pif (PID: 7908)
- Democracy.pif (PID: 8128)
Process drops legitimate windows executable
- Democracy.pif (PID: 7908)
The process creates files with name similar to system file names
- Democracy.pif (PID: 7908)
Executing commands from a ".bat" file
- XenoApp V2.exe (PID: 7692)
- XenoApp V2.exe (PID: 5444)
Starts a Microsoft application from unusual location
- RegAsm.exe (PID: 8108)
Connects to unusual port
- RegAsm.exe (PID: 8108)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6792)
- RegAsm.exe (PID: 8108)
- msedge.exe (PID: 3912)
- WinRAR.exe (PID: 7196)
- WinRAR.exe (PID: 6176)
- WinRAR.exe (PID: 7136)
- WinRAR.exe (PID: 3932)
- WinRAR.exe (PID: 5276)
- WinRAR.exe (PID: 7840)
Checks supported languages
- default-browser-agent.exe (PID: 7396)
- XenoApp V2.exe (PID: 7692)
- Democracy.pif (PID: 7908)
- RegAsm.exe (PID: 8108)
- identity_helper.exe (PID: 1440)
The process uses the downloaded file
- chrome.exe (PID: 7852)
- WinRAR.exe (PID: 6792)
- WinRAR.exe (PID: 7284)
- XenoApp V2.exe (PID: 7692)
- WinRAR.exe (PID: 7196)
- WinRAR.exe (PID: 6176)
- WinRAR.exe (PID: 3932)
- WinRAR.exe (PID: 5276)
Application launched itself
- chrome.exe (PID: 5756)
- firefox.exe (PID: 7520)
- msedge.exe (PID: 3912)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7284)
- chrome.exe (PID: 2796)
- msedge.exe (PID: 7060)
- WinRAR.exe (PID: 7136)
Reads the computer name
- XenoApp V2.exe (PID: 7692)
- Democracy.pif (PID: 7908)
- RegAsm.exe (PID: 8108)
- identity_helper.exe (PID: 1440)
Process checks computer location settings
- XenoApp V2.exe (PID: 7692)
Creates a new folder
- cmd.exe (PID: 7892)
- cmd.exe (PID: 1432)
Reads mouse settings
- Democracy.pif (PID: 7908)
Create files in a temporary directory
- Democracy.pif (PID: 7908)
- XenoApp V2.exe (PID: 7692)
Reads the machine GUID from the registry
- RegAsm.exe (PID: 8108)
Creates files or folders in the user directory
- RegAsm.exe (PID: 8108)
Reads the software policy settings
- slui.exe (PID: 8172)
- slui.exe (PID: 7508)
Reads Environment values
- identity_helper.exe (PID: 1440)
Checks proxy server information
- slui.exe (PID: 7508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(8108) RegAsm.exe
C2 (1)185.196.9.26:6302
Botnet@dxrkl0rd
Options
ErrorMessage
Keys
XorFootguards
Total processes
260
Monitored processes
116
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5976 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 712 | "C:\Windows\System32\cmd.exe" /c copy Issn Issn.bat & Issn.bat | C:\Windows\SysWOW64\cmd.exe | XenoApp V2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1176 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7656 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1200 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5848 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1432 | cmd /c md 639817 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6588 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1440 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1576 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=33 --mojo-platform-channel-handle=7128 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1732 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6492 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1340 --field-trial-handle=2360,i,2254401935671407282,17569867485650079286,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
26 342
Read events
26 208
Write events
121
Delete events
13
Modification events
| (PID) Process: | (5756) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5756) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5756) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5756) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5756) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000131C4B121023DB01 | |||
| (PID) Process: | (6792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\ExеًсX.zip | |||
| (PID) Process: | (6792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6792) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
47
Suspicious files
1 079
Text files
269
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF8bfed.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF8bfed.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF8bfed.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF8bfed.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF8bfed.TMP | — | |
MD5:— | SHA256:— | |||
| 5756 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
210
DNS requests
240
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7744 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7744 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6324 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7356 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7356 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7356 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7356 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7356 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7356 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1752 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5756 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6444 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
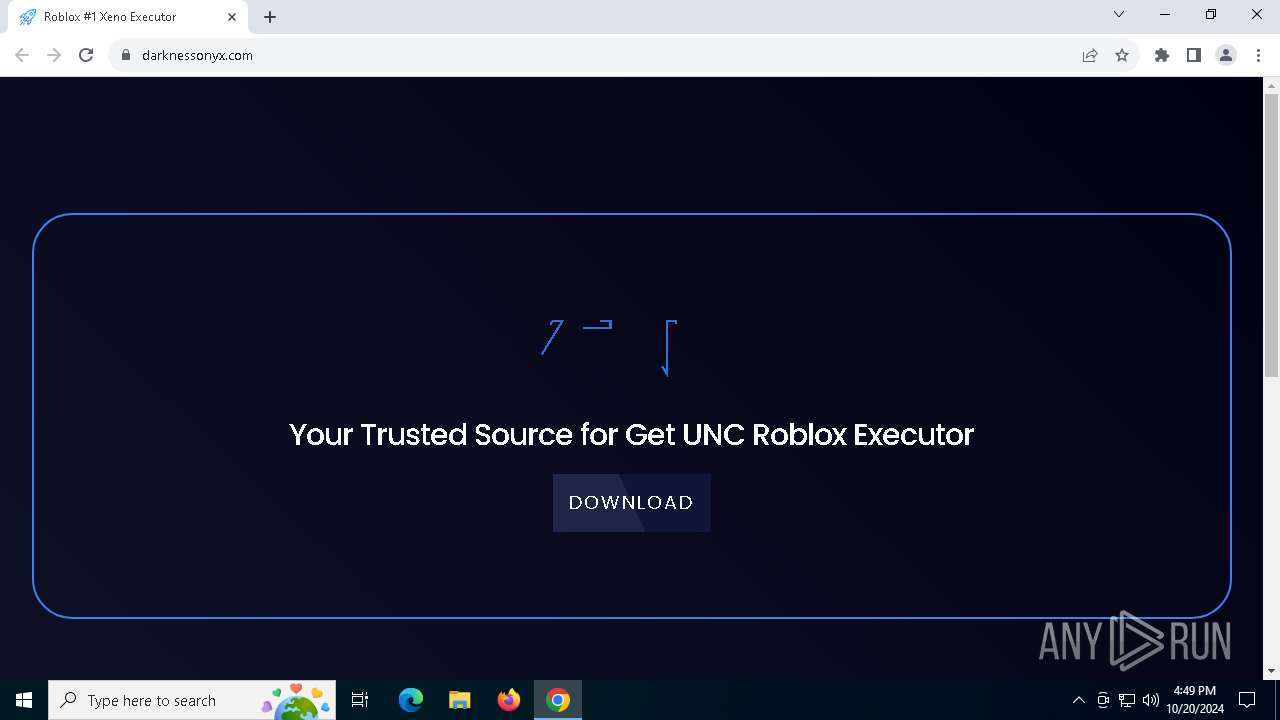
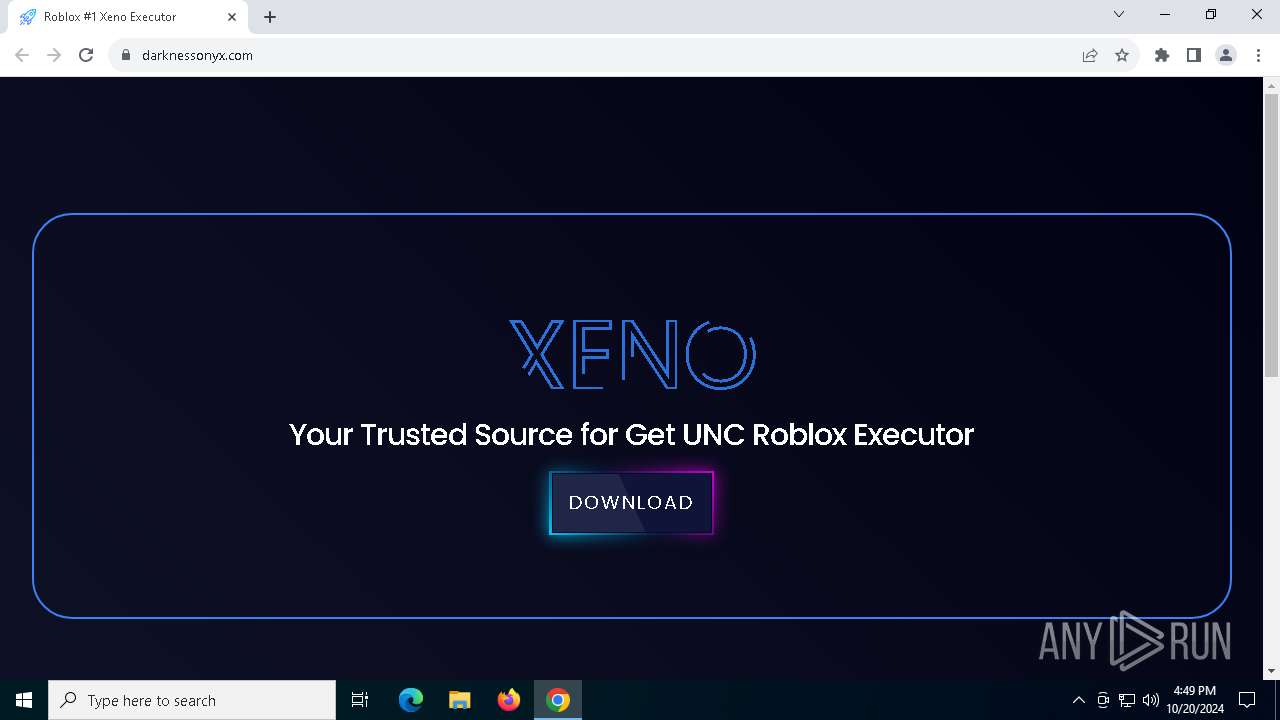
6444 | chrome.exe | 172.67.196.169:443 | deveonyx.cc | CLOUDFLARENET | US | unknown |
6444 | chrome.exe | 185.212.130.204:443 | darknessonyx.com | IT WEB LTD | VG | unknown |
6444 | chrome.exe | 151.101.65.229:443 | cdn.jsdelivr.net | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
deveonyx.cc |
| unknown |
accounts.google.com |
| whitelisted |
darknessonyx.com |
| unknown |
cdn.jsdelivr.net |
| whitelisted |
cdn.tailwindcss.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6444 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6444 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6444 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6444 | chrome.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6444 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6444 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
6444 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6444 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6444 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6444 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |