| URL: | https://openbullet.store/ |
| Full analysis: | https://app.any.run/tasks/9a021971-a497-4380-bb85-c1f0dabc7569 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | February 21, 2020, 14:17:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3F4A1493EB09A419542AE564C3AFC0E9 |
| SHA1: | 052C5657B085D34D3852F28B7780916E126C1DDA |
| SHA256: | 2ECF9BB24C74E4E86B372EF06DB1F02E17468DECD9B9334DEA2A9E731F6461B6 |
| SSDEEP: | 3:N8cuHVv:2cuHx |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3548)
- GoogleChrome.exe (PID: 1028)
- GoogleChrome.exe (PID: 3244)
Application was dropped or rewritten from another process
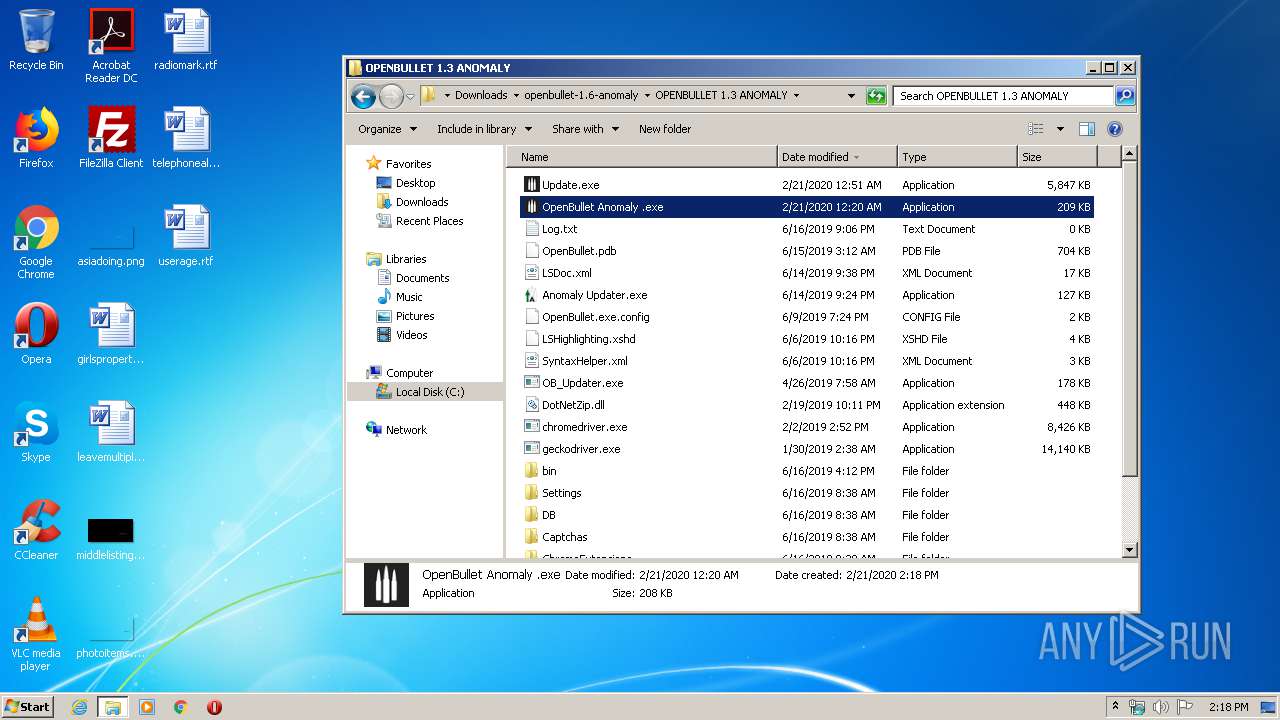
- OpenBullet Anomaly .exe (PID: 2124)
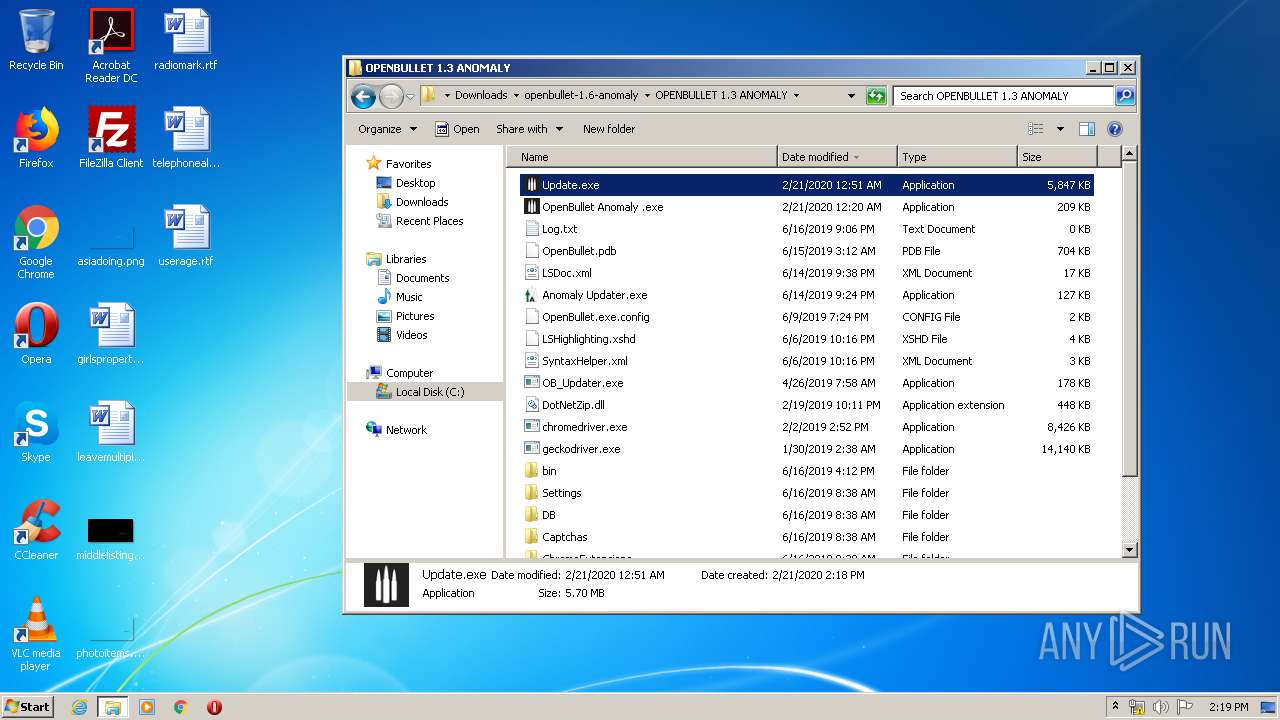
- Update.exe (PID: 3084)
- Update.exe (PID: 2160)
- OpenBullet Anomaly .exe (PID: 3108)
- Update.exe (PID: 3924)
- Update.exe (PID: 3524)
- Update.exe (PID: 3492)
- Update.exe (PID: 4052)
- Update.exe (PID: 2844)
- Update.exe (PID: 348)
- GoogleChrome.exe (PID: 3244)
- GoogleChrome.exe (PID: 1028)
Writes to a start menu file
- OpenBullet Anomaly .exe (PID: 2124)
Looks like application has launched a miner
- Update.exe (PID: 348)
Connects to CnC server
- GoogleChrome.exe (PID: 1028)
- GoogleChrome.exe (PID: 3244)
Changes the autorun value in the registry
- Update.exe (PID: 348)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3144)
Creates files in the user directory
- OpenBullet Anomaly .exe (PID: 2124)
- Update.exe (PID: 348)
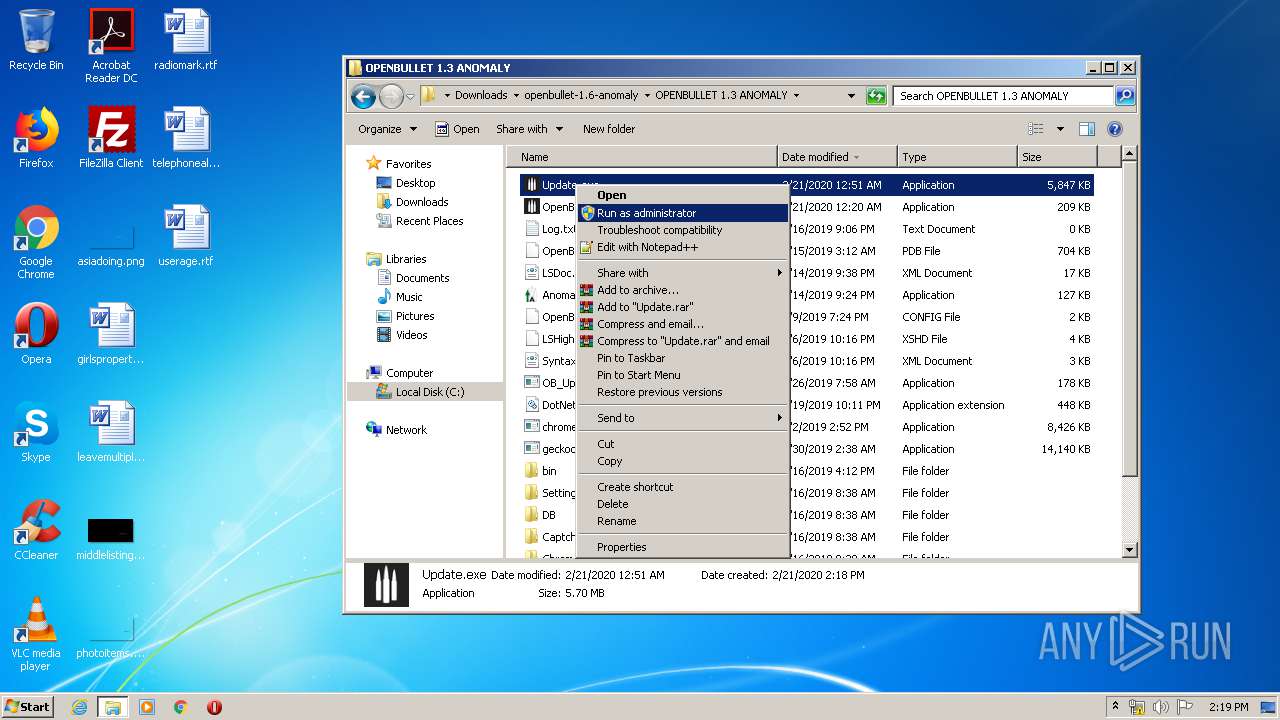
Application launched itself
- OpenBullet Anomaly .exe (PID: 2124)
- Update.exe (PID: 3084)
- Update.exe (PID: 2844)
Executable content was dropped or overwritten
- Update.exe (PID: 348)
- WinRAR.exe (PID: 1500)
Connects to unusual port
- GoogleChrome.exe (PID: 1028)
- GoogleChrome.exe (PID: 3244)
INFO
Application launched itself
- chrome.exe (PID: 3144)
Reads the hosts file
- chrome.exe (PID: 952)
- chrome.exe (PID: 3144)
Manual execution by user
- WinRAR.exe (PID: 1500)
- OpenBullet Anomaly .exe (PID: 2124)
- Update.exe (PID: 3084)
- Update.exe (PID: 2844)
Reads Internet Cache Settings
- chrome.exe (PID: 3144)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
90
Monitored processes
47
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=4842288746164901683 --mojo-platform-channel-handle=1068 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13409825364490510653 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4456 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
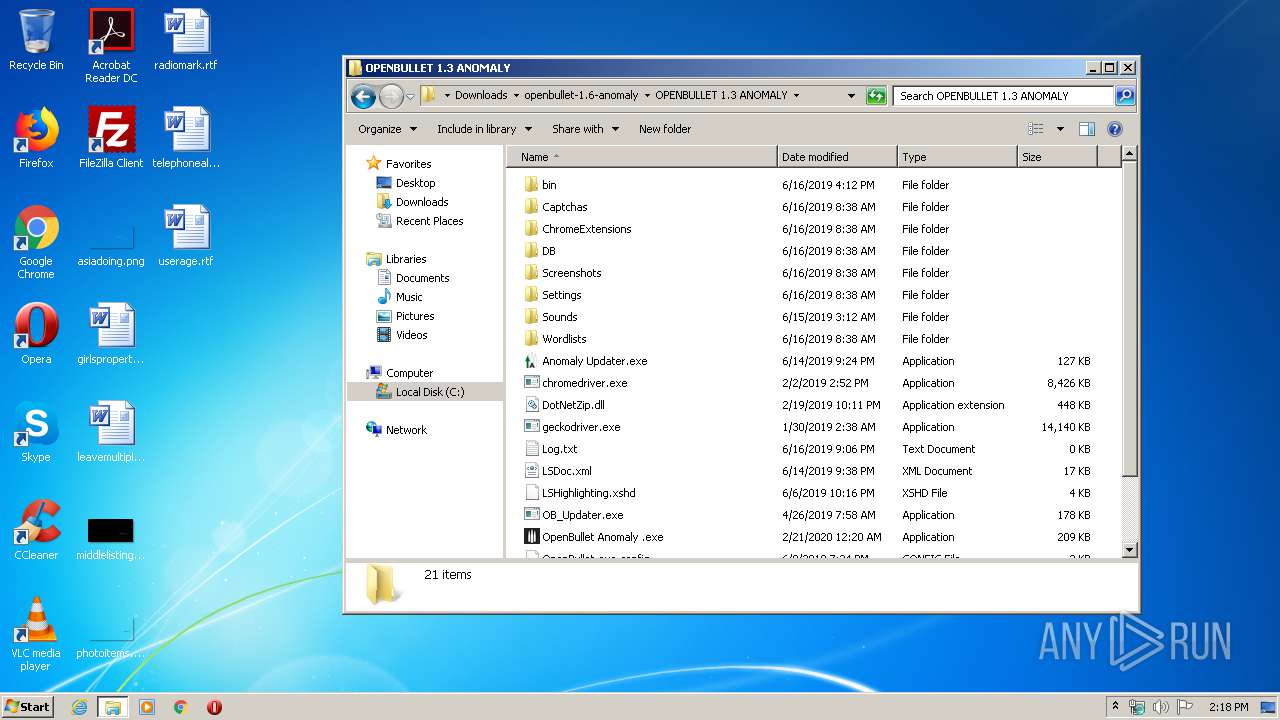
| 348 | "C:\Users\admin\Downloads\openbullet-1.6-anomaly\OPENBULLET 1.3 ANOMALY\Update.exe" | C:\Users\admin\Downloads\openbullet-1.6-anomaly\OPENBULLET 1.3 ANOMALY\Update.exe | Update.exe | ||||||||||||
User: admin Company: MPC-HC Team Integrity Level: MEDIUM Description: MPC-HC.1.7.13.x64 Exit code: 0 Version: 4.6.5.6 Modules
| |||||||||||||||
| 852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3054449828178363845 --mojo-platform-channel-handle=2056 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=17113336225704085878 --mojo-platform-channel-handle=1560 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | -o stratum+tcp://btc.viabtc.com:3333 -u zipix.001 -p x -a sha256d | C:\Users\admin\AppData\Roaming\Google\GoogleChrome.exe | Update.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1500 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\openbullet-1.6-anomaly.rar" C:\Users\admin\Downloads\openbullet-1.6-anomaly\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11057778038969303497 --mojo-platform-channel-handle=5204 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3866554222974402661 --mojo-platform-channel-handle=2456 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,10596789459854590459,10455669666248413247,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13343803360777961207 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3836 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 714
Read events
1 606
Write events
103
Delete events
5
Modification events
| (PID) Process: | (3200) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3144-13226768274121875 |
Value: 259 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
149
Suspicious files
88
Text files
294
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E4FE692-C48.pma | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\fcba535a-faad-43ee-a06d-fc7c220cc8af.tmp | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RFa65e74.TMP | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa65f7d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
53
DNS requests
39
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
952 | chrome.exe | GET | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 520 b | whitelisted |
952 | chrome.exe | GET | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 515 b | whitelisted |
952 | chrome.exe | GET | 200 | 87.245.200.147:80 | http://r8---sn-gxuog0-n8vl.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=85.206.166.82&mm=28&mn=sn-gxuog0-n8vl&ms=nvh&mt=1582294396&mv=u&mvi=7&pl=23&shardbypass=yes | RU | crx | 293 Kb | whitelisted |
952 | chrome.exe | GET | 200 | 87.245.200.144:80 | http://r5---sn-gxuog0-n8vl.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=85.206.166.82&mm=28&mn=sn-gxuog0-n8vl&ms=nvh&mt=1582294396&mv=u&mvi=4&pl=23&shardbypass=yes | RU | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
952 | chrome.exe | 104.18.59.174:443 | openbullet.store | Cloudflare Inc | US | suspicious |
952 | chrome.exe | 172.217.22.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
952 | chrome.exe | 104.17.65.4:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | unknown |
952 | chrome.exe | 104.26.14.104:443 | shoppy.gg | Cloudflare Inc | US | unknown |
952 | chrome.exe | 172.217.23.109:443 | accounts.google.com | Google Inc. | US | suspicious |
952 | chrome.exe | 74.125.140.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
952 | chrome.exe | 172.217.22.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
952 | chrome.exe | 216.58.207.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
952 | chrome.exe | 172.217.22.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
952 | chrome.exe | 216.58.207.36:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
openbullet.store |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
shoppy.gg |
| malicious |
fonts.gstatic.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
Threats
4 ETPRO signatures available at the full report