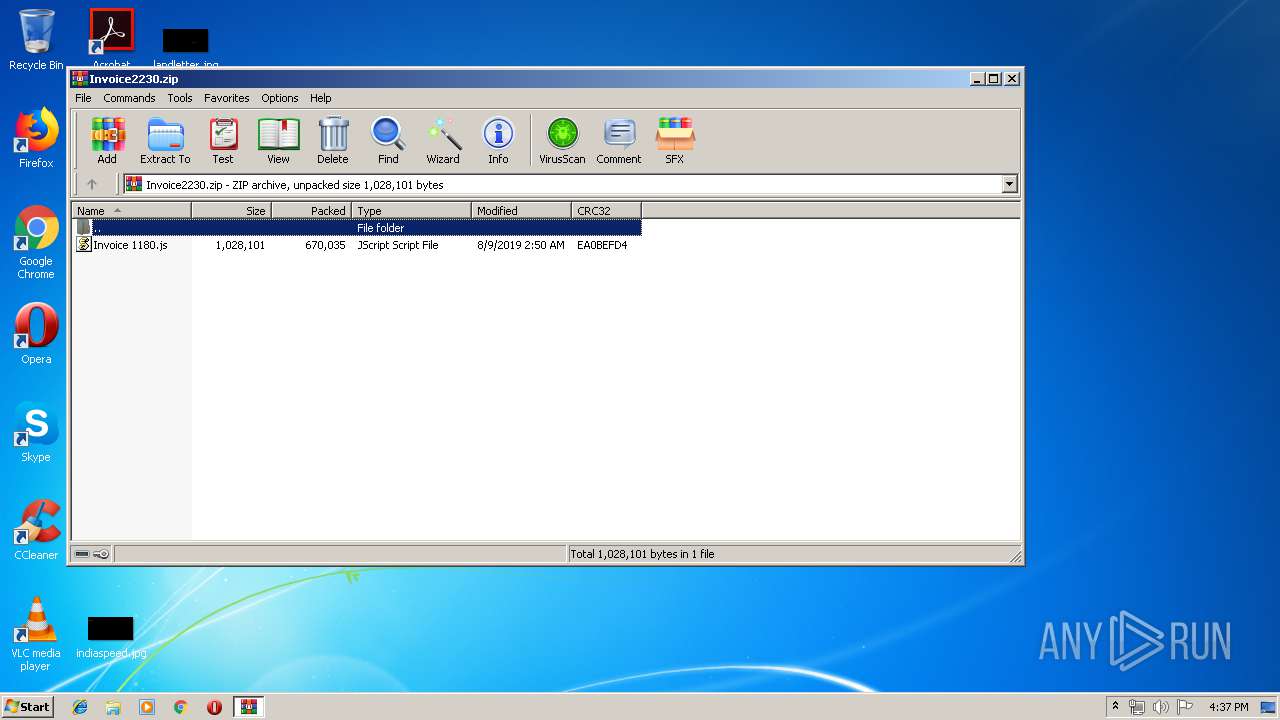
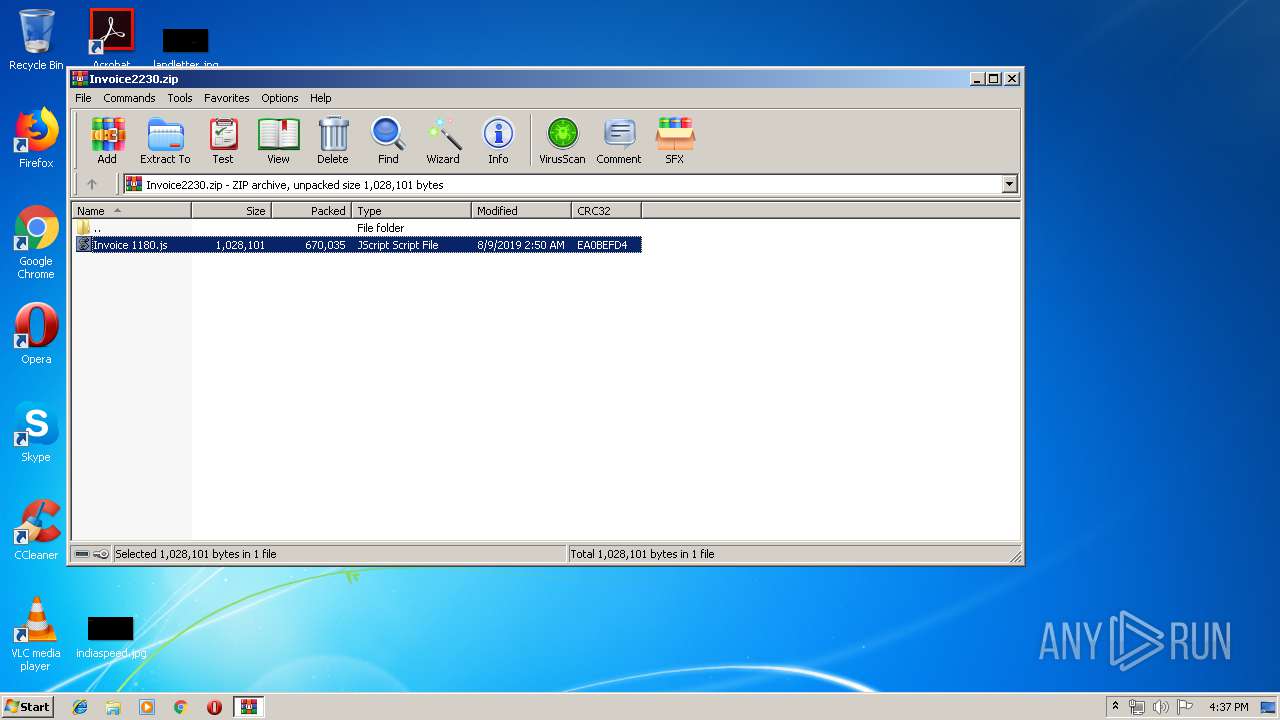
| download: | Invoice2230.zip |
| Full analysis: | https://app.any.run/tasks/bad75944-2aad-42a0-bcfb-6fbd6bd274ac |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | August 13, 2019, 15:36:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 825D349347D39EA3D83013CF9EF2D2FB |
| SHA1: | D5A2DC80098F5805F4B7E6D7FCD158234ACDAEE2 |
| SHA256: | 2ECBA2D985DF9C35ED87326E8944132964DC791012BE367248A6F922639FB574 |
| SSDEEP: | 12288:jWieAYnyp3c994L3wCNc9L5BkXOX/uNsIhwPbdClzhUhoUt+i:jpqno3Qy3wCuBk+vMfhubslehX5 |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 3268)
- java.exe (PID: 2504)
- WScript.exe (PID: 1244)
- java.exe (PID: 2204)
- javaw.exe (PID: 2572)
Application was dropped or rewritten from another process
- java.exe (PID: 2504)
- javaw.exe (PID: 3268)
- javaw.exe (PID: 2572)
- java.exe (PID: 2204)
Changes the autorun value in the registry
- reg.exe (PID: 2988)
- WScript.exe (PID: 4068)
AdWind was detected
- java.exe (PID: 2204)
- java.exe (PID: 2504)
UAC/LUA settings modification
- regedit.exe (PID: 4032)
Uses TASKKILL.EXE to kill security tools
- javaw.exe (PID: 2572)
WSHRAT was detected
- WScript.exe (PID: 4068)
Turns off system restore
- regedit.exe (PID: 4032)
Connects to CnC server
- WScript.exe (PID: 4068)
Changes Image File Execution Options
- regedit.exe (PID: 4032)
Writes to a start menu file
- WScript.exe (PID: 4068)
SUSPICIOUS
Application launched itself
- WScript.exe (PID: 1244)
Creates files in the user directory
- WScript.exe (PID: 1244)
- WScript.exe (PID: 4068)
- xcopy.exe (PID: 4028)
- javaw.exe (PID: 3268)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3268)
- java.exe (PID: 2504)
- java.exe (PID: 2204)
- javaw.exe (PID: 2572)
Executes scripts
- cmd.exe (PID: 2488)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 3796)
- cmd.exe (PID: 3288)
- WinRAR.exe (PID: 2160)
- cmd.exe (PID: 3160)
- cmd.exe (PID: 3860)
- cmd.exe (PID: 3016)
- cmd.exe (PID: 3344)
- WScript.exe (PID: 1244)
Executes JAVA applets
- WScript.exe (PID: 1244)
- javaw.exe (PID: 3268)
Starts itself from another location
- javaw.exe (PID: 3268)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 3268)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 3268)
Executable content was dropped or overwritten
- xcopy.exe (PID: 4028)
- javaw.exe (PID: 2572)
Uses WMIC.EXE to obtain a system information
- javaw.exe (PID: 2572)
Uses TASKKILL.EXE to kill process
- javaw.exe (PID: 2572)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:08:09 02:50:13 |
| ZipCRC: | 0xea0befd4 |
| ZipCompressedSize: | 670035 |
| ZipUncompressedSize: | 1028101 |
| ZipFileName: | Invoice 1180.js |
Total processes
281
Monitored processes
130
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive5592489970407452072.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 272 | taskkill /IM fsgk32.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 276 | taskkill /IM capinfos.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 304 | taskkill /IM NisSrv.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive7583001329626857009.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 340 | taskkill /IM cavwp.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 592 | taskkill /IM escanpro.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 768 | taskkill /IM GdBgInx64.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 796 | taskkill /IM fshoster32.exe /T /F | C:\Windows\system32\taskkill.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 912 | regedit.exe /s C:\Users\admin\AppData\Local\Temp\gVIMDIoEwf8767031250345333778.reg | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 837
Read events
1 583
Write events
254
Delete events
0
Modification events
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Invoice2230.zip | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4804 |
Value: JScript Script File | |||
| (PID) Process: | (2160) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
111
Suspicious files
10
Text files
79
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1244 | WScript.exe | C:\Users\admin\AppData\Roaming\ttmPnejtED.js | text | |
MD5:— | SHA256:— | |||
| 2160 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2160.12546\Invoice 1180.js | text | |
MD5:— | SHA256:— | |||
| 1244 | WScript.exe | C:\Users\admin\AppData\Roaming\gblxsjccg.txt | java | |
MD5:— | SHA256:— | |||
| 3268 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2504 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 4068 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ttmPnejtED.js | text | |
MD5:— | SHA256:— | |||
| 3268 | javaw.exe | C:\Users\admin\AppData\Local\Temp\Retrive8781430371351909717.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
| 4028 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\release | text | |
MD5:1BCCC3A965156E53BE3136B3D583B7B6 | SHA256:03A4DB27DEA69374EFBAF121C332D0AF05840D16D0C1FBF127D00E65054B118A | |||
| 3268 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\83aa4cc77f591dfc2374580bbd95f6ba_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
| 2504 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive6976597835969152408.vbs | text | |
MD5:3BDFD33017806B85949B6FAA7D4B98E4 | SHA256:9DA575DD2D5B7C1E9BAB8B51A16CDE457B3371C6DCDB0537356CF1497FA868F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
1
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4068 | WScript.exe | POST | — | 67.207.93.17:7744 | http://pluginsrv.duckdns.org:7744/is-ready | US | — | — | malicious |
4068 | WScript.exe | POST | — | 67.207.93.17:7744 | http://pluginsrv.duckdns.org:7744/is-ready | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4068 | WScript.exe | 67.207.93.17:7744 | pluginsrv.duckdns.org | Digital Ocean, Inc. | US | malicious |
2572 | javaw.exe | 37.48.92.195:1350 | — | LeaseWeb Netherlands B.V. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pluginsrv.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1064 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2572 | javaw.exe | A Network Trojan was detected | AV TROJAN Malicious SSL certificate detected (Adwind Fake Oracle Cert) |
2572 | javaw.exe | A Network Trojan was detected | AV TROJAN Malicious SSL certificate detected (Adwind Fake Oracle Cert) |
2572 | javaw.exe | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.Java.Adwind.cu |
4068 | WScript.exe | A Network Trojan was detected | ET TROJAN WSHRAT CnC Checkin |
4068 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |
4068 | WScript.exe | A Network Trojan was detected | MALWARE [PTsecurity] KJw0rm/Dunihi.VBS.Worm |
4068 | WScript.exe | A Network Trojan was detected | ET TROJAN WSHRAT CnC Checkin |
4068 | WScript.exe | A Network Trojan was detected | ET TROJAN Worm.VBS Dunihi/Houdini/H-Worm Checkin 1 |
4068 | WScript.exe | A Network Trojan was detected | MALWARE [PTsecurity] KJw0rm/Dunihi.VBS.Worm |