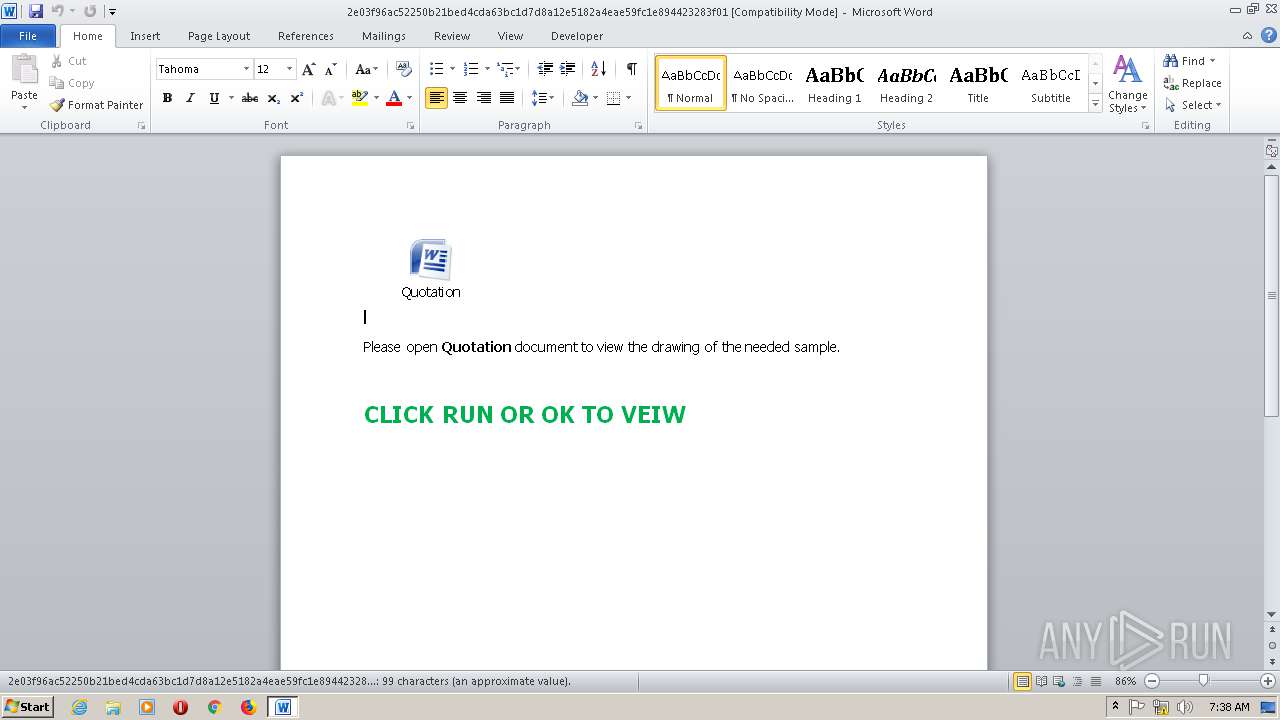
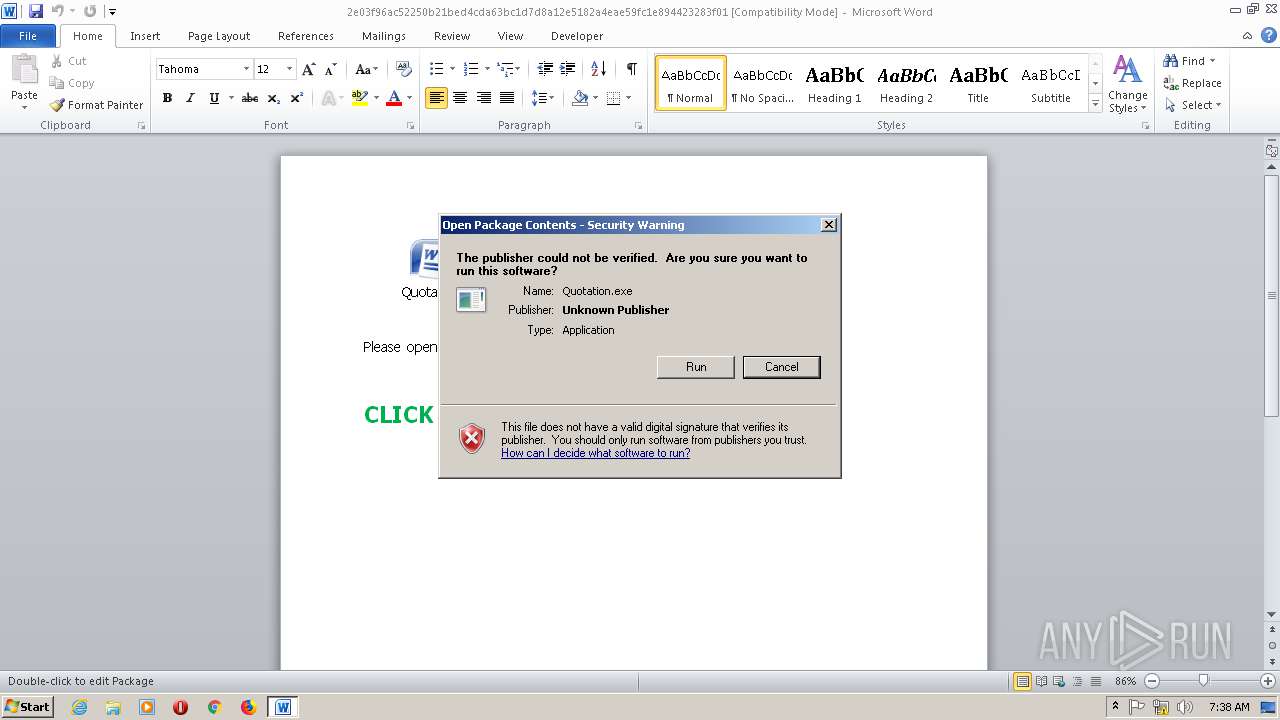
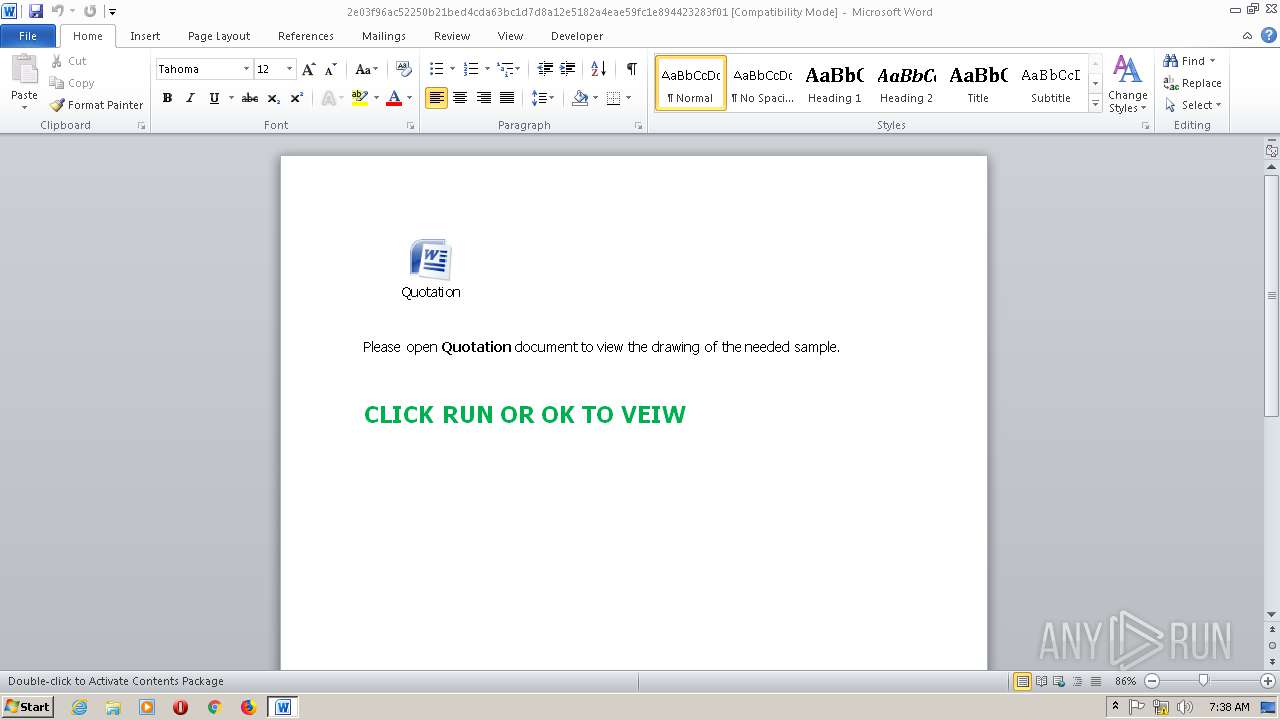
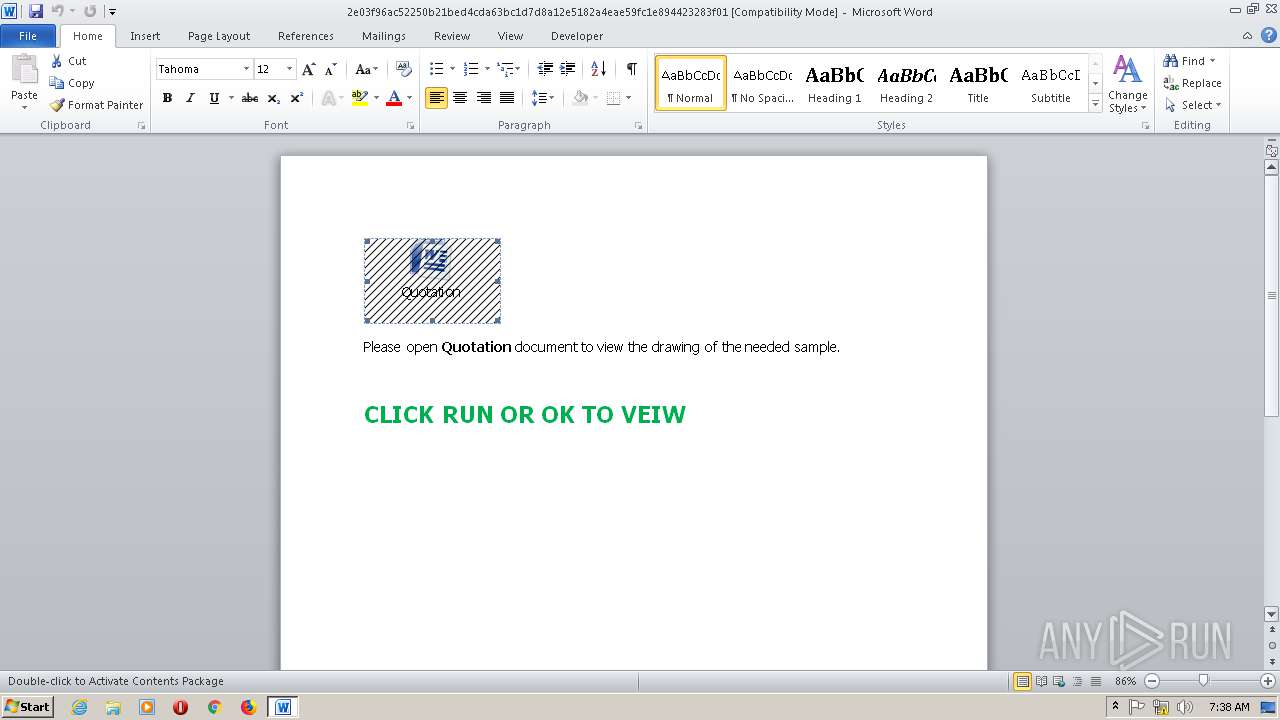
| File name: | 2e03f96ac52250b21bed4cda63bc1d7d8a12e5182a4eae59fc1e894423283f01.doc |
| Full analysis: | https://app.any.run/tasks/89d12a6d-1b09-4f39-bcc5-4cf88820d8e9 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 15, 2019, 07:37:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Black Panther, Template: Normal.dotm, Last Saved By: doggy, Revision Number: 5, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Tue May 14 22:15:00 2019, Last Saved Time/Date: Tue May 14 22:46:00 2019, Number of Pages: 1, Number of Words: 17, Number of Characters: 103, Security: 0 |
| MD5: | A80AF34921C58947921B109EC1DC0094 |
| SHA1: | B4E719FC583BC9EF8ED63BCAFB2B615AEAACC940 |
| SHA256: | 2E03F96AC52250B21BED4CDA63BC1D7D8A12E5182A4EAE59FC1E894423283F01 |
| SSDEEP: | 12288:kDquErHF6xC9D6DmR1J98w4oknqO/CyQf4TblfS3rygecr82yVLTASC/:prl6kD68JmlokQf4PlabygHyVLTAP/ |
MALICIOUS
Actions looks like stealing of personal data
- RegAsm.exe (PID: 1264)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2464)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2464)
Application was dropped or rewritten from another process
- Quotation.exe (PID: 896)
Changes the autorun value in the registry
- Quotation.exe (PID: 896)
AGENTTESLA was detected
- RegAsm.exe (PID: 1264)
SUSPICIOUS
Executable content was dropped or overwritten
- Quotation.exe (PID: 896)
Checks for external IP
- RegAsm.exe (PID: 1264)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2464)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2464)
Creates files in the user directory
- WINWORD.EXE (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Black Panther |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | doggy |
| RevisionNumber: | 5 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 3.0 minutes |
| CreateDate: | 2019:05:14 21:15:00 |
| ModifyDate: | 2019:05:14 21:46:00 |
| Pages: | 1 |
| Words: | 17 |
| Characters: | 103 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 119 |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 39 |
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
Total processes
35
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Users\admin\AppData\Local\Temp\Quotation.exe" | C:\Users\admin\AppData\Local\Temp\Quotation.exe | WINWORD.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1264 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | Quotation.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5483 (Win7SP1GDR.050727-5400) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\2e03f96ac52250b21bed4cda63bc1d7d8a12e5182a4eae59fc1e894423283f01.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
Total events
1 594
Read events
1 153
Write events
434
Delete events
7
Modification events
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | i{& |
Value: 697B2600A0090000010000000000000000000000 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320091690 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091774 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091775 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: A0090000221F6225F10AD50100000000 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ""& |
Value: 22222600A009000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | ""& |
Value: 22222600A009000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2464) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
2
Suspicious files
0
Text files
3
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR53D9.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\2e03f96ac52250b21bed4cda63bc1d7d8a12e5182a4eae59fc1e894423283f01.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Quotation.exe | executable | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8ACBCA88.emf | emf | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\Desktop\~$03f96ac52250b21bed4cda63bc1d7d8a12e5182a4eae59fc1e894423283f01.doc | pgc | |
MD5:— | SHA256:— | |||
| 896 | Quotation.exe | C:\Users\admin\sppsvc\windeploy.exe | executable | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Quotation.exe:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1264 | RegAsm.exe | GET | 200 | 52.206.161.133:80 | http://checkip.amazonaws.com/ | US | text | 16 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1264 | RegAsm.exe | 52.206.161.133:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
1264 | RegAsm.exe | 198.54.125.159:26 | mail.sonofgraceoffice.website | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail.sonofgraceoffice.website |
| malicious |
checkip.amazonaws.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1264 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] AgentTesla IP Check |
1264 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan-Spy.Keylogger.AgentTesla Exfiltration by SMTP |
3 ETPRO signatures available at the full report